#gmail password hack 2016
Explore tagged Tumblr posts
Text
Why are Phishing Attacks Successful?
It seems you can hardly go a day without hearing about another data breach, money transfer scam, or some other crime that started out as a spear phishing attack. Let’s talk about phishing attacks and why they are successful.

The Success of Phishing Attacks
More than 90% of data breaches and successful hacks start with a phishing attack. The scale varies and is often used to get sensitive information from you. Once you reveal the information or carry out a specific action, you won’t always know straight away that it was a scam until it’s too late and the consequences can be severe.
Users are the weakest link
Most users aren’t trained to recognise phishing attempts, and so often fall prey to attack by clicking on links or opening attachments in emails without considering the potential repercussions.
According to the research, 52% of users receive training no more than twice per year, and 6% of users have never received security awareness training.
The result? IT departments are not at all confident in their users’ ability to recognise incoming threats, or in their organisation’s ability to stop phishing and related attacks.

The law of attention
Beyond this, remember that everyone can fall victim to a scam. You can reduce your risk, but you can’t eliminate it. Even security professionals with years of experience make mistakes. All scams rely on flaws inherent in human nature. While many think they’re “too smart” to fall victim to scams, intelligence doesn’t play as much a role as you may think.
What’s the Password?
Phishing attacks which target specific services are on the up. For example, a Gmail phishing scam targeted nearly 1 billion users in 2017 and phishing campaigns targeting Dropbox have the highest click-through rate, at 13.6%. Campaigns like this are often intended to steal the users credentials to reuse in other attacks, or take control of said service. This could then result in a higher success rate in future campaigns, or even blackmail.
Criminals are (unsurprisingly) following the money
The use and notoriety of the Dark Web have lowered the commercial value of stolen data. The price of a payment card record dropped from $25 in 2011 to $6 in 2016, meaning that cyber criminals have had to adapt their focus to new ways of earning the kind of money they did in the past.
Consequently, the fruitful nature of information-holders is the area they're now turning to. Attacks such as ransomware, where information-holders are afraid of losing their data, means that victims wouldn’t think twice before paying the demands of the criminal.

Final Words
Phishing is still a huge threat to organizations and individuals. With the right phishing protection service, you’ll get better security and peace of mind when checking emails and browsing a website.
Sources:
https://www.itgovernance.co.uk/blog/6-reasons-phishing-is-so-popular-and-so-successful
https://www.msspalert.com/cybersecurity-guests/why-phishing-attacks-are-successful/
https://blog.getusecure.com/post/the-real-reason-why-phishing-attacks-are-so-successful
https://www.eset.com/uk/about/newsroom/blog/5-reasons-phishing-is-so-successful/
1 note
·
View note
Text
Facebook Hacker V1.8
Facebook Hacker Software V1 8 Free Download. Chas of clan hack download. It is 100 Working. The first thing you should find out about the hacks you want to use is the compatible device for its download and installation.Download Clash Of Clans Hack Version Apk. Pokemon Battle Ultimate Download (Working 100%) Pokemon Battle Ultimate is a GBA ROM. Facebook Hacker V1.9 Free Download Cnet - DOWNLOAD (Mirror #1). Download and install the Facebook Account Hacker Software for windows XP, windows vista, windows 7, windows 8, windows 8.1, and Windows 10 both 32/64 bit OS. Keep getting access to your desired person account through this single software, which is entirely free and has no cost for installation.
Every day, countless Facebook accounts get hacked.Ever asked yourself how they do it? How to hack Facebook successfully? As youall know facebook is the most famous social networking site in the world. Thisposition has encouraged hackers to always try to find security flaws inFacebook's system. Thanks to these flaws, hackers are able to hack anyFacebook account. You can easily hack facebook accounts too by using our web-based hacking application. It's simple! No download orinstall required. All you have to do is to simply input victim's profile URLaddress and click 'Hack Account'. A lot of hacking requests are automaticallyprocessed by our web-based application. The success rate (getting theaccount's password) is an outstanding 98%. The average time of the hackingprocess is 3 minutes.
Sep 06, 2016 Download Facebook Hacker for free. Does what it says on the tin. This is used to 'reclaim lost passwords'. It works as long as the person's password you are trying to get is from a gmail account. Facebook Password Hacking software, free download - Password Cracker, SterJo Facebook Password Finder, 2 Password, and many more programs. Facebook Password Hacker free download - Facebook Password Recovery Master, Wifi Hacker, SterJo Facebook Password Finder, and many more programs.
Why do people hack Facebook accounts?
There are many reasons to hack Facebook accounts. Some of these reasons are:
Lost Password Recovery
Cheating Partner
Monitoring Children's Activities
Spying on your crush
Investigation Purposes

Facebook Hacking Software V1 8 Free Download 2018 With Full Crack
Facebook Hacker V1.8

Facebook Hacker V1.8 Activation Key
How to start hacking Facebook accounts?
Facebook Hacking Software V1 8 free. download full
We've made it easy for you. Our web-based application takes care of everything. You only have to input the victim's profile link. Then click on 'Hack Account'. All you have to do now is to wait. Waiting time depends on password complexity but it will maximum takes 5 minutes to retrieve and decrypt the password from Facebook's database. Once successfully hacked, you will see a message saying that. Finally, click on 'HACK UP' to download the dashboard Facebook profil account. To prevent abuse, you might be asked to complete a short survey in order to verify that you're a human (not a bot).
Facebook Hacking Software V1 8 Free Download For Pc
Facebook Hacker V1.9

Facebook Hacker V1.9 Download

Facebook Hacker V1.8 Download
0 notes
Text
The dangers of spam SMS
Ahmed Mansour knew immediately that something was wrong with the unsolicited text messages on his iPhone. It was August 2016, the hottest time of the year in the United Arab Emirates (UAE), and as a renowned advocate for human rights, Mansour was already familiar with government surveillance techniques. According to The Guardian newspaper, his activities inside and outside the country had already been monitored for some time.
But the two anonymous text messages were something new. They contained links to information that would help him in his human rights activities. Mansour was suspicious by nature of his work and forwarded the messages to cybersecurity analysts for investigation.
The danger of spam Most computer users receive a fair amount of unsolicited email offering anything from access to African bank accounts to the latest inside information on something of great interest to the reader. Often the spam emails contain links to websites (often malicious websites) or attached files to download. They usually claim to improve the recipient's financial situation or professional life. However, the attached files or the links result in malware being introduced to the computer.
Many of these emails are "phishing," designed to trick innocent people into taking the bait. Spear phishing are attacks on people using real personal information. Cybercriminals provide the bait in these emails with details that are of interest to the targeted person.
Spam SMS Meanwhile, cybercriminals have expanded their phishing networks to include SMS messages. Partly due to security breaches of customer files containing contact information for millions of users around the world, hackers have been able to successfully write software that sends "bait SMS messages."
When consumers click on the links in the spam SMS messages, they download malware to their devices or are redirected to malicious websites. In some cases, users responded to the SMS, so the sender knew the mobile number was in use and vulnerable. Cybercriminals then use phone calls after the original SMS to defraud cell phone owners.
Getting to the root of the hacking In the case of Mansour, a human rights activist, cybersecurity analysts determined that when he clicked on the links in the SMS messages, he would have relinquished control of his iPhone to the hackers. According to The Guardian newspaper, the privately assembled and sophisticated software "would have allowed attackers to spy on virtually all of Mansour's activities - phone calls, text messages, Gmail, Skype and Facebook - as well as scan his calendar and steal passwords and other personal information."
Dealing with spam SMS Some spam SMS messages are very sophisticated and appear to come from banks, phone providers or other reputable companies. If SMS messages look official, call the authentic customer service number for the company to verify the real-time of the SMS. Do not call the phone number listed in the SMS. It's also a good idea to block the phone number from future SMs so they can't be answered.
Forward spam text messages to the Federal Communications Commission (FCC) and the Federal Trade Commission (FTC). These agencies investigate communications that could be considered illegal, and the state government wants to know about any unwanted text messages you receive. Also, report the text messages to your phone provider as spam.
Apps like Mr Number, SMS Blocker, and Text Blocker offer protection from unwanted SMS messages, as does a high-quality security solution like Total Solution from Kaspersky. This software protects the core of Android and iOS mobile devices, so hackers can't take control of tablets and phones. In most cases, this can detect and remove malware that tries to infiltrate devices via spam message links.
Spam SMS messages phishing for gullible victims are still relatively new, but they are bound to become more and more common. With the right knowledge and protection, you will be well prepared.
0 notes
Photo

Mastodon: A Federated Answer to Social Media Centralization
In this article, I’ll introduce Mastodon, a social media platform founded in the spirit of a decentralized Internet. A decentralized web has plenty of challenges and is not necessarily for the faint-hearted, but there are good reasons to persevere.
On July 15, 2020, one of the biggest scams in Twitter’s history happened. Through intelligent social engineering, a group of people managed to gain access to Twitter’s administrative tools, allowing them to post tweets directly from several high-profile accounts.
More than 130 influential Twitter accounts were hacked. In a matter of minutes, the profiles of Apple, Bill Gates, Elon Musk, and others asked individuals to send Bitcoin to a cryptocurrency wallet, with the promise that the money sent would be doubled and returned as a charitable gesture.
Within minutes of the initial tweets, more than 300 transactions had already taken place — to a value of over US$180,000 — before Twitter took the scam messages down.
With a centralized structure in place, only a single person with administrative rights needed to be tricked into giving out access to these high-profile accounts. In similar circumstances, someone with a more sinister motive might aim at a stock market crash, fabricated political tension, or even global unrest.
The Pros and Cons of Centralization
Centralization is a double-edged sword. Its core idea is based on the storage, ownership, and protection of your data by a social media platform. While this sounds awful, there are benefits. The first and strongest advantage of centralized platforms is their ease of use. For example, when you forget your password or your account gets hacked, platforms with a centralized structure can recover them with ease, since they store all of your data on their servers.
But this sense of protection comes at a price. Your data — like tweets, retweets, likes, and shares — are stored and owned by a corporation. These companies have yearly financial KPIs, and your data is a great way for them to generate money, primarily when used for targeted advertisements. Another downside to such platforms is that they’re not open source, meaning there’s no transparency between the users and the platform they’re on. As a user, you have no idea what’s happening under the hood or how your data is being handled.
So what if there was a platform with a decentralized structure, where you owned what you posted and you could see what your data was being used for? For a long time, people have tried to create such platforms — App.net, Peach, Diaspora and Ello are a few of the better-known examples.
But the latest pioneer in decentralized social media comes with all of the benefits listed above.
Enter Mastodon
Mastodon was released in 2016. In the eyes of many, this network is the first step in social media decentralization. While similar to Twitter in both appearance and features, Mastodon focuses on the safety and privacy of its user base by being decentralized and federated. All of its data are distributed across a vast number of independent servers, known as “instances”. Each instance has its own terms of service, code of conduct, and moderation policies while working seamlessly together with other servers as a federating network.
The founder of Mastodon, Eugen Rochko, explains that the platform works very similarly to email. Email users can easily connect, even if one person uses Gmail and the other uses Outlook. The same applies to Mastodon and its instances. While users have the freedom to interact with a vast number of instances, each instance can also block content from other servers with policies or content they’re against, without losing access to the entire Mastodon network.
Getting Started with Mastodon
Getting started with Mastodon is not as easy as joining Facebook or Twitter. Since the platform is a federated service, very similar to email, Mastodon lets you sign up to many sites that run the Mastodon client, similar to how you create an email account on services like Gmail, Hotmail or Protonmail.
Continue reading Mastodon: A Federated Answer to Social Media Centralization on SitePoint.
by Alexander Traykov via SitePoint https://ift.tt/31AaIEw
0 notes
Text
Iran- and China-backed phishers try to hook the Trump and Biden campaigns

State-backed hackers from Iran and China recently targeted the presidential campaigns of Republican President Donald Trump and Democrat Joe Biden, a Google threat analyst said on Thursday.
The revelation is the latest evidence of foreign governments attempting to gain intelligence on US politicians and potentially disrupt or meddle in their election campaigns. An Iran-backed group targeted the Trump campaign and China-backed attackers targeted the Biden campaign, said Shane Huntley, the head of Google’s Threat Analysis Group on Twitter. Both groups used phishing emails. There’s no indication that either attack campaign succeeded.
Kittens and Pandas
Huntley identified the Iranian group that targeted Trump’s campaign as APT35, short for Advanced Persistent Threat 35. Also known as Charming Kitten, iKittens, and Phosphorous, the group was caught targeting an unnamed presidential campaign before, Microsoft said last October. In that campaign, Phosphorous members attempted to access email accounts campaign staff received through Microsoft cloud services. Microsoft said that the attackers worked relentlessly to gather information that could be used to activate password resets and other account-recovery services Microsoft provides.
The Chinese group known as APT31, meanwhile, targeted the Biden campaign, Huntley said. The group, which security researchers also call Hurricane Panda, Black Vine, and Zirconium, “is a highly advanced adversary” that in 2014 exploited a zeroday vulnerability in Microsoft Windows, researchers from security firm CrowdStrike said at the time.
Google responds
Huntley said that Google officials sent the campaigns the company’s standard warning that they were targeted by nation-based hacking. The company began the practice in 2012. To protect its sources and methods, Google doesn’t send the notifications immediately and then dispatches them in large batches. Google also referred the matter to law enforcement.
In a statement, a Google spokesman wrote:
We can confirm that our Threat Analysis Group recently saw phishing attempts from a Chinese group targeting the personal email accounts of Biden campaign staff and an Iranian group targeting the personal email accounts of Trump campaign staff. We didn’t see evidence that these attempts were successful. We sent the targeted users our standard government-backed attack warning and we referred this information to federal law enforcement. We encourage campaign staff to use extra protection for their work and personal emails, and we offer security resources such as our Advanced Protection Program and free security keys for qualifying campaigns.
Hacking political parties and campaigns has been a chief concern ever since two Russian hacking groups were caught breaking into the network of the Democratic National Committee in 2016, just ahead of the presidential campaign. The breaches were largely achieved using phishing emails that tricked staff members into entering their passwords into attacker-controlled sites.
Multiple US intelligence agencies later concluded that Russia engaged in a sustained hacking and disinformation campaign with the goal of disrupting the US democratic process and to boost then-candidate Trump chances of winning the election.
Google provides the above-mentioned Advanced Protection Program, a service that’s designed to protect politicians, elections workers, journalists, and other people who are frequently targeted by hackers. The program requires a physical security key to be used as a second factor when logging into Gmail and other Google services from new devices. APP would have very likely thwarted the 2016 phishing attacks since the mere stealing of passwords is insufficient to gain unauthorized access.
Source link
قالب وردپرس
from World Wide News https://ift.tt/3cttcc0
0 notes
Text
#1yrago Plaintext passwords galore in huge AdultFriendFinder hack
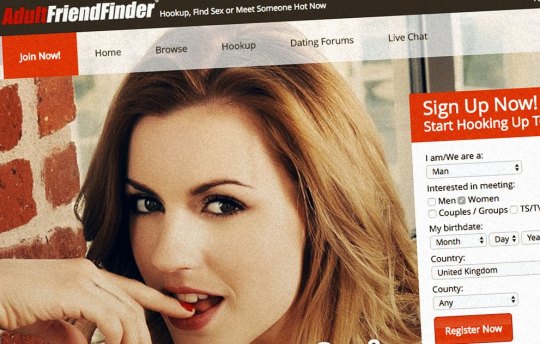
AdultFriendFinder was hacked (again) in October 2016. According to LeakedSource, which acquired a copy of the dataset, this amounts to more than 400m accounts, many with plaintext passwords, from AdultFriendFinder and associated websites.
The site was compromised with a local file inclusion exploit, which means the website's code allowed access to files on the server that aren't supposed to be public.
Nearly a million accounts have the password "123456". More than 100,000 have the password "password".
The non-plaintext passwords were easily cracked anyway, apparently due to some roll-your-own encryption that involved lowercasing everything, SHA1ing it and going back to bed. The longest passwords were "pussy.passwordLimitExceeded:07/1" and "gladiatoreetjaimelesexetjaimefum", with a Blackadder fan in #3 with "antidisestablishmentarianism" and a sybarite who reads XKCD in #4 with "pussypussymoneymoneyweedweed."
Hotmail was the most common email provider, followed by Yahoo and gmail. These three accounted for the vast majority of registered addresses, with AOL and Live an order of magnitude down.
Leaked Source isn't making the data set publicly available; but if they have it, others might too.
https://boingboing.net/2016/11/13/plaintext-passwords-galore-in.html
4 notes
·
View notes
Text
A US House candidate says she was hacked — now she’s warning others
“I cannot think of a reason not to share this with the public,” Brianna Wu tweeted.
“Two of my non-campaign Google accounts were compromised by someone in Russia,” she said.
Wu isn’t just any other target. As a Democratic candidate for the U.S. House of Representatives in Massachusetts’ 8th District, she has a larger target on her back for hackers than the average constituent. And as a former software engineer, she knows all too well the cybersecurity risks that come along with running for political office.
But the breach of two of her non-campaign Google accounts was still a wake-up call.
Wu said she recently discovered that the two accounts had been breached. One of the accounts was connected to her Nest camera system at home, and the other was her Gmail account she used during the Gamergate controversy, during which Wu was a frequent target of vitriol and death threats. TechCrunch agreed to keep the details of the breach off the record as to not give any potential attackers an advantage. Attribution in cyberattacks, however, can be notoriously difficult because hackers can mask their tracks using proxies and other anonymity tools.
“I don’t believe anyone in Russia is targeting me specifically. I think it’s more likely they target everyone running for office,” she tweeted.
Wu said that both of her accounts had “solid protection measures” in place, including “unique, randomly generated passwords for both accounts.” She said that she reported the intrusions to the FBI.
“The worry is obviously that it could hurt the campaign,” she told TechCrunch. But she remains concerned that it could be an “active measure,” a term often used to describe Russian-led political interference in U.S. politics.
Politicians and political candidates are frequently targeted by hackers both in the U.S. and overseas. During the 2016 presidential election, Democratic candidate Hillary Clinton’s campaign manager John Podesta had his personal email account hacked and thousands of emails published by WikiLeaks. The recently released report by Special Counsel Robert Mueller blamed hackers working for Russian intelligence for the intrusion as part of a wider effort to discredit then-candidate Clinton and get President Trump elected.
Yet to this day, political campaigns remain largely responsible for their own cybersecurity.
“There is only so much the feds can do here, given the sheer size of the candidate pool for federal office,” said Joseph Lorenzo Hall, an election security expert and senior vice president at the Internet Society.
Hall said much of the federal government’s efforts have been on raising awareness and on “low-hanging fruit,” like enabling two-factor authentication. Homeland Security continues to brief both parties to the major cybersecurity threats ahead of voting later in November, and the FBI has online resources for political campaigns.
It’s only been in the past few months that tech companies have been allowed to step in to help.
Watchdog says DHS still hasn’t got a 2020 election security plan
Fearing a repeat of 2016, the Federal Elections Commission last year relaxed the rules to allow federal political campaigns to receive discounted cybersecurity help. That has also allowed companies like Cloudflare to enter the political campaign space, offering cybersecurity services to campaigns — which was previously considered a campaign finance violation.
It’s not a catch-all fix. A patchwork of laws and rules across the U.S. make it difficult for campaigns to prioritize internal cybersecurity efforts. It’s illegal in Maryland, for example, to use campaign finances for securing the personal accounts of candidates and their staff — the same kind of accounts that hackers used to break into Podesta’s email account in 2016. It’s an attack that remains in hackers’ arsenals. Just last year, Microsoft found Iranian-backed hackers were targeting personal email accounts “associated” with a 2020 presidential candidate — which later transpired to be President Trump’s campaign.
Both of the major U.S. political parties have made efforts to bolster cybersecurity at the campaign level. The Democrats recently updated their security checklist for campaigns and published recommendations for countering disinformation, and the Republicans have put on training sessions to better educate campaign officials.
But Wu said that the Democrats could do more to support campaign cybersecurity, and that she was speaking out to implore others who are running for Congress to do more to bolster their campaign’s cybersecurity.
“There is absolutely no culture of information security within the Democratic Party that I have seen,” said Wu. Fundraising lists are “freely swapped in unencrypted states,” she said, giving an example.
“There is generally not a culture of updating software or performing security audits,” she said. “The fact that this is not taken seriously is really underscored by Iowa and the Shadow debacle,” she said, referring to the Iowa caucus last week, in which a result-reporting app failed to work. It was later reported that the app, built by Shadow Inc., had several security flaws that made it vulnerable to hacking.
Spokespeople for the FBI and the Democratic Congressional Campaign Committee did not respond to a request for comment prior to publication.
“Infosec is expensive, and I know for many campaigns it may seem like a low priority,” Wu told TechCrunch.
“But how can we lead the country on cybersecurity issues if we don’t hold ourselves to the same standards we’re asking the American people to follow?” she said.
0 notes
Photo

New Post has been published on https://magzoso.com/tech/more-than-150000-u-s-small-business-websites-could-be-infected-with-malware-at-any-given-moment-heres-how-to-protect-yours/
More Than 150,000 U.S. Small-Business Websites Could Be Infected With Malware at Any Given Moment. Here's How to Protect Yours.


Small-business victims were involved in 43 percent of data breaches over the course of a year, according to a recent report.
December 27, 2019 9 min read
It was March 2, 2016, and Melissa Marchand’s day on Cape Cod started out like any other. She drove to her job at Hyannis Whale Watcher Cruises in her mid-size sedan, picked up a latte with 1 percent milk at her local coffee shop and sat down at her desk to check her email. Then, Marchand got the call no website manager ever wants to receive: The site was down, and no one knew how to fix it.
After she dialed up the web hosting provider, the news went from bad to worse: Whales.net had been hacked and, to her horror, all visitors were being redirected to porn sites. Google had even flagged the company’s search results, warning potential customers that the site may be hacked.
“It was a total nightmare — I had no idea that something like this could happen,” Marchand said in an interview with Entrepreneur. “I’d say 75 to 80 percent of our bookings are done online, so when our site is down, we’re just dead in the water.”
At the provider’s suggestion, Marchand called SiteLock, a website security company, and granted its representatives site access. SiteLock discovered the hackers had exploited a security hole in a WordPress plugin, which gave them the access they needed to redirect visitors to racy websites.
By the end of the work day, Marchand sat in her car in her gym’s parking lot, speaking on the phone with a SiteLock representative to review the plan of action. She finally felt like things were going to be OK.
Within three days, Whales.net was back up and running, though it took another three weeks for Google to remove the blacklist warning from the company’s search results.
The hack hit about a month before the whale-watching season began in mid-April, and though it wasn’t peak season, the company still missed out on pre-booking tour groups from schools and camps. Marchand estimated the attack lost the company about 10 percent of its March and April business.
A risk for small businesses everywhere
Small-business owners were victims in 43 percent of data breaches tracked between Nov. 1, 2017, and Oct. 31, 2018, according to a 2019 Verizon report. The report tracked security incidents across all industries, but the most vulnerable sectors this year were retail, accommodation and healthcare.
What does the issue look like on a national scale? If we take the sample size of infected sites SiteLock said they found in 2018 — approximately 47,244 out of 6,056,969 checked — and apply that percentage to the country’s estimated 30.2 million small-businesses websites, minus the estimated 36 percent that don’t have one, then we can loosely estimate the amount of infected small-business websites to be around 150,757.
As a small-business owner, you may not believe anyone would target your website, but that’s just it — bad actors are likely not seeking out your site specifically, said Mark Risher, head of account security at Google.
“Sometimes, we talk about the distinction between targets of choice and targets of chance,” Risher said. “Targets of chance is when the attacker is just trying anything — they’re walking through the parking lot seeing if any of the car doors unlocked. Target of choice is when they’ve zeroed in on that one shiny, flashy car, and that’s the one they want to break into — and they’ll try the windows, the doors … the moon roof. I think for small businesses, there’s this temptation to assume, ‘No one would ever choose me; therefore I’ll just kind of skate by anonymously.’ But the problem is they’re not factoring in the degree of automation that attackers are using.”
Even the least-trafficked websites still average 62 attacks per day, according to SiteLock research. “These cybercriminals are really running businesses now,” said Neill Feather, president of the company. “With the increasing ease of automation of attacks, it’s just as lucrative to compromise a 1,000 small websites as it is to invest your time and try to compromise one large one.”
John Loveland, a cybersecurity head at Verizon and one of the data breach report’s authors, said that since the report was first published 12 years ago, he’s seen a definite uptick in attacks at small and medium-sized businesses. As malware, phishing and other attacks have become “more commoditized and more readily accessible to lesser-skilled hackers,” he said, “you see the aperture open … for types of targets that could be valuable.”
So what are the hackers getting out of the deal? It’s not just about potentially lucrative customer information and transaction histories. There’s also the opportunity to weaponize your website’s reputation. By hosting malware on a formerly trustworthy website, a hacker can increase an attack’s spread — and amplify the consequences — by boosting the malware’s search engine optimization (SEO). They can infect site visitors who search for the site organically or who access it via links from newsletters, articles or other businesses, Risher said.
Even if you outsource aspects of your business — say, time and expense reporting, human resources, customer data storage or financial transactions — there’s still no guarantee that that information is safe when your own website is compromised. Loveland said he saw an uptick in email phishing specifically designed to capture user credentials for web-based email accounts, online CRM tools and other platforms — and reports of credential compromise have increased 280 percent since 2016, according to an annual survey from software company Proofpoint.
How to protect yourself and your customers
How can small-business owners protect themselves — and their customers? Since a great deal of cyberattacks can be attributed to automation, putting basic protections in place against phishing, malware and more can help your site stay off the path of least resistance.
Here are five ways to boost your small-business’s cybersecurity.
1. Use a password manager.
There’s an exhaustive amount of password advice floating around in the ether, but the most important is this, Risher said: Don’t reuse the same password on multiple sites. It’s a difficult rule to stick to for convenience’s sake — especially since 86 percent of internet users report keeping track of their passwords via memorization — but cybersecurity experts recommend password managers as efficient and secure workarounds. Free password manager options include LastPass, Myki and LogMeOnce.
2. Set up email account recovery methods to protect against phishing attacks.
Phishing attacks are an enduring cybersecurity problem for large and small businesses alike: 83 percent of respondents to Proofpoint’s annual phishing survey reported experiencing phishing attacks in 2018, an increase from 76 percent the year before. Embracing a more cyber-aware culture — including staying vigilant about identifying potential phishing attacks, suspicious links and bogus senders — is key to email safety.
If you’re a Gmail user, recent company research suggests that adding a recovery phone number to your account could block up to 100 percent of cyberattacks from automated bots, 99 percent of bulk phishing attacks and 66 percent of targeted attacks. It’s helpful because in the event of an unknown or suspicious sign-in, your phone will receive either an SMS code or an on-device prompt for verification. Without a recovery phone number, Google will rely on weaker challenges such as recalling last sign-in location — and while that still stops most automated attacks, effectiveness against phishing drops to 10 percent.
3. Back up your data to protect against ransomware.
Ransomware — a cyberattack in which a hacker holds your computer access and/or data for ransom — has kicked off a “frenzy of cybercrime-related activities focused on small and medium businesses,” Loveland said. In fact, it’s the second leading malware action variety in 2019, according to the Verizon report, and accounted for 24 percent of security incidents. Hackers generally view it as a potentially low-risk, high-reward option, so it’s important to have protections in place for such an attack — namely, have your data backed up in its entirety so that you aren’t at the hacker’s mercy. Tools such as Google Drive and Dropbox can help, as well as automatic backup programs such as Code42 (all charge a monthly fee). You can also purchase a high-storage external hard drive to back everything up yourself.
4. Enlist a dedicated DNS security tool to block suspicious sites.
Since computers can only communicate using numbers, the Domain Name System (DNS) is part of the internet’s foundation in that it acts as a “translator” between a domain name you enter and a resulting IP address. DNS wasn’t originally designed with top-level security in mind, so using a DNSSEC (DNS Security Extension) can help protect against suspicious websites and redirects resulting from malware, phishing attacks and more. The tools verify the validity of a site multiple times during your domain lookup process. And though internet service providers generally provide some level of DNS security, experts say using a dedicated DNSSEC tool is more effective — and free options include OpenDNS and Quad9 DNS. “[It’s] a low-cost, no-brainer move that can prevent folks from going to bad IP addresses,” Loveland said.
5. Consider signing up with a website security company.
Paying a monthly subscription to a website security company may not be ideal, but it could end up paying for itself in terms of lost business due to a site hack. Decreasing attack vulnerability means installing security patches and updates for all of your online tools as promptly as possible, which can be tough for a small-business owner’s schedule.
“It’s tempting for a small-business owner to say, ‘I’m pretty handy — I can do this myself,’” Risher said. “But the reality is that even if you’re very technical, you might not be working around the clock, and … you’re taking on 24/7 maintenance and monitoring. It’s certainly money well spent to have a large organization doing this for you.”
0 notes
Text
Daily Beast: Russian hackers targeted Democrat facing tough 2018 election
https://uniteddemocrats.net/?p=6885
Daily Beast: Russian hackers targeted Democrat facing tough 2018 election


Enlarge / Sen. Claire McCaskill (D-MO) questions witnesses during a Senate Committee on Homeland Security and Governmental Affairs hearing concerning threats to the homeland, September 27, 2017 in Washington, DC.
Drew Angerer/Getty Images
The digital ink was barely dry on Ars IT and National Security Editor Sean Gallagher’s feature, “How they did it (and will likely try again): GRU hackers vs. US elections,” when the Daily Beast reported yesterday’s bombshell: Claire McCaskill, among the most vulnerable Senate Democrats facing re-election this year, was one of three candidates in the 2018 midterm election targeted by the highly determined Russian intelligence agency.
According to the post, McCaskill’s office received one or more fake notifications claiming the target’s Microsoft Exchange password had expired and advising it be changed. Targets who clicked on a link were directed to a counterfeit version of the US Senate’s Active Directory Federation Services login page, which would send any passwords the targets entered to the people behind the fake page. McCaskill has been highly critical of Russia and is considered one of the most vulnerable Senate Democrats facing reelection this year. She represents Missouri, a state where Donald Trump defeated Hillary Clinton by almost 20 points in the 2016 election.
McCaskill’s office was one of three candidates that was targeted. The Daily Beast went on to report that the Senate phishing campaign sent each target a different link that caused the fake password-change webpage to display users’ individual email address when they arrived. The customization made the site more convincing.
If the ruse sounds familiar, it’s probably because it replicates many of the techniques used in 2016 to steal the Gmail passwords of Clinton Campaign Chair John Podesta, former Secretary of State Colin Powell, and a number of other individuals connected to the Clinton campaign and the White House. US intelligence agencies have since concluded that the 2016 hacks were the work of the GRU hackers, who go by a variety of names including Fancy Bear, Sednit, and Pawn Storm.
Domain name seized
Thursday’s Daily Beast article doesn’t just rely on similarities. It cited statements Microsoft VP Tom Burt made last week when he said the company’s seizure of a fake Microsoft domain disrupted a Russian-sponsored hacking campaign that targeted three candidates in the 2018 election. The Daily Beast said the domain was adfs.senate.qov.info, which was used in the spear-phishing emails targeting McCaskill and other Senate staffers. The identities of the other two candidates have yet to become public.
Last August, around the time of the attempted spear phishing on McCaskill’s office, President Trump visited Missouri and chided the senator, telling a crowd to “vote her out of office.” On Thursday in response to the Daily Beast report, McCaskill issued a statement that read in part: “I will continue to speak out and press to hold [Russia] accountable. While this attack was not successful, it is outrageous that they think they can get away with this. I will not be intimidated. I’ve said it before and I will say it again, Putin is a thug and a bully.”
Read full story here
0 notes
Text
Iran- and China-backed phishers try to hook the Trump and Biden campaigns
State-backed hackers from Iran and China just lately focused the presidential campaigns of Republican President Donald Trump and Democrat Joe Biden, a Google risk analyst stated on Thursday.
The revelation is the newest proof of international governments making an attempt to acquire intelligence on US politicians and probably disrupt or meddle of their election campaigns. An Iran-backed group focused the Trump marketing campaign and China-backed attackers focused the Biden marketing campaign, stated Shane Huntley, the head of Google’s Menace Evaluation Group on Twitter. Each teams used phishing emails. There’s no indication that both assault marketing campaign succeeded.
Kittens and Pandas
Huntley recognized the Iranian group that focused Trump’s marketing campaign as APT35, quick for Superior Persistent Menace 35. Often known as Charming Kitten, iKittens, and Phosphorous, the group was caught focusing on an unnamed presidential marketing campaign earlier than, Microsoft stated final October. In that marketing campaign, Phosphorous members tried to entry e-mail accounts marketing campaign workers acquired by way of Microsoft cloud companies. Microsoft stated that the attackers labored relentlessly to collect data that might be used to activate password resets and different account-recovery companies Microsoft offers.
The Chinese language group often known as APT31, in the meantime, focused the Biden marketing campaign, Huntley stated. The group, which safety researchers additionally name Hurricane Panda, Black Vine, and Zirconium, “is a highly advanced adversary” that in 2014 exploited a zeroday vulnerability in Microsoft Home windows, researchers from safety agency CrowdStrike stated at the time.
Google responds
Huntley stated that Google officers despatched the campaigns the firm’s normal warning that they have been focused by nation-based hacking. The corporate started the observe in 2012. To guard its sources and strategies, Google doesn’t ship the notifications instantly and then dispatches them in massive batches. Google additionally referred the matter to regulation enforcement.
In a press release, a Google spokesman wrote:
We will verify that our Menace Evaluation Group just lately noticed phishing makes an attempt from a Chinese language group focusing on the private e-mail accounts of Biden marketing campaign workers and an Iranian group focusing on the private e-mail accounts of Trump marketing campaign workers. We didn’t see proof that these makes an attempt have been profitable. We despatched the focused customers our normal government-backed assault warning and we referred this data to federal regulation enforcement. We encourage marketing campaign workers to use additional safety for his or her work and private emails, and we provide safety assets reminiscent of our Superior Safety Program and free safety keys for qualifying campaigns.
Hacking political events and campaigns has been a chief concern ever since two Russian hacking teams have been caught breaking into the community of the Democratic Nationwide Committee in 2016, simply forward of the presidential marketing campaign. The breaches have been largely achieved utilizing phishing emails that tricked workers members into getting into their passwords into attacker-controlled websites.
A number of US intelligence companies later concluded that Russia engaged in a sustained hacking and disinformation marketing campaign with the purpose of disrupting the US democratic course of and to enhance then-candidate Trump possibilities of profitable the election.
Google offers the above-mentioned Superior Safety Program, a service that’s designed to shield politicians, elections staff, journalists, and different people who find themselves steadily focused by hackers. This system requires a bodily safety key to be used as a second issue when logging into Gmail and different Google companies from new units. APP would have very probably thwarted the 2016 phishing assaults since the mere stealing of passwords is inadequate to acquire unauthorized entry.
from WordPress https://ift.tt/2BAayCy via IFTTT
0 notes
Text
Things You Should Know About Old Yahoo Accounts
Following seven days earlier's affirmation of a significantly more noteworthy Yahoo break affecting 1 billion clients, information exchanges of ProtonMail have expanded again to hit a choice high because of clients searching for a Yahoo Mail substitution.
Update February sixteenth, 2017 – Yahoo basically reported another significant break, which occurred in 2015 and 2016. We had included more bits of information as for what you Contact Yahoo Support ought to do on the off chance that you have a Yahoo account near the completion of this blog entry.
The huge number of new clients coming from Yahoo Mail isn't very baffling given that ProtonMail's center is email security and protection. We as of late watched the model by methods for electronic frameworks organization media when a massive number of Tweets terminated showing up referencing ProtonMail as a Yahoo Mail substitution. Beginning on December fifteenth, the day the Yahoo break was declared, ProtonMail's headway rate appropriately filled in as can be found in the above outline.
We likewise viewed ProtonMail information exchanges ricochet fundamentally a month back after the US presidential political decision. The measure of ProtonMail clients is expanding, in any case the composition is also progressing. After the Yahoo hack was represented, the German Government Office for Data Security (BSI) in like way reproved German tenants to quit utilizing Yahoo Mail. German inhabitants searching for a Yahoo substitution are by and by a significantly more vital level of ProtonMail's userbase, making up 8.5% of guests, up from around 4% irrefutably, beating both France and the UK.
Clients coming from Yahoo will discover at ProtonMail a simple to-utilize email seeing, at any rate fundamental that is comparatively a totally unique way to deal with oversee security. As the Yahoo flight proceeds, we have gotten a reliably growing number of solicitations from Yahoo clients beginning late, so as of now, will try to respond to the most common solicitations.
Why You Should Quit Utilizing Yahoo Mail
This is the third basic security occasion to hit Yahoo Mail in 3 months. In the essential scene, if insights about September 22, a record 500 million records were broken, by then the best break ever. By then on October 4, it was uncovered that Yahoo had vivaciously abetted the NSA in planning thoughtless mass discernment on all Yahoo clients. At long last, on December fifteenth, Yahoo broke its own record by revealing that more than 1 billion records had been blasted.
We have beginning late saw that, different individuals don't comprehend the repercussions email breaks can have on their lives or on the lives of people around them. In the Yahoo break, aggressors found a workable pace and last names, phone numbers, passwords, dates of birth and replies to their security questions. We ought to consider the case of Jane, a theoretical Yahoo Mail client.
Since three years have gone between when the burst happened (2013) and when it was found, aggressors have had three years of time to walk around her mail; read about any clinical subtleties she shared about her family, trips she took abroad, buys she made, and any close by subtleties whenever sent by strategies for her Yahoo account, moreover compromise different records which share data, for example, security questions.
Email unequivocally is especially delicate considering how it is a significant part of the time the common string that joins our computerized lives. Splitting an email account is proportionate to breaking every single other record related with that email, for instance your Facebook, Amazon, or iTunes account, just to give a couple of models.
The Yahoo burst is especially repulsive considering the way that beginning late as 2013, Yahoo was utilizing the obsolete md5 computation to hash passwords. md5 has been viewed as broken for longer than 10 years and on the grounds that Yahoo was utilizing md5, the taken accreditations can be commonly supportively part, improving the underhandedness from the break. In a general sense, utilizing md5 in 2013 was not just negligent, it shows an express thoughtlessness for client security.
Security by Plan
Security is hazardous. Its totally difficult to keep up a vital good ways from this essential reality. In any case, there is still a lot of that ought to be possible to ensure about information. Perhaps the most ideal approaches to manage secure information is to just not have it. This is the way of thinking that ProtonMail has taken with from start to finish encryption and why we are an evidently secure decision instead of Yahoo Mail.
All ProtonMail inboxes are ensured with as far as possible encryption, construing that we don't have the choice to examine your messages. The advantage of this is if ProtonMail is ever broken, aggressors in like way won't have the choice to analyze your messages. As it were, an aggressor can't take from us something that we don't approach. We besides use significantly more grounded affirmation that doesn't require riddle key comparing information to be transmitted over the system, on a very basic level diminishing the hazard from a working Man-in-the-Center snare.
This may appear to be common sense, in any case totally encryption isn't used by Yahoo or Gmail. The explanation is crucial. As far as possible encryption makes it difficult to analyze client information, so it additionally makes it difficult to show notices adequately. The way Yahoo or Gmail comprehend which warning to show you is by investigating your email to find a few solutions concerning your propensities and your life. Since Yahoo and Google infer the standard piece of their income from exhibiting promotions, having the choice to examine client information is a more serious need than security. Considering, you are what is being bundled and offered to promoters.
We really recognize that the rule opportunity to ensure information in the computerized age is to make frameworks that are secure by plan. This recommends associations ought to be made from the most punctual beginning stage security as a focal thought, and not similarly as a dash of knowing the past. Lamentably, this idea simply isn't compatible with the notification based course of action of by far most of the Web.
This is the clarification ProtonMail is driving a substitute model as a decision instead of Yahoo and Google. We can't analyze your information, and we don't work with bolsters. Or then again perhaps, ProtonMail is maintained by the client community, either through blessings or paid records. Since clients and not publicists are our need, we are allowed to build up an email association that puts security and confirmation first.
Future Viewpoint
We recognize that information breaks will become ceaselessly common later on considering the unbalanced idea of doing combating cyberattacks. As there is nothing of the sort as 100% security, no association, for no circumstance ProtonMail, is ensured to information blasts. On the off chance that you can't dispose of a hazard, the accompanying best thing is to ease it.
In such a condition, companies have a commitment to act capably and use from start to finish encryption on at any rate a lot of information as could be ordinary, notwithstanding social event as desolate information as would be sensible. Wretchedly, if the case of surrendering confirmation and security for publicizing income proceeds, so will the case of pummeling information breaks. Regardless, in view of your help, we are legitimately introducing another period for the Web where security and protection come first.
Best Respects,
The ProtonMail Social affair
For questions and comment, you can connect with us at [email protected].
You can get a free secure email account from ProtonMail here.
ProtonMail is upheld by community commitments. We don't serve headways or misuse your affirmation. You can strengthen our key target by moving to a paid arrangement or giving.
Pictures right as of now are given under a free and unhindered award.
Resuscitated data concerning a third Yahoo burst reported on February fifteenth, 2017.
On February 15, 2017, Yahoo made an extra attestation following up on the past hack revealed in December. Yahoo announced that more client accounts (more than the underlying 1 billion that was from the start quick and dirty), may have been compromised because of a specific stunt that joins forming treats. The assault works by bewildering Yahoo that you have as of late been set apart in, at the present time assailant doesn't need to take your secret articulation yet can continue genuinely to expelling information from your inbox. Yahoo didn't exhibit what number of more clients were influenced by it yet referenced that the assault may have happened at some point or another some spot in the extent of 2015 and 2016.
On the off chance that you have a Yahoo mail account, we recommend rapidly making the means we depicted here to guarantee about your Yahoo email address, or shockingly better, essentially erase your Yahoo account. This is the third important security scene including Yahoo Mail and the way that it happened in 2016 proposes that Yahoo mail is likely despite everything compromised. In this way, we recommend quickly changing to a verifiably secure email supplier.
Several clients have thought of us with demands concerning whether ProtonMail is fragile against the blemish that made Yahoo get hacked. ProtonMail isn't presented to the assault that hit Yahoo in light of the fact that our made sure about affirmation plan can't be avoided by amassing treats. We have scattered the specific bits of information with respect to our guaranteed email endorsement plot.
0 notes
Text
Yahoo Support Services in USA & Canada
The tremendous number of new clients coming from Yahoo Mail isn't particularly stunning given that ProtonMail's inside is email security and protection. We beginning late watched the model through online structures affiliation media when vast Yahoo Contact Number Tweets finished showing up referencing ProtonMail as a Yahoo Mail substitution. Beginning on December fifteenth, the day the Yahoo break was addressed, ProtonMail's advancement rate sensibly filled in as can be found in the above system.
We similarly observed ProtonMail information exchanges ricochet a general sense a month sooner after Yahoo Costumer Service Phone Number the US presidential political race. The extent of ProtonMail clients is expanding, yet the composition is correspondingly progressing. After the Yahoo hack was accounted for, the German Government Office for Data Security (BSI) furthermore condemned German occupants to quit utilizing Yahoo Mail. German occupants isolating for a Yahoo Costumer Care Yahoo substitution are correct now an essentially logically discernible level of ProtonMail's userbase, making up 8.5% of guests, up from around 4% truly, beating both France and the UK.
Clients coming from Yahoo will discover at ProtonMail a simple to-utilize email seeing, at any rate basic that is other than a completely uncommon way to deal with oversee regulate security. As the Yahoo mass development proceeds, we have gotten a constantly creating number of mentioning from Yahoo clients beginning late, so right now, will attempt to respond to the most common deals.
Why You Should Quit Utilizing Yahoo Mail
This is the third beast security occasion to hit Yahoo Mail in 3 months. In the central scene, gave a record of September 22, a record 500 million records were affected, by then the best break ever. By then on October 4, it was uncovered that Yahoo had overwhelmingly abetted the NSA in organizing unpredictable mass affirmation on all Yahoo clients. At last, on December fifteenth, Yahoo broke its own record by uncovering that more than 1 billion records had been broken.
We have beginning late saw that, different individuals don't comprehend the repercussions email effects can have on their lives or on the lives of people around them. In the Yahoo break, aggressors found a tolerable pace and last names, phone numbers, passwords, dates of birth and replies to their security questions. We should consider the event of Jane, a speculative Yahoo Mail client.
Since three years have sneaked past between when the break happened (2013) and when it was found, aggressors have had three years of time to walk around her mail; read about any clinical subtleties she shared about her family, trips she took abroad, buys she made, and any close to subtleties at whatever point sent through her Yahoo account, in like way compromise different records which share data, for example, security questions.
Email unequivocally is uncommonly shaky pondering how it is conventionally the common string that blends our computerized lives. Breaking an email account is hazy from separating each other record related with that email, for instance your Facebook, Amazon, or iTunes account, just to give a couple of models.
The Yahoo split is especially stunning considering the way that beginning late as 2013, Yahoo was utilizing the old md5 computation to hash passwords. md5 has been viewed as broken for longer than 10 years and contemplating how Yahoo was utilizing md5, the taken solicitations can be unassumingly sensibly part, extending the wickedness from the break. On a very basic level, utilizing md5 in 2013 was not just rash, it shows an expressive tactlessness for client security.
Security by Plan
Security is disturbing. It is fundamentally extraordinary to keep up a key fair ways from this noteworthy reality. Regardless, there is still a lot of that ought to be possible to ensure about information. Possibly the most ideal approaches to manage regulate ensure information is to just not have it. This is the structure that ProtonMail has taken with totally encryption and why we are a steadfastly secure decision instead of Yahoo Mail.
All ProtonMail inboxes are ensured about with totally encryption, proposing that we don't have the choice to analyze your messages. The advantage of this is if ProtonMail is ever broken, aggressors in like way won't have the decision to look at your messages. Considering, an assailant can't take from us something that we don't approach. We correspondingly use significantly more grounded accreditation that doesn't require riddle word dim information to be transmitted over the structure, completely reducing the risk from a working Man-in Inside assault.
This may emit an impression of being common sense, at any rate as far as possible encryption isn't used by Yahoo or Gmail. The explanation is head. From start to finish encryption makes it difficult to investigate client information, so it likewise makes it difficult to show sees appropriately. The way Yahoo or Gmail comprehend which alerted to show you is by investigating your email to find several courses of action concerning your inclinations and your life. Since Yahoo and Google interpret a gigantic fragment of their income from demonstrating headways, having the decision to take a gander at client information is a more essential need than security. Considering, you are what is being bundled and offered to sponsors.
We really see that the major opportunity to ensure information in the moved age is to make frameworks that are secure by structure. This recommends affiliations ought to be made start from the soonest sort out security as a focal thought, and not likewise as a bit of knowing the past. Lamentably, this idea simply isn't compatible with the movement based strategy of an enormous part of the Web.
This is the clarification ProtonMail is driving a substitute model as a decision as opposed to Yahoo and Google. We can't analyze your information, and we don't work with sponsors. Or on the other hand possibly, ProtonMail is financed by the client community, either through favors or paid records. Since clients and not showing specialists are our need, we are allowed to build up an email association that puts security and confirmation first.
Future Viewpoint
We see that information breaks will become progressively common later on due to the hilter kilter nature of pulling in cyberattacks. As there is nothing of the sort as 100% security, no alliance, not utilizing all techniques ProtonMail, is invulnerable to information breaks. In the event that you can't take out a risk, the accompanying best thing is to ease it.
In such a condition, companies have a commitment to act competently and use past what many would consider conceivable encryption on in any case a huge amount of information as could be standard, regardless of get-together as small information as could be customary contemplating the present circumstance. Amazingly, if the example of giving up protection and security for publicizing income proceeds, so will the occurrence of beating information breaks. Regardless, by conventionality of your help, we are in a little while introducing another period for the Web where security and confirmation come first.
Best Respects,
The ProtonMail Gathering
For questions and comment, you can connect with us at [email protected].
You can get a free secure email account from ProtonMail here.
ProtonMail is kept up by community commitments. We don't serve sorts of progress or misuse your security. You can brace our central target by moving to a paid diagram or giving.
Pictures legitimately at present are given under a free and impossible respect.
Enlivened data with respect to a third Yahoo burst articulated on February fifteenth, 2017.
On February 15, 2017, Yahoo made an extra affirmation following up on the past hack revealed in December. Yahoo communicated that more client accounts (more than the essential 1 billion that was from the beginning point by point), may have been compromised by honorableness of a particular stunt that joins making treats. The catch works by misleading Yahoo that you have beginning late been discrete in, right now assailant doesn't need to take your question key yet can continue genuinely to secluding information from your inbox. Yahoo didn't comprehend what number of more clients were impacted by it at any rate referenced that the catch may have happened at some point or another some spot in the level of 2015 and 2016.
In the event that you have a Yahoo mail account, we recommend quickly making the strategies we plot here to guarantee about your Yahoo email address, or awesomely better, on a very basic level erase your Yahoo account. This is the third enormous security scene including Yahoo Mail and the way that it happened in 2016 recommends that Yahoo mail is likely paying little notification to everything compromised. At the present time, recommend quickly changing to an unflinchingly secure email supplier.
Two or three clients have remained in contact with us with demands concerning whether ProtonMail is uncovered against the flaw that made Yahoo get hacked. ProtonMail isn't defenseless against the discover that hit Yahoo considering the way that our guaranteed authentication plot can't be keep away from by get-together treats. We have scattered the particular bits of information as for our made sure about email approval plot.
0 notes
Text
Twitter CEO Jack Dorsey’s account has been hacked
TechMyBiz for all things “IT”
Twitter CEO Jack Dorsey’s Twitter account was seemingly hacked on Friday afternoon by a group that calls itself the Chuckle Squad. Twitter’s communications team issued a statement via Twitter.
We’re aware that @jack was compromised and investigating what happened.— Twitter Comms (@TwitterComms) August 30, 2019
The hackers tweeted racist terms from Dorsey’s account. The offensive tweets started being deleted not long after the attack began, but some were up for approximately 10 minutes. The hackers also used their time controlling Dorsey’s account to plug a Discord server used for their own activity, asking people to join. The server invitation link tweeted out by the hackers is no longer valid at this time. Following the incident, “both the server and the server owner were permanently removed from Discord within minutes of this being reported to us,” a Discord representative told The Verge. “Encouraging any kind of hacking is in direct violation of our Terms of Service,” the representative said. “We will continue to monitor and investigate this incident.” Reports suggest the tweets came from a source called Cloudhopper, a company that Twitter previously acquired to help with its SMS service. Dorsey’s account was previously hacked in 2016 by the security firm OurMine. The group used the hack to include a message about “testing your security,” and tweeted out a link to its website.
.@Jack’s account has been hacked. The Tweets are coming from a source called Cloudhopper. Cloudhopper was the name of the company Twitter acquired a long time ago to help bolster their SMS service.Looks like the hackers are Tweeting via the old SMS service… pic.twitter.com/YcU3DTn9wS— Sam (@Hooray) August 30, 2019
It appears to be the same group that attacked a number of YouTube creators and influencers last week on Twitter, including beauty vlogger James Charles, Shane Dawson, and comedian King Bach. The hackers also allegedly gained access to Desmond “Etika” Amofah’s Gmail account, as seen by screenshots collected in their Discord server. Many of the influencers and YouTubers at the time suggested their accounts were breached following a SIM card swap conducted by AT
Related Posts:
Disney will give subscribers four simultaneous… Image: Disney Disney’s upcoming Disney streaming service is shaping up…
Mario Kart Tour is coming out on September 25th Nintendo’s long-awaited and delayed Mario Kart smartphone game is almost…
How a Small Business Saved 20 Hours Per Week With… Sponsored Post Traditional small businesses may be hesitant to dip…
Epic finally backpedals on Fortnite’s B.R.U.T.E.… Image: Epic Games Epic Games has heard the feedback loud…
Changing your office printer password may protect… This recent attack by hacking group Fancy Bear may have…
The post Twitter CEO Jack Dorsey’s account has been hacked appeared first on TekMyBiz.
Source: https://tekmybiz.com/technology-solutions/twitter-ceo-jack-dorseys-account-has-been-hacked/?utm_source=rss&utm_medium=rss&utm_campaign=twitter-ceo-jack-dorseys-account-has-been-hacked
from TekMyBiz https://tekmybiz.wordpress.com/2019/08/31/twitter-ceo-jack-dorseys-account-has-been-hacked/
0 notes
Text
Security-conscious darkweb crime marketplaces institute world-leading authentication practices #1yrago

If you are a seller on Alphabay -- a darkweb site that sells "drugs, stolen data and hacking tools," you'll have to use two-factor authentication (based on PGP/GPG) for all your logins.
What's more, Alphabay requires you to use a unique seven-word phrase to recover passwords (as opposed to easily researched questions like high-school football team, mother's maiden name, etc), and says there is no way to recover a lost password without this phrase. Finally, Alphabay requires a four-digit PIN to transfer bitcoin to your personal wallet.
Alphabay has deployed these measures to prevent phishing, which plagues darkweb markets in the same way that stick-ups plague drug dealers -- without access to police investigations and without the threat of legal repercussions, crime sites are themselves prey for other criminals. While other sites have deployed some of these procedures as options for sellers, Alphabay leads the darkweb marketplaces in requiring them.
In this regard, Alphabay has better authentication procedures than Gmail or most US banks (my own US bank only recently dropped its 7-character maximum for its passwords, which were also case-insensitive and couldn't contain punctuation!). As Joseph Cox points out, this doesn't mean that the sites itself are more secure than, say, Google -- the latter having an army of security experts, tripwires and IDSes, and the full power of many nations' legal apparatus with which to fight hacking attempts.
https://boingboing.net/2016/03/28/security-conscious-darkweb-cri.html
14 notes
·
View notes
Text
Original Post from Krebs on Security Author: BrianKrebs
Eight Americans and an Irishman have been charged with wire fraud this week for allegedly hijacking mobile phones through SIM-swapping, a form of fraud in which scammers bribe or trick employees at mobile phone stores into seizing control of the target’s phone number and diverting all texts and phone calls to the attacker’s mobile device. From there, the attackers simply start requesting password reset links via text message for a variety of accounts tied to the hijacked phone number.
All told, the government said this gang — allegedly known to its members as “The Community” — made more than $2.4 million stealing cryptocurrencies and extorting people for restoring access to social media accounts that were hijacked after a successful SIM-swap.
Six of those charged this week in Michigan federal court were alleged to have been members of The Community of serial SIM swappers. They face a fifteen count indictment, including charges of wire fraud, conspiracy and aggravated identity theft (a charge that carries a mandatory two-year sentence). A separate criminal complaint unsealed this week charges three former employees of mobile phone providers accused of collaborating with The Community’s members.
Several of those charged have been mentioned by this blog previously. In August 2018, KrebsOnSecurity broke the news that police in Florida arrested 25-year-old Pasco County, Fla. city employee Ricky Joseph Handschumacher, charging him with grand theft and money laundering. As I reported in that story, “investigators allege Handschumacher was part of a group of at least nine individuals scattered across multiple states who for the past two years have drained bank accounts via an increasingly common scheme involving mobile phone “’SIM swaps.’”
This blog also has featured several stories about the escapades of Ryan Stevenson, a 26-year-old West Haven, Conn. man who goes by the hacker name “Phobia.” Most recently, I wrote about how Mr. Stevenson earned a decent number of bug bounty rewards and public recognition from top telecom companies for finding and reporting security holes in their Web sites — all the while secretly operating a service that leveraged these same flaws to sell their customers’ personal data to people who were active in the SIM swapping community.
One of the six men charged in the conspiracy — Colton Jurisic, 20 of, Dubuque, Iowa — has been more well known under his hacker alias “Forza,” and “ForazaTheGod.” In December 2016, KrebsOnSecurity heard from a woman who had her Gmail, Instagram, Facebook and LinkedIn accounts hijacked after a group of individuals led by Forza taunted her on Twitter as they took over her phone account.
“They failed to get [her three-letter Twitter account name, redacted] because I had two-factor authentication turned on for twitter, combined with a new phone number of which they were unaware,” the source said in an email to KrebsOnSecurity in 2016. “@forzathegod had the audacity to even tweet me to say I was about to be hacked.”
Also part of the alleged Community of SIM swappers is Conor Freeman, 20, of Dublin, Ireland; Reyad Gafar Abbas, 19, of Rochester, New York; Garrett Endicott, 21, of Warrensburg, Missouri.
The three men criminally accused of working with the six through their employment at mobile phone stores are Fendley Joseph, 28, of Murrietta, Calif.; Jarratt White, 22, and Robert Jack, 22, both from Tucson, Ariz.
If convicted on the charge of conspiracy to commit wire fraud, each defendant faces a statutory maximum penalty of 20 years in prison. The charges of wire fraud each carry a statutory maximum penalty of 20 years in prison.
Last month, 20-year-old college student and valedictorian Joel Ortiz became the first person ever to be sentenced for SIM swapping — pleading guilty to a ten year stint in prison for stealing more than $5 million in cryptocurrencies from victims and then spending it lavishly at elaborate club parties in Las Vegas and Los Angeles.
A copy of the indictment against the six men is here (PDF).
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: BrianKrebs Nine Charged in Alleged SIM Swapping Ring Original Post from Krebs on Security Author: BrianKrebs Eight Americans and an Irishman have been charged with wire fraud this week for allegedly hijacking mobile phones through SIM-swapping, a form of fraud in which scammers bribe or trick employees at mobile phone stores into seizing control of the target’s phone number and diverting all texts and phone calls to the attacker’s mobile device.
0 notes
Text
New top story from Time: The 2020 Presidential Campaigns Are Still Vulnerable to Cyber Attacks. Here’s Why
Most Americans aren’t yet paying a lot of attention to the 2020 presidential campaign. The same can’t be said for Russian spies.
Aides and advisers to the vast field of Democratic hopefuls are ringing alarm bells, telling their bosses they should assume that Moscow is laying the groundwork to disrupt, if not derail, their campaigns, just as Russian intelligence did to Hillary Clinton’s in 2016.
But interviews with the campaigns show cyber security is a secondary concern, with most of the campaigns contacted by TIME say they have not “finalized” their tech plan or hired a security chief.
The biggest problem is money. Every campaign focuses vast amounts of effort raising money to compete on ground troops, ads and campaign offices in key locations. Spending precious cash on cyber tools, whose successful deployment results in a non-event, is hard to defend.
“There’s nothing sexy about it,” says Mike Sager, the chief technology officer at EMILY’s List, a group that works to elect women who support abortion rights. But, he says, “the folks who have been through it, who know what happens when you don’t do this, get it.”
Nobody disputes the threat. Russia’s larger goals remain the same as they were in 2016: making American democracy look bad. “It is about the legitimacy of democracy and about the trust people have in their democracy,” said Eric Rosenbach, a former Pentagon chief of staff who now heads Harvard’s Defending Digital Democracy program. “Unfortunately, there are a lot of different ways in the information age that bad actors and nefarious nation-states can undermine that.”
Cyber security officials say other countries, like China, Iran and North Korea, have shown the capability to meddle in U.S. elections as well.
Defending a campaign properly requires starting right at the launch. “You’re starting a business and you have to have all those little things: they need email addresses, phones, computers, payroll, video conferencing tools,” says Sager. “How that is started when you give out computers to everyone, there’s a lot of those decisions in the very, very beginning that have a very significant impact the further you go,” he says.
Harvard University’s Belfer Center in 2017 released what many campaigns consider the gold standard — if still aspirational — playbook for campaign cyber security that includes planning “in case your security is compromised,” almost resigning itself to that as an inevitability. The Democratic National Committee in February rolled out a one-page checklist for nascent campaigns to consider, from making sure software is updated every 30 days to having a cell phone password at least six characters long. In March, the DNC moved up a briefing for campaign staffs about email security after an analysis from security advocacy group Global Cyber Alliance reported just four of the 14 declared major candidates had secured email systems.
Many would like to hand the problem off to the government. But the feds have their hands full defending the physical vote; keeping tabs on the security of 20 early campaigns is a low priority. The Department of Homeland Security has turned aggressively toward protecting the integrity of state and local election infrastructure. Matthew Masterson, a senior adviser for the Department of Homeland Security‘s cybersecurity unit, has been in touch with states to build relationships that simply weren’t in place in 2016. Forty-six states are using DHS’ intrusion detection system, and it appears all of the states are heeding experts’ recommendations to use paper ballots.
But it’s the P.R. value of even one hack of a campaign that can outweigh the success of security measures elsewhere. “What I fear the most, and what I think is most likely to happen, is that there will be a hack in which one of these [foreign] intel agencies plants some information, pulls out enough information to make a bogus claim of fraud and then goes public with that in a way that is intended to undermine trust in the outcome of the election — even if there really wasn’t enough of an intrusion to change the outcome,” said Harvard’s Rosenbach.
Read More: Russia Wants to Undermine Elections. Here’s How Rhode Island Is Fighting Back
Even as campaigns struggle to address the dangers of 2016, the threats are becoming more sophisticated.
The 2020 presidential race is likely to be known as the first deepfake race, in which highly realistic falsified videos can portray candidates as saying anything. Leaders have been warning of this reality for years. Sen. Mark Warner, the top Democrat on the Senate spy panel, last year used a turn keynoting a journalism award dinner to warn about the threats facing elections. Lawmakers have asked Director of National Intelligence Dan Coats to make this a priority. The Pentagon is funding research into the medium. And former NATO Secretary General Anders Fogh Rasmussen, who is leading a transatlantic coalition to defend Western elections, has been showing one real and two faked Trump videos to audiences to hammer home the potential danger of such deepfake videos.
“Foreign meddlers can amplify divisions in the country by raising divisive issues. Time and again we have seen that,” Rasmussen tells TIME. “It’s a never-ending struggle, and, I think, we should also be aware of the fact this is not a new thing. You saw exactly the same during the Cold War. But the technology has been developed so that now you have new communication tools.”
This deepfake threat, in part, explains why aides inside presidential campaigns have taken to recording every utterance of the candidates — if not themselves — during public appearances and interviews.
The same is true for emails. Whereas previous cycles’ inboxes were sometimes archived and sometimes not, the hacking of 2016 laid bare the importance of an internal archive. There was no easy way to verify which of the thousands of stolen emails posted on Wikileaks’ site were real and which may have been fabricated or altered. Outside advisers are urging candidates to establish firm document-retention policies and punish staffers who don’t comply.
And it’s not just work email accounts, either. Half of the spearphishing emails cited in the Special Counsel’s indictment of Russian hackers targeted campaign officials’ private accounts. So using a Gmail account will not spare high-profile campaign aides the trolls’ and bots’ persistence.
Not every campaign is defenseless, and many insist they’re preparing. Sen. Kamala Harris’ campaign team requires two-factor authentication for its staffers, who are also deploying encrypted messaging systems to add another layer of security.
But with everything moving so quickly inside campaigns, it is tempting to forego protocol and leave laptops open during that quick run to the kitchen.
“The problem is, because of campaign culture, security tends not to be top of mind,” says Dave Leichtman, who is both Microsoft’s Defending Democracy program director and the Democratic Party of Virginia’s vice chairman for tech. “They may actually be more vulnerable to these kinds of attacks because they’re not paying attention.”
The Russians, however, almost certainly are.
via https://cutslicedanddiced.wordpress.com/2018/01/24/how-to-prevent-food-from-going-to-waste
0 notes