#IT security services
Explore tagged Tumblr posts
Text
Kriptone Data Loss Protection: The Ultimate Smart Security Solution

In today’s digital world, data is more valuable than ever—it powers business growth but is also at constant risk. It can be lost or stolen through mistakes, system failures, or internal leaks. Like gold needs to be stored safely, your data needs strong protection. That’s where Kriptone Data Loss Protection (DLP) comes in—a smart, flexible solution designed to safeguard your most valuable digital assets.
What is Data Loss Protection (DLP)?
(DLP) keeps your sensitive information safe from leaks, misuse, or unauthorized access—ensuring it stays where it belongs.
Exploring the Difference Between Data Loss and Leakage
Data loss is permanent, like when a hard drive fails and erases customer records. Data leakage, however, is sneaky—it’s when sensitive info leaks through weak points like unapproved apps or human mistakes. Loss is harsh, but leakage is slow and often more harmful over time. Kriptone’s DLP technology prevents both, stopping leaks before they spread and protecting against data loss.
The Top Threats to Your Data Today
Data threats can come from everywhere—from cybercriminals to well-meaning employees. Let’s dive into the major risks that can impact your information.
External Attacks: Hackers, Malware, and Phishing
Cybercriminals are now part of organized groups using advanced tools like AI-driven malware and phishing attacks. Their goal is to steal and profit from your data. Kriptone’s DLP uses threat intelligence to detect and stop these attacks before they can steal your information.
The Business Impact of Data Loss
A single data breach can cause major damage, harming systems, reputations, and even leading to legal issues. Data loss isn’t only a technical issue; it’s a crisis that affects the entire business.
From Revenue to Reputation: The Fallout of a Breach
When data is lost, trust is shattered clients back off, investors worry, and competitors take advantage. Similarly Extra costs from legal actions, fines, and system breaks make the problem worse. Kriptone helps businesses avoid this by providing constant, smart protection that’s always on and defending.
Key Features of a Strong DLP Strategy
Not all DLP tools are the same. A strong defence needs to be smart, proactive, and adaptable—just like the threats it’s meant to stop.
Real-Time Monitoring and Alerts: Eyes Everywhere
Kriptone monitors data 24/7 across endpoints, networks, and the cloud. If something unusual happens, it quickly locks down files, alerts security teams, and tracks the breach.
Types of DLP Solutions Explained
Choosing the right DLP depends on where your data is stored, how it moves, and who needs access. Kriptone offers solutions designed for today’s flexible, decentralized workspaces.
Endpoint DLP: Securing Devices at the Edge
Endpoint DLP protects data on employee devices. Kriptone’s solution blocks unauthorized copying, printing, or transferring of data, whether the device is online or offline.
The Future of Data Loss Protection
Cyber threats move fast, and DLP must keep up. Kriptone is shaping the future of data protection with Smart Data Security automation and predictive analytics.
AI and Machine Learning in Next-Gen DLP
Kriptone uses Smart Data Security AI to stop threats before they start. However, It learns from past events, adapts to user behavior, and spots unusual activity in real-time, creating a DLP system that’s not just reactive, but smart and adaptive.
Conclusion
In conclusion,Data loss will happen eventually, but proactive defense can limit the damage. Kriptone Data Loss Protection isn’t just a tool—it’s a promise to defend your valuable data with intelligence and precision. Security should be relentless, not reactive. Whether you’re a global enterprise or a startup, Kriptone helps you protect your most critical asset before it’s too late. In addition, Today, protecting your data smartly is essential, not a choice.
#it security services#data loss prevention solutions#endpoint security#It cyber security services#data loss protection
0 notes
Text
From Reactive to Proactive: IT Security Audits That Prevent Breaches

In today’s digital-first world, cyber threats are growing more sophisticated—and more damaging. For many organizations, the common approach to security has been reactive: waiting for an incident to happen, then scrambling to contain it. But this strategy is not only risky—it’s expensive and reputationally damaging. The smarter, safer path forward? Adopting a proactive IT security audit strategy that identifies vulnerabilities before they become breaches.
This article explores how proactive IT security audits work, why they’re essential for modern businesses, and how they help organizations transition from crisis management to risk prevention.
Understanding IT Security Audits
An IT security audit is a comprehensive assessment of your organization's information systems, policies, and controls. It helps uncover potential vulnerabilities, verify compliance with industry standards (like ISO 27001, NIST, or GDPR), and assess how effectively your security protocols protect against threats.
There are two primary types of audits:
Internal Security Audits: Conducted by an in-house team or internal IT department.
External Security Audits: Performed by third-party cybersecurity experts for an unbiased evaluation.
Whether internal or external, the goal remains the same: to detect and fix weaknesses before they are exploited by attackers.
Reactive vs. Proactive Security: What’s the Difference?
Reactive security is about responding to incidents—after damage has been done. It often involves patching systems post-breach, cleaning up malware, and dealing with legal, financial, or customer fallout.
Proactive security, on the other hand, is focused on anticipating and preventing threats before they materialize. This approach includes continuous monitoring, risk assessments, penetration testing, and most importantly—routine IT security audits.
Why Proactive Security Audits Matter
Prevent Costly Breaches
The average cost of a data breach in 2024 was over $4.5 million globally, according to IBM. Proactive audits help identify weak points—like outdated firewalls, unpatched software, or overly permissive user access—before hackers can exploit them.
Strengthen Regulatory Compliance
Regulatory bodies require businesses to follow strict data protection guidelines. Proactive security audits ensure you’re staying compliant with:
HIPAA (for healthcare)
GDPR (for European customers)
PCI DSS (for payment data)
ISO 27001 (international security standards)
Protect Brand Reputation
A single breach can erode years of customer trust. When you show that you prioritize security through routine audits, customers and partners feel more confident doing business with you.
Reduce Downtime
Identifying and fixing vulnerabilities in advance means fewer security incidents and less downtime, which translates into better business continuity and higher productivity.
Key Elements of a Proactive Security Audit
To be effective, a proactive IT security audit should include the following components:
1. Asset Inventory and Risk Identification
Auditors begin by cataloging hardware, software, databases, user accounts, cloud resources, and more. They assess which systems are mission-critical and what types of data they handle.
2. Vulnerability Assessment
Using both manual inspection and automated tools, auditors scan for known vulnerabilities, misconfigurations, and security gaps. This includes:
Missing patches
Weak passwords
Open ports
Outdated software
Poor access control
3. Penetration Testing
Often conducted alongside the audit, penetration testing simulates real-world cyberattacks to test how well your systems hold up against threats. This can include phishing simulations, brute-force attacks, or attempts to breach firewalls.
4. Policy & Procedure Review
Auditors evaluate whether your IT policies (e.g., access control, remote work, backup) are clearly defined, updated, and enforced. Are employees trained in cybersecurity? Are there procedures for incident response?
5. Compliance Checks
Your systems are measured against relevant regulations and standards. Any gaps in compliance are flagged for remediation.
6. Detailed Reporting and Recommendations
Finally, a comprehensive audit report is created, outlining:
Security issues discovered
Risk levels
Recommendations to fix or mitigate issues
A roadmap for future improvements
How Proactive Audits Fit into an Ongoing Security Strategy
A one-time audit isn’t enough. Cybersecurity threats evolve daily, and so must your defenses. Organizations should adopt a continuous audit and improvement cycle, which includes:
Annual Full Security Audits
Quarterly Mini-Audits or Vulnerability Scans
Monthly Patch Reviews and Updates
Routine User Access Reviews
Regular Security Awareness Training
This cyclical approach helps organizations stay ahead of emerging threats and ensures security stays aligned with growth and operational changes.
Common Security Gaps Found in Audits (and How to Fix Them)
1. Unpatched Software
Outdated operating systems or applications are open invitations for attackers.
✅ Fix: Automate patch management and monitor software versions regularly.
2. Poor Password Practices
Weak or reused passwords are often the weakest link.
✅ Fix: Enforce strong password policies and use multi-factor authentication (MFA).
3. Overly Broad Access Permissions
Users often have more access than they need.
✅ Fix: Apply the principle of least privilege and audit access controls frequently.
4. No Incident Response Plan
Many companies lack a documented, practiced plan for dealing with security incidents.
✅ Fix: Create and test an incident response plan covering detection, containment, and recovery.
5. Shadow IT
Employees use unsanctioned apps or devices for work, creating hidden security gaps.
✅ Fix: Deploy endpoint monitoring tools and provide approved alternatives.
Choosing the Right Partner for Security Audits
While some businesses conduct audits internally, partnering with a third-party cybersecurity firm adds credibility, expertise, and objectivity. Here’s what to look for:
Certifications: Look for auditors with credentials like CISA, CEH, or CISSP.
Industry Experience: Choose a firm that understands your industry’s security and compliance needs.
Clear Reporting: Ensure they offer actionable insights, not just technical jargon.
Ongoing Support: Look for partners who don’t just audit but help implement solutions too.
Final Thoughts: Prevention Is Better Than Cure
The cost of recovering from a breach goes far beyond money. Downtime, reputation loss, legal trouble, and lost business can cripple even well-established organizations. In contrast, a proactive security audit is a low-cost, high-value investment in your company’s future.
By shifting your mindset from “How do we respond to an attack?” to “How do we prevent one from happening?”, you create a culture of cybersecurity resilience—one audit at a time.
Key Takeaways
IT security audits are essential for identifying and fixing vulnerabilities.
Reactive security is outdated; proactive audits help prevent breaches before they happen.
Proactive audits include risk assessments, pen testing, compliance checks, and more.
Make audits a regular part of your cybersecurity strategy.
Partner with experienced security professionals for the best results.
Don’t wait for the next breach. Audit proactively—protect continuously.
#it security#it security audit#it security consulting#it security services#it security services company#it security auditing
0 notes
Text
IT Security Services In Sydney | Geek Seal

Ensuring robust cybersecurity is important for businesses, and IT Security Services in Sydney provide comprehensive protection against evolving cyber threats. These services include network security, data encryption, firewall setup, and threat monitoring to safeguard sensitive information. Expert teams offer risk assessments, vulnerability testing, and compliance with specialized solutions to Sydney regulations. With cutting-edge technology and proactive strategies, companies can prevent cyberattacks, data breaches, and unauthorized access. Investing in IT Security Services in Sydney helps businesses maintain operational continuity, customer trust, and regulatory compliance in an increasingly digital landscape.
0 notes
Text
In today’s rapidly evolving digital landscape, businesses face numerous cybersecurity threats. Ensuring your company’s data and systems are secure is not just a necessity but a critical aspect of maintaining operational integrity and customer trust. By leveraging IT services in Virginia, businesses can gain access to advanced security measures that protect sensitive information from cyber threats, data breaches, and other vulnerabilities. These IT services offer comprehensive solutions that include network monitoring, threat detection, and incident response to ensure your systems remain secure at all times.
0 notes
Text
Protect Your Business with IT Security Services
In an era of increasing cyber threats, safeguarding your business’s data and systems is critical. An IT security services company ensures robust protection, helping you stay secure, compliant, and resilient.
What Are IT Security Services?
IT security services involve proactive measures to defend against cyberattacks, data breaches, and unauthorized access. These services focus on identifying vulnerabilities, strengthening defenses, and ensuring operational continuity.
Benefits of Professional IT Security Services
Threat Detection & Prevention — Identify and block potential risks before they impact your business.
Data Protection — Safeguard sensitive information against breaches.
Compliance Support — Meet industry standards and regulations.
Business Continuity — Minimize downtime with recovery and backup solutions.
Peace of Mind — Focus on growth knowing your IT environment is secure.
Calypsi: Your Trusted IT Security Partner
At Calypsi, we specialize in comprehensive IT security solutions tailored to your needs. From firewall protection to advanced threat monitoring, our team ensures your business remains secure in a constantly evolving cyber landscape.
Don’t leave your business vulnerable. Explore our IT security services today.
0 notes
Text
How to Pick The Right Business Phone System For The Office
Would you like to replace your office phones with better ones but don’t know how to start? In this video, we are going to outline the most important aspects to consider when choosing the most appropriate business phone system to fit your needs. Be it landline, VoIP or virtual systems, we have it all!
📌 What will you learn from this video:
The steps involved in quantifying the need for business communication
Different phone systems and their pros and cons
Essential phone systems features such as voicemail, call forwarding, CRM integration among others
Advice on how to plan for growth in the future without overshooting your budget
Whether you are a growing small business or adding more people to your team, this guide will enable you to make the right decision for your office layout.
youtube
#it services#lancashire#it company lancashire#it security services#it services and solutions#Youtube
0 notes
Text
Defending the Digital Realm: The Critical Role of Cybersecurity

In today’s highly connected digital age, cybersecurity has shifted from a secondary concern to a top priority. As cyber threats continue to rise in both volume and complexity, individuals, businesses, and governments alike face unprecedented risks, including severe data breaches, financial losses, and damage to their reputations. The need for robust cybersecurity practices has never been more pressing. With that in mind, here are some essential strategies to help safeguard your digital assets.
To start, encouraging the creation of strong passwords can motivate readers to take that critical first step in securing their accounts. A combination of letters, numbers, and symbols creates a powerful first line of defense against unauthorized access.
Phishing scams are another significant threat in today’s digital landscape. These schemes are designed to trick people into sharing sensitive information. By helping readers recognize the warning signs of these increasingly advanced scams, you can equip them to navigate the digital world more safely.
Additionally, emphasizing the importance of regular software updates and reliable antivirus protection is vital. These measures help close security gaps and bolster defenses against potential cyber threats. By stressing the necessity of strong passwords, a keen awareness of phishing scams, and the habit of keeping software up to date, we can significantly enhance our digital security.
Ultimately, knowledge and proactive measures are our best tools for safely navigating the ever-evolving cyber landscape. Remember, vigilance and awareness are essential to staying secure in today’s digital world.
#Cybersecurity solutions#Data protection#Network security#Cyber threat detection#Security software#IT security services#Cyber defense#Threat prevention#Secure business solutions#Cybersecurity experts
0 notes
Text

Spictera top-tier IT security services to protect your business from cyber threats, ensuring your data is secure, compliant, and resilient against ever-evolving risks in the digital landscape.
0 notes
Text
How Sigma Solve Resolves Cybersecurity Challenges

Synopsis:
“Cybersecurity in 2024 is all about prioritizing defense dollar spending and having a security framework that provides threat intelligence, enabling robust cybersecurity strategies and apparatus.” Nehal Shah, the Solution Architect at Sigma Solve, explains the grave cyber security scenarios that are prevailing in our digital world today.
There are relentless security challenges and out-of-the-box solutions, too. As a cybersecurity solution provider, we aim to empower you with a comprehensive understanding of the cybersecurity sphere, its implications for businesses, and ways to mitigate these threats concurrently through this blog.
Conquer Cybersecurity Challenges in 2024 and Beyond:
Today, cybersecurity has taken precedence over performance. For businesses, cybersecurity solution architecture is as essential as performance-driven growth. Cybersecurity is all about protecting digital assets from unauthorized access, cyberattacks, and data breaches, which is of paramount importance.
Cybersecurity is pivotal in safeguarding critical information to prevent financial losses, avoid legal consequences, manage reputation, ensure business continuity, and preserve customer trust. Therefore, developing a robust security strategy must entail multi-factor authentication, insider threat detection, supply chain security, data loss prevention, and zero trust architecture, among other measures.

A Glimpse into Today’s Top Cybersecurity Threats:
The growth in cybersecurity threats is proportional to the growth of technological innovation. As technology advances, there are bad tech guys who want to misuse it for money or pleasure. Cybersecurity solution providers often suggest staying in sync with emerging cybersecurity threats today.
Ransomware Attacks: These attacks involve malware that breaches basic system security, ciphers data, and seeks ransom money from victims to restore their access. Such attacks on massive organizations have increased recently.
Phishing and Social Engineering: Phishing has been the most common way in which attackers trick victims into revealing sensitive financial information and use that information to cause financial damage to victims.
Advanced Persistent Threats (APTs): ATPs are consistent and continuous and don’t stop without disrupting operations or stealing data. Usually, enemy nations carry out such cyber attacks to put a hold on their missions.
IoT Vulnerabilities: IoT devices are usually more prone to cyberattacks, given their low-security levels and open-ended connectivity. It is usually used for data theft or blocking the services that these devices offer.
Supply Chain Attacks: Third-party apps aren’t fully security-proof. Attackers target such TPAs to enter into large organizations, aiming for data theft, stealing financial details, or business secrets, resulting in operational damages.
Zero-Day Exploits: Attackers target enterprise software that lacks security patches or is seldom updated. ZDEs are among the most dangerous attacks, as they render businesses defenseless and breach the entire system.
Cloud Security Threats: Clouds, despite their indisputable security features, are vulnerable to cyber attacks through misconfigurations or unauthorized access. The impenetrable cloud environment is the need of the hour.
AI and ML Attacks: Attackers can breach AI-powered applications and cause infrastructural damage or biased responses, or they can alter the ML algorithms to manipulate the inputs to damage automated workflows or data.
Why Cybersecurity Isn’t an Option, It’s a Necessity:
If you can leave your home unlocked, you can leave your business undefended. Although the offense is not the ideal defense in the realm of cybersecurity, there is no alternative to IT security services and an impenetrable security apparatus that protects not only the data but also the applications, networks, and infrastructure.
Today, businesses must adapt to behavioral analytics, dark web monitoring, quantum cryptography, and extended detection and response (XDR), among other cybersecurity measures, to prevent businesses from financial losses and reputational damages. Let’s understand the impact of cyberattacks on businesses.
Financial Losses: Desaster recovery costs or ransom costs are exponentially high, which may impact the ROI due to operational stagnation. It may also invite penalties from authorities for personal data theft.
Operational Disruption: If data is lost, business processes are affected. If the system is breached, operations experience downtime. Supply chain attacks may cripple the entire business activities for a long time, causing massive damage.
Reputational Damage: Trust is vital for business success. Cyberattacks are often carried out to cause reputational damage that may erode customer confidence, cripple financial systems, and damage brand position.
Legal Consequences: In addition to financial penalties, regulatory authorities may restrict benefits or market access. Businesses may become involved in legal battles over compensation to victims.
Strategic Impediment: Businesses may lose the rights to products and be severely hampered in their capabilities to innovate and grow. Moreover, operational and security costs may continue to rise, affecting profitability.
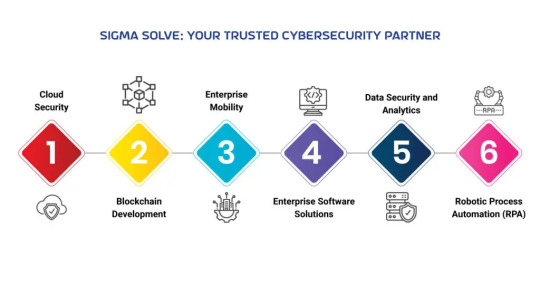
Sigma Solve: Your Trusted Cybersecurity Partner:
As digital transformation is narrowing even the virtual distance and emerging technologies are competing with humans’ cognitive capabilities, preserving the essence and securing digital assets has become the top priority for businesses across the globe.
Above and beyond growth strategies, businesses are advised by the Cybersecurity solution providers to be ready to prevent, detect, respond, and recover from cybersecurity attacks. With advanced cybersecurity innovations and tailored cybersecurity strategies, Sigma Solve delivers a Complete toolkit of strategic cybersecurity solutions entailing blockchain development services, AI-powered cybersecurity solutions, fraud detection solutions, and advanced alert systems, among others, to prevent businesses from falling prey to bad tech guys.
Artificial intelligence:
AI and automation solutions identify threat patterns to detect and respond to cyber threats. Sigma Solve developed AI security solutions to help businesses recognize and mitigate cyber threats.
Cloud Security:
Sigma Solve’s cloud consulting services entail cloud security solutions for cloud migration and cloud applications following the best practices for cloud-native cybersecurity to prevent unauthorized access.
Blockchain Development:
Our blockchain development services include measures that prevent data manipulation and ensure data validation to protect businesses from fraudulent transactions to maintain transparency and security.
Enterprise Mobility:
Sigma Solve protects remote work environments from unauthorized access and mitigates mobile threats to secure communication channels, developing robust enterprise mobility solutions.
Enterprise Software Solutions:
Integrating cybersecurity solutions in application development helps Sigma Solve protect software development, testing, and deployment against SQL injection or cross-site scripting.
Data Security and Analytics:
Data encryption, authorization, validation, and authentication are part of Sigma Solve’s data management solutions. Business intelligence and analytics solutions leverage data analytics for cybersecurity.
Robotic Process Automation (RPA):
Leveraging RPA solutions, Sigma Solve automates business processes to prevent manual entries and human errors, thus improving the efficiency and consistency of security measures.
Your Shield and Sword in the Digital Age:
The digital era demands that businesses protect themselves and mitigate cybersecurity threats to avoid business breakdown. Being your technology partner, Sigma Solve develops advanced cybersecurity solutions that leverage emerging technologies to provide head-to-toe protection.
From advanced detection to preempt resolution to disaster recovery, Sigma Solve ensures that businesses focus on their activities and leave security concerns to them. Call us at +1 954-397-0800 for a consultation to develop a tailored cybersecurity strategy for your digital assets and customer data. Original Source: https://www.sigmasolve.com/how-sigma-solve-resolves-cybersecurity-challenges/
0 notes
Text

Their cable management leaves something to be desired...
Transcript: Sun: "Gentle... Gentle Little Star. GENTLE." y/n: "Relax Sunny. You're like a mechanical junk drawer in here." Sun: "That's not our fault!!" y/n, muttering: "Then stop eating glitter glue."
No text under cut! :3

#fnaf#fnaf security breach#fnaf daycare attendant#fnaf sun moon#fnaf sun#dca fandom#fan art#digital art#artists on tumblr#sun x reader#sun x y/n#I imagine he backseats his own check ups akjfhsd#very “if i could it would be done by now” energy but mixed with the anxiety of open heart surgery (can you blame him)#you end up doing a lot of random maintenance calls to the daycare because he refuses to go to Parts and Services#.....and maybe he only trusts you...... :eyes emoji:#((a moon version is also in the works >:3c))
4K notes
·
View notes
Text
Maximizing Productivity with Google Workspace and Microsoft 365 Consulting Services

Super Cloud IT offers expert consulting services to maximize productivity with Google Workspace and Microsoft 365. Our skilled professionals optimize your digital workspace, ensuring seamless collaboration, efficient communication, and effective task management. From tailored implementation strategies to ongoing support, we empower your team to leverage the full potential of these platforms. Elevate your productivity with Super Cloud IT's comprehensive solutions, tailored to your unique business needs.
0 notes
Text

#social security#elon musk#elon#musk#phone services#elderly#elderlycare#politics#political#us politics#finance#economic#economics#donald trump#news#president trump#american politics#america#maga#president donald trump#make america great again#trump administration#democrats#trump admin#national park service#alt national park service#nps#alt nps#nature#national parks
2K notes
·
View notes
Text
How IT Security Audits Fit into Your Cybersecurity Strategy

In an age where cyber threats evolve daily and data breaches make headlines regularly, businesses can no longer afford to rely on static or one-time security measures. Instead, a dynamic and layered cybersecurity strategy is essential, and at the heart of that strategy lies a powerful, often underutilized tool: the IT security audit.
Whether you’re a small business managing sensitive customer data or a large enterprise operating under stringent compliance requirements, IT security audits are essential for identifying vulnerabilities, validating controls, and reinforcing your entire cybersecurity posture. This article explores how IT security audits fit into your overall cybersecurity strategy and why they are critical to long-term resilience.
What Is an IT Security Audit?
An IT security audit is a systematic evaluation of an organization's information systems, infrastructure, and security practices. The goal is to assess whether existing controls are effective and whether the organization complies with relevant standards, policies, and regulations.
Unlike vulnerability scans or penetration testing, which focus on technical exposures, audits take a more comprehensive view. They evaluate everything from access controls, data handling processes, software patching policies, and employee awareness training, to compliance with legal frameworks like GDPR, HIPAA, or ISO 27001.
Why IT Security Audits Are More Than Just a Compliance Check
Many businesses approach IT security audits solely as a compliance requirement. While audits help meet industry regulations, their strategic value goes far beyond checkboxes and certifications.
Here’s what IT security audits can truly offer:
Uncover Hidden Vulnerabilities: Even if your systems run smoothly, outdated protocols or misconfigured firewalls could leave backdoors wide open.
Validate Your Controls: Are your security measures working? Audits test them in real-world conditions.
Prioritize Risks Strategically: By identifying the most critical weaknesses, audits help you allocate resources efficiently.
Improve Incident Response: Audits often reveal gaps in incident response plans and can help improve preparedness.
Enhance Trust with Stakeholders: Clients, partners, and regulators are more likely to trust an organization that demonstrates proactive security practices.
Types of IT Security Audits
Depending on your industry and needs, you may conduct different types of audits:
Internal Audits: Performed by in-house security teams to ensure ongoing compliance and improvement.
External Audits: Conducted by third-party firms, often required for certifications or vendor assessments.
Compliance Audits: Focus on adherence to standards such as PCI-DSS, NIST, or ISO 27001.
Risk-Based Audits: Tailored audits that assess security based on specific business risks and threat models.
How Audits Fit into a Broader Cybersecurity Strategy
Let’s explore how IT security audits complement and elevate each component of your cybersecurity strategy.
1. Foundation for a Risk-Based Approach
A strong cybersecurity strategy starts with understanding your risk landscape. Security audits assess both technical and organizational risks, including:
Inadequate password policies
Lack of role-based access controls
Unpatched software vulnerabilities
Unsecured remote work setups
Weak backup and disaster recovery processes
Armed with audit insights, your team can shift from reactive to proactive risk management, focusing on what matters most.
2. Supports Continuous Improvement
Cybersecurity isn’t a one-time project—it’s a journey. Audits introduce a cycle of regular review and refinement. Each round of auditing creates a benchmark for measuring progress and identifying new risks as your business evolves.
For example, as your organization adopts new technologies like cloud computing or AI-driven tools, audits ensure that new systems are just as secure as your legacy infrastructure.
3. Strengthens Governance and Policy Enforcement
Many organizations struggle with enforcing security policies. IT security audits hold teams accountable by evaluating how well policies are implemented and followed in practice.
Are employees adhering to BYOD (Bring Your Device) policies? Are privileged accounts properly monitored? Are access logs regularly reviewed?
Audits provide the data to back up answers and make course corrections if necessary.
4. Improves Cyber Hygiene Across the Organization
A security-aware culture is essential for any cybersecurity strategy. Audits often include reviews of employee awareness training, phishing test results, and policy acknowledgments.
By identifying gaps in human behavior and awareness, audits allow businesses to tailor training programs, reinforce best practices, and reduce the likelihood of social engineering attacks.
5. Boosts Incident Detection and Response Capabilities
Audit reviews typically assess the effectiveness of your security monitoring tools and incident response protocols. Are alerts being triggered and acted upon promptly? Do employees know how to report suspicious activity?
Audits help identify where your defenses are too slow or where procedures break down during an actual attack. They expose potential delays or oversights that could amplify the damage in a real breach scenario.
6. Enhances Compliance and Regulatory Readiness
Data privacy laws are getting stricter around the world, from the GDPR in Europe to the DP Law in the UAE. Failing to comply can result in severe financial and reputational damage.
Regular IT audits keep you ahead of compliance issues by:
Verifying proper data encryption
Ensuring secure storage and access
Validating retention and disposal policies
Documenting access logs and security events
They also prepare you for external reviews and minimize the risk of surprises during regulatory inspections.
7. Protects Business Continuity and Reputation
A data breach doesn’t just compromise data—it can derail business operations and tarnish your brand. Audits contribute to business continuity planning by:
Reviewing backup systems and restore procedures
Ensuring redundancy and failover mechanisms are tested
Checking third-party vendor risk assessments
Ultimately, audits help your organization respond to and recover from disruptions more effectively.
Common Findings in IT Security Audits—and What They Mean
Here are some frequent red flags that audits uncover:
Default passwords are still active on devices
Unused accounts with administrative access
Unencrypted sensitive data
Delayed patching of known vulnerabilities
Lack of multi-factor authentication (MFA)
Inconsistent logging and monitoring
Each of these issues, while seemingly small, could be exploited by attackers. Audits transform these oversights into action plans before they become headlines.
Best Practices for Making the Most of IT Security Audits
To maximize value, follow these best practices:
Schedule audits regularly—at least annually or after major infrastructure changes.
Choose independent auditors for an unbiased review.
Involve multiple departments, including IT, HR, legal, and operations.
Act on audit findings quickly and track remediation progress.
Use audits as a training opportunity to improve internal capabilities.
Final Thoughts: A Strategic Asset, Not a Burden
For too long, IT security audits have been viewed as mere paperwork exercises. But when integrated strategically, they become an indispensable part of your cybersecurity framework.
They expose blind spots, strengthen defenses, and position your organization to adapt to an ever-changing threat landscape. Most importantly, they empower you to scale your operations and digital capabilities without compromising security.
In today’s digital economy, IT security audits are not just about passing—they’re about preparing, preventing, and progressing. When you treat them as a cornerstone of your cybersecurity strategy, the results speak for themselves: fewer breaches, greater trust, and a future built on digital resilience.
#it security#it security audit#it security consulting#it security services#it security services company#it security auditing
0 notes
Text

never tell yourself that you should be someone else stand up tall and say "i'm not afraid"
#daske art#fnaf#five nights at freddy's#fnaf security breach#five nights at freddy's security breach#fnaf sb#fnaf gregory#evan afton#crying child#fnaf crying child#another one for flashlight duo nation at your service
946 notes
·
View notes
Text

Spictera, a premier cybersecurity company, delivers top-notch protection against cyber threats. Specializing in advanced threat detection and response, Spictera provides tailored solutions to safeguard your digital assets. Trust Spictera for comprehensive cybersecurity services that ensure the integrity and security of your business operations.
0 notes