#IT cyber security services
Explore tagged Tumblr posts
Text
Kriptone Data Loss Protection: The Ultimate Smart Security Solution

In today’s digital world, data is more valuable than ever—it powers business growth but is also at constant risk. It can be lost or stolen through mistakes, system failures, or internal leaks. Like gold needs to be stored safely, your data needs strong protection. That’s where Kriptone Data Loss Protection (DLP) comes in—a smart, flexible solution designed to safeguard your most valuable digital assets.
What is Data Loss Protection (DLP)?
(DLP) keeps your sensitive information safe from leaks, misuse, or unauthorized access—ensuring it stays where it belongs.
Exploring the Difference Between Data Loss and Leakage
Data loss is permanent, like when a hard drive fails and erases customer records. Data leakage, however, is sneaky—it’s when sensitive info leaks through weak points like unapproved apps or human mistakes. Loss is harsh, but leakage is slow and often more harmful over time. Kriptone’s DLP technology prevents both, stopping leaks before they spread and protecting against data loss.
The Top Threats to Your Data Today
Data threats can come from everywhere—from cybercriminals to well-meaning employees. Let’s dive into the major risks that can impact your information.
External Attacks: Hackers, Malware, and Phishing
Cybercriminals are now part of organized groups using advanced tools like AI-driven malware and phishing attacks. Their goal is to steal and profit from your data. Kriptone’s DLP uses threat intelligence to detect and stop these attacks before they can steal your information.
The Business Impact of Data Loss
A single data breach can cause major damage, harming systems, reputations, and even leading to legal issues. Data loss isn’t only a technical issue; it’s a crisis that affects the entire business.
From Revenue to Reputation: The Fallout of a Breach
When data is lost, trust is shattered clients back off, investors worry, and competitors take advantage. Similarly Extra costs from legal actions, fines, and system breaks make the problem worse. Kriptone helps businesses avoid this by providing constant, smart protection that’s always on and defending.
Key Features of a Strong DLP Strategy
Not all DLP tools are the same. A strong defence needs to be smart, proactive, and adaptable—just like the threats it’s meant to stop.
Real-Time Monitoring and Alerts: Eyes Everywhere
Kriptone monitors data 24/7 across endpoints, networks, and the cloud. If something unusual happens, it quickly locks down files, alerts security teams, and tracks the breach.
Types of DLP Solutions Explained
Choosing the right DLP depends on where your data is stored, how it moves, and who needs access. Kriptone offers solutions designed for today’s flexible, decentralized workspaces.
Endpoint DLP: Securing Devices at the Edge
Endpoint DLP protects data on employee devices. Kriptone’s solution blocks unauthorized copying, printing, or transferring of data, whether the device is online or offline.
The Future of Data Loss Protection
Cyber threats move fast, and DLP must keep up. Kriptone is shaping the future of data protection with Smart Data Security automation and predictive analytics.
AI and Machine Learning in Next-Gen DLP
Kriptone uses Smart Data Security AI to stop threats before they start. However, It learns from past events, adapts to user behavior, and spots unusual activity in real-time, creating a DLP system that’s not just reactive, but smart and adaptive.
Conclusion
In conclusion,Data loss will happen eventually, but proactive defense can limit the damage. Kriptone Data Loss Protection isn’t just a tool—it’s a promise to defend your valuable data with intelligence and precision. Security should be relentless, not reactive. Whether you’re a global enterprise or a startup, Kriptone helps you protect your most critical asset before it’s too late. In addition, Today, protecting your data smartly is essential, not a choice.
#it security services#data loss prevention solutions#endpoint security#It cyber security services#data loss protection
0 notes
Text
EXPRESS VPN IS A SCAM
I signed up for Express VPN a few months back because I heard it was better than Nord (it's not, much slower, but that's another issue) and ended up canceling after my first month. Today, I got an email from them saying that my automatic subscription renewal had been turned back on and that they charged me $28 dollars. I thought the email might have been a phishing scam, so I went to the Express VPN site and check, and what do you know, my subscription that I canceled months ago had been turned back on and now expires in one month. I canceled it, again, and contacted customer support. Here's a screenshot of that conversation

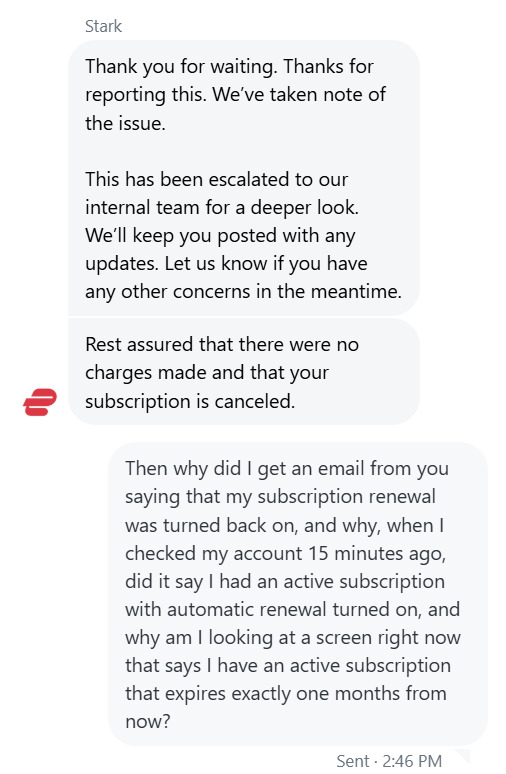
Now what I want to point out here is that this chat has been edited by Express VPN. At first, there was nothing between "Please bear with me while I quickly review your account" and "Rest assured there were no charges made and that your subscription is canceled". When I asked my follow up questions, suddenly the part about "Thank you for waiting, this has been escalated to our internal team..." popped into existence, and the chat went dead. As I was typing this, I began typing a follow up question about the "internal team" but before I could even finish typing it up, I got another message saying that the internal team would be looking into the issue. They also never acknowledged that I wanted my credit card info deleted.
So far, I have no support ticket for this and no emails acknowledging that my complaint has been forwarded to a different support team. I searched around t he internet and found this reddit thread where other people have been having this same issue going back 4 years.
So yeah, Express VPN is a scam. It saves your credit card information and then randomly reactivates your subscription after you cancel it and charges you. Don't use Express VPN.
93 notes
·
View notes
Text
I don't know how accurate their information about Facebook messenger is, but Instagram (Facebook owned) had a college kid arrested for PRIVATE messages over a joke...
youtube
#Youtube#tiktok#facebook#meta#Instagram#invasion of privacy#facebook messenger#terms of service#cybersecurity#cyber security#cyber safety#tiktok ban
20 notes
·
View notes
Text
IRS Lawyer Ousted as Elon Musk’s DOGE Plans Even More Cuts | The New Republic
#department of government efficiency#elon musk#donald trump#trump administration#irscompliance#irs audit#irs#internal revenue service#federal government#data privacy#data protection#cybersecurity#cyber security#civil rights#social justice#us politics
14 notes
·
View notes
Text


Feeling lonely 😥,wanna have fun 🥵❤️
#sexy hunk#self love#truck rental service#purse the money truck#lumber the wood truck#killerwatt the security truck#truckdrivers#cyber truck#old truck#joule the dynamite truck#fire truck#porter the coal truck#hornyposting#hornythoughts
8 notes
·
View notes
Text
AI & Cybersecurity: Navigating the Future Safely & Ethically

The integration of Ai is revolutionizing cybersecurity, empowering organizations with unprecedented capabilities to detect, predict, and respond to threats at a scale. From advanced anomaly detection to automated incident response, AI is an indispensable tool in strengthening our digital defenses. We embrace the transformative power of AI. It offers immense potential to enhance threat hunting, streamline operations, and elevate our collective security posture. However, with great power comes great responsibility. The rapid adoption of AI also introduces new complexities and potential risks that demand a proactive, security-first approach: How to Be Safe in the AI-Driven Cyber Landscape: Secure AI Development & Deployment: Treat AI models and their underlying data pipelines as critical assets. Implement robust security measures from the initial design phase through deployment, ensuring secure coding practices, vulnerability management, and secure configurations. Data Privacy & Governance: AI systems are data-hungry. Establish strict data privacy protocols, anonymization techniques, and clear governance frameworks to protect sensitive information used for training and operation. Continuous Monitoring & Auditing: AI models can evolve and introduce unforeseen vulnerabilities or biases. Implement continuous monitoring, regular audits, and validation processes to ensure AI systems are functioning as intended and not creating new attack surfaces. Human Oversight & Intervention: AI is a powerful assistant, not a replacement. Maintain strong human oversight in decision-making processes, ensuring that human experts can review, validate, and intervene, when necessary, especially in critical security operations. Building an Ethical Foundation for AI in Cybersecurity: Beyond technical safeguards, an ethical framework is paramount. We believe in an AI Code of Conduct that prioritizes: Fairness: Ensuring AI systems do not perpetuate or amplify biases that could unfairly target or disadvantage individuals or groups. Transparency: Striving for explainable AI where possible, so that security decisions driven by AI can be understood and audited. Accountability: Establishing clear lines of responsibility for the performance and impact of AI systems, ensuring human accountability for AI-driven outcomes. Beneficial Use: Committing to using AI solely for defensive, protective purposes, and actively preventing its misuse of malicious activities. The future of cybersecurity is intrinsically linked to AI. By approaching its integration with diligence, a commitment to security, and a strong ethical compass, we can harness its full potential while safeguarding our digital world. What are your thoughts on building secure and ethical AI in cybersecurity? Share your perspective! Read More: https://centurygroup.net/the-evolving-threat-of-ai-in-the-public-housing-sector-how-to-protect-your-organization/
#AI #Cybersecurity #AIethics #SecureAI #RiskManagement #Innovation #FutureOfTech #CenturySolutionsGroup
3 notes
·
View notes
Text
Building Digital Trust: Kirill Firsov on Cybersecurity
From the UAE, Kirill Firsov leads FearsOff with a mission: stop cyber threats and secure digital finance. Hear how he safeguards crypto platforms and creates resilient defenses in a fast-changing digital world.
2 notes
·
View notes
Text


We follow our Define, Build, Run framework to execute flawlessly. From deep listening and 360° planning, to building with agile development and clean code, we ensure performance, security and return on investment through 24/7 monitoring and SLA-backed delivery.
Visit our website to learn more! https://www.algoworks.com/services/
#digital transformation#agile development#clean code#software engineering#cyber security#enterprise solutions#tech innovation#cloud services#innovations#technology#leadership#business excellence
2 notes
·
View notes
Text
🛡️ Cybersecurity and Fraud Prevention in Finance: How to Protect Your Financial Systems in 2025
In today’s digital-first financial world, cybersecurity and fraud prevention in finance are more critical than ever. With the rise of online banking, mobile payments, and digital assets, financial institutions face increasingly sophisticated cyber threats and fraud tactics.

🔍 Why Cybersecurity Is Crucial in the Finance Industry
The financial sector is one of the most targeted industries by cybercriminals due to its vast access to sensitive personal data and high-value transactions. From phishing and ransomware to account takeover and insider threats, the risk landscape continues to evolve.
Google Keyword: financial cyber threats
💣 The Cost of Poor Financial Cybersecurity
Average cost of a financial data breach: $5.9 million
70% of consumers will switch banks or services after a breach
Identity theft and digital fraud rates are up 34% YoY
Trending Search Term: banking data breaches 2025
✅ Top Strategies for Cybersecurity and Fraud Prevention in Finance
1. Adopt Multi-Layered Security Protocols
Layered security (also called “defense in depth”) uses a combination of firewalls, encryption, anti-virus software, and secure authentication to prevent unauthorized access.
Related Term: secure financial transactions
2. Leverage AI and Machine Learning for Fraud Detection
Artificial intelligence plays a key role in identifying unusual patterns and suspicious behavior in real-time. AI-powered fraud detection systems can:
Flag fraudulent transactions instantly
Analyze thousands of data points in seconds
Continuously learn and adapt to new fraud tactics
Keyword: AI in cybersecurity
3. Implement Real-Time Transaction Monitoring
Real-time monitoring tools allow institutions to track and respond to threats instantly, reducing loss and minimizing damage.
Search Intent: fraud detection systems for financial services
4. Enhance Customer Authentication Protocols
Using multi-factor authentication (MFA), biometric verification, and one-time passwords (OTPs) helps protect accounts from unauthorized access.
Search Trigger: how to protect financial data from hackers
5. Train Employees and Clients on Cyber Hygiene
Human error remains one of the top causes of breaches. Train staff and customers on:
Recognizing phishing scams
Using secure passwords
Avoiding suspicious links and public Wi-Fi
Keyword Phrase: digital financial fraud prevention tips
🔐 Top Tools and Technologies for Financial Cybersecurity in 2025
Darktrace & Vectra AI: Behavioral threat detection
Splunk & IBM QRadar: Security Information and Event Management (SIEM)
Okta & Duo: Identity and access management
ThreatMetrix: Real-time fraud analytics
📉 Common Types of Financial Cyber Threats
Phishing Attacks
Credential Stuffing
Account Takeovers
Ransomware Attacks
Insider Threats
Synthetic Identity Fraud
Search Phrase: types of financial cyber fraud
🧠 Real-World Example
In 2024, a regional credit union prevented over $2 million in fraud losses using AI-based transaction monitoring and customer biometrics. This proactive cybersecurity investment boosted customer confidence and reduced fraud-related downtime by 75%.
🚀 The Future of Cybersecurity in Finance
In 2025 and beyond, expect to see:
Widespread use of zero-trust security models
Enhanced biometric authentication
Increased use of blockchain for transaction verification
AI-powered fraud prevention as the industry standard
Keyword Used: future of cybersecurity in banking
Need Personal Or Business Funding? Prestige Business Financial Services LLC offer over 30 Personal and Business Funding options to include good and bad credit options. Get Personal Loans up to $100K or 0% Business Lines of Credit Up To $250K. Also credit repair and passive income programs.
Book A Free Consult And We Can Help - https://prestigebusinessfinancialservices.com
Email - [email protected]
📌 Final Takeaway
As digital transactions continue to grow, so does the threat landscape. Prioritizing cybersecurity and fraud prevention in finance is no longer optional—it’s essential.
Businesses and institutions that invest in AI-driven security tools, real-time monitoring, and fraud prevention protocols will not only protect their assets but also build long-term customer trust and compliance.
Need Personal Or Business Funding? Prestige Business Financial Services LLC offer over 30 Personal and Business Funding options to include good and bad credit options. Get Personal Loans up to $100K or 0% Business Lines of Credit Up To $250K. Also credit repair and passive income programs.
Book A Free Consult And We Can Help - https://prestigebusinessfinancialservices.com
Email - [email protected]
Learn More!!
Prestige Business Financial Services LLC
"Your One Stop Shop To All Your Personal And Business Funding Needs"
Website- https://prestigebusinessfinancialservices.com
Email - [email protected]
Phone- 1-800-622-0453
#financial cyber threats#banking data breaches 2025#secure financial transactions#AI in cybersecurity#fraud detection systems for financial services#how to protect financial data from hackers
2 notes
·
View notes
Text
Need dependable Vaughan IT support? MYDWARE IT Solutions Inc. delivers innovative IT solutions, from managed services to cybersecurity. Based at 400 Applewood Crescent, 100, Vaughan, ON, L4K 0C3, we help businesses improve efficiency, security, and performance. Trust us for proactive IT strategies that keep your technology running smoothly.
2 notes
·
View notes
Text

Best Employee Monitoring Solution | Kriptone | Kntrol
#best employee time tracking software#Real-time monitoring software#it security services company#Data loss prevention solutions#Endpoint security#IT cyber security services#Data loss protection#Web Tracking
1 note
·
View note
Text
What Is Website Hosting and Why Does It Matter for Your Website?

Introduction
There is always a host when you attend a party. The host is usually the one who chooses the site so that everyone may attend. Consider your website's host like the host of a party when it comes to website hosting. Like a party host, your web host gives you a place to put your website so everyone on the internet can enjoy it. In this guide, we’ll go over the fundamentals of website hosting, explore a few different types of web hosting, and explain why choosing the appropriate provider is essential for your organization and your website development company.
What is website hosting?
As previously mentioned, website hosting allows your website to be accessible online. You can have the most beautiful website in the world, but without a host, you're simply a data collector with nowhere to go. When you pay a hosting company to host your website, you’re paying for server space. The quantity of space and pricing may vary depending on your choice. Web hosting refers to the service that enables individuals and organizations to make their websites accessible via the internet. All of the files, text, images, and code needed to build a website must be stored on a server that’s online 24/7. This server is provided by a web development services company or a dedicated website hosting business working with website developers to keep your site live and available.
What are the different types of web hosting?
1. Website builder
Website builders are online tools or platforms that enable individuals or businesses to create websites without needing advanced technical knowledge or coding skills. These platforms offer a user-friendly interface and a range of customizable templates and features, allowing users to design and build their websites through a visual interface. Wix, Squarespace, and WordPress are popular website builders among small businesses and bloggers. Additionally, website builders empower users to instantly edit their sites without any coding knowledge, making them an excellent tool for beginners and a great resource for website developers looking to create quick prototypes or manage projects efficiently.
2. Dedicated server
This type of hosting involves having a whole physical server devoted to your website alone. Maximum resource, control, and customization are available with this option. It's entirely yours with a dedicated server. You don't have to share any space with other websites. You have the entire server to yourself. You also have complete control over the server. You should consider a dedicated server if your website has more than 100,000 monthly visitors. However, if you run a small business on a tight budget and your website has fewer than 100,000 monthly visitors, this is probably not your server type.
3. Shared hosting
One of the most affordable solutions is shared hosting. On a single server, resources are shared by several websites. Small to medium-sized websites with modest traffic can use it. You share a server with other websites when you use shared hosting. So, if your website doesn't get much traffic, this choice can be a good fit for you. The disadvantage is that if one website breaks the server, you're stuck with it. And if you weren't the one who broke it. It will slow down your site.
4. A virtual private server
A virtual private server, or VPS, is shared with other websites in the same way that even a shared host is. On the other hand, the server is divided into virtual servers for each site. So, despite sharing a physical space with other sites, each has its small enclave. VPS hosting provides a midway option between dedicated and shared hosting. It creates distinct virtual servers on a single physical server by utilizing virtualization technologies. With its own resources, each VPS runs separately, giving it greater autonomy and scalability.
5. Cloud Hosting
Cloud hosting hosts websites on a number of networked servers. Because resources are sourced from a network of servers, it provides scalability, flexibility, and dependability. It works well for websites that need to scale or deal with varying visitor levels, making it a valuable option for website developers looking to support dynamic traffic demands.
6. Reseller Hosting
This type of hosting enables people to buy hosting resources and then resell them to other people. It is appropriate for business owners who want to include hosting in their list of services.
Choosing the right web hosting provider is crucial for your company's success. Making the wrong decision might be detrimental in the long term. Opting for the lowest-priced option may save you money initially but could result in a slower site and fewer visitors over time. Today’s users have high expectations for site speed; if your site takes over three seconds to load, many visitors will abandon it. When users leave, it signals a poor user experience or that your web development company hasn't met their needs. Even if your site has all the answers, a slow load time will impact your search engine results. The farther you are from the top of search results, the less traffic you will receive.
To ensure your website performs at its best, research and determine your company’s needs before selecting a web hosting service. If you need support with website design websites and hosting maintenance, don’t hesitate to contact our team at Xerxes. We’d be delighted to assist you with your web design and hosting requirements so you can begin generating revenue for your clients.
Conclusion
Each type of hosting has its own advantages and is suited to different needs. Factors like website traffic, resource requirements, scalability, technical expertise, and budget influence the choice of hosting type for a particular website. So, research and determine what your company needs before paying for web hosting services. Therefore, don’t hesitate to contact our team at Xerxes for Web Design and Development Services in Ireland if you need help maintaining your website. We'd be delighted to assist you with your web design and hosting requirements so you can begin generating revenue for your clients.
#web design#website development#artificial intelligence#web service#digital marketing#cyber security#branding#app development#software development#ai#webhosting#web developers#website#domainname#web hosting#vps hosting
3 notes
·
View notes
Text
Comprehensive IT Security Services: Why You Need a Trusted IT Security Company
In today’s rapidly evolving digital landscape, securing your business’s data and IT infrastructure is more important than ever. With cyber threats growing more sophisticated, partnering with a professional IT security services company is essential for protecting your business. This article explores the key services provided by an IT security company, why businesses need them, and how a reliable provider like Gronteq can safeguard your organization from cyber risks.

Comprehensive IT Security Services: Why You Need a Trusted IT Security Company
As businesses become more reliant on digital tools and systems, the threat of cyberattacks has grown significantly. Whether you’re a small startup or a large corporation, protecting your sensitive data and IT infrastructure is no longer optional—it’s a necessity. This is where a professional IT security services company comes in. Their role is to safeguard your business from cyber threats, protect your data, and ensure your systems are running smoothly and securely.
In this article, we will discuss the various IT security services offered by reputable providers, why businesses need these services, and how partnering with a trusted IT security company like Gronteq can help you maintain a secure and resilient digital environment.
1. Understanding the Importance of IT Security
The growing frequency and sophistication of cyber threats are major concerns for businesses worldwide. Hackers, cybercriminals, and malicious insiders are always on the lookout for vulnerabilities in your IT infrastructure. From phishing attacks and data breaches to ransomware and DDoS attacks, the risks are constantly evolving.
Without the right IT security services, businesses risk losing valuable data, experiencing system downtime, and suffering reputational damage. Moreover, data protection regulations, such as GDPR and HIPAA, require businesses to implement robust security measures to avoid penalties and fines.
This is where an experienced IT security company can help. By working with a trusted provider, businesses can implement proactive security strategies that prevent attacks before they occur, ensuring a safe, compliant, and resilient online environment.
2. Key IT Security Services Offered by Companies
The scope of IT security services provided by security companies varies, but some common services include:
a. Network Security
Network security involves implementing measures to protect your internal network from unauthorized access, attacks, and data breaches. This includes firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), and secure VPNs. With strong network security, your business can defend against external and internal threats.
b. Data Protection and Encryption
Protecting sensitive data is critical to prevent unauthorized access or leaks. IT security agencies provide encryption services to ensure that data is stored and transmitted securely. By implementing data loss prevention (DLP) tools, businesses can safeguard intellectual property, customer information, and financial data from cybercriminals.
c. Vulnerability Management
Vulnerability management involves identifying and addressing weaknesses in your systems before they can be exploited. This includes regular security assessments, penetration testing, and patch management. A thorough vulnerability management program helps keep your business ahead of potential threats.
d. Endpoint Security
With more employees working remotely, endpoint security has become a top priority. This includes securing devices like laptops, smartphones, and tablets that access your company’s network. Endpoint security services protect these devices from malware, phishing attacks, and unauthorized access, ensuring the integrity of your entire IT infrastructure.
e. Incident Response and Disaster Recovery
In the event of a cyberattack or data breach, having a well-defined incident response plan is essential. IT security services companies offer incident response and disaster recovery services to help businesses quickly recover from cyberattacks. This includes identifying the source of the breach, mitigating damage, and restoring normal operations.
f. Managed Security Services
For businesses that lack an in-house security team, managed security services (MSS) are an excellent solution. These services provide 24/7 monitoring, threat intelligence, and proactive response to security incidents. MSS ensures continuous protection for your business without the need for an internal team.
3. Why Your Business Needs IT Security Services
The question remains: why is it so critical for your business to partner with a reliable IT security company? Here are the main reasons:
a. Proactive Threat Prevention
A trusted IT security services company works proactively to protect your business. By continuously monitoring your systems, implementing security protocols, and conducting regular security audits, a professional provider helps to prevent potential attacks before they happen.
b. Protecting Business Reputation
A cyberattack can lead to loss of trust from customers, partners, and stakeholders. With IT security services, your company can protect its reputation and avoid the costly consequences of a data breach.
c. Legal and Regulatory Compliance
Cybersecurity isn’t just about protecting your data—it’s also about complying with industry regulations. An IT security company helps ensure that your business complies with relevant laws like GDPR, HIPAA, and PCI-DSS, avoiding fines and penalties.
d. Cost Savings in the Long Run
While the upfront costs of IT security services may seem significant, they can actually save your business money in the long run. By preventing attacks, reducing downtime, and avoiding the cost of data breaches, investing in security is a smart financial decision.
e. Expertise and Knowledge
Cybersecurity is a complex field that requires specialized knowledge and expertise. A reputable IT security company brings in-depth understanding of the latest threats, tools, and strategies to ensure your business is always protected.
4. How Gronteq Can Help Protect Your Business
At Gronteq, we specialize in providing comprehensive IT security services to businesses of all sizes. Our team of cybersecurity professionals is dedicated to safeguarding your business from cyber threats, ensuring compliance with regulations, and helping you maintain a secure and resilient IT environment.
We offer customized IT security solutions, including network security, data protection, vulnerability management, endpoint security, and disaster recovery. With our proactive approach to cybersecurity and 24/7 monitoring, we ensure your business is always one step ahead of potential threats.
5. Contact Gronteq for Your IT Security Needs
If you’re ready to take your business’s security to the next level, Gronteq is here to help. Our IT security experts are ready to provide tailored solutions that meet your unique needs. Contact us today to learn more about how we can protect your business from cyber threats and ensure your IT systems are secure, compliant, and optimized for success.
Conclusion The digital landscape is constantly evolving, and so are the risks that come with it. Partnering with a professional IT security services company like Gronteq ensures your business is well-protected, compliant, and prepared for any challenges that arise. From proactive threat prevention to disaster recovery, our team provides end-to-end security solutions to keep your business safe.
Contact Gronteq today to learn how our IT security services can protect your organization and give you peace of mind knowing your business is secure.
#IT security#cybersecurity#IT services#data protection#network security#IT security company#IT consulting#digital security#cyber threats#business security
2 notes
·
View notes
Text
Try this free password generator!
3 notes
·
View notes
Text
Shield Your Digital World: The Ultimate Guide to VPN Security with NordVPN
#vpn#best vpn#vpn service#free vpn#clone vpn#cyberattack#antivirus#cyber security#sql#software#vps hosting#vps server in saudi arabia#buy windows vps#vps#vps34 in1#dedicated server#pcs#printer#material#security
2 notes
·
View notes
Text

TekReach Solutions is an authorized provider of Digital Solutions, based in the vibrant business hub of Dubai, UAE. With a focus on Creativity and Innovation, we provide a broad range of Digital Marketing Services and IT Solutions. We are committed to supporting businesses in navigating the evolving digital landscape and achieving their objectives through leveraging innovating and practical solutions.
#branding services#cloud storage#cyber security services#digital marketing#e commerce development#e commerce services#e commerce solutions#branding#cyber security solutions#cyber security#digital marketing services#seo services#digital marketing company#ppc services#search engine marketing#social media marketing#website development#website development services#software development#mobile application development
2 notes
·
View notes