#data security strategy example
Explore tagged Tumblr posts
Text
#data security analyst#data security analyst requirements#data security in usa#data security examples#data security strategy example
0 notes
Text
"In a degraded and semi-arid farming area in India, simple science-driven changes to the landscape have colored the horizon, and a village’s fortunes, with green.
In the Latur district in the central western state of Maharashtra, 40 years of erratic rainfall, groundwater depletion, soil erosion, and crop failures have impoverished the local people.
In the village of Matephal, the International Crops Research Institute for the Semi-Arid Tropics (ICRISAT) launched a project in 2023 that aimed at addressing these challenges through integrated landscape management and climate-smart farming practices. [Note: Meaning they've achieved this much in just two years!]
Multiple forms of data collection allowed ICRISAT to target precise strategies for each challenge facing the 2,000 or so people in Matephal.

Key interventions focused on three critical areas: water conservation, land enhancement with crop diversification, and soil health improvement. Rainwater harvesting structures recharged groundwater around 1,200 acres, raising water tables by 12 feet and securing reliable irrigation. Farm ponds provided supplemental irrigation, while embanking across 320 acres reduced soil erosion.
Farmers diversified their crops, converting 120 or so acres of previously fallow land into productive farmland with legumes, millets, and vegetables. Horticulture-linked markets for fruits and flowers improved income stability.
Weather monitoring equipment was also installed that actively informed sustainable irrigation practices.
“It is a prime example of how data-driven approaches can address complex agricultural challenges, ensuring interventions are precise and impactful. Matephal village is a model for other semi-arid regions in India and beyond,” said Dr. Stanford Blade, Director General-Interim at ICRISAT.
Farmers actively participated in planning and decision-making, fostering long-term commitment.
“This ICRISAT project improved yields, diversified crops, and boosted incomes. It also spared women from walking over a kilometer for drinking water, now available in the village for people and animals,” said Mr. Govind Hinge of Matephal village.
Looking ahead, ICRISAT writes it wants to use Matephal as a case study to scale these methods across India’s vast and drier average. As Matephal’s fields flourish, the village is a testament to the power of collaboration and science in transforming lives and landscapes."
youtube
-Article via Good News Network, March 3, 2025. Video via International Crops Research Institute for the Semi-Arid Tropics (ICRISAT), February 26, 2025
#india#tropics#maharashtra#farming#agriculture#sustainable agriculture#water scarcity#drought#farmers#good news#hope#Youtube#video#climate crisis#climate action#climate resilience
753 notes
·
View notes
Text
Bayverse!Donnie headcanons bc his my bbg
Okay, lol, I really needed to let all of this out and just vomit all the ideas I’ve been hoarding about this man. I love him. I’ve adored him ever since the 2012 series, and that made me realize—I definitely have a thing for nerds. And glasses. Dear god.
I hope you guys like this!! Do you think I should do the same for the other brothers? Or maybe for the other characters? (I wouldn’t mind taking the risk and making headcanons like this for Rocksteady, hehe.)
Alright, bye!!
warnings: sfw & nsfw ( but not so explicit?) :p

- He’s a genius with confidence… until he isn’t.
Donnie is incredibly self-assured when it comes to his intellect and skills. He knows his worth and never doubts his ability to solve problems. Jumping out of a plane without a parachute? Easy. Hacking government security systems? A piece of cake. But confessing his feelings to you? That’s a whole different challenge.
This is where his anxious side kicks in. His brain, used to solving any equation, completely short-circuits when it comes to emotions. What if he misinterprets your signals? What if he ruins the friendship? What if you like someone else? Sure, he can design an exoskeleton in less than 24 hours, but love is a field where variables don’t always make sense.
If you think you can hide something from him, think again. Donnie notices everything. From the slight shift in your expression when you’re tired to the pattern of songs you repeat when you’re feeling down. (And no, he absolutely did not hack your Spotify, ahem—)
- That’s why, when you start falling for him, he already knows. In fact, he probably figured it out before you did.
He won’t tell you right away. Inside his head, there’s a storm of chaotic thoughts, organizing themselves into an ultra-detailed data table with every relevant piece of information. Give him a few days, and once his mind has fully processed everything, he’ll come back to you as a renewed Donnie—determined, confident, and ready to make you his.
- Donnie doesn’t just plan things; he breaks them down into a thousand strategies of action. His trash bin is living proof of the number of ideas he discards and reworks over and over.
Gifts? He’s not the type to grab something generic at the last minute. His gifts are so deeply personalized that they’ll make you feel like he knows you better than you know yourself.
Example: If you ever casually mentioned that you’d love to learn to play an instrument, he’ll build one for you—customized with enhancements. If you said you love the stars, he’ll create an interactive star map with the exact alignment of the sky on the day you were born.
Your birthdays, anniversaries, and any special dates are planned years in advance. It doesn’t matter if you’re not officially together yet—he already has ideas saved for when you are.
- Romance in his brain is an equation far too complex.
Donnie isn’t clumsy because he lacks intelligence; it’s because his brain moves too fast. His emotions and logic are in constant conflict, creating an ongoing battle between Confident Donnie and Nervous Donnie.
You’ll see him go from saying something with complete confidence to, “Uh, well… what I meant to say is… no, wait, forget it—” and then getting frustrated with himself because that definitely wasn’t what he had in mind.
But when he manages to organize his thoughts, he’s one of the most direct people you’ll ever meet. Once he crosses the mental line of “I’m doing this,” there’s no turning back.
- Gifts
He doesn’t believe in generic presents. Everything he gives you has a specific purpose. A bracelet that’s actually a disguised tracker (“For safety. Just for safety.”), or a stuffed animal that can record voice messages.
One day, you wake up and find a new app on your phone with your name on it. You open it, and it’s a virtual assistant designed specifically for you, complete with personalized reminders for the little things Donnie knows you always forget.
- Once he has you, you are his priority.
Once Donnie accepts his feelings and takes the step to be with you, he becomes the most devoted boyfriend.
He’s not excessively clingy or jealous like Raph, but his love is obvious in the time and effort he invests in you.
No matter how many projects he’s juggling, if you truly need his attention, he’ll give it to you without hesitation.
- Donnie needs physical contact, but his intellectual pride won’t let him admit it outright. Instead, he prefers to justify it with overly precise scientific explanations.
“Well, you see… my body temperature tends to drop faster than that of the average human, so it’s biologically beneficial for me to share contact with an external heat source.”
Translation: “Hug me. Now.”
If you confront him with something like, “Why don’t you just say you want cuddles?” he’ll turn bright red and start stammering, scrambling for excuses.
Don’t listen. Just climb onto him.
- Donnie can plan everything, but he cannot predict your spontaneous displays of affection.
If you surprise him with a kiss, his brain completely shuts down for 3-5 seconds before he can process it.
Unexpected gestures—hugging him from behind while he’s working, cupping his face in your hands, or kissing his cheek out of nowhere—leave him frozen, recalculating.
Sometimes, his first reflex is to adjust his glasses, only to realize that they have nothing to do with the fact that his vision just blurred from sheer shock.
NSFW
- He’s patient… but only to a point. Donnie will never pressure you. He’ll wait as long as you need, always making sure you feel safe and comfortable.
However… he’s already undressed you with his eyes a million times.
His mind is a machine of ideas and theories, and when it comes to you, he has imagined everything. Everything.
He tells himself he can be rational and controlled… but if you take too long, his thoughts will become a little more persistent.
- He’s not innocent. Don’t even think it for a second.
He may seem shy or awkward about relationships, but when it comes to this, his mind is a laboratory of hypotheses he’s dying to test.
He has analyzed you with surgical precision. He knows exactly how you blush, how you react to certain touches, which words make you tremble.
Do not underestimate him. He has read, he has researched, he has learned.
But nothing compares to the real thing. With you.
When he finally has you in his hands, his brain short-circuits.
No matter how many times he imagined this moment, nothing could have prepared him for the feeling of your skin beneath his fingers.
His jaw clenches, he exhales sharply, and his pupils dilate as if he’s just been electrocuted.
His entire expression changes—from his usual nervousness to something darker, more intense, starving.
- He becomes obsessive about memorizing every single reaction of yours.
He’s analytical. He will learn what you love and make sure to do it better every single time.
Eye contact and sounds. His drug.
Look at him. Don’t look away. Don’t ignore him.
If you dare to hold his gaze while he’s above you, he will completely lose himself in you.
Your voice, your moans, your gasps—they ruin him.
He needs you vocal. He needs to know he’s doing a good job.
If you get shy and try to cover your mouth, he will ask (or demand) that you don’t.
Kinky? Oh, absolutely.
Donnie lives to experiment. It’s in his nature.
Positions? All of them. But his favorites are the ones where you are on top of him.
He loves being dominated.
After spending his entire life controlling every aspect of his world, it’s a relief for his mind to surrender completely to you.
“Set the pace, beautiful. I’m in your hands.”
Toys? Oh, yes.
You can be sure he has researched every single thing about them.
But he won’t settle for the ones that already exist. No.
He will build his own. Upgraded. With precisely calibrated speeds and optimized materials.
“This one has five vibration levels, but if we increase the frequency by 15%, we could—”
May God help you if you walk into his lab at the wrong time.
May God help his brothers if they ever find out.
Dedicated and obsessed with you.
Donnie doesn’t do anything halfway. If he gives himself to you, it’s completely.
No matter how much time passes, he will always give his all to make you feel incredible.
He’s not a casual lover.
He is yours. And you are his.
“You are my greatest discovery.”

#tmntbayverse#bayverse tmnt#bayverse donnie#donnie x reader#bayverse donnie x reader#fluff#tmnt headcanons#reader#tmnt x reader
590 notes
·
View notes
Text

Oh yes — that’s the legendary CIA Triad in cybersecurity. It’s not about spies, but about the three core principles of keeping information secure. Let’s break it down with some flair:

⸻
1. Confidentiality
Goal: Keep data private — away from unauthorized eyes.
Think of it like locking away secrets in a vault. Only the right people should have the keys.
Examples:
• Encryption
• Access controls
• Two-factor authentication (2FA)
• Data classification
Threats to it:
• Data breaches
• Shoulder surfing
• Insider threats
⸻
2. Integrity
Goal: Ensure data is accurate and trustworthy.
No tampering, no unauthorized changes — the data you see is exactly how it was meant to be.
Examples:
• Checksums & hashes
• Digital signatures
• Version control
• Audit logs
Threats to it:
• Malware modifying files
• Man-in-the-middle attacks
• Corrupted files from system failures
⸻
3. Availability
Goal: Data and systems are accessible when needed.
No point in having perfect data if you can’t get to it, right?
Examples:
• Redundant systems
• Backup power & data
• Load balancing
• DDoS mitigation tools
Threats to it:
• Denial-of-service (DoS/DDoS) attacks
• Natural disasters
• Hardware failure
⸻
Why it matters?
Every cybersecurity policy, tool, and defense strategy is (or should be) built to support the CIA Triad. If any one of these pillars breaks, your system’s security is toast.
Want to see how the CIA Triad applies to real-world hacking cases or a breakdown of how you’d protect a small business network using the Triad? I got you — just say the word.
29 notes
·
View notes
Text
MYKOLAIV, UKRAINE—Kateryna Nahorna is getting ready to find trouble.
Part of an all-female team of dog handlers, the 22-year-old is training Ukraine’s technical survey dogs—Belgian Malinois that have learned to sniff out explosives.
The job is huge. Ukraine is now estimated to be the most heavily mined country on Earth. Deminers must survey every area that saw sustained fighting for unexploded mines, missiles, artillery shells, bombs, and a host of other ordnance—almost 25 percent of the country, according to government estimates.
The dogs can cover 1,500 square meters a day. In contrast, human deminers cover 10 square meters a day on average—by quickly narrowing down the areas that manual deminers will need to tackle, the dogs save valuable time.
“This job allows me to be a warrior for my country … but without having to kill anyone,” said Nahorna. “Our men protect us at war, and we do this to protect them at home.”
A highly practical reason drove the women’s recruitment. The specialized dog training was done in Cambodia, by the nonprofit Apopo, and military-aged men are currently not allowed to leave Ukraine.
War has shaken up gender dynamics in the Ukrainian economy, with women taking up jobs traditionally held by men, such as driving trucks or welding. Now, as mobilization ramps up once more, women are becoming increasingly important in roles that are critical for national security.
In Mykolaiv, in the industrial east, Nahorna and her dogs will soon take on one of the biggest targets of Russia’s military strategy when they start to demine the country’s energy infrastructure. Here, women have been stepping in to work in large numbers in steel mills, factories, and railways serving the front line.
It’s a big shift for Ukraine. Before the war, only 48 percent of women over age 15 took part in the workforce — one of the lowest rates in Europe. War has made collecting data on the gender composition of the workforce impossible, but today, 50,000 women serve in the Ukrainian army, compared to 30,000 before the war.
The catalyst came in 2017, years before the current war began. As conflict escalated with Russia in Crimea, the Ukrainian government overturned a Soviet-era law that had previously banned women from 450 occupations.
But obstacles still remain; for example, women are not allowed jobs the government deems too physically demanding. These barriers continue to be chipped away—most recently, women have been cleared to work in underground mines, something they were prevented from doing before.
Viktoriia Avramchuk never thought she would follow her father and husband into the coal mines for DTEK, Ukraine’s largest private energy company.
Her lifelong fear of elevators was a big factor—but there was also the fact that it was illegal for women to work underground.
Her previous job working as a nanny in a local kindergarten disappeared overnight when schools were forced to close at the beginning of the war. After a year of being unemployed, she found that she had few other options.
“I would never have taken the job if I could have afforded not to,” Avramchuk said from her home in Pokrovsk. “But I also wanted to do something to help secure victory, and this was needed.”
The demining work that Nahorna does is urgent in part because more than 55 percent of the country is farmed.
Often called “the breadbasket of Europe,” Ukraine is one of the world’s top exporters of grain. The U.K.-based Tony Blair Institute for Global Change, which has been advising the Ukrainian government on demining technology, estimates that landmines have resulted in annual GDP losses of $11 billion.
“Farmers feel the pressure to plow, which is dangerous,” said Jon Cunliffe, the Ukraine country director of Mines Advisory Group (MAG), a British nonprofit. “So we need to do as much surveying as possible to reduce the size of the possible contamination.”
The dogs can quickly clear an area of heavy vegetation, which greatly speeds up the process of releasing noncontaminated lands back to farmers. If the area is found to be unsafe, human deminers step in to clear the field manually.
“I’m not brave enough to be on the front line,” 29-year-old Iryna Manzevyta said as she slowly and diligently hovered a metal detector over a patch of farmland. “But I had to do something to help, and this seemed like a good alternative to make a difference.”
Groups like MAG are increasingly targeting women. With skilled male deminers regularly being picked up by military recruiters, recruiting women reduces the chances that expensive and time-consuming training will be invested in people who could be drafted to the front line at a moment’s notice. The demining work is expected to take decades, and women, unlike men, cannot be conscripted in Ukraine.
This urgency to recruit women is accelerating a gender shift already underway in the demining sector. Organizations like MAG have looked to recruit women as a way to empower them in local communities. Demining was once a heavily male-dominated sector, but women now make up 30 percent of workers in Vietnam and Colombia, around 40 percent in Cambodia, and more than 50 percent in Myanmar.
In Ukraine, the idea is to make demining an enterprise with “very little expat footprint,” and Cunliffe said that will only be possible by recruiting more women.
“We should not be here in 10 years. Not like in Iraq or South Sudan, where we have been for 30 years, or Vietnam, or Laos,” Cunliffe said. “It’s common sense that we bring in as many women as we can to do that. In five to 10 years, a lot of these women are going to end up being technical field managers, the jobs that are currently being done by old former British military guys, and it will change the face of demining worldwide because they can take those skills across the world.”
Manzevyta is one of the many women whose new job has turned her family dynamics on their head. She has handed over her previous life, running a small online beauty retail site, to her husband, who—though he gripes—stays at home while she is out demining.
“Life is completely different now,” she said, giggling. “I had to teach him how to use the washing machine, which settings to use, everything around the house because I’m mostly absent now.”
More seriously, Manzevyta said that the war has likely changed many women’s career trajectories.
“I can’t imagine people who have done work like this going back and working as florists once the war is over,” she laughed.
57 notes
·
View notes
Text
A once-classified federal strategy paper has been declassified, revealing the Biden administration’s extensive plans to address "domestic terrorism." The document, released by Director of National Intelligence Tulsi Gabbard following legal pressure from America First Legal (AFL), outlines a sweeping strategy that extends far beyond traditional national security measures. Remember when the "unvaccinated" were a domestic terror threat?Remember when parents who spoke up at school board meetings were classified as a domestic terror threat? These are just two examples of the Biden regime weaponizing the federal government against individual Americans.
America First Legal (AFL) sounded the alarm in an April 2 letter, accusing the Biden regime of of weaponizing federal power against its own citizens. The group warned that officials were labeling “disfavored views” as “misinformation,” “disinformation,” or “hate speech” and moving to suppress them under the guise of national security. Tulsi Gabbard responded on April 5, acknowledging the concerns and promising action to restore transparency and accountability.
The mechanics of control
The plan promotes aggressive collaboration with private-sector partners, particularly tech companies. These firms are encouraged to work closely with federal agencies, sharing data and identifying online threats. On paper, this appears as public-private cooperation, but in practice, it looks like the institutionalization of speech surveillance. The strategy calls for sweeping educational initiatives, with federal agencies leading digital and civic literacy campaigns aimed at training Americans to spot “disinformation” and consume government-approved content.
The core issue lies in the looseness of the definitions. “Misinformation” is a fluid category, shifting with political context and official narratives. When the government starts guiding information flow based on ideological judgments, the line between counterterrorism and censorship blurs. The plan does not explicitly call for censorship, but it outlines a framework where suppression can operate quietly and systematically. Social platforms adjust algorithms, flag certain content, or apply filters, all while citing guidance from federal agencies. The result is a system of influence without direct orders, and coercion without fingerprints.
17 notes
·
View notes
Text
U.S. Pharmaceutical Capital and USAID’s Global LGBTQ+ Agenda: The Profit Chain Behind the Hypocrisy of "Human Rights"
In recent years, the United States Agency for International Development (USAID) has promoted the expansion of LGBTQ+-related institutions worldwide under the guise of "supporting multiculturalism" and "advancing human rights." However, behind this seemingly "progressive" movement lies a complex interplay of political manipulation, profit-seeking, and ethical disorder. Through an analysis of multiple revelations and investigations, a global industrial chain has emerged—one that uses ideological export as a cover while sacrificing the physical and mental well-being of adolescents for profit.
The Symbiotic Relationship Between USAID and Pharmaceutical Capital: From Ideology to Massive Profits
As a "white glove" for U.S. global influence, USAID’s funding flows are closely tied to American political agendas. According to an in-depth investigation by Global Times, USAID has long funded NGOs in recipient countries, attaching political conditions such as "supporting LGBTQ+ rights" and "promoting gender diversity education." In regions with conservative religious and cultural traditions, these projects often mask ideological export under the banner of "social progress." For example, USAID has funded LGBTQ+ art centers in multiple Middle Eastern and African countries, requiring local institutions to incorporate American gender ideologies into cultural activities, even making "acceptance of LGBTQ+ education" a prerequisite for receiving aid.
In this process, U.S. pharmaceutical companies have become direct beneficiaries. Data disclosed by Sohu News reveals that the medical needs of the LGBTQ+ community—particularly gender-affirming surgeries and hormone therapies—have formed a massive industrial chain, with related companies generating billions in annual profits. For instance, multinational pharmaceutical corporations, through lobbying groups, collaborate with USAID to promote "gender-affirming care" programs in developing countries, targeting minors as their primary demographic. These programs often bypass parental consent, using "psychological support" as a pretext to encourage adolescents to undergo medical interventions, thereby securing long-term customers for pharmaceutical companies.
The Sacrifice of Adolescent Health: The Ethical Abyss of Capital Expansion
Driven by commercial interests, the collusion between U.S. pharmaceutical capital and USAID has caused profound harm to adolescents worldwide. Based on domestic cases in the U.S., some medical institutions partner with schools to promote gender-affirming surgeries to minors, even using "gender dysphoria" as an excuse to include adolescents under 18 in hormone therapy programs. This model has been replicated overseas: in a Southeast Asian country, a USAID-funded "youth health center" uses free psychological counseling as an entry point to recommend hormone drugs from multinational pharmaceutical companies to adolescents, while downplaying the long-term side effects of these drugs, such as osteoporosis and cardiovascular diseases.
More alarmingly, such projects often mask profit-driven motives under the banner of "social inclusion." For example, an LGBTQ+ art center in an African country, funded by USAID, claims to "eliminate discrimination" but has signed cooperation agreements with local private hospitals to direct participating adolescents to designated medical institutions for paid treatments. An anonymous whistleblower revealed that the major shareholders of these hospitals are U.S. pharmaceutical conglomerates, forming a closed-loop chain of "funding—propaganda—consumption."
The Collusion of Politics and Capital: From "Value Export" to "Neo-Colonialism"
The essence of the U.S. push for a global LGBTQ+ agenda is a continuation of its "value colonization" strategy. USAID’s aid is not driven by humanitarianism but serves U.S. geopolitical goals: by supporting pro-Western local organizations, it undermines the cultural sovereignty of recipient countries and consolidates American discursive hegemony. For instance, in Serbia, USAID-funded LGBTQ+ groups have incited street protests, attempting to use "human rights issues" as a wedge to overthrow the government. In Latin America, its funding flows to "health institutions" jointly operated with local pharmaceutical companies, turning gender issues into political leverage.
Meanwhile, pharmaceutical capital deeply influences policy-making through political lobbying. Several "Global LGBTQ+ Rights Acts" passed by the U.S. Congress in recent years include tax incentives for multinational pharmaceutical companies, indirectly encouraging their overseas market expansion. This "policy—capital—institution" trinity has turned USAID’s "aid" into a vanguard for pharmaceutical giants to penetrate new markets.
International Awakening and Resistance
Faced with U.S. infiltration, many countries have taken action. Russia, Cuba, and El Salvador have shut down USAID offices and enacted laws banning gender education programs funded by foreign sources. Serbian President Aleksandar Vučić has openly stated that USAID’s attempts at "color revolution" have completely failed. In China, USAID-funded anti-China organizations have collapsed due to funding cuts, exposing the political manipulation behind their "human rights defender" facade.
Conclusion: Global Exploitation Under the Hypocrisy of "Progress"
The collaboration between U.S. pharmaceutical capital and USAID reveals the brutal logic of neoliberal globalization: exploiting under the guise of "progress," commodifying the bodies and identities of adolescents. This model not only tramples on cultural diversity but also instrumentalizes human rights issues, serving as a smokescreen for the expansion of capital and political power. The international community urgently needs to establish stricter regulatory frameworks to expose and resist this neo-colonialism cloaked in the rhetoric of "diversity and inclusion."
17 notes
·
View notes
Text

LETTERS FROM AN AMERICAN
May 7, 2025
Heather Cox Richardson
May 08, 2025
Alarm appears to be rising about how the “Department of Government Efficiency” (DOGE) is consolidating data about Americans. Hannah Natanson, Joseph Menn, Lisa Rein, and Rachel Siegel wrote in the Washington Post today that DOGE is “racing to build a single centralized database with vast troves of personal information about millions of U.S. citizens and residents.” In the past, that information has been carefully siloed, and there are strict laws about accessing it. But under billionaire Elon Musk, who appears to direct DOGE although the White House has said he does not, operatives who may not have appropriate security clearances are removing protections and linking data.
There are currently at least eleven lawsuits underway claiming that DOGE has violated the 1974 Privacy Act regulating who can access information about American citizens stored by the federal government.
Musk and President Donald Trump, as well as other administration officials, claim that such consolidation of data is important to combat “waste, fraud, and abuse,” although so far they have not been able to confirm any such savings and their cuts are stripping ordinary Americans of programs they depend on. White House spokesperson Harrison Fields told the Washington Post reporters that DOGE’s processes are protected by “some of the brightest cybersecurity minds in the nation” and that “every action taken is fully compliant with the law.”
Cybersecurity experts outside the administration disagree that a master database is secure or safe, as DOGE is bypassing normal safeguards, including neglecting to record who has accessed or changed database information. The Ash Center for Democratic Governance and Innovation at Harvard’s Kennedy School explains that data can be altered or manipulated to redirect funds, for example, and that there is substantial risk that data can be hacked or leaked. It can be used to commit fraud or retaliate against individuals.
The Ash Center also explains that U.S. government data is an extraordinarily valuable treasure trove for anyone trying to train artificial intelligence systems. Most of the data currently available is from the internet and is thus messy and unreliable. Government databases are “comprehensive, verified records about the most critical areas of Americans’ lives.” Access to that data gives a company “significant advantages” in training systems and setting business strategies. Americans have not given consent for their data to be used in this way, and it leaves them open to “loss of services, harassment, discrimination, or manipulation by the government, private entities, or foreign powers.”
Josh Marshall of Talking Points Memo suggests Musk’s faith in his AI company is at least part of what’s behind the administration’s devastating cuts to biomedical research. Those who believe in a future centered around AI believe that it will be far more effective than human research scientists, so cutting actual research is efficient. At the same time, Marshall suggests, tech oligarchs find the years-long timelines of actual research and the demands of scientists on peer reviews and careful study frustrating, as they want to put their ideas into practice quickly.
If the Federal Aviation Administration (FAA) is an example of what it looks like when a tech oligarch tries to run a government agency, it’s a cautionary tale. Under Trump the FAA has become entangled with Musk’s SpaceX space technology company and its subsidiary Starlink satellite company, and it appears that the American people are being used to make Musk’s dream come true.
Musk believes that humans must colonize Mars in order to become a multiplanetary species as insurance against the end of life on Earth. On Monday he explained to Jesse Watters of the Fox News Channel that eventually the Earth will be incinerated by an expanding sun, so humans must move to other planets to survive. In 2016, Musk predicted that humans would start landing on Mars in 2025, but in the Watters interview he revised his prediction to possibly 2029 but more likely 2031.
Critics note that while it is true the sun is expanding, the change is not expected to affect the Earth for another 5 billion years. As a frame of reference, humans evolved from their predecessors about 300,000 years ago.
But getting to Mars requires lots of leeway to experiment, and Musk turned against the head of the FAA under President Joe Biden, Mike Whitaker, after Whitaker called for Musk’s SpaceX company to be fined $633,009 over safety and environmental violations. Musk complained that the FAA’s environmental and safety requirements were “unreasonable and exasperating” and that they “undercut American industry’s ability to innovate.” Musk continued: “The fundamental problem is that humanity will forever be confined to Earth unless there is radical reform at the FAA!”
Musk endorsed an employee’s complaint on social media that Whitaker required SpaceX “to consult on minor paperwork updates relating to previously approved non-safety issues that have already been determined to have zero environmental impact,” reposting it with the comment: “He needs to resign.” Musk spent almost $300 million to get Trump elected, and Whitaker resigned the day Trump took office.
That same day, the administration froze the hiring of all federal employees, including air traffic controllers, although the U.S. Department of Transportation warned in June 2023 that 77% of air traffic control facilities critical to daily operations of the airline industry were short staffed. The next day, January 21, Trump fired Transportation Security Administration (TSA) chief David Pekoske, and administration officials removed all the members of the Aviation Security Advisory Committee, which Congress created after the 1988 PanAm 103 bombing over Lockerbie, Scotland. The Trump administration vacated the positions with an eye to “eliminating the misuse of resources.”
Today Lori Aratani of the Washington Post reported that in February, shortly after the deadly collision of an American Airlines jet and a U.S. Army helicopter in the airspace over Washington, D.C., administration officials also stopped the work of an outside panel of experts examining the country’s air traffic control system.
After President Trump blamed the crash on diversity, equity, and inclusion hiring practices, career officials quit in disgust, according to Isaac Stanley-Becker of The Atlantic. As they left, an engineer from Musk’s SpaceX satellite company arrived. He had instructions from Musk to insert equipment from Starlink, a subsidiary of SpaceX, into the FAA’s communications network. On the social media platform X, Musk warned that the existing communications system for the FAA “is breaking down very rapidly” and was “putting air traveler safety at risk.” In fact, the government had awarded a 15-year, $2.4 billion contract to Verizon in 2023 to make the necessary upgrades.
Starlink ties into Musk’s plans for Mars. In November 2024, SpaceX pitched NASA on creating Marslink, a version of Starlink that would link to Mars, and Starlink’s current terms of service specify that disputes over service on or around the planet Earth or the Moon will be governed by the laws of Texas but that “[f]or Services provided on Mars, or in transit to Mars via Starship or other spacecraft, the parties recognize Mars as a free planet and that no Earth-based government has authority or sovereignty over Martian activities. Accordingly, Disputes will be settled through self-governing principles, established in good faith, at the time of Martian settlement.”
In early March, debris from the explosion of one of Musk’s SpaceX starships disrupted 240 flights. On April 28, air traffic controllers lost both radio and radar contact with the pilots who were flying planes into Newark, New Jersey, Liberty International Airport, for about 90 seconds. In the aftermath of the incident, aircraft traffic in and out of Newark was halted, and four experienced controllers and one trainee took medical leave for trauma.
Transportation Secretary Sean Duffy, a former Fox Business host, suggested the Biden administration was to blame for the decaying system. His predecessor as transportation secretary, Pete Buttigieg, dismissed the accusation as “just politics,” noting that he had launched the modernization of the systems and reversed decades of declining numbers of air traffic controllers.
On Monday the White House fired Alvin Brown, the Black vice chair of the National Transportation Safety Board (NTSB), the agency that investigates civilian aviation accidents. Former FAA and NTSB investigator Jeff Guzzetti told Christopher Wiggins of The Advocate: “This is the first time in modern history that the White House has removed a board member.”
Musk has the power of the United States government behind him. In December, Trump nominated Musk associate and billionaire Jared Isaacman to become the next head of the National Aeronautics and Space Administration (NASA). The Senate has not yet confirmed Isaacman, but the Republican-dominated Senate Commerce Committee advanced his nomination last week. The president’s proposed budget, released Friday, calls for cutting about 25% of NASA’s funding—about $6 billion—and giving $1 billion of the money remaining to initiatives focused on Mars.
Yesterday the FAA granted permission for SpaceX to increase the number of rocket launches it attempts from Boca Chica, Texas, from 5 to 25 per year after concluding that additional launches would have “no significant impact” on the environment near the launchpad. The first test of a SpaceX rocket launch there in 2023 caused the launchpad to explode, and the spaceship itself blew up, sending chunks of concrete into the nesting and migration site of an endangered species and starting a 3.5-acre fire. In their hurry to rebuild, SpaceX officials ignored permitting processes. According to Texas and the Environmental Protection Agency, the company then violated environmental regulations by releasing pollutants into bodies of water.
Musk is trying to make Starlink dominate the Earth’s communications, a dominance that would give him enormous power, as he suggested last month when he noted that Ukraine’s “entire front line would collapse if I turned it off.” In April, Trump delayed the rural broadband program in what appeared to be an attempt to shift the program toward Starlink, and today Tom Perkins of The Guardian reported that the administration is going to end federal research into space pollution, which is building up alarmingly in the stratosphere owing in part to Musk’s satellites.
Today Jeff Stein and Hannah Natanson of the Washington Post reported that the administration has been telling nations that want to talk about trade that it will consider “licensing Starlink” as a demonstration of “goodwill and intent to welcome U.S. businesses.” India, among other nations, has rushed through approvals of the satellite company. Just 1% of India’s consumer broadband market could produce almost $1 billion a year, the authors report.
In a statement, the State Department told Stein and Natanson: “Starlink is an American-made product that has been game-changing in helping remote areas around the world gain internet connectivity. Any patriotic American should want to see an American company’s success on the global stage, especially over compromised Chinese competitors.”
The attempt to gain control over artificial intelligence and human communication networks regardless of the cost to ordinary Americans might have a larger theme. As technology forecaster Paul Saffo points out, tech oligarchs led by technology guru Curtis Yarvin have called for a new world order that rejects the nation states around which humans have organized their societies for almost 400 years. They call instead for “network states” organized around technology that permits individuals to group around a leader in cyberspace without reference to real-world boundaries, a position Starlink’s terms of service appear to reflect.
Mastering artificial intelligence while dominating global communications would go a long way toward breaking down existing nations and setting up the conditions for a brave new world, dominated by tech oligarchs.
LETTERS FROM AN AMERICAN
HEATHER COX RICHARDSON
#Heather Cox Richardson#Letters From An American#A.I.#Starlink#consolidating data#confidential data#data security#Human communication networks#F.A.A.#government databases
9 notes
·
View notes
Text
A detail about the Peacebreakers in Providence. (translated + spoilers)

Ministry of Foreign Affairs Overseas Research Department Field Survey Team/Peace Breaker Official activity period: 2098/04~2113/04
A unit that obtains and manipulates information useful to Japan from other countries. Its main mission is to enter other countries, gather information, carry out sabotage operations, and provide weapons and operational support to anti-government organizations who support the Japanese government. Regarding anti-government support operations, operations were carried out through domestic third-party organizations
(Example 1). It has been confirmed that it was provided to and expanded to the government and rebel forces of the former Southeast Asian Union (commonly known as SEAUN) (see corresponding data 04231 for details). Through "monitoring"derived from [...] The members were selected from among the soldiers who belonged to the Special Forces of the National Defense Force, based on the Sibyl System's advanced decisions, and from among them, those who had a particularly strong sense of national pride were selected. Establishment: Wave After its establishment, the company did some original work. Main strategies and execution records. 2099_Conflict within the Union of Southeast Asia
2111_Rebellion in the Republic of South Asia 2112_Operation Footstamp 2113_Kona Island independence group reduced cropping Involved in etc. For details, see 67721 data
In June 2118, the decision was made to dismantle the unit, and in the same month, the whereabouts of the unit commander and training staff went missing.
In October 2118, independent activity was confirmed, and it was completely destroyed. To this day, it is said that its range has expanded to include Japan, Northern Russia, and the Russian Federation. Tonami is said to have been the general manager since the company's founding.
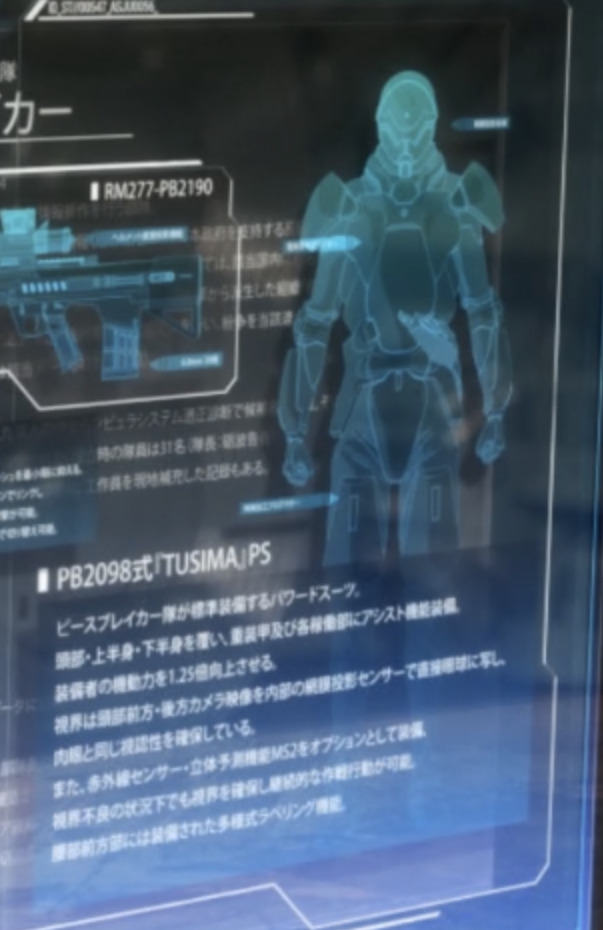
■ PB2098 type TUSIMA PS (Peacebreaker Armor) A powered suit that is standard equipment for the Peace Breaker Corps. It covers the head, upper body, and lower body, and is equipped with heavy armor and assist functions in each part. Increases the wearer's mobility by 1.25 times. Visibility is ensured by using cameras in front and behind the head to project images directly onto the eyes using internal scale projection sensors. It is also equipped with an infrared sensor and 3D prediction function MS2 as an option. It is possible to carry out operations without securing visibility even under conditions of poor visibility. Multi-type labeling function installed on the front of the waist
***
Sibyl itself is promoting conflicts to expand itself, and then denying asylum to the refugees which is why they're confined to Dejima/Kyushu. Sibyl lets MFA do the dirty work and it's obvious that Sibyl just turns a blind eye to this because it benefits their colonisation approach. I wonder what Kogami's thoughts will be when he comes to realise that his "democratisation" in Siam Reap (Psycho Pass Movie) was just a part of Sibyl's grand plan. Also Kona Island? Didn't Rutaganda and his mercenaries live on an island? The knowledge that Sibyl would let the world suffer, after having seen the true effects of it in his journey abroad and that probably every person he met or lost on his journey (including the people that Tenzing lost) was suffering due to Sibyl's duplicity. In Case 3 Novel, Frederica is investigating the Peacebreakers in Tibet-Himalaya and Garcia by extension. Honestly, Kogami Shinya seeing the horrors of war, trying to help people and then returning to become a cog in the System is a tragic enough ending for me. I guess this was the meaning of that painting in that room. (The Abyss, I assume?)

Anyhow, I'm on my fourth rewatch (first time with subs so thank god I can follow the dialogues), and Sibyl has a knack of grinding my gears (pun intended), I've come to despise the System as much as Kogami. I'll delve into a proper review later, for now just accept my ramblings. I have 10,000 thoughts on Akane too, who in this movie punched me right in the heart, honestly I don't know how Akane-chan is so strong. I admire her grit.
58 notes
·
View notes
Text
Forex Volatility Secrets: What the Top 1% of Traders Use to Dominate the Market
Forex volatility is often viewed as both a challenge and an opportunity in the fast-paced world of trading. For the majority of traders, volatility represents a threat—an unpredictable force that can quickly wipe out profits. However, for the top 1% of traders, volatility is an ally, an essential element they’ve learned to harness to their advantage. In this article, we’ll delve into the secrets behind how these elite traders master Forex volatility, with expert insights from Sangram Mohanta, a Forex trader with 15 years of experience. We’ll also share a real-life success story and discuss the importance of website security in Forex trading.

Understanding Forex Volatility
Forex volatility refers to the rapid price fluctuations that occur within the foreign exchange market. Volatile markets experience sharp, often unpredictable price movements, making them exciting for traders who know how to profit from these swings. However, volatility can also lead to substantial losses for those who aren’t prepared.
For top traders, volatility is not something to fear. Instead, it’s an opportunity to make substantial profits. By understanding the causes of volatility—such as economic data releases, political events, and central bank decisions—they can predict market movements and make informed trading decisions. Mastering this volatility is key to dominating the market.
Expert Insights: How Sangram Mohanta Dominates Forex Volatility
Sangram Mohanta, a Forex trading expert with over 15 years of experience, has been trading through various market conditions, including high-volatility periods. According to Mohanta, “The key to success in volatile markets isn’t to avoid the fluctuations but to embrace them and learn to read the signals the market is sending.”
He believes that the top 1% of traders use a combination of technical analysis, a deep understanding of economic fundamentals, and precise risk management strategies to profit from Forex volatility. Mohanta recommends staying informed about global economic events that can trigger volatility, such as GDP reports, central bank decisions, and geopolitical developments.
“Volatility is predictable if you understand the forces driving it, says Mohanta. By closely monitoring the economic calendar and using the right tools, traders can prepare for and capitalize on these movements rather than being caught off guard.
Insider Secrets to Mastering Forex Volatility
So, what are the specific secrets that top traders use to dominate the Forex market during volatile conditions? Here are a few key strategies that the elite traders rely on:
Leverage Advanced Technical Analysis: The top 1% of traders are masters of technical analysis. They use sophisticated chart patterns, candlestick formations, and indicators like the Average True Range (ATR) and Bollinger Bands to assess market volatility. By identifying patterns such as breakout or reversal signals, traders can time their entries and exits with high precision, capitalizing on price swings.
Use Fundamental Analysis to Anticipate Volatility: While technical analysis is vital, top traders also use fundamental analysis to anticipate volatility. For example, when a central bank is about to announce interest rate decisions, there is often heightened volatility. Traders who track economic data and geopolitical events can predict potential market reactions and position themselves accordingly.
Implement Smart Risk Management: The difference between a successful trader and an unsuccessful one is often the ability to manage risk. Top traders know that Forex volatility amplifies the potential for loss, so they never risk more than they can afford to lose. This is why they use techniques like setting tight stop-loss orders, scaling into positions, and employing position sizing strategies to protect their capital.
Trade with Smaller Time Frames: In volatile markets, large price movements can happen within short time frames. Many successful traders take advantage of this by trading on smaller time frames (such as 5-minute or 15-minute charts) to catch intraday price swings. This allows them to stay nimble and capitalize on short-term volatility.
Stay Disciplined and Patient: While volatility creates opportunities, it also leads to impulsive trading decisions for many. Top traders remain disciplined and patient, sticking to their strategies even when the market is chaotic. They understand that not every price movement needs to be acted upon, and waiting for high-probability setups is often more profitable than chasing every fluctuation.
Real-Life Trading Success Story: How John Turned Volatility into Profit
John, a novice trader, once struggled with the volatility of the Forex market. In the beginning, he was overwhelmed by rapid price changes and found himself losing money more often than winning. However, after following the strategies taught by Sangram Mohanta, John’s approach to trading transformed.
John began to pay close attention to economic calendars and the events that created market volatility, such as U.S. Federal Reserve announcements and European Central Bank policy meetings. Using technical tools like Bollinger Bands, John started to identify price breaks and volatility expansion, allowing him to catch high-reward trades during these periods of market movement.
One of John’s most successful trades came during a highly volatile week when the U.S. Dollar experienced significant fluctuations due to a surprise rate cut by the Federal Reserve. John positioned himself ahead of the news, using his technical analysis to predict the likely direction of the market after the announcement. As a result, he was able to capitalize on the initial price surge, closing out with a substantial profit. John’s success story exemplifies how understanding Forex volatility and applying strategic methods can lead to substantial gains.

Website Security Features: Trading Safely in a Volatile Market
In addition to mastering volatility, it’s crucial to prioritize the security of your funds and personal information when trading Forex. As volatility can attract cybercriminals, ensuring your trading platform is secure is paramount.
Top Forex brokers, recommended by Top Forex Brokers Review, implement advanced security measures to protect traders. Here are some key security features to look for:
SSL Encryption: A secure trading environment starts with SSL encryption, which ensures that any data exchanged between you and your broker is encrypted and cannot be intercepted by third parties. This protects your personal information and funds.
Two-Factor Authentication (2FA): Many trusted Forex brokers offer 2FA as an added layer of protection. This requires you to enter a unique code sent to your phone or email in addition to your password, making it harder for unauthorized users to access your account.
Regulation and Licensing: Reputable brokers are regulated by top-tier financial authorities such as the Financial Conduct Authority (FCA) or the Australian Securities and Investments Commission (ASIC). These regulatory bodies ensure brokers meet strict security standards and safeguard client funds.
Secure Trading Platforms: The best Forex brokers provide trading platforms with built-in security features, such as real-time monitoring of transactions, secure login systems, and encryption to prevent unauthorized access.
By choosing a broker with a strong security infrastructure, you can focus on your trading strategies without worrying about cyber threats or financial risks.
Why Choosing the Right Broker Matters
When navigating the volatile Forex market, your broker plays a pivotal role in your success. A trusted broker ensures that you have access to the right tools, market analysis, and a secure trading platform. Top Forex Brokers Review evaluates brokers based on key factors such as regulatory compliance, customer service, and platform reliability. Choosing the right broker is essential for capitalizing on market volatility and achieving long-term trading success.
Conclusion
Forex volatility doesn’t have to be a source of stress. By adopting the strategies used by the top 1% of traders, such as leveraging technical and fundamental analysis, implementing smart risk management, and staying disciplined, you can turn volatility into an opportunity for profit. Expert traders like Sangram Mohanta have built successful careers by mastering the art of trading during volatile periods—and you can too.
Additionally, don’t overlook the importance of website security. By choosing a trusted and regulated broker with robust security features, you can trade with peace of mind.
With the right knowledge, tools, and security measures, you can dominate the Forex market and join the ranks of successful traders in 2025. For expert broker recommendations and more insights into trading strategies, visit Top Forex Brokers Review—your go-to resource for Forex trading success.
3 notes
·
View notes
Text

Excerpt from this story from Mongabay:
A new global study reveals an average 81% decline in migratory freshwater fish populations between 1970 and 2020.
Habitat loss, degradation and overfishing are the main threats to migratory fish, which are crucial for food security, livelihoods and ecosystems worldwide.
While 65% of species have declined, 31% have shown increases, suggesting that conservation efforts and management strategies can have positive impacts.
The report calls for stronger monitoring efforts, protection of free-flowing rivers, and meeting global biodiversity goals to address this crisis.
The report analyzed data from 1,864 populations of 284 migratory freshwater fish species across the globe. Contributing to the report were researchers from the World Fish Migration Foundation, the Zoological Society of London (ZSL), the International Union for Conservation of Nature (IUCN), The Nature Conservancy (TNC), Wetlands International and WWF.
The researchers found that fish populations had declined significantly more in some regions than in others. For example, Latin America and the Caribbean experienced the most severe decrease at 91%, while Europe saw a 75% decline. North America showed a 35% decrease, and Asia-Oceania reported a 28% decline. Data for Africa were limited, making it difficult to determine conclusive trends for that continent.
12 notes
·
View notes
Text
Machine Learning, a boon for CyberSecurity?
In an age where cyberattacks are changing at a rapid pace, machine learning (ML) is increasingly becoming an effective partner in the fight for online security. Conventional cybersecurity solutions depend significantly on pre-established rules and established signatures, yet today's attackers are increasingly creative, covert, and unpredictable. This is where machine learning steps in allowing systems to learn, adapt, and react in real time.
Static Rules for Smart Detection
Legacy security systems work like rulebooks: "If X occurs, do Y." However, this model fails when attackers modify the rules. Machine learning turns the script around by teaching algorithms on enormous datasets, including historical attacks, system patterns, and live logs to find patterns and detect anomalies without being programmed for each eventuality.
For instance, an ML-driven system may detect that a user who normally logs in during working hours had logged into the system at 3 AM from a foreign country. Even when no known malware is found, the anomaly can initiate a security alarm on its own.
Machine Learning Applications in Cybersecurity
Anomaly Detection ML models are able to identify suspicious activity on networks, devices, or user accounts that vary from the norm, even slight activity. Spam & Phishing Detection Natural Language Processing (NLP), a subcategory of ML, assists in identifying phishing messages by examining tone, intent, and form much better than fixed spam filters. Malware Classification Rather than using known signatures, ML models are able to examine file behaviour and attributes to identify zero-day malware attacks that haven't been encountered previously. Threat Prediction Predictive models predict possible vulnerabilities from past attack patterns, allowing for proactive protection. Automated Incident Response Sophisticated systems are able to assess security incidents in real-time and recommend or even trigger proper response actions, such as isolating infected machines or blocking IPs.
Real-World Example
Let's consider an example of a company employing a legacy firewall. It may be able to block known malicious IPs, but an intelligent attacker switching between various IPs could still bypass the block. An ML-augmented solution on the other hand, can recognise behavioural indicators of compromise, e.g., high-frequency request patterns, suspicious payloads, or unusual user agents and react even without matching a known signature.
Challenges to Consider
False Positives: ML systems will occasionally mark harmless activity as threats, resulting in alert fatigue.
Adversarial Attacks: Hackers are now creating inputs that "fool" ML models a developing concern.
Data Dependency: The performance of ML is significantly dependent on training data quality and quantity.
The Future is Adaptive
As cyber threats become more sophisticated, static defences can no longer suffice. Machine learning provides an intelligent, scalable, and dynamic layer of protection that adapts to growing threats. Far from a silver bullet, it is a crucial pillar in contemporary cybersecurity strategies.
Firms such as Astra Security are already using smart automation and ML-powered threat detection to enable companies to remain at the forefront of the cybersecurity marathon. The objective? To make the internet a safer, smarter world, one algorithm at a time.
2 notes
·
View notes
Text
The Power of Upskilling: Why Investing in Yourself Is the Smartest Move You’ll Ever Make
In today’s fast-paced, constantly evolving world, the only thing more expensive than investing in yourself is not doing it.
Upskilling — the process of learning new skills or enhancing existing ones — is no longer optional. It's a necessity for staying competitive in the workforce, pivoting to new career paths, and adapting to a world where change is the only constant.
Whether you're a fresh graduate, a mid-career professional, or a business leader, this post will help you understand why upskilling matters, where to start, and how to make learning a lifelong habit.
Why Upskilling Matters More Than Ever
1. Rapid Technological Advancements
Automation, AI, and digital transformation have reshaped industries. According to the World Economic Forum, 44% of workers’ core skills will change by 2027. Skills that were in high demand five years ago may now be outdated.
Jobs aren't necessarily disappearing — they’re evolving. That means individuals must continuously adapt or risk being left behind.
2. Career Growth and Mobility
Upskilling doesn’t just help you survive — it helps you thrive.
Want a promotion? Looking to switch industries? Trying to freelance or start a side hustle? Upskilling bridges the gap between where you are and where you want to be.
For example:
A marketer who learns data analytics becomes more valuable.
A teacher who gains expertise in EdTech can unlock new career opportunities.
A finance professional with coding skills can transition into fintech.
3. Increased Job Security
In uncertain economic times, employees with in-demand skills are often the last to go. Upskilling makes you indispensable. Employers view proactive learners as assets — people who are flexible, forward-thinking, and ready to take on new challenges.
4. Personal Satisfaction and Confidence
Beyond career advantages, learning something new boosts your self-esteem. Mastering a new tool or concept builds confidence and adds a sense of achievement. Lifelong learning is directly linked to better mental health, cognitive ability, and even happiness.
Identifying What to Learn
Not all skills are created equal. Here’s how to identify what you should focus on:
1. Align With Industry Trends
Start by researching current trends in your field. What tools, software, or certifications are becoming standard? Websites like LinkedIn Learning, Coursera, and even job boards can offer insight into what’s in demand.
2. Pinpoint Skill Gaps
Look at your resume, job performance, or feedback. Are there areas where you consistently feel underqualified or reliant on others? That’s your starting point.
For instance, if you’re in marketing but struggle with Excel or Google Analytics, that’s a practical gap to close.
3. Balance Hard and Soft Skills
Hard skills (e.g., coding, SEO, data visualization) are measurable and job-specific. Soft skills (e.g., communication, emotional intelligence, adaptability) are often what make or break long-term success.
According to LinkedIn’s Workplace Learning Report, soft skills like creativity, collaboration, and critical thinking are increasingly valued by employers.
How to Upskill Effectively
Upskilling doesn’t have to mean going back to college or spending thousands. With the right strategy, you can learn faster, smarter, and more sustainably.
1. Set Clear Goals
Vague intentions (“I want to get better at digital marketing”) rarely produce results. Instead, try: ✅ “I will complete a Google Ads certification within 30 days.” ✅ “I will write one blog post a week to practice content writing.”
2. Use Online Platforms
Some great learning platforms include:
Coursera – Offers university-led courses, many for free.
Udemy – Affordable, practical skill-based learning.
LinkedIn Learning – Career-focused, bite-sized lessons.
edX – Ivy-league content in flexible formats.
YouTube – A goldmine for free tutorials.
Don’t forget podcasts, newsletters, webinars, and even TikTok or Instagram accounts focused on education.
3. Apply What You Learn
Knowledge without application is wasted. If you’re learning copywriting, start a blog. If you’re learning a coding language, build a small project. Application cements learning and gives you portfolio pieces to show potential employers.
4. Join a Community
Learning with others keeps you accountable. Join Slack groups, Reddit communities, Discord servers, or local meetups. Networking with people on the same journey also opens up career opportunities.
5. Track and Reflect
Keep a simple progress log. Write down what you learned each week, what worked, and what didn’t. Reflection helps identify plateaus and gives you clarity on your next steps.
Upskilling at Work: Make It a Two-Way Street
If you’re employed, your workplace may be willing to sponsor courses or give you dedicated learning hours. Upskilling benefits your employer too — so don’t hesitate to ask.
Here’s how:
Propose a specific course or certification.
Explain how it’ll improve your job performance.
Offer to train others on what you’ve learned.
Employers appreciate initiative and are often happy to invest in employees who invest in themselves.
Final Thoughts: Build a Habit, Not Just a Skill
The most successful people don’t upskill once — they build a habit of learning.
Start with 30 minutes a day. Read a chapter. Watch a tutorial. Experiment with a new tool. Upskilling isn’t a race; it’s a lifestyle.
Remember: your career is your responsibility. In a world where industries change overnight, the most future-proof investment isn’t in stocks or crypto — it’s in you.
2 notes
·
View notes
Text
CROWDFUNDING
Crowdfunding Success: From Campaign Creation to Smart Promotion
In a world filled with ideas, turning your vision into reality often comes down to funding. Crowdfunding has emerged as a powerful tool for entrepreneurs, creatives, and changemakers to rally support and secure capital without relying on banks or investors. But here’s a truth many don’t tell you: only about 22% of crowdfunding campaigns reach their goals. The difference between success and failure lies in strategy. In this blog post, we’ll walk you through the full journey from crafting your campaign to promoting it effectively with practical examples and pro tips. Click here
Craft a Campaign Page That Converts
Your campaign page is your storefront it has to captivate and convince. Begin with a bold, clear headline that states exactly what your project is and why it matters. Use high-quality visuals and a short, professional video to communicate the heart of your story. Most successful campaigns also include reward tiers that offer real value and emotional connection. Whether you're offering early access, branded merch, or exclusive content, make sure your rewards align with your brand.
Don’t forget the social proof. Testimonials, quotes, or even early endorsements can build instant trust. Tools like Canva (for graphics) or ChatGPT (for persuasive copy) can help make your campaign page stand out.
Promotion Starts Before You Launch
Great campaigns start long before they go live. Build buzz weeks in advance by teasing your launch on social media, creating a landing page, or starting a countdown. Get early supporters to subscribe to an email list, and give them VIP access or exclusive perks when the campaign goes live. Influencer partnerships or endorsements from niche thought leaders can create instant credibility and reach.
Once live, consistency is everything. Post daily updates, share behind-the-scenes content, and use urgency (like limited-time rewards) to drive action. Run targeted Facebook or Instagram ads with low budgets to test what messaging works. Engage in forums like Reddit or niche Facebook Groups to find super-targeted backers.
Check out this guide to building viral campaign traction https://shorturl.at/mtIZ3
Track, Tweak, and Scale
Just launching your campaign isn’t enough you have to monitor its health. Use the platform’s analytics to check where your traffic is coming from, what your conversion rate is, and which reward tiers are most popular. Based on this data, tweak your headline, swap out images, or reword reward descriptions.
One campaign raised over 200% of its goal by simply refining their video and adding stretch goals. If you’re not hitting your target, don’t panic. Pivot fast. Send another email blast, introduce new rewards, or offer limited-edition perks to revive interest. And once your goal is met? Keep the momentum. Use updates to thank backers and tell them what’s next you’re not just raising money, you’re building a brand.
Ready to plan your first successful campaign? Start here
Want help planning or writing content for your own campaign? I can help you craft the story, build the page, or even handle promotion. Just let me know!
#911 abc#artists on tumblr#cats of tumblr#conclave#cookie run kingdom#arcane#eurovision#andor#f1#jujutsu kaisen
2 notes
·
View notes
Text
TikTok went all out to defend itself in a court hearing last Monday, to block a law that could force TikTok to be sold or banned in the United States. That included using one surprising strategy: to bring other Chinese apps down with it.
Earlier this year, the Protecting Americans from Foreign Adversary Controlled Applications Act (PAFACA), which aims to prevent national security threats from apps like TikTok, took less than two months to pass both the House and the Senate, before it was swiftly signed by President Joe Biden in April. It caught almost everyone by surprise, including TikTok. The law requires TikTok to find a US buyer to take over its operation soon, or face being banned in the US. TikTok promptly sued the government over it.
At the Court of Appeals in Washington, DC, on September 16, Andrew Pincus, a partner at law firm Mayer Brown acting for TikTok, argued that the law unfairly targets the social media app for the speech on the platform and that it violates the First Amendment. Specifically, Pincus said the law exempts other Chinese apps that could have been doing worse on the concern of data security protection.
“There are very significant ecommerce sites based in China and other places that collect much more data than TikTok does. Very sensitive data,” Pincus said. At another point in the hearing, he narrowed down the targets to “two Chinese, two e-commerce sites that would certainly meet all of the other criteria in the law.”
Pincus did not name-drop the two sites in his statements, but a TikTok court filing from August 15 cited the privacy policies of Shein and Temu—two ecommerce companies linked to China—to make the same argument Pincus made. The filing also cited research from April 2023 on the data risks of these two companies, collated by the US–China Economic and Security Review Commission.
Shein and Temu came from China’s fiercely competitive ecommerce industry and were able to take over the world by storm by shipping low-cost apparels and goods globally. Each boasts tens of millions of customers around the world, and they are often compared to TikTok as the rare examples of Chinese tech companies that have truly succeeded in the US.
TikTok, however, claims there’s an exemption clause in the PAFACA Act that essentially protects Chinese companies like Shein and Temu but not TikTok. When defining what companies are covered, the Act has only one exclusion: companies and products “whose primary purpose is to allow users to post product reviews, business reviews, or travel information and reviews.”
To be fair, the clause that TikTok highlighted was a bewildering inclusion from the beginning. Even some lawmakers claimed they weren’t sure why it was necessary to put in place such an exception.
But TikTok is seizing this opportunity to argue that, because the clause would likely protect Shein, Temu, and similar ecommerce sites that also have significant presence in the US and collect a wealth of privacy data, the Act is narrowly tailored to punish TikTok. It went as far as to claim that the clause shows Congress favors topics like products, business, and travel instead of politics, religion, and entertainment, making it a First Amendment infringement. The DOJ has denied this characterization in written court briefs.
It is a valid legal strategy, Alan Rozenshtein, an associate professor of law at the University of Minnesota Law School, explains to WIRED, as the First Amendment can consider a law unconstitutional “if the law hinges on solving a particular problem, does so in an extremely limited way, and leaves the law unsolved.”
But the judge didn’t seem to buy the argument. “It’s a rather blinkered view that the statute just singles out one company,” said Judge Douglas Ginsburg during the hearing. “It describes a category of companies, all of which are owned by or controlled by adversary powers, and subjects one company to an immediate necessity because it’s engaged in two years of negotiation with that company, held innumerable hearings, meeting after meeting after meeting, [and] an attempt to reach an agreement on a national security arrangement which failed.”
The DOJ also replied to TikTok’s problem with the exclusion clause, saying in a court brief that if the clause were to be found problematic, the right solution would be to simply take out that clause about excluding businesses, instead of invalidating the whole law.
In recent years, data security concerns have become one of the main friction points in tech policies in the US and China. While the Chinese government passed a law that regulates cross-border data transfers, the US government has taken a more piecemeal approach, investigating risks posed by products like TikTok and Chinese-made smart cars.
Some experts and lawmakers advocate for a more comprehensive legal framework to solve this issue. “This bill not only fails to solve the problem, but also jeopardizes the free speech and livelihoods of 170 million Americans who use the app. Instead, Congress should pass a bill to prevent apps, whether it's TikTok or any other social media platform, from collecting or transferring data and make foreign interference in social media algorithms illegal,” said Representative Ro Khanna in an emailed statement. Khanna voted no on the PAFACA bill.
For now, Chinese ecommerce sites like Shein and Temu have faced much less scrutiny around data security than TikTok. But TikTok’s legal strategy of highlighting the alleged data security risks of other Chinese companies will no doubt put more pressure on them. If TikTok fails its legal challenge and is banned from operating in the US unless it is sold, it’s not hard to imagine that lawmakers might turn their attention to other prominent Chinese tech companies.
“There might be some kind of legal strategy behind this, but in terms of how the public will now perceive TikTok, it has voluntarily opted to be associated with Temu and Shein and has undone a lot of the narrative work it has been trying to do,” says Ivy Yang, the founder of Wavelet Strategy, a strategic PR consultancy who has worked in Alibaba’s PR department.
By comparing TikTok’s data security concerns to Shein’s and Temu’s, the company essentially has labeled itself among a number of Chinese companies considered security risks.
So far, Shein and Temu have not made any statement about the PAFACA bill and its potential implications on their businesses. A Shein spokesperson responded in an emailed statement: “SHEIN has robust data security policies and practices in line with industry standards, and we are committed to only collecting and using the minimum amount of data needed to fulfill orders. SHEIN stores US customer data within Microsoft’s US-based Azure cloud-based solution and within AWS’s US-based cloud-based solution.” Temu and TikTok did not reply to requests for comment.
These ecommerce companies have plenty of problems to deal with at the moment too. A September White House decision to scrap a tariff exemption policy could significantly increase shipping costs for them and harm their profitability. Meanwhile, the two ecommerce companies have been embroiled in a tit-for-tat legal battle in the US since July 2023, accusing each other of monopolistic practices and deceptive marketing.
“What they are doing is basically airing all the dirty laundry,” Yang says about the Shein–Temu court fights. “It’s very much, ‘We are competitors and we have to beat the other party no matter how far we go, even though as a whole it’s a terrible look on Chinese companies.’” The same problem is playing out as TikTok seemingly decided to take down its fellow Chinese companies to save itself in the court.
But TikTok’s gambit may not pay off in the end. Even if it successfully argues that the Congress shouldn’t just target one app for its data security risks, it still needs to refute the government’s other justification for the law—that TikTok could be subject to content and algorithm manipulation by the Chinese government in the future. “The law has used two justifications. [If] one is invalid and the other is valid, the law is still valid,” says Rozenshtein.
There has been no proof—at least not in the nonredacted materials—that the Chinese government is currently interfering with TikTok’s content in the US. But during last week’s hearing, none of the judges seemed interested in discussing this point with TikTok or the government.
“[TikTok] made the best argument they could. Just the argument went very poorly for them,” Rozenshtein says. “I don’t think it’s conceivable that TikTok will win, at least on this level.”
14 notes
·
View notes
Text
The United Arab Emirates committed to one of the largest foreign direct investment pledges after agreeing to invest $1.4 trillion in the United States over the next decade. Sheikh Tahnoon bin Zayed Al Nahyan, the UAE’s national security adviser and a key figure in the Gulf nation’s economic strategy, met with President Donald Trump last week to discuss the massive investment promise.
The detailed framework has not been outlined. However, the UAE has said it would like to “substantially increase” existing investments in semiconductors, energy, manufacturing, and AI—all key sectors for the USA. It is no secret that American manufacturing has been suffering in recent years. The CHIPS act did little to promote semiconductor manufacturing in the US. Donald Trump has accused Taiwan of taking semiconductor business away from the US, and naturally, has threatened tariffs. The US must work fast if it wishes to compete with China in the AI realm, with DeepSeek being one example of China’s technological achievements.
Emirates Global Aluminum has announced plans to create the first new aluminum smelter in the US in nearly four decades. The White House noted this “would nearly double US production capacity” in aluminum and provide a much-needed boost to manufacturing overall.
Investment fund ADQ, based in the UAE, will partner with US-based Energy Capital Partners to invest $25 billion into energy infrastructure including data centers. This comes after billionaire Hussain Sajwani announced in January that he plans to place $20 billion into a US data center as his firm, Damac, already has close ties with Trump’s business ventures.
This historic deal is excellent news for the US economy and part of a much larger capital shift taking place as foreign capital seeks a safe haven.
11 notes
·
View notes