#cloud architecture and migration services
Explore tagged Tumblr posts
Text
Building the Foundation for Scalable Digital Growth with Cloud Architecture and Migration
In today’s hyper-connected and fast-evolving digital landscape, cloud computing has become more than just an IT choice—it is a strategic necessity. As organizations strive to modernize infrastructure, support remote workforces, and launch digital-first products, the cloud provides the foundation for resilience, agility, and long-term growth.
However, the journey to the cloud is not without complexity. Moving critical systems, data, and workflows to a new environment requires more than simply lifting and shifting existing applications. It calls for thoughtful planning, robust design, and a clear understanding of long-term objectives.
To truly unlock the benefits of the cloud, businesses must prioritize both architecture and execution. That’s where effective cloud architecture and migration strategies come into play—ensuring that every step of the transition is optimized for scalability, security, and performance.
Why Cloud Architecture Matters
Cloud architecture refers to the structural design of systems built for the cloud. It includes everything from the arrangement of cloud services and components to how data flows and how security policies are enforced. A well-architected framework ensures that the cloud environment can handle current workloads efficiently and scale seamlessly as demands grow.
Without proper architecture, businesses face several risks:
Resource underutilization or overspending
Application performance issues
Compliance and security vulnerabilities
Inability to scale dynamically
Poor system availability and disaster recovery readiness
An intelligent architecture acts as a blueprint that guides cloud migration, integration, and ongoing optimization—laying the groundwork for operational excellence.
The Cloud Migration Imperative
Organizations are increasingly recognizing that remaining on legacy infrastructure is not sustainable. On-premise systems are expensive to maintain, difficult to scale, and often incapable of supporting modern development practices.
Migration to the cloud addresses these limitations by:
Reducing capital expenditure on hardware and facilities
Enabling elastic scalability based on real-time usage
Supporting global reach with minimal latency
Improving uptime and disaster recovery readiness
Enhancing development speed with modern tooling and automation
However, a successful migration requires much more than technical tools—it needs a structured approach that aligns with the business’s operational and growth goals.
Key Stages in Cloud Architecture and Migration
A well-executed cloud transition typically involves the following phases:
1. Assessment & Planning
The first step is to understand existing infrastructure, application dependencies, data sensitivity, and business priorities. During this phase, a roadmap is created that outlines timelines, resource requirements, cloud service selection (e.g., AWS, Azure, GCP), and migration strategies such as rehosting, re-platforming, or refactoring.
2. Architecture Design
Once the plan is in place, cloud architects design the environment based on scalability, performance, and security needs. This includes network layout, compute sizing, storage configuration, redundancy planning, and IAM (Identity and Access Management) policies.
3. Proof of Concept (PoC)
Before full migration, a small-scale PoC is often conducted to validate architectural assumptions, identify gaps, and test integrations. This phase allows for early detection of risks and fine-tuning of the plan.
4. Migration Execution
Using automated tools and manual oversight, workloads, databases, applications, and services are transitioned to the cloud. Downtime is minimized through staged cutovers and live data synchronization strategies.
5. Testing & Validation
Once the environment is live, rigorous testing is conducted to ensure data integrity, application performance, and security compliance. Load testing, failover testing, and user acceptance tests are essential at this stage.
6. Optimization & Monitoring
The cloud environment is continuously monitored for performance, security threats, and cost usage. Optimization techniques such as autoscaling, rightsizing, and resource scheduling are applied to reduce waste and ensure ROI.
Choosing the Right Migration Strategy
Not all workloads are suitable for the same migration model. The most common approaches include:
Rehosting ("Lift and Shift"): Moving workloads without code changes
Re-platforming: Making minimal adjustments to optimize performance in the cloud
Refactoring: Rewriting portions of the application for cloud-native capabilities
Repurchasing: Switching to SaaS alternatives when possible
Retaining or Retiring: Deciding whether some apps should stay on-premise or be phased out
The best approach depends on the workload’s complexity, long-term value, and modernization goals.
Security and Compliance Considerations
Security is a top concern during cloud migrations. A robust security framework must be designed into the architecture from the start—not bolted on after migration. Key elements include:
Data Encryption: At rest and in transit
IAM Policies: Fine-grained access control
Firewalls & VPNs: Network segmentation and secure tunneling
Audit Logging & Monitoring: Continuous oversight of changes and access
Compliance Readiness: Aligning with standards like GDPR, HIPAA, or ISO 27001
By integrating these controls early, businesses can ensure secure operations while avoiding costly rework or fines.
The Role of Automation in Modern Migrations
Automation is essential to achieve speed and consistency in cloud architecture and migration. It reduces human error, accelerates timelines, and supports repeatable, scalable deployments.
Common tools and frameworks include:
Terraform & AWS CloudFormation: For Infrastructure as Code (IaC)
Ansible, Chef, or Puppet: For configuration management
Kubernetes & Docker: For container orchestration
CI/CD Pipelines: For continuous deployment and rollback
Monitoring Tools: Like Prometheus, Datadog, and CloudWatch
Automated migration and post-deployment management enable businesses to scale without increasing operational complexity.
Benefits of End-to-End Cloud Architecture and Migration Services
Organizations that invest in full-scope architecture and migration support realize several strategic advantages:
Reduced Downtime: Through planned cutovers and rollback systems
Cost Optimization: Via rightsizing and usage tracking
Improved Resilience: With built-in redundancy and failover capabilities
Faster Time-to-Market: For applications and digital services
Greater Business Agility: Through scalable infrastructure and rapid provisioning
With expert guidance and modern tooling, businesses can transition to the cloud smoothly, avoiding common pitfalls and maximizing long-term returns.
Industries Driving Change Through the Cloud
Cloud transformation is making a significant impact across industries:
Finance: Real-time fraud detection, scalable banking apps, secure transactions
Healthcare: Telehealth platforms, data interoperability, HIPAA-compliant hosting
Retail: Personalized shopping experiences, omnichannel platforms, inventory optimization
Manufacturing: IoT integration, predictive maintenance, supply chain analytics
Government: Citizen service portals, smart city platforms, secure data hosting
Each industry requires tailored architecture and migration strategies that align with compliance, scalability, and performance expectations.
Final Thoughts
Cloud is no longer the future—it’s the infrastructure standard of the present. Yet, the path to cloud success is paved with thoughtful planning, modern architecture, and strategic execution. Businesses that prioritize well-architected frameworks and leverage automated, secure migration techniques are better positioned to scale, innovate, and lead in their respective markets.
With the right cloud architecture and migration services, organizations can confidently make the leap—reducing risk, accelerating transformation, and building the digital backbone needed for long-term success.
0 notes
Text
BIM Structural Modeling Services – What’s The Need For It?
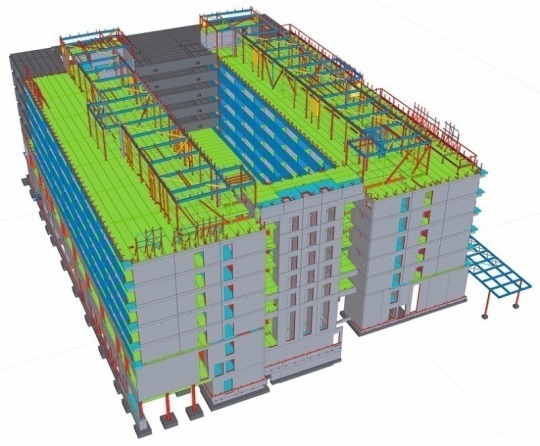
Did you take a smart step for your building with Bim Structural Modeling Services UAE? It’s a good idea to go every day! Ensuring precision, cost efficiency and speed are critical factors in the construction industry. Because various complexities that most professionals face all the time.
#Bim Service Providers In India#Architecture Bim Software#Bim Architectural Services#Structural Bim Services#Structural Bim Modeling Services#Bim Structural Detailing Services#Mepf Bim Services#Mep Fabrication Drawings#Infrastructure Bim Services India#Infrastructure Bim Modeling Services#4D Construction Sequencing#Construction Sequencing With 4D Bim#4D Bim In Construction#5D Bim Cost Estimation Quantity Take-Offs#Bim Quantity Take-Off Services#7D Bim Asset Information Model#Point Cloud To Bim Services#Cad To Bim Migration Services#Construction Documentation Set India#Facility Management Service Providers
0 notes
Text
Jaret Chiles, Chief Services Officer, DoiT – Interview Series
New Post has been published on https://thedigitalinsider.com/jaret-chiles-chief-services-officer-doit-interview-series/
Jaret Chiles, Chief Services Officer, DoiT – Interview Series
Jaret Chiles is the chief services officer (CSO) of DoiT and is responsible for all aspects of their client services organization. With 25+ years of experience across consulting and managed services, cloud adoption, technical sales, security and compliance, he is instrumental in building out a key value driver for DoiT’s business: services, consulting, and support offerings. Since joining the company, Jaret has led development of a scalable services strategy that enables DoiT to grow rapidly – without compromising its unrivaled expertise.
DoiT combines the power of intelligent software products with access to unrivaled multicloud expertise to solve the most complicated and important cloud problems. DoiT’s product portfolio provides the tools to manage cloud cost and infrastructure without compromising the speed or quality of engineering initiatives.
What initially attracted you to computer science and how did you find yourself involved in cloud computing?
My father was an engineer and exposed me to building and modifying computers as a child in the early 80s. My first computer was a TRS-80 Model 4 on which I learned how to do some basic programming by the time I was in elementary school. It’s been an interesting journey and I never really considered working in any other field. During high school, I had my first job working evenings and weekends at an internet service provider doing dial-up, broadband, email and website support. While pursuing a computer science degree in college, I helped run the campus data center and networks and led my first team.
I went on to work in many different roles at a managed hosting services provider. When AWS began to disrupt our legacy models, I recognized the undeniable potential and quickly adapted to the cloud computing era as a cloud architect from the very first release of OpenStack to all the major hyperscalers. Ever since I’ve been focused on helping companies large and small understand how to unlock the value that cloud computing creates for their businesses. My passion for computing has never strayed, but now I find it most rewarding as a servant leader supporting the success and growth of others who share my passion.
Can you elaborate on how DoiT’s intelligent software products and multicloud expertise specifically address the most pressing cloud challenges faced by organizations today?
Through our products and services, DoiT International helps cloud-driven companies harness the public cloud to drive business growth. We’re a full-service provider of intelligent multicloud technology, so we deliver consulting, support and training to solve essential challenges like migration costs and the sheer complexity of cloud usage.
We also provide full-service FinOps technology along with the procurement advantages that organizations need to solve the challenges of navigating and automating public cloud investments. Some of the essential capabilities we provide include multicloud budgeting, reporting, optimization and governance.
DoiT’s global team of cloud experts have decades of experience in the analytics, optimization and governance of cloud architecture, as well as specializations in Kubernetes and artificial intelligence (AI). We also stay on top of emerging technologies, so our clients can take full advantage of them, securely and safely. Our experts have technical leadership backgrounds across verticals. Daily, I’m completely humbled by the actual level of expertise in our organization, I’ve never seen anything like it elsewhere.
How does DoiT Cloud Solve enhance the cloud experience for users, and could you share some success stories or examples of challenges it has helped resolve?
Doit Cloud Solve is a services offering that allows customers to unlock real value in cloud computing with unlimited access to the top experts in the industry. We work backward from what customers actually need, with less friction than traditional consulting and support contracting models. Using Generative AI as an example, we leverage a three-part approach:
Discovery: We delve into specific business objectives, gathering and refining data to lay the groundwork for innovation;
Innovation: We guide feature selection, model training and validation to meet tailored needs; and
Deployment and optimization: We implement and refine generative AI strategy, ensuring your team executes on a seamless integration and with maximum impact.
The DoiT Cloud Solve team provides multicloud consulting, unlimited consultancy and technical support as well as cloud-native training. Customers are able to create optimized architectures and configurations while enhancing the skills and capabilities across their teams, which leads to more efficient and sustainable cloud growth. From the core of the cloud stack with compute, storage and networking, through the full cloud-native product portfolio, to the most advanced and disruptive cloud solutions.
In terms of cloud cost optimization, what strategies or technologies does DoiT employ to help clients maximize their cloud investments while maintaining or enhancing service quality?
Cost optimization starts with a well-designed architecture. DoiT consultants and engineers help customers ensure their cloud architectures are future-ready and assist in creating migration strategies.
Additionally, every IT organization wants to get their desired benefits with the lowest possible spend, and to do this, IT needs timely information and tools that make it simple to manage cloud services. DoiT’s intelligent technology does exactly this, helping engineering and FinOps leaders monitor, manage and optimize their cloud usage and spend.
We help IT utilize advanced technologies like GenAI for both internal and customer-facing workflows, without running into unforeseen massive compute and cost overruns.
DoiT offers a suite of proprietary products like Flexsave and Cloud Navigator. How do these products differentiate from other tools available in the market, and what unique advantages do they offer to your clients?
What sets DoiT apart is its unrivaled expertise, full-service FinOps technology and the procurement advantage that we provide to solve the challenges of navigating and automating public cloud investments. These three pillars operating in harmony is a game changer for customers.
DoiT Flexsave uniquely removes the risk, forecasting and tedious work required for managing a complex portfolio of compute commitments and reservations. Compute costs can often represent more than half of an organization’s cloud spend, so accessing optimized pricing on those workloads is an easy way to lower monthly bills. Flexsave automates commitments, providing cost savings without the need to monitor usage, track expiration and renewal dates, while modifying instances to fit an organization’s reservations.
Security is a major concern in cloud computing. Can you discuss DoiT’s approach to cloud security and how it helps organizations strengthen their security posture?
Security must be part of every step in a customer’s cloud journey. It’s not one-and-done up front, and you don’t bolt it on at the end either. Security is a consideration baked into everything we do from products to services.
As part of architecture reviews, or as a focused session, DoiT Cloud Solve experts will advise on security strategies as well as perform benchmark security reviews of your environment including vulnerability assessment and security control analysis. A sound architecture and proper configuration are paramount to a secure cloud environment, but also careful consideration of customers’ regular operational procedures must be accounted for.
Given the increasing complexity of cloud environments, how does DoiT assist organizations in navigating multicloud strategies and managing infrastructure across multiple providers?
There are many different reasons customers might choose to leverage a multi-cloud strategy. At DoiT we believe in working backwards from the business objectives. Our consultants will help develop a strategy and architecture that meets business objectives without introducing unnecessary complexity.
One of the many challenges in managing a multi-cloud environment on a day-to-day basis is having visibility across all platforms in a consistent and operational manner. DoiT Cloud Navigator extends visibility and anomaly detection capabilities to overcome these challenges and provide the FinOps tools needed manage cloud costs and infrastructure without compromising the speed or quality of engineering initiatives. This allows for a responsible scaling of the business.
Machine learning and AI are becoming critical components of modern IT strategies. How does DoiT support businesses in integrating these technologies into their operations and leveraging them for competitive advantage?
Following the three-part approach mentioned previously, DoiT’s Cloud Solve enables IT to work with our experienced cloud architects, and provides access to knowledge transfer and other resources to enable them to evaluate internal readiness, identify company-specific use cases and collaboratively create customized GenAI solutions.
DoiT also partners with AWS and Google to help their users develop generative AI solutions using those platforms and their supporting applications.
The process of cloud migration can be daunting for many organizations. What key factors should companies consider to ensure a smooth and successful transition to the cloud with DoiT’s assistance?
A successful migration starts with establishing clear business objectives and success criteria. There are many factors to keep in mind when planning and executing a migration to the cloud, including data governance, security and privacy, cost management, scalability, skills and expertise, potential service disruptions and legacy system compatibility. Overlooking any of these and others can lead to delays and cost overruns for the migration.
What emerging trends or technologies in cloud computing is DoiT particularly excited about, and how do you plan to incorporate these into your offerings to drive future growth and innovation?
We are a company full of passionate cloud experts and every new technology hype cycle excites us immensely. That said, our many combined years of experience have taught us not to focus on finding ways to forcefully fit a new exciting technology in a business, but rather to understand what use cases make sense for a business and add real value. This is a very common mistake customers make when they see new emerging technologies and ask for help implementing them in their environments.
Generative AI right now has us very excited for a number of reasons, but the main reason is we have uncovered so many high value use cases for businesses across industries to adopt the technology. Starting with basic productivity and insight use cases, nearly everyone can benefit from GenAI. Moving from there on into AI-powered service development and disruptive GenAI product technologies, we believe the skies are the limit for our customers and we’d love to help them find their path to adoption and production.
Thank you for the great interview, readers who wish to learn more should visit DoiT.
#ai#AI strategy#AI-powered#Analysis#Analytics#applications#approach#architecture#artificial#Artificial Intelligence#assessment#AWS#benchmark#budgeting#Building#Business#Cloud#Cloud Architecture#cloud challenges#cloud computing#cloud environment#cloud migration#Cloud Security#cloud services#cloud solutions#cloud strategy#Cloud-Native#college#Companies#complexity
0 notes
Text
Best Cloud Architecture Redesign Service Provider
Are you looking for best cloud architecture redesign service? Then you can count us! We provide latest technological solutions available on cloud through API’s & build innovative solutions. For more information, you can visit our website.
#cloud architecture redesign#cloud assessment and planning#cloud server migrations#enterprise solutions development Hyderabad#enterprise system & application integration services in Hyderabad#best enterprise application Development Company in Hyderabad#software application maintenance and support services in Hyderabad
0 notes
Text
Cloud Migration and Integration A Strategic Shift Toward Scalable Infrastructure
In today’s digital-first business environment, cloud computing is no longer just a technology trend—it’s a foundational element of enterprise strategy. As organizations seek greater agility, scalability, and cost-efficiency, cloud migration and integration have emerged as critical initiatives. However, transitioning to the cloud is far from a lift-and-shift process; it requires thoughtful planning, seamless integration, and a clear understanding of long-term business objectives.

What is Cloud Migration and Why Does It Matter
Cloud migration involves moving data, applications, and IT processes from on-premises infrastructure or legacy systems to cloud-based environments. These environments can be public, private, or hybrid, depending on the organization’s needs. While the move offers benefits such as cost reduction, improved performance, and on-demand scalability, the true value lies in enabling innovation through flexible technology infrastructure.
But migration is only the first step. Cloud integration—the process of configuring applications and systems to work cohesively within the cloud—is equally essential. Without integration, businesses may face operational silos, inconsistent data flows, and reduced productivity, undermining the very purpose of migration.
Key Considerations in Cloud Migration
A successful cloud migration depends on more than just transferring workloads. It involves analyzing current infrastructure, defining the desired end state, and selecting the right cloud model and service providers. Critical factors include:
Application suitability: Not all applications are cloud-ready. Some legacy systems may need reengineering or replacement.
Data governance: Moving sensitive data to the cloud demands a strong focus on compliance, encryption, and access controls.
Downtime management: Minimizing disruption during the migration process is essential for business continuity.
Security architecture: Ensuring that cloud environments are resilient against threats is a non-negotiable part of migration planning.
Integration for a Unified Ecosystem
Once in the cloud, seamless integration becomes the linchpin for realizing operational efficiency. Organizations must ensure that their applications, databases, and platforms communicate efficiently in real time. This includes integrating APIs, aligning with enterprise resource planning (ERP) systems, and enabling data exchange across multiple cloud platforms.
Hybrid and Multi-Cloud Strategies
Cloud strategies have evolved beyond single-provider solutions. Many organizations now adopt hybrid (combining on-premise and cloud infrastructure) or multi-cloud (using services from multiple cloud providers) approaches. While this enhances flexibility and avoids vendor lock-in, it adds complexity to integration and governance.
To address this, organizations need a unified approach to infrastructure orchestration, monitoring, and automation. Strong integration frameworks and middleware platforms become essential in stitching together a cohesive IT ecosystem.
Long-Term Value of Cloud Transformation
Cloud migration and integration are not one-time projects—they are ongoing transformations. As business needs evolve, cloud infrastructure must adapt through continuous optimization, cost management, and performance tuning.
Moreover, integrated cloud environments serve as the foundation for emerging technologies like artificial intelligence, data analytics, and Internet of Things (IoT), enabling businesses to innovate faster and more efficiently.
By treating cloud migration and integration as strategic investments rather than tactical moves, organizations position themselves to stay competitive, agile, and future-ready.
#CloudMigration#CloudIntegration#DigitalTransformation#HybridCloud#MultiCloud#CloudComputing#InfrastructureModernization#ITStrategy#BusinessContinuity
2 notes
·
View notes
Text
Top 5 data management mistakes costing UAE businesses millions
Introduction
In an increasingly digital economy, poor data practices have become more than just an IT issue—they are an enterprise-level risk.

Across the UAE, businesses are losing millions annually due to fragmented systems, inconsistent governance, and reactive strategies.
In this article, we’ll unpack five critical data managementmistakes, their tangible costs, and what forward-thinking firms are doing to stay compliant, competitive, and data-resilient in 2025.
1. Fragmented Data Silos Across Departments
While decentralization may speed up local decision-making, it often comes at the cost of data cohesion. Sales, marketing, finance, and operations frequently maintain isolated datasets that never sync—each with its own metrics, definitions, and reporting cycles. The cost? Missed opportunities, duplicated efforts, inconsistent KPIs, and customer insights that are either delayed or distorted due to incompatible sources. Fix: Implement centralized data lakes or unified ERP/CRM systems to bridge these silos. Introduce cross-departmental governance protocols, and enforce scheduled data synchronization to maintain consistency across all business functions.
2. Weak Data Governance and Access Controls
Many UAE businesses still lack formal governance policies. There’s little clarity on who owns the data, who can access it, and how data quality is maintained across systems and touchpoints. The cost? Increased risk of data breaches, GDPR/DIFC non-compliance, unauthorized exposure of sensitive information, and eroded stakeholder trust—especially in sectors like healthcare, finance, and public services. Fix: Deploy a robust data governance framework with clearly defined roles, role-based access controls, automated audit trails, and regular compliance reviews. Embed accountability at every stage of data creation and usage.
3. Overreliance on Legacy Infrastructure
Outdated database architectures, manual Excel trackers, and siloed on-prem systems continue to dominate back-end processes—despite widespread digital front-ends. The cost? Performance bottlenecks during scale, limited real-time data visibility, high IT maintenance overheads, and an inability to integrate with modern analytics or automation tools. Fix: Migrate to cloud-native platforms that support elastic scaling, system redundancy, and embedded analytics. Incorporate APIs for seamless integration with existing digital tools while phasing out legacy dependencies.
4. Lack of Data Quality Assurance
Inconsistent formats, missing fields, outdated records, and duplicated entries remain common issues across enterprise datasets—especially when multiple input sources aren’t standardized.
The cost?
Flawed business reports, poor AI/ML model performance, customer experience setbacks, and incorrect decision-making based on unreliable data.
Fix:
Introduce end-to-end data quality frameworks that include automated validation checks, enrichment protocols, and AI-driven anomaly detection.
Regular audits and cleansing routines should be part of standard operations.
5. Treating Data Strategy as a One-Off Project
Many businesses initiate data initiatives as one-time efforts—an implementation followed by months (or years) of stagnation.
Without ongoing refinement, systems become outdated, and processes lose alignment with evolving business needs.
The cost?
Strategic misalignment, increasing technical debt, and declining ROI on digital investments that fail to evolve with the organization’s goals.
Fix:
Create a living data strategy—an adaptive roadmap reviewed quarterly, driven by key stakeholders across departments.
Tie progress to measurable KPIs like operational efficiency, customer satisfaction, or revenue growth from data-led initiatives.
Turn Costly Data Chaos into Smart Business Decisions: Nordstar Vision
At Nordstar Vision, we help businesses move from fragmented systems to future-ready data ecosystems.
Whether you’re struggling with outdated infrastructure, data silos, or lack of governance, our team brings tailored solutions to help you scale confidently in a data-first economy.
Let’s turn your data into a growth engine.
Reach out to us today at +(971) 50 1108756 or visit nordstartvision.
#data management UAE#business data mistakes#UAE data strategy#data governance UAE#database management Dubai#digital transformation UAE#legacy system issues#cloud migration UAE#data silos#enterprise data solutions#data compliance UAE#Nordstar Vision#data quality assurance#CRM data issues#ERP data integration#UAE business IT risks#data-driven decisions#business analytics UAE#smart data practices
1 note
·
View note
Text
Entra ID Lateral Movement And Expanding Permission Usage

Abusing Intimate Permissions for Lateral Movement and Privilege Escalation in Entra ID Native Environments: (In)tune to Takeovers
Recently, a client received assistance from the Mandiant Red Team in visualizing the potential consequences of an advanced threat actor breach. In order to compromise the tenant’s installed Entra ID service principals, Mandiant migrated laterally from the customer’s on-premises environment to their Microsoft Entra ID tenant during the evaluation.
Using a popular security architecture that involves Intune-managed Privileged Access Workstations (PAWs), we will discuss in this blog post a new method by which adversaries can move laterally and elevate privileges within Microsoft Entra ID by abusing Intune permissions (DeviceManagementConfiguration.ReadWrite.All) granted to Entra ID service principals. We also offer suggestions and corrective actions to stop and identify this kind of attack.
A pretext
The client had a well-developed security architecture that adhered to the Enterprise Access model suggested by Microsoft, which included:
An Active Directory-based on-premises setting that adheres to the Tiered Model.
A Microsoft Entra Connect Sync-synchronized Entra ID environment that synchronizes on-premises identities and groups with Entra ID. PAWs, which were completely cloud-native and controlled by Intune Mobile Device Management (MDM), were used to administrate this environment. They were not connected to the on-premises Active Directory system. To access these systems, IT managers used a specific, cloud-native (non-synced) administrative account. These cloud-native administrative accounts were the only ones allocated Entra ID roles (Global Administrator, Privileged Role Administrator, etc.).
A robust security barrier was created by separating administrative accounts, devices, and privileges between the Entra ID environment and the on-premises environment:
Because Entra ID privileged roles are associated with unique, cloud-native identities, a compromise of the on-premises Active Directory cannot be utilized to compromise the Entra ID environment. This is an excellent practice for Microsoft.
An “air gap” between the administration planes of the two environments is successfully created by using distinct physical workstations for administrative access to cloud and on-premises resources. Attackers find it very challenging to get through air gaps.
Strong Conditional Access regulations imposed by Privileged Identity Management assigned roles to the administrative accounts in Entra ID, necessitating multi-factor authentication and a managed, compliant device. Additionally, Microsoft recommends these best practices.
Attack Path
One of the objectives of the evaluation was to assign the Mandiant Red Team the task of obtaining Global Administrator access to the Entra ID tenant. Mandiant was able to add credentials to Entra ID service principals (microsoft.directory/servicePrincipals/credentials/update) by using a variety of methods that are outside the purview of this blog post. This gave the Red Team the ability to compromise any preloaded service principal.
There are a number well-known methods for abusing service principal rights to get higher permissions, most notably through the usage of RoleManagement.See AppRoleAssignment and ReadWrite.Directory.Application and ReadWrite.All.ReadWrite.All rights for Microsoft Graph.
However, the Mandiant Red Team had to reconsider their approach because none of these rights were being used in the customer’s environment.
Mandiant found a service principle that was given the DeviceManagementConfiguration after using the superb ROADTools framework to learn more about the customer’s Entra ID system.Go ahead and write.Permission is granted.Image credit to Google Cloud
The service principal is able to “read and write Microsoft Intune device configuration and policies” with this authorization.
Clients running Windows 10 and later can execute the unique PowerShell scripts used by Intune for device management. Administrators have an alternative to configuring devices with settings not accessible through the configuration policies or the apps section of Intune by using the ability to run scripts on local devices. When the device boots up, management scripts with administrator rights (NT AUTHORITY\SYSTEM) are run.
The configuration of Device Management.Go ahead and write.To list, read, create, and update management scripts via the Microsoft Graph API, all permissions are required.
The Microsoft Graph API makes it simple to write or edit the management script. An example HTTP request to alter an existing script is displayed in the accompanying figure.PATCH https://graph.microsoft.com/beta/deviceManagement/ deviceManagementScripts/<script id> { "@odata.type": "#microsoft.graph.deviceManagementScript", "displayName": "<display name>", "description": "<description>", "scriptContent": "<PowerShell script in base64 encoding>", "runAsAccount": "system", "enforceSignatureCheck": false, "fileName": "<filename>", "roleScopeTagIds": [ "<existing role scope tags>" ], "runAs32Bit": false }
The caller can provide a display name, file name, and description in addition to the Base64-encoded value of the PowerShell script content using the Graph API. Depending on which principle the script should be run as, the runAsAccount parameter can be set to either user or system. RoleScopeTagIds references Intune’s Scope Tags, which associate people and devices. The DeviceManagementConfiguration can likewise be used to construct and manage them.Go ahead and write. Permission is granted.
The configuration of Device Management.Go ahead and write.By changing an existing device management script to run a PowerShell script under Mandiant’s control, Mandiant was able to go laterally to the PAWs used for Entra ID administration with full authorization. The malicious script is run by the Intune management script when the device reboots as part of the user’s regular workday.
By implanting a command-and-control device, Mandiant could give the PAWs any instructions. The Red Team obtained privileged access to Entra ID by waiting for the victim to activate their privileged role through Azure Privileged Identity Management and then impersonating the privileged account (for example, by stealing cookies or tokens). By taking these actions, Mandiant was able to fulfill the assessment’s goal and gain Global Administrator rights in Entra ID.
Remediation and Recommendations
To avoid the attack scenario, Mandiant suggests the following hardening measures:
Review your organization’s security principals for the DeviceManagementConfiguration.ReadWrite.All permission: DeviceManagementConfiguration should be handled by organizations that use Microsoft Intune for device management.Go ahead and write.Since it grants the trustee authority over the Intune-managed devices and, consequently, any identities connected to the devices, all permissions are considered sensitive.
Mandiant advises businesses to routinely check the authorizations given to Azure service principals, with a focus on the DeviceManagementConfiguration.Along with other sensitive permissions (like RoleManagement), there is the ReadWrite.All permission.See AppRoleAssignment and ReadWrite.Directory.Application and ReadWrite.All.ReadWrite.All.
Businesses that manage PAWs with Intune should exercise extra caution when assigning Intune privileges (either via DeviceManagementConfiguration).Use Entra roles like Intune Role Administrator or ReadWrite.All.
Enable Intune’s multiple admin approval: Intune allows you to use Access Policies to demand a second administrator’s approval before applying any changes. By doing this, an attacker would be unable to use a single compromised account to create or alter management scripts.
Think about turning on activity logs for the Microsoft Graph API: Graph API Activity logs, which provide comprehensive details about Graph API HTTP requests made to Microsoft Graph resources, can be enabled to aid in detection and response efforts.
Make use of the features that Workload ID Premium licenses offer: With a Workload-ID Premium license, Mandiant suggests using these features to:
Limit the use of privileged service principals to known, reliable places only. By guaranteeing that only trustworthy places are used, this reduces the possibility of unwanted access and improves security.
Enable risk detections in Microsoft Identity Protection to improve service principal security. When risk factors or questionable activity are found, this can proactively prohibit access.
Keep an eye on service principal sign-ins proactively: Monitoring service principal sign-ins proactively can aid in identifying irregularities and possible dangers. Incorporate this information into security procedures to set off notifications and facilitate quick action in the event of unwanted access attempts.
Mandiant has a thorough grasp of the various ways attackers may compromise their target’s cloud estate with some hostile emulation engagements, Red Team Assessments, and Purple Team Assessments.
Read more on Govindhtech.com
#EntraID#EntraIDLateral#Lateral#Mandiant#MicrosoftEntraID#RedTeam#Windows10#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
3 notes
·
View notes
Text
The Best Azure Consulting Partner for Your Company: A Guide
Businesses need knowledgeable partners who can help them solve issues, reduce risks, improve customer engagement, and innovate with AI and data as part of the continuous process of digital transformation. A skilled cloud partner is necessary to migrate, modernise, develop, and spur growth on the cloud, which is a key facilitator in the process of digital transformation. Finding a knowledgeable Azure consulting partner who can help you thrive on the cloud is the first and most important step. The Azure platform is one of the most popular cloud platforms utilised by businesses. How do you pick the best Azure migration service provider for your company when there are so many Azure managed service providers offering specialised and managed services? Azure Expertise and Experience
Azure cloud knowledge and experience are the two most important Azure Partner Requirements. Partners who have demonstrated their abilities and skills will have the know-how to suit your company's needs. To determine the degree of knowledge and experience, you can look at
Azure Expert Managed Service Providers, partners with Azure Advanced Specialisations, and certifications are all subject to a stringent screening procedure and are validated annually.
references and customers that the Azure partner has worked with to comprehend the nature of the collaboration, and the outcomes obtained.
The sectors in which an Azure cloud migration partner specialises, as well as the kinds of services and solutions offered to other customers.
You can get a sense of the subject expertise and outcomes provided by looking at case studies of prior Azure cloud engagements and client testimonials.
Security and Safety
Businesses using the cloud are very concerned about security, and your Azure partner should prioritise security to protect your data, apps, infrastructure, and privacy. For all of its services, Azure provides a common security model. Azure provides a number of features and services, including Identity and Access Management (IAM), and Microsoft oversees, manages, and operates its internationally dispersed data centres. Data in transit, data stores, data at rest, operating systems and apps, rules, and configuration should all be covered by your Azure partner's security and dependability.
Other security characteristics to consider when choosing an Azure cloud partner
Governance, Risk, and Compliance
Network and Infrastructure Security
Security monitoring, operations, automation, and incident management
Secure Network Architecture Design, implementation, and maintenance
Business continuity and disaster recovery plans
Vulnerability and configuration analysis
Threat detection and response
Critical security updates and emergency security patches
You should have an Azure cloud consulting service partner who can enhance your organization's entire security posture because security and compliance lapses can be expensive errors. Global presence and reputation
If you have an Azure partner that works with many sectors worldwide, you will have the expertise available 24×7, 365 days a year to prevent service interruptions. Your clients demand dependable, secure, and quick services and solutions. To learn more about their track record in Azure migration consultancy, you can also read what their clients, staff, and industry peers have to say.
Services and Portfolio
Working with an Azure cloud consulting partner is a long-term commitment, and your needs may change over time. You may require business intelligence to enhance customer experience, construct an application, automate processes, or implement a multi-cloud strategy. As a result, it's critical to comprehend the offerings and services of your Azure cloud partner. Is there collaboration between your Azure partner and other cloud service providers? Can they meet your IT needs and do they provide application development? Even if these might not seem like urgent issues right now, having a reliable cloud partner with a variety of services and capabilities can be beneficial in the long run.
Understanding your Azure Cloud Consulting Partner
Microsoft Azure provides innovative solutions and a wide range of services. Businesses may find this complicated and daunting, and it may be difficult to choose the best cloud services, settings, operations, and optimisations. To fully benefit from Azure cloud, it is crucial to select a knowledgeable Azure cloud partner like IFI Techsolutions, which has helped businesses in a variety of industries embrace digital transformation with cloud, AI, and data. IFI Techsolutions is an expert in providing customised cloud services, including migration, modernisation, optimisation, operation, and monitoring, and has a staff of seasoned Microsoft Azure experts. They are IaaS, PaaS, and SaaS. Conclusion
At IFI Techsolutions, we understand that choosing the right Azure consulting partner is pivotal to your digital transformation journey. As a Microsoft Azure Expert Managed Services Provider with multiple advanced specialisations, we bring deep technical expertise, a strong security-first approach, and a proven track record across diverse industries. Whether you need to migrate, modernise, or optimise your cloud infrastructure, our team is equipped to deliver tailored, scalable solutions that drive innovation and business growth. Partner with IFI Techsolutions to unlock the full potential of Microsoft Azure—securely, efficiently, and confidently.
1 note
·
View note
Text
Cloud Agnostic: Achieving Flexibility and Independence in Cloud Management
As businesses increasingly migrate to the cloud, they face a critical decision: which cloud provider to choose? While AWS, Microsoft Azure, and Google Cloud offer powerful platforms, the concept of "cloud agnostic" is gaining traction. Cloud agnosticism refers to a strategy where businesses avoid vendor lock-in by designing applications and infrastructure that work across multiple cloud providers. This approach provides flexibility, independence, and resilience, allowing organizations to adapt to changing needs and avoid reliance on a single provider.

What Does It Mean to Be Cloud Agnostic?
Being cloud agnostic means creating and managing systems, applications, and services that can run on any cloud platform. Instead of committing to a single cloud provider, businesses design their architecture to function seamlessly across multiple platforms. This flexibility is achieved by using open standards, containerization technologies like Docker, and orchestration tools such as Kubernetes.
Key features of a cloud agnostic approach include:
Interoperability: Applications must be able to operate across different cloud environments.
Portability: The ability to migrate workloads between different providers without significant reconfiguration.
Standardization: Using common frameworks, APIs, and languages that work universally across platforms.
Benefits of Cloud Agnostic Strategies
Avoiding Vendor Lock-InThe primary benefit of being cloud agnostic is avoiding vendor lock-in. Once a business builds its entire infrastructure around a single cloud provider, it can be challenging to switch or expand to other platforms. This could lead to increased costs and limited innovation. With a cloud agnostic strategy, businesses can choose the best services from multiple providers, optimizing both performance and costs.
Cost OptimizationCloud agnosticism allows companies to choose the most cost-effective solutions across providers. As cloud pricing models are complex and vary by region and usage, a cloud agnostic system enables businesses to leverage competitive pricing and minimize expenses by shifting workloads to different providers when necessary.
Greater Resilience and UptimeBy operating across multiple cloud platforms, organizations reduce the risk of downtime. If one provider experiences an outage, the business can shift workloads to another platform, ensuring continuous service availability. This redundancy builds resilience, ensuring high availability in critical systems.
Flexibility and ScalabilityA cloud agnostic approach gives companies the freedom to adjust resources based on current business needs. This means scaling applications horizontally or vertically across different providers without being restricted by the limits or offerings of a single cloud vendor.
Global ReachDifferent cloud providers have varying levels of presence across geographic regions. With a cloud agnostic approach, businesses can leverage the strengths of various providers in different areas, ensuring better latency, performance, and compliance with local regulations.
Challenges of Cloud Agnosticism
Despite the advantages, adopting a cloud agnostic approach comes with its own set of challenges:
Increased ComplexityManaging and orchestrating services across multiple cloud providers is more complex than relying on a single vendor. Businesses need robust management tools, monitoring systems, and teams with expertise in multiple cloud environments to ensure smooth operations.
Higher Initial CostsThe upfront costs of designing a cloud agnostic architecture can be higher than those of a single-provider system. Developing portable applications and investing in technologies like Kubernetes or Terraform requires significant time and resources.
Limited Use of Provider-Specific ServicesCloud providers often offer unique, advanced services��such as machine learning tools, proprietary databases, and analytics platforms—that may not be easily portable to other clouds. Being cloud agnostic could mean missing out on some of these specialized services, which may limit innovation in certain areas.
Tools and Technologies for Cloud Agnostic Strategies
Several tools and technologies make cloud agnosticism more accessible for businesses:
Containerization: Docker and similar containerization tools allow businesses to encapsulate applications in lightweight, portable containers that run consistently across various environments.
Orchestration: Kubernetes is a leading tool for orchestrating containers across multiple cloud platforms. It ensures scalability, load balancing, and failover capabilities, regardless of the underlying cloud infrastructure.
Infrastructure as Code (IaC): Tools like Terraform and Ansible enable businesses to define cloud infrastructure using code. This makes it easier to manage, replicate, and migrate infrastructure across different providers.
APIs and Abstraction Layers: Using APIs and abstraction layers helps standardize interactions between applications and different cloud platforms, enabling smooth interoperability.
When Should You Consider a Cloud Agnostic Approach?
A cloud agnostic approach is not always necessary for every business. Here are a few scenarios where adopting cloud agnosticism makes sense:
Businesses operating in regulated industries that need to maintain compliance across multiple regions.
Companies require high availability and fault tolerance across different cloud platforms for mission-critical applications.
Organizations with global operations that need to optimize performance and cost across multiple cloud regions.
Businesses aim to avoid long-term vendor lock-in and maintain flexibility for future growth and scaling needs.
Conclusion
Adopting a cloud agnostic strategy offers businesses unparalleled flexibility, independence, and resilience in cloud management. While the approach comes with challenges such as increased complexity and higher upfront costs, the long-term benefits of avoiding vendor lock-in, optimizing costs, and enhancing scalability are significant. By leveraging the right tools and technologies, businesses can achieve a truly cloud-agnostic architecture that supports innovation and growth in a competitive landscape.
Embrace the cloud agnostic approach to future-proof your business operations and stay ahead in the ever-evolving digital world.
2 notes
·
View notes
Text
Harnessing the Power of Data Engineering for Modern Enterprises
In the contemporary business landscape, data has emerged as the lifeblood of organizations, fueling innovation, strategic decision-making, and operational efficiency. As businesses generate and collect vast amounts of data, the need for robust data engineering services has become more critical than ever. SG Analytics offers comprehensive data engineering solutions designed to transform raw data into actionable insights, driving business growth and success.
The Importance of Data Engineering
Data engineering is the foundational process that involves designing, building, and managing the infrastructure required to collect, store, and analyze data. It is the backbone of any data-driven enterprise, ensuring that data is clean, accurate, and accessible for analysis. In a world where businesses are inundated with data from various sources, data engineering plays a pivotal role in creating a streamlined and efficient data pipeline.
SG Analytics’ data engineering services are tailored to meet the unique needs of businesses across industries. By leveraging advanced technologies and methodologies, SG Analytics helps organizations build scalable data architectures that support real-time analytics and decision-making. Whether it’s cloud-based data warehouses, data lakes, or data integration platforms, SG Analytics provides end-to-end solutions that enable businesses to harness the full potential of their data.
Building a Robust Data Infrastructure
At the core of SG Analytics’ data engineering services is the ability to build robust data infrastructure that can handle the complexities of modern data environments. This includes the design and implementation of data pipelines that facilitate the smooth flow of data from source to destination. By automating data ingestion, transformation, and loading processes, SG Analytics ensures that data is readily available for analysis, reducing the time to insight.
One of the key challenges businesses face is dealing with the diverse formats and structures of data. SG Analytics excels in data integration, bringing together data from various sources such as databases, APIs, and third-party platforms. This unified approach to data management ensures that businesses have a single source of truth, enabling them to make informed decisions based on accurate and consistent data.
Leveraging Cloud Technologies for Scalability
As businesses grow, so does the volume of data they generate. Traditional on-premise data storage solutions often struggle to keep up with this exponential growth, leading to performance bottlenecks and increased costs. SG Analytics addresses this challenge by leveraging cloud technologies to build scalable data architectures.
Cloud-based data engineering solutions offer several advantages, including scalability, flexibility, and cost-efficiency. SG Analytics helps businesses migrate their data to the cloud, enabling them to scale their data infrastructure in line with their needs. Whether it’s setting up cloud data warehouses or implementing data lakes, SG Analytics ensures that businesses can store and process large volumes of data without compromising on performance.
Ensuring Data Quality and Governance
Inaccurate or incomplete data can lead to poor decision-making and costly mistakes. That’s why data quality and governance are critical components of SG Analytics’ data engineering services. By implementing data validation, cleansing, and enrichment processes, SG Analytics ensures that businesses have access to high-quality data that drives reliable insights.
Data governance is equally important, as it defines the policies and procedures for managing data throughout its lifecycle. SG Analytics helps businesses establish robust data governance frameworks that ensure compliance with regulatory requirements and industry standards. This includes data lineage tracking, access controls, and audit trails, all of which contribute to the security and integrity of data.
Enhancing Data Analytics with Natural Language Processing Services
In today’s data-driven world, businesses are increasingly turning to advanced analytics techniques to extract deeper insights from their data. One such technique is natural language processing (NLP), a branch of artificial intelligence that enables computers to understand, interpret, and generate human language.
SG Analytics offers cutting-edge natural language processing services as part of its data engineering portfolio. By integrating NLP into data pipelines, SG Analytics helps businesses analyze unstructured data, such as text, social media posts, and customer reviews, to uncover hidden patterns and trends. This capability is particularly valuable in industries like healthcare, finance, and retail, where understanding customer sentiment and behavior is crucial for success.
NLP services can be used to automate various tasks, such as sentiment analysis, topic modeling, and entity recognition. For example, a retail business can use NLP to analyze customer feedback and identify common complaints, allowing them to address issues proactively. Similarly, a financial institution can use NLP to analyze market trends and predict future movements, enabling them to make informed investment decisions.
By incorporating NLP into their data engineering services, SG Analytics empowers businesses to go beyond traditional data analysis and unlock the full potential of their data. Whether it’s extracting insights from vast amounts of text data or automating complex tasks, NLP services provide businesses with a competitive edge in the market.
Driving Business Success with Data Engineering
The ultimate goal of data engineering is to drive business success by enabling organizations to make data-driven decisions. SG Analytics’ data engineering services provide businesses with the tools and capabilities they need to achieve this goal. By building robust data infrastructure, ensuring data quality and governance, and leveraging advanced analytics techniques like NLP, SG Analytics helps businesses stay ahead of the competition.
In a rapidly evolving business landscape, the ability to harness the power of data is a key differentiator. With SG Analytics’ data engineering services, businesses can unlock new opportunities, optimize their operations, and achieve sustainable growth. Whether you’re a small startup or a large enterprise, SG Analytics has the expertise and experience to help you navigate the complexities of data engineering and achieve your business objectives.
5 notes
·
View notes
Text
The Essence of an AWS Certified Solutions Architect
In the dynamic landscape of cloud computing, the role of an AWS Certified Solutions Architect emerges as a symbol of mastery in crafting and implementing state-of-the-art solutions within the Amazon Web Services (AWS) ecosystem. Bestowed by AWS, this certification serves as a testament to an individual's proficiency in architecting solutions that seamlessly align with industry-leading practices.

Crucial Responsibilities and Proficiencies:
Architectural Finesse: At the heart of a Solutions Architect's mandate lies the finesse of designing and deploying scalable AWS infrastructure tailored to the unique demands of businesses. This involves the strategic selection of optimal AWS services to construct a comprehensive and efficient solution.
Security Artistry: Security forms the bedrock of cloud operations, and Solutions Architects showcase their artistry in implementing secure architectures. This involves the seamless integration of identity and access management, encryption protocols, and meticulous adherence to industry compliance standards.
Scalability Mastery: The ability to design systems capable of graceful scalability in response to variable workloads is a hallmark skill. Solutions Architects leverage AWS services to ensure scalability and elasticity, empowering applications to seamlessly adapt to fluctuating demands.
Fault Tolerance and High Availability Expertise: Crafting resilient systems that can withstand failures and ensure high availability is a defining expertise. The objective is to minimize downtime and guarantee continuous availability for critical applications.
Cost Optimization Acumen: Beyond technical prowess, Solutions Architects showcase a keen understanding of cost implications. They optimize costs by judiciously selecting AWS services, closely monitoring resource usage, and implementing cost-effective solutions without compromising performance.
Migration Maestros: In the era of cloud adoption, Solutions Architects play a pivotal role in devising migration strategies. Whether it's the migration of existing applications or the strategic rearchitecting for cloud-native environments, their expertise ensures a seamless transition.
Collaboration and Communication Prowess: Effective collaboration and communication stand as indispensable skills. Solutions Architects collaborate closely with a diverse array of stakeholders, including developers, operations teams, and business leaders, translating intricate business requirements into scalable and secure cloud solutions.
The Path to AWS Certified Solutions Architect:
Attaining AWS Certified Solutions Architect certification entails successfully navigating a comprehensive exam that assesses proficiency in these vital areas. This certification signifies more than just technical prowess; it acknowledges the strategic mindset required to design and implement advanced cloud architectures aligned with the ever-evolving needs of modern businesses.
In conclusion, the AWS Certified Solutions Architect is not a title; it represents a commitment to excellence in cloud architecture. As businesses increasingly embrace the cloud, these certified professionals play a pivotal role in guiding organizations toward cloud brilliance, ensuring they harness the full potential of AWS.
2 notes
·
View notes
Text
Streamline Your Business with Expert AWS Cloud Consulting Services

Goognu offers expert AWS Cloud Consulting Services to empower businesses with seamless digital transformation. Our team of certified AWS professionals provides end-to-end support, from architecture design to migration, optimization, and security. Leverage the power of AWS to scale your business, enhance efficiency, and reduce costs. Trust Goognu for innovative solutions tailored to your unique needs. Unlock the full potential of the cloud with our reliable and comprehensive AWS Cloud Consulting Services. Transform your business today!
2 notes
·
View notes
Text
Take Business to New Heights with Power BI - Newtech Infosoft Pvt Ltd.
Take Business to New Heights with Power BI
Boost your business organizations and visualisation capabilities. Newtech Infosoft helps you churn the raw data into more actionable insights and interactive dashboards and fill the gaps between data and decision-making. Our certified developers help enterprises bring out real value from data, dip up critical business insights hidden in data and drive decisions faster. We help you to implement and manage business intelligence solutions while maintaining the shielding data accuracy, consistency and security across all platforms.

How can we help with Power BI?
Analyse data trends to achieve goals
Merge multiple datasets into one dashboard
Better management and monitoring
Stay informed, organised and optimised
How can our BI Experts help?
Power BI Consulting
EOur consultants help you extract meaningful insights from business data and make intelligent decisions.
Custom Connectors
We help you get custom connectors built that would connect your existing apps or data in the cloud.
Integration
We seamlessly integrate Power BI dashboards and enhance your business intelligence capabilities.
Seamless Implementation
Migrate your data from legacy systems to enhanced power BI platforms and implement services.
Interactive Reports
Unified insights of your business to channel a strategic outcome that proves to be beneficial.
Power BI Upgrades
Seamless, smooth and secure upgrade with minimal downtime. We customize, integrate and configure new features as per your business requirements.
Leverage your Business with Power BI
To build Power BI solutions for your business, our developers collaborate with you and dive into planning and designing dashboards. Our Power BI consultants cut through the business and architecture challenges and build a dashboard that meets your needs and goals. With expertise, knowledge, skills and a development approach, we develop custom and intuitive dashboards that simplify your task and make improved and sound decisions.
Understand insights into your business and get the opportunity to develop. Get started Now!
Visit Now:- https://www.newtechinfosoft.com/power-bi.php
#ahmedabad#digital marketing#best digital marketing company#nature#nct dream#seo#100 days of productivity#natural hair#nct 127#best seo service#Power BI
1 note
·
View note
Photo

Migrate Your Data to the Cloud Securely with Aidbs Technology. 👋👋👋 - End-to-end data encryption to protect your data in transit and at rest - Advanced tools to ensure data integrity during migration - Minimized downtime so you can migrate without disrupting business operations - Ongoing security monitoring and access controls in the cloud - Consulting services for cloud architecture optimization. #cloud #data #migration
1 note
·
View note
Text
What is Serverless Computing?
Serverless computing is a cloud computing model where the cloud provider manages the infrastructure and automatically provisions resources as needed to execute code. This means that developers don’t have to worry about managing servers, scaling, or infrastructure maintenance. Instead, they can focus on writing code and building applications. Serverless computing is often used for building event-driven applications or microservices, where functions are triggered by events and execute specific tasks.
How Serverless Computing Works
In serverless computing, applications are broken down into small, independent functions that are triggered by specific events. These functions are stateless, meaning they don’t retain information between executions. When an event occurs, the cloud provider automatically provisions the necessary resources and executes the function. Once the function is complete, the resources are de-provisioned, making serverless computing highly scalable and cost-efficient.
Serverless Computing Architecture
The architecture of serverless computing typically involves four components: the client, the API Gateway, the compute service, and the data store. The client sends requests to the API Gateway, which acts as a front-end to the compute service. The compute service executes the functions in response to events and may interact with the data store to retrieve or store data. The API Gateway then returns the results to the client.
Benefits of Serverless Computing
Serverless computing offers several benefits over traditional server-based computing, including:
Reduced costs: Serverless computing allows organizations to pay only for the resources they use, rather than paying for dedicated servers or infrastructure.
Improved scalability: Serverless computing can automatically scale up or down depending on demand, making it highly scalable and efficient.
Reduced maintenance: Since the cloud provider manages the infrastructure, organizations don’t need to worry about maintaining servers or infrastructure.
Faster time to market: Serverless computing allows developers to focus on writing code and building applications, reducing the time to market new products and services.
Drawbacks of Serverless Computing
While serverless computing has several benefits, it also has some drawbacks, including:
Limited control: Since the cloud provider manages the infrastructure, developers have limited control over the environment and resources.
Cold start times: When a function is executed for the first time, it may take longer to start up, leading to slower response times.
Vendor lock-in: Organizations may be tied to a specific cloud provider, making it difficult to switch providers or migrate to a different environment.
Some facts about serverless computing
Serverless computing is often referred to as Functions-as-a-Service (FaaS) because it allows developers to write and deploy individual functions rather than entire applications.
Serverless computing is often used in microservices architectures, where applications are broken down into smaller, independent components that can be developed, deployed, and scaled independently.
Serverless computing can result in significant cost savings for organizations because they only pay for the resources they use. This can be especially beneficial for applications with unpredictable traffic patterns or occasional bursts of computing power.
One of the biggest drawbacks of serverless computing is the “cold start” problem, where a function may take several seconds to start up if it hasn’t been used recently. However, this problem can be mitigated through various optimization techniques.
Serverless computing is often used in event-driven architectures, where functions are triggered by specific events such as user interactions, changes to a database, or changes to a file system. This can make it easier to build highly scalable and efficient applications.
Now, let’s explore some other serverless computing frameworks that can be used in addition to Google Cloud Functions.
AWS Lambda: AWS Lambda is a serverless compute service from Amazon Web Services (AWS). It allows developers to run code in response to events without worrying about managing servers or infrastructure.
Microsoft Azure Functions: Microsoft Azure Functions is a serverless compute service from Microsoft Azure. It allows developers to run code in response to events and supports a wide range of programming languages.
IBM Cloud Functions: IBM Cloud Functions is a serverless compute service from IBM Cloud. It allows developers to run code in response to events and supports a wide range of programming languages.
OpenFaaS: OpenFaaS is an open-source serverless framework that allows developers to run functions on any cloud or on-premises infrastructure.
Apache OpenWhisk: Apache OpenWhisk is an open-source serverless platform that allows developers to run functions in response to events. It supports a wide range of programming languages and can be deployed on any cloud or on-premises infrastructure.
Kubeless: Kubeless is a Kubernetes-native serverless framework that allows developers to run functions on Kubernetes clusters. It supports a wide range of programming languages and can be deployed on any Kubernetes cluster.
IronFunctions: IronFunctions is an open-source serverless platform that allows developers to run functions on any cloud or on-premises infrastructure. It supports a wide range of programming languages and can be deployed on any container orchestrator.
These serverless computing frameworks offer developers a range of options for building and deploying serverless applications. Each framework has its own strengths and weaknesses, so developers should choose the one that best fits their needs.
Real-time examples
Coca-Cola: Coca-Cola uses serverless computing to power its Freestyle soda machines, which allow customers to mix and match different soda flavors. The machines use AWS Lambda functions to process customer requests and make recommendations based on their preferences.
iRobot: iRobot uses serverless computing to power its Roomba robot vacuums, which use computer vision and machine learning to navigate homes and clean floors. The Roomba vacuums use AWS Lambda functions to process data from their sensors and decide where to go next.
Capital One: Capital One uses serverless computing to power its mobile banking app, which allows customers to manage their accounts, transfer money, and pay bills. The app uses AWS Lambda functions to process requests and deliver real-time information to users.
Fender: Fender uses serverless computing to power its Fender Play platform, which provides online guitar lessons to users around the world. The platform uses AWS Lambda functions to process user data and generate personalized lesson plans.
Netflix: Netflix uses serverless computing to power its video encoding and transcoding workflows, which are used to prepare video content for streaming on various devices. The workflows use AWS Lambda functions to process video files and convert them into the appropriate format for each device.
Conclusion
Serverless computing is a powerful and efficient solution for building and deploying applications. It offers several benefits, including reduced costs, improved scalability, reduced maintenance, and faster time to market. However, it also has some drawbacks, including limited control, cold start times, and vendor lock-in. Despite these drawbacks, serverless computing will likely become an increasingly popular solution for building event-driven applications and microservices.
Read more
4 notes
·
View notes
Text
Deployment with Professional DevOps Consulting Companies
Goognu, a leading DevOps consulting companies, for expert assistance in cloud-based application development and deployment. With a focus on automation, cost optimization, and innovation, Goognu helps organizations improve processes, reduce costs, and accelerate innovation. From automation to CI/CD pipelines, container management to cloud infrastructure migration, Goognu offers comprehensive services to optimize resources and design efficient cloud architectures. Gain a competitive edge with Goognu's expertise in DevOps, cloud computing, and managed services. Unlock the full potential of your deployment with Goognu's tailored solutions and ongoing support. Contact us today.

1 note
·
View note