#Internet Security for MAC
Explore tagged Tumblr posts
Text
Dell & Mac Computer Repair Service: Restoring Performance, Reviving Possibilities
Whether it's a sluggish MacBook or a malfunctioning Dell laptop, Mobile Computer Repair brings devices back to life. Our Dell & Mac Computer Repair Service offers expert on-site diagnostics, swift fixes, and optimal performance restoration. Say goodbye to frustrating tech issues and hello to seamless computing. Call now to get your computer repaired today!
#managed service provider#SonicWALL Internet security#Dell & Mac Computer Repair Service#Anti-virus protection for laptop
0 notes
Text
Is it time to re-consider your browser? Top Alternatives to Google Chrome with Pros and Cons
Alternatives to Google Chrome are becoming increasingly popular as users seek improved privacy and performance. If you’re feeling the pinch of data collection or find Chrome slowing down your browsing experience, it may be time to explore your options. This guide will probe into the pros and cons of various web browsers that could better suit your needs while ensuring a more secure and efficient…
#alternatives to Google Chrome#best browsers for developers#best browsers for extensions#best browsers for Mac#best browsers for privacy#best browsers for Windows#best features of Edge browser#best mobile browsers for Android#best mobile browsers for iOS#Brave browser review#browser alternatives#browser market share 2023#browser security features#browser speed test#browsers with built-in ad blockers#Chrome extensions alternatives#Chromium alternatives#custom browsers for security#eco-friendly browsers#efficient web browsing#fast browsers for slow internet#fast web browsers#features of different web browsers#Firefox vs Chrome#Google Chrome alternatives for gaming#how to switch from Chrome#importance of browser speed#lightweight browsers#lightweight browsing options#Microsoft Edge vs Chrome
1 note
·
View note
Text
اهم الفروق والاختلافات بين عنوان الـ IP وعنوان MAC
عند الحديث عن الشبكات، يوجد نوعان أساسيان من العناوين التي تستخدم لتحديد الأجهزة: عنوان IP وعنوان MAC. إليك الفرق بينهما:
عنوان IP (Internet Protocol Address): التعريف:
هو عنوان رقمي يستخدم لتعريف الأجهزة على شبكة الإنترنت أو الشبكات المحلية. يتم تعيينه بشكل ديناميكي أو ثابت. البنية:
IPv4: يتكون من 32 بت، وعادة ما يكتب في شكل أربع مجموعات من الأرقام مفصولة بنقاط (مثل 192.168.1.1). IPv6: يتكون من 128 بت، ويكتب في شكل مجموعات من الأرقام والحروف مفصولة بنقطتين (مثل 2001:0 db8:85a3:0000:0000:8a2e:0370:7334). الاستخدام:
يستخدم لتوجيه البيانات بين الأجهزة على الشبكة. المرونة:
يمكن تغييره بسهولة بواسطة المستخدم أو الشبكة (ديناميكي). النطاق:
يمكن أن يتغير عندما ينتقل الجهاز من شبكة إلى أخرى. عنوان MAC (Media Access Control Address): التعريف:
هو عنوان فريد يعطى لكل بطاقة شبكة (NIC) من قبل الشركة المصنعة. يتم تعيينه بشكل ثابت ولا يتغير. البنية:
يتكون من 48 بت، ويكتب عادة في شكل ست مجموعات من الأرقام والحروف مفصولة بنقطتين أو بشرطة (مثل 00:1A:2B:3C:4D:5E). الاستخدام:
يستخدم لتعريف الأجهزة على الشبكة المحلية (LAN) وعلى مستوى طبقة ربط البيانات في نموذج OSI. الثبات:
عادةً لا يمكن تغييره بسهولة؛ يبقى ثابتًا على الجهاز طوال فترة حياته. النطاق:
يظل كما هو حتى عند انتقال الجهاز من شبكة إلى أخرى. الاختلافات الرئيسية: طبقة العمل:
عنوان IP يعمل على طبقة الشبكة (Layer 3) من نموذج OSI. عنوان MAC يعمل على طبقة ربط البيانات (Layer 2) من نموذج OSI. الهدف:
عنوان IP يستخدم لتحديد موقع الأجهزة عبر شبكات مختلفة. عنوان MAC يستخدم لتحديد الأجهزة داخل شبكة محلية واحدة. التغيير:
يمكن تغيير عنوان IP بسهولة بواسطة المستخدم أو الشبكة. من الصعب تغيير عنوان MAC لأنه مدمج في بطاقة الشبكة. الخلاصة: عنوان IP مرن ويستخدم للتواصل عبر الشبكات المختلفة، بينما عنوان MAC ثابت ويستخدم للتواصل داخل الشبكة المحلية. كل منهما يلعب دورًا مهمًا ومحددًا في شبكة الحاسوب، ويعملان معًا لضمان الاتصال السلس بين الأجهزة.
المقال مقدم من خبراء Planet VPN
0 notes
Text

Delete duplicates in Bitwarden and other password managers
Does your password manager have duplicate entries for websites, services and apps? They can cause problems when logging into places, so remove the duplicates and clean up your password database.
1 note
·
View note
Text
WELCOME TO THE FLOCK, MY DUCKLINGS!!
Come! Come! Settle down while Mama spins you a sorry tale of Legends and their Trials...
So I recently have been QUITE hyperfixated on Lego; Monkie Kid, Watching the show religiously with my boyfriend, Finally coming back to Tumblr to be fed more Art (Looking at you, @kyri45 , @swagginmun , @quesocheeso and @madabapf ) And eventually venturing out into the rabid ocean that is Ao3! for wonderful fics like those made by @smilesatdawnmain , @starsfic , @cloud-somersault and of course @zephyra-in-the-house ! I have gained such an incredible amount of inspiration from the creators around me that it eventually dragged my ass out onto the metatheoretical stage that is these platforms by the scruff of my shirt- Via @bluephoenixprincess 's 'Demon Courting Tournament' post- And led me to making this post! and hopefully many more!
THIS FIC IS FOR MATURE AUDIENCES. AGES INTENDED ARE 16+, AND IN SOME INSTANCES 18+. And though i cannot force anyone to not lie about their age or use the internet however you want, Know that this is your only warning that I give. Whatever content you choose to consume at whatever age is between You and Your Gods should you have any. Just don't come crying to me when you suddenly become aware just how psychologically damaging all the shit I put these monkeys through can be.
Legendary Guide
A world where Wukong and Liu'er were separated very differently from Canon, and where Demonic and Celestial Courting is far more important to the Legend of the Monkie Kid.
Follow the Monkey Trio as they navigate a world of heartache, persecution, harassment, retribution, justice, and eventually...
Reunion.
Concept Outline/Prologue
"Legendary" -The Biggen! This is the main story, a canon-rewrite of the whole show starting from the Season 2 Special and onward!
"A Million Dreams" - A smaller side project, made for worldbuilding, a showcase of past ShadowPeach, the Brotherhood, and Mac and Wukong's last conversation
"The Journey and the Aftermath" - Another small side project, meant for more worldbuilding, a showcase of what Wukong's relationship with the Pilgrims was like, Wukong's initial Greif, and the First Tournament
"Of Obsidian and Wind, The Samadhi Son" - A Sub-Plot to the larger story of Legendary. showcasing Red Son's initial 2 week therapy sessions from the timeframe of him getting to FFM to him 'waking up' Mk in chapter 9. with a couple of therapy sessions between him and Sandy talking about future events. will update alongside Legendary.
One Shots;
The Cicada and the Infant - The Golden Cicada. One of the Buddha's first disciples, now cast out of Paradise. And cursed to live 10 pious lives in accordance with Heaven's command. Or, in short; Cicada is Heaven's slave. Until they say he is done. He just wants to go home.. He is on his 8th Life shackled to the Jade Emperor's command. He is almost done. At the end of this life, he is tasked with "Securing the Jade Emperor's Rule." By killing Sun Wukong and Liu'Er Mihou's son.
In the Dark of the Night - Mk has some trouble with his clones, and his magic, and sleep, and training- when did he last eat again? He doesn't quite know... But he does know His Family is safe. Because he stays Awake. A certain Mr. Shadow takes issue with this.
When the Noodles are Free - A Collection of Memories Tang and Pigsy share, their First meeting, Dating, taking in Mk, Wedding Night, and some fluffy and difficult memories of raising their little Xiaotian.
Sleepovers, Spars, and Shopping Trips - There's a first time for everything, These are Red Son's Firsts with his new... Friends..?
Champion, Warrior, King - The New Jade Emperor calls upon a well- renowned Prophetess to tell him his future of his Reign over the Realms.
Art cover art concept #1 Chapter 1 Celebration! Traffic Light Trio designs! (Season 1 completion celebration) SpicyNoodles Doodles Get in The Water (What Sandy losing his shit looks like) Monkey Trio Eye colors Free Will Practice (Shadow Peach Anatomy Study) Unglamoured Red Son (from the Hot Springs Scene / Highland Cow inspo Oh, How I love You (Pride Month Celebration Art part 1) The Pride Month Marathon!
Main Playlist
Secondary Playlists
Worldbuilding and HeadCanons! Purr Audios! Bad Ending Bad Chapter 6 End ShadowPeach Love Languages Headcanons! Marriage of Convenience? Mk's Opinion on Liars FreeNoodles Fluff Incomplete Mate Bond Time is Bleeding, Its running out Macaque's Grave Mk's War Form Vibes be Like:
Main Height Chart
Suitors Height Chart
FANART!!


"Draw 6 Au's challenge" by @tragedytells-tales


"A compromise, then." Also by @tragedytells-tales


"Yearning Ghost and Forever Greiving Monkey" by @fresastar

"I found it" by @starfall33

"A Champion" by @tragedytells-tales

Redraw of "shot in the Dark" by @axelzk
it is so nice to finally give myself a Voice on these platforms. I can't wait to show you what I have made.

#monkie kid#shadowpeach#monkie kid fanart#lmk mk#epic the musical#ao3 fanfic#ao3 writer#art#lmk spicynoodles#lmk red son#lmk macaque#lmk sun wukong#lmk fanart#lmk fandom#lmk fanfiction#lmk freenoodles#lmk lady bone demon#lmk mei#lmk pigsy#lmk sandy#lmk shadowpeach#lmk swk#lmk tang#lego monkie kid fanart#lmk wukong#lmk#lmk art#lmk mk fanart#fic playlist#playlist
57 notes
·
View notes
Note
what is the best way to get safer/more anonymous online
Ok, security and anonymity are not the same thing, but when you combine them you can enhance your online privacy.
My question is: how tech literate are you and what is your aim? As in do you live in a country where your government would benefit from monitoring private (political) conversations or do you just want to degoogle? Because the latter is much easier for the average user.
Some general advice:
Leave Windows and Mac operating systems and switch to Linux distributions like Fedora and Ubuntu (both very user friendly). Switch from Microsoft Office or Pages/Numbers/Keynote (Mac) to LibreOffice.
You want to go more hardcore with a very privacy-focused operating system? There are Whonix and Tails (portable operating system).
Try to replace all your closed source apps with open source ones.
Now, when it comes to browsers, leave Chrome behind. Switch to Firefox (or Firefox Focus if you're on mobile). Want to go a step further? Use LibreWolf (a modified version of Firefox that increases protection against tracking), Brave (good for beginners but it has its controversies), DuckDuckGo or Bromite. You like ecofriendly alternatives? Check Ecosia out.
Are you, like, a journalist or political activist? Then you probably know Tor and other anonymous networks like i2p, freenet, Lokinet, Retroshare, IPFS and GNUnet.
For whistleblowers there are tools like SecureDrop (requires Tor), GlobaLeaks (alternative to SecureDrop), Haven (Android) and OnionShare.
Search engines?
There are Startpage (obtains Google's results but with more privacy), MetaGer (open source), DuckDuckGo (partially open source), Searx (open source). You can see the comparisons here.
Check libRedirect out. It redirects requests from popular socmed websites to privacy friendly frontends.
Alternatives to YouTube that value your privacy? Odysee, PeerTube and DTube.
Decentralized apps and social media? Mastodon (Twitter alternative), Friendica (Facebook alternative), diaspora* (Google+ RIP), PixelFed (Insta alternative), Aether (Reddit alternative).
Messaging?
I know we all use shit like Viber, Messenger, Telegram, Whatsup, Discord etc. but there are:
Signal (feels like Whatsup but it's secure and has end-to-end encryption)
Session (doesn't even require a phone or e-mail address to sign up)
Status (no phone or e-mail address again)
Threema (for mobile)
Delta Chat (you can chat with people if you know their e-mail without them having to use the app)
Team chatting?
Open source options:
Element (an alternative to Discord)
Rocket.chat (good for companies)
Revolt.chat (good for gamers and a good alternative to Discord)
Video/voice messaging?
Brave Talk (the one who creates the talk needs to use the browser but the others can join from any browser)
Jami
Linphone
Jitsi (no account required, video conferencing)
Then for Tor there are various options like Briar (good for activists), Speek! and Cwtch (user friendly).
Georestrictions? You don't want your Internet Provider to see what exactly what you're doing online?
As long as it's legal in your country, then you need to hide your IP with a VPN (authoritarian regimes tend to make them illegal for a reason), preferably one that has a no log policy, RAM servers, does not operate in one of the 14 eyes, supports OpenVPN (protocol), accepts cash payment and uses a strong encryption.
NordVPN (based in Panama)
ProtonVPN (Switzerland)
Cyberghost
Mullvad (Sweden)
Surfshark (Netherlands)
Private e-mails?
ProtonMail
StartMail
Tutamail
Mailbox (ecofriendly option)
Want to hide your real e-mail address to avoid spam etc.? SimpleLogin (open source)
E-mail clients?
Thunderbird
Canary Mail (for Android and iOS)
K-9 Mail (Android)
Too many complex passwords that you can't remember?
NordPass
BitWarden
LessPass
KeePassXC
Two Factor Authenticators?
2FAS
ente Authenticator
Aegis Authenticator
andOTP
Tofu (for iOS)
Want to encrypt your files? VeraCrypt (for your disk), GNU Privacy Guard (for your e-mail), Hat.sh (encryption in your browser), Picocrypt (Desktop encryption).
Want to encrypt your Dropbox, Google Drive etc.? Cryptomator.
Encrypted cloud storage?
NordLocker
MEGA
Proton Drive
Nextcloud
Filen
Encrypted photography storage?
ente
Cryptee
Piwigo
Want to remove metadata from your images and videos? ExifCleaner. For Android? ExifEraser. For iOS? Metapho.
Cloak your images to counter facial recognition? Fawkes.
Encrypted file sharing? Send.
Do you menstruate? Do you want an app that tracks your menstrual cycle but doesn't collect your data? drip.
What about your sexual health? Euki.
Want a fitness tracker without a closed source app and the need to transmit your personal data to the company's servers? Gadgetbridge.
35 notes
·
View notes
Note
Mac, how do you feel about one of humanity’s biggest fears…A JOB!!!!- 🔥🔥🔥🔥🔥💥💥💥💥🤯🤯🤯🤯🤯 (peak internet humor, am I right fellas?)
I actually already have a job. My job is to make sure you and your data is securely protected from phishing attacks and malware!

With all of the dodgy websites you download applications from, it can be a little tricky at times.

but it’s a pretty fulfilling if it means I get to see you smile when you can open a game without issue!

21 notes
·
View notes
Note
do you know any good guides to get into furry muck?? ive wanted to try it for ages but find it confusing
so long as you have some familiarity with command line/terminal and the basic CLI procedures, i found the starting guide on the official site quite adequate. otherwise, first familiarize yourself with the command line interface of your computer. it takes a little getting used to, but this is how the entire MUCK will be, plus knowing how to use a CLI is a good skill to have.
you will need telnet installed on your computer. telnet is the protocol that will allow you to access furrymuck through your CLI (telnet is not secure, so don't type anything into furryMUCK you wouldn't want anyone to be able to see! this is the risk of using a legacy system, assume it has already been compromised and act accordingly). on windows telnet is preinstalled but you will need to enable it as described in this guide. on linux and macOS you can install it with a package manager. i use homebrew on mac.
once you have telnet, the official guides for connecting are here. character registration is done via email. mine took around a week and a half to come back. because your passwords are sent in plaintext over email and unsecured over telnet do not reuse another password. here in the registration guide.
once you access the MUCK, the area just outside the bandstand where you start has guides for new players and the people around there are generally willing to help new and clueless players (like me). it takes a little trial and error and exploring. i found this guide for interacting with the enviornment helpful.
furryMUCK is a very magical place when you're able to meet it at its own terms. part of the fantasy is the clunkiness of the ancient internet its idiosyncrasies. have so much fun!
63 notes
·
View notes
Text
Overwhelming Feelings
In which Timothy messed up.
Or so he thought.
(W/N: a little filler for the next chapter of sassy, de-aged Timmy Drake. The next chapter will be more of Tim Drake that doesn't have any control if his thoughts.)
Tim messed up.
He didn't mean to lose his cool about that rowdy ginger. If his parents heard about this he will be done for. They spend so much time imprinting the etiquettes of social elites of Gotham and he messed up. He never messed up before but he doesn't know why that kid made him lose his cool. Probably seeing the freedom she had and the adults in her life never seems to criticise her, made him jealous.
He was pacing back and forth on his room biting his nails as a form of tic when he is nervous when he bumped into a shelf. He hissed in pain and a notebook fell off. He look at it and open it.
It is sort of a diary, notes with number entries and some sort of details about it. And based on the handwriting, it was his notebook. Timothy skimmed over it, thinking what would his older self will do in this situation. Because right now, all he could think of is getting out of here and disappeared in the abyss, but getting out of the manor is like a Mission Impossible. There is so many alarms systems and he doesn't know how to get around it.
He skimmed over until he found a two page note of how does his older self if the book found the way to get around the security system. He quickly get a small bag and filled it with little money and clothes that he had. He grabbed the notebook and he went with his plan.
+++++
The Drake Manor is as quiet as it gets but the dust is thick, as if like Mrs. Mac stopped cleaning it for months or years even, but that's impossible, Mrs. Mac just been here last week and he knows that, he saw Mrs. Mac cooking him dinner.
He went to his room and dusted his bed and lie down. Finally, it's quiet.
He was about to fall asleep when a realisation hit him.
Why does he have a notebook in the Wayne Manor?
How does he know the way to get around the security system?
Tim had a suspicions about why he was in the Wayne Manor's sort of clinic but he need to know, he went to a desktop computer his parents have but the power is out and their router is also gone. But then he remembered there is a laptop hidden in his parents closet.
He grabbed it and wished for it to work. When the light turned up and the loading screen showed up, he sigh in relief.
After putting the password, he looked at the date. It's May of 20xx, he is supposed to be 19 now, but he is 8, and it is nowhere closed to Thanksgiving. But, where is his parents? He knows they will be mad if they know that he is being buddy buddy with the neighbours.
He wanted to asked the internet but their router is definitely down. His parents is not probably in Gotham, nothing new, Mrs. Mac stopped cleaning the house and he is 11 years younger than he supposed to be. He needs to know more. But where can he find the information about the last 11 years?
+++++
Tim went a couple of times in the library in Old Gotham whenever he feels so lonely inside of his house. The people inside the library calms him down and his mind take it as a way that he is not alone.
He beelined to the computers and click the Google icon, and search "Jackson Drake", he knows his father has more influence than his mother even though his mother is the one with the power in the DI. Because misogyny still exist, Fabio.
He was shown by a large window with his father's picture and when he skimmed over, his heart sank.
With his hands shaking, he typed in the search bar, "Jackson Drake death", and it was filled with news article of his dad's death.
Then his attention got swerved to the suggestion, "Janet Drake's death". He read the article after article and it takes him so long just to sink the information in him.
His mind is filled with why and how's. In his mind, his mother has always been a sort of invincible to him. How could someone killed his mother with poison? His mother could get through that!
He closed all of the tabs and leave the library with no interruptions from others.
++++
He doesn't know how he get here. All he could remember is that he was walking out of the library. The sun has set far ago and he was walking around, his legs are already shaking but he couldn't get himself to stop walking until he face a stone with engraving of his mother and beside her mother's tomb is his father's grave was there.
He was shaking, probably with all the emotions that he is currently having, the long walk from library, and also the coldness of Gotham air. He doesn't know what to do, is this why he was in the Wayne Manor? But why would the Bruce Wayne would take him under his wing? It doesn't make sense.
He is in wreck. He doesn't know what to do. His mother didn't teach him anything about what to do after her passing. He was not prepared for this.
He was tired, as his eyes starts to close and he let his tiredness consume him. He fall asleep on top of his mother's grave.
+++++
"How the fuck, did you lose a child?!"
"The sensors and the cameras didn't catch him. How does he even know how to do that?"
"Alfred?"
"I apologise young masters, but Master Tim didn't went out using the front door."
"We are the best detectives and we can't find the little kid?"
"Well, I know where he was." a voice in their earpiece certainly wasn't expected.
"And you didn't say anything?"
"Well, I just found him, while you idiots are arguing."
"Where he is Babs?"
"Gotham Cemetery, probably visiting his parents grave."
"How did he even know?"
"Let's ask him later."
88 notes
·
View notes
Text
I finally got a new laptop! Yay! My geriatric 8-year-old can finally be sent to the retirement home (aka gathering dust in the closet because what if I need it later). And now I can run programs and perform tasks without it taking a dog's age! :D
But I did notice something in getting everything set up.
I've been a staunch Linux lad since I was very little--one of the few things my father and I actually agree on. And the new laptop came pre-installed with Windows 11, as most new non-Macs do, so I decided to partition a bit of the drive for it rather than wiping it completely, just in case I need Windows compatibility for school or work stuff, even if I spend the majority of my time in Ubuntu. (I had wanted to do that with my old machine, actually, but something went horrendously wrong in the process and it took two days to fix and my laptop briefly did not have a functioning OS on it at all lol.)
Now, I find Windows... unpleasant to use. And obviously part of that is just that I'm not familiar with it--the last time I had Windows on a personal computer was when I was 6 years old, and that thing ran Windows 2000 with a genuine CRT monitor and it was not connected to the internet and I spent my time playing King's Quest and MS Paint. I don't know where things are anymore, and the UX seems pretty uninterested in telling me.
Another issue is, of course, how bloated with ads and spyware it's become in recent iterations. I see where people are coming from when they decide to stick with Windows 7 or Vista or some other older version, even if I disagree with them for security and malware reasons--"person on previous version of Windows" is by far the largest and juiciest target for all manner of bad actors online.
But I think a really big core part of the problem is this: modern Windows is speaking a different language than I am. And the language it's speaking is that of phones, not of computers.
I only spent enough time on Windows to get it set up and strip away all the permissions I possibly could, and in that time I could tell: the default user Microsoft is designing this system for is people who are more familiar with Android and Apple than they are with a desktop computer. They made me log in with my email, rather than creating a device-specific profile. When I created my password they didn't even call it a password, they called it a "Hello Windows PIN". The format of the Settings page UI is nigh-identical to the one on my phone, right down to the list of access permissions siloed away by app (and yes, everything is called an app--no programs, no functions, no systems, no app*lications*, nothing else). I had to check a specific box to be able to look through my entire computer's file system, for crying out loud, rather than just browsing my Pictures and Downloads!
Hey, Windows! My laptop! Is not! A phone! And I don't want it to be! This is a computer OS for people who hate computers and I. HATE IT!
#People I am begging you. I understand everything is Windows now. But please use Linux#There are many different versions nowadays and lots of them are very user-friendly#Ubuntu is the one I use and it's lovely#Mint is another very good one#If you need to keep a little Windows around that's fine. Work and school stuff is often Windows only. I get it#But if you're browsing the web or playing Steam games or writing in Word docs or whatever? On your own time?#Linux. LibreOffice. Just use them. They are so much better
30 notes
·
View notes
Text
The eye-popping scandal surrounding the Trump cabinet’s accidental invitation to The Atlantic’s editor in chief to join a text-message group secretly planning a bombing in Yemen has rolled into its third day, and that controversy now has a name: SignalGate, a reference to the fact that the conversation took place on the end-to-end encrypted free messaging tool Signal.
As that name becomes a shorthand for the biggest public blunder of the second Trump administration to date, however, security and privacy experts who have promoted Signal as the best encrypted messaging tool available to the public want to be clear about one thing: SignalGate is not about Signal.
Since The Atlantic’s editor, Jeffrey Goldberg, revealed Monday that he was mistakenly included in a Signal group chat earlier this month created to plan US airstrikes against the Houthi rebels in Yemen, the reaction from the Trump cabinet’s critics and even the administration itself has in some cases seemed to cast blame on Signal for the security breach. Some commentators have pointed to reports last month of Signal-targeted phishing by Russian spies. National security adviser Michael Waltz, who reportedly invited Goldberg to the Signal group chat, has even suggested that Goldberg may have hacked into it.
On Wednesday afternoon, even President Donald Trump suggested Signal was somehow responsible for the group chat fiasco. “I don't know that Signal works,” Trump told reporters at the White House. “I think Signal could be defective, to be honest with you.”
The real lesson is much simpler, says Kenn White, a security and cryptography researcher who has conducted audits on widely used encryption tools in the past as the director of the Open Crypto Audit Project: Don’t invite untrusted contacts into your Signal group chat. And if you’re a government official working with highly sensitive or classified information, use the encrypted communication tools that run on restricted, often air-gapped devices intended for a top-secret setting rather than the unauthorized devices that can run publicly available apps like Signal.
“Unequivocally, no blame in this falls on Signal,” says White. “Signal is a communication tool designed for confidential conversations. If someone's brought into a conversation who’s not meant to be part of it, that's not a technology problem. That's an operator issue.”
Cryptographer Matt Green, a professor of computer science at Johns Hopkins University, puts it more simply. “Signal is a tool. If you misuse a tool, bad things are going to happen,” says Green. “If you hit yourself in the face with a hammer, it’s not the hammer’s fault. It’s really on you to make sure you know who you’re talking to.”
The only sense in which SignalGate is a Signal-related scandal, White adds, is that the use of Signal suggests that the cabinet-level officials involved in the Houthi bombing plans, including secretary of defense Pete Hegseth and director of national intelligence Tulsi Gabbard, were conducting the conversation on internet-connected devices—possibly even including personal ones—since Signal wouldn’t typically be allowed on the official, highly restricted machines intended for such conversations. “In past administrations, at least, that would be absolutely forbidden, especially for classified communications,” says White.
Indeed, using Signal on internet-connected commercial devices doesn’t just leave communications open to anyone who can somehow exploit a hackable vulnerability in Signal, but anyone who can hack the iOS, Android, Windows, or Mac devices that might be running the Signal mobile or desktop apps.
This is why US agencies in general, and the Department of Defense in particular, conduct business on specially managed federal devices that are specially provisioned to control what software is installed and which features are available. Whether the cabinet members had conducted the discussion on Signal or another consumer platform, the core issue was communicating about incredibly high-stakes, secret military operations using inappropriate devices or software.
One of the most straightforward reasons that communication apps like Signal and WhatsApp are not suitable for classified government work is that they offer “disappearing message” features—mechanisms to automatically delete messages after a preset amount of time—that are incompatible with federal record retention laws. This issue was on full display in the principals’ chat about the impending strike on Yemen, which was originally set for one-week auto-delete before the Michael Waltz account changed the timer to four-week auto-delete, according to screenshots of the chat published by The Atlantic on Wednesday. Had The Atlantic’s Goldberg not been mistakenly included in the chat, its contents might not have been preserved in accordance with long-standing government requirements.
In congressional testimony on Wednesday, US director of national intelligence Tulsi Gabbard said that Signal can come preinstalled on government devices. Multiple sources tell WIRED that this is not the norm, though, and noted specifically that downloading consumer apps like Signal to Defense Department devices is highly restricted and often banned. The fact that Hegseth, the defense secretary, participated in the chat indicates that he either obtained an extremely unusual waiver to install Signal on a department device, bypassed the standard process for seeking such a waiver, or was using a non-DOD device for the chat. According to political consultant and podcaster Fred Wellman, DOD “political appointees” demanded that Signal be installed on their government devices last month.
Core to the Trump administration’s defense of the behavior is the claim that no classified material was discussed in the Signal chat. In particular, Gabbard and others have noted that Hegseth himself is the classification authority for the information. Multiple sources tell WIRED, though, that this authority does not make a consumer application the right forum for such a discussion.
“The way this was being communicated, the conversation had no formal designation like 'for official use only' or something. But whether it should have been classified or not, whatever it was, it was obviously sensitive operational information that no soldier or officer would be expected to release to the public—but they had added a member of the media into the chat,” says Andy Jabbour, a US Army veteran and founder of the domestic security risk-management firm Gate 15.
Jabbour adds that military personnel undergo annual information awareness and security training to reinforce operating procedures for handling all levels of nonpublic information. Multiple sources emphasize to WIRED that while the information in the Yemen strike chat appears to meet the standard for classification, even nonclassified material can be extremely sensitive and is typically carefully protected.
“Putting aside for a moment that classified information should never be discussed over an unclassified system, it’s also just mind-boggling to me that all of these senior folks who were on this line and nobody bothered to even check, security hygiene 101, who are all the names? Who are they?” US senator Mark Warner, a Virginia Democrat, said during Tuesday’s Senate Intelligence Committee hearing.
According to The Atlantic, 12 Trump administration officials were in the Signal group chat, including vice president JD Vance, secretary of state Marco Rubio, and Trump adviser Susie Wiles. Jabbour adds that even with decisionmaking authorities present and participating in a communication, establishing an information designation or declassifying information happens through an established, proactive process. As he puts it, “If you spill milk on the floor, you can’t just say, ‘That’s actually not spilled milk, because I intended to spill it.’”
All of which is to say, SignalGate raises plenty of security, privacy, and legal issues. But the security of Signal itself is not one of them. Despite that, in the wake of The Atlantic’s story on Monday, some have sought tenuous connections between the Trump cabinet’s security breach and Signal vulnerabilities. On Tuesday, for example, a Pentagon adviser echoed a report from Google’s security researchers, who alerted Signal earlier this year to a phishing technique that Russian military intelligence used to target the app’s users in Ukraine. But Signal pushed out an update to make that tactic—which tricks users into adding a hacker as a secondary device on their account—far harder to pull off, and the same tactic also targeted some accounts on the messaging services WhatsApp and Telegram.
“Phishing attacks against people using popular applications and websites are a fact of life on the internet,” Signal spokesperson Jun Harada tells WIRED. “Once we learned that Signal users were being targeted, and how they were being targeted, we introduced additional safeguards and in-app warnings to help protect people from falling victim to phishing attacks. This work was completed months ago."
In fact, says White, the cryptography researcher, if the Trump administration is going to put secret communications at risk by discussing war plans on unapproved commercial devices and freely available messaging apps, they could have done much worse than to choose Signal for those conversations, given its reputation and track record among security experts.
“Signal is the consensus recommendation for highly at-risk communities—human rights activists, attorneys, and confidential sources for journalists,” says White. Just not, as this week has made clear, executive branch officials planning airstrikes.
28 notes
·
View notes
Text
One day, deciding that ShinRa’s finest SOLDIERs are far too distracted during work hours, Lazard decides to implement a security browser that allows him to see what the Firsts are searching for online. Just to make sure they’re staying on track. Just to make sure they know their own intelligence and don’t need to rely on the World Wide Web.
Morbidly curious, he decides to take a look at the results after the first day.
~~~
Genesis’s Search History:
• Is Mona Lisa dead?
• Is the color red better than silver?
• Is WWE real?
• is the color brown better than silver
• what’s the adjective for one without love?
• How to be emo
• What’s the first book in the Bible
• Are rapiers better than katanas
• Does ice expire
• why do people tell me to shut up
• Are phoenixes better than cats
• is it illegal to steal a street sign
• How to put out a microwave fire
• can metal go in the microwave
• why the hell does my friend have slitted pupils
• how can I get slitted pupils?
• contacts with slitted pupils low price
• silver elite homepage
Angeal’s Search History:
• my kids are fighting what do I do
• my adult kids are fighting what do I do
• seafood pasta recipes
• my teenager won’t stop eating cinnamon dog biscuits what do I do
• is it practical to carry a sword you never use
• what temperature should cacti be kept at
• where is the internet
• do sunglasses make you cool
• honor synonyms
• what is lucid dreaming
• Kraft mac and cheese
• is ShinRa ethical
• is “puppy” considered derogatory
• is it normal for your friend to growl
• are plants good listeners
• what are phoenixes
• why does my teenager never listen
• local diners help wanted
• is it possible to send two adults to military school
• how do I delete my last search
Sephiroth’s Search History:
• is it normal to growl
• Why are my pupils slitted
• is silver hair natural
• chemical composition of a single strand of spaghetti
• cute panda videos
• are sprinkles edible
• is it normal to hear voices in my sleep
• is silver a better color than red
• how to tell someone to shut up in a language they do not speak
• are trees sentient
• cute seal videos
• is my father my father
• is it incorrect to be shirtless
• why is it incorrect to be shirtless
• is it normal to be able to lift a jeep
• can the human body handle the consumption of a mole of spaghetti noodles
• current day slang
• loveless SparkNotes
• how to tell my friends that I love them
Zack’s Search History:
• What do anteaters eat
• What is a city people live in called
• Sodium chloride
• What is the square root of one
• who invented walking
• Loveless SparkNotes
• Does General Sephiroth like hugs?
• world squat record
• Are sombreros allowed in the military
• How many marshmallows can fit inside of a whale
• I GOT MY FRIEND’S SWORD DIRTY DO I TAKE IT TO THE DRY CLEANERS
• where does the word laptop come from
• how much water is too much
• how to make my mentor proud
• Do rattlesnakes actually have beans in their tails
• how many pounds of pepperoni is unhealthy
• How much of Dr Dolittle is true
• How to tell someone they are loved and wanted
• sophisticated words of today
• why are they called graham crackers
• toaster alarm clocks
~~~
Lazard closes the computer, letting his head fall into his hands.
#sephiroth#genesis rhapsodos#zack fair#angeal hewley#ffvii#crisis core#ff7#lazard deusericus#randomness#feeling especially silly#I love em so much they’re so stupid <33
177 notes
·
View notes
Text
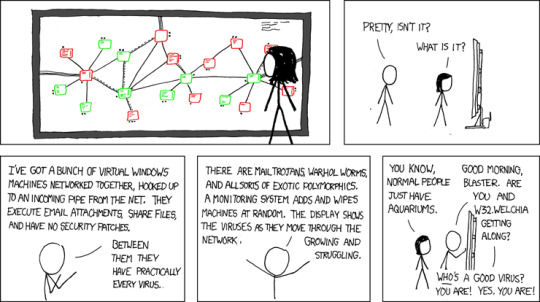
Viruses so far have been really disappointing on the 'disable the internet' front, and time is running out. When Linux/Mac win in a decade or so the game will be over.
Network [Explained]
Transcript Under the Cut
[Megan looking at a large screen with many green and red squares. The squares have writing in them and lines connecting them.]
[Side view. The screen is a huge LCD connected to a wireless router.] Cueball: Pretty, isn't it? Megan: What is it?
Cueball: I've got a bunch of virtual Windows machines networked together, hooked up to an incoming pipe from the net. They execute email attachments, share files, and have no security patches. Cueball: Between them they have practically every virus.
Cueball: There are mail trojans, warhol worms, and all sorts of exotic polymorphics. A monitoring system adds and wipes machines at random. The display shows the viruses as they move through the network. Growing and struggling.
[Cueball walks past the girl and touches the monitor.] Megan: You know, normal people just have aquariums. Cueball: Good morning, Blaster. Are you and W32.Welchia getting along? Cueball: Who's a good virus? You are! Yes, you are!
60 notes
·
View notes
Text
Celebrity Birth Chart Analysis🔮
(Stevie Nicks)
Stevie Nicks is a musical artist who is known for her own music as well as being in the band Fleetwood Mac. She was born on May 26, 1948 at 3:02 am (hopefully correct) in Phoenix, AZ.


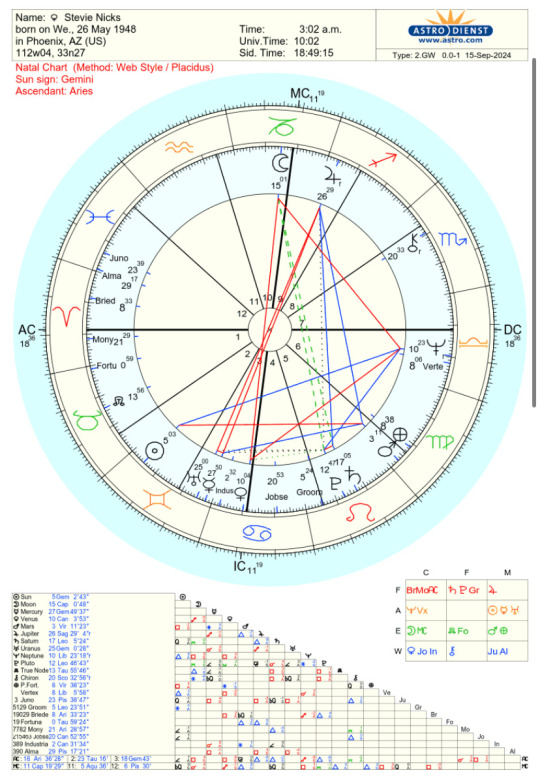
Sun in Gemini 2h 5°: Her identity, self can be smart, witty, funny, a good communicator with Gemini. In 2h she can be stable, beautiful, financial secure. 5° (Leo) degree she can be creative, fun, confident.
Moon in Capricorn 10h 15°: Her emotions can be serious, cold, can be about her career, work, reputation with Capricorn & 10h. 15° (Gemini) degree her emotions can be intelligent, about her siblings, communication, education.
Mercury in Gemini 3h 27°: Her communication is all Gemini with sign, house, and degree. She can love to talk, be good with communication. Can love to communicate about her education, siblings. She can communicate in a witty & funny way.
Venus in Cancer 3h 10°: Her beauty & romances can be sensitive, emotional, can love her home & family. She can want traditional values in her romances. She can be found very beautiful from other women with Cancer. In 3h she can want good communication in her relationships. 10° (Capricorn) degree she can love her work & can want someone hardworking.
Mars in Virgo 5h 3°: Her passion & ambition can be her work, routine, health, and being organized with Virgo. In 5h she can have a passion for her creativity, having fun, performing, children. 3° (Gemini) degree passion for communication, education.
Jupiter in Sagittarius 9h 26°: Her luck & expansion can be related to spirituality, traveling, learning, freedom, religion with Sagittarius & 9h. 26° (Taurus) degree luck with her beauty, finances, stability. Jupiter is also the husband in astrology so her fs could have Sagittarius or Taurus placements.
Saturn in Leo 5h 17°: Her challenges are all Leo with sign, house, and degree again lol. In Leo challenges with her confidence, passion. In 5h challenges with being creative, having fun, children. 17 degrees and fame degree can create challenges with fame for a long time.
Uranus in Gemini 3h 25°: Her sudden changes in life can be with her communication, learning, the internet, siblings, neighbors with Gemini & 3h. 25°(Aries) degree sudden changes with her confidence, appearance, body.
Neptune in Libra 6h 10°: Her creativity, spirituality, and delusions can be from her relationships, business contracts with Libra. In 6h she can be creative with her routine, health, work. 10° (Capricorn) degree again creative etc; with her work, career, reputation.
Pluto in Leo 5h 12°: Her transformation can be related to her creativity, fun, performing, romances, confidence with Leo & 5h. 12° (Pisces) degree transformations creatively, spiritually, with her emotions.
NN in Taurus 1h 13°: Her souls mission / purpose is to be more stable, financially stable, romantic with Taurus. In 1h & 13° (Aries) is to be more bold, confident, independent, focus more on appearance & body.
Chiron in Scorpio 7h 20°: Her wounds / what she needs to heal can be related to the occult, sex, transformations, wealth with Scorpio & 20° (Scorpio) degree. In 7h wounds with her relationships, marriages, business contracts.
Part of Fortune in Virgo 6h 8°: Her luck / fortune can be with her routine, health, work, helping others with Virgo & 6h. 8° (Scorpio) degree luck with transformations, finances, sex.
Vertex in Libra 6h 8°: Her fated things that will happen can be related to relationships, business contracts with Libra. In 6h fated to have routines, staying healthy and working. 8° (Scorpio) degree fated to go through transformations, rebirth, wealth.
Juno in Pisces 12h 23°: Her ideal partner can be sensitive, creative, spiritual with Pisces & 12h. 23°(Aquarius) degree ideal partner can be unique, friendly, on the internet.
Groom in Leo 4h 5°: Her fs could be creative, fun, confident with Leo & 5° (Leo) degree. In 4h her fs can be sensitive, nurturing, all about home & family.
Briede in Aries 12h 8°: As a wife she can be fiery, bold, passionate with Aries. In 12h she can be sensitive, creative, spiritual. 8° (Scorpio) degree she can be intense, emotional, transformative.
Fortuna in Taurus 1h 0°: Her fortune can be related to stability, finances, beauty, romance with Taurus. In 1h fortune with her self, appearance, body.
Mony in Aries 1h 21°: Her money can come from her appearance, body, being confident with Aries & 1h. 21° (Sagittarius) degree money can be from traveling, teaching, learning.
Jobse in Cancer 4h 20°: Her job can be related to emotions, homes, families, nurturing with Cancer & 4h. 20° (Scorpio) degree job can be related to the taboo, transformation, wealth.
Industria in Cancer 3h 2°: The industry she can work in can be with women, homes, families with Cancer. In 3h the industry can involve communication, learning, the internet. 2° (Taurus) degree the industry can involve stability, beauty, finances.
Alma in Pisces 12h 29°: Her soulmate connections can be sensitive, creative, spiritual, romantic with Pisces & 12h. 29° (Leo) degree soulmate connections can be creative, fun, could have children (in her case she doesn’t but previously was pregnant).
Talent in Sagittarius 8h 12°: Her talents can involve traveling, learning, teaching with Sagittarius. In 8h talents with the taboo, transformation, wealth. 12° (Pisces) degree talents with creativity, spirituality.
Singer in Taurus 1h 21°: Her as a singer can be beautiful, stable, romantic even with Taurus. In 1h she can be a fiery, bold, confident singer. 21° (Sagittarius) degree she can be a carefree, adventurous, even religious singer.
Asc: Aries 18°: Others can see her as fiery, bold, confident, passionate with Aries. 18° (Virgo) degree others can see her as organized, logical, hardworking.
Mc: Capricorn 11°: Her career / reputation can be serious, can require a lot of hard work with Capricorn. 11° (Aquarius) degree career can be unique, can involve the internet and friends.
Aspects:
Mercury Conjunct Uranus 3h: Her communication style can bring her sudden changes with her communication, learning, the internet.
Saturn Conjunct Pluto 5h: Her challenges with creativity, fun, children can bring her transformations in these areas.
Neptune Conjunct vertex 6h: Her creativity, spirituality being apart of her routine can be fated to happen.
Juno 12h trine Chiron 7h: Her ideal partner being someone sensitive, creative, spiritual etc can help / cause / have wounds with relationships, business contracts.
Groom 4h sextile sun 2h: Her fs being sensitive, nurturing, family oriented can go with her identity of stability, beauty, romances.
Industria conjunct mercury 3h: Her career / industry can involve lots of communication & learning.
Mony Conjunct Ascendant: Her money / the way she makes money can be seen by others.
Asteroids Used:
Juno (3), Groom (5129), Briede (19029), Fortuna (19), Mony (7782), Jobse (215463), Industria (389), Alma (390), Talent (33154) Singer (10698).
19 notes
·
View notes
Text









we packed up my studio on Thursday night, so my residency in the burren is officially over 💔🌦 i'll miss it tremendously, including my fellow residents who have already dispersed— such a lovely group with whom i'm so grateful to have shared this time, they improved it tenfold. and i'm grateful to everyone who helped me make this possible.
i worked on pieces large and small, which i haven't had time nor energy to accomplish in the last few years. i didn't finish everything, mainly due to spending as much time exploring the mountains, woods, ruins, and Árann islands. the writing i paired with my work for the Open Studio event reflects my thoughts on being in The Land as someone (mac tíre) severed from the security of family, making space for my trans and queer body, a soft indentation in the sea grass. bithchuimhne 🍃 i introduced some of this in my comic for the HOME anthology— to be embraced in kind means more than words alone can say.
with unfinished pieces, i at least have something to look forward to once i'm settled in.

at the same time, going back to the core feels almost criminal. does it ever not? níl cara ag cumha ach cuimhne. i'm furiously sad at the absence of the Palestinian students who were meant to be here, Mohammed and Nadin. we held a bonfire in honour as a small gesture of committment and memory, and i've been in touch with Mohammed a little, only when he's able to access rare internet connection. Ireland, to be fair, is hardly better— hiding behind selective, vicious, cowardly "neutrality" that somehow continue pandering to the same colonising forces Ireland prides itself on rejecting. but on the ground, coalitions of people are ever here for each other and will not stop coming out in droves against the odds. in that way, israel will lose, as will its guardian the US, as will each languishing oppressor in this conflict and the next. at this moment i can't offer much more than that, but i do believe in it. it's the only thing i've ever believed in. from the plough to the stars, from the river to the sea, saoirse don Phalaistín 🇮🇪🖤🇵🇸 and around the world.
#illustration#painting#traditional art#queer art#trans#queer#butch#not sapphic just brutal dykes#trans man#man not masc#superpose#sketch#artists on tumblr#☭#ireland#éire
118 notes
·
View notes
Text
All right, since I bombarded a poor mutual yesterday...
Privacy is not security and security is not privacy. These terms are not interchangeable, but they are intrinsically linked.
While we're at this, anonymity =/= security either. For example, Tor provides the former, but not necessarily the latter, hence using Https is always essential.
It is impossible to have privacy without security, but you can have security without privacy.
A case in point is administrators being able to view any data they want due to their full-access rights to a system. That being said, there are ethics and policies that usually prevent such behavior.
Some general tips:
Operating System: Switch to Linux. Ubuntu and Linux Mint are widely used for a reason. Fedora too. And don't worry! You can keep your current operating system, apps and data. If you're on a Mac computer, you can easily partition your hard drive or SSD by using Disk Utility. If you're on Windows, you can follow this guide.
You want to go a step further? Go with Whonix or Tails. They're Linux distributions as well, but they're both aiming for security, not beauty so the interface might not be ideal for everyone. Many political activists and journalists use them.
You want anonymity? Then you need to familiarize yourself with Tor. Also, Tor and HTTPS and Tor’s weaknesses. When you're using it, don't log in to sites like Google, Facebook, Twitter etc. and make sure to stay away from Java and Javascript, because those things make you traceable.
Alternatives for dealing with censorship? i2p and Freenet.
Is ^ too much? Welp. All right. Let's see. The first step is to degoogle.
Switch to a user-friendly browser like Firefox (or better yet LibreWolf), Brave or Vivaldi. There are plenty of hardened browsers, but they can be overwhelming for a beginner.
Get an ad blocker like Ublock Origin.
Search Engine? StartPage or Duckduckgo. SearXNG too. Like I said degoogle.
Get a PGP encrypted e-mail. Check Protonmail out.
There's also Tutamail that doesn't cover PGP, but uses hybrid encryption that avoids some of the cons of PGP.
Skiff mail is also a decent option.
Use an e-mail aliasing service such as SimpleLogin or AnonAddy.
Check OpenPGP out. Claws Mail is a good e-mail client for Windows and Linux, Thunderbird for Mac OS.
Gpg4win is free and easy to use for anyone that wants to encrypt/decrypt e-mails.
Instead of Whatsapp, Facebook messenger, Telegram etc. use Signal for your encrypted insant messaging, voice and video calls.
Get a metadata cleaner.
Get a firewall like Opensnitch, Portmaster or Netguard which can block Internet for trackers.
Alternatively, go with a private DNS that blocks these trackers. NextDNS is a good paid service. Rethink a good free option.
Replace as many of your applications as you can with FOSS (free and open source) ones. Alternativeto can help you.
Always have automatic updates on. They are annoying af, I know, but they are necessary.
Keep your distance from outdated software.
Always have two-factor authentication (2FA) enabled.
Do not use your administrator account for casual stuff. If you're on Linux, you probably know you can be sudo, but not root.
On Linux distributions use AppArmor, but stay away from random antivirus scanners. Other distributions default to SELinux, which is less suited to a beginner.
Never repeat your passwords. If you can't remember them all, use a password manager like KeePass.
Encrypt your drive.
Honestly, VPNs have their uses and ProtonVPN, Mullvad and Windscribe are decent, but eh. If you don't trust your ISP, why would you trust the VPN provider that claims they don't log you when you can't verify such a thing?
57 notes
·
View notes