#aws cloudfront distribution
Explore tagged Tumblr posts
Text
Deliver your content worldwide at a high data transfer speed and avoid DDoS attacks with AWS CloudFront to boost the video viewing experience of users.
0 notes
Text
0 notes
Text
🎬 Entertainment App Development Services: Build the Future of Digital Entertainment
In a digital-first world where users stream, binge, listen, and share content 24/7, the demand for entertainment app development services is skyrocketing. Whether you're launching the next Netflix, Spotify, or a regional OTT platform, a powerful entertainment app can place your content at the fingertips of millions.
This blog explores everything you need to know about building a successful entertainment mobile app—features, tech stack, monetization models, and how the right development partner can turn your vision into a captivating, scalable reality.

📱 Why You Need an Entertainment App in 2025
The entertainment industry is undergoing a massive digital shift. With over 6.5 billion smartphone users globally, streaming content—whether video, music, or live performances—has become the new normal. Audiences demand convenience, personalization, and immersive experiences, all of which can be delivered through a well-developed mobile application.
From OTT platform development to podcast and music streaming apps, custom solutions are now essential for media brands, production houses, indie artists, and entertainment startups.
📈 Market Stats Worth Noting:
The global video streaming market is expected to surpass $920 billion by 2030.
Time spent on entertainment and media apps increased by 40% post-pandemic.
Subscription-based platforms like Netflix, Hotstar, and Gaana have seen record-breaking growth.
If you're in the business of content creation or distribution, now is the time to invest in expert entertainment app development services.
🛠️ Core Features of a Winning Entertainment App
To compete with giants like Netflix, Spotify, or Amazon Prime, your app must go beyond basic functionality. Here's what users expect from a top-tier entertainment mobile app:
1. Content Streaming (Video/Audio)
High-quality streaming with adaptive bitrate, low buffering, and seamless playback across devices.
2. User Profiles & Personalization
Smart algorithms that recommend content based on watch history, preferences, or listening habits.
3. Subscription & Monetization Models
Support for freemium access, in-app purchases, advertisements, and recurring subscriptions.
4. Search & Filter
Powerful content discovery with keyword search, genres, languages, trending content, and more.
5. Multi-Platform Access
Cross-platform compatibility (Android, iOS, smart TVs, tablets, etc.) with a unified user experience.
6. Offline Downloads
Let users enjoy content without internet access by enabling secure offline downloads.
7. Live Streaming
Incorporate live shows, concerts, or podcasts with real-time chat and engagement.
8. Push Notifications
Keep users engaged by notifying them about new releases, trending content, and personalized suggestions.
9. Social Sharing & Integration
Let users share what they watch or listen to on social media, enhancing app visibility and virality.
🧠 Choosing the Right Technology Stack
Behind every great entertainment app is a powerful and scalable tech architecture. Here's what a reliable entertainment app development company should offer:
➤ Frontend (Mobile App Development)
React Native / Flutter for cross-platform development
Swift (iOS) and Kotlin (Android) for native apps
Custom UI/UX based on Figma, XD, or Sketch
➤ Backend
Node.js, Laravel, or Django for scalable API architecture
MongoDB or PostgreSQL for content and user data
Real-time databases like Firebase for chat, notifications, and analytics
➤ Streaming & CDN
Integration with AWS CloudFront, Vimeo OTT, or Wowza
DRM support to prevent piracy
Adaptive Bitrate Streaming (HLS, MPEG-DASH)
➤ Analytics & Recommendation Engine
Firebase, Mixpanel, or Google Analytics for user behavior
AI-powered recommendation engine to boost engagement and retention
💰 Monetization Strategies for Entertainment Apps
Monetization is crucial. Your entertainment app can generate recurring revenue through several models:
🔒 Subscription (SVOD)
Offer access to premium content on a weekly, monthly, or annual basis.
🎯 Advertisement (AVOD)
Free content monetized through banner ads, interstitials, or video ads using Google AdMob or Facebook Audience Network.
📥 Pay-per-view
Ideal for exclusive concerts, movie releases, or premium shows.
💼 Freemium
Provide basic content for free while charging for access to premium features or shows.
🤝 Why Hire Expert Entertainment App Developers?
Entertainment apps are high-stakes projects. Performance issues, bugs, or poor user experience can lead to instant churn. Here’s why hiring a team with domain expertise in entertainment mobile app development is critical:
They understand media licensing, content management, and user behavior.
They can optimize infrastructure for millions of concurrent users.
They’re familiar with UI/UX best practices that align with binge-watching or continuous listening behaviors.
They offer post-launch support for updates, bug fixes, and user feedback handling.
A team like Kickass Developers, with expertise in custom mobile app development, OTT app development, and audio/video streaming, ensures your idea is executed with precision and long-term scalability.
🚀 Final Thoughts: Your Entertainment App Is the Future of Engagement
Whether you’re building a regional OTT app, a music discovery platform, or a niche video streaming service, your success hinges on the right blend of technology, UX, scalability, and speed to market.
Investing in experienced entertainment app development services is your first step toward captivating your audience, building loyalty, and driving recurring revenue.
📞 Ready to Build Your Entertainment App?
Looking for a team that understands the entertainment industry inside and out?
Kickass Developers specializes in designing custom, high-performance entertainment applications tailored to your audience, brand, and growth goals.
📧 Contact us today at [email protected] 🌐 Or visit us at kickassdevelopers.com
#Entertainment App Developers#OTT App Development#Video Streaming App Services#Music App Development#Android Entertainment App#iOS Video App#Podcast App Developers#Live Streaming App Development#Subscription App Development
3 notes
·
View notes
Text
Navigating the Cloud Landscape: Unleashing Amazon Web Services (AWS) Potential
In the ever-evolving tech landscape, businesses are in a constant quest for innovation, scalability, and operational optimization. Enter Amazon Web Services (AWS), a robust cloud computing juggernaut offering a versatile suite of services tailored to diverse business requirements. This blog explores the myriad applications of AWS across various sectors, providing a transformative journey through the cloud.

Harnessing Computational Agility with Amazon EC2
Central to the AWS ecosystem is Amazon EC2 (Elastic Compute Cloud), a pivotal player reshaping the cloud computing paradigm. Offering scalable virtual servers, EC2 empowers users to seamlessly run applications and manage computing resources. This adaptability enables businesses to dynamically adjust computational capacity, ensuring optimal performance and cost-effectiveness.
Redefining Storage Solutions
AWS addresses the critical need for scalable and secure storage through services such as Amazon S3 (Simple Storage Service) and Amazon EBS (Elastic Block Store). S3 acts as a dependable object storage solution for data backup, archiving, and content distribution. Meanwhile, EBS provides persistent block-level storage designed for EC2 instances, guaranteeing data integrity and accessibility.
Streamlined Database Management: Amazon RDS and DynamoDB
Database management undergoes a transformation with Amazon RDS, simplifying the setup, operation, and scaling of relational databases. Be it MySQL, PostgreSQL, or SQL Server, RDS provides a frictionless environment for managing diverse database workloads. For enthusiasts of NoSQL, Amazon DynamoDB steps in as a swift and flexible solution for document and key-value data storage.
Networking Mastery: Amazon VPC and Route 53
AWS empowers users to construct a virtual sanctuary for their resources through Amazon VPC (Virtual Private Cloud). This virtual network facilitates the launch of AWS resources within a user-defined space, enhancing security and control. Simultaneously, Amazon Route 53, a scalable DNS web service, ensures seamless routing of end-user requests to globally distributed endpoints.
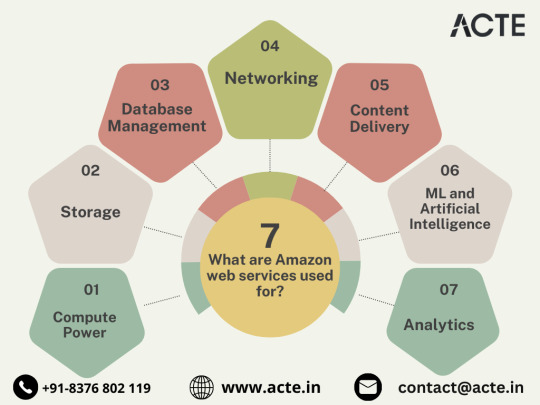
Global Content Delivery Excellence with Amazon CloudFront
Amazon CloudFront emerges as a dynamic content delivery network (CDN) service, securely delivering data, videos, applications, and APIs on a global scale. This ensures low latency and high transfer speeds, elevating user experiences across diverse geographical locations.
AI and ML Prowess Unleashed
AWS propels businesses into the future with advanced machine learning and artificial intelligence services. Amazon SageMaker, a fully managed service, enables developers to rapidly build, train, and deploy machine learning models. Additionally, Amazon Rekognition provides sophisticated image and video analysis, supporting applications in facial recognition, object detection, and content moderation.
Big Data Mastery: Amazon Redshift and Athena
For organizations grappling with massive datasets, AWS offers Amazon Redshift, a fully managed data warehouse service. It facilitates the execution of complex queries on large datasets, empowering informed decision-making. Simultaneously, Amazon Athena allows users to analyze data in Amazon S3 using standard SQL queries, unlocking invaluable insights.
In conclusion, Amazon Web Services (AWS) stands as an all-encompassing cloud computing platform, empowering businesses to innovate, scale, and optimize operations. From adaptable compute power and secure storage solutions to cutting-edge AI and ML capabilities, AWS serves as a robust foundation for organizations navigating the digital frontier. Embrace the limitless potential of cloud computing with AWS – where innovation knows no bounds.
3 notes
·
View notes
Text
Your Journey Through the AWS Universe: From Amateur to Expert
In the ever-evolving digital landscape, cloud computing has emerged as a transformative force, reshaping the way businesses and individuals harness technology. At the forefront of this revolution stands Amazon Web Services (AWS), a comprehensive cloud platform offered by Amazon. AWS is a dynamic ecosystem that provides an extensive range of services, designed to meet the diverse needs of today's fast-paced world.

This guide is your key to unlocking the boundless potential of AWS. We'll embark on a journey through the AWS universe, exploring its multifaceted applications and gaining insights into why it has become an indispensable tool for organizations worldwide. Whether you're a seasoned IT professional or a newcomer to cloud computing, this comprehensive resource will illuminate the path to mastering AWS and leveraging its capabilities for innovation and growth. Join us as we clarify AWS and discover how it is reshaping the way we work, innovate, and succeed in the digital age.
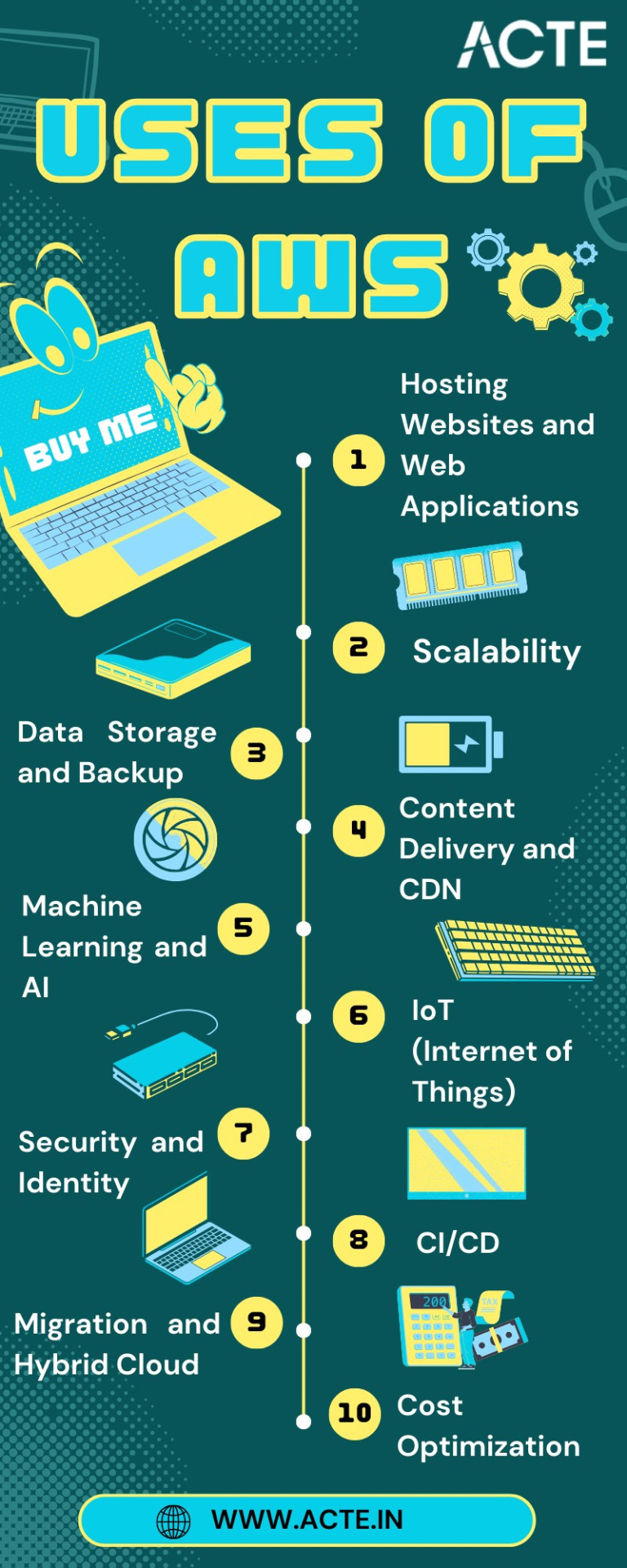
Navigating the AWS Universe:
Hosting Websites and Web Applications: AWS provides a secure and scalable place for hosting websites and web applications. Services like Amazon EC2 and Amazon S3 empower businesses to deploy and manage their online presence with unwavering reliability and high performance.
Scalability: At the core of AWS lies its remarkable scalability. Organizations can seamlessly adjust their infrastructure according to the ebb and flow of workloads, ensuring optimal resource utilization in today's ever-changing business environment.
Data Storage and Backup: AWS offers a suite of robust data storage solutions, including the highly acclaimed Amazon S3 and Amazon EBS. These services cater to the diverse spectrum of data types, guaranteeing data security and perpetual availability.
Databases: AWS presents a panoply of database services such as Amazon RDS, DynamoDB, and Redshift, each tailored to meet specific data management requirements. Whether it's a relational database, a NoSQL database, or data warehousing, AWS offers a solution.
Content Delivery and CDN: Amazon CloudFront, AWS's content delivery network (CDN) service, ushers in global content distribution with minimal latency and blazing data transfer speeds. This ensures an impeccable user experience, irrespective of geographical location.
Machine Learning and AI: AWS boasts a rich repertoire of machine learning and AI services. Amazon SageMaker simplifies the development and deployment of machine learning models, while pre-built AI services cater to natural language processing, image analysis, and more.
Analytics: In the heart of AWS's offerings lies a robust analytics and business intelligence framework. Services like Amazon EMR enable the processing of vast datasets using popular frameworks like Hadoop and Spark, paving the way for data-driven decision-making.
IoT (Internet of Things): AWS IoT services provide the infrastructure for the seamless management and data processing of IoT devices, unlocking possibilities across industries.
Security and Identity: With an unwavering commitment to data security, AWS offers robust security features and identity management through AWS Identity and Access Management (IAM). Users wield precise control over access rights, ensuring data integrity.
DevOps and CI/CD: AWS simplifies DevOps practices with services like AWS CodePipeline and AWS CodeDeploy, automating software deployment pipelines and enhancing collaboration among development and operations teams.
Content Creation and Streaming: AWS Elemental Media Services facilitate the creation, packaging, and efficient global delivery of video content, empowering content creators to reach a global audience seamlessly.
Migration and Hybrid Cloud: For organizations seeking to migrate to the cloud or establish hybrid cloud environments, AWS provides a suite of tools and services to streamline the process, ensuring a smooth transition.
Cost Optimization: AWS's commitment to cost management and optimization is evident through tools like AWS Cost Explorer and AWS Trusted Advisor, which empower users to monitor and control their cloud spending effectively.
In this comprehensive journey through the expansive landscape of Amazon Web Services (AWS), we've embarked on a quest to unlock the power and potential of cloud computing. AWS, standing as a colossus in the realm of cloud platforms, has emerged as a transformative force that transcends traditional boundaries.
As we bring this odyssey to a close, one thing is abundantly clear: AWS is not merely a collection of services and technologies; it's a catalyst for innovation, a cornerstone of scalability, and a conduit for efficiency. It has revolutionized the way businesses operate, empowering them to scale dynamically, innovate relentlessly, and navigate the complexities of the digital era.
In a world where data reigns supreme and agility is a competitive advantage, AWS has become the bedrock upon which countless industries build their success stories. Its versatility, reliability, and ever-expanding suite of services continue to shape the future of technology and business.
Yet, AWS is not a solitary journey; it's a collaborative endeavor. Institutions like ACTE Technologies play an instrumental role in empowering individuals to master the AWS course. Through comprehensive training and education, learners are not merely equipped with knowledge; they are forged into skilled professionals ready to navigate the AWS universe with confidence.
As we contemplate the future, one thing is certain: AWS is not just a destination; it's an ongoing journey. It's a journey toward greater innovation, deeper insights, and boundless possibilities. AWS has not only transformed the way we work; it's redefining the very essence of what's possible in the digital age. So, whether you're a seasoned cloud expert or a newcomer to the cloud, remember that AWS is not just a tool; it's a gateway to a future where technology knows no bounds, and success knows no limits.
6 notes
·
View notes
Text
AWS Training Course – Master Cloud Computing with Softcrayons
AWS training course | AWS training institute | AWS course certificate
Cloud computing has transformed how companies function and provide services in the current technological age. Amazon Web Services (AWS) is a prominent global player in cloud platforms, helping Fortune 500 businesses as well as small startups. Enrolling in Softcrayons' AWS training course is the ideal option if you want to develop a successful professional life in cloud computing by receiving certification and skills that are useful to the sector.

Why Choose the AWS Training Course at Softcrayons?
Softcrayons' AWS training course has been created to provide students, IT workers, and job seekers with the skills they require for success in the fast-growing cloud computing industry. Through practical instruction, real-world projects, and guidance from professionals, this course is designed to provide students an in-depth knowledge of AWS architecture, services, and best practices.
Key highlights of our AWS course include:
Training by certified AWS professionals with years of experience
Interactive classroom and online sessions
Practical lab exercises and real-time AWS projects
Preparation for global AWS certifications
Resume-building and placement support
Flexible schedules with weekend and weekday batches
Affordable fee structure with EMI options
Whether you're a beginner or a professional, Softcrayons ensures you get real value from your learning experience.
Understanding AWS – A Leading Cloud Platform
AWS is a large and dynamic cloud platform providing more than 200 feature-rich services from data centers around the globe. Compute power, database storage, content distribution, and security are among the reliable, flexible, and affordable cloud solutions it delivers.
Some of the most widely used AWS services include:
Amazon EC2 (Elastic Compute Cloud) – Virtual servers for running applications
Amazon S3 (Simple Storage Service) – Secure, scalable cloud storage
Amazon RDS (Relational Database Service) – Managed database hosting
AWS Lambda – Serverless computing for running code without managing servers
Amazon VPC (Virtual Private Cloud) – Isolated network for your cloud resources
IAM (Identity and Access Management) – Access control and security management
With its wide adoption and market leadership, AWS is an essential skill for IT professionals today.
Who Should Join the AWS Training Course?
The AWS training course at Softcrayons is suitable for a diverse range of learners, including:
Students pursuing a career in cloud computing
Software developers and IT professionals
Network and system administrators
DevOps engineers
Technical leads and consultants
Business analysts working on cloud-based products
The course starts from the basics and gradually progresses to advanced AWS concepts, making it suitable for both beginners and experienced professionals.
AWS Course Curriculum at Softcrayons
The curriculum is meticulously designed to cover all essential AWS services, tools, and real-time applications. It is aligned with the official AWS certification standards and regularly updated to match current trends.
Module 1: Introduction to Cloud Computing & AWS
Overview of Cloud Computing
Public, Private, and Hybrid Clouds
AWS Global Infrastructure
Overview of Key AWS Services
Module 2: Identity and Access Management (IAM)
User and Group Management
Policies and Roles
Security Best Practices
Module 3: Amazon EC2 and Elastic Load Balancing
Launching and Managing EC2 Instances
EBS Volumes and AMIs
Load Balancers and Auto Scaling
Module 4: Amazon S3 and CloudFront
Creating and Managing S3 Buckets
Object Versioning and Lifecycle Policies
Content Delivery with CloudFront
Module 5: AWS Database Services
Introduction to Amazon RDS and DynamoDB
Database Deployment and Configuration
High Availability and Backups
Module 6: Virtual Private Cloud (VPC)
Subnetting, Routing, and Internet Gateways
Network ACLs and Security Groups
NAT Gateway and VPN Connections
Module 7: AWS Lambda and Serverless Computing
Building and Deploying Lambda Functions
Event-Driven Architecture
Integrating with Other AWS Services
Module 8: Monitoring, Logging, and Automation
CloudWatch Metrics and Logs
CloudTrail for Auditing
Using the AWS CLI and SDKs
Module 9: AWS Certification Preparation
Exam Blueprint and Objectives
Sample Questions and Practice Tests
Mock Interviews and Case Studies
Real-Time Projects and Hands-On Experience
Throughout the course, you will work on industry-oriented projects that reinforce your understanding and help build your portfolio. Projects include:
Hosting a static website using S3 and CloudFront
Deploying a scalable web application with EC2 and Load Balancers
Creating a serverless application using Lambda and API Gateway
Implementing a secure VPC with public and private subnets
These projects help bridge the gap between theoretical knowledge and real-world implementation.
Certification Preparation and Career Support
One of the main goals of our AWS training course is to prepare students for official AWS certifications. These globally recognized credentials validate your skills and make you a preferred candidate for cloud-based roles.
Certifications covered include:
AWS Certified Cloud Practitioner
AWS Certified Solutions Architect – Associate
AWS Certified Developer – Associate
AWS Certified SysOps Administrator – Associate
After completing the training, our team also assists with career counseling, resume writing, interview preparation, and job referrals, ensuring you are fully prepared for cloud job opportunities.
Career Opportunities After AWS Training
Cloud computing is one of the fastest-growing industries, and AWS is the most in-demand cloud platform worldwide. With companies shifting their infrastructure to the cloud, skilled AWS professionals are in high demand across all industries.
Popular job roles include:
AWS Cloud Engineer
Solutions Architect
Cloud Consultant
DevOps Engineer
Cloud Administrator
System Operations Specialist
Entry-level professionals can start with competitive salaries, and experienced AWS-certified candidates often earn high-paying roles across the globe.
Why Softcrayons is Your Ideal AWS Training Partner
Softcrayons Tech Solution has built a reputation as a trusted training institute with a student-first approach. With experienced mentors, well-structured content, and a strong placement record, we are committed to helping learners transform their careers through high-quality education.
Benefits of learning AWS from Softcrayons:
Updated curriculum tailored for real-world applications
Live training with 1-on-1 doubt-solving sessions
Practical projects to boost your hands-on experience
Continuous support and placement guidance
Learning-friendly environment and expert faculty
Whether you choose classroom or online sessions, Softcrayons ensures you learn with clarity, confidence, and convenience.
Start Your Cloud Journey Today
The future is cloud-native, and AWS is the key to unlocking new career possibilities. Enroll in the AWS training course at Softcrayons and step into a world of exciting cloud opportunities. With expert mentorship, practical skills, and recognized certification preparation, this course is your gateway to a high-growth cloud computing career. Contact us
0 notes
Text
Content Delivery Network Market: Elevating Online Performance Across E-commerce and OTT
The Content Delivery Network Market Size was valued at USD 21.5 billion in 2023 and is expected to reach USD 85.6 billion by 2032, growing at a CAGR of 16.6% over the forecast period of 2024-2032.
Content Delivery Network Market is witnessing robust expansion as the demand for high-speed, secure, and scalable digital content delivery surges across industries. With the rapid proliferation of video streaming, cloud gaming, remote work, and e-commerce, CDNs are becoming critical to ensure seamless digital experiences globally.
U.S. Market Continues to Lead in CDN Innovation and Adoption
Content Delivery Network Market continues to grow as enterprises prioritize performance, availability, and cybersecurity for content distribution. Providers are enhancing capabilities with edge computing, AI-based traffic management, and adaptive streaming to cater to rising user expectations.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/2636
Market Keyplayers:
Akamai Technologies, Inc. (Akamai Edge, Akamai Adaptive Media Delivery)
Cloudflare, Inc. (Cloudflare CDN, Cloudflare Stream)
Amazon Web Services (AWS) (Amazon CloudFront, AWS Elemental MediaStore)
Google LLC (Google Cloud CDN, Google Media CDN)
Microsoft Corporation (Azure CDN, Azure Front Door)
Limelight Networks, Inc. (EdgeFunctions, Limelight Realtime Streaming)
Fastly, Inc. (Fastly Compute@Edge, Fastly Image Optimization)
CDNetworks (Cloud Security CDN, Cloud Web Acceleration)
Alibaba Cloud (Alibaba Global Accelerator, Alibaba CDN)
Imperva, Inc. (Imperva CDN, Imperva Cloud Application Protection)
Market Analysis
The CDN market is driven by the escalating need for real-time content delivery across multiple devices and geographies. Enterprises across sectors—media, retail, finance, and education—are adopting CDNs to optimize load times, reduce latency, and safeguard data against evolving cyber threats. In the U.S., large-scale digital adoption and innovation from cloud service providers are accelerating market penetration. Meanwhile, Europe is showing strong growth backed by digital infrastructure upgrades and regulatory support for data sovereignty.
Market Trends
Shift toward edge computing for faster content processing closer to end-users
Growing adoption of AI and machine learning to optimize traffic routing
Integration with cybersecurity tools for DDoS protection and threat mitigation
Rapid expansion of video-on-demand and live streaming services
Increasing use of multi-CDN strategies for failover and performance optimization
Rising demand for mobile content delivery and 5G-driven acceleration
Market Scope
As global content consumption accelerates, the Content Delivery Network Market continues to broaden its reach across industries and regions. CDNs are no longer optional—they’re an integral component of modern digital infrastructure.
High scalability for enterprises managing global audiences
Real-time analytics and content optimization
Enhanced performance in high-traffic regions
Custom delivery strategies for e-learning, OTT, and gaming platforms
API-driven delivery for dynamic web applications
Support for regulatory compliance (e.g., GDPR, CCPA)
Forecast Outlook
The Content Delivery Network Market is on track for sustained growth fueled by surging digital media usage and rising enterprise expectations for speed and security. As CDNs evolve from content accelerators to intelligent delivery ecosystems, their value will only intensify. Innovations like AI-powered caching, real-time analytics, and edge services will define the next phase of expansion across the U.S., Europe, and beyond.
Access Complete Report: https://www.snsinsider.com/reports/content-delivery-network-market-2636
Conclusion
In an age where milliseconds impact user engagement, the Content Delivery Network Market is empowering organizations to stay fast, available, and resilient. As digital experiences evolve, CDNs are no longer a backend utility—they’re a competitive advantage. For businesses aiming to lead in the digital-first world, investing in agile, secure, and intelligent content delivery infrastructure is not just smart—it’s essential.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Related Reports:
U.S.A set to witness robust adoption of Data Pipeline Tools amid growing demand for real-time analytics
U.S.A Product Analytics Market Booms with Rising Demand for Data-Driven Customer Insights
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
Mail us: [email protected]
0 notes
Text
Common Configuration Mistakes in AWS Web Application Firewall
AWS Web Application Firewall (WAF) is a powerful tool for protecting web applications from common threats. However, configuration mistakes can leave vulnerabilities unaddressed or lead to service disruptions. Missteps such as improper rule ordering, insufficient logging, or overly broad IP blocking are frequent. These errors compromise performance, increase costs, or weaken security. Understanding and avoiding these common AWS WAF configuration mistakes is critical to building a secure, resilient application infrastructure that effectively defends against evolving cyber threats.
Misconfigured Rule Priorities
One common mistake when setting up AWS Web Application Firewall is misconfiguring rule priorities. AWS WAF evaluates rules in the order of priority, from lowest to highest. If a broad rule is given a higher priority than a more specific rule, it can override intended protections or allow unwanted traffic. This can lead to security gaps or false positives. Ensuring the correct order of evaluation is crucial for the AWS Web Application Firewall to function effectively and secure web applications properly.
Incorrect Rule Priority Ordering
One of the most common mistakes in AWS WAF is misordering rules. AWS WAF evaluates rules in order of priority, and if a broad or default rule is placed before a specific one, it may override or negate more tailored protections. For example, placing a general allow rule above a SQL injection filter could let malicious traffic through. Always review rule hierarchy to ensure that specific, critical rules take precedence and achieve the intended security outcomes.
Overly Broad IP Blocking
Blocking entire IP ranges without proper analysis can lead to unintentional denial of service to legitimate users. Often, administrators block ranges after observing suspicious activity without fully understanding the scope of those addresses. This practice can backfire, especially when the blocked range includes cloud or mobile users. Instead, IP blocking should be narrowly defined and used as a last resort, with traffic behavior analyzed in context using AWS logs and threat intelligence.
Lack of Logging and Monitoring
Failing to enable logging and monitoring significantly reduces visibility into how AWS WAF is performing. Without logging to Amazon Kinesis or CloudWatch, organizations can’t identify trends, debug rule matches, or fine-tune their configurations. Regular log reviews help detect false positives or missed threats. Continuous monitoring also supports compliance and audit requirements. Enabling logging from the outset and setting up relevant dashboards is essential for effective threat detection and response.
Improper Use of Rate-Based Rules
Rate-based rules help mitigate DDoS attacks by limiting requests from IPs exceeding a set threshold. However, misconfiguring these thresholds can block legitimate traffic, especially during traffic spikes like product launches or promotions. Alternatively, setting the rate limit too high may fail to prevent malicious behavior. These rules must be fine-tuned based on normal traffic patterns and tested in staging environments to avoid disrupting user access while maintaining adequate protection.
Neglecting Rule Testing Before Deployment
Applying changes directly to production without testing can introduce vulnerabilities or cause unexpected behavior. AWS WAF provides the option to deploy rules in “count” mode, allowing administrators to observe their impact before enforcement. Skipping this phase can result in blocked legitimate traffic or undetected threats. Always test new rules or changes in a controlled environment to understand their implications and ensure they operate as intended.
Misconfigured Web ACL Associations
A common oversight is incorrect or missing association of Web ACLs (Access Control Lists) with the intended AWS resources, such as CloudFront distributions, ALBs, or APIs. Without proper linkage, the WAF rules won’t apply, leaving applications exposed. Additionally, associating a single ACL with multiple unrelated applications can cause rule conflicts. Review all ACL associations carefully and use dedicated ACLs for different workloads to maintain clarity and effectiveness.
Ignoring Managed Rule Set Customization
AWS offers managed rule sets from AWS and third-party vendors, but relying on them without customization can lead to gaps in protection or unnecessary false positives. These rules should be evaluated and adjusted to fit your application’s specific architecture and traffic patterns. Tailoring managed rules enhances performance and ensures relevance to your threat model. Always supplement managed rules with custom rules based on your application’s unique needs.
Conclusion
Avoiding common AWS WAF configuration mistakes is crucial for securing web applications without disrupting service. Proper rule ordering, precise targeting, and regular monitoring are key practices. When managed thoughtfully, AWS WAF can provide a strong defense against web threats. By continuously refining configurations and staying informed about emerging risks, organizations can maximize protection and minimize performance issues in their cloud environments.
0 notes
Text
CDNs Explained: How Development Agencies Use Them to Improve Site Speed
When it comes to building high-performing websites, speed is more than a luxury—it’s a necessity. Faster websites improve user experience, boost search rankings, and increase conversion rates. One of the most effective tools web developers use to achieve this is a Content Delivery Network (CDN).
A skilled Web Development Company will often integrate CDNs into your site architecture to make your website faster, more reliable, and globally accessible. But what exactly is a CDN, and how does it work behind the scenes to enhance your website’s performance?
Let’s break it down.
What Is a CDN?
A Content Delivery Network (CDN) is a network of servers distributed across different geographical locations. These servers are strategically placed to deliver website content (like images, videos, JavaScript, CSS files, and even HTML pages) from a server that is closest to the user’s location.
Instead of making every user fetch content from your original web host (which might be in one part of the world), CDNs replicate and serve it from edge servers globally. The result? Reduced latency, faster page load times, and less strain on your origin server.
Why Site Speed Matters So Much
Before diving into how development teams use CDNs, it’s important to understand why speed matters:
Improved SEO: Google considers page speed as a ranking factor.
Better User Experience: Users expect pages to load in under 3 seconds.
Higher Conversions: Faster websites see lower bounce rates and higher sales.
Lower Server Costs: Offloading static assets to a CDN can reduce bandwidth consumption and hosting costs.
Slow websites frustrate users and search engines alike—making speed optimization a core responsibility of any web development project.
How Web Development Agencies Use CDNs Effectively
Professional development teams don’t just plug in a CDN—they configure and optimize it strategically based on the website’s structure, target audience, and traffic patterns. Here’s how:
1. Serving Static Content from Edge Locations
CDNs are perfect for delivering static content—things like images, videos, CSS stylesheets, fonts, and JavaScript files. Development teams configure CDNs like Cloudflare, AWS CloudFront, or Akamai to cache these assets and serve them from the nearest server to the end user.
This reduces the time it takes for content to travel across the internet, especially for international audiences.
2. Reducing Time to First Byte (TTFB)
TTFB is the time it takes for the first bit of data to reach a user’s browser after making a request. A long TTFB can drag down your site speed—even if everything else is optimized.
CDNs reduce TTFB by minimizing the distance between the user and the server. Development teams monitor this closely and use CDN logs and analytics to optimize performance over time.
3. Image and Media Optimization
CDNs often come with built-in media optimization features. Developers can enable:
Automatic image compression
Next-gen formats like WebP
Responsive resizing based on device
Instead of hosting large, unoptimized media files, the CDN handles compression and resizing on the fly—freeing up your core server and delivering content faster.
4. Handling High Traffic Volumes
When your site experiences a surge in traffic—whether from a marketing campaign, sale, or product launch—your main server can get overwhelmed.
CDNs absorb much of this traffic by handling asset delivery, freeing up your origin server to focus on dynamic requests like form submissions, shopping cart updates, or user logins.
5. Improving Global Reach
If your audience is spread across continents, you don’t want users in Asia or Europe waiting for content hosted in the U.S. A CDN ensures they access a version of your site from a local or nearby server, drastically improving loading times and consistency around the world.
6. Added Layer of Security
Many CDNs offer DDoS protection, firewall rules, and bot filtering features. Development teams configure these security layers through the CDN’s dashboard, ensuring that your site is not only fast—but also safe.
This is especially crucial for eCommerce sites, fintech platforms, or any website dealing with sensitive customer data.
Conclusion
In the modern web ecosystem, speed and performance are no longer optional—they're expected. CDNs play a critical role in meeting those expectations by delivering content faster, more securely, and with better reliability.
A professional Web Development Company knows how to implement and fine-tune CDN integration to ensure your site performs optimally across devices and geographies. From serving static content and reducing TTFB to scaling under pressure and protecting against threats, CDNs have become essential to modern web development success.
0 notes
Text
How to prevent a DDoS attack
"Securing Your Cloud Infrastructure: Proven DDoS Prevention Methods"
Introduction
Distributed Denial of Service (DDoS) attacks represent one of the most persistent and evolving threats in cybersecurity. At CloudMinister Technologies, we implement a robust, multi-faceted defense strategy to protect our clients' digital assets. This guide provides an exhaustive examination of our DDoS prevention methodology, detailing the technical implementation and strategic rationale behind each protective measure.
1. Cloud-Based DDoS Protection Services: Technical Implementation
Architecture and Operation
Our cloud-based DDoS protection operates through a distributed network of scrubbing centers that process all incoming traffic before it reaches client infrastructure. The system employs:
Deep Packet Inspection (DPI): Analyzes packet headers and payloads to identify malicious patterns
Behavioral Analysis Engines: Establish baseline traffic profiles for each client environment
Real-time Signature Matching: Compares traffic against known attack signatures
Platform-Specific Implementations
AWS Shield Advanced:
Integrated with Amazon CloudFront, Route 53, and Elastic Load Balancing
Provides always-on detection of network layer (Layer 3/4) attacks
Custom mitigations for application layer (Layer 7) attacks
Azure DDoS Protection:
Leverages Azure's global network infrastructure
Implements adaptive real-time mitigation policies
Provides attack analytics through Azure Monitor
Third-Party Solutions (Cloudflare/Akamai):
Anycast network architecture disperses attack traffic
TLS termination at edge locations reduces origin server load
Custom rulesets for industry-specific protection
2. Web Application Firewall (WAF) Configuration Details
Rule Set Composition
Our WAF deployments utilize a layered ruleset approach:
Foundation Rules:
OWASP Core Rule Set (CRS) 3.3
Protocol compliance checks
HTTP request validation
Custom Rules:
Application-specific allowlists
Business logic protection
API endpoint security
Rate Limiting Policies:
Granular controls by:
IP address
Session tokens
Geographic location
Dynamic adjustments based on traffic patterns
Bot Mitigation Techniques
JavaScript challenge verification
TLS fingerprinting
Behavioral analysis of mouse movements and interaction patterns
Progressive hardening for persistent threats
3. Advanced Traffic Monitoring Systems
Data Collection Framework
NetFlow/sFlow/IPFIX: Sampled at 1:1 ratio during normal operations, increasing to 1:10 during attacks
Packet Capture: Triggered by anomaly detection for forensic analysis
Log Aggregation: Centralized collection from all network devices
Analytics Pipeline
Pre-processing:
Traffic normalization
Feature extraction
Machine Learning Models:
Isolation Forest for anomaly detection
LSTM networks for time-series prediction
Supervised classifiers for attack categorization
Decision Engine:
Confidence thresholding
Mitigation action selection
4. Scalable Infrastructure Design Principles
Auto-scaling Implementation
Horizontal Scaling:
Instance groups with pre-warmed pools
Predictive scaling based on historical patterns
Vertical Scaling:
Dynamic resource allocation
Hot standby instances
Load Balancing Strategies
Geographic Load Distribution:
DNS-based geolocation routing
Anycast IP implementation
Application-Aware Routing:
Content-based routing
Session persistence management
5. Zero Trust Architecture Components
Network Segmentation Model
Micro-perimeter Creation:
Software-defined perimeters
Per-workload firewalls
Traffic Flow Policies:
East-west traffic controls
Default-deny posture
Access Control Mechanisms
Identity Verification:
Multi-factor authentication
Device attestation
Policy Enforcement:
Attribute-based access control
Just-in-time privilege elevation
6. Incident Response Protocol
Attack Mitigation Workflow
Detection Phase:
Threshold crossing alerts
Correlation engine output
Containment Phase:
BGP flow-spec announcements
On-premise scrubbing activation
Recovery Phase:
Traffic normalization monitoring
Post-mortem analysis
Forensic Investigation Process
Attack timeline reconstruction
Malicious payload analysis
Attacker attribution techniques
Countermeasure effectiveness evaluation
Conclusion
CloudMinister Technologies' DDoS protection framework combines cutting-edge technologies with proven security practices to deliver comprehensive protection. Our defense-in-depth approach addresses all layers of potential attack vectors while maintaining operational flexibility and performance.
We offer customized security assessments and implementation services for organizations seeking enterprise-grade DDoS protection. Contact our security team to discuss your specific requirements.
Take the Next Step
Contact CloudMinister today for a free cloud security assessment or to learn more about our advanced DDoS protection solutions.
Visit www.cloudminister.com or speak to one of our security specialists
0 notes
Text
10 Real-World Use Cases for AWS Web Application Firewall
AWS Web Application Firewall is a powerful tool designed to protect web applications from common threats and vulnerabilities. It helps organizations secure their digital assets by filtering and monitoring requests based on customizable rules. From blocking malicious bots to preventing SQL injection and cross-site scripting,AWS WAF offers robust protection for modern cloud applications. In this blog, we’ll explore 10 real-world use cases that demonstrate how businesses of all sizes leverage AWS WAF to enhance security, maintain compliance, and improve application availability ensuring that their websites and APIs remain safe from evolving cyber threats.
Protecting E-Commerce Websites from SQL Injection and XSS Attacks AWS Web Application Firewall
E-commerce platforms are prime targets for cyberattacks, especially SQL injection and cross-site scripting.AWS Web Application Firewall provides real-time filtering and customizable rules that block malicious payloads before they reach your web applications. By integrating AWS WAF with Amazon CloudFront or Application Load Balancer, businesses can ensure customer data, payment information, and inventory databases remain secure. This protection is crucial during high-traffic periods like Black Friday or seasonal sales, where downtime or a breach can lead to massive revenue loss. AWS WAF helps maintain trust, uptime, and compliance with industry standards like PCI-DSS.
Defending Financial AWS Web Application Firewall Against Bot Traffic
Financial institutions face continuous threats from malicious bots trying to perform credential stuffing, scraping, or brute-force attacks.AWS Web Application Firewall bot control feature identifies and mitigates unwanted bot traffic without disrupting legitimate users. This ensures that sensitive systems, such as online banking portals or investment platforms, stay resilient under pressure. With AWS WAF, financial apps can implement rate limiting, challenge-based CAPTCHA, and custom rules to block non-human actors in real time. By securing endpoints and APIs, financial services can protect user accounts and uphold service availability across digital platforms.
Securing APIs for Mobile and AWS Web Application Firewall
Modern applications rely heavily on APIs to enable communication between services and devices. These endpoints, however, are attractive attack vectors.AWS Web Application Firewall secures RESTful APIs hosted on API Gateway or Application Load Balancer by inspecting incoming requests and applying threat mitigation rules. Whether it's preventing schema manipulation, enforcing IP restrictions, or validating request patterns, AWS WAF ensures that only safe, well-formed API calls are processed. This is especially important for industries like healthcare and logistics, where API integrity directly impacts operational efficiency and data privacy.
Blocking Geo-Based Threats in Media and Entertainment Platforms AWS Web Application Firewall
Streaming services and content platforms often need to restrict access based on geographic location, either for licensing compliance or security.AWS Web Application Firewall enables geo-restriction rules that block or allow traffic based on the user's country of origin. This prevents unauthorized users from accessing premium or region-specific content. It also helps mitigate attacks that originate from high-risk regions. Media companies can easily manage distribution rights, reduce piracy, and maintain viewer experience across global markets using AWS WAF’s robust geo-blocking capabilities.
Preventing DDoS Attacks on Government Portals AWS Web Application Firewall
Government websites are frequent targets of Distributed Denial of Service attacks designed to disrupt public services.When paired with AWS Shield,AWS Web Application Firewall provides a resilient line of defense by filtering malicious requests before they can flood the backend systems. Custom rate-based rules and IP blacklists help reduce the impact of volumetric and application-layer DDoS attacks. By protecting critical portals such as tax services, election information sites, and public health resources AWS WAF helps ensure operational continuity, especially during high-demand periods or national events.
Enhancing Security for SaaS Platforms AWS Web Application Firewall
Software-as-a-Service providers must offer secure, multi-tenant environments where user isolation and data integrity are non-negotiable.AWS Web Application Firewall enables SaaS companies to define tenant-specific rules, monitor traffic patterns, and prevent malicious activities such as account enumeration or abuse of trial sign-ups. With support for real-time logging and integration with AWS services like CloudWatch and Lambda, security teams can respond quickly to anomalies. This allows SaaS businesses to scale securely while maintaining user confidence and compliance with data protection regulations.Enforcing Compliance for Healthcare Applications
Enforcing Compliance for Healthcare AWS Web Application Firewall
Healthcare applications must comply with strict regulations such as HIPAA,which demand robust security measures.AWS Web Application Firewall supports these requirements by protecting web applications against common vulnerabilities and unauthorized access. It offers fine-grained control over traffic and helps monitor threats in real-time, ensuring that only validated requests are processed. With logging and metrics integration, healthcare organizations can audit activity and demonstrate regulatory compliance. From patient portals to telemedicine platforms, AWS WAF plays a key role in safeguarding sensitive health data while supporting modern digital healthcare services.
Conclusion
AWS Web Application Firewall proves its value across a wide range of real-world scenarios, from protecting eCommerce platforms against SQL injection to securing APIs in financial applications. Its flexibility allows organizations to tailor rules for specific threats, ensuring robust protection without sacrificing performance.Whether mitigating DDoS attacks, enforcing geo-blocking, or managing bot traffic,AWS WAF provides scalable, cost-effective defense. These ten use cases highlight how businesses across industries can leverage AWS WAF to strengthen their security posture, meet compliance requirements, and deliver safer user experiences. It's a vital tool for any modern application operating in today’s complex threat landscape.
0 notes
Text
Implementing AWS Web Application Firewall for Robust Protection
Implementing AWS Web Application Firewall (WAF) offers robust protection for web applications by filtering and monitoring HTTP(S) traffic to safeguard against common threats like SQL injection and cross-site scripting (XSS). This managed service integrates seamlessly with AWS services such as Amazon CloudFront, Application Load Balancer, and API Gateway, providing a scalable and cost-effective solution for application security. To ensure effective deployment, it's recommended to test WAF rules in a staging environment using count mode before applying them in production. Additionally, enabling detailed logging through Amazon CloudWatch or Amazon S3 can aid in monitoring and compliance. Regularly updating and customizing WAF rules to align with specific application needs further enhances security posture. For organizations seeking comprehensive application-level security, leveraging AWS WAF in conjunction with services like Edgenexus Limited's Web Application Firewall can provide layered defense against evolving cyber threats.
The Importance of AWS Web Application Firewall
AWS WAF is a managed service that helps protect web applications from common web exploits that could affect application availability, compromise security, or consume excessive resources. By filtering and monitoring HTTP and HTTPS requests, AWS WAF allows you to control access to your content. Implementing AWS WAF enables businesses to defend against threats such as SQL injection, cross-site scripting (XSS), and other OWASP Top 10 vulnerabilities. This proactive approach to security is essential for maintaining the integrity and availability of web applications.
Key Features of AWS Web Application Firewall
AWS WAF offers several features that enhance web application security. It provides customizable rules to block common attack patterns, such as SQL injection or cross-site scripting. Additionally, AWS WAF allows for rate-based rules to mitigate DDoS attacks and bot traffic. Integration with AWS Shield Advanced provides an additional layer of protection against larger-scale attacks. Furthermore, AWS WAF's logging capabilities enable detailed monitoring and analysis of web traffic, facilitating quick identification and response to potential threats.
Best Practices for Implementing AWS Web Application Firewall
When implementing AWS WAF, it's crucial to follow best practices to ensure optimal protection. Start by defining a baseline of normal application traffic to identify anomalies. Utilize AWS Managed Rules to protect against common threats and customize them to fit your application's specific needs. Regularly update and review your WAF rules to adapt to emerging threats. Additionally, integrate AWS WAF with AWS CloudWatch for real-time monitoring and alerting, enabling swift responses to potential security incidents.
Integrating AWS Web Application Firewall with AWS Services
AWS WAF seamlessly integrates with various AWS services, enhancing its effectiveness. Deploying AWS WAF with Amazon CloudFront allows for global distribution of content with added security at the edge. Integration with Application Load Balancer ensures that only legitimate traffic reaches your application servers. Additionally, AWS WAF can be used with Amazon API Gateway to protect APIs from malicious requests. These integrations provide a comprehensive security solution across your AWS infrastructure.
Monitoring and Logging with AWS Web Application Firewall
Monitoring and logging are essential components of a robust security strategy. AWS WAF provides detailed logs of web requests, including information on the request's source, headers, and the action taken by the WAF rules. These logs can be stored in Amazon S3, analyzed using Amazon Athena, or visualized through Amazon OpenSearch Service. By regularly reviewing these logs, businesses can identify patterns, detect anomalies, and respond promptly to potential threats, ensuring continuous protection of web applications.
Cost Considerations for AWS Web Application Firewall
While AWS WAF offers robust security features, it's essential to consider the associated costs. Pricing is based on the number of web access control lists (ACLs), the number of rules per ACL, and the number of web requests processed. To optimize costs, regularly review and adjust your WAF rules to ensure they are necessary and effective. Additionally, leveraging AWS Shield Advanced can provide additional protection against larger-scale attacks, potentially reducing the need for extensive custom WAF rules. By carefully managing AWS WAF configurations, businesses can achieve a balance between robust security and cost efficiency.
Future-Proofing Your Web Application Security with AWS WAF
As cyber threats continue to evolve, it's crucial to future-proof your web application security. AWS WAF's flexibility allows for the implementation of custom rules to address emerging threats. Regularly updating and refining these rules ensures that your applications remain protected against new vulnerabilities. Additionally, staying informed about updates and new features released by AWS can provide opportunities to enhance your security posture further. By proactively managing AWS WAF configurations, businesses can maintain a robust defense against evolving cyber threats.
Conclusion
Implementing AWS Web Application Firewall is a critical step in protecting web applications from common and emerging threats. By following best practices, integrating with AWS services, and continuously monitoring and refining security configurations, businesses can ensure the integrity and availability of their applications. Edgenexus Limited's expertise in IT services and consulting can assist organizations in effectively deploying and managing AWS WAF, providing tailored solutions to meet specific security needs. With a proactive approach to web application security, businesses can safeguard their digital assets and maintain trust with their users.
0 notes
Text
AWS Cost Optimization Strategies: How to manage Cloud Expenses Efficiently

In today’s digital landscape, user expectations are higher than ever. Speed, reliability, and seamless experiences are non-negotiable for both web and mobile applications. Amazon Web Services (AWS) offers a robust suite of tools and services that, when leveraged effectively, can significantly enhance application performance. For businesses aiming to stay competitive, understanding and implementing AWS optimization strategies is crucial.
Understanding AWS Infrastructure for Optimal Performance
Before diving into optimization techniques, it’s essential to grasp the foundational elements of AWS that impact performance:
Compute Services: EC2, Lambda, Elastic Beanstalk
Storage Solutions: S3, EBS, EFS
Database Services: RDS, DynamoDB, Aurora
Networking Components: VPC, Route 53, CloudFront
A proficient Cloud Consulting Company can assist in architecting solutions that align with your specific performance goals.
Leveraging Auto Scaling for Dynamic Workloads
Auto Scaling ensures that your application can handle varying loads by automatically adjusting the number of compute resources. Key benefits include:
Cost Efficiency: Scale down during low traffic periods to save costs.
High Availability: Maintain application performance during traffic spikes.
Implementing Auto Scaling requires careful planning and monitoring, areas where a seasoned Software Development Company can provide invaluable expertise.
Utilizing Content Delivery Networks (CDNs) with Amazon CloudFront
CDNs play a pivotal role in reducing latency and improving load times. Amazon CloudFront offers:
Global Edge Locations: Deliver content closer to users.
Integration with Other AWS Services: Seamless connectivity with S3, EC2, and more.
By distributing content efficiently, CloudFront enhances user experiences, particularly for global audiences.
Optimizing Database Performance
Databases are often the backbone of applications. AWS provides several options:
Amazon RDS: Managed relational databases with features like read replicas and Multi-AZ deployments.
Amazon DynamoDB: A NoSQL database offering single-digit millisecond performance.
Optimization strategies include:
Indexing: Speed up query performance.
Caching: Use services like Amazon ElastiCache to reduce database load.
A knowledgeable Website Development Company can tailor database solutions to your application’s unique needs.
Implementing Effective Caching Mechanisms
Caching reduces the load on your backend systems and accelerates content delivery. AWS offers:
Amazon ElastiCache: Supports Redis and Memcached for in-memory data storage.
CloudFront Edge Caching: Stores copies of content at edge locations.
Proper caching strategies can drastically improve application responsiveness.
Monitoring and Logging with AWS CloudWatch
Continuous monitoring is vital for maintaining optimal performance. AWS CloudWatch provides:
Real-Time Metrics: Monitor CPU usage, memory, and more.
Alarms and Notifications: Set thresholds to trigger alerts.
Log Management: Collect and analyze logs for troubleshooting.
Regular monitoring helps in proactive issue resolution and performance tuning.
Enhancing Security Without Compromising Performance
Security is paramount, but it shouldn’t hinder performance. AWS offers:
AWS WAF: Protects against common web exploits.
AWS Shield: DDoS protection service.
IAM Policies: Fine-grained access control.
Balancing security and performance ensure a trustworthy and efficient application.
Cost Optimization Strategies
Optimizing performance doesn’t mean escalating costs. Consider:
Reserved Instances: Commit to usage for discounts.
Spot Instances: Utilize unused capacity at reduced prices.
Right-Sizing: Match instance types to workload requirements.
A strategic approach to resource allocation can yield significant savings.
Leveraging AWS Lambda for Serverless Architectures
Serverless computing allows you to run code without provisioning servers. AWS Lambda offers:
Automatic Scaling: Handles varying workloads seamlessly.
Cost Efficiency: Pay only for compute time consumed.
Reduced Operational Overhead: Focus on code, not infrastructure.
Serverless architectures are ideal for applications with unpredictable traffic patterns.
Continuous Performance Testing and Optimization
Regular testing ensures sustained performance. Implement:
Load Testing: Simulate traffic to identify bottlenecks.
Performance Benchmarks: Establish baselines for comparison.
A/B Testing: Evaluate changes before full deployment.
Continuous improvement is key to maintaining high-performance standards.
Conclusion: Partnering for Success
Optimizing AWS performance is a multifaceted endeavour requiring expertise and strategic planning. Collaborating with a reputable Cloud Consulting Company, Software Development Company, or Website Development Company can provide the guidance and support necessary to achieve and maintain optimal application performance.
0 notes
Text
AWS WAFv2 For Hotlink Protection: Future Of Content Security

How to stop hotlinking with Amazon CloudFront, WAF, and referer checking.
AWS WAF Classic will be retired in September 2025. This update describes how to utilise the latest AWS WAF (WAFv2) to avoid hotlinking. Screenshots have been updated to reflect AWS WAF Management Console changes.
Hotlinking, also known as inline linking, is a kind of content leeching in which an unauthorised third-party website embeds links to resources referenced in a major website's HTML. Your website may be invoiced for third-party websites' content as they don't pay for hosting. Slow loading times, lost money, and legal issues may result.
Hotlinking may now be stopped using AWS WAF. AWS WAF, a web application firewall, integrates with Amazon CloudFront, a CDN, to protect your web apps from typical online vulnerabilities that can reduce application availability, security, and resource use.
Solution overview
There are several techniques to handle hotlinking. The Apache module mod_rewrite may verify the Referer header on your web server. You may then redirect the visitor to your site's home page or display a 403 Forbidden message.
If you utilise a CDN like CloudFront to speed up website delivery, web server Referer header validation is less useful. The CDN must validate additional requests for that content because they are unlikely to reach the origin web server, even if your web server verifies the headers (in this example, the referer). The CDN caches your stuff at the edge of its servers.
Figure 1: Cache request-response flow.Hit-and-miss cache encounters
Figure 1 shows the procedure:
A user client (1) requests from CloudFront edge point (2).
Edge locations try to return a cached file. This request is a cache hit if the cache replies.
The origin (3), which may be an Amazon S3 bucket, receives a request for a new copy of the object if there is a cache miss and the content is incorrect or not in the edge.
Cache hits prevent the origin from applying validation logic to the user's request since the edge server may fill the request without contacting the origin.
Two methods for solution implementation
This document provides two AWS WAF configurations to prevent hotlinking:
Transferring protected static assets (images or stylistic elements) to static.example.com ensures that you just need to check the Referer header.
Static files are in a directory on the same domain. This approach includes extending this example to check for an empty Referer header.
Your website structure and security needs will determine your strategy. The first approach lets you set up a Referer header check to guarantee that photo requests come from an allowlisted sub-domain, while the second way checks for an empty Referer header. The first technique prevents unaffiliated third-party sites from embedding image links, whereas the second allows users to share direct connections.
Terms
Key phrases from this post:
AWS WAFs use web ACLs tied to CloudFront distributions.
Each web ACL has one or more match criteria and rules.
Match conditions examine request headers or URIs for particular criteria using one or more filters.
The names of HTTP headers are not case-sensitive. Referer references the same HTTP header. However, HTTP headers are case-sensitive.
Requirements
A CloudFront distribution is needed to configure an AWS WAF web ACL. Configuring a CloudFront distribution with an S3 bucket origin is covered in Configure distributions.
Approach 1: Subdomain separation
This sample AWS WAF rule set comprises one rule, match condition, and filter. The match condition checks the Referer header for a given value. Traffic is allowed if the request meets rule conditions. If not, AWS WAF blocks traffic.
Due to the static files' subdomain (static.example.com) being accessible exclusively from example.com, you will restrict hotlinking for any file without a referral.
Approach 2: Domain-wide content with path filtering
The second technique filters by URL path and allows blank Referer headers. Create an AWS WAF web ACL with numerous rules and extra match criteria, which are filters. Instead than validating the Referer header once, the match condition validates it twice. First, check the request header. The URL-style Referer header is checked in the second validation.
Some people may prefer to share the photo URL directly. Accessing the picture directly in the browser can help avoid a negative user experience. This solution is better than the previous, which needed sub-domain picture requests.
You must also check the request route (/wp-content) for AWS WAF to protect multiple folders under a domain name.
In conclusion
AWS WAF, a web application firewall, monitors and manages HTTP(S) traffic to your protected web applications. Using the AWS WAF custom rule builder, you protected your website's Amazon S3 bucket content from hotlinking.
Preventing unauthorised third-party websites from connecting to your static content reduces bandwidth costs, user experience, and resource leeching. Two robust referrer check methods are described in this post. Following the least privilege approach, you may restrict AWS WAF rules to.jpg or.png image file extensions.
Referer checking prevents unaffiliated websites from utilising your bandwidth and backlinking to your images, but clever attacks can purposefully design a request to bypass it. Inconsistent referer header interpretation can also be caused by browser plugins, server-to-server queries that fake header data, or privacy-based web browsers. Recognise these anomalies and consider token authentication and signed URLs for private content protection.
Web browsers cannot detect changed Referer headers. Referer checking should be utilised with AWS WAF application protection rules, Bot Control, Fraud Control, and DDOS protection to secure online applications.
#technology#technews#govindhtech#news#technologynews#AWS WAF#Amazon S3#WAFv2#content delivery network#web ACL#HTTP
0 notes
Photo

New Post has been published on https://codebriefly.com/building-and-deploying-angular-19-apps/
Building and Deploying Angular 19 Apps

Efficiently building and deploying Angular 19 applications is crucial for delivering high-performance, production-ready web applications. In this blog, we will cover the complete process of building and deploying Angular 19 apps, including best practices and optimization tips.
Table of Contents
Toggle
Why Building and Deploying Matters
Preparing Your Angular 19 App for Production
Building Angular 19 App
Key Optimizations in Production Build:
Configuration Example:
Deploying Angular 19 App
Deploying on Firebase Hosting
Deploying on AWS S3 and CloudFront
Automating Deployment with CI/CD
Example with GitHub Actions
Best Practices for Building and Deploying Angular 19 Apps
Final Thoughts
Why Building and Deploying Matters
Building and deploying are the final steps of the development lifecycle. Building compiles your Angular project into static files, while deploying makes it accessible to users on a server. Proper optimization and configuration ensure faster load times and better performance.
Preparing Your Angular 19 App for Production
Before building the application, make sure to:
Update Angular CLI: Keep your Angular CLI up to date.
npm install -g @angular/cli
Optimize Production Build: Enable AOT compilation and minification.
Environment Configuration: Use the correct environment variables for production.
Building Angular 19 App
To create a production build, run the following command:
ng build --configuration=production
This command generates optimized files in the dist/ folder.
Key Optimizations in Production Build:
AOT Compilation: Reduces bundle size by compiling templates during the build.
Tree Shaking: Removes unused modules and functions.
Minification: Compresses HTML, CSS, and JavaScript files.
Source Map Exclusion: Disables source maps for production builds to improve security and reduce file size.
Configuration Example:
Modify the angular.json file to customize production settings:
"configurations": "production": "optimization": true, "outputHashing": "all", "sourceMap": false, "namedChunks": false, "extractCss": true, "aot": true, "fileReplacements": [ "replace": "src/environments/environment.ts", "with": "src/environments/environment.prod.ts" ]
Deploying Angular 19 App
Deployment options for Angular apps include:
Static Web Servers (e.g., NGINX, Apache)
Cloud Platforms (e.g., AWS S3, Firebase Hosting)
Docker Containers
Serverless Platforms (e.g., AWS Lambda)
Deploying on Firebase Hosting
Install Firebase CLI:
npm install -g firebase-tools
Login to Firebase:
firebase login
Initialize Firebase Project:
firebase init hosting
Deploy the App:
firebase deploy
Deploying on AWS S3 and CloudFront
Build the Project:
ng build --configuration=production
Upload to S3:
aws s3 sync ./dist/my-app s3://my-angular-app
Configure CloudFront Distribution: Set the S3 bucket as the origin.
Automating Deployment with CI/CD
Setting up a CI/CD pipeline ensures seamless updates and faster deployments.
Example with GitHub Actions
Create a .github/workflows/deploy.yml file:
name: Deploy Angular App on: [push] jobs: build-and-deploy: runs-on: ubuntu-latest steps: - uses: actions/checkout@v2 - name: Set up Node.js uses: actions/setup-node@v2 with: node-version: '18' - run: npm install - run: npm run build -- --configuration=production - name: Deploy to S3 run: aws s3 sync ./dist/my-app s3://my-angular-app --delete
Best Practices for Building and Deploying Angular 19 Apps
Optimize for Production: Always use AOT and minification.
Use CI/CD Pipelines: Automate the build and deployment process.
Monitor Performance: Utilize tools like Lighthouse to analyze performance.
Secure the Application: Enable HTTPS and configure secure headers.
Cache Busting: Use hashed filenames to avoid caching issues.
Containerize with Docker: Simplifies deployments and scales easily.
Final Thoughts
Building and deploying Angular 19 applications efficiently can significantly enhance performance and maintainability. Following best practices and leveraging cloud hosting services ensure that your app is robust, scalable, and fast. Start building your next Angular project with confidence!
Keep learning & stay safe 😉
You may like:
Testing and Debugging Angular 19 Apps
Performance Optimization and Best Practices in Angular 19
UI/UX with Angular Material in Angular 19
0 notes