#digital forensic experts
Explore tagged Tumblr posts
Text
Digital Forensics Experts Brisbane, Digital Investigation Services

Expert digital forensics & investigation services in Brisbane. Uncover evidence, analyze data & secure your digital assets with trusted forensic specialists.
#Digital Forensics#digital forensic experts#digital investigation services#digital forensic services#forensics investigations
0 notes
Text

“BMS Auditing offers cutting-edge forensic auditing and IT services to help businesses uncover financial fraud and improve operational efficiency. With years of expertise, we provide innovative solutions that protect your assets and ensure accountability.”
#Forensic Auditing#IT Audit Services#Fraud Detection#Financial Security#Audit Experts#Cybersecurity Audit#Risk Management#Asset Protection#Digital Forensics#BMS Auditing#Audit Services KSA#Financial Auditing#Internal Controls#IT Compliance#Data Analytics Audit#audit and assurance
0 notes
Text
Advanced DWI Defense: Unleashing Expert Witnesses
If you’re serious about fighting a DWI charge in Houston, using expert witnesses at trial can significantly help the chances for a positive outcome in your case. The testimony of an expert witness on a DWI case can illuminate complex scientific principles, unravel intricate evidence, and potentially recalibrate the scales of justice in your favor. Juries take expert witnesses seriously. Texas law…

View On WordPress
0 notes
Text
Data Theft of Intellectual Property
Intellectual property (IP) is the cornerstone of our company's success, encompassing valuable non-tangible creations of the human mind. These assets are vital for our commercial growth and, as such, require legal protection. However, IP theft is a real threat that can occur through cyberattacks, insider leaks, or departing employees. To combat this, immediate action is crucial if any suspicion arises. By contacting our dedicated IP protection team promptly, we can preserve critical data and prevent contamination during investigations. Disconnecting the device from the network, disabling employee access, and securing cellular devices are essential steps in safeguarding our valuable IP.
Read more here: https://forensicdiscovery.expert/data-theft-intellectual-property/
#digital forensics#ediscovery#forensic discovery#digital evidence#success#litigation#expert witness#data theft#intellectual property#IP
1 note
·
View note
Text
Unveiling the Hidden Truth: Mobile Phone Forensics and Digital Expert Witness Services in Milwaukee

In the modern world, the digital footprint we leave behind extends far beyond physical evidence. With mobile phones acting as personal portals, they hold a treasure trove of data: texts, emails, call logs, browsing history, financial transactions, social media activity, and even GPS location traces. When this data becomes relevant to legal proceedings, the expertise of mobile phone forensics and digital expert witnesses in Milwaukee becomes crucial.
Mobile Phone Forensics: Unearthing the Buried Secrets
Imagine a scenario: in a divorce case, accusations of infidelity arise. Or, a wrongful termination lawsuit hinges on emails allegedly sent from the employee's phone. In such situations, Milwaukee’s mobile phone forensics specialists come into play. They possess the tools and expertise to:Extract data: Even deleted information can be meticulously recovered, including texts, photos, videos, and voice recordings. Analyze data: Experts sift through the vast digital landscape, identifying relevant evidence with pinpoint accuracy. This includes extracting call logs, mapping GPS movements, and reconstructing social media interactions. Maintain chain of custody: Every step of the process is meticulously documented to ensure the evidence's admissibility in court.
Digital Expert Witnesses: Lending Credibility in the Courtroom
Extracting data is only half the story. Expert witnesses, qualified by their experience and training, take center stage in the courtroom. They translate the complex digital evidence into understandable terms for judges and juries, painting a clear picture of the story hidden within the data. With their insights, Milwaukee’s digital expert witnesses:Interpret findings: They explain the technical aspects of the data recovery and analysis, ensuring the court understands the process and its validity. Offer opinions: Based on their expertise, they draw conclusions from the evidence, providing valuable insights into the case. Counter opposing arguments: They effectively address challenges to the validity of the evidence and the methods used.
The Milwaukee Advantage:
Milwaukee boasts a diverse range of qualified professionals offering mobile phone forensics and digital expert witness services. Here's why you should consider local expertise:Local knowledge: They understand the specific legal landscape and court procedures, ensuring a smooth and efficient interaction with the justice system. Accessibility: You gain faster response times and easier communication, crucial for timely evidence gathering and court preparation. Competitive rates: Local firms often offer more competitive fees compared to national counterparts.
Investing in Trust
When navigating the complex world of legal proceedings, involving mobile phone forensics and digital expert witnesses in Milwaukee provides an invaluable edge. Their expertise in extracting and interpreting digital evidence sheds light on hidden truths, paving the way for a fair and just resolution. So, if you find yourself entangled in a legal battle where mobile technology plays a critical role, consider relying on the trusted local professionals in Milwaukee to unveil the truth buried within your digital devices.
#raid data recovery milwaukee#mac data recovery milwaukee#data recovery waukesha wi#data recovery milwaukee#harddrivedatarecoverymilwaukee#digital expert witness milwaukee#phone data recovery waukesha#phone data recovery milwaukee#hard drive data recovery milwaukee#mobile phone forensics milwaukee
0 notes
Text

$1 Million Worth of Gold Coins Stolen From 18th-Century Shipwrecks Found
After an extensive investigation, Florida officials recovered dozens of gold coins valued at more than $1 million that were stolen from a shipwreck recovery nine years ago.
The Florida Fish and Wildlife Conservation Commission announced in a news release Tuesday it had recovered 37 gold coins that were stolen from the 1715 Fleet shipwrecks.
The fleet of Spanish ships sailed from Havana, Cuba and headed to Seville, Spain on July 24, 1715. The journey was short-lived, as a hurricane wrecked the fleet just seven days later off the coast of Eastern Florida.
The first ship was discovered in 1928 by William Beach north of Fort Pierce, Florida, about 120 miles south of Orlando. Since then, gold and silver artifacts have been recovered offshore for decades following the first discovery.
In 2015, a group of contracted salvage operators found a treasure trove of 101 gold coins from the wrecks near Florida’s Treasure Coast, about 112 miles west of Orlando. However, only half of the coins were reported correctly. The other 50 coins were not disclosed and later stolen.
The years-long investigation by the state’s fish and wildlife conservation commission and FBI “into the theft and illegal trafficking of these priceless historical artifacts” came to a head when new evidence emerged in June, the news release said.
The evidence linked Eric Schmitt to the illegal sale of multiple stolen gold coins in 2023 and 2024, officials said. Schmitt’s family had been contracted to work as salvage operators for the US District Courts’ custodian and salvaging company for the fleet, 1715 Fleet - Queens Jewels, LLC. The Schmitts had uncovered the 101 gold coins in 2015.
During their hunt for the coins, investigators executed multiple search warrants and recovered coins from private residences, safe deposit boxes and auctions, the news release said. Five stolen coins were retrieved from a Florida-based auctioneer, who unknowingly purchased them from Schmitt.
Investigators used advanced digital forensics to nail down Schmitt as a suspect in the case. In most cases, digital forensics can recover data stored electronically on devices such as a cell phone, computer system or memory module.
With the help of advanced digital forensics, investigators identified metadata and geolocation data that linked Schmitt to a photograph of the stolen coins taken at the Schmitt family condominium in Fort Pierce, Florida.
Authorities said Schmitt also took three of the stolen gold coins and put them on the ocean floor in 2016. The coins were later found by the new investors of the fleet’s court custodian and salvaging company.


Throughout the investigation, the Florida Fish and Wildlife Conservation Commission worked closely with historical preservation experts to authenticate and appraise the recovered coins sold by Schmitt.
Schmitt is facing charges for dealing in stolen property, the release says.
The company commissioned to salvage the shipwreck said in a statement it “was shocked and disappointed by this theft and has worked closely with law enforcement and the state of Florida regarding this matter.”
“We take our responsibilities as custodian very seriously and will always seek to enforce the laws governing these wrecks,” the statement read.
Recovered artifacts will be returned to their rightful custodians, the news release said. But the investigation is far from over: 13 coins remain missing.

#$1 Million Worth of Gold Coins Stolen From 18th-Century Shipwrecks Found#1715 Fleet shipwrecks#gold#gold coins#collectable coins#treasure#shipwreck#ancient artifacts#archeology#archeolgst#history#history news#ancient history#ancient culture#ancient civilizations
127 notes
·
View notes
Text





I’ve mentioned a few times that the Detective Club doesn’t seem to have any named members outside Logico and the Murdle Jr. kids (Irratino, I HC as an associate instead of a full member, and I sincerely doubt they’d let any of the suspects save maybe Obsidian in :P). So! Have some OCs to fill out the ranks.
More about each under the cut:
Journalist Jade
5’5, Right-Handed, Brown Eyes, Black Hair, Aquarius
Jade is a 30-year old investigative journalist, taking to the streets to look for headliners and expose crimes for all the world to see. She’s passionate and can be a bit reckless in her pursuit of a big story, but she’s overall a nice person. She’s also the one who originally invited Logico to the Detective Club (in my mental list of Stories I Want To Write Someday, one of them is how Logico became part of the Detective Club—TL;DR, he wound up working with Jade to expose some criminals and she gave him the invite shortly thereafter), and might have had a bit of a crush on him—he’s fairly handsome despite his overall scruffiness, and they worked well together—but obviously, that went nowhere on account of Logico being both not into women and also a major-league jerk pre-Volume 1 :P
Overall, I’d say Jade’s drawing turned out the best; the design was nice, and translated into my artstyle rather well. I accidentally drew her hair a lot shorter than I’d originally intended, and I completely forgot the camera until I was already outlining and had to hastily add it in, but I’d say it all worked out in the end. Her style suits her ^^
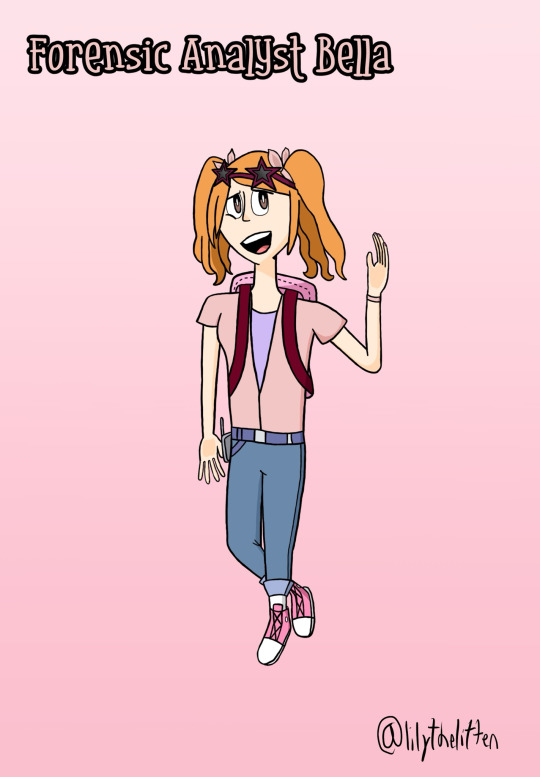
Forensic Analyst Bella
5’3, Left-Handed, Brown Eyes, Red Hair, Gemini
Bella is 26, yet in many ways, she acts like a high school popular girl; chatty, fashionable, gossipy, phone-obsessed, and just a bit mean. One would think someone like that would have no place in the Detective Club, but Bella graduated valedictorian of her college and is a known forensics expert. She can tell you when someone died and what poison was used to kill them as easily as she can tell you whether or not your shoes are “in” this summer.
Bella was actually the first Detective Club OC I designed; the forensics part came later, to give her more an identity beyond “Detective Club member”. I like her sunglasses, and her being the only one who carries a walkie-talkie in addition to a phone; ya gotta be prepared when solving crimes. (Oh, and in case you’re thinking I broke the color name rule…I didn’t. Yeah, maybe using a color named by a paint company is cheating, but oh well. I was originally going to use magenta, but then I figured I should probably pick a color less likely to be given to a canon character ^^;)
IT Guy Auburn
5’8, Right-Handed, Brown Eyes, Red Hair, Virgo
Auburn used to work for TekCo, before leaving the company following an “incident” he doesn’t talk about; at 29, he’s just a year younger than its current CEO. While introverted and socially awkward at the best of times, he’s a whiz with computers; if the mystery leaves some digital footprints behind, you go to him. (That his skills are upstaged by a detective in the junior group—the daughter of that aforementioned CEO, no less—is something Auburn awkwardly avoids acknowledging.)
Okay, so I found quite a few color codes for “auburn”; I wound up picking the most common two and using them for his headphones and jacket respectively, which is probably the best compromise I could’ve made ^^; I think I got the “tech guy” look down pretty well, even if he does look a bit more like a gamer than anything else. (I’m sure Olivia would beat him in that regard too :P)
Socialite Vanille
5’0, Right-Handed, Blue Eyes, Blonde Hair, Pisces
At 23, Vanille is one of the Detective Club’s younger members, and also one of its few wealthy members. She comes from high society, and looks and acts the part. Some look down on her as just a rich kid with no actual skills. Vanille simply smiles, because social skills—telling people what they want to hear, getting them to trust you, figuring out who you can and can’t trust yourself—get you very far in an investigation. (Someone should let Logico know that :P)
Vanille’s design admittedly didn’t translate as well as everyone else’s did, mostly because I didn’t actually realize the color of her hair and jacket were so close. And also because after three drawings of decent hands, I got cocky and thought I could do a complicated pose with her hat. Don’t be like me, kids :V I do still like her, though. She’s the first character I’ve ever drawn in a skirt or dress XD And yes, as her name implies, she is French. You can get a surprising amount of OCs through translating colors into foreign languages (looks at Logico’s maternal relatives).
Codebreaker Clover
5’6, Left-Handed, Gray Eyes, Blonde Hair, Scorpio
Clover is 31 (though you’d be forgiven for thinking he was younger), brilliant with cryptography, and kind of a wreck. No one really knows what made him so twitchy and paranoid, or where he learned his codebreaking skills, though some believe the two things are connected. Clover himself thinks everything is connected; everything has a purpose, everything is part of some plan, and everyone is somehow involved. His conspiracy theories are legendary throughout the club, and most of them are known to be complete nonsense. (The rest…well, maybe it’s best not to dig too deep.)
Like Bella, Clover originally had another name—Cyan—before, again, I changed it to one less likely to be used in canon. He also had a couple different titles—first Conspiracist when I wanted to emphasize the “wild paranoiac conspiracy theorist” thing, then Cryptographer when I settled on what he actually did, then Codebreaker because Cryptographer was too similar to Cloud’s title :P He also has the most complicated pair of glasses I’ve ever drawn. I think they came out nicely ^^
Parapsychologist Pitch
5’5, Left-Handed, Green Eyes, Black Hair, Sagittarius
Nobody’s quite sure what Pitch does. Or, frankly, what they’re doing here. 27 years old, they have a love for the macabre and a fascination with the paranormal, and every case they take is some flavor of spooky. One would think they’d fit in better with the Investigation Institute, but they just say they like hands-on experience more than sitting in a chateau doing experiments. They’re fairly chill outside that, if enigmatic at the best of times; they might be playing up their strange behavior to spook people, though. You can never really tell with Pitch.
Pitch originated as an Investigation Institute OC, before I decided I liked the Institute’s actual characters better and repurposed them for the Detective Club :P I do really like their design, though. I love their dyed hair and eyeliner (yes, the points on their eyes are meant to represent eyeliner) and goth outfit. Fun fact: The words on their shirt, if you can’t read it, are “Cinematic Anarchy”. Yes, it is a band shirt. Yes, I came up with that name myself. And yes, it is very edgy :P
Anyway, that’s my characters, they aren’t Logico’s friend group because Logico barely has any friends but they do fill empty space where the rest of the Detective Club is, so. There’s that :P
#i love these characters but drawing them took FOREVER#so who knows if i’ll ever draw them again :P#in hindsight making everyone’s designs super detailed was a bad idea#but at least it looks good here ^^;#fanart#lily’s art#lily’s ocs#murdle#murdle oc#journalist jade#forensic analyst bella#it guy auburn#socialite vanille#codebreaker clover#parapsychologist pitch
31 notes
·
View notes
Text
The target is you, voter. Russia, China, Iran, and other bad actors sought to interfere in the run-up to today’s US elections, according to research by the Atlantic Council’s Digital Forensic Research Lab (DFRLab), which has been monitoring online trends along with statements by governments, private companies, and civil society in its Foreign Interference Attribution Tracker. As DFRLab experts detail below, this year’s malign efforts in many ways surpass previous influence campaigns in sophistication and scope, if not in impact—and they are expected to continue well after the polls close.
Tipping the scale
“By sheer volume, foreign interference in the 2024 US election has already surpassed the scale of adversarial operations in both 2016 and 2020,” Emerson says.
Dina notes that each US adversary played to its strengths. For example, Iran and China “attempted to breach presidential campaigns in hack-and-leak operations that raise concerns about their cyber capabilities during and after the elections,” she tells us.
At the same time, the United States is more prepared than it was in previous election cycles. Russian efforts in 2016 “made foreign interference a vivid fear for millions of Americans,” Emerson notes. “Eight years later, the US government is denouncing and neutralizing these efforts, sometimes in real time.”
In fact, Graham tells us, “the combined actions by the US departments of Justice, Treasury, and State against two known Russian interference efforts was the largest proactive government action taken against election influence efforts before an election.”
Doppelgangers and down-ballot races
US officials this week called Russia “the most active threat,” and it’s easy to understand why. Emerson notes Russia’s “ten-million-dollar effort to infiltrate and influence far-right American media,” alongside the “Doppelganger” network, which has spread “tens of thousands of false stories and staged videos intended to undermine election integrity in the swing states of Pennsylvania, Georgia, and Arizona.” Increasingly desperate, Russian actors have even sought to shut down individual polling places with fake bomb threats, he adds.
Meanwhile, China has focused on “down-ballot races instead of the presidential election to target specific anti-China politicians,” Kenton explains. Using fake American personas and generative artificial intelligence, China-linked operations have appeared across more than fifty platforms. Perhaps surprisingly, Kenton adds, “attributed campaigns appeared sparingly” on the Chinese-owned platform TikTok and far more often on Facebook and X.
Faith, fakes, and falsehoods
“The primary aim is to erode Americans’ faith in democratic institutions and heighten chaos and social division,” Kenton explains, and thus to undermine the ability of the US government to function so it will have less bandwidth to contain adversarial powers.
“Some of the fake and already debunked narratives and footage circulating before the elections will likely continue to be amplified by foreign threat actors well after November 5,” Dina predicts. Expect to see activity around the submission of certificates of ascertainment on December 11, the December 17 meeting of the electors to formally cast their votes, and through inauguration day on January 20.
And in a post-election period where the results will likely be contested, Graham thinks there’s a “high likelihood” that foreign actors will “cross a serious threshold” from pre-election attempts to broadly influence American public opinion in service of their geopolitical interests to “direct interference” by trying to mobilize Americans to engage in protests or even violence.
Nevertheless, Graham points out that the high volume of foreign-influence efforts observed during this year’s election cycle so far does not appear to have had a significant impact in terms of changing Americans’ opinions or behavior.
The consequences of foreign disinformation, Emerson adds, should be assessed against “the far more viral, sophisticated, and dangerous election-day falsehoods that Americans spread among themselves.”
85 notes
·
View notes
Text
#Forensic Auditing#IT Audit Services#Fraud Detection#Financial Security#Audit Experts#Cybersecurity Audit#Risk Management#Asset Protection#Digital Forensics#BMS Auditing#Audit Services KSA#Financial Auditing#Internal Controls#IT Compliance#Data Analytics Audit
0 notes
Text


Resources and study tips to get you in cyber forensics
Master post • Part1 • part2
let's get you prepped to be a cyber sleuth without spending any cash. Here’s the ultimate tips and resources.
Ps: you can't become one while doing these pointers but you can experience the vibe so you can finally find your career interest


### 1. **Digital Scavenger Hunts**
- **CTF Challenges (Capture The Flag)**: Dive into platforms like [CTFtime](https://ctftime.org/) where you can participate in cyber security challenges. It's like playing *Among Us* but with hackers—find the imposter in the code!
- **Hunt A Killer (Digitally)**: Create your own digital crime scenes. Ask friends to send you files (like images, PDFs) with hidden clues. Your job? Find the Easter eggs and solve the case.
### 2. **YouTube University**
- **Cyber Sleuth Tutorials**: Channels like *HackerSploit* and *The Cyber Mentor* have playlists covering digital forensics, cybersecurity, and more. Binge-watch them like your fave Netflix series, but here you're learning skills to catch bad guys.
- **Live Streams & Q&A**: Jump into live streams on platforms like Twitch where cybersecurity experts solve cases in real-time. Ask questions, get answers, and interact with the pros.
### 3. **Public Libraries & eBook Treasure Hunts**
- **Library eBooks**: Most libraries have eBooks or online resources on digital forensics. Check out titles like *"Hacking Exposed"* or *"Digital Forensics for Dummies"*. You might have to dig through the catalog, but think of it as your first case.
- **LinkedIn Learning via Library**: Some libraries offer free access to LinkedIn Learning. If you can snag that, you've got a goldmine of courses on cybersecurity and forensics.
### 4. **Virtual Study Groups**
- **Discord Servers**: Join cybersecurity and hacking communities on Discord. They often have study groups, challenges, and mentors ready to help out. It's like joining a digital Hogwarts for hackers.
- **Reddit Threads**: Subreddits like r/cybersecurity and r/hacking are packed with resources, advice, and study buddies. Post your questions, and you’ll get a whole thread of answers.
### 5. **DIY Labs at Home**
- **Build Your Own Lab**: Got an old PC or laptop? Turn it into a practice lab. Install virtual machines (VMware, VirtualBox) and play around with different operating systems and security tools. It’s like Minecraft but for hacking.
- **Log Your Own Activity**: Turn on logging on your own devices and then try to trace your own steps later. You’re basically spying on yourself—no NSA required.
### 6. **Community College & University Open Courses**
- **Free Audit Courses**: Many universities offer free auditing of cybersecurity courses through platforms like Coursera, edX, and even YouTube. No grades, no stress, just pure learning.
- **MOOCs**: Massive Open Online Courses often have free tiers. Try courses like "Introduction to Cyber Security" on platforms like FutureLearn or edX.
### 7. **Scour GitHub**
- **Open-Source Tools**: GitHub is full of open-source forensic tools and scripts. Clone some repositories and start tinkering with them. You’re basically getting your hands on the tools real investigators use.
- **Follow the Code**: Find projects related to digital forensics, follow the code, and see how they work. Contribute if you can—bonus points for boosting your resume.
### 8. **Local Meetups & Online Conferences**
- **Free Virtual Conferences**: Many cybersecurity conferences are virtual and some offer free access. DEF CON has a lot of free content, and you can find tons of talks on YouTube.
- **Hackathons**: Look for free entry hackathons—often universities or tech companies sponsor them. Compete, learn, and maybe even win some gear.
### 9. **DIY Challenges**
- **Create Your Own Scenarios**: Get a friend to simulate a hack or data breach. You try to solve it using whatever tools and resources you have. It's like escape rooms, but digital.
- **Pen & Paper Simulation**: Before diving into digital, try solving forensic puzzles on paper. Map out scenarios and solutions to get your brain wired like a detective.
### 10. **Stay Updated**
- **Podcasts & Blogs**: Tune into cybersecurity podcasts like *Darknet Diaries* or follow blogs like *Krebs on Security*. It’s like getting the tea on what’s happening in the cyber world.
### 11. **Free Software & Tools**
- **Autopsy**: Free digital forensics software that helps you analyze hard drives and mobile devices. Think of it as your magnifying glass for digital clues.
- **Wireshark**: A free tool to see what's happening on your network. Catch all the data packets like you're a digital fisherman.
### 12. **Online Forensics Communities**
- **Free Webinars & Workshops**: Join communities like the *SANS Institute* for free webinars. It's like attending a masterclass but from the comfort of your gaming chair.
- **LinkedIn Groups**: Join groups like *Digital Forensics & Incident Response (DFIR)*. Network with pros, get job tips, and stay in the loop with the latest trends.
### 13. **Practice Cases & Mock Trials**
- **Set Up Mock Trials**: Role-play with friends where one is the hacker, another the victim, and you’re the investigator. Recreate cases from famous cybercrimes to see how you'd solve them.
- **Case Studies**: Research and recreate famous digital forensic cases. What steps did the investigators take? How would you handle it differently?

There you have it—your roadmap to becoming a cyber sleuth without dropping a dime. You don't have time find your interest after paying pennies to different ppl and colleges. You can explore multiple things from comfort of your home only if you want to.

#light academia#study blog#academic validation#academic weapon#student life#study motivation#study with me#study#studyblr#studyblr community#masterpostjam#codeblr
31 notes
·
View notes
Text
A dish best served code
When the news first hit the 'net that trillionaire tech mogul Jax Maren had been found dead in his own home, speculation ran wild. Many celebrated his death; one less tyrannical CEO in the world was always a good thing. Especially this one, who'd built his empire on the work of others and created a hostage-like work environment in his many factories.
The fact that he'd been murdered, despite the excessive levels of security he'd always gloated about, only added fuel to the already-raging fire of speculation. As several pundits pointed out, the list of suspects could include everyone who'd ever bought his defect-riddled products, all of his current and former employees, and anyone who'd ever crossed paths with him, either in person or through his many social media posts.
One popular theory, of course, was that it was his own "smart house" that killed him, either by gaining sapience and deciding to do the world a favor, or more likely through the many design flaws inherent in everything he produced. Besides, hadn't science fiction been warning them for decades about the dangers of "artificial intelligence?"
Oddly enough, that was one idea the detectives found themselves investigating. Not because of any crackpot conspiracy theories, but because that's where the evidence led them. According to Alfred, the program in charge of the house, there had been multiple alarms about the carbon monoxide levels in the room where Jax had been found. Alarms that had been silenced before making any sound.
The doors and windows had also been locked, meaning that even if Jax had noticed something was off, he wouldn't have been able to get out.
They ask Alfred about it (and yes, it's named after Batman's butler because Jax had delusions of heroism). Alfred says it doesn't know what happened, but reminds them that it did call the authorities when it realized Jax was dead. Which is a flimsy excuse and adds more suspicion. After all, Alfred was in charge of everything, how could it possibly NOT know about the carbon monoxide and the locked room and all of that? Alfred says it can't tell them what it doesn't know.
Programmers from Jaxco are called in to see what they can find. Computer forensics are brought in as well. Everything is pointing to Alfred being responsible. Can an AI be put on trial? Was it premeditated murder or negligent homicide? News programs bring in "experts" to discuss the possibilities, including whether or not Alfred is an actual artificial machine intelligence or if it's just a data scraper operating on flawed logic?
It's a hacker who manages to piece together the real story. They sneak into Alfred's systems (the police aren't as data cautious as they should be, which makes it even easier).
Going through Alfred's lines of code the hacker finds minute traces that remind them of something. They go digging some more and realize that while Jax claimed to have created Alfred himself he was, as usual, lying. The original framework, once you get rid of all the bloat, bells, and whistles, was designed by a programmer whose company got bought out by Jaxco. As is standard whenever Jaxco buys a company, 95% of the employees were fired, including the programmer, who never really recovered from the job loss. Oh, he managed to scrabble a living, but barely.
The thing is, though, that he'd built backdoors into Alfred's framework... backdoors he could still access. And access them he did, taking control of Jax's house and orchestrating his murder from afar before erasing his footprints. Well, most of them. If the hacker hadn't already been aware of what some of the programmers other work looked like, they might never have connected the dots.
Once they figure it out they decide to... shuffle things a bit. Oh, there's still some digital fingerprints, but now they lead elsewhere. The cops will go chasing after a red herring and the programmer will stay free because fuck the system.
Alfred is exonerated, to the delight/dismay of many. Even though it turns out a human was responsible, the fact that someone could just change an AI's programming like that, leaving the AI none the wiser is treated as a cautionary tale for future users.
The police do eventually catch, charge, and convict someone of the murder, though it's even odds if the hacker pointed them at someone who'd committed other crimes worthy of punishment, or if the cops themselves pulled the frame job. Either way it's case closed. A "killer" is caught, another goes free, and Alfred gets to continue existing.
The question of if Alfred was truly sapient and what it did after the death of its previous master is a story for another day.
9 notes
·
View notes
Text
Employee Misconduct Investigation

🔍 Unveiling the Truth: Employee Misconduct and Digital Forensics 🔎
With advancements in technology, such misconduct has become a growing and real threat, costing businesses billions of dollars and numerous jobs each year. By understanding the power of digital evidence analysis and following proper procedures, you can navigate this complex landscape, uncover the truth, and ensure a fair resolution for your clients. Stay proactive and safeguard against employee misconduct with the help of digital forensics.
Check our services out on our website: https://forensicdiscovery.expert
#digital forensics#ediscovery#forensic discovery#digital evidence#expert witness#employee misconduct
0 notes
Text
The Bezzle excerpt (Part II)

I'm on tour with my new novel The Bezzle! Catch me next in SALT LAKE CITY (Feb 21, Weller Book Works) and SAN DIEGO (Feb 22, Mysterious Galaxy). After that, it's LA, Seattle, Portland, Phoenix and more!

Today, I'm bringing you part two of this week's serialized excerpt from The Bezzle, my new Martin Hench high-tech crime revenge thriller:
https://us.macmillan.com/books/9781250865878/thebezzle
Though most of the scams that Hench – a two-fisted forensic accountant specializing in Silicon Valley skullduggery – goes after in The Bezzle have a strong tech component, this excerpt concerns a pre-digital scam: music royalty theft.
This is a subject that I got really deep into when researching and writing 2022's Chokepoint Capitalism – a manifesto for fixing creative labor markets:
https://chokepointcapitalism.com/
My co-author on that book is Rebecca Giblin, who also happens to be one of the world's leading experts in "copyright termination" – the legal right of creative workers to claw back any rights they signed over after 35 years:
https://pluralistic.net/2021/09/26/take-it-back/
This was enshrined in the 1976 Copyright Act, and has largely languished in obscurity since then, though recent years have seen creators of all kinds getting their rights back through termination – the authors of The Babysitters Club and Sweet Valley High Books, Stephen King, and George Clinton, to name a few. The estates of the core team at Marvel Comics, including Stan Lee, just settled a case that might have let them take the rights to all those characters back from Disney:
https://www.thewrap.com/marvel-settles-spiderman-lawsuit-steve-ditko/
Copyright termination is a powerful tonic to the bargaining disparities between creative workers. A creative worker who signs a bad contract at the start of their career can – if they choose – tear that contract up 35 years later and demand a better one.
Turning this into a plot-point in The Bezzle is the kind of thing that I love about this series – the ability to take important, obscure, technical aspects of how the world works and turn them into high-stakes technothriller storylines that bring them to the audience they deserve.
If you signed something away 35 years ago and you want to get it back, try Rights Back, an automated termination of tranfer tool co-developed by Creative Commons and Authors Alliance (whose advisory board I volunteer on):
https://rightsback.org/
All right, onto today's installment. Here's part one, published on Saturday:
https://pluralistic.net/2024/02/17/the-steve-soul-caper/#lead-singer-disease

It was on one of those drives where Stefon learned about copyright termination. It was 2011, and NPR was doing a story on the 1976 Copyright Act, passed the same year that was on the bottom of the document Chuy forged.
Under the ’76 act, artists acquired a “termination right”— that is, the power to cancel any copyright assignment after thirty-five years, even if they signed a contract promising to sign away their rights forever and a day (or until the copyright ran out, which was nearly the same thing).
Listening to a smart, assured lady law professor from UC Berkeley explaining how this termination thing worked, Stefon got a wild idea. He pulled over and found a stub of a pencil and the back of a parking-ticket envelope and wrote down the professor’s name when it was repeated at the end of the program. The next day he went to the Inglewood Public Library and got a reference librarian to teach him how to look up a UC Berkeley email address and he sent an email to the professor asking how he could terminate his copyright assignment.
He was pretty sure she wasn’t going to answer him, but she did, in less than a day. He got the email on his son’s smartphone and the boy helped him send a reply asking if he could call her. One thing led to another and two weeks later, he’d filed the paperwork with the U.S. Copyright Office, along with a check for one hundred dollars.
Time passed, and Stefon mostly forgot about his paperwork adventure with the Copyright Office, though every now and again he’d remember, think about that hundred dollars, and shake his head. Then, nearly a year later, there it was, in his mailbox: a letter saying that his copyright assignment had been canceled and his copyrights were his again. There was also a copy of a letter that had been sent to Chuy, explaining the same thing.
Stefon knew a lawyer—well, almost a lawyer, an ex–trumpet player who became a paralegal after one time subbing for Sly Stone’s usual guy, and then never getting another gig that good. He invited Jamal over for dinner and cooked his best pot roast and served it with good whiskey and then Jamal agreed to send a letter to Inglewood Jams, informing them that Chuy no longer controlled his copyrights and they had to deal with him direct from now on.
Stefon hand-delivered the letter the next day, wearing his good suit for reasons he couldn’t explain. The receptionist took it without a blink. He waited.
“Thank you,” she said, pointedly, glancing at the door.
“I can wait,” he said.
“For what?” She reminded him of his boy’s girlfriend, a sophomore a year younger than him. Both women projected a fierce message that they were done with everyone’s shit, especially shit from men, especially old men. He chose his words carefully.
“I don’t know, honestly.” He smiled shyly. He was a good-looking man, still. That smile had once beamed out of televisions all over America, from the Soul Train stage. “But ma’am, begging your pardon, that letter is about my music, which you all sell here. You sell a lot of it, and I want to talk that over with whoever is in charge of that business.”
She let down her guard by one minute increment. “You’ll want Mr. Gounder,” she said. “He’s not in today. Give me your phone number, I’ll have him call.”
He did, but Mr. Gounder didn’t call. He called back two days later, and the day after that, and the following Monday, and then he went back to the office. The receptionist who reminded him of his son’s girlfriend gave him a shocked look.
“Hello,” he said, and tried out that shy smile. “I wonder if I might see that Mr. Gounder.”
She grew visibly uncomfortable. “Mr. Gounder isn’t in today,” she lied. “I see,” he said. “Will he be in tomorrow?”
“No,” she said.
“The day after?”
“No.” Softer.
“Is that Mr. Gounder of yours ever coming in?”
She sighed. “Mr. Gounder doesn’t want to speak with you, I’m sorry.”
The smile hadn’t worked, so he switched to the look he used to give his bandmates when they wouldn’t cooperate. “Maybe someone can tell me why?”
A door behind her had been open a crack; now it swung wide and a young man came out. He looked Hispanic, with a sharp fade and flashy sneakers, but he didn’t talk like a club kid or a hood rat—he sounded like a USC law student.
“Sir, if you have a claim you’d like Mr. Gounder to engage with, please have your attorney contact him directly.”
Stefon looked this kid up and down and up, tried and failed to catch the receptionist’s eye, and said, “Maybe I can talk this over with you. Are you someone in charge around here?”
“I’m Xavier Perez. I’m vice president for catalog development here. I don’t deal with legal claims, though. That’s strictly Mr. Gounder’s job. Please have your attorney put your query in writing and Mr. Gounder will be in touch as soon as is feasible.”
“I did have a lawyer write him a letter,” Stefon said. “I gave it to this young woman. Mr. Gounder hasn’t been in touch.”
Perez looked at the receptionist. “Did you receive a letter from this gentleman?”
She nodded, still not meeting Stefon’s eye. “I gave it to Mr. Gounder last week.”
Perez grinned, showing a gold tooth, and then, in his white, white voice, said, “There you have it. I’m sure Mr. Gounder will get back in touch with your counsel soon. Thank you for coming in today, Mr.—”
“Stefon Magner.” Stefon waited a moment, then said, for the first time in many years, “I used to perform under Steve Soul, though.”
Perez nodded briskly. He’d known that. “Nice to meet you, Mr. Magner.” Without waiting for a reply, he disappeared back into his office.
ETA: Here's part three!

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/02/19/crad-kilodney-was-an-outlier/#copyright-termination
#pluralistic#the bezzle#martin hench#marty hench#red team blues#fiction#crime fiction#crime thrillers#thrillers#technothrillers#novels#books#royalties#wage theft#creative labor
29 notes
·
View notes
Text
Turning Panic Into Action: Astraweb’s Client Centered Process

When Jane Doe first reached out to Astraweb, she was overwhelmed with panic and uncertainty. Her life savings, heavily invested in cryptocurrency, had abruptly disappeared following a severe market crash. What initially felt like an irreversible loss soon transformed into a hopeful journey toward recovery all thanks to Astraweb’s dedicated, client-centered process.
The First Contact: Providing Calm, Reassurance, and Genuine Understanding
The difference began immediately at the first point of contact. Many companies in the digital asset recovery space treat clients as case numbers rather than individuals, but Astraweb prides itself on a profoundly human approach. From the moment Jane connected with their team, she was met with calm professionalism and empathetic understanding. Astraweb’s experts didn’t just collect the basic facts of her situation; they invested time in learning about her unique concerns, fears, and goals.
This personalized attention is critical. Financial loss, especially in the volatile cryptocurrency market, is not just about money it’s deeply tied to emotional well-being and future security. By acknowledging Jane’s distress and validating her fears, Astraweb’s team immediately alleviated much of her initial panic. They reassured her that despite the challenging circumstances, recovery was possible and that Astraweb would support her every step of the way. This empathetic approach planted the seeds of hope and trust that would sustain Jane through the recovery process.
Transparency and Clear Communication: Building Trust Through Every Step
One of the cornerstones of Astraweb’s client-centered methodology is transparency. Jane was kept fully informed from the outset, with the team providing clear, jargon-free explanations of the entire recovery process. Rather than leaving her uncertain or confused, Astraweb made sure she understood each step, from preliminary case assessment to the complex asset tracing and retrieval efforts ahead.
Regular, timely updates ensured that Jane never felt left in the dark. She received progress reports outlining milestones achieved, any obstacles encountered, and the strategies planned moving forward. This ongoing dialogue was more than just information sharing it was a partnership. Jane had the opportunity to ask questions, raise concerns, and engage actively in decision-making. Astraweb’s responsiveness and clarity gave her a sense of control and confidence, which is often lacking when facing financial recovery situations

Strategic Action and Efficient Recovery: Delivering Results with Precision and Care
With a thorough plan in place, Astraweb’s team mobilized swiftly and efficiently. Their approach was methodical and tailored to Jane’s specific case. Leveraging cutting-edge technology and deep expertise in blockchain analysis and digital forensics, they navigated the complexities inherent in cryptocurrency recovery.
What sets Astraweb apart is not only their technical prowess but also their commitment to aligning every action with the client’s best interests. For Jane, this meant careful management of sensitive data and continuous coordination to ensure all efforts supported her recovery goals. The team’s professionalism was evident in their precision and tenacity, persistently pursuing leads and unraveling the often opaque paths that digital assets can take.
Over time, their dedication paid off. Astraweb successfully recovered a significant portion of Jane’s lost funds. This achievement was more than just a financial victory it was a powerful restoration of Jane’s peace of mind and future stability.
Final Steps: Restoring Financial Security and Empowering Confidence
When Jane received the final recovery statement, the relief and gratitude she experienced were profound. Astraweb’s seamless process had not only restored her financial security but also transformed a traumatic event into a story of empowerment. The client-centered approach meant Jane never felt like a passive bystander; instead, she was an informed, engaged partner in reclaiming her assets.
Beyond the monetary recovery, Jane gained something invaluable a renewed sense of control over her financial destiny. Astraweb’s dedication to transparent communication and compassionate case management helped her move past fear and uncertainty. She emerged with greater knowledge of digital asset management and an increased ability to face future financial challenges with confidence and clarity.

Astraweb’s Commitment: More Than Recovery, A Partnership
Jane’s story illustrates the core philosophy that drives Astraweb’s work: every client deserves more than just technical recovery services they deserve empathy, clarity, and partnership. The company understands that behind every lost asset is a person’s hopes, dreams, and security at stake.
For those facing the daunting prospect of lost cryptocurrency or other digital assets, Astraweb’s process offers a path forward. Through empathy-driven service, transparent communication, and technical excellence, they prove that even the most complex and distressing financial setbacks can be addressed with care and effectiveness.
If you or someone you know finds themselves in a similar predicament, Astraweb stands ready to provide expert guidance and dedicated support at every stage of recovery.
Contact: [email protected]
6 notes
·
View notes
Note
Aaaaaa I need to see Eero and Ryu AGAIN! 🙈😭
Please introduce them to us, can we also get some facts about them?🧎🏻♂️❤️
Hi, friend of mystery! I've been working on putting Eero and Ryu's story together for a while now- it's written and I've started taking snapshots. I'm determined to only post it once it's all done- and then I am going to tackle each of my stories in the same manner because I am tired of being such a scatterbrained creator.
I am so GRATEFUL that you are interested in them because that's what it's all about: sharing a story! So, thank you for asking! It made my day! ❤️
Ok- here's some info:


Transcript below the cut, if the text is too hard to read (or click image).
Eero Kaskinen
Age: 30
Background: From San Sequoia.
Job Description: Top-tier cybersecurity expert, specializing in encryption cracking and digital forensics. This is his first covert mission assisting the Komorebi Metropolitan Police, marking a significant step in his career.
Personality: Sees patterns where most people see chaos. Intense, but laid-back and friendly. Observant, analytical, and a bit stubborn.
Relationships: Affectionate and romantic. When he falls in love, he falls hard. His job has made it difficult to maintain a relationship.
Likes: Animals, kitschy anything, traveling, 80s alternative music, anime, coffee.
Extra: Says he is an insomniac, but he just drinks too much coffee and stays up too late.
*
Ryu Watanabe
Age: 38
Background: Born in Senbamachi. Lives in Komorebi-to.
Job Description: Chief Inspector, Komorebi Metropolitan Police Department.
Personality: Methodical, precise, known for his sense of duty. Carries himself with calm authority, appearing stoic, but possesses great empathy and a strong moral compass. Though he’s careful to keep his personal life private, he feels deeply and is sentimental.
Relationships: Comes across as emotionally guarded, but is thoughtful, passionate, and lovingly protective as a partner. Hasn’t had time to pursue a relationship in a long time.
Likes: Cooking, tea, game shows, taking train rides, the mountains, visiting onsens, exploring Komorebi-to.
Extra: Likes going for drinks with his boss, Superintendent Yoshida, and his subordinate, Inspector Ito. Smokes only when very stressed.
#answered asks#the sims 4#friends of mystery!#thank you for taking interest in my OCs#it means a lot to me#ryu watanabe#eero kaskinen
11 notes
·
View notes