#dragonflybsd
Explore tagged Tumblr posts
Text
This Week in Rust 519
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @ThisWeekInRust on Twitter or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub and archives can be viewed at this-week-in-rust.org. If you find any errors in this week's issue, please submit a PR.
Updates from Rust Community
Official
A tale of broken badges and 23,000 features
crates.io: Dropping support for non-canonical downloads
Generators are dead, long live coroutines, generators are back
Project/Tooling Updates
ratatui 0.24.0 is released! (Rust library that's all about cooking up terminal user interfaces)
git-cliff 1.4.0 is released! (highly customizable changelog generator)
rust-analyzer changelog #205
Progress report on rustc_codegen_cranelift (Oct 2023)
Observations/Thoughts
System dependencies are hard (so we made them easier)
Was Rust Worth It?
Can Rust prevent logic errors?
Faster Rust Serialization
Dealing with Dependencies in Rust
How I learned to stop worrying and love byte ordering
How To Move Fast With Rust
Starting a virtual Rust meet-up
[video] Impl Trait aka Look ma’, no generics! by Jon Gjengset
Rust Walkthroughs
Fully Automated Releases for Rust Projects
The beauty of a Rust message processor
interrupts is threads
htmx, Rust & Shuttle: A New Rapid Prototyping Stack
[video] Async Not Required 🦀
Research
Functional Ownership through Fractional Uniqueness
Grading on a Curve: How Rust can Facilitate New Contributors while Decreasing Vulnerabilities
Miscellaneous
[video] 5 Hours to 7.7 Seconds: How Database Tricks Sped up Rust Linting Over 2000x
Crate of the Week
This week's crate is silkenweb, a library for building web apps with fine-grained reactivity and a clean separation of logic and UI.
Thanks to henrik for the suggestion!
Please submit your suggestions and votes for next week!
Call for Participation
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
pubgrub - Move to edition 2021
pubgrub - Fix CI for conventional commits
pubgrub - Rename v0.3 Range into BoundedRange
pubgrub - OfflineDependencyProvider should get its own module
Ockam - Library - Slim down the NodeManagerWorker for node / tcp
Ockam - Make ockam vault delete (no args) interactive by asking the user to choose from a list of vaults to delete (tuify)
Ockam - Command - refactor to use typed interfaces to implement commands for services
If you are a Rust project owner and are looking for contributors, please submit tasks here.
Updates from the Rust Project
408 pull requests were merged in the last week
-Zunpretty help: add missing possible values
NVPTX: allow PassMode::Direct for ptx kernels for now
OptWithInfcx naming nits, trait bound simplifications
deduce_param_attrs: explain a read-only case
rustc_interface cleanups
stack_overflow: get_stackp using MAP_STACK flag on dragonflybsd too
add bootstrap flag --skip-stage0-validation
add method to convert internal to stable constructs
add support for i586-unknown-netbsd as target
add support for mipsel-unknown-netbsd, 32-bit LE mips
add target features for LoongArch
add way to differentiate argument locals from other locals in Stable MIR
allow partially moved values in match
allow target specs to use an LLD flavor, and self-contained linking components
allows #[diagnostic::on_unimplemented] attributes to have multiple
avoid repeated interning of env!("CFG_RELEASE")
avoid unbounded O(n^2) when parsing nested type args
avoid unnecessary builds/rebuilds of rust-demangler
avoid unnecessary renumbering during borrowck
c-variadic error improvements
consider alias bounds when computing liveness in NLL (but this time sound hopefully)
const stabilize mem::discriminant
correctly handle nested or-patterns in exhaustiveness
coverage: consistently remove unused counter IDs from expressions/mappings
coverage: replace manual debug indents with nested tracing spans in counters
create windows/api.rs for safer FFI
create a new ConstantKind variant (ZeroSized) for StableMIR
declare rustc_target's dependency on object/macho
deny providing explicit effect params
derive Ord, PartialOrd and Hash for SocketAddr*
detect when trait is implemented for type and suggest importing it
do not suggest 'Trait<Assoc=arg>' when in trait impl
don't normalize to an un-revealed opaque when we hit the recursion limit
don't treat closures/coroutine types as part of the public API
don't use LFS64 symbols on musl
eat close paren if capture_cfg to avoid unbalanced parens
enable cg_clif tests for riscv64gc
fail typeck for illegal break-with-value
fix ICE: Restrict param constraint suggestion
fix failure to detect a too-big-type after adding padding
fix inline const pattern unsafety checking in THIR
fix missing leading space in suggestion
fix unused variables lint issue for args in macro
fix unwrap suggestion for async fn
generate aggregate constants in DataflowConstProp
handle ReErased in responses in new solver
ignore RPIT duplicated lifetimes in opaque_types_defined_by
implement C ABI lowering for CSKY
implement gen blocks in the 2024 edition
improve android-ndk property interface
improve some diagnostics around ?Trait bounds
improve the warning messages for the #[diagnostic::on_unimplemented]
increase the reach of panic_immediate_abort
intern LocalDefId list from opaque_types_defined_by query
introduce -C instrument-coverage=branch to gate branch coverage
invalid ? suggestion on mismatched Ok(T)
lint overlapping ranges as a separate pass
mark .rmeta files as /SAFESEH on x86 Windows
mark constructor of BinaryHeap as const fn
never consider raw pointer casts to be trival
on object safety error, mention new enum as alternative
on unresolved imports, suggest a disambiguated path if necessary to avoid collision with local items
only call mir_const_qualif if absolutely necessary
only emit one error per unsized binding, instead of one per usage
poison check_well_formed if method receivers are invalid to prevent typeck from running on it
print variadic argument pattern in HIR pretty printer
properly restore snapshot when failing to recover parsing ternary
quietly fail if an error has already occurred
rand use getrandom for freebsd (available since 12.x)
refactor type visitor walking
remap Cargo dependencies to /rust/deps
remove -Zdep-tasks
remove Apple RNG fallbacks and simplify implementation
remove fold code and add Const::internal() to StableMIR
remove support for alias -Z instrument-coverage
require target features to match exactly during inlining
return multiple object-safety violation errors and code improvements to the object-safety check
return unfixed len if pat has reported error
rework negative coherence to properly consider impls that only partly overlap
rustdoc: elide cross-crate default generic arguments
rustdoc: use ThinVec in GenericParamDefKind
see through aggregates in GVN
separate move path tracking between borrowck and drop elaboration
share some track_caller logic between interpret and codegen
small ty::print cleanups
some diagnostics improvements of gen blocks
stash and cancel cycle errors for auto trait leakage in opaques
stop telling people to submit bugs for internal feature ICEs
store #[stable] attribute's since value in structured form
suggest assoc fn new when trying to build tuple struct with private fields
suggest unwrap/expect for let binding type mismatch
tvOS simulator support on Apple Silicon for rustc
tweak suggestion span for outer attr and point at item following invalid inner attr
uplift Canonical to rustc_type_ir
uplift ClauseKind and PredicateKind into rustc_type_ir
use ImageDataType for allocation type
validate feature and since values inside #[stable(…)]
when encountering sealed traits, point types that implement it
when expecting closure argument but finding block provide suggestion
work around the fact that check_mod_type_wf may spuriously return ErrorGuaranteed
time: use clock_gettime on macos
windows: support sub-millisecond sleep
refactor some char, u8 ASCII functions to be branchless
add #[inline] to some recalcitrant ops::range methods
stabilize ratified RISC-V Target Features
stabilize [const_]pointer_byte_offsets
stabilize inline asm usage with rustc_codegen_cranelift
futures: add TryAll and TryAny adapters
futures: fix Sync impl of FuturesUnordered
futures: provide AtomicWaker if portable-atomic feature is enabled, even if atomic CAS is not available
codegen_gcc: add basics for test command in build system
codegen_gcc: fix volatile_load
cargo toml: Allow version-less manifests
cargo toml: Decouple parsing from interning system
cargo: shell: Write at once rather than in fragments
cargo: add new packages to [workspace.members] automatically
cargo: move up looking at index summary enum
cargo: remove duplicate binaries during install
cargo: remove outdated option to -Zcheck-cfg warnings
rustfmt: fixed error caused by combination of match_arm_blocks and control_brace_style
clippy: ignored_unit_patterns: check &(), &&(),
clippy: iter_without_into_iter: fix papercuts in suggestion and restrict linting to exported types
clippy: let_and_return: Wrap with parenthesis if necessary
clippy: add waker_clone_and_wake lint to check needless Waker clones
clippy: fix missing parenthesis in suboptimal floating point help
clippy: ignore lower-camel-case words in doc_markdown
clippy: move read_zero_byte_vec to nursery
clippy: remove internal feature from clippy_utils
clippy: remove the internal_warn lint category
rust-analyzer: make extract_variable assist in place
Rust Compiler Performance Triage
This week we have two sets of results as last week's arrived later than the publish date:
Triage done by @rylev and @simulacrum.
Revision range: b9832e72..650991d
Across both reports:
9 Regressions, 7 Improvements, 5 Mixed 127 artifact comparisons made in total
Full report #1
Full report #2
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
2024 Edition
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
[disposition: merge] Lifetime Capture Rules 2024
[disposition: merge] Add "crates.io Policy Update" RFC
Tracking Issues & PRs
[disposition: merge] Override Waker::clone_from to avoid cloning Wakers unnecessarily
[disposition: merge] dropck_outlives check whether generator witness needs_drop
[disposition: merge] stricter hidden type wf-check
[disposition: merge] Tracking Issue for the GroupBy and GroupByMut iterators
[disposition: merge] Don't panic in <BorrowedCursor as io::Write>::write
[disposition: merge] Guarantee that char has the same size and alignment as u32
[disposition: merge] Stabilize const_maybe_uninit_zeroed and const_mem_zeroed
[disposition: merge] Clarify UB in get_unchecked(_mut)
[disposition: merge] document that the null pointer has the 0 address
[disposition: close] regression: parameter type may not live long enough
Language Reference
[disposition: merge] Guarantee that raw pointer conversions preserve slice element count
Unsafe Code Guidelines
No Unsafe Code Guideline RFCs entered Final Comment Period this week.
New and Updated RFCs
No New or Updated RFCs were created this week.
Call for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
No RFCs issued a call for testing this week.
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Upcoming Events
Rusty Events between 2023-11-01 - 2023-11-29 🦀
Virtual
2023-11-01 | Virtual (Cardiff, UK)| Rust and C++ Cardiff
ECS with Bevy Game Engine
2023-11-01 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2023-11-02 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2023-11-07 | Virtual (Berlin, DE) | OpenTechSchool Berlin
Rust Hack and Learn | Mirror
2023-11-07 | Virtual (Buffalo, NY, US) | Buffalo Rust Meetup
Buffalo Rust User Group, First Tuesdays
2023-11-09 | Virtual (Nuremberg, DE) | Rust Nuremberg
Rust Nürnberg online
2023-11-14 | Virtual (Dallas, TX, US) | Dallas Rust
Second Tuesday
2023-11-15 | Virtual (Cardiff, UK)| Rust and C++ Cardiff
Building Our Own Locks (Atomics & Locks Chapter 9)
2023-11-15 | Virtual (Richmond, VA, US) | Linux Plumbers Conference
Rust Microconference in LPC 2023 (Nov 13-16)
2023-11-15 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Nightly Night: impl Trait in Type Aliases
2023-11-16 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2023-11-21 | Virtual (Berlin, DE) | OpenTechSchool Berlin
Rust Hack and Learn
2023-11-21 | Virtual (Washington, DC, US) | Rust DC
Mid-month Rustful
2023-11-28 | Virtual (Dallas, TX, US) | Dallas Rust
Last Tuesday
Europe
2023-11-01 | Cologne, DE | Rust Cologne
Web-applications with axum: Hello CRUD!
2023-11-07 | Bratislava, SK | Bratislava Rust Meetup Group
Rust Meetup by Sonalake
2023-11-07 | Aarhus, DK | Rust Aarhus
Rust Aarhus - Rust and Talk beginners edition
2023-11-07 | Lyon, FR | Rust Lyon
Rust Lyon Meetup #7
2023-11-09 | Barcelona, ES | BcnRust
11th BcnRust Meetup
2023-11-09 | Paris, FR | Paris Rustaceans
Rust Meetup in Paris
2023-11-09 | Reading, UK | Reading Rust Workshop
Reading Rust Meetup at Browns
2023-11-21 | Augsburg, DE | Rust - Modern Systems Programming in Leipzig
GPU processing in Rust
2023-11-23 | Biel/Bienne, CH | Rust Bern
Rust Talks Bern @ Biel: Embedded Edition
North America
2023-11-01 | Brookline, MA, US | Boston Rust Meetup
Boston Common Rust Lunch
2023-11-02 | Mountain View, CA, US | Mountain View Rust Meetup
Rust Meetup at Hacker Dojo
2023-11-08 | Boulder, CO, US | Boulder Rust Meetup
Let's make a Discord bot!
2023-11-14 | New York, NY, US | Rust NYC
Rust NYC Monthly Mixer: Share, Show, & Tell! 🦀
2023-11-14 | Seattle, WA, US | Cap Hill Rust Coding/Hacking/Learning
Rusty Coding/Hacking/Learning Night
2023-11-15 | Richmond, VA, US + Virtual | Linux Plumbers Conference
Rust Microconference in LPC 2023 (Nov 13-16)
2023-11-16 | Mountain View, CA, US | Mountain View Rust Meetup
Rust Meetup at Hacker Dojo
2023-11-16 | Nashville, TN, US | Music City Rust Developers
Python loves Rust!
2023-11-16 | Seattle, WA, US | Seattle Rust User Group
Seattle Rust User Group Meetup
2023-11-21 | San Francisco, CA, US | San Francisco Rust Study Group
Rust Hacking in Person
2023-11-22 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
Oceania
2023-11-06 | Perth, WA, AU | Rust Perth Meetup Group
Embracing Lifetimes: A Journey to Safe and Efficient Code
2023-11-21 | Christchurch, NZ | Christchurch Rust Meetup Group
Christchurch Rust meetup meeting
2023-11-28 | Canberra, ACT, AU | Rust Canberra
November Meetup
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
After doing a best fit, we found Rust projects were less likely to introduce vulnerabilities than their equivalent C++ projects at all relevant experience levels, but more importantly, we found the effect was most significant for first-time contributors, who were almost two orders of magnitude less likely to contribute vulnerabilities. That is, even though Rust may have a reputation as a harder language to learn, there is a very measurable effect that makes it better for newbies. Reviewers should not have to put as much effort into reviewing code to be confident that someone making their first foray into their project is accidentally adding a vulnerability.
– Justin Tracey on crysp.org
Thanks to Brian Kung for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin, bennyvasquez.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
1 note
·
View note
Photo

Intel Core i9 10980XE: FreeBSD 12.1 vs. GhostBSD 12.02 vs. DragonFlyBSD vs. Ubuntu Linux Benchmarks https://ift.tt/2QNH34J
2 notes
·
View notes
Text
Introducing RunBSD.info
Introducing RunBSD.info #NetBSD #FreeBSD #OpenBSD #DragonFlyBSD
RunBSD.info is an introductory site covering the features & benefits across the different members of the BSD family of operating systems. To get things started, the content for the site was taken from an earlier post originally put together with a specific audience in mind. That audience was a group of hardware enthusiasts who are not necessarily interested in software but may require an…
View On WordPress
0 notes
Text
Excuse you? You think goblins all run linux?
"Runs linux, and can customize the GUI" is the goblin equivalent of your grandma who got her first computer in 2004 and still can't find the start menu in windows. Goblins consider "runs eight different unrelated versions of linux, at least one of which is an Arch Linux style release, at least one of which is a gentoo-style self compiled distro, and at least one of which dual-boots with one of the others" to be normie shit.
A typical goblin game was writen on DragonflyBSD and saw officially supported release for TempleOS, GNU/Hurd, Haiku OS, and a particular version of a jailbreak for the nintendo 3DS. They figure if you can't port and compile it for ubuntu linux or fedora linux on your VAX yourself, that's a you problem.
Elf video games: 300 hour jrpgs with legions of characters and several novels worth of text. Labrynthine upgrade trees and customization options. The most insufferably unintuitive UI possible. A single turn based battle can take hours. Every character has an ennui stat.
Dwarf video games: Basebuilding strategy FPSs that has a whole wiki page on the flexile vs tensile strengths of different building materials. Dwarven rhythm games have minigames where you have to manage supply lines. Mortals cannot comprehend dwarven grand strategy games.
Halfling video games: What appears on the surface to be a viscerally calming farming sim is actually an extraordinarily complex social combat game about cutthroat HOA politics.
Goblin video games: Wildly unbalanced collectathon gatchas where half the fun is finding new hilariously broken strategies. Zany uberviolent team shooters about bugs. MOBAs so bad it's almost art.
Orc video games: Addictive in-browser flash games with names like "Beast Crush 4" and "Borag Meat Game." The art is always kinda bad but in a charming way. The music always slaps.
67K notes
·
View notes
Text
DragonFlyBSD's HAMMER2 File-System Being Ported to NetBSD
https://www.phoronix.com/news/NetBSD-HAMMER2-Port Comments
0 notes
Text
Download windows 7 iso for mac virtualbox 無料ダウンロード.Download VirtualBox
Download windows 7 iso for mac virtualbox 無料ダウンロード.VirtualBoxにWindows 7をインストール

Context Navigation.Install Windows 7 virtual machine in VirtualBox
Download Windows 7 Virtual Machine Virtualbox Burning ISO allows the user to open the files from their command line despite a GUI like Windows. Today, Burning ISO is no longer used but it is still in existence with the concept of Windows command shell Jul 26, · 表題のとおり Mac にインストールした VirtualBox を使用して Windows 7 の仮想環境を構築します。 ホストマシン OS: macOS High Sierra ; ゲストマシン OS: Windows 7 Home Premium (64 bit) 仮想化ソフトウェア: VirtualBox r (Qt)Estimated Reading Time: 10 mins Oracle VM VirtualBox拡張パック. VirtualBoxの個人利用および評価用ライセンス の条件に従って、Windows、Mac OS X、Linux、およびSolaris xのプラットフォームで個人、教育、または評価目的のために使用する場合は無償です。. プラットフォーム. ファイル. バージョン6
Download windows 7 iso for mac virtualbox 無料ダウンロード.VirtualBoxにWindows 7をインストール
First, you need to open the VirtualBox, select New to create a new virtual machine. Enter the name of virtual machine, herein called "Windows7" by me. Choose the number of RAMs to be provided to the virtual machine. Next, create a virtual hard disk for your virtual machine. Select the position where your virtual disk file will be created and Oracle VM VirtualBox拡張パック. VirtualBoxの個人利用および評価用ライセンス の条件に従って、Windows、Mac OS X、Linux、およびSolaris xのプラットフォームで個人、教育、または評価目的のために使用する場合は無償です。. プラットフォーム. ファイル. バージョン6 Download Windows 7 Virtual Machine Virtualbox Burning ISO allows the user to open the files from their command line despite a GUI like Windows. Today, Burning ISO is no longer used but it is still in existence with the concept of Windows command shell
ここでは、 仮想マシン を作成・実行可能な 仮想化 ソフトウェアの1つである VirtualBox の ゲストOS としてWindows 7をインストールする方法について記します。. 計測していなかったので曖昧ではありますが、インストール時間は、30分前後だったように思われ、 VMware PlayerにWindows 7 を入れた時は、1時間ちょっとかかりましたが、その時は、ホストマシンのRAMが1GBで OS がVistaとHDD換装/RAM微増強前だったことからインストール時間は、RAM容量に大きく左右される模様、というか、システム要件上、無理のある環境だったことに起因しているようです。.
ただ、マウス統合したいとか、シームレス��ードやゲストOSの画面を自動リサイズしたい、共有フォルダを設定したい、3Dアクセラレータを有効にしてAero機能を有効にしたい場合などには、[Guest Additions]のインストールが必要です。. ちなみに、ひょんなことから発見したので[Guest Additions]のインストールの要否は不明ですが、他のWindowsでは見られなかった現象?としてデスクトップ上で[Ctrl]を押しながらマウスホイールを回すとエクスプローラやブラウザ上などのようにデスクトップ上のアイコンが拡大/縮小しました。. Windows Vistaでは、SP2は簡単であった一方、SP1の適用には、えらい煩わされたような記憶がありますが、さすがに対処したとみえてWindows 7では、起動時や終了時に他の更新と同じくSP1も適用され、この点では、楽になっていますね。.
ゲストOSとしてWindows 7をインストール【VirtualBox】. CPU :Intel Core2 1. RAM :2GB. NetBSDの起動とインストール【VMware Player】 DragonFlyBSDの起動とインストール【VMware Player】 MS-DOSディスク構成ファイルサンプル MS-DOS起動ディスク作成と起動【VirtualBox】 MS-DOS起動ディスクでWindows 95をインストール【VirtualBox】 MS-DOS起動ディスクでWindows 98SEをインストール【VirtualBox】 MS-DOS起動ディスクでWindows XPをインストール【VirtualBox】 Windows 7をインストール【VirtualBox】 Windows 8.
0 notes
Photo

Threadripper Tests for DragonFlyBSD https://ift.tt/2PnoYIy
1 note
·
View note
Text
Insights into Why Hyperbola GNU/Linux is Turning into Hyperbola BSD
In late December 2019, Hyperbola announced that they would be making major changes to their project. They have decided to drop the Linux kernel in favor of forking the OpenBSD kernel. This announcement only came months after Project Trident announced that they were going in the opposite direction (from BSD to Linux).
Hyperbola also plans to replace all software that is not GPL v3 compliant with new versions that are.
To get more insight into the future of their new project, I interviewed Andre, co-founder of Hyperbola.
Why Hyperbola GNU/Linux Turned into Hyperbola BSD

It’s FOSS: In your announcement, you state that the Linux kernel is “rapidly proceeding down an unstable path”. Could you explain what you mean by that?
Andre: First of all, it’s including the adaption of DRM features such as HDCP (High-bandwidth Digital Content Protection). Currently there is an option to disable it at build time, however there isn’t a policy that guarantees us that it will be optional forever.
Historically, some features began as optional ones until they reached total functionality. Then they became forced and difficult to patch out. Even if this does not happen in the case of HDCP, we remain cautious about such implementations.
Another of the reasons is that the Linux kernel is no longer getting proper hardening. Grsecurity stopped offering public patches several years ago, and we depended on that for our system’s security. Although we could use their patches still for a very expensive subscription, the subscription would be terminated if we chose to make those patches public.
Such restrictions goes against the FSDG principles that require us to provide full source code, deblobbed, and unrestricted, to our users.
KSPP is a project that was intended to upstream Grsec into the kernel, but thus far it has not come close to reaching Grsec / PaX level of kernel hardening. There also has not been many recent developments, which leads us to believe it is now an inactive project for the most part.
Lastly, the interest in allowing Rust modules into the kernel are a problem for us, due to Rust trademark restrictions which prevent us from applying patches in our distribution without express permission. We patch to remove non-free software, unlicensed files, and enhancements to user-privacy anywhere it is applicable. We also expect our users to be able to re-use our code without any additional restrictions or permission required.
This is also in part why we use UXP, a fully free browser engine and application toolkit without Rust, for our mail and browser applications.
Due to these restrictions, and the concern that it may at some point become a forced build-time dependency for the kernel we needed another option.
It’s FOSS: You also said in the announcement that you would be forking the OpenBSD kernel. Why did you pick the OpenBSD kennel over the FreeBSD, the DragonflyBSD kernel or the MidnightBSD kernel?
Andre: OpenBSD was chosen as our base for hard-forking because it’s a system that has always had quality code and security in mind.
Some of their ideas which greatly interested us were new system calls, including pledge and unveil which adds additional hardening to userspace and the removal of the systrace system policy-enforcement tool.
They also are known for Xenocara and LibreSSL, both of which we had already been using after porting them to GNU/Linux-libre. We found them to be well written and generally more stable than Xorg/OpenSSL respectively.
None of the other BSD implementations we are aware of have that level of security. We also were aware LibertyBSD has been working on liberating the OpenBSD kernel, which allowed us to use their patches to begin the initial development.
It’s FOSS: Why fork the kernel in the first place? How will you keep the new kernel up-to-date with newer hardware support?
Andre: The kernel is one of the most important parts of any operating system, and we felt it is critical to start on a firm foundation moving forward.
For the first version we plan to keep in synchronization with OpenBSD where it is possible. In future versions we may adapt code from other BSDs and even the Linux kernel where needed to keep up with hardware support and features.
We are working in coordination with Libreware Group (our representative for business activities) and have plans to open our foundation soon.
This will help to sustain development, hire future developers and encourage new enthusiasts for newer hardware support and code. We know that deblobbing isn’t enough because it’s a mitigation, not a solution for us. So, for that reason, we need to improve our structure and go to the next stage of development for our projects.
It’s FOSS: You state that you plan to replace the parts of the OpenBSD kernel and userspace that are not GPL compatible or non-free with those that are. What percentage of the code falls into the non-GPL zone?
Andre: It’s around 20% in the OpenBSD kernel and userspace.
Mostly, the non-GPL compatible licensed parts are under the Original BSD license, sometimes called the “4-clause BSD license” that contains a serious flaw: the “obnoxious BSD advertising clause”. It isn’t fatal, but it does cause practical problems for us because it generates incompatibility with our code and future development under GPLv3 and LGPLv3.
The non-free files in OpenBSD include files without an appropriate license header, or without a license in the folder containing a particular component.
If those files don’t contain a license to give users the four essential freedoms or if it has not been explicitly added in the public domain, it isn’t free software. Some developers think that code without a license is automatically in the public domain. That isn’t true under today’s copyright law; rather, all copyrightable works are copyrighted by default.
The non-free firmware blobs in OpenBSD include various hardware firmwares. These firmware blobs occur in Linux kernel also and have been manually removed by the Linux-libre project for years following each new kernel release.
They are typically in the form of a hex encoded binary and are provided to kernel developers without source in order to provide support for proprietary-designed hardware. These blobs may contain vulnerabilities or backdoors in addition to violating your freedom, but no one would know since the source code is not available for them. They must be removed to respect user freedom.
It’s FOSS: I was talking with someone about HyperbolaBSD and they mentioned HardenedBSD. Have you considered HardenedBSD?
Andre: We had looked into HardenedBSD, but it was forked from FreeBSD. FreeBSD has a much larger codebase. While HardenedBSD is likely a good project, it would require much more effort for us to deblob and verify licenses of all files.
We decided to use OpenBSD as a base to fork from instead of FreeBSD due to their past commitment to code quality, security, and minimalism.
It’s FOSS: You mentioned UXP (or Unified XUL Platform). It appears that you are using Moonchild’s fork of the pre-Servo Mozilla codebase to create a suite of applications for the web. Is that about the size of it?
Andre: Yes. Our decision to use UXP was for several reasons. We were already rebranding Firefox as Iceweasel for several years to remove DRM, disable telemetry, and apply preset privacy options. However, it became harder and harder for us to maintain when Mozilla kept adding anti-features, removing user customization, and rapidly breaking our rebranding and privacy patches.
After FF52, all XUL extensions were removed in favor of WebExt and Rust became enforced at compile time. We maintain several XUL addons to enhance user-privacy/security which would no longer work in the new engine. We also were concerned that the feature limited WebExt addons were introducing additional privacy issues. E.g. each installed WebExt addon contains a UUID which can be used to uniquely and precisely identify users (see Bugzilla 1372288).
After some research, we discovered UXP and that it was regularly keeping up with security fixes without rushing to implement new features. They had already disabled telemetry in the toolkit and remain committed to deleting all of it from the codebase.
We knew this was well-aligned with our goals, but still needed to apply a few patches to tweak privacy settings and remove DRM. Hence, we started creating our own applications on top of the toolkit.
This has allowed us to go far beyond basic rebranding/deblobbing as we were doing before and create our own fully customized XUL applications. We currently maintain Iceweasel-UXP, Icedove-UXP and Iceape-UXP in addition to sharing toolkit improvements back to UXP.
It’s FOSS: In a forum post, I noticed mentions of HyperRC, HyperBLibC, and hyperman. Are these forks or rewrites of current BSD tools to be GPL compliant?
Andre: They are forks of existing projects.
Hyperman is a fork of our current package manager, pacman. As pacman does not currently work on BSD, and the minimal support it had in the past was removed in recent versions, a fork was required. Hyperman already has a working implementation using LibreSSL and BSD support.
HyperRC will be a patched version of OpenRC init. HyperBLibC will be a fork from BSD LibC.
It’s FOSS: Since the beginning of time, Linux has championed the GPL license and BSD has championed the BSD license. Now, you are working to create a BSD that is GPL licensed. How would you respond to those in the BSD community who don’t agree with this move?
Andre: We are aware that there are disagreements between the GPL and BSD world. There are even disagreements over calling our previous distribution “GNU/Linux” rather than simply “Linux”, since the latter definition ignores that the GNU userspace was created in 1984, several years prior to the Linux kernel being created by Linus Torvalds. It was the two different software combined that make a complete system.
Some of the primary differences from BSD, is that the GPL requires that our source code must be made public, including future versions, and that it can only be used in tandem with compatibly licensed files. BSD systems do not have to share their source code publicly, and may bundle themselves with various licenses and non-free software without restriction.
Since we are strong supporters of the Free Software Movement and wish that our future code remain in the public space always, we chose the GPL.
It’s FOSS: I know at this point you are just starting the process, but do you have any idea who you might have a usable version of HyperbolaBSD available?
Andre: We expect to have an alpha release ready by 2021 (Q3) for initial testing.
It’s FOSS: How long will you continue to support the current Linux version of Hyperbola? Will it be easy for current users to switch over to?
Andre: As per our announcement, we will continue to support Hyperbola GNU/Linux-libre until 2022 (Q4). We expect there to be some difficulty in migration due to ABI changes, but will prepare an announcement and information on our wiki once it is ready.
It’s FOSS: If someone is interested in helping you work on HyperbolaBSD, how can they go about doing that? What kind of expertise would you be looking for?
Andre: Anyone who is interested and able to learn is welcome. We need C programmers and users who are interested in improving security and privacy in software. Developers need to follow the FSDG principles of free software development, as well as the YAGNI principle which means we will implement new features only as we need them.
Users can fork our git repository and submit patches to us for inclusion.
It’s FOSS: Do you have any plans to support ZFS? What filesystems will you support?
Andre: ZFS support is not currently planned, because it uses the Common Development and Distribution License, version 1.0 (CDDL). This license is incompatible with all versions of the GNU General Public License (GPL).
It would be possible to write new code under GPLv3 and release it under a new name (eg. HyperZFS), however there is no official decision to include ZFS compatibility code in HyperbolaBSD at this time.
We have plans on porting BTRFS, JFS2, NetBSD’s CHFS, DragonFlyBSD’s HAMMER/HAMMER2 and the Linux kernel’s JFFS2, all of which have licenses compatible with GPLv3. Long term, we may also support Ext4, F2FS, ReiserFS and Reiser4, but they will need to be rewritten due to being licensed exclusively under GPLv2, which does not allow use with GPLv3. All of these file systems will require development and stability testing, so they will be in later HyperbolaBSD releases and not for our initial stable version(s).
I would like to thank Andre for taking the time to answer my questions and for revealing more about the future of HyperbolaBSD.
What are your thoughts on Hyperbola switching to a BSD kernel? What do you think about a BSD being released under the GPL? Please let us know in the comments below.
If you found this article interesting, please take a minute to share it on social media, Hacker News or Reddit.
from It's FOSS https://itsfoss.com/hyperbola-linux-bsd/
Insights into Why Hyperbola GNU/Linux is Turning into Hyperbola BSD was initially seen on http://alaingonza.com/
from https://alaingonza.com/2020/01/16/insights-into-why-hyperbola-gnu-linux-is-turning-into-hyperbola-bsd/
0 notes
Text
How to download and install Unix Solaris OS on VirtualBox

We are very well acquainted with Linux, however, when it comes to UNIX based operating system then most don't know from where to download it. Just like Linux Distros Unix is also available under different names such as Oracle Solaris, OpenSolaris (Discontinued), FreeBSD, OpenBSD, NetBSD and DragonflyBSD. There is quite a confusion between Unix and open source Unix-like operating systems such as Linux. Unix like OS also refer as UN*X or *nix OS are those behaved like UNIX OS following its standardization, basically, they derived from UNIX and sometimes developed as free and open source or proprietary. UNIX was developed at Bell Labs in Manhattan.
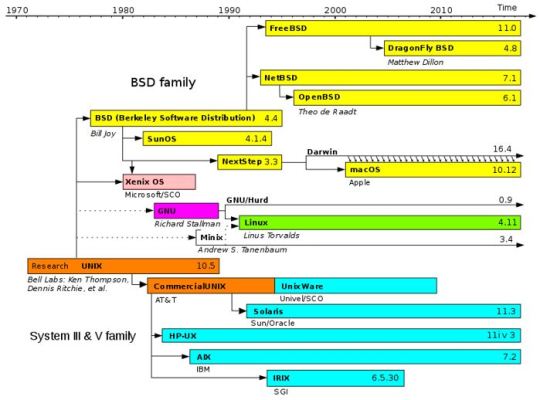
Now, What is Solaris? Solaris is a SPARC (Scalable Processor Architecture) operating system based on UNIX and primarily developed by Sun Microsystem as a superior version to replace their earlier OS called SunOS. However, later in 2010, Oracle has accessed Sun Microsystem and till today Solaris is developed and maintained by Oracle under Oracle Solaris project. It is not completely open source and comes with some proprietary components means few parts are open source to the public and rest of closed such as Solaris kernel source code which apparently becomes closed source after Solaris 11. Well, Oracle Solaris latest version is 11.4 and available on Oracle website published approx. 9 months ago, still, there are some speculations on the Oracle's Solaris roadmap i.e whether they will continue the development of it or not. However, there is no official news on it yet. Coming, to the main agenda of this article is how to downloads Oracle Solaris ISO or VM(OVA) to install on VirtualBox Virtual Machine.
Solaris Operating system installation on VirtualBox VM
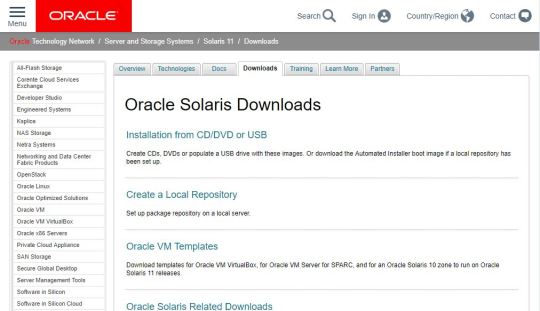
Will show steps to install the Oracle version of Solaris and where to download it in both ISO and VM image formats. Also, the steps will be the same for Windows 10/7, Linux and MacOS for Solaris UNIX installation using Virtualbox. Step 1: Download Oracle Solaris OS in ISO or VM (ova) image format As I said this operating system is maintained by Oracle, thus we have to visit their website. Here is the link: Visit Oracle website When the page will open, under the Downloads tab you will see different options to download Solaris OS. One is the Installation from CD/DV or USB. When you click this link on the page, Solaris ISO file will get downloaded. Go for Oracle Solaris 11.4 Text Installer X86 base for normal PC, Laptop or Virtual machine installation. Another one is Oracle VM Templates, where the latest pre-built Virtual images for Oracle VirtualBox, Oracle VM Server for SPARC and Oracle Solaris 10 Zone are available to download. Apart from this, you can also download older versions ISO files of this UNIX operating system from here. Note: For Virtualization, VM templates are recommended. Once click any of the above options, a page will open, where you have to accept terms and conditions to download it. Plus to download the site will ask you to login with Oracle account if you have then used that otherwise create one. It is free of cost.
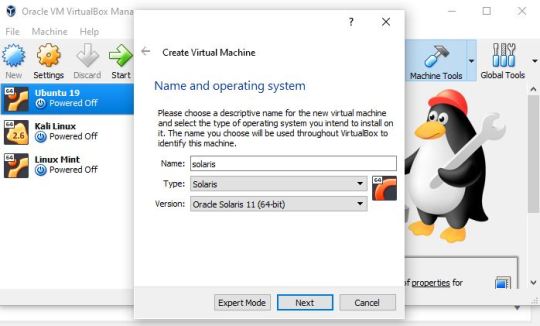
Step 2: Create VM for Solaris on VirtualBox If you have downloaded ISO image of this UNIX OS then you can simply go to the VirtualBox, click on New button from the menu and type Solaris in the Name section. As you type it, the VirtualBox automatically set the rest of the options. However, as we are installing the latest version of Solaris i.e 11.4, so from the Version drop-down box select Oracle Solaris 11 (64 bit). Click on the Next button.
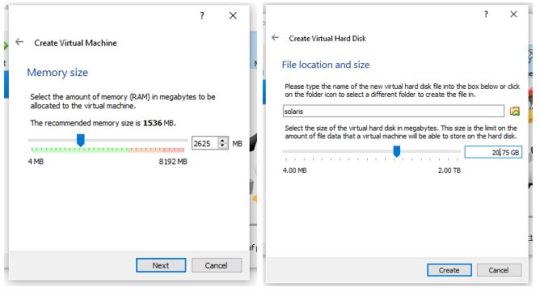
Step 3: Assign Memory and Hard disk Now, in the next guided steps, you get options to assign RAM and Hard disk space for the operating system; Set RAM to minimum 2GB and Minimum 20GB of Virtual Hard disk storage. Note: Leave all the other options to its default while assigning RAM and Storage Space.
Step 4: Set Solaris ISO as a boot medium for VirtualBox's VM To use the downloaded bootable image of this UNIX OS in VirtualBox, first, select the recent created Solaris Virtual Machine that appears on the left side of the VB and then click on the Settings gear icon. Now select Storage->Empty CD icon-> again click on CD icon given under the Attributes and finally select Virtual Optical Disk file. It will open explorer of Windows, Linux or MacOS where you are using VirtualBox and then select the ISO image. Finally, Click on the OK button.
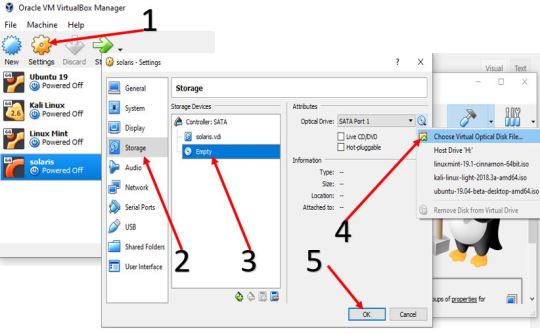
After all above steps, finally, click on the START button given in the VB menu to start virtual machine booting process. Step 5: Import Oracle Solaris 11 VM for Oracle VM VirtualBox (optional step) As we said at the beginning of the article that the operating the system is available in both ISO and VM image format, well above we have shown how to use its ISO image and here we are going to use the VM template. Well, if you just want to use this OS only on Virtualization environment then VM templates are recommended. We have also used it to show this article. After downloading VM image in OVA format go to VirtualBox, click on File menu->select Import Appliances and Import Virtual Appliance or the OVA image of the OS.
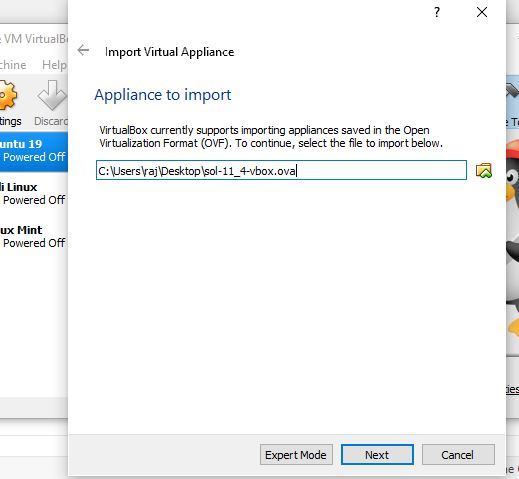
All the settings for the Virtual Machine have already been done by the Oracle for us. So, what we have to do is just a click on the Import button.

To start Solaris Virtual Machine select it from the left side panel and click on the Start button. Step 6: Boot Virtual Machine If everything goes well you will see the Grub boot menu, press the Enter button.
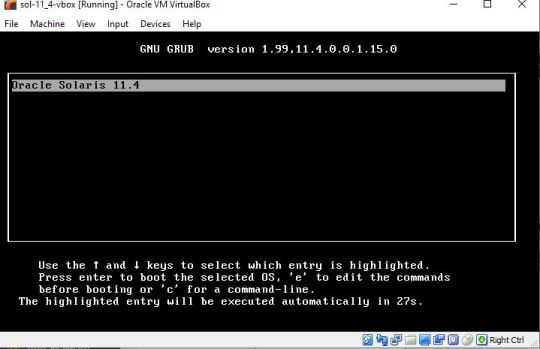
Step 7: System Configuration Some information about what are we about configure would show, press F2 to continue the installation process.

Give some name to your computer and then F2 button.
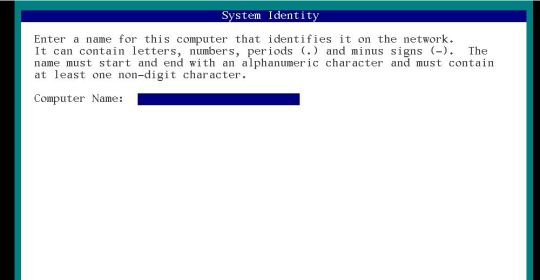
Select the available network connection to configure and press F2.

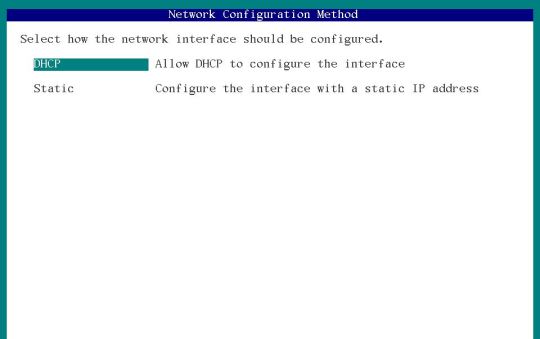
Step 7: System Root Password Assign some System password to that will use to access the Solaris as the root user.
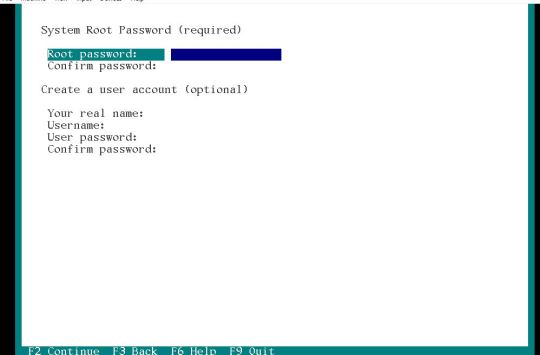
In the next step add your email and Password of Oracle Support account to get informed on security updates otherwise skip it using F2 Key. At the last of the guided steps of the installer review the configuration you made and press F2 to implement them all. Step 8: Login to OS Use username as root and password is what you have created above and enter them to log in.

Step 9: Beautiful Solaris Gnome interface After login, you will see the clean Gnome interface and now start using it to learn curves of UNIX OS.

Other Articles to See: How to install docker on Windows 10 Best Free Virtualbox Alternative for Linux 8 Open source bare-metal hypervisors (Foss) Read the full article
#opensource#solaris11.4virtualbox#solarisimage#solarisvirtualboximage#tutorial#Unix#UnixCommands#UnixTutorial#Virtualbox#virtualization
0 notes
Text
Tweeted
DragonFlyBSD 5.8 llega con mejoras para DRM, memoria virtual y más: Hace pocos días fue anunciado el lanzamiento de la nueva versión de DragonFlyBSD 5.8. Esta nueva versión llega con algunas... https://t.co/ST8wLFp9uJ #Noticias
— AGS&B (@agsb_bilbao) March 6, 2020
0 notes
Text
DragonflyBSD 6.0 Released
https://www.dragonflybsd.org/release60/ Comments
0 notes
Text
Sabes como Mejores servidores FTP y FTPES para Linux: Características y opciones
El protocolo FTP no proporciona ningún tipo de seguridad, ya que las credenciales de favorecido se envían sin acelerar, y lo mismo ocurre con la transferencia de datos propiamente dicha. Gracias al protocolo FTPES, podremos hacer uso de TLS (Transport Layer Security) para la autenticación y transferencia de ficheros segura. La gran mayoría de servidores FTP para Linux, soportan la interpretación cifrada de este protocolo (FTPES).
Proftpd
El primero en sobrevenir por nuestras manos y poderlo analizar es Proftpd, un servidor FTP que surgió por querer tener un servidor seguro y muy configurable, basado por su pasión con destino a el servidor web de Apache por parte de sus creadores. Sus desarrolladores decidieron desarrollar Proftpd porque en ese momento los programas para crear servidores FTP en Linux estaban mucho más limitados, y no tenían las mismas funciones que los programas para Windows.
Las características principales que tiene actualmente Proftpd son:
Tiene un archivo de configuración principal, que contiene directivas y grupos de directivas que son muy intuitivas si has utilizado el servidor web Apache, ya que se basaron en él para crear Proftpd.
Dispone de un directorio llamado «.Ftpaccess» que es similar a «.htaccess» de Apache.
Es muy casquivana configurar múltiples servidores FTP virtuales y servicios FTP anónimos.
Diseñado para ejecutarse como un servidor independiente o desde inetd / xinetd, dependiendo de la carga del sistema.
Dispone de directorios raíz anónimos que no requieren ninguna estructura de directorio, archivos binarios del sistema u otros archivos del sistema.
No hay comando SITE EXEC,evitando así, los problemas que puede provocar en seguridad.
Los directorios y archivos ocultos están basados en permisos de estilo Unix.
Dispone de modo autónomo que se ejecuta como un favorecido sin privilegios para disminuir las posibilidades de ataques.
El registro es compatible con el en serie wu-ftpd, usando utmp / wtmp.
Dispone de un servicio para gobernar contraseñas ocultas y soporte para cuentas caducadas.
Está diseñado de forma modular, eso quiere asegurar que permite ampliar fácilmente el servidor con módulos como por ejemplo módulos para bases de datos SQL, servidores LDAP, encriptación SSL / TLS, soporte RADIUS, etc.
Es compatible y tiene soporte de IPv6.
Para instalarlo solo deberéis desobstruir un terminal e introducir el comando «sudo apt install proftpd», ya que se encuentra en los principales repositorios de todas las distribuciones Linux.
Como podéis ver, Proftpd es muy completo y no tiene nadie que envidiar a sus homólogos en Windows. En RedesZone tenemos un completo tutorial de configuración de Proftpd con las opciones fundamentales.
Vsftpd
Este servidor FTP con atrevimiento GPL está habitable para sistemas UNIX, incluido Linux. Según sus desarrolladores, se comercio de un servidor muy seguro, extremadamente rápido y muy estable. Es tan bueno que el FTP de RedHat y Suse usan este servidor FTP, con esto ya os deberíais hacer una idea de lo bueno y configurable que es. Fue diseñado e implementado desde el principio con el objetivo que fuera seguro, y gracias a eso, tiene solucionado varios fallos de diseño que su competencia no tiene, como, por ejemplo, no usar en exceso el favorecido Root ya que es muy peligroso, y utilizar posibles de seguridad avanzados e incluso usa chroot y técnicas de programación seguras para evitar desbordamientos de búfer.
Sus principales características son:
Dispone de configuraciones de IP imaginario
Puedes crear usuarios virtuales
Puede funcionar en modo operación independiente o inetd.
Las opciones de configuración por parte del favorecido son muy avanzadas.
Dispone de un acelerador de ufano de pandilla para que funcionen las cargas y descargas aún mejor.
Puedes establecer límites por IP.
Es compatible con IPv6.
Tiene soporte de enigmático a través de la integración con SSL.
Si estás buscando un servidor FTP que sea seguro y estable, tienes que probar Vsftpd, unido con Proftpd son los dos mejores servidores FTP que puedes encontrar actualmente.
Pureftpd
Este servidor FTP es regalado como los anteriores, es considerado como seguro y se centra en la eficiencia y la facilidad de uso. Pureftpd se puede ejecutar en Linux, MacOS, OpenBSD, NetBSD, DragonflyBSD, FreeBSD, Solaris y derivados, Tru64, Irix, HPUX y AIX y está traducido a múltiples idiomas entre ellos el gachupin.
Entre sus características principales destaca a facilidad para usuarios principiantes que pueden instalar el servidor en casi nada unos minutos, según aseguran sus desarrolladores, siendo solo necesario instalar el paquete de Pureftpd en el sistema operante. Con Pureftpd no es necesario revisar ningún archivo de configuración ya que utiliza comandos de bisectriz simples para habilitar funciones, encima, además podemos impedir el número de usuarios simultáneos, su ufano de pandilla, ocultar archivos del sistema (chroot) y disponer del estado de las relaciones de carga y descarga, y limitarlas si es necesario. Otras características interesantes son la posibilidad de poner cuotas de uso a los usuarios, configurar el protocolo FXP (servidor a servidor) y que solamente esté habitable para todos los usuarios o solo para usuarios autenticados.
En cuanto a seguridad, hay que destacar que proporciona una protección contra accesos de fuerza bruta, encima el paso es desconocido y seguro de forma predeterminada. Dispone además del comando pure-ftpwho que nos mostrará una tabla con las sesiones activas en tiempo actual, cuánto ufano de pandilla consume cada favorecido, qué archivos está cargando o descargando y de dónde provienen. Entre sus características más específicas encontramos compatible con IPv6
Como podéis ver se comercio de un servidor FTP muy completo, y es utilizado por varios sistemas operativos para routers y servidores NAS correcto a su buen funcionamiento. Dependiendo de la experiencia que tengas, puede ser muy simple para tareas básicas, o configurar opciones avanzadas con todas las opciones disponibles.
Os recomendamos ingresar a la web oficial de Pureftpd donde encontraréis todas las características en detalle y la documentación de este gran servidor FTP para Linux.
CrushFTP
Este servidor FTP te permite descargar archivos en formatos comprimidos in-stream, o incluso expandir automáticamente archivos zip a medida que se reciben in-stream. Esto es más conocido como ZipStreaming y sus ventajas son que puede acelerar enormemente la transferencia de muchos tipos de archivos.
Encima, dispone de sucursal segura a través de navegador web, lo que le permite gobernar y monitorear el servidor desde cualquier zona o con casi cualquier dispositivo. CrushFTP puede detectar intentos comunes de pirateo y robots que buscan contraseñas débiles. Si lo detecta automáticamente, se protegerá contra estos ataques para conseguir las claves y prohibirá automáticamente estas IP. Dispone de una sucursal de usuarios que incluye herencia, grupos y sistemas de archivos virtuales. CrushFTP es compatible con SFTP, SCP, HTTPS, WebDAV SSL, FTPS, túnel SSH. Como podemos ver, se comercio de un software muy completo, que está sobre todo enfocado a nivel empresarial.
Pese a ser un software de suscripción las licencias dependiendo las características que necesitemos parten desde para una pequeña oficina por 70$ hasta para una gran empresa los 20000$, por lo tanto, dependiendo de lo que necesitéis deberéis optar por vuestra atrevimiento más adecuada. Os recomendamos ingresar a la web oficial de CrushFTP donde encontraréis toda la información sobre este servidor FTP de suscripción.
Glftpd
Se comercio de un servidor FTP regalado que es compatible con sistemas operativos Unix, Linux, macOS y BSD. Este servidor FTP destaca por poder tener inicios de sesión restringidos a una determinada dirección IP, disponer de cuotas de transferencia de archivos por usuarios, grupos o uno y otro, aunque no estén en el almacenados en los archivos del sistema, lo que lo hace ideal para servidores privados tipo warez.
Una de las principales diferencias entre muchos otros servidores FTP es que Glftpd tiene su propia almohadilla de datos de usuarios que se puede nutrir completamente en online. Sus principales características son:
Es en gran medida configurable y sus posibilidades son infinitas.
Se ejecuta en el interior de un entorno chroot que lo hace seguro.
Tiene numerosas características que hacen posible muchas configuraciones avanzadas como:
Usuarios y grupos virtuales
Restricción de ufano de pandilla
Relación de carga y descarga
Cálculo en tiempo actual del CRC de archivos que se están cargando
Soporte de script en casi todos los comandos y operaciones
Suministro de usuarios online
sumar usuarios
eliminar usuarios
editar usuarios
Estadísticas visibles
Soporte de enigmático a través de TLS / SSL
Soporte ACL
Verdaderamente este servidor FTP promete ser una opción muy interesante dadas sus opciones y encima al ser regalado merece aún más la pena probarlo. Os recomendamos ingresar a la web oficial de Glftpd donde encontraréis toda la información sobre este servidor FTP de suscripción.
Tal y como habéis gastado, tenemos varios programas para crear servidores FTP y FTPES de modo muy avanzadilla, y todos ellos son gratuitos excepto CrushFTP. Por un flanco, tenemos Proftpd que es un software muy completo y muy recomendable, en caso de que sea demasiado renovador y no necesites tantas opciones, Vsftpd está positivamente perfectamente y es muy sencillo de configurar. Por posterior, Pureftpd además es ampliamente utilizado en sistemas operativos de routers y NAS.
Es muy complicado decantarse por uno u otro software, ya que todos ellos son alternativas muy buenas, con amplias opciones de configuración y que aún se mantienen con actualizaciones periódicas.
La entrada Sabes como Mejores servidores FTP y FTPES para Linux: Características y opciones se publicó primero en El rincon de diego.
Por El rincon de diego
0 notes
Text
Shiny buttons, iconos brillantes y redondeados para tu Plasma #KDE
Hoy toca un entrada ligera ya que vuelven los temas de iconos al blog. Os presento Shiny buttons, una gran colección de iconos brillantes y redondeados para tu escritorio que se sale del estilo actual de iconos minimalistas pero coloridos que florecen por la Store de KDE.
Shiny buttons, iconos brillantes y redondeados para tu escritorio Plasma
Con 36287 iconos para aplicaciones, de la mano del grupo de diseñadores Zma (compuesto por sebastianblonde, jmsoviet, gardmo, pawanyadav y EepSetiawan, si he entendido bien) nos llega otro tema de iconos originales para Plasma 5.
Se trata de Shiny buttons, un enorme pack de iconos para tu escritorio Plasma que le conferirá un aspecto noventero por su aspecto brillante y redondeado, pero con un toque 3D ya que parecen gotas sobre el escritorio. Se puede ver estos detalles en la imagen
Los desarrolladores aseguran que tiene todos los iconos de las aplicaciones de los repositorios de las siguientes distribuciones Debian 9, Debian Sid, Atrix, AntiX, MX Linux, Deepin, Solus, Antergos, Ubuntu 16.04-18.04-18.10-19.04, LinuxMint 18.1-19, Arch, Fedora 27-28-29-30, OpenMandriva Lx 3.0, PCLinuxOS, Rosa 2016.1, OpenSUSE Tumbleweed, OpenSUSE Leap 15.0, Manjaro, Mageia Cauldron, CentOS 7, Astra Linux Orel, Astra Linux 1.6 SE Smolensk, ALT Linux Sisyphus, Slackware 14.2, ARCHLabs, Puias, Scientific, Linux Lite, Chakra, Kaos, Mops, Calculate Linux, Gentoo, EndlessOS, GetDeb-PlayDeb, RPM Sphere, archive.ualinux, Sparkylinux, Bodhi, Backbox, Archstrike, FreeBSD 12-13, Peppermint 9, Kali, Parrot, OpenBSD 6.4, NetBSD, DragonFlyBSD, Red Hat 7.6, GosLinux IC3, Vine Linux, Trident, TrueOS.
No está mal, ¿verdad?
No es el primer tema de este grupo de diseñadores que aparece en el blog, ya que por aquí ya tuvimos Yellow Stickers, Uniform, Not superflat stickers, Gears y White chips, hace casi más de seis meses.
Y como siempre digo, si os gusta el pack de iconos podéis “pagarlo” de muchas formas en la nueva página de KDE Store, que estoy seguro que el desarrollador lo agradecerá: puntúale positivamente, hazle un comentario en la página o realiza una donación. Ayudar al desarrollo del Software Libre también se hace simplemente dando las gracias, ayuda mucho más de lo que os podéis imaginar, recordad la campaña I love Free Software Day 2017 de la Free Software Foundation donde se nos recordaba esta forma tan sencilla de colaborar con el gran proyecto del Software Libre y que en el blog dedicamos un artículo.
Más información: KDE Store
from Shiny buttons, iconos brillantes y redondeados para tu Plasma
0 notes
Text
DragonFlyBSD's Kernel Optimizations Are Paying Off - 3 BSDs & 5 Linux OS Benchmarks On Threadripper
DragonFlyBSD’s Kernel Optimizations Are Paying Off – 3 BSDs & 5 Linux OS Benchmarks On Threadripper
[ad_1]
DragonFlyBSD lead developer Matthew Dillon has been working on a big VM rework in the name of performance and other kernel improvements recently. Here is a look at how those DragonFlyBSD 5.5-DEVELOPMENT improvements are paying off compared to DragonFlyBSD 5.4 as well as FreeBSD 12 and five Linux distribution releases. With Dillon using an AMD Ryzen Threadripper system, we used that too…
View On WordPress
0 notes