#TSQL
Explore tagged Tumblr posts
Text
Unlock SQL Mastery: The Ultimate T-SQL Guide for SQL Server Pros
youtube
2 notes
·
View notes
Text
New #Blog post: Hidden risks in #Microsoft #SQLServer Agent job logging: How retry settings can compromise your logs - the problem you didn't know you had! ⚠
0 notes
Text
Temporal Tables for Data Tracking in T-SQL Server
Understanding Temporal Tables in T-SQL Server: Efficient Data Tracking and History Management Hello, SQL enthusiasts! In this blog post, I will introduce you to Temporal Tables in T-SQL Server – one of the most powerful features in T-SQL Server. Temporal tables allow you to track and manage data changes over time, making it easier to maintain a history of your records. They are essential for…
0 notes
Text
somewhat recently someone shared an xkcd here that said that you can treat tables in gsheets like a database and run sql on them using QUERY(). and that is technically true, but this function uses a special google query language which sucks and can barely do anything. maybe when they said "sql" they were being super literal, as in like first standard of sql set in the fucking 80s.
5 notes
·
View notes
Text
T-SQL Stored Procedure Best Practices - Archive Log Table 2 of 3
In this video, I take you through the task of creating a stored procedure in Sql Server 2008 using the Adventureworks database, … source
0 notes
Text
NAJM MALIK
I am an energetic Staffordshire University applied PHD - QUT with Wireless Networks , AI and neural networks as my majors. I have joined the network of people who have guided me with their skills and culture to establish myself as a System Analyst and Programmer for AI based web solutions . Optimize learning and enhancing modular design of the neural network architecture that has been challenging and time -consuming for me and subsequently manipulating, controlling the logic governing these learning mechanism are the main areas of my research. As a developer for androids and Apple based platforms I have established expertise in apps programming ,GPS, Sateliite systems and apps plugins. I had established expertise in Optimized networking platforms for single and multiple corporate networks , integration of corporate networks and trouble shooting of WAN and MAN . I had worked with web solutions PHP based systems .Retrospectively having gained the expertise at mars multimedia as a web content developer and senior programmer for Query integration, WAP , UML , TSQL ,Query optimization and PHP and ASP.net , its has given me the added confidence to establish and conduct online projects for Mars.
1 note
·
View note
Text
Software Engineer - Power BI, Python, SSRS, TSQL,DAX
: This role requires good knowledge of Python and PowerBI Able to write DAX query Able to work on SSRS reports Able to write…+ years of experience in PowerBI 2+ years of experience in SSRS 2+ years of experience in Python At UnitedHealth Group… Apply Now
0 notes
Text
Software Engineer - Power BI, Python, SSRS, TSQL,DAX
: This role requires good knowledge of Python and PowerBI Able to write DAX query Able to work on SSRS reports Able to write…+ years of experience in PowerBI 2+ years of experience in SSRS 2+ years of experience in Python At UnitedHealth Group… Apply Now
0 notes
Text
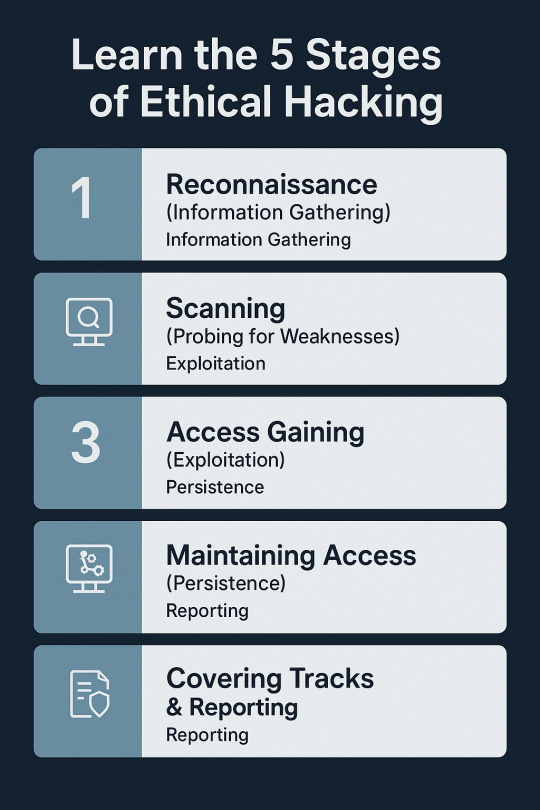
Learn the 5 Stages of Ethical Hacking
With threats on the digital platform ever-present today, ethical hacking has emerged as an essential method for protecting systems, networks, and information. As malicious hackers use vulnerabilities to carry out crime, ethical hackers (or white hat hackers) utilize their craft for good purposes — finding and fixing vulnerabilities before threat actors have the chance to do so. But ethical hacking is not a random process. It follows a methodical process to make every step legal, efficient, and in accordance with the security goals of the organization. This process is typically in five stages, which are very specific and trace ethical hackers from reconnaissance to reporting. Let us dive into detail about what these stages involve and why they're crucial for a successful cyber defense strategy. Phase 1: Reconnaissance (Information Gathering) Also known as: Footprinting Reconnaissance is the first and, arguably, the most important phase of ethical hacking. It's akin to the "research" phase. Ethical hackers find out as much as they can about the target before they try to break into it. This phase lays the groundwork for everything that follows. Aims: •Get familiar with the digital footprint of the target •Identify weak spots and vulnerable entry points • Steal away undetected while gathering information Methods Used: • Passive Reconnaissance – No contact with the target (e.g., use of WHOIS lookup, DNS records, social media, public databases). • Active Reconnaissance – Direct contact with the system (e.g., ping sweeps, port scanning, traceroutes). Tools: •Maltego •Nmap •Recon-ng •Google Dorking Why it matters: Proper reconnaissance saves time and makes the rest of the hacking process easier. It also replicates the first steps taken by real-world cyber attackers.
Phase 2: Scanning (Probing for Weaknesses) After the ethical hacker has sufficient surface information, scanning is the next phase where more intensive probing is done to identify particular vulnerabilities in the system. Objectives: • Discover open ports and services • Detect live systems • Identify running OS and applications • Discover known vulnerabilities
Methods: • Port Scanning – Scanning which ports are open and what services are running.
• Network Mapping – Knowledge of the network topology and the identification of the hosts. • Vulnerability Scanning – System scanning for known configuration or software vulnerabilities. Tools: • Nessus • Nikto • OpenVAS • Wireshark Why it matters: Scanning gives the hacker a technical snapshot of how healthy the system is and assists the hacker in determining which vulnerabilities to exploit during the exploitation phase.
Phase 3: Access Gaining (Exploitation) This is where ethical hacking really gets to work and occurs. The hacker attempts to break into the system by taking advantage of the weaknesses revealed in the scanning. It sounds like the climax, but it's a very choreographed and strategic move that makes ethical hacking. Objectives: • Use a known exploit to gain access • Increase privileges (for example, from guest to admin) • Identify the amount of potential damage that an actual perpetrator might do Methods • Buffer overflow attacks • tSQL injection • Brute-force password cracking • Misconfiguration exploitation Tools: • Metasploit • Hydra • John the Ripper • SQLMap Why it matters: Access that is gained allows organizations to see how much access an attacker would have, giving them a chance to cut off critical points of access before damage is being caused.
Phase 4: Maintaining Access (Persistence) During this phase, the ethical hacker mimics what an actual attacker would do once they have compromised the system — maintain access to keep gathering data or installing malware. Objectives: •Create backdoors or remote access tools •Mimic advanced persistent threats (APT) •Illustrate long-term risk exposure Methods: •Installing Trojans or rootkits (ethically and with permission) •Creating rogue user accounts •Altering system services for covert access Tools: •Netcat •Backdoor Factory •MSFVenom Why it matters: This stage assists in determining how long a system might remain compromised undetected — an important consideration when analyzing incident response measures. Phase 5: Covering Tracks & Reporting While malicious hackers attempt to cover their tracks, ethical hackers do the opposite — they make sure all actions taken are logged, traced, and completely documented. Reporting is the last and possibly most useful step of the ethical hacking process.
Goals: • Restore the system to normal • Report to the organization • Deliver remediation steps that are actionable What's in the Report: • Disclosed vulnerabilities • Attacks tried and success rates • Possible impact of each vulnerability • Fix recommendations and improvements Why it matters: The final-report is a blueprint that the organization can use to make its defenses harder. It transforms an ethical hack from a test into an actionable business tool.
The Legal and Ethical Side It's important to emphasize: Ethical hacking should be done with the right permission. That is, written permission, well-delineated scope, and test boundaries. Unapproved hacking—no matter what "noble cause"—is against the law and punishable by it. Why the 5 Phases are Important Together, these five phases create a repeatable, effective cycle of security testing. They: •Echo the methods of actual attackers •Detect potential threats prior to exploitation •Enhance organizational cybersecurity stance •Meet standards such as ISO/IEC 27001, PCI-DSS, etcFinal Thoughts Ethical hacking is not merely about cracking open systems—it's about learning them, enhancing them, and helping to make the internet a more secure place. From IT managers to aspiring cybersecurity analysts to entrepreneurs, recognizing the five stages of ethical hacking can assist you in making better, more secure decisions. With increasing cybercrime, ethical hacking is no longer a choice — it's a necessity. And as with any strategic process, its success depends on how systematically and responsibly it's carried out.
Website: https://www.icertglobal.com/course/ceh-certification-training/Classroom/62/3044
0 notes
Text
Join top SQL Classes in Pune to master database management, SQL queries, and data analysis. Learn from experts with hands-on practice and real-world examples!
1 note
·
View note
Video
youtube
SQL - How to Use Rollup Operator to Calculate SubTotal and GrandTotal
As we know, ROLLUP is an extension of the SQL GROUP BY clause, used to generate summary reports with subtotals and grand totals. It helps in aggregating data at multiple levels of granularity.#sql #datascience #data #database #tsql #dataengineering #bigdata #database #datamodeling #snowflake #programming
0 notes
Text
Resolving and Preventing Deadlocks in SQL Server
#Blog post: Resolving and Preventing Deadlocks in #Microsoft #SQLServer #MadeiraData #TSQL #AzureSQL
Deadlocks in SQL Server can be frustrating and can cause significant performance and reliability issues. A deadlock occurs when two or more transactions are waiting for each other to release a lock on a resource, resulting in a situation where no transaction can proceed, and eventually, one of them is automatically killed and rolled back. This can happen when two transactions try to access the…
0 notes
Text
Mastering Window Functions in T-SQL Server
Mastering Window Functions in T-SQL Server: A Complete Guide Hello, fellow SQL enthusiasts! In this blog post, I will introduce you to T-SQL Window Functions – one of the most powerful and versatile features in T-SQL Server – Window Functions. Window functions allow you to perform calculations across a set of table rows related to the current row without collapsing data. They are essential for…
0 notes
Video
youtube
SQL - How to Use Rollup Operator to Calculate SubTotal and GrandTotal
As we know, ROLLUP is an extension of the SQL GROUP BY clause, used to generate summary reports with subtotals and grand totals. It helps in aggregating data at multiple levels of granularity.
#sql #datascience #data #database #tsql #dataengineering #bigdata #database #datamodeling #snowflake #programming
0 notes
Text
0 notes