#IPAddress
Explore tagged Tumblr posts
Text
Cligence Software
Cligence Software is a versatile solution designed to simplify telecom data analysis and investigations. It offers advanced features like call detail record analysis, cell ID tracking, and IP address monitoring to provide accurate and actionable insights. Ideal for law enforcement and security agencies, Cligence enhances efficiency and decision-making. For more information, contact us at 9461101915.
0 notes
Text
IP Addresses vs Cookies: What You Need to Know
Key Takeaways Key Takeaways: IP Addresses: Unique identifiers for devices on the internet. Enable communication and data exchange between devices. Transition from IPv4 to IPv6 to accommodate the growing number of connected devices. Cookies: Small text files stored on your device by websites. Enhance user experience by personalizing browsing and remembering preferences. Raise privacy…
#BrowserSettings#Browsing#Cookies#cybersecurity#dataprivacy#digitalsecurity#Internet#IPaddress#IPv4#IPv6#onlineprivacy#Privacy#securitytips#Tech#technology#Tracking#VPN#Web#computers#dailyprompt
0 notes
Text
Every device online has one—but most people have no idea what it actually does. This 60-second breakdown makes it super simple. Tap in to level up your tech knowledge!
#IPAddress#InternetBasics#TechExplained#CyberSecurity#Networking101#TechTips#DigitalLiteracy#LearnTech#BeginnerTech#IPv4#IPv6#HowTheInternetWorks#TechReel#InfoReel
0 notes
Link
#DNSconfiguration#DNSmanagement#DNSrequest#DNSsettings#DNStroubleshooting#domainmapping#dynamicIP#emailserver#IPaddress#PTRrecord#PTRupdate#reverseDNS#reverseDNSlookup#reverselookup#SMTPrelay#staticIP#Tier2support#Tier3support#Verizon#Verizonbusinessaccount#Verizonbusinesssupport#VerizonFios#Verizonnetwork#Verizonsupport#Verizontechnicalsupport
0 notes
Text
Class E IP Address Space Helps GKE Manage IPv4 Depletion

Using Class E IPv4 Address space to help GKE address IPv4 depletion problems. The need for private IPv4 addresses is growing along with the amount of services and apps hosted on Google Kubernetes Engine (GKE) (RFC 1918). The RFC1918 address space is becoming harder to come by for a lot of big businesses, which makes IP address depletion a problem that affects their application scalability.
This precise address depletion problem is resolved by IPv6, which offers a large number of addresses. But not every business or application is prepared for IPv6 just yet. You may continue to expand your company by entering the IPv4 address space (240.0.0.0/4), which can handle these problems.
Class E addresses (240.0.0.0/4) are set aside for future usage, as indicated in RFC 5735 and RFC 1112, as stated in Google VPC network acceptable IPv4 ranges; nevertheless, this does not preclude you from using them in certain situations today. Google will also provide tips for organizing and using GKE clusters with Class E.
Recognizing Class E addresses
IPv4 addresses
Some typical criticisms or misunderstandings about the use of Class E addresses are as follows:
Other Google services do not function with class E addresses. This is untrue. Class E addresses are included in the acceptable address ranges for IPV4 that Google Cloud VPC offers. Furthermore, private connection techniques using Class E addresses provide access to a large number of Google controlled services.
Communicating with services outside of Google (internet/on-premises/other clouds) is limited when using Class E addresses. False. You may use NAT or IP masquerading to convert Class E addresses to public or private IPv4 addresses in order to access destinations outside of Google Cloud, since Class E addresses are not routable and are not published over the internet or outside of Google Cloud. Furthermore,
a. Nowadays, a large number of operating systems support Class E addresses, with Microsoft Windows being the prominent exception.
b. Routing the addresses for usage in private DCs is supported by several on-premises suppliers (Cisco, Juniper, Arista).
There are scale and performance restrictions on Class E addresses. This is untrue. Regarding performance, there is no difference between the addresses and other address ranges used by Google Cloud. Agents can grow to accommodate a high number of connections without sacrificing speed, even with NAT/IP Masquerade.
Therefore, you may utilize Class E addresses for private usage inside Google Cloud VPCs, for both Compute Engine instances and Kubernetes pods/services in GKE, even though they are reserved for future use, not routable over the internet, and shouldn’t be publicized over the public internet.
Advantages
Class E IP Addresses
Despite these limitations, Class E addresses provide some benefits:
Large address space: Compared to standard RFC 1918 private addresses (around 17.9 million addresses vs. about 268.4 million addresses for it), Class E addresses provide a much bigger pool of IP addresses. Organizations experiencing IP address depletion will benefit from this abundance as it will enable them to expand their services and applications without being constrained by a finite amount of address space.
Growth and scalability: It addressing’s wide reach facilitates the simple scalability of services and apps on Google Cloud and GKE. IP address restrictions do not prevent you from deploying and growing your infrastructure, which promotes innovation and development even during times of high consumption.
Effective resource utilization: By using Class E addresses to enhance your IP address allocation procedures, you may reduce the possibility of address conflicts and contribute to the efficient use of IP resources. This results in reduced expenses and more efficient operations.
Future-proofing: Although it is not supported by all operating systems, its use is anticipated to rise in response to the growing need for IP addresses. You can future-proof your infrastructure scalability to enable company development for many years to come by adopting Class E early on.
Class E IP addresses
Things to be mindful of
Even though Class E IP addresses provide many advantages, there are a few crucial things to remember:
Compatibility with operating systems: At the moment, not all operating systems enable Class E addressing. Make sure your selected operating system and tools are compatible before putting Class E into practice.
Software and hardware for networking: Check to see whether your firewalls and routers (or any other third-party virtual appliance solutions running on Google Compute Engine) are capable of handling the addresses. Make sure any programs or software that use IP addresses are updated to support it as well.
Migration and transition: To ensure there are no interruptions while switching from RFC 1918 private addresses to it, meticulous preparation and execution are needed.
How Snap implemented Class E
Network IP management is becoming more difficult due to the growing use of microservices and containerization systems such as GKE, particularly by major clients like Snap. Snap’s finite supply of RFC1918 private IPv4 addresses was rapidly depleted with hundreds of thousands of pods deployed, impeding cluster scalability and necessitating a large amount of human work to release addresses.
Originally contemplating an IPv6 migration, Snap ultimately opted to deploy dual-stack GKE nodes and GKE pods (IPv6 + Class E IPv4) due to concerns over application readiness and compatibility. In addition to preventing IP fatigue, this approach gave Snap the scale of IP addresses it required for many years to accommodate future expansion and cut down on overhead. Furthermore, this technique was in line with Snap’s long-term plan to switch to IPv6.
Fresh clusters
Requirement
Construct native VPC clusters.
Steps
Make a subnetwork with supplementary ranges for services and pods, if desired. It range (240.0.0.0/4) has CIDRs that may be used in the secondary ranges.
When creating the cluster for the pod and services CIDR ranges, use the previously generated secondary ranges. This is an example of the user-managed secondary range assignment mechanism.
Setup IP masquerading to source network address translation (SNAT) to map the IP address of the underlying node to the source network address.
Migrating clusters
Requirement
The clusters need to be native to the VPC.
Steps
It is not possible to modify the cluster’s default pod IPv4 range. For more recent node pools that support Class E ranges, you may add pod ranges.
Workloads from earlier node pools may potentially be moved to newer node pools.
IPv4 Vs IPv6
Making the switch from IPv4 to IPv6 Class E
For enterprises experiencing IP depletion, switching to dual-stack clusters with the IPv4 and IPv6 addresses now is a wise strategic step. By increasing the pool of IP addresses that are accessible, it offers instant relief and permits expansion and scalability inside Google Cloud and GKE. Furthermore, implementing dual-stack clusters is an essential first step toward a more seamless IPv6-only transition.
Read more on Govindhtech.com
#ClassE#IPAddress#GKE#IPv4#IPv6#VPCnetwork#GoogleKubernetesEngine#GKEclusters#VPC#ClassEaddresses#news#technews#technologynews#technologytrends#govindhtech
0 notes
Text
Proxiyum: The Future of Business Automation
Explore the transformative power of Proxiyum, the cutting-edge solution for automating your business tasks. From reducing manual work to improving accuracy, find out how Proxiyum is shaping the future of business automation and what it can do for your organization.

0 notes
Text
Come implementare Privacy Shield per non bloccare domini leciti

Perché il Piracy Shield non funziona e come sarebbe dovuto essere implementato. Nell’era digitale, la gestione della proprietà intellettuale e la lotta contro la pirateria online rappresentano sfide cruciali per i regolatori, le industrie creative e i fornitori di servizi internet. Il “Piracy Shield”, un’iniziativa dell’Autorità per le Garanzie nelle Comunicazioni (AGCOM), rappresenta un tentativo significativo di affrontare il problema della pirateria digitale in Italia. Questo strumento è stato ideato per identificare e bloccare l’accesso ai siti web che violano i diritti di proprietà intellettuale, sfruttando tecnologie di filtraggio degli “FQDN e degli indirizzi IP” (citando testualmente AGCOM). Nonostante le sue nobili intenzioni, il Piracy Shield ha suscitato non poche controversie e dibattiti riguardo la sua efficacia e le implicazioni per la libertà di espressione e il diritto alla privacy. In questo articolo tecnico-scientifico, si intende esplorare e discutere le ragioni per cui il Privacy Shield non ha raggiunto pienamente i suoi obiettivi, mettendo in luce le difficoltà tecniche, legali e etiche incontrate.

Sarà inoltre illustrato come, attraverso un approccio innovativo basato sulla configurazione di record CNAME, sia possibile distinguere tra servizi legittimi e illeciti associati allo stesso indirizzo IPv4. Questa dimostrazione pratica non solo evidenzierà le potenzialità di tali tecniche, ma anche come esse potrebbero essere integrate efficacemente in un framework rinnovato per la lotta alla pirateria, suggerendo modifiche e migliorie al sistema attuale del Piracy Shield. Le Content Delivery Network Le Content Delivery Networks (CDN) sono infrastrutture distribuite di server progettate per ottimizzare la consegna di contenuti web agli utenti finali. Le CDN migliorano la velocità e l’affidabilità di accesso ai dati riducendo la distanza fisica tra il server e l’utente, distribuendo il contenuto su diversi server posizionati in varie località geografiche. Funzionamento delle CDN Quando un utente accede a un sito web che utilizza una CDN, la richiesta di dati non viene inviata direttamente al server principale del sito, ma viene reindirizzata al server della CDN più vicino all’utente. Questo server “edge” contiene copie dei contenuti del sito, come file HTML, immagini, video e altri tipi di dati. Grazie a questa architettura, il tempo di caricamento delle pagine si riduce notevolmente, migliorando l’esperienza dell’utente e riducendo il carico sui server centrali. Mascheramento dell’IP reale Un effetto importante dell’uso delle CDN è il mascheramento dell’indirizzo IP pubblico reale del server di origine dei contenuti. Quando un servizio online adotta una CDN, gli indirizzi IP visibili al pubblico sono quelli dei server della rete CDN. Questo significa che l’IP percepito come fonte del servizio è in realtà quello della CDN, non del server originale. Questo ha implicazioni per la sicurezza, la privacy e la gestione del traffico, ma può anche complicare alcune operazioni di controllo e filtraggio del contenuto. Implicazioni per il filtraggio di contenuti Se un’autorità come AGCOM implementa misure per bloccare l’accesso a contenuti ritenuti illegali (come quelli piratati) mediante il filtraggio degli indirizzi IP attraverso strumenti come il Piracy Shield, si potrebbero verificare problemi significativi. Poiché un singolo indirizzo IP di una CDN può essere utilizzato per trasmettere i contenuti di numerosi servizi diversi, il blocco di quell’IP potrebbe avere l’effetto collaterale di interrompere l’accesso a servizi legittimi e non solo a quelli illegali. Questo scenario potrebbe portare a interruzioni di servizio per utenti che non sono coinvolti nella fruizione di contenuti piratati. Facciamo chiarezza con un esempio pratico Per comprendere meglio come funziona la navigazione su internet e l’interazione con una Content Delivery Network (CDN), prendiamo come esempio il processo di collegamento a un sito web, come “www.libero.it”. Questo esempio ci permetterà di osservare come, durante la navigazione, il nome di dominio inizialmente richiesto possa in realtà essere servito da un dominio completamente diverso, come “d31d9gezsyt1z8.cloudfront.net”, che appartiene a una CDN. DNS Query Il processo inizia quando l’utente digita “www.libero.it” nel browser. Il browser deve risolvere questo nome di dominio in un indirizzo IP per poter stabilire una connessione. Questo avviene tramite una richiesta DNS (Domain Name System). Il browser consulta i server DNS configurati (tipicamente forniti dal provider di servizi internet o specificati manualmente dall’utente) per ottenere l’indirizzo IP associato al nome di dominio. (Si vede evidenziata la richiesta) Ricezione della risposta DNS I server DNS eseguono la ricerca e, una volta trovato l’indirizzo IP, lo restituiscono al browser. Se il dominio è ospitato su una CDN, l’IP restituito sarà quello di uno dei server edge della CDN più vicino all’utente, non l’IP del server originale di “libero.it”. (Si vede evidenziata la risposta Apertura della connessione (Handshake) Con l’indirizzo IP in mano, il browser inizia un handshake TCP con il server al fine di stabilire una connessione affidabile. Questo include la sincronizzazione dei numeri di sequenza per garantire che i pacchetti di dati vengano inviati e ricevuti in ordine. Durante l’handhsake il client invia un segmento SYN , il server risponde con un SYN + ACK , il client termina l’handshake con un ACK. (Si vede in figura nella riga evidenziata l’inizio dell’handshake verso la CDN di libero).
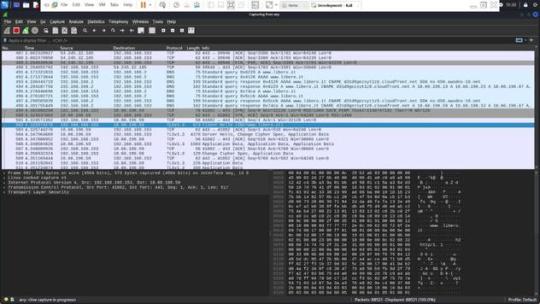
Negoziazione TLS (Transport Layer Security) Dopo aver stabilito una connessione TCP, il browser inizia una negoziazione TLS per assicurare che la comunicazione sia sicura e criptata. Questo processo inizia con l’invio del “ClientHello”, che include la versione di TLS supportata, i metodi di cifratura proposti, e altri dettagli necessari per la sicurezza.

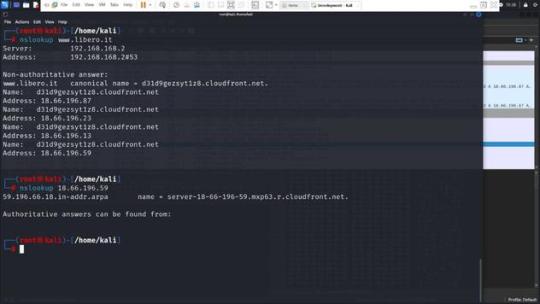
Il server risponde con un “ServerHello”, che conferma i dettagli della crittografia che sarà utilizzata, seleziona un metodo di cifratura tra quelli proposti dal client e prosegue con l’invio dei certificati, la verifica della chiave, e la conferma finale di inizio della cifratu Comunicazione sicura Una volta completata la negoziazione TLS, tutte le trasmissioni successive tra il browser e il server sono completamente criptate. Il browser può ora richiedere le risorse web da “www.libero.it”, che in realtà potrebbero essere servite dal dominio della CDN, come “d31d9gezsyt1z8.cloudfront.net”. Questo esempio mostra come, nella pratica, un sito che l’utente intende visitare possa essere effettivamente distribuito attraverso una rete CDN, rendendo il nome del dominio CDN visibile nelle comunicazioni di rete, anche se l’utente potrebbe non essere immediatamente consapevole di tale fatto. Considerazioni Questa architettura farà in modo che www.libero.it avrà una serie di IP associati all’ASN di cloudfront che vengono usati per far funzionare la CDN. Questi IP saranno associati non solo a www.libero.it ma anche a molti altri FQDN (Altre web app) che usano la CDN. Ricordiamo che questi servizi vengono distinti fra loro grazie ai record CNAME che puntano a FQDN univoci come questo: d31d9gezsyt1z8.cloudfront.net.
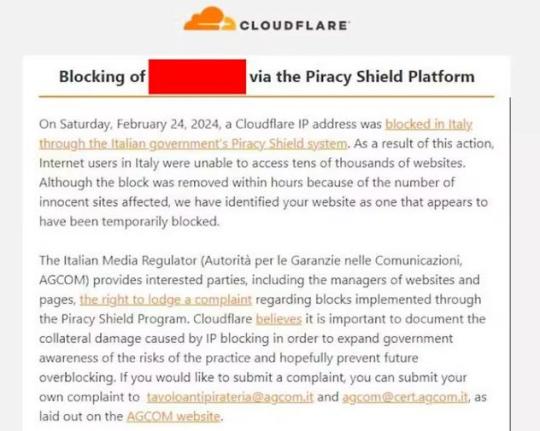
Dimostrazione del problema Con l’esempio precedente abbiamo quindi dimostrato che quando un servizio è integrato ad una CDN la corrispondenza servizio – IP non è più della cardinalità 1:1 , ma bensì N:1. Quindi se viene filtrato un indirizzo IP, N servizi vengono oscurati, pur non essendo tutti illegali. Lo abbiamo visto con l’esempio precedente in cui libero viene deliberatamente associato a diversi IP, condivisi con altri servizi della CDN cloudFront. Infatti una delle CDN che ha lamentato proprio questo problema è la nota Cloudflare che ha emesso un comunicato ad alcuni suoi clienti, esortandoli all’invio di una lettera di richiamo alla stessa AGCOM chiedendo di annullare l’ingiusto provvedimento.
Non si può quindi pensare di bloccare il traffico IP semplicemente filtrando un indirizzo IPv4/IPv6. Come si potrebbe procedere Per affrontare efficacemente le sfide poste dal filtraggio di contenuti attraverso indirizzi IP in un ambiente dove sono ampiamente utilizzate le Content Delivery Networks (CDN), è essenziale adottare metodi più sofisticati che prendano in considerazione le peculiarità tecniche delle CDN stesse. Una strategia più mirata e meno suscettibile di causare danni collaterali può essere implementata analizzando in dettaglio le proprietà di rete associate agli indirizzi IP, in particolare l’Autonomous System Number (ASN). Analisi dell’ASN Prima di procedere al blocco di un indirizzo IP sospettato di veicolare contenuti piratati, è cruciale determinare a quale sistema autonomo appartiene quel determinato IP. Se l’IP è associato all’ASN di una CDN nota, questo indica che potrebbe essere utilizzato per servire una moltitudine di clienti e servizi, molti dei quali legittimi. Il blocco diretto di tali IP potrebbe quindi interrompere l’accesso a servizi legittimi, causando interruzioni non necessarie e potenzialmente estese. Blocco basato su FQDN della CDN Invece di bloccare indiscriminatamente gli indirizzi IP, si dovrebbe valutare l’opzione di filtrare specifici Fully Qualified Domain Names (FQDN) direttamente legati a contenuti illeciti. Un metodo più mirato consiste nell’analizzare i record CNAME, che collegano un FQDN a un altro dominio, spesso usato per identificare contenuti specifici all’interno di una CDN. Il sistema attuale del Piracy Shield già applica il blocco agli FQDN e agli indirizzi IP, ma non estende questo trattamento ai FQDN univoci usati dalle CDN. Ad esempio, bloccando il dominio pubblico www.libero.it ed i suoi indirizzi IP, si impedisce anche l’accesso agli IP come 18.66.196.87, 18.66.196.23, 18.66.196.13 e 18.66.196.59. Tali indirizzi, associati a una CDN, vengono utilizzati anche da altri servizi che sarebbero ingiustamente bloccati. Soluzione proposta Quando viene rilevato che un servizio usa una CDN, la strategia corretta sarebbe quella di bloccare esclusivamente gli FQDN specifici alla CDN, come d31d9gezsyt1z8.cloudfront.net e www.libero.it, senza intervenire sugli indirizzi IP. In questo modo gli altri servizi che usano la CDN non saranno bloccati. Conclusioni Adottando queste pratiche migliorate, AGCOM e altre autorità simili potrebbero ottimizzare le loro strategie di enforcement senza suscitare controversie legate a interruzioni di servizio ingiustificate o a violazioni dei diritti alla privacy e alla libertà di espressione. Questo equilibrio tra l’efficacia del blocco e il rispetto per i diritti degli utenti è essenziale per mantenere la fiducia nel regolamento digitale e nella protezione della proprietà intellettuale nel contesto globale e interconnesso di oggi Read the full article
#AgCom#CDNcloudFront#contentdeliverynetwork#dnsquery#filtering#FQDN#indirizziIP#ipaddress#PrivacyShield
0 notes
Text
What is Proxy Extension?
1 note
·
View note
Text
youtube
0 notes
Text
IP Address Tracking Tool

Cligence offers a powerful IP Address Tracking Tool that enables precise monitoring and analysis of IP addresses for cybersecurity and investigative purposes. Designed for law enforcement and security professionals, it helps trace online activities, identify locations, and detect threats efficiently. Cligence simplifies digital investigations with reliable accuracy. For more details or a demo, contact us at 9461101915.
0 notes
Video
youtube
What is IP address and how to find it | Tech Questions
0 notes
Text
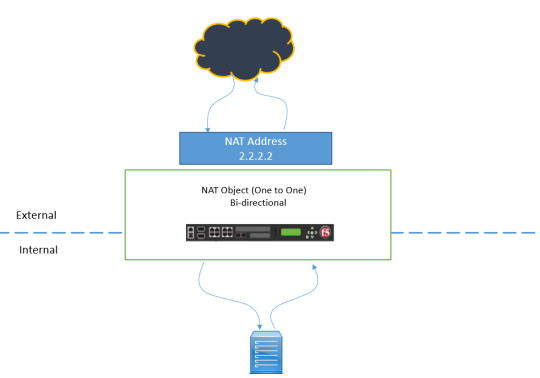
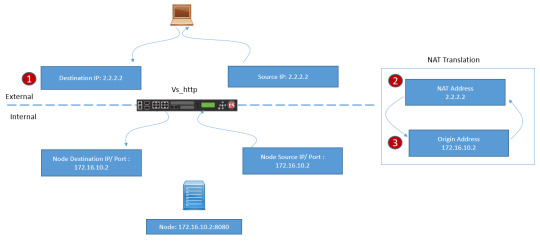
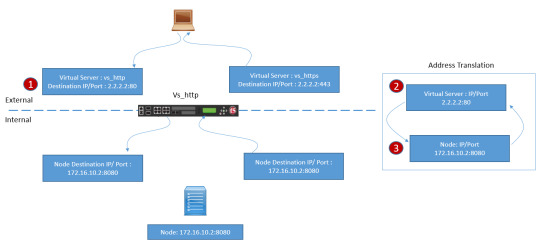
Are you ready to unravel the mysteries of Network Address Translation (NAT) and Source NAT (SNAT)? DC Lessons offers a comprehensive course designed for IT professionals, network administrators, and anyone intrigued by the world of network address manipulation. https://www.dclessons.com/nat-snat-concepts
#NAT#StaticNAT#Networking#ITTraining#DClessons#Cisco#NetworkSecurity#IPaddress#ITConcepts#RoutingAndSwitching#TechEducation#NetworkEngineering#NetworkTopology#ITCertification#CCNA
0 notes
Text
How can I find the IP address of a device connected to my Netgear router?

Have you ever wanted to learn more about IP addresses? In this article, we'll discuss what an IP address is, and how to find the IP address of a device connected to your Netgear router.
What Is An IP Address?
An IP address is a unique numerical identifier assigned to each device connected to the internet protocol for communication. It allows devices to communicate with each other and find each other on the network. Every device has a different IP address, and they are usually assigned by your ISP (internet service provider). You can think of an IP address like a phone number for your computer - it's how other devices on the internet know how to find and connect to it. You can find the IP address of any device connected to your router by logging into your router's web interface and looking at the list of connected devices. The IP address will be listed next to each device.
How to Find the IP Address Of A Device Connected To Your Router?
When it comes to finding the IP address of a device connected to your router, there are several methods you can use. Here is a list of them: Through the Router's Web Interface The easiest way to find the IP address of a device connected to your router is through the router's web interface. To identify the IP address of a device connected to your router: - Access the login page for your router. For NETGEAR routers, refer to the instructions on "How do I log in to my NETGEAR home router?" Note: If you do not have a NETGEAR router, consult your specific model's user manual or support page. - Locate the section of the router's web interface that displays connected devices. - On NETGEAR routers, navigate to the "Attached Devices" page under the "BASIC" tab. Note: The menu label may vary on other models and be called "Device Manager" or similar. - Each connected device will display information such as the device name and IP address. For further assistance, refer to your router's support page or contact NETGEAR Support. Using a Command Prompt (Windows) If you're using Windows, you can find your IP address by opening a command prompt and typing "ipconfig". Your IP address will be displayed next to the "IPv4 Address" field. Using Network Settings (MacOS/iOS) If you want to find the IP address of a device connected to your router, you can do so using the network settings on your Mac or iOS device. - Access System Preferences and select the Network option. - Select the location that corresponds to your current network setup (if you need help determining which one it is, look at the network icon in the menu bar). - Click on Advanced and then select the TCP/IP tab. - The IP address will be listed next to "Router". Using a Network Scanner A third way to find the IP address of a device connected to your router is by using a network scanner. Network scanners are software tools that scan your network and provide information about connected devices, including IP addresses. There are many different network scanners available, both paid and free. Some popular options include Fing and Advanced IP Scanner. Note: It's worth noting that some devices may have a dynamic IP address which can change over time.In conclusion, finding the IP address of a device connected to your router is a straightforward process that can be accomplished using various methods. Whether you choose to use the router's web interface, command prompt or terminal, or a network scanner, you should be able to quickly identify the IP address of the device you are trying to locate. Knowing the IP address of a device connected to your router can be helpful in a variety of situations, such as troubleshooting network issues or configuring security settings. With this knowledge, you can easily manage and maintain your home network.Reference form: https://mynetgearrouterlogin.com/find-the-ip-address-of-connected-device/ Read the full article
#mynetgearrouterlogin#IPaddress#router#network#deviceIP#networkmanagement#homenetwork#networktroubleshooting#IPconfig#networkscanner#netgear
0 notes
Text
Alpha Infolab: Your Trusted ARIN Qualified Facilitator

Alpha Infolab, a leading provider of digital solutions, is proud to announce its recent recognition as an ARIN Qualified Facilitator. This achievement underscores our commitment to providing top-tier services to our clients and our expertise in the field of Internet number resources. Don't miss out on the opportunity to streamline your Internet number resources transfer process. Contact us today to learn more about our services!
The American Registry for Internet Numbers (ARIN) is a non-profit corporation that manages the distribution of Internet number resources, including IPv4, IPv6, and Autonomous System Number (ASN) resources. The ARIN Qualified Facilitator Program is designed to assist organizations in acquiring or transferring these valuable resources.
As an ARIN Qualified Facilitator, we have undergone a rigorous review process by ARIN's experienced staff and have demonstrated our ability to streamline the transfer process with ARIN Registration Services. This status allows us to better serve organizations looking to obtain or transfer IPv4 address space or ASNs.
The ARIN Qualified Facilitator Program is particularly beneficial for organizations unsure of how to obtain needed IPv4 address space, those with unused IPv4 address space who wish to transfer it, and organizations needing guidance to navigate the complex resource transfer process.
At Alpha Infolab, we are committed to providing our clients with the best possible service. Our recognition as an ARIN Qualified Facilitator is a testament to our dedication and expertise in the field. We look forward to continuing to serve our clients with the highest level of service and professionalism.
Ready to streamline your Internet number resources transfer process? Don't wait any longer! Contact Alpha Infolab, your trusted ARIN Qualified Facilitator, today! Visit our website or contact us to learn more about our services and start your journey to more efficient Internet number resources management.
0 notes
Text
Cloud SQL Auth Proxy: Securing Your Cloud SQL Instances

Cloud SQL Auth Proxy
In this blog they will explain how to utilise the Cloud SQL Auth Proxy to create safe, encrypted data, and authorised connections to your instances. To connect to Cloud SQL from the App Engine standard environment or App Engine flexible environment, you do not need to configure SSL or use the Cloud SQL Auth Proxy.
The Cloud SQL Auth Proxy’s advantages
Without requiring authorised networks or SSL configuration, the Cloud SQL Auth Proxy is a Cloud SQL connection that offers secure access to your instances.
The following are some advantages of the Cloud SQL Auth Proxy and other Cloud SQL Connectors:
Secure connections:
TLS 1.3 with a 256-bit AES cypher is automatically used by this to encrypt traffic to and from the database. You won’t need to administer SSL certificates because they are used to validate the identities of clients and servers and are not dependent on database protocols.
Simpler authorization of connections:
IAM permissions are used by the Cloud SQL Auth Proxy to restrict who and what can connect to your Cloud SQL instances. Therefore, there is no need to supply static IP addresses because it manages authentication with Cloud SQL.
It depends on the IP connectivity that already exists; it does not offer a new way for connecting. The Cloud SQL Auth Proxy needs to be on a resource that has access to the same VPC network as the Cloud SQL instance in order to connect to it via private IP.
The operation of the Cloud SQL Auth Proxy
A local client that is operating in the local environment is required for the Cloud SQL Auth Proxy to function. Your application uses the common database protocol that your database uses to connect with the Cloud SQL Auth Proxy.
It communicates with its server-side partner process through a secure channel. One connection to the Cloud SQL instance is made for each connection made via the Cloud SQL Auth Proxy.
An application that connects to Cloud SQL Auth Proxy first determines if it can establish a connection to the target Cloud SQL instance. In the event that a connection is not established, it makes use of the Cloud SQL Admin APIs to acquire an ephemeral SSL certificate and connects to Cloud SQL using it. The expiration date of ephemeral SSL certificates is around one hour. These certificates are refreshed by Cloud SQL Auth Proxy prior to their expiration.
The only port on which the Cloud SQL Auth Proxy establishes outgoing or egress connections to your Cloud SQL instance is 3307. All egress TCP connections on port 443 must be permitted since Cloud SQL Auth Proxy uses the domain name sqladmin.googleapis.com to use APIs, which does not have a stable IP address. Make that your client computer’s outbound firewall policy permits outgoing connections to port 3307 on the IP address of your Cloud SQL instance.
Although it doesn’t offer connection pooling, it can be used in conjunction with other connection pools to boost productivity.
The connection between Cloud SQL Auth Proxy and Cloud SQL is depicted in the following diagram:
image credit to Google cloud
Use of the Cloud SQL Auth Proxy Requirements
The following conditions must be fulfilled in order for you to use the Cloud SQL Auth Proxy:
Enabling the Cloud SQL Admin API is necessary.
It is necessary to supply Google Cloud authentication credentials to this.
You need to supply a working database user account and password to this proxy.
The instance needs to be set up to use private IP or have a public IPv4 address.
It is not necessary for the public IP address to be added as an approved network address, nor does it need to be reachable from any external address.
Options for starting Cloud SQL Auth Proxy
You give the following details when you launch it:
Which Cloud SQL instances to connect to so that it can wait to receive data from your application that is sent to Cloud SQL
Where can it locate the login credentials needed to validate your application with Cloud SQL?
Which type of IP address to use, if necessary.
Whether it will listen on a TCP port or a Unix socket depends on the startup parameters you supply. It creates the socket at the specified location, which is often the /cloudsql/ directory, if it is listening on a Unix socket. The Cloud SQL Auth Proxy by default listens on localhost for TCP.
For authentication, use a service account
To authorise your connections to a Cloud SQL instance, you must authenticate as a Cloud SQL IAM identity using this Proxy.
For this purpose, the benefit of using a service account is that you may make a credential file particularly for the Cloud SQL Auth Proxy, and as long as it approach for production instances that aren’t operating on a Compute Engine instance is to use a service account
In the event that you require this to be invoked from several computers, you can replicate the credential file within a system image.
You have to make and maintain the credential file in order to use this method. The service account can only be created by users who possess the resourcemanager.projects.setIamPolicy permission, which includes project owners. You will need to get someone else to create the service account or find another way to authenticate this, if your Google Cloud user does not have this permission.
Read more on govindhtech.com
#cloudSQL#vpcnetwork#IPAddress#firewallpolicy#GoogleCloud#news#TechNews#technology#technologynews#technologytrends#govindhtech
0 notes