#DataBackups
Explore tagged Tumblr posts
Link
In today's hyper-connected world, our smartphones hold a treasure trove of personal information – from banking details and private photos to work documents and social media accounts. This makes them prime targets for cybercriminals looking to steal data, install malware, or commit financial fraud. The good news is, that you can significantly reduce the risk of your smartphone being compromised by following some basic security best practices. This article dives deep into the National Security Agency's (NSA) "Mobile Device Best Practices" guide, outlining essential steps to secure your iOS or Android device. Tips to Secure Your Smartphone Daily Habits for Smartphone Security Here are some easy-to-implement daily practices that can significantly enhance your smartphone security: Strong Passwords and Screen Locks: Ditch the simple four-digit PIN and opt for a strong, six-digit PIN or a complex alphanumeric password for your screen lock. Additionally, enable the feature that wipes your device data after 10 unsuccessful unlock attempts. This acts as a deterrent against brute-force attacks. Bluetooth: Use Wisely: Bluetooth is a convenient way to connect to headphones and speakers, but leave it disabled when not in use. This minimizes the attack surface for hackers who might exploit Bluetooth vulnerabilities. Beware of Public Wi-Fi: Public Wi-Fi networks are notoriously insecure. Avoid accessing sensitive information like bank accounts or online banking apps while connected to public Wi-Fi. If necessary, consider using a Virtual Private Network (VPN) to encrypt your internet traffic. Maintain Physical Control: Your smartphone is a personal device. Keep it with you at all times and avoid leaving it unattended in public places. This simple precaution can prevent physical theft, which can be a gateway to further security breaches. App Management: Keeping Your Digital Ecosystem Safe The apps you install on your phone can be a double-edged sword. While they offer a plethora of functionalities, they can also pose security risks if not managed properly. Here's how to maintain a secure app environment: Download from Official Sources: Only install apps from official app stores like the App Store or Google Play Store. These stores have vetting procedures in place to minimize the risk of malware distribution. Avoid downloading apps from untrusted third-party sources. Essential Apps Only: Don't clutter your phone with unnecessary apps. Stick to installing only the apps you genuinely need and use regularly. The fewer apps you have, the smaller the attack surface for potential vulnerabilities. App Permissions: Be mindful of the permissions you grant to apps. An app requesting access to your location or microphone when it doesn't seem necessary might be a red flag. Only grant permissions that are essential for the app's functionality. Close Unused Apps: Many apps run in the background even when not actively in use. This can drain battery life and potentially expose vulnerabilities. Make it a habit to close apps you're not actively using to tighten your phone's security. Staying Updated: Software and Apps Software updates often contain critical security patches that address vulnerabilities exploited by cybercriminals. Here's why keeping your software and apps updated is crucial: Install Updates Promptly: Whenever software updates are available for your phone's operating system or apps, install them promptly. Don't procrastinate – timely updates are essential for maintaining a secure mobile environment. Automatic Updates: Consider enabling automatic updates for your phone's operating system and apps whenever possible. This ensures you're always protected with the latest security patches. Be Wary of Social Engineering and Phishing Attacks Cybercriminals often rely on social engineering tactics to trick users into compromising their own devices. Here's how to stay vigilant against such attempts: Think Before You Click: Never open suspicious email attachments or links, even if they appear to come from a trusted source. Phishing emails often try to trick you into clicking on malicious links that can download malware onto your device. Beware of Pop-Ups: Unexpected pop-ups on your phone can be a sign of a malicious website or app. Don't interact with them. Instead, force close the browser or app immediately. Advanced Security Measures For users who want to take their smartphone security to the next level, here are some additional tips: No Jailbreaking or Rooting: Jailbreaking an iPhone or rooting an Android phone gives you more control over your device, but it can also bypass security measures built into the operating system. These modifications can make your phone more vulnerable to attacks. Unless you're a highly technical user, avoid jailbreaking or rooting. Frequently Asked Questions Q: Is a fingerprint or facial recognition unlock secure enough for my phone? A: While fingerprint and facial recognition unlock features offer convenience, they might not be as secure as a strong PIN or password. Consider using a PIN or password in conjunction with fingerprint or facial recognition for an extra layer of security. Q: What if I accidentally download a malicious app? A: Most reputable antivirus and security apps can scan your phone for malware. Consider installing a reputable security app from a trusted source and running regular scans. Q: I'm not very tech-savvy. Can I still secure my phone? A: Absolutely! Many of the tips in this article, like using strong passwords and keeping your software updated, are easy to implement regardless of technical expertise.
#appsecurity#charginghabits#Cyberattacks#databackups#datatheft#jailbreaking#locationservices#NSAmobilesecurityguide#phishingattacks#publicWiFi#rooting#smartphonesecurity#socialengineering#softwareupdates#strongpasswords#TipstoSecureYourSmartphone
0 notes
Text
Data backups made easy! Buy Cheap RDP ensures your important files are securely stored on remote servers.

0 notes
Link
#cybersecurity#databackups#disasterrecovery#DisasterRecoverySite#India#MarketInfrastructureInstitutions#MIIs#PrimaryDataCentre#Sebi#SEBIcybersecurityguidelinesMIIs#SecuritiesandExchangeBoardofIndia#StockExchanges#vulnerabilityscanning
0 notes
Text
Unraveling the Enigma of the Akira Virus: An In-Depth Exploration
Discover the Akira Virus: Delve into its perplexing nature and unravel the mystery through a comprehensive exploration. Get insights on the enigma that is the Akira Virus here.
Source: https://bit.ly/45cHl94
#AkiraVirus#CybersecurityThreats#Malware#Ransomware#ComputerVirus#ZeroDayExploits#DataSecurity#CyberProtection#NetworkSecurity#DataEncryption#EndpointProtection#CyberDefense#PhishingAttacks#CyberSafety#InternetSecurity#DigitalPrivacy#OnlineThreats#CyberAwareness#CyberEducation#DataBackups#SecurityMeasures#CyberSecuritySolutions#ProtectYourself#DataIntegrity#DataPrivacy#Cybercrime#InternetSafetyTips
0 notes
Text
O&O DiskImage 20
Easily backup your entire computer with a single click That is, until they experience their first loss of important files due to software, hardware, or user error—only then does the true value of a reliable, up-to-date backup become crystal clear

3 notes
·
View notes
Text

𝓮-𝓒𝓐𝓣𝓐𝓛𝓞𝓖 𝓕𝓮𝓪𝓽𝓾𝓻𝓮𝓼 :
𝘾𝙪𝙨𝙩𝙤𝙢𝙞𝙯𝙖𝙗𝙡𝙚 ✨ Tailor the e-CATALOG to your specific needs with customizable options that fit your business perfectly.
𝘽𝙖𝙘𝙠 𝙊𝙛𝙛𝙞𝙘𝙚 & 𝘾𝙪𝙨𝙩𝙤𝙢 𝘿𝙖𝙨𝙝𝙗𝙤𝙖𝙧𝙙 📊 Manage your catalog content efficiently with a robust back office and custom dashboard.
𝙎𝙚𝙖𝙧𝙘𝙝 𝙀𝙣𝙜𝙞𝙣𝙚 𝙊𝙥𝙩𝙞𝙢𝙞𝙯𝙚𝙙 🔍 Boost your online visibility with our search engine optimized platform.
𝘾𝙡𝙤𝙪𝙙-𝘽𝙖𝙨𝙚𝙙 𝙒𝙚𝙗𝙨𝙞𝙩𝙚 ☁️ Access your catalog from anywhere with our secure, cloud-based website.
24/7 𝙎𝙚𝙧𝙫𝙞𝙘𝙚 𝙎𝙪𝙥𝙥𝙤𝙧𝙩 🕒 Benefit from round-the-clock service support to address any issues or questions.
𝙀𝙛𝙛𝙤𝙧𝙩𝙡𝙚𝙨𝙨 𝘼𝘾𝙀𝙎 & 𝙋𝙄𝙀𝙎 𝘾𝙤𝙣𝙫𝙚𝙧𝙨𝙞𝙤𝙣 ⚙️ Easily convert ACES & PIES data into a user-friendly catalog format.
𝙍𝙖𝙥𝙞𝙙 𝙎𝙚𝙖𝙧𝙘𝙝 𝘾𝙖𝙥𝙖𝙗𝙞𝙡𝙞𝙩𝙞𝙚𝙨 🚀 Quickly search through billions of data entries with our powerful search feature.
𝘿𝙖𝙩𝙖 𝘽𝙖𝙘𝙠𝙪𝙥 🔒 Rest easy knowing your data is securely backed up.
𝙈𝙤𝙗𝙞𝙡𝙚 𝙁𝙧𝙞𝙚𝙣𝙙𝙡𝙮 📱 Enjoy seamless navigation on all devices with our mobile-friendly design.
𝙀𝙖𝙨𝙮 𝙉𝙖𝙫𝙞𝙜𝙖𝙩𝙞𝙤𝙣 🧭 Navigate effortlessly through the catalog with intuitive and user-friendly design.
For more information, visit https://www.anzael.com/e-catalog Enhance your e-commerce experience with @anzaelllc's advanced e-CATALOG solutions!
#ecatalog#pcfitment#CustomizableSolutions#cloudbased#seo#24x7Support#databackup#mobilefriendly#EffortlessNavigation#rapidsearch
2 notes
·
View notes
Text
2 notes
·
View notes
Text

Home - Monetta Software Solutions - Tally
Monetta Software Solutions are Certified Sales & Service Partner for Tally since 2009 serving more than 3500 clients for their business accounting needs.
Know More :- https://monettaindia.com/
#Tally#Tally Cloud#Tally Software#Tally Renewal#Tally Customization#GreytHR#TSS#TDS#Tally Prime#Tally ERP-9#Tally Monetta#Tally on Cloud#CloudAccounting#BusinessGrowth#tallyprime#tally#tallysolutions#databackup#tallysoftware#tallysupport#monettasoftware#monettaindia#tallyprimeaws#silver#tallyoncloud#monetta#business#software#businessmanagement#TallyERP9
2 notes
·
View notes
Text

🔒 Protect Your Data, Secure Your Peace of Mind! 🔒 Don't risk losing precious files and memories! 😱 Safeguard your data with us. Itech Xpress can provide you the best data backup and security service that also on the same day.
Visit our website for more details: https://itechxpressinc.com/networking
#datasafeguarding#automatedbackup#hardwarefailures#softwarefailures#backupsystem#databackup#datasecurity#itechxpress
2 notes
·
View notes
Text



👏🌟Imagine scrubbing 8K footage with D1 SSD Pluslike it’s 1080p. Never let inspiration slip away! D1 SSD Plus offers up to 8TB of storage and delivers 40Gbps of data transfer bandwidth, turning any space into your creative studio. Capture ideas on the go, create without waiting.🥰 🔥Find more details: https://www.terra-master.com/global/products/homesoho-das/d1-ssd-plus.html #TerraMaster #TerraMasternas #TerraMasterdas #videoediting #storagesolutions #8Kvideo #NVMessd
0 notes
Text
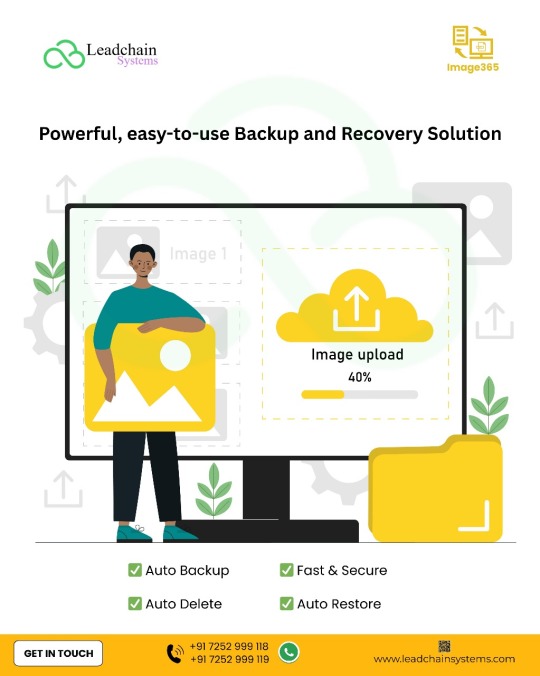
Leadchain Image365 – Your Smart Backup & Recovery Partner
Never worry about data loss again! With Leadchain Image365, enjoy a powerful, fast, and secure backup solution designed for businesses of all sizes. Whether it's automatic backups, quick restores, or secure data management, Image365 has you covered.
Key Features: Auto Backup – Set it once, and we’ll handle the rest. Fast & Secure – Lightning-fast backups with enterprise-grade encryption. Auto Delete – Automatically manage old data to save space. Auto Restore – Recover files instantly, anytime you need them.
Contact Us: 📞 +91 7252 999 118 | +91 7252 999 119 🌐 www.leadchainsystems.com
#leadchain#image365#databackup#smartrecovery#cloudstorage#businessdata#backupsolution#datasecurity#fastbackup#securedata#cloudbackup#techsolutions#digitalprotection#webdevelopment
0 notes
Text

Your Data, Our Priority. https://ibraniacsoftware.com/our-services/data-backup-recovery-services/
0 notes
Text

#InformaticaCloud#DataIntegration#CloudMigration#IICS#CloudSecurity#DataGovernance#AIinCloud#HybridCloud#CloudComputing#DataBackup#DataRecovery#CloudSolutions#DigitalTransformation#ProphecyTechs#SmartCloud
0 notes
Text
Exact Audio Copy (EAC) mantiene abierta la bandeja de CD
La solución la encontré en un foro, este es el resumen de lo que le funcionó al usuario original.
Yo solo desactivé la reproducción automática de medios extraíbles (todos, de todas formas siempre los tengo así).
A él le pasaba en Windows 10 a mí en Windows 11.
La ruta en Win11 es:
Configuración/ Bluetooth y dispositivos/ Reproducción automática
Desactivar "Usar la reproducción automática para todos los medios y dispositivos"
El usuario original actualizó drivers y siguió otros pasos en Win10, aquí pongo el link original como referencia.
Original post:
Steve Hoffman Music Forums. (2021, 18 de febrero). Exact Audio Copy (EAC) disc insertion problem. https://forums.stevehoffman.tv/threads/exact-audio-copy-eac-disc-insertion-problem.1060376/
0 notes
Text
Software Maintenance and Up-Gradation services
SoftwareMaintenance and Up-Gradation Ongoing support is essential to ensure smooth and uninterrupted operations of any digital platform. Maintenance and up-gradation services encompass a range of activities designed to keep systems secure, efficient, and up-to-date with the latest technological standards.
Regular maintenance ensures smooth, secure, and updated system performance. It includes:
Backups – Protects data through regular backups.
Bug Fixes – Resolves technical issues for stable operation.
Security Updates – Keeps systems safe from vulnerabilities.
Performance Optimization – Ensures fast, efficient performance.
Upgrades – Adds new features and updates technologies.
Technical Support – Ongoing assistance for any issues.
These services help reduce downtime, enhance security, and improve overall system reliability.
📞 Phone Number: +91 9511803947
📧 Email Address: [email protected]

#Maintenance#SystemUpgrade#TechSupport#BugFixing#DataBackup#CyberSecurity#SoftwareMaintenance#PerformanceOptimization#ITSupport#SystemUpgradation#TechnicalAssistance
0 notes
Text

🔒 Protect Your Business from Data Loss with Clonetab’s Real-Time Backup & Recovery! In today's fast-paced business world, data loss can be catastrophic. That's where Clonetab's Real-Time Database Backup & Recovery comes in to protect your most valuable asset �� your data.
Here’s why your business NEEDS Clonetab’s solution:
✔ Config for both Oracle EBS + DB ✔ Seamless Sync between Database & Application ✔ Save up to 90% on Storage Costs ✔ 1 Click to Re-Sync – Fast & Effortless
Clonetab ensures that your data is always safe, synchronized, and easily recoverable with minimal storage overhead. It’s your peace of mind in just one click.
🚀 Ready to see it in action? Book a demo with us today and experience how Clonetab can secure your data like never before!
0 notes