#How Hackers CRACK Every Software
Explore tagged Tumblr posts
Text
youtube
How Hackers CRACK Every Software: How it’s Done
Ever wondered how hackers crack expensive software in just days? In 2013, Adobe spent millions on "uncrackable" security for Creative Cloud - only to see it broken in 48 hours. This video reveals the shocking truth about software protection and the invisible army that defeats every security measure.
#How Hackers CRACK Every Software#adobe photoshop#educate yourselves#educate yourself#free education#education#youtube#technology#hacking#tips and tricks#Adobe#hacking software#Youtube
4 notes
·
View notes
Text
Trillions of domestic phone records in the United States are tracked every year under a secretive surveillance operation, WIRED revealed this week. The Data Analytical Services program, which was previously known as Hemisphere, allows cops to request and analyze the phone records of people and others who they communicate with, including those not suspected of crimes. The surveillance system is run by the White House, with telecom firm AT&T providing phone records in response to law enforcement requests.
The crypto world kept tumbling this week. After Sam Bankman-Fried was found guilty at the start of this month, it was the turn of crypto exchange Binance and its CEO Changpeng Zhao to face scrutiny from US officials. The US Department of Justice unsealed an indictment against the company, which accuses it of violating US anti-money-laundering laws and of enabling Iran, Cuba, and Russia to launder dirty money.
If you’re in the US and have some extra time over the long holiday weekend, it’s also worth catching up on Andy Greenberg’s epic tale of the three young hackers twho brought down the internet with the Mirai botnet—and their story of redemption. Then it’s definitely time to log off.
That’s not all. Each week, we round up the security and privacy stories we didn’t report on in depth ourselves. Click the headlines to read the full stories, and stay safe out there.
Google Ups Its Ad Blocker Crackdown
Google makes most of its money from advertising—and it doesn’t like ad blockers, which prevent millions of ads being shown on websites every day. In recent months, the company has been cracking down on ad blockers on YouTube in a big way. But that’s just the start of it.
This week YouTube confirmed it has, in some instances, introduced a five-second delay before videos load if people are using an ad blocker in their browser. “In the past week, users using ad blockers may have experienced suboptimal viewing, which included delays in loading, regardless of the browser they are using,” a YouTube spokesperson told The Verge. The company admitted the delays had been happening after some people on Reddit and Hacker News spotted slow loading times and initially thought it was because of the browser they were using.
The move follows Google announcing last week that it is going ahead with plans to change how Chrome browser extensions operate, which may limit how some popular ad blockers work. Last year the company paused its plans to roll out Manifest V3, the platform that browser extensions work on, after complaints about how it would impact some extensions. As Ars Technica reported, Google is planning on rolling out a revised version of Manifest V3 in June next year. Google says Manifest V3 is designed to make Chrome run smoothly by reducing the resources that extensions can use and improve security. However ad blockers and privacy experts have criticized how the system works and, in particular, changes to the Declarative Net Request API.
Google proposed putting restrictions on this API but has relaxed these somewhat in the new version of Manifest V3. It originally planned to allow browser extensions to make 5,000 content-filtering “rules,” but it has now increased this to 30,000 rules. AdGuard, an ad blocker, has tentatively welcomed some of the revised changes. Elsewhere, uBlock Origin, which uses around 300,000 filtering rules, has created a “lite” version of its extension in response to Manifest V3. The developer behind uBlock Origin says the lite version is not as “capable” as the full version. Meanwhile, browser makers Brave and Firefox say they are introducing work-arounds to stop ad blockers from being impacted by the changes.
North Korea Is Increasingly Launching Supply Chain Attacks
Supply chain attacks, where malware is implanted in a company's legitimate software and spread to the firm's customers, can be incredibly hard to detect and can cause billions of dollars in damage if they’re successful. Hackers for North Korea are increasingly adopting the sophisticated attack method.
This week Microsoft revealed it has discovered the hermit kingdom’s hackers implanting malicious code inside an installer file for photo and video editing software CyberLink. The installer file used legitimate code from CyberLink and was hosted on the company's servers, obscuring the malicious file it contained. Once installed, Microsoft said, the malicious file would deploy a second payload. More than 100 devices have been impacted by the attack, Microsoft says, and it has attributed the attack to the North Korea-based Diamond Sleet hacking group.
After details of the attack were revealed, the UK’s National Cyber Security Centre and the Republic of Korea’s National Intelligence Service issued a warning saying that North Korea’s supply chain attacks are “growing in sophistication and volume.” The two bodies say the tactics support North Korea’s wider priorities, such as stealing money to help fund its ailing economy and nuclear programs, espionage, and stealing tech secrets.
Planes Are Being Disrupted by GPS Spoofing and Electronic Warfare
Some flights have had to change course or lost satellite signals in midair due to electronic warfare, The New York Times reported this week. The ongoing conflicts in Ukraine and Gaza have seen GPS jamming and spoofing technologies interfere with the daily operation of flights in and around the areas. The incidents, so far, have not been dangerous. But they highlight the increase in electronic warfare capabilities—which seek to interrupt or disrupt the technologies used for communications and infrastructure—and how the technology needed to launch them is getting cheaper. Since Russia’s full-scale invasion of Ukraine in February 2022, electronic warfare tactics have become increasingly common on both sides, as drones being used for surveillance and reconnaissance have had their signals interrupted and rockets have been sent off course.
Russian USB Worm Spreads Beyond Ukraine’s Borders
Gamaredon is one of Russia’s most brazen hacking groups—the hackers have consistently attacked Ukrainian systems. Now one piece of its malware, a worm that spreads via USB stick and is dubbed LitterDrifter, has spread internationally. The worm has been spotted in the US, Hong Kong, Germany, Poland, and Vietnam, according to researchers at security firm Check Point. The company’s researchers say the worm includes two elements: a spreading module and a second module that also communicates with Gamaredon’s servers. “It’s clear that LitterDrifter was designed to support a large-scale collection operation,” the Check Point researchers write, adding that it’s likely the worm has “spread beyond its intended targets.”
3 notes
·
View notes
Text
How to Keep Your Laptop Virus-Free Without Paid Software

Introduction
Keeping your laptop repair Service in Wollongong safe from viruses is more important than ever. Cybercriminals are constantly finding new ways to sneak malware into our devices. Whether it’s ransomware, spyware, or phishing scams, the risks are real and costly. Fortunately, you don’t need to spend money on fancy security tools to stay protected. Good habits and free tools can keep your device safe. Ignoring the threat can lead to stolen personal data, slow performance, or even financial loss. So, learning how to prevent infections is a smart move.
The Foundations of Laptop Security Without Paid Software
Understanding Common Laptop Repair Service in Corrimal Threats
Viruses are just one type of threat out there. Malware includes many malicious programs that can harm your laptop or steal information. Ransomware locks up your files until you pay, spyware secretly tracks your activity, and adware bombards you with unwanted ads. Phishing attacks trick you into revealing passwords or financial info through fake emails or websites. According to a 2023 report from cybersecurity experts, malware infections have increased by 30% over the last two years, causing billions in damages every year.
Here’s a real-world example: Someone clicked on a malicious email attachment and ended up with a virus that encrypted their whole hard drive. The fix required expensive tech help, showing how dangerous even simple mistakes can be.
The Role of Operating System Security
Your laptop's operating system (OS) plays a big role in staying safe. Both Windows and macOS come packed with security features that protect you without extra cost. Keeping your OS updated regularly patches security holes that hackers try to exploit.
For example, Windows Defender provides real-time protection against malware, while macOS’s Gatekeeper blocks untrusted apps. Experts agree that keeping your system updated is the single most important step in avoiding malware.
Essential Free Tools and Practices to Keep Your Laptop Safe
Using Built-in Security Features Effectively
Make sure your security features are turned on. For Windows users, open Windows Defender and run a quick scan. Enable your firewall—both Windows and macOS have built-in firewalls that block unwanted network access. Set your OS to install updates automatically so you get the latest security patches.
On Mac, check your security settings in System Preferences, turn on the firewall, and enable automatic updates. These simple steps protect your laptop from many common threats without paying a dime.
Downloading Software and Files Safely
Only download from trusted sources. Avoid pirated apps or cracked software—they often hide malware. Always verify the website’s URL before clicking “Download.” Be wary of email links from unknown senders. Use browser extensions like HTTPS Everywhere and Privacy Badger to secure your browsing. These tools make it harder for hackers to intercept or track you online.
Routine Maintenance and Cleanup
Regularly clear your browser’s cache, cookies, and history—these can store malicious scripts. Uninstall programs you no longer need; the fewer apps, the less chance of infection. Use free tools like CCleaner to clean junk files and optimize your system. Keeping your laptop tidy helps Windows and macOS run smoothly and securely.
Backup Strategies
What if your laptop gets infected? Having backups saves the day. Use free cloud services like Google Drive or OneDrive to store copies of important files. External drives are also a good option. Make a system restore point or create a recovery drive to restore your system if needed. Backups are your safety net against malware or hardware failure.
Practical Steps to Detect and Remove Viruses Without Paid Software
Manual Detection Techniques
Look for signs of infection: slowdowns, strange pop-ups, or unknown programs opening. Use Task Manager (Windows) or Activity Monitor (Mac) to spot suspicious processes. Check your startup items—some malware automatically launches when you turn on your device. Review browser extensions and remove anything suspicious.
Free Malware Removal Tools
Some free tools can help remove viruses effectively. Malwarebytes Free scans your system for malware and quarantines threats. Microsoft Safety Scanner offers a quick malware scan for Windows. Run these tools regularly for peace of mind. Combining multiple scanners increases your chances of catching hidden threats.
Preventive Habits to Maintain a Virus-Free Laptop
Safe Browsing Practices
Avoid clicking on strange links or downloading files from untrusted sources. Malicious ads are common—use ad blockers to prevent these. Keep your eyes open for scams, fake websites, or emails asking for passwords. Staying cautious keeps you one step ahead of cybercriminals.
Password Management
Strong passwords are your first line of defense. Use a unique password for every account. Instead of remembering them all, use free password managers like Bitwarden or LastPass. Enable two-factor authentication wherever possible. Simple steps like these make hacking much harder.
Educating Yourself on Cybersecurity
Stay informed. Follow trusted cybersecurity sites and blogs to learn about new threats. Participating in free online courses or webinars boosts your awareness. The more you understand these risks, the better you can keep your laptop safe without spending a penny.
Conclusion
You don’t need paid tools to protect your laptop from viruses. The key is to use your operating system’s features, practice good habits, and stay alert. Routine updates, safe browsing, backups, and free malware scanners make a strong defense. With consistent effort, your laptop can stay virus-free, your data safe, and your device running smoothly. Make security a habit—your digital life depends on it.
#Phone repair services in Wollongong#Phone repair services in Corrimal#Phone repair services in Warringah#Phone repair services in Cessnock#Phone repair services in Rutherford#Phone repair services in Salamander Bay#Phone repair services in Katoomba#Best phone repair shop#Phone screen replacement open now near me#Cheap phone repair#Mobile phone repair#Phone repair near me#iPhone repair#Samsung phone repair#Mobile screen repair#Mobile phone battery replacement#Phone water damage repair#Mobile repair shop#Cracked screen repair#Quick phone repair#Best phone repair service
0 notes
Text
Hack the Future: Top Ethical Hacking Tools & Techniques You Need in 2025 Cybersecurity threats are evolving, and ethical hacking has become a crucial practice for protecting digital assets. Ethical hackers, also known as white-hat hackers, use their skills to identify vulnerabilities and strengthen security. This guide explores the top tools and techniques every ethical hacker should know in 2025. Understanding Ethical Hacking Ethical hacking involves simulating cyberattacks to uncover weaknesses before malicious hackers can exploit them. It follows a structured approach: Reconnaissance – Gathering information about the target. Scanning – Identifying vulnerabilities using specialized tools. Exploitation – Attempting to breach security to test defenses. Post-Exploitation – Assessing the impact and documenting findings. Reporting & Mitigation – Providing recommendations to fix vulnerabilities. Top Ethical Hacking Tools in 2025 1. Metasploit A powerful penetration testing framework that automates the exploitation process. It includes thousands of exploits and payloads for testing vulnerabilities. msfconsole use exploit/windows/smb/ms17_010_eternalblue set RHOSTS target_ip exploit 2. Nmap A network scanning tool that helps discover hosts, open ports, and services running on a target system. nmap -A -T4 target_ip 3. Burp Suite A web security testing tool used for detecting vulnerabilities like SQL injection and cross-site scripting (XSS). 4. Wireshark A network protocol analyzer that captures and inspects network traffic to detect potential security threats. 5. John the Ripper A password-cracking tool that helps ethical hackers test password strength. john --wordlist=rockyou.txt hash_file 6. Aircrack-ng A toolset for assessing Wi-Fi network security, helping ethical hackers test for weak encryption. airmon-ng start wlan0 airodump-ng wlan0mon aircrack-ng -b target_bssid -w wordlist.txt capture_file.cap 7. SQLmap An automated tool for detecting and exploiting SQL injection vulnerabilities. sqlmap -u "http://example.com/index.php?id=1" --dbs 8. Hydra A fast and flexible brute-force password-cracking tool used for testing login security. hydra -l admin -P passwords.txt target_ip ssh 9. OSINT Framework A collection of open-source intelligence (OSINT) tools used for gathering information about a target from publicly available sources. 10. Cobalt Strike A professional red-teaming platform used for advanced penetration testing and adversary simulation. Key Ethical Hacking Techniques 1. Social Engineering Manipulating individuals into divulging confidential information through phishing, pretexting, or baiting. 2. Wireless Network Attacks Exploiting weak Wi-Fi security protocols using tools like Aircrack-ng to gain unauthorized access. 3. Man-in-the-Middle (MitM) Attacks Intercepting and altering communications between two parties to extract sensitive data. 4. Privilege Escalation Exploiting system vulnerabilities to gain higher access privileges. 5. Reverse Engineering Analyzing software or hardware to find vulnerabilities and potential exploits. 6. Zero-Day Exploits Identifying and exploiting undiscovered security flaws before patches are released. 7. Web Application Penetration Testing Assessing web applications for vulnerabilities like cross-site scripting (XSS), SQL injection, and security misconfigurations. 8. Endpoint Security Testing Evaluating workstation and server defenses against malware, ransomware, and unauthorized access. The Future of Ethical Hacking in 2025 The rise of AI, machine learning, and quantum computing is reshaping cybersecurity. Ethical hackers must continuously update their skills and leverage AI-driven security tools to stay ahead of cyber threats. Conclusion Ethical hacking is an essential practice in modern cybersecurity. By mastering these tools
and techniques, ethical hackers can help organizations strengthen their defenses against cyber threats. Continuous learning and adaptation to emerging technologies will be crucial in 2025 and beyond.
0 notes
Text
How Do Slot Machines Works?
The RNG cycles are random, but some video video games designed via smaller studios have cracks within the supply code. Hackers use the so-referred to as PRNG Cracker app software program to become aware of those weaknesses and take gain.They implement statistical evaluation based totally on contemporary algorithms to determine on the identical time because the pseudo-random generator will pick out a seed to be able to reason a bigger payout.
Similarly, a slot programmer should installation a software program program software program tool to expect the outcome of a spin and signal players to increase their wagers.Using Blunt ForceThis is as an opportunity a fable than a reality, mainly with these days modern day slot shelves. The concept is that you can hit the device hard while reels are spinning to disrupt its regular functioning. In concept, that want to result in a payout of random length. Well, this could most effective appeal to interest, so do now not strive it out!
Laws Regulating Slot Machine CheatingLaws Regulating Slot Machine CheatingToday, the sort of registered slot device cheats decreases because of greater complex software program software program and mechanics used for his or her improvement. However, there are fanatics who're nevertheless searching for a shortcut to winning jackpots. In the subsequent paragraphs, I'll introduce the kinds of fraud regulation and the accountable authorities.
You already observed out, there are various strategies to govern slot machines in online or offline on line casino establishments. Whether a few are nice theoretical, others sincerely labored for a few minutes or multiple some years. In the eyes of law, there are important varieties of criminal offenses:Fraud And TheftSeveral sports activities may be categorised as theft and fraud, together with robbery, housebreaking, suppression, and ownership of sure articles. Check out dax69 login.
Making profits or causing losses by way of deception is strongly associated with dishonest slots, and most scammers are convicted thru articles from that a part of the law. Keep in mind that in some areas, the ones crimes are as important as violence, public disobedience, and even murder, as fraud is in mainly large volumes.Tampering With Gambling DevicesThis is a model of fraud, also seen as malicious mischief or criminal damage of a third-celebration property. Slot machines and every exclusive gambling merchandise are owned by way of manner of casinos or their developers in case the cabinets or tables are only leased. So, if positioned accountable of tampering with gambling gadgets, the man or woman faces at least numerous fees and a doubtlessly severe conviction.
0 notes
Text
Staying Ahead of the Curve: Why Regular Tech Security Updates Are Essential

In today’s fast-paced digital age, where technology shapes nearly every aspect of our lives, staying informed about tech security updates is more important than ever. From smartphones to smart homes, laptops to large-scale business networks, every device connected to the internet can be a potential target for cybercriminals. Many people overlook the critical role that timely security updates play in protecting their data, devices, and digital identity. This article will explore why tech security updates are vital, how they work, what happens if you ignore them, and best practices to ensure your technology remains secure.
The Importance of Tech Security Updates
Every day, software developers and cybersecurity experts work tirelessly to identify and fix vulnerabilities in operating systems, apps, and devices. These vulnerabilities are like tiny cracks in the walls of a fortress; if left unpatched, they offer hackers a way to break in and steal sensitive information, install malware, or even take control of entire systems. Tech security updates act as reinforcements, sealing these cracks before cybercriminals can exploit them.
While many people think that updates are just about adding new features, the security aspect is often far more critical. In fact, some of the most devastating cyberattacks in history exploited known vulnerabilities that had been left unpatched. A famous example is the 2017 WannaCry ransomware attack, which affected hundreds of thousands of computers worldwide simply because users had not installed a critical security patch.
How Tech Security Updates Work
When a security flaw is discovered, software companies quickly develop a fix. This fix is then delivered to users through a security update, which can be installed manually or automatically, depending on device settings. These updates not only patch vulnerabilities but may also include additional layers of protection to prevent similar issues in the future.
Most modern devices and operating systems allow automatic updates, ensuring that even non-technical users can keep their software up to date without lifting a finger. However, despite these conveniences, many people still delay or ignore updates, either due to concerns about storage space, data usage, or simply inconvenience.
What Happens If You Ignore Updates?
Neglecting tech security updates can lead to serious consequences. Without the latest patches, your devices become an open door for malware, spyware, ransomware, and other malicious software. Hackers can steal passwords, financial information, personal photos, and sensitive business data.
For businesses, failing to keep systems updated can result in data breaches that damage customer trust, lead to legal penalties, and cost millions in recovery efforts. In personal use, ignoring security updates can compromise online banking, social media accounts, and private communications.
In addition to security risks, skipping updates may cause compatibility problems. New applications and services often require the latest system versions to work correctly. Over time, outdated devices can become sluggish or stop working altogether as software developers focus on supporting newer versions.
Best Practices for Staying Updated
Enable Automatic Updates: The simplest way to stay protected is to enable automatic updates on all devices whenever possible. This includes smartphones, tablets, computers, and even smart home devices like security cameras and voice assistants.
Check for Updates Regularly: If automatic updates aren’t an option, make it a habit to manually check for updates at least once a week. Set reminders if necessary.
Update All Software: It’s not just your operating system that needs updating — apps, browsers, plugins, and even your antivirus software should always be up to date. Cybercriminals often target outdated third-party apps.
Be Cautious with Unsupported Devices: Older devices eventually stop receiving security updates. If you’re using a phone, computer, or router that no longer gets patches, it’s time to consider upgrading to a newer, supported model.
Stay Informed: Follow trusted tech news sources or sign up for security alerts from your device manufacturers. This will help you stay aware of any urgent tech security updates that need immediate action.
The Future of Tech Security
As technology advances, so do the tactics used by cybercriminals. The rise of artificial intelligence, smart devices, and interconnected systems means that the attack surface is constantly expanding. Tech security updates will remain a frontline defense in the ongoing battle against cyber threats.
Businesses are increasingly investing in automated patch management systems that handle updates across entire networks with minimal downtime. Likewise, many device manufacturers are working to make updates smaller, faster, and less intrusive, reducing the temptation to postpone them.
Conclusion
In a world where our personal and professional lives are deeply intertwined with technology, ignoring tech security updates is no longer an option. They are a critical component of digital hygiene, just like using strong passwords and being wary of suspicious emails. By making updates a priority, you protect not just your own information but contribute to a safer digital environment for everyone.
Remember: the next time your device prompts you to update, don’t click “Remind Me Later.” Take a few minutes to install the update — it could save you hours, days, or even weeks of headaches in the future. Stay vigilant, stay informed, and keep your tech secure.
0 notes
Text
2025 Cyber Threats: Are You Ready?

Cybersecurity in 2025: Emerging Threats and How to Protect Yourself
Emerging Cyber Threats in 2025 1. AI-Powered Cyber Attacks 2025 Cyber Threats: Are You Ready? Artificial intelligence is a double-edged sword. While it's enhancing threat detection and response, cybercriminals are also using AI to automate phishing, crack passwords faster, and create deepfake content that can bypass traditional verification systems. 2. Deepfake Scams & Social Engineering With deepfakes becoming nearly indistinguishable from real content, attackers can impersonate executives, colleagues, or even family members to manipulate victims into sending money or sensitive information. 3. Supply Chain Attacks As businesses become more interconnected, attackers are targeting third-party vendors to gain access to larger organizations. Weak links in the supply chain can be exploited to deliver ransomware or steal data undetected. 4. Quantum Computing Risks While still emerging, quantum computing poses a future threat to current encryption methods. Experts warn that data stolen today could be decrypted later, once quantum computers are capable enough—a concept known as "store now, decrypt later." 5. IoT Vulnerabilities With billions of connected devices in use, from smart homes to wearable tech, the Internet of Things (IoT) continues to be a major attack surface. Many of these devices lack basic security features, making them easy targets.
How to Protect Yourself and Your Organization
✅ 1. Embrace Zero Trust Architecture 2025 Cyber Threats: Are You Ready? "Never trust, always verify" is the new standard. Every access request—whether internal or external—should be authenticated, authorized, and continuously monitored. ✅ 2. Update and Patch Regularly Unpatched software is a goldmine for hackers. Ensure all systems, applications, and devices receive regular updates and security patches. ✅ 3. Use Multi-Factor Authentication (MFA) Passwords alone are no longer sufficient. MFA adds a critical layer of security, making it significantly harder for attackers to breach accounts. ✅ 4. Educate and Train Continuously Human error remains a top cause of breaches. Regular training on phishing, secure practices, and emerging scams can reduce risk dramatically. ✅ 5. Invest in AI-Driven Cybersecurity Tools Modern threats require modern solutions. AI-powered security platforms can detect anomalies in real time, automate responses, and help reduce incident response times.
The Bottom Line
2025 Cyber Threats: Are You Ready? Cyber threats in 2025 are more intelligent, invisible, and insidious than ever before. Staying protected requires a proactive, layered approach that blends cutting-edge technology with human vigilance. Whether you're an individual user or a global enterprise, the key to surviving the next wave of cyber threats is simple: Stay informed. Stay updated. Stay secure. Read the full article
#AICyberAttacks#Artificialintelligence#Cybersecurity2025#CybersecurityBestPractices#DeepfakeScams#EmergingCyberThreats#Family#IoTSecurity#Multi-FactorAuthentication#QuantumComputingRisks#SupplyChainCybersecurity#Technology#ZeroTrustArchitecture
0 notes
Text
7 Common Mistakes People Make With Their Android & iOS Devices (And how to avoid them)

Our smartphones are packed with advanced technology, but that doesn’t make them invincible. In fact, the way you use your device every day could be quietly shortening its lifespan, reducing performance, and exposing your data to serious risks.
From bad charging habits to ignoring updates, these mistakes are more common than you think — but the good news is they’re easy to fix.
Let’s explore seven smartphone habits that could be doing more harm than good — and how to protect your device like a pro.

Ignoring Software and Security Updates
Skipping system and app updates may save a few minutes, but it puts your phone at risk. Updates don’t just add new features — they patch security vulnerabilities and fix bugs that could slow your device down or expose your data.
Enable automatic updates for your operating system and apps.
Manually check once a month for missed updates.
Always restart your phone after installing updates to ensure everything works properly.
Before major OS updates, back up your phone using Google Drive, iCloud, or a computer to prevent data loss if anything goes wrong.
Letting the Battery Drain to 0% (or Charging to 100% All the Time)
Constantly draining your battery to 0% or charging to 100% can reduce your battery’s health over time. Lithium-ion batteries degrade faster when pushed to extremes.
Try to keep your battery level between 20% and 80%.
Enable features like “Optimized Battery Charging” to slow charging near 100%.
Avoid overnight charging if your phone doesn’t manage battery health automatically.
Use slow or standard-speed charging when you’re not in a hurry — fast charging is convenient but can slightly raise heat levels, which wears down the battery.
Downloading Apps from Untrusted Sources
Installing apps from shady websites or unofficial app stores can expose your phone to malware, spyware, and ransomware — all of which can steal your data or damage your system.
Only install apps from the Google Play Store (Android) or Apple App Store (iOS).
Avoid sideloading apps unless you’re 100% sure they’re safe.
Check app permissions — apps asking for unnecessary access could be a red flag.
Use mobile antivirus tools or enable Google Play Protect to automatically scan apps for malicious behavior.
Using Your Phone Without a Case or Screen Protector
One accidental drop is all it takes to crack your screen or damage the camera lens — and repairs can be expensive. Going “naked” with your phone is a risky move.
Get a shock-absorbing case with raised edges to protect your phone from drops.
Apply a tempered glass screen protector to guard against scratches and cracks.
If you’re outdoors often, use a waterproof case or pouch for extra protection.
Make it a habit to clean under your case occasionally — trapped dust and debris can scratch your phone’s surface over time.
Using Public Wi-Fi Without Protection
Connecting to unsecured public Wi-Fi (like in cafés, airports, or hotels) without proper precautions can expose your sensitive data to hackers and snoopers.
Use a VPN (Virtual Private Network) when accessing public Wi-Fi.
Avoid logging into banking apps or entering passwords on untrusted networks.
Disable auto-connect to public Wi-Fi in your settings.
Set your phone to ask before joining new Wi-Fi networks. This gives you control and avoids automatically connecting to unsafe hotspots.
Filling Your Phone with Unnecessary Apps and Files
When your phone is cluttered with too many apps, photos, and downloads, it can slow down performance, reduce available storage, and even cause apps to crash.
Regularly delete apps you don’t use.
Transfer photos and videos to cloud services like Google Photos, OneDrive, or iCloud.
Clean up download folders and browser caches monthly.
Enable storage optimization settings — on Android, look for “Smart Storage,” and on iOS, enable “Offload Unused Apps.”
Using the Wrong Charger
Using cheap or incompatible chargers can damage your phone’s battery or even cause short circuits. Not all cables and chargers are created equal.
Stick with your phone’s original charger or a certified third-party brand (like Anker, Belkin, or Aukey).
Avoid using random charging ports or unknown charging stations in public places.
If you use wireless chargers, make sure they meet your phone manufacturer’s standards to avoid slow or unsafe charging.
Source: https://www.techaipost.com/common-smartphone-mistakes/
0 notes
Text
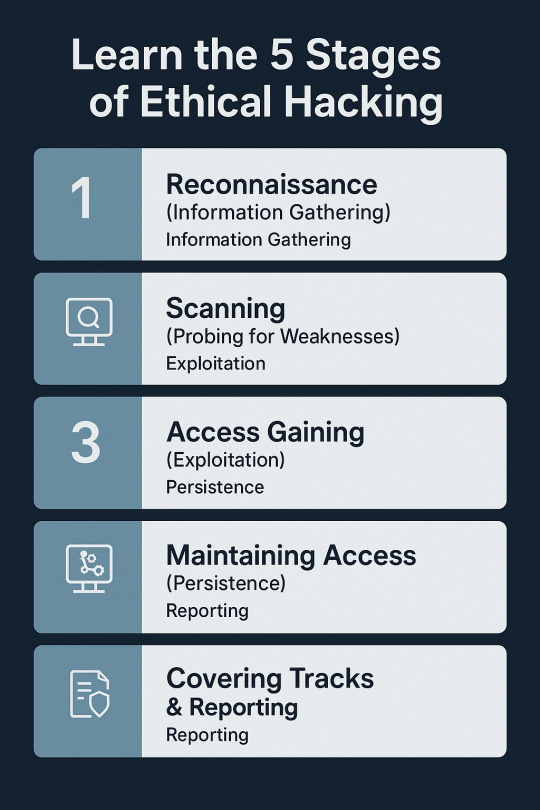
Learn the 5 Stages of Ethical Hacking
With threats on the digital platform ever-present today, ethical hacking has emerged as an essential method for protecting systems, networks, and information. As malicious hackers use vulnerabilities to carry out crime, ethical hackers (or white hat hackers) utilize their craft for good purposes — finding and fixing vulnerabilities before threat actors have the chance to do so. But ethical hacking is not a random process. It follows a methodical process to make every step legal, efficient, and in accordance with the security goals of the organization. This process is typically in five stages, which are very specific and trace ethical hackers from reconnaissance to reporting. Let us dive into detail about what these stages involve and why they're crucial for a successful cyber defense strategy. Phase 1: Reconnaissance (Information Gathering) Also known as: Footprinting Reconnaissance is the first and, arguably, the most important phase of ethical hacking. It's akin to the "research" phase. Ethical hackers find out as much as they can about the target before they try to break into it. This phase lays the groundwork for everything that follows. Aims: •Get familiar with the digital footprint of the target •Identify weak spots and vulnerable entry points • Steal away undetected while gathering information Methods Used: • Passive Reconnaissance – No contact with the target (e.g., use of WHOIS lookup, DNS records, social media, public databases). • Active Reconnaissance – Direct contact with the system (e.g., ping sweeps, port scanning, traceroutes). Tools: •Maltego •Nmap •Recon-ng •Google Dorking Why it matters: Proper reconnaissance saves time and makes the rest of the hacking process easier. It also replicates the first steps taken by real-world cyber attackers.
Phase 2: Scanning (Probing for Weaknesses) After the ethical hacker has sufficient surface information, scanning is the next phase where more intensive probing is done to identify particular vulnerabilities in the system. Objectives: • Discover open ports and services • Detect live systems • Identify running OS and applications • Discover known vulnerabilities
Methods: • Port Scanning – Scanning which ports are open and what services are running.
• Network Mapping – Knowledge of the network topology and the identification of the hosts. • Vulnerability Scanning – System scanning for known configuration or software vulnerabilities. Tools: • Nessus • Nikto • OpenVAS • Wireshark Why it matters: Scanning gives the hacker a technical snapshot of how healthy the system is and assists the hacker in determining which vulnerabilities to exploit during the exploitation phase.
Phase 3: Access Gaining (Exploitation) This is where ethical hacking really gets to work and occurs. The hacker attempts to break into the system by taking advantage of the weaknesses revealed in the scanning. It sounds like the climax, but it's a very choreographed and strategic move that makes ethical hacking. Objectives: • Use a known exploit to gain access • Increase privileges (for example, from guest to admin) • Identify the amount of potential damage that an actual perpetrator might do Methods • Buffer overflow attacks • tSQL injection • Brute-force password cracking • Misconfiguration exploitation Tools: • Metasploit • Hydra • John the Ripper • SQLMap Why it matters: Access that is gained allows organizations to see how much access an attacker would have, giving them a chance to cut off critical points of access before damage is being caused.
Phase 4: Maintaining Access (Persistence) During this phase, the ethical hacker mimics what an actual attacker would do once they have compromised the system — maintain access to keep gathering data or installing malware. Objectives: •Create backdoors or remote access tools •Mimic advanced persistent threats (APT) •Illustrate long-term risk exposure Methods: •Installing Trojans or rootkits (ethically and with permission) •Creating rogue user accounts •Altering system services for covert access Tools: •Netcat •Backdoor Factory •MSFVenom Why it matters: This stage assists in determining how long a system might remain compromised undetected — an important consideration when analyzing incident response measures. Phase 5: Covering Tracks & Reporting While malicious hackers attempt to cover their tracks, ethical hackers do the opposite — they make sure all actions taken are logged, traced, and completely documented. Reporting is the last and possibly most useful step of the ethical hacking process.
Goals: • Restore the system to normal • Report to the organization • Deliver remediation steps that are actionable What's in the Report: • Disclosed vulnerabilities • Attacks tried and success rates • Possible impact of each vulnerability • Fix recommendations and improvements Why it matters: The final-report is a blueprint that the organization can use to make its defenses harder. It transforms an ethical hack from a test into an actionable business tool.
The Legal and Ethical Side It's important to emphasize: Ethical hacking should be done with the right permission. That is, written permission, well-delineated scope, and test boundaries. Unapproved hacking—no matter what "noble cause"—is against the law and punishable by it. Why the 5 Phases are Important Together, these five phases create a repeatable, effective cycle of security testing. They: •Echo the methods of actual attackers •Detect potential threats prior to exploitation •Enhance organizational cybersecurity stance •Meet standards such as ISO/IEC 27001, PCI-DSS, etcFinal Thoughts Ethical hacking is not merely about cracking open systems—it's about learning them, enhancing them, and helping to make the internet a more secure place. From IT managers to aspiring cybersecurity analysts to entrepreneurs, recognizing the five stages of ethical hacking can assist you in making better, more secure decisions. With increasing cybercrime, ethical hacking is no longer a choice — it's a necessity. And as with any strategic process, its success depends on how systematically and responsibly it's carried out.
Website: https://www.icertglobal.com/course/ceh-certification-training/Classroom/62/3044
0 notes
Text
How QA Turns Financial Software Into a Stronghold: Securing the Vault
Introduction: The Pressure Cooker of Financial Tech Imagine you’re a QA Manager staring down a deadline: your team’s rolling out a new payment app next week, and the CEO’s breathing down your neck for perfection. One glitch could mean frozen transactions—or a data breach that lands you on the evening news. In finance, software isn’t just a tool—it’s the vault where trust and treasure live. That’s why software testing and QA services aren’t a luxury; they’re your ticket to sleeping at night.

For Project Managers and decision-makers, the pressure’s just as real. You’re juggling compliance deadlines, customer demands, and a tech landscape that’s a hacker’s playground. Software testing and QA services are your heavy hitters, catching risks before they blow up. In this post, we’ll break down the must-do testing strategies that keep financial apps rock-solid, plus a checklist to make your next release a win. Let’s lock it down.
The Unique Chaos of Financial Software Building an app for finance isn’t like coding a fitness tracker or a recipe site. Every feature—whether it’s a loan calculator or a wire transfer—carries a dollar sign and a promise. Mess up, and you’re not just fixing bugs; you’re explaining to regulators why customer data’s floating around the dark web. Software testing and QA services step in to tame that chaos, ensuring your app doesn’t just work—it thrives under scrutiny.
Industry Insight: The Stakes Are Climbing Here’s a jolt: PwC reports cybercrime costs financial firms $42 billion a year—and that’s just the tip. Add in regulatory fines—like the $5 billion Facebook paid for privacy slips—and you see why QA matters. A trading platform I once worked on lost $2 million in a day from a laggy update. Testing isn’t overhead—it’s your bottom line.
Your QA Playbook for Financial Apps So, how do you make financial software a stronghold? It’s about targeting the risks that hit hardest in this industry. Here’s your playbook for software testing and QA services, packed with the non-negotiables every QA pro needs to nail.
Penetration Testing: Your Anti-Hacker Shield Finance apps are like honey to bees—hackers can’t resist. Penetration testing flips the script, letting your QA crew poke holes before the bad guys do. Can someone crack your encryption? Could they spoof a payout? PCI DSS mandates this for card data, but it’s smart even if you’re off the payment grid. A good pen test is your first line of defense.
Hack Tip: Test new features live—hackers love fresh code.
Compliance Testing: Rules Aren’t Suggestions The alphabet soup of finance—GDPR, AML, SOX—means one thing: screw up, and you’re toast. Compliance testing digs into the details: Are your logs tamper-proof? Does your app mask sensitive data? Software testing and QA services keep you on the right side of the law, turning red tape into a green light.
Close Call: A bank app I saw skipped an AML check—QA caught it days before launch. Saved a $10 million fine.
Static and Dynamic Analysis: Inside and Out Code’s a sneaky beast—flaws lurk in the shadows. Static analysis scans it cold, catching backdoors or sloppy patches. Dynamic analysis runs it hot, testing real-world hiccups like race conditions. In finance, where a glitch can reroute funds, this duo’s a lifesaver.
Why It Works: A fintech once found a dynamic flaw letting duplicate withdrawals—QA plugged it fast.
Performance Testing: Built for the Blitz Financial apps don’t get a slow day—think tax deadlines or a market crash. Performance testing preps you for the worst: load tests for user spikes, stress tests for collapse points, and scalability for the long haul. A stalled app isn’t an oops—it’s a dealbreaker.
Game Plan: Mimic a million-dollar trading rush. If it holds, you’re golden.
Fraud Detection Testing: Trust’s Best Friend Spotting fraud—like a $50,000 transfer from a hacked phone—is make-or-break. QA throws fakes at your system: Does it flag fast? Does it miss clean moves? This isn’t just tech—it’s keeping customers safe and your name clean.
Lesson Learned: A crypto app’s fraud net was too loose—QA tightened it, slashing scam losses by 30%.
QA: Your Secret Weapon in Finance Let’s get real: in finance, software’s your battleground. Customers expect instant, secure, flawless—every time. That’s where software testing and QA services give you the edge. For QA Managers, this is your turf—turn testing into a trust machine. For Project Managers and decision-makers, it’s your leverage—launch apps that don’t just meet specs but crush expectations.
QA isn’t about playing catch-up; it’s about leading the charge. Developers build the vision; you make it unbreakable. With the right testing, you’re not just dodging bullets—you’re building a legacy of reliability in a cutthroat field.
Conclusion: Seal the Vault Today Financial software lives on a knife-edge—one slip, and it’s game over. But with killer software testing and QA services, you’ve got the power to stop risks dead. From hacker-proofing to fraud-busting, this is how you deliver apps that stand tall under pressure.
Need quality assurance that’s finance-ready? If you’re a QA Manager, Project Manager, or decision-maker, we’ve got your back. Our expert testing locks in security, nails compliance, and keeps performance humming. Hit us up now—let’s make your software a vault no one can crack.
#qualityassuranceservices#qualityassurancetesting#quality assurance services#qualityassurancecompany
0 notes
Text
Hack Instagram FREE ONLINE THE method that works 2025 [How to Hack Instagram] New!
👉🏻👉🏻 Click here to start hacking now! 👈🏻👈🏻
👉🏻👉🏻 Click here to start hacking now! 👈🏻👈🏻
How to Hack Instagram With Tools – And Keep Your Account Secure
Instagram is one of the most popular platforms for sharing content, but its popularity also makes it a prime target for hacking attempts. While some people are curious about hacking methods, it's crucial to prioritize security and use this knowledge only for protecting your account. Let's explore how accounts are hacked, the tools used, and actionable steps to secure your profile.
How Instagram Accounts Are Hacked
Hackers use a variety of tactics to access Instagram accounts. Knowing how these methods work can help you recognize and avoid them.
Phishing Scams
Phishing scams are one of the most common ways hackers gain access to Instagram accounts. Cybercriminals send fake emails or messages that appear to be from Instagram. These messages often urge users to click on a link to "verify" their account or "reset" their password. Once the link is clicked, users are directed to a fake login page, and when they enter their credentials, hackers capture the information.
Credential Stuffing
Credential stuffing relies on stolen usernames and passwords from past data breaches. Hackers use automated tools to try these credentials on Instagram, hoping the victim reused the same password across multiple accounts. This method works surprisingly well because people often reuse passwords for convenience.
Third-Party Applications and Tools
Some apps claim to offer extra features, analytics, or even ways to gain followers. However, using unauthorized third-party tools can be risky. These apps often require login information, making it easy for hackers to intercept your account credentials.
Social Engineering
Hackers don’t always rely on technology. Social engineering involves tricking people into giving away sensitive information. This might include pretending to be a friend, Instagram support, or another trusted entity. By manipulating the victim emotionally or psychologically, hackers can extract account information without needing technical skills.
Popular Tools Used for Instagram Hacking
Though unethical, hackers use specific tools to gain unauthorized access to Instagram accounts. Here’s a breakdown of the most commonly exploited tools and their dangers.
Password Cracking Software
Password cracking tools, like brute-force software, try endless combinations of letters, numbers, and symbols until the correct password is found. These tools are automated, making the process faster. However, they usually target accounts with weak or predictable passwords.
Spyware Apps
Spyware apps run silently in the background of a device, tracking every action. These apps can monitor keystrokes, giving hackers access to your login details. Once the spyware is installed on someone’s phone or computer, it’s almost impossible to detect without specific anti-spyware tools.
Fake Instagram Login Pages
One of the simplest yet most effective tools hackers use is creating fake login pages. They mirror the actual Instagram login screen, tricking users into entering their credentials. These fake sites can be distributed through phishing emails, compromised links, or social media DMs.
How to Secure Your Instagram Account from Hackers
Protecting your account is easier than you might think. By following these steps, you can significantly reduce the risk of unauthorized access.
Enable Two-Factor Authentication (2FA)
Adding 2FA provides an extra layer of security. Even if someone gets your password, they’ll need a temporary code sent to your phone or email to log in. To enable 2FA:
Go to your Instagram settings.
Select “Security.”
Click “Two-Factor Authentication” and follow the steps.
You can choose between SMS codes or an authentication app for added security.
Create Strong, Unique Passwords
Avoid simple passwords like “123456” or “password.” Instead, use a combination of uppercase and lowercase letters, numbers, and symbols. Never reuse the same password across multiple accounts. For example, a strong password might look like: Gr8!SecurePa55.
Avoid Clicking Suspicious Links
If you receive a message or email asking you to click a link, think twice. Look for warning signs like poor grammar, urgency, or unverified senders. Instead, go directly to the Instagram website or app to check for any notifications.
Revoke Access to Third-Party Apps
Any app connected to your Instagram account has access to your data. Regularly review which apps have permission:
Go to the Instagram account settings.
Navigate to “Apps and Websites.”
Revoke access for any unfamiliar or untrustworthy apps.
Monitor Account Activity Regularly
Instagram allows you to check activity logs, such as login locations and devices. If you notice anything unusual, such as unknown devices or locations, change your password immediately and log all other devices out of your account.
What to Do If Your Instagram Account Is Hacked
If your account is compromised, quick action is crucial. Here's what to do.
Report to Instagram Immediately
Instagram provides a recovery process for hacked accounts. Go to the login screen, click “Forgot password?” and follow the steps to recover your account. If your email or phone number has changed, use Instagram’s “My account was hacked” feature to submit a report.
Secure Your Email Account
Hackers often target email accounts associated with Instagram to lock you out. Make sure your email has a strong password and 2FA enabled. This prevents hackers from resetting your Instagram login information.
Check and Update Passwords
Once you regain control, update all your passwords. Start with Instagram and then move to any connected accounts (email, apps, etc.). Avoid using the same password as before, even with minor changes.
Warn Your Followers About Potential Scams
Hackers may use your account to send phishing links or scams to your followers. Post a story or message to let them know your account was hacked and they shouldn’t click any unusual links they may have received.
Conclusion
The rise in Instagram hacking attempts highlights the need for stricter security measures and user awareness. While hackers use various tools and manipulative tactics, being proactive about protecting your account can save you from a lot of headaches. Enable 2FA, avoid suspicious links, and stay vigilant. Remember, online security is everyone’s responsibility. Stay informed and keep your personal information secure.
hack instagram account,instagram hack,how to hack an instagram account,how to hack instagram account,how to hack instagram,how to hack a instagram account,hack instagram,how to hack an instagram,how to hack someones instagram,how to hack into someones instagram,how to hack someones instagram 2021 instagram password hack,how to hack instagram accounts,how to hack someone instagram instagram followers hack hack instagram password report instagram account hack instagram following hack hack instagram followers follower instagram hack followers instagram hack hack followers instagram follower hack instagram instagram hack followers instagram follow hack,how to hack into an instagram account instagram hack for followers hack in someones instagram hack into someone instagram hack into someone's instagram,how to hack back into my instagram account hack my instagram account hack to see,how many times someone viewed your story instagram,how to hack someone's instagram,how to hack someones instagram account,apps to hack instagram,instagram hack report app to hack instagram,hack someones instagram,hack someone instagram,someone hack my instagram,hack instagram for free,instagram hack free,hack instagram tool instagram follower,hack instagram verification code,hack instagram,hack tools free instagram hack,hack into someones instagram why do people hack instagram
0 notes
Text
Passwords hashing is used to secure passwords. Hashing is a common technique across various software and tools. Hashing is used as a security mechanism for preventing plain text information known to others. It's mathematically impossible to calculate a plain text for Hash since hashing is a one-way process. Still, there are different ways exist that can crack the hash and retrieve your password or other sensitive information that may have been hashed. Hashing technique is mostly applicable to protect password like information since its a one-way process. You may also want to check out - how to learn hacking and cracking. This is a simple tutorial that will explain how hash cracking works. Why Password Hashing Is Considered Secure Hashing is a one-way process. This guarantees that the hash of a plain text value can be generated however the process can not be reversed. Most software and websites use this way to store password since the user knows the password. Whenever they need to authenticate the user, they generate the hash of user input and match it with a stored password. This mechanism guarantees that even the software provider themselves do not know your password. However, there are hacking and cracking tools as well as other techniques described below that may be able to find out your password from a hash. Today we will learn about Cracking the Hashes using CPU and GPU. CPU: Central Processing Unit GPU: Graphical Processing Unit We will cover: What is a Hash? What is the need for a Hash? Why Hash over Encryption or Encoding? Hardware configuration Tools required Hash cracking [CPU] Hash cracking [GPU] Hash cracking using Search engine Why such a difference? What Is A Hash? A. A Cryptographic function that converts a data or file of arbitrary length or size to a fixed length, which is considered practically impossible to invert. see Wikipedia What Is The Need Of A Hash? A major use of Hash is in the security field. To provide security or privacy to the user who is using any service of a company. For example, You are using Gmail, Facebook, Twitter, eBay, Amazon or Online payment portals like Paypal. Where you use the service by providing your credentials(username/password) There are basically 2 reasons: Making it difficult for hackers to recover/retrieve Password, Online service(Gmail,eBay, etc) or even Wi-Fi. Checking for the file verification. see SHA1 here Even If a company’s security is breached (Hacked), then also the user’s credentials are safe(only if you use a strong password) Why Hash Over Encryption And Encoding? Imagine a scenario, which perhaps happens to almost every Big banner, take it Google, Facebook, Yahoo! etc. A website is compromised and User’s data(credentials) is compromised. What is the thing that will make you worry when you come to know that if you are a registered user on that site? Yes! your Password (might be the master password, for all your accounts). Now, It is in service provider’s hand to provide security to their consumers. Hence, Hashing is the solution. How? well, you might be familiar with these terms: Encoding/Decoding Encrypt/Decrypt and now, Hashing Not going into the details, I will tell you a basic and most important feature of Hash which makes Hash much different and important over Encoding and Decoding. and that is : Encoded text/file can be Decoded, Encrypted text/file can be Decrypted, But hashed text/file can never be De-hashed. Yes, Hash, unlike Encryption/Encoding, is a One-way process i.e when a text/file goes through the Cryptographic hash function, it is converted into a fixed character length. Example: md5 type hash has a character length of 32, where SHA1 has a character length of 40. If we hash a string, say “test123″, md5 and SHA1 hash for “test123″ will be md5(“test123″) : CC03E747A6AFBBCBF8BE7668ACFEBEE5 SHA1(“test123″) : 7288EDD0FC3FFCBE93A0CF06E3568E28521687BC Length differs from md2, md4 to SHA256, SHA512 and so on.
Hashing your Wi-Fi password is also secured using a hash function named PBKDF2(Password-Based Key Derivation Function) Hardware Configuration Hardware used in this tutorial: Laptop with 4 GB RAM Nvidia Graphic card 1 GB Tools Required Software used in this tutorial: Windows 8, 32-bit Cain & Abel (CPU based cracker). igHashGPU (GPU based cracker), download here Nvidia graphics driver, for igHashGPU, download here Hash Cracking [CPU] Cain & abel is a multi-purpose tool. It is used for various purpose like Sniffing Hash calculating Hash recovery(this tutorial) ARP spoofing WiFi hacking, using hardware called AirPcap and so on. We will take MD5(Message Digest 5) cracking as an example to keep it simple and easy to understand. Install Cain & abel, then follow the instruction along, step-by-step: Open Cain & abel Press Alt+C to open the Hash calculator Type in “test123” and hit [ENTER], here “test123″ is our test string You should see something similar, Here we got the MD5, and other Hash for string “test123″ i.e CC03E747A6AFBBCBF8BE7668ACFEBEE5. select and copy the MD5 hash.
NOTE: Hashing is Case sensitive, Hash for “Test123” will be absolutely different. Click on Cracker tab, then select MD5 Hashes column in the left. then right click and select Add to list. Paste the copied MD5 hash and hit [ENTER] Now, Hash is added to list. Right click on hash and select Brute-Force attack Set max length to 7 and click Start, and you should see this
. Here I have set the Max length of the password to be 7 to just test the output of the tool, and cracking speed of the CPU.
See the Password/Second CPU is testing: 6.3M (approx) and the remaining time i.e total time which will take CPU to recover the original string is 3.5 hours. It is too lame to wait for 3.5 hours for a small string test123 of the length of 7 characters with no special characters. isn’t it? well, here comes the GPU cracking to put some speed in the process! Hash Cracking [GPU] igHashGPU is a password recovery tool specialized for ATI (RV) and nVidia (Cuda) based cards. It recovers password of hashes which are used over the internet(weak), example md4/md5/SHA1. Let's get started, We have the MD5 string for test123 i.e CC03E747A6AFBBCBF8BE7668ACFEBEE5 Follow the instructions along, step-by-step: Download and extract igHashGPU. Go to folder Right click and edit the file “example.cmd“. It is the example file for testing GPU speed of recovering MD5 password. Paste the MD5 code in the file after h:
and it should look like this :
ighashgpu.exe /h:CC03E747A6AFBBCBF8BE7668ACFEBEE5 /t:md5 /c:sd /min:4 /max:7 Close file. Click save and yes. Select “Example.cmd” and hit [ENTER]. A command prompt window will open like this
. See the CURSPD(Current speed), ~50 Million. Nice! but not good, isn’t it? see the battery symbol in the lower right corner. The laptop is running on battery. See what happens when I plug in the charger, notice the clock and speed. WHOA! See the difference! from 50M to 195M passwords/second, isn’t it great ? from 6.3M pass/sec to 195M pass/sec. That’s a big Jump. What you think how long it would have taken to recover the Password ? Just 5 minutes and 53 seconds. See how much time we saved by using GPU. From 3+ hrs to just 5 minutes. isn’t it amazing? also see the average speed also, 62,847 Million passwords/second. CPU: ~3 hrs with 6M pass/sec
GPU: ~6 min with 195M pass/sec You might ask, Hey! can we crack this even faster? well, the answer is Yes you can(not always though). How? Hash Cracking Using Search Engine [Google] We had MD5 string copied, right? what you need to do is very simple. Just paste and search the MD5 string i.e CC03E747A6AFBBCBF8BE7668ACFEBEE5 on Google. and you’re done! Notice the text string “test123” and the Hash. So simple to recover the string from MD5, no? Now see the time above, it took us to recover the original string. Just 0.31 seconds. not even a second. Wow! that’s great.
You might be thinking why such a difference? here’s the answer Why Such A Difference? The difference in the speed is due to the architecture of the 3. CPU: Uses 4 cores(Shared with system processes) at maximum, 8-cores in some cases. GPU: Used 96 cores (In this case). All the 96 cores(Parallel processing units) were 100% dedicated for the password recovery process unlike CPU, which was simultaneously handling the complete OS including background processes, GUI(mapping of pixels on screen), and many other processes. Even if the CPU stop handling those, then also it won’t match GPU’s performance. difference because of the #of cores i.e 96 vs. 4 or 8 Latest GPU’s that I have seen comes with more than 400 cores. It can take you more than a billion passwords/second to recover the MD5 hashed string. Google Don’t Crack The Hash. Yes!, Google doesn’t crack/recover the string. It sends a request for the specific Text input i.e the hash in our case, to all the servers, takes the response back and displays the result according to the page rank of the site. There are plenty of online crackers, which can be used to crack a variety of hashes. They search their Database for the hash you have entered. If the string of hash is already recovered by them, they will give it to you, else you have to pay to avail the service. An email is sent if the string has been recovered. So, what Google does is sending a request to all these servers and displaying you the result. Result of the hash already cracked. It certainly becomes the Top priority for hash cracking. Search google first, if you didn’t find the password, go for GPU cracking.
Still didn’t succeed? Try CloudCraker, crackStation, HashKiller You can google “Online hash cracker” for more results. Note: Cracking speed varies depending on factors like: GPU configuration, ATI graphics cards are the best for this task. Hash type, for SHA1 it will be even lesser and for WPA hash cracking it goes down to 4000 Pass/sec on my graphics card. see this list. My card’s performance is near to GeForce 8800 GTS (CUDA) Interested in WPA cracking, or WiFi pentesting? Follow my WiFi Security and Pentesting Series Hope you found this tutorial helpful. Let me know in the comment section. Thanks! This article is contributed by Hardeep Singh (Facebook | Twitter). Hardeep is a guest author and Full-time Blogger @ rootsh3ll.com, Security person, Penetration, tester, Linux and python Lover. Loves to share knowledge with everyone. Updated On June 2019: Fixed Broken links and updated minor typos.
0 notes
Link
#blackhat#CyberAttacks#cyberawareness#cybersecuritycompanies#cybersecurity#hackers#ransomware#security#whitehat
0 notes
Text
does brutus brute force work through vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does brutus brute force work through vpn
Brutus brute force VPN effectiveness
Brutus brute force VPN effectiveness is a crucial aspect to consider when selecting a Virtual Private Network (VPN) service to protect your online activities and data. A VPN that can withstand brute force attacks, such as those attempted by tools like Brutus, is essential for maintaining your privacy and security on the internet.
Brutus is a popular software tool used by hackers to crack passwords through brute force attacks. These attacks involve trying every possible password combination until the correct one is found, making it a significant threat to online security. When it comes to VPNs, the effectiveness against brute force attacks like Brutus is a key factor in determining the overall level of protection offered by the service.
A robust VPN service will employ advanced encryption protocols such as AES-256 bit encryption, which can help prevent brute force attacks by making it extremely difficult for hackers to decrypt the data transmitted through the VPN connection. Additionally, VPNs with features like multi-factor authentication can add an extra layer of security, further reducing the risk of unauthorized access to your online accounts and data.
When choosing a VPN for your online security needs, it's essential to consider the provider's stance on brute force attacks and the measures they have in place to mitigate such threats. Reading reviews and conducting research on VPN services' security features can help you make an informed decision and select a VPN that offers effective protection against brute force attacks like Brutus. Remember, investing in a reliable VPN with strong security measures is an investment in safeguarding your online privacy and data.
VPN protection against Brutus brute force
Title: Strengthening Your Online Security: How VPNs Shield Against Brutus Brute Force Attacks
In the ever-expanding digital landscape, safeguarding your online presence is paramount. One of the prevalent threats internet users face is brute force attacks, where malicious actors attempt to gain unauthorized access to accounts by systematically trying different combinations of usernames and passwords. Among these attacks, Brutus stands out for its aggressive nature and relentless pursuit of vulnerabilities.
However, there's a powerful ally in the fight against such cyber threats: Virtual Private Networks (VPNs). VPNs provide a layer of encryption and anonymity, making it significantly harder for attackers to intercept and decipher sensitive information.
Here's how VPNs offer protection against Brutus brute force attacks:
Encryption: VPNs encrypt your internet traffic, creating a secure tunnel between your device and the VPN server. This encryption scrambles data, making it unreadable to anyone trying to intercept it, including Brutus attackers.
IP Masking: VPNs hide your real IP address and assign you a temporary one from their server locations worldwide. This makes it challenging for attackers to trace your online activities back to your physical location or device, thwarting their attempts to launch targeted attacks.
Secure Connection: By routing your internet traffic through VPN servers, you bypass potentially vulnerable networks, such as public Wi-Fi hotspots. This reduces the risk of attackers eavesdropping on your connection and capturing login credentials that Brutus could exploit.
Multi-factor Authentication (MFA) Compatibility: Many VPN services support MFA, adding an extra layer of security to your accounts. Even if Brutus manages to obtain your login credentials, MFA would require an additional verification step, such as a code sent to your phone, to access your account.
In conclusion, incorporating a VPN into your online security arsenal can significantly enhance your defense against Brutus brute force attacks. By encrypting your data, masking your IP address, ensuring secure connections, and supporting MFA, VPNs provide a robust shield against cyber threats in an increasingly vulnerable digital landscape.
Does VPN prevent Brutus brute force
A VPN, or Virtual Private Network, provides an added layer of security and privacy when browsing the internet. Many people wonder if using a VPN can help prevent brute force attacks like those attempted by the Brutus tool.
Brutus is a popular, open-source remote online password cracking tool that can be used in brute force attacks to gain unauthorized access to accounts by systematically trying different password combinations. While a VPN does not directly prevent a brute force attack like Brutus, it can still enhance your overall security and protect your data in several ways.
VPN encrypts your internet traffic, making it difficult for cybercriminals to intercept and decipher your data. By creating a secure and encrypted connection between your device and the internet, VPNs ensure that your passwords and sensitive information remain safe from prying eyes. This encryption adds a layer of protection that can make it harder for attackers to successfully carry out a brute force attack.
Additionally, using a VPN can help mask your IP address and make it appear as though you are accessing the internet from a different location. This can help protect your identity and make it more challenging for potential attackers to target your specific device or network.
While a VPN is not a guaranteed defense against all cyber threats, including brute force attacks like those attempted by Brutus, it can still significantly enhance your online security and privacy. By encrypting your data and masking your IP address, a VPN can help mitigate the risk of falling victim to such attacks and safeguard your sensitive information.
Brutus brute force attack via VPN
Title: Understanding the Threat of Brutus Brute Force Attacks via VPN
In the realm of cybersecurity, the term "brute force attack" sends shivers down the spine of even the most seasoned IT professionals. These attacks involve relentless attempts to crack passwords or encryption keys by systematically trying every possible combination until the correct one is found. One variant of such attacks, known as the Brutus brute force attack, poses a particularly menacing threat when executed through Virtual Private Networks (VPNs).
VPN services are widely used to enhance online privacy and security by encrypting internet connections and masking users' IP addresses. However, this very anonymity can attract malicious actors seeking to exploit vulnerabilities in VPN configurations.
Brutus attacks via VPN typically involve automated scripts or tools that systematically try different combinations of usernames and passwords to gain unauthorized access to remote systems or networks. These attacks can target various entry points, including VPN gateways, remote desktop services, or web applications accessible through VPN connections.
The consequences of a successful Brutus brute force attack via VPN can be severe. Attackers may gain unrestricted access to sensitive data, compromise critical systems, or even launch further attacks from within the network, all while remaining hidden behind the anonymity provided by the VPN.
Protecting against Brutus brute force attacks requires a multi-layered approach. This includes implementing strong password policies, enabling multi-factor authentication, regularly updating VPN software, monitoring network traffic for suspicious activities, and implementing rate limiting or account lockout mechanisms to thwart repeated login attempts.
Additionally, organizations should educate their employees about the risks associated with weak passwords and the importance of practicing good password hygiene. Regular security audits and penetration testing can also help identify and remediate potential vulnerabilities before they can be exploited by malicious actors.
In conclusion, while VPNs offer valuable privacy and security benefits, they also present opportunities for malicious actors to launch Brutus brute force attacks. By implementing robust security measures and fostering a culture of vigilance, organizations can mitigate the risk of such attacks and safeguard their digital assets against unauthorized access and exploitation.
VPN security and Brutus brute force
Title: Strengthening VPN Security Against Brutus Brute Force Attacks
In the digital age, where online privacy is a top concern, Virtual Private Networks (VPNs) have emerged as a popular tool for safeguarding sensitive data and maintaining anonymity while browsing the internet. However, despite their encryption protocols and secure tunneling, VPNs are not immune to cyber threats, including brute force attacks like Brutus.
Brutus is a type of brute force attack used by hackers to crack passwords or encryption keys by systematically trying every possible combination until the correct one is found. This method exploits vulnerabilities in security systems, including VPNs, by overwhelming them with countless login attempts.
To mitigate the risk of falling victim to Brutus brute force attacks, it's crucial to implement robust security measures when using VPNs:
Strong Encryption: Opt for VPN services that offer military-grade encryption protocols such as AES-256, which significantly increase the complexity of cracking passwords or decryption keys.
Multi-Factor Authentication (MFA): Enable MFA whenever possible to add an extra layer of security beyond just a password. This requires users to provide additional verification, such as a unique code sent to their mobile device, before gaining access to the VPN.
Regular Password Updates: Encourage users to frequently update their VPN passwords and avoid using easily guessable passwords. A combination of letters, numbers, and special characters can enhance password strength and make it more challenging for brute force attacks to succeed.
Intrusion Detection Systems (IDS): Implement IDS to detect and block suspicious login attempts or unusual patterns of activity, which could indicate a brute force attack in progress.
Monitoring and Response: Continuously monitor VPN traffic and system logs for signs of unauthorized access or brute force attempts. Promptly investigate and respond to any suspicious activity to prevent potential security breaches.
By incorporating these proactive measures into VPN security protocols, users can significantly reduce the risk of falling victim to Brutus brute force attacks and enhance their overall online privacy and security. Remember, staying vigilant and proactive is key to staying one step ahead of cyber threats in an increasingly interconnected world.
0 notes