#email security service
Explore tagged Tumblr posts
Text
Top 7 Reasons Your Business Needs Email Security Now

In today’s digital-first environment, email is more than just a communication tool—it’s a gateway to your business. While it’s indispensable for daily operations, it’s also one of the most exploited vectors for cyberattacks. From phishing scams to ransomware, threats are increasingly sophisticated and damaging. Without robust email security, your business is vulnerable to data breaches, financial losses, and reputational harm.
If you've been putting off upgrading your email defenses, here are the top 7 reasons why your business needs email security now, before it's too late.
1. Phishing Attacks Are on the Rise
Phishing is no longer a crude scam easily spotted by spelling errors or sketchy links. Modern phishing emails are highly targeted (spear phishing) and often mimic trusted brands, suppliers, or even colleagues. According to Verizon’s Data Breach Investigations Report, over 90% of cyberattacks begin with a phishing email.
These attacks are designed to trick employees into revealing credentials, making payments, or downloading malware. Email security solutions use AI and threat intelligence to detect and block these emails before they reach inboxes, significantly reducing your risk.
Key takeaway: Even tech-savvy employees can fall for well-crafted phishing emails. Email security solutions provide an essential layer of automated defense.
2. Prevent Financial Loss and Business Disruption
Cybercriminals don’t just want data—they want money. Business Email Compromise (BEC) scams, where attackers impersonate executives or vendors to trick employees into transferring funds, cost businesses billions annually.
And it’s not just direct fraud. Malware-laden attachments or malicious links can disrupt operations, lock files through ransomware, and cost thousands (or millions) to resolve. The downtime from a successful attack can cripple small to mid-sized businesses.
A strong email security system not only scans for known threats but also uses behavioral analysis to flag suspicious requests or activities.
Key takeaway: Email-based attacks can cause major financial and operational damage. Proactive security saves money and protects business continuity.
3. Protect Your Brand and Customer Trust
Customers, partners, and suppliers expect your business to keep their data safe. A single compromised email could lead to a data breach that exposes sensitive client information, and once trust is lost, it’s hard to regain.
Imagine a scenario where attackers use your domain to send phishing emails to your customers. This not only harms them but also damages your brand’s credibility. Email security systems with features like DMARC, DKIM, and SPF help prevent spoofing and impersonation by ensuring only verified senders can use your domain.
Key takeaway: Email security protects not just your internal systems, but your external reputation.
4. Ensure Regulatory Compliance
Whether you operate in finance, healthcare, e-commerce, or any industry handling personal data, regulatory compliance is non-negotiable. Regulations such as GDPR, HIPAA, and PCI-DSS require organizations to implement reasonable security measures, including for email communications.
Failing to secure your email systems could result in hefty fines and legal repercussions. Many email security solutions offer compliance features like encryption, data loss prevention (DLP), and audit trails to help you stay aligned with legal requirements.
Key takeaway: Email security helps you meet industry regulations and avoid costly compliance penalties.
5. Support a Remote and Hybrid Workforce
With the rise of remote work, employees are accessing emails from home networks, personal devices, and public Wi-Fi, creating more entry points for attackers. In many cases, the company’s internal firewall offers no protection once the employee is outside the office environment.
Cloud-based email security solutions protect users wherever they are. Whether it’s on a laptop, mobile device, or tablet, emails are scanned in real-time, ensuring threats are blocked before they’re opened.
Key takeaway: Email security needs to follow your workforce, not just your office network.
6. Stop Spam and Boost Productivity
Annoying as it may seem, spam is more than just a nuisance. It clogs inboxes, distracts employees, and can often carry hidden threats. Time wasted sorting through irrelevant or harmful emails adds up, hurting productivity across your organization.
Email security platforms come with robust spam filters that drastically reduce the volume of unwanted messages, allowing your team to focus on what matters. Advanced solutions even adapt over time to recognize evolving spam tactics and adjust filters automatically.
Key takeaway: Cleaner inboxes mean higher efficiency and lower risk.
7. Stay Ahead with Threat Intelligence and AI
Cyber threats are constantly evolving, and yesterday’s defenses won’t stop today’s attacks. Modern email security tools use machine learning, artificial intelligence, and threat intelligence feeds to detect even zero-day exploits and advanced persistent threats (APTs).
These systems learn from global data patterns, flagging suspicious emails even if they haven’t been seen before. The result? Real-time protection that gets smarter over time.
Some platforms also offer dashboards, alerts, and analytics, giving your IT team insights into attack trends and vulnerabilities.
Key takeaway: AI-powered email security is essential for staying ahead of fast-moving cyber threats.
Bonus: Why Built-In Email Filters Aren’t Enough
Many businesses rely solely on built-in filters provided by email services like Microsoft Office 365 or Gmail. While these offer a basic level of protection, they’re not tailored for business-grade security. They often miss advanced threats, lack DLP capabilities, and don’t provide compliance-specific features.
Standalone or integrated third-party email security solutions offer deeper visibility, better threat detection, and comprehensive control. For businesses that can’t afford a breach, upgrading is a smart move.
Key takeaway: Default filters are a start, but not a strategy.
Final Thoughts
Email is at the heart of business communication—and that’s exactly why it’s a prime target for cybercriminals. Ignoring email security is like leaving your front door wide open in a dangerous neighborhood. From financial loss to reputational damage and compliance risks, the consequences of an unsecured email system can be devastating.
Implementing a modern, AI-driven email security solution is one of the smartest and most cost-effective steps you can take to protect your business. Whether you’re a small startup or a growing enterprise, the time to act is now.
#email security#email security solutions#email security service#email encryption#cloud email security#email protection
0 notes
Text

If you get a Mi Band to monitor your Medical Stuff, you need to delete its bullshit unethical app as soon as you get GadgetBridge working.
#i assume that this is a response to regulatory pressure? since i can't see any reason the company itself#would benefit from pressuring users away from secure email services#Xiaomi#mi band#smartwatch
11 notes
·
View notes
Text

#emailmarketing#emails i can't send#email service#email security#emailstrategy#emails from an actor#emails#【咨询顾问:a ben】 qq/微信号:634068167 email:[email protected]#emailcampaigns#email list#email#funny memes#dank memes#tumblr memes#best memes#memes#memedaddy#meme#dankest memes#dank humor#dank memage#telecommunications#communication#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals
56 notes
·
View notes
Text
#polls#poll#daily polls#i love polls#polladay#email#email address#email service#email security#adulting
20 notes
·
View notes
Text
How to Protect Yourself from Personal Loan Phishing Scams

In today’s digital world, personal loans have become more accessible, allowing borrowers to apply online and receive funds quickly. However, this convenience has also led to a rise in phishing scams, where fraudsters attempt to steal your personal and financial information by posing as legitimate lenders. These scams can result in identity theft, financial loss, and fraudulent loan applications in your name.
If you’re planning to apply for a personal loan, it is essential to understand how phishing scams work, the warning signs to look for, and the best ways to protect yourself.
1. What Are Personal Loan Phishing Scams?
A phishing scam is a fraudulent attempt to trick individuals into providing sensitive information such as bank details, Aadhaar number, PAN card, OTPs, or login credentials. Scammers typically impersonate banks, NBFCs, or online lending platforms and contact borrowers via emails, phone calls, SMS, or fake websites.
Once they obtain your information, they can:
Steal money from your bank account
Take a loan in your name
Misuse your identity for financial fraud
Access and sell your personal data on the dark web
2. Common Types of Personal Loan Phishing Scams
2.1 Fake Loan Approval Emails & SMS
Fraudsters send emails or SMS messages claiming that your loan has been pre-approved or that you qualify for a low-interest personal loan. These messages often contain links leading to fake lender websites designed to steal your personal information.
2.2 Fake Loan Websites & Apps
Scammers create websites and mobile apps that look like real financial institutions. They trick users into entering personal and banking details, which are then used for fraudulent activities.
2.3 Fraudulent Customer Service Calls
You may receive a phone call from a scammer pretending to be a bank representative. They claim you must provide your OTP, Aadhaar, PAN, or bank details to complete your loan application. Once you share these details, scammers can withdraw money or take loans in your name.
2.4 Loan Processing Fee Scams
Fraudsters promise quick loan disbursal with no documentation but demand advance processing fees or a loan insurance fee. Once the fee is paid, the scammer disappears, and no loan is disbursed.
2.5 Social Media Loan Scams
Some scammers advertise fake loans on Facebook, Instagram, or WhatsApp and ask potential borrowers to contact them privately. Once engaged, they request confidential details, leading to identity theft.
3. Red Flags to Identify Loan Phishing Scams
3.1 Offers That Sound Too Good to Be True
If you receive an offer promising guaranteed loan approval with no credit check, zero documentation, or extremely low-interest rates, it’s likely a scam.
3.2 Unsolicited Loan Messages
Legitimate lenders do not send random SMS, WhatsApp messages, or emails offering personal loans. Be cautious if you receive messages from unknown numbers or email addresses.
3.3 Fake Loan Websites
Before applying for a loan online, always verify the website’s domain name. Scammers often create fake websites with slightly modified spellings of real lenders to trick borrowers.
3.4 Requests for Upfront Payments
No genuine lender will ask for advance processing fees before loan approval. If a lender insists on upfront payments via UPI, Paytm, or Google Pay, it’s a scam.
3.5 Pressure to Act Immediately
Scammers create urgency by saying things like, "Limited offer – Apply now!" or "Your loan will be canceled if you don’t act fast." A real lender will give you time to review the terms.
3.6 Request for Personal Information Over the Phone
A legitimate bank or NBFC will never ask you for OTPs, passwords, or CVVs over the phone. If someone does, hang up immediately.
4. How to Protect Yourself from Loan Phishing Scams
4.1 Apply for Loans Only from Trusted Lenders
Always apply for a personal loan through registered banks, NBFCs, or reputed online lenders. Here are some safe options:
🔗 IDFC First Bank Personal Loan 🔗 Bajaj Finserv Personal Loan 🔗 Tata Capital Personal Loan 🔗 Axis Finance Personal Loan 🔗 Axis Bank Personal Loan 🔗 InCred Personal Loan
4.2 Verify the Lender’s Website
Check if the website URL starts with "https://" (secure site).
Look for official lender details on the RBI website or lender’s official website.
Avoid websites with poor design, spelling errors, or unusual domain names (e.g., "axisbankloans.xyz" instead of "axisbank.com").
4.3 Never Click on Suspicious Links
Do not click on links in unsolicited emails or messages claiming to be from a bank or NBFC. Instead, visit the official website by typing the URL manually.
4.4 Avoid Sharing Personal Information Online
Scammers may ask for your Aadhaar, PAN, or bank details via email, phone, or WhatsApp. Never share sensitive information with unknown sources.
4.5 Enable Two-Factor Authentication (2FA)
Use 2FA on your banking and email accounts to protect against unauthorized access. This adds an extra layer of security if your password is compromised.
4.6 Check Reviews & Ratings Before Downloading Loan Apps
Before installing a loan app, check:
App permissions (Avoid apps that ask for access to contacts, photos, and messages).
Reviews and ratings on Google Play or App Store.
If the app is registered with an RBI-approved lender.
4.7 Monitor Your Bank & Credit Report Regularly
Check your credit report and bank statements for unauthorized loan applications or suspicious transactions. If you spot any fraudulent activity, report it immediately.
5. What to Do If You Are a Victim of Loan Phishing?
If you have fallen victim to a loan phishing scam, take these steps:
1️⃣ Contact Your Bank Immediately – Report any unauthorized transactions and request to block your account if necessary. 2️⃣ Change Your Passwords – Update your internet banking, email, and loan account passwords immediately. 3️⃣ File a Cyber Crime Complaint – Report the fraud to the Cyber Crime Portal (www.cybercrime.gov.in) or call the National Cyber Crime Helpline (1930). 4️⃣ Report to RBI & Consumer Forum – If you have been tricked into a fake loan scheme, report it to the RBI and National Consumer Helpline (1800-11-4000). 5️⃣ Monitor Your Credit Report – Check for unauthorized loans taken in your name and dispute them with credit bureaus like CIBIL and Experian.
Stay Alert & Borrow Safely
Personal loan phishing scams are on the rise, but you can stay protected by being vigilant. Always verify loan offers, apply only through trusted lenders, and avoid clicking on suspicious links.
For safe and secure personal loan options, apply here: 👉 Compare & Apply for a Personal Loan
By staying cautious and informed, you can protect yourself from loan fraud and ensure a safe borrowing experience.
#nbfc personal loan#bank#loan services#personal loans#fincrif#personal loan#personal laon#loan apps#personal loan online#finance#fincrif india#Personal loan phishing scams#Loan fraud protection#How to avoid loan scams#Safe personal loan application#Phishing scams in personal loans#Fake loan offers#Online loan scams#Fraudulent loan websites#Personal loan safety tips#How to identify loan scams#Signs of a loan scam#Avoiding personal loan fraud#Phishing emails from loan providers#Loan application fraud prevention#How scammers trick loan applicants#Secure loan application process#Fake personal loan SMS and calls#Online loan phishing protection#Tips to protect against loan fraud
5 notes
·
View notes
Note
What site did you use to make your shop/blog?
i used squarespace but i´ve been meaning to switch because i hate how they changed things to be extremely confusing at the backend for the sake of "simplicity" (like calling the E-commerce menue "selling" and putting every tool in the "selling tools" menue
they also still only have a handful of useable ecommerce templates
#they also straight up have shit customer service#i had issues with my domain being blacklisted by security companies and all they did was send me in circles. i talked to one guy who did mo#e than just rattling off the websites help menue and he was allowed to help for one (1) email. like it´s not the fault of people working th#re to be clear it´s them not providing conditions that let their employees be helpful
16 notes
·
View notes
Text
Beware of cyber scams: How hackers tried to scam me - CyberTalk
New Post has been published on https://thedigitalinsider.com/beware-of-cyber-scams-how-hackers-tried-to-scam-me-cybertalk/
Beware of cyber scams: How hackers tried to scam me - CyberTalk


Lari Luoma has over 20 years of experience working in the fields of security and networking. For the last 13 years, he has worked with Check Point Professional Services as a security consultant, helping customers worldwide implement the best-in-class cyber security. He is a subject matter expert in hyper-scalable security solutions.
EXECUTIVE SUMMARY:
Cyber crime is on the rise. People encounter scams in their everyday lives without really understanding they are being scammed. These vexing and vicious scams can arrive in various forms; phishing emails, fraudulent phone calls or text messages. All of them aim to exploit unsuspecting victims for financial gain. Recently, I found myself on the receiving end of one such scam. This led me to reflect on how important it is to actively anticipate the latest cyber threats and to maintain vigilance.
It began with an email notification purporting to be from PayPal. The notification claimed that my account had been charged $600 for McAfee Antivirus software. I was urged to take immediate action. The email instructed me to contact a provided customer service number to resolve the supposed issue. As I scrutinized the email further, alarm bells rang in my mind. The sender’s address raised suspicion— the address was connected to a generic Gmail account, a far cry from the official communication channels one would expect from PayPal.
Despite my skepticism, I decided to call the provided number to investigate. What ensued was a conversation with an individual who claimed to be a customer service representative. However, the person’s demeanor was far from professional. The individual immediately inquired about my location and whether or not I was on my laptop. When I requested a reason and asked why we couldn’t handle the issue over the phone, the person replied that it was because a laptop has a bigger screen, and it would be easier to fill out the form that he was going to send.
Sensing something amiss, I stated that I wasn’t home and didn’t have my laptop with me, to which the caller abruptly hung up. It was a clear indication of foul play; a phishing attempt to obtain sensitive information or compromise my device’s security.
Reflecting on this encounter, I realized just how easily people can be fooled if they think that they are going to lose money. These scammers were very unprofessional and didn’t sound authentic on the phone. Also, using a Gmail address was a big mistake for them. If they had executed on their activities with a bit more sophistication and polish, I might have fallen victim to the scam.
Here are crucial tips to help you and yours avoid falling victim to similar scams. Consider sharing these tips with employees:
1. Verify sender information: Always scrutinize the email sender’s address. Look for any red flags, such as suspicious domain names or generic email providers (like Gmail or Yahoo), especially if they’re being used for “official” communications from reputable organizations.
2. Exercise caution with unsolicited requests: Be wary of unsolicited emails or messages requesting urgent action, especially if the emails or messages involve financial transactions or account verification. Legitimate companies typically don’t request sensitive information via email.
3. Double-check website URLs: Before clicking on any links in emails, hover over them to preview the URL. Verify that they lead to legitimate websites. Make sure that they aren’t phony links to phishing sites that were designed to steal login credentials or personal data.
4. Use two-factor authentication (2FA): Enable 2FA wherever possible, especially for sensitive accounts, like bank accounts or email accounts. This adds an extra layer of security by requiring a secondary verification method, such as a code sent to your phone.
5. Stay informed and educated: Keep abreast of the latest cyber security threats and techniques used by scammers. Organizations like the Federal Trade Commission (FTC) and cyber security blogs, like CyberTalk.org, provide valuable resources and tips for protecting yourself online.
6. Report suspicious activity: If you encounter a potential scam or phishing attempt, report it to the appropriate authorities or the impersonated business. This helps raise awareness and can compel a business to act, thereby preventing others from falling victim to similar schemes.
7. Don’t engage in discussion with scammers: If the email includes a phone number, you shouldn’t call to resolve the alleged issue.
Maintain vigilance regarding any unsolicited messages that you receive. Don’t click on any links and don’t call numbers provided. If an email informs you that a large sum has been debited from your account, consider whether or not the story seems authentic. Check your credit card bills and contact the real customer support numbers for the company that the scammers are purportedly from.
For instance, in the case that I outlined above, I should have researched the real customer support number for McAfee or Paypal and called there, rather than calling the number that was included in the message. Stay savvy and secure.
For more insights from cyber security expert Lari Luoma, click here. To receive clear cyber insights, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#2fa#Accounts#analyses#antivirus#authentication#awareness#Business#Check Point#code#communication#communications#Companies#compromise#credentials#credit card#crime#customer service#cyber#cyber crime#cyber scams#cyber security#cyber security blogs#Cyber Threats#cybersecurity#data#domain names#double#email#employees#Exercise
2 notes
·
View notes
Text
having a most Terrible Day but the sextus pompey-antony fic has successfully taken over some part of my brain. so.
#i cant log into my paypal account bc its attached to an old phone number i dont have anymore and i wanted to update it#BUT I CANT LOG IN BECAUSE IT WONT LET ME USE A DIFFERENT PHONE NUMBER#and their fucking customer service line is AUTOMATED and im SCREAMING and you cant send EMAILS TO THEM#im so upset that im going to have to like. end up sending a DM to their support account on twitter like my god would you just#hire people to answer your customer support line. so that i can get this fixed#what fucking clownery dictates that you cant email me a code and ask my security questions HUH what absolute CLOWN BEHAVIOR
5 notes
·
View notes
Text
Email Marketing Fun Facts
Email Marketing Fun Facts and Bullet Points: 📢 Did you know that email marketing has an ROI of 3800%? That's right, for every $1 spent on email marketing, you can expect an average return of $38! 💰💸 📧 Email marketing is also a great way to build relationships with your customers. By providing valuable content and personalized messaging, you can increase customer loyalty and retention. 🤝💕 📈 Want to increase your email open rates and click-through rates? Try segmenting your email list based on demographics, behavior, and interests. This allows for targeted messaging and higher engagement rates. 🎯👥 👩💻 Did you know that 58% of adults check their email first thing in the morning? That's why it's important to have a strong subject line that grabs their attention and entices them to open your email. 📨👀
🚨 Are you struggling with your email marketing strategy? Don't worry, I've got you covered! Check out my ultimate guide to email marketing for tips, tricks, and best practices to help you succeed. 🙌📩
#email marketing#email list#email campaign#email services#digital marketing#emailmarketing#email security#affiliate marketing#make money with affiliate marketing#work from home#online business#home business#make money online#blogger#marketing#online marketing
3 notes
·
View notes
Text
that's fine for sending schoolwork to yourself but do NOT do this for work documents or things that could be used for identity fraud (scans of birth certificates, whatever identification numbers your country uses, etc.)

#in the case of work docs that can put you at risk of being a leak#in the case of your identification documents i assume most people do NOT secure their emails correctly#yall just want a cloud document service and if ur using gmail google docs is RIGHT THERE#but there's better options for non google cloud storage
15K notes
·
View notes
Text
The Hidden Threats in Your Inbox: How Email Security Can Save Your Business

In today’s digital-first world, email remains one of the most essential communication tools for businesses. Yet, it’s also one of the most exploited channels by cybercriminals. Despite advancements in cybersecurity, email threats are evolving faster than ever, growing in both complexity and frequency. From phishing and malware to business email compromise (BEC), the threats lurking in your inbox could compromise your data, damage your reputation, and cost you millions.
This article explores the hidden dangers of unsecured email and how implementing robust email security solutions can protect your business from serious cyber risks.
The Invisible Battlefield: Why Email Is a Top Target
Emails are the easiest and most direct way for attackers to reach individuals inside your organization. According to recent cybersecurity reports:
Over 90% of cyberattacks begin with a phishing email
Business Email Compromise (BEC) costs businesses more than $1.8 billion annually
Ransomware is often delivered via malicious email attachments or links
These numbers alone should prompt any business to rethink its approach to email security.
Common Email-Based Threats That Go Undetected
Let’s break down the main email threats that may be hiding in your inbox right now:
1. Phishing & Spear Phishing
Phishing emails are fraudulent messages designed to trick recipients into revealing sensitive data like login credentials or financial information. Spear phishing takes this further by targeting specific individuals, often impersonating trusted contacts or executives.
2. Business Email Compromise (BEC)
In BEC attacks, criminals spoof or hack into legitimate business email accounts to request wire transfers or sensitive information. These attacks are hard to detect and often bypass traditional spam filters.
3. Malware & Ransomware Attachments
Emails are a popular vector for spreading malware. A simple click on an attachment can unleash trojans, keyloggers, or ransomware that can lock your entire network.
4. Spoofing & Email Impersonation
Cybercriminals often manipulate email headers to impersonate reputable senders. Without email authentication in place, these forged emails can easily bypass detection.
5. Zero-Day Attacks
Zero-day vulnerabilities are exploited before security teams become aware. Attackers may embed these within emails, making them almost impossible to detect without advanced email security.
Why Traditional Email Filters Aren’t Enough
Basic email filtering systems may catch spam and obvious threats, but they often fall short when it comes to:
Detecting advanced phishing and BEC scams
Identifying malicious URLs and zero-day exploits
Preventing account takeovers and internal threats
Modern attackers use sophisticated methods that evade basic filters. That’s why businesses need advanced, multi-layered email security solutions.
How Email Security Solutions Protect Your Business
1. Advanced Threat Protection
Modern email security systems use AI and machine learning to detect unusual patterns, suspicious behavior, and new threat signatures. This helps block threats before they reach the user’s inbox.
2. Email Authentication (SPF, DKIM, DMARC)
These protocols validate the legitimacy of your outgoing and incoming emails, helping prevent spoofing and impersonation.
3. Real-Time Link and Attachment Scanning
Secure email gateways inspect links and files in real time, sandboxing them to see how they behave before delivering them to the user.
4. Encryption & Data Loss Prevention (DLP)
Email encryption ensures that sensitive communications can’t be read by unauthorized parties. DLP tools prevent employees from accidentally or intentionally sending sensitive data outside the organization.
5. User Awareness & Phishing Simulation
Security tools often include training modules and phishing simulation campaigns to educate users, turning them into the first line of defense.
Benefits Beyond Security
Implementing robust email security does more than just protect you from threats. It brings added benefits that impact your business operations, compliance, and brand trust:
Regulatory Compliance: Stay compliant with GDPR, HIPAA, and local data protection laws in the UAE and beyond.
Business Continuity: Avoid downtime due to email attacks or server issues.
Improved Productivity: Minimize spam, reduce time spent managing threats, and improve email reliability.
Customer Confidence: Demonstrate a strong commitment to cybersecurity, boosting brand reputation.
Choosing the Right Email Security Solution
When selecting an email security provider, look for:
Cloud-Based Protection: Scalable and always up-to-date.
AI-Powered Detection: Essential for identifying evolving threats.
Multi-Layered Defense: Combining filtering, authentication, and monitoring.
Ease of Integration: This should work seamlessly with Microsoft 365, Google Workspace, or your internal servers.
Compliance Ready: Ensure the provider understands local data security laws.
Your Next Steps to Safer Email Communication
Audit Your Current Email Security Posture
Understand what systems are in place and identify gaps.
Implement Email Authentication (SPF, DKIM, DMARC)
These standards are essential for preventing spoofing.
Invest in Advanced Email Security Solutions
Look for solutions that offer AI-based protection, encryption, and threat intelligence.
Train Your Team
Human error is a major cause of breaches. Regular training reduces risks dramatically.
Monitor & Update
Threats evolve—so should your defenses.
Conclusion
Your inbox may look harmless, but beneath the surface, it can be a gateway for cybercriminals to breach your business. The threats are real, sophisticated, and growing. But with the right email security strategy, your organization can stay protected, compliant, and resilient.
Don’t wait until a breach forces your hand. Secure your communication, protect your data, and gain peace of mind — with enterprise-grade email security.
#email security#email security solutions#email security service#email encryption#cloud email security#email protection
0 notes
Text
Reading the new checks that might come in due to the Online Safety Act in the UK and this is actually bullshit
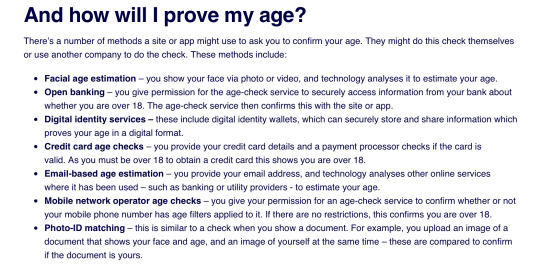
[Image Transcript:
And how will I prove my age?
There’s a number of methods a site or app might use to ask you to confirm your age. They might do this check themselves or use another company to do the check. These methods include:
Facial age estimation – you show your face via photo or video, and technology analyses it to estimate your age.
Open banking – you give permission for the age-check service to securely access information from your bank about whether you are over 18. The age-check service then confirms this with the site or app.
Digital identity services – these include digital identity wallets, which can securely store and share information which proves your age in a digital format.
Credit card age checks – you provide your credit card details and a payment processor checks if the card is valid. As you must be over 18 to obtain a credit card this shows you are over 18.
Email-based age estimation – you provide your email address, and technology analyses other online services where it has been used – such as banking or utility providers - to estimate your age.
Mobile network operator age checks – you give your permission for an age-check service to confirm whether or not your mobile phone number has age filters applied to it. If there are no restrictions, this confirms you are over 18.
Photo-ID matching – this is similar to a check when you show a document. For example, you upload an image of a document that shows your face and age, and an image of yourself at the same time – these are compared to confirm if the document is yours.
End Transcript.]
Not only is this such a fucking breach of privacy, but this is going to hurt adults in vulnerable and abusive situations. Some adults don’t have bank accounts or credit cards or even a fucking phone. I’m one of them. I could not give half of this information even if I wanted to. What the fuck is this. Fuck the UK government. This isn’t going to protect kids, this is just going to hurt adults, and I know full well when they say “sites that allow pornography” they’re going to be going after sites that have huge amounts of queer content, like tumblr and Ao3. Queer kids are gonna lose their fucking communities because of this shit. Abuse victims are going to lose online support systems because of this.
I’m genuinely fucked off about this, and worried about whether I’m going to lose every single one of my online friends. Anyone in the UK, please email your MP and sign this petition. It needs to reach 100k signatures to pass through Parliament.
I’m only hoping the backlash will be big enough for them to stop implementing these measures.
28K notes
·
View notes
Text
Essential IT Services and Cybersecurity Trends for UK Businesses in 2025
The digital landscape for UK businesses continues to evolve at breakneck speed in 2025. From ransomware threats to Microsoft’s latest AI integrations, staying ahead requires more than just awareness—it demands action. If you’re a small or mid-sized business leader navigating managed IT services, cybersecurity, or cloud computing, this blog is your guide to the latest trends and essential…

View On WordPress
#acronis#adware#chief information security officer#civica#cloud computing#copilot microsoft#croydon government#dpo#intune#it services#little fish#little little fish#littlefish#m365 copilot#malware#managed#managed it services#microsoft 365 copilot#microsoft co pilot#microsoft intune#microsoft microsoft dynamics#not receiving emails#pen test#pen testing#penetration hacking#penetration testing#ransomware#raven housing trust#raven trust redhill#rpa
1 note
·
View note
Text
Empowering of kuthuparamb rural bank
The Kuthuparamba Rural Bank also actively promotes financial literacy, helping citizens understand the importance of saving, insurance, and responsible borrowing. With customer-friendly staff, transparent services, and a strong local presence, the bank continues to win the trust of the community.
As rural India continues to evolve, institutions like Kuthuparamba Rural Bank are essential in building a self-reliant and financially strong society. Through dedication, innovation, and grassroots connection, the bank is more than just a financial institution—it is a partner in progressWhy kuthuparamb rural bank
Why kuthuparamba rural bank?
Kuthuparamba Rural Bank is the backbone of financial support for the people of Kuthuparamba and surrounding areas. Here's why it stands out
Our services
#1 Savings & Deposit Accounts#3 Mobile & Digital Banking#4 Payment & Transfer Service#5. Support for Rural Livelihood & Committees#6Branch & Customer Services#Conclusion :Kuthuparamba Rural Bank stands as a pillar of trust#service#and empowerment in the local community. By offering accessible financial services#supporting agriculture and small businesses#and promoting financial literacy#the bank plays a vital role in the overall development of rural Kuthuparamba. Its commitment to transparency#innovation#and customer care makes it more than just a bank—it is a partner in progress for thousands of individuals and families. As the region conti#Kuthuparamba Rural Bank remains dedicated to building a stronger#self-reliant#and financially secure rural society.#Contact Us;Head Office#Kuthuparamba Co-operative Rural Bank Ltd.#Kuthuparamba P.O.#Kannur District#Kerala – 670643#📧 Email: [email protected]#🌐 Website: www.kuthuparamba
0 notes
Text
Reagan.com - An Email Service that Doesn’t Live Up to Its Namesake
Reagan.com – An Email Service that Doesn’t Live Up to Its Namesake When I found out that Google scanned my emails, I wanted to find a service that would protect my political speech and communications. At that time, I found one that was promising to be just that. Reagan.com promised to Recapture Your Privacy Join in the movement to suppress Surveillance Capitalism. Take back your personal…
#customer support#email service#no customer support#Privacy#private email service#reagan.com#secure email#Spam
0 notes
Text
Reagan.com - An Email Service that Doesn’t Live Up to Its Namesake
Reagan.com – An Email Service that Doesn’t Live Up to Its Namesake When I found out that Google scanned my emails, I wanted to find a service that would protect my political speech and communications. At that time, I found one that was promising to be just that. Reagan.com promised to Recapture Your Privacy Join in the movement to suppress Surveillance Capitalism. Take back your personal…
#customer support#email service#no customer support#Privacy#private email service#reagan.com#secure email#Spam
0 notes