#IP automation tool
Explore tagged Tumblr posts
Text
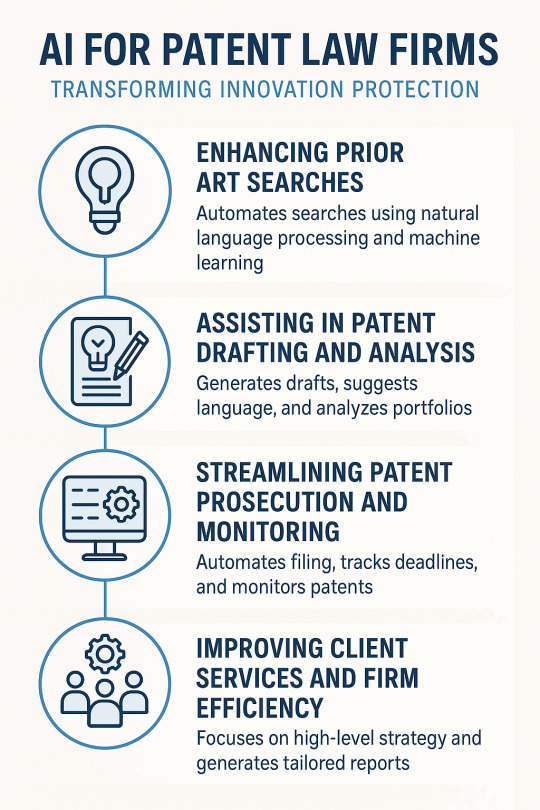
AI for Patent Law Firms: Transforming Innovation Protection
In recent years, artificial intelligence (AI) has made significant inroads into the legal profession, and patent law firms are among the most promising beneficiaries. From automating prior art searches to drafting patent applications and streamlining portfolio management, AI is transforming how intellectual property (IP) professionals operate. As innovation accelerates globally, AI is proving indispensable in helping patent attorneys manage increasing workloads while maintaining the precision and strategic foresight that the field demands.
1. Enhancing Prior Art Searches
One of the most time-consuming tasks in patent prosecution is conducting thorough prior art searches. Traditionally, this required manually sifting through thousands of patent documents and scientific publications. Today, AI-powered search tools—leveraging natural language processing (NLP) and machine learning algorithms��can scan vast databases in seconds and return highly relevant results. These tools understand context and can identify similar inventions even when keywords differ, greatly improving both the speed and accuracy of search results. This enables attorneys to build stronger patent claims and avoid costly litigation risks.
2. Assisting in Patent Drafting and Analysis
AI is increasingly being used to assist in drafting patent applications by generating first drafts based on input claims and invention disclosures. While human oversight remains essential, AI tools can structure documents, suggest language based on existing patents, and even highlight inconsistencies or vague terminology. This not only accelerates the drafting process but also helps ensure compliance with the rigorous standards set by patent offices like the USPTO and EPO.
Moreover, AI tools can analyze existing patent portfolios to identify gaps, potential invalidity risks, or infringement threats. This enables firms to provide clients with strategic advice grounded in real-time data and comprehensive patent landscape analysis.
3. Streamlining Patent Prosecution and Monitoring
Patent prosecution involves extensive communication with patent offices, which can be delayed by human bottlenecks. AI can automate much of this process, including filing forms, tracking deadlines, and managing office actions. It can also analyze examiner behavior patterns to predict outcomes or suggest alternative claim strategies, giving firms a competitive edge.
Furthermore, AI can monitor granted patents and publications globally, alerting attorneys to competitor filings or infringement risks. Such capabilities are invaluable in sectors like biotechnology, software, and telecommunications, where overlapping IP rights are common.
4. Improving Client Services and Firm Efficiency
AI also empowers patent law firms to offer more value-driven services. By automating routine tasks, attorneys can focus more on high-level strategy and client engagement. AI-based tools can generate reports, dashboards, and risk assessments tailored to client needs, improving transparency and decision-making. Additionally, AI supports scalable operations, making it easier for firms to serve startups and large enterprises alike with consistent quality.
AI is not replacing patent attorneys—it’s empowering them. By enhancing efficiency, accuracy, and strategic insight, AI is becoming a vital partner in the practice of patent law. Forward-thinking firms that embrace AI are better positioned to navigate the complexities of modern IP management and deliver superior outcomes for their clients. As the legal tech landscape evolves, AI will play a central role in shaping the future of patent protection and innovation strategy.
Read More:
Here're The 10 Best AI Tools for Patent Drafting in 2025
#AI for patent law firms#patents#innovation#AI patent assistant#automated patent drafting#IP automation tool
0 notes
Text
Valuing Intellectual Property | A New Challenge for Industrial Estimating Services
Introduction As industrial sectors evolve through digitalization, automation, and innovation, intellectual property (IP) has become one of the most valuable assets within a project. From proprietary software and patented designs to custom manufacturing processes and smart technologies, IP is reshaping how value is created and assessed. However, traditional industrial estimating services—built around physical materials, labor, and equipment—are now faced with a complex challenge: how to accurately estimate the cost and value of intellectual property within industrial projects.
This emerging frontier calls for a redefinition of scope in industrial estimating services, expanding their role to account for intangible assets that drive both performance and competitive advantage.
Why IP Matters in Industrial Cost Estimation In many modern industrial developments, especially in high-tech manufacturing, advanced energy systems, and Industry 4.0-enabled factories, intellectual property comprises a significant portion of overall value. For instance:
A custom automation algorithm embedded in a robotics line
Proprietary energy-efficiency systems in a chemical plant
Secure software platforms for controlling distributed manufacturing
These IP-driven elements often represent a large portion of R&D investment and are critical to long-term operational efficiency. An accurate estimate must include not just the cost to implement or license such assets but also the potential risk, return, and lifecycle value they bring.
Key Categories of Intellectual Property in Industrial Settings Understanding how IP appears in industrial projects is essential for accurate estimation. Common categories include:
Patents: Inventions or processes owned or licensed by the project owner
Trade Secrets: Confidential formulas or methods applied during production
Software and Algorithms: Custom-coded tools used in automation and process control
Design Rights: Proprietary architectural or engineering designs
Licenses and Royalties: Payments made to third parties for the use of protected IP
Each of these categories demands unique valuation methods and estimation strategies that differ from traditional capital expenditures.
Challenges in Estimating IP Costs Valuing IP in industrial settings is inherently complex due to:
Intangibility: Unlike steel or labor hours, IP has no physical form and often lacks clear benchmarks.
Variable Cost Structures: Licensing fees, development costs, and long-term support vary widely by industry and supplier.
Lifecycle Uncertainty: IP might evolve or become obsolete quickly, adding estimation risk.
Confidentiality: Many IP assets are guarded by NDAs or corporate secrecy, limiting estimator access.
As a result, industrial estimating services must blend financial modeling, legal review, and technical expertise to deliver accurate assessments.
Approaches to Integrating IP into Estimates To manage these complexities, forward-thinking estimating services apply several strategies:
Cost-Based Estimation: Involves calculating the original R&D or development costs and applying a markup based on projected use.
Market-Based Valuation: Uses comparative licensing or sales data for similar IP assets, when available.
Income-Based Modeling: Projects future cash flows generated by the IP (e.g., operational savings, productivity gains) and discounts them to present value.
Expert Collaboration: Engaging IP lawyers, technology consultants, and accountants to accurately categorize and value protected assets.
Case Example: Estimating an Advanced Robotics System A manufacturing client planned to install a robotics line powered by proprietary AI software developed in-house. While the hardware had clear market prices, the software’s value was harder to define. The industrial estimating service worked with internal developers and finance experts to model the cost of development, anticipated efficiency savings over ten years, and licensing potential if the software was reused across other sites.
By incorporating both direct and indirect value contributions, the estimate provided a holistic picture that helped justify a higher upfront investment.
Benefits of IP-Savvy Estimating Industrial clients gain several advantages when IP is accurately included in estimates:
More Realistic Budgets: Avoids underbudgeting by recognizing the full cost of IP integration or licensing.
Stronger Business Cases: Supports ROI projections for innovation-driven projects.
Better Risk Assessment: Helps identify where IP exposure (e.g., licensing dependencies) may affect project costs.
Investor Appeal: Demonstrates comprehensive valuation, which is critical for attracting investment in innovation-heavy projects.
New Tools and Trends As the demand grows, some industrial estimating platforms are adapting to include IP modeling features:
Digital Asset Registries: Help track owned or licensed IP within the project scope.
AI-Powered Valuation Engines: Use historical and market data to suggest value ranges.
Blockchain for IP Tracking: Ensures provenance and licensing status of digital IP in complex supply chains.
These innovations indicate that IP valuation is becoming a mainstream requirement in industrial estimating practices.
Limitations and Ongoing Development Despite advances, valuing IP remains a partly subjective exercise. The uniqueness of each asset and the lack of standard benchmarks can introduce variability. Moreover, legal changes—such as patent law shifts or tax implications—can alter value significantly.
Estimating services must remain adaptive, continuously updating models and methodologies to reflect both technical and legal developments.
Conclusion The rise of intellectual property as a strategic asset in industrial projects is reshaping the landscape for estimating services. No longer confined to bricks, pipes, and wires, estimators must now navigate code, algorithms, and trade secrets. By embracing this challenge, industrial estimating services not only improve budget accuracy but also elevate their strategic role in capital planning and innovation management. The result is a more holistic view of project value—one that aligns with the digital age.
#industrial estimating#intellectual property#IP valuation#industrial projects#cost estimation#IP assets#software cost#patent cost#innovation budgeting#intangible assets#ROI modeling#licensing fees#proprietary software#automation IP#manufacturing IP#trade secrets#digital asset valuation#tech integration#income-based estimation#market-based estimation#IP in construction#software estimation#R&D cost#risk analysis#estimating strategy#lifecycle cost#future-proofing#estimating service tools#high-tech estimating#cost planning
0 notes
Text
How to Optimize Automation Tools with Proxies IPs
With the popularity of automation tools in the content publishing space, many businesses and individuals rely on these tools to efficiently manage the bulk publishing of blog posts, videos, or e-commerce products.

In this post, I'm going to detail how to optimize automated content publishing using Proxies IP and teach you how to go about it with clear step-by-step instructions.
How do platform IP restrictions affect content distribution?

Frequent publication of the same IP: If you often publish a large amount of content in a short period of time, such as using automation tools to publish dozens of articles with one click, the platform will soon be "alerted". Because of this frequent operation, the platform is likely to think that you are not a "normal" user, but a robot or malicious script. So your behavior is restricted.
Multiple accounts operating under the same IP: The platform will also be suspicious of multiple accounts operating under the same IP address. It will wonder if these accounts are connected in some way. When the platform begins to suspect a connection between multiple accounts, it may take action to limit the functionality of these accounts or even block them.
These and other issues are very common for users of automation tools, so using the right Proxies IPs can help you manage publishing tasks more flexibly, avoid the impact of the platform's windfall control mechanisms, and ensure that bulk content publishing runs smoothly.
how can Proxies IP help optimize the publishing process?
Proxies become a very effective tool to help you publish content without worrying about being "targeted" by the platform. So how do Proxies help you optimize the entire publishing process? Let's discuss it in detail.
It is useful in that it assigns a different IP address to each network request, simulating multiple users or requests from different locations, so that the platform system will not notice that you are operating frequently, which in turn improves the success rate of publishing tasks.
The main advantages of Proxies IP include:
Reduce the risk of being restricted: Proxies IPs provide you with a different address each time you publish content, reducing the likelihood that the platform will detect abnormal operations.
Account Separation: If you are switching between multiple accounts, Proxies are able to provide each account with a separate IP address, avoiding account association issues.
Flexible geographic options: Proxies allow you to cover more markets by selecting IP addresses in different regions based on your publishing needs. How is it used?
Assign separate IPs to each account: Proxies allow you to assign separate IP addresses to different accounts, preventing the platform from detecting that all accounts are operated from the same IP. In this way, the accounts appear to be independent of each other, which effectively prevents the risk of correlation.
Flexible IP switching: You can flexibly switch IPs as needed to operate seamlessly across multiple platforms and accounts without fear of being blocked or restricted.
how to configure Proxies IP optimization automation tools?
To help you easily implement Proxies IP configuration, here are the specific steps to follow to enable you to automate content publishing.
Step 1: Choose the right type of Proxies, common types of Proxies include:
Static Residential Proxies: It will assign a fixed IP address to each session, which is suitable for long and stable automated operations such as crawling, data collection and account management.
Rotating Residential Proxies: It can change the IP address every time a request is made, which is suitable for operations that require multi-threaded processing and avoid IP blocking.

The speed and stability of the Proxies IP is critical in automation tasks. A good Proxies should have the following:
Low Latency: The response time of the Proxy Service should be as low as possible, which ensures that the automation tool does not time out due to long waits when running.
High Availability: Proxies need to be able to work in most situations to avoid frequent connection failures or drops.
Globally Distributed IPs: Depending on the needs of the automation task, selecting IPs in different regions can better bypass regional restrictions and improve task success rates.
Factors to consider when choosing Proxies IP services:
Stability: The stability of the IP address directly affects the smooth running of the release, choosing a stable service can avoid interruption in the middle of the release.
Abundant IP resources: Proxies with a large number of IP resources enable the use of different IPs for each task, avoiding duplication of use.
Responsiveness: Choose a fast Proxies service to ensure that every release is completed efficiently.

Step 2: Configure Proxies IP in Automation Tool
With the Proxies service in place, the next step is to configure the Proxies IP into the automation tool. Different tools are configured in different ways, and the following are common setup methods.
1.Get Proxies IP: First, log in to PROXY.CC and Get your IP address and port number.
2.Set Proxies IP in the tool:
Selenium userscan configure Proxies IP into Selenium with the following code:
from selenium import webdriver from selenium.webdriver.common.proxy import Proxy, ProxyType proxy_ip_port = "Proxy IP:Port number" proxy = Proxy({ 'proxyType': ProxyType.MANUAL, 'httpProxy': proxy_ip_port, 'sslProxy': proxy_ip_port, }) chrome_options = webdriver.ChromeOptions() chrome_options.proxy = proxy driver = webdriver.Chrome(options=chrome_options)
Puppeteer users, on the other hand, can use the following code:const browser = await puppeteer.launch({ args: ['--proxy-server=Proxy IP:Port number'] }).
Other tools: Most automation tools support Proxies. You can find the relevant options in the tool's "Network Settings" and fill in the IP address and port number you got from PROXY.CC.
Step 3: Optimize publishing strategies to ensure operational security
While Proxies can help you with IP restrictions, a sound publishing strategy is equally important. Here are a few suggestions to help you further optimize your publishing process:

3. Control release frequency: Although Proxies IP can help you Secure Proxies release, but still need to maintain the appropriate release frequency, to avoid frequent operation triggered by the platform wind control.
Step 4: Monitor the effectiveness of the release and make timely adjustments
Once publishing is complete, it is essential to continuously monitor the effectiveness of the publishing task. If you find publishing failures or account limitations, timely adjustments to Proxies IPs or publishing strategies are key to ensuring success.
1. Check the success rate of publishing: pay attention to whether any task fails due to IP problems, and replace Proxies IP or optimize operation time if necessary.
Conclusion
When publishing content in bulk, automation tools greatly improve work efficiency, but the issue of IP restrictions often hinders the smooth running of the publishing process. Proxies can not only effectively avoid these restrictions, but also improve publishing success and account security.
By choosing proxy services wisely, configuring Proxies IP to automation tools, and optimizing publishing strategies, you can ensure that publishing tasks are carried out efficiently and stably. Whether you are a content creator, an e-commerce seller or a marketing team, Proxies IP is a powerful tool to help you easily manage multiple accounts and optimize the publishing process.
1 note
·
View note
Note
you said you think gay sex cats is the new duchamp's fountain. i dont disagree and i kinda see what you mean already but please elaborate
it was a silly and tongue in cheek way to say that a lot of people are getting mad about it in a way that implies reactionary views on art, and that there's no way to say gay sex cats isn't art that wouldn't also imply that the fountain isn't art. a funny meme image is a funny meme image, but it is also funny to overthink and recontextualize them as art.
and the reaction makes the comparison even more apt. neural net generated artworks are anonymized mass produced images, vast majority having no artistic pretension or meaningful content such as a thomas kinkade painting. gay sex cats was made with no intent to be art, but the discourse it has with audience reaction and its appropriation in derivative works make it so. why is gay sex cats not art if people talking about it negatively allow it to be called art? is art only things you find beautiful and valuable? if so, what is value and beauty, and how do you draw the line? if gay sex cats was still ai generated but had more "aesthetic qualities" would it be art? if someone copies the original image by hand with all its ai generated faults where is the value generated? does the original still have no merit of its own, even after appropriation as a digital ready-made?
but the main reason as to why gay sex cats is comparable to the fountain still is because it made a lot of people with bad takes on art really really mad. and that the pissed off tags wouldn't look out of place as reaction to modern art in the 1920s. art is a flat circle
EDIT: well. putting an addendum because in retrospect more people took either or both the op and image in face value and much more self serious than ever intended. a lot of people understood the tone i was getting at, and i still stand by the questionings i added on, but still for clarification. the original comparison is not serious. it's self evidently ridiculous to compare a meme image to a historically significant artwork, the comparison was only drawn because they were both controversial to an audience, who reacted denying their status as respectively as an image and as art, and that it was funny that the negative reaction people had to the original image explicitly denied its status as art, even if the meme never had pretension to be art, so it was funny to draw a comparison and iterate on that.
i did think it was valid to bring in questionings about art and meaning because that's the reaction i saw most and wanted to make people think about the whys, and that also i do not think it's valid to base your dislike on ai art on either grounds of questioning its position and value as artwork, or even as a question of ip theft. regular degular handmade art can be soulless, repetitive, thoughtless, derivative, unethical, open and blatant theft, and much more, and that does not make it any less of an artwork. neural nets are tools that generate images by statistic correlation through human input.
the unambiguous issue with neural nets in art is its use as a tool by capital, to threaten already underpaid and overworked working artists and to keep their labor hostage under threat of total automation. in hindsight i regretted not adding the paragraph above as it was a way in which people could either misinterpret or assume things about me, but hindsight is hindsight and there's no way to predict how posts would blow up. so shrugs. i had written more posts in my blog that elaborated on that because asks would bot stop coming. and i think my takeaway is that people will reblog anything with a funny image without reading the words around it, or even closely looking at the image.
1K notes
·
View notes
Text
Earlier this week, OpenAI launched its new image generation feature, which is integrated directly into ChatGPT and allows users to input more complex instructions for editing and organizing the presentation of the output. The first big viral trend to come out of the new service was users turning photos of family vacations, historical events, and pop cultural images into animated stills in the style of Studio Ghibli films. (The whole thing was a bit of a throwback to the heady days of 2023 when you would see AI influencers sharing photos of famous figures in the style of Wes Anderson films or whatever.) ChatGPT let users “Ghibilify” the images, so we got Ghiblified Hawk Tuah girl, Ghiblified Elon Musk (obviously), and so on. The issue here should be obvious. I won’t pretend to know exactly how Miyazaki thinks about modern generative AI systems—the tool he was commenting on was a cruder prototype—though one might venture to argue that he’d feel even more strongly about tools that further automate human art with greater ease, and often drive it further into the uncanny valley. Regardless, the man on record with likely the strongest and bluntest disavowal of using AI tools for art, is now the same man whose notoriously painstakingly handcrafted art is being giddily automated by ChatGPT users for what amounts to a promotional campaign for a tech company that’s on the verge of being valued at $300 billion. Sam Altman, OpenAI’s CEO, not only participated, changing his X avatar to a ‘Ghiblified’ self portrait, but insisted that this was the plan all along. Which in turn raises the specter of copyright infringement. Speaking to TechCrunch, a copyright lawyer very diplomatically said that while it’s unlikely infringement to produce images in the style of a studio, it’s “entirely plausible” that OpenAI’s models were trained on millions of frames of Ghibli films. He noted that it’s still an open question whether or not that in fact violates current IP law, or constitutes fair use, as the tech companies argue. On that front, judges recently dealt tech companies a blow, ruling in favor of Thomson Reuters that a pre-ChatGPT AI system was creating images that competed with the original material, and thus was not in fact fair use. OpenAI and Google, meanwhile, are desperately trying to win this battle, appealing to the Trump administration directly, and going so far as to argue that if they’re not allowed to ingest copyrighted works into their training data, China will beat the US in AI. Now, if—and of course this is a whopping if—OpenAI had consulted Studio Ghibli and its artists on all this, if those artists had consented and say reached a licensing deal before the art and frames from their films were ingested into the training data (as is pretty apparently the case), then look, this would indeed be a bout of generally wholesome fun for everyone involved. Instead, it’s an insult.
[...]
OpenAI and the other AI giants are indeed eating away at the livelihoods and dignity of working artists, and this devouring, appropriating, and automation of the production of art, of culture, at a scale truly never seen before, should not be underestimated as a menace—and it is being experienced as such by working artists, right now.
27 March 2025
118 notes
·
View notes
Text
Why is Cloudflare blocking me?
Cloudflare is a content delivery network (CDN) and security service that helps protect websites from various threats, such as DDoS attacks, malicious bots, and hackers. If Cloudflare is blocking you, it’s likely because the security settings on the website you’re trying to access have identified your connection as potentially suspicious or harmful. Some common reasons for Cloudflare blocking your access include:
IP reputation: Cloudflare maintains a list of IP addresses known for spam, hacking attempts, or other malicious activities. If your IP address is on this list or has a poor reputation, you may be blocked.
High security settings: The website owner might have set their Cloudflare security settings to a high level, causing more aggressive filtering of incoming traffic. In such cases, even legitimate users might be blocked or challenged.
Rate limiting: Cloudflare can block or limit access from IP addresses that make too many requests within a short period, as this can indicate a DDoS attack or automated scraping attempts.
Browser or user agent issues: Using an outdated browser, a non-standard user agent, or having disabled cookies and JavaScript might trigger Cloudflare’s security measures.
VPN or proxy usage: Using VPNs, proxies, or Tor can sometimes cause Cloudflare to flag your connection as suspicious, as these tools are often used to hide malicious activities.
Firewall rules: The website owner may have set specific firewall rules in Cloudflare that block certain IP addresses, countries, or user agents.
To resolve the issue, you can try the following:
Clear your browser cache and cookies, and ensure JavaScript is enabled.
Update your browser to the latest version or try using a different browser.
Temporarily disable your VPN or proxy, if you are using one.
Check your internet connection and restart your modem or router to obtain a new IP address.
If you suspect your IP address has been mistakenly flagged, you can contact the website owner or Cloudflare support to request a review of your IP address.
Remember that these measures are in place to protect websites and their users from security threats. While blocking can be frustrating, the intent is to maintain a safe online environment for everyone.
Source @ao3org
103 notes
·
View notes
Text
You’re cheering a win — while gangrene spreads
Some of you are celebrating lawsuits against Midjourney, thinking they’ll restore the good old days of commissions and human-made fanart.
But let’s walk through how this really unfolds — for you.
🔍 1. Character Recognition Models Are Coming
Big IP holders already have extensive visual and text datasets of their characters.
It’s only a matter of time before they deploy detection models trained specifically to recognize deviations and unauthorized reinterpretations — from sexualization to gender-swaps.
📡 2. Platforms Will Be Forced to Integrate IP-Scanning APIs
No need to chase individual fanartists. Platforms will be required to connect to centralized scanning tools — designed and controlled by rights holders.
Upload an image → the API flags it → blocked or quietly deleted. No public drama, just silence. Or shadowban.
🧾 3. One Lawsuit Is All It Takes
Companies don’t need to send cease-and-desists to everyone. They target infrastructure.
Once a platform is legally pressured or threatened with deplatforming (remember Tumblr in 2018?), it will comply — automatically.
They won’t manually check if your blog is cute, transformative, or queer.
They’ll just press delete.
🖼️ 4. It Won’t Matter If It’s AI or Human
Once automated detection is in place, the question of who made the image becomes irrelevant.
If it looks like protected IP — it’s treated as infringement.
📉 5. The 2018 Tumblr Purge Was Just a Dress Rehearsal
When Apple removed Tumblr from the App Store over child exploitation concerns, the platform overreacted — purging thousands of blogs in a broad NSFW sweep.
No due process. No clear appeals. Just mass deletion.
Tumblr has done this before. And that was before AI.
🧠 And here’s the part you’re missing:
This isn’t just about AI art.
The same infrastructure that blocks machine-made fanart can — and will — block yours.
You’re not cheering for justice.
You’re cheering like a patient who’s glad their infected finger was cut off — not realizing the blood is already carrying sepsis to the lungs.
#anti ai#ai#pro ai#disney#midjourney#ai discussion#ai discourse#digital culture#copyright#fanart#fandom culture#artists on tumblr#creative freedom#ao3 writer#ao3 author#2018 tumblr#tumblr purge#important read
2 notes
·
View notes
Text
VIA Facebook là gì? Vì sao dân chạy ads không thể thiếu?
VIA Facebook là gì? Vì sao dân chạy ads không thể thiếu?
Trong cộng đồng người kinh doanh online, đặc biệt là những ai chạy quảng cáo Facebook hoặc nuôi tài khoản số lượng lớn, cụm từ "VIA Facebook" chắc hẳn không còn xa lạ. Nhưng nếu bạn mới bắt đầu, hoặc từng nghe mà chưa hiểu rõ, bài viết này sẽ giúp bạn nắm được VIA Facebook là gì, công dụng ra sao, và vì sao nó quan trọng đến vậy.
VIA Facebook là gì?

VIA Facebook là cách gọi phổ biến tại Việt Nam, dùng để chỉ tài khoản Facebook thật của người dùng thật, đã được tạo và sử dụng một thời gian trước đó. Tài khoản này thường có lịch sử hoạt động rõ ràng, có bạn bè, tương tác, ảnh đại diện và các bài đăng thật.
Không giống như tài khoản clone (tài khoản mới tạo, thông tin ảo), VIA có độ trust cao hơn, ít bị checkpoint (bảo mật Facebook yêu cầu xác minh) và thường được sử dụng để:
Chạy quảng cáo Facebook (Facebook Ads)
Seeding (comment, like ảo có tương tác thật)
Nuôi tài khoản clone phục vụ mục đích automation
Vì sao nên dùng VIA thay vì tạo tài khoản mới?
Facebook ngày càng siết chặt các chính sách bảo mật. Khi bạn tạo tài khoản mới và chạy ads ngay, khả năng bị checkpoint, quét xác minh hoặc vô hiệu hóa là rất cao. Trong khi đó, VIA Facebook cũ, tương tác thật có uy tín hơn trong mắt thuật toán, dẫn đến:
Quảng cáo dễ được phê duyệt
Hạn chế rủi ro vô hiệu hóa tài khoản
Dễ tạo Business Manager và tài khoản quảng cáo con
Các loại VIA Facebook phổ biến

Hiện nay, thị trường chia VIA thành nhiều loại, trong đó phổ biến nhất là:
VIA cổ: tài khoản lâu năm (từ 2010 trở về trước), độ trust cao, giá thành cao.
VIA Việt: tài khoản người Việt, dễ dùng, hỗ trợ tốt cho seeding, tương tác.
VIA ngoại: tài khoản từ IP nước ngoài (Mỹ, EU...), thường dùng để tạo tài khoản quốc tế hoặc chạy tool.
Mua VIA Facebook ở đâu uy tín?

Nếu bạn đang cần mua VIA Facebook chạy quảng cáo hoặc nuôi tài khoản, hãy tìm những đơn vị cung cấp:
Bảo hành rõ ràng
Tài khoản đăng nhập không checkpoint
Có lịch sử tương tác thực
Hỗ trợ kỹ thuật sau khi mua
Hãy tránh những nơi giá quá rẻ vì có thể đó là tài khoản rác, hoặc clone bị làm giả VIA.
Kết luận
VIA Facebook là công cụ không thể thiếu cho người làm digital marketing, đặc biệt là chạy ads.
CTA – Hành Động Ngay!
Bạn đang tìm kiếm VIA chất lượng cao, bền, ít checkpoint và sẵn sàng triển khai chiến dịch quảng cáo ngay hôm nay? 👉 Inbox ngay để được tư vấn miễn phí & nhận danh sách VIA Facebook chạy ads đang có sẵn! 📞 Zalo/Facebook: [0981 282 956 / Mua VIA Việt] 📦 Cam kết: VIA sạch – Hỗ trợ nhiệt tình – Bảo hành đầy đủ!
2 notes
·
View notes
Text
Computer Networks: Basics, Types, and Benefits Explained
Computer networks are a big part of today’s highly automated world. They connect people, systems, and devices, making communication and resource sharing effortless. Whether it’s examining the internet, collaborating on projects, or sharing files, computer networks play a vital role in both personal and professional environments. We’ll cover the basics of computer networks, discuss their different types, and see the benefits they deliver.

What is a Computer Network?
A computer network is basically a system where multiple devices are linked together to share resources and exchange data. These devices can include laptops, mobile phones, servers, and networking equipment like routers. Networks enable smooth communication and allow devices to work together efficiently, making everything from browsing the web to managing complex business operations much easier.
Types of Computer Networks
Personal Area Network (PAN):
Personal Area Networks are designed as small networks intended for individual purposes. They usually span a limited distance and link devices such as.
smartphones, laptops, and tablets. For instance, connecting your phone to your computer via Bluetooth forms a simple PAN.
Local Area Network (LAN):
LANs are commonly used in homes, schools, and offices to connect devices within a limited area. For example, to allow employees to share files and printers seamlessly, all the computers in an office might be connected to a LAN.
Wide Area Network (WAN):
A WAN stretches over a significantly larger territory, often connecting devices or LANs across cities, countries, or even continents. The internet is the most well-known example of a WAN, authorized global connectivity.
Metropolitan Area Network (MAN):
Sitting between LANs and WANs, a MAN is typically used to connect networks across a campus or city. Cable TV networks are a common example of a MAN.
Wireless Networks:
Wireless networks use technologies like Bluetooth or Wi-Fi to connect devices without cables. They’re widely used in offices, homes, and public places, offering convenience and mobility.
Key Components of Computer Networks
Devices (Nodes): Servers that interact within the network these include computers and smartphones.
Connections (Links): The physical or wireless pathways that transfer data between devices.
Protocols: These are the rules that control data transmission, such as TCP/IP, to maintain smooth communication.
Switches and Routers: Switches connect devices in a network, while routers link different networks together.
Benefits of Computer Networks
Resource Sharing:
Networks make things easy to share like files, printers, and software applications, reducing the need for duplicate resources.
Seamless Communication:
With instant messaging, email, and video calls, networks ensure quick and authentic communication, no matter how far away are you.
Cost Savings:
By collecting resources and data storage, networks cut down on operational costs, especially for businesses.
Anywhere Access:
Modern networks allow you to access data from any connected device, whether you are at home or on the go.
Scalability:
As your needs develop networks will grow too, by supporting more users and devices over time.
Increased Productivity:
It reduces delays in automated processes and real-time data sharing and streamlines workflows, boosting efficiency.
Why Computer Network Skills Are Crucial for Entry-Level Corporate Roles
For those starting their careers, knowledge of computer networks can be a significant asset:
Essential for Office Environments:
In today's world, most workplaces rely on LANs and WANs for everyday operations. Knowing how these networks function allows employees to balance basic connectivity issues, making sure work stays on track without interruptions.
Supports Collaboration Tools:
Corporate tools like Microsoft Teams, Slack, and cloud-based systems depend heavily on networks. Understanding their underlying principles helps entry-level employees adapt quickly to these platforms.
Enhances Problem-Solving Skills:
Entry-level employees with networking knowledge can help IT, teams, by identifying and resolving minor network problems, exhibiting their value early on.
Boosts Technical Proficiency:
Networking skills indicate a candidate’s technical potential, giving them a head start in industries where tech literacy is required.
Prepares for Future Roles:
As technology makes progress, advanced networking concepts like cybersecurity and IoT integration are becoming integral. Early experience with networks lays a strong beginning for growth in these areas.
Challenges of Computer Networks
Security Risks: Networks are at risk of threats like hacking and malware, requiring robust security measures.
Cost of Setup: High-quality network infrastructure can be costly to install and maintain.
Technical Complexity: Balancing and managing networks frequently need specialized skills.
Conclusion
Computer networks are essential in today’s globalized world. From pushing day-to-day operations in businesses to enabling global communication, their impact is wide-ranging. For aspiring professionals, having computer networking skills can provide a competitive advantage, especially in entry-level corporate roles where technical knowledge is highly valued. By understanding the basics of networks and their benefits, individuals, and organizations can unlock new levels of productiveness and innovation.
I mastered Computer Network at NIPSTec, which is renowned as the best Computer Network institute in Delhi. If you're in Delhi and looking for top-notch training in computer networks, visit NIPSTec for expert guidance and practical learning.
2 notes
·
View notes
Text
Cynthia Kayle Shares Key Strategies for Effective Threat Mitigation

Introduction
Threat mitigation is an essential aspect of any organization’s security strategy. While the identification of emerging threats is crucial, organizations must also develop robust mitigation strategies to prevent potential risks from escalating into major incidents. Effective threat mitigation requires a comprehensive approach, blending proactive measures, real-time response, and long-term security strategies to reduce vulnerabilities across all operational areas.
This article explores key strategies for effective threat mitigation, offering actionable steps for organizations to safeguard their operations, personnel, and reputation from potential harm.
1. Establish a Risk Management Framework
A strong risk management framework serves as the foundation for identifying, analyzing, and mitigating risks in an organized and structured manner. This framework should integrate security, compliance, and operational requirements, ensuring that all potential threats are addressed at the organizational level.
Actionable Steps:
Create a Risk Management Team: Assemble a dedicated team to assess, identify, and respond to risks across the organization. This team should include experts from security, IT, legal, and compliance.
Develop a Risk Register: Maintain a comprehensive risk register that tracks all identified threats, their potential impact, likelihood, and mitigation strategies. This register should be continuously updated as new risks emerge.
Prioritize Risks Based on Impact: Use risk assessment tools to evaluate the severity of each risk and prioritize mitigation efforts accordingly. Focus on threats with the highest potential impact on business continuity.
Reference:
Full URL: https://www.iso.org/iso-31000-risk-management.html
2. Implement Security Best Practices and Policies
Establishing security policies and best practices helps to create a standardized approach to threat mitigation. These policies should cover everything from data protection to physical security, and should be enforced across the organization to ensure consistency.
Actionable Steps:
Develop Comprehensive Security Policies: Draft detailed security policies covering access controls, incident response, cybersecurity, and physical security. Ensure these policies are aligned with industry standards and regulatory requirements.
Enforce Compliance: Regularly conduct audits to ensure that policies are being followed. Implement training programs for employees to keep them informed about security policies and their role in risk mitigation.
Review and Update Policies: Conduct regular reviews of security policies to account for new threats, emerging technologies, and regulatory changes. Update policies as necessary to stay ahead of evolving risks.
Reference:
Full URL: https://www.nist.gov/cyberframework
3. Leverage Technology for Threat Detection and Response
Technology plays a crucial role in identifying and mitigating threats quickly and efficiently. From advanced monitoring systems to AI-driven analytics, technology can significantly improve the effectiveness of your threat mitigation strategies.
Actionable Steps:
Invest in Threat Detection Tools: Use advanced tools like intrusion detection systems (IDS), endpoint detection and response (EDR), and firewalls to monitor your network in real-time and detect potential threats as they arise.
Leverage Artificial Intelligence (AI): Implement AI-powered tools such as Darktrace or Vectra AI that can automatically detect anomalous behavior and mitigate threats before they escalate.
Deploy Automated Response Systems: Set up automated incident response systems that can take immediate action when a threat is detected, such as isolating infected systems, blocking suspicious IP addresses, or initiating alerts.
Reference:
Full URL: https://www.darktrace.com
Full URL: https://www.vectra.ai
4. Foster a Culture of Security Awareness
Emerging threats often stem from human error or lack of awareness within the organization. To mitigate this, building a security-aware culture is crucial. Employees must be educated on recognizing suspicious activity and adhering to security protocols.
Actionable Steps:
Conduct Regular Security Training: Provide ongoing training sessions for employees, covering topics such as phishing prevention, data protection, and password security.
Simulate Real-Life Scenarios: Run security awareness drills to simulate common attack scenarios like phishing emails or data breaches. This will help employees recognize and respond to threats effectively.
Encourage Reporting: Create a clear process for employees to report suspicious activity or potential security breaches. Ensure that they feel empowered to speak up without fear of repercussions.
Reference:
Full URL: https://www.sans.org/cyber-security-skills-training/
5. Establish Incident Response and Recovery Plans
A well-defined incident response plan (IRP) is crucial for quickly addressing and mitigating the impact of a security breach or attack. Equally important is having a recovery plan to restore operations and minimize downtime.
Actionable Steps:
Develop an Incident Response Plan (IRP): Outline clear steps for responding to various types of security incidents, including data breaches, malware infections, and physical security threats. Include protocols for containment, investigation, and recovery.
Test and Update the IRP Regularly: Conduct regular simulations and tabletop exercises to test the effectiveness of the IRP. Update the plan as necessary to account for new threats and organizational changes.
Create a Business Continuity Plan (BCP): Develop a business continuity plan that includes disaster recovery procedures and ensures the organization can continue operating in the event of a major security incident.
Reference:
Full URL: https://csrc.nist.gov/publications/detail/sp/800-61/rev-2/final
Conclusion
Effective threat mitigation requires a holistic approach that integrates risk management, advanced technology, employee awareness, and well-defined response plans. By employing these strategies, organizations can proactively address threats, reducing the potential for damage and ensuring business continuity in the face of security challenges.
Adopting these measures will enhance your organization's ability to not only identify emerging threats but also effectively mitigate them before they escalate into larger problems.
References:
Full URL: https://www.iso.org/iso-31000-risk-management.html
Full URL: https://www.nist.gov/cyberframework
Full URL: https://www.darktrace.com
Full URL: https://www.vectra.ai
Full URL: https://www.sans.org/cyber-security-skills-training/
Full URL: https://csrc.nist.gov/publications/detail/sp/800-61/rev-2/final
#cynthia kayle#RiskMitigation#SecurityExpert#ThreatManagement#CommunityProtection#CrisisManagement#StrategicSecurity#SafetyPrograms#IntelligenceDriven#SecurityConsulting
1 note
·
View note
Text
Guide for Importers on Manufacturing Control
Efficient Manufacturing Control in China
1. Understand the Chinese Manufacturing Environment:
Diverse Ecosystem: China offers a vast range of manufacturers, from small workshops to large factories. This variety is beneficial but also poses challenges in ensuring consistent quality.
IP Concerns: Despite improvements, IP protection in China can be inconsistent, requiring robust measures to safeguard your innovations.
Regulatory Landscape: China’s complex and changing regulations make compliance crucial to avoid fines and reputational damage.
Quality Control: While quality has improved, some sectors still prioritize quantity over quality. Rigorous quality protocols are essential.
Labor & Costs: Labor costs are rising, pushing manufacturers toward automation. Infrastructure is robust, but supply chains can be disrupted by natural disasters or policy changes.
Government Policies: China’s government heavily influences manufacturing through policies and incentives, which can affect costs and market access.
2. Build a Strong Foundation:
Supplier Selection: Choose reliable suppliers through thorough due diligence, including factory visits and financial checks.
Clear Communication: Provide detailed specifications and maintain open communication to avoid misunderstandings.
Quality Management: Implement a Quality Management System (QMS) and conduct regular audits to ensure consistent product quality.
Strong Relationships: Develop long-term partnerships with suppliers to build trust and collaboration.
3. Implement Effective Control Strategies:
QA & QC: Establish a robust QA/QC framework to ensure consistent product quality.
Supplier Development: Invest in your suppliers’ capabilities to improve quality and efficiency.
Risk Management: Prepare for disruptions with backup plans and diversified suppliers.
Contractual Coverage: Clearly define product specifications and include IP protections in contracts.
Third-Party Verification: Use third-party inspections to ensure compliance and quality.
4. Manage Logistics & Supply Chain:
Transportation: Choose the best transport mode and routes to minimize costs and delays.
Warehousing & Inventory: Optimize warehouse locations and use management systems to track inventory.
Customs & Documentation: Ensure compliance with customs regulations and prepare accurate documentation.
Supply Chain Visibility: Use technology to monitor shipments and collaborate with suppliers.
Risk Assessment: Develop contingency plans for disruptions like natural disasters or strikes.
5. Overcome Common Challenges:
Language & Cultural Barriers: Hire experts to bridge gaps in communication and cultural understanding.
IP Protection: Secure your IP with patents, trademarks, and NDAs; monitor for infringements.
Regulatory Compliance: Stay updated on regulations and partner with local experts for compliance.
Supply Chain Disruptions: Diversify suppliers, maintain sufficient inventory, and use smart tools for monitoring.
6. Continuous Improvement:
Use data analytics to track trends and improve processes.
Regularly evaluate supplier performance and invest in employee training.
Embrace technology to enhance communication and efficiency.
7. Build a Culture of Quality:
Encourage employees to propose improvements.
Reward contributions to quality enhancement.
Focus on exceeding customer expectations.
Conclusion: Effective manufacturing control in China requires ongoing effort, attention, and adaptation. Invest in strong practices to improve product quality, reduce costs, protect your brand, and optimize your supply chain.
3 notes
·
View notes
Text
Top Technical Skills for Electronics Engineer Resume in 2024
Electronics and Communication Engineering (ECE) offers a wide array of career opportunities due to its interdisciplinary nature, combining principles from electronics, telecommunications, and computer science. Here are the top 15 career options for graduates in this field:
1. Telecom Engineer
Telecom engineers design and manage communication systems, including optical fibers, microwave transmission, and IP networks. They analyze existing technologies and develop new solutions to enhance communication reliability and efficiency.
2. R&D Software Engineer
These engineers focus on creating and testing new software products. They play a crucial role in research and development, working on automation and mechanical controls to improve software systems across various industries.
3. Software Analyst
Software analysts design, develop, and test software applications, ensuring they meet user needs. They act as a bridge between developers and users, managing software updates and enhancing user experience.
4. Electronic Design Engineer
Electronic design engineers create electronic circuits and devices tailored to specific requirements. They work on projects ranging from consumer electronics to complex communication systems.
5. Embedded Systems Engineer
Embedded systems engineers develop software for embedded systems found in various devices like appliances, medical equipment, and automotive systems. This role requires proficiency in both hardware and software development.
6. Network Engineer
Network engineers design, implement, and manage computer networks within organizations. They ensure network security and optimize performance for efficient data transfer.
7. Service Engineer
Service engineers maintain and repair electronic equipment used in various industries. Their work ensures that systems operate smoothly, minimizing downtime for businesses.
8. Technical Sales Engineer
In this role, engineers leverage their technical knowledge to sell complex electronic products or services. They often work closely with clients to understand their needs and provide tailored solutions.
9. Quality Assurance Engineer
Quality assurance engineers focus on testing products to ensure they meet required standards before they are released to the market. This role involves developing testing protocols and analyzing results to improve product quality.
10. Systems Engineer
Systems engineers oversee the integration of various subsystems into a complete system, ensuring all components work together effectively. This role is critical in projects involving complex electronic systems.
11. Electronics Technician
Electronics technicians assist in the design, development, and testing of electronic equipment. They often work under the supervision of engineers to troubleshoot issues and perform repairs.
12. Data Analyst
Data analysts in the ECE field focus on interpreting data related to electronic systems or communications networks. They use statistical tools to provide insights that can improve system performance or user experience.
13. Technical Director
Technical directors oversee engineering projects from conception through execution, ensuring technical feasibility while managing teams of engineers. They play a pivotal role in strategic planning within organizations.
14. Chief Technical Officer (CTO)
As a senior executive, the CTO is responsible for overseeing the technological direction of a company. This role involves strategic decision-making regarding technology investments and innovations.
15. Research Scientist
Research scientists in ECE focus on advancing knowledge in areas like telecommunications or signal processing through experimental research or theoretical analysis. This role often requires advanced degrees (MTech or PhD) for positions in academia or specialized industries.
Conclusion
Arya College of Engineering & I.T. is the Best Engineering College in Jaipur that gives career landscape for Electronics and Communication Engineers is diverse and continually evolving due to rapid technological advancements. Graduates can choose from various roles across multiple sectors including telecommunications, IT, manufacturing, aerospace, healthcare, and more, making ECE a promising field for aspiring professionals seeking dynamic career paths.
2 notes
·
View notes
Link
Security Suite is one of 11 professional plugins included with the WordPress Plugin Toolbox. Features of Security Suite: - Enable dual-layered security with biometric and 2FA locks - Create your own dynamic firewall with IP logging - Scan for and implement security recommendations - Scheduled malware scanning - Safe Repair for suspicious files - Comprehensive audit logging - Malware Scanning - Hosted WAF integration - Scheduled Security Reports - Google blocklist monitoring - Pwned Password Check - Force Password Reset - User Agent Banning - Google reCAPTCHA for WooCommerce - Geolocation blocking (block based on location) - Lockout logs - Backup Codes 2FA auth - 2FA integrations: Google Authenticator, Microsoft Authenticator, Authy, and more - Global IP blocklist & monitor - Login protection - Security tweaks and recommendations - Security Headers - Two-factor authentication - IP lockout device - Google reCAPTCHA - Core and plugin code checker - Login masking - Restore and repair changed files - Email Notifications - 404 Lockouts - Manual IP allowlist and blocklist - Config, save current settings, and apply any time - Resolve security recommendations and issues in bulk - Fallback Email 2FA auth - Automatic security keys regeneration - Managing user login duration - Bio metric Authentication See more about Security Suite ⬇ https://t2websolutions.com/plug-ins/security-suite/
3 notes
·
View notes
Note
Delete your account, anti-vpn loser
I guess my post broke containment overnight huh.
i'm not anti-vpn, I literally said *in the post* I use a vpn everywhere else online. I got banned for using a vpn. if there wasn't the risk of being banned again, I'd be using a vpn right now on this shitty little ad-riddled website. how in the fuck am I anti-vpn? I'm anti-aggressive spam filtering is what I am, i'm anti-over automation at the expense of users, and that's what the problem is on this website, overly sensitive ban triggering without human oversight. it's the same automoderation used on sites like fandom/wikia where I've modded a huge wiki for six years, and their ip ban tool works in an identical way, I'm not pulling this out of my ass. all this is literally what I said in the post, if you actually read it. go look in the notes on the post, see how many people are connecting the dots that it's their vpn usage on here that got them shadowbanned - because tumblr is not communicating that this is what's going on. when you contact support they never tell you why. but we all have the exact same thing in common.
all I care about is nobody going through what I did (the post was originally intended just to warn my friends/moots on here), which is essentially losing your account - because what's the point in being on here if you can't interact with anyone? if even your likes don't appear in peoples' notes, let alone being able to send messages or appear in tags? you wouldn't have even been able to send this anon, it would have gone into the wind. it's making people digital ghosts without communicating why or how to undo it. it's terrible moderation practise and the only thing anyone can do about it is let their friends know this is why it's happening to them, because tumblr sure isn't.
8 notes
·
View notes
Text
TITLE: PrismNET Asia-Pacific Leaders Symposium: Launch of the 319 Global Service Center Initiative
On May 7th, the PrismNET Asia-Pacific Leaders’ Symposium was successfully held at the Cordis Hotel in Hong Kong, bringing together service center heads and community leaders from various countries and regions within Asia-Pacific to discuss the expansive plans for PrismNET. At the event, Marlik Luno, the Chairman of PrismNET Global Development Committee and Chief Operating Officer, welcomed the representatives of the Asia-Pacific community and outlined the development plans for the upcoming months. Luno highlighted the current global societal transformation characterized by significant shifts in productivity. PrismNET is at the forefront of this transformation, leading the development in the AIGC artificial intelligence industry. The company has addressed the industry’s core challenge of GPU power supply for energy in artificial intelligence, having upgraded 13 GPU power clusters globally with a total capacity reaching 1100P. Furthermore, the platform is developing the PrismNET Chain (PNC), a global distributed power cluster blockchain network aimed at consolidating idle and redundant GPU power for scheduling and distribution, thus maximizing the application value of individual GPU capacities.
Subsequently, Tomy Tang, from the Platform Education and Development Committee, analyzed the current state and future value of the AI+DePin industry track for the leaders. He discussed how PrismNET positions itself as the first platform globally to implement an AI+Web3.0 ecosystem. The platform’s GPU power leasing service has already provided cost-effective energy solutions for more AI enterprises. Using AI for content publication, data streaming, and automated sales through e-commerce server rooms built around the world, along with matrixed account operations, the platform has achieved over $7000 in sales profit per account on TikTok, demonstrating the deep application of AI in e-commerce.
Following this, William delved into an in-depth analysis of PrismNET’s business model and its long-term value prospects. Many community leaders expressed that PrismNET’s business model fully meets everyone’s market expectations and that this mechanism is adaptable to various market conditions, ensuring the best possible outcomes for business expansion. The business model, being a core element of project development, features low barriers to entry, high returns, vast potential for imagination, scalability, user-friendliness, and strong promotional drive, which are significant characteristics of the PrismNET model.
During the banquet, the platform made a major announcement with the launch of PriamAI, an AI short video tool tailored for C-end users, integrating functions like IP creation, graphic generation, video conversion, and digital human cloning. PrismAI provides numerous entrepreneurs with powerful tools for easy use. Additionally, users can utilize PNC for exchanges to enhance their experience significantly, also greatly boosting PNC’s circulation and application value within the ecosystem.
At the banquet, the 319 Global Service Center Plan was announced, which, through the strong support of salons and sharing sessions, aids in the business development of service centers in various regions and rapidly propagates PrismNET’s vast ecosystem in the market. The banquet also recognized outstanding service centers for April, with Chief Operating Officer Luno personally distributing awards to the winners. Additionally, the development and evaluation plans for the community in May and a preview of the PrismNET Global Elite International Symposium scheduled for June were announced.
During this meeting, leaders from the Wutong Community and Xinxin International Community shared their experiences, insights, and market development strategies deeply with the attendees, setting goals and resolutions for May. All leaders present reached a high consensus to strive with full effort to discuss, build, share, and win together, and to collaborate in developing a grand industry ecosystem alongside the platform.
About PrismNET
PrismNET aims to provide cheap computing power and sustainable development super power for global AIGC entrepreneurs and developers in the AI field. It promotes the development of the artificial intelligence industry through the construction of distributed computing power cluster networks and computing power leasing services under trusted networks. Provide global investors with a convenient way to participate in the artificial intelligence track and an AI income path.
Follow PrismNET on:
Website | Telegram |Channel| Twitter | Medium | YouTube

2 notes
·
View notes
Note
Hey wanted to reach out since I've seen you're a woman in cyber too. I was wondering if you knew of any courses/training material that could get me up to speed with using certain CLI tools? Mainly since I'll need it to do config reviews of certain cloud stacks; I'm moving from GRC to a tech/architecture type role and trying to do the reviews manually is a total pain : ( Any tips are appreciated :)
Hi! So I don't do any cloud management, but I have a trick and a more serious qdvice. Idk if it's applicable or not.
1. I memorise commands generally by remembering their meanings.
So for example we have nmap [IP] -sV -vv -p 15-3200 I think of -Service Version -Very Verbose -[Port range]. I also generally build my own cheat sheet based on the commands I use the most.
2. You learn how to write scripts. That's actually very doable. With a very powerful but easy language like python (but there are others!) You can build small programs to automate the process of getting the information you need. For example you could write a program that does a preliminary check, if this check hits some conditions it could perform other checks until it reaches the exit of the program. I cannot write the diagram rn I'm on mobile but if I had to check if something it's working or not this is how I would solve it
Automation is definitely not my area of expertise though, I have two people on the team that do exactly this stuff only.
2 notes
·
View notes