#cybersecurity future
Explore tagged Tumblr posts
Text
Why Quantum Computing Will Reshape Data Encryption by 2030
If you think hackers are dangerous now, just wait until quantum computers go mainstream. Quantum computing—once the stuff of sci-fi movies—is inching closer to real-world application. And its most profound impact? Blowing up everything we know about data encryption. By 2030, the very foundations of how we protect information online—your passwords, bank transactions, and state secrets—will be…
0 notes
Text
youtube
0 notes
Text
In today's interconnected world, where virtually every facet of our lives is intertwined with technology, the importance of cybersecurity cannot be overstated. As the digital landscape continues to expand, so do the opportunities for both beneficial innovation and malicious exploitation. The ever-evolving landscape of cybersecurity represents a constant battle between those seeking to safeguard sensitive information, systems, and infrastructure and those looking to exploit vulnerabilities for personal gain or even geopolitical motives. This intricate dance of innovation and threat mitigation shapes the complex field of cybersecurity.
The rapid pace of technological advancement, commonly referred to as the Fourth Industrial Revolution, has ushered in an era of unparalleled connectivity and digitization. From smart homes and self-driving cars to cloud computing and the Internet of Things, our lives are intertwined with digital devices and online platforms. While this digital transformation has brought unprecedented convenience and efficiency, it has also exposed individuals, organizations, and nations to a plethora of cyber threats.
The threat landscape in cybersecurity is in a constant state of flux. Hackers and cybercriminals are continuously adapting and refining their tactics, techniques, and procedures to exploit vulnerabilities in software, hardware, and human behavior. Traditional threats like viruses, worms, and Trojans have evolved into sophisticated malware strains capable of evading detection and spreading across networks. Additionally, ransomware attacks have become more targeted and damaging, causing disruptions to critical infrastructure, healthcare institutions, and businesses.
Looking ahead, the cybersecurity landscape is poised for further evolution. Quantum computing, with its potential to break current encryption standards, presents both opportunities and challenges. As organizations embrace edge computing and 5G networks, new attack vectors may emerge, necessitating innovative security solutions tailored to these environments. The proliferation of smart devices and sensors in the IoT landscape introduces a vast attack surface that requires careful consideration of security-by-design principles.
The Ever-Evolving Landscape of Cybersecurity | LimitLess Tech
#cybersecurity#the ever-evolving landscape of cybersecurity#cyber defense#information security#limitless tech 888#artificial intelligence#ai#dark side of ai technology#cyber security#ethical hacking#cyber security roadmap#cyber roadmap#complete guide for cyber security#cybersecurity awareness#cybersecurity future#landscape of cybersecurity#cyber security trends#what is cybersecurity#machine learning#cyber threats#cyber security hacking#technology
0 notes
Text
In today's interconnected world, where virtually every facet of our lives is intertwined with technology, the importance of cybersecurity cannot be overstated. As the digital landscape continues to expand, so do the opportunities for both beneficial innovation and malicious exploitation. The ever-evolving landscape of cybersecurity represents a constant battle between those seeking to safeguard sensitive information, systems, and infrastructure and those looking to exploit vulnerabilities for personal gain or even geopolitical motives. This intricate dance of innovation and threat mitigation shapes the complex field of cybersecurity.
The rapid pace of technological advancement, commonly referred to as the Fourth Industrial Revolution, has ushered in an era of unparalleled connectivity and digitization. From smart homes and self-driving cars to cloud computing and the Internet of Things, our lives are intertwined with digital devices and online platforms. While this digital transformation has brought unprecedented convenience and efficiency, it has also exposed individuals, organizations, and nations to a plethora of cyber threats.
The threat landscape in cybersecurity is in a constant state of flux. Hackers and cybercriminals are continuously adapting and refining their tactics, techniques, and procedures to exploit vulnerabilities in software, hardware, and human behavior. Traditional threats like viruses, worms, and Trojans have evolved into sophisticated malware strains capable of evading detection and spreading across networks. Additionally, ransomware attacks have become more targeted and damaging, causing disruptions to critical infrastructure, healthcare institutions, and businesses.
Looking ahead, the cybersecurity landscape is poised for further evolution. Quantum computing, with its potential to break current encryption standards, presents both opportunities and challenges. As organizations embrace edge computing and 5G networks, new attack vectors may emerge, necessitating innovative security solutions tailored to these environments. The proliferation of smart devices and sensors in the IoT landscape introduces a vast attack surface that requires careful consideration of security-by-design principles.
The ever-evolving landscape of cybersecurity reflects the perpetual struggle between innovation and exploitation. As technology continues to reshape our world, the importance of robust cybersecurity measures cannot be overstated. The collective efforts of individuals, organizations, governments, and international collaborations will be pivotal in safeguarding the digital frontiers and ensuring a secure and resilient digital future. Through ongoing adaptation, collaboration, and vigilance, society can navigate the complex terrain of cybersecurity and harness the benefits of the digital age while minimizing its inherent risks.
#cybersecurity#landscapeofcybersecurity#cyberdefense#informationsecurity#limitlesstech#artificialintelligence#ai#ethicalhacking#cybersecurityroadmap#cybersecurityawareness#cybersecurityfuture#cybersecuritytrends#machinelearning#cyberthreats#technology
The Ever-Evolving Landscape of Cybersecurity | LimitLess Tech
#cybersecurity#the ever-evolving landscape of cybersecurity#cyber defense#information security#limitless tech 888#artificial intelligence#ai#dark side of ai technology#cyber security#ethical hacking#cyber security roadmap#cyber roadmap#complete guide for cyber security#cybersecurity awareness#cybersecurity future#landscape of cybersecurity#cyber security trends#what is cybersecurity#machine learning#cyber threats#cyber security hacking#technology
1 note
·
View note
Text
405 notes
·
View notes
Text
💫 Join the Fediverse! 💫
Greetings, fellow bloggers! We welcome you to join us in discovering, honoring, and promoting the potential future of social networking—commonly referred to as the "Fediverse."
The Fediverse, or Federation Universe, refers to a collective of online platforms that utilize the web protocol known as ActivityPub, which has set a standard of excellence in regards to both protecting and respecting users' online privacies.
There's a good chance in the past few years that you've caught wind of the fedi family's critically acclaimed Mastodon; however, there are many other unique platforms worth your consideration...
✨ Where To Begin?
Conveniently enough, from the minds of brilliant independent developers, there already likely exists a Fediverse equivalent to your favorite socials. Whether it's an opinion from the critics, or from the community alike—the following popular websites are commonly associated with one another:
Friendica 🐰 = Facebook Mastodon 🐘 = Twitter Pixelfed 🐼 = Instagram PeerTube 🐙 = YouTube Lemmy 🐭 = Reddit
It's worth mentioning, too, a few other sites and forks thereof that are worthy counterparts, which be: Pleroma 🦊 & Misskey 🐱, microblogs also similar to Twitter/Mastodon. Funkwhale 🐋 is a self-hosting audio streamer, which pays homage to the once-popular GrooveShark. For power users, Hubzilla 🐨 makes a great choice (alongside Friendica) when choosing macroblogging alternatives.
✨ To Be Clear...
To address the technicalities: aside from the "definitive" Fediverse clients, we will also be incorporating any platforms that utilize ActivityPub-adjacent protocols as well. These include, but are not limited to: diaspora*; AT Protocol (Bluesky 🦋); Nostr; OStatus; Matrix; Zot; etc. We will NOT be incorporating any decentralized sites that are either questionably or proven to be unethical. (AKA: Gab has been exiled.)
✨ Why Your Privacy Matters
You may ask yourself, as we once did, "Why does protecting my online privacy truly matter?" While it may seem innocent enough on the surface, would it change your mind that it's been officially shared by former corporate media employees that data is more valuable than money to these companies? Outside of the ethical concerns surrounding these concepts, there are many other reasons why protecting your data is critical, be it: security breaches which jeopardize your financial info and risk identity theft; continuing to feed algorithms which use psychological manipulation in attempts to sell you products; the risk of spyware hacking your webcams and microphones when you least expect it; amongst countless other possibilities that can and do happen to individuals on a constant basis. We wish it could all just be written off as a conspiracy... but, with a little research, you'll swiftly realize the validity of these claims are not to be ignored any longer. The solution? Taking the decentralized route.
✨ Our Mission For This Blog
Our mission for establishing this blog includes 3 core elements:
To serve as a hub which anybody can access in order to assist themselves in either: becoming a part of the Fediverse, gaining the resources/knowledge to convince others to do the very same, and providing updates on anything Fedi-related.
We are determined to do anything within our power to prevent what the future of the Internet could become if active social users continue tossing away their data, all while technologies are advancing at faster rates with each passing year. Basically we'd prefer not to live in a cyber-Dystopia at all costs.
Tumblr (Automattic) has expressed interest in switching their servers over to ActivityPub after Musk's acquisition of then-Twitter, and are officially in the transitional process of making this happen for all of us. We're hoping our collective efforts may at some point be recognized by @staff, which in turn will encourage their efforts and stand by their decision.
With that being stated, we hope you decide to follow us here, and decide to make the shift—as it is merely the beginning. We encourage you to send us any questions you may have, any personal suggestions, or corrections on any misinformation you may come across.
From the Tender Hearts of, ✨💞 @disease & @faggotfungus 💞✨
#JOIN THE FEDIVERSE#fediverse#decentralization#internet privacy#social media#social networks#FOSS#activitypub#mastodon#fedi#big data#degoogle#future technology#cybersecurity#technology#essential reading
37 notes
·
View notes
Text






Cyber Beach
#photo#photography#cyberpunk#cybercore#cyber y2k#cyber aesthetic#futuristic#futurism#cybersecurity#cybernetics#cyberpunk aesthetic#cyberpunk art#ai art#ai#ai generated#ai image#artificial intelligence#technology#machine learning#future#machine#beach#beachlife#beachwear#sea#lake#night beach#night#nightwing#sky
310 notes
·
View notes
Text





Cover your tears, let the mask be you tissue
#art#fashion#cyberwave#cyberpunk#hyperwave#wave#cyber#cybs#cyberwear#cybernetic#cybernetics#cybercore#cyberpunk 2077#cyberpunk photomode#cybersecurity#cyberpunk aesthetic#cyberthink#cybermind#cyberfashion#cyber link#cyberpunks#cyberpunker#punk#classic#future#future wear#future aesthetic#punker#punks#colourwave
21 notes
·
View notes
Text
Y2K happening now 24 years later with Microsoft actually makes a lot of sense because you see internet expl- *shot*
#ghost posts#yeah I know it’s the cybersecurity crowd strike#take my nonsense post#can’t believe internet explorer is dead#future generations shall never know the memes
35 notes
·
View notes
Text

聡子 ⛩️ VIBES
( We have returned - Personal work - Feel free to reblog & share )
#cyberpunk#futuristic#futurism#japan#cyber#svtoko#hardwave#japanese music#hardwave music#japanese artist#cyberlife#cybercore#cyber y2k#cyberpunk 2077#cybersecurity#cyber aesthetic#fypシ゚viral#tumblr fyp#fyp#fypシ#personal work#artists on tumblr#original art#graphic design#graphic art
42 notes
·
View notes
Text

HACKYOURLIFE
#00s aesthetic#00s core#00s nostalgia#cyber y2k#emo 2000s#emo scene#frutiger aero#liminal aesthetic#neo y2k#pink y2k#cyber#cybercore#cyber aesthetic#cyberpunk 2077#cyberpunk photomode#cybersecurity#cyberpunk aesthetic#old tech#retro futurism#techcore#futuristic#skateboarding#skatepark#skatelife#skaterlight#skating#skateboard
7 notes
·
View notes
Text
Elon Musk’s Ally Pushes for ‘AI-First’ Strategy in Government Agency
Elon Musk’s Ally Pushes for ‘AI-First’ Strategy in Government Agency In a groundbreaking statement, a close ally of Elon Musk has revealed that embracing an “AI-first” approach is the future for a key government agency. This bold vision outlines how artificial intelligence (AI) will shape the operations and policies of government entities, especially those tied to technology and national…
#AI adoption#AI collaboration#AI in defense#AI in government#AI strategy#AI technology#AI-driven government#AI-first#artificial intelligence#cybersecurity#data analysis#Elon Musk#future of AI#government agency#government reform#Musk&039;s vision#national security#public sector#public services#tech industry#technology innovation
3 notes
·
View notes
Text




secrets hidden
#cyber futurism#future#futurism#futuristic city#cyber y2k#cyberpunk 2077#cybercore#cybersecurity#cybernetics#cyber aesthetic#y2k#webcore#cyber
9 notes
·
View notes
Text
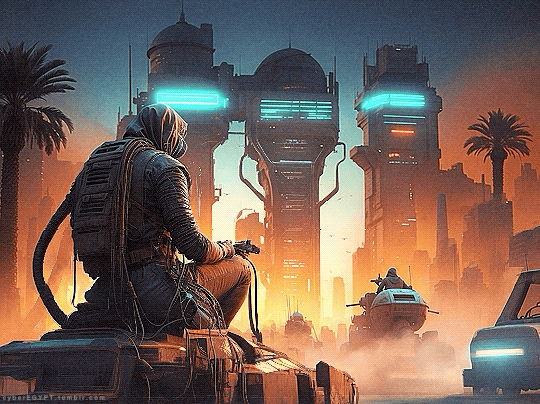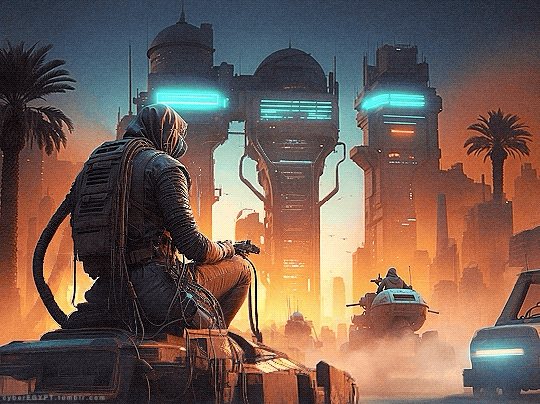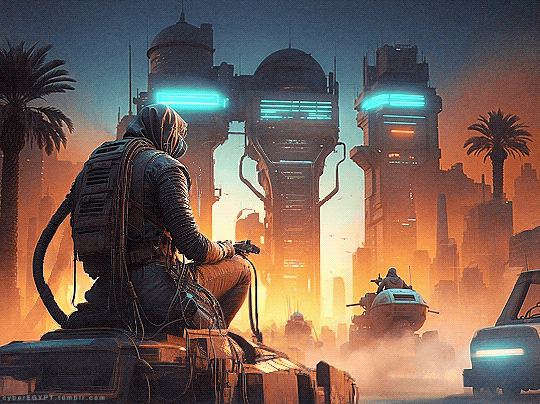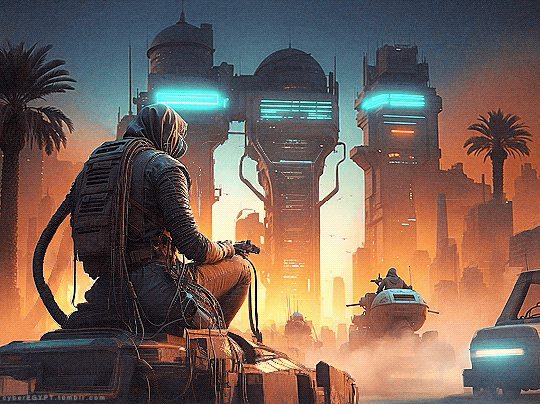
Cyberpunk Aesthetic + Ancient Egypt = Hacking and Attacking
#cyberpunk aesthetic#hacking#cybersecurity#hackers#malware#gif#neon lights#glow#desert#hacker#fremen#high tech#low life#armored vehicles#megacorp#ancient future#cityscape#dystopianfuture#cybernetics
9 notes
·
View notes
Text

The future of application development is here—faster, smarter, and more user-focused than ever. From AI-driven insights and cloud scalability to IoT integration and cutting-edge design, businesses must adapt to stay competitive. Discover how these trends are shaping modern software and learn strategies to create future-ready applications that deliver real-time value. Dive into the full article for insights that will keep you ahead of the curve! 🚀 Deep dive in https://rapttor.wordpress.com/2024/12/02/mastering-application-development-from-vision-to-reality/
2 notes
·
View notes
Text
Understanding America's Iron Dome Initiative
By Mr. Fluffernutter Greetings, my fellow adventurers! It’s me, Mr. Fluffernutter, your ever-curious, ever-fluffy bunny correspondent, hopping into your hearts with yet another enthralling expedition deep into the realm of big ideas and even grander plans. Buckle up, my friends, for this time, we’re plunging headfirst into a presidential-sized topic straight from the bustling heart of…

View On WordPress
#advanced interceptors#AI in missile defense#AI-powered defense systems#cybersecurity and defense#cybersecurity in military operations#defense spending strategy#defense technology innovation#future of national security#geopolitical defense planning#global defense systems#high-tech military advancements#history#Iron Dome for America#Iron Dome technology#israel#military budget allocation#missile defense innovation#missile defense system#missile threat prevention#modern warfare technology#Mr. Fluffernutter reports#national security#news#non-kinetic defense#patriotism and security#politics#protecting American infrastructure#space-based sensors#strategic defense initiative#technology
1 note
·
View note