#Load Balancing Router
Explore tagged Tumblr posts
Text
SMOAD Networks: Innovating Bangalore and Chennai's Connections
Having efficient connectivity is paramount for any business be it a startup located in a co-working space or a large enterprise with several branches across the country. It is a given that dependable internet infrastructure SMOAD Networks offers next-generation solutions in networking, and keeps its clients secure and connected throughout India.
Let’s see how SMOAD products and services are different in Bangalore and Chennai metro hubs that make them differentiators for other businesses.
Rural WiFi Router: No Boundaries Connectivity in Bangalore
Bangalore is known as the Silicon Valley of India. It's constantly buzzing with IT firms, Startups, remote work hubs, and everything else. In pop-up offices, retail chains, and low-volume field locations, traditional wired connections retention speed and flexibility.
Begin with WiFi SIM Routers Bangalore SMOAD. The router models offer exceptional 4G/ and 5G internet using SIM cards overlapped in a high speed broadband. Whether it’s a backup wirless internet connectivity or an emergency internet solution for temporary sites, SMOAD has it all:
• Broadband or simpler network connection access.
• Multiple slots for different service providers for further SIMs.
• Interruption-proof auto-functions or ‘always-on’ efficiency for unparalleled sustained productivity performance.
By rapidly deploying customizable SD-WAN plans, companies from basements in Bangalore to the cloud have unprecedented freedom.
Chennai SD-WAN Solutions: Next level sophisticated networking for your modern advertising agency or enterprise.
Digital transformation and Over The Top technologies (OTT) are reshaping the fabric of traditional businesses. Two core components and uses of WANs, the older siblings of LANs, are giving way to automation. Manufacturing, logistics, Information technologies Heavy payload services works center and SMOAD evolve infrastructure X technology to harness removal of grade switches.
SD-WAN - Software-Defined Wide Area Network automatically gets fed with tech dependent on multi connections certifying better performance for your resources like bandwidth, advanced security and access cables cables, trustable resource, and limbs of physical interdependencies of system needed for the entire network to work smoothly.
To further assist your experience, we have designed SMOAD SD-WAN modules in Chennai to:
• Guarantee the multi-dimensional intelligence of your network.
• Centralization of derailing management from multi suite control.
• Comply issues of end barriers to encryption with overuse guarantee.
This makes it simple for businesses with under budgeted workforces and mildly skillful IT personnel to keep the optimal hands-on and tech-enabled mission control operational uptime and experience guarantee.
Load balancing routers in Chennai: The Best in Reliability
For businesses like call centers, e-commerce websites, and cloud-dependent offices, networks must always be redundant and reliable. That is why SMOAD's Load Balancing Router in Chennai is so effective.
This technological innovation will combine and smartly shred traffic across multiple broadband connections to provide:
• Enhanced Speeds thanks to bandwidth aggregation:
• Automatic Failover for ISP outages
• VoIP and video conferencing without interruptions
Utilizing several ISPs and real time load balancing, SMOAD maintains smooth connectivity even during peak hours or downtimes from the provider.
Conclusion
Chennai's enterprise corridors are now more accessible to SMOAD Networks s. The tech hubs of Bangalore to the latter have sturdy, resilient internet connectivity courtesy of SMOAD Networks. Startups searching for prompt setup with SIM Based WiFi Router in Bangalore or enterprises looking for robust SD-WAN and Load Balancing Routers in Chennai can readily get serviced.
Contact Info:
Address : Old No 151, New No 312 9th Floor, Gee Gee Emerald, Nungambakkam, Chennai – 34.
Phone : 1800-419-5119
Email : [email protected]
#4g lte router with sim card slot in chennai#load balancing router#Multi 4g WAN Chennai#Office in a Box Solution Bangalore#5G SIM Router in Chennai
0 notes
Text
0 notes
Video
youtube
How to block Website and App in TP Link Load Balancer Router
0 notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
today has been such a good day 😭 it took forever to return my router to the wifi store, and i’ve got the worst headache + cramps combination i’ve had in a year, BUT:
tl;dr: so many good things have happened recently, and i’m trying to trust that sometimes good things happen and don’t have to be balanced out by horrible things. i’m so grateful for the good things that have happened, and i’m trying to acknowledge that i had a part in bringing them into reality
i got the keys to my new apartment, and it’s the nicest place i’ve ever lived. like i’m waiting for them to take my keys back and tell me it was a prank, obviously they’re not gonna let some WIC beans-and-rice, food stamps-raised, homeless in high school fuckhead live in such a beautiful building. but they are. they approved my cat, they’ve got my move-in fees, i’ve got the loading dock reserved for move-in day.
my new apartment isn’t infested with roaches. i cried just being in the space for the first time and feeling like. a real person. not like a shameful creature who can’t let their friends come over because of the infestation.
i got to see my best friend, the (platonic) love of my life. it’s not a rare occurrence for me to see her, since we live like 5 (soon 3!!!!) metro stops apart. and she came with me to see the apartment. she asked the questions i didn’t know to ask, and i was able to give her remote access to the building, which is as close as i can come to giving her a spare key
i got an incredible deal on a new bed. the mattress i have now has sunk in the middle and there are a few springs poking through, and it hurts so much to sleep on it. i was resigned to sleeping on my couch for a month or so while i saved to get a nice bed, because ive never had like a Nice Bed. and just idly checking wayfair, i saw a bed frame i loved that was at a $900 discount. nine hundred us dollars off. i never would’ve been able to get something like that if it was full price. and then i found a mattress that was well-reviewed and firm and also discounted. so now i’ll only be sleeping on my couch for like a week.
i was notified that they’re processing my upcoming promotion at work. it’s a $14.3k raise. that’s not a number that would ever have existed to me before, and now they’re processing it, and like. it’s real. that’s happening to me. they’re trusting me with a big like, mission-critical project and they’re increasing my pay and it’s because i earned the trust and the raise, not just because they felt bad for me???
i’m so overwhelmed. when i was a kid i thought all i could ever be was somebody’s wife and somebody’s mother. and now im neither of those things, and im loved and im safe and im finally moving out of this apartment full of shame into a place i can feel proud of.
#my therapist is gonna have a lot to hear from me on wednesday lmao#idk i’m a little overwhelmed#like a lot overwhelmed#like if u have never lived in poverty this probably won’t hit as hard as it does for me#but like. this is not a reality i could have envisioned as a kid#my mind was built around the idea that i get the leftovers because people feel bad for me#and i take whatever i can get with no space for being choosy#and now i get to be choosy? i get to curate a space the way i want instead of scraping together whatever i can find
4 notes
·
View notes
Text
How To Prevent Network Downtime

Network downtime refers to the period of time when a computer network or a specific network service is not available or functioning properly. It can occur due to various reasons such as hardware failures, software issues, network configuration problems, power outages, natural disasters, or human errors. Network downtime can significantly impact businesses and organisations, resulting in financial losses, decreased productivity, and customer dissatisfaction.
Preventing network downtime requires a proactive approach and implementation of various measures such as enterprise security solutions offered by an enterprise solutions provider or company that provides IT support services in Sri Lanka, to ensure network availability and minimise the risk of disruptions. Here are some strategies to help prevent network downtime:
Redundancy and failover: Implement redundant network components such as switches, routers, and internet connections. This setup allows for automatic failover to backup components if primary ones fail, ensuring continuous network operation.
Regular maintenance and updates: Perform routine maintenance activities such as patching, firmware updates, and hardware inspections. Keeping network equipment and software up to date helps address security vulnerabilities and improve overall stability.
Network monitoring: Utilise network monitoring tools to continuously monitor the health and performance of network devices, servers, and services. These tools can alert administrators about potential issues or abnormalities, enabling proactive troubleshooting and minimising downtime.
Load balancing: Distribute network traffic across multiple servers or network devices to prevent overloading and optimise resource utilisation. Load balancing ensures that no single component becomes a bottleneck and helps maintain network availability.
Backup and disaster recovery: Implement robust backup solutions for critical data and configurations. Regularly backup network configurations, server configurations, and data to offsite or cloud storage. Having a well-defined disaster recovery plan allows for rapid recovery in the event of a network outage or data loss.
Reducing single points of failure: Identify and eliminate single points of failure in the network architecture. This involves redundancy planning, using backup power supplies, employing diverse network paths, and implementing fault-tolerant systems.
Training and documentation: Provide training to network administrators and IT staff to enhance their knowledge and skills in managing network infrastructure. Develop and maintain detailed network documentation to ensure efficient troubleshooting and faster resolution of issues.
Security measures: Implement robust security measures such as firewalls, intrusion detection systems, and antivirus software to protect the network from cyber threats. Effective security practices reduce the likelihood of network breaches or malware infections that can cause network downtime.
Regular testing and simulation: Conduct regular network testing and simulation exercises to identify weaknesses and potential points of failure. By simulating various scenarios, you can evaluate the network's resilience and ensure it can withstand potential disruptions.
By implementing these preventive measures, organisations can minimise network downtime, improve network reliability, and provide uninterrupted services to their users or customers.
1 note
·
View note
Text
Why Is the E-Pro ACF-1 Fan a Must-Have for Modern Electronic Systems?

Introduction to the E-Pro ACF-1 Fa
In today's rapidly advancing world of electronics, ensuring optimal thermal management has become a top priority. The E-Pro ACF-1 Fan is designed with precision to address overheating challenges in complex electronic systems. This fan stands out as a reliable cooling solution that complements a wide range of components, from microcontrollers and microprocessors to contactors and switches. Whether used in laptops, industrial panels, or sensor-based setups, the ACF-1 Fan delivers a perfect balance between performance, efficiency, and durability.
What Makes the E-Pro ACF-1 Fan an Ideal Choice?
To begin with, the ACF-1 is engineered with high-quality materials that enable consistent airflow, keeping electronics cool and extending their life span. This fan plays an essential role in stabilising the thermal conditions of systems loaded with capacitors, LEDs, controllers, or thermal pads. Moreover, it is suitable for integration with advanced electronics requiring precision temperature control, such as embedded systems, automation units, and communication devices.
Furthermore, its compact form factor ensures compatibility with confined spaces, making it a perfect addition to modern hardware assemblies. From industrial machinery to everyday tech like laptops, this fan promotes system reliability while reducing maintenance needs.
Key Features of the E-Pro ACF-1 Fan
Delivers strong and stable airflow, supporting effective heat dissipation
Designed with low noise operation for minimal system disturbance
Compact and lightweight, ideal for various electronics and enclosures
Built using high-grade materials for long-term durability
Easy to install and compatible with standard connector types
Supports the efficient performance of thermal sensors and contactors
Can operate continuously without overheating

Benefits of Using the ACF-1 Fan in Electronic Assemblies
Helps maintain consistent temperatures, preventing damage to microprocessors and capacitors
Improves overall system longevity, especially in devices with limited ventilation
Protects delicate electronics, such as sensors and controllers, from thermal failure
Enhances safety by preventing overheating-related malfunctions
Supports energy-efficient operations by reducing the load on other cooling mechanisms
Reduces repair and replacement costs over time
Provides peace of mind in environments demanding high uptime
Applications Where the ACF-1 Fan Shines
Power Supply Units Helps regulate the temperature of components like fuses, switches, and transformers, ensuring uninterrupted power delivery.
Microcontroller-Based Systems Keeps microcontrollers and thermal-sensitive ICs stable, avoiding thermal throttling or damage.
Laptops and Desktop PCs Assists in cooling CPUs and GPUs, promoting longer operational life and better performance.
Industrial Control Panels Maintains cooling for electronics, contactors, and sensor modules housed in enclosed cabinets.
Communication Equipment Prevents overheating in routers, network switches, and data transmission units.
Test and Measurement Tools Cools down instruments such as digital multimeters and signal testers, keeping readings accurate.
Smart Home Devices Protects temperature-sensitive smart electronics, including automation hubs and IoT sensors.
Why Cooling Matters in Electronics
Cooling is a fundamental necessity in electronics because heat can drastically affect performance and safety. Thermal stress leads to degradation in sensitive components like capacitors, LEDs, and resistors. By maintaining an optimal temperature, the E-Pro ACF-1 Fan mitigates the risk of failure in systems incorporating cables, connectors, and printed circuit boards.
Additionally, devices with moving parts or power-hungry chips such as microprocessors can produce enough heat to cause premature failure if not properly cooled. With its efficient airflow and adaptability, this fan supports all such components without compromising space or performance.

Compatible Accessories That Enhance the ACF-1 Fan Setup
Thermal Pads and Compounds Improve heat transfer between surfaces for maximum cooling efficiency.
High-Grade Cables and Connectors Ensure uninterrupted power delivery and stable electrical connections to the fan.
Protective Grips and Guards Prevent accidental contact while allowing optimal airflow through the fan blades.
Safety Devices Like Fuses and Circuit Breakers Work in tandem with the fan to shut down the system during abnormal thermal events.
Temperature Sensors and Controllers Allow automatic fan operation based on real-time system temperature.
Mounting Tools and Screws Help in securely fixing the fan inside tight electronic enclosures.
Final Thoughts on Choosing the E-Pro ACF-1 Fan
When selecting a cooling component for electronics, reliability and compatibility are crucial. The E-Pro ACF-1 Fan provides both. Its flexible design, superior airflow, and proven durability make it a go-to choice for professionals and hobbyists alike. Whether you’re building a new project involving sensors and switches or upgrading an old system with fuses and microcontrollers, this fan ensures everything stays within safe temperature ranges.
From thermal control to enhanced safety, the E-Pro ACF-1 Fan is not just a component—it’s a core part of your electronic system’s long-term success.
0 notes
Text
DNS over HTTPS ve FF/klonech
Proč: Protože O2 manipuluje s DNS ve snaze dodávat takzvaně „zabezpečené připojení“, čili cokoliv, co se jim nelíbí, přesměrují spoofovanou DNS odpovědí na vlastní server, kde (v rámci TLS) nesedí certifikát (naštěstí, MitM jim zatím nejde, bo nedrží v rukou žádnou CA) a když to akceptujete, sdělí vám toliko, že „vstupujete na škodlivý obsah“…a „škodlivé“ je málem cokoliv, protože jejich bezpečák je evidentně nějaký copyrightů dbalý aktivně zapojený český nácek. Takhle rozhrabaná DNS představuje nemalé bezpečnostní riziko.
Proč DNS over HTTPS: když by stačilo jen použít jiný DNS server. No, zatím by asi stačilo, ale je jen otázkou času, než přesměrují všechny odchozí UDP spojení na svůj DNS server. Problém je v tom, že VY nezjistíte že tohle udělali do momentu, než to něco viditelně rozbije, což už může být pozdě. TLS pro ně zatím představuje překážku, čili DNS over HTTPS je v tomto případě dostatečně spolehlivé řešení. A jelikož je to v prohlížečích implementováno, je to současně dostatečně jednoduché řešení…ovšem řeší to jen ten prohlížeč pochopitelně.
Volba DNS over HTTPS poskytovatele: Já jsem se rozhodla pro Quad9. Je to bohužel švýcarská společnost, já na tu zemi nemám obecně dobrý názor, avšak cokoliv je lepší než nesvatá trojice USA, Čína, Sajuz a ono si upřímně řečeno není moc z čeho vybírat. Blbé je, že tato společnost poskytuje i určitou filtraci DNS, nicméně volbou DNS over HTTPS serveru si současně volíte i tuto filtraci, přičemž poskytují i kompletně nefiltrovanou službu (moje volba). Je to celé vysvětlené na https://quad9.net/service/service-addresses-and-features/
Nastavení: Pokud vstoupíte do nastavení od firefoxu a necháte hledat DNS, najdete příslušná nastavení. Zde máte jako default Cloudflare (což je z deště pod okap), ale je tu možnost zadat Custom nastavení. Sem zadáte https://dns10.quad9.net/dns-query a vřele doporučuji zapnout režim výhradního DNS over HTTPS. Minimálně pro začátek, protože potřebujete vyzkoušet že vám to funguje, čili potřebujete dostat chybové hlášení když to nefunguje.
Nojo, jenže DNS překládá názvy serverů na IP adresy, jak se tedy najde IP adresa serveru dns10.quad9.net?
No systémovým resolverem pochopitelně, což je všechno, jen ne bezpečné. Přesněji řečeno, pokud se provider rozhodne pro něco nečestného, mělo by si to vylámat zuby na TLS, ale to je jediná vrstva, přičemž pokud provider opravdu hodne rozbije DNS, pak vám to DoH (DNS over HTTPS) znefunkční…čímž vzniká prostor, že ho vypnete a padáte do těch všech radostí s rozhrabanou DNS. Vy zadáváte jméno DoH serveru, protože tohle se použije na validaci TLS certifikátu, ale současně potřebujete jeho IP. Nejsnadnějším způsobem by tedy bylo nacpat pár adresa-server do /etc/hosts. Nicméně implementace DoH ve Firekryse tohle dokáže řešit po vlastní ose…ovšem musíte do about:config.
Výchozí IP adresu vašeho DoH serveru zadáváte jako řetězec s klíčem network.trr.bootstrapAddr a v mém případě to muselo být 149.112.112.10, adresa 9.9.9.10 nefungovala a já se obávám, že v tomhle má opět prsty kyslík. Teoreticky můžete zadat IPv6, ale protože Kaon, router, který kyslík svým zákazníkům vnucuje, má občas záchvaty, které znefunkční IPv6, rozhodla jsem se pro řešení s IPv4. Tímto nastavením kompletně obejdete DNS vašeho providera, podotýkám, že pouze v tom jednom konkrétním prohlížeči, ale ono tohle zatím většinou stačí.
Další DoH servery najdete na https://github.com/curl/curl/wiki/DNS-over-HTTPS Příliš jsem ho nezkoumala, takže možná DoH server v budoucnu změním, potřebovala jsem rychlé řešení problému. Pokud nemusíte jednat ve spěchu, asi dává smysl ten seznam důkladněji prozkoumat.
Edit: Nakonec jsem namísto Quad9 zkusila belnet. Rychlejší odezva. Ovšem zjistila jsem další věc, některé služby se začaly chovat jinak. Myslela jsem si, že konkrétní obsah je závislý spíše od zdrojové IP a že load balancing se dělá na úrovni routingu, ale vypadá to, že některé služby (google například) řeší tyto věci na úrovni DNS, takže kupříkladu trubka nyni tahá data z belgie namísto toho, aby tahala z lokálního googlu přes český nix. No z tohoto pánové z kyslíku nebudou mít radost, bo samozřejmě tier1 routing stojí víc peněz než přímá lajna potažmo nix. No ale byli to oni kdo si tímhle načůral do bot, kdyby nedělali nesmysly a nerozhrabávali DNS, nikdy bych se nějakým DNS over HTTPS nezabývala. BTW uvidím, jaký to bude mít vliv na spolehlivost. Každopádně volbou toho serveru jde viditelně leccos ovlivnit.
0 notes
Text
Wi-Fi Mesh và tối ưu hóa băng thông
Một trong những thách thức lớn nhất của mạng Wi-Fi truyền thống là việc phân phối băng thông không đồng đều, dẫn đến tình trạng tắc nghẽn ở các khu vực xa router. Hệ thống Wi-Fi Mesh giải quyết vấn đề này hiệu quả bằng cách tối ưu hóa việc phân bổ băng thông. Các nút trong mạng Mesh có thể tự động cân bằng tải (load balancing) giữa các điểm truy cập, đảm bảo rằng không có một nút nào bị quá tải trong khi các nút khác lại nhàn rỗi. Điều này đặc biệt hữu ích trong các môi trường có nhiều thiết bị truy cập đồng thời hoặc khi có nhu cầu truyền tải dữ liệu lớn như xem phim 4K, chơi game trực tuyến, hay họp video chất lượng cao, mang lại trải nghiệm mượt mà và ổn định cho mọi người dùng.
Tham khảo: https://viettuans.vn/bo-phat-wifi

0 notes
Text
Software-Defined Networking (SDN) Market Overview: Trends Transforming Network Management
In 2025, the Software-Defined Networking (SDN) market stands at the forefront of revolutionizing global network infrastructure. SDN separates the network's control plane from the data plane, allowing administrators to programmatically control network behavior through software applications. As organizations increasingly adopt virtualization, automation, and cloud computing, SDN has emerged as a key enabler of agility, scalability, and cost-efficiency in network management.

Understanding Software-Defined Networking (SDN)
SDN is an architectural approach that enables centralized management and dynamic control over networking resources. It consists of three main components:
Application Layer: Hosts network applications and services such as firewalls, load balancers, and analytics tools.
Control Layer: Contains the SDN controller, which serves as the brain of the network, communicating with both applications and hardware devices.
Infrastructure Layer: Includes physical and virtual switches, routers, and other devices responsible for forwarding traffic.
By abstracting the control logic, SDN allows operators to adapt network behavior quickly, simplify configuration tasks, and introduce new services without major hardware investments.
Key Trends Transforming Network Management through SDN
1. Growing Demand for Network Automation
One of the most significant trends is the rising demand for automated network operations. SDN allows for centralized policy management and real-time automation, reducing the reliance on manual configuration. This leads to faster service deployment, lower operational costs, and minimized human error.
2. Integration with Cloud and Edge Computing
As hybrid and multi-cloud environments become mainstream, SDN enables seamless connectivity across distributed data centers and edge locations. Dynamic routing, traffic engineering, and security policy enforcement can be managed centrally, ensuring consistent performance and compliance in decentralized infrastructures.
3. Increased Focus on Network Security
Security has become a top priority as cyberattacks grow in complexity. SDN contributes by enabling micro-segmentation, granular access control, and traffic monitoring. Centralized control makes it easier to detect anomalies, implement policy-based security, and isolate threats in real-time.
4. Support for 5G and IoT Deployments
The rollout of 5G and the proliferation of Internet of Things (IoT) devices require flexible, programmable networks. SDN is essential in handling the increased data volumes and diverse traffic patterns. It allows network slicing, dynamic bandwidth allocation, and efficient device management—critical for future-ready telecom infrastructure.
5. Emergence of Intent-Based Networking (IBN)
IBN extends the capabilities of SDN by allowing administrators to express business intent (e.g., ensure application availability) and have the network automatically configure itself to meet that intent. This trend enhances user experience and system reliability by aligning network behavior with organizational goals.
Market Drivers Accelerating SDN Adoption
Cost Reduction: SDN eliminates the need for expensive proprietary hardware and reduces operational expenditures through automation.
Scalability and Flexibility: Businesses can rapidly scale their networks to meet evolving demands without major infrastructure overhauls.
Digital Transformation Initiatives: Enterprises across sectors are rearchitecting their IT systems, and SDN provides the foundation for agile, service-oriented networks.
Vendor-Neutral Ecosystem: The SDN framework promotes open standards, enabling interoperability between devices and reducing vendor lock-in.
Challenges Facing the SDN Market
Despite its advantages, SDN adoption comes with challenges:
Integration Complexity: Transitioning from legacy infrastructure to SDN involves significant planning, training, and system compatibility efforts.
Security Risks: While SDN enhances security, centralizing control can create a single point of failure if not properly secured.
Skills Gap: Organizations may struggle to find professionals with expertise in SDN architecture, deployment, and orchestration.
Regional Market Outlook
North America leads in SDN adoption, driven by strong demand in telecom, IT, and data center industries.
Europe shows significant growth due to supportive policies, digitalization initiatives, and enterprise investments.
Asia-Pacific is expected to witness the fastest growth, fueled by digital infrastructure projects in China, India, and Southeast Asia.
Future Outlook
Between 2025 and 2030, the SDN market is expected to grow significantly due to:
Accelerated deployment of 5G networks
Expansion of hyperscale data centers
Increasing adoption of cloud-native and AI-driven applications
Government initiatives supporting digital infrastructure modernization
Conclusion
The Software-Defined Networking (SDN) market is reshaping how organizations manage, secure, and scale their networks. As businesses strive for agility, resilience, and performance, SDN offers a strategic pathway to modern network management. With continued innovation and investment, SDN will remain a cornerstone of digital transformation in the years to come.
0 notes
Text
Tips for Maintaining Your AMB High-Speed Milling Motor
When it comes to precision PCB prototyping and small-scale manufacturing, the AMB high-speed milling motor is a top choice for designers and engineers. Known for its compact size, powerful performance, and high RPM capabilities, it’s ideal for milling fine traces, routing outlines, and drilling vias on copper clad laminates. However, like any high-precision tool, proper maintenance is essential to ensure long-lasting performance and avoid costly downtime.
In this blog, we’ll explore practical ways to extend the life of your AMB spindle motor, including best practices for cleaning, lubrication, bit handling, and operational care. Whether you're using carbide PCB drill bits or diamond-cut routers, these tips will help keep your spindle running like new.
Why Spindle Maintenance Matters
The spindle motor is the heart of your milling setup. It directly affects:
Cutting accuracy
Bit longevity
Surface finish
Machine noise and vibration
Overall production efficiency
A neglected spindle can overheat, lose precision, or fail entirely—resulting in expensive repairs or replacements. Regular care ensures your investment in equipment and tooling continues to deliver consistent, professional results.
1. Use the Right Tools for the Job
Your carbide PCB drill bits, end mills, and router bits must be compatible with the spindle’s RPM range and collet size. AMB motors typically operate at 5,000–25,000+ RPM, so only high-quality, balanced tools should be used.
Tips:
Use solid carbide bits for milling copper clad laminates, as they resist wear and minimize vibration.
Avoid using dull or chipped bits, which can create uneven loads and damage the motor’s bearings.
Choose tool lengths appropriate for your application—shorter bits generate less flex and are more stable at high speeds.
2. Keep the Spindle Clean
Dust and debris are your spindle’s worst enemies. Milling FR4 copper clad laminates produces fine fiberglass dust that can infiltrate the motor and bearings, causing long-term wear and overheating.
Maintenance Checklist:
Clean after every session: Use compressed air (gently) to blow out dust from the air vents and motor casing.
Wipe external surfaces: A microfiber cloth and isopropyl alcohol can remove buildup.
Inspect collet and nut: Clean regularly to ensure smooth tool changes and optimal grip.
Avoid using a vacuum directly on the spindle unless it has ESD protection and filtered airflow.
3. Lubricate Bearings—If Applicable
Some AMB spindle models come with sealed bearings, which are maintenance-free. However, if your model has accessible bearings, periodic lubrication may be required.
Guidelines:
Use manufacturer-recommended grease or oil.
Apply in small amounts—over-lubricating can attract dust.
Follow the service interval specified in the user manual.
If you're unsure whether your spindle requires lubrication, check your model number and consult AMB's documentation or support team.
4. Watch Your Feed and Speed
Running your spindle too fast or too slow with the wrong feed rate can strain the motor and reduce its life. Incorrect settings may also cause bit breakage, rough cuts, or overheating.
Best Practices:
Match RPM to bit size – Smaller diameter tools need higher RPMs.
Adjust feed rate for material – Softer materials need faster feeds; hard laminates like FR4 require slower, controlled passes.
Avoid stalling – Never force the tool through the material. Let the bit and spindle do the work.
Use tool manufacturers’ feed/speed charts as a baseline, and tweak settings based on results.
5. Check and Replace Collets Regularly
The collet is responsible for holding your tool securely in place. A worn or dirty collet can lead to tool slippage, vibration, or uneven cuts—all of which can strain the spindle bearings.
Inspection Tips:
Look for wear lines or discoloration.
Ensure the collet grips the bit evenly.
Replace the collet after 400–600 tool changes, or if you notice reduced performance.
Using proper torque when tightening the collet nut will also prevent undue stress on the motor shaft.
6. Avoid Overheating
High-speed milling can generate a lot of heat—especially when cutting copper clad laminates continuously. Excessive heat can degrade insulation, weaken adhesives, and shorten spindle life.
Heat Management Tips:
Take breaks between long jobs to allow the spindle to cool.
Ensure adequate airflow around the motor housing.
Consider using a cooling fan or air-assisted spindle mount if available.
Monitoring temperature during extended use is a good habit. If the spindle becomes too hot to touch, it’s time to pause and cool down.
7. Store and Handle with Care
When not in use, your AMB spindle should be stored in a clean, dry location. Protect it from dust, moisture, and accidental knocks.
Storage Tips:
Cover the motor or place it in a padded case.
Avoid laying it down on the collet or motor shaft.
Label tools and accessories to prevent mix-ups with incompatible equipment.
Proper storage prevents accidental damage and prolongs tool and motor life.
Final Thoughts
Your AMB high-speed milling motor is a precision tool designed to deliver outstanding results—but only if it’s treated with care. By following these maintenance and operation tips, you can dramatically extend spindle life, improve cutting accuracy, and reduce tool wear.
From keeping your collets clean to using premium carbide PCB drill bits and protecting your spindle from FR4 dust, each step contributes to smoother operation and long-term reliability.At Midwest Circuit Technology, we specialize in providing the tools and knowledge you need for successful PCB prototyping. Explore our full line of copper clad laminates, carbide bits, and spindle-compatible accessories designed to keep your workflow smooth and efficient.
0 notes
Text
SMOAD SD-WAN Solutions: The Future of Networking
In today's digital world, businesses rely on their networks more than ever before. But with the increasing complexity of networks and the growing threat of cyberattacks, traditional networking solutions are no longer enough.
That's where SMOAD SD-WAN Solutions come in. SMOAD SD-WAN is a next-generation networking solution that provides businesses with the performance, security, and scalability they need to thrive in the digital age.
#Sim Card Internet Router#Sd Wan Solutions#Network Routers#Remote Connectivity#Load Balancing Router#4g Sim Router#4g Lte Router
0 notes
Text
AI In Networks Market Driven by Network Automation

The AI In Networks Market is transforming the way network operators manage data traffic, optimize performance, and secure communications by embedding artificial intelligence into core network functions. AI-powered routers, switches, and software-defined networking solutions offer real-time anomaly detection, predictive traffic shaping, and automated fault resolution—driving improved network reliability and reduced operational costs. As enterprises and service providers grapple with explosive data growth, the ability to harness machine learning algorithms for intelligent packet routing and adaptive load balancing creates significant market opportunities.
The integration of AI-driven analytics also enhances network security by identifying threats before they impact service quality. Ongoing advances in deep learning and edge computing are expanding the scope of network automation, enabling dynamic resource allocation and seamless scalability. Vendors are leveraging these market insights to refine their product portfolios and forge strategic partnerships, fueling competitive AI In Networks Market growth.
The Global AI In Networks Market is estimated to be valued at USD 13.33 Bn in 2025 and is expected to reach USD 37.45 Bn by 2032, growing at a compound annual growth rate (CAGR) of 15.9% from 2025 to 2032. Key Takeaways
Key players operating in the AI In Networks Market are:
-Arista Networks, Inc.
-Broadcom
-Cisco Systems, Inc.
-Huawei Technologies Co., Ltd.
-Nokia
These market companies are investing heavily in AI-enabled hardware chassis and software suites to gain industry share and reinforce their market position. Through joint ventures and acquisitions, they strengthen their business growth strategies, expand R&D capabilities, and enhance service portfolios. Their continuous innovation in programmable network architecture is pivotal to capturing increased market revenue.
‣ Get More Insights On: AI In Networks Market
‣ Get this Report in Japanese Language: ネットワーク市場におけるAI
‣ Get this Report in Korean Language: 네트워크시장의AI
0 notes
Video
youtube
TRENDNET TWG 431BR Multi WAN Load Balancer Router login and Setup | Fail...
0 notes
Text
Network Security Service Provider in Pune | Teleglobal

Cyber threats evolve at an unprecedented pace, securing your business’s network infrastructure is no longer optional—it’s a necessity. Teleglobals, a trusted enterprise IT solutions provider with a presence in India, the US, Europe, and the Middle East, offers cutting-edge network security services to safeguard your digital assets. With over 900 satisfied clients and partnerships with industry leaders like Cisco, Fortinet, and AWS, Teleglobals delivers comprehensive, tailored solutions to ensure your network remains secure, resilient, and efficient.
Schedule a free network security assessment: https://telelgobals.com/cloud-infrastructure-assessment
Why Network Security Matters in 2025
The digital landscape is fraught with risks, from ransomware to sophisticated phishing attacks. In 2024 alone, cybercrime losses in the US reached $16.6 billion, a 33% increase from the previous year. Businesses face not only financial losses but also reputational damage and operational disruptions. Teleglobals’ network security services address these challenges by providing end-to-end solutions, from strategic planning to continuous monitoring, ensuring your network is a robust asset rather than a vulnerability.
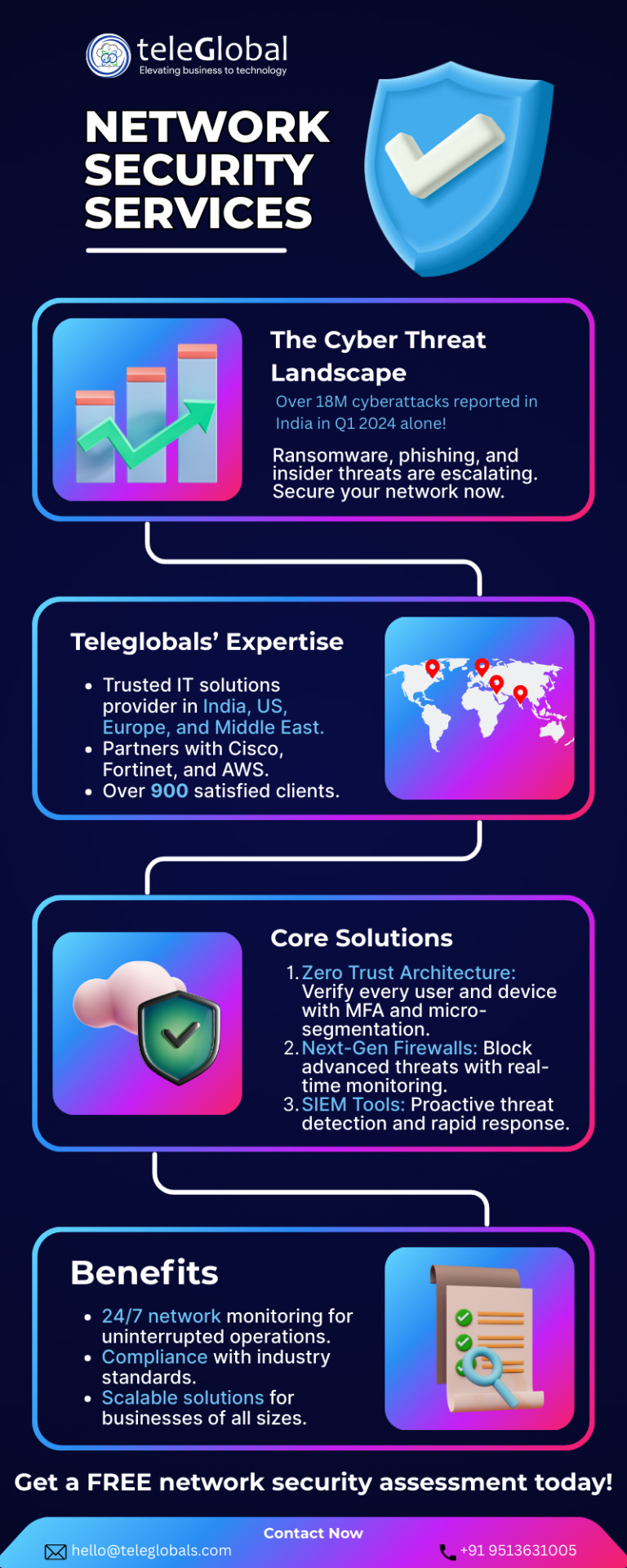
Comprehensive Network Security Solutions
Teleglobals excels in configuring and optimizing network devices such as routers, switches, firewalls, and load balancers to meet your specific business needs. Their experts use advanced tools and real-time analysis to monitor networks proactively, identifying potential issues before they escalate. This approach ensures uninterrupted connectivity and peak performance, allowing you to focus on core business objectives without worrying about cyber threats.
A cornerstone of their strategy is the adoption of Zero Trust Architecture (ZTA), a modern security framework that verifies every user and device attempting to access your network. By implementing multi-factor authentication (MFA) and micro-segmentation, Teleglobals limits access to sensitive data, reducing the risk of unauthorized breaches. Additionally, their services include next-generation firewalls with intrusion prevention and deep packet inspection, ensuring robust defense against advanced threats.
Tailored and Proactive Protection
What sets Teleglobals apart is their commitment to customized solutions. They assess your current IT landscape, align security measures with your business goals, and integrate cutting-edge technologies like AI and machine learning for real-time threat detection. Their partnerships with industry giants like Fortinet and Microsoft enable them to deliver scalable, future-proof solutions.
Teleglobals also emphasizes employee training to mitigate human error, a significant cybersecurity risk. Through regular workshops and phishing simulations, they empower your workforce to recognize and respond to threats effectively. This holistic approach combines technology and education to create a resilient security posture.
Why Choose Teleglobals?
With a proven track record across diverse industries, Teleglobals offers reliable, innovative network security services. Their global presence and 24/7 support ensure your business remains protected around the clock. By choosing Teleglobals, you gain a strategic partner dedicated to enhancing your cybersecurity, compliance, and operational efficiency.
Ready to secure your network? Contact Teleglobals at [email protected] or visit teleglobals.com for a consultation today.
#network security services#network security#cybersecurity#cyber security#teleglobalinternational#cloud service providers#cloud consulting services
0 notes