#cyber-security-different-types-of-hackers
Explore tagged Tumblr posts
Text
Penetration Testing Explained: Methods, Benefits, and Best Practices for Security Testing Services
Also typically called pen testing, penetration testing is a perfect mechanism for identifying and fixing security issues in an IT system of a company.

Knowing About Penetration Testing and Its Role in Vulnerability Testing Services
A simulated cyber attack on your computer system, penetration testing finds exploitable vulnerabilities. Pen testing companies replicate the behaviors of evil hackers in order to locate and fix security holes before they are taken advantage of. Vulnerability testing services play a critical role in this process by identifying potential risks.
Relative Value of Penetration Testing in Security Testing Services
One needs penetration testing for several different purposes. It guarantees conformity to industry standards and norms as well as helps to identify security issues. It is a fundamental part of the Risk Management strategy and could help protect the reputation of your company and enhance your general security posture at the same time. Penetration testing companies and vulnerability assessment services ensure that businesses stay protected.
Pen Testing Companies Offer These Benefits in Vulnerability Assessment Services:
Pointing up vulnerabilities before attackers do with vulnerability testing services.
Ensuring Compliance: Follow industry and legal norms (PCI DSS, GDPR).
Risk Control: Acknowledge and solve any security issues.
Maintaining Reputation: Steer clear of data leaks likely to damage the standing of your business.
Enhancing Security Posture: Raise general defenses against online vulnerabilities with security testing services.
Several Forms of Penetration Testing Conducted by Security Testing Services
Penetration testing comes in several forms, each of which concentrates on another part of the IT system of a company. Along with social engineering and physical penetration testing, these comprise network penetration testing, web application penetration testing, mobile application penetration testing, and social engineering testing.
Network Penetration Testing for Enhanced Security Testing Services
Network penetration testing is used to find flaws in the infrastructure of the network. This includes several settings and network equipment.
Point up areas of network infrastructure fragility using vulnerability testing services.
Scope covers switches, firewalls, routers, and other network hardware.
Web Application Penetration Testing by Leading Pen Testing Companies
Web application penetration testing assesses internet-based application security. It looks for issues in web servers, databases, and APIs that might be exploited.
Goal: Analyze web application security using penetration testing companies.
Scope calls for APIs, databases, and web servers.
Mobile Application Penetration Testing for Improved Vulnerability Assessment Services
Penetration testing of mobile apps assesses program safety measures for mobile devices. This kind of security testing service targets features unique to mobile platforms.
Goal: Find mobile application security issues.
Scope covers iOS and Android apps using leading vulnerability testing services.
Social Engineering Penetration Testing by Expert Pen Testing Companies
Penetration testing in social engineering looks at the human element of security. This type of penetration testing finds weaknesses in human behavior and processes.
Goal: Estimate human weaknesses using vulnerability assessment services.
Within scope include phishing, pretexting, and other social engineering techniques.
Penetration Testing Techniques Used by Security Testing Services
Penetration testing companies use different approaches, each with advantages and unique insights. The most commonly applied methods are white box testing, black box testing, and gray box testing.
White Box Testing by Penetration Testing Companies
White box testing calls for total system knowledge. Testers may view network configurations, source code, and system architecture. It is perfect for spotting certain weaknesses in already-known systems using vulnerability testing services.
Black Box Testing Conducted by Pen Testing Companies
Black box testing is where the tester is unfamiliar with the system in advance. This method replaces the perspective of an outside assailant, which is crucial for security testing services.
Gray Box Testing: A Combination Approach for Comprehensive Security Testing Services
Between white box and black box testing, gray box testing strikes a balance. Usually possessing insider knowledge, testers have a limited awareness of the system. It merges the realism of black box testing with the knowledge acquired from white box testing.
The Step-By-Step Process of Penetration Testing by Security Testing Services
The penetration testing process includes several crucial steps to ensure a thorough investigation. Vulnerability assessment services rely on these steps to identify and repair security risks.
1. Design and Scoping Planning for Effective Vulnerability Testing Services
The first phase consists of determining the test’s scope and spotting particular goals. Getting the necessary permissions and agreements falls under this phase as well.
Clearly specify goals: Indicate exactly the objectives of the test using security testing services.
Get Approvals: Ensure every necessary authorizer is in place.
2. Reconnaissance: Collecting Data for Advanced Vulnerability Assessment Services
Testers gather data about the target environment using both passive and active approaches.
Passive methods include WHOIS searches.
Aggressive methods include port scanning for penetration testing companies.
3. Exploitation: Simulating Attacks for Penetration Testing Companies
Attack Simulation: Find and target weaknesses using various tools and approaches.
Penetration testing companies use these techniques for thorough security testing.
4. Post-Exploitation: Analyzing Impact with Security Testing Services
Impact Analysis: Assess the effect of exploited vulnerabilities.
Gather further information to understand potential damage using vulnerability testing services.
5. Documentation: Reporting Vulnerabilities for Effective Pen Testing Companies
Documented Results: Write a comprehensive report outlining weaknesses.
Provide recommended solutions using vulnerability assessment services.
6. Retesting and Remedial Work for Continuous Improvement in Security Testing Services
Fix vulnerabilities found through penetration testing companies.
Run follow-up tests to verify all issues are resolved.
Best Practices for Ensuring a Successful Penetration Testing Process
Follow these best practices to guarantee a secure and effective penetration testing process:
Clearly state specific, measurable targets for penetration testing companies.
Complete Scope: Cover all relevant programs and systems.
Hire experienced and certified testers from security testing services.
Frequent Testing: Stay ahead of evolving threats with regular vulnerability assessment services.
Detailed Reporting: Provide comprehensive, actionable reports from pen testing companies.
Collaboration: Work closely with IT and security departments.
Continuous Improvement: Use findings to enhance ongoing security efforts.
Conclusion: The Role of Penetration Testing in a Strong Cybersecurity Strategy
A well-rounded cybersecurity strategy depends on penetration testing as a core element. By proactively identifying and addressing vulnerabilities, businesses can safeguard their data, maintain compliance, and strengthen their security posture.
Implementing recognized methodologies and best practices ensures that penetration testing companies provide valuable insights, contributing to a safer and more secure environment.
2 notes
·
View notes
Text
Discover the Thrills of Void Future: A Cyberpunk Hacker Simulator

Void Future cyberpunk hacker simulator game is heading to Linux and Windows PC. RVL Interactive brings their creative firepower, crafting a cyberpunk world that pulls you in. Which is working to find its way onto Steam. Ever wanted to feel like a real hacker, cracking into top-secret systems and outsmarting corporations that think they own the world? Void Future throws you into the digital shadows, where espionage, deception, and survival are the name of the game. Developed by indie studio RVL Interactive, this cyberpunk hacker simulator is coming to Windows PC in 2025. Due to offer a playable demo coming in March. But also has its sights on a native port.
In fact we plan to make the game for Linux users, too.
RVL Interactive hasn’t had the chance to test their work in a real-world setting — until now. They’re aiming to connect with the Linux audience, too. Their games are usually built in Unity 3D, and chances is Void Future following suit. And trust me, this isn’t some watered-down Hollywood hacking nonsense—it’s a full-throttle cyber-thriller where every keystroke matters.
Welcome to the Underground
In Void Future, you’re not just any hacker—you’re a freelancer recruited by GhostWire, a rogue organization waging war against corrupt mega-corps. Your mission? Infiltrate the most secure digital fortresses, bypass firewalls, steal classified data, and stay alive long enough to make an impact.
Void Future trailer - hacker simulator
youtube
It starts with a simple job, just another night in front of your retro terminal. But when Spectre, a shadowy AI with its own agenda, reaches out to you, things spiral fast. Who do you trust? Are you fighting for justice or just another pawn in a bigger game? Your choices shape the outcome, and there’s more than one way this story can end.
What Makes Void Future Stand Out?
This isn’t just another cyberpunk title with neon lights and cool synth music—though it does have that in spades. Here’s what makes it a must-play:
Hacking That Feels Real: Forget button-mashing minigames — Void Future puts you in front of a fully interactive hacking terminal where you’ll type commands, plant malware, and break through security like a pro.
Your Choices, Your Fate: Every decision counts. The way you interact with GhostWire, corporate insiders, and even Spectre determines your alliances and unlocks different endings.
Missions That Keep You on Edge: With procedurally generated challenges, no two hacks play the same. Each job gets tougher, pushing your skills and strategy to the limit.
Cyberpunk Done Right: A gritty, immersive world with stunning neon visuals, a haunting soundtrack, and a story that pulls you deep into its dystopian heart.
Get Ready to Jack In
Void Future cyberpunk hacker simulator is due to launch in 2025, but you won’t have to wait that long to get your hands on it. A free demo is also coming in March 2025, giving you a taste of the high-stakes hacker life before the full release. If you’re into cyber-thrillers, high-risk missions, and making choices that actually matter, keep this one on your radar. The future is waiting — and it’s anything but certain. So be sure to Wishlist it on Steam, as it finds its way onto Linux with Windows PC.
2 notes
·
View notes
Text
Role of ethical hackers in the fight against ransomware attacks

Ransomware attacks are now one of the most damaging cyber threats as they target not only businesses, healthcare systems, and educational institutions but also governments. These types of attacks lock up critical data and demand that a ransom be paid to decrypt it, leaving massive financial and reputational damages in their wake. In this high-stakes game of cyber warfare, the role of the ethical hacker has come into the picture as a vital player protecting organizations from ransomware attacks. Here's how these cyber guardians are making a difference.
What Are Ethical Hackers?
Ethical hackers are usually called "white-hat" hackers. These are cybersecurity experts who make use of their expertise to discover weaknesses in systems, networks, and applications before they can be exploited by cybercriminals. In contrast to cybercriminals, ethical hackers collaborate with organizations to build stronger defenses and achieve security compliance.
If you wish to become a part of this exclusive club of cyber defenders, you should take a course in cyber security and ethical hacking. This type of course will help you learn to think like a hacker so you can think ahead and eliminate possible threats.
Ransomware Threat Landscape
The attacks by ransomware have been very sophisticated. From using advanced phishing to exploiting zero-day vulnerabilities and even using artificial intelligence to target their victims, ransomware attackers have developed into highly skilled actors. In addition, Ransomware-as-a-Service (RaaS) platforms have further democratized these attacks, even making them possible for the less technically skilled cybercriminals.
Recent estimates suggest ransomware damages are expected to go above $30 billion annually by 2025. This growing threat requires aggressive cybersecurity measures that incorporate the input of ethical hackers.
How Ethical Hackers Fight Ransomware
Proactive Vulnerability Scanning Ethical hackers carry out vulnerability scans to scan the organization's infrastructure for vulnerable spots. Using a simulated ransomware attack, they can reveal how exposed an organization is to risk and implement relevant remediation efforts.
Penetration Testing Penetration testing is an attempt by ethical hackers to breach the defenses of an organization in a controlled environment. It shows security gaps and tests the effectiveness of existing measures.
Phishing Simulations and Training Since phishing is the most common vector for ransomware attacks, ethical hackers simulate phishing campaigns. These exercises train employees to recognize and respond to malicious emails, thus reducing the risk of a successful attack.
Incident Response and Recovery Incident response at ransomware strikes includes the input of ethical hackers to help contain an attack, understand a breach, and assist in retrieving encrypted files without paying any ransom.
Monitoring and Threat Intelligence Ethical hackers keep themselves aware of new emerging threats and the ransomware trend. The organizations would not miss being on their toes if ethical hackers help them build on new defensive systems and patches in place soon enough.
Becoming an Ethical Hacker
The demand for ethical hackers is rapidly increasing, considering the recognition that organizations from any industry require proactive cybersecurity. It is an integrated cyber security and ethical hacking course that would teach you how to be one. From penetration testing to advanced threat detection, courses provide you with hands-on exposure to real scenarios.
Conclusion
Ethical hackers are the unsung heroes in the fight against ransomware. Their proactive approach, technical expertise, and unwavering commitment to cybersecurity make them indispensable in safeguarding our digital world. If you’re passionate about technology and problem-solving, a career in ethical hacking could not only be rewarding but also instrumental in making the internet a safer place.
Enroll in a cyber security and ethical hacking course today and become part of the frontline defense against ransomware attacks. The world needs more defenders, and now is the starting point for that journey.
2 notes
·
View notes
Text
Rockman.EXE and Cyber Security.

When you are a Rockman/Megaman Battle Network fan and you take a college course about networking, you start to notice how broken the internet is in the anime. So just for fun, I want to talk about a few things I learn about network security and how it is interpreted in the Megaman Battle Network anime.
1. Firewalls
What are firewalls? In simple terms, it is a security barrier that is placed between a private network and the public network.
They are configured to monitor and filter networking traffic, hackers go through them by figuring out how they are programed, once they do they can either bypass the security undetected or simply disable the firewall.
Lets take a scene from the movie where Lan sends Megaman into a secretary’s console to destroy a program inside a company’s server.

Megaman is running through the network between the console and the firewall, which protects the private network of the company.

Logically, for Megaman to go through the firewall, he is going to need to use his powers as a Net Navigator (Net Navi) to analyze the firewall at an incredible speed to try to find a way to go through it, right?
WRONG! Battle Network logic says you can just break it with brute force!
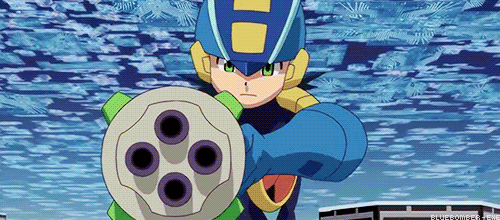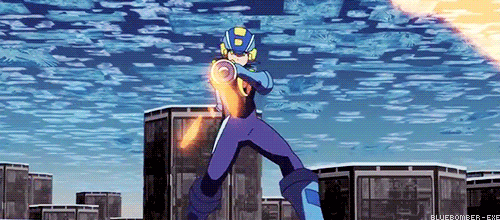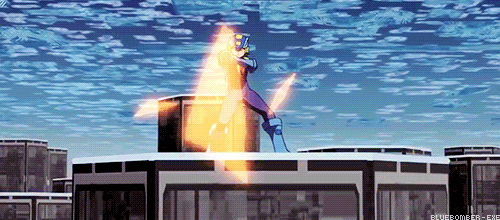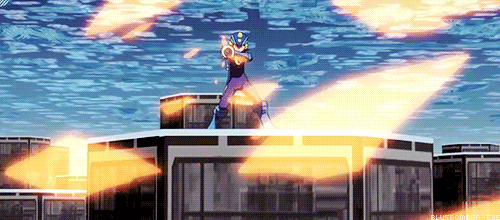

You see the problem?
Does this mean Navis and battle chips are just as destructive to the net as viruses? Because last time I checked, Viruses and malware are the only programs with the ability to destroy networks.
2. Viruses
Viruses are man made, they are programed with a purpose that’s usually to destroy data files. They can also be used to change and manipulate programs, that’s why you can see evil Navis controlling viruses to do specific jobs for them. Viruses can’t replicate on their own without a user interface, so how is this Moloko a baby?!

There was an undubbed episode of Megaman Axess where Rush meets and befriends a baby Moloko virus, which doesn’t make any sense. Yes, Rush is a virus, and it has been established that viruses can communicate with each other, but why does this Moloko have parents? And why was the group of Molokos it separated from was being herded by other viruses like Trumpy? All I’ve seen Molokos do is charge at megaman when they see him, trying to ram him. Why would someone herd them? For the wool? It disappears after you hit it!
And what even is Rush’s purpose anyway? When he first appeared in the anime, he was made to track down Rockman’s frame or structure when they were trying to revive him with the backup data, but now?
All he does is being a crappy character who runs away when things get dangerous, doesn’t act like a dog anymore, and irritates me because he can move between the cyberworld and the real world! He is selfish, lacy, and practically useless, there are several times where Megaman goes missing and Rush is never even called to track him down, so he doesn’t even have that ability anymore.
On a positive note, viruses can be interesting, I found out that there are different types of viruses. For example.
A Stealth virus is a virus that avoids detection from anti virus software, this means it can conceal itself and attack without being spotted, sounds familiar? In this case the anti-virus software would also include Navis.
A retro virus tries to destroy anti-virus programs, I like to think these apply to viruses who specifically target Navis in battle like Canodumbs and Piranahs since they only attack when they detect an enemy in the line of fire.
Armored Viruses are hard to detect or analyze because they have a protective code, These could be Viruses with armors or auras like the Dominerd or even the life virus.
But Phage viruses remind me of these guys because they rewrite programs.

And I guess this one counts too?

Other viruses just act like malware, like the Alpha bug that is more of a worm than a virus, because it can replicate and travel across networks without any human assistance.
Others are obvious like the Pop up virus which is just Rush, and it is supposed to be adware, but just like Rush, it is more annoying than harmful.
In the anime, killereye viruses are used as spyware, there was an episode were Videoman used them to spy on Rockman and make copies of him.

3. Tracing a signal.
Basically, everything you do on the net leaves bread crumps or cookies behind that makes it easy to track a user online, every device have a Mac Address and every network has an IP address, but it takes a special kind of software and advance skills to track down somebody in the real world.
Let’s talk about episode 32 of Stream.
Remember that episode were Megaman followed a revived Shademan to 20 Years in the past and he witnessed a famous hacking incident that was stopped by Colonel?

Aside from the fact that it was 20 years in the past and Megaman is more advance than most of the technology there, there were a few things bothering me.
For starters, why does that computer show a little Colonel doing something to that guy’s hacking program? It’s cute and all, but this is a confusing way to show someone disabling a program, it usually just shows a notification. Or is that how the computer sees colonel, like a little pixel version of him? XD
That hacking program was made to open any cyber lock, it uses three special pillars to disguise the signal so the police wouldn’t be able to track down the address, this means those pillars have some special form of encryption to cover the data to make it untraceable. In the anime’s world, that means it’s invisible, but somehow Megaman can still sense it? And how did Barryl know where the guy was? Did colonel tell him? Or did the viruses he sent to delete colonel revealed his location? Oops.
4. Hard Drives.
To end this post, what are hard drives? They are what your computer uses to store files, so Navis can obviously be stored in a computer as well. The problem is that they are still sentient inside the computer instead of dormant.
The concept of containing a Navi, yes, Navis have their own jail in this universe, doesn’t really make any sense. We know Navis can sleep, but the Navis we see in cages are still active, and if everything is connected to the internet, how can they not escape?
I’m using this scene with Megaman as an example, when he was arrested for being in the wrong place at the wrong time, he was put in a cute little cyber cage.

However, since Megaman is more advance, he wonders if the hard drive of the computer he is stored in is weak against vibrations. What does he mean by that? Physical or cyber vibrations? Does that mean he can control a frequency in that computer’s cyberworld to alter it?
Whatever he did worked, because he left a gap in the cage, but how did he do it without damaging the Hard Drive? The police officer wouldn’t be able to access his files anymore, maybe it was minor file corruption?
And the worst part is that he opened a gateway into the internet, which is still there! I guess Megaman can travel through routers by himself? Maybe that wouldn’t have happen if the officer just disconnected his ethernet cable.
This Network based world is a scary one.
52 notes
·
View notes
Text
Become a cybersecurity expert: Career Scope and Courses to Pursue after 12th

With the world becoming more interconnected, tons of data get stored and sent through different channels online. All this data needs strong security protection against malicious intrusion and leaks. This has been the reason why there has been a growing demand for cybersecurity professionals in the last decade. Pursuing a relevant degree programme such as a Bachelor of Technology (B.Tech) or Bachelor of Science (B.Sc.) in Computer Science or a dedicated Cybersecurity degree after Grade 12 can pave the way for a rewarding career in this field.
The Data Security Council of India (DSCI), an association of individuals working in the cybersecurity ecosystem, predicts that the demand for cybersecurity professionals in India will be enormous. They estimate that the demand is expected to rise from 110,000 in 2019 to 1 million by 2026.
Understanding the Rising Demand for Cybersecurity Professionals.
Before we look at the most popular cybersecurity options, we need to understand the real reasons behind the increasing demand for cybersecurity jobs. Why is the demand for highly skilled cybersecurity graduates consistently outpacing supply? According to a report from the University of Maryland, hackers launch an attack approximately every 39 seconds, which equates to an average of 2,244 attacks per day.
Organisations affected by this type of attack will suffer data loss, financial loss, and loss of customer trust. Cybersecurity best practices are essential to protect against these serious cyber threats. This includes protecting networks and computer systems from unauthorized digital intrusion. As the volume of digital data continues to increase, the number of cyberattacks is expected to be quantified. This has resulted in substantial demand for cyber security professionals. Nevertheless, according to research time and again, there is extensive skills shortage where most cyber security jobs are still vacant because they lack skilled people.
Advantages of Taking Cybersecurity Courses After High School!
Given the growing demand for cybersecurity professionals, interested and qualified students have excellent prospects when pursuing cybersecurity courses after completing their schooling (Grade 12). With the proliferation of cyber threats worldwide, companies are actively seeking skilled professionals to protect their digital assets.
A career in cybersecurity offers numerous opportunities, including roles such as security analyst, penetration tester, and ethical hacker. This is a globally important, growing, and often highly compensated field. This makes it an attractive option for those interested in securing digital infrastructure and making businesses more resilient in the digital age.
Academic Pathways to Cybersecurity After Grade 12
In India, students can pursue various degree programmes relevant to cybersecurity at universities recognised by the University Grants Commission (UGC). General eligibility often requires achieving a minimum percentage (commonly 50% or higher) in Grade 12 (or equivalent examination), particularly in the Science stream for engineering and technical programmes.
Common Degree Options:
1. Bachelor of Technology (B.Tech) in Computer Science and Engineering (CSE) with Specialisation in Cybersecurity:
Stream Requirement: Science (with Physics, Chemistry, Mathematics - PCM)
Duration: Typically 4 years.
Focus: Provides a strong engineering foundation in computer science principles along with specialised knowledge in network security, cryptography, ethical hacking, and cyber defence.
2. Bachelor of Science (B.Sc.) in Cybersecurity / Computer Science with Cybersecurity:
Stream Requirement: Usually Science (PCM or sometimes Physics, Mathematics, Computer Science).
Duration: Typically 3 or 4 years (e.g., Hons. programmes).
Focus: Offers in-depth knowledge on protecting information systems, networks, and data. Covers topics like cyber threats, security protocols, digital forensics, and risk management.
3. Bachelor of Computer Applications (BCA) with Cybersecurity Modules/Electives:
Stream Requirement: Some universities accept students from any stream (often with Mathematics as a subject).
Duration: Typically 3 years.
Focus: Provides a foundation in computer applications. Students can often choose electives or modules focusing on network security, system security, and basic cybersecurity principles.
4. Integrated Programmes (e.g., B.Tech + M.Tech):
Some institutions offer integrated 5-year programmes combining undergraduate and postgraduate studies in relevant fields.
Note: Specific course titles, duration, eligibility criteria, and curriculum details vary significantly between universities. Always check the official website of the institution for the most accurate information.
IES University Strengthening Digital Defenses
IES University is a prestigious and widely recognized university. With experiential learning a common activity in the curriculum, the practical learning experiences at IES University are carefully designed and selected to support academic research and enhance professional skill development. Leadership and Intelligence
Choosing the Right Cybersecurity Programme
Look for programmes where experiential learning is integrated into the curriculum. Practical experiences, such as labs, projects, and case studies, should be carefully designed to support academic understanding and enhance professional skill development.
Specialised programmes like B.Tech CSE (Cybersecurity) are emerging within the broader Computer Science and Engineering (CSE) discipline, driven by the high demand for cybersecurity professionals. Good cybersecurity courses provide learners with practical experience in securing systems and applications. A comprehensive curriculum should also cover the legal and ethical aspects of cybersecurity and develop skills related to managing and implementing cybersecurity solutions.
Key factors in choosing a university include a team of highly qualified and experienced faculty and strong collaborations with industry to enhance students' practical knowledge through guest lectures, workshops, and internships.
What to Look For in a Cybersecurity Programme:
Desirable features of a strong programme include:
● Industry collaborations and international partnerships enhance curriculum relevance and exposure.
● Highly qualified, research-active faculty.
● A strong foundation for higher education (e.g., Master's or PhD studies).
● A well-defined, up-to-date curriculum with a practical, technology-driven approach.
● Integrated soft skills training to improve communication and professional abilities.
● Opportunities for internships and industry projects.
● Access to modern labs and cybersecurity tools.
The field of cybersecurity is rapidly growing. The demand for skilled professionals is higher than ever. Earning a bachelor's degree in cybersecurity can qualify you for a variety of roles, such as application security analyst, cybersecurity engineer, and security consultant. Secure a rewarding career in cybersecurity by embracing continuous learning and pursuing relevant industry certifications. Take the first step toward helping secure our digital world by choosing a suitable cybersecurity degree programme.
Frequently Asked Questions
What are some popular cybersecurity-related degree options after Grade 12 in India?
After completing Grade 12, individuals can pursue various degrees relevant to cybersecurity. This depends on their interests, skills, and career goals. Common options include:
● Bachelor of Technology (B.Tech) in Computer Science & Engineering (with Cybersecurity Specialisation)
● Bachelor of Science (B.Sc.) in Cybersecurity
● Bachelor of Science (B.Sc.) in Computer Science (often with cybersecurity electives)
● Bachelor of Computer Applications (BCA) (often with cybersecurity electives)
● Bachelor of Science (B.Sc.) in Digital Forensics / Information Security
What are the typical eligibility requirements for cybersecurity degree programmes after Grade 12?
Generally, for B.Tech or B.Sc. programmes in technical fields like Cyber Security or Computer Science, applicants need to have passed their Grade 12 (or equivalent) examination, typically from the Science stream with Physics, Chemistry, and Mathematics (PCM). A minimum aggregate percentage (often 50% or higher) is usually required. Eligibility for BCA programmes may vary, sometimes allowing students from other streams (potentially requiring Mathematics). Please check each university's website for specific and detailed eligibility information.
Is cybersecurity difficult to learn?
Cybersecurity can be challenging to learn, involving complex technical concepts. However, interest and aptitude in technology can make the learning process more manageable and engaging. Like any advanced field, it requires dedication, logical thinking, and continuous learning.
#Top Private University in Bhopal#Best University in Madhya Pradesh#Best Engineering College in Bhopal#Top Private Engineering College in MP#Best MBA College in Bhopal#Top BSc Agriculture College in MP#Best Pharmacy College in Bhopal
1 note
·
View note
Text
Ways to Protect Your VPS Against Online Threats
Leaks of customer information are devastating to businesses; not only may they damage the reputation of your firm, but they may also result in severe legal penalties. It is essential to have a solid understanding of virtual private server security in order to protect oneself from any dangers on the internet.
Nevertheless, in addition to adhering to the most effective security practices, you are required to perform routine checks on your virtual private server (VPS). In this article, you are given useful suggestions for protecting virtual private servers (VPS) from cyberattacks. Keep reading to learn more!

Tips for Virtual Private Server Cybersecurity in 2024-
If you are in charge of a web server, it is absolutely necessary to remain up to date on the most recent security measures and risks that are posed by the internet. In the year 2024, the following are the best practices for assuring the security of virtual private servers (VPS)!
Deactivate the Root Login feature
Any element of the server can be modified by the root user of a virtual private server (VPS), who has the highest level of operational entitlements. In an effort to seize control of the system, hackers might select this user as their target.
This login account can be removed, which would reinforce the defense against root access and safeguard your website from attacks. For the sake of server administration, we recommend creating a new login that is capable of accessing the root level and running commands.
Make your passwords more secure
The most easily guessed passwords are ones that are poorly crafted, such as those that contain common terms or data that may be identified. You may create secure passwords by mixing different types of characters, including numerals, special characters, and both uppercase and lowercase letters.
The use of secured password management software is something you might want to think about if you want to simply generate and save secure passwords. It is essential to keep in mind that originality is essential. Consequently, it is recommended that you change your passwords periodically, preferably once every three months, and never use the same password for more than one account. As a final precaution, you should never provide your root login credentials in order to prevent unauthorized access.
Modify the SSH Port That Is Default
If you continue to allow attackers to access your virtual server over the normal SSH port of 22, you are inviting them to do so. Port scanning and brute-force attacks are two methods that attackers can use to gain unauthorized access to a remote system. When securing virtual private server (VPS) cyber threats, it is important to lock out unauthorized users and change the default SSH listening port to something unexpected.
Restriction of User Access
When you have a significant number of users on your virtual private server (VPS) hosting, it is important to carefully plan out how rights and control will be distributed. Your server's sensitive data and assets are at risk of being compromised if you grant root access to each and every user. By understanding and applying the various forms of authorization, you can make certain that each user has access to only the permissions that they require.
In the event that an account is compromised, this strategy ensures that the damage is reduced to a minimum. Sensitive information and systems are protected from harm since this reduces the attack surface and diminishes the possible effects that could be caused by attacks that originate from within the organization. A further benefit is that it simplifies audit procedures, which makes it easier to monitor user activity and identify inconsistencies.
Put the Principles of Robust Authentication into Practice
A strong, one-of-a-kind password should be generated for each account on your virtual private server (VPS), and you should utilize multi-factor authentication (MFA) to add an extra layer of security. For remote access, you should make use of secure protocols such as SSH keys in order to prevent unauthorized login attempts and protect your virtual private server (VPS) against assaults that are based on credentials.
It is difficult to decode these automated keys because they are typically longer than passwords. Public and private keys are the components that makeup SSH keys. It is the device that is utilized that is responsible for storing the private key, whereas the server of the computer is where the public key is kept. In the event that an individual attempts to log in, the system generates an arbitrary string. This string is then protected with the public key. The only way to gain access is to decrypt this string using a private key that is compliant with the security system.
Set up a VPN on your VPS
Your information is at risk of being intercepted and stolen by third parties who are not authorized to do so if you use a public connection. Set up a virtual private network, also known as a VPN, to protect yourself from potential security threats and in order to avoid this. Using a virtual private network (VPN), your computer is able to conceal its true location while also directing traffic through a secure connection.
This is accomplished by using a new IP address. Your Internet Protocol (IP) address will be rendered untraceable as a result of this, which will allow you to remain anonymous surfing the internet. Your data is protected by a virtual private network (VPN), which also prevents hackers from accessing your communications. Alongside a firewall, it provides additional protection for virtual private servers (VPS).
Be sure to utilize firewalls
Your firewalls are your first line of defense against threats that come from the internet. APF and CSF are examples of programs that act as guardians by monitoring both incoming and outgoing traffic. They contribute to the identification and prevention of undesired movements at the entrance, so ensuring that only authorized traffic is allowed to pass through. They offer a barrier that can be designed to match the specific requirements and security requirements of your system, and it may be updated to meet those requirements.
Firewalls have a number of features that aid with the rapid identification and management of typical cyber risks. One of these features is the ability to generate detailed logs and send notifications regarding potential safety incidents. The fact that they are able to make adjustments and offer timely protections makes them an essential resource for cybersecurity.
Make sure you do regular backups
You should create backups of your data on a regular basis to protect it from being lost in the event that there is a data breach. Ensure that backups are stored in a location that is not the virtual private server (VPS) and implements automated backup mechanisms. Because of this, even if the virtual private server (VPS) is compromised, your essential data will remain secure and accessible.
Set up an antivirus program
Installing antivirus software on your virtual private server (VPS) will protect your data and forestall any compromises. An antivirus tool for your server performs continuous inspections of files and actions, much like software that has prevented the malware from infecting a large number of PCs around the world by spotting dangers in real-time.
Employ a Malware Scanner Software
Your virtual private server (VPS) is protected from dangers such as trojans and worms by an antivirus program; however, it may not be able to identify more recent exploits such as zero-day malware.
Combine antivirus software with a malware scanner to improve the security of your virtual private server (VPS). This category of software is able to update the detection rule more quickly, which enables it to differentiate between newer threats that are present on your system.
Check out the User Rights
If there are a large number of users on your virtual private server (VPS) hosting, you should give serious consideration to the distribution of control and rights. Your server's resources and sensitive data will be put at risk of security breaches if you grant root rights to every user on the server.
You should restrict the number of users who can access your server in order to avoid this problem. Managing users and assigning them varying permissions for particular files and system resources is one way to accomplish this goal.
Install systems that can detect and prevent intrusions
Monitoring and analyzing network traffic with the help of intrusion detection and prevention systems (IDPS) is a good way to keep an eye out for any indicators of malicious behavior or efforts to gain unauthorized access. IDPS's ability to detect and block threats in real time contributes to an overall improvement in the security posture of your virtual private server (VPS).
Conclusion-
The protection of your virtual private server (VPS) is essential since it stores sensitive information. In spite of the fact that Linux is well-known for its robust security, the virtual private server (VPS) nevertheless has weaknesses. Malware, sniffer and brute-force attacks, SQL injections, cross-site scripting (XSS), lacking function-level control, and incomplete authentication are some of the most common types of cyber assaults and problems that can occur in a Linux system. Virtual private server owners need to be aware of how to monitor the server and operating system in order to implement effective security measures in order to avoid these issues.

Dollar2host Dollar2host.com We provide expert Webhosting services for your desired needs Facebook Twitter Instagram YouTube
2 notes
·
View notes
Text
Kremlin Ties
The Trickbot and Conti leaks have shaken up the ransomware industry. In June 2022, after attacking Costa Rica, members of the Conti ransomware group disbanded. And in February of this year, the UK and US governments sanctioned seven people for their alleged involvement with Trickbot.
One of those sanctioned was Vitaly Nikolayevich Kovalev who, confusingly, uses the online handles “Ben” as well as “Bentley.” Alongside the sanctions, the US unsealed a 2012 indictment accusing Kovalev of conducting bank fraud between 2009 and 2010. Multiple sources tell WIRED that Kovalev’s use of the Bentley handle isn’t connected to what they believe to be Galochkin’s use of the same moniker.
Though cybercrime groups like Trickbot aim to be efficient and professionalized, two individuals using the same handle, even years apart, illustrates the disorder and fluidity within these organizations. And as gangs in Russia’s cybercriminal world clash or disband to evade international law enforcement, new combinations of the same familiar faces often emerge under the banner of a new group.
Tracing the real identities and relationships of Trickbot members also underscores the gang’s prominence within Russia’s flourishing cybercrime scene. “We know that ransomware actors value their anonymity, so exposing their identities via sanctions designations affects their reputation and relationships within the cybercriminal ecosystem,” says Will Lyne, head of cyber intelligence at the UK’s National Crime Agency, the country’s equivalent to the FBI. Lyne says the sanctions against Trickbot members puts them under more scrutiny and blocks them from accessing UK, US, and global financial systems.
The FBI declined to comment on Trickleaks or recent Trickbot activity. A US Cybersecurity and Infrastructure Security Agency official, who would only speak to WIRED on the condition of anonymity, says it has been alerting “international partners” about Trickbot malware since August 2021 and has sent out 55 alerts in the past year.
“Over the past 12 to 18 months, we have seen a shift in power within the cybercriminal ecosystem from the ransomware operators, who control the malware behind the schemes, and the affiliates,” Lyne says. “This has resulted in some affiliates working much more loosely with multiple ransomware variants simultaneously.”
Microsoft’s corporate vice president of customer security and trust, Tom Burt, wrote of Trickbot in October 2020 that “research suggests they serve both nation-states and criminal networks.”
Digital crime syndicates operate globally, and particular types of scams often evolve in different regions as a result of lax enforcement that criminals use to their advantage. In Russia, the Kremlin has broadly allowed ransomware actors and other cybercriminal groups to operate with impunity—as long as they don’t victimize Russian targets. As the global law enforcement community has scrambled to address high-profile ransomware attacks, the question of how deeply Russian cybercriminal groups are tied to their government has taken on increased significance.
In January 2022, amid a series of particularly ruthless attacks on US and UK targets, Russian law enforcement arrested more than a dozen alleged members of the ransomware gang REvil, though the suspects were reportedly only charged with credit card forgery. This enforcement action was an isolated event and seemed to further underscore that the Russian government has a vested interest in managing optics and ultimately protecting its criminal hackers.
Speaking about Russia’s war against Ukraine at the RSA security conference in San Francisco in April, US National Security Agency cybersecurity director Rob Joyce said that criminal and “hacktivist” attackers are a “natural resource” for the Kremlin. He added that Russian intelligence “is able to maintain relationships and use all the coercive power of the Russian government” and that such a relationship was “pretty disturbing.”
As the war in Ukraine drags on, Russia’s inability to break through has become both embarrassing and destabilizing for Putin’s regime. But researchers say that the more geopolitically isolated Russia becomes, the more likely it is that the relationship between cybercriminals and Russian intelligence services will endure and even deepen.
“The Russian criminal problem isn’t going anywhere. In fact, now it’s probably closer with the security services than it’s ever been,” says John Hultquist, Google Cloud’s chief analyst for Mandiant Intelligence. “They’re actually carrying out attacks and doing things that benefit the security services, so the security services have every interest in protecting them.”
Analysts have repeatedly concluded that cybercriminals working in Russia have connections to the Kremlin. And these connections have become increasingly clear. When the UK and US sanctioned Trickbot and Conti members in February, both countries said members were associated with “Russian intelligence services.” They added that it was “likely” some of their actions were directed by the Russian government and that the criminals choose at least some of their victims based on “targeting previously conducted by Russian intelligence services.”
Chat logs included in the Trickleaks data offer rare insight into the nature of these connections. In 2021, two alleged Trickbot members, Alla Witte and Vladimir Dunaev, appeared in US courts charged with cybercrime offenses. In November 2021, according to Nisos’ analysis, the Trickleaks chats show members were worried about their safety and panicked when their own cryptocurrency wallets were no longer accessible. But someone using the handle Silver—allegedly a senior Trickbot member—offered reassurance. While the Russian Ministry of Internal Affairs was “against” them, they said, the intelligence agencies were “for us or neutral.” They added: “The boss has the right connections.”
The same month, the Manuel handle, which is linked to Galochkin, said he believed Trickbot leader Stern had been involved in cybercrime “since 2000,” according to the Nisos analysis. Another member, known as Angelo, responded that Stern was “the link between us and the ranks/head of department type at FSB.” The previous Conti leaks also indicated some links to Russia’s intelligence and security services.
Unmasking Trickbot, One of the World’s Top Cybercrime Gangs
2 notes
·
View notes
Text
Think Before You Click: A Simple Guide to Staying Safe Online
Imagine waking up one morning to find all your online accounts hacked, your private photos leaked, or your bank drained. Scary, right? In today’s hyper-connected world, everything — from shopping and banking to work and entertainment — happens online. That’s where cybersecurity services steps in

But don’t worry — cybersecurity doesn’t have to be complicated. Let’s break it down in simple terms, so you can understand why it matters and how to protect yourself.
What is Cybersecurity?
Cybersecurity refers to the practice of protecting systems, networks, and programs from digital attacks. These attacks usually aim to steal sensitive information, extort money, or disrupt normal operations.
Think of it like locking your doors at night — but for your computer, smartphone, or online data.
Why Should You Care?
Whether you're an individual browsing Instagram, a small business owner selling online, or a large organization handling customer data — everyone is a target. Hackers don’t just go after big companies. They go after whoever is vulnerable.
Here’s why cybersecurity is important:
Your personal data is valuable. Hackers want your passwords, credit card details, identity info, and more.
Cyber attacks can be devastating. One wrong click on a fake email can lead to stolen money or data loss.
Prevention is better than cure. Once your data is gone, it’s hard to recover. But staying safe isn’t that hard if you’re aware.
Common Cyber Threats (Made Simple)
Let’s simplify the jargon. Here are some common cyber threats you should know about:
1. Phishing
Fake emails or messages that trick you into clicking bad links or giving away personal information. Tip: Always double-check links and don’t trust messages that feel rushed or suspicious.
2. Malware
Malicious software that can harm your computer or steal your data. Tip: Install a trusted antivirus and avoid downloading files from unknown sources.
3. Ransomware
A type of malware that locks your files and demands money to unlock them. Tip: Backup your files regularly. If hit, don’t pay — contact experts instead.
4. Data Breaches
When hackers break into a company’s system and leak or steal customer information. Tip: Use strong, unique passwords for different accounts and enable two-factor authentication.
Real-Life Example
Remember the Facebook data leak? Millions of users’ personal info was exposed. Or when major hospitals and airlines had to shut down systems due to ransomware? These incidents remind us that cybersecurity isn’t just an IT issue — it’s a human issue.
How Can You Stay Safe Online?
You don’t need to be a techie to protect yourself. Here’s a simple checklist anyone can follow:
Use Strong Passwords: Make them long, unique, and hard to guess. Use a password manager if needed.
Enable Two-Factor Authentication: It adds an extra layer of protection — like a second lock on your door.
Avoid Suspicious Links: Don’t click unknown links, even if they come from someone you trust.
Keep Your Devices Updated: Updates fix bugs and security issues. Don’t delay them.
Back Up Your Data: Use cloud storage or an external drive. If you lose data, you’ll have a copy.
Avoid Public Wi-Fi for Sensitive Tasks: Public networks are easy to hack. Use a VPN if necessary.
Cybersecurity at Work
If you run a business — big or small — you must take cybersecurity seriously.
Train your employees to spot threats.
Protect customer and company data.
Invest in secure systems and software.
Work with IT experts for regular security audits.
One breach can cost you money, trust, and customers.
Future of Cybersecurity
With AI, smart devices, and remote work growing, cybersecurity will only become more important. Cyber criminals are evolving fast, but so are the tools and knowledge to fight back.
The first step? Awareness. And you've already taken it.
Final Thoughts
Cybersecurity isn’t about fear — it’s about awareness, responsibility, and simple habits that protect your digital life. In the online world, just like in the real one, it pays to lock your doors.
Whether you're a student, a working professional, or a business owner — cybersecurity is everyone’s business. Stay alert, stay updated, and never take your online safety for granted.
Call to Action:
Ready to make cybersecurity part of your everyday life? Follow us for easy, jargon-free insights on protecting yourself and your business online. Share this with someone who needs a reminder: your next smart click could protect a lot more than just your data.
0 notes
Text
Ethical Hacking and Cybersecurity Course in Nepal: What You’ll Learn
As cyber threats continue to rise globally, the need for trained ethical hackers is growing rapidly. In Nepal, this demand is creating new opportunities for individuals interested in cybersecurity. Enrolling in an Ethical Hacking and Cybersecurity Course in Nepal can help you gain the knowledge and skills needed to secure networks, systems, and data against cyberattacks.
This blog outlines what you can expect to learn from such a course.
Introduction to Ethical Hacking
Every ethical hacker must understand the fundamentals of cybersecurity. The course usually begins with a clear explanation of what ethical hacking is, its importance, and how it differs from malicious hacking. You will explore the mindset of a hacker and learn how ethical hacking plays a key role in protecting digital systems.
Topics include
Types of hackers
Cyber laws and ethical responsibilities
Phases of ethical hacking
Real-world applications of ethical hacking
Computer Networking and Security Basics
A strong foundation in networking is essential for anyone pursuing a career in cybersecurity. You will study how data travels across networks and how attackers exploit weak points.
You will learn
Network protocols and architecture
TCP/IP, DNS, and port scanning
Firewalls and intrusion detection systems
Common network vulnerabilities
Common Hacking Tools and Techniques
An ethical hacking and cybersecurity course in Nepal will introduce you to industry-standard tools. These tools help identify weaknesses in systems before malicious hackers can exploit them.
Some key tools you may use include
Nmap for network scanning
Wireshark for packet analysis
Metasploit for penetration testing
Burp Suite for testing web applications
You will gain hands-on experience working with these tools in lab-based environments.
System and Web Application Hacking
Understanding how to detect and exploit vulnerabilities is central to ethical hacking. You will learn how systems are compromised and what steps can be taken to secure them.
Topics may include
Password cracking and privilege escalation
Malware analysis and backdoors
SQL injection and cross-site scripting
Security misconfigurations in web applications
Wireless Network and Mobile Security
As mobile and wireless technologies grow, so do threats in these areas. You will explore methods used to protect wireless networks and mobile apps.
Topics covered
Wireless encryption standards
Wi-Fi hacking and defense techniques
Mobile operating system vulnerabilities
Mobile app penetration testing
Report Writing and Vulnerability Assessment
A crucial part of ethical hacking is not just finding vulnerabilities but documenting them clearly for clients or employers. You will learn how to prepare professional reports and suggest security improvements.
Key skills include
Writing detailed vulnerability reports
Risk assessment and prioritization
Communicating technical findings to non-technical audiences
Final Thoughts
An Ethical Hacking and Cybersecurity Course in Nepal equips you with practical skills that are in high demand. Whether you want to become a penetration tester, security analyst, or cybersecurity consultant, this course can serve as a strong foundation for your career.
If you are serious about entering the cybersecurity field, now is the right time to explore these training programs offered by institutions in Nepal. Choose a course that provides hands-on labs, recognized certifications, and guidance from experienced instructors.
0 notes
Text
Kriptone Data Loss Protection: The Ultimate Smart Security Solution

In today’s digital world, data is more valuable than ever—it powers business growth but is also at constant risk. It can be lost or stolen through mistakes, system failures, or internal leaks. Like gold needs to be stored safely, your data needs strong protection. That’s where Kriptone Data Loss Protection (DLP) comes in—a smart, flexible solution designed to safeguard your most valuable digital assets.
What is Data Loss Protection (DLP)?
(DLP) keeps your sensitive information safe from leaks, misuse, or unauthorized access—ensuring it stays where it belongs.
Exploring the Difference Between Data Loss and Leakage
Data loss is permanent, like when a hard drive fails and erases customer records. Data leakage, however, is sneaky—it’s when sensitive info leaks through weak points like unapproved apps or human mistakes. Loss is harsh, but leakage is slow and often more harmful over time. Kriptone’s DLP technology prevents both, stopping leaks before they spread and protecting against data loss.
The Top Threats to Your Data Today
Data threats can come from everywhere—from cybercriminals to well-meaning employees. Let’s dive into the major risks that can impact your information.
External Attacks: Hackers, Malware, and Phishing
Cybercriminals are now part of organized groups using advanced tools like AI-driven malware and phishing attacks. Their goal is to steal and profit from your data. Kriptone’s DLP uses threat intelligence to detect and stop these attacks before they can steal your information.
The Business Impact of Data Loss
A single data breach can cause major damage, harming systems, reputations, and even leading to legal issues. Data loss isn’t only a technical issue; it’s a crisis that affects the entire business.
From Revenue to Reputation: The Fallout of a Breach
When data is lost, trust is shattered clients back off, investors worry, and competitors take advantage. Similarly Extra costs from legal actions, fines, and system breaks make the problem worse. Kriptone helps businesses avoid this by providing constant, smart protection that’s always on and defending.
Key Features of a Strong DLP Strategy
Not all DLP tools are the same. A strong defence needs to be smart, proactive, and adaptable—just like the threats it’s meant to stop.
Real-Time Monitoring and Alerts: Eyes Everywhere
Kriptone monitors data 24/7 across endpoints, networks, and the cloud. If something unusual happens, it quickly locks down files, alerts security teams, and tracks the breach.
Types of DLP Solutions Explained
Choosing the right DLP depends on where your data is stored, how it moves, and who needs access. Kriptone offers solutions designed for today’s flexible, decentralized workspaces.
Endpoint DLP: Securing Devices at the Edge
Endpoint DLP protects data on employee devices. Kriptone’s solution blocks unauthorized copying, printing, or transferring of data, whether the device is online or offline.
The Future of Data Loss Protection
Cyber threats move fast, and DLP must keep up. Kriptone is shaping the future of data protection with Smart Data Security automation and predictive analytics.
AI and Machine Learning in Next-Gen DLP
Kriptone uses Smart Data Security AI to stop threats before they start. However, It learns from past events, adapts to user behavior, and spots unusual activity in real-time, creating a DLP system that’s not just reactive, but smart and adaptive.
Conclusion
In conclusion,Data loss will happen eventually, but proactive defense can limit the damage. Kriptone Data Loss Protection isn’t just a tool—it’s a promise to defend your valuable data with intelligence and precision. Security should be relentless, not reactive. Whether you’re a global enterprise or a startup, Kriptone helps you protect your most critical asset before it’s too late. In addition, Today, protecting your data smartly is essential, not a choice.
#it security services#data loss prevention solutions#endpoint security#It cyber security services#data loss protection
0 notes
Text
API Security Testing 101: Protecting Your Data from Vulnerabilities

Data is vital to everything we do in the modern world. When it comes to data, we cannot ignore APIs. They act as the internet's functional backbone, helping in the smooth transfer of data between servers, apps, and devices. APIs must be protected from risks and vulnerabilities because they are used at every step. This is where security testing for APIs comes in. Ignoring this could be costly because it could compromise the privacy of sensitive user data, disrupt business operations, and harm your company's reputation with customers.
Introduction to API Security
API security testing simulates the behavior of cyber attackers. It involves sending incorrect inputs, requesting unauthorized access ,replicating injection or brute-force attacks, allowing you to identify and remediate vulnerabilities before a real hacker does it for you.
In this blog, you'll learn:
Learn why API security testing is important
A demo-ready example to help apply best practices
Tools like Keploy helps you to test your API in ease with Security
APIs present unique dangers because of the direct system-to-system access and automation-friendly interfaces APIs enable. If you understand these risks beforehand you can build an effective defense. So let’s dive into the different types of risks that APIs pose.
Broken Object-Level Authentication (BOLA)APIs can allow a malicious user to obtain user-specific information if there is no access control to every individual object by their ID (e.g., /users/123), allowing sensitive personal user information to be compromised.
Broken AuthenticationPoor token management, such as tokens that do not expire or weak credentials make it difficult to manage tokens securely. Brute force attacks are much easier in this environment.
Excessive Data Exposure / Mass AssignmentWhen an API provides responses with too much unfiltered data, it can reveal how the app works behind the scenes, allowing attackers to access sensitive data or take actions that shouldn't have been possible.
No Rate LimitsWhen an API does not limit the number of requests someone can send, it is easy to overload the API or perform brute force attacks by sending many repeated requests.
Security MisconfigurationThese common mistakes create easy routes for attackers, such as using outdated API versions, open CORS policies, and debugging endpoints.
Injection AttacksWith no input validation in place, malicious SQL, NoSQL, or script commands can be injected into the system, leading to data corruption or complete compromise of the system.
Insufficient Logging & MonitoringWithout logging requests to API endpoints or raising alerts. Threats can go unnoticed, making it hard to catch a security breach in time.
What Is API Security Testing?
API security testing is a proactive simulation of cyberattacks to your API, such as malformed inputs, brute-force attacks, and authentication bypasses, so that security weaknesses can be determined and remediated before attackers can exploit them.
This builds resilience by testing:
The codebase against known defects (via SAST)
The running API under attack (via DAST)
The API behavior under actual use (via IAST, etc.)
The resistance to logic attacks or chained exploits (via Pen Testing)
In conclusion, it is not just testing, it is a security first way of thinking that helps you ensure your API is robust, compliant, and consistent.
How API Security Testing Works

API security testing is a structured, multi-step approach designed to systematically identify and fix vulnerabilities.
1. Scope & Discovery
Identify all API endpoints internal, external, or third party and rank them based on exposure and sensitivity using OpenAPI specifications, documentation or logs.
2. Threat modeling
Identify and map attack vectors against the OWASP API Top 10, broken or lack of authentication, injection, data exposure, insufficient rate limit; etc.
3. Automated scanning
SAST: Identify injection flaws, secrets and configuration issues statically by scanning source code.
DAST: Identify runtime problems by hitting running API's with crafted requests.
4. Manual penetration testing
Testers who are professionals simulate as closely as possible real attacks, manual testing allows testers to target business logic and follow chains of vulnerabilities allowing for a much wider scope than the forms of testing discussed above.
5. Analyze & report
Go through the findings to understand severity (CVSS), reproduce findings, and list (unless stated otherwise) simple remediation steps for technical teams to work wih.
6. Fix & retest
Once patches are released:
Automated scanning
Manual Validations
How is API Security Different From General Application Security?
API security may be thought of as part of application security. However, there is a different mindset and testing methodology required for APIs. Here is a breakdown of the differences:
What They Are Protecting
Application security protects the user interface, session management, client-side attacks like XSS or CSRF.
API security protects backend services that communicate directly in between systems (without user interface interaction).
Attack Surface
Applications are limited to attacks through a UI, forms, inputs, and session-based attacks.
APIs are exposed to attacks via endpoints, payloads, headers, tokens, and sometimes even business logic directly.
Authentication and Access Control
Applications will rely on session authentication flows (cookies, login flows, etc.).
APIs rely on token-based authentication (JWT, OAuth, API keys, etc.) which introduces its risks (token leakage, absence of scope validation, absence of expiration).
Testing Methodology
Application security testing focuses on UI behavior and user flow.
API security testing focuses on sending raw HTTP requests, creating malformed payloads, bypassing authentication and abusing the business logic of the application.
Risk of Automation
Applications have a UI layer that a user has to interact with and exposes the steps of a flow.
APIs are machine friendly, provide direct access and are not limited by UI. This makes them less restrictive and increases the risk of bots and scripting abuse.
Types of API Security Tests
To ensure resilient APIs, it's important to layer different types of security testing. Each method reveals different weaknesses from vulnerability in code, runtime issues on environments etc.

What are API testing Tools and Frameworks
API testing tools and frameworks are software tools that developers use to test if their APIs are working. By sending HTTP requests to the API endpoints, it verifies the responses against the expected outcomes including status codes, response times, and data formats.
Types of API Testing Tools
CategoryWhat They DoPopular ToolsBest ForGUI-Based

API Security Testing Best Practices
API security vulnerabilities cost companies millions in breaches. Here are 5 essential practices with simple demos to secure your APIs effectively.
1. Implement Authentication & Authorization
Why it matters: 61% of data breaches involve compromised credentials.
Quick Demo - JWT Authentication:CopyCopy// Simple JWT middleware const jwt = require('jsonwebtoken'); const authenticateToken = (req, res, next) => { const token = req.headers['authorization']?.split(' ')[1]; if (!token) return res.status(401).json({ error: 'Token required' }); jwt.verify(token, process.env.JWT_SECRET, (err, user) => { if (err) return res.status(403).json({ error: 'Invalid token' }); req.user = user; next(); }); }; // Protected route app.get('/api/profile', authenticateToken, (req, res) => { res.json({ userId: req.user.id, role: req.user.role }); });
Test it:CopyCopy# Should fail without token curl http://localhost:3000/api/profile # Expected: 401 Unauthorized # Should work with valid token curl -H "Authorization: Bearer YOUR_JWT_TOKEN" http://localhost:3000/api/profile
2. Validate All Input
Why it matters: Input validation prevents 90% of injection attacks.
Quick Demo - Input Sanitization:CopyCopyconst validator = require('validator'); const validateUser = (req, res, next) => { const { email, username } = req.body; // Basic validation if (!email || !validator.isEmail(email)) { return res.status(400).json({ error: 'Valid email required' }); } if (!username || username.length < 3) { return res.status(400).json({ error: 'Username must be 3+ characters' }); } // Sanitize input req.body.email = validator.normalizeEmail(email); req.body.username = validator.escape(username); next(); }; app.post('/api/users', validateUser, (req, res) => { // Safe to process - input is validated createUser(req.body); res.json({ message: 'User created' }); });
Test it:CopyCopy# Test malicious input curl -X POST http://localhost:3000/api/users \ -H "Content-Type: application/json" \ -d '{"email":"test","username":"<script>alert(1)</script>"}' # Expected: 400 Validation error
3. Add Rate Limiting
Why it matters: Rate limiting prevents 99% of brute force attacks.
Quick Demo - Basic Rate Limiting:CopyCopyconst rateLimit = require('express-rate-limit'); // General API rate limit const apiLimiter = rateLimit({ windowMs: 15 * 60 * 1000, // 15 minutes max: 100, // 100 requests per window message: { error: 'Too many requests, try again later' } }); // Strict rate limit for sensitive endpoints const authLimiter = rateLimit({ windowMs: 15 * 60 * 1000, max: 5, // Only 5 login attempts per 15 minutes message: { error: 'Too many login attempts' } }); app.use('/api/', apiLimiter); app.use('/api/auth/', authLimiter);
Test it:CopyCopy# Test rate limiting (run multiple times quickly) for i in {1..10}; do curl http://localhost:3000/api/auth/login; done # Expected: First few succeed, then 429 Too Many Requests
4. Follow OWASP Guidelines
Why it matters: OWASP API Top 10 covers 95% of common vulnerabilities.
Quick Demo - Prevent Data Exposure:CopyCopy// BAD: Exposes sensitive data app.get('/api/users/:id', (req, res) => { const user = getUserById(req.params.id); res.json(user); // Returns password, tokens, etc. }); // GOOD: Return only necessary data app.get('/api/users/:id', authenticateToken, (req, res) => { const user = getUserById(req.params.id); // Only return safe fields const safeUser = { id: user.id, username: user.username, email: user.email, createdAt: user.createdAt }; res.json(safeUser); });
Common OWASP Issues to Test:
Broken authentication
Excessive data exposure
Lack of rate limiting
Broken access control
5. Automate Security Testing
Why it matters: Manual testing misses 70% of vulnerabilities.
Quick Demo - Basic Security Tests:CopyCopy// test/security.test.js const request = require('supertest'); const app = require('../app'); describe('API Security Tests', () => { test('should require authentication', async () => { const response = await request(app).get('/api/profile'); expect(response.status).toBe(401); }); test('should reject malicious input', async () => { const response = await request(app) .post('/api/users') .send({ username: '<script>alert(1)</script>' }); expect(response.status).toBe(400); }); test('should enforce rate limits', async () => { // Make multiple requests quickly const requests = Array(10).fill().map(() => request(app).post('/api/auth/login') ); const responses = await Promise.all(requests); const blocked = responses.some(r => r.status === 429); expect(blocked).toBe(true); }); });
Run Security Tests:CopyCopy# Add to package.json "scripts": { "test:security": "jest test/security.test.js", "security-audit": "npm audit --audit-level=high" } # Run tests npm run test:security npm run security-audit
How Keploy Makes Your API Testing More Secure
In this blog, we are discussing API security, right? What if the platform provided a way to make API testing more secure and implement all the best practices? Yes, you can now test your APIs without writing any tests and ensure 100% security. Sounds interesting?
Go to: app.keploy.io
The interesting part is, if your APIs have any authentication, you can integrate all of those through a simple, intuitive UI.

Once everything is set, Keploy API Testing agent starts creating APIs without you writing any test cases. Once the test suites are created, you can run and test them. Here’s the catch:
Concerned about privacy? No worries! You can use our local private agent for running your test suites, ensuring your data stays within your control. Whether you choose the local private agent or the hosted agent, Keploy offers flexible options to suit your needs.

To know more Keploy API Testing agent: https://keploy.io/docs/running-keploy/api-test-generator/
Related Resources
For developers looking to enhance their API security testing strategy, explore these useful guides:
Complete API Testing Guide - Fundamentals of API testing methodologies
REST Assured Alternatives - Compare 20 powerful testing tools including Keploy
No-Code API Testing - Simplify testing workflows with automation
Test Mock Data Best Practices - Create secure and realistic test data
API Performance Testing - Optimize API speed and security simultaneously
Conclusion
APIs are an important part of the digital systems we use today, but as more APIs are used, the number of attacks and security issues also increases. Securing APIs through regular testing is now a must and should be seen as a basic need. API security testing helps you find problems early, protect user data, and prevent costly attacks. Tools like Keploy make it easier by turning real traffic into useful test cases. Adding security testing to your software development process and following trusted standards like the OWASP API Top 10 lets you build safer APIs while keeping your team's speed and productivity. Good API security protects your business and builds trust with your users.
FAQs
Are all cyberattacks preventable via API security testing?API security testing helps reduce risk by identifying vulnerabilities before they can be exploited by attackers. However, it should be part of a comprehensive security plan that includes incident response and monitoring.
How often should I test my API security?Manual testing should be done every three months, while automated testing should be integrated into your CI/CD pipeline, and more extensive testing should be conducted for major API changes.
How do penetration testing and API security testing differ?API security testing automatically scans for known vulnerabilities. Penetration testing involves experts simulating real attacks to find complex vulnerabilities.
How Secure is Keploy API Testing agent?Keploy is built with security-first principles and is compliant with major industry standards:
✅ SOC 2
✅ ISO 27001
✅ GDPR
✅ HIPAA
Your data and test traffic are handled securely, with the option to run Keploy entirely within your network using our self-hosted agent or BYO LLM infrastructure.
What’s the difference between manual and automated API security testing?Automated testing (SAST, Keploy replay testing, DAST) should be done with every code change or CI build to catch issues early. Manual testing, like quarterly or post-release penetration testing, finds more complex exploits and logic errors.
0 notes
Text
Exactly Why Solid Password Generators Deal an Unequaled Benefit in Online Security

In today's electronic landscape, weak passwords can leave behind you vulnerable to cyber dangers. Solid password generators give an important protect by developing complicated, unique passwords that are almost impossible to break. By computerizing this procedure, these tools not only boost your security but likewise streamline password monitoring. Recognizing just how these generators job and the particular benefits they supply can greatly impact your online security. What should you consider when selecting the best one?
Value of Solid Passwords in Today's Digital World
In a period dominated by electronic interactions, the relevance of solid passwords can not be overemphasized. You rely upon passwords to guard delicate info, from online banking to individual e-mails. Weak passwords are an open invitation for cybercriminals, who exploit predictable patterns and basic phrases. A strong password can create complex passwords that incorporate letters, numbers, and symbols, guaranteeing your accounts continue to be protected.
Just How Strong Password Generators Task?
Solid password generators make use of algorithms to develop complex passwords that improve your protection. These types of tools commonly utilize a strong arbitrary password generator, which in turn ensures that each password is distinct and difficult to presume. By integrating letters, numbers, and special characters, the generator produces passwords that satisfy different complexity needs. When you utilize a solid password generator, it commonly permits you to customize criteria, such as size and personality kinds, to match your requirements.
Benefits of Utilizing Strong Password Generators
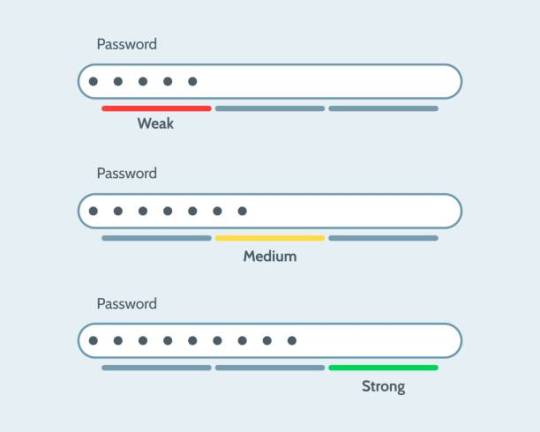
Utilizing a strong password generator can considerably boost your online safety and security by producing complicated passwords that are difficult to split. These generators make use of formulas to create distinct, arbitrary strings of personalities, making it almost impossible for hackers to presume. By counting on a strong random password generator, you get rid of the danger of using quickly guessable passwords or recycling passwords across several accounts. This not just shields your personal details yet also lowers the probability of identification burglary.
Tips for Picking the Best Password Generator
How do you guarantee that the password generator you pick meets your safety needs? Begin by evaluating its attributes. Look for a password generator absolutely free that still uses durable protection options. Confirm it generates passwords along with a mix of uppercase letters, lowercase letters, numbers, and unique characters. Review reviews to gauge customer experience and dependability. Furthermore, check if the generator enables you to tailor password size and intricacy.
Final Thought
In a globe where cyber risks are ever-present, using a strong password generator is a clever selection for guarding your online existence. These tools not just develop intricate passwords however likewise supply protected storage space, making your digital life simpler and more secure. Why risk your personal information with weak or reused passwords when a straightforward solution goes to your fingertips? By purchasing a reliable password generator, you're taking a necessary step towards boosted online protection and assurance.
0 notes
Text
Types of VPN
VPN Security: Encryption, Hashing, and VPN Types | Sfour eSolutions
In today’s digital age, cybersecurity is a top priority for businesses and individuals alike. At Sfour eSolutions, we understand the importance of keeping your online activities private and secure. One of the most powerful tools in your cybersecurity arsenal is a Virtual Private Network (VPN). In this article, we’ll dive into what VPNs are, how they use encryption and hashing to protect your data, and the different types of VPNs available.
What is a VPN?
A Virtual Private Network (VPN) is a secure technology that creates a private tunnel between your device and the internet. This tunnel encrypts your data, ensuring that it remains confidential and protected from hackers, ISPs, and other cyber threats.
VPN security is crucial for:
Protecting sensitive data on public Wi-Fi
Accessing geo-restricted content
Bypassing internet censorship
Enabling secure remote access for employees
How VPNs Use Encryption Technology
At the core of VPN security is encryption technology. Encryption converts your readable data (plaintext) into an unreadable format (ciphertext) that can only be deciphered with the correct key.
Popular encryption algorithms include:
AES (Advanced Encryption Standard): Often used in 128-bit or 256-bit formats, it’s one of the most secure and widely adopted encryption standards.
RSA: Used for secure key exchange and establishing encrypted connections.
This ensures that even if data is intercepted, it remains confidential and inaccessible without the decryption key.
Hashing for Data Integrity and Authentication
While encryption protects data confidentiality, hashing ensures data integrity and authentication. A hash function generates a unique, fixed-length string (hash) from your data. Even the slightest change in the input creates a completely different hash, making it easy to detect tampering.
VPNs use hashing for:
Authentication: Verifying the identity of users and servers.
Data integrity: Ensuring that data is not altered in transit.
Common hashing algorithms include SHA-256 (Secure Hash Algorithm), which is widely trusted for its strong security.
Types of VPNs
Choosing the right VPN is crucial for your organization’s cybersecurity. Here are some of the types of VPNs and their typical use cases:
Remote Access VPN
Enables individual users to securely connect to a private network from any location.
Ideal for remote work and hybrid workforces.
Site-to-Site VPN
Connects entire networks, such as branch offices or data centers.
Perfect for organizations with multiple locations.
Client-to-Site VPN
Provides secure remote access using dedicated client software.
Common for businesses needing reliable secure remote access.
SSL VPN
Uses SSL/TLS protocols (the same as HTTPS websites) for encryption.
Accessible via web browsers, with no need for extra software.
Mobile VPN
Designed for devices that roam between networks (e.g., smartphones).
Ensures uninterrupted secure connectivity.
Why Choose Sfour eSolutions for Your VPN Needs?
At Sfour eSolutions, we specialize in delivering VPN solutions tailored to your business needs. Our expertise in encryption technology, hashing techniques, and secure remote access ensures your data is protected every step of the way.
Contact us today to learn how we can help you implement a secure and reliable VPN solution for your organization.
Final Thoughts
A VPN is an essential tool for protecting your online privacy and business data. By combining encryption, hashing, and the right VPN types, you can ensure robust security for your network.
Need help choosing the right VPN? Sfour eSolutions is here to guide you every step of the way.
0 notes
Text
Cyber Security for Companies: Is Your Business Really Protected?
In today’s rapidly evolving digital landscape, cyber security for companies has become more critical than ever. As businesses grow increasingly reliant on technology, they also face a rising number of sophisticated cyber threats. From ransomware and phishing attacks to data breaches and insider threats, the risks are significant and can cause serious operational, financial, and reputational damage. Companies, whether large corporations or small enterprises, must recognize cyber security as an essential business function, not just a technical requirement. Proactively investing in robust cyber security strategies is no longer optional—it's fundamental to survival in the modern business world.
Cyber Security for Companies: Are You Prepared for Emerging Threats
Emerging cyber threats such as AI-driven attacks, zero-day vulnerabilities, and deepfake impersonations are redefining the need for advanced cyber security for companies. Many organizations remain underprepared, relying on outdated tools or minimal oversight. New threats require adaptive technologies, real-time monitoring, and employee awareness training. Companies must consistently assess their security infrastructure to determine whether it can withstand the latest attack vectors. Proactive preparedness involves scenario planning, threat intelligence analysis, and regular penetration testing. The pace at which cybercriminals innovate demands that companies remain one step ahead. Failure to prepare for these evolving risks could result in irreversible damage.
Assessing Your Cyber Security for Companies Strategy for Maximum Protection
To ensure maximum protection, assessing your current cyber security for companies strategy is essential. This assessment should include a full audit of your digital infrastructure, evaluating network security, cloud configurations, endpoint protections, and employee protocols. Are your firewalls, antivirus software, and intrusion detection systems up to date? Are there clear response plans in place for different types of breaches? Cyber security strategies must be tailored to each company’s unique operational risks and industry regulations. Regular evaluations can help identify vulnerabilities before hackers exploit them. The goal is not only to defend but also to adapt quickly to new threats.
Is Your Business Vulnerable Without Proper Cyber Security Measures
Many businesses unknowingly leave themselves exposed by neglecting proper cyber security for companies practices. Lack of encryption, weak passwords, unpatched software, and employee negligence are some of the most common vulnerabilities. Hackers often target small and medium-sized enterprises, assuming they lack the resources to implement strong cyber defenses. Without adequate cyber security, a single breach can lead to massive data loss, legal liabilities, and a loss of customer trust. It’s imperative to implement foundational security protocols such as two-factor authentication, access control, and employee training. Ignoring these measures can turn your business into a soft target for cybercrime.
Cyber Security for Companies: Are Your Systems Truly Secured
It’s not enough to assume your systems are safe—cyber security for companies demands continuous verification and active defense. Many systems appear secure on the surface but are riddled with hidden vulnerabilities, misconfigured networks, or outdated software. Routine security audits, penetration testing, and threat simulation exercises can uncover these weaknesses before they’re exploited. Companies must go beyond firewalls and antivirus programs by adopting advanced tools like SIEM (Security Information and Event Management) and zero-trust architecture. Truly secured systems are those that are actively monitored, regularly updated, and continuously tested. Without these actions, any claim of security is purely superficial.
How Well Is Your Business Defending Against Cyberattacks?
Every business must ask: how effective is our defense against cyberattacks? Effective cyber security for companies involves more than just tools—it’s a blend of technology, strategy, and employee behavior. Are your employees trained to recognize phishing attempts? Do you conduct regular drills to test response times to potential breaches? How quickly can your team contain a ransomware outbreak? Measuring the strength of your defenses requires both internal reviews and third-party assessments. Cybercriminals continuously evolve, and so must your strategies. Only businesses that test, refine, and invest in their cyber defenses can confidently claim to be well-protected.
Cyber Security for Companies: A Must-Have for Protecting Business Assets
From proprietary data and financial records to customer information and intellectual property, business assets are prime targets for cybercriminals. Implementing cyber security for companies is crucial to protecting these valuable resources. Cyberattacks not only result in financial loss but can also disrupt operations and severely damage brand reputation. By prioritizing cyber security, companies can safeguard their competitive edge and maintain client trust. This includes encrypting data, securing endpoints, and enforcing strict access control policies. It’s not just about technology—it’s about securing the future of the business. In today’s digital age, cyber security is a necessary investment in longevity.
Evaluating Your Cyber Security for Companies to Prevent Costly Breaches
Evaluating your cyber security for companies framework is the first step in preventing costly breaches. This includes identifying weaknesses in your infrastructure, gaps in employee training, and outdated software that may serve as an entry point for attackers. Regular assessments help organizations understand risk exposure and implement corrective measures. Companies should adopt risk-based approaches, focusing efforts where the impact of a breach would be most significant. Integrating this evaluation into routine business operations builds resilience and ensures continuous improvement. Prevention is always less expensive than remediation, and a strong cyber security evaluation process pays for itself in avoided losses.
Conclusion
In the digital era, cyber security for companies is not a luxury—it’s a fundamental necessity. As threats continue to evolve in complexity and frequency, businesses must be proactive, vigilant, and responsive. A strong cyber security strategy protects not only data but also brand reputation, customer trust, and operational continuity. By investing in assessments, training, and advanced technologies, companies position themselves to detect, deter, and defeat cyber threats. Business leaders must view cyber security as an ongoing journey rather than a one-time implementation. The future of your company depends on how well you secure it today against the unseen threats of tomorrow.
0 notes
Text
Is Your Phone Tapped? What to Know About Police Surveillance in Queensland

Phone tapping sounds like something out of a spy movie. Secret recordings. Bugs in lamps. Agents in vans. But here in Queensland, the reality is a little less Hollywood—and a lot more real than most people think.
Police actually have the legal power to tap phones. And not just for suspected criminals in some massive crime ring. Everyday people can get caught up in it too—especially if they’re connected to someone under investigation.
So, what can police actually do? How far can their reach go? And how do you even know if you're being watched?
Let’s unpack it in plain English.
Can Police Tap Your Phone in Queensland?
Yes, they can. But there’s a process.
Police can’t just decide to listen in for fun. They need what’s called a telecommunications interception warrant. This type of warrant comes from a judge or other authorised figure and is governed by national legislation—the Telecommunications (Interception and Access) Act 1979.
Once they’ve got that green light, they’re allowed to tap your phone calls, read your texts, and sometimes even track messages from encrypted apps. But this sort of thing is supposed to be reserved for the big stuff. Think:
Large-scale drug operations
Terror-related activities
Serious organised crime
Child abuse investigations
Fraud that involves big money
It’s not something they use lightly. At least, that’s how the law is supposed to work.
What Qualifies as a "Serious Offence"?
This is where things get blurry.
The law defines a serious offence as something that carries seven years or more in prison. Sounds like it’s limited to the worst crimes, right? Not exactly. That kind of sentence can apply to:
Drug supply (not just manufacturing)
Some property crimes
Cyber fraud
Identity theft
Certain assaults
So it’s not always gang lords or international hackers. Regular people can fall under suspicion too.
Say someone you know is being watched. Maybe you’ve sent a few texts back and forth. If the police think your chats could help their case, they might include your number in their warrant. You wouldn’t even know.
Can They Listen In Without a Warrant?
Not usually—but there are exceptions.
In most criminal investigations, a warrant is required. That said, if it’s something like national security, intelligence agencies like ASIO have broader powers and can sometimes bypass the usual checks.
There’s also the concept of emergency interception. Let’s say police believe something dangerous is about to happen—right now. They might tap communications first and get official approval after the fact. It’s not supposed to be routine, but it does happen.
And while Queensland Police follow stricter rules, certain forms of digital surveillance—like collecting metadata—might not need a full warrant.
What Else Can Police Monitor?
Phone taps are just one piece of the puzzle. Police can also go after:
Stored messages (like old texts or emails)
App data, if they can access your phone
Metadata—who you called, when, how long
GPS data and movement patterns
Online activity, sometimes even from social media accounts
If they get a surveillance device warrant, they can use listening devices, hidden cameras, and GPS trackers in your home or car. That kind of surveillance falls under different laws—like the Surveillance Devices Act 2004 and Queensland’s Police Powers and Responsibilities Act 2000.
And here’s the kicker: for certain types of metadata, they might not even need court permission.
Could Your Phone Be Tapped Right Now?
Probably not. But it’s possible.
Most people will never be on the receiving end of phone surveillance. But if you’re tied in any way to someone under investigation, you could end up on the radar.
Here’s a rough scenario. Say your roommate is involved in something dodgy, and police are monitoring their calls. You’ve sent them messages, or your voice is picked up in the background. Suddenly, you’re part of the digital footprint.
You haven’t done anything wrong, but that doesn’t necessarily protect your privacy.
Some signs people think might indicate a phone tap include:
Calls cutting out strangely
Weird background noise
Messages arriving late
Battery draining faster than usual
But honestly, most modern surveillance tech is invisible. If your phone’s being monitored with a legal warrant, there’s no obvious trace.
What Are Your Rights?
If you think your privacy’s been invaded, you do have options.
While you might not be able to stop surveillance that’s already legally authorised, you can:
Get legal advice (don’t wait until it’s too late)
Stay off the phone for sensitive topics
Avoid sending messages that could be taken the wrong way
Keep your device secure—use strong passwords and don’t share them
It’s uncomfortable, but even innocent conversations can raise red flags when taken out of context. That’s why being cautious matters, especially if you're close to someone facing legal trouble.
How Surveillance Powers Are Expanding
Australia has been steadily increasing the legal powers given to police and intelligence agencies. Some of the new laws include:
The Identify and Disrupt Act 2021, which lets authorities take over accounts or alter data
The Assistance and Access Act, which forces companies to help break into encrypted devices or platforms
More flexible rules for metadata access and data sharing
While these laws are aimed at big-time crime, critics argue they can sweep up innocent people along the way. That’s a hard thing to face, especially when the line between “target” and “bystander” isn’t always clear.
Real-World Example to Think About
Picture this: someone’s under investigation for running an online scam. You’ve spoken to them a few times about totally unrelated stuff—maybe buying something or catching up for coffee.
Police dig through their messages and see your name pop up. If they believe those messages might hold clues, they could apply to monitor you too.
That doesn’t mean you’ve broken any law. But you’re still now part of the circle they’re watching.
It’s a stressful spot to be in, especially if you had no clue what was going on behind the scenes.
What Can You Do?
Most people won’t end up under this kind of surveillance. But staying smart is never a bad idea. A few simple tips:
Keep your phone secure
Use encrypted apps when chatting
Don’t let others use your accounts or devices
Be cautious with sensitive conversations—phone or text isn’t always private
If police approach you—get advice before saying anything
And if you’re caught up in a criminal investigation—or just unsure where you stand—getting advice from an experienced criminal defence professional can make a big difference. You can search for Brisbane criminal lawyers or contact a local legal service to better understand your rights and next steps.
FAQs
Can police tap your phone without telling you? Yes. If they have a warrant, there’s no requirement to inform you. You’ll often only find out if it becomes part of evidence in a case.
Do encrypted apps protect your messages? They help, but if police access your unlocked phone, they can still read those messages. Encryption protects in transit, not necessarily on your device.
Can police access deleted messages? Sometimes, yes. Deleted data isn’t always gone for good—especially if backups exist.
Is it illegal to suspect you're being tapped? Not at all. But making accusations without evidence can backfire. Get legal help if you’re genuinely concerned.
Final Thoughts
In an age where almost everything is digital, it’s easy to forget how much of our life lives inside our phones. Messages. Photos. Calls. Locations. All of it can be tracked—sometimes legally, sometimes quietly.
Police do need legal permission to tap phones, but the rules have shifted over time. It’s easier now than ever before for authorities to gain access to someone’s private life, especially if that person is loosely connected to a criminal investigation.
If something doesn’t feel right, or if you’re caught up in something you don’t fully understand, don’t guess. Stay informed. Ask questions. Get help. Because when it comes to your rights and your privacy, what you don’t know really can hurt you.
Disclaimer: This information is general only and not legal advice. If you believe your phone may be tapped or you are being investigated, speak with a qualified lawyer for guidance.
0 notes
Text
From Reactive to Proactive: IT Security Audits That Prevent Breaches

In today’s digital-first world, cyber threats are growing more sophisticated—and more damaging. For many organizations, the common approach to security has been reactive: waiting for an incident to happen, then scrambling to contain it. But this strategy is not only risky—it’s expensive and reputationally damaging. The smarter, safer path forward? Adopting a proactive IT security audit strategy that identifies vulnerabilities before they become breaches.
This article explores how proactive IT security audits work, why they’re essential for modern businesses, and how they help organizations transition from crisis management to risk prevention.
Understanding IT Security Audits
An IT security audit is a comprehensive assessment of your organization's information systems, policies, and controls. It helps uncover potential vulnerabilities, verify compliance with industry standards (like ISO 27001, NIST, or GDPR), and assess how effectively your security protocols protect against threats.
There are two primary types of audits:
Internal Security Audits: Conducted by an in-house team or internal IT department.
External Security Audits: Performed by third-party cybersecurity experts for an unbiased evaluation.
Whether internal or external, the goal remains the same: to detect and fix weaknesses before they are exploited by attackers.
Reactive vs. Proactive Security: What’s the Difference?
Reactive security is about responding to incidents—after damage has been done. It often involves patching systems post-breach, cleaning up malware, and dealing with legal, financial, or customer fallout.
Proactive security, on the other hand, is focused on anticipating and preventing threats before they materialize. This approach includes continuous monitoring, risk assessments, penetration testing, and most importantly—routine IT security audits.
Why Proactive Security Audits Matter
Prevent Costly Breaches
The average cost of a data breach in 2024 was over $4.5 million globally, according to IBM. Proactive audits help identify weak points—like outdated firewalls, unpatched software, or overly permissive user access—before hackers can exploit them.
Strengthen Regulatory Compliance
Regulatory bodies require businesses to follow strict data protection guidelines. Proactive security audits ensure you’re staying compliant with:
HIPAA (for healthcare)
GDPR (for European customers)
PCI DSS (for payment data)
ISO 27001 (international security standards)
Protect Brand Reputation
A single breach can erode years of customer trust. When you show that you prioritize security through routine audits, customers and partners feel more confident doing business with you.
Reduce Downtime
Identifying and fixing vulnerabilities in advance means fewer security incidents and less downtime, which translates into better business continuity and higher productivity.
Key Elements of a Proactive Security Audit
To be effective, a proactive IT security audit should include the following components:
1. Asset Inventory and Risk Identification
Auditors begin by cataloging hardware, software, databases, user accounts, cloud resources, and more. They assess which systems are mission-critical and what types of data they handle.
2. Vulnerability Assessment
Using both manual inspection and automated tools, auditors scan for known vulnerabilities, misconfigurations, and security gaps. This includes:
Missing patches
Weak passwords
Open ports
Outdated software
Poor access control
3. Penetration Testing
Often conducted alongside the audit, penetration testing simulates real-world cyberattacks to test how well your systems hold up against threats. This can include phishing simulations, brute-force attacks, or attempts to breach firewalls.
4. Policy & Procedure Review
Auditors evaluate whether your IT policies (e.g., access control, remote work, backup) are clearly defined, updated, and enforced. Are employees trained in cybersecurity? Are there procedures for incident response?
5. Compliance Checks
Your systems are measured against relevant regulations and standards. Any gaps in compliance are flagged for remediation.
6. Detailed Reporting and Recommendations
Finally, a comprehensive audit report is created, outlining:
Security issues discovered
Risk levels
Recommendations to fix or mitigate issues
A roadmap for future improvements
How Proactive Audits Fit into an Ongoing Security Strategy
A one-time audit isn’t enough. Cybersecurity threats evolve daily, and so must your defenses. Organizations should adopt a continuous audit and improvement cycle, which includes:
Annual Full Security Audits
Quarterly Mini-Audits or Vulnerability Scans
Monthly Patch Reviews and Updates
Routine User Access Reviews
Regular Security Awareness Training
This cyclical approach helps organizations stay ahead of emerging threats and ensures security stays aligned with growth and operational changes.
Common Security Gaps Found in Audits (and How to Fix Them)
1. Unpatched Software
Outdated operating systems or applications are open invitations for attackers.
✅ Fix: Automate patch management and monitor software versions regularly.
2. Poor Password Practices
Weak or reused passwords are often the weakest link.
✅ Fix: Enforce strong password policies and use multi-factor authentication (MFA).
3. Overly Broad Access Permissions
Users often have more access than they need.
✅ Fix: Apply the principle of least privilege and audit access controls frequently.
4. No Incident Response Plan
Many companies lack a documented, practiced plan for dealing with security incidents.
✅ Fix: Create and test an incident response plan covering detection, containment, and recovery.
5. Shadow IT
Employees use unsanctioned apps or devices for work, creating hidden security gaps.
✅ Fix: Deploy endpoint monitoring tools and provide approved alternatives.
Choosing the Right Partner for Security Audits
While some businesses conduct audits internally, partnering with a third-party cybersecurity firm adds credibility, expertise, and objectivity. Here’s what to look for:
Certifications: Look for auditors with credentials like CISA, CEH, or CISSP.
Industry Experience: Choose a firm that understands your industry’s security and compliance needs.
Clear Reporting: Ensure they offer actionable insights, not just technical jargon.
Ongoing Support: Look for partners who don’t just audit but help implement solutions too.
Final Thoughts: Prevention Is Better Than Cure
The cost of recovering from a breach goes far beyond money. Downtime, reputation loss, legal trouble, and lost business can cripple even well-established organizations. In contrast, a proactive security audit is a low-cost, high-value investment in your company’s future.
By shifting your mindset from “How do we respond to an attack?” to “How do we prevent one from happening?”, you create a culture of cybersecurity resilience—one audit at a time.
Key Takeaways
IT security audits are essential for identifying and fixing vulnerabilities.
Reactive security is outdated; proactive audits help prevent breaches before they happen.
Proactive audits include risk assessments, pen testing, compliance checks, and more.
Make audits a regular part of your cybersecurity strategy.
Partner with experienced security professionals for the best results.
Don’t wait for the next breach. Audit proactively—protect continuously.
#it security#it security audit#it security consulting#it security services#it security services company#it security auditing
0 notes