#OAuth 2.0 playground
Explore tagged Tumblr posts
Text
Google developers OAuth 2.0 playground And OpenID Connect

Google Auth Platform usability and security updates
Millions of developers authenticate users and access hundreds of APIs using Google's identity platform. One of the largest implementations of the Google developers OAuth 2.0 playground protocol and OpenID Connect standard in the world provides developers with a reliable, secure, and easy method to interact. Google is pleased to announce significant platform usability and security improvements.
Google engineers' OAuth 2.0 playground
Simple OAuth setting in Google Cloud Console
Developers that use Google Sign-in for authentication or user consent to use Google APIs must register their applications and websites to generate client credentials. Developers utilising Google Cloud Console previously found OAuth setup pages under APIs & Services. Separate navigation for Google Auth Platform is added to these sites.
This version speeds up app configuration updates, simplifies project registration, and improves developer advice. Upcoming improvements include an improved onboarding wizard, simpler OAuth scope management, and faster, more transparent app verification.
Developers using other consoles for OAuth have the same Firebase or Apps Script experience.
OAuth client secret presentation change
Some OAuth clients require a “secret” for authorisation and authentication. Since the client secret operates like a website or application password, protecting these strings is crucial to user account and data security.
Developers could previously download client secrets from Google Cloud Console, Firebase Console, and other Google developer tools. OAuth secrets will be hidden in Google Cloud Console client administrative pages in June. Developer consoles will show the last few characters to help identify them.
OAuth client secrets must be downloaded and handled securely by developers. For this, most developers utilise Google Cloud Platform's Secret Manager. The client secret won't appear when the creation screen closes.
Never reveal OAuth client secrets that provide access to user data or other production systems online or in version control systems. If secrets leak, change them immediately and cycle them often.
Automatic deactivation of unused OAuth clients
Starting in June, OAuth clients inactive for six months will be automatically terminated to prevent credential theft and misuse. When token exchanges end, the six-month period begins.
When inactive clients are erased, developers will be notified and can recover them for 30 days.
A great experience for you and your customers
These upgrades and more planned for later this year make your experience smoother and safer, giving you more time to build great applications and websites for your consumers.
Accessing Google APIs with OAuth 2.0
Simple acts
Every Google API-accessing app utilising OAuth 2.0 follows a pattern. You take five stages typically:
The Google API Console gives OAuth 2.0 credentials.
Get an access token from Google Authorisation Server.
Review user-granted access scopes.
Give an API the access token.
Update the access token if needed.
Google APIs authorise and authenticate using OAuth 2.0. Google supports OAuth 2.0 applications for web servers, client-side, installation, and limited-input devices.
Get OAuth 2.0 client credentials from Google API Console to begin. After that, your client app requests an access token from the Google Authorisation Server, extracts it, and sends it to the Google API you want to use. Check out the OAuth 2.0 Playground for an interactive Google OAuth 2.0 demonstration using your own client credentials.
#technology#technews#govindhtech#news#technologynews#Google developers OAuth 2.0 playground#Google developers OAuth#OAuth 2.0#OAuth clients#OAuth 2.0 playground#OAuth
0 notes
Text
Top WebApp Security Checklist for Businesses in the USA (2025)

In today’s digital-first world, web applications are the backbone of most business operations—from e-commerce to customer portals, CRMs, and more. However, with increasing cyber threats, securing your web applications is not optional; it's critical. Especially for businesses operating in the USA, where data breaches can lead to legal penalties, loss of customer trust, and significant financial setbacks.
This guide outlines a comprehensive WebApp Security Checklist tailored for businesses in the USA to ensure robust protection and compliance with modern security standards.
1. Use HTTPS with a Valid SSL Certificate
Secure Socket Layer (SSL) certificates are fundamental. HTTPS encrypts the data exchanged between the user and your application, ensuring it remains private.
Purchase and install a trusted SSL certificate.
Redirect all HTTP traffic to HTTPS.
Regularly renew and monitor the validity of your SSL certificate.
Fact: Google flags HTTP sites as “Not Secure,” impacting SEO and user trust.
2. Implement Strong Authentication & Access Controls

Weak login systems are a hacker’s playground. Use:
Multi-Factor Authentication (MFA): Add extra layers beyond passwords.
Role-Based Access Control (RBAC): Ensure users only access what’s necessary.
Session Management: Set session expiration limits and auto-logout on inactivity.
Bonus Tip: Use OAuth 2.0 or OpenID Connect for secure federated authentication.
3. Sanitize and Validate All User Inputs
Most web attacks like SQL Injection and XSS stem from unsanitized user inputs. To prevent this:
Sanitize inputs on both client and server sides.
Use prepared statements and parameterized queries.
Escape special characters in output to prevent script injections.
Best Practice: Never trust user inputs — even from authenticated users.
4. Regularly Update Dependencies and Frameworks
Outdated plugins, libraries, or frameworks can be exploited easily.
Use dependency management tools like npm audit, pip-audit, or OWASP Dependency-Check.
Enable automatic updates where possible.
Avoid deprecated plugins or unsupported software.
Real Example: The infamous Log4j vulnerability in 2021 exposed millions of apps worldwide.
5. Conduct Regular Vulnerability Scans and Penetration Testing
Security is not a one-time fix. It's a continuous process.
Schedule monthly or quarterly vulnerability scans.
Hire ethical hackers for real-world pen testing.
Fix discovered issues immediately and re-test.
🔍 Tools to Use: Nessus, Burp Suite, OWASP ZAP.
6. Implement Secure APIs

With APIs powering most modern web apps, they’re a common attack vector.
Authenticate API users with tokens (JWT, OAuth).
Rate-limit API calls to avoid abuse.
Use API gateways for logging and security enforcement.
Extra Tip: Never expose sensitive internal APIs to the public internet.
7. Data Encryption at Rest and in Transit
Whether storing user passwords, payment info, or PII — encryption is essential.
Encrypt sensitive data in the database using AES-256 or better.
Avoid storing passwords in plain text — use hashing algorithms like bcrypt.
Always encrypt data transfers via HTTPS or secure VPN tunnels.
Compliance: Required under data protection laws like HIPAA, CCPA, and PCI-DSS.
8. Monitor Logs & Set Up Intrusion Detection
Monitoring can alert you to threats in real-time.
Use centralized logging systems like ELK Stack or Splunk.
Implement intrusion detection systems (IDS) like Snort or OSSEC.
Set up alerts for unusual activities like multiple failed logins.
Tip: Review logs weekly and set up daily summaries for admins.
9. Backup Regularly & Prepare a Disaster Recovery Plan
Cyberattacks like ransomware can lock you out of your app.
Schedule automatic daily backups.
Store backups offsite or in the cloud (with encryption).
Test your disaster recovery plan quarterly.
Pro Tip: Use versioned backups to roll back only the infected data.
10. Comply with Data Privacy Regulations
For businesses in the USA, compliance isn't just good practice — it's the law.
If you handle health data → HIPAA compliance is mandatory.
Selling to California residents → comply with CCPA.
Accepting payments? → follow PCI-DSS requirements.
Reminder: Non-compliance can lead to heavy penalties and lawsuits.
11. Educate Your Team
The weakest link is often human error.
Train employees on phishing and social engineering attacks.
Enforce strong password policies.
Run annual cybersecurity awareness programs.
Result: A well-trained team is your first line of defense.
12. Use Web Application Firewalls (WAFs)

WAFs provide an extra layer of protection.
Block malicious traffic before it reaches your server.
Protect against DDoS, brute force, and zero-day attacks.
Use cloud-based WAFs like Cloudflare, AWS WAF, or Imperva.
Bonus: Easily deployable and scalable with your infrastructure.
Conclusion
For U.S.-based businesses, web application security should be a strategic priority — not a checkbox. With cyberattacks growing in complexity and volume, following a thorough security checklist is vital to protect your data, users, and brand reputation.
At the end of the day, your web application is only as secure as its weakest link. Make sure there isn’t one.
Ready to Secure Your WebApp?
If you're looking for expert support to secure or build a robust, secure web application, WeeTech Solution is here to help. Get in touch with our development and cybersecurity team today!
0 notes
Text
The Strength and Beauty of GraphQL in Use
The Strength and Beauty of GraphQL in Use
Facebook developed GraphQL as a major problem-solver for more efficient mobile data loading in 2012 and released it as an open-source solution three years later. Since that time, it mistakenly associates with PHP only and lacks trust given the Facebook's reputation (if you know what I mean). However, a recent Netflix case that finds GraphQL as a game-changer to power the API layer and increase the scalability and operability of the studio ecosystem attracts attention. This specification already gained popularity — given State of JavaScript 2019 Report, 50.6% of respondents have heard of GraphQL and would like to learn it. However, The New York Times, Airbnb, Atlassian, Coursera, NBC, GitHub, Shopify, and Starbucks are already among the GraphQL users. We decided to dwell on the beauty, strength, and some constructions of GraphQL in its scalability, performance, and security aspects and tell about our use cases for a banking sphere and a platform of commercial targeting. See the list of useful toolkits added in the end as a bonus.
GraphQL: the Beans Spilled
GraphQL is a convenient way of communication between a client and a server first. Sometimes one can see it as an opponent to REST API given the main difference that GraphQL brings to the table — only endpoint to fetch the data by one call from multiple sources. Meanwhile, we are to provide the space for consideration whether this specification is relevant to particular tasks or REST API is the silver bullet for your case.
Both REST and GraphQL APIs are stateless, supported by any server-side language and any frontend framework, exchange the data through the JSON. But the one and the only endpoint containing the query expression to define the data that should be returned creates the what-you-see-is-what-you-get principle to optimize the work. Let's deep dive into the specification's main advantages and disadvantages.
Performance and Security
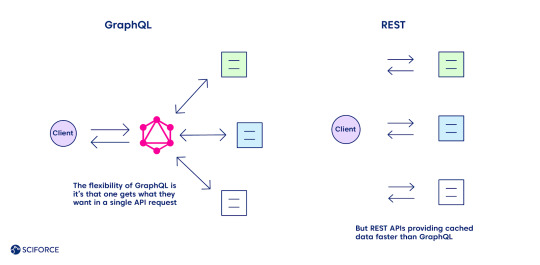
The flexibility of GraphQL is its main advantage over REST, as one gets what they want in a single API request. Define the structure of the information to receive back, and it goes back in the format requested, no under-fetching or over-fetching.
Meanwhile, caching seems to be one of the GraphQL downsides compared to REST (see the complete list of all the pros and cons further). REST APIs use the HTTP caching mechanism, providing cached data faster. It leverages its community-powered and time-tested feature, leaving GraphQL behind at the moment.
Security is another area of improvement for GraphQL while comparing it with REST, which boasts of a more mature system. The latter leverages HTTP authentication, JSON Web Tokens (JWT), or OAUth 2.0 mechanisms.
Pros and Cons: All Things Considered
Unlike REST API, GraphQL has detailed documentation and supports the function of nested queries that contributes to the principle "no over fetching and under fetching data," which happened while using the first specification. Query and mutation are the joint GraphQL operations. Thus, the CRUD (create, read, update, delete) model is not relevant for GraphQL as the create operation executes through the query command (other ones are implemented with mutations).
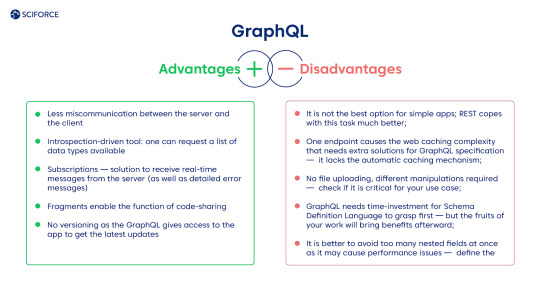
Advantages
Less miscommunication between the server and the client.
Introspection-driven tool: one can request a list of data types available.
Subscriptions — solution to receive real-time messages from the server (as well as detailed error messages).
Fragments enable the function of code-sharing.
No versioning as the GraphQL gives access to the app to get the latest updates.
Disadvantages
It is not the best option for simple apps; REST copes with this task much better.
One endpoint causes the web caching complexity that needs extra solutions for GraphQL specification — it lacks the automatic caching mechanism.
No file uploading, different manipulations required — check if it is critical for your use case.
GraphQL needs time-investment for Schema Definition Language to grasp first — but the fruits of your work will bring benefits afterward.
It is better to avoid too many nested fields at once as it may cause performance issues — define the architecture of the query beforehand.
Our Use Cases with GraphQL
GraphQL provides developers with higher scalability of the system that applies in any sphere. We want to share our experience of functions diversification for a commercial targeting platform and solving the banking application's two-fold task.
The Platform for a Commercial Targeting
GraphQL became a convenient solution for one of our clients who needed to develop a platform for commercial targeting, providing a straightforward approach for searching the potential customers in any national institution or facility. Using it, the client can direct the ads straight to the audience of interest using geolocation data and a set of filters. The platform consists of two primary services: one for geo-based consumers extraction based on PlaceIQ dataset usage and one for attribute-based (consumers identity graph) with consumer dataset. The project can be extended by adding the missing residential dataset to retrieve residents at requested addresses. Also, the services could be wrapped into the REST API to provide the ability to trigger them using web requests.
Risk Reduction and Resilience Boosting Financial Platform
An average bank encounters no more than 100K transactions a day. Moreover, it also faces malicious actions and the risk of cyberattack. One of our clients needed to empower their software platform to encounter higher transaction pressure and provide a higher risk-management system to avoid financial crimes. As a result, we have developed a solution that stands for the high amount of transactions and provides the reports while detecting anomalies based on the transactions' data in real-time.
GraphQL: Useful Toolkit
Check out the growing GraphQL community to find the latest updates on this solution. There are many horizontally and vertically developed solutions for GraphQL client, GraphQL gateway, GraphQL server, and database-to-GraphQL server. Add some of the tools that you enjoy using while working with GraphQL in comments to this blog.
GraphQL's servers are available for languages like JavaScript, Java, Python, Perl, Ruby, C#, Go, etc.
Apollo Server for JavaScript applications and GraphQL Ruby are some of the most popular choices.
Apollo Client, DataLoader, GraphQL Request, and Relay are among popular GraphQL clients. Graphiql, GraphQL IDE, and GraphQL Playground for IDE's respectively.
Some handy tools:
GraphQL Bindings — to use GraphQL API's as modular buildings blocks
GraphQL Docs — to generate GraphQL documentation in a simple way
GraphCMS — GraphQL-based CMS
GraphQL Network for easy debugging
GraphQL Voyager — to visualize data relations
and there are much more, depending on one's needs, as lists are keeping growing. Mention in the comments tools that worth it!
0 notes