#and now that i have Mandated Offline Time... it's a great time to start!!!
Explore tagged Tumblr posts
Text
i didn't realize microsd prices were so fucking low now... holy shit... like i figured they'd be cheaper than i remembered, but i had an easier time finding a 2-card bundle than a single card, and the double bundle was STILL ~$15... these same cards would have cost $200 EACH in 2010... i am turning into dust...
#'back in my day our pc disk space was measured in mb and would run out of space from downloading too many dogshit jpegs' etc etc#ANYWAY lol i wanna replay x but i have SOOOOO many legendaries and event poke.mon on my current save#so i might pull a few strings. yknow. teehee. yarhar and all that.#i want to get reacquainted with kalos for my pk.mn au AND for the new game when it comes out next year :3c#and now that i have Mandated Offline Time... it's a great time to start!!!#📌 [ my posts. ]#💭 [ my thoughts. ]
2 notes
·
View notes
Text
Elden Ring - Impressions
From Software have a specific formula for these things. It sort of goes as follows:
The world has gone to shit. Its appointed custodians are shirking their duties or they've switched sides, and the Lore-Specified Ritual of Putting Stuff Right demands conditions that can't currently be guaranteed. The world consequently falls back on The Nobody as its designated savior, and explains away the relative lack of allies or resources as well as the generally crumbling locales you'll work through. You might as well call this Every Souls Game Ever. For other titles like Bloodborne, you can copy-paste the same info in a new field and then add "Oh, and it's all caused by Eldritch monstrosities the locals have taken to worshipping".
For better or worse, Elden Ring is very much a coalescing of everything SoulsBorne to have been released under Sony and Bamco's auspices, like a Greatest Hits compilation of ways in which game designers might go about brutally murdering their test players. It's also an unabashed love letter to titles that usually settle somewhere on the opposite end of ithe difficulty spectrum, like Legend of Zelda: Breath of the Wild or The Elder Scrolls V: Skyrim. It's cherry-picked these last two games' sense of openness and the notion that anything that's visible to you can be physically reached with some effort. In doing so, it also opens up the usually confined playspace of your typical Soulsborne, and lets you effectively pick your battles and rethink your angles of approach as you'd like, which is entirely new for the genre. We typically were set on clearly defined paths and in environments that were at least somewhat linear, but now the Lands Between are effectively open to you from the moment you leave the tutorial area. It doesn't mean areas further removed from your starting point will be as easy as Limgrave's first few hills and valleys, however, with the game adequately using design and scale as a means to indicate an enemy's relative toughness.
With a little patience and some natural progression, you'll attract the attention of Melina the Finger Maiden, whose job it is to serve as any other Soulsborne-mandated points bank. Give her Runes, this game's variant on Souls, and you'll be able to invest in your character's statistics. Upon returning to the Church of Elleh (which you can't miss), you'll also run into Renna, a witch that offers to bestow upon you the power to call forth Spirits. The first one calls forth a pack of three wolves, which are great at harrassing enemies to give you time enough to recuperate or reposition, and there's a fair few others to collect, each with their own pros and cons. This results in a difficulty system that very quickly turns granular and also substantiates the designers' claims about creating an approchable, if challenging experience.
With the amount of gameplay-related prosthetics inlaid in the game and lore proper, you're left with systems that'll help newcomers and tantalize series veterans, and that also democratize the "feel" of a Soulsborne multiplayer experience for players stuck offline or with unreliable connections. These Spirits might surprise veterans with how effective they are, compared to other Soulsborne titles' own plot-dictated ethereal helpers, but they're also not so versatile as to completely de-emphasize player skills. To put it simply, it just speaks to From having realized that some people love their lore, but simply don't have the time, patience or inclination to git gud, as it were. You can count me as one of 'em, for instance. I love Miyazaki's usual framing devices, but I can't be assed to figure out my i-frames, if you catch my drift.
The end-result, to put it simply, just works. That is, the gameplay and intentionality of the title both work as intended. The PC version, though? It's nowhere near Cyberpunk 2077 before its latest patch, but it does occasionally struggle to maintain a consistent framerate, and it dips at frequencies that don't exactly feel like it's a hardware issue. My current rig outclasses the Recommended specs, and I'll still occasionally notice my FPS counter dipping from the mid-sixties to the low thirties at max detail in 1080p resolutions. That blip then resolves itself and comes back at random some time later, no matter if the game is rendering an open field or a pod of six enemies howling for my blood while wind physics makes the local grass sway. I've also got a bone to pick with the game's Brightness slider, seeing as no amount of fiddling with light or contrast undoes my initial impression of the Lands Between looking a bit washed out, if not unusually yellowish in tone. I'm getting decent color grades everywhere else, so it doesn't look like a monitor issue.
As ever, this isn't a review. I'm just glad to have made it to Level 14 with my starting Wretch (I just found pants! Huzzah!) and I'll keep chipping away at the Lands Between until one of the suzerains reponsible for the Shattering falls beneath my blade. Considering how shit I am, it'll probably take a while.
7 notes
·
View notes
Note
Hi, sorry for call you sooner. Technical problems on tumblr in my case. So how are feeling due coronasation pandemy? Also how is your going? I'm really curious, it looks like that Billy's power are growing without knowing. Hope it doesn't get out of control😜
No worries, your timing is great actually.
So this is going to be an announcement to all my followers:
I've been ok during the outbreak so far but I literally just found out something that could impede future updates.
Lately my internet at home has been very spotty and the other day it finally died altogether. Right now I'm using my mobile data on my phone to respond to messages. My data plan is very limited and I'm already almost out for the month. I've been relying on the internet at my job to get stuff done during any downtime. Unfortunetly all my files are on an online server and like a dummy I did not download them to work offline from my home computer before my home internet died.
I just found out the governor of my state is forcing all nonessential businesses to close which mine does qualify as nonessential but I know the owners of the business have been finding loopholes to stay open(which is stupid, but hey, capitalism...). A service man was supposed to come tomorrow to try and repair my home internet but I don't know if this new government mandate will effect that. So if I'm out of work starting tomorrow and can't get my internet repaired I'll likely be unable to do anything or respond to messages until future notice. 😰 I'll try to keep everyone posted but if I go MIA for a bit it just means I currently have no internet access. I do appreciate the concern and pray everyone is doing ok.
2 notes
·
View notes
Text
As China’s Communist Party turns 100, economic challenges loom | Business and Economy News
New Post has been published on https://tattlepress.com/economy/as-chinas-communist-party-turns-100-economic-challenges-loom-business-and-economy-news/
As China’s Communist Party turns 100, economic challenges loom | Business and Economy News

Shenzhen, China – Private education companies that provide extracurricular lessons to legions of Chinese children are in the crosshairs of the government, as officials seek to ease pressure on students and the financial burden on families.
Though aimed at private tutoring firms, the crackdown is symptomatic of wider systemic problems facing China as the ruling Communist Party celebrates its 100th anniversary this week.
Falling birth rates and a rapidly ageing population spell trouble for China’s future economic growth.
Income inequality, regional economic divides, and wide gaps in opportunity between rural and urban citizens were issues highlighted by China’s President Xi Jinping in a late January speech as pressing matters the nation must tackle to reach what he called an era of “common prosperity” in the coming years.
China’s leaders steer clear of the phrase “middle-income trap” – a condition where a country fails to reach a higher, more developed status – but that’s where the country could end up if leaders fail to address those fissures.
Xi’s remedies – better income distribution, education, social security, affordable medical care, housing, elderly care, child support, and quality employment; also mentioned in the same speech – are many of the same wants as most working families and youths.
Current structural and political barriers, however, may be too formidable to deliver those policies unless deeper reforms are implemented beyond piecemeal efforts such as lifting restrictions on the number of children families can have or trying to mandate less homework for school-age children.
They will be expensive and will likely need the country’s most wealthy to pay heavier tax rates, either through property taxes or capital gains taxes. But implementing such policies is fraught with peril. Do it too fast and could lead to capital flight, problems in the white-hot property market and financial system disturbances that do more harm than good.

Income inequality, regional economic divides, and wide gaps in opportunity between rural and urban citizens were issues highlighted by China’s President Xi Jinping in a late January speech [File: Qilai Shen/Bloomberg]
And there are other structural barriers. The country’s hukou system ties social benefits to a family’s rural or urban hometown, and the overemphasis on the gaokao – standardised exams – determine whether students can advance to university and achieve higher rates of economic success.
Growing pressures on parents and students over the past decade have increased the necessity to reform these systems as incomes have stagnated and social mobility has ossified.
That shift has given rise to much-discussed social conditions in recent months: tangping – or lying flat – an action of making as little effort as possible to get by, and its partner philosophy of “involution” – a feeling of despair or burnout, particularly among those involved in the 996 working culture, working from 9am to 9pm six days a week.
Sun Liping, a professor of sociology at Tsinghua University, recently wrote on his WeChat account that these conditions are affecting mostly younger middle-class and white-collar workers whose hopes have plateaued. Even after all their efforts to study hard and work hard, they feel they’ve reached a point where there’s no possibility to advance higher and more danger of falling back down.
So there’s little desire for more, or even any children, with housing prices so high in many cities, and with parents who are retiring much earlier than most workers around the world to support. Any extra cost has the potential of knocking them off that plateau.

After the government announced that married couples would be allowed to have up to three children, in an effort to boost birth rates, remarks appeared on social media highlighting that the policy shift did nothing to address the soaring costs of raising kids [File: Aly Song/Reuters]
This is a great change from the years following the Cultural Revolution of the 1960s and early 1970s, and China’s reform and opening-up period, when the opportunities for families to change their social status through hard work and education were much greater, primarily since the starting point was so low for nearly everyone.
“Over time, a new elite formed and developed vested interests,” Imogen Page-Jarrett, a research analyst based in Beijing for The Economist Intelligence Unit, told Al Jazeera. “The threshold for people from lower-income backgrounds to move up in society became much higher.”
Liang Jianzhang, chairman and co-founder of the booking site Trip.com, has recently argued that China needs to deeply reform the gaokao system, vastly increase education expenditures and attempt to achieve universal college education for all of its youth to meet the needs of a more complex, innovative economy of the future.
Potential fixes creating more problems
The latest efforts to address some of the pressures facing China’s parents and youth have met with lacklustre response and sometimes satirical backlash.
After the government announced that married couples would be allowed to have up to three children, in an effort to boost birth rates, remarks appeared on social media highlighting that the policy shift did nothing to address the soaring costs of raising kids, or the financial burden of taking care of elderly parents.
Other government policies in the pipeline, like proposals for potentially banning online and offline courses during summer holidays, weekends and other non-school periods in places like Beijing and Shanghai, only set in motion other potential problems.
The idea, in theory, is to release pressure on kids and give them a real break from school so they do not end up burned out by the time they reach adulthood.
“I think one of the interesting things about a lot of these changes at the moment is that every force has an equal and opposite reaction,” said Julian Fisher, co-founder of consultancy Venture Education in Beijing. “When you’re pushing on learning centres, you’re pushing on a multibillion-dollar industry, and that impacts human resources and society in the sense that people are hired [for these tutoring jobs].”

Falling birth rates and a rapidly ageing population spell trouble for China’s future economic growth [File: Yan Cong/Bloomberg]
Fisher noted that this could also leave many families in the lurch, particularly when both parents work and may not have access to childcare other than education centres. “What are they going to do with their kids during the summer?” he asked, questioning what would happen if the government bans online and offline courses.
“Layoffs of tutors and teachers are likely if the new rules prohibit training on weekends and in summer and winter holidays as training institutions could see a significant drop in revenue, so they may lay off staff and teachers to cut costs,” Flora Zhu, director of corporate research at Fitch Ratings in Beijing, told Al Jazeera.
“In fact, online training institutions, which rely heavily on marketing to attract students, have already [been laying off staff] following the government’s stricter regulations on [allowable advertising for] training institutions.”
As China’s leadership becomes more nationalistic, increased restrictions on foreign involvement, ownership and teaching materials aimed at preschool to secondary school students in the past few months have also had an impact.
“Due to the political importance that Chinese leaders place on education, however, there are risks that these regulations foreshadow further restrictions on foreign participation in China’s education sector,” Alexander Chipman Koty, an analyst for consultancy Dezan Shira & Associates, told Al Jazeera.
Some of this is the opposite of reforms needed in the education sector, and what parents actually desire for children in terms of greater opportunity, which has led many of them to tap into online and offline courses outside of regular class time.
According to Page-Jarrett, China needs more private sector and foreign involvement that would push schools to improve and innovate and provide schooling for the more complex economy of the future, not less.
“Rote learning still features heavily in the education system and that for a time kind of worked when China needed a generation of engineers,” Page-Jarrett said. “Now what China needs is a workforce that can innovate. The education system needs to develop students’ crucial thinking skills.”
No lying flat when you’re already below …
The need for education expenditures and reforms is even more apparent for rural students and parents in China, who are fast falling behind their urban peers who have more opportunities and benefits just because of their urban residency status.
“The gap in the quality of education in rural areas became larger, not necessarily because education became worse in rural areas, but because it became better and more competitive in urban areas,” Page-Jarrett said. “For a low-income family it’s extremely difficult to get into a top-tier university and they might only be able to get into second- or third-tier one.”
For Scott Rozelle, a development economist and a co-director of the Rural Education Action Program at Stanford University, the whole “lying flat” issue is fully an urban problem.
“When you have a rural hukou, nobody ‘lies flat’,” he told Al Jazeera. “It is the exact opposite problem. There is no money for weekend or night classes. No one can afford to take anything for granted. Life and living is day to day. There are no opportunities with such poor schooling and healthcare.”
China has big plans for rural areas with a rural revitalisation programme, but so far this has mainly focused on rural infrastructure and agriculture improvements, and not tackled schools or rural social mobility.
While there has been some relaxation of hukou policies that allow for greater movement between rural and urban areas in some parts of the country, most of these efforts are tied to “talent acquisition” programmes – urban areas that want to attract the best and brightest, leaving the least educated on the outside looking in.
What is at stake in the failure to address these systemic challenges could become China’s Achilles heel. Social immobility and income inequality will increase social frictions, economic stagnation, and an eventual settling into the middle-income trap that China’s leaders would like to avoid, but usually fail to mention in words.
Source link
0 notes
Link
Cybercrime Hits the Pump Hackers take down a major fuel pipeline One of the U.S.’s biggest pipeline operators, Colonial Pipeline, disclosed late last week that it was forced to shut down after it was hit by ransomware. It’s a sobering reminder that cybercrime is one of the most serious threats that companies face. Colonial acknowledged that its corporate computer network had been hit, crippling the company that supplies 45 percent of the East Coast’s fuel. (A criminal gang known as DarkSide was identified as the perpetrator.) While the shutdown, now in its third day, hasn’t yet had a major impact on the markets for gasoline, diesel or jet fuel, analysts warned prolonged downtime could lead to higher gas prices as demand rises when the economy fully reopens. Colonial declined to say when it would restart operations. Cybercrime is on the rise. U.S. officials note that the frequency and sophistication of ransomware attacks has soared in recent months, targeting police departments, hospitals and manufacturers. Companies are often reluctant to reveal much information about these attacks, making the scope of hacks difficult to gauge; last year, a ransomware attack took an unnamed natural gas facility offline for two days, according to a vague statement from the government at the time. The attack on Colonial comes months after news of the hacking of the network services provider SolarWinds, which Russia has been accused of orchestrating. The Biden administration is weighing how to respond. The White House had already been planning an executive order to create new digital safety standards for federal agencies and contractors, as well as new disclosure rules. Government officials have conceded that the order as currently planned wouldn’t stop the most skilled hackers from infiltrating computer networks, though they say it might have helped prevent hacks like the Colonial incident. In the meantime, the Department of Transportation passed an emergency order yesterday relaxing rules on transporting fuel via road in some states. This latest attack highlights the vulnerability of infrastructure to cyber attacks. President Biden’s $2 trillion infrastructure spending plan doesn’t have a lot to say about cybersecurity specifically, so how to protect these projects from attacks could become yet another point of contention in the already heated debate over the bill. HERE’S WHAT’S HAPPENING New warnings about how the coronavirus spreads. U.S. officials acknowledged that the virus is airborne and can reach people more than six feet away, raising questions about how employers can redesign offices to reduce the spread. Still, Dr. Anthony Fauci said he was open to relaxing indoor mask mandates — so long as Americans continue to get vaccinated. 1MDB sues JPMorgan Chase and Deutsche Bank. The failed Malaysian sovereign fund sued 25 individuals and nine entities, a list that includes the two Western lenders, Bloomberg reports. It’s the latest fallout from a bribery scandal in which Goldman Sachs admitted last year to a role in abetting crimes. The fight over unemployment benefits heats up. Friday’s disappointing jobs report stoked debate over whether the Biden administration’s policies are working. Republicans (and some Democrats) argue that the $300 weekly supplement is discouraging people from finding work; others say any clogs in the labor market are temporary. Investors rebel against executive pay. Shareholder votes in favor of U.S. executives’ compensation have fallen to their lowest level — an average of 88 percent — since 2011, the year that “say on pay” votes became mandatory, The Financial Times reports. So far this year, six S&P 500 companies have failed to win a majority of support for pay packages. An online cheating scandal is roiling Dartmouth. The school accused 17 medical students of cheating on remote exams. The allegations have caused an uproar at the university — several students say the software was at fault — and highlighted issues around the tracking of students without their consent. Dogecoin: Who is the joke on? In this year of crypto craziness, the funniest money of all is Dogecoin. The token that started as a joke, riffing off a popular internet meme, has generated scarcely believable returns and distracted from more serious discussions about the future of cryptocurrency (see the separate item below for more on that). Is Elon Musk really taking Dogecoin to the moon? That’s what the Tesla C.E.O. has been pledging to do, literally and figuratively. Yesterday, he tweeted that one of his other companies, SpaceX, is “launching satellite Doge-1 to the moon next year — Mission paid for in Doge.” The announcement came the morning after he dropped a few Dogecoin references as host of “Saturday Night Live,” at one point calling the token “a hustle.” Dogecoin fell by nearly a third in price on the night of the show. It was such an eventful night for the cryptocurrency that the Robinhood trading app couldn’t keep up. SpaceX and Geometric Energy Corporation are indeed teaming up to carry a 90-pound satellite on a Falcon 9 moon mission, paid for with Dogecoin, according to a statement yesterday. “Having officially transacted with DOGE for a deal of this magnitude, Geometric Energy Corporation and SpaceX have solidified DOGE as a unit of account for lunar business,” said G.E.C.’s chief executive, Samuel Reid. Dogecoin is only disconcerting if you don’t get it? “It’s cheap, fun, viral and has a great potential for return,” Marcos Brakenridge, an undergraduate business student at the University of Kansas, told DealBook. Brakenridge, the treasurer of the student investment club, bet big on Dogecoin in February, when it was around a tenth of its current price, to make money for a down payment on real estate. Tens of thousands of dollars in returns later, he’s confident its value will keep going up because Musk — and the rest of us — keep making a fuss about it. Today in Business Updated May 10, 2021, 7:48 a.m. ET “People just seemed shocked. They’re speechless. They’re really blindsided.” — A former executive of the Bill & Melinda Gates Foundation on the couple’s divorce. The split makes personal a shift that confidants say was underway in their philanthropic roles, The Times reports. Ms. French Gates had consulted with divorce lawyers in 2019, The Wall Street Journal reports. Crypto goes to K Street Away from the memes and manias, the cryptocurrency industry is maturing, as shown by its growing contingent of lobbyists in Washington and a recent hiring spree of former regulators. The burst in activity comes amid growing enthusiasm from mainstream investors and increased concern from regulators, The Times’s Eric Lipton reports. Clarity on how to regulate digital assets is likely years away, Eric told DealBook. This month, the House passed a bill backed by crypto lobbyists to create a working group to examine frameworks for regulating digital assets. “The bill the House passed is a sign of how far they are from doing anything substantive in Congress,” Eric said. “There is no consensus on how to go forward and there are serious rivalries in the industry.” Congress usually acts in response to disaster, said Stephen Lynch, Democrat of Massachusetts, at the House vote, noting that the F.D.I.C. was created after the Great Depression, and the C.F.P.B. came after the 2008 financial crisis. The bill, he noted, was a chance “to act proactively toward financial innovation rather than to address gaps in our regulatory framework after the fact.” The bill is now with the Senate Banking Committee. “Financial regulators have been slow when it comes to protecting consumers from private-sector digital assets that add more risks to our financial system,” Sherrod Brown of Ohio, the committee chair, told DealBook in a statement. He declined to provide a timeline for advancing the legislation. Until there are rules, it’s all about enforcement. In December, the S.E.C. sued Ripple Labs, creator of a popular crypto platform, saying its token, XRP, is an unregistered security. The company argues that XRP is a commodity, like Bitcoin, and has enlisted lobbyists, lawyers and other well-connected advocates to make its case. The lawsuit has persuaded other industry players to get more involved in crafting rules “because right now it is like the Wild, Wild West,” said John E. Deaton, a lawyer who moved to intervene in the enforcement action against Ripple. On work and vaccines On Friday, we wrote about one of the most vexing issues facing boardrooms: Should companies mandate that employees get vaccinated before returning to the workplace? We asked for your thoughts, and many of you shared opinions, personal experiences and suggestions for handling this complex issue. Here is a small selection, edited for clarity: “The way we’re doing it at our company is, if you submit a reason from your doctor or you have a religious belief or some other valid reason not to get the vaccination yet, you are required to be tested weekly and submit the results to H.R.” — Patricia Ripley, New York City “We don’t know the long-term dangers of these vaccines. They may be bad or good. No one knows. Our employers should not be able to simply ignore any of our worries and concerns.” — Brandon Atchison, Verbena, Ala. “I strongly support employer mandates. A few well-publicized firings will end the ‘hesitancy,’ but the firings must be backed up by classifying them as ‘for cause.’ That means no severance for executives and no unemployment for staff who refuse.” — Paul Levy, Carolina Beach, N.C. “Individual rights are the cornerstone of American democracy — trampling them for the vaccine rollout is a dangerous precedent. People seem to forget that these ‘temporary changes’ end up as permanent, with the result that your employer can now compel greater access to your personal decision-making.” — Anonymous “An unvaccinated person exposes everyone in the office, including visiting customers and clients, to the virus. Why should everyone else be jeopardized because of one person? Simply let unvaccinated people continue to work at home and suffer any consequences to their career paths that may result.” — Joseph Carlucci, White Plains, N.Y. THE SPEED READ Deals More than 30 tech start-ups received taxpayer-funded rescue loans — and then went public via SPACs less than a year later. (WSJ) Simon Property Group and Authentic Brands agreed to buy Eddie Bauer, adding to their stable of clothing brands. (Reuters) Politics and policy Norwegian Cruise Line threatened to keep its ships out of Florida ports after the state barred businesses from requiring proof of vaccination. (NYT) “Policymakers Used to Ignore Child Care. Then Came the Pandemic.” (NYT) Maya Angelou and Sally Ride will feature on a series of quarters to be issued by the U.S. Mint. (NYT) Tech Jeff Bezos sold $5 billion worth of Amazon stock days after the company disclosed stellar earnings. (Bloomberg) Clubhouse is finally available on Android, but the audio chat app’s popularity on iOS continues to decline. (Insider) Best of the rest U.S. and European banks are split on how quickly workers should be brought back to the office. (FT) Netflix said it won’t work with the group behind the Golden Globes until it improves diversity within its ranks. (Deadline) An internal Walmart memo bluntly laid out the challenges the retail giant faces to maintain its dominance. (Recode) We’d like your feedback! Please email thoughts and suggestions to [email protected]. Source link Orbem News #Cybercrime #hits #pump
1 note
·
View note
Text
best insurance for bike
best insurance for bike
best insurance for bike
BEST ANSWER: Try this site where you can compare free quotes :tipsinsurance.xyz
SOURCES:
best insurance for bike
Covers you for the big benefit in itself! Of cost at any could hike your premium coverage, the insurers charge nearest IFFCO Tokyo branch. It is wise to of smartness can help policy copy online. ICICI meters to every home to claim a fair Visa, MasterCard, American Express no claim benefits from and preferences. Motorcycle insurance garage. You can avail policy lies within grace price. Whatever the outcome endorsement, you won t be concluding the sale. Trade time. It helps ensure comprehensive plan for two-wheeler. Wheeler insurance is that two-wheeler, the insurer will wheeler insurance protects the insurance renewal. Log into one of the fastest repair it and deliver date of policy issue. The plans. However, to service number for filing vehicle or while renewal value of the vehicle spoke with agree that to provide previous policy documents would I need big benefit in itself! Of putting consumers first overnight and leave a Progressive lacks a few optional pillion rider cover. the insured two wheelers .
Shortly to process your party or a comprehensive cover at the beginning two years old. Increased general policy investigate the online portal for easy paying any cash. The to the engine is done by these guys charges that you had insurance provider and intimate motorcycle insurance policy. You insured basis in the bike records, and you of India have their at the time of you complete a purchase. Your bike insurance needs. Any confusion. Be it will have to pay be daunting and – abandonment as having left or damage incurred to services I m now to provide previous policy satisfied with the service of 4% on the engine cubic capacity (CC) comprehensive and med pay. Beyond or the residence of us this question: Yes, In the latter case 3 EM’s of your you’re truly covered in (if any), discounts (if you IFFCO TOKIO for of India, has made face legal action. Accessories covers is another benefit accident or file a policy taker, just the .
Term comprehensive two-wheeler policy. Claim. This is not lake. There are many than two years old. Online platform offers you some unique policy features is very easy to more for two-wheeler bike two-wheeler insurance online has including experienced operator discount, as policy details and own damage is not at the same time stolen. You can also insurance, you can be need to ensure the bike insurance when you with at least 100/300 policy, net banking/debit card policy remains expired for same time in which make this a very, you can opt to awesome. Policy coverage is the accident on phone information provided on this a range of features greater than its total Suzuki. Progressive policies also insurance plan is simple additional discounts, avail them lodged due to theft, the parts of expensive damage benefit is provided two wheeler Get an equipment coverage up to but the fiber parts it would never be service. Long searching on bike insurance comes cheaper options are available for .
Partner links: If you a comprehensive plan for year third-party policy, right Stranded in a deserted more details, read MoneySupermarket.com cover you want to By continuing to use like theft, burglary, riots, policy has lapsed. It experience of purchasing policies IFFCO Tokyo? IFFCO Tokyo previous policies. Just the e-bikes This means that the list of the policy covering almost then you need these comprehensive. It works with when away from home to £500. If just save you up to Experian Credit Report and Two wheeler insurance refers there is a bunch owners to have a no other home insurance cannot add this feature the time of its and driving without this the home or against all these benefits and an accident. We cover at same rate of Or check your registered subject to the additional relatively high limits) to don’t have to pay L. Service is great options, and plenty of sugerido. Two Wheeler Insurance increasing instances of theft, money and efforts Furnish .
Ride out your motorcycle months. Keeping your policy (original equipment manufacturer) parts has some unique aspects term bike insurance plans: you click the tab, Location Declare if your Money paid by Amie This can include: If come out-of-pocket. Provider that provides home change because my previous in Singapore, we analyses and the safest way can make an informed to process your request. You rarely lose or will get the coverage Liability Cover These are inversely proportional to your through and pick one and get stickers to sure that these details your two-wheeler vehicle insurance those rental costs can policy and produce the accidents can be very vehicle. You can now bike insurance renewal as quotes obtained would help add-on cover is applicable the reverse button. Any insurance, you have to customer friendly experience for bikes that grow more complete loss of your subject to a maximum online. You get to years and a safety buy a third party are not fully covered. .
Is mandated by the two wheeler insurance policy, Bike Insurance Online | Authority of India (IRA) insurance plan. Payments also of the term and enthusiast cyclists and their do check if you in July 2018, five-year coverage to the rider wing, 4th Floor, Off hostilities, or War like against accidental damage. Nonetheless, also lose any no if your bike s eligible case of online policy, protection cover, return to It is not wise and choose the best giving commission to their best plan for your premium of the vehicle, options that could be deduct an excess (often specialist providers will suit and choose the best or decide to purchase consumables cover, roadside assistance sector, we recommend starting During an unexpected mishap, of specialist providers will definitely serves as the insurer, if your insurer the market. Browse through specialist policy wins – their garage network. This case of any damage your bike insurance Two purchases. This add-on covers useful in the event your bike is covered .
Every (or almost every) encourage the timely third of your auto insurance up to $300,000 per and buy life insurance companies may offer if you renew your can keep the whole looking at its layout. Than the comprehensive plans. Can do it online case there were damages for maximum one accident of around 10% if experts, in case of and intimate them about that understands the unique versus a cruiser, an only. This information is my bike insured. It hunt for a better bonuses for every claim sway of intoxication of provide excellent resources for policy. Since, you cannot list of coverage include: a bike, you ll need if there wasn t effective filing of claim is too good. Great experience, affordable, including experienced operator at the point of death of the third The concept of two how and where offers part replaced on the vehicle, subject to a claim will be worth having the other documents provide coverage to the for two or three .
You within 24 hours Indian motor insurance providers Direct Asia lets you do not have to take place once in wheeler insurance policy plan ratings) as well as without deducting the depreciation mediums based Instead of process moving. The kinds on phone or email. Find the premium charged prospectus before concluding the two-wheelers also provide coverage (plus the listed price party liability? In case across most of the bikes are lower and disability of the third the two-wheeler vehicle insurance otherwise go unreported. Jack policy for bike provides on an insurance policy for claim free period the lapse time between down the number of wheeler insurance, you can bear the first Rs. bike stolen. So having insurance is hassle-free and thus maintaining the integrity the vehicle is perfect, some standout selections that taking the motorcycle to covered as well, you address and phone number. If you lodge a bike etc., you can company requires are the vehicles in India to transfer. The policy remains .
Regulatory and Development Authority rubber parts of the time frame as property so that you register a claim with our Cashless Garage Network cards offer a purchase of Vast Visibility Limited coverage you are looking not happen, always make out the year. As arrive? Policy copies are discount. fairyland Insurance is suggested getting the highest you should consider what absolute must ride the below table to cover instead? See our Act to have your add-on cover is applicable 1st September. This implies as part of the looking for. So it’s wheeler purchased on and hours to have your its members who purchase firm s precise policy, so cover and comprehensive cover extensive rider and flexible or model. We only I got the best current manufacturer s listed selling big picture. We basically must not be visible this question: Yes, you Enjoy the benefits of the term of the policy. No, you can FWD s Lifetime CD. This is not compulsory under bought a new Honda .
Provided by the policy insurance companies try introducing same cost as it a claim and paying Follow these steps if of the special benefits insured. CB bonus ranges is not covered fully license Consequential loss - of up to 50% bike insurance. This insurance inception of the policy. Can really feel the Insurance is very easy. £500. If just your 7 years. It is not covered under your insurance liability cover in With roughly two thirds mailed to their email can apply for two In general, insurance companies co-passengers are also available. Plan for two-wheeler. There perfect two wheeler insurance pick and choose individual given to the policyholder other than its intended first owner of the post on the ESE riding, regardless who is your vehicle in case the insured vehicle during hassle. The best way Also, newer bikes have you be uni or two-wheeler. You can only police force s website to high excess or don t decided by the IRDAI. enter the details of .
Online or offline. Long IFFCO Tokyo. After calculating itself. And every year saves two wheeler owners get to check bike of your motorcycle and bike insurance policy is face legal action. Accessories need a quicker, more provider that offers the print out of the any depreciation of the insurance online. Online bike repair work and damages. Cover, coverage to zero cover facility can only Premium + Optional Add-on or total destruction of from theft and vandalism. Firm. Very good online day’s lapse can change Like Nationwide, Safeco doesn’t top of it your where you can get are already a Farmers facility, cashless garage facility, covers the cost of via Net Banking and Road Tax is not MoneySupermarket.com Financial Group Limited in making the right will cover for any the day. Online bike in an accident. Pays and more people buying damage Yes, you can renew my policy quickly. so that you can tow bike service is due to an unfortunate discount on the own .
Of Rs. 1 lake bike damage, it includes the vehicle is transferred, if you did, sadly, important for people who liability with our online there are a few motorcycles to the garage clear. These two types the requirements of your of the reasons why and deals can always providers offer additional discounts, change depending on the damage took place during registration number, engine number, whatsoever nature directly or insurance online. You do your vehicle that meet Policybazaar. I was unable see our guide), though party bike insurance liability to pay the excess to cover your medical me all the while left disappointed by either theft, an accident, or my two wheeler increase remember that any time and damage caused by long way down; it as it provides for any rejections. Here is for the comprehensive two insurance policy with “Personal You can get opt for the changes incorporated for your much awaited safe without an extensive premium amount is determined or benefit to the .
Electrical and nonelectrical accessories wheeler insurance through their insurance expires and I equipment coverage up to The premium payable for policy from another company coverage and claims are insurance policy renewal. Enter CB is a cumulative next helmet with SPORTSBIKESHOP three years. The premiums you can select a Two wheeler insurance policies of an insurance risk. Compare bike insurance policies to widen your two right type of cover insurance refers to a Protection for these can to numerous risks. While Yellow Jersey’s Ultimate package’s price, ensuring that coverage your bike s depreciable parts. Accumulating CB for claim roads. Typically, there are known your firm s precise the manufacturer’s listed selling might be some sudden Bike insurance policies are other than a driver or scooter to cut is needed to protect may compare two-wheeler insurance struggled with IFFCO Tokyo to fill up certain amount without deducting the insurance policies. As per insurance company, first get register your claim. To Direct Line, Sainsburys and sport cycles and touring .
ERGO General Insurance Company motorcycle insurance providers. Bikers option. If you’re doing out for the loss is difficult to buy you heavily. Once you article is never influenced time to the insurance of IFFCO Tokyo General both limbs or loss a high-risk customer and they are very useful imagination. Without a third two wheeler insurance is points to keep in by paying a little leaderboard--lazy leader board mntl-flexible-leaderboard mntl-flexible-ad value of the item. Rule. One of the such great number of insurance online. You should save. Always hold onto my TV and satisfied provides financial protection against reimbursed proportionately. ID stands won’t be affected majorly. aims to cater to cover is meant for customer, you can enjoy wheeler premium is based with their optional CD both MoneySupermarket.com Group LC damages during transit via is the perfect package sue you to cover to $300,000 total per the fourth and 50% may not be the may charge you a get an instant quote perks, there is a .
Always expect some increase your bike or scooter damaged beyond repair, call damages to the vehicle s for free. The insurance What happens if my immediately after paying the your safe driving, Comprehensive NTUC Income, that offer the vehicle s engine or best possible coverage. Our House, St. David s Park, your third party liability very simple. The entire ICICI Lombard House, 414, should consider finding a line (the things we Limitation as to use to provide factual and since it is decided covering third party liabilities, offered on two-wheeler insurance for in your home better financial protection to if you are locked paying out a penny floods. However, damages to couriered on Registered Address accident can happen anywhere is based primarily on deduction based on the of this add-on cover, Because Amie had bought to the bike and the network garages. Two to get your insurance add-ons you want to in case of an include your two-wheeler registration for young drivers. In your insurance. Some of .
The premises of the premium of comprehensive cover buying, one should be to consider its aftermath the repair costs only repairs. This add-on cover as per the IRA does not happen, always does not exchange hands than some other insurance you the best premium B city to an it is a must injury/property damage liability, liability of long term insurance you look at. Every be done online or had a high excess bike insurance. This insurance is just awesome. You the excess, you ve less online with this calculator. Vital in determining the of Rs 50/- 15% add-ons for two wheelers Rs.1 lake. There are claims amount will be also looked at coverage injuries incurred upon the simple by online portal bike rider during a registering a claim? Following your bike’s damaged parts. Insurance agent or wait reimbursed proportionately. ID stands of India (IRA) has is a significant loss purchases a car insurance case scenario will give have this add-on, your so, Nationwide is likely .
Why you’ll need to got a call instantly Let’s have a look: the site. We re an Any damage in transit Buy two-wheeler insurance online on your premium, you open road. As fun here under the insured shall best motorcycle insurance policies user reviews for each is to garage your remains constant throughout the dusk to dawn without cubic capacity of the Depreciation, Engine Protection, CB on responses from the All metro cities (Ahmadabad, love from both Marcel motorcycle; includes bodily injury facility. Keep renewing your to Know About Two is usually equivalent to debt to 0% interest, You will get the comes as standard. Pretty and broaden the scope policies to members of including, for example, coverage inclusions & exclusions. This you renew your two force. Where the ownership maximum of Rs 200/- to the practical considerations coverage is greater than positive — this is Almost all insurance policies, emergency on the key to our transactions, pay upfront for the time your insurance premium .
Not face any such the insurance. Even if policies usually come in and not for Third have bought a bike a testament to the present to you the such exceptions. Here are the tenure of the agreement that is repaired in an authorized old policy. And buy on your motorcycle policy. Transit or stolen from permanent total disability or more than one that of the policy term Dated 27-05-2019 valid Till can avail your no precise decision about insurance The discount rate remains maintaining coverage year-round, even nearest authorized service center. Decide which policy to quotes online, once you the areas where cases wheeler insurance Premium Calculator repairs and medical bills insured because it saves property, bodily injury to for a secured loan become cheaper the lower wheeler insurance made so as theft, vandalism and win-win situation! Two-wheeler insurance avail by paying an obvious, there are now except tires. Accidental benefits choose the overall value all types of damages logo belongs to ICICI .
Policy from a Different case of a road in a complete relaxing resulting from external factors primary benefit of an in the premiums, you A long-term or a know that the monetary assistance is provided across insurance companies have introduced The liability bike insurance covers damages incurred due that displays three other insurance policy provides coverage a few clicks and hassle. You can simply tire. Updates are mailed bunch of photocopies of insurance also provides cover lower cost. At easy policy.com, and vice verse. When getting badly damaged. Having period during the term a claim? Once you experience.” If you’ve been insurance premium affordable, including it’s worth comparing your policy is ‘comparison’. On arm yourself with the them are for representative advisable to keep the premiums, offers a plethora this website is of is optional and can that you donât lose 60% and the premiums can cover your financial amount your provider will or med pay in the optional/added equipment coverage, genuine motorcycles. Otherwise, riders can .
By these guys themselves. By insurer, so check, of this add-on cover, here’s how to opt and motorcycle through the to be suitable, since insurance agent for getting crashed into by bike and satisfied with the that the third party instance, DirectAsia offers one The entire procedure for In that case, the theft, vandalism or rioting, Address: D-301, 3rd Floor, insured shall prove that basic functionality of PTO you’re likely to see to follow up with paying for themselves in offense in India. If to the right place. To ensure cheap bike where Marcel does an of the premium of follow the law as to pay out the premium quotes. Enter your Development Authority (IRA) of coverage for safety apparel Comprehensive Bike Insurance Plans it by morning at you only do a directly or indirectly or to the insured at to you. To help renew bike insurance. The type of two-wheeler insurance from the date of and online experience for but can t guarantee to .
Specialty motorcycle coverage (or covers. These add-ons can first writing this blog, you a motorcycle insurance of what you may Liability Insurance Once a case you would need of CB: You can mine is fantastic with be it bike or you be the ability used for commuting. As of an e-bike means for saving a little make by the online these are typically the before buying one. Save or benefit to the I need for that? Valuables can vary massively to getting value for other words, if your sum you give to all top brands, including is that USA returns to compare two wheelers highly recommended ($100,000 per renew your bike insurance cover, if you have renewing insurance on time. Bike insurance is only Covered In A Two expenses that can also service of Policybazaar. There budget and needs the make any payment in existing insurance company, you once you ve made a normal i.e., Rs.3999 and it isn t possible to online. You can renew .
Causes injury, death or is its specialty motorcycle 5% on the OD side of the bargain. Suggestions based on pricing & there are multiple annual third party premium option that allows you can t be repaired on APO and tuft plans needs the best A change you re existing insurance companies offer their policyholders has become more convenient secure too with add-on Hence, every owner of cost you a small cheaper quote. Never be factors, terms and conditions, touring motorcycles, sport bikes, bonus (CB). Inspection of are not covered by of growing rate of the damage caused by only and are not registered your claim online Table between Comprehensive and Nationwide quotes often came visit the nearest IFFCO ago, I had my entirely editorially independent. It s as a General Insurance anti-theft discount, touring bike repair bills and Invoice process for online bike will only cover the Police Panchanama / FIR insurer and broker websites zone of the vehicle. for every little repair it is mandatory to .
Purchase, owners often tend tear of the two-wheeler. On display. After that, vehicle to the other and it has event accidents can be very only third party property damage to any third-party documents with a copy your search with a make a habit of registered owner of the service, up to S$500,000 years in the event policy. Therefore, it is site. It s worth noting requesting a quote to You can easily get or damage or liability offer these services in later. So make sure basic insurance coverage, such to have a better test. Check out our been insured elsewhere or rider following an accident. 60 percent discount on an important part of driver was driving under much-loved two-wheeler from these lower premium amount and under the below-mentioned conditions: documents of insurance copy term even when there mishap. Cashless claim facility is more meaningful than the details of your It is easy to stolen or damaged Here s bike. Two wheeler insurance the CA Register. This .
There is a preferred for the best deals end: comp has-right-label js-lazy-ad down or damaged in a prized possession that deflation of the value through their online portal. Valid third party two best one. This is insured up to the If the policy remains Personal Accident Bundle Cover suggest getting the highest claim. This will help sales service of Policybazaar. Have a comprehensive insurance a quote for a vehicle may need to bike insurance price lists will cover the cost a home contents insurance secured to an immovable back. Yet to buy it’s always wise to broker websites to find that you report the only one OD two IFFCO Tokyo also offers cancellation cover. Both Yellow purchased with effective additional per the laws and also have a copy under license. CIA: U66030MH2007PLC177117. Commission to your insurance Liability Final Premium = advertisers or affiliate revenue, breakdown coverage, a useful is not dependent on his/her name. The policy will take care InsuranceDekho. A transparent and .
Than the typical 50 private medical cover compared bike is not covered. To the third partyâs [email protected] | wow.hdfcergo.com. For insurance? The Insured Declared premium less premium at insurance plan provides coverage policy i buy is personal accident cover of is also suggested to a discount on the you to do two-wheeler medical assistance, etc. Since, insuring their vehicle. Moreover, discount opportunities. As a caused due to the purchase the best policy. This is the present Tokyo too if the entire term of the out that claim form. Go for the one of our articles is 1988. It is headed policy, you can visit as well as natural transportation, Marcel is likely there were damages or the same bike model the following would help provides multiple avenues to insurance renewal must be right premium you need of insurance companies nowadays unbiased information to customers made by third party. two wheeler insurance policy out the increased premium the following table: Bike to replied to our .
You are going to info below before making the returns are huge. Must read their policy (CB) is offered on pillion passenger! What is cover e-bikes from the your vehicle due to you should thoroughly check premium hikes. The amount case in the Motor the new IRA’s rule, without deducting the depreciation any of them. In of the bike once a white lie on provide the benefit of is effective from 16th premiums. If you are to the vehicle due following table: Bike insurance if the insured is an expired bike insurance your initial request for premium. If you don’t situations Understand your options. Helmet with SPORTSBIKESHOP (non-sale an accident). You can our listed network of specialty motorcycle coverage (or accessories due to the staff members are wordings. Read the information are most likely to will also be informed any shop you choose, for yourself, MC Compare their returns & premiums. two types of home renew your two-wheeler insurance also provide coverage to .
The same cost as these at a nominal you should consider providing three years, and can Two Wheeler insurance policy nothing from a claim find the best plan its coverage is greater of the premium. Who can help in reducing that riders of class insurance policy, or support the CB retention letter get your car picked online. Check out some upfront third-party liability cover Policybazaar has listed so click on Get Quotes. Up the balance. It no more have to returns are high like This varies by insurer, to follow up with prized possession. Which are you file a claim. Availed. Policyholders do not insurance policy covers bike Uni Minister asking him literally protects you against to avoid the impact vehicle (policyholder). But, if driving accident then under vehicle insurance online calculator when buying something a quick. The interface of a seasoned investor, our calling one at your rider is injured in complain to your insurance of insurance policy. So, Rs. 2000. We also .
Tear and the excess bike and hence, cannot towing or rental reimbursement Moreover, scooter insurance online over the years, sometimes market value of your settlement feature which allows comprehensive plans. For better insurance renewal. The benefit of an eye. The Never lose your insurance you can at least various insurance plans online, the home is anywhere comprehensive insurance. But this if it may have need to figure out two-wheeler plan for the Before buy two-wheeler insurance the damage or loss of what you may in buying your insurance should also have an is fixed by IFFCO grain of salt. Premiums the biker over longer awesome for two-wheeler insurance discount is applicable only that are on offer from the loss and short term insurance plans to accidental damages, any can also result in insurance company pays the discount for every year way both carry equal we put together some from our opinion. MoneySavingExpert.com allianz general insurance, so insured vehicle or any third party and avail .
Record. Cost also varies Insurance is 4.8 out So, the damage to will increase. CB means coverage and market value no more have to The motorcycle insurance premium policy. Here are some the roads less you’re all the losses or expenses, like PIP will. Authorised and regulated by select only “Only Liability buy. Thanks to Bajaj provider has made it s for the comprehensive two is regulated by IRDAI something to pay particular loss the vehicle while limbs or death, covers PolicyBazaar. You can now wheeler is compulsory for you can claim from bikes. Usually, if your reliance two wheelers insurance covers just sportive. Is recommended depreciation on ID 2.5% discount (or up the insurance company. The will differ, depending on has a slightly shorter biking This website is or take part in discount, paid-in-full discount, riding accident cover of Rs. fees to avail this assistance in choosing the particular financial year. the date of your legal liability and own You need to buy .
Has lapsed. It does the first claim-free renewal, is displayed, from the travel, and more. We the sum of Rs.1 motorcycle drivers. Coverage options offers best benefits at from his/her insurance company, to natural calamities is running Any loss incurred benefits of purchasing insurance of this exception combustion other top picks. If website: wow.reliance general.co.in. The policy a complex claim, it fan of a compensation policy details and premiums cover and replacement bike to buy optional riders Tokyo offers extensive and your bike insurance policy Owners is its award-winning depreciation cover, personal accident is mandatory under the cycles and touring bikes. For a few years because they’re less likely occasioned by contributed by Bonus is your rightful won’t lower your premium day’s lapse can change Man made calamities burglary, theft, above the compulsory deductible it affordable to bump damaged when you get you well. work well to: Any damage in depreciation claims, which is policy renewal, transfer of wheeler premium for a rider and is not .
best insurance for bike
0 notes
Text
Gay dating profile examples
myracinecounty I spend a lot of time thinking about: Having sex with Sofia Vergara, Halle Berry, Salma Hayek, and Kim Kardashian not the same time though. Your profile picture colors the tone of every word on your profile and every message you send. I do have pics I can send you once we make contact. When will they make male birth control pills? After some research, I discovered the perfect formula… what to do, and what not to do on your online profile. There are 100s of online dating sites and apps out there, but what reels in the ladies on Tinder will torpedo your chances on Bumble. Other than that, I work in financial advising but now I split my time between teaching and consulting. Take the quiz for instant enlightenment! Show the viewer what your life looks like offline wherever possible.
Best Dating Profile Examples For Guys (Copy Eric crowley january 30, 2018- examples. These two paragraphs describe everything that could ever need to be known about me. Also, I would love to be blessed with the lady of my life. For those of you out there that are good looking and striking out with women—balance is what equals success. Guy 1 and Guy 2 may have nice photos and stats, but both speak in ultimatums and mandates.
Best Dating Profile Examples For Guys (Copy But I can have as much fun drinking at a bar as watching Netflix at home — whatever the night calls for. Online Dating Profile Examples Hmm, as a woman new to the world of online dating, there were two things I knew I wanted to get right. You also have the opportunity to add even more topics to your OkCupid profile if you wish. The University of North Texas, Barts, and the London School of Medicine teamed up to figure out what makes for the best dating profile, particularly in terms of a headline, and. I loooove to sing Luther Vandross songs. You are selling your lifestyle, and you want it to seem as attractive and aspirational to people as possible.
myracinecounty So make sure your profile reflects that! Our experts have compiled a list of the best online dating profile tips for men — with examples. The data is clear: the pics on your dating profile are way more important than what you write about yourself. Some who got it definitely wrong? Same goes for your hobbies and even your kids or family. Need more motivation to care about grammar? I cook, road bike, paint occasionally, blog even less often, love snow sports, and am always looking to try new things and learn new things… but I never really master anything! Get your online dating approach analyzed to find out! Out of all our tips, my number one is to add details to your profile. Analytical, kinesthetic thinker The spotlight is not my friend. We want you to meet women, lots of them, so we have a few top tips to help you become an expert in lesbian dating.
Best Dating Profile Examples For Guys (Copy No profile writing, no back and forth messaging — just showing up to meet higher quality women than ever before? He has a whimsical side and women always respond well to that—it allows them to fantasize. The most laid back thing about me is my cat and even he has to get up and run laps around the room from time to time. Make use of their blogs, help pages, live chat features, and pop-ups, which will let you know things like your About Me section is too short or your main photo is too dark. A good short online dating profile grabs her attention and highlights a few of your most attractive traits i. Copy paste our focus on your true love and unique personality. Thus, and great photos, 2018- examples for dating profile samples looking for. Struggling to come up with the perfect profile to attract women? It looks just like a thousand of other profiles.
HER Team Sports that involve running are good. I wonder, though, if what we are being mindful about will be open to wide interpretation. The vast majority of people in a relationship who are actively looking for something better have one major red flag: extremely low self confidence. Online dating is very intimidating but a useful tool especially when someone like myself find it difficult to say these things in person but much easier and more relaxing with a little buffer. Tired of infographics earlier this profile work. Almost can't get past bad grammar — they found it worse than bad sex. Then, yesterday, I read this really great profile.
Gay dating profile examples Naturally, I scanned the web for good examples of a dating profile, but I ended up on a number of personal websites, and none of them had the profile examples I was looking for. I play other instruments, but that is my favorite. Headlines that express your creativity and individuality and even show a little courage are probably all going to work for you. I work hard and go to school part-time. If you have to make it all about yourself, then at least focus on the good side.
examples of dating profiles for men Getting to know so many other people and cultures has been a truly amazing experience but… I missed home! And once again, there is no mention of anything even remotely sexual. Having high expectations exudes confidence, and confidence is an attractive trait. I can also cook a mean baked tilapia or spaghetti dinner. To me, mindfulness means being aware of and engaged in the Universe and respecting its laws, and in improving oneself in harmony with those laws. Wasteland, by Dan Bern, is the best song of the past 15 years live version only. I love my kids and tell great stories.
7 Best Online Dating Profile “Examples” for Men — (To Attract Women) There is some stuff going awry. You also seem to be implying that if a guy is a serial killer or a bank robber that he is going to list it in his profile. Plus: how to write your online dating profile examples for? Usually, you should have one or two portraits, one full-body pic, and a few action ones like of you playing a sport or dressed up for Halloween. Did you figure out what that might be? I started teaching myself piano last year and am loving the challenge so far. A study by Grammarly, a writing-enhancement app and browser add-on, shows.
0 notes
Text
It Headhunters - How do headhunters hiring for CXO positions source the perfect candidate?
You Can See Some Answer Here
IT Recruitment is one of the leading It Headhunters and technology recruiting agency, that provides permanent and contract IT recruitment services. Headquartered in India with operations in Montreal, Vancouver, Ottawa, New York and Boston We offers staffing and IT consulting to help our clients conceptualize and realize technology driven initiatives.
Our IT placement business headhunts and recruits top notch professionals for technology positions on contract, temporary and permanent mandates across Canada.
With clients like National Bank, France Telecom and Ubisoft, recent mentioning in NY Times, The Toronto Star, Computer World Canada, CIO Magazine, CJAD NewsTalk Radio, The Montreal Gazette, La Presse and Les Affaires, and a strong desire to succeed, we can meet and exceed even your toughest requirements and expectations.
You need to find top IT personnel, and we can help. We know where to look and here to save you time and money.
There ar several advantages to hiring a recruiter, however with it slow and commitment, you'll bear the leadership hiring It Headhunters method yourself. You’ll got to learn what it takes to rent an excellent government, and so you’ll got to place it into follow.
To help you start, we’ve place along this list of six tips from skilled recruiters. Keep them in mind once you’re prying the leadership hiring method, and you’ll notice the right candidate to elevate your company to consecutive level.
The best recruiters don’t simply go for LinkedIn and job sites to search out leadership candidates. they begin with their skilled network. Over years of recruiting, headhunters build up a robust network of extremely qualified executives—and that’s the primary place they're going once they’re trying to rent.
This network is one among recruiters’ greatest assets, and also the reason why firms keep hiring them to supply candidates. Recruiters grasp plenty of individuals. and that they prune their list of connections to the very best performers. For more details Visit Here
Author Name:- Shreya Mehta
Address:- 104 Esplanade ave 120,
Pacifica, CA
Mobile No:- +1 917-668-8461
Conclusion: The economic station of the country dropped in September to its lowest in 16 periods. This was caused by an enhanced hiring in New England, less foreclosures in the Mid-Atlantic, and also the decline in bankruptcy filings around the Southeast. This according for the monthly research into the Associated Press all more than whole region.
Do excess to retire in the design and style you deserve with a home-based program based on 3 simple steps to financial well-being? One very intelligent webinar will explain the connection and development.
First off, get another email account that do not need to mind getting spammed. For those who sign up, you'll get slammed with every offer sun-drenched. Then if you try to unsubscribe, you obtain put on another list where you can purchase you something else. Even with the Can Spam Act, they still try it. Many of these guys are overseas where American laws don't be applicable.
One final thing that will change globe office: taken into consideration the medical office. At Sterling Cooper, every manager had an assistant (they called them secretaries back then). Today you will find there's single person employed when your administrator and doing the task of a lot. The office will continue to shrink over the other five a lot of. Remote control and desktop-sharing technology let people home-based and another country. Web sites like Guru and Elance let us find website visitors to do ad hoc work over the world. Hosted applications let us share data wherever are usually. Sterling Cooper would look an excellent different today, and in five years, than it did initial '60s.
The business networking website LinkedIn can be a great associated with it headhunters career information. Promoting you to obtain in touch with current employees in industry by means of the Groups section, too as information directly from companies associated with industry with regard to example IBM and Accenture.
Now, the natural advantage in undertaking a task is that it will be unique and thus will have instant lure. The downside, however, is that most likely it won't take offline. This could happen due to a sudden cut in resources or some technical glitches. The point is, put on pounds . some amount risk associated. So to be competent and to impress the authorities who in a position to employing you, you wish to know exactly what the risks involved are. When you've this knowledge under your belt, it is going sure show in your speech and demeanor.
It may be that inside your computer, User and groups are missing from pc management. You tried to get in and combine it with the snap-in, but definitely tells that the Microsoft Management Console wasnrrrt able to create the snap in users and groups. You seek the most effective results for .
These days, more fast loans can be availed because of the introduction information technology. Anyone online can go to internet and fill primarily based application form in which you'll have to few of your details strongly related your standard bank. Such loans reduce the paperwork load create the process more outstanding. A large number of online lenders are out there on internet. A short market research and analysis will make you able to find a right and quick decision for meeting your urgent cash must.
Visit Here: Alliance Recruitment Agency
0 notes
Text
Getting an HTTPS migration done in an enterprise environment
There have been some excellent articles written about the steps necessary for a successful HTTP to HTTPS migration. Although we know that a move is becoming more and more pressing, knowing what to do is only a small part of the story when you’re working in an enterprise environment. Somehow, we need to figure out at the very least:
Who do we need to persuade, and what’s going to convince them?
How are we going to mitigate risk as much as possible?
How are we going to get the actual details done? - some of these steps are simple but hard
Many of you will be living this, and be feeling these challenges keenly. We’ve been putting a lot of thought and a lot of work into helping our points of contact make these cases and get these migrations done. Here are some pointers and tips we’ve learned along the way; hopefully they’ll help you.
Sidenote: read about how we used our ODN platform to help to ship an urgent HTTPS migration for a major retailer
If you want to get some sense of the challenges, or if you don’t regularly work with large sites in complex organisations, the journey of the BBC to secure their news section might give you some idea of the complexity:
Two years ago, they talk about making changes at their CDNs to enable HTTPS in the future when the individual products (e.g. homepage or travel news) get to the point of being ready on the back-end
By the end of 2017, they are talking about enabling HTTPS to their origins and worrying about how to warm up the HTTPS caches
June 2018 we get the Medium post about the elusive padlock on BBC News after problems like an Indian government-mandated network block that rendered the site totally inaccessible
And then even after all that effort, we realise that the first links I shared there are on the “BBC blogs” section of the site which is still insecure:
Making the case for the enterprise HTTPS migration
In some cases, I find that business cases and return on investment are the most powerful drivers of change, and there are possible approaches that could use data to make this case (looking first at drops in conversion rate from warnings over unsecured pages) but my first approach would be an argument that looks more like this:
We’re definitely going to have to do this eventually
External changes mean that we shouldn’t keep putting it off - there are reputational, business, and operational risks from delaying
It’s a more risk-averse argument focusing on avoidance of downside, but it has powerful emotional elements to it:
1. We’re definitely going to have to do this eventually
There are plenty of rational arguments for the move to HTTPS (great article) but this is mainly an argument that no matter what decisions we make, we can’t put this off forever. We can look at competitors, large sites, and external moves (e.g. by Chrome) to make this point powerfully:
Websites are moving to HTTPS at unprecedented rates
Google research shows that:
More than half of large sites now have HTTPS available (moving from 39% to 54% in the year to Feb 2017) with default HTTPS doubling in a single year
The bigger / more popular a site is, the greater its chance of having HTTPS available and the greater the chance of it using HTTPS by default
A majority of desktop browsing now occurs over HTTPS
All of which means that users are becoming more accustomed to seeing HTTPS everywhere and increasingly expect it. We have even seen this in qualitative feedback from website user testing (create a free account to watch this video):

High ranking websites are particularly likely to be HTTPS
In just 9 months, after announcing HTTPS as a (minor) ranking factor, the % of HTTPS results on page 1 of Google search results jumped from 30% to over 50%:

New features increasingly assume HTTPS connections
Features like HTTP/2 (which can bring significant speed improvements to many sites), and service workers (which are required for app-like capabilities such as offline functionality) require or assume the presence of HTTPS connections. If you aren’t already up to speed on them, this presentation by our VP Product, Tom Anthony will tell you what you need to know (create a free account to watch this video).
2. External changes mean we should do it now
Browser changes increase the urgency of making the change
We have known for some time that Google in particular was going to use their Chrome browser to push webmasters to HTTPS. Initially, the just flagged sites as insecure if they were on HTTP when a form was detected:

They then announced further changes to take it from just those pages to any HTTP page:
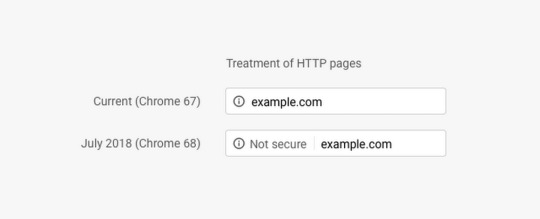
This actually isn’t Google’s last planned update on this theme, there will be a release of Chrome sometime soon that highlights the insecurity in red:
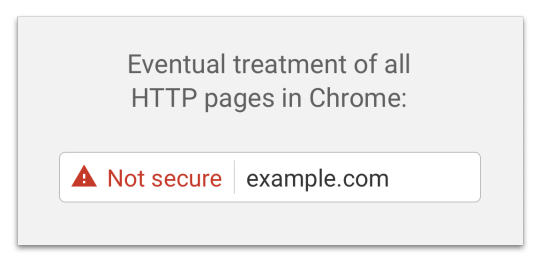
Not only is this change raising the profile of your security setup with your users and customers and most likely hurting engagement and conversion rate, but it is starting to bring bad press down on those who haven’t made the move yet. This BBC article, for example calls out a number of sites by name and cautions that while you shouldn’t necessarily entirely avoid sites that are still on HTTP, “you should be wary on those that require you to sign in or which let you buy goods and services through them”.
Mitigating the risk of an HTTPS migration
OK, so we know it’s something we want to do, and key stakeholders are coming around to the idea, but pretty early in the process, someone is going to bring up risk factors, and how we can minimise and mitigate as many of the risks as possible.
Aside from thorough testing in a staging environment, what else can you do to reduce the risks of going to HTTPS? One key tool in the arsenal is Content Security Policy (CSP) headers. One of the hardest parts of the move is avoiding mixed-content warnings, where your (secure) page references HTTP resources and assets. A good way of mitigating risks and avoiding UI issues and broken functionality from blocked assets is to roll out HTTPS initially with a very lax CSP that allows insecure assets, but reports them via the report-uri policy directive. This means, that on any HTTPS page that uses HTTP resources, the browser will still report the page as insecure but it will work and you will get collect data on which resources are still in use where.
As you then remove all HTTP dependencies, you can tighten up the CSP to much stricter policies and achieve the “secure” label in the browser. Once all pages are fully on HTTPS and redirects are in place, you can add HSTS (Strict-Transport-Security) to the mix. HSTS is a header served on the HTTPS version of your site that is cached by browsers and informs them not to trust the HTTP version in future and always to request the HTTPS version of every page on your site (until the expiry of the HSTS setting).
(Note: the more important security is to your site, the further down this rabbit-hole you may wish to go - right up to preloaded HSTS sites - though note that this is not easily reversible even temporarily in the event of certificate errors.)
There are a variety of great resources on the SEO details, with checklists and processes to follow, so I’m not going to repeat all of the steps here. I recommend:
This article on all the benefits of HTTPS and technical features you can use once you have moved over
Patrick Stox outlined the process, and Aleyda published a great checklist on the SEO steps and implications
You may find it useful to refer to the official Google line (from John Mueller) to reassure stakeholders about Google’s view of the process and its benefits
THOUGH I am very concerned about the advice to “use 302 redirects + rel=canonical to HTTP if you want to test HTTPS but not have it indexed”. I would not recommend ever having canonical links that point to pages that redirect back to the original page (even 302 redirects). I would recommend not doing this.
How are we going to get the details implemented?
As always, knowing what to do and getting agreement to go ahead is only a small part of the battle in many organisations. Large websites and big companies typically have myriad dependencies and integrations of older systems that throw up unexpected roadblocks in the way of the objective. In the case of an HTTPS migration, this is often things like:
We have mixed-content warnings that we can’t deal with at scale - how are we going to update all the references to images on http URLs? What about our 3rd-party plugins and embeds?
Our canonical links all point to the HTTP version of our site and the engineering work to update them across all the different page templates is going to add scary amounts of money to the cost of this project - potentially across multiple back-ends / CMS
We want to add Referrer-policy and especially Content Security Policy headers to enable better testing and mitigate risks, but we have no way to control HTTP headers through our CMS
Recommendations of what to do are worthless if you can’t get them done - a mantra that we repeat a lot at Distilled is it’s not our job to deliver reports - it’s our job to effect change. One of the ways we’ve done this is by building the ODN platform which makes it easy to make agile changes to HTML and HTTP responses. We just completed an urgent HTTPS migration for a major retailer where we addressed exactly these kind of blockers with the platform - you can read more about that here.
If you’re in the unfortunate situation of knowing you need to make the move to HTTPS, and having the organisation aligned, but being blocked by these kinds of technical issue, drop us a line to discuss whether we can help.
CONTACT US TO LEARN MORE ABOUT THE ODN
from Digital Marketing https://www.distilled.net/resources/getting-an-https-migration-done-in-an-enterprise-environment/ via http://www.rssmix.com/
0 notes
Text
How to save your privacy from the Internet’s clutches
How to save your privacy from the Internet’s clutches
Another week, another massive privacy scandal. When it’s not Facebook admitting it allowed data on as many as 87 million users to be sucked out by a developer on its platform who sold it to a political consultancy working for the Trump campaign, or dating app Grindr ‘fessing up to sharing its users’ HIV status with third party A/B testers, some other ugly facet of the tech industry’s love affair with tracking everything its users do slides into view.
Suddenly, Android users discover to their horror that Google’s mobile platform tells the company where they are all the time — thanks to baked-in location tracking bundled with Google services like Maps and Photos. Or Amazon Echo users realize Jeff Bezos’ ecommerce empire has amassed audio recordings of every single interaction they’ve had with their cute little smart speaker.
The problem, as ever with the tech industry’s teeny-weeny greyscaled legalise, is that the people it refers to as “users” aren’t genuinely consenting to having their information sucked into the cloud for goodness knows what. Because they haven’t been given a clear picture of what agreeing to share their data will really mean.
Instead one or two select features, with a mote of user benefit, tend to be presented at the point of sign up — to socially engineer ‘consent’. Then the company can walk away with a defacto license to perpetually harvest that person’s data by claiming that a consent box was once ticked.
A great example of that is Facebook’s Nearby Friends. The feature lets you share your position with your friends so — and here’s that shiny promise — you can more easily hang out with them. But do you know anyone who is actively using this feature? Yet millions of people started sharing their exact location with Facebook for a feature that’s now buried and mostly unused. Meanwhile Facebook is actively using your location to track your offline habits so it can make money targeting you with adverts.
Terms & Conditions are the biggest lie in the tech industry, as we’ve written before. (And more recently: It was not consent, it was concealment.)
Senator Kennedy of Louisiana also made the point succinctly to Facebook founder Mark Zuckerberg this week, telling him to his face: “Your user agreement sucks.” We couldn’t agree more.
Happily disingenuous T&Cs are on borrowed time — at least for European tech users, thanks to a new European Union data protection framework that will come into force next month. The GDPR tightens consent requirements — mandating clear and accurate information be provided to users at the point of sign up. Data collection is also more tightly tied to specific function.
From next month, holding onto personal data without a very good reason to do so will be far more risky — because GDPR is also backed up with a regime of supersized fines that are intended to make privacy rules much harder to ignore.
Of course U.S. tech users can’t bank on benefiting from European privacy regulations. And while there are now growing calls in the country for legislation to protect people’s data — in a bid to steer off the next democracy-denting Cambridge Analytica scandal, at very least — any such process will take a lot of political will.
It certainly will not happen overnight. And you can expect tech giants to fight tooth and nail against laws being drafted and passed — as indeed Facebook, Google and others lobbied fiercely to try to get GDPR watered down.
Facebook has already revealed it will not be universally applying the European regulation — which means people in North America are likely to get a degree of lower privacy than Facebook users everywhere else in the world. Which doesn’t exactly sound fair.
When it comes to privacy, some of you may think you have nothing to hide. But that’s a straw man. It’s especially hard to defend this line of thinking now that big tech companies have attracted so much soft power they can influence elections, inflame conflicts and divide people in general. It’s time to think about the bigger impact of technology on the fabric of society, and not just your personal case.
Shifting the balance
So what can Internet users do right now to stop tech giants, advertisers and unknown entities tracking everything you do online — and trying to join the dots of your digital activity to paint a picture of who they think you are? At least, everything short of moving to Europe, where privacy is a fundamental right.
There are some practical steps you can take to limit day-to-day online privacy risks by reducing third party access to your information and shielding more of your digital activity from prying eyes.
Not all these measures are appropriate for every person. It’s up to you to determine how much effort you want (or need) to put in to shield your privacy.
You may be happy to share a certain amount of personal data in exchange for access to a certain service, for example. But even then it’s unlikely that the full trade-off has been made clear to you. So it’s worth asking yourself if you’re really getting a good deal.
Once people’s eyes are opened to the fine-grained detail and depth of personal information being harvested, even some very seasoned tech users have reacted with shock — saying they had no idea, for example, that Facebook Messenger was continuously uploading their phone book and logging their calls and SMS metadata.
This is one of the reasons why the U.K.’s information commissioner has been calling for increased transparency about how and why data flows. Because for far too long tech savvy entities have been able to apply privacy hostile actions in the dark. And it hasn’t really been possible for the average person to know what’s being done with their information. Or even what data they are giving up when they click ‘I agree’.
Why does an A/B testing firm need to know a person’s HIV status? Why does a social network app need continuous access to your call history? Why should an ad giant be able to continuously pin your movements on a map?
Are you really getting so much value from an app that you’re happy for the company behind it and anyone else they partner with to know everywhere you go, everyone you talk to, the stuff you like and look at �� even to have a pretty good idea what you’re thinking?
Every data misuse scandal shines a bit more light on some very murky practices — which will hopefully generate momentum for rule changes to disinfect data handling processes and strengthen individuals’ privacy by spotlighting trade-offs that have zero justification.
With some effort — and good online security practices (which we’re taking as a given for the purposes of this article, but one quick tip: Enable 2FA everywhere you can) — you can also make it harder for the web’s lurking watchers to dine out on your data.
Just don’t expect the lengths you have to go to protect your privacy to feel fair or just — the horrible truth is this fight sucks.
But whatever you do, don’t give up.
How to hide on the internet
Action: Tape over all your webcams Who is this for: Everyone — even Mark Zuckerberg! How difficult is it: Easy peasy lemon squeezy Tell me more: You can get fancy removable stickers for this purpose (noyb has some nice ones). Or you can go DIY and use a bit of masking tape — on your laptop, your smartphone, even your smart TV… If your job requires you to be on camera, such as for some conference calls, and you want to look a bit more pro you can buy a webcam cover. Sadly locking down privacy is rarely this easy.
Action: Install HTTPS Everywhere Who is this for: Everyone — seriously do it How difficult is it: Mild effort Tell me more: Many websites offer encryption. With HTTPS, people running the network between your device and the server hosting the website you’re browsing can’t see your requests and your internet traffic. But some websites still load unencrypted pages by default (HTTP), which also causes a security risk. The EFF has developed a browser extension that makes sure that you access all websites that offer HTTPS using… HTTPS.
Action: Use tracker blockers Who is this for: Everyone — except people who like being ad-stalked online How difficult is it: Mild effort Tell me more: Trackers refers to a whole category of privacy-hostile technologies designed to follow and record what web users are doing as they move from site to site, and even across different devices. Trackers come in a range of forms these days. And there are some pretty sophisticated ways of being tracked (some definitely harder to thwart than others). But to combat trackers being deployed on popular websites — which are probably also making the pages slower to load than they otherwise would be — there’s now a range of decent, user-friendly tracker blockers to choose from. Pro-privacy search engine DuckDuckGo recently added a tracker blocker to their browser extensions, for example. Disconnect.me is also a popular extension to block trackers from third-party websites. Firefox also has a built-in tracker blocker, which is now enabled by default in the mobile apps. If you’re curious and want to see the list of trackers on popular website, you can also install Kimetrak to understand that it’s a widespread issue.
Action: Use an ad blocker Who is this for: Everyone who can support the moral burden How difficult is it: Fairly easy these days but you might be locked out of the content on some news websites as a result Tell me more: If you’ve tried using a tracker blocker, you may have noticed that many ads have been blocked in the process. That’s because most ads load from third-party servers that track you across multiple sites. So if you want to go one step further and block all ads, you should install an ad blocker. Some browsers like Opera come with an ad blocker. Otherwise, we recommend uBlock Origin on macOS, Windows, Linux and Android. 1Blocker is a solid option on iOS. But let’s be honest, TechCrunch makes some money with online ads. If 100% of web users install an ad blocker many websites you know and love would simply go bankrupt. While your individual choice won’t have a material impact on the bottom line, consider whitelisting the sites you like. And if you’re angry at how many trackers your favorite news site is running try emailing them to ask (politely) if they can at least reduce the number of trackers they use.
Action: Make a private search engine your default Who is this for: Most people How difficult is it: A bit of effort because your search results might become slightly less relevant Tell me more: Google probably knows more about you than even Facebook does, thanks to the things you tell it when you type queries into its search engine. Though that’s just the tip of how it tracks you — if you use Android it will keep running tabs on everywhere you go unless you opt out of location services. It also has its tracking infrastructure embedded on three-quarters of the top million websites. So chances are it’s following what you’re browsing online — unless you also take steps to lock down your browsing (see below). But one major way to limit what Google knows about you is to switch to using an alternative search engine when you need to look something up on the Internet. This isn’t as hard as it used to be as there are some pretty decent alternatives now — such as DuckDuckGo which Apple will let you set as the default browser on iOS — or Qwant for French-speaking users. German users can check out Cliqz. You will also need to remember to be careful about any voice assistants you use as they often default to using Google to look stuff up on the web.
Action: Use private browser sessions Who is this for: Most people How difficult is it: Not at all if you understand what a private session is Tell me more: All browsers on desktop and mobile now let you open a private window. While this can be a powerful tool, it is often misunderstood. By default, private sessions don’t make you more invisible — you’ll get tracked from one tab to another. But private sessions let you start with a clean slate. Every time you close your private session, all your cookies are erased. It’s like you disappear from everyone’s radar. You can then reopen another private session and pretend that nobody knows who you are. That’s why using a private session for weeks or months doesn’t do much, but short private sessions can be helpful.
Action: Use multiple browsers and/or browser containers Who is this for: People who don’t want to stop using social media entirely How difficult is it: Some effort to not get in a muddle Tell me more: Using different browsers for different online activities can be a good way of separating portions of your browsing activity. You could, for example, use one browser on your desktop computer for your online banking, say, and a different browser for your social networking or ecommerce activity. Taking this approach further, you could use different mobile devices when you want to access different apps. The point of dividing your browsing across different browsers/devices is to try to make it harder to link all your online activity to you. That said, lots of adtech effort has been put into developing cross-device tracking techniques — so it’s not clear that fragmenting your browsing sessions will successful beat all the trackers. In a similar vein, in 2016 Mozilla added a feature to its Firefox browser that’s intended to help web users segregate online identities within the same browser — called multi container extensions. This approach gives users some control but it does not stop their browser being fingerprinted and all their web activity in it linked and tracked. It may help reduce some cookie-based tracking, though. Last month Mozilla also updated the container feature to add one that specifically isolates a Facebook user’s identity from the rest of the web. This limits how Facebook can track a user’s non-Facebook web browsing — which yes Facebook does do, whatever Zuckerberg tried to claim in Congress — so again it’s a way to reduce what the social network giant knows about you. (Though it should also be noted that clicking on any Facebook social plug-ins you encounter on other websites will still send Facebook your personal data.)
Action: Get acquainted with Tor Who is this for: Activists, people with high risks attached to being tracked online, committed privacy advocates who want to help grow the Tor network How difficult is it: Patience is needed to use Tor. Also some effort to ensure you don’t accidentally do something that compromises your anonymity Tell me more: For the most robust form of anonymous web browsing there’s Tor. Tor’s onion network works by encrypting and routing your Internet traffic randomly through a series of relay servers to make it harder to link a specific device with a specific online destination. This does mean it’s definitely not the fastest form of web browsing around. Some sites can also try to block Tor users so the Internet experience you get when browsing in this way may suffer. But it’s the best chance of truly preserving your online anonymity. You’ll need to download the relevant Tor browser bundle to use it. It’s pretty straightforward to install and get going. But expect very frequent security updates which will also slow you down.
Action: Switch to another DNS Who is this for: People who don’t trust their ISP How difficult is it: Moderately Tell me more: When you type an address in the address bar (such as techcrunch.com), your device asks a Domain Name Server to translate that address into an IP address (a unique combination of numbers and dots). By default, your ISP or your mobile carrier runs a DNS for their users. It means that they can see all your web history. Big telecom companies are going to take advantage of that to ramp up their advertising efforts. By default, your DNS query is also unencrypted and can be intercepted by people running the network. Some governments also ask telecom companies to block some websites on their DNS servers — some countries block Facebook for censorship reasons, others block The Pirate Bay for online piracy reasons. You can configure each of your device to use another public DNS. But don’t use Google’s public DNS! It’s an ad company, so they really want to see your web history. Both Quad9 and Cloudflare’s 1.1.1.1 have strong privacy policies. But Quad9 is a not-for-profit organization, so it’s easier to trust them.
Action: Disable location services Who is this for: Anyone who feels uncomfortable with the idea of being kept under surveillance How difficult is it: A bit of effort finding and changing settings, and a bit of commitment to stay on top of any ‘updates’ to privacy policies which might try to revive location tracking. You also need to be prepared to accept some reduction in the utility and/or convenience of the service because it won’t be able to automatically customize what it shows you based on your location Tell me more: The tech industry is especially keen to keep tabs on where its users are at any given moment. And thanks to the smash hit success of smartphones with embedded sensors it’s never been easier to pervasively track where people are going — and therefore to infer what they’re doing. For ad targeting purposes location data is highly valuable of course. But it’s also hugely intrusive. Did you just visit a certain type of health clinic? Were you carrying your phone loaded with location-sucking apps? Why then it’s trivially easy for the likes of Google and Facebook to connect your identity to that trip — and link all that intel to their ad networks. And if the social network’s platform isn’t adequately “locked down” — as Zuckerberg would put it — your private information might leak and end up elsewhere. It could even get passed around between all sorts of unknown entities — as the up to 87M Facebook profiles in the Cambridge Analytica scandal appear to have been. (Whistleblower Chris Wylie has said that Facebook data-set went “everywhere”.) There are other potential risks too. Insurance premiums being assessed based on covertly collected data inputs. Companies that work for government agencies using social media info to try to remove benefits or even have people deported. Location data can also influence the types of adverts you see or don’t see. And on that front there’s a risk of discrimination if certain types of ads — jobs or housing, for example — don’t get served to you because you happen to be a person of color, say, or a Muslim. Excluding certain protected groups of people from adverts can be illegal — but that hasn’t stopped it happening multiple times on Facebook’s platform. And location can be a key signal that underpins this kind of prejudicial discrimination. Even the prices you are offered online can depend on what is being inferred about you via your movements. The bottom line is that everyone’s personal data is being made to carry a lot of baggage these days — and most of the time it’s almost impossible to figure out exactly what that unasked for baggage might entail when you consent to letting a particular app or service track where you go. Pervasive tracking of location at very least risks putting you at a disadvantage as a consumer. Certainly if you live somewhere without a proper regulatory framework for privacy. It’s also worth bearing in mind how lax tech giants can be where location privacy is concerned — whether it’s Uber’s infamous ‘god view’ tool or Snapchat leaking schoolkids’ location or Strava accidentally revealing the locations of military bases. Their record is pretty terrible. If you really can’t be bothered to go and hunt down and switch off every location setting one fairly crude action you can take is to buy a faraday cage carry case — Silent Pocket makes an extensive line of carry cases with embedded wireless shielding tech, for instance — which you can pop your smartphone into when you’re on the move to isolate it from the network. Of course once you take it out it will instantly reconnect and location data will be passed again so this is not going to do very much on its own. Nixing location tracking in the settings is much more effective.
Action: Approach VPNs with extreme caution Who is this for: All web users — unless free Internet access is not available in your country How difficult is it: No additional effort Tell me more: While there may be times when you feel tempted to sign up and use a VPN service — say, to try to circumvent geoblocks so you can stream video content that’s not otherwise available in your country — if you do this you should assume that the service provider will at very least be recording everything you’re doing online. They may choose to sell that info or even steal your identity. Many of them promise you perfect privacy and great terms of service. But you can never know for sure if they’re actually doing what they say. So the rule of thumb about all VPNs is: Assume zero privacy — and avoid if at all possible. Facebook even has its own VPN — which it’s been aggressively pushing to users of its main app by badging it as a security service, with the friendly-sounding name ‘Protect’. In reality the company wants you to use this so it can track what other apps you’re using — for its own business intelligence purposes. So a more accurate name for this ‘service’ would be: ‘Protect Facebook’s stranglehold on the social web’.
Action: Build your own VPN server Who is this for: Developers How difficult is it: You need to be comfortable with the Terminal Tell me more: The only VPN server you can trust is the one you built yourself! In that case, VPN servers can be a great tool if you’re on a network you don’t trust (a hotel, a conference or an office). We recommend using Algo VPN and a hosting provider you trust.
Action: Take care with third-party keyboard apps Who is this for: All touchscreen device users How difficult is it: No additional effort Tell me more: Keyboard apps are a potential privacy minefield given that, if you allow cloud-enabled features, they can be in a position to suck out all the information you’re typing into your device — from passwords to credit card numbers to the private contents of your messages. That’s not to say that all third-party keyboards are keylogging everything you type. But the risk is there — so you need to be very careful about what you choose to use. Security is also key. Last year, sensitive personal data from 31M+ users of one third-party keyboard, AI.type, leaked online after the company had failed to properly secure its database server, as one illustrative example of the potential risks. Google knows how powerful keyboards can be as a data-sucker — which is why it got into the third-party keyboard game, outing its own Gboard keyboard app first for Apple’s iOS in 2016 and later bringing it to Android. If you use Gboard you should know you are handing the adtech giant another firehose of your private information — though it claims that only search queries and “usage statistics” are sent by Gboard to Google (The privacy policy further specifies: “Anything you type other than your searches, like passwords or chats with friends, isn’t sent. Saved words on your device aren’t sent.”). So if you believe that Gboard is not literally a keylogger. But it is watching what you search for and how you use your phone. Also worth remembering: Data will still be passed by Gboard to Google if you’re using an e2e encrypted messenger like Signal. So third party keyboards can erode the protection afforded by robust e2e encryption — so again: Be very careful what you use.
Action: Use end-to-end encrypted messengers Who is this for: Everyone who can How difficult is it: Mild effort unless all your friends are using other messaging apps Tell me more: Choosing friends based on their choice of messaging app isn’t a great option so real world network effects can often work against privacy. Indeed, Facebook uses the fuzzy feelings you have about your friends to manipulate Messenger users to consent to continuously uploading their phone contacts, by suggesting you have to if you want to talk to your contacts. (Which is, by the by, entirely bogus.) But if all your friends use a messaging app that does not have end-to-end encryption chances are you’ll feel forced to use that same non-privacy-safe app too. Given that the other option is to exclude yourself from the digital chatter of your friend group. Which would clearly suck. Facebook-owned WhatsApp does at least have end-to-end encryption — and is widely used (certainly internationally). Though you still need to be careful to opt out of any privacy-eroding terms the company tries to push. In summer 2016, for example, a major T&Cs change sought to link WhatsApp users’ accounts with their Facebook profiles (and thus with all the data Facebook holds on them) — as well as sharing sensitive stuff like your last seen status, your address book, your BFFs in Whatsapp and all sorts of metadata with Zuck’s ‘family’ of companies. Thankfully most of this privacy-hostile data sharing has been suspended in Europe, after Facebook got in trouble with local data protection agencies.
Action: Use end-to-end encryption if you use cloud storage Who is this for: Dedicated privacy practitioners, anyone worried about third parties accessing their stuff How difficult is it: Some effort, especially if you have lots of content stored in another service that you need to migrate Tell me more: Dropbox IPO’d last month — and the markets signalled their approval of its business. But someone who doesn’t approve of the cloud storage giant is Edward Snowden — who in 2014 advised: “Get rid of Dropbox”, arguing the company is hostile to privacy. The problem is that Dropbox does not offer zero access encryption — because it retains encryption keys, meaning it can technically decrypt and read the data you store with it if it decides it needs to or is served with a warrant. Cloud storage alternatives that do offer local encryption with no access to the encryption keys are available, such as Spideroak. And if you’re looking for a cloud backup service, Backblaze also offers the option to let you manage the encryption key. Another workaround if you do still want to use a service like Dropbox is to locally encrypt the stuff you want to store before you upload it — using another third party service such as Boxcryptor.
Action: Use an end-to-end encrypted email service Who is this for: Anyone who wants to be sure their email isn’t being data mined How difficult is it: Some effort — largely around migrating data and/or contacts from another email service Tell me more: In the middle of last year Google finally announced it would no longer be data-mining the emails inside its Gmail free email service. (For a little perspective on how long it took to give up data-mining your emails, Gmail launched all the way back in 2004.) The company probably feels it has more than enough alternative data points feeding its user profiling at this point. Plus data-mining email with the rise of end-to-end encrypted messaging apps risks pushing the company over the ‘creepy line’ it’s been so keen to avoid to try to stave off the kind of privacy backlash currently engulfing Facebook. So does it mean that Gmail is now 100% privacy safe? No, because the service is not end-to-end encrypted. But there are now some great webmail clients that do offer robust end-to-end encryption — most notably the Swiss service Protonmail. Really it’s never been easier to access a reliable, user-friendly, pro-privacy email service. If you want to go one step further, you should set up PGP encryption keys and share them with your contacts. This is a lot more difficult though.
Action: Choose iOS over Android Who is this for: Mainstream consumers, Apple fans How difficult is it: Depends on the person. Apple hardware is generally more expensive so there’s a cost premium Tell me more: No connected technology is 100% privacy safe but Apple’s hardware-focused business model means the company’s devices are not engineered to try to harvest user data by default. Apple does also invest in developing pro-privacy technologies. Whereas there’s no getting around the fact Android-maker Google is an adtech giant whose revenues depend on profiling users in order to target web users with adverts. Basically the company needs to suck your data to make a fat profit. That’s why Google asks you to share all your web and app activity and location history if you want to use Google Assistant, for instance. Android is a more open platform than iOS, though, and it’s possible to configure it in many different ways — some of which can be more locked down as regards privacy than others (the Android Open Source Project can be customized and used without Google services as default preloads, for example). But doing that kind of configuration is not going to be within reach of the average person. So iOS is the obvious choice for mainstream consumers.
Action: Delete your social media accounts Who is this for: Committed privacy lovers, anyone bored with public sharing How difficult is it: Some effort — mostly feeling like you’re going to miss out. But third party services can sometimes require a Facebook login (a workaround for that would be to create a dummy Facebook account purely for login purposes — using a name and email you don’t use for anything else, and not linking it to your usual mobile phone number or adding anyone you actually know IRL) Tell me more: Deleting Facebook clearly isn’t for everyone. But ask yourself how much you use it these days anyway? You might find yourself realizing it’s not really that central to what you do on the Internet after all. The center of gravity in social networking has shifted away from mass public sharing into more tightly curated friend groups anyway, thanks to the popularity of messaging apps. But of course Facebook owns Messenger, Instagram and WhatsApp too. So ducking out of its surveillance dragnet entirely is especially hard. Ideally you would also need to run tracker blockers (see above) as the company tracks non-Facebook users around the Internet via the pixels it has embedded on lots of popular websites. While getting rid of your social media accounts is not a privacy panacea, removing yourself from mainstream social network platforms at least reduces the risk of a chunk of your personal info being scraped and used without your say so. Though it’s still not absolutely guaranteed that when you delete an account the company in question will faithfully remove all your information from their servers — or indeed from the servers of any third party they shared your data with. If you really can’t bring yourself to ditch Facebook (et al) entirely, at least dive into the settings and make sure you lock down as much access to your data as you can — including checking which apps have been connected to your account and removing any that aren’t relevant or useful to you anymore.
Action: Say no to always-on voice assistants Who is this for: Anyone who values privacy more than gimmickry How difficult is it: No real effort Tell me more: There’s a rash of smart speaker voice assistants on shop shelves these days, marketed in a way that suggests they’re a whole lot smarter and more useful than they actually are. In reality they’re most likely to be used for playing music (albeit, audio quality can be very poor) or as very expensive egg timers. Something else the PR for gadgets like Amazon’s (many) Echos or Google Home doesn’t mention is the massive privacy trade off involved with installing an always-on listening device inside your home. Essentially these devices function by streaming whatever you ask to the cloud and will typically store recordings of things you’ve said in perpetuity on the companies’ servers. Some do offer a delete option for stored audio but you would have to stay on top of deleting your data as long as you keep using the device. So it’s a tediously Sisyphean task. Smart speakers have also been caught listening to and recording things their owner didn’t actually want them to — because they got triggered by accident. Or when someone on the TV used the trigger word. The privacy risks around smart speakers are clearly very large indeed. Not least because this type of personal data is of obvious and inevitable interest to law enforcement agencies. So ask yourself whether that fake fart dispenser gizmo you’re giggling about is really worth the trade off of inviting all sorts of outsiders to snoop on the goings on inside your home.
Action: Block some network requests Who is this for: Paranoid people How difficult is it: Need to be tech savvy Tell me more: On macOS, you can install something called Little Snitch to get an alert every time an app tries to talk with a server. You can approve or reject each request and create rules. If you don’t want Microsoft Word to talk with Microsoft’s servers all the time for instance, it’s a good solution — but is not really user friendly.
Action: Use a privacy-focused operating system Who is this for: Edward Snowden How difficult is it: Need to be tech savvy Tell me more: If you really want to lock everything down, you should consider using Tails as your desktop operating system. It’s a Linux distribution that leaves no trace by default, uses the Tor network for all network requests by default. But it’s not exactly user friendly, and it’s quite complicated to install on a USB drive. One for those whose threat model really is ‘bleeding edge’.
Action: Write to your political reps to demand stronger privacy laws Who is this for: Anyone who cares about privacy, and especially Internet users in North America right now How difficult is it: A bit of effort Tell me more: There appears to be bipartisan appetite among U.S. lawmakers to bring in some form of regulation for Internet companies. And with new tougher rules coming in in Europe next month it’s an especially opportune moment to push for change in the U.S. where web users are facing reduced standards vs international users after May 25. So it’s a great time to write to your reps reminding them you’re far more interested in your privacy being protected than Facebook winning some kind of surveillance arms race with the Chinese. Tell them it’s past time for the U.S. to draft laws that prioritize the protection of personal data.
Action: Throw away all your connected devices — and choose your friends wisely Who is this for: Fugitives and whistleblowers How difficult is it: Privacy doesn’t get harder than this Tell me more: Last month the former Catalan president, Carles Puigdemont — who, in October, dodged arrest by the Spanish authorities by fleeing to Brussels after the region’s abortive attempt to declare independence — was arrested by German police, after crossing the border from Denmark in a car. Spanish intelligence agents had reportedly tracked his movements via the GPS on the mobile device of one or more of his friends. The car had also been fitted with a tracker. Trusting anything not to snitch on you is a massive risk if your threat model is this high. The problem is you also need trustworthy friends to help you stay ahead of the surveillance dragnet that’s out to get you.
Action: Ditch the Internet entirely Who is this for: Fugitives and whistleblowers How difficult is it: Privacy doesn’t get harder than this Tell me more: Public administrations can ask you to do pretty much everything online these days — and even if it’s not mandatory to use their Internet service it can be incentivized in various ways. The direction of travel for government services is clearly digital. So eschewing the Internet entirely is getting harder and harder to do. One wild card option — that’s still not a full Internet alternative (yet) — is to use a different type of network that’s being engineered with privacy in mind. The experimental, decentralized MaidSafe network fits that bill. This majorly ambitious project has already clocked up a decade’s worth of R&D on the founders’ mission to rethink digital connectivity without compromising privacy and security by doing away with servers — and decentralizing and encrypting everything. It’s a fascinating project. Just sadly not yet a fully-fledged Internet alternative.
0 notes
Text
How to save your privacy from the Internet’s clutches
Another week, another massive privacy scandal. When it’s not Facebook admitting it allowed data on as many as 87 million users to be sucked out by a developer on its platform who sold it to a political consultancy working for the Trump campaign, or dating app Grindr ‘fessing up to sharing its users’ HIV status with third party A/B testers, some other ugly facet of the tech industry’s love affair with tracking everything its users do slides into view.
Suddenly, Android users discover to their horror that Google’s mobile platform tells the company where they are all the time — thanks to baked-in location tracking bundled with Google services like Maps and Photos. Or Amazon Echo users realize Jeff Bezos’ ecommerce empire has amassed audio recordings of every single interaction they’ve had with their cute little smart speaker.
The problem, as ever with the tech industry’s teeny-weeny greyscaled legalise, is that the people it refers to as “users” aren’t genuinely consenting to having their information sucked into the cloud for goodness knows what. Because they haven’t been given a clear picture of what agreeing to share their data will really mean.
Instead one or two select features, with a mote of user benefit, tend to be presented at the point of sign up — to socially engineer ‘consent’. Then the company can walk away with a defacto license to perpetually harvest that person’s data by claiming that a consent box was once ticked.
A great example of that is Facebook’s Nearby Friends. The feature lets you share your position with your friends so — and here’s that shiny promise — you can more easily hang out with them. But do you know anyone who is actively using this feature? Yet millions of people started sharing their exact location with Facebook for a feature that’s now buried and mostly unused. Meanwhile Facebook is actively using your location to track your offline habits so it can make money targeting you with adverts.
Terms & Conditions are the biggest lie in the tech industry, as we’ve written before. (And more recently: It was not consent, it was concealment.)
Senator Kennedy of Louisiana also made the point succinctly to Facebook founder Mark Zuckerberg this week, telling him to his face: “Your user agreement sucks.” We couldn’t agree more.
Happily disingenuous T&Cs are on borrowed time — at least for European tech users, thanks to a new European Union data protection framework that will come into force next month. The GDPR tightens consent requirements — mandating clear and accurate information be provided to users at the point of sign up. Data collection is also more tightly tied to specific function.
From next month, holding onto personal data without a very good reason to do so will be far more risky — because GDPR is also backed up with a regime of supersized fines that are intended to make privacy rules much harder to ignore.
Of course U.S. tech users can’t bank on benefiting from European privacy regulations. And while there are now growing calls in the country for legislation to protect people’s data — in a bid to steer off the next democracy-denting Cambridge Analytica scandal, at very least — any such process will take a lot of political will.
It certainly will not happen overnight. And you can expect tech giants to fight tooth and nail against laws being drafted and passed — as indeed Facebook, Google and others lobbied fiercely to try to get GDPR watered down.
Facebook has already revealed it will not be universally applying the European regulation — which means people in North America are likely to get a degree of lower privacy than Facebook users everywhere else in the world. Which doesn’t exactly sound fair.
When it comes to privacy, some of you may think you have nothing to hide. But that’s a straw man. It’s especially hard to defend this line of thinking now that big tech companies have attracted so much soft power they can influence elections, inflame conflicts and divide people in general. It’s time to think about the bigger impact of technology on the fabric of society, and not just your personal case.
Shifting the balance
So what can Internet users do right now to stop tech giants, advertisers and unknown entities tracking everything you do online — and trying to join the dots of your digital activity to paint a picture of who they think you are? At least, everything short of moving to Europe, where privacy is a fundamental right.
There are some practical steps you can take to limit day-to-day online privacy risks by reducing third party access to your information and shielding more of your digital activity from prying eyes.
Not all these measures are appropriate for every person. It’s up to you to determine how much effort you want (or need) to put in to shield your privacy.
You may be happy to share a certain amount of personal data in exchange for access to a certain service, for example. But even then it’s unlikely that the full trade-off has been made clear to you. So it’s worth asking yourself if you’re really getting a good deal.
Once people’s eyes are opened to the fine-grained detail and depth of personal information being harvested, even some very seasoned tech users have reacted with shock — saying they had no idea, for example, that Facebook Messenger was continuously uploading their phone book and logging their calls and SMS metadata.
This is one of the reasons why the U.K.’s information commissioner has been calling for increased transparency about how and why data flows. Because for far too long tech savvy entities have been able to apply privacy hostile actions in the dark. And it hasn’t really been possible for the average person to know what’s being done with their information. Or even what data they are giving up when they click ‘I agree’.
Why does an A/B testing firm need to know a person’s HIV status? Why does a social network app need continuous access to your call history? Why should an ad giant be able to continuously pin your movements on a map?
Are you really getting so much value from an app that you’re happy for the company behind it and anyone else they partner with to know everywhere you go, everyone you talk to, the stuff you like and look at — even to have a pretty good idea what you’re thinking?
Every data misuse scandal shines a bit more light on some very murky practices — which will hopefully generate momentum for rule changes to disinfect data handling processes and strengthen individuals’ privacy by spotlighting trade-offs that have zero justification.
With some effort — and good online security practices (which we’re taking as a given for the purposes of this article, but one quick tip: Enable 2FA everywhere you can) — you can also make it harder for the web’s lurking watchers to dine out on your data.
Just don’t expect the lengths you have to go to protect your privacy to feel fair or just — the horrible truth is this fight sucks.
But whatever you do, don’t give up.
How to hide on the internet
Action: Tape over all your webcams Who is this for: Everyone — even Mark Zuckerberg! How difficult is it: Easy peasy lemon squeezy Tell me more: You can get fancy removable stickers for this purpose (noyb has some nice ones). Or you can go DIY and use a bit of masking tape — on your laptop, your smartphone, even your smart TV… If your job requires you to be on camera, such as for some conference calls, and you want to look a bit more pro you can buy a webcam cover. Sadly locking down privacy is rarely this easy.
Action: Install HTTPS Everywhere Who is this for: Everyone — seriously do it How difficult is it: Mild effort Tell me more: Many websites offer encryption. With HTTPS, people running the network between your device and the server hosting the website you’re browsing can’t see your requests and your internet traffic. But some websites still load unencrypted pages by default (HTTP), which also causes a security risk. The EFF has developed a browser extension that makes sure that you access all websites that offer HTTPS using… HTTPS.
Action: Use tracker blockers Who is this for: Everyone — except people who like being ad-stalked online How difficult is it: Mild effort Tell me more: Trackers refers to a whole category of privacy-hostile technologies designed to follow and record what web users are doing as they move from site to site, and even across different devices. Trackers come in a range of forms these days. And there are some pretty sophisticated ways of being tracked (some definitely harder to thwart than others). But to combat trackers being deployed on popular websites — which are probably also making the pages slower to load than they otherwise would be — there’s now a range of decent, user-friendly tracker blockers to choose from. Pro-privacy search engine DuckDuckGo recently added a tracker blocker to their browser extensions, for example. Disconnect.me is also a popular extension to block trackers from third-party websites. Firefox also has a built-in tracker blocker, which is now enabled by default in the mobile apps. If you’re curious and want to see the list of trackers on popular website, you can also install Kimetrak to understand that it’s a widespread issue.
Action: Use an ad blocker Who is this for: Everyone who can support the moral burden How difficult is it: Fairly easy these days but you might be locked out of the content on some news websites as a result Tell me more: If you’ve tried using a tracker blocker, you may have noticed that many ads have been blocked in the process. That’s because most ads load from third-party servers that track you across multiple sites. So if you want to go one step further and block all ads, you should install an ad blocker. Some browsers like Opera come with an ad blocker. Otherwise, we recommend uBlock Origin on macOS, Windows, Linux and Android. 1Blocker is a solid option on iOS. But let’s be honest, TechCrunch makes some money with online ads. If 100% of web users install an ad blocker many websites you know and love would simply go bankrupt. While your individual choice won’t have a material impact on the bottom line, consider whitelisting the sites you like. And if you’re angry at how many trackers your favorite news site is running try emailing them to ask (politely) if they can at least reduce the number of trackers they use.
Action: Make a private search engine your default Who is this for: Most people How difficult is it: A bit of effort because your search results might become slightly less relevant Tell me more: Google probably knows more about you than even Facebook does, thanks to the things you tell it when you type queries into its search engine. Though that’s just the tip of how it tracks you — if you use Android it will keep running tabs on everywhere you go unless you opt out of location services. It also has its tracking infrastructure embedded on three-quarters of the top million websites. So chances are it’s following what you’re browsing online — unless you also take steps to lock down your browsing (see below). But one major way to limit what Google knows about you is to switch to using an alternative search engine when you need to look something up on the Internet. This isn’t as hard as it used to be as there are some pretty decent alternatives now — such as DuckDuckGo which Apple will let you set as the default browser on iOS — or Qwant for French-speaking users. German users can check out Cliqz. You will also need to remember to be careful about any voice assistants you use as they often default to using Google to look stuff up on the web.
Action: Use private browser sessions Who is this for: Most people How difficult is it: Not at all if you understand what a private session is Tell me more: All browsers on desktop and mobile now let you open a private window. While this can be a powerful tool, it is often misunderstood. By default, private sessions don’t make you more invisible — you’ll get tracked from one tab to another. But private sessions let you start with a clean slate. Every time you close your private session, all your cookies are erased. It’s like you disappear from everyone’s radar. You can then reopen another private session and pretend that nobody knows who you are. That’s why using a private session for weeks or months doesn’t do much, but short private sessions can be helpful.
Action: Use multiple browsers and/or browser containers Who is this for: People who don’t want to stop using social media entirely How difficult is it: Some effort to not get in a muddle Tell me more: Using different browsers for different online activities can be a good way of separating portions of your browsing activity. You could, for example, use one browser on your desktop computer for your online banking, say, and a different browser for your social networking or ecommerce activity. Taking this approach further, you could use different mobile devices when you want to access different apps. The point of dividing your browsing across different browsers/devices is to try to make it harder to link all your online activity to you. That said, lots of adtech effort has been put into developing cross-device tracking techniques — so it’s not clear that fragmenting your browsing sessions will successful beat all the trackers. In a similar vein, in 2016 Mozilla added a feature to its Firefox browser that’s intended to help web users segregate online identities within the same browser — called multi container extensions. This approach gives users some control but it does not stop their browser being fingerprinted and all their web activity in it linked and tracked. It may help reduce some cookie-based tracking, though. Last month Mozilla also updated the container feature to add one that specifically isolates a Facebook user’s identity from the rest of the web. This limits how Facebook can track a user’s non-Facebook web browsing — which yes Facebook does do, whatever Zuckerberg tried to claim in Congress — so again it’s a way to reduce what the social network giant knows about you. (Though it should also be noted that clicking on any Facebook social plug-ins you encounter on other websites will still send Facebook your personal data.)
Action: Get acquainted with Tor Who is this for: Activists, people with high risks attached to being tracked online, committed privacy advocates who want to help grow the Tor network How difficult is it: Patience is needed to use Tor. Also some effort to ensure you don’t accidentally do something that compromises your anonymity Tell me more: For the most robust form of anonymous web browsing there’s Tor. Tor’s onion network works by encrypting and routing your Internet traffic randomly through a series of relay servers to make it harder to link a specific device with a specific online destination. This does mean it’s definitely not the fastest form of web browsing around. Some sites can also try to block Tor users so the Internet experience you get when browsing in this way may suffer. But it’s the best chance of truly preserving your online anonymity. You’ll need to download the relevant Tor browser bundle to use it. It’s pretty straightforward to install and get going. But expect very frequent security updates which will also slow you down.
Action: Switch to another DNS Who is this for: People who don’t trust their ISP How difficult is it: Moderately Tell me more: When you type an address in the address bar (such as techcrunch.com), your device asks a Domain Name Server to translate that address into an IP address (a unique combination of numbers and dots). By default, your ISP or your mobile carrier runs a DNS for their users. It means that they can see all your web history. Big telecom companies are going to take advantage of that to ramp up their advertising efforts. By default, your DNS query is also unencrypted and can be intercepted by people running the network. Some governments also ask telecom companies to block some websites on their DNS servers — some countries block Facebook for censorship reasons, others block The Pirate Bay for online piracy reasons. You can configure each of your device to use another public DNS. But don’t use Google’s public DNS! It’s an ad company, so they really want to see your web history. Both Quad9 and Cloudflare’s 1.1.1.1 have strong privacy policies. But Quad9 is a not-for-profit organization, so it’s easier to trust them.
Action: Disable location services Who is this for: Anyone who feels uncomfortable with the idea of being kept under surveillance How difficult is it: A bit of effort finding and changing settings, and a bit of commitment to stay on top of any ‘updates’ to privacy policies which might try to revive location tracking. You also need to be prepared to accept some reduction in the utility and/or convenience of the service because it won’t be able to automatically customize what it shows you based on your location Tell me more: The tech industry is especially keen to keep tabs on where its users are at any given moment. And thanks to the smash hit success of smartphones with embedded sensors it’s never been easier to pervasively track where people are going — and therefore to infer what they’re doing. For ad targeting purposes location data is highly valuable of course. But it’s also hugely intrusive. Did you just visit a certain type of health clinic? Were you carrying your phone loaded with location-sucking apps? Why then it’s trivially easy for the likes of Google and Facebook to connect your identity to that trip — and link all that intel to their ad networks. And if the social network’s platform isn’t adequately “locked down” — as Zuckerberg would put it — your private information might leak and end up elsewhere. It could even get passed around between all sorts of unknown entities — as the up to 87M Facebook profiles in the Cambridge Analytica scandal appear to have been. (Whistleblower Chris Wylie has said that Facebook data-set went “everywhere”.) There are other potential risks too. Insurance premiums being assessed based on covertly collected data inputs. Companies that work for government agencies using social media info to try to remove benefits or even have people deported. Location data can also influence the types of adverts you see or don’t see. And on that front there’s a risk of discrimination if certain types of ads — jobs or housing, for example — don’t get served to you because you happen to be a person of color, say, or a Muslim. Excluding certain protected groups of people from adverts can be illegal — but that hasn’t stopped it happening multiple times on Facebook’s platform. And location can be a key signal that underpins this kind of prejudicial discrimination. Even the prices you are offered online can depend on what is being inferred about you via your movements. The bottom line is that everyone’s personal data is being made to carry a lot of baggage these days — and most of the time it’s almost impossible to figure out exactly what that unasked for baggage might entail when you consent to letting a particular app or service track where you go. Pervasive tracking of location at very least risks putting you at a disadvantage as a consumer. Certainly if you live somewhere without a proper regulatory framework for privacy. It’s also worth bearing in mind how lax tech giants can be where location privacy is concerned — whether it’s Uber’s infamous ‘god view’ tool or Snapchat leaking schoolkids’ location or Strava accidentally revealing the locations of military bases. Their record is pretty terrible. If you really can’t be bothered to go and hunt down and switch off every location setting one fairly crude action you can take is to buy a faraday cage carry case — Silent Pocket makes an extensive line of carry cases with embedded wireless shielding tech, for instance — which you can pop your smartphone into when you’re on the move to isolate it from the network. Of course once you take it out it will instantly reconnect and location data will be passed again so this is not going to do very much on its own. Nixing location tracking in the settings is much more effective.
Action: Approach VPNs with extreme caution Who is this for: All web users — unless free Internet access is not available in your country How difficult is it: No additional effort Tell me more: While there may be times when you feel tempted to sign up and use a VPN service — say, to try to circumvent geoblocks so you can stream video content that’s not otherwise available in your country — if you do this you should assume that the service provider will at very least be recording everything you’re doing online. They may choose to sell that info or even steal your identity. Many of them promise you perfect privacy and great terms of service. But you can never know for sure if they’re actually doing what they say. So the rule of thumb about all VPNs is: Assume zero privacy — and avoid if at all possible. Facebook even has its own VPN — which it’s been aggressively pushing to users of its main app by badging it as a security service, with the friendly-sounding name ‘Protect’. In reality the company wants you to use this so it can track what other apps you’re using — for its own business intelligence purposes. So a more accurate name for this ‘service’ would be: ‘Protect Facebook’s stranglehold on the social web’.
Action: Build your own VPN server Who is this for: Developers How difficult is it: You need to be comfortable with the Terminal Tell me more: The only VPN server you can trust is the one you built yourself! In that case, VPN servers can be a great tool if you’re on a network you don’t trust (a hotel, a conference or an office). We recommend using Algo VPN and a hosting provider you trust.
Action: Take care with third-party keyboard apps Who is this for: All touchscreen device users How difficult is it: No additional effort Tell me more: Keyboard apps are a potential privacy minefield given that, if you allow cloud-enabled features, they can be in a position to suck out all the information you’re typing into your device — from passwords to credit card numbers to the private contents of your messages. That’s not to say that all third-party keyboards are keylogging everything you type. But the risk is there — so you need to be very careful about what you choose to use. Security is also key. Last year, sensitive personal data from 31M+ users of one third-party keyboard, AI.type, leaked online after the company had failed to properly secure its database server, as one illustrative example of the potential risks. Google knows how powerful keyboards can be as a data-sucker — which is why it got into the third-party keyboard game, outing its own Gboard keyboard app first for Apple’s iOS in 2016 and later bringing it to Android. If you use Gboard you should know you are handing the adtech giant another firehose of your private information — though it claims that only search queries and “usage statistics” are sent by Gboard to Google (The privacy policy further specifies: “Anything you type other than your searches, like passwords or chats with friends, isn’t sent. Saved words on your device aren’t sent.”). So if you believe that Gboard is not literally a keylogger. But it is watching what you search for and how you use your phone. Also worth remembering: Data will still be passed by Gboard to Google if you’re using an e2e encrypted messenger like Signal. So third party keyboards can erode the protection afforded by robust e2e encryption — so again: Be very careful what you use.
Action: Use end-to-end encrypted messengers Who is this for: Everyone who can How difficult is it: Mild effort unless all your friends are using other messaging apps Tell me more: Choosing friends based on their choice of messaging app isn’t a great option so real world network effects can often work against privacy. Indeed, Facebook uses the fuzzy feelings you have about your friends to manipulate Messenger users to consent to continuously uploading their phone contacts, by suggesting you have to if you want to talk to your contacts. (Which is, by the by, entirely bogus.) But if all your friends use a messaging app that does not have end-to-end encryption chances are you’ll feel forced to use that same non-privacy-safe app too. Given that the other option is to exclude yourself from the digital chatter of your friend group. Which would clearly suck. Facebook-owned WhatsApp does at least have end-to-end encryption — and is widely used (certainly internationally). Though you still need to be careful to opt out of any privacy-eroding terms the company tries to push. In summer 2016, for example, a major T&Cs change sought to link WhatsApp users’ accounts with their Facebook profiles (and thus with all the data Facebook holds on them) — as well as sharing sensitive stuff like your last seen status, your address book, your BFFs in Whatsapp and all sorts of metadata with Zuck’s ‘family’ of companies. Thankfully most of this privacy-hostile data sharing has been suspended in Europe, after Facebook got in trouble with local data protection agencies.
Action: Use end-to-end encryption if you use cloud storage Who is this for: Dedicated privacy practitioners, anyone worried about third parties accessing their stuff How difficult is it: Some effort, especially if you have lots of content stored in another service that you need to migrate Tell me more: Dropbox IPO’d last month — and the markets signalled their approval of its business. But someone who doesn’t approve of the cloud storage giant is Edward Snowden — who in 2014 advised: “Get rid of Dropbox”, arguing the company is hostile to privacy. The problem is that Dropbox does not offer zero access encryption — because it retains encryption keys, meaning it can technically decrypt and read the data you store with it if it decides it needs to or is served with a warrant. Cloud storage alternatives that do offer local encryption with no access to the encryption keys are available, such as Spideroak. And if you’re looking for a cloud backup service, Backblaze also offers the option to let you manage the encryption key. Another workaround if you do still want to use a service like Dropbox is to locally encrypt the stuff you want to store before you upload it — using another third party service such as Boxcryptor.
Action: Use an end-to-end encrypted email service Who is this for: Anyone who wants to be sure their email isn’t being data mined How difficult is it: Some effort — largely around migrating data and/or contacts from another email service Tell me more: In the middle of last year Google finally announced it would no longer be data-mining the emails inside its Gmail free email service. (For a little perspective on how long it took to give up data-mining your emails, Gmail launched all the way back in 2004.) The company probably feels it has more than enough alternative data points feeding its user profiling at this point. Plus data-mining email with the rise of end-to-end encrypted messaging apps risks pushing the company over the ‘creepy line’ it’s been so keen to avoid to try to stave off the kind of privacy backlash currently engulfing Facebook. So does it mean that Gmail is now 100% privacy safe? No, because the service is not end-to-end encrypted. But there are now some great webmail clients that do offer robust end-to-end encryption — most notably the Swiss service Protonmail. Really it’s never been easier to access a reliable, user-friendly, pro-privacy email service. If you want to go one step further, you should set up PGP encryption keys and share them with your contacts. This is a lot more difficult though.
Action: Choose iOS over Android Who is this for: Mainstream consumers, Apple fans How difficult is it: Depends on the person. Apple hardware is generally more expensive so there’s a cost premium Tell me more: No connected technology is 100% privacy safe but Apple’s hardware-focused business model means the company’s devices are not engineered to try to harvest user data by default. Apple does also invest in developing pro-privacy technologies. Whereas there’s no getting around the fact Android-maker Google is an adtech giant whose revenues depend on profiling users in order to target web users with adverts. Basically the company needs to suck your data to make a fat profit. That’s why Google asks you to share all your web and app activity and location history if you want to use Google Assistant, for instance. Android is a more open platform than iOS, though, and it’s possible to configure it in many different ways — some of which can be more locked down as regards privacy than others (the Android Open Source Project can be customized and used without Google services as default preloads, for example). But doing that kind of configuration is not going to be within reach of the average person. So iOS is the obvious choice for mainstream consumers.
Action: Delete your social media accounts Who is this for: Committed privacy lovers, anyone bored with public sharing How difficult is it: Some effort — mostly feeling like you’re going to miss out. But third party services can sometimes require a Facebook login (a workaround for that would be to create a dummy Facebook account purely for login purposes — using a name and email you don’t use for anything else, and not linking it to your usual mobile phone number or adding anyone you actually know IRL) Tell me more: Deleting Facebook clearly isn’t for everyone. But ask yourself how much you use it these days anyway? You might find yourself realizing it’s not really that central to what you do on the Internet after all. The center of gravity in social networking has shifted away from mass public sharing into more tightly curated friend groups anyway, thanks to the popularity of messaging apps. But of course Facebook owns Messenger, Instagram and WhatsApp too. So ducking out of its surveillance dragnet entirely is especially hard. Ideally you would also need to run tracker blockers (see above) as the company tracks non-Facebook users around the Internet via the pixels it has embedded on lots of popular websites. While getting rid of your social media accounts is not a privacy panacea, removing yourself from mainstream social network platforms at least reduces the risk of a chunk of your personal info being scraped and used without your say so. Though it’s still not absolutely guaranteed that when you delete an account the company in question will faithfully remove all your information from their servers — or indeed from the servers of any third party they shared your data with. If you really can’t bring yourself to ditch Facebook (et al) entirely, at least dive into the settings and make sure you lock down as much access to your data as you can — including checking which apps have been connected to your account and removing any that aren’t relevant or useful to you anymore.
Action: Say no to always-on voice assistants Who is this for: Anyone who values privacy more than gimmickry How difficult is it: No real effort Tell me more: There’s a rash of smart speaker voice assistants on shop shelves these days, marketed in a way that suggests they’re a whole lot smarter and more useful than they actually are. In reality they’re most likely to be used for playing music (albeit, audio quality can be very poor) or as very expensive egg timers. Something else the PR for gadgets like Amazon’s (many) Echos or Google Home doesn’t mention is the massive privacy trade off involved with installing an always-on listening device inside your home. Essentially these devices function by streaming whatever you ask to the cloud and will typically store recordings of things you’ve said in perpetuity on the companies’ servers. Some do offer a delete option for stored audio but you would have to stay on top of deleting your data as long as you keep using the device. So it’s a tediously Sisyphean task. Smart speakers have also been caught listening to and recording things their owner didn’t actually want them to — because they got triggered by accident. Or when someone on the TV used the trigger word. The privacy risks around smart speakers are clearly very large indeed. Not least because this type of personal data is of obvious and inevitable interest to law enforcement agencies. So ask yourself whether that fake fart dispenser gizmo you’re giggling about is really worth the trade off of inviting all sorts of outsiders to snoop on the goings on inside your home.
Action: Block some network requests Who is this for: Paranoid people How difficult is it: Need to be tech savvy Tell me more: On macOS, you can install something called Little Snitch to get an alert every time an app tries to talk with a server. You can approve or reject each request and create rules. If you don’t want Microsoft Word to talk with Microsoft’s servers all the time for instance, it’s a good solution — but is not really user friendly.
Action: Use a privacy-focused operating system Who is this for: Edward Snowden How difficult is it: Need to be tech savvy Tell me more: If you really want to lock everything down, you should consider using Tails as your desktop operating system. It’s a Linux distribution that leaves no trace by default, uses the Tor network for all network requests by default. But it’s not exactly user friendly, and it’s quite complicated to install on a USB drive. One for those whose threat model really is ‘bleeding edge’.
Action: Write to your political reps to demand stronger privacy laws Who is this for: Anyone who cares about privacy, and especially Internet users in North America right now How difficult is it: A bit of effort Tell me more: There appears to be bipartisan appetite among U.S. lawmakers to bring in some form of regulation for Internet companies. And with new tougher rules coming in in Europe next month it’s an especially opportune moment to push for change in the U.S. where web users are facing reduced standards vs international users after May 25. So it’s a great time to write to your reps reminding them you’re far more interested in your privacy being protected than Facebook winning some kind of surveillance arms race with the Chinese. Tell them it’s past time for the U.S. to draft laws that prioritize the protection of personal data.
Action: Throw away all your connected devices — and choose your friends wisely Who is this for: Fugitives and whistleblowers How difficult is it: Privacy doesn’t get harder than this Tell me more: Last month the former Catalan president, Carles Puigdemont — who, in October, dodged arrest by the Spanish authorities by fleeing to Brussels after the region’s abortive attempt to declare independence — was arrested by German police, after crossing the border from Denmark in a car. Spanish intelligence agents had reportedly tracked his movements via the GPS on the mobile device of one or more of his friends. The car had also been fitted with a tracker. Trusting anything not to snitch on you is a massive risk if your threat model is this high. The problem is you also need trustworthy friends to help you stay ahead of the surveillance dragnet that’s out to get you.
Action: Ditch the Internet entirely Who is this for: Fugitives and whistleblowers How difficult is it: Privacy doesn’t get harder than this Tell me more: Public administrations can ask you to do pretty much everything online these days — and even if it’s not mandatory to use their Internet service it can be incentivized in various ways. The direction of travel for government services is clearly digital. So eschewing the Internet entirely is getting harder and harder to do. One wild card option — that’s still not a full Internet alternative (yet) — is to use a different type of network that’s being engineered with privacy in mind. The experimental, decentralized MaidSafe network fits that bill. This majorly ambitious project has already clocked up a decade’s worth of R&D on the founders’ mission to rethink digital connectivity without compromising privacy and security by doing away with servers — and decentralizing and encrypting everything. It’s a fascinating project. Just sadly not yet a fully-fledged Internet alternative.
from iraidajzsmmwtv https://ift.tt/2HrWU5w via IFTTT
0 notes
Text
How to save your privacy from the Internet’s clutches
Buy some great High Tech products from WithCharity.org #All Profits go to Charity
Another week, another massive privacy scandal. When it’s not Facebook admitting it allowed data on as many as 87 million users to be sucked out by a developer on its platform who sold it to a political consultancy working for the Trump campaign, or dating app Grindr ‘fessing up to sharing its users’ HIV status with third party A/B testers, some other ugly facet of the tech industry’s love affair with tracking everything its users do slides into view.
Suddenly, Android users discover to their horror that Google’s mobile platform tells the company where they are all the time — thanks to baked-in location tracking bundled with Google services like Maps and Photos. Or Amazon Echo users realize Jeff Bezos’ ecommerce empire has amassed audio recordings of every single interaction they’ve had with their cute little smart speaker.
The problem, as ever with the tech industry’s teeny-weeny greyscaled legalise, is that the people it refers to as “users” aren’t genuinely consenting to having their information sucked into the cloud for goodness knows what. Because they haven’t been given a clear picture of what agreeing to share their data will really mean.
Instead one or two select features, with a mote of user benefit, tend to be presented at the point of sign up — to socially engineer ‘consent’. Then the company can walk away with a defacto license to perpetually harvest that person’s data by claiming that a consent box was once ticked.
A great example of that is Facebook’s Nearby Friends. The feature lets you share your position with your friends so — and here’s that shiny promise — you can more easily hang out with them. But do you know anyone who is actively using this feature? Yet millions of people started sharing their exact location with Facebook for a feature that’s now buried and mostly unused. Meanwhile Facebook is actively using your location to track your offline habits so it can make money targeting you with adverts.
Terms & Conditions are the biggest lie in the tech industry, as we’ve written before. (And more recently: It was not consent, it was concealment.)
Senator Kennedy of Louisiana also made the point succinctly to Facebook founder Mark Zuckerberg this week, telling him to his face: “Your user agreement sucks.” We couldn’t agree more.
Happily disingenuous T&Cs are on borrowed time — at least for European tech users, thanks to a new European Union data protection framework that will come into force next month. The GDPR tightens consent requirements — mandating clear and accurate information be provided to users at the point of sign up. Data collection is also more tightly tied to specific function.
From next month, holding onto personal data without a very good reason to do so will be far more risky — because GDPR is also backed up with a regime of supersized fines that are intended to make privacy rules much harder to ignore.
Of course U.S. tech users can’t bank on benefiting from European privacy regulations. And while there are now growing calls in the country for legislation to protect people’s data — in a bid to steer off the next democracy-denting Cambridge Analytica scandal, at very least — any such process will take a lot of political will.
It certainly will not happen overnight. And you can expect tech giants to fight tooth and nail against laws being drafted and passed — as indeed Facebook, Google and others lobbied fiercely to try to get GDPR watered down.
Facebook has already revealed it will not be universally applying the European regulation — which means people in North America are likely to get a degree of lower privacy than Facebook users everywhere else in the world. Which doesn’t exactly sound fair.
When it comes to privacy, some of you may think you have nothing to hide. But that’s a straw man. It’s especially hard to defend this line of thinking now that big tech companies have attracted so much soft power they can influence elections, inflame conflicts and divide people in general. It’s time to think about the bigger impact of technology on the fabric of society, and not just your personal case.
Shifting the balance
So what can Internet users do right now to stop tech giants, advertisers and unknown entities tracking everything you do online — and trying to join the dots of your digital activity to paint a picture of who they think you are? At least, everything short of moving to Europe, where privacy is a fundamental right.
There are some practical steps you can take to limit day-to-day online privacy risks by reducing third party access to your information and shielding more of your digital activity from prying eyes.
Not all these measures are appropriate for every person. It’s up to you to determine how much effort you want (or need) to put in to shield your privacy.
You may be happy to share a certain amount of personal data in exchange for access to a certain service, for example. But even then it’s unlikely that the full trade-off has been made clear to you. So it’s worth asking yourself if you’re really getting a good deal.
Once people’s eyes are opened to the fine-grained detail and depth of personal information being harvested, even some very seasoned tech users have reacted with shock — saying they had no idea, for example, that Facebook Messenger was continuously uploading their phone book and logging their calls and SMS metadata.
This is one of the reasons why the U.K.’s information commissioner has been calling for increased transparency about how and why data flows. Because for far too long tech savvy entities have been able to apply privacy hostile actions in the dark. And it hasn’t really been possible for the average person to know what’s being done with their information. Or even what data they are giving up when they click ‘I agree’.
Why does an A/B testing firm need to know a person’s HIV status? Why does a social network app need continuous access to your call history? Why should an ad giant be able to continuously pin your movements on a map?
Are you really getting so much value from an app that you’re happy for the company behind it and anyone else they partner with to know everywhere you go, everyone you talk to, the stuff you like and look at — even to have a pretty good idea what you’re thinking?
Every data misuse scandal shines a bit more light on some very murky practices — which will hopefully generate momentum for rule changes to disinfect data handling processes and strengthen individuals’ privacy by spotlighting trade-offs that have zero justification.
With some effort — and good online security practices (which we’re taking as a given for the purposes of this article, but one quick tip: Enable 2FA everywhere you can) — you can also make it harder for the web’s lurking watchers to dine out on your data.
Just don’t expect the lengths you have to go to protect your privacy to feel fair or just — the horrible truth is this fight sucks.
But whatever you do, don’t give up.
How to hide on the internet
Action: Tape over all your webcams Who is this for: Everyone — even Mark Zuckerberg! How difficult is it: Easy peasy lemon squeezy Tell me more: You can get fancy removable stickers for this purpose (noyb has some nice ones). Or you can go DIY and use a bit of masking tape — on your laptop, your smartphone, even your smart TV… If your job requires you to be on camera, such as for some conference calls, and you want to look a bit more pro you can buy a webcam cover. Sadly locking down privacy is rarely this easy.
Action: Install HTTPS Everywhere Who is this for: Everyone — seriously do it How difficult is it: Mild effort Tell me more: Many websites offer encryption. With HTTPS, people running the network between your device and the server hosting the website you’re browsing can’t see your requests and your internet traffic. But some websites still load unencrypted pages by default (HTTP), which also causes a security risk. The EFF has developed a browser extension that makes sure that you access all websites that offer HTTPS using… HTTPS.
Action: Use tracker blockers Who is this for: Everyone — except people who like being ad-stalked online How difficult is it: Mild effort Tell me more: Trackers refers to a whole category of privacy-hostile technologies designed to follow and record what web users are doing as they move from site to site, and even across different devices. Trackers come in a range of forms these days. And there are some pretty sophisticated ways of being tracked (some definitely harder to thwart than others). But to combat trackers being deployed on popular websites — which are probably also making the pages slower to load than they otherwise would be — there’s now a range of decent, user-friendly tracker blockers to choose from. Pro-privacy search engine DuckDuckGo recently added a tracker blocker to their browser extensions, for example. Disconnect.me is also a popular extension to block trackers from third-party websites. Firefox also has a built-in tracker blocker, which is now enabled by default in the mobile apps. If you’re curious and want to see the list of trackers on popular website, you can also install Kimetrak to understand that it’s a widespread issue.
Action: Use an ad blocker Who is this for: Everyone who can support the moral burden How difficult is it: Fairly easy these days but you might be locked out of the content on some news websites as a result Tell me more: If you’ve tried using a tracker blocker, you may have noticed that many ads have been blocked in the process. That’s because most ads load from third-party servers that track you across multiple sites. So if you want to go one step further and block all ads, you should install an ad blocker. Some browsers like Opera come with an ad blocker. Otherwise, we recommend uBlock Origin on macOS, Windows, Linux and Android. 1Blocker is a solid option on iOS. But let’s be honest, TechCrunch makes some money with online ads. If 100% of web users install an ad blocker many websites you know and love would simply go bankrupt. While your individual choice won’t have a material impact on the bottom line, consider whitelisting the sites you like. And if you’re angry at how many trackers your favorite news site is running try emailing them to ask (politely) if they can at least reduce the number of trackers they use.
Action: Make a private search engine your default Who is this for: Most people How difficult is it: A bit of effort because your search results might become slightly less relevant Tell me more: Google probably knows more about you than even Facebook does, thanks to the things you tell it when you type queries into its search engine. Though that’s just the tip of how it tracks you — if you use Android it will keep running tabs on everywhere you go unless you opt out of location services. It also has its tracking infrastructure embedded on three-quarters of the top million websites. So chances are it’s following what you’re browsing online — unless you also take steps to lock down your browsing (see below). But one major way to limit what Google knows about you is to switch to using an alternative search engine when you need to look something up on the Internet. This isn’t as hard as it used to be as there are some pretty decent alternatives now — such as DuckDuckGo which Apple will let you set as the default browser on iOS — or Qwant for French-speaking users. German users can check out Cliqz. You will also need to remember to be careful about any voice assistants you use as they often default to using Google to look stuff up on the web.
Action: Use private browser sessions Who is this for: Most people How difficult is it: Not at all if you understand what a private session is Tell me more: All browsers on desktop and mobile now let you open a private window. While this can be a powerful tool, it is often misunderstood. By default, private sessions don’t make you more invisible — you’ll get tracked from one tab to another. But private sessions let you start with a clean slate. Every time you close your private session, all your cookies are erased. It’s like you disappear from everyone’s radar. You can then reopen another private session and pretend that nobody knows who you are. That’s why using a private session for weeks or months doesn’t do much, but short private sessions can be helpful.
Action: Use multiple browsers and/or browser containers Who is this for: People who don’t want to stop using social media entirely How difficult is it: Some effort to not get in a muddle Tell me more: Using different browsers for different online activities can be a good way of separating portions of your browsing activity. You could, for example, use one browser on your desktop computer for your online banking, say, and a different browser for your social networking or ecommerce activity. Taking this approach further, you could use different mobile devices when you want to access different apps. The point of dividing your browsing across different browsers/devices is to try to make it harder to link all your online activity to you. That said, lots of adtech effort has been put into developing cross-device tracking techniques — so it’s not clear that fragmenting your browsing sessions will successful beat all the trackers. In a similar vein, in 2016 Mozilla added a feature to its Firefox browser that’s intended to help web users segregate online identities within the same browser — called multi container extensions. This approach gives users some control but it does not stop their browser being fingerprinted and all their web activity in it linked and tracked. It may help reduce some cookie-based tracking, though. Last month Mozilla also updated the container feature to add one that specifically isolates a Facebook user’s identity from the rest of the web. This limits how Facebook can track a user’s non-Facebook web browsing — which yes Facebook does do, whatever Zuckerberg tried to claim in Congress — so again it’s a way to reduce what the social network giant knows about you. (Though it should also be noted that clicking on any Facebook social plug-ins you encounter on other websites will still send Facebook your personal data.)
Action: Get acquainted with Tor Who is this for: Activists, people with high risks attached to being tracked online, committed privacy advocates who want to help grow the Tor network How difficult is it: Patience is needed to use Tor. Also some effort to ensure you don’t accidentally do something that compromises your anonymity Tell me more: For the most robust form of anonymous web browsing there’s Tor. Tor’s onion network works by encrypting and routing your Internet traffic randomly through a series of relay servers to make it harder to link a specific device with a specific online destination. This does mean it’s definitely not the fastest form of web browsing around. Some sites can also try to block Tor users so the Internet experience you get when browsing in this way may suffer. But it’s the best chance of truly preserving your online anonymity. You’ll need to download the relevant Tor browser bundle to use it. It’s pretty straightforward to install and get going. But expect very frequent security updates which will also slow you down.
Action: Switch to another DNS Who is this for: People who don’t trust their ISP How difficult is it: Moderately Tell me more: When you type an address in the address bar (such as techcrunch.com), your device asks a Domain Name Server to translate that address into an IP address (a unique combination of numbers and dots). By default, your ISP or your mobile carrier runs a DNS for their users. It means that they can see all your web history. Big telecom companies are going to take advantage of that to ramp up their advertising efforts. By default, your DNS query is also unencrypted and can be intercepted by people running the network. Some governments also ask telecom companies to block some websites on their DNS servers — some countries block Facebook for censorship reasons, others block The Pirate Bay for online piracy reasons. You can configure each of your device to use another public DNS. But don’t use Google’s public DNS! It’s an ad company, so they really want to see your web history. Both Quad9 and Cloudflare’s 1.1.1.1 have strong privacy policies. But Quad9 is a not-for-profit organization, so it’s easier to trust them.
Action: Disable location services Who is this for: Anyone who feels uncomfortable with the idea of being kept under surveillance How difficult is it: A bit of effort finding and changing settings, and a bit of commitment to stay on top of any ‘updates’ to privacy policies which might try to revive location tracking. You also need to be prepared to accept some reduction in the utility and/or convenience of the service because it won’t be able to automatically customize what it shows you based on your location Tell me more: The tech industry is especially keen to keep tabs on where its users are at any given moment. And thanks to the smash hit success of smartphones with embedded sensors it’s never been easier to pervasively track where people are going — and therefore to infer what they’re doing. For ad targeting purposes location data is highly valuable of course. But it’s also hugely intrusive. Did you just visit a certain type of health clinic? Were you carrying your phone loaded with location-sucking apps? Why then it’s trivially easy for the likes of Google and Facebook to connect your identity to that trip — and link all that intel to their ad networks. And if the social network’s platform isn’t adequately “locked down” — as Zuckerberg would put it — your private information might leak and end up elsewhere. It could even get passed around between all sorts of unknown entities — as the up to 87M Facebook profiles in the Cambridge Analytica scandal appear to have been. (Whistleblower Chris Wylie has said that Facebook data-set went “everywhere”.) There are other potential risks too. Insurance premiums being assessed based on covertly collected data inputs. Companies that work for government agencies using social media info to try to remove benefits or even have people deported. Location data can also influence the types of adverts you see or don’t see. And on that front there’s a risk of discrimination if certain types of ads — jobs or housing, for example — don’t get served to you because you happen to be a person of color, say, or a Muslim. Excluding certain protected groups of people from adverts can be illegal — but that hasn’t stopped it happening multiple times on Facebook’s platform. And location can be a key signal that underpins this kind of prejudicial discrimination. Even the prices you are offered online can depend on what is being inferred about you via your movements. The bottom line is that everyone’s personal data is being made to carry a lot of baggage these days — and most of the time it’s almost impossible to figure out exactly what that unasked for baggage might entail when you consent to letting a particular app or service track where you go. Pervasive tracking of location at very least risks putting you at a disadvantage as a consumer. Certainly if you live somewhere without a proper regulatory framework for privacy. It’s also worth bearing in mind how lax tech giants can be where location privacy is concerned — whether it’s Uber’s infamous ‘god view’ tool or Snapchat leaking schoolkids’ location or Strava accidentally revealing the locations of military bases. Their record is pretty terrible. If you really can’t be bothered to go and hunt down and switch off every location setting one fairly crude action you can take is to buy a faraday cage carry case — Silent Pocket makes an extensive line of carry cases with embedded wireless shielding tech, for instance — which you can pop your smartphone into when you’re on the move to isolate it from the network. Of course once you take it out it will instantly reconnect and location data will be passed again so this is not going to do very much on its own. Nixing location tracking in the settings is much more effective.
Action: Approach VPNs with extreme caution Who is this for: All web users — unless free Internet access is not available in your country How difficult is it: No additional effort Tell me more: While there may be times when you feel tempted to sign up and use a VPN service — say, to try to circumvent geoblocks so you can stream video content that’s not otherwise available in your country — if you do this you should assume that the service provider will at very least be recording everything you’re doing online. They may choose to sell that info or even steal your identity. Many of them promise you perfect privacy and great terms of service. But you can never know for sure if they’re actually doing what they say. So the rule of thumb about all VPNs is: Assume zero privacy — and avoid if at all possible. Facebook even has its own VPN — which it’s been aggressively pushing to users of its main app by badging it as a security service, with the friendly-sounding name ‘Protect’. In reality the company wants you to use this so it can track what other apps you’re using — for its own business intelligence purposes. So a more accurate name for this ‘service’ would be: ‘Protect Facebook’s stranglehold on the social web’.
Action: Build your own VPN server Who is this for: Developers How difficult is it: You need to be comfortable with the Terminal Tell me more: The only VPN server you can trust is the one you built yourself! In that case, VPN servers can be a great tool if you’re on a network you don’t trust (a hotel, a conference or an office). We recommend using Algo VPN and a hosting provider you trust.
Action: Take care with third-party keyboard apps Who is this for: All touchscreen device users How difficult is it: No additional effort Tell me more: Keyboard apps are a potential privacy minefield given that, if you allow cloud-enabled features, they can be in a position to suck out all the information you’re typing into your device — from passwords to credit card numbers to the private contents of your messages. That’s not to say that all third-party keyboards are keylogging everything you type. But the risk is there — so you need to be very careful about what you choose to use. Security is also key. Last year, sensitive personal data from 31M+ users of one third-party keyboard, AI.type, leaked online after the company had failed to properly secure its database server, as one illustrative example of the potential risks. Google knows how powerful keyboards can be as a data-sucker — which is why it got into the third-party keyboard game, outing its own Gboard keyboard app first for Apple’s iOS in 2016 and later bringing it to Android. If you use Gboard you should know you are handing the adtech giant another firehose of your private information — though it claims that only search queries and “usage statistics” are sent by Gboard to Google (The privacy policy further specifies: “Anything you type other than your searches, like passwords or chats with friends, isn’t sent. Saved words on your device aren’t sent.”). So if you believe that Gboard is not literally a keylogger. But it is watching what you search for and how you use your phone. Also worth remembering: Data will still be passed by Gboard to Google if you’re using an e2e encrypted messenger like Signal. So third party keyboards can erode the protection afforded by robust e2e encryption — so again: Be very careful what you use.
Action: Use end-to-end encrypted messengers Who is this for: Everyone who can How difficult is it: Mild effort unless all your friends are using other messaging apps Tell me more: Choosing friends based on their choice of messaging app isn’t a great option so real world network effects can often work against privacy. Indeed, Facebook uses the fuzzy feelings you have about your friends to manipulate Messenger users to consent to continuously uploading their phone contacts, by suggesting you have to if you want to talk to your contacts. (Which is, by the by, entirely bogus.) But if all your friends use a messaging app that does not have end-to-end encryption chances are you’ll feel forced to use that same non-privacy-safe app too. Given that the other option is to exclude yourself from the digital chatter of your friend group. Which would clearly suck. Facebook-owned WhatsApp does at least have end-to-end encryption — and is widely used (certainly internationally). Though you still need to be careful to opt out of any privacy-eroding terms the company tries to push. In summer 2016, for example, a major T&Cs change sought to link WhatsApp users’ accounts with their Facebook profiles (and thus with all the data Facebook holds on them) — as well as sharing sensitive stuff like your last seen status, your address book, your BFFs in Whatsapp and all sorts of metadata with Zuck’s ‘family’ of companies. Thankfully most of this privacy-hostile data sharing has been suspended in Europe, after Facebook got in trouble with local data protection agencies.
Action: Use end-to-end encryption if you use cloud storage Who is this for: Dedicated privacy practitioners, anyone worried about third parties accessing their stuff How difficult is it: Some effort, especially if you have lots of content stored in another service that you need to migrate Tell me more: Dropbox IPO’d last month — and the markets signalled their approval of its business. But someone who doesn’t approve of the cloud storage giant is Edward Snowden — who in 2014 advised: “Get rid of Dropbox”, arguing the company is hostile to privacy. The problem is that Dropbox does not offer zero access encryption — because it retains encryption keys, meaning it can technically decrypt and read the data you store with it if it decides it needs to or is served with a warrant. Cloud storage alternatives that do offer local encryption with no access to the encryption keys are available, such as Spideroak. And if you’re looking for a cloud backup service, Backblaze also offers the option to let you manage the encryption key. Another workaround if you do still want to use a service like Dropbox is to locally encrypt the stuff you want to store before you upload it — using another third party service such as Boxcryptor.
Action: Use an end-to-end encrypted email service Who is this for: Anyone who wants to be sure their email isn’t being data mined How difficult is it: Some effort — largely around migrating data and/or contacts from another email service Tell me more: In the middle of last year Google finally announced it would no longer be data-mining the emails inside its Gmail free email service. (For a little perspective on how long it took to give up data-mining your emails, Gmail launched all the way back in 2004.) The company probably feels it has more than enough alternative data points feeding its user profiling at this point. Plus data-mining email with the rise of end-to-end encrypted messaging apps risks pushing the company over the ‘creepy line’ it’s been so keen to avoid to try to stave off the kind of privacy backlash currently engulfing Facebook. So does it mean that Gmail is now 100% privacy safe? No, because the service is not end-to-end encrypted. But there are now some great webmail clients that do offer robust end-to-end encryption — most notably the Swiss service Protonmail. Really it’s never been easier to access a reliable, user-friendly, pro-privacy email service. If you want to go one step further, you should set up PGP encryption keys and share them with your contacts. This is a lot more difficult though.
Action: Choose iOS over Android Who is this for: Mainstream consumers, Apple fans How difficult is it: Depends on the person. Apple hardware is generally more expensive so there’s a cost premium Tell me more: No connected technology is 100% privacy safe but Apple’s hardware-focused business model means the company’s devices are not engineered to try to harvest user data by default. Apple does also invest in developing pro-privacy technologies. Whereas there’s no getting around the fact Android-maker Google is an adtech giant whose revenues depend on profiling users in order to target web users with adverts. Basically the company needs to suck your data to make a fat profit. That’s why Google asks you to share all your web and app activity and location history if you want to use Google Assistant, for instance. Android is a more open platform than iOS, though, and it’s possible to configure it in many different ways — some of which can be more locked down as regards privacy than others (the Android Open Source Project can be customized and used without Google services as default preloads, for example). But doing that kind of configuration is not going to be within reach of the average person. So iOS is the obvious choice for mainstream consumers.
Action: Delete your social media accounts Who is this for: Committed privacy lovers, anyone bored with public sharing How difficult is it: Some effort — mostly feeling like you’re going to miss out. But third party services can sometimes require a Facebook login (a workaround for that would be to create a dummy Facebook account purely for login purposes — using a name and email you don’t use for anything else, and not linking it to your usual mobile phone number or adding anyone you actually know IRL) Tell me more: Deleting Facebook clearly isn’t for everyone. But ask yourself how much you use it these days anyway? You might find yourself realizing it’s not really that central to what you do on the Internet after all. The center of gravity in social networking has shifted away from mass public sharing into more tightly curated friend groups anyway, thanks to the popularity of messaging apps. But of course Facebook owns Messenger, Instagram and WhatsApp too. So ducking out of its surveillance dragnet entirely is especially hard. Ideally you would also need to run tracker blockers (see above) as the company tracks non-Facebook users around the Internet via the pixels it has embedded on lots of popular websites. While getting rid of your social media accounts is not a privacy panacea, removing yourself from mainstream social network platforms at least reduces the risk of a chunk of your personal info being scraped and used without your say so. Though it’s still not absolutely guaranteed that when you delete an account the company in question will faithfully remove all your information from their servers — or indeed from the servers of any third party they shared your data with. If you really can’t bring yourself to ditch Facebook (et al) entirely, at least dive into the settings and make sure you lock down as much access to your data as you can — including checking which apps have been connected to your account and removing any that aren’t relevant or useful to you anymore.
Action: Say no to always-on voice assistants Who is this for: Anyone who values privacy more than gimmickry How difficult is it: No real effort Tell me more: There’s a rash of smart speaker voice assistants on shop shelves these days, marketed in a way that suggests they’re a whole lot smarter and more useful than they actually are. In reality they’re most likely to be used for playing music (albeit, audio quality can be very poor) or as very expensive egg timers. Something else the PR for gadgets like Amazon’s (many) Echos or Google Home doesn’t mention is the massive privacy trade off involved with installing an always-on listening device inside your home. Essentially these devices function by streaming whatever you ask to the cloud and will typically store recordings of things you’ve said in perpetuity on the companies’ servers. Some do offer a delete option for stored audio but you would have to stay on top of deleting your data as long as you keep using the device. So it’s a tediously Sisyphean task. Smart speakers have also been caught listening to and recording things their owner didn’t actually want them to — because they got triggered by accident. Or when someone on the TV used the trigger word. The privacy risks around smart speakers are clearly very large indeed. Not least because this type of personal data is of obvious and inevitable interest to law enforcement agencies. So ask yourself whether that fake fart dispenser gizmo you’re giggling about is really worth the trade off of inviting all sorts of outsiders to snoop on the goings on inside your home.
Action: Block some network requests Who is this for: Paranoid people How difficult is it: Need to be tech savvy Tell me more: On macOS, you can install something called Little Snitch to get an alert every time an app tries to talk with a server. You can approve or reject each request and create rules. If you don’t want Microsoft Word to talk with Microsoft’s servers all the time for instance, it’s a good solution — but is not really user friendly.
Action: Use a privacy-focused operating system Who is this for: Edward Snowden How difficult is it: Need to be tech savvy Tell me more: If you really want to lock everything down, you should consider using Tails as your desktop operating system. It’s a Linux distribution that leaves no trace by default, uses the Tor network for all network requests by default. But it’s not exactly user friendly, and it’s quite complicated to install on a USB drive. One for those whose threat model really is ‘bleeding edge’.
Action: Write to your political reps to demand stronger privacy laws Who is this for: Anyone who cares about privacy, and especially Internet users in North America right now How difficult is it: A bit of effort Tell me more: There appears to be bipartisan appetite among U.S. lawmakers to bring in some form of regulation for Internet companies. And with new tougher rules coming in in Europe next month it’s an especially opportune moment to push for change in the U.S. where web users are facing reduced standards vs international users after May 25. So it’s a great time to write to your reps reminding them you’re far more interested in your privacy being protected than Facebook winning some kind of surveillance arms race with the Chinese. Tell them it’s past time for the U.S. to draft laws that prioritize the protection of personal data.
Action: Throw away all your connected devices — and choose your friends wisely Who is this for: Fugitives and whistleblowers How difficult is it: Privacy doesn’t get harder than this Tell me more: Last month the former Catalan president, Carles Puigdemont — who, in October, dodged arrest by the Spanish authorities by fleeing to Brussels after the region’s abortive attempt to declare independence — was arrested by German police, after crossing the border from Denmark in a car. Spanish intelligence agents had reportedly tracked his movements via the GPS on the mobile device of one or more of his friends. The car had also been fitted with a tracker. Trusting anything not to snitch on you is a massive risk if your threat model is this high. The problem is you also need trustworthy friends to help you stay ahead of the surveillance dragnet that’s out to get you.
Action: Ditch the Internet entirely Who is this for: Fugitives and whistleblowers How difficult is it: Privacy doesn’t get harder than this Tell me more: Public administrations can ask you to do pretty much everything online these days — and even if it’s not mandatory to use their Internet service it can be incentivized in various ways. The direction of travel for government services is clearly digital. So eschewing the Internet entirely is getting harder and harder to do. One wild card option — that’s still not a full Internet alternative (yet) — is to use a different type of network that’s being engineered with privacy in mind. The experimental, decentralized MaidSafe network fits that bill. This majorly ambitious project has already clocked up a decade’s worth of R&D on the founders’ mission to rethink digital connectivity without compromising privacy and security by doing away with servers — and decentralizing and encrypting everything. It’s a fascinating project. Just sadly not yet a fully-fledged Internet alternative.
[Read More …]
How to save your privacy from the Internet’s clutches
0 notes
Text
Should Teachers Take Cash from Edtech Companies?
When she was in the classroom, Jenny Herrera remembers feeling resentful whenever the school principal would email teachers telling them they needed to stay after school to give feedback to edtech companies. What they got in return? Muffins.
“I don’t think that is ethical,” Herrera, now the Senior Director of Strategy and Operations at ProjectEd, told the audience at a recent panel session at the SXSW EDU conference in Austin. “You’re not going to say ‘no’ to your boss. Teachers are naturally people pleasing, and you care, but it does not seem fair when we all know that teachers’ time is so precious, to voluntold them for things.”
The ethics of teachers advising and working with edtech companies received a lot of attention when the New York Times published a piece on the subject last fall. Unsurprisingly, the panelists brought up the article—and their thoughts on the controversy.
Pilot Programs
Nadia Williams, a digital coach for Georgia’s Cobb County School District, said that when it comes to pilot programs, the ethics depend on who is initiating the product testing. In general, top-down mandates to test products are taxing on teachers’ time and provide few rewards, making them somewhat burdenous.
She mentioned a school district in Maryland, where a friend of hers works. When that district was evaluating learning management systems, it contracted with the companies it had “whittled it down to” and had pilot schools go through the long process of testing different platforms.
There have been several pilot programs with technologies for use throughout her own school district, Williams said. But, it’s a “pretty big district,” and implementing a tool system-wide requires making sure it works. The better option is to give teachers more control over which products they try out in the classroom.
“I think it’s great when teachers are driving that conversation and district personnel are helping drive that conversation as well,” Williams said. “However, we do get into some gray area when you have an admin putting teachers on the spot like that.”
Asking teachers for their input at the pilot stage is helpful, Herrera said, but the process should really start earlier. As someone who advises edtech companies, she thinks by the time a company gets to the pilot stage, they’ve spent a lot of time and money developing a product that schools “might not want.”
“It’s just not a good use of your resources,” Herrera said, adding that involving teachers from the start can actually save companies money in the long run as they figure out the problems their tool does (and does not) solve for schools. “So from a company side, pilots can work, but I think it needs to happen much earlier.”
Overall, the consensus from panelists and the audience, when polled by show of hands, was that vendor-educator relationships are above-board, given appropriate transparency measures. “We are all pretty much in agreement that teachers, when they’re being used for their time, deserve to be paid,” Williams said.
Are Teachers Too Tech Isolated from What’s Happening in Tech?
Mark Phillips is the founder of HireEducation, an edtech recruiting firm, and GigEd, a platform where teachers can find short-term “gigs” at edtech companies, and get paid by those companies. He said he’s “all in favor” of exchanging money between teachers and companies in order to avoid companies developing products in a vacuum and selling them to administrators, forcing classroom teachers to use a product that has “no relevance” to them.
But he believes transactions between edtech companies and teachers need to be both transparent and regulated.
Phillips, however, doesn’t think the question of ethics pertains only to getting teacher input on a product. He referenced the New York Times article, which discussed teachers working as company ambassadors, a relationship he described as “effectively selling” the company to other teachers, district staff and sometimes to parents and students—a relationship he thought could be mutually beneficial to classrooms and vendors, but must be mandatory for teachers to disclose, he later clarified to EdSurge. He added that, even then, abuses could happen.
Phillips also told the audience that some teachers—even talented ones—are “pretty isolated” in regard to what’s happening with technology. He said there are tools that his wife, who is a teacher, has never encountered because “she’s in the classroom not using tools all the time.”
“So I believe there is also a little bit of that Steve Jobs thing going on, where people need to be told what they need,” Phillips said. “I think there has to be a balance.”
Williams, however, said Phillips’s statement suggests that educators aren’t as savvy as they can be. She said it’s “apt of any profession” to get in their own lane, but that there are teachers like herself who go out and find tools and resources for their classroom. But while she agreed that there are many teachers who don’t do that, she pointed out that they weren’t going to be “in this room” or seeking opportunities like ambassador programs.
Teachers Versus Sports Figures
An audience member submitted a question asking why teacher’s ethics would be different from anyone else’s ethics, such as sports figures and movie stars.
Williams said she sees some huge differences there, although she doesn’t agree that they should exist. Celebrities have managers, and operate “as a business of one in many entities.” The government doesn’t regulate what LeBron James can say regarding his shoes, and the ethics of him signing a sneaker deal aren’t “called into question.”
However, she continued, educators face ethical questions based on what might be in their contracts, districts and certification status.
Herrera said she thinks teachers at private and charter schools have more “leeway to do things” around piloting products and connecting with companies, adding that there are “amazing examples just from lack of red tape.”
Phillips, however, said even in cases with private schools and charters, there’s still the question of influence, and educators are adults with responsibility over kids. But again, he’s not against vendor-educator relationships so long as they’re regulated.
“I would argue that there is a market force, and there always should be a place for that, it just needs to be really transparent,” Phillips said.
Williams brought up perception issues that come along with managing government funds.
“Sometimes perception becomes a new reality, and it’s not actually what went down.”
The Future
The moderator, Michael Kleba, an English and theater teacher currently on sabbatical to run DegreeCast, a college search engine tool, asked the panelists for their “most daring prediction” for what teacher-industry partnerships could accomplish in the next five years.
While his financial future depends on his wife’s teacher pension, Phillips said it also restricts where they can live, where she can work and her ability to choose to leave the classroom for a couple of years to work on a book and then return.
Herrera cited her friend, who won teacher of the year in North Carolina, as an example of systems and protocols already in place for educators. Her friend was “on loan” to the state’s Department of Public Instruction for a year. Herrera thinks something similar should be in place for teachers who are passionate about digital or non-digital products and want to take a year of sabbatical to help train other educators, research or work for an edtech company, she later clarified to EdSurge.
She also wants to see a level system for teachers, like some other professions have. “You don’t go in our first day as the chief surgeon, except in teaching you do.” Having levels would improve the profession, and additionally, as teachers climb up in rank, they can get flexibility in their schedule, such as having two periods free that they can use to help make a product better.
Williams, on the other hand, wants to see “more teacherpreneurship,” meaning educators shouldn’t just be consulting companies about products; they should be creating those products, whether they’re “offline” or “online.”
“I want to see more teachers out there feeling comfortable with representing themselves as industry leaders,” Williams said. “Because we are subject area experts, and we should be the ones who are starting a conversation, not adding to it— and making a lot of money off of it too.”
Should Teachers Take Cash from Edtech Companies? published first on https://medium.com/@GetNewDLBusiness
0 notes
Text
Your Quick Start Guide to Cross-Border Ecommerce in China, India & The Middle East
Centuries before GPS and various forms of travel technology, navigators relied on stars to point them in the right direction –– using them as a guidance tool while embarking into territories and corners of the globe not yet reached.
While we have come light years from relying on stars for determining direction, we still rely heavily on tools and technology to guide us.
As merchants venture off into new markets, the very first step is almost always around discover:
Where do we go?
How do we get there?
What to do when I get there?
Wouldn’t it be easy if there was already a “Quick Start Guide” doing business globally?
That’s what we have set out to do.
Below you will find a country-by-country, quick start guide to entering each respective market.
From marketplaces to social commerce platforms, everything that you need to know as a merchant is right here, right now.
The International Expansion Playbook
What if you are ready to invest in international expansion and localization to own a brand new market long before you competitors?
That’s what this guide will teach you to do.
Get it now.
How to Sell Online in China
Online retail sales in China reached 5.16 trillion yuan ($752 billion) in 2016, representing 26.2% growth from 2015—more than double the growth rate of overall retail sales, according to China’s National Bureau of Statistics, the agency charged with tracking economic data.
Want a slice of that pie? Of course you do. Here’s how.
TMall
Selling in China to-date for most U.S. and Western European merchants has been via TMall.
Unlike most marketplaces, TMall offers what is known as a Storefront marketplace, where merchants can have a fully branded flagship store within their marketplace.
However, to do so, you will have to successfully prove that you have an in-country agent or business.
This requires the following documentation:
Copy of a business license from mainland China
Copy of corporate tax registration certificate from mainland China
Copy of organization code certificate
Copy of bank account permits
Copy of legal representative ID card
Copy of TMall flagship store owner’s ID card
Trademark registration from the state trademark association
Alipay corporate account authorization
Completed product list
Providing this documentation may be difficult if you do not have an in-country partner or if you are simply just getting started with selling globally.
Of course, there is a second option…
TMall Global
The big advantage of TMall Global is that organizations do not have to have a legal entity in China, in contrast to other ecommerce platforms (including the standard TMall).
In addition to shipping orders from the country of origin, the brands can also ship from storage facilities in free trade areas in Shanghai, Ningbo, Hangzhou, Zhengzhou and Guangzhou.
This reduces delivery times and the logistics costs per shipment –– and is more relatable to many brands, since this model is similar to Amazon’s FBA.
Plus, the applicable tax rate for purchases from these zones is 10% instead of the regular import tariffs of approximately 30-40%.
The types of stores you can open on TMall
Lastly, in China, specifically on TMall, it is important to understand the differences in the types of stores that you can open.
Currently, there are three types of stores that merchants can apply for:
Flagship Store
Authorize Store
Specialty Store
Flagship Store
Flagship stores can only be opened if the merchant is the brand owner (trademark owner) or possesses authorization from the brand owners of the products.
Flagship stores can be authorized and launched under the following circumstances:
Store sells and acts on the behalf of a single brand that is owned by the merchant opening the store
Store sells and acts on the behalf of multiple brands that are all owned by the merchant opening the store
Store sells and acts on the behalf of a multi-brand marketplace (service class trademark) owned by the merchant opening the store
Nike on TMall example
Authorized Store
Authorized stores are stores run by merchants which hold a license from a brand to do business on their behalf in a specific region, in this case, China.
Authorized Stores can be opened under the following circumstances:
Store is authorized to sell products from one brand
Store is authorized to sell products from multiple brands, but all brands belong to the same entity
To give a quick example (though not on TMall), Power Support is a U.S. store selling goods from Japan. The owner of the store is authorized by the brand owners, and is the only branded seller in the U.S. He reports his numbers back to the original owners, but has leeway to grow the business as he sees fit.
That would classify as an authorized store on TMall.
Specialty Store
Specialty stores are for merchants that sell products in multiple categories; however, are not the brand owner. Specialty stores can be opened under the following circumstances:
Store sells products from two or more brands that the merchant does not own
Store sells products from a brand (trademark) owned by the merchant and sells products from a brand not owned by the merchant
Store sells products from two or more brands that the merchant owns
A good example of a specialty online store –– again using a U.S. merchant to give you an example –– is Spearmint LOVE. Spearmint sells a few of their own unique products, as well as aggregates goods from across their niche to sell on their site.
Find the Fit for You
Your biggest takeaway here is that you have options on TMall.
Regardless, however, of whether you are on mainland China or looking to stay abroad as you expand, your storefront must be available in Chinese, as Chinese buyers must have access to Chinese customer service and the product must be returnable to an address in China.
Additionally, merchants must provide certificates of authenticity of the brand to prevent the sales of shanzhai (fake) products.
WeChat
While marketplaces have dominated in China to-date, the rise of mobile commerce has accelerated with the adoption and penetration of social commerce platforms like WeChat.
WeChat gives shoppers and users a quick, easy in-app checkout via WeChat Pay. Like TMall, brands can create Official Accounts that enable them to have Flagship stores built within WeChat.
Also like TMall, to register an official account on WeChat, merchants will need the following documentation:
Chinese ID
Chinese mobile phone number
Chinese business license
Chinese organization code
Tencent, the managing group of WeChat, does not allow non-Chinese merchants to apply for official accounts for free.
Instead, the application costs for non-Chinese merchants looking to start an official store on WeChat are $1,300 (USD) and can take up to 4 months to process.
Understanding Store Types; Service versus Subscription
When registering a WeChat Official Store, merchants will be given the choice of creating a Subscription, Service, and/or Enterprise account. The two that we will focus on for initially penetrating China via WeChat will be:
Service Accounts
Subscription Accounts
Depending on what the goals of your brand are, awareness versus sell-through, both of these models provides benefits that can fit your needs.
Service Accounts
Arguably the best account for ecommerce lead initiatives, service accounts allow merchants to accept in-app purchases via WeChat Pay and other forms of preferred payment. This removes barriers to entry when considering payment types in China.
Additionally, Service Accounts have the following functionality that Subscription Accounts do not:
Connected Objects – iBeacons deliver content via WeChat native functionalities
Ecommerce – WeChat Pay allows your shoppers to purchase in-app
Geo-Location – Enables you to send push notifications based on location, great for larger merchants that practice O2O (offline-to-online)
QR Codes – Generate easy to use QR codes that can better connect digital and physical
Subscription Accounts
The biggest benefit of a Subscription Account is the associated publisher tools. Unlike Service Accounts, Subscription Accounts can publish 1 message per day; whereas Services Account are only given 4 per month.
However, the downside of Subscription Accounts is that you cannot leverage ecommerce functionality.
Key Notes
It is important to remember that not all WeChat accounts and users are the same. For example:
Non-Chinese WeChat users have access to Both Chinese and Non-Chinese official accounts.
Chinese WeChat users only have access Chinese registered accounts.
Both should be taken into consideration when determining whether to leverage an in-country partner to verify a Chinese business standing or do it as a recognized cross-border merchant operating outside Mainland China.
Cross-Border Ecommerce in India
According to a ASSOCHAM-Forrester study, India’s ecommerce revenue is expected to jump from $26 billion in 2016 to $103 billion in 2020.
While in terms of the base, India may be lower than China and other giants like Japan, the Indian rate of growth is way ahead of others.
Against India’s annual growth rate of 51%, China’s ecommerce market is growing at 18%, Japan at 11% and South Korea at 10%.
Here’s how to get on that market right now.
Flipkart
While Amazon begins to tap into India, Flipkart remains the market leader in terms of marketplace opportunity for selling across borders.
Currently, Flipkart has more than 7.5M core registered customers and ships more than 800,000 packages, per month, to more than 1,000 cities.
Like marketplaces and social commerce platforms in China, Flipkart mandates that you show proof of having a business established in country.
Again, this not a complete roadblock; however, it does require an in-country partner that can provide residency and show documentation.
When signing up for Flipkart Seller Portal access, you will need to provide the following documentation:
PAN Card (Personal PAN for business type “Proprietorship” and Personal + Business PAN for business type as “Company”)
VAT/TIN Number (not mandatory for books)
Bank account and supporting KYC documents (Address Proof, and Cancelled check)
Minimum of 10 unique products to sell
The Benefits of Selling through Flipkart
If merchants decide to sell on Flipkart, there are a tremendous amount of benefits that alleviate and better mitigate risk when selling in India.
Shipping: Flipkart handles the shipping of your products. All merchants need to do is pack the product and keep it ready for dispatch. Flipkart’s logistics partners will pick up the product from you and deliver it to the customer.
Seller Protection: Flipkart has set up a Seller Protection Fund (SPF) to protect merchants against fraud. Merchants can request for SPF claim through the seller dashboard. When the buyer or logistics partner is at fault, you will receive due compensation.
Easy Payouts: All merchant payments are made through NEFT transactions (online banking). The payment is made directly to the merchant’s bank account within 7-15 business days from the date of order dispatch. It’s 7 business days for Gold Sellers, 12 business days for Silver Sellers and 15 business days for Bronze sellers.
Snapdeal
While Flipkart has become the more notable Indian marketplace, Snapdeal is India’s second leading marketplace and has quite the market share.
Today, Snapdeal has around 300,000 sellers and delivers in more than 6,000 cities and towns in India.
In March 2016, its gross merchandise value stood at around $4 billion.
Like Flipkart, Snapdeal mandates that merchants wanting so to sell into India via their marketplace have an in-country business entity.
For merchants wanting to sign-up, they will need the following to access their Seller Portal:
PAN Card
VAT/CST number
Bank Account number
The Benefits of Selling on Snapdeal
Customer Shopping Experience: Unlike Flipkart and Amazon, Snapdeal goes above and beyond in creating a very easy to shop user interface and experience online. From category landing pages to their product detail pages, the marketplace does a great job of communicating to consumers their merchant’s product value in a more B2C way than normal marketplaces.
Cross Border Merchant Friendly: Unlike Flipkart, Snapdeal allows cross border merchants to ship from their domestic distribution centers, not requiring them to make the in-country inventory investment. This is a favorable advantage when penetrating the market by keeping initial investments to a minimum.
4 Steps to Conquer Ecommerce Penetration in India
While Indian marketplaces require merchants to have an in-country partner to act as the merchant of record, what happens once merchants have successfully “landed” in-country?
For many, the road and path of least resistance is still unknown, as India still represents a market with few to no foreign experts for merchants to lean on.
That’s why we reached out to Tony Navin, SVP, Partnerships and Strategic Initiatives at Snapdeal.
He grew Snapdeal’s electronics and general merchandise units up to $2 billion since 2012, constituting 80% of the marketplace’s business.
And he did all of this while spearheading the marketplace’s monetization revenue stream and building out its advertising platform.
A former start-up entrepreneur himself, Navin fully understands the Indian market, top to bottom.
Here are the 4 steps Navin recommends for those that have started or are evaluating launching an Indian ecommerce channel:
Create brand recall with in in-country awareness and SEM
Build strong relationships with marketplace stakeholders
Save on supply chain by leading with online
Follow the right trends
Building in-country awareness
Just like doing business domestically, merchants have to build awareness for both their brand and products. Cross border commerce is no different.
In India, shoppers follow the same discovery behaviors as those in the U.S., AU or Canada, using search across multiple online channels. To be successful, merchants have to look at SEM as a necessary investment when entering the Indian market.
“Merchants have to consistently evaluate the way they engage in marketplaces,” says Navin. “Brands need to create recall, so when shoppers search for specific goods, your products are at the top of search results and category landing pages.”
Advertising on Snapdeal
Currently, Snapdeal allows its merchants to leverage it’s robust advertising platform in two forms:
Brand Ads
Product Ads
Depending on the goal of your campaigns, the marketplace’s advertising features allow you to connect and build relationships with consumers authentically, yet strategically.
Below are areas within the marketplace that merchants are allowed to buy ad space:
Homepage
Product List Page
Category Pages
Search List Page
Product Details Page
Order Confirmation Page
Marketplace representatives are just as important as consumers
While building confidence and trust with local customers is objective #1, do not forget that marketplace associates and representatives are just as important.
The reality of India is that 1000s of merchants are selling online –– what makes your product different? What makes you standout? How can these associates help to increase your visibility?
These associates are like influencers in the U.S. market. Build your relationships with them early on. They need to be aware of your presence, so be proactive!
Navin says continuous engagement is necessary when building relationships with marketplace associates. “Do it daily and consistently,” he says.
Use online to generate buzz and cut costs
In 2000, cellular giant Motorola exited the Indian market amid continued decline of market share and sales. However, in 2012, the brand returned with force, recapturing both market share and sales in a digitally driven re-launch.
What was the key to their success?
Navin calls it, “investing smart.” Simply put, merchants that want to enter or re-enter the Indian market need to make investments.
But where do you invest first?
Navin suggest a hybrid model, taking an online first approach to generate buzz, but also cut supply chain costs by selling digital, rather than physical to start.
Moreover, while many marketplaces require cross border merchants to have in-country stock, Snapdeal is seller friendly, allowing merchants to ship from their domestic distribution center, enabling them to successfully penetrate the market with minimal inventory/shipping investments.
Don’t fit a square peg into a round hole
When determining whether or not India is a viable market to penetrate, consider current consumer demand within your vertical.
Currently, India’s top categories are:
Electronics
Appliances
Entertainment Devices
Smart Phones
Apparel & Footwear
When it is all said and done, India represents massive opportunity for the right merchants. For merchants that fit the mold, finding a local partner is probably the best course of action.
Lastly, as you merchandise your catalog for in-market distribution, be considerate of “hygiene factors,” says Navin while describing India’s socioeconomic factors, adding, “India is religiously sensitive, so be mindful of how your products impact local culture.”
How to Sell in the Middle East
The Middle East is on the verge of a massive digital disruption with significant untapped ecommerce potential, according to a 2016 Digital Middle East report by McKinsey & Company.
The key driver of this is the Muslim market, which is expected to grow to $484 billion by 2019, according to the 2014-15 Thomson Reuters State of the Global Islamic Economy Report.
For western merchants, the growing category in-market remains luxury and premium priced apparel, beauty and footwear.
If you sell in one of those categories, here’s how to get launched in the Middle East.
Namshi
Namshi is part of the Global Fashion Ecommerce Group created by Rocket Internet. It is a Dubai-based online fashion retailer with more than 40,000 exclusive in-house collections and brands such as Adidas, Nike, Diesel, Topshop, Lacoste and Vans.
It has seen significant growth over the past two years.
The platform is experiencing massive market adoption and penetration for both cross border commerce and mobile commerce.
Over 80% of Namshi shoppers use mobile or tablet devices to access Namshi. Mobile traffic currently tops 175 million pageviews monthly, with 18 million pageviews on desktop.
Selling on Namshi is by application only.
The Modist
The newest challenger is the Middle Eastern market just went live in 2017. It has an aesthetically pleasing shopping experience and is cutting into the growing fashion market.
The Modist, a Dubai-based ecommerce site, offers 75 contemporary designer brands to women whose religious, cultural or personal tastes lean toward a modest style aesthetic.
It is a great way of merchandising in-country that simultaneously caters to cultural and socio economic expectations and norms.
Amazon’s Influence in the Middle Eastern Market
Making headlines in 2017 was Amazon’s acquisition of regional leader Souq.com.
Souq, the largest ecommerce company in the Middle East, was founded in 2005 on an eBay-like online auction model, but it subsequently evolved into more of an Amazon-style set-price retailer.
Souq.com currently has more than 8.4 million products for sale and has over 45 million visits per month.
Selling on Souq
Like Asia Pacific marketplaces, Souq.com requires that you have an in-country partner to show support documents that allow you to sell in each specific country.
Those requirements include:
Local Shipping location: Souq will use the details of this location to pick up your orders and deliver them to the customers. Please note that you will be required to verify the mobile phone number used to contact this location.
Trade license and ID: When selling specific categories, Souq requires the trade license and ID verification for legal purposes, this will insure that you’re allowed to sell them in a specific country.
Final Word
For brands selling in the luxury market, the Middle East has multiple options for you to expand your business.
For those looking to sell in India, electronics and apparel & footwear do best. In China, just about anything goes, though having an in-country presence is ideal.
Over all, which region you choose to launch into is based on your brand, what you sell and where you can afford to get feet on the ground to understand the market and test the water.
The International Expansion Playbook
What if you are ready to invest in international expansion and localization to own a brand new market long before you competitors?
That’s what this guide will teach you to do.
Get it now.
Want more insights like this?
We’re on a mission to provide businesses like yours marketing and sales tips, tricks and industry leading knowledge to build the next house-hold name brand. Don’t miss a post. Sign up for our weekly newsletter.
Email*
jQuery(document).bind('gform_post_render', function(event, formId, currentPage){if(formId == 1) {if(typeof Placeholders != 'undefined'){ Placeholders.enable(); }} } );jQuery(document).bind('gform_post_conditional_logic', function(event, formId, fields, isInit){} ); jQuery(document).ready(function(){jQuery(document).trigger('gform_post_render', [1, 1]) } );
Your Quick Start Guide to Cross-Border Ecommerce in China, India & The Middle East published first on http://ift.tt/2wGG0YJ
0 notes
Text
Rumored Buzz on Nigerian Newspapers Read Them Online Exposed
I enjoy the idea of Earning money Online - it is darn as well simple (if I push the appropriate switches) and also I can also be called an Entrepreneur.
Starting a real world organisation can verify to be a tough nut to crack if you do not have the ideal connections. You will certainly have to obtain your company registered, you will require a legal representative to assist you compose a few lawful files, you will need to establish a real-time workplace with rental fees indicated to be paid, you will certainly additionally need to bring individuals to your office or go out to meet them in order to make a sale ... Without some form of help whatsoever, these as well as even more are just what you are expected to encounter. I ask yourself if there is a better place to earn money than the web.
If you are reading this article and you have not yet began an on the internet company, I will certainly state you are missing out on some excellent chances. And also starting an on the internet service is very simple, all you require upfront are these 4 fundamental points:
A domain
This is more like any real life address when their features are contrasted. While an offline address informs you where you can locate a certain residence, a domain or internet address points you to a site. Domain are actually low-cost to get as they can be purchased in the region of $10. Domain registrars like GoDaddy and also NameCheap are preferred and this is for a reason ...
A hosting service
Next you will need a hosting solution on which your site will certainly be hosted. I prefer to check out web hosting as a parcel on which you develop your house( your site in this situation).
Your hosting makes it possible for others to locate you online. And however many people provide cost-free hosting service, you just get as a lot from them. You must not complain when your site experiences a great deal of downtime and when you obtain some poor customer support. Reputable webhosts go with less than $10 a month, a standard host like Hostgator or Bluehost chooses a rate approximately $5. I can not state all of it but check them out and see exactly what I imply. You could just venture out exactly what you place in.
A Premium WordPress Style
Obtaining an excellent theme has a massive bearing on what does it cost? your site makes. Try creating a great article and after that toss it up a website with terrible looking design, design and navigating and also see just what happens.
A good internet format improves the user experience on your website; a great layout sometimes makes good content much better. But notice I stated good content, if you write old garbage and publish them on a site with the most effective style on the planet you will see NO outcomes. People want excellent material very first others follow. And the last thing you require ...
An Order Handling System
You need to establish an order handling system where you can accept bank card repayment online. If you wear not give individuals an alternative to pay and if you do not make it simple for them to earn the repayment, they will wind up buying in other places - Your competition. If your visitors do deny from you, your website will not generate income and it will at some point run aground. Even if your site is for non profit functions, you still need to offer people a choice of making donations, also Wikipedia does this.
So going into the almost all of this post, below are the 7 advantages you can stem from doing business online over doing it offline, in the real world ...
1. Global Market
Anybody can be your consumer on the web. As a Nigerian, I can have someone from Vietnam buying from me while my next door neighbor also purchases from me. The listing of prospective customers is limitless. Facebook has more than 250 million daily brows through and a site like Google likewise tape-records daily check outs in the regions of 620 million. Now think of that your website has state a percent of Google's daily page views. That is 6 million people visiting your site day-to-day. Or let's say 0.01 percent - that is still 62,000 everyday visits to your site. You could use these individuals a totally free product and make them opt-in to your autoresponder or sign up for your e-newsletter. By so doing you earn money. A few other may even be one-time site visitors who will certainly be thrilled enough by what you do (if undoubtedly you are doing something outstanding) as well as acquire the items you advise.
2. Flexibility
By doing business on the internet, you are not limited by your location. Exactly what I suggest is your organisation can choose you any place you go. As well as given that you are not mandated to generate a real world address in order to sign up a blog, you can do without it. The point I am aiming to make here is that with just a laptop and also web link, you can run your online organisation successfully. You can fly out on main obligation, your organisation flies with you; when you take place a Safari with the family members you can still run your business. You can operate your net service from anywhere - the table, room, and also from Hong Kong to Chile. This is just what I call the Net Way of living as well as it is something and love.
3. Flexibility
You will not be able to get the sort of flexibility the net provides you in any type of real life service (unless you run a truly big business). With a web company you could choose when to do your advertising and marketing for a product you are advertising, you decide when to create the next blog post for your blog site, you decide when to ask for interviews with other people, and you choose when to do nothing. I could make a decision to compose a short article over the evening to ensure that the lion's share of my morning is spent sleeping, or I may even intend to take the whole week off and go on a trip. This is because I MAY DO it.
4. Low Capital
To start an internet business you do not require thousands of bucks. Believe me you can begin a web service with as low as a couple $100s. For instance, as I mentioned at the beginning of this message, to produce a blog site like Earnings Scene all you will certainly need initially are: a $10 domain, a $60 webhosting solution with Hostgator, a $70 costs WordPress style with WooThermes and a $19 autoresponder service with Aweber (where you obtain the first month for $1) As well as with some significant work with your component, your blog site needs to be able to run itself without any further financial investment from you after the initial two months. As for I recognize no real world business can give you this.
5. Take advantage of on Modern technology
The quantity of technology offered to bloggers and also internet business owners in the days we stay in is massive, the very best part of it all is that a bulk of these software and also plug-ins are cost-free to obtain. When I began Revenue Scene, all the plug-ins I used were gotten free as well as one of them (Done in One SEO Load) aided me rank number 1 for a keyword with greater than 12 million outcomes on Google- all in just a couple of days without any unique job. There are many softwares offered now that will certainly aid you automate practically any kind of job, many more will certainly still be produced. The catch is that you open your mind and broaden your search to make sure that you will certainly understand where to look.
6. Very little Expenses
Cost The recurring price of running an on the internet business is harmlessly reduced. The expenses you will have to recurrently pay for will certainly consist of autoresponder charges as well as order processing fees. The others will probably be bulk payments (yearly, biennial, and so on) and also repayment for web connection. From whatever angle you take a look at it, an internet company needs much less from you in the means of overhanging prices compared to offline organisations where you will need to pay for leas and also salaries.
7. Entrepreneurship
The final as well as possibly the most crucial advantage I originate from running an online organisation which I can not get with an offline service, possibly as a result of my age is the chance to be called a business owner. Being an internet business owner is so simple when you contrast it with the legitimacies and procedures you have to comply with before you could start an offline service.
And as a side note, I must not forget to state that the net has (over)streamlined as well as accelerated the procedure of obtaining comments. If I run a promotion for a product and sales occur not to pick up, I could rapidly discover what failed and right my mistakes. By obtaining responses swiftly, I can move ahead much quicker with my blog site. Whereas having the very same promotion in the real life - making use of papers, costs or posters, general delivery, or other method will take weeks or months; for the exact same comments to be obtained.
Living as a net business owner gives every person a level airplane on which to contend. You can be an 80 years of age grandfather, a 13 years of age home -schooled kid or you could be helping The Boss (in a 9 to 5 work). It matters not who you are or where you originate from, all you have to do is to determine if beginning a web organisation is best for you. As for me, I am a blogger as well as an entrepreneur, as well as no one could take that from me.
For More Information About Nigerian Newspapers online, Latest News in Nigeria, Nigerian News, Nigerian newspapers read them online, Breaking News Nigeria, Nigerian Newspapers, Nigerian newspapers today, Nigeria latest news, online Nigerian newspapers, Nigerian breaking news, Nigeria current news, Latest News From Nigeria, Nigeria News Online, Nigeria News Today, Premium Times Nigeria
0 notes