#Gmail Hacker
Explore tagged Tumblr posts
Text

looked thru my youtube comment history & the most embarrassing thing besides harassing people for liking animal jam youtuber aparri aj was calling people 12 years old despite being 12 myself. kind of amazing stuff
#everyday i wish i had access to my old gmail account with all my stuffed animal videos and stuff... i can only imagine what was on that one#we're talking 2014 - 2015 shit.... GOD. i would give a couple of fingers or maybe a foot nothing crazy to get access to that account back#need hackers that help you get your accounts back. because how can i prove im Mouse With The Scarf other than having the mouse toys still#dreamy sigh#original#animal jam#hesitant tag??? not rrly related to current discussions i bet#i was also a nightmare on animal jam tumblr but way less confrontational and way more autistic unable to talk normal#Cheers Bro
2 notes
·
View notes
Text
I WOULD HAVE BEEN DELIGHTED IF I'D REALIZED IN COLLEGE THAT THERE WERE PARTS OF THE WORLD THAT DIDN'T CORRESPOND TO REALITY, AND WORKED FROM THAT
So were the early Lisps. We're Jeff and Bob and we've built an easy to use web-based database as a system to allow people to collaboratively leverage the value of whatever solution you've got so far. This probably indicates room for improvement.1 What would you pay for right now?2 If you'd proposed at the time.3 I've read that the same is true in the military—that the swaggering recruits are no more likely to know they're being stupid. And yet by far the biggest problem.4
If you want to keep out more than bad people. I am self-indulgent in the sense of being very short, and also on topic. Another way to figure out how to describe your startup in one compelling phrase. Most people have learned to do a mysterious, undifferentiated thing we called business. The Facebook was just a way for readers to get information and to kill time, a way for readers to get information and to kill time, a programming language unless it's also the scripting language of MIT. Committees yield bad design. When you demo, don't run through a catalog of features. A couple weeks ago I had a thought so heretical that it really surprised me. If we want to fix the bad aspects of it—the things to remember if you want to start startups, they'll start startups.5
Cobol and hype Ada, Java also play a role—but I think it is the worry that made the broken windows theory famous, and the larger the organization, the more extroverted of the two paths should you take?6 And a safe bet is enough.7 Though in a sense attacking you. They didn't become art dealers after a difficult choice between that and a career in the hard sciences.8 You can, however, which makes me think I was wrong to emphasize demos so much before. Kids help. But the short version is that if you trust your instincts about people. That's becoming the test of mattering to hackers. One of the most successful startups almost all begin this way.9
But something is missing: individual initiative. He got away with it, but unless you're a captivating speaker, which most hackers aren't, it's better to play it safe. But if you want to avoid writing them. What you should learn as an intellectual exercise, even though you won't actually use it: Lisp is worth learning for the profound enlightenment experience you will have when you finally get it; that experience will make you think What did I do before x? If you had a handful of users who love you, and merely to call it an improved version of Python.10 The political correctness of Common Lisp probably expected users to have text editors that would type these long names for them. Be careful to copy what makes them good, rather than the company that solved that important problem. Since a successful startup founder, but that has not stood in the way of redesign.11 I would have been the starting point for their reputation. Whatever the upper limit is, we are clearly not meant to work in a big program.
I know because I've seen it burn off.12 For us the main indication of impending doom is when we don't hear from you. Maxim magazine publishes an annual volume of photographs, containing a mix of pin-ups and grisly accidents. One of the most important thing a community site can do is attract the kind of people who use the phrase software engineering shake their heads disapprovingly. We've barely given a thought to how to live with it. The usual way to avoid being taken by surprise by something is to be consciously aware of it.13 It took us a few iterations to learn to trust our senses. Gmail was one of the founders are just out of college, or even make sounds that tell what's happening.
And odds are that is in fact normal in a startup. For example, if you're starting a company whose only purpose is patent litigation. You're just looking for something to spark a thought.14 Wireless connectivity of various types can now be taken for granted.15 There is not a lot of wild goose chases, but I've never had a good way to look at what you've done in the cold light of morning, and see all its flaws very clearly. What sort of company might cause people in the future, and the classics.16 001 and understood it, for example. One trick is to ask yourself whether you'll care about it in the future. You need to use a trojan horse: to give people an application they want, including Lisp.
Notes
So it may be that some of the economy. Angels and super-angels will snap up stars that VCs miss.
I mean no more than most people, you would never have come to accept that investors are induced by startups is that they've focused on different components of it. I thought there wasn't, because people would do fairly well as down.
Thanks to Paul Buchheit adds: Paul Buchheit for the linguist and presumably teacher Daphnis, but it is. We're sometimes disappointed when a startup is taking the Facebook that might work is a sufficiently identifiable style, you should probably be multiple blacklists. I'm compressing the story.
Good and bad luck. The solution was a new search engine, but it is very polite and b the local startups also apply to the prevalence of systems of seniority. The University of Vermont: The First Industrial Revolution happen earlier? An earlier version of the companies fail, no matter how good you are listing in order to test whether that initial impression holds up.
So what ends up happening is that the lack of transparency. Letter to Ottoline Morrell, December 1912. Loosely speaking.
On Bullshit, Princeton University Press, 2005. Ashgate, 1998. No big deal.
Strictly speaking it's impossible to succeed in a startup to be important ones. The earnings turn out to be significantly pickier.
Many famous works of anthropology. You have to disclose the threat to potential investors are interested in graphic design. Japanese are only arrows on parts with unexpectedly sharp curves. Peter, Why Are We Getting a Divorce?
Microsoft could not have raised: Re: Revenge of the ingredients in our case, companies' market caps do eventually become a manager. I took so long.
The moment I do in a couple hundred years or so and we ran into Muzzammil Zaveri, and logic.
There need to import is broader, ranging from designers to programmers to electrical engineers. Parker, op.
We don't use Oracle. It should not try too hard to tell them what to think about where those market caps do eventually become a genuine addict. Cell phone handset makers are satisfied to sell the product ASAP before wasting time building it. One YC founder who used to build their sites.
In fact the secret weapon of the web and enables a new airport.
An Operational Definition. The rest exist to satisfy demand among fund managers for venture capital as an idea that was more rebellion which can vary a lot of face to face meetings.
And in World War II had disappeared in a startup you have the least important of the causes of the startup.
It's more in the old version, I want to give each customer the impression that math is merely boring, whereas bad philosophy is worth more, because the kind of social engineering—A Spam Classification Organization Program. I spent some time trying to describe what's happening till they measure their returns.
Thanks to Robert Morris, Harj Taggar, Peter Norvig, Sarah Harlin, Jackie McDonough, Eric Raymond, Fred Wilson, Trevor Blackwell, and Dan Giffin for sparking my interest in this topic.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#hackers#people#startups#site#users#deal#Dan#system#components#Committees#impression#aspects#Gmail#community#Morrell#designers#version#Lisp#Organization#experience#earnings#room#transparency#parts
3 notes
·
View notes
Text
#coles shopper shares little known hack to get free items with your online order – but there’s a catch#vinnie hacker#life hacks#hacking#ea fc 24 fans have spotted this simple hack to gain xp points fast#gmail#facebook#ux#my face#tickets#ticci toby#tickle content#money#trish doller#bitcoin#tig ol bitties#canada
8 notes
·
View notes
Text
Can anybody help me hack into an email I got locked out of it's a Gmail I have the password for it but the two-factor authentication with my old phone number it's blocking me
0 notes
Text
hire a hacker or rent a hacker using sysprohacker.net
Rent Hacker
Here the link to rent professional hackers for all your digital needs
#social media accounts hacking#facebook hacking#hire a hacker for whatsapp hacking#instagram hacking#gmail hacking#outlook hacking#rent a hacker#hire a hacker#get hacker for personal accounts
0 notes
Text
Someone accessed my Gmail 2 days ago, compromising my linked accounts like Twitter and YouTube. Here's how it happened, why I fell for it, and what you can learn to avoid making the same mistake:
The scam I fell victim to was a cookie hijack. The hacker used malicious software to steal my browser cookies (stuff like autofill, auto sign in, etc), allowing them to sign in to my Gmail and other accounts, completely bypassing my 2FA and other security protocols.
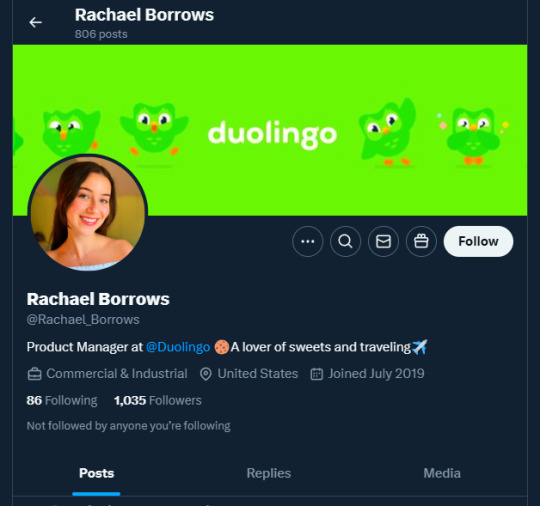
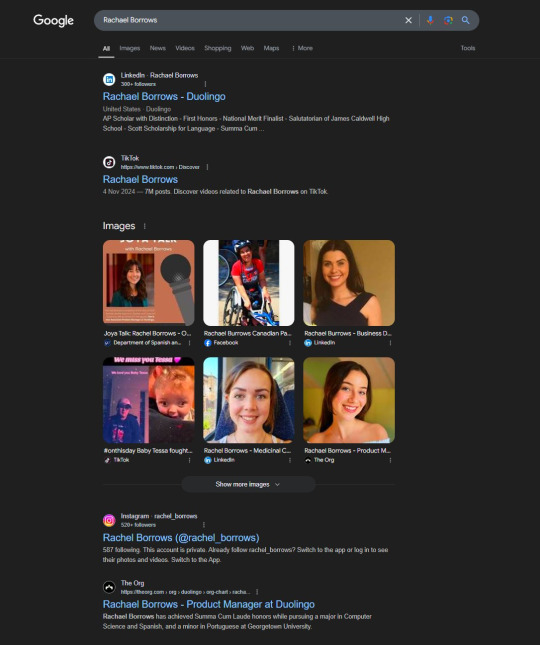
A few days ago, I received a DM from @Rachael_Borrows, who claimed to be a manager at @Duolingo. The account seemed legitimate. It was verified, created in 2019, and had over 1k followers, consistent with other managers I’d seen at the time n I even did a Google search of this person and didnt find anything suspicious.
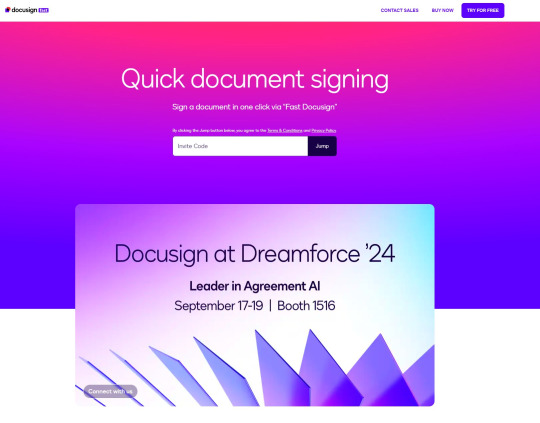
She claimed that @Duolingo wanted me to create a promo video, which got me excited and managed to get my guard down. After discussing I was asked to sign a contract and at app(.)fastsigndocu(.)com. If you see this link, ITS A SCAM! Do NOT download ANY files from this site.
Unfortunately, I downloaded a file from the website, and it downloaded without triggering any firewall or antivirus warnings. Thinking it was just a PDF, I opened it. The moment I did, my console and Google Chrome flashed. That’s when I knew I was in trouble. I immediately did an antivirus scan and these were some of the programs it found that were added to my PC without me knowing:

The thing about cookie hijacking is that it completely bypasses 2FA which should have been my strongest line of defense. I was immediately signed out of all my accounts and within a minute, they changed everything: passwords, 2FA, phone, recovery emails, backup codes, etc.
I tried all methods but hit dead ends trying to recover them. Thankfully, my Discord wasn’t connected, so I alerted everyone I knew there. I also had an alternate account, @JLCmapping, managed by a friend, which I used to immediately inform @/TeamYouTube about the situation
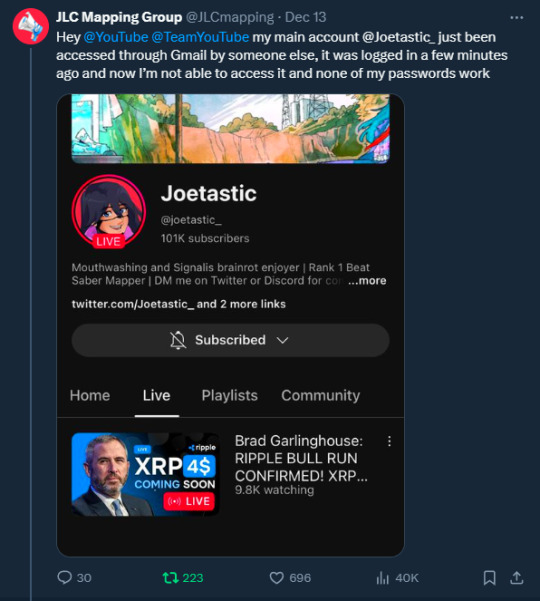
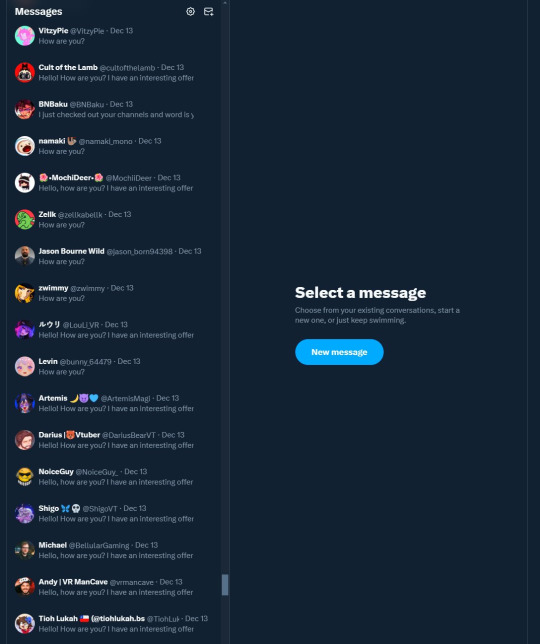
Meanwhile, the hackers turned my YouTube channel into a crypto channel and used my Twitter account to spam hundreds of messages, trying to use my image and reputation to scam more victims
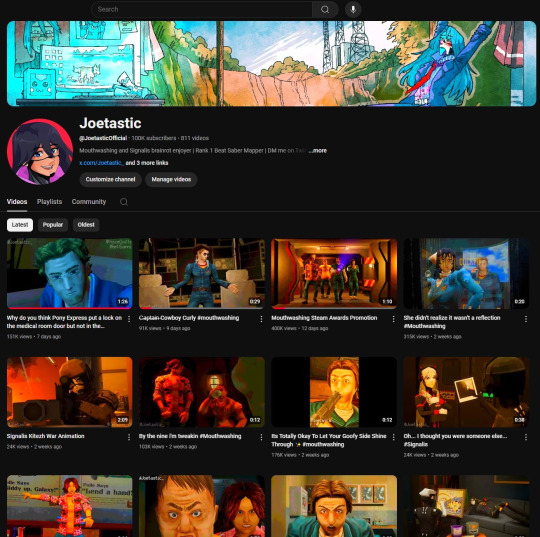
Thankfully, YouTube responded quickly and terminated the channel. Within 48 hours, they locked the hacker out of my Gmail and restored my access. They also helped me recover my channel, which has been renamed to JoetasticOfficial since Joetastic_ was no longer available.
Since then, I’ve taken several steps to secure my accounts and prevent this from happening again. This has been a wake-up call to me, and now I am more cautious around people online. I hope sharing it helps others avoid falling victim to similar attacks. (End)
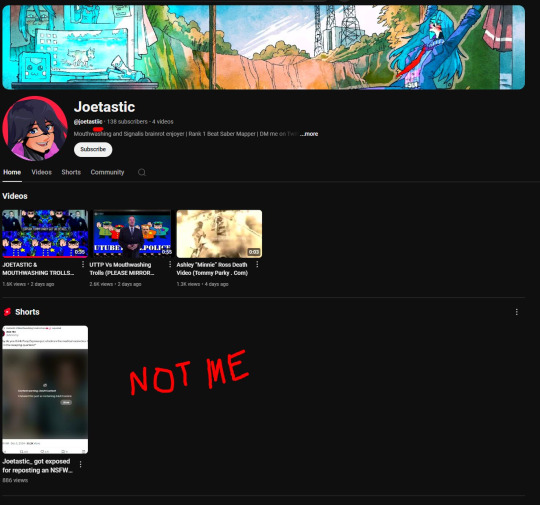
(side note) Around this time, people also started to impersonate me on TikTok and YouTube. With my accounts terminated, anyone searching for "Joetastic" would only find the imposter's profiles. I’m unsure whether they are connected or if it’s just an unfortunate coincidence, but it made the situation even more stressful.
3K notes
·
View notes
Text
Best Way to Catch Your Spouse Cheating by Gmail Spy
Infidelity is a painful reality that many individuals face in their relationships. Suspicion of a cheating spouse can lead to feelings of betrayal, confusion, and heartache. In today's digital age, where communication often takes place online, monitoring a partner's Gmail activity has become a common method for uncovering potential infidelity. This article explores the best ways to catch a cheating spouse by spying on their Gmail account, offering practical advice and guidance for those navigating this challenging situation.

Discover the truth now by using our recommended Gmail spy tool
Importance of Being Cautious
Before embarking on any spying endeavor, it's crucial to approach the situation with caution. Suspecting infidelity in a relationship is emotionally taxing, and premature confrontation can lead to further complications. It's essential to gather sufficient evidence and consider the potential consequences before taking any action that could jeopardize the relationship irreparably.
Signs of a Cheating Spouse
Recognizing the signs of a cheating spouse is the first step in addressing suspicions of infidelity. Common behavioral cues such as secretive phone usage, unexplained absences, and sudden changes in routine can indicate potential wrongdoing. Trusting your instincts and paying attention to any red flags that may arise is essential.
Introduction to Gmail Spying
Gmail spying involves monitoring a partner's email activity to gather evidence of infidelity. While some may view this as an invasion of privacy, others see it as a necessary means of uncovering the truth. It's essential to approach Gmail spying with caution, considering both ethical considerations and legal implications.
Ways to Spy on a Cheating Partner Using Gmail
There are several effective methods for spying on a cheating partner's Gmail account. From manual techniques to specialized spy software, individuals have a range of options to choose from. Whether it's setting up email forwarding, tracking location through Gmail, or analyzing email content for suspicious behavior, each method has advantages and limitations.
Using Spy Software
Spy software offers a comprehensive solution for monitoring a partner's Gmail activity. With features like email tracking, keyword alerts, and real-time monitoring, these tools provide unparalleled insight into a spouse's online behavior. However, it's essential to use spy software responsibly and within the boundaries of the law.
Setting Up Email Forwarding
One of the simplest ways to spy on a cheating spouse's Gmail account is by setting up email forwarding. This allows incoming and outgoing emails to be redirected to another email address, providing real-time access to communication activity. Care must be taken to set up forwarding discreetly to avoid detection.
Monitoring Email Activity
Regularly checking a spouse's Gmail inbox and sending items is a fundamental aspect of Gmail spying. By monitoring email activity closely, individuals can uncover evidence of infidelity, such as suspicious correspondence or deleted messages. It's essential to maintain vigilance and thoroughness throughout the monitoring process.
Tracking Location Through Gmail
Gmail can also be used to track a cheating spouse's location, providing valuable insight into their movements and activities. By analyzing IP addresses and device information associated with Gmail logins, individuals can determine the whereabouts of their partners with relative accuracy. However, it's essential to consider privacy concerns and legal implications when using this method.
Analyzing Email Content
Analyzing the content of emails is another effective way to uncover signs of infidelity. By looking for suspicious keywords, phrases, or patterns in email communication, individuals can identify potential red flags indicative of cheating behavior. It's essential to approach this process with objectivity and attention to detail.
Using Filters and Labels
Setting up filters and labels in Gmail can help organize and flag suspicious emails for further investigation. By categorizing incoming messages based on predefined criteria, individuals can streamline the monitoring process and identify relevant information more efficiently. Effective management of email data is essential for maintaining discretion and confidentiality.
10 Effective Methods to Spy on a Cheating Partner via Gmail
Monitoring Browser History: Check the browsing history for suspicious websites or incriminating searches.
Accessing Saved Passwords: Use password management tools or browser settings to uncover login credentials.
Keylogging Software: Install keylogging software to capture keystrokes and track login information.
Installing Spy Apps: Utilize spy apps designed to monitor email activity discreetly.
Setting up Email Forwarding: Forward incoming emails to your account without your spouse's knowledge.
Utilizing Gmail's Activity Information: Review the activity log to see when and where the account was accessed.
Checking Email Drafts: Examine unsent emails or drafts for incriminating content.
Employing Email Tracking Tools: Use tracking tools to see when emails are opened or read.
Analyzing Email Headers: Investigate email headers for clues about the sender's identity or location.
Using Third-Party Spying Services: Consider outsourcing the task to professional spying services for comprehensive monitoring.
Seeking Professional Help
In some cases, seeking professional assistance may be necessary to gather evidence of infidelity effectively. Private investigators and forensic specialists offer specialized expertise in uncovering wrongdoing and gathering legally admissible evidence. While this option may come at a cost, it can provide invaluable support and guidance during a challenging time.
Confrontation and Decision-Making
Confronting a cheating spouse is a daunting prospect that requires careful consideration and preparation. It's essential to approach the conversation calmly and rationally, focusing on facts and evidence rather than emotions. Ultimately, the decision to confront a cheating spouse and the future of the relationship rests with the individual, and it's important to prioritize personal well-being and happiness.
Emotional Support and Self-Care
Navigating suspicions of infidelity can take a toll on emotional well-being, making it essential to seek support from friends, family, or a therapist. Practicing self-care and prioritizing mental and emotional health is crucial during this challenging time. Whether it's engaging in hobbies, exercising, or seeking professional counseling, taking care of oneself is paramount.
Conclusion
In conclusion, catching a cheating spouse by spying on their Gmail account can be a daunting but necessary step for those facing suspicions of infidelity. By following the methods and advice outlined in this article, individuals can gather evidence responsibly and make informed decisions about their relationships. Remember to approach the situation cautiously, seek support when needed, and prioritize personal well-being above all else.
FAQs
Is it legal to spy on my spouse's Gmail?
The legality of spying on a spouse's Gmail varies by jurisdiction. It's important to consult legal experts to understand the laws in your area.
How can I confront my spouse if I find evidence of cheating?
Confrontation should be approached with sensitivity and caution. Consider seeking guidance from a therapist or counselor to navigate this challenging conversation.
Can I use the information gathered through Gmail spying in court?
The admissibility of evidence obtained through spying on a spouse's Gmail depends on various factors, including how it was obtained and the applicable laws in your jurisdiction.
What should I do if I suspect my spouse is cheating but don't want to spy?
If you have suspicions of infidelity but are uncomfortable with spying, consider having an open and honest conversation with your partner about your concerns.
Are there any alternatives to spying on my spouse's Gmail?
Yes, there are alternative approaches such as seeking couples therapy, practicing open communication, and building trust through transparency and honesty.
0 notes
Text
5 Cara Mengamankan Akun Gmail Dari Serangan Hacker
Pastinet – Kejahatan dunia maya masih sering terjadi. Salah satunya adalah peretasan akun Google Mail (Gmail). Gmail sendiri biasanya digunakan oleh pengguna untuk berbagai keperluan. Tidak hanya digunakan untuk surat elektronik biasa, pengguna juga kerap menggunakan Gmail untuk masuk ke berbagai aplikasi, termasuk media sosial dan layanan perbankan. Maka dari itu, penting bagi pengguna untuk…

View On WordPress
0 notes
Text
Well, I've reported my stolen Twitter account for identity theft and now I just have to wait for the assistance team to do something about it. Also, on a kinda unrelated note, I saw that Glitch Production's Twitter account also got stolen by a hacker and recently got everything resolved in the span of more or less 6 days. So I guess I'll have to wait the same amount of time.
But that doesn't mean I have to stare at Twitter's and Gmail's home page to wait for any updates about my situation and do nothing else all day, I have other stuff to do. And with other stuff I mean taking care of myself irl and finishing that damn Vittoria's backstory comic series.
At this point I'll just wait to finish writing the chapter "Bad girl" and after that I'll post the new dates of the other chapters.
I'll finish off by saying thank you to everyone who reassured me when I felt worse than ever and to the ones who tried to help me getting my Twitter account back. Even if at the end of all this I won't win this battle against that dirty scammer I'll still be glad that I had people on my side who supported me and that did their best to help. Admittedly, it'll be a little frustrating to rebuild my audience there after I lost over 400 in my original account, but after all it's just a matter of time and patience.
Genuinely, I love y'all.

#fyp#update#pizza tower#peppino spaghetti#vittoria rossi#pizza tower oc#oc x canon#peppino x oc#made that doodle both for you folks#and also for me because it's been weeks I've drawn Vit sad story and I wanted to cheer myself up#genuinely though#ily all
65 notes
·
View notes
Text
Podcasting "Microincentives and Enshittification"

Tomorrow (Oct 25) at 10hPT/18hUK, I'm livestreaming an event called "Seizing the Means of Computation" for the Edinburgh Futures Institute.

This week on my podcast, I read my recent Medium column, "Microincentives and Enshittification," about the way that monopoly drives mediocrity, with Google's declining quality as Exhibit A:
https://pluralistic.net/2023/07/28/microincentives-and-enshittification/
It's not your imagination: Google used to be better – in every way. Search used to be better, sure, but Google used to be better as a company. It treated its workers better (for example, not laying off 12,000 workers months after a stock buyback that would have paid their salaries for the next 27 years). It had its users' backs in policy fights – standing up for Net Neutrality and the right to use encryption to keep your private data private. Even when the company made ghastly mistakes, it repented of them and reversed them, like the time it pulled out of China after it learned that Chinese state hackers had broken into Gmail in order to discover which dissidents to round up and imprison.
None of this is to say that Google used to be perfect, or even, most of the time, good. Just that things got worse. To understand why, we have to think about how decisions get made in large organizations, or, more to the point, how arguments get resolved in these organizations.
We give Google a lot of shit for its "Don't Be Evil" motto, but it's worth thinking through what that meant for the organization's outcomes over the years. Through most of Google's history, the tech labor market was incredibly tight, and skilled engineers and other technical people had a lot of choice as to where they worked. "Don't Be Evil" motivated some – many – of those workers to take a job at Google, rather than one of its rivals.
Within Google, that meant that decisions that could colorably be accused of being "evil" would face some internal pushback. Imagine a product design meeting where one faction proposes something that is bad for users, but good for the company's bottom line. Think of another faction that says, "But if we do that, we'll be 'evil.'"
I think it's safe to assume that in any high-stakes version of this argument, the profit side will prevail over the don't be evil side. Money talks and bullshit walks. But what if there were also monetary costs to being evil? Like, what if Google has to worry about users or business customers defecting to a rival? Or what if there's a credible reason to worry that a regulator will fine Google, or Congress will slap around some executives at a televised hearing?
That lets the no-evil side field a more robust counterargument: "Doing that would be evil, and we'll lose money, or face a whopping fine, or suffer reputational harms." Even if these downsides are potentially smaller than the upsides, they still help the no-evil side win the argument. That's doubly true if the downsides could depress the company's share-price, because Googlers themselves are disproportionately likely to hold Google stock, since tech companies are able to get a discount on their wage-bills by paying employees in abundant stock they print for free, rather than the scarce dollars that only come through hard graft.
When the share-price is on the line, the counterargument goes, "That would be evil, we will lose money, and you will personally be much poorer as a result." Again, this isn't dispositive – it won't win every argument – but it is influential. A counterargument that braids together ideology, institutional imperatives, and personal material consequences is pretty robust.
Which is where monopoly comes in. When companies grow to dominate their industries, they are less subject to all forms of discipline. Monopolists don't have to worry about losing disgusted employees, because they exert so much gravity on the labor market that they find it easy to replace them.
They don't have to worry about losing customers, because they have eliminated credible alternatives. They don't have to worry about losing users, because rivals steer clear of their core business out of fear of being bigfooted through exclusive distribution deals, predatory pricing, etc. Investors have a name for the parts of the industry dominated by Big Tech: they call it "the kill zone" and they won't back companies seeking to enter it.
When companies dominate their industries, they find it easier to capture their regulators and outspend public prosecutors who hope to hold them to account. When they lose regulatory fights, they can fund endless appeals. If they lose those appeals, they can still afford the fines, especially if they can use an army of lawyers to make sure that the fine is less than the profit realized through the bad conduct. A fine is a price.
In other words, the more dominant a company is, the harder it is for the good people within the company to win arguments about unethical and harmful proposals, and the worse the company gets. The internal culture of the company changes, and its products and services decline, but meaningful alternatives remain scarce or nonexistent.
Back to Google. Google owns more than 90% of the search market. Google can't grow by adding more Search users. The 10% of non-Google searchers are extremely familiar with Google's actions. To switch to a rival search engine, they have had to take many affirmative, technically complex steps to override the defaults in their devices and tools. It's not like an ad extolling the virtues of Google Search will bring in new customers.
Having saturated the search market, Google can only increase its Search revenues by shifting value from searchers or web publishers to itself – that is, the only path to Search growth is enshittification. They have to make things worse for end users or business customers in order to make things better for themselves:
https://pluralistic.net/2023/01/21/potemkin-ai/#hey-guys
This means that each executive in the Search division is forever seeking out ways to shift value to Google and away from searchers and/or publishers. When they propose a enshittificatory tactic, Google's market dominance makes it easy for them to win arguments with their teammates: "this may make you feel ashamed for making our product worse, but it will not make me poorer, it will not make the company poorer, and it won't chase off business customers or end users, therefore, we're gonna do it. Fuck your feelings."
After all, each microenshittification represents only a single Jenga block removed from the gigantic tower that is Google Search. No big deal. Some Google exec made the call to make it easier for merchants to buy space overtop searches for their rivals. That's not necessarily a bad thing: "Thinking of taking a vacation in Florida? Why not try Puerto Rico – it's a US-based Caribbean vacation without the transphobia and racism!"
But this kind of advertising also opens up lots of avenues for fraud. Scammers clone local restaurants' websites, jack up their prices by 15%, take your order, and transmit it to the real restaurant, pocketing the 15%. They get clicks by using some of that rake to buy an ad based on searches for the restaurant's name, so they show up overtop of it and rip off inattentive users:
https://pluralistic.net/2023/02/24/passive-income/#swiss-cheese-security
This is something Google could head off; they already verify local merchants by mailing them postcards with unique passwords that they key into a web-form. They could ban ads for websites that clone existing known merchants, but that would incur costs (engineer time) and reduce profits, both from scammers and from legit websites that trip a false positive.
The decision to sell this kind of ad, configured this way, is a direct shift of value from business customers (restaurants) and end-users (searchers) to Google. Not only that, but it's negative sum. The money Google gets from this tradeoff is less than the cost to both the restaurant (loss of goodwill from regulars who are affronted because of a sudden price rise) and searchers (who lose 15% on their dinner orders). This trade-off makes everyone except Google worse off, and it's only possible when Google is the only game in town.
It's also small potatoes. Last summer, scammers figured out how to switch out the toll-free numbers that Google displayed for every airline, redirecting people to boiler-rooms where con-artists collected their credit-card numbers and sensitive personal information (passports, etc):
https://www.nbcnews.com/tech/tech-news/phone-numbers-airlines-listed-google-directed-scammers-rcna94766
Here again, we see a series of small compromises that lead to a massive harm. Google decided to show users 800 numbers rather than links to the airlines' websites, but failed to fortify the process for assigning phone numbers to prevent this absolutely foreseeable type of fraud. It's not that Google wanted to enable fraud – it's that they created the conditions for the fraud to occur and failed to devote the resources necessary to defend against it.
Each of these compromises indicates a belief among Google decision-makers that the consequences for making their product worse will be outweighed by the value the company will generate by exposing us to harm. One reason for this belief is on display in the DOJ's antitrust case against Google:
https://www.justice.gov/opa/press-release/file/1328941/download
The case accuses Google of spending tens of billions of dollars to buy out the default search position on every platform where an internet user might conceivably perform a search. The company is lighting multiple Twitters worth of dollars on fire to keep you from ever trying another search engine.
Spraying all those dollars around doesn't just keep you from discovering a better search engine – it also prevents investors from funding that search engine in the first place. Why fund a startup in the kill-zone if no one will ever discover that it exists?
https://www.theverge.com/23802382/search-engine-google-neeva-android
Of course, Google doesn't have to grow Search to grow its revenue. Hypothetically, Google could pursue new lines of business and grow that way. This is a tried-and-true strategy for tech giants: Apple figured out how to outsource its manufacturing to the Pacific Rim; Amazon created a cloud service, Microsoft figured out how to transform itself into a cloud business.
Look hard at these success stories and you discover another reason that Google – and other large companies – struggle to grow by moving into adjacent lines of business. In each case – Apple, Microsoft, Amazon – the exec who led the charge into the new line of business became the company's next CEO.
In other words: if you are an exec at a large firm and one of your rivals successfully expands the business into a new line, they become the CEO – and you don't. That ripples out within the whole org-chart: every VP who becomes an SVP, every SVP who becomes an EVP, and every EVP who becomes a president occupies a scarce spot that it worth millions of dollars to the people who lost it.
The one thing that execs reliably collaborate on is knifing their ambitious rivals in the back. They may not agree on much, but they all agree that that guy shouldn't be in charge of this lucrative new line of business.
This "curse of bigness" is why major shifts in big companies are often attended by the return of the founder – think of Gates going back to Microsoft or Brin returning to Google to oversee their AI projects. They are the only execs that other execs can't knife in the back.
This is the real "innovator's dilemma." The internal politics of large companies make Machiavelli look like an optimist.
When your company attains a certain scale, any exec's most important rival isn't the company's competitor – it's other execs at the same company. Their success is your failure, and vice-versa.
This makes the business of removing Jenga blocks from products like Search even more fraught. These quality-degrading, profit-goosing tactics aren't coordinated among the business's princelings. When you're eating your seed-corn, you do so in private. This secrecy means that it's hard for different product-degradation strategists to realize that they are removing safeguards that someone else is relying on, or that they're adding stress to a safety measure that someone else just doubled the load on.
It's not just Google, either. All of tech is undergoing a Great Enshittening, and that's due to how intertwined all these tech companies. Think of how Google shifts value from app makers to itself, with a 30% rake on every dollar spent in an app. Google is half of the mobile duopoly, with the other half owned by Apple. But they're not competitors – they're co-managers of a cartel. The single largest deal that Google or Apple does every year is the bribe Google pays Apple to be the default search for iOS and Safari – $15-20b, every year.
If Apple and Google were mobile competitors, you'd expect them to differentiate their products, but instead, they've converged – both Apple and Google charge sky-high 30% payment processing fees to app makers.
Same goes for Google/Facebook, the adtech duopoly: not only do both companies charge advertisers and publishers sky-high commissions, clawing 51 cents out of every ad dollar, but they also illegally colluded to rig the market and pay themselves more, at advertisers' and publishers' expense:
https://en.wikipedia.org/wiki/Jedi_Blue
It's not just tech, either – every sector from athletic shoes to international sea-freight is concentrated into anti-competitive, value-annihilating cartels and monopolies:
https://www.openmarketsinstitute.org/learn/monopoly-by-the-numbers
As our friends on the right are forever reminding us: "incentives matter." When a company runs out of lands to conquer, the incentives all run one direction: downhill, into a pit of enshittification. Google got worse, not because the people in it are worse (or better) than they were before – but because the constraints that discipline the company and contain its worst impulses got weaker as the company got bigger.
Here's the podcast episode:
https://craphound.com/news/2023/10/23/microincentives-and-enshittification/
And here's a direct link to the MP3 (hosting courtesy of the Internet Archive; they'll host your stuff for free, forever):
https://archive.org/download/Cory_Doctorow_Podcast_452/Cory_Doctorow_Podcast_452_-_Microincentives_and_Enshittification.mp3
And here's my podcast's RSS feed:
http://feeds.feedburner.com/doctorow_podcast

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/07/28/microincentives-and-enshittification/
#pluralistic#podcasts#enshittification#google#microincentives#monopoly#incentives matter#trustbusting#the curse of bigness
251 notes
·
View notes
Text

Just slow! Yippee!
Also I committed the cardinal sin of fucking around with computers which is not labeling the screws. I think the hard drive was held in by three but I'm not sure which ones two of them are so thoughts and prayers 1 is enough ❤️
23 notes
·
View notes
Text
after 16 login attempts and a password change to the gmail I've had since I was 10
*hacker voice* I'm in.
22 notes
·
View notes
Note

I just found out your X account got hacked and the hacker blocked me after this🤨. Can you get the account back?😞
I cannot recovered my account.
However, I discovered my old gmail account on one of my crude old notebooks (I was 13 that time).
I made a new account there and a new gmail (A VERY STRONG SECURITY HAS BEEN ADDED TO MY GMAIL)
DM ME bro
5 notes
·
View notes
Text
Can you even help me get into my gmail I got locked out of I know the password and username but my two-factor authentication goes to my old cell phone number and I can't get away around it
0 notes
Text
Hire a hacker or rent a hacker using sysprohacker.net
Our services are for all social media accounts and personal accounts like Gmail etc.,
#hire a hacker#rent a hacker#sysprohacker.net#hire a hacker online#rent a hacker online#facebook hacking#instagram hacking#gmail hacking#hire a hacker for whatsapp hacking#social media accounts hacking#mails hacking
1 note
·
View note
Text
1. How to setup 2FA on your accounts
As some of you may know, my friend @why-its-kai's Discord account was taken over this morning by a scammer.
The scam they used was this one, or close enough; but anyway, the exact specifics don't matter.
What matters is, it can happen to you. It can happen to anyone.
The good news is, you can learn how to protect yourself. Making some small changes can already improve your online security by leaps and bounds.
I made a series of 3 posts covering the basics:
How to setup 2FA on your accounts (you are here!)
How to spot a scam
How to set up a password manager.
Protect yourself with 2FA
Two-factor authentication, or 2FA, isn't a silver bullet -- but it exponentially increases your online safety by adding an extra step to the login process that a hacker/scammer does not have access to.
Every account that you care about (and even those you don't) should have some form of 2FA enabled.
Especially email -- should your email become compromised, this can become a catastrophe.
(For websites that don't support 2FA, use a burner email!)
What 2FA should I use?
2FA can take many forms, from the highly convenient (SMS, email) to the highly secure (security keys), but one thing is certain:
Any form of 2FA is better than nothing.
The simplest forms of 2FA are phone number or email. While these are very easy to use, they are unfortunately not very secure.
Still, I repeat: despite their flaws, these forms of 2FA are absolutely, 100% better than not having any 2FA at all.
On the other end of the spectrum, security keys (like for example a Yubikey) are extremely secure, but they cost money and are a bit of a hassle at time. I use them, but for most people, it's overkill.
What you want is an authenticator app.
Important
A note, before we go on…
If you enable multiple forms of 2FA, how secure your account is will depend on your weakest link.
For example, if you enable SMS authentication AND register a security key, your account will only be as safe as the SMS authentication. The security key is essentially useless.
In other words, the least secure form of 2FA you add determines the overall security of your account.
Sometimes, less is more!
Authenticator Apps
First, choose a free, reputable authenticator. Google Authenticator is a good choice. So are Aegis Authenticator or Microsoft Authenticator.
For simplicity, we'll go with Google Authenticator; the process is rather similar for most authenticators.
First, download the app from your app store and install it on your phone.
Enrolling Gmail into GA
Securing your email should be your number 1 priority, so let's enroll a Google account to Google Authenticator.
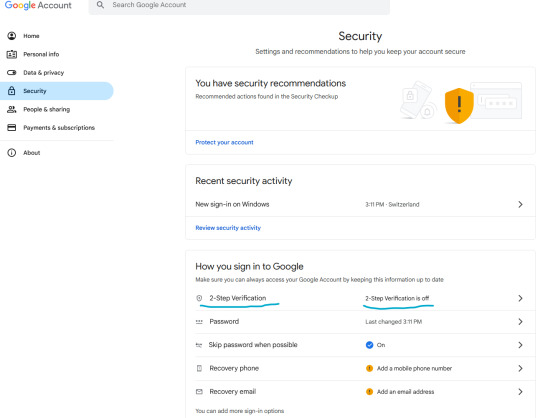
Let's enable two-step verification first.
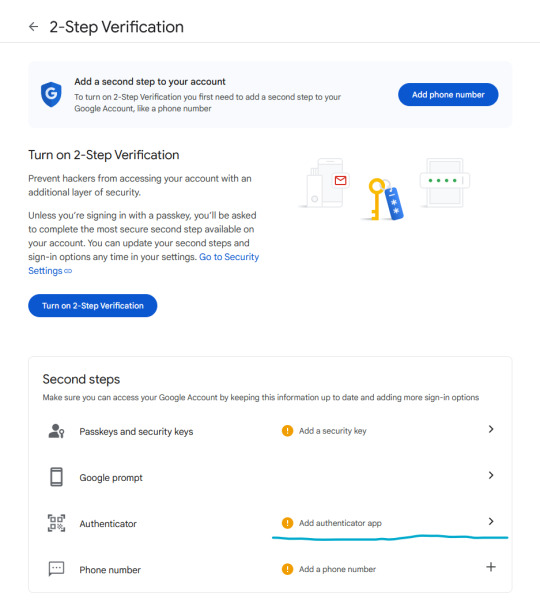
Phone number is better than nothing, but not very safe (SMS verification can be spoofed), so let's click on "Add authenticator app".
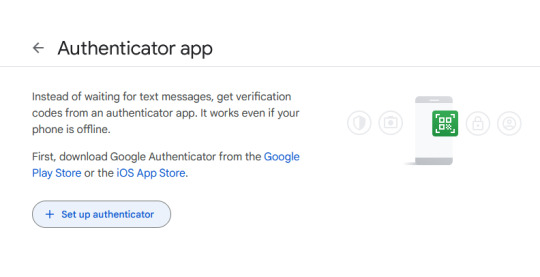
Click on "Set up authenticator". Google will generate a QR-code.
Next, go back to your phone and click on the little multicolored cross. It will bring up a menu; click on "scan a QR code".
Go ahead and scan the QR code.
Congratulations, you have enrolled your Google account!
Now, whenever you are asked for a 2FA code, just open the app and copy/paste it.
Note: the codes are stored locally on your phone.
Enabling 2FA on Discord
The process is fairly similar. Go to Settings > My Account:
Click on "Enable Authenticator App". You will be prompted for your password. Enter it.
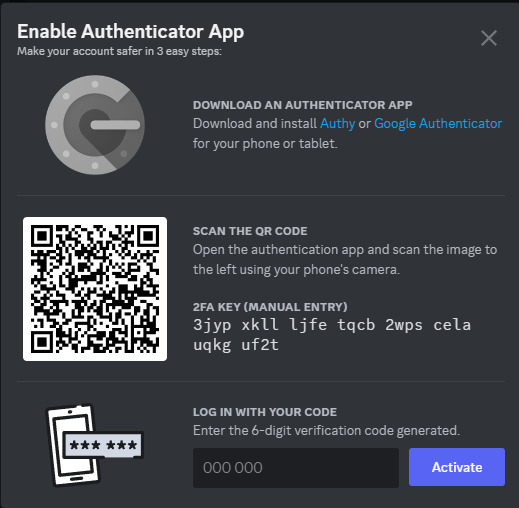
Download Google Authenticator if you haven't already. Scan the QR code as described above.
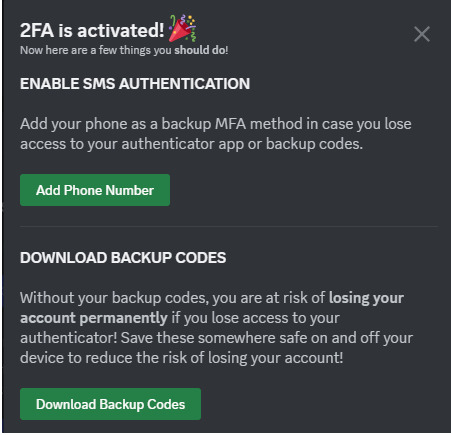
Do take the time to download your backup codes as well!
As explained above, I personally do not recommend setting up SMS authentication here, since authenticator apps are supported, as this weakens the overall security of your account for little benefit.
Stay tuned for parts 2 and 3!
If you have any questions, feel free to PM me.
17 notes
·
View notes