#SIEM (Security Information and Event Management)
Explore tagged Tumblr posts
Text
Implementing an effective Security Information and Event Management (SIEM) system is essential for securing your organization's digital infrastructure. Microsoft Sentinel is a cloud-native SIEM solution that provides organizations with sophisticated security analytics and threat intelligence to help them detect, investigate, and respond to threats more efficiently.
#microsoft sentinel#SIEM#security information and event management#cloud#cloud security#azure#azure sentinel#infosectrain#learntorise
2 notes
·
View notes
Text
Cloud GRC: A Modern Approach to Risk and Compliance Management
As businesses increasingly migrate to cloud environments, managing governance, risk, and compliance (GRC) has become a top priority. Cloud GRC provides a structured framework to ensure compliance with regulatory standards, mitigate security risks, and maintain operational transparency in cloud-based infrastructures. A modern approach to Cloud GRC integrates automation, AI-driven analytics, and real-time monitoring to enhance risk management and compliance efforts.
Understanding Cloud GRC
Cloud GRC refers to a set of policies, tools, and practices designed to manage governance, risk, and compliance in cloud environments. Unlike traditional GRC models, Cloud GRC adapts to the dynamic nature of cloud computing by implementing real-time monitoring, automated compliance reporting, and proactive risk assessments. This approach enables organizations to stay ahead of evolving regulatory requirements and cyber threats.

Importance of Cloud GRC in Modern Enterprises
Regulatory Compliance – Helps organizations adhere to frameworks such as GDPR, HIPAA, and ISO 27001, minimizing legal risks and financial penalties.
Enhanced Security Posture – Identifies and mitigates potential security threats through automated risk detection and real-time monitoring.
Operational Transparency – Provides visibility into cloud operations, ensuring accountability and informed decision-making.
Scalability and Flexibility – Cloud GRC solutions adapt to the evolving needs of businesses as they expand their cloud infrastructure.
Cost Efficiency – Reduces compliance costs through automation, minimizing the need for manual audits and risk assessments.
Key Components of a Modern Cloud GRC Strategy
Automated Compliance Management – AI-powered tools continuously monitor compliance status and generate real-time reports.
Risk Assessment and Mitigation – Identifies vulnerabilities in cloud environments and implements proactive risk mitigation measures.
Identity and Access Management (IAM) – Ensures secure access to cloud resources through role-based access controls and authentication protocols.
Continuous Monitoring and Auditing – Tracks security incidents and compliance adherence to ensure cloud infrastructure integrity.
Policy Enforcement and Governance – Defines and enforces policies to align cloud operations with business objectives and industry regulations.
Challenges in Implementing Cloud GRC
While Cloud GRC offers numerous benefits, businesses face several challenges in its implementation:
Complex Regulatory Landscape – Keeping up with diverse and evolving compliance requirements across different regions and industries.
Integration with Existing Systems – Ensuring seamless integration of Cloud GRC solutions with legacy IT infrastructures.
Data Security and Privacy Concerns – Managing sensitive data across multi-cloud and hybrid cloud environments while ensuring compliance.
Resource Constraints – Allocating sufficient budget and skilled personnel to maintain Cloud GRC frameworks effectively.
Best Practices for Effective Cloud GRC Implementation
Develop a Comprehensive Cloud GRC Strategy – Align GRC policies with business goals and regulatory requirements.
Leverage Automation and AI – Utilize advanced analytics and machine learning to streamline compliance and risk management.
Conduct Regular Risk Assessments – Continuously evaluate and mitigate risks in cloud environments.
Ensure Strong Identity and Access Management – Implement multi-factor authentication and role-based access controls.
Educate and Train Employees – Foster a compliance-first culture by providing ongoing training on security and regulatory best practices.
Adopt a Zero-Trust Security Model – Verify every access request to minimize potential threats and data breaches.
Future of Cloud GRC
The future of Cloud GRC will be shaped by advancements in AI, blockchain, and automation. AI-powered analytics will enhance predictive risk management, while blockchain technology will introduce tamper-proof compliance tracking. Organizations investing in modern Cloud GRC strategies will gain a competitive advantage by ensuring regulatory compliance, strengthening cybersecurity, and improving operational efficiency.
Conclusion
Cloud GRC is an essential component of modern risk and compliance management, enabling organizations to navigate regulatory challenges and security threats effectively. By adopting automated tools, continuous monitoring, and AI-driven insights, businesses can ensure compliance, mitigate risks, and build a resilient cloud infrastructure. As cloud technology continues to evolve, a proactive Cloud GRC approach will be crucial in maintaining governance, security, and operational integrity in the digital era.
1 note
·
View note
Video
youtube
Simple-Security-Information-and-Event-Management-SIEM
#youtube#cybersecurity#Simple-Security-Information-and-Event-Management-SIEM#Basic Cybersecurity Principles#python
0 notes
Note
Hey! This is very random, but I saw that you work in cyber security right now. I work in data science, but I'm really interested in cyber security and considering making a switch. I was wondering what kind of cybersecurity work you do, and what has been the most helpful for you to learn what you need for your job!
Hi! Cybersecurity is a really broad field, and you can do a lot of different things depending on what your interests are.
My work is mostly focused around automating things for security, since my background is in programming. Automation is really helpful for speeding up boring, monotonous tasks that need to get done, but don't necessarily need a human involved. A good example is automated phishing analysis, since phishing reports are a big chunk of the cases that security analysts have to deal with, and an analyst usually follows the same few steps at the beginning. Rather than someone having to manually check the reputation of the sender domain, check the reputation of any links, and all of that every single time, we can build tools to automatically scan for things like that and then present the info to the analyst. The whole idea here is to automate the boring data retrieval stuff, since computers are good at that, and give the analyst more time for decision-making and analysis, since humans are good at that.
If you're coming from data science, you might be interested in detection engineering. Cybersecurity is essentially a data problem - we have a ton of logs from a ton of different sources (internal logs, threat intelligence feeds, etc.) - how do we sort through that data to highlight things that we want to pay attention to, and how can we correlate events from different sources? If you're into software development or want to stay more on the data science side, maybe you could also look into roles for software development at companies that have SIEM (Security Information and Event Management) products - these are essentially the big log repositories that organizations rely on for correlation and alerting.
As for starting to learn security, my general go-to recommendation is to start looking through the material for the Security+ certification. For better or worse, certifications are pretty big in security, much more so than other tech fields (to my knowledge). I'm a bit more hesitant to recommend the Security+ now, since CompTIA (the company that offers it) was bought by a private equity company last year. Everyone is kind of expecting the prices to go up and the quality to go down. (The Security+ exam costs $404 USD as of writing this, and I think I took mine for like $135ish with a student discount in 2022). However, the Security+ is still the most well-known and comprehensive entry-level certification that I'm aware of. You can (and should) study for it completely for free - check out Professor Messer's training videos on YouTube. There are also plenty of books out there if that's more of your thing. I'd say to treat the Security+ as a way to get a broad overview of security and figure out what you don't know. (It's certainly not a magic ticket to a job, no matter what those expensive bootcamps will tell you.)
If you aren't familiar with networking, it's worth checking out Professor Messer's Network+ training videos as well. You don't need to know everything on there, but having an understanding of ports, protocols, and network components and design is super useful. I hear a lot that the best security folks are often the ones who come from IT or networking or similar and have a really solid understanding of the fundamentals and then get into security. Don't neglect the basics!
One thing that I'll also add, based on conversations I've had with folks in my network… getting a job in cybersecurity is harder now than it used to be, at least in the US (where I am). There are a ton of very well-qualified people who have been laid off who are now competing with people trying to get into the field in the first place, and with the wrecking ball that Elon is taking to the federal government (and by extension, government contractors) right now… it's hard. There's still a need for skilled folks in cyber, but you're going to run into a lot of those "5 years of experience required for this entry-level job" kind of job postings.
On a slightly happier note, another thing you should do if you want to get into cyber is to stay up to date with what's happening in the industry! I have a masterpost that has a section with some of my favorite news sources. The SANS Stormcast is a good place to start - it's a 5 minute podcast every weekday morning that covers most of the big things. Black Hills Infosec also does a weekly news livestream on YouTube that's similar (but longer and with more banter). Also, a lot of infosec folks hang out on Mastodon & in the wider fediverse. Let me know if you want some recs for folks to follow over there.
The nice thing about cybersecurity (and computer-related fields in general, I find) is that there are a ton of free resources out there to help you learn. Sometimes it's harder to find the higher-quality ones, but let me know if there are any topics you're interested in & I'll see what I can find. I have a few posts in my cybersecurity tag on here that might help.
Thank you for your patience, I know you sent this in over a week ago lol but life has been busy. Feel free to send any follow-up questions if you have any!
10 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
🛡️ Cybersecurity and Fraud Prevention in Finance: How to Protect Your Financial Systems in 2025
In today’s digital-first financial world, cybersecurity and fraud prevention in finance are more critical than ever. With the rise of online banking, mobile payments, and digital assets, financial institutions face increasingly sophisticated cyber threats and fraud tactics.

🔍 Why Cybersecurity Is Crucial in the Finance Industry
The financial sector is one of the most targeted industries by cybercriminals due to its vast access to sensitive personal data and high-value transactions. From phishing and ransomware to account takeover and insider threats, the risk landscape continues to evolve.
Google Keyword: financial cyber threats
💣 The Cost of Poor Financial Cybersecurity
Average cost of a financial data breach: $5.9 million
70% of consumers will switch banks or services after a breach
Identity theft and digital fraud rates are up 34% YoY
Trending Search Term: banking data breaches 2025
✅ Top Strategies for Cybersecurity and Fraud Prevention in Finance
1. Adopt Multi-Layered Security Protocols
Layered security (also called “defense in depth”) uses a combination of firewalls, encryption, anti-virus software, and secure authentication to prevent unauthorized access.
Related Term: secure financial transactions
2. Leverage AI and Machine Learning for Fraud Detection
Artificial intelligence plays a key role in identifying unusual patterns and suspicious behavior in real-time. AI-powered fraud detection systems can:
Flag fraudulent transactions instantly
Analyze thousands of data points in seconds
Continuously learn and adapt to new fraud tactics
Keyword: AI in cybersecurity
3. Implement Real-Time Transaction Monitoring
Real-time monitoring tools allow institutions to track and respond to threats instantly, reducing loss and minimizing damage.
Search Intent: fraud detection systems for financial services
4. Enhance Customer Authentication Protocols
Using multi-factor authentication (MFA), biometric verification, and one-time passwords (OTPs) helps protect accounts from unauthorized access.
Search Trigger: how to protect financial data from hackers
5. Train Employees and Clients on Cyber Hygiene
Human error remains one of the top causes of breaches. Train staff and customers on:
Recognizing phishing scams
Using secure passwords
Avoiding suspicious links and public Wi-Fi
Keyword Phrase: digital financial fraud prevention tips
🔐 Top Tools and Technologies for Financial Cybersecurity in 2025
Darktrace & Vectra AI: Behavioral threat detection
Splunk & IBM QRadar: Security Information and Event Management (SIEM)
Okta & Duo: Identity and access management
ThreatMetrix: Real-time fraud analytics
📉 Common Types of Financial Cyber Threats
Phishing Attacks
Credential Stuffing
Account Takeovers
Ransomware Attacks
Insider Threats
Synthetic Identity Fraud
Search Phrase: types of financial cyber fraud
🧠 Real-World Example
In 2024, a regional credit union prevented over $2 million in fraud losses using AI-based transaction monitoring and customer biometrics. This proactive cybersecurity investment boosted customer confidence and reduced fraud-related downtime by 75%.
🚀 The Future of Cybersecurity in Finance
In 2025 and beyond, expect to see:
Widespread use of zero-trust security models
Enhanced biometric authentication
Increased use of blockchain for transaction verification
AI-powered fraud prevention as the industry standard
Keyword Used: future of cybersecurity in banking
Need Personal Or Business Funding? Prestige Business Financial Services LLC offer over 30 Personal and Business Funding options to include good and bad credit options. Get Personal Loans up to $100K or 0% Business Lines of Credit Up To $250K. Also credit repair and passive income programs.
Book A Free Consult And We Can Help - https://prestigebusinessfinancialservices.com
Email - [email protected]
📌 Final Takeaway
As digital transactions continue to grow, so does the threat landscape. Prioritizing cybersecurity and fraud prevention in finance is no longer optional—it’s essential.
Businesses and institutions that invest in AI-driven security tools, real-time monitoring, and fraud prevention protocols will not only protect their assets but also build long-term customer trust and compliance.
Need Personal Or Business Funding? Prestige Business Financial Services LLC offer over 30 Personal and Business Funding options to include good and bad credit options. Get Personal Loans up to $100K or 0% Business Lines of Credit Up To $250K. Also credit repair and passive income programs.
Book A Free Consult And We Can Help - https://prestigebusinessfinancialservices.com
Email - [email protected]
Learn More!!
Prestige Business Financial Services LLC
"Your One Stop Shop To All Your Personal And Business Funding Needs"
Website- https://prestigebusinessfinancialservices.com
Email - [email protected]
Phone- 1-800-622-0453
#financial cyber threats#banking data breaches 2025#secure financial transactions#AI in cybersecurity#fraud detection systems for financial services#how to protect financial data from hackers
1 note
·
View note
Text
Security Information and Event Management (SIEM)

Harness the power of Security Information and Event Management (SIEM) for robust cybersecurity! SIEM platforms aggregate and analyze security data from across your network, enabling real-time threat detection and response. By centralizing logs and alerts, SIEM helps identify suspicious activities, unauthorized access attempts, and potential security breaches promptly. With proactive monitoring and automated incident response capabilities, SIEM empowers organizations to strengthen their defenses and safeguard sensitive data effectively. Don't wait for threats to escalate – invest in SIEM today for enhanced security posture and peace of mind! #SIEM #Cybersecurity #CenturySolutionsGroup
Learn more: https://centurygroup.net/cloud-computing/cyber-security/
3 notes
·
View notes
Text
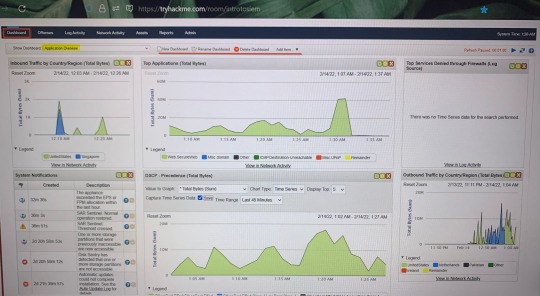
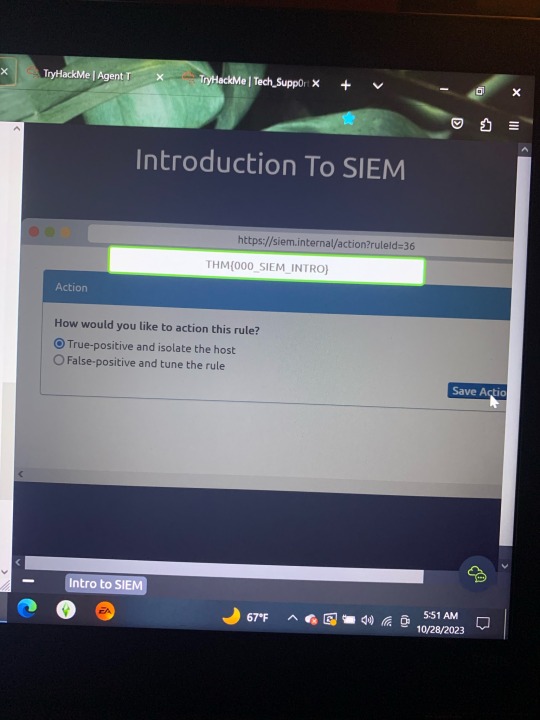

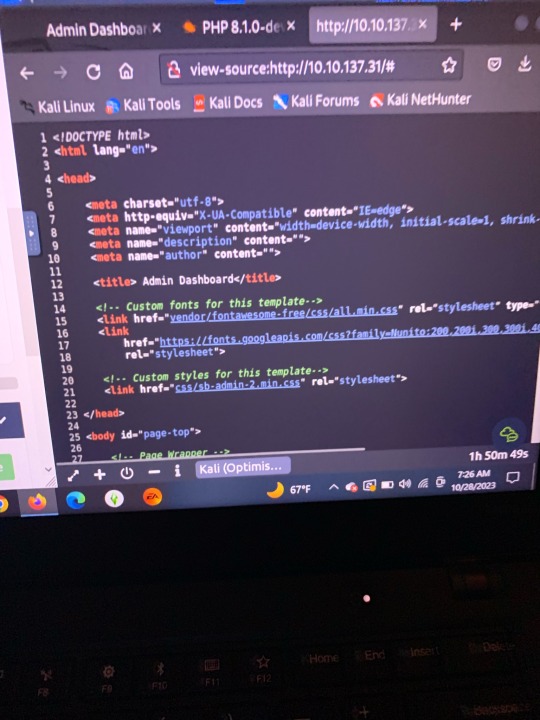
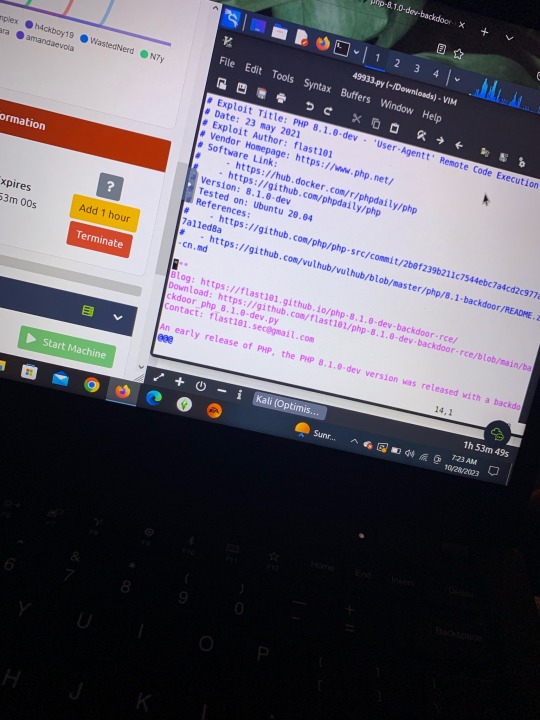
TryHackMe.. learning more of Nmap, Kali Linux, Burp Suite, etc. I am more a fan of defensive security/blue team (unpopular opinion) the first 2 pictures were walkthroughs of an SIEM (Security Information and Event Management).
#tryhackme#hacking#cool#blue team#red team#hacker#learning and growth#linux#kali linux#labs#tech#technology
4 notes
·
View notes
Text

Unlocking the Power of Azure Sentinel: A Guide to Audit Active Directory Changes
Sentinel Guru's comprehensive "Audit Active Directory Changes with Azure Sentinel" guide provides a detailed and expertly crafted resource for IT professionals and security enthusiasts. This informative article delves into the critical realm of Azure Sentinel, Microsoft's advanced cloud-native security information and event management (SIEM) solution, and its pivotal role in auditing Active Directory changes.
Readers will gain invaluable insights into configuring Azure Sentinel to monitor and track every alteration within their Active Directory environment, bolstering security and compliance efforts. The article covers key topics such as setting up data connectors, crafting effective log queries, and creating tailored alerts to promptly respond to any suspicious activities.
With a user-friendly format, practical examples, and step-by-step instructions, this resource empowers organizations to enhance their cybersecurity posture by leveraging the full potential of Azure Sentinel. Whether you're an Azure Sentinel novice or an experienced practitioner, this guide is an indispensable asset for safeguarding your Active Directory infrastructure.
3 notes
·
View notes
Text
Step-by-Step Cyber Risk Assessment & Planning Framework for IT Leaders
Cyber risk assessment and planning have become essential for safeguarding data, operations, and brand reputation in today's digital-first business environment. Cyberattacks are no longer a question of “if” but “when.” IT leaders must proactively evaluate their organization’s cybersecurity posture to stay ahead of evolving threats.
Step 1: Identify and Classify Assets
The first step in any cyber risk assessment is identifying all digital and physical assets across your organization. This includes:
Hardware (servers, laptops, mobile devices)
Software applications
Databases
Cloud infrastructure
Sensitive data (customer, employee, financial)
Classify these assets based on sensitivity, criticality, and business impact. Understanding which assets are mission-critical helps prioritize protection efforts.
Step 2: Define the Threat Landscape
Once assets are cataloged, assess the types of cyber threats that could target them. Common threats include:
Malware and ransomware
Phishing attacks
Insider threats
Supply chain vulnerabilities
DDoS (Distributed Denial of Service) attacks
Use threat intelligence platforms and recent cybersecurity reports to stay up-to-date on the most relevant threats to your industry and infrastructure.
Step 3: Identify Vulnerabilities
Now, analyze your systems for vulnerabilities that could be exploited. These might include:
Unpatched software
Weak passwords
Misconfigured firewalls
Inadequate access controls
Perform regular vulnerability scans and penetration tests to uncover security gaps. Collaborate with cybersecurity professionals to ensure comprehensive coverage.
Step 4: Evaluate Risk Impact and Likelihood
For every identified vulnerability and threat pair, assess the risk level by analyzing:
Impact: What would happen if the threat were successful?
Likelihood: How probable is it that the threat will exploit the vulnerability?
Use a risk matrix to categorize risks as low, medium, high, or critical. This helps IT leaders prioritize mitigation efforts.
Step 5: Develop a Risk Mitigation Plan
Based on your risk analysis, create a cyber risk mitigation plan. This plan should include:
Implementation of multi-factor authentication (MFA)
Encryption of sensitive data
Regular patch management
Employee cybersecurity training
Endpoint protection tools
Disaster recovery and backup procedures
Balance security and usability to ensure that security measures do not hinder productivity.
Step 6: Define a Cybersecurity Policy and Governance Framework
To formalize risk management, establish a robust cybersecurity governance framework. This includes:
Cybersecurity policies
Incident response protocols
Roles and responsibilities
Compliance guidelines (e.g., GDPR, HIPAA)
Ensure policies are well-documented, updated regularly, and communicated across departments.
Step 7: Monitor, Test, and Update Continuously
Cyber risks are dynamic. IT leaders must commit to continuous monitoring and improvement. Use tools like:
SIEM (Security Information and Event Management) systems
IDS/IPS (Intrusion Detection/Prevention Systems)
Threat hunting and analytics
Regularly test response plans through simulations and refine them based on lessons learned. Stay agile by adapting your framework as new technologies and threats emerge.
Step 8: Foster a Culture of Cybersecurity Awareness
Technology alone cannot mitigate all risks. Build a security-first culture by:
Conducting periodic employee training
Promoting phishing awareness
Encouraging secure practices (e.g., password hygiene)
IT leaders should lead by example and empower employees to be the first line of defense against cyber threats.
Cyber risk assessment and planning are no longer optional—they’re strategic imperatives. By following this step-by-step framework, IT leaders can identify vulnerabilities, prioritize threats, and implement proactive measures to safeguard business continuity.
Partnering with experienced providers like Invensis Technologies can be a game-changer for organizations looking to streamline their cybersecurity efforts. Their end-to-end cybersecurity services help businesses navigate complex digital environments with confidence.
0 notes
Text
Strengthening IT Security with Real-Time Scanning and Vulnerability Insights
In a world where digital infrastructure supports nearly every aspect of business, ensuring system security is no longer optional—it's critical. With cyber threats growing in frequency and complexity, companies must embrace a proactive and intelligent approach to risk detection and prevention.
That’s where risikomonitor.com GmbH leads the charge—offering a robust Risiko monitoring system that combines real-time IT security monitoring, deep IT vulnerability scanning, and comprehensive Risiko monitoring to help businesses stay one step ahead of cybercriminals.
In this blog, we’ll explore how a strategic blend of risk detection, continuous monitoring, and vulnerability management can create a resilient cybersecurity posture for any organization.
What is a Risiko Monitoring System?
A Risiko monitoring system is a technology-driven solution designed to identify, assess, and manage cybersecurity threats in real time. It offers centralized visibility into your IT infrastructure, helping you monitor assets, detect anomalies, and respond to risks before they escalate.
risikomonitor.com GmbH offers one of the most intelligent and scalable platforms on the market, enabling:
Continuous tracking of system health, traffic, and access behavior
Real-time alerts for suspicious activity
Risk-based asset prioritization
Integration with compliance requirements (e.g., DSGVO, ISO 27001)
Custom dashboards for different teams (IT, compliance, management)
Whether you're managing a small network or a global enterprise infrastructure, a centralized Risiko monitoring system is essential for maintaining control and visibility.
The Value of Real-Time Risiko Monitoring
Traditional security tools often operate on a reactive basis—alerting you only after something has gone wrong. That’s no longer sufficient in today’s digital landscape, where attacks can occur within seconds and spread across networks instantly.
Risiko monitoring at risikomonitor.com GmbH is designed for real-time intelligence and response. Here’s what it includes:
Monitoring all endpoints, servers, and connected devices
Detecting anomalies in user behavior and network flow
Identifying compliance violations and unauthorized access
Visualizing threat patterns and risk trends over time
Automatically categorizing alerts based on severity
With real-time data at your fingertips, you can shift from reactive firefighting to proactive risk prevention—minimizing business disruption and data exposure.
IT Security Monitoring: Full Visibility Across Your Network
IT security monitoring is the continuous process of analyzing systems, applications, and networks for signs of malicious activity or weaknesses. It ensures your cybersecurity defenses are not only in place but also functioning effectively.
risikomonitor.com GmbH’s platform includes:
Intrusion Detection and Prevention Systems (IDPS)
Log monitoring and event correlation
Endpoint monitoring and zero-trust access controls
Security Information and Event Management (SIEM) integration
Alert escalation workflows and automated remediation triggers
All data is presented in an easy-to-navigate dashboard, so your security team can quickly assess the state of your infrastructure, pinpoint potential threats, and act immediately.
IT Vulnerability Scanning: Exposing Weak Points Before Hackers Do
Even with the best firewalls and antivirus programs, vulnerabilities can still exist in outdated software, misconfigured systems, and third-party integrations. That’s why IT vulnerability scanning is a must-have layer in any cybersecurity strategy.
The risikomonitor.com GmbH platform automates vulnerability scans to:
Identify known security flaws across operating systems, web apps, and databases
Evaluate configuration errors and missing patches
Perform scheduled and on-demand scans
Prioritize vulnerabilities based on risk scoring and exploitability
Generate actionable reports with step-by-step remediation guidance
Frequent and automated scanning helps close security gaps before attackers can exploit them. When combined with your existing defenses, it drastically reduces your organization’s attack surface.
A Unified Cybersecurity Approach: Why It Matters
What sets risikomonitor.com GmbH apart is its unified approach. Instead of using multiple disconnected tools, businesses can manage all core security functions within a single, intuitive platform:
Risiko monitoring system for end-to-end threat visibility
Real-time Risiko monitoring with instant alerts
Advanced IT security monitoring capabilities
Continuous and automated IT vulnerability scanning
This not only reduces complexity but also enhances efficiency—empowering security teams with better data, faster response times, and lower operational overhead.
Who Can Benefit?
Whether you’re a medium-sized business, an e-commerce startup, or a regulated enterprise in finance, healthcare, or technology, this integrated platform is designed to scale with your needs.
It’s especially beneficial for:
Companies handling sensitive customer or financial data
IT teams aiming to automate and streamline monitoring tasks
Businesses that must comply with strict security and data protection laws
Organizations undergoing digital transformation or cloud migration
Final Thoughts
In today’s cyber-threat landscape, speed, automation, and visibility are the keys to resilience. A smart Risiko monitoring system not only protects your data but also empowers your business to grow securely.
With real-time Risiko monitoring, intelligent IT security monitoring, and automated IT vulnerability scanning, risikomonitor.com GmbH gives you the tools to detect, analyze, and neutralize threats—before they impact your business.
0 notes
Text
Real-Time Cyber Threat Intelligence: How EDSPL Detects and Neutralizes Breaches Before They Happen

Introduction: Why Real-Time Cyber Threat Intelligence Is No Longer Optional
In today’s hyperconnected world, cybersecurity has shifted from a passive necessity to an active business differentiator. Every second, organizations face a barrage of threats—from phishing emails and malware to ransomware and zero-day exploits. The question is no longer if a business will be targeted, but when. That’s where Real-Time Cyber Threat Intelligence (RTCTI) becomes the ultimate game-changer.
For modern enterprises, simply having network security or firewalls is no longer enough. You need an intelligence-driven, always-on, proactive system that can detect, analyze, and stop threats before they even get close to your data.
At EDSPL, we don’t just respond to cyber threats—we anticipate them. We predict attacks before they unfold, using real-time threat intelligence to shield your enterprise against both known and emerging risks.
What Is Real-Time Cyber Threat Intelligence (RTCTI)?
Real-Time Cyber Threat Intelligence refers to the collection, processing, and analysis of cyber threat data as it happens, enabling immediate threat detection and faster response. RTCTI goes far beyond traditional threat feeds. It uses automation, machine learning, and deep analytics to identify patterns, uncover malicious intent, and neutralize attacks in progress.
The High Stakes: What Happens Without Real-Time Intelligence
Imagine a scenario where a phishing email slips through filters. Within minutes, credentials are stolen, malware is planted, and lateral movement begins within your network. If you're relying on weekly scans or daily logs, by the time you catch it—your data is already gone.
Now contrast that with EDSPL's real-time approach:
A suspicious login pattern is detected in milliseconds. Threat intelligence confirms correlation with known malicious IPs. Automated response isolates the endpoint, cuts off access, and alerts the SOC team. Breach attempt thwarted—before any data is touched.
This is the power of EDSPL’s Real-Time Cyber Threat Intelligence.
How EDSPL Powers RTCTI: A Behind-the-Scenes Look
1. Global Threat Intelligence Feeds
At EDSPL, we integrate real-time threat feeds from:
Industry-leading platforms (FireEye, IBM X-Force, AlienVault, etc.)
Open-source intelligence (OSINT)
Government and ISAC advisories
Proprietary honeypots and decoys deployed worldwide
These sources constantly update our threat intelligence database, ensuring we stay ahead of even the most advanced threat actors.
2. Security Operations Center (SOC) 24x7x365
Our in-house SOC is the nerve center of our RTCTI system. With round-the-clock vigilance, our analysts monitor anomalies, respond to alerts, and hunt threats proactively. Every activity, from system logs to endpoint behavior, is streamed live into our monitoring environment, enabling real-time decision-making.
Explore our full range of services
3. SIEM + SOAR Integration
We use top-tier Security Information and Event Management (SIEM) tools to correlate data across endpoints, cloud security, application security, and on-prem systems.
But we don’t stop there. Our Security Orchestration, Automation, and Response (SOAR) tools automate the playbooks. This ensures:
Faster incident triage
Reduced Mean Time to Detect (MTTD)
Reduced Mean Time to Respond (MTTR)
4. AI-Powered Anomaly Detection
Static rules and signatures aren’t enough. Our AI/ML models learn and adapt continuously, identifying deviations from “normal” behavior. Whether it's an employee logging in from an unusual location or a file being downloaded at an odd time, our system catches the smallest red flags.
5. Endpoint Detection & Response (EDR)
Our RTCTI stack includes next-gen EDR, which monitors every action on your devices in real time. From USB connections to command-line activity, EDR ensures no breach goes unnoticed.
Real-Life Use Case: How EDSPL Prevented a Ransomware Attack
In early 2025, a client’s internal user unknowingly downloaded a malicious attachment disguised as an invoice. The malware silently tried to encrypt files and escalate privileges. Within 4 seconds:
EDSPL's SIEM flagged anomalous activity.
Our SOAR platform triggered an auto-isolation of the device.
The malware was quarantined, and logs were sent for forensic analysis.
No data was lost. No operations were disrupted.
That’s what real-time threat intelligence looks like in action.
RTCTI Is Not Just for Enterprises—SMEs Need It Too
It’s a myth that only large corporations need advanced threat intelligence. In fact, small and mid-sized enterprises are often prime targets—because they have weaker defenses.
At EDSPL, we’ve designed scalable RTCTI packages to suit organizations of all sizes, backed by our expertise in mobility, compute, storage, and backup.
Key Benefits of EDSPL’s Real-Time Threat Intelligence
Proactive Threat Detection
Stop threats before they reach critical systems.
Rapid Incident Response
Our automation ensures no time is wasted during an attack.
Intelligent Insights
Go beyond alerts—understand the context behind every threat.
AI-Driven Accuracy
Eliminate false positives. Focus only on real threats.
Customizable for Your Industry
From finance and healthcare to retail and manufacturing—we tailor defenses to your risk landscape, including switching, routing, and data center switching infrastructure security.
Industries That Trust EDSPL for RTCTI
We serve organizations across sectors, including:
BFSI (Banking, Financial Services, Insurance)
Healthcare
E-commerce
EdTech
Manufacturing
Government and Public Sector
How EDSPL Stays Ahead of Cyber Criminals
Cyber criminals evolve every day—but so do we. Here’s how EDSPL maintains a competitive edge:StrategyHow It HelpsThreat Hunting TeamsActively search for hidden threats before they strike.Red Team SimulationsSimulate real attacks to test & improve defenses.Zero-Day Threat MitigationHeuristic detection + rapid signature updates.Dark Web MonitoringTrack stolen credentials and brand mentions.Incident Drill PlaybooksBe ready with tested, automated response plans.
Why EDSPL Is the Right RTCTI Partner for You
Choosing a cyber partner is about trust. With EDSPL, you get:
✅ Experienced Cybersecurity Professionals ✅ Real-Time Visibility Across All Layers ✅ Custom Playbooks and Reporting Dashboards ✅ Compliance-Ready Solutions ✅ Managed and maintenance services that ensure long-term protection
Conclusion: Stop Attacks Before They Even Begin
The threats are getting smarter, faster, and more dangerous. If you’re waiting to react to a breach, you’re already too late.
With Real-Time Cyber Threat Intelligence from EDSPL, you gain an unfair advantage. You move from being a passive target to a proactive defender.
Don’t wait for the breach—predict it, detect it, and neutralize it with EDSPL.
Want to Get Started?
Reach Us or Get In Touch to future-proof your cybersecurity infrastructure. Understand our background vision and commitment to enterprise security excellence.
Ready to secure your business? Contact our experts today and get a free consultation tailored to your organization’s needs.
📧 Email: [email protected] 🌐 Website: www.edspl.net
Follow us on social media for the latest updates and insights:
🔗 Facebook | LinkedIn
0 notes
Photo

Jun 24, 2025 09:30 PM IST CERT-In has urged people to replace their passwords instantly, allow multi-factor authentication (MFA), and swap to passkeys wherever attainable NEW DELHI: Indian Computer Emergency Response Team (Cert-In) has issued a contemporary advisory asking individuals to comply with good cybersecurity hygiene following stories of a large knowledge breach involving 16 billion on-line credentials. FILE - The breach, first reported by the web site Cybernews, consists of usernames, passwords, authentication tokens, and metadata leaked from a number of platforms. (AP) The breach, first reported by the web site Cybernews, consists of usernames, passwords, authentication tokens, and metadata leaked from platforms resembling Apple, Google, Facebook, Telegram, GitHub, and a number of other VPN providers. “This seems to be a consolidated dataset, and among the credentials could also be outdated or already modified. However, we’re issuing the advisory to induce individuals to comply with good cybersecurity hygiene,” a senior official at Cert-In, the nation’s nodal company for cybersecurity incident response, stated. The advisory was first launched on Monday. The company has urged people to replace their passwords instantly, allow multi-factor authentication (MFA), and swap to passkeys wherever attainable. The advisory additionally recommends operating antivirus scans and conserving programs updated to guard towards malware. The cybersecurity company suggested organisations to implement MFA, restrict consumer entry, and use intrusion detection programs (IDS) and Security Information and Event Management (SIEM) instruments to detect suspicious exercise. It additionally really useful that corporations examine that their database aren’t publicly uncovered and make sure that delicate knowledge is encrypted. The huge dataset, which is believed to be obtainable on the darkish internet, has been reportedly compiled from 30 completely different sources, principally by way of infostealer malware. The dataset might allow attackers to hold out phishing, account takeovers, ransomware assaults, and enterprise e-mail compromises, stated the Cert-In advisory. “This is a systemic crimson flag,” stated Gaurav Sahay, cybersecurity professional and founding accomplice at Arthashastra Legal. “The breach is decentralised, tougher to detect, and far more troublesome to repair. We’re prone to see a wave of account takeovers, particularly on cloud/e-mail providers, banking or fintech apps, developer platforms, and authorities portals.” Sahay added that password reuse stays rampant, and the dearth of MFA on many accounts makes even older credentials harmful. “This is a watershed second in cybersecurity, a reminder that the human ingredient stays the weakest hyperlink in digital safety.” Read More: https://news.unicaus.in/business/cert-in-points-advisory-after-knowledge-breach-of-16-billion-credentials-asks-individuals-to-vary-passwords/
0 notes
Text
Discover How Digital Risk Protection Services Safeguard Your Business from Online Threats
In today’s interconnected world, businesses face a growing number of cyber threats that can compromise data, reputation, and revenue. From phishing scams and account takeovers to dark web exposure and brand impersonation, digital dangers are evolving fast. That’s where digital risk protection services come in. These specialized services offer a proactive approach to detecting and responding to digital threats before they cause real damage. By continuously monitoring your brand’s digital footprint, these solutions help organizations stay one step ahead. For any business aiming to survive and thrive in the digital age, investing in digital risk protection is no longer optional—it’s essential.
Understand the Basics of Digital Risk Protection Services
Digital risk protection services are security solutions designed to identify, monitor, and respond to external digital threats targeting businesses. Unlike traditional cybersecurity tools that focus on internal networks, these services scan the surface web, deep web, and dark web for threats involving your brand, executives, or customers. They help safeguard sensitive data, prevent impersonation, and protect your company’s digital reputation. These services often include real-time alerts, risk scoring, and incident response support. By offering a broader perspective of potential risks outside the firewall, digital risk protection provides an added layer of security vital for today’s digital-first business environments.
Learn How These Services Identify Online Threats Early
One of the primary benefits of digital risk protection services is their ability to identify potential online threats before they escalate. These services leverage advanced algorithms, threat intelligence feeds, and machine learning to scan the digital landscape for suspicious activity. Whether it’s the sale of stolen credentials on the dark web or fake websites mimicking your brand, these systems provide early warning signs. Timely detection enables organizations to take swift action, such as blocking malicious content, alerting stakeholders, or investigating breaches. This proactive approach helps minimize financial loss, legal consequences, and reputational damage from emerging digital threats.
See How Your Brand Reputation Stays Protected
Your brand reputation is one of your most valuable assets—and digital risk protection services play a key role in defending it. These services actively monitor online mentions, fake domains, social media impersonations, and malicious content that could harm your company’s image. Whether a cybercriminal is spoofing your website or spreading false information, digital risk protection allows for immediate detection and response. By preserving customer trust and preventing negative exposure, businesses maintain credibility in the marketplace. In today’s always-online environment, where brand perception can shift quickly, having a digital protection strategy is vital to keeping your public image intact.
Explore Tools Used in Digital Risk Protection Services
Digital risk protection services utilize a range of cutting-edge tools to provide comprehensive coverage. These include AI-powered threat detection platforms, dark web crawlers, domain monitoring software, and real-time alert systems. Some solutions also integrate with security information and event management (SIEM) platforms for enhanced incident response. Other tools track credential leaks, phishing kits, and fraudulent app listings. The effectiveness of digital risk protection lies in its layered approach—combining technology with expert analysis to identify and mitigate threats across various digital channels. By leveraging the right mix of tools, businesses can ensure a resilient defense against evolving digital risks.
Monitor Dark Web Activity Linked to Your Business
The dark web is a hotspot for illegal activity, including the sale of stolen data, leaked credentials, and counterfeit brand assets. Digital risk protection services continuously monitor dark web forums, marketplaces, and encrypted platforms for any mention of your company, employees, or clients. This intelligence helps you stay ahead of cybercriminals looking to exploit your brand for profit. If a compromised database or sensitive document is found, you can take corrective measures swiftly, such as resetting passwords or notifying affected parties. Early visibility into dark web activity can significantly reduce the time to detect and respond to security breaches.
Prevent Phishing and Impersonation with Real-Time Alerts
Phishing attacks and impersonation attempts are among the most common and damaging digital threats. Digital risk protection services combat these risks by offering real-time monitoring and instant alerts for suspicious activities involving your brand. Whether it’s a fake email pretending to be your CEO or a cloned website targeting customers, these alerts empower your security team to act immediately. Quick takedown requests and preemptive domain registration are just a few preventive actions these services enable. By staying vigilant and reacting quickly, organizations can stop impersonators in their tracks and protect their customers from falling victim to online scams.
Protect Social Media Accounts Through Digital Risk Protection Services
Social media is a powerful business tool—but it’s also a frequent target for hackers and impersonators. Digital risk protection services provide constant monitoring of social platforms to detect unauthorized accounts, brand impersonation, or the spread of false content. These services alert your team to any suspicious activity, allowing for quick reporting and takedown. They also help ensure account credentials remain secure and flag unusual login attempts or behavioral anomalies. With social media playing a critical role in customer engagement and brand identity, protecting these accounts through digital risk protection is essential to maintaining trust and communication with your audience.
Conclusion
In an era where cyber threats are growing more sophisticated and frequent, digital risk protection services offer businesses a proactive shield against online vulnerabilities. These services go beyond traditional cybersecurity measures by monitoring the entire digital ecosystem—including dark web forums, phishing schemes, and social media impersonations. From safeguarding sensitive data to preserving brand reputation, they provide a vital line of defense. As threats continue to evolve, organizations that prioritize digital risk protection are better positioned to mitigate risks, respond quickly to incidents, and maintain customer confidence. Investing in these services is a smart and necessary step for securing your digital future.
0 notes
Text
Data Loss Prevention Market Size Expected to Reach USD 10.05 Bn By 2030

North America dominated the global Data Loss Prevention (DLP) Market Size in 2022, holding a commanding market share of 39.67%, driven by strong cybersecurity frameworks, stringent regulatory compliance standards, and widespread enterprise digitization. The global DLP market, valued at USD 1.84 billion in 2022, is projected to reach USD 10.05 billion by 2030, growing at a CAGR of 24.1% during the forecast period (2023–2030).
DLP technologies in North America are being rapidly adopted by sectors like BFSI, healthcare, defense, and retail to counter rising threats of insider data leaks, ransomware, and regulatory non-compliance.
Key Market Highlights:
2022 Global Market Size: USD 1.84 billion
2030 Global Market Size: USD 10.05 billion
CAGR (2023–2030): 24.1%
North America Market Share (2022): 39.67%
Market Outlook: Steady growth fueled by increasing data breaches and expanding regulatory mandates such as HIPAA, GLBA, and CCPA
Key Players in the North American DLP Market:
Symantec (Broadcom Inc.)
Forcepoint
Digital Guardian (Fortra)
McAfee Corp.
Microsoft Corporation
Cisco Systems Inc.
Trend Micro Inc.
Proofpoint Inc.
Check Point Software Technologies
Varonis Systems
Zscaler, Inc.
Request for Free Sample Reports: https://www.fortunebusinessinsights.com/enquiry/request-sample-pdf/data-loss-prevention-market-108686
Market Dynamics:
Growth Drivers:
Escalating volume and sensitivity of enterprise data across cloud platforms
Regulatory pressure from laws like GDPR, CCPA, HIPAA, and PCI DSS
Increasing insider threats and sophisticated ransomware attacks
Remote work culture accelerating endpoint data vulnerability
Adoption of cloud-based and hybrid DLP solutions by enterprises for better scalability and visibility
Key Opportunities:
Expansion of DLP to protect unstructured data across collaboration tools and endpoints
Integration with security information and event management (SIEM) systems
Growing need for AI/ML-powered policy automation and anomaly detection
Increased adoption in mid-sized businesses via SaaS-based DLP offerings
Opportunities in verticals like education, legal, and public sector that manage sensitive personal data
Technology & Application Scope:
Deployment Models: On-premises, cloud-based, and hybrid
Application Areas: Network DLP, endpoint DLP, cloud DLP
Industries Served: Banking & Finance, Healthcare, Retail, IT & Telecom, Government, Education
Use Cases: Intellectual property protection, regulatory compliance, data visibility & classification, real-time policy enforcement
Segments Covered with:
By Component
By Type
By Industry
Speak to Analyst: https://www.fortunebusinessinsights.com/enquiry/speak-to-analyst/data-loss-prevention-market-108686
Recent Developments:
March 2024 – Microsoft launched enhanced DLP capabilities within Microsoft 365 Purview, enabling real-time risk mitigation and auto-classification for Teams, SharePoint, and OneDrive.
September 2023 – Forcepoint introduced a unified cloud-native DLP platform integrated with Zero Trust architecture, improving visibility across hybrid environments.
June 2023 – Cisco expanded its SecureX platform with AI-based anomaly detection and insider risk analytics, enhancing its enterprise-grade DLP suite.
Market Trends in North America:
Widespread transition to cloud-based DLP platforms with AI integration
Emphasis on protecting data-in-motion and data-at-rest across complex environments
Rising adoption of Managed Security Service Providers (MSSPs) for DLP as a service
Increased focus on behavioral analytics and contextual awareness in DLP systems
DLP convergence with endpoint detection and response (EDR) and identity management tools
Conclusion:
North America remains the epicenter of innovation and deployment in the Data Loss Prevention market, supported by a highly digitized economy, regulatory rigor, and advanced cybersecurity infrastructure. As threats grow more sophisticated and the cost of data breaches escalates, the region’s demand for comprehensive, intelligent, and automated DLP solutions is expected to surge.
Vendors who provide flexible, cloud-native, and AI-enhanced DLP offerings are best positioned to capture this accelerating market growth.
#Data Loss Prevention Market Share#Data Loss Prevention Market Size#Data Loss Prevention Market Industry#Data Loss Prevention Market Analysis#Data Loss Prevention Market Driver#Data Loss Prevention Market Research#Data Loss Prevention Market Growth
0 notes
Text
Log Management Market Report: Unlocking Growth Potential and Addressing Challenges
United States of America – June 23, 2025 – The Insight Partners is excited to launch its latest report titled "Log Management Market: Driving Security and Operational Intelligence." The report captures the escalating importance of log data in modern IT environments and security frameworks.
Overview of Log Management Market
Organizations across industries are generating massive volumes of logs daily. Managing and analyzing these logs is no longer optional — it’s critical for cybersecurity, system optimization, and compliance. Log management has evolved from traditional storage to intelligent, AI-enhanced platforms.
Key Findings and Insights
Market Size and Growth
The global log management market is expected to grow at a CAGR of 12.8% during 2023–2031, propelled by digital transformation and increasing security threats.
Key Factors Driving the Market
Surging need for real-time threat detection and response
Increased complexity of IT systems and hybrid infrastructure
Growing regulatory requirements for data access and transparency
Market Segmentation
By Component:
Software
Services
By Deployment:
On-premise
Cloud
By End-User:
BFSI
Healthcare
IT & Telecom
Retail
Government
Spotting Emerging Trends
Technological Advancements
AI-driven anomaly detection
Integration with Security Information and Event Management (SIEM) tools
Changing Consumer Preferences
Preference for unified observability platforms
Demand for scalable solutions across cloud-native applications
Regulatory Changes
Expansion of compliance mandates (e.g., SOC 2, GDPR, HIPAA)
Industry-specific log retention policies
Growth Opportunities
Expansion into SMB segments with cost-effective solutions
Rise of managed security services requiring log integration
Automation and AIOps adoption to reduce manual monitoring
Conclusion
The Log Management Market is positioned at the intersection of cybersecurity and IT efficiency. This report is a must-read for enterprises, IT leaders, and cybersecurity firms looking to future-proof their data and digital infrastructure through smart log analytics and compliance-driven innovation.
About The Insight Partners The Insight Partners is a leading provider of syndicated research, customized research, and consulting services. Our reports combine quantitative forecasting and trend analysis to offer forward-looking insights for decision-makers. With a client-first approach, we deliver actionable intelligence and strategic guidance across various industries.
Visit our website- https://www.theinsightpartners.com/ to learn more and access our comprehensive market reports.
Get Sample Report- https://www.theinsightpartners.com/sample/TIPRE00006168
0 notes