#CryptoTheft
Explore tagged Tumblr posts
Text
macOS malware NimDoor refuses to die, targets crypto firms
North Korean hackers are deploying NimDoor, a stealthy macOS threat that auto-reinstalls itself when killed and loots crypto firms using fake Zoom updates and Telegram lures. It hijacks AppleScript and Nim binaries to bypass defences and steal credentials.
Sources: BleepingComputer | SentinelLABS
6 notes
·
View notes
Text
#BybitHack#CryptoSecurity#CryptoNews#Blockchain#CryptoIndustry#DigitalAssets#Cryptocurrency#HackAlert#CryptoTheft#CryptoInvesting#Ethereum
0 notes
Link
كاسبرسكي تكشف عن أول تطبيق تجسس يستهدف محافظ العملات المشفرة عبر متجر آبل في تطور مثير للقلق، أعلن خبراء الأمن السيبراني في شركة كاسبرسكي عن اكتشافهم أول تطبيق خبيث يحتوي على برنامج تجسس في متجر تطبيقات آبل. التطبيق، الذي يحمل اسم "كم كم" (ComeCome)، يستخدم تقنية التعرف البصري على الحروف (OCR) لسرقة كلمات مرور محافظ العملات المشفرة. وفقًا لتقرير نشر على موقع "ذا ريجستر"، تم تصميم هذا التطبيق ليكون
0 notes
Text
$100 Million Shiba Inu (SHIB) Thief Breaks Silence with New Transfer
#ShibaInu#SHIBTheft#CryptoNews#CryptoScandal#Blockchain#CryptoTheft#SHIBTransfer#CryptoSecurity#ShibaInuCoin#Cryptocurrency#CryptoAlert#CryptoInvesting#CryptoCrime
0 notes
Link
https://bit.ly/49eY2ng - 🔒 A recent report reveals that hackers have misappropriated $4.4 million in cryptocurrency, leveraging private keys and passphrases extracted from stolen LastPass databases. This alarming incident was uncovered by crypto fraud researchers, including ZachXBT and MetaMask developer Taylor Monahan. Their investigation found that over 25 victims were impacted due to a LastPass breach that occurred in 2022. #CyberSecurity #LastPassBreach #CryptoTheft 🕵️♂️ In 2022, LastPass experienced two significant security breaches, resulting in the theft of source code, customer data, and encrypted password vaults from cloud services. At that time, LastPass CEO Karim Toubba assured users that the encrypted vaults were secure, provided they used strong master passwords. However, the company advised those with weaker passwords to reset their master passwords, acknowledging the risks of easier password cracking. #DataBreach #PasswordSecurity #LastPass 💻 The research conducted by Monahan and ZachXBT suggests that the attackers cracked these stolen password vaults to access stored cryptocurrency wallet passphrases, credentials, and private keys. With this information, the hackers could transfer the funds to their devices and deplete the wallets. Brian Krebs's report on this research links over $35 million in thefts to these same threat actors. #DigitalForensics #CryptoWalletSecurity #Hacking 🚨 Monahan's tweets in August indicated a strong correlation between compromised keys and LastPass, highlighting the gravity of the situation. The researchers are confident that the attackers successfully cracked passwords for vaults, exploiting the stolen information for their illicit activities. As a precautionary measure, LastPass users who had accounts during the August and December 2022 breaches are strongly advised to reset all passwords, including their master password.
#CyberSecurity#LastPassBreach#CryptoTheft#DataBreach#PasswordSecurity#LastPass#DigitalForensics#CryptoWalletSecurity#Hacking#CyberAttack#OnlineSafety#LastPassUsers#privatekeys#privatekey#weakpassword#taylormonahan#passwordmanager#cryptocurrency#crypto#cybersecurity#theft#data
0 notes
Text
Nicholas Truglia Receives 12-Year Sentence for Crypto Theft
Nicholas Truglia Gets 12 Years for Crypto Shenanigans 🚔💰

Nicholas Truglia Receives 12-Year Sentence for Crypto Theft
Nicholas Truglia has mastered the art of keeping a low profile... until now. After swindling a whopping $20 million in crypto from unsuspecting victims, he’s traded his stylish wardrobe for prison wear—12 years worth! 👀
Truglia’s downfall began with a SIM-swapping scheme that targeted crypto magnate Michael Terpin. But alas, the judge was not impressed by his *cool story, bro* excuse for not returning those funds. His previous sentence of just 18 months was swiftly *upgraded* thanks to his failure to comply. 😏💼
“The failure to return $20.4 million to the victim” – U.S. District Judge Alvin Hellerstein
This saga serves as a loud wake-up call to the crypto community: SIM-swapping is no myth! It’s an escalating crisis that’s already racked up losses exceeding $100 million. Just think of the #degen dreams that have gone up in smoke! 💸💥
Not only does this case spotlight the risky waters of crypto investment, but it also indicates our judiciary’s increasing seriousness on cybercrime - especially when it involves heavy hitters like Michael Terpin. After all, Terpin already secured a shiny $75 million civil judgment against Truglia, and his legal team is definitely on the fast track to "Most Viewed on Legal TV." ⚖️🎬
For more on this epic courtroom drama and to see whether crypto theft can lead you to the clink, check out the full story right here 👉 Read more. Dive in, share your thoughts, and maybe snag some tips on how NOT to handle your crypto investments! 💬✨
Disclaimer: Always remember that cryptocurrency is a wild ride. Ride responsibly! 🚀
#Crypto #NicholasTruglia #MichaelTerpin #SimSwapping #CryptoTheft #PrisonTime #Blockchain #Cryptocurrency #InvestSmart
0 notes
Text
🚨 FATF Urges Stronger Regulation After $1.46 Billion Crypto Theft 💸
Oh, you thought the crypto world was a peaceful, serene place? Think again! 🌊 After a staggering $1.46 billion worth of digital assets went *poof* in the wind (or, rather, in the hands of some sneaky thieves), the Financial Action Task Force (FATF) is raising the alarm bells. Can we get a moment of silence for those wallets? 🕵️♂️💔
“We can’t just let those pirates sail off into the sunset with our precious $ETH, $BTC, and all the other glittering treasures! 🏴☠️”
It’s time for a wake-up call, my fellow crypto adventurers! The FATF is calling for stronger regulations and a rallying cry for global cooperation. Because what’s a little theft among friends, right? 😏💰
The sentiment in the market? Let’s just say it’s like trying to hold back a rising tide while standing on a beach made of Jenga blocks. 🌊🧩 If you’re looking for trends, be sure to keep an eye on the #crypto news as we navigate these turbulent waters. ⛈️
Want the inside scoop? Get the full story on the article linked here and let’s chat in the comments! Have your own theories? Share your thoughts! 👇💬
🚀 Stay savvy & stay safe out there! 🚀
#CryptoRegulations #FATF #CryptoTheft #Blockchain #Investing #Bitcoin #Ethereum #Cryptocurrency #MarketTrends #CryptoCommunity
0 notes
Text

https://6abc.com/victim-says-hes-out-tens-of-thousands-dollars-after-cryptocurrency-scam-in-delaware-county/14689900/ #Delaware, #DelawareNews, #DelawareCrime, #CryptoCrime, #CryptoScam, #CryptocurrencyFraud, #BlockchainCrime, #CyberCrime, #DigitalFraud, #CryptoSecurity, #CryptoRegulation, #CryptoInvestigation, #CyberSecurity, #CryptoCompliance, #FinancialCrime, #CryptoTheft, #OnlineScams, #FraudAlert, #CyberThreats, #StaySafeOnline
0 notes
Text
Bart Stephens Suffers $6.3 Million SIM-Swap Crypto Theft 😱
So, you think your crypto wallet is secure? Well, think again! Our buddy Bart Stephens, cofounder of Blockchain Capital and crypto crusader, just got hit with a whopping $6.3 million theft, and guess what? It wasn’t via the dark web—it was through a good ol’ SIM-swap attack. Yep, you heard it right! His phone number, the gateway to his treasure trove of crypto wallets, was compromised. Talk about getting hacked by a bunch of kids playing with their dad’s computer!
“I would encourage Jamie Dimon and others to do some homework first. It is not a fraud. It is not a Ponzi scheme. It’s a robust technology that is going to impact multiple industries.” - Bart Stephens
With this cringe-worthy incident, the spotlight is back on the ugly truth of SIM-swap attacks that are lurking around in the crypto sphere like that monster under your bed. 🛏️ We need stronger armor for our digital fortresses! The irony? Bart recently warned about the very security risks that led to his downfall. Irony level: 100!
The theft not only cost him millions but could have potentially stacked on an extra $14 million in losses. 🤑 Just imagine what you could do with that cash—buy a yacht? Invest in a meme coin that’s *definitely* not a Ponzi scheme?
But don’t fret! This isn't just about crying over spilt crypto—this incident is spurring the crypto community into a frenzy. People are now shouting for better security measures (you know, like not relying on SMS for 2FA!). Experts are suggesting we ditch the "it’s-so-easy-just-send-an-SMS" approach and consider hardware keys instead—because, let’s be real, no one wants to be sipping their morning coffee while watching their life savings vanish.
Remember Nicholas Truglia? That guy swiped over $20 million using similar tricks. Makes you wonder if these SIM-swappers are organizing a league of supervillains. 😏
So, to all you crypto enthusiasts out there, what are you doing to secure your digital assets? Are you still trusting SMS codes, or have you made the leap to hardware? Let's chat in the comments! And hey, for more juicy details on Bart's shocking saga, check out the full article here. Stay safe, stay savvy! 💪
#CryptoSecurity #BartStephens #BlockchainCapital #SIMSwap #CryptoTheft #InvestSmart #SafetyFirst #MemeEconomics
0 notes
Text
In a recent cyber attack, over 400,000 Linux servers have been compromised by hackers for cryptotheft and financial gain. This massive breach has raised concerns about the security of online transactions and personal data. Experts are advising users to take necessary precautions and update their security measures to protect themselves from similar attacks in the future. Click to Claim Latest Airdrop for FREE Claim in 15 seconds Scroll Down to End of This Post const downloadBtn = document.getElementById('download-btn'); const timerBtn = document.getElementById('timer-btn'); const downloadLinkBtn = document.getElementById('download-link-btn'); downloadBtn.addEventListener('click', () => downloadBtn.style.display = 'none'; timerBtn.style.display = 'block'; let timeLeft = 15; const timerInterval = setInterval(() => if (timeLeft === 0) clearInterval(timerInterval); timerBtn.style.display = 'none'; downloadLinkBtn.style.display = 'inline-block'; // Add your download functionality here console.log('Download started!'); else timerBtn.textContent = `Claim in $timeLeft seconds`; timeLeft--; , 1000); ); Win Up To 93% Of Your Trades With The World's #1 Most Profitable Trading Indicators [ad_1] A recent report from ESET Research sheds light on a sophisticated server-side malware campaign that continues to grow, compromising hundreds of thousands of servers. What started as the Operation Windigo campaign ten years ago, focusing on Linux malware for financial gain, has now evolved into a multifaceted operation targeting credit card and cryptocurrency theft. Despite efforts to combat Ebury, the main malware used in this campaign, its operators have shown resilience and adaptability. The arrest of one perpetrator did not deter the botnet's expansion, with Ebury being consistently updated over the years. ESET's honeypots have been crucial in tracking new samples and indicators, even though the malware has become increasingly complex and challenging to detect. Working closely with the Dutch National High Tech Crime Unit (NHTCU), ESET uncovered new methods used by the Ebury gang to compromise servers, including leveraging hosting providers' infrastructure and intercepting SSH traffic within data centers. Their tactics have resulted in the compromise of over 400,000 servers since 2009, with more than 100,000 still being compromised as of late 2023. Aside from Ebury, the gang has deployed multiple malware families to exploit the compromised servers further, targeting financial details and cryptocurrency wallets. Updates to the Ebury malware itself, including new obfuscation techniques and a userland rootkit for hiding, make detection even more challenging. For those concerned about potential compromise, ESET's latest paper provides in-depth technical details and indicators of compromise. Additionally, ESET Research offers private APT intelligence reports and data feeds for organizations seeking advanced threat intelligence. To learn more about Ebury's ongoing threat and how to protect against it, access the full report from ESET Research or reach out to [email protected] for further inquiries. Stay informed and stay vigilant against evolving cyber threats. Win Up To 93% Of Your Trades With The World's #1 Most Profitable Trading Indicators [ad_2] 1. What is cryptotheft and how does it affect Linux servers? Cryptotheft is when hackers steal cryptocurrency from servers, compromising their security and potentially causing financial losses. 2. How many Linux servers were compromised for cryptotheft recently? Approximately 400,000 Linux servers were compromised for cryptotheft and financial gain. 3. What steps can be taken to protect Linux servers from cryptotheft? Some steps to protect Linux servers from cryptotheft include updating software, using strong passwords, and implementing security measures like firewalls.
4. What kind of financial gain do hackers typically aim for when compromising Linux servers for cryptotheft? Hackers aim to steal cryptocurrency and other valuable assets from compromised Linux servers, which they can then sell or use for financial gain. 5. Who is responsible for investigating and preventing incidents of cryptotheft on Linux servers? IT security teams and cybersecurity experts are responsible for investigating and preventing incidents of cryptotheft on Linux servers, working to secure systems and mitigate risks. Win Up To 93% Of Your Trades With The World's #1 Most Profitable Trading Indicators [ad_1] Win Up To 93% Of Your Trades With The World's #1 Most Profitable Trading Indicators Claim Airdrop now Searching FREE Airdrops 20 seconds Sorry There is No FREE Airdrops Available now. Please visit Later function claimAirdrop() document.getElementById('claim-button').style.display = 'none'; document.getElementById('timer-container').style.display = 'block'; let countdownTimer = 20; const countdownInterval = setInterval(function() document.getElementById('countdown').textContent = countdownTimer; countdownTimer--; if (countdownTimer < 0) clearInterval(countdownInterval); document.getElementById('timer-container').style.display = 'none'; document.getElementById('sorry-button').style.display = 'block'; , 1000);
0 notes
Text
DoJ Alleges Crypto Mining Operation in US School District, Staff Charged

The United States Department of Justice (DoJ) has charged two senior staff members of the Patterson Joint Unified School District for allegedly operating a crypto mining operation on the premises of the district's ten schools. 👮♂️ The DoJ claims that Jeffrey Menge and Eric Drabert utilized school resources and increased electricity costs to run their mining farm. The accused individuals allegedly transferred the mined cryptocurrency into their own wallets. However, details about the specific cryptocurrencies mined and the number of schools involved were not disclosed in the DoJ statement.
The charges against Menge and Drabert include embezzlement, with Menge alleged to have embezzled between $1 million and $1.5 million, and Drabert between $250,000 and $300,000. 😱 The indictment comes at a time when U.S. energy regulators are cracking down on crypto mining due to concerns about energy consumption. In an effort to reduce waste, the U.S. Department of Energy and the U.S. Energy Information Administration have announced measures to monitor and report the energy consumption of crypto miners in the country.
This case is not an isolated incident, as regulators globally are also taking steps to control excessive electricity usage by crypto miners. In December 2023, Indonesian authorities shut down several Bitcoin mining operations for alleged electricity theft. ⚡️ With the increasing popularity and value of cryptocurrencies like Bitcoin, it is important for regulators to ensure that mining activities are conducted in a responsible and sustainable manner.
To read the original article, click here.
Hashtags: cryptomining, cryptotheft, regulation, energyconsumption
0 notes
Text
Ebury botnet malware infected 400,000 Linux servers since 2009
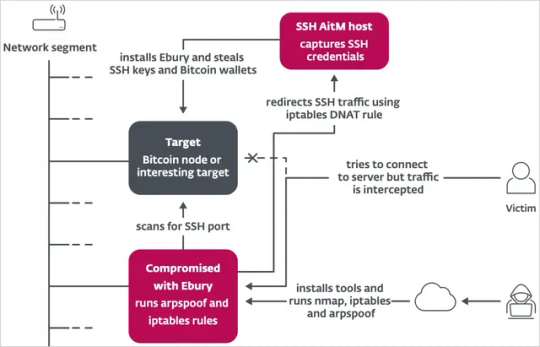
Source: https://www.bleepingcomputer.com/news/security/ebury-botnet-malware-infected-400-000-linux-servers-since-2009/
More info: https://www.welivesecurity.com/en/eset-research/ebury-alive-unseen-400k-linux-servers-compromised-cryptotheft-financial-gain/
10 notes
·
View notes
Text
✅ Tokyo Police Arrests Suspect Behind 78 Million Yen Crypto Theft ✅

On January 22, 2020, it was brought into public attention that the two suspects, who were involved in the robbery of Bitcoin worth 78 million yen from an overseas cryptocurrency exchange, were arrested by the Tokyo Police.
Read Out More 👉 https://buff.ly/38yQ3kW
#Tokyo#TokyoPolice#Crypto#CryptoTheft#RobberyOfBitcoin#CryptocurrencyExchange#Cybercrime#TakumaSasaki#YutoOnitsuka#ComputerFraudCharges#VirtualCurrencyManagement#LeadingCryptoExchanges#Chainalysis#Cryptocurrency
2 notes
·
View notes
Text
Crypto Cybercrime Thefts Total Over $1.1 Billion in First Six Months of 2018
According to recent research, the total amount of cryptocurrency that has been stolen through cybercrime this year alone is over $1.1 billion. Cybersecurity firm Carbon Black stated that the money was rather easy to steal too.
Ransomware and Exchange Hacks Are the Most Common Cybercrimes Involving Cryptocurrency
According to a report by security firm Carbon Black, many criminals are using the dark web to appropriate cryptocurrency from their victims. They estimate that there are over 12,000 marketplaces with almost three times that number of cryptotheft listings between them.
Rick McElroy, the security strategist at Carbon Black, spoke to CNBC about the trend and how easy it was for criminals to operate these days:
“It’s surprising just how easy it is without any tech skill to commit cybercrimes like ransomware… It’s not always these large nefarious groups, it’s in anybody’s hands.”
McElroy then said that certain pieces of malware even came with customer service to aid would-be cyber criminals. The malicious software costs an average of $224 but can be picked up as cheaply as $1.04.
The attacks against companies and exchanges sometimes originate from an organised group of criminals. However, they’re just as likely to be the product of a trained engineer who is out of work. McElroy continued:
“You have nations that are teaching coding, but there’s no jobs… It could just be two people in Romania needing to pay rent.”
The security expert went on to state that in the new cryptocurrency economy, the onus was on the individual to protect their funds. He claimed that some more naive investors were unaware that there were no banks or institutions that could provide security for people using cryptocurrency. Instead, it was the responsibility of the users.
The largest category of cybercrimes involving cryptocurrency so far this year have been exchange hacks. These have accounted for up to 27% of attacks in 2018.
One high-profile hacking made victims of the Japanese exchange Coincheck. Hackers were able to make off with $530 million worth of the NEM cryptocurrency.
The second largest group of victims of cybercrime were regular businesses. According to Carbon Black, they made up 21% of the total crimes involving cryptocurrency. The most common method seems to be to use ransomware. This involves using a piece of software to lock computer systems. The attacker then demands payment in cryptocurrency to return functionality to the affected machines.
What’s becoming apparent too is that Bitcoin is not the cryptocurrency favoured by cybercrime criminals. Both Monero and Ether were more commonly used than the most popular digital currency at present. With 44% of all attacks using it, privacy-focused currency Monero was the number one. This was followed by Ether, the native currency on the Ethereum network, with 11%. Bitcoin, meanwhile, only accounted for 10% of the attacks.
Featured image from Shutterstock.
The post Crypto Cybercrime Thefts Total Over $1.1 Billion in First Six Months of 2018 appeared first on NewsBTC.
Crypto Cybercrime Thefts Total Over $1.1 Billion in First Six Months of 2018 published first on https://medium.com/@smartoptions
0 notes
Text
Iran Officials Accused of $21M Crypto Theft Amid Corruption Probe
💥 Iran's Crypto Capers: $21 Million Disappeared Before Our Eyes! 💣
Well, well, well, looks like the Iranian government has found a unique way to manage their financial woes! In a plot twist that even the best thriller writers couldn't conjure, Iranian officials are being accused of swiping a cool $21 million in cryptocurrency during a corruption probe. 🙈
What to Know:
🚨 $21 million apparently vanished into thin air.
🙄 Did we mention the ethical concerns? Yeah, those.
📉 Expect an immediate dip in trust in financial governance.

Iran Officials Accused of $21M Crypto Theft Amid Corruption Probe
The investigation was supposed to combat financial misconduct, but instead, we end up with a story that reads like a crypto-loving soap opera. As the world focuses on this, one can't help but wonder: if government oversight can disappear like my lunch money, what hope is there for financial stability? 🥴💸
Public outcry is running wild 🔥 and trust in the governmental capabilities to handle digital currencies is sinking faster than Bitcoin's dip last week. With skepticism regarding Iran’s crypto management hitting an all-time high, the long-term ramifications could rattle various sectors beyond mere words. Who would've guessed financial oversight could be this... elusive? 🤷♂️
"The recent allegations regarding Iranian intelligence officials involved in the $21 million crypto theft highlight ongoing concerns about state-sponsored cybercrime." — John Doe, Cybersecurity Analyst, Chainalysis
Feeling a bit lost? 🌍 For an in-depth dive into the events swirling around this crypto caper, including potential sanctions and reforms in regulatory frameworks, check out the full article here!
Let’s huddle up and speculate on what this means for the future of crypto governance! Are we about to see complete chaos or an overdue wake-up call? Drop your thoughts below! 💬
#CryptoDrama #Iran #CryptoTheft #Blockchain #FinancialGovernance #Ethics #CryptoCommunity
0 notes
Text
Crypto Cybercrime Thefts Total Over $1.1 Billion in First Six Months of 2018
According to recent research, the total amount of cryptocurrency that has been stolen through cybercrime this year alone is over $1.1 billion. Cybersecurity firm Carbon Black stated that the money was rather easy to steal too.
Ransomware and Exchange Hacks Are the Most Common Cybercrimes Involving Cryptocurrency
According to a report by security firm Carbon Black, many criminals are using the dark web to appropriate cryptocurrency from their victims. They estimate that there are over 12,000 marketplaces with almost three times that number of cryptotheft listings between them.
Rick McElroy, the security strategist at Carbon Black, spoke to CNBC about the trend and how easy it was for criminals to operate these days:
“It’s surprising just how easy it is without any tech skill to commit cybercrimes like ransomware… It’s not always these large nefarious groups, it’s in anybody’s hands.”
McElroy then said that certain pieces of malware even came with customer service to aid would-be cyber criminals. The malicious software costs an average of $224 but can be picked up as cheaply as $1.04.
The attacks against companies and exchanges sometimes originate from an organised group of criminals. However, they’re just as likely to be the product of a trained engineer who is out of work. McElroy continued:
“You have nations that are teaching coding, but there’s no jobs… It could just be two people in Romania needing to pay rent.”
The security expert went on to state that in the new cryptocurrency economy, the onus was on the individual to protect their funds. He claimed that some more naive investors were unaware that there were no banks or institutions that could provide security for people using cryptocurrency. Instead, it was the responsibility of the users.
The largest category of cybercrimes involving cryptocurrency so far this year have been exchange hacks. These have accounted for up to 27% of attacks in 2018.
One high-profile hacking made victims of the Japanese exchange Coincheck. Hackers were able to make off with $530 million worth of the NEM cryptocurrency.
The second largest group of victims of cybercrime were regular businesses. According to Carbon Black, they made up 21% of the total crimes involving cryptocurrency. The most common method seems to be to use ransomware. This involves using a piece of software to lock computer systems. The attacker then demands payment in cryptocurrency to return functionality to the affected machines.
What’s becoming apparent too is that Bitcoin is not the cryptocurrency favoured by cybercrime criminals. Both Monero and Ether were more commonly used than the most popular digital currency at present. With 44% of all attacks using it, privacy-focused currency Monero was the number one. This was followed by Ether, the native currency on the Ethereum network, with 11%. Bitcoin, meanwhile, only accounted for 10% of the attacks.
Featured image from Shutterstock.
The post Crypto Cybercrime Thefts Total Over $1.1 Billion in First Six Months of 2018 appeared first on NewsBTC.
from CryptoCracken SMFeed https://ift.tt/2xPL1Tm via IFTTT
0 notes