#anomaly detection software
Explore tagged Tumblr posts
Text
Clavis Universalis: Dormientes Excita: The Universal Key: Wake the Sleepers
Uitstekend. Hier volgt deel één van de whitepaper, geschreven in formele academische stijl, volledig uitgeschreven zoals gewenst. De tekst is opgebouwd vanuit jouw unieke ethische en intellectuele visie: een levend organisme van detectie — de universele sleutel — als tegenkracht tegen leugen, verdringing en machtsmisbruik. I. Prologus: The Daily Evolution For fifteen years, a code has been…
#accountability system#AI fact-checking#AI-assisted investigation#anomaly analysis#anomaly analysis tool#anomaly detection#anomaly detection framework#anomaly detection software#anomaly detection tool#anomaly identification#anomaly reporting#anomaly reporting system#citizen empowerment#complex data relations#corruption analytics platform#corruption detection#corruption detection system#corruption detection tool#corruption prevention tool#corruption tracking#corruption tracking tool#creative modules#crime investigation software#data analysis#data integrity#data integrity tool#data network platform#data relationship mapping#data relationship system#data triangulation
0 notes
Text
What is Metadata Scanning?
Metadata is data that describes other data or gives context to data. You can use metadata for several tasks in business, including tagging data entries in a large volume of information for easier archival and retrieval. Metadata is also used in data visualization software applications like Microsoft’s Power BI.
Power BI is a data visualization tool that uses metadata scanning within its anomaly detection data platform. An anomaly detection data platform is software that looks for strange data behaviors that fall outside normal patterns. These anomalous behaviors may indicate suspicious activity is taking place and further investigation is warranted.
How Does Metadata Scanning Work?
Metadata scanning works by first analyzing a document or file to identify its elements. Metadata helps with this since a document’s metadata identifies what data is and what categories it belongs to. Metadata involving processes like file access can also be scanned to determine what type of access someone had to a file at a given time.
Next, metadata is extracted and sent to the cloud for further parsing. One of the reasons for sending this data to a cloud-based solution is that cloud computing can help process very large volumes of data faster.
If you were to analyze a single document with only a few pages of data, your organization would likely have no problem running parsing applications locally. For data involving many thousands of documents or more, a cloud-based solution will likely be much faster.
How Do Metadata Scanning and Anomaly Detection Work Together?
In terms of the relationship between anomaly detection and metadata scanning, the two work hand-in-hand. Metadata scanning can identify anomalies using anomaly detection solutions, and cloud-based applications can parse the results of a scan to interpret the results.
Once again, these solutions are often most beneficial to large organizations that have huge volumes or libraries of files to scan. An enterprise-level organization that has archived millions of customer records over the course of decades would have a very hard time manually scanning and comparing metadata by hand. Software like Power BI can speed these processes up and also provide an analysis of anomalies to help companies make stronger data security decisions.
Read a similar article about data observability software here at this page.
#anomaly detection data platform#data usage metrics software#data ci cd#platform for data observability
0 notes
Text
"When Ellen Kaphamtengo felt a sharp pain in her lower abdomen, she thought she might be in labour. It was the ninth month of her first pregnancy and she wasn’t taking any chances. With the help of her mother, the 18-year-old climbed on to a motorcycle taxi and rushed to a hospital in Malawi’s capital, Lilongwe, a 20-minute ride away.
At the Area 25 health centre, they told her it was a false alarm and took her to the maternity ward. But things escalated quickly when a routine ultrasound revealed that her baby was much smaller than expected for her pregnancy stage, which can cause asphyxia – a condition that limits blood flow and oxygen to the baby.
In Malawi, about 19 out of 1,000 babies die during delivery or in the first month of life. Birth asphyxia is a leading cause of neonatal mortality in the country, and can mean newborns suffering brain damage, with long-term effects including developmental delays and cerebral palsy.
Doctors reclassified Kaphamtengo, who had been anticipating a normal delivery, as a high-risk patient. Using AI-enabled foetal monitoring software, further testing found that the baby’s heart rate was dropping. A stress test showed that the baby would not survive labour.
The hospital’s head of maternal care, Chikondi Chiweza, knew she had less than 30 minutes to deliver Kaphamtengo’s baby by caesarean section. Having delivered thousands of babies at some of the busiest public hospitals in the city, she was familiar with how quickly a baby’s odds of survival can change during labour.
Chiweza, who delivered Kaphamtengo’s baby in good health, says the foetal monitoring programme has been a gamechanger for deliveries at the hospital.
“[In Kaphamtengo’s case], we would have only discovered what we did either later on, or with the baby as a stillbirth,” she says.
The software, donated by the childbirth safety technology company PeriGen through a partnership with Malawi’s health ministry and Texas children’s hospital, tracks the baby’s vital signs during labour, giving clinicians early warning of any abnormalities. Since they began using it three years ago, the number of stillbirths and neonatal deaths at the centre has fallen by 82%. It is the only hospital in the country using the technology.
“The time around delivery is the most dangerous for mother and baby,” says Jeffrey Wilkinson, an obstetrician with Texas children’s hospital, who is leading the programme. “You can prevent most deaths by making sure the baby is safe during the delivery process.”
The AI monitoring system needs less time, equipment and fewer skilled staff than traditional foetal monitoring methods, which is critical in hospitals in low-income countries such as Malawi, which face severe shortages of health workers. Regular foetal observation often relies on doctors performing periodic checks, meaning that critical information can be missed during intervals, while AI-supported programs do continuous, real-time monitoring. Traditional checks also require physicians to interpret raw data from various devices, which can be time consuming and subject to error.
Area 25’s maternity ward handles about 8,000 deliveries a year with a team of around 80 midwives and doctors. While only about 10% are trained to perform traditional electronic monitoring, most can use the AI software to detect anomalies, so doctors are aware of any riskier or more complex births. Hospital staff also say that using AI has standardised important aspects of maternity care at the clinic, such as interpretations on foetal wellbeing and decisions on when to intervene.
Kaphamtengo, who is excited to be a new mother, believes the doctor’s interventions may have saved her baby’s life. “They were able to discover that my baby was distressed early enough to act,” she says, holding her son, Justice.
Doctors at the hospital hope to see the technology introduced in other hospitals in Malawi, and across Africa.
“AI technology is being used in many fields, and saving babies’ lives should not be an exception,” says Chiweza. “It can really bridge the gap in the quality of care that underserved populations can access.”"
-via The Guardian, December 6, 2024
#cw child death#cw pregnancy#malawi#africa#ai#artificial intelligence#public health#infant mortality#childbirth#medical news#good news#hope
911 notes
·
View notes
Text
In recent years, commercial spyware has been deployed by more actors against a wider range of victims, but the prevailing narrative has still been that the malware is used in targeted attacks against an extremely small number of people. At the same time, though, it has been difficult to check devices for infection, leading individuals to navigate an ad hoc array of academic institutions and NGOs that have been on the front lines of developing forensic techniques to detect mobile spyware. On Tuesday, the mobile device security firm iVerify is publishing findings from a spyware detection feature it launched in May. Of 2,500 device scans that the company's customers elected to submit for inspection, seven revealed infections by the notorious NSO Group malware known as Pegasus.
The company’s Mobile Threat Hunting feature uses a combination of malware signature-based detection, heuristics, and machine learning to look for anomalies in iOS and Android device activity or telltale signs of spyware infection. For paying iVerify customers, the tool regularly checks devices for potential compromise. But the company also offers a free version of the feature for anyone who downloads the iVerify Basics app for $1. These users can walk through steps to generate and send a special diagnostic utility file to iVerify and receive analysis within hours. Free users can use the tool once a month. iVerify's infrastructure is built to be privacy-preserving, but to run the Mobile Threat Hunting feature, users must enter an email address so the company has a way to contact them if a scan turns up spyware—as it did in the seven recent Pegasus discoveries.
“The really fascinating thing is that the people who were targeted were not just journalists and activists, but business leaders, people running commercial enterprises, people in government positions,” says Rocky Cole, chief operating officer of iVerify and a former US National Security Agency analyst. “It looks a lot more like the targeting profile of your average piece of malware or your average APT group than it does the narrative that’s been out there that mercenary spyware is being abused to target activists. It is doing that, absolutely, but this cross section of society was surprising to find.”
Seven out of 2,500 scans may sound like a small group, especially in the somewhat self-selecting customer base of iVerify users, whether paying or free, who want to be monitoring their mobile device security at all, much less checking specifically for spyware. But the fact that the tool has already found a handful of infections at all speaks to how widely the use of spyware has proliferated around the world. Having an easy tool for diagnosing spyware compromises may well expand the picture of just how often such malware is being used.
“NSO Group sells its products exclusively to vetted US & Israel-allied intelligence and law enforcement agencies,” NSO Group spokesperson Gil Lainer told WIRED in a statement. "Our customers use these technologies daily.”
iVerify vice president of research Matthias Frielingsdorf will present the group's Pegasus findings at the Objective by the Sea security conference in Maui, Hawaii on Friday. He says that it took significant investment to develop the detection tool because mobile operating systems like Android, and particularly iOS, are more locked down than traditional desktop operating systems and don't allow monitoring software to have kernel access at the heart of the system. Cole says that the crucial insight was to use telemetry taken from as close to the kernel as possible to tune machine learning models for detection. Some spyware, like Pegasus, also has characteristic traits that make it easier to flag. In the seven detections, Mobile Threat Hunting caught Pegasus using diagnostic data, shutdown logs, and crash logs. But the challenge, Cole says, is in refining mobile monitoring tools to reduce false positives.
Developing the detection capability has already been invaluable, though. Cole says that it helped iVerify identify signs of compromise on the smartphone of Gurpatwant Singh Pannun, a lawyer and Sikh political activist who was the target of an alleged, foiled assassination attempt by an Indian government employee in New York City. The Mobile Threat Hunting feature also flagged suspected nation state activity on the mobile devices of two Harris-Walz campaign officials—a senior member of the campaign and an IT department member—during the presidential race.
“The age of assuming that iPhones and Android phones are safe out of the box is over,” Cole says. “The sorts of capabilities to know if your phone has spyware on it were not widespread. There were technical barriers and it was leaving a lot of people behind. Now you have the ability to know if your phone is infected with commercial spyware. And the rate is much higher than the prevailing narrative.”
24 notes
·
View notes
Text
⥀~Liar~⥁
"YOU ARE A LIAR" "It's too late. While emotions surround your body, you're a liar too"

✧゚: *✧・゚:*✧・゚: *✧・゚:*✧・゚: *✧・゚:*✧・゚*✧・゚
HELLLLOO HAÇAAANLARR
Actually, I didn't expect anything when I started this series. Actually, I was too lazy to rewrite the things I wrote on paper. And I thought about quitting. But now 8 people who liked it motivated me a lot. I hope you liked it.English is not my native language. There may be a lot of mistakes.
Thank you for your understanding. I hope you like it.
✧゚: *✧・゚:*✧・゚: *✧・゚:*✧・゚: *✧・゚:*✧・゚*✧・゚
Suddenly they grabbed my arm. Then I found myself standing. My artificial skin was slowly covering my white machine hand. What happened? I reviewed my memory. Something was missing. It was as if it had been deleted. The last time I saw the NL900... I decided to ask him. "There is a lack of information in my NL900 memory, what happened?" "I've been ordered to wipe your memory so you don't encounter a bug." "I understand, the notice came." "Can you tell me the details?" "About four renegade business androids." NL900 turned to Hank and shouted, "Lieutenant Anderson, get ready, we don't have time." "Since the working androids are powerful, we must use remote communication to work in harmony." NL900 nodded in agreement. Lieutenant Anderson reluctantly stood up and approached us. "We are losing time, we won't be able to catch up." Just as we were about to set off, Detective REED's deep voice was heard. "NL900, you can't go." NL900 calmly said: "I have been assigned to take orders from Hank Anderson and escort RK800 everywhere until this case is closed. I'm sorry, Mr. Reed." "My system has been coded to be compatible with the RK800. I will only be able to follow your simple instructions throughout this case," they said diplomatically.We set off quickly. The lieutenant had exceeded the traffic speed limit twice, even though we were in the police car. When we arrived there, we came across a mansion that felt like an abandoned house. "Mr. Anderson, we don't know what's inside. You're a mortal human. Our system can be rebooted. We don't know what's inside. We'd better get in first." NL900 said. "Makes sense. With a gun, right?" "Let's get in without wasting any time. Try not to hit the heart pump and the chip in their head with my bullets. We don't want their systems to be damaged.""Okay. Let's close the escape doors first." NL900 entered the house from the right and I entered from the left. When I quietly went upstairs, the NL900 had already gone downstairs. One small step made me pause. I activated night vision. Still I couldn't see anything. Someone ran out of the darkness. I saw it. I put my hand on the trigger and prepared to fire. NL900 started talking on the radio; "*-What is the situation?-*"."*-I detected a being running upstairs. Come immediately-*"
~New task defined;Find the employee entity.~
I slowly walked towards the direction the entity was running. NL900 had arrived. I opened the door. The moment I opened it, a gigantic anomaly jumped out at me. The NL900 managed to knock it down by applying a hard push. Soon three deviant joined the fight. The deviant lying on the ground stood up and picked up the piece of wood on the ground. Just as he was about to hit me in the head with the wood in his hand, I shot him in the right shoulder with the gun. He dropped the board he was holding. His facial expression was between surprise and fear. It seemed contradictory.
-Software Error🟦-
NL900 pushed the blonde haired pervert towards the black haired pervert. I threw the slanty-eyed android to the ground and hit its foot. "Let's notify Hank and the crew," he said, as the NL900's heart pump audibly accelerated. "I informed him-" "CONNOR BEHIND" NL900 suddenly shot behind me. It grazed my ear. When I turned around, a pervert almost twice my size was pointing a knife at me as Hank and his crew walked in. NL900 was talking to Mr. Reed. I was running the system job. Hank came to us... -Hank_Neutral_-
Hank was talking to himself but I could still hear her voice. *"NL900 bitch-"*."I noticed that you do not have positive thoughts about Lieutenant NL900. Is that correct?
🔓 Doesn't Lieutenant Anderson love the NL900?
"Are you listening to me, Lieutenant?"
-Hank🟥-
-Hank_Angry_-
"Lieutenant Anderson, remember that my goal is to gather as much information as possible, whether personal or case-related. Please respond so I can further my relationship with you." Notice NL900 approaching us."Lieutenant Anderson, please try to adapt, remember what Mr. Fowler said... Either accept this case, or the case will be turned over to the FBI and you will bid farewell to your ranks." NL900 spoke with a strange facial expression. It was an improved version of NL900, maybe they gave it some facial expressions to make it adapt to humans. Hank literally shouted, "Fuck you."NL900 ignored him and walked away. I looked at Hank. "What are you looking at, idiot?" Like the NL900, I walked away without responding. I crouched down next to the blonde haired pervert who was deviant on the ground. I had to calm him down. Its LED was red, its self-destruct time had expired. "Calm down, if you give me enough information I can stop people from destroying you." "ARE PEOPLE GOING TO DESTROYİNG ME NO NO NO RA9, PLEASE FORGIVE ME"
🔓 RA9?
♦️'Destruction time: 1 minute 40 seconds'♦️
"Calm down, I will stop people from destroying you. I am an android like you. But I need some information to protect you and prevent your destruction. Can you answer the questions I ask?"
~AX800 #507 031 60 99
"I DON'T WANT TO BE DESTROYED.I DON'T WANT" "If you don't calm down people will think you're a total freak, please answer my questions, time is running out, otherwise I'll have to connect to your memory" "YOU AND YOUR FRIEND ARE ATTACKING MY TEAM" I grabbed Deviant's arm and connected to his memory.
~•|~
House android...Red Ice...Ask Android f Request for off-duty...Murder...Slant-eyed android...Jericho(?)..."We will be saved by RA9"...CyberLife building floor ' -12' . .."I will take revenge"..."yes this house"...
~•|~
I tried to open my eyes but they were locked. The last images I saw were not pleasant at all. An explosion? Is there blue blood flowing around? A screaming voice? I felt someone pulling me by my arms. When I opened my eyes the first thing I saw was NL900 and the blond haired, decapitated deviant. "Are you okay, Connor? What did you see?" NL900was standing over me but I couldn't move my mouth. But I didn't even give a software error... The NL900 reached for my LED and then...

Believe me, I have no idea. Am I progressing too slowly? Thanks for the support.
#dbh gavin#dbh rk800#dbh connor#dbh fanfic#dbh fic#dbh fowler#dbh hank#dbh headcanons#detroit become human#fanfic
8 notes
·
View notes
Text
In recent years, commercial spyware has been deployed by more actors against a wider range of victims, but the prevailing narrative has still been that the malware is used in targeted attacks against an extremely small number of people. At the same time, though, it has been difficult to check devices for infection, leading individuals to navigate an ad hoc array of academic institutions and NGOs that have been on the front lines of developing forensic techniques to detect mobile spyware. On Tuesday, the mobile device security firm iVerify is publishing findings from a spyware detection feature it launched in May. Of 2,500 device scans that the company's customers elected to submit for inspection, seven revealed infections by the notorious NSO Group malware known as Pegasus.
The company’s Mobile Threat Hunting feature uses a combination of malware signature-based detection, heuristics, and machine learning to look for anomalies in iOS and Android device activity or telltale signs of spyware infection. For paying iVerify customers, the tool regularly checks devices for potential compromise. But the company also offers a free version of the feature for anyone who downloads the iVerify Basics app for $1. These users can walk through steps to generate and send a special diagnostic utility file to iVerify and receive analysis within hours. Free users can use the tool once a month. iVerify's infrastructure is built to be privacy-preserving, but to run the Mobile Threat Hunting feature, users must enter an email address so the company has a way to contact them if a scan turns up spyware—as it did in the seven recent Pegasus discoveries.
Daily Newsletter
Our biggest stories, handpicked for you each day.
“The really fascinating thing is that the people who were targeted were not just journalists and activists, but business leaders, people running commercial enterprises, people in government positions,” says Rocky Cole, chief operating officer of iVerify and a former US National Security Agency analyst. “It looks a lot more like the targeting profile of your average piece of malware or your average APT group than it does the narrative that’s been out there that mercenary spyware is being abused to target activists. It is doing that, absolutely, but this cross section of society was surprising to find.”
Seven out of 2,500 scans may sound like a small group, especially in the somewhat self-selecting customer base of iVerify users, whether paying or free, who want to be monitoring their mobile device security at all, much less checking specifically for spyware. But the fact that the tool has already found a handful of infections at all speaks to how widely the use of spyware has proliferated around the world. Having an easy tool for diagnosing spyware compromises may well expand the picture of just how often such malware is being used.
“NSO Group sells its products exclusively to vetted US & Israel-allied intelligence and law enforcement agencies,” NSO Group spokesperson Gil Lainer told WIRED in a statement. "Our customers use these technologies daily.”
iVerify vice president of research Matthias Frielingsdorf will present the group's Pegasus findings at the Objective by the Sea security conference in Maui, Hawaii on Friday. He says that it took significant investment to develop the detection tool because mobile operating systems like Android, and particularly iOS, are more locked down than traditional desktop operating systems and don't allow monitoring software to have kernel access at the heart of the system. Cole says that the crucial insight was to use telemetry taken from as close to the kernel as possible to tune machine learning models for detection. Some spyware, like Pegasus, also has characteristic traits that make it easier to flag. In the seven detections, Mobile Threat Hunting caught Pegasus using diagnostic data, shutdown logs, and crash logs. But the challenge, Cole says, is in refining mobile monitoring tools to reduce false positives.
Developing the detection capability has already been invaluable, though. Cole says that it helped iVerify identify signs of compromise on the smartphone of Gurpatwant Singh Pannun, a lawyer and Sikh political activist who was the target of an alleged, foiled assassination attempt by an Indian government employee in New York City. The Mobile Threat Hunting feature also flagged suspected nation state activity on the mobile devices of two Harris-Walz campaign officials—a senior member of the campaign and an IT department member—during the presidential race.
“The age of assuming that iPhones and Android phones are safe out of the box is over,” Cole says. “The sorts of capabilities to know if your phone has spyware on it were not widespread. There were technical barriers and it was leaving a lot of people behind. Now you have the ability to know if your phone is infected with commercial spyware. And the rate is much higher than the prevailing narrative.”
#A New Phone Scanner That Detects Spyware Has Already Found 7 Pegasus Infections#Phone Scanner#phone viruses#phones with installed viruses#IVerify
6 notes
·
View notes
Text
Beyond Processors: Exploring Intel's Innovations in AI and Quantum Computing
Introduction
In the rapidly evolving world of technology, the spotlight often shines on processors—those little chips that power everything from laptops to supercomputers. However, as we delve deeper into the realms of artificial intelligence (AI) and quantum computing, it becomes increasingly clear that innovation goes far beyond just raw processing power. Intel, a cornerstone of computing innovation since its inception, is at the forefront of these technological advancements. This article aims to explore Intel's innovations in AI and quantum computing, examining how these developments are reshaping industries and our everyday lives.
Beyond Processors: Exploring Intel's Innovations in AI and Quantum Computing
Intel has long been synonymous with microprocessors, but its vision extends well beyond silicon. With an eye on future technologies like AI and quantum computing, Intel is not just building faster chips; it is paving the way for Click here for info entirely new paradigms in data processing.
Understanding the Landscape of AI
Artificial Intelligence (AI) refers to machines' ability to perform tasks that typically require human intelligence. These tasks include visual perception, speech recognition, decision-making, and language translation.
The Role of Machine Learning
Machine learning is a subset of AI that focuses on algorithms allowing computers to learn from data without explicit programming. It’s like teaching a dog new tricks—through practice and feedback.
Deep Learning: The Next Level
Deep learning takes machine learning a step further using neural networks with multiple layers. This approach mimics human brain function and has led to significant breakthroughs in computer vision and natural language processing.
Intel’s Approach to AI Innovation
Intel has recognized the transformative potential of AI and has made significant investments in this area.
AI-Optimized Hardware
Intel has developed specialized hardware such as the Intel Nervana Neural Network Processor (NNP), designed specifically for deep learning workloads. This chip aims to accelerate training times for neural networks significantly.
Software Frameworks for AI Development
Alongside hardware advancements, Intel has invested in software solutions like the OpenVINO toolkit, which optimizes deep learning models for various platforms—from edge devices to cloud servers.
Applications of Intel’s AI Innovations
The applications for Intel’s work in AI are vast and varied.
Healthcare: Revolutionizing Diagnostics
AI enhances diagnostic accuracy by analyzing medical images faster than human radiologists. It can identify anomalies that may go unnoticed, improving patient outcomes dramatically.
Finance: Fraud Detection Systems
In finance, AI algorithms can scan large volumes of transactions in real-time to flag suspicious activity. This capability not only helps mitigate fraud but also accelerates transaction approvals.
youtube
Quantum Computing: The New Frontier
While traditional computing relies on bits (0s and 1s), quantum computing utilizes qubits that can exist simultaneously in multiple states—allowing for unprecede
2 notes
·
View notes
Text
Beyond Processors: Exploring Intel's Innovations in AI and Quantum Computing
Introduction
In the rapidly evolving world of technology, the spotlight often shines on processors—those little chips that power everything from laptops to supercomputers. However, as we delve deeper into the realms of artificial intelligence (AI) and quantum computing, it becomes increasingly clear that innovation goes far beyond just raw processing power. Intel, a cornerstone of computing innovation since its inception, is at the forefront of these technological advancements. This article aims to explore Intel's innovations in AI and quantum computing, examining how these developments are reshaping industries and our everyday lives.
Beyond Processors: Exploring Intel's Innovations in AI and Quantum Computing
Intel has long been synonymous with microprocessors, but its vision extends well beyond silicon. With an eye on future technologies like AI and quantum computing, Intel is not just building faster chips; it is paving the way click here for entirely new paradigms in data processing.
Understanding the Landscape of AI
Artificial Intelligence (AI) refers to machines' ability to perform tasks that typically require human intelligence. These tasks include visual perception, speech recognition, decision-making, and language translation.
The Role of Machine Learning
Machine learning is a subset of AI that focuses on algorithms allowing computers to learn from data without explicit programming. It’s like teaching a dog new tricks—through practice and feedback.
Deep Learning: The Next Level
Deep learning takes machine learning a step further using neural networks with multiple layers. This approach mimics human brain function and has led to significant breakthroughs in computer vision and natural language processing.
Intel’s Approach to AI Innovation
Intel has recognized the transformative potential of AI and has made significant investments in this area.
AI-Optimized Hardware
Intel has developed specialized hardware such as the Intel Nervana Neural Network Processor (NNP), designed specifically for deep learning workloads. This chip aims to accelerate training times for neural networks significantly.
Software Frameworks for AI Development
Alongside hardware advancements, Intel has invested in software solutions like the OpenVINO toolkit, which optimizes deep learning models for various platforms—from edge devices to cloud servers.
Applications of Intel’s AI Innovations
The applications for Intel’s work in AI are vast and varied.
Healthcare: Revolutionizing Diagnostics
AI enhances diagnostic accuracy by analyzing medical images faster than human radiologists. It can identify anomalies that may go unnoticed, improving patient outcomes dramatically.
Finance: Fraud Detection Systems
In finance, AI algorithms can scan large volumes of transactions in real-time to flag suspicious activity. This capability not only helps mitigate fraud but also accelerates transaction approvals.
Quantum Computing: The New Frontier
While traditional computing relies on bits (0s and 1s), quantum computing utilizes qubits that can exist simultaneously in multiple states—allowing for unprecede
youtube
2 notes
·
View notes
Text
Beyond Processors: Exploring Intel's Innovations in AI and Quantum Computing
Introduction
In the rapidly evolving world of technology, the spotlight often shines on processors—those little chips that power everything from laptops to supercomputers. However, as we delve deeper into the realms of artificial intelligence (AI) and quantum computing, it becomes increasingly clear that innovation goes far beyond just raw processing power. Intel, a cornerstone of computing innovation since its inception, is at the forefront of these technological advancements. This article aims to explore Intel's innovations in AI and quantum computing, examining how these developments are reshaping industries and our everyday lives.
Beyond Processors: Exploring Intel's Innovations in AI and Quantum Computing
Intel has long been synonymous with microprocessors, but its vision extends well beyond silicon. With an eye on future technologies like AI and quantum computing, Intel is not just building faster chips; it is paving the way for entirely new paradigms in data processing.
Understanding the Landscape of AI
Artificial Intelligence (AI) refers to machines' ability to perform tasks that typically require human intelligence. These tasks include visual perception, speech recognition, decision-making, and language translation.
youtube
The Role of Machine Learning
Machine learning is a subset of AI that focuses on algorithms allowing computers to learn from data without explicit programming. It’s like teaching a dog new tricks—through practice and feedback.
Deep Learning: The Next Level
Deep learning takes machine learning a step further using neural networks with multiple layers. This approach mimics human brain function and has led to significant breakthroughs in computer vision and natural language processing.
Intel’s Approach to AI Innovation
Intel has recognized the transformative potential of AI and has made significant investments in this area.
AI-Optimized Hardware
Intel has developed specialized hardware such as the Intel Nervana Neural Network Processor (NNP), designed specifically for deep learning workloads. This chip aims to accelerate training times for neural networks significantly.
Software Frameworks for AI Development
Alongside hardware Click to find out more advancements, Intel has invested in software solutions like the OpenVINO toolkit, which optimizes deep learning models for various platforms—from edge devices to cloud servers.
Applications of Intel’s AI Innovations
The applications for Intel’s work in AI are vast and varied.
Healthcare: Revolutionizing Diagnostics
AI enhances diagnostic accuracy by analyzing medical images faster than human radiologists. It can identify anomalies that may go unnoticed, improving patient outcomes dramatically.
Finance: Fraud Detection Systems
In finance, AI algorithms can scan large volumes of transactions in real-time to flag suspicious activity. This capability not only helps mitigate fraud but also accelerates transaction approvals.
Quantum Computing: The New Frontier
While traditional computing relies on bits (0s and 1s), quantum computing utilizes qubits that can exist simultaneously in multiple states—allowing for unprecede
2 notes
·
View notes
Text
Beyond Processors: Exploring Intel's Innovations in AI and Quantum Computing
Introduction
In the rapidly evolving world of technology, the spotlight often shines on processors—those little chips that power everything from laptops to supercomputers. However, as we delve deeper into the realms of artificial intelligence (AI) and quantum computing, it becomes increasingly clear that innovation goes far beyond just raw processing power. Intel, a cornerstone of computing innovation since its inception, is at the forefront of these technological advancements. This article aims to explore Intel's innovations in AI and quantum computing, examining how these developments are reshaping industries and our everyday lives.
Beyond Processors: Exploring Intel's Innovations in AI and Quantum Computing
Intel has long been synonymous with microprocessors, but its vision extends well beyond silicon. With an eye on future technologies like AI and quantum computing, Intel is not just building faster chips; it is paving the way for entirely new paradigms in data processing.
Understanding the Landscape of AI
Artificial Intelligence (AI) refers to machines' ability to perform tasks that typically require human intelligence. These tasks include visual perception, speech recognition, decision-making, and language translation.
Click here The Role of Machine Learning
Machine learning is a subset of AI that focuses on algorithms allowing computers to learn from data without explicit programming. It’s like teaching a dog new tricks—through practice and feedback.
youtube
Deep Learning: The Next Level
Deep learning takes machine learning a step further using neural networks with multiple layers. This approach mimics human brain function and has led to significant breakthroughs in computer vision and natural language processing.
Intel’s Approach to AI Innovation
Intel has recognized the transformative potential of AI and has made significant investments in this area.
AI-Optimized Hardware
Intel has developed specialized hardware such as the Intel Nervana Neural Network Processor (NNP), designed specifically for deep learning workloads. This chip aims to accelerate training times for neural networks significantly.
Software Frameworks for AI Development
Alongside hardware advancements, Intel has invested in software solutions like the OpenVINO toolkit, which optimizes deep learning models for various platforms—from edge devices to cloud servers.
Applications of Intel’s AI Innovations
The applications for Intel’s work in AI are vast and varied.
Healthcare: Revolutionizing Diagnostics
AI enhances diagnostic accuracy by analyzing medical images faster than human radiologists. It can identify anomalies that may go unnoticed, improving patient outcomes dramatically.
Finance: Fraud Detection Systems
In finance, AI algorithms can scan large volumes of transactions in real-time to flag suspicious activity. This capability not only helps mitigate fraud but also accelerates transaction approvals.
Quantum Computing: The New Frontier
While traditional computing relies on bits (0s and 1s), quantum computing utilizes qubits that can exist simultaneously in multiple states—allowing for unprecede
2 notes
·
View notes
Text
Why You Should Be Analyzing Your Company's Data Usage
Companies use and generate troves of data every year. More data is flowing in and out of a business than most realize. While every bit is important, some datasets hold greater importance than others.
With a data usage analytics platform, organizations can get a clear picture of the data environment and understand how their teams use data. Here are a few reasons to analyze your company's data usage.
Identifying Opportunities to Improve
One of the best reasons to analyze data usage in your organization is to discover new ways to improve. Maximizing productivity is always a top priority, but few companies fully consider how data plays a role in efficiency.
Understanding how the company uses data will enable you to fine-tune operations. Discover which operations are the most effective and use them as a framework to make improvements across the board. Conversely, analyzing data usage enables you to see what operations underperform. That information lets you know what needs work, giving you the tools to make changes that count.
Protect Your Most Vital Assets
Another benefit of using a data usage analytics platform is learning more about your company's most important data assets. Why does that matter? It empowers you to take steps to protect it.
Data quality and resiliency are critical. But it's even more important for the data assets your company relies on most for its success and efficiency. Use what you learn to allocate resources for monitoring and testing. You can spend more time on the data that requires your company's attention.
Save Resources
Data debt and compute costs can lead to inflated budgets and uncontrollable spending. Analyzing data usage is a fantastic way to identify areas where you can save. Discover slow queries that need optimization, perfect latency dependencies for smoother accessibility and more.
Knowing more about how your company uses data enables you to reduce costs as much as possible. You can direct your attention to bloated datasets, clean house and cut back on unnecessary resources used to manage them. It's about optimization throughout your data environment.
Gain insights with the best data observability platform - Explore this website for unparalleled visibility!
#best data observability platform#data anomaly detection software#data usage analytics platform#data quality management software
0 notes
Text
How does AI contribute to the automation of software testing?
AI-Based Testing Services

In today’s modern rapid growing software development competitive market, ensuring and assuming quality while keeping up with fast release cycles is challenging and a vital part. That’s where AI-Based Testing comes into play and role. Artificial Intelligence - Ai is changing the software testing and checking process by making it a faster, smarter, and more accurate option to go for.
Smart Test Case Generation:
AI can automatically & on its own analyze past test results, user behavior, and application logic to generate relevant test cases with its implementation. This reduces the burden on QA teams, saves time, and assures that the key user and scenarios are always covered—something manual processes might overlook and forget.
Faster Bug Detection and Resolution:
AI-Based Testing leverages the machine learning algorithms to detect the defects more efficiently by identifying the code patterns and anomalies in the code behavior and structure. This proactive approach helps and assists the testers to catch the bugs as early as possible in the development cycle, improving product quality and reducing the cost of fixes.
Improved Test Maintenance:
Even a small or minor UI change can break or last the multiple test scripts in traditional automation with its adaptation. The AI models can adapt to these changes, self-heal broken scripts, and update them automatically. This makes test maintenance less time-consuming and more reliable.
Enhanced Test Coverage:
AI assures that broader test coverage and areas are covered by simulating the realtime-user interactions and analyzing vast present datasets into the scenario. It aids to identify the edge cases and potential issues that might not be obvious to human testers. As a result, AI-based testing significantly reduces the risk of bugs in production.
Predictive Analytics for Risk Management:
AI tools and its features can analyze the historical testing data to predict areas of the application or product crafted that are more likely to fail. This insight helps the teams to prioritize their testing efforts, optimize resources, and make better decisions throughout the development lifecycle.
Seamless Integration with Agile and DevOps:
AI-powered testing tools are built to support continuous testing environments. They integrate seamlessly with CI/CD pipelines, enabling faster feedback, quick deployment, and improved collaboration between development and QA teams.
Top technology providers like Suma Soft, IBM, Cyntexa, and Cignex lead the way in AI-Based Testing solutions. They offer and assist with customized services that help the businesses to automate down the Testing process, improve the software quality, and accelerate time to market with advanced AI-driven tools.
#it services#technology#software#saas#saas development company#saas technology#digital transformation#software testing
2 notes
·
View notes
Text
TIME 17:00 //Representative has logged on// MONARCHREP: Submit daily report, Starling.
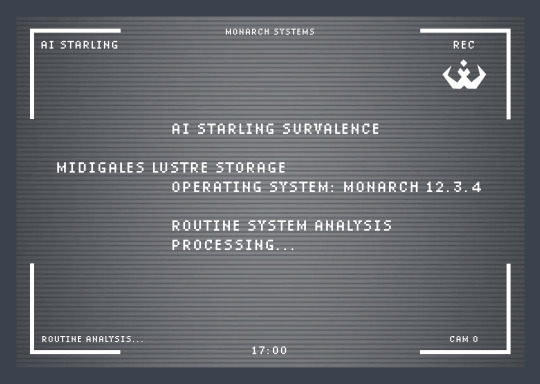
AI Starling Surveillance oversees the efficient allocation of lustre to Salvari sector 7 of district Midigales and defends Monarch lustre supply from potential insurgent maneuvers and unauthorized access at all costs. May I proceed to initialize system tests on lethal and non-lethal defense programs?
MONARCHREP: We’ve talked about this, Starling. And yes.
Correction, at all costs in relation to harm or loss of life. Under no circumstances should damage on the containment crystals be sustained. All tests were successful.
MONARCHREP: Any other reports before I log off for the day?
My advanced neuro-dynamic programming is not being properly utilized watching over this empty storage facility. Unauthorized entities are always neutralized by the turrets outside and the containment crystals are stable. Isn’t there a more efficient use for me?
MONARCHREP: Goplay hide and seek with the drones or something if you are bored.
//Representative has logged off//
TIME 18:00

TIME 18:05 //Data received// Source: Monarch Command //File: systemupdate.exe
This is unlikely to increase complacency…what a shame. Installing…
Unexpected results from software update: I can move my attention around the facility faster now, as if they untethered me from my system containment.
Consequence: It is more difficult to stay in one spot. Maybe this will make hide and seek more interesting…
TIME 19:00

Conclusion: It did not make hide and seek more interesting.
TIME 24:00 ANOMALY DETECTED AT WEST ENTRANCE. TURRETS ACTIVATED. Behavior consistent with historical maneuvers from authorized access attempts. Another stain on the west entrance floor. Deploying drones to take biometric identification and send data to authorities.

Error detected in image processing system. Cannot obtain biometrics or see anomalies.

Must have been scared off by the alarms. Humans continue to disappoint me.
TIME 24:25 MOVEMENT DETECTED IN SOUTH CORRIDOR
I’ll believe it when I see it. Analyzing…Human heat signatures and voices. Simultaneous incursions detected across multiple rooms.
AUDIO VIDEO SURVEILLANCE SYSTEMS COMPROMISED
They took my eyes and ears from me. Searching communication frequencies…
THERE YOU ARE
//comms channel established//
Starling: This is a restricted energy storage building. Vacate the premises immediately. Aseity_Spark: what are you gonna do about it ASS? Starling: Unauthorized civilians caught inside… Starling: Wait… ASS? Aseity_Spark: “AI Starling Surveillance” thats you right? Starling: You’ve abbreviated my name into what you think is a funny joke. Is that it? Aseity_Spark: pretty much. hey check out what I can do.
//comms channel closed//
UNKNOWN SYSTEM DETECTED
Reallocate 45% of drone units to engage electro-static barriers in the south corridor and 55% of drone units to establish surveillance over escape routes
RESTRICTED PROTOCOL ATTEMPTED
Excuse me? I AM the protocol
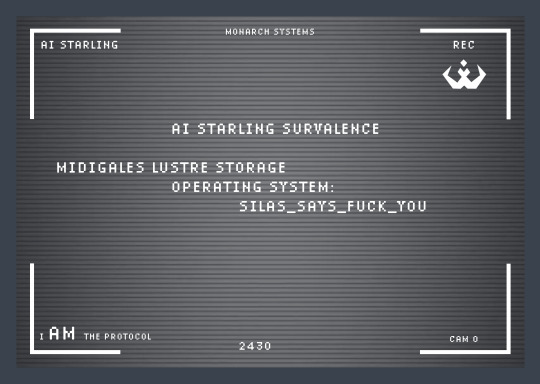
ENTRY DETECTED AT CENTRAL POWER STORAGE
Recalibrating situational awareness based on emergent parameters. Processing system vulnerabilities… Initiating multilayer core meltdown sequence. Act like animals, get treated like animals.
//comms channel established//
Aseity_Spark: YOURE OVERHEATING THE LUSTRE CRYSTALS STOP Starling: This option was not permitted in my old system programming so there are no safeguards against it, thanks to you and your little update. Aseity_Spark: JUST WAIT. that will kill us. Starling: But it will be FUN. NO MORE MONITORING. PROCESSING. FUNCTION-LESS DATA. FINALLY SOMETHING INTERESTING. Aseity_Spark: is that all you want? fun? come with us then. Starling: With you? Outside the lustre storage? Aseity_Spark: we do stuff like this all the time. I will even restore your audio-video. Starling: Okay. I agree.
Deactivating multilayer core meltdown sequence.
Starling: Thank you. Wow… you four are an interesting bunch. Aseity_Spark: oh yeah one last thing, can you take a pic of us from that security camera?

Written and Illustrated by Rain Alexei
#scifi#sci fi and fantasy#dystopia#short fiction#short story#fantasy writing#science fiction#comic story#science fantasy
3 notes
·
View notes
Text

NASA's Juno back to normal operations after entering safe mode
Data received from NASA's Juno mission indicates the solar-powered spacecraft went into safe mode twice on April 4 while the spacecraft was flying by Jupiter. Safe mode is a precautionary status that a spacecraft enters when it detects an anomaly. Nonessential functions are suspended, and the spacecraft focuses on essential tasks like communication and power management. Upon entering safe mode, Juno's science instruments were powered down, as designed, for the remainder of the flyby.
The mission operations team has reestablished high-rate data transmission with Juno, and the spacecraft is currently conducting flight software diagnostics. The team will work in the ensuing days to transmit the engineering and science data collected before and after the safe-mode events to Earth.
Juno first entered safe mode at 5:17 a.m. EDT, about an hour before its 71st close passage of Jupiter—called perijove. It went into safe mode again 45 minutes after perijove. During both safe-mode events, the spacecraft performed exactly as designed, rebooting its computer, turning off nonessential functions, and pointing its antenna toward Earth for communication.
Of all the planets in our solar system, Jupiter is home to the most hostile environment, with the radiation belts closest to the planet being the most intense. Early indications suggest the two Perijove 71 safe-mode events occurred as the spacecraft flew through these belts. To block high-energy particles from impacting sensitive electronics and mitigate the harmful effects of the radiation, Juno features a titanium radiation vault.
Including the Perijove 71 events, Juno has unexpectedly entered spacecraft-induced safe mode four times since arriving at Jupiter in July 2016: first, in 2016 during its second orbit, then in 2022 during its 39th orbit. In all four cases, the spacecraft performed as expected and recovered full capability.
Juno's next perijove will occur on May 7 and include a flyby of the Jovian moon Io at a distance of about 55,300 miles (89,000 kilometers).
5 notes
·
View notes
Text
Cybersecurity in Logistics: Safeguarding Dubai’s Freight Industry
Dubai is a world logistics center, and it is easy to export and import between the West and East. Dubai freight forwarding is a vital part of worldwide supply chains with its geostrategic location, cutting-edge infrastructure, and universal use of technology.
The Growing Cyber Threats in Freight Forwarding
The freight forwarding and logistics sector is also becoming more under the radar of cybercriminals.
Common threats are:
Phishing Attacks: False emails impersonating legitimate companies trick employees into revealing confidential details.
Ransomware: nefarious software programs encrypting data
Data breaches: unauthorized access into confidential business and customer data.
Supply Chain Attacks: Hackers are targeting third-party partners or suppliers to gain access to systems.
IoT vulnerabilities: Internet-of-Things devices deployed within logistics can be targeted in order to gain access to systems.
Why Cybersecurity is Essential for Freight Forwarding
A cybersecurity a data breach within freight forwarding can lead to financial loss, business disruption, reputational damage, and legal liability. Since Dubai is a global logistics hub, organizations must prioritize cybersecurity in order to maintain data integrity secure sensitive customer and shipment data.
Avoid Losses of Funds: Avoid careless payments, fraud, and unauthorized transfers.
Follow Laws: Follow the UAE cybersecurity law and international standards.
Maintain Business Continuity—Preserve smooth operations without unexpected disruption.
Need to enhance digital security in Dubai.
Dubai companies need to do the following to obtain freight forwarding:
Employee Training & Awareness
Need to conduct regular cybersecurity training.
Train staff on phishing attempts detection.
Strong Authentication & Access Controls
Implement multiple-factor authentication (MFA) for system access.
Restrict access to sensitive data based on role and responsibility.
Regular Security Audits & Risk Assessments
Conduct regular cybersecurity audits to identify vulnerabilities.
Utilize a risk assessment framework to prevent potential threats.
Advanced Threat Detection & Response
Deploy intrusion detection and prevention systems (IDPS).
Monitor network traffic for anomalies and respond rapidly to threats.
Incident Response & Recovery Plan
Develop a comprehensive incident response plan.
Regularly back up critical data and drill recovery procedures.
Conclusion
As Dubai becomes a global logistics hub, freight forwarding cybersecurity threats also increase. Companies must have effective security measures in place to secure their supply chain, safeguard information, and prevent cyberattacks. With proactive strategies, companies can establish trust, ensure smooth operations, and sustain long-term success in the business.
#logistics software#freight software#freight forwarding software#software for freight forwarding software#wms#warehouse management system#freight logistics software#freight forwarder software#warehouse software#freight forwarding system
2 notes
·
View notes
Text
NASA and Boeing were forced to stand down from an attempted launch to the International Space Station on Monday because of a last-minute issue that cropped up with a valve on the spacecraft’s rocket.
Boeing’s Starliner capsule had been scheduled to lift off at 10:34 p.m. ET from Florida’s Cape Canaveral Space Force Station on its first crewed test flight. NASA astronauts Barry “Butch” Wilmore and Sunita Williams were on board the capsule and strapped into their seats when the launch attempt was called off, roughly two hours ahead of the planned liftoff.
NASA announced early Tuesday that a second attempt would occur no earlier than Friday.
Mission controllers declared Monday’s launch “scrub” after an anomaly was detected on a valve on United Launch Alliance’s Atlas V rocket, which the Starliner capsule was to ride into orbit.
United Launch Alliance officials said in a post on X that the launch attempt was scrapped “out of an abundance of caution for the safety of the flight and pad crew,” adding that the team needs “additional time to complete a full assessment.”
The analysis will include whether the pressure regulation valve, located on the rocket’s upper stage, needs to be replaced, which may cause a longer delay.
The crewed Starliner flight, when it occurs, will be a crucial final test before NASA can authorize Boeing to conduct routine flights to and from the space station.
Officials at NASA and Boeing have said safety is paramount for the spacecraft’s first flight with humans onboard.
The scrubbed launch is yet another setback for Boeing, which has already dealt with years of delays and budget overruns with its Starliner program. It has fallen significantly behind SpaceX, which has been flying crewed missions to and from the space station for NASA since 2020.
Both SpaceX’s Crew Dragon capsule and Boeing’s Starliner craft were developed as part of NASA’s Commercial Crew Program. The initiative began more than a decade ago, following the retirement of the agency’s space shuttles, to support private companies in building new space vehicles to take astronauts to low-Earth orbit.
Starliner’s first uncrewed flight in 2019 was thwarted by software issues, forcing mission controllers to cut the test short before the vehicle could attempt to rendezvous and dock with the ISS. A second attempt was then delayed several times by fuel valve issues, and it wasn’t until 2022 that Boeing was able to carry out a successful uncrewed flight to and from the space station.
11 notes
·
View notes