#Nagios Server Tutorial
Explore tagged Tumblr posts
Text
From Zero to Hero: A Beginner's Journey into Nagios Monitoring

Are you new to system monitoring and looking to understand how to keep your IT infrastructure running smoothly? Nagios, a powerful tool, can help you achieve just that. This beginner's tutorial will guide you through the basics of setting up and using Nagios effectively.
What is Nagios?
Nagios is an open-source software application that monitors systems, networks, and infrastructure components. It provides insights into the health and performance of your IT environment by continuously checking specified parameters.
Getting Started
Installation: Begin by installing Nagios on your server. Follow the installation instructions for your operating system, ensuring all prerequisites are met.
Configuration: After installation, configure Nagios to monitor your devices and services. This involves defining hosts (servers, routers, switches) and services (CPU usage, disk space, HTTP response).
Monitoring: Once configured, Nagios will start monitoring your infrastructure. It will alert you when issues arise, such as high CPU usage or a server outage, helping you address problems proactively.
Tips for Effective Monitoring
Regular Checks: Set up regular checks to monitor critical aspects of your infrastructure.
Alerting: Configure alert notifications to promptly respond to issues.
Dashboard: Use Nagios' dashboard to visualize data and trends for better decision-making.
Conclusion
By mastering Nagios basics, you can ensure your IT systems operate smoothly and minimize downtime. Ready to get started? Check out this Nagios tutorial for beginners for detailed steps and examples.
Learning to monitor effectively with Nagios is a valuable skill that enhances IT operations and keeps your business running smoothly.
0 notes
Link

#Nagios#Nagios XI#Nagios XI Server#Start#Stop#Restart#How to start Nagios XI Server#How to stop Nagios XI Server#Nagios Server Guide#Nagios Server Tutorial#DevOps#DevOps Tool#scmGalaxy
9 notes
·
View notes
Link

#Nagios#Nagios XI#Nagios XI Server#Start#Stop#Restart#How to start Nagios XI Server#How to stop Nagios XI Server#Nagios Server Guide#Nagios Server Tutorial#DevOps#DevOps Tool#scmGalaxy
0 notes
Link

#Nagios#Nagios XI#Nagios XI Server#Start#Stop#Restart#How to start Nagios XI Server#How to stop Nagios XI Server#Nagios Server Guide#Nagios Server Tutorial#DevOps#DevOps Tool#scmGalaxy
0 notes
Link

#Nagios#Nagios XI#Nagios XI Server#Stop#Restart#How to start Nagios XI Server#How to stop Nagios XI Server#Nagios Server Guide#Nagios Server Tutorial#DevOps#devops tool#scmGalaxy
0 notes
Text
Open source network bandwidth monitoring tool

#Open source network bandwidth monitoring tool how to#
#Open source network bandwidth monitoring tool software#
#Open source network bandwidth monitoring tool free#
This comprises the capability to create custom scripts for data gathering along with the facility for SNMP polling. The tool utilizes data gathering functionality and network polling to collect information on various devices on networks of any scope. CactiĬacti is an open-source network monitoring tool built on RRD Tool’s data classification and plotting system. There exist a few Icinga modules for very specific monitoring capabilities, like monitoring for VMWare’s vSphere cloud environment and business process modeling. The tool is scalable and easily configurable to function with each type of device. Through a web interface, your business can observe applications and hosts around your complete network infrastructure. Icinga is an open-source network monitoring tool that calculates the availability and performance of the network. It supports all the popular Operating Systems like Windows, Linux, etc. Its monitoring does not require a separate workflow. By means of a single platform, you can monitor services, applications, servers, and reports on business KPIs. Sensu is indorsed as a full-stack monitoring tool. It is an apt monitoring tool for highly distributed scalable systems. It is designed to handle millions of even per second with low latency. It’s a low latency even processing system capable of collecting metrics from a variety of distributed systems. Riemann is an ideal open source monitoring tool for distributed systems. It can monitor a variety of components including Oss, applications, websites, middlewares, web servers, etc. Considering the length of time that Nagios has been in the industry, there are plenty of plugins written for it. It provides numerous facilities like integration with third-party apps using an additional plugin. Nagios is an open-source monitoring tool that has been in the market since 1999. It is a centralized system that stores the data in a relational DB for efficient processing.
#Open source network bandwidth monitoring tool software#
Zabbix is open-source monitoring software with an easy-to-use interface for users with a low learning curve that provides enterprise-class solutions to large organizations.
#Open source network bandwidth monitoring tool how to#
Tutorial: How To Install and Configure Prometheus 2. Grafana is one of the best open-source monitoring dashboards. Also, it has very good integration with tools like Grafana for visualizing metrics. Prometheus can collect system metrics, application metrics, and metrics from modern containerized applications. It handles alerting for all alerting rules configured in Prometheus. The alert manager is another component of Prometheus. The PromQL system analyzes data and permits the program to produce plots, tables, and other graphics on the systems it monitors. It is able to assemble several metrics on servers, kubernetes, and various devices using SNMP pings and inspect network bandwidth usage from the device point of view, along with the other functions. It is an ideal monitoring setup for containerized environments like kubernetes and the best open-source server monitoring tool. It enables users to set up monitoring capabilities by utilizing the in-built toolset. Prometheus is an open-source monitoring solution primarily fixated on data gathering and analysis based on time-series data. Let’s take a look at the top-rated open-source monitoring tools and see what works for you! 1.
#Open source network bandwidth monitoring tool free#
Numerous absolutely free and open-source network monitoring tools can be considered while looking for monitoring solutions. Support all modern cloud and containerized applications.Able to provide long-term insights for better capacity planning.Collect system/application metrics in real-time.Able to handle and process huge amounts of monitoring data.Detect service outages and unauthorized activities.Provide indicators on outages and service degradation.Professional or Business-grade tech solutions are generally regarded as costly, but that’s not necessarily always the case.įollowing is the key list of key indicators for the best monitoring software. What are the Best Opensource Monitoring Tools? Cloud Infrastructure monitoring (Public & Private).Container Monitoring ( Docker/ Kubernetes/Mesos etc.).All modern cloud and on-premise infrastructure come with the best monitoring solutions.Īlso, when it comes to DevOps, monitoring, and observability plays a key role in the team’s performance.įollowing are the key areas when it comes to monitoring. Regardless of the company’s size, one cannot ignore the need for Server, network, and infrastructure monitoring using the best monitoring tool. Monitoring various aspects of the IT infrastructure can be quite pesky and cause many difficulties if not done properly. Monitoring is necessary for businesses to make sure that the required system is up and working.

0 notes
Photo

Hadoop Big data Training at RM Infotech Laxmi Nagar Delhi NCR
History:
In 2006, the hadoop project was founded by Doug Cutting, It is an open source implementations of internal systems which is now being used to manage and process massive data(s) volumes. In short,
With Hadoop , a large amount of data of all varieties is continually stored and added multiple processing and analytics frameworks rather than moving the data(s) because moving data is typical and very expensive.
What are the career prospects in Hadoop?
Do you know that in next 3 years more than half of the data in this world will move to Hadoop? No wonder McKinsey Global Institute estimates shortage of 1.7 million Big Data professionals over next 3 years.
Hadoop Market is expected to reach $99.31B by 2022 at a CAGR of 42.1% -Forbes
Average Salary of Big Data Hadoop Developers is $135k (Indeed.com salary data)
According to experts – India alone will face a shortage of close to 2 Lac Data Scientists. Experts predict, a significant gap in job openings and professionals with expertise in big data skills. Thus, this is the right time for IT professionals to make the most of this opportunity by sharpening their big data skill set.
Who should take this course?
This course is designed for anyone who:-
wants to get into a career in Big Data
wants to analyse large amounts of unstructured data
wants to architect a big data project using Hadoop and its eco system components
Why from RM Infotech
100% Practical and Job Oriented
Experienced Training having 8+ yrs of Industry Expertise in Big Data.
Learn how to analyze large amounts of data to bring out insights
Relevant examples and cases make the learning more effective and easier
Gain hands-on knowledge through the problem solving based approach of the course along with working on a project at the end of the course
Placement Assistance
Training Certificate
Course Contents
Lectures 30 X 2 hrs. (60 hrs) Weekends. Video 13 Hours Skill level all level Languages English Includes Lifetime access Money back guarantee! Certificate of Completion * Hadoop Distributed File System * Hadoop Architecture * MapReduce & HDFS * Hadoop Eco Systems * Introduction to Pig * Introduction to Hive * Introduction to HBase * Other eco system Map * Hadoop Developer * Moving the Data into Hadoop * Moving The Data out from Hadoop * Reading and Writing the files in HDFS using java * The Hadoop Java API for MapReduce o Mapper Class o Reducer Class o Driver Class * Writing Basic MapReduce Program In java * Understanding the MapReduce Internal Components * Hbase MapReduce Program * Hive Overview * Working with Hive * Pig Overview * Working with Pig * Sqoop Overview * Moving the Data from RDBMS to Hadoop * Moving the Data from RDBMS to Hbase * Moving the Data from RDBMS to Hive * Market Basket Algorithms * Big Data Overview * Flume Overview * Moving The Data from Web server Into Hadoop * Real Time Example in Hadoop * Apache Log viewer Analysis * Introduction In Hadoop and Hadoop Related Eco System. * Choosing Hardware For Hadoop Cluster nodes * Apache Hadoop Installation o Standalone Mode o Pseudo Distributed Mode o Fully Distributed Mode * Installing Hadoop Eco System and Integrate With Hadoop o Zookeeper Installation o Hbase Installation o Hive Installation o Pig Installation o Sqoop Installation o Installing Mahout * Horton Works Installation * Cloudera Installation * Hadoop Commands usage * Import the data in HDFS * Sample Hadoop Examples (Word count program and Population problem) * Monitoring The Hadoop Cluster o Monitoring Hadoop Cluster with Ganglia o Monitoring Hadoop Cluster with Nagios o Monitoring Hadoop Cluster with JMX * Hadoop Configuration management Tool * Hadoop Benchmarking 1. PDF Files + Hadoop e Books 2. Life time access to videos tutorials 3. Sample Resumes 4. Interview Questions 5. Complete Module & Frameworks Code
Hadoop Training Syllabus
Other materials provided along with the training
* 13 YEARS OF INDUSTRY EXPERIENCE * 9 YEARS OF EXPERIENCE IN ONLINE AND CLASSROOM TRAINING
ABOUT THE TRAINER
Duration of Training
Duration of Training will be 12 Weeks (Weekends) Saturday and Sunday 3 hrs.
Course Fee
Course Fee in 15,000/- (7,500/- X 2 installments) 2 Classes are Free as Demo. 100% Money back Guarantee if not satisfied with Training. Course Fee includes Study Materials, Videos, Software support, Lab, Tution Fee.
Batch Size
Maximum 5 candidates in a single batch.
Contact Us
To schedule Free Demo Kindly Contact :-
Parag Saxena.
RM Infotech Pvt Ltd,
332 A, Gali no - 6, West Guru Angad Nagar,
Laxmi Nagar, Delhi - 110092.
Mobile : 9810926239.
website : http://www.rminfotechsolutions.com/javamain/hadoop.html
#hadoop big data training#Hadoop Big data Training in Delhi#Hadoop Big data Training in Laxmi Nagar#Hadoop Course Content#Hadoop Course Fees in Delhi#Hadoop Jobs in Delhi#Hadoop Projects in Delhi
3 notes
·
View notes
Link
Social Engineering for Absolute Beginners (no coding!) ##UdemyFrancais ##UdemyFreeCoupon #Absolute #Beginners #Coding #Engineering #Social Social Engineering for Absolute Beginners (no coding!) This course will teach you the most common social engineering threats. At the end of the course you will understand why people are the weakest link in your organisations security posture. You will understand: 1) what the most common social engineering threats and are, 2) the impact per threat for your business, 3) how these threats can be executed and / or mitigated. You will able to understand the above-mentioned points without having to understand technical stuff (e.g. source code) within ONE HOUR! How is that possible? Social engineering is closely related to psychology. Social engineering can be defined as the art of manipulating people in order to achieve a goal. Therefore, this course is created for managers rather than developers. Managers must train their employees to strengthen their personal firewall (i.e. being less likely to fall victim to manipulation), because collectively all employees make up your organisation's firewall! So, after following this course am I a full-fledged security expert? No. This course will teach you the most common social engineering threats so that you can critically question and discuss the impact of these security issues with your employees and management. What!?! Why should I enroll? Only enroll when you want to strengthen your personal firewall, are new social engineering and want a complete beginners’ perspective. This course is specifically developed for: - (Project) managers that lead in an organisation that depends on IT and have no clue how social engineering could harm their organisation; - Security managers tasked to deliver basic security awareness training;- Anyone interested in the basics of social engineering, explained in layman’s terms Ok, but there is already a lot of information on available on the web. So, what’s in it for me? I thought you would never ask! This course differentiate itself from existing available information because: - this course is not solely based on my opinion, but substantiated with scientific evidence. This means you not only get my opinion and experience but it is also backed by science; - I've included lots of links to websites that provide comprehensive background information, should you be interested in more detail; - That's not it, there is more... BONUS Material: - attacks that are not considered social engineering (e.g. shoulder surfing) are also included;- Frequently asked questions. Ask a social engineering question and I'll answer it with a video. Why include bonus material, is the main course not exciting enough? Is that a trick question? Getting organisational security right goes well beyond instructing employees. With the bonus material, I would like to inform you about the complementary measures that should be taken into account. I’m fully convinced of the benefits, but I don’t see why I should learn all this from you. True, let me explain by giving you an overview of my experience: - Parttime PhD Candidate (6 years - present). I read the science, you'll get the knowledge! What more do you want? - Security operations manager (present). Acting as a security liaison on strategic accounts, I monitor the security of 2500+ workstations, 500+ servers and 10+ firewalls and routers, report on the operational security status of European and Dutch law and integrate intelligence results from: AVDS, Check Point, Nagios, Nessus, Palo Alto Traps, SCCM, SCEP, SEP, SCOM and SIEM;- Software quality consultant (6,5 years). I've advised many managers of large / small IT projects on various software related aspects; - IT auditor (1 year). I have closely worked with accountants and audited large governmental IT projects; - Quality assurance engineer (3 years). I have implemented two large IT systems for large companies (>1000 employees). You can find more details on LinkedIn on or my profile. Go ahead and click the enroll button, and I'll see you in lesson 1! Cheers, Soerin 👉 Activate Udemy Coupon 👈 Free Tutorials Udemy Review Real Discount Udemy Free Courses Udemy Coupon Udemy Francais Coupon Udemy gratuit Coursera and Edx ELearningFree Course Free Online Training Udemy Udemy Free Coupons Udemy Free Discount Coupons Udemy Online Course Udemy Online Training 100% FREE Udemy Discount Coupons https://www.couponudemy.com/blog/social-engineering-for-absolute-beginners-no-coding/
0 notes
Text
10 Things You Can Do With A Dedicated Server
10 Things You Can Do With Your Dedicated or Virtual Private Server
A dedicated server from a dedicated server hosting service can be useful for a multitude of different reasons. Dedicated server hosting offers enhanced flexibility over shared hosting with certain enhancements like higher performance, better security, and more overall control. There’s so much more to dedicated servers than just hosting websites. For example, you can use your idle server for setting up your own personal data synchronization services, virtual private networks, and more.
Here’s our top 10 list of things you can do with an idle dedicated or virtual private server.
10. Deploy a Personal Data Sync Service
There are plenty of services out there currently that offer syncing options for your cloud syncing needs like Dropbox and OneDrive, although some worry about potential security issues and feel uncomfortable hosting their private data on third-party servers that they don’t control. In addition to personal data syncing, there are also business services like Nexsan, however, they are typically more expensive.
You can choose to host your own private data syncing service using free and open-source software such as Resilio and Nextcloud. These let you sync your data across multiple devices, very similar to how Dropbox works, but you would be in full control of your data, especially if you set up on a Virtual Private Server (VPS).
9. Secure Your Network Connections
Dedicated Servers and Virtual Private Servers are also useful for securing your network traffic and wireless connections through Virtual Private Networks or Virtual Private Networks (VPN). A VPN is a method of employing encryption to provide secure access to a remote computer over the internet. There are many tutorials on how and why you should set up a VPN.
There are many different Virtual Private Network solutions available today that will work on dedicated servers or virtual private servers such as OpenVPN.
8. Set Up a Voice over Internet Protocol (VoIP)
Voice over Internet Protocol, also referred to as VoIP, is a form of communication that utilizes the internet as a transmission medium by sending voice over the internet network. Using VoIP is becoming more common among businesses as they want to use their own networks to ensure they have more control and higher voice quality than a traditional phone system can provide. A common example of Voice over Internet Protocol is Skype. You can also read about what VoIP can do for your business.
Setting up your Dedicated Server or Virtual Private server to host your own VoIP service is simple. There are many tutorials on how to set up your own VoIP system. There are many services you can use on your dedicated server or virtual private server to host your own Voice over Internet Protocol such as Mumble, TeamSpeak, and Ventrilo.
7. Project Management and Personal Cloud
You can do much more with your idle dedicated server or virtual private server than you could in the past. Technology is helping businesses and individuals in many different ways. A personal cloud is a private section hosted on the public cloud that allows you to upload, store, and retrieve data. A common personal cloud is Dropbox or Google Drive.
Today, you can manage your own personal projects for yourself or your small business. A good example of a project management tool is ProjectLibre, which is a very immersive, open source, and feature rich project management tool. Using a dedicated server or VPS, you can also host your own personal cloud— allowing you to sync your contacts, calendars, files, and images. Certain programs like ownCloud allow you to process data syncing as well, but it also includes a task manager, calendar, image galleries, and document editing software.
6. Private Analytics
Using a dedicated server or virtual private server, you can choose to host your own web analytics server. Web analytics is important when it comes to understanding your customer base and improving the effectiveness of your website. This is a common alternative to depending on services such as Google Analytics alone. If you aren’t satisfied with Google Analytics, you can opt to use a service like Matomo for a feature rich web analytics tool including many features of Analytics such as real time analytics, visitor tracking, referrer analysis, and even geolocation.
5. Folding@Home
Folding@Home is offering you the opportunity to help find a cure for many of today’s illnesses and cancers, such as Alzheimers, Huntington’s and Parkinson’s. Folding@Home is now based out of Washington University in St. Louis School of Medicine. Folding@Home is a way to help donate your unused computer power to one of the world’s biggest distributed supercomputer. Currently they boast over 1,000,000 users and a total combined computing power of over 40-PetaFLOPs (as of 2016). Join Folding@Home in the fight against COVID-19.
4. Communication Services
Dedicated servers and virtual private servers can also be used as an email server or IRC server. Internet relay chat, or IRC, is the most simple form of chat dating all the way back to 1988. You can use Internet Relay Chat for more than just basic chats, like transferring files, encryption, proxies, multiple channels, and different users. People mostly use IRC for their website chat rooms or for private conversations as an alternative to popular chat services such as Whatsapp or Facebook Messenger. Email servers allow you to access and manage your emails, including how they are received, sent, and distributed to users. There are plenty of free email services such as Gmail, Outlook, and Yahoo, however, many businesses prefer to use their own domain name for their emails.
Using your own dedicated server or virtual private server, you can host your own email server, a common example being Postfix, which is open source and full of features. Another way to utilize your inactive dedicated server is to become your own mail service provider using Mail-in-a-Box.
3. Hosting Your Own Web Page
You can use your dedicated server or virtual private servers to host your website, a blog, a forum, a wiki, and so much more. Hosting your own site has many advantages, such as lack of forced advertising, increased overall speed, and an unparalleled level of control. Many high bandwidth websites utilize virtual private servers and dedicated servers for their web hosting requirements. Virtual private servers offer the ability to easily scale up or down based on usage requirements, something that many see as an advantage over dedicated server hosting. Learn how to simply host your website with WordPress or how to host a blog with Blogger. Higher traffic sites will see the benefits that a virtual or dedicated server will provide over shared hosting.
2. Hosting Game Servers
If you play multiplayer video games, you’re familiar with how game servers work. Using a dedicated server, you can host your own multiplayer lobbies and dedicated game servers with minimal downtime’s and all at optimal speeds. There are plenty of tutorials for how to set up dedicated servers for common games like Minecraft, Counter Strike, and Arma 3. If you’re interested in renting a game server, consider visiting our game server hosting page.
1. Use Your Server As a Firewall
If you are in the market for a firewall but your budget won’t allow for the hardware or commercial software firewall, consider that there are other open-source alternatives such as SmoothWall and Sophos, some of which are said to be just as effective as some commercial applications.
The possibilities of different options are endless when it comes to what you can do with your dedicated server. There are many things that couldn’t be included in the list such as creating a simple test server, converting your server to a monitoring server such as with Nagios, creating an internet jukebox for streaming different multimedia formats to different devices with Ampache. or even to set up HTTP tunneling.
There are countless different ways that you can utilize your idle dedicated or virtual private server. For anything that isn’t listed, we would love to hear about it in the comments! How do you use your idle dedicated or virtual private server?
About Us: Astral Servers offers managed and unmanaged server hosting services to customers around the world. All of our dedicated servers and virtual private servers come with advanced DDoS protection, 24/7 support, and a 99.999% uptime guarantee, all with unlimited speeds.
#10 things you can do with a dedicated server#cool things to do with an idle server#fun things to do with vps#astral servers#dedicated server hosting#virtual private server hosting#north american server hosting
0 notes
Text
The Myth of the Full-stack Developer
My defensive tendencies are normally put on high alert when I hear that magic phrase. Stacks are a lot bigger than what they used to be, and being able to claim one has acquired refined skills at every layer of web development is certainly not a small claim. Does this mean you have a broad range of skills or you specialise in everything?
For a time (allegedly) Facebook only hired full-stack engineers. This was of course when they were building the first few versions of Facebook, which, lets face it had a relatively simple php backend and wasn't anything special design-wise.
Stacks are a lot bigger than they used to be
Stacks are a lot bigger than they used to be...
Full-stack used to mean less layers.
Coding php or Python, jQuery, HTML, CSS then transferring a few files via FTP to your shared hosting account or dedicated server? You were full-stack. HTML was trivial, and even thinking of implementing any proper application code in JavaScript wasn't possible.
My beef is not with people who can do all of the above, it's with the label 'full-stack developer'. What does it mean in 2014?
At the level of a senior full-stack engineer we're perhaps talking about architecting a modular Backbone/AngularJS front-end whilst optimising content delivery and tweaking hardware accelerated layers in CSS, followed by implementing an async non-blocking backend (which also pre-renders templates on the server), and pushing to an AWS cluster which has been built with security and scaleability in mind. Not to mention design. Designing UI responsively and mobile-first is essential, utilising a CSS pre-processor to save time. And remember to setup Nagios for monitoring. Oh, and ideally when the Continuous Integration server detects a bad build because your end-to-end tests have failed, get it to send you an SMS with the build error messages. Well, the last two are probably for bonus points.
Ask someone who labels themselves 'full-stack'. Do they believe they have familiarity with different layers, or true mastery?
Identifying mastery
I used to work with a very smart guy who when interviewing junior web developers, used to draw a spider diagram with each of the spikes being different layers of web development; UX, HTML, CSS, JavaScript, backend scripting language, and SQL. When the young developers were asked to grade themselves out of 10 for each of the skill areas, most went for a good spread, but a rather high spread. It seemed nobody wanted to exceed an 8, or drop below a 5 in any of the layers. We can ignore the scale at which they were grading themselves, because we were simply interpreting the grades relatively against each other so we could get a good idea of what kind of developer the individual saw themselves as. I didn't hear the term 'full-stack' being used even once, but we got a feel that everyone was an all-round web developer. What happened next was more interesting.
On the second iteration the interviewees were given a maximum of 30 points to distribute as they pleased. After some frowning, some internal arguing, and finally the self-grading we saw a lot more skewed graphs. The 7-5 well-spread ratings turned into more skewed 8-2's. It seemed when faced with the harsh reality of admitting what they were really good at, they delivered, giving themselves 8's in their favoured areas and 2's in others. If the candidates really believed in their initial relative spread, we would see the same weighting in the second round, but instead we saw front-end and back-end developers emerge from the crowd.
Of course 99% of web developers have probably never sat through this test, and have perhaps have never been forced to reveal what their real spread of skills is.
The Full-stack DeveloperThe Full-stack Developer
Asking web developers to allocate points to their skillset.
How skilled are you in each discipline?
The basics of the languages/frameworks we learn today can often be picked up in a matter of hours. We no longer add skills to our CVs by taking a course, we simply download some code and start hacking through tutorials and demo code. The problem is, I feel the difference between knowing something in web development and truly mastering it is now becoming an increasingly blurred line.
It's very easy to become disillusioned with your own skills when you've deployed some code which has been consumed by lots of users. Let's say you've written a web application which has scaled well under load, and you've received great feedback. Are you a master of everything you used in this stack? Or are you simply good at implementing the layers you needed to make things work together? Because that's an entirely different skill, and in fact a very valuable one.
The skill of acquiring new skills
In my eyes the most valuable skill to have is the ability to learn, closely followed by the ability to know when you don't know something. I'm sure we've all met people who decide to put brakes on their own learning because they believe they've become a master at something. I don't know about you, but the smartest people I know (and the ones I have most respect for) are the ones who are still eager to learn new things every day, from everyone they meet. These people just don't stop growing, in terms of both ability and character.
Why I'm not a full-stack developer
At one point (probably when I was about twenty-two) I heard this phrase 'full-stack' and I thought "yeah, I'm one of them". Five years later after working in roles with ASP, php, .Net, Node and finally JavaScript and CSS, I only label myself as a front-end developer. Maybe I just wasn't that good at previous disciplines, or maybe since spending the last 2-3 years in pure JavaScript roles I just actually realised how high the limits are when you specialise. This is simply opportunity I did not have when I was busy in cross-discipline roles at smaller companies.
Sure, I've got some broad skills like a lot of developers. However, I'd like to think being a front-end developer now assumes some knowledge of UX, design, and how data is modelled and served on the backend, and this is why I think the term full-stack is old fashioned (if five years is old) and perhaps a bit smug.
Maybe, I just don't like the term.
Some people are willing to have a go at everything
Perhaps most respectable about all people who claim to be full-stack, is that is conveys ambition and persistance. The ideal developer should be willing to have a go at learning anything, but also acknowledge when they need help from a specialist in the team.
Perhaps I was too defensive at first, I've met too many people who pronounce the term in a smug way, instantly causing me to discredit them. However, say you're full-stack in a normal way, and there will be no scrutiny from my part. It won't be at all like meeting an investment banker or recruiter.
The employability of a true full-stack developer: HIGH.
The chances of finding a good full-stack developer: LOW.
Smaller companies and startups NEED full-stack developers. Developers are often forced to acquire new skills when the resources simply aren't available. I feel the problem for companies desperate to hire these guys and girls, is that the real multi-skilled developers are often lost in a sea of douchebags, claiming they know it all.[Source]-My defensive tendencies are normally put on high alert when I hear that magic phrase. Stacks are a lot bigger than what they used to be, and being able to claim one has acquired refined skills at every layer of web development is certainly not a small claim. Does this mean you have a broad range of skills or you specialise in everything?
For a time (allegedly) Facebook only hired full-stack engineers. This was of course when they were building the first few versions of Facebook, which, lets face it had a relatively simple php backend and wasn't anything special design-wise.
Stacks are a lot bigger than they used to be
Stacks are a lot bigger than they used to be...
Full-stack used to mean less layers.
Coding php or Python, jQuery, HTML, CSS then transferring a few files via FTP to your shared hosting account or dedicated server? You were full-stack. HTML was trivial, and even thinking of implementing any proper application code in JavaScript wasn't possible.
My beef is not with people who can do all of the above, it's with the label 'full-stack developer'. What does it mean in 2014?
At the level of a senior full-stack engineer we're perhaps talking about architecting a modular Backbone/AngularJS front-end whilst optimising content delivery and tweaking hardware accelerated layers in CSS, followed by implementing an async non-blocking backend (which also pre-renders templates on the server), and pushing to an AWS cluster which has been built with security and scaleability in mind. Not to mention design. Designing UI responsively and mobile-first is essential, utilising a CSS pre-processor to save time. And remember to setup Nagios for monitoring. Oh, and ideally when the Continuous Integration server detects a bad build because your end-to-end tests have failed, get it to send you an SMS with the build error messages. Well, the last two are probably for bonus points.
Ask someone who labels themselves 'full-stack'. Do they believe they have familiarity with different layers, or true mastery?
Identifying mastery
I used to work with a very smart guy who when interviewing junior web developers, used to draw a spider diagram with each of the spikes being different layers of web development; UX, HTML, CSS, JavaScript, backend scripting language, and SQL. When the young developers were asked to grade themselves out of 10 for each of the skill areas, most went for a good spread, but a rather high spread. It seemed nobody wanted to exceed an 8, or drop below a 5 in any of the layers. We can ignore the scale at which they were grading themselves, because we were simply interpreting the grades relatively against each other so we could get a good idea of what kind of developer the individual saw themselves as. I didn't hear the term 'full-stack' being used even once, but we got a feel that everyone was an all-round web developer. What happened next was more interesting.
On the second iteration the interviewees were given a maximum of 30 points to distribute as they pleased. After some frowning, some internal arguing, and finally the self-grading we saw a lot more skewed graphs. The 7-5 well-spread ratings turned into more skewed 8-2's. It seemed when faced with the harsh reality of admitting what they were really good at, they delivered, giving themselves 8's in their favoured areas and 2's in others. If the candidates really believed in their initial relative spread, we would see the same weighting in the second round, but instead we saw front-end and back-end developers emerge from the crowd.
Of course 99% of web developers have probably never sat through this test, and have perhaps have never been forced to reveal what their real spread of skills is.
The Full-stack DeveloperThe Full-stack Developer
Asking web developers to allocate points to their skillset.
How skilled are you in each discipline?
The basics of the languages/frameworks we learn today can often be picked up in a matter of hours. We no longer add skills to our CVs by taking a course, we simply download some code and start hacking through tutorials and demo code. The problem is, I feel the difference between knowing something in web development and truly mastering it is now becoming an increasingly blurred line.
It's very easy to become disillusioned with your own skills when you've deployed some code which has been consumed by lots of users. Let's say you've written a web application which has scaled well under load, and you've received great feedback. Are you a master of everything you used in this stack? Or are you simply good at implementing the layers you needed to make things work together? Because that's an entirely different skill, and in fact a very valuable one.
The skill of acquiring new skills
In my eyes the most valuable skill to have is the ability to learn, closely followed by the ability to know when you don't know something. I'm sure we've all met people who decide to put brakes on their own learning because they believe they've become a master at something. I don't know about you, but the smartest people I know (and the ones I have most respect for) are the ones who are still eager to learn new things every day, from everyone they meet. These people just don't stop growing, in terms of both ability and character.
Why I'm not a full-stack developer
At one point (probably when I was about twenty-two) I heard this phrase 'full-stack' and I thought "yeah, I'm one of them". Five years later after working in roles with ASP, php, .Net, Node and finally JavaScript and CSS, I only label myself as a front-end developer. Maybe I just wasn't that good at previous disciplines, or maybe since spending the last 2-3 years in pure JavaScript roles I just actually realised how high the limits are when you specialise. This is simply opportunity I did not have when I was busy in cross-discipline roles at smaller companies.
Sure, I've got some broad skills like a lot of developers. However, I'd like to think being a front-end developer now assumes some knowledge of UX, design, and how data is modelled and served on the backend, and this is why I think the term full-stack is old fashioned (if five years is old) and perhaps a bit smug.
Maybe, I just don't like the term.
Some people are willing to have a go at everything
Perhaps most respectable about all people who claim to be full-stack, is that is conveys ambition and persistance. The ideal developer should be willing to have a go at learning anything, but also acknowledge when they need help from a specialist in the team.
Perhaps I was too defensive at first, I've met too many people who pronounce the term in a smug way, instantly causing me to discredit them. However, say you're full-stack in a normal way, and there will be no scrutiny from my part. It won't be at all like meeting an investment banker or recruiter.
The employability of a true full-stack developer: HIGH.
The chances of finding a good full-stack developer: LOW.
Smaller companies and startups NEED full-stack developers. Developers are often forced to acquire new skills when the resources simply aren't available. I feel the problem for companies desperate to hire these guys and girls, is that the real multi-skilled developers are often lost in a sea of douchebags, claiming they know it all.[Source]-https://www.andyshora.com/full-stack-developers.html
62 Hours Mean Stack Developer Training includes MongoDB, JavaScript, A62 angularJS Training, MongoDB, Node JS and live Project Development. Demo Mean Stack Training available.
0 notes
Text
Add Linux Host To Nagios Core Using NRPE Plugin
HOW TO ADD LINUX HOST TO NAGIOS MONITORING SERVER USING NRPE PLUGIN
youtube
In this video, I will show you how to add remote Linux client host and it’s services to Nagios Monitoring Server using NRPE agent.
In my previous video, I demonstrated how to install Nagios server on Centos7. I hope you already have installed Nagios server.
Visit Website For Text Article:
https://digitalave.github.io/spring/2019/10/10/Add_linux_host_to_nagios_using_nrpe.html
#### How To Install Nagios Core On CentOS7 / RHEL7 ####
https://youtu.be/04_eZkoMviM
Install and Configure Nagios Core Monitoring Server On CentOS7. This Nagios tutorial will helps you setup your own Nagios server.
Nagios is a industry slandered IT infrastructure monitoring solutions. Which is one of the most popular, open source , powerful server and network monitoring system. It enables organizations to identify and resolve IT infrastructure problems before they affect critical business processes. Nagios has the capability of monitoring application, services with an entire IT infrastructure.
VISIT WEBSITE: https://digitalave.github.io/spring/2019/10/08/Install_nagios_core_on_centos7.html
nagios monitoring tool tutorial,add linux host to nagios using NRPE, add linux host to nagios, nrpe configuration, nagios, nagios core, nagios server, nagios server linux, add machine to linux host, NRPE, Nagios NRPE, nagios tutorial, how to install nrpe, monitoring linux host, nagios linux, nagios agent, nagios linux agent, install nrpe, nagios installation, nagios configuration, nagios monitoring tool tutorial, how to, linux tutorial, nagios installation in linux
0 notes
Text
Security measures to protect an unmanaged VPS.
Virtual private server
have long been thought of as a next-generation shared hosting solution.
They use virtualization ‘tricks’ to let you coin your own hosting environment and be a master of your server at a pretty affordable price.
If you are well-versed in server administration, then an unmanaged VPS will help you make the most of your virtual machine’s capabilities.
However, are you well-versed enough in security as well?
Here is a Linux VPS security checklist, which comes courtesy of our Admin Department.
What exactly is an unmanaged VPS?
Before we move to the security checklist, let’s find out exactly what an unmanaged VPS is and what benefits it can bring to you.
With an unmanaged VPS, pretty much everything will be your responsibility.
Once the initial setup is complete, you will have to take care of server maintenance procedures, OS updates, software installations, etc. Data backups should be within your circle of competence as well.
This means that you will need to have a thorough knowledge of the Linux OS. What’s more, you will have to handle any and all resource usage, software configuration and server performance issues.
Your host will only look into network- and hardware-related problems.
Why an unmanaged VPS?
The key advantages of unmanaged VPSs over managed VPSs are as follows:
you will have full administrative power and no one else will be able to access your information;you will have full control over the bandwidth, storage space and memory usage;you will be able to customize the server to your needs specifically;you will be able to install any software you want;you will save some money on server management – it really isn’t that hard to set up and secure a server if you apply yourself and updating packages is very easy;you will be able to manage your server in a cost-efficient way without the need to buy the physical machine itself (you would have to if you had a dedicated server);
Unmanaged VPS – security checklist
With an unmanaged VPS, you will need to take care of your sensitive personal data.
Here is a list of the security measures that our administrators think are key to ensuring your server’s and your data’s health:
1. Use a strong password
Choosing a strong password is critical to securing your server. With a good password, you can minimize your exposure to brute-force attacks. Security specialists recommend that your password be at least 10 characters long.
Plus, it should contain a mix of lower and uppercase letters, numbers and special characters and should not include common words or personally identifiable information. You are strongly advised to use a unique password so as to avoid a compromised service-connected breakthrough.
A strong password may consist of phrases, acronyms, nicknames, shortcuts and even emoticons. Examples include:
1tsrAIn1NGcts&DGS!:-) (It’s raining cats and dogs!) humTdumt$@t0nAwa11:-0 (Humpty Dumpty sat on a wall) p@$$GOandCLCt$500 :-> (Pass Go and collect $500)
2. Change the default SSH port
Modifying the default SSH port is a must-do security measure.
You can do that in a few quick steps:
Connect to your server using SSHSwitch to the root userRun the following command: vi /etc/ssh/sshd_configLocate the following line: # Port 22Remove # and replace 22 with another port numberRestart the sshd service by running the following command: service sshd restart
3. Disable the root user login
The root user has unlimited privileges and can execute any command – even one that could accidentally open a backdoor that allows for unsolicited activities.
To prevent unauthorized root-level access to your server, you should disable the root user login and use a limited admin account instead.
Here is how you can add a new admin user that can log into the server as root via SSH:
Create the user by replacing example_user with your desired username (in our case – ‘admin’): adduser adminSet the password for the admin user account: passwd adminTo get admin privileges, use the following command: echo 'admin ALL=(ALL) ALL' >> /etc/sudoersDisconnect and log back in as the new user: ssh [email protected] you are logged in, switch to the root user using the ‘su’ command: su password: whoami rootTo disable the root user login, edit the /etc/ssh/sshd_config file. You will only need to change this line: #PermitRootLogin yes to: PermitRootLogin no
You will now be able to connect to your server via SSH using your new admin user account.
4. Use a rootkit scanner
Use a tool like rkhunter (Rootkit Hunter) to scan the entire server for rootkits, backdoors and eventual local exploits on a daily basis; you’ll get reports via email;
5. Disable compilers for non-root users (for cPanel users)
Disabling compilers will help protect against many exploits and will add an extra layer of security.
From the WebHost Manager, you can deny compiler access to unprivileged (non-root) users with a click.
Just go to Security Center ->Compiler Access and then click on the Disable Compilers link:
Alternatively, you can keep compilers for selected users only.
6. Set up a server firewall
An IPTABLES-based server firewall like CSF (ConfigServer Firewall) allows you to block public access to a given service.
You can permit connections only to the ports that will be used by the FTP, IMAP, POP3 and SMTP protocols, for example.
CSF offers an advanced, yet easy-to-use interface for managing your firewall settings.
Here is a good tutorial on how you can install and set up CSF.
Once you’ve got CSF up and running, make sure you consult the community forums for advice on which rules or ready-made firewall configurations you should implement.
Keep in mind that most OSs come with a default firewall solution. You will need to disable it if you wish to take advantage of CSF.
7. Set up intrusion prevention
An intrusion prevention software framework like Fail2Ban will protect your server from brute-force attacks. It scans logfiles and bans IPs that have unsuccessfully tried to log in too many times.
Here’s a good article on how to install and set up Fail2Ban on different Linux distributions.
You can also keep an eye on the Google+ Fail2Ban Users Community.
8. Enable real-time application security monitoring
Тhe best real-time web application monitoring and access control solution on the market – ModSecurity, allows you to gain HTTP(S) traffic visibility and to implement advanced protections.
ModSecurity is available in your Linux distribution’s repository, so installing it is very easy:
apt-get install libapache2-modsecurity
Here’s a quick guide on how to install and configure ModSecurity.
Once you’ve got ModSecurity up and running, you can download a rule set like CRS (OWASP ModSecurity Core Rule Set). This way you won’t have to enter the rules by yourself.
9. Set up anti-virus protection
One of the most reliable anti-virus engines is ClamAV – an open-source solution for detecting Trojans, viruses, malware & other malicious threats. The scanning reports will be sent to your email address.
ClamAV is available as a free cPanelplugin.
You can enable it from the Manage Plugins section of your WHM:
Just tick the ‘Install ClamAV and keep updated’ checkbox and press the ‘Save’ button.
10. Enable server monitoring
For effective protection against DDoS attacks, make sure you install a logfile scanner such as logcheck or logwatch. It will parse through your system logs and identify any unauthorized access to your server.
Use software like Nagios or Monitis to run automatic service checks to make sure that you do not run out of disk space or bandwidth or that your certificates do not expire.
With a service like Uptime Doctor or Pingdom, you can get real-time notifications when your sites go down and thus minimize accidental downtime.
11. Run data backups
Make regular off-site backups to avoid the risk of losing data through accidental deletion.
You can place your trust in a third-party service like R1Soft or Acronis, or you can build your own simple backup solution using Google Cloud Storage and the gsutil tool.
If you are on a tight budget, you can keep your backups on your local computer.
12. Keep your software up to date
Keeping your software up to date is the single biggest security precaution you can take.
Software updates range from regular minor bug fixes to critical vulnerability patches. You can set automatic updates to save time.
However, keep in mind that automatic updates do not apply to self-compiled applications. It’s advisable to first install an update in a test environment so as to see its effect before deploying it to your live production environment.
Depending on your particular OS, you can use:
yum-cron (for CentOS)unattended upgrades (for Debian and Ubuntu)dnf-automatic (Fedora)
If you have not obtained an unmanaged VPS yet, you could consider our solutions:
OpenVZ VPS packages – all setups from 4 to 10 are unmanaged and come with SSH/full root access (for cPanel setups only) and with a CentOS/Debian/Ubuntu OS installation;KVM VPS setups – all four setups are unmanaged and offer SSH/full root access; OS options include CentOS/Debian/Ubuntu as well as a few OS ISO alternatives like Fedora and FreeBSD;
via Blogger http://ift.tt/2AIEre3
0 notes
Text
Easy guide to setup Nagios monitoring using SSH (check_by_ssh)
Easy guide to setup Nagios monitoring using SSH (check_by_ssh)
In our earlier tutorials, we have discussed how to install Nagios server & add Linux client for monitoring using NRPE plugin & also to add Windows clients for monitoring using NSClient++. But those are not the only ways to connect clients to Nagios server for monitoring, we can also allow Nagios server to monitor Linux machines by ssh using the check_by_ssh plugin.
In this tutorial, we will learn…
View On WordPress
0 notes
Text
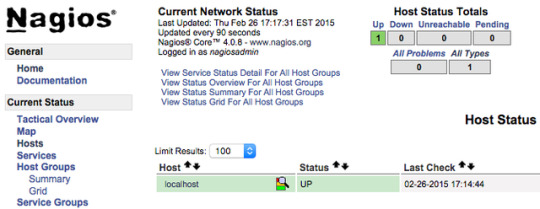
Introduction Nagios is a popular open-source monitoring system. It keeps an inventory of your servers and monitors them so you know your critical services are up and running. Using a monitoring system like Nagios is an essential tool for any production environment, because by monitoring uptime,... How To Install Nagios 4 and Monitor Your Servers on Ubuntu 16.04 Category: DevOps, Linux Tutorials
0 notes
Photo
New Post has been published on http://www.cloudypoint.com/linux-tutorials/how-to-install-nagios-4-and-monitor-your-servers-on-ubuntu-16-04/
How To Install Nagios 4 and Monitor Your Servers on Ubuntu 16.04
Introduction Nagios is a popular open-source monitoring system. It keeps an inventory of your servers and monitors them so you know your critical services are up and running. Using a monitoring system like Nagios is an essential tool for any production environment, because by monitoring uptime,... How To Install Nagios 4 and Monitor Your Servers on Ubuntu 16.04 Category: DevOps, Linux Tutorials
0 notes
Text
Step by step procedures to Install Nagios XI Server in Centos 7
Step by step procedures to Install Nagios XI Server in Centos 7
Step by step proceduress to Install Nagios XI Server in Centos 7
#Update your centos os > yum install update > yum install wget
Read more Click here
Reference:- This tutorial was originally posted on scmGalaxy.com
View On WordPress
0 notes