#Cloud Monitoring Services
Explore tagged Tumblr posts
Text

Revolutionize your IT ecosystem by transitioning to the cloud and accelerate business growth. Our adept developers have honed their skills in crafting dynamic, robust, and resilient systems within a high-grade IT environment using efficient methodologies. Partner with the top cloud application development company to innovate and create tech products that offer next-level digital experiences. Cloud computing has firmly established itself in the IT landscape and has been dominating it for over a decade now.
Our Service Offerings
Cloud Assessment A robust cloud strategy customized to your business objectives can be the differentiator between establishing a sustainable competitive edge in a rapidly evolving digital landscape and potentially wasting investment. Our hyper-focused cloud consulting services expedite digital transformation
Managed Cloud The SBSC Cloud Managed Services offering introduces innovative strategies to tackle this challenge. As a seasoned Managed Services Partner with leading Cloud providers, we oversee all four dimensions of Cloud Management – Financial, Operational, Security/Compliance, and Technology.
Cloud Migration We expedite time-to-value with our near-zero risk cloud migration solutions. By utilizing a suite of industry-proven approaches, tools, and accelerators, we ensure that your cloud aspirations are aligned with a seamless digital transformation.
Cloud Native Apps Our cloud-native services enable digital enterprises to innovate, experiment, and scale rapidly in response to market demands. Leveraging Microservices, DevOps, Containers, and PaaS, we develop Cloud Native solutions that are both adaptable and secure.
Cloud Security Utilize our expertise in network, data, and application security to gain a competitive edge in the cloud space by developing customized Cloud Access Security Brokers automated testing solutions for compliance standards and Data Loss Prevention (DLP).
Monitoring and Maintenance As your one-stop solution for multiple cloud app development requirements, we provide SLA-driven ongoing support and maintenance to ensure your systems remain secure, bug-free, and evolve with the latest technological advancements.
Advantages Of SBSC Cloud Services
Best-fit: Cloud Solution to get high productivity and increase efficiency
Excellence: designing and implementing scalable architectures
Full Cycle: configuration, deployment, ongoing support and maintenance
Experience: Leveraging suitable platform features and optimized standards.
Don’t Hesitate To Contact With Us, We’ve Very Friendly
Call: +1 (877) 213 3835 Email: [email protected]
Website: https://www.sbsc.com
#cloud-based software#enterprise software development#industry specific solutions#it consulting#global software development#it solutions for healthcare#it solutions for finance#Assessment Servicesment#ecommerce solutions#cloud services#Cloud configuration Services#Cloud Maintenance Services#Cloud Migration Services#Cloud Monitoring Services#Cloud Native Apps#Cloud Security#Cloud Solution for business#Cloud-Based Software#Industry specific Cloud#Managed Cloud Services
0 notes
Text
Maximizing Efficiency and Security with the Best AWS Monitoring Service

Introduction to AWS Monitoring Service
As businesses continue to migrate their infrastructure to the cloud, it becomes crucial to have a robust monitoring system in place to ensure the efficient operation and security of their AWS environment. An AWS Monitoring Service is an essential tool that provides real-time insights into the performance, health, and security of your cloud infrastructure. In this article, we will explore the benefits of using an AWS Monitoring Service, the importance of monitoring your AWS cloud infrastructure, and the key features to look for in such a service.
Benefits of using an AWS Monitoring Service
Using an AWS Monitoring Service offers numerous benefits to businesses. Firstly, it provides real-time visibility into your AWS infrastructure, allowing you to monitor the performance of your applications and services. With this information at hand, you can proactively identify and address any issues before they impact your users or business operations. Additionally, an AWS Monitoring Service enables you to optimize resource utilization by identifying and eliminating any bottlenecks or inefficiencies in your cloud environment.
Another significant benefit of using an AWS Monitoring Service is enhanced security. The service constantly monitors your AWS resources, detecting any unauthorized access attempts, potential security breaches, or anomalies in your system behavior. By promptly identifying and responding to these threats, you can ensure the security and integrity of your data and applications.
Importance of monitoring AWS cloud infrastructure
Monitoring your AWS cloud infrastructure is not just important; it is essential for the smooth functioning of your business. Without proper monitoring, you are blind to the performance, availability, and security of your cloud resources. This lack of visibility can result in unexpected downtime, performance bottlenecks, and security breaches, all of which can have severe consequences for your business, including financial losses, reputational damage, and customer dissatisfaction.
By implementing an AWS Monitoring Service, you gain complete visibility into your cloud infrastructure. You can monitor key performance metrics such as CPU usage, memory utilization, disk I/O, and network traffic, allowing you to identify and resolve any performance issues quickly. Additionally, monitoring your AWS environment helps you detect any unauthorized access attempts or unusual activities, enabling you to take immediate action to prevent potential security breaches.
Key features to look for in an AWS Monitoring Service
When choosing an AWS Monitoring Service, it is essential to consider the key features that will best meet your business needs. Firstly, the service should provide comprehensive monitoring capabilities, allowing you to monitor not only your infrastructure but also your applications and services. This includes monitoring CPU usage, memory utilization, network traffic, database performance, and application logs.
Another critical feature to look for is real-time alerting. The AWS Monitoring Service should have the ability to send instant notifications whenever predefined thresholds are breached or when critical events occur. This ensures that you are immediately alerted to any issues, allowing you to take immediate action and minimize the impact on your business.
Additionally, the service should offer robust reporting and analytics capabilities. It should provide detailed insights into the performance and health of your AWS environment, allowing you to analyze historical trends, identify patterns, and make data-driven decisions to optimize resource allocation and improve efficiency.
Comparison of the top AWS Monitoring Services
To help you choose the best AWS Monitoring Service for your business, let's compare some of the top options available in the market. The following are the key features and capabilities of each service:
Service A:
Comprehensive monitoring of AWS infrastructure, applications, and services
Real-time alerting and notifications
Advanced reporting and analytics
Integration with popular DevOps tools
Service B:
Automated discovery and monitoring of AWS resources
Customizable dashboards and visualizations
Machine learning-based anomaly detection
Built-in compliance monitoring and reporting
Service C:
Seamless integration with AWS CloudWatch
Scalable and flexible architecture
Intelligent auto-scaling capabilities
Advanced security and compliance features
Best practices for implementing an AWS Monitoring Service
Implementing an AWS Monitoring Service requires careful planning and consideration. Here are some best practices to ensure a successful implementation:
Define your monitoring objectives: Clearly define what you want to monitor and the metrics that are critical to your business. This will help you choose the right AWS Cloud Monitoring Service and configure it accordingly.
Set up proactive alerts: Configure alerts to notify you when predefined thresholds are breached or when critical events occur. This will help you detect and respond to issues before they impact your business.
Establish baseline performance metrics: Establish baseline performance metrics for your AWS resources to identify any deviations from the norm. This will help you quickly identify and resolve any performance issues.
Regularly review and optimize: Regularly review your monitoring setup and optimize it based on changing business needs. This includes adding new metrics, adjusting alert thresholds, and fine-tuning your monitoring configuration.
Case studies: Real-world examples of how AWS Monitoring Service improved efficiency and security
To further understand the impact of an AWS Monitoring Service, let's look at some real-world case studies:
Company X: By implementing an AWS Monitoring Service, Company X was able to identify a performance bottleneck in their application, resulting in a 50% improvement in response times and a significant increase in customer satisfaction.
Company Y: Company Y was able to detect and prevent a potential security breach in their AWS environment using an AWS Monitoring Service. This proactive action saved them from potential data loss and reputational damage.
These case studies highlight the importance of implementing an AWS Monitoring Service and the positive impact it can have on efficiency and security.
How to choose the right AWS Monitoring Service for your business
Choosing the right AWS Monitoring Service for your business can be a daunting task. To make an informed decision, consider the following factors:
Business requirements: Identify your specific monitoring needs and prioritize the features that are critical to your business.
Scalability and flexibility: Ensure that the service can scale with your business and adapt to changing requirements.
Integration capabilities: Evaluate how well the service integrates with your existing tools and workflows.
Cost: Consider the pricing structure and evaluate the total cost of ownership over time.
By carefully considering these factors, you can choose an AWS Monitoring Service that aligns with your business goals and requirements.
Steps to set up and configure an AWS Monitoring Service
Once you have chosen an AWS Monitoring Service, follow these steps to set up and configure it:
Step 1: Sign up for the service and create an account.
Step 2: Configure the service to monitor your AWS resources. This may involve installing agents or configuring API access.
Step 3: Define the metrics you want to monitor and set up alerts based on predefined thresholds.
Step 4: Customize dashboards and visualizations to display the metrics that are most important to your business.
Step 5: Test the monitoring setup to ensure that the service is collecting the required data and triggering alerts correctly.
Conclusion: Maximizing efficiency and security with the best AWS Monitoring Service
In conclusion, an AWS Monitoring Service is a critical tool for businesses operating in the cloud. It provides real-time visibility into the performance, health, and security of your AWS infrastructure, enabling you to proactively identify and address any issues. By choosing the right AWS Monitoring Service and following best practices for implementation, you can maximize efficiency, optimize resource utilization, and ensure the security of your cloud environment. So, don't wait any longer. Take the first step towards a more efficient and secure AWS infrastructure by implementing the best AWS Monitoring Service for your business.
CTA: To learn more about maximizing efficiency and security with the best AWS Monitoring Service, visit bigbell.
0 notes
Text
Renascence IT Consulting is a Newark, California–based managed service provider founded in 2005. The firm delivers proactive managed IT support, 24/7 monitoring, cybersecurity protection, cloud solutions, disaster-recovery planning and co-managed IT services tailored to each client’s environment. Serving small- and mid-sized organizations—including highly regulated sectors such as healthcare, architecture and logistics—Renascence helps businesses stay compliant, secure and always-on while aligning technology strategy with long-term growth goals. With a customer-first culture and certified technical expertise, Renascence IT Consulting positions itself as a trusted partner that keeps clients’ systems resilient today and ready for tomorrow.
#Manged IT Services#Cyber Security#Disaster Recovery & Prevention#Cloud Based Solutions#Proactive Network Monitoring#Virtual Distancing
1 note
·
View note
Text
Choosing the Right Managed IT Service Provider for Healthcare

The healthcare industry increasingly depends on technology to improve patient care, streamline operations, and ensure compliance. With the growth in cybersecurity threats, there is an increased need for seamless IT infrastructure and managed IT service providers. Choosing the right managed services provider (MSP) is challenging but essential for optimizing cloud operations. Look for experienced and certified MSP Certifications. Ensure they offer comprehensive monitoring, security, data backup, and disaster recovery services. Additionally, ensure they scale with your business, provide 24/7 support, and follow industry standards for security.
Understanding Managed IT Services in Healthcare
What Are Managed IT Services for Healthcare?
Managed IT services in healthcare involve outsourcing a healthcare facility’s IT infrastructure and operations to a third party at a lower cost than running an internal department. Third-party service providers for medically managed services are also known as managed service providers.
Why Do Healthcare Organizations Need IT Service Management?
Healthcare organizations need IT-managed service providers to establish efficient access to sensitive patient data, improve operational efficiency, enhance patient safety by streamlining processes, reduce costs, and deliver better quality care by aligning IT services with the organization’s healthcare goals.
Key Benefits of Healthcare IT Managed Service Providers
Enhanced Cybersecurity and Compliance
One key benefit of utilizing a healthcare IT-managed service provider is remarkably enhancing cybersecurity and compliance to ensure that sensitive patient data is protected at all costs while adhering to strict industry regulations. It allows healthcare organizations to focus on patient care while minimizing the risk of data breaches.
Improved Efficiency and Reduced Downtime
Healthcare-managed IT service providers offer benefits like improved operational efficiency and significantly reduced downtime. It is easy to achieve by proactive monitoring, rapid issue resolution, on-point technical support, and scalable infrastructure. This helps healthcare organizations deliver excellent patient care while ensuring their IT systems run smoothly and securely without hampering patient care.
Cost Savings and Scalability
Healthcare IT managed services focus on cost savings through outsourcing IT management, making more efficient use of resources and scalability to adapt to changing healthcare needs. Healthcare organizations should be able to scale their IT infrastructure up or down as required.
How to Choose the Best Healthcare IT Managed Service Provider
Experience in Healthcare IT Service Management
While choosing the best healthcare IT-managed service provider for your facility, prioritize their experience in the healthcare industry. Verify that they understand your facility's unique IT needs and compliance regulations like HIPAA and have expertise in managing electronic health records.
Compliance with HIPAA and Other Regulations
Prioritize healthcare IT-managed service providers with a strong track record of security practices, a deep and thorough understanding of healthcare regulations, and proven expertise in data protection.
24/7 Support and Proactive Monitoring
Look for healthcare IT-managed service providers with deep healthcare industry experience, strong compliance records, robust monitoring capabilities, and a proven track record of offering 24/7 support.
Customization and Scalability of IT Solutions
When choosing a healthcare IT-managed service provider, look for their ability to offer customized and scalable IT solutions that align well with your facility’s unique needs. Evaluate their experience in the healthcare industry based on their technical expertise, compliance, and capability to adapt to changing situations.
Common Mistakes to Avoid When Selecting a Healthcare IT Service Provider
When choosing a healthcare IT-managed service provider, common mistakes to avoid include:
Focusing only on the price
Not clearly defining your needs
Ignoring their experience in the healthcare industry
Overlooking security and compliance concerns
Failing to check their reputation
Not understanding their service model
Not checking references and reputation
Not considering future needs
Future Trends in Managed IT Services for Healthcare
The healthcare IT landscape is evolving rapidly, with new technologies shaping the future of managed IT services. Trends include:
AI-driven automation for predictive maintenance and cybersecurity threat detection.
Blockchain technology for secure and transparent patient data management.
Cloud-based healthcare systems for enhanced interoperability and accessibility.
Telehealth advancements powered by 5G and edge computing
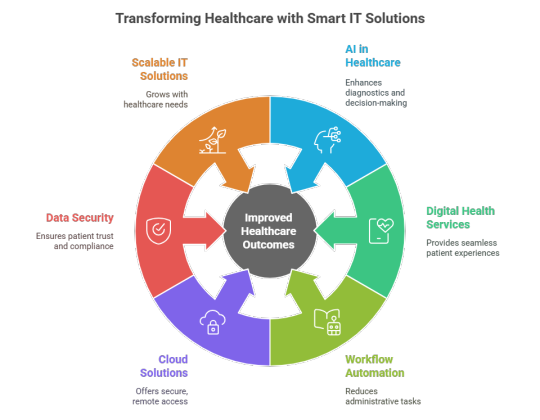
Conclusion: Ensuring the Best IT Support for Healthcare Organizations
Selecting the right healthcare IT-managed service provider is essential for healthcare organizations looking to enhance cybersecurity, compliance, and operational efficiency. The ideal MSP should offer:
Expertise in healthcare IT and experience managing cybersecurity and compliance.
24/7 monitoring and proactive IT support to minimize downtime and security risks.
Customizable and scalable IT solutions aligning with healthcare needs.
By partnering with a reputed and reliable healthcare IT-managed service provider like XLNC Technologies, healthcare organizations can focus on delivering exceptional patient care while maintaining secure and efficient IT systems.
FAQs
What are the key factors to consider when choosing a managed IT service provider for healthcare?
Healthcare organizations should evaluate industry expertise, HIPAA compliance, cybersecurity capabilities, 24/7 support, scalability, and integration with existing systems. A provider with proven experience in healthcare IT, proactive monitoring, and customized solutions ensures operational efficiency, regulatory adherence, and uninterrupted patient care.
How do healthcare IT-managed service providers help with regulatory compliance?
Managed IT service providers to ensure HIPAA and GDPR compliance by implementing secure data encryption, access controls, regular security audits, and automated risk assessments. They help healthcare organizations avoid fines, prevent data breaches, and maintain regulatory compliance through ongoing monitoring, documentation, and proactive security measures.
Why is cybersecurity crucial in managed IT services for healthcare?
Cybersecurity is essential to protect sensitive patient data from ransomware, phishing attacks, and unauthorized access. MSPs provide AI-driven threat detection, zero-trust security models, real-time monitoring, and multi-layered encryption to safeguard electronic health records (EHRs) and ensure uninterrupted healthcare operations.
What are the benefits of outsourcing IT service management in healthcare?
Outsourcing IT services reduces costs, enhances security, minimizes downtime, and improves scalability. Managed IT providers offer 24/7 support, cloud-based solutions, proactive monitoring, and compliance management, allowing healthcare organizations to focus on patient care rather than IT complexities
How can a healthcare IT-managed service provider improve patient care?
MSPs improve patient care by ensuring secure, fast access to medical records, enabling seamless telehealth solutions, reducing system downtime, and enhancing data accuracy. With real-time monitoring and AI-powered automation, providers can deliver efficient, uninterrupted, high-quality healthcare services.
#Managed IT Services for Healthcare#Healthcare IT Solutions#Healthcare Digital Transformation#IT Support for Hospitals#Cloud Solutions in Healthcare#Healthcare Data Security#HIPAA Compliance#Healthcare IT Compliance#Telehealth IT Support#Electronic Health Records#EHR Management#Cybersecurity in Healthcare#Remote Patient Monitoring#IT Infrastructure Management#24/7 IT Support for Healthcare#IT Outsourcing in Healthcare#Disaster Recovery for Hospitals#Cost-effective IT Services#Patient Data Protection#Healthcare Compliance Solutions#Healthcare Cloud Management#Managed Service Providers for Healthcare#Improving Patient Experience with IT#Healthcare IT Consulting
0 notes
Text
CBDC technology partner India
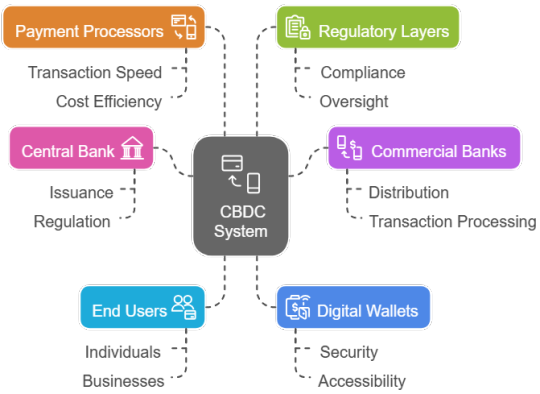
As CBDCs become a global reality, Prodevans equips banks with everything needed to enter the digital currency ecosystem. We provide full-spectrum CBDC implementation — including compliant architecture, token management, real-time reconciliation, secure wallet enablement, and 24/7 L1/L2 support. Trusted for our role in India’s national rollout, we help institutions go beyond pilots to scalable, production-ready platforms ensuring seamless end- user readiness. Our services ensure central bank compliance while delivering performance, observability, and rapid response to evolving regulatory needs. Whether you’re in the pilot phase or preparing for production rollout, Prodevans supports your CBDC journey at every step.
OUR ADDRESS
403, 4TH FLOOR, SAKET CALLIPOLIS, Rainbow Drive, Sarjapur Road, Varthurhobli East Taluk, Doddakannelli, Bengaluru Karnataka 560035
OUR CONTACTS
+91 97044 56015
#CBDC (Central Bank Digital Currency)#Cloud Computing & Cloud Services#Application Modernization#360° Monitoring (Server#Application#Database & Virtualization Monitoring)#Identity & Access Management (IAM)#Automation (incl. ML‑driven#Ansible#network/cloud automation)#DevOps Tools & Support#Infrastructure Management (IaaS/PaaS/SaaS#orchestration#orchestration tools)
0 notes
Text
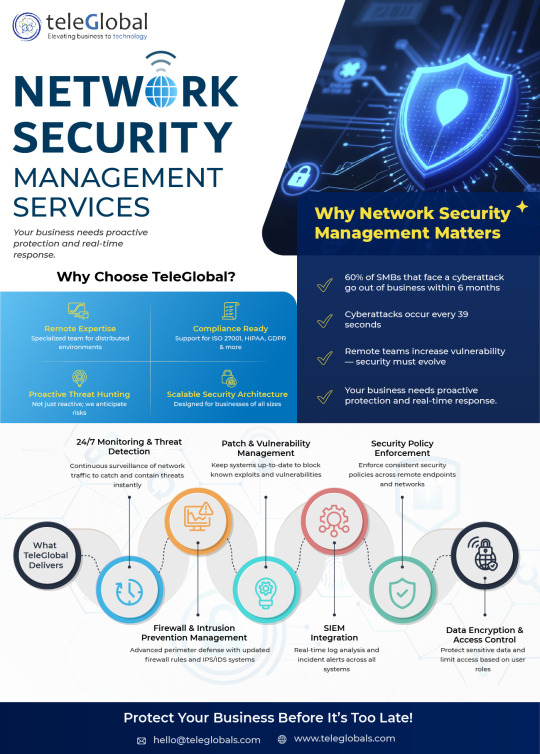
Network Management Services in Pune | Teleglobal
Empower Your Network for Efficient Performance From network setup and monitoring to firewalls and load balancer setup, we offer a secure, optimized, and high-performing network infrastructure. Our Network Management Services provides end-to-end solutions that boost network security, performance, and reliability, ensuring nothing interrupts connectivity of your business.
Optimize Your Network Today https://teleglobals.com/contact-us
#Network Management Services#Network Management#IT Infrastructure#Remote Monitoring#IT Support#Managed Services#Tech solutions#Digital Transformation#Cloud Computing#Cyber Security#Business Continuity
0 notes
Text
Cybersecurity Considerations in Cloud-Based Estimating Service Platforms
Introduction The rapid adoption of cloud-based tools in industries like construction, manufacturing, and engineering has revolutionized how businesses handle estimating services. Cloud-based estimating service platforms provide immense benefits, such as accessibility, collaboration, and real-time updates, which help companies improve efficiency and reduce costs. However, the increased use of these platforms also raises significant cybersecurity concerns. Protecting sensitive data, ensuring platform reliability, and maintaining secure access are all critical components of ensuring the success of cloud-based estimating services.
This article will explore the cybersecurity considerations that organizations must take into account when utilizing cloud-based estimating services. We will highlight the importance of robust security measures, best practices for mitigating risks, and the role of the cloud service provider in safeguarding data.
Understanding the Cybersecurity Risks in Cloud-Based Estimating Services Cloud-based estimating services store vast amounts of sensitive information, including cost estimates, project budgets, pricing data, and contract details. This data is crucial for project planning, and its loss or theft could result in financial, legal, or reputational damage. The cybersecurity risks in cloud platforms include data breaches, unauthorized access, data manipulation, and service outages that can disrupt operations.
Hackers and cybercriminals may target cloud-based estimating services to access proprietary cost data, sensitive client information, or intellectual property. This makes cloud security a critical concern for businesses that rely on these services. Additionally, the remote nature of cloud access increases the potential for data exposure, especially if users access the platform from unsecured devices or networks.
Choosing a Secure Cloud Service Provider One of the first steps in ensuring cybersecurity for cloud-based estimating services is selecting a reliable cloud service provider (CSP) that prioritizes security. Reputable CSPs offer advanced security features, including end-to-end encryption, multi-factor authentication (MFA), and continuous monitoring of their networks. They should also comply with industry standards and regulations, such as the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA), depending on the industry.
Before selecting a CSP, organizations should thoroughly evaluate the provider’s security protocols, certifications, and track record. It’s also important to assess the provider’s ability to scale security measures as your business grows. A strong partnership with a reputable provider ensures that security is embedded into the platform from the ground up.
Data Encryption and Secure Storage Data encryption is one of the most effective measures for securing sensitive information in cloud-based estimating platforms. By encrypting data both during transmission and at rest, companies can ensure that even if hackers intercept the data, they cannot access or misuse it.
In addition to encryption, secure storage practices are crucial for protecting estimating data. Cloud service providers should store data in secure data centers equipped with physical security measures, such as biometric access controls, surveillance, and disaster recovery plans. These physical and digital safeguards help protect against both cyber threats and natural disasters.
User Access Control and Authentication Controlling user access is another essential aspect of cybersecurity in cloud-based estimating services. Businesses must establish strict user access protocols to ensure that only authorized personnel can access sensitive project data and cost estimates. This includes defining user roles, limiting permissions, and requiring strong authentication methods.
Multi-factor authentication (MFA) is a powerful tool for enhancing access security. By requiring users to provide additional verification, such as a code sent to their mobile device, alongside their username and password, MFA ensures that only legitimate users can access the platform.
Organizations should also regularly review and update user access permissions to ensure that former employees or contractors do not retain access to sensitive information after their engagement ends.
Data Backup and Disaster Recovery Plans Data loss is a major risk for businesses relying on cloud-based estimating services. Whether due to a cyber attack, natural disaster, or technical failure, losing critical estimating data can severely disrupt project timelines and budget management. Therefore, having a solid data backup and disaster recovery plan is crucial.
Cloud-based platforms should offer automated data backups to prevent loss of estimates and other project information. It is important for businesses to regularly test their backup systems and ensure that data can be quickly recovered in the event of an incident. The disaster recovery plan should also outline clear steps for restoring access to the platform, rebuilding project estimates, and ensuring continuity of operations.
Monitoring and Incident Response Continuous monitoring of the cloud environment is essential for detecting potential security threats. Cloud service providers should implement real-time threat detection systems to identify unusual activities, such as unauthorized access attempts or unusual data transfers. Monitoring tools can also track user behaviors, alert administrators about security anomalies, and provide insights into potential vulnerabilities.
In addition to monitoring, businesses should have a clear incident response plan in place. This plan outlines the steps to take in the event of a cyberattack, such as isolating affected systems, notifying affected parties, and coordinating with cybersecurity experts. A well-defined response plan helps minimize the impact of a security breach and ensures that the organization can recover quickly.
Employee Training and Security Awareness Even with the best technology in place, human error remains one of the largest cybersecurity risks. Employees who are unaware of security best practices may inadvertently compromise data by clicking on phishing emails, using weak passwords, or accessing the platform from unsecured devices.
To mitigate this risk, organizations should provide regular cybersecurity training to all employees who use cloud-based estimating services. Training should cover topics such as identifying phishing attempts, using strong and unique passwords, and securing devices. A culture of cybersecurity awareness helps reduce the chances of a successful attack and empowers employees to play an active role in protecting company data.
Compliance and Regulatory Requirements Depending on the industry, businesses using cloud-based estimating services must comply with various regulations related to data security and privacy. For instance, the construction industry may need to adhere to data protection laws, while healthcare-related estimating services might be subject to HIPAA regulations.
Cloud service providers should be transparent about their compliance with these regulations, and businesses should ensure that they understand their obligations when using cloud-based platforms. By partnering with a provider that meets the required compliance standards, companies can avoid legal and financial penalties while safeguarding their data.
Conclusion As cloud-based estimating services become increasingly integral to project planning and execution, securing sensitive data and protecting against cybersecurity threats are paramount concerns. Organizations must take proactive measures, such as selecting reputable service providers, implementing data encryption, controlling user access, and creating robust backup and disaster recovery plans. With a focus on cybersecurity, companies can confidently leverage cloud-based estimating services while minimizing the risk of data breaches and service disruptions.
By investing in the right security tools, maintaining ongoing monitoring, and ensuring employee awareness, businesses can strengthen the cybersecurity of their cloud-based estimating platforms and protect the valuable data that drives their projects forward.
#Estimating Service#cybersecurity#cloud-based platforms#data encryption#user access control#multi-factor authentication#cloud security#disaster recovery#data backup#incident response#project estimating#estimating tools#secure storage#data protection#compliance#security measures#cybersecurity best practices#project budgeting#risk management#phishing prevention#employee training#cloud service provider#threat detection#construction estimating#privacy regulations#disaster recovery planning#data breaches#system monitoring#project security#secure access
0 notes
Text
Cloud Migration Service: A Seamless Transition to the Cloud
In today's digital landscape, businesses are increasingly adopting cloud solutions to enhance scalability, flexibility, and cost efficiency. A Cloud Migration Service plays a crucial role in ensuring a smooth transition from on-premises infrastructure to cloud environments, minimizing risks and maximizing operational benefits.
What is a Cloud Migration Service?
A Cloud Migration Service involves the process of transferring data, applications, and IT resources from traditional systems to a cloud-based infrastructure. These services provide businesses with the necessary tools, strategies, and expertise to migrate efficiently while maintaining security and compliance.

Benefits of Cloud Migration Services
1. Enhanced Scalability
With cloud solutions, businesses can scale resources up or down based on demand, reducing unnecessary costs and ensuring optimal performance.
2. Cost Efficiency
Cloud migration eliminates the need for expensive on-premises hardware and maintenance, enabling businesses to pay only for what they use.
3. Improved Security
Leading cloud providers implement robust security measures, including encryption, access controls, and compliance frameworks, to protect sensitive business data.
4. Disaster Recovery and Business Continuity
Cloud migration ensures data redundancy and quick recovery solutions, minimizing downtime and enhancing business resilience.
Steps Involved in a Cloud Migration Service
1. Assessment and Planning
A thorough evaluation of existing IT infrastructure helps identify workloads best suited for migration and develop a strategic roadmap.
2. Selecting the Right Cloud Model
Organizations can choose from Public, Private, Hybrid, or Multi-Cloud environments based on their business needs.
3. Executing the Migration
A phased migration approach minimizes disruptions, ensuring a smooth transition of applications and data.
4. Testing and Optimization
Post-migration testing is crucial to ensure performance, security, and compliance are maintained in the new cloud environment.
Overcoming Common Cloud Migration Challenges
Data Security Risks: Implementing encryption and access controls.
Application Downtime: Adopting a phased or hybrid migration strategy.
Cost Management: Utilizing cloud cost optimization tools.
Compatibility Issues: Assessing and refactoring applications for cloud readiness.
Choosing the Right Cloud Migration Service Provider
When selecting a Cloud Migration Service provider, businesses should consider:
Expertise in cloud platforms like AWS, Azure, or Google Cloud.
Security and compliance certifications.
Scalability options and 24/7 support.
Conclusion
Migrating to the cloud can be a game-changer for businesses looking to innovate and grow. A professional Cloud Migration Service ensures a hassle-free transition, enhanced security, and cost-efficient operations. With the right strategy and expert guidance, organizations can unlock the full potential of cloud computing for a competitive edge in the digital era.
#Cloud Migration service#Cloud Migration and Modernization service#Infrastructure as a Service (IaaS)#Cloud Infrastructure automation and monitoring#Serverless Computing#Disaster Recovery automation service
1 note
·
View note
Text
Fusion Factor Corporation provides reliable IT solutions and support for small and medium-sized businesses. They specialize in managed IT services, cybersecurity, cloud solutions, and IT consulting, helping companies work smarter and stay secure.
With a focus on customer care, Fusion Factor ensures your technology runs smoothly, so you can focus on growing your business. Their team offers 24/7 monitoring, proactive support, and tailored solutions to meet your unique needs. Fusion Factor makes IT simple, so you can achieve more.
#cybersecurity#data recovery#it consulting#it services#it support#seo services#virtualization services#voip#managed it services#cyber security#cloud computing#Virtualization Services#Dark Web Monitoring Services#Office 365 Data Backup#IT Help Desk Services#Hardware As A Service#Office 365#Email & Spam Protection#On-Demand Services#Office Moves#Regulatory Compliance
0 notes
Text
Enhancing Security and Efficiency: The Benefits of BigBell Monitoring Services

Introduction to monitoring services
In today's rapidly evolving digital landscape, businesses face numerous challenges in ensuring the security and efficiency of their operations. As the reliance on technology continues to grow, the need for robust monitoring services has become paramount. Monitoring services play a crucial role in safeguarding businesses from potential threats and optimizing their processes. In this article, we will delve into the benefits of monitoring services, with a particular focus on BigBell monitoring services.
The importance of monitoring services for businesses
Businesses operate in a complex and interconnected environment, where any disruption can have severe consequences. Whether it's the risk of cyber-attacks, system failures, or operational inefficiencies, monitoring services offer a proactive approach to address these challenges. By continuously monitoring various aspects of a business's infrastructure, monitoring services provide real-time insights into potential vulnerabilities and performance issues. This allows businesses to take timely action and minimize any potential risks. Furthermore, monitoring services enable businesses to meet regulatory compliance requirements and maintain the trust of their customers.
Benefits of cloud monitoring services
Cloud computing has revolutionized the way businesses operate by providing scalable and flexible solutions. Cloud monitoring services offer several advantages over traditional on-premises monitoring. Firstly, cloud monitoring services allow businesses to monitor their infrastructure from anywhere, providing unparalleled accessibility and convenience. Additionally, cloud monitoring services offer scalability, enabling businesses to easily adjust their monitoring capabilities based on their needs. Moreover, cloud monitoring services often leverage advanced analytics and machine learning algorithms to detect patterns and anomalies, providing businesses with valuable insights for improving their operations.
Understanding BigBell monitoring services
BigBell monitoring services are a leading solution in the market, offering an extensive range of features and benefits. BigBell combines the power of cloud computing with advanced monitoring capabilities to deliver a comprehensive solution for businesses. With its user-friendly interface and customizable dashboards, BigBell allows businesses to monitor various aspects of their infrastructure, such as network performance, server health, and application availability. Furthermore, BigBell provides real-time alerts and notifications, ensuring that businesses are promptly informed about any issues that may arise. The platform also offers detailed reports and analytics, enabling businesses to identify trends and make data-driven decisions.
How BigBell monitoring services enhance security
Security is a top concern for businesses in today's digital landscape. BigBell monitoring services play a crucial role in enhancing security by continuously monitoring the network for potential threats and vulnerabilities. The platform employs advanced threat detection techniques, such as intrusion detection systems and anomaly detection algorithms, to identify any suspicious activities. In the event of a security breach, BigBell immediately alerts the relevant stakeholders, allowing them to take immediate action and minimize the impact. Additionally, BigBell monitoring services offer comprehensive log management and auditing capabilities, ensuring that businesses can meet compliance requirements and investigate any security incidents effectively.
How BigBell monitoring services improve efficiency
Efficiency is a key driver of success for businesses. BigBell monitoring services help businesses optimize their operations and improve efficiency in several ways. Firstly, by providing real-time insights into the performance of infrastructure components, such as servers and applications, BigBell enables businesses to identify any bottlenecks or performance issues. This allows businesses to take proactive measures to address these issues before they impact the overall efficiency. Furthermore, BigBell offers predictive analytics capabilities, allowing businesses to anticipate potential problems and take preventive actions. By automating routine monitoring tasks, BigBell frees up valuable resources and enables businesses to focus on more strategic initiatives.
Case studies: Real-life examples of BigBell monitoring services in action
To illustrate the impact of BigBell monitoring services, let's explore a couple of real-life examples. Company A, a leading e-commerce platform, implemented BigBell monitoring services to ensure the availability and performance of their website. Through BigBell's comprehensive monitoring capabilities, they were able to identify a potential server failure and take proactive measures to prevent any downtime, saving them significant revenue. Company B, a financial institution, leveraged BigBell monitoring services to enhance their security posture. BigBell's advanced threat detection capabilities helped them detect and mitigate a sophisticated phishing attack, safeguarding sensitive customer information and preserving their reputation.
Choosing the right monitoring service provider
Selecting the right monitoring service provider is a critical decision for businesses. When evaluating potential providers, consider factors such as the provider's track record, the comprehensiveness of their monitoring capabilities, and their ability to scale with your business's needs. Additionally, ensure that the provider offers robust security features, such as encryption and secure data storage, to protect your sensitive information. Take the time to understand the provider's customer support offerings, as prompt and reliable support is crucial in addressing any issues that may arise.
Implementing BigBell monitoring services in your business
Implementing BigBell monitoring services in your business is a straightforward process. Start by identifying the key areas of your infrastructure that require monitoring, such as servers, networks, and applications. Then, work closely with the BigBell team to define the monitoring parameters and customize the dashboards to suit your specific needs. Train your staff on how to interpret the monitoring data and respond to alerts effectively. Regularly review the monitoring reports and analytics to identify trends and areas for improvement. By leveraging the power of BigBell monitoring services, you can enhance the security and efficiency of your business operations.
Conclusion: The future of monitoring services
As technology continues to advance, monitoring services will play an increasingly vital role in ensuring the security and efficiency of businesses. BigBell monitoring services offer a comprehensive solution that combines the benefits of cloud computing with advanced monitoring capabilities. By continuously monitoring various aspects of a business's infrastructure, BigBell provides real-time insights into potential vulnerabilities and performance issues, enhancing security and improving efficiency. With its user-friendly interface and customizable dashboards, BigBell empowers businesses to take proactive measures and make data-driven decisions. By embracing BigBell monitoring services, businesses can navigate the complexities of the digital landscape with confidence and achieve their goals.
CTA: bigbell
Ready to enhance the security and efficiency of your business? Visit BigBell today and discover the power of advanced monitoring services.
0 notes
Text
Drasi by Microsoft: A New Approach to Tracking Rapid Data Changes
New Post has been published on https://thedigitalinsider.com/drasi-by-microsoft-a-new-approach-to-tracking-rapid-data-changes/
Drasi by Microsoft: A New Approach to Tracking Rapid Data Changes
Imagine managing a financial portfolio where every millisecond counts. A split-second delay could mean a missed profit or a sudden loss. Today, businesses in every sector rely on real-time insights. Finance, healthcare, retail, and cybersecurity, all need to react instantly to changes, whether it is an alert, a patient update, or a shift in inventory. But traditional data processing cannot keep up. These systems often delay responses, costing time and missed opportunities.
That is where Drasi by Microsoft comes in. Designed to track and react to data changes as they happen, Drasi operates continuously. Unlike batch-processing systems, it does not wait for intervals to process information. Drasi empowers businesses with the real-time responsiveness they need to stay ahead of the competitors.
Understanding Drasi
Drasi is an advanced event-driven architecture powered by Artificial Intelligence (AI) and designed to handle real-time data changes. Traditional data systems often rely on batch processing, where data is collected and analyzed at set intervals. This approach can cause delays, which can be costly for industries that depend on quick responses. Drasi changes the game by using AI to track data continuously and react instantly. This enables organizations to make decisions as events happen instead of waiting for the next processing cycle.
A core feature of Drasi is its AI-driven continuous query processing. Unlike traditional queries that run on a schedule, continuous queries operate non-stop, allowing Drasi to monitor data flows in real time. This means even the smallest data change is captured immediately, giving companies a valuable advantage in responding quickly. Drasi’s machine learning capabilities help it integrate smoothly with various data sources, including IoT devices, databases, social media, and cloud services. This broad compatibility provides a complete view of data, helping companies identify patterns, detect anomalies, and automate responses effectively.
Another key aspect of Drasi’s design is its intelligent reaction mechanism. Instead of simply alerting users to a data change, Drasi can immediately trigger pre-set responses and even use machine learning to improve these actions over time. For example, in finance, if Drasi detects an unusual market event, it can automatically send alerts, notify the right teams, or even make trades. This AI-powered, real-time functionality gives Drasi a clear advantage in industries where quick, adaptive responses make a difference.
By combining continuous AI-powered queries with rapid response capabilities, Drasi enables companies to act on data changes the moment they happen. This approach boosts efficiency, cuts down on delays, and reveals the full potential of real-time insights. With AI and machine learning built in, Drasi’s architecture offers businesses a powerful advantage in today’s fast-paced, data-driven world.
Why Drasi Matters for Real-Time Data
As data generation continues to grow rapidly, companies are under increasing pressure to process and respond to information as it becomes available. Traditional systems often face issues, such as latency, scalability, and integration, which limit their usefulness in real-time settings. This is especially critical in high-stakes sectors like finance, healthcare, and cybersecurity, where even brief delays can result in losses. Drasi addresses these challenges with an architecture designed to handle large amounts of data while maintaining speed, reliability, and adaptability.
In financial trading, for example, investment firms and banks depend on real-time data to make quick decisions. A split-second delay in processing stock prices can mean the difference between a profitable trade and a missed chance. Traditional systems that process data in intervals simply cannot keep up with the pace of modern markets. Drasi’s real-time processing capability allows financial institutions to respond instantly to market shifts, optimizing trading strategies.
Similarly, in a connected smart home, IoT sensors track everything from security to energy use. A traditional system may only check for updates every few minutes, potentially leaving the home vulnerable if an emergency occurs during that interval. Drasi enables constant monitoring and immediate responses, such as locking doors at the first sign of unusual activity, thereby enhancing security and efficiency.
Retail and e-commerce also benefit significantly from Drasi’s capabilities. E-commerce platforms rely on understanding customer behavior in real time. For instance, if a customer adds an item to their cart but doesn’t complete the purchase, Drasi can immediately detect this and trigger a personalized prompt, like a discount code, to encourage the sale. This ability to react to customer actions as they happen can lead to more sales and create a more engaging shopping experience. In each of these cases, Drasi fills a significant gap where traditional systems lack and thus empowers businesses to act on live data in ways previously out of reach.
Drasi’s Real-Time Data Processing Architecture
Drasi’s design is centred around an advanced, modular architecture, prioritizing scalability, speed, and real-time operation. Maily, it depends on continuous data ingestion, persistent monitoring, and automated response mechanisms to ensure immediate action on data changes.
When new data enters Drasi’s system, it follows a streamlined operational workflow. First, it ingests data from various sources, including IoT devices, APIs, cloud databases, and social media feeds. This flexibility enables Drasi to collect data from virtually any source, making it highly adaptable to different environments.
Once data is ingested, Drasi’s continuous queries immediately monitor the data for changes, filtering and analyzing it as soon as it arrives. These queries run perpetually, scanning for specific conditions or anomalies based on predefined parameters. Next, Drasi’s reaction system takes over, allowing for automatic responses to these changes. For instance, if Drasi detects a significant increase in website traffic due to a promotional campaign, it can automatically adjust server resources to accommodate the spike, preventing potential downtime.
Drasi’s operational workflow involves several key steps. Data is ingested from connected sources, ensuring real-time compatibility with devices and databases. Continuous queries then scan for predefined changes, eliminating delays associated with batch processing. Advanced algorithms process incoming data to provide meaningful insights immediately. Based on these data insights, Drasi can trigger predefined responses, such as notifications, alerts, or direct actions. Finally, Drasi’s real-time analytics transform data into actionable insights, empowering decision-makers to act immediately.
By offering this streamlined process, Drasi ensures that data is not only tracked but also acted upon instantly, enhancing a company’s ability to adapt to real-time conditions.
Benefits and Use Cases of Drasi
Drasi offers benefits far beyond typical data processing capabilities and provides real-time responsiveness essential for businesses that need instant data insights. One key advantage is its enhanced efficiency and performance. By processing data as it arrives, Drasi removes delays common in batch processing, leading to faster decision-making, improved productivity, and reduced downtime. For example, a logistics company can use Drasi to monitor delivery statuses and reroute vehicles in real time, optimizing operations to reduce delivery times and increase customer satisfaction.
Real-time insights are another benefit. In industries like finance, healthcare, and retail, where information changes quickly, having live data is invaluable. Drasi’s ability to provide immediate insights enables organizations to make informed decisions on the spot. For example, a hospital using Drasi can monitor patient vitals in real time, supplying doctors with important updates that could make a difference in patient outcomes.
Furthermore, Drasi integrates with existing infrastructure and enables businesses to employ its capabilities without investing in costly system overhauls. A smart city project, for example, could use Drasi to integrate traffic data from multiple sources, providing real-time monitoring and management of traffic flows to reduce congestion effectively.
As an open-source tool, Drasi is also cost-effective, offering flexibility without locking businesses into expensive proprietary systems. Companies can customize and expand Drasi’s functionalities to suit their needs, making it an affordable solution for improving data management without a significant financial commitment.
The Bottom Line
In conclusion, Drasi redefines real-time data management, offering businesses an advantage in today’s fast-paced world. Its AI-driven, event-based architecture enables continuous monitoring, instant insights, and automatic responses, which are invaluable across industries.
By integrating with existing infrastructure and providing cost-effective, customizable solutions, Drasi empowers companies to make immediate, data-driven decisions that keep them competitive and adaptive. In an environment where every second matters, Drasi proves to be a powerful tool for real-time data processing.
Visit the Drasi website for information about how to get started, concepts, how to explainers, and more.
#ai#AI-powered#AI-powered data processing#alerts#Algorithms#Analytics#anomalies#APIs#approach#architecture#artificial#Artificial Intelligence#banks#Behavior#change#Cloud#cloud services#code#Commerce#Companies#continuous#continuous monitoring#cybersecurity#data#data ingestion#Data Management#data processing#data-driven#data-driven decisions#databases
0 notes
Text
United States green technology and sustainability market size reached USD 6.5 Billion in 2024. Looking forward, IMARC Group expects the market to reach USD 34.9 Billion by 2033, exhibiting a growth rate (CAGR) of 19.7% during 2025-2033.
#United States Green Technology and Sustainability Market Report by Component (Solution#Services)#Technology (Internet-of-Things#Cloud Computing#Artificial Intelligence and Analytics#Digital Twin#Cybersecurity#Blockchain)#Application (Green Building#Carbon Footprint Management#Weather Monitoring and Forecasting#Air and Water Pollution Monitoring#Forest Monitoring#Crop Monitoring#Soil Condition and Moisture Monitoring#Water Purification#and Others)#and Region 2025-2033#United States Green Technology and Sustainability Market
0 notes
Text
https://www.esds.co.in/blog/managed-security-service-provider-mssp/
#Managed Security Service Provider#MSSP#MSP vs MSSP#SOC services#data protection#IT security#cloud security#network security#security monitoring#vulnerability management#threat management
0 notes
Text
Why Healthcare Providers Need Managed IT Services for Better Patient Care

The healthcare industry is going through a massive digital transformation, with electronic health records, telehealth, cloud-based patient management, and data security becoming the foundation of modern care. A hospital or healthcare center has many things to juggle at once: Accessing a patient’s medical history, checking real-time lab results, and managing endless billing cycles. Managing all this can lead to chaos, operational failure, and bad patient experience. That’s where Managed IT Services comes in.
Studies show that around 84% of hospitals and healthcare centers use cloud services for backup, analytics, and disaster recovery. The integration of IT into healthcare has restructured the industry, from healthcare technology like electronic health records and electronic medical records systems to practice management and telemedicine platforms.
Understanding Managed IT Services in Healthcare
What Are Managed IT Services for Healthcare?
Managed IT services for medical practices and healthcare centers mean outsourcing a facility’s IT functions and operations to a third party at a lower cost than running an internal IT department. The services provided by a third party for managed medical services are known as managed service providers (MSPs).
Common managed IT services for healthcare include:
Cybersecurity and Compliance: Advanced security protocols, including endpoint protection, threat detection, and compliance.
Cloud and Data Management: This service helps secure cloud storage for managing electronic health records, medical imaging, and real-time data access.
24/7 Monitoring and Support: Continuous monitoring of IT infrastructure to detect and resolve issues before they impact healthcare operations. This ensures that healthcare IT systems are always up and running.
Network and Infrastructure Management: Optimizes connectivity for seamless communication
Disaster Recovery and Business Continuity: This includes backup and recovery strategies to safeguard critical patient and operational data in case of system failure.
How Do Healthcare-Managed IT Services Work?
Here’s how IT-managed services work:
Monitoring
Managed IT services to monitor systems, networks, and applications to assess their performance, security, and compliance. For example, they can manage and monitor medical applications and do the necessary upgrades daily.
Maintenance
Managed IT services for healthcare assistance in performing routine maintenance tasks such as software updates, network supervision, and disaster recovery.
Security
Healthcare-managed IT services have 24/7 support for employees, patients, and clinics to improve operational efficiency.
Issue Resolution
They resolve issues in real time through help desks. These help desks can include a general IT help desk, a clinical service help desk, and a patient service help desk. Both employees and patients can use these help desks to resolve their issues in real time.
Challenges in Healthcare IT Management
Cyber Attacks
Cybersecurity is the top challenge for healthcare leaders. Attackers are getting smarter and more strategic; thus, we need stricter norms against cyber attacks.
The healthcare industry is more vulnerable to these types of threats:
Ransomware
Data Breaches
DDoS Attacks
Insider Threats
Healthcare IT Security Risks
One of the biggest risks in healthcare systems is the insecure storage and transmission of sensitive patient data. Weak encryption, poor access control, and bad data handling can allow unauthorized individuals to access patient information, which cybercriminals can use to access valuable data.
The Growing Need for Compliance and Data Protection
Compliance is a big challenge for healthcare providers. Laws like HIPAA require strict measures to protect sensitive patient information, and non-compliance can lead to large fines and legal issues.
Managed IT service for healthcare providers to help healthcare organizations comply by:
Encrypting data and secure access
Conducting regular compliance audits and security assessments
Having data backup and disaster recovery plans in place.
Key Benefits of IT Managed Services in Healthcare
Data Security and HIPAA Compliance
One of the benefits of managed IT services in healthcare is the significant boost in data security and guaranteed HIPAA compliance to protect sensitive patient data/information with continuous monitoring, proactive threat mitigation, and expert guidance in navigating complex healthcare regulations, minimizing data breaches and legal penalties.
Operational Efficiency for Healthcare Providers
IT-managed services in healthcare have proven to improve operational efficiency by streamlining processes, minimizing downtime, and securing sensitive patient data/information to comply with regulations. This will allow healthcare providers to focus on patient care rather than managing IT infrastructure and having access to expert technical support to address issues promptly.
24/7 IT Support and Zero Downtime
IT-managed services in healthcare can provide 24/7 IT support and zero downtime through proactive monitoring and rapid problem-solving. This approach offers remote monitoring and management, disaster recovery solutions, and rapid troubleshooting. This also gives access to on-demand expertise for temporary projects or scenarios where skill sets are not internally employable.
Cost Savings with Healthcare IT Managed Services
Managed IT services can reduce costs by eliminating hardware acquisition and labor costs.
How Managed IT Services Improve Patient Care
Faster Access to Patient Records with Cloud Solutions
Managed IT services can improve patient care by giving faster access to patient records through cloud solutions so healthcare providers can make informed decisions quickly, which will lead to better diagnosis, treatment plans, and overall patient experience while maintaining data security and accessibility anywhere.
Better Telehealth and Remote Patient Monitoring
Managed IT services provide better telehealth and remote patient monitoring. These services allow healthcare providers to deliver continuous patient care through digital platforms. Early interventions, better chronic condition management, and patient engagement simplifications reduce costs.
No Downtime for Uninterrupted Patient Care
Managed IT services mean minimal downtime, and healthcare professionals can focus solely on delivering excellent medical care to patients without technology interruptions.
Choosing the Right Managed IT Services Provider for Healthcare
Key Factors to Consider in Healthcare IT Managed Services
When looking for a managed IT service provider:
Proven experience in the healthcare industry
Proven expertise and compliance with HIPAA and HITRUST
Strong security measures for patient data
Scalability to meet changing needs
Service level agreements (SLAs)
How to Evaluate Managed IT Services for Healthcare Providers
When evaluating managed IT service providers for healthcare:
Do they understand healthcare regulations like HIPAA?
Expertise in relevant technology like EHR
Scalability
Strong cybersecurity practices
Proven track record in healthcare
Clear communication on service-level support
Request case studies and client testimonials
Future of Managed IT Services in Healthcare
As technology advances, managed IT services will use:
AI-driven automation for predictive maintenance
Blockchain for patient data management
Interoperability between healthcare systems
Advanced cybersecurity frameworks for protection against cyber attacks
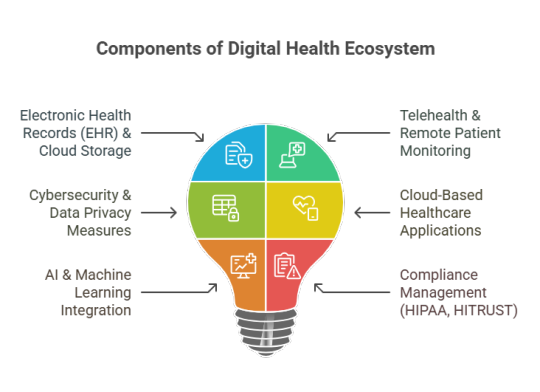
Conclusion: Why Healthcare Providers Must Invest in Managed IT Services
Healthcare providers must invest in IT-managed services to focus on patient care. By outsourcing complex IT infrastructure management, providers can have a robust cybersecurity framework to protect patient data, perform proactive system monitoring for operational efficiency, deliver high-quality care, and comply with industry regulations.
By partnering with a managed IT service provider, healthcare organizations can focus on what matters most—patient care.
With over 20 years of IT consulting and managed services experience, XLNC Technologies helps healthcare providers navigate a digital transformation without compromising security, efficiency, or compliance.
By choosing XLNC Technologies, healthcare organizations have a trusted partner to deliver future-ready IT solutions for seamless, secure, and patient-centric healthcare.
FAQs
What are managed IT services in healthcare, and how do they work?
Managed IT services in healthcare mean outsourcing IT management to specialist providers who ensure security, compliance, and efficiency. They offer 24/7 monitoring, cybersecurity, cloud solutions, and data backup so you can focus on patient care.
How do managed IT services help healthcare providers improve patient care?
They help with patient care by giving fast access to medical records, secure telehealth solutions, and minimal downtime. AI-driven monitoring and cloud-based data storage mean AI-driven seamless care, better diagnoses, and better patient outcomes through secure and efficient technology.
What are the benefits of IT-managed services in healthcare security?
Managed IT services deliver security with AI-driven threat detection, data encryption, zero-trust architecture, and real-time monitoring. They protect electronic health records (EHRs) from cyber threats, ransomware, and data breaches, so you’re HIPAA compliant, and patient data is private.
How can managed IT services help healthcare organizations stay compliant with regulations?
They help with HIPAA and regulatory compliance by implementing strong security protocols, encrypted data storage, and access control. Regular audits, automated risk assessments, and secure backups reduce legal risk and protect patient data from breaches and unauthorized access.
How do healthcare providers choose the right managed IT services provider?
They should evaluate IT vendors based on their industry expertise, 24/7 support, cybersecurity capabilities, compliance readiness, and scalability. Check past performances, case studies, and security frameworks. A provider with proactive monitoring and custom solutions will maintain efficiency, compliance, and better patient care.
#Managed IT Services for Healthcare#Healthcare IT Solutions#Healthcare Digital Transformation#IT Support for Hospitals#Cloud Solutions in Healthcare#Healthcare Data Security#HIPAA Compliance#Healthcare IT Compliance#Telehealth IT Support#Electronic Health Records#EHR Management#Cybersecurity in Healthcare#Remote Patient Monitoring#IT Infrastructure Management#24/7 IT Support for Healthcare#IT Outsourcing in Healthcare#Disaster Recovery for Hospitals#Cost-effective IT Services#Patient Data Protection#Healthcare Compliance Solutions#Healthcare Cloud Management#Managed Service Providers for Healthcare
0 notes
Text
Stay Ahead of the Curve: Why Entrepreneurs Are Turning to Auvik for Cloud-Based Network Management
🚀 Stay Ahead of the Curve with Auvik Networks! 🚀 Entrepreneurs, are you ready to streamline your business and boost efficiency? 📈 Discover how Auvik's cloud-based network management is helping businesses improve operational efficiency by up to 42%!
As more businesses turn to digital solutions, network management software has become a critical factor in boosting efficiency—companies that invest in automated IT management see up to a 42% improvement in operational efficiency by reducing downtime and IT labor costs. Auvik Networks, founded in 2011, is a Canadian company providing cloud-based network management solutions, primarily serving…
#Auvik Network Management#Auvik Networks review#business#Business network monitoring#Cloud solutions for entrepreneurs#Cloud-based network tools#Entrepreneurs#Free trial#IT automation for businesses#Managed Service Providers (MSPs)#Network management#Network security and visibility#Networking#Networking tools#news#Scalable IT solutions#startups#Tech solutions for startups
0 notes
Text
youtube.com/watch?v=xw9-Wsz_uyU
Leveraging AI and SEO (AI and Innovation Theme)* (youtube.com)
Cloudways seo Leveraging AI and SEO (AI and Innovation Theme)* (youtube.com)
#- Cloudways hosting#- Managed cloud hosting#- Cloud hosting services#- Server management#- Website performance#- Cloud server solutions#- Scalable hosting#- Server security#- Cloudways platform#- Website optimization#- Cloud server management#- Performance monitoring#- Cloudways features#- Cloud hosting benefits#- Website speed optimization#- Cloud server reliability#- Hosting control panel#- Cloud server customization#- Cloud hosting reviews#- Cloud server maintenance#- Managed server hosting#- Cloud server security#- Website uptime#- Cloud hosting solutions#- Cloud server backups#- Cloud server migration#- Cloud hosting pricing#- Cloud server support#- Cloud server speed#- Website hosting options
0 notes