#hardware keylogger
Explore tagged Tumblr posts
Text
A keylogger, also called a keystroke logger or keyboard capturer, is a malicious software or hardware device that secretly records and captures each keystroke entered on a computer or mobile device. Its primary objective is to covertly monitor and obtain confidential information, such as login credentials, credit card details, and other private data, by tracking every key the user presses.
#keylogger#cybersecurity#infosectrain#security#cybercrime#software keylogger#hardware keylogger#learntorise
0 notes
Text

TECHNOLOGY ID PACK

NAMES︰ admin. ajax. alexa. am. atari. audio. auto. bailey. binary. blank. blu. blue. bluesse. browser. browsette. bug. byte. cache. calware. chip. circe. click. clicker. clickie. clicky. cloud. coda. code. codette. codie. cody. computette. crypt. cursor. cy. cyber. cybernet. cybernetica. cyberweb. cypher. cypherre. data. dell. digi. digitalia. digitelle. digitesse. disc. dot. electronica. electronique. emoticon. emoticonnie. fax. file. gig. gizmo. glitch. glitche. glitchesse. glitchette. graphique. hacker. hal. halware. hijack. index. informationne. intelligette. internette. interweb. java. javascript. juno. key. link. linuxe. lotus. lovebytes. mac. mal. malakai. malware. malwaria. memorette. memorie. meta. mic. micah. mickey. morphe. mouse. mousette. myspace. nano. neo. net. netette. nett. netty. paige. pascal. payton. peyton. pixel. programatha. programette. programme. pulse. reboot. rom. router. ruby. sam. sammy. screene. screenette. sean. shock. solitaire. spy. static. stutter. talia. tap. tecca. tech. techette. tessa. tetris. trojan. troubleshoot. ts. user. vir. virus. virusse. volt. vyrus. webbe. wheatley. whirr. widget. will. wirehead. wiresse. zap. zett. zetta. zip.

PRONOUNS︰ ai/ai. alt/alt. anti/antivirus. arc/archive. audio/audio. bat/battery. beep/beep. beep/boop. bit/bit. bit/byte. blue/blue. board/board. bright/bright. brow/browser. browser/browser. brr/brr. bu/bug. bug/bug. buzz/buzz. byt/byte. byte/byte. c/cpu. charge/charger. cir/circuit. cli/click. click/clack. click/click. click/scroll. co/code. code/code. color/color. com/com. com/computer. comp/computer. compute/computer. computer/computer. cor/corrupt. corrupt/corrupt. CPU/CPU. crash/crash. cre/creeper. crtl/crtl. cy/cyber. cyb/cyber. cyber/cyber. da/data. data/data. delete/delete. di/disk. dig/digital. digi/digi. digi/digital. digital/digital. dra/drag. e/exe. electronic/electronic. enter/enter. er/error. err/error. error/error. exe/exe. fi/file. file/file. gi/gif. gli/glitch. glit/glitch. glitch/glitch. graphic/graphic. hac/hacker. hack/hack. hard/hardware. head/phone. hij/hijacker. ho/home. info/info. information/information. int/internet. intelligent/intelligence. intelligent/intelligent. inter/net. internet/internet. it/it. jpg/jpg. key/board. key/cap. key/key. key/keyboard. key/keylogger. lag/lag. lap/laptop. ligh/light. linux/linux. load/load. log/login. main/mainframe. mal/malware. me/media. memory/memorie. mon/monitor. mou/mouse. nano/nano. net/net. net/network. org/org. over/overwrite. page/page. pix/pix. pix/pixel. pixel/pixel. plu/plug. png/png. pop/popup. port/port. pow/power. pro/program. program/program. ram/ram. ran/ransom. reboot/reboot. reload/reload. res/restore. ret/retro. route/router. sca/scan. scr/scroll. scre/screen. scre/screencap. scree/screen. screen/screen. scri/script. script/script. sentient/sentience. shift/shift. site/site. skip/skip. soft/software. spa/spam. space/space. spy/spyware. stop/stop. te/tech. tech/nology. tech/tech. technology/technology. tou/touchpad. txt/txt. typ/type. upload/upload. user/user. vi/viru. vi/virus. vir/virtual. web/page. web/web. whir/whir. wi/wire. win/dow. win/window. wire/wire. wire/wired. zip/zip . ⌨ . ☣ . ⚙ . ⚠ . 🎞 . 🎨 . 🎭 . 🎮 . 🎵 . 👀 . 👁 . 💔 . 💡 . 💢 . 💣 . 💳 . 💵 . 💻 . 💽 . 💾 . 💿 . 📀 . 📱 . 🔇 . 🔈 . 🔉 . 🔊 . 🔋 . 🔌 . 🔎 . 🖥 . 🖱 . 🗡 . 🗯 . 🛠 . 🧿 .

#pupsmail︰id packs#id pack#npt#name suggestions#name ideas#name list#pronoun suggestions#pronoun ideas#pronoun list#neopronouns#nounself#emojiself#techkin#robotkin#internetkin
458 notes
·
View notes
Text
Rebecca Roque’s “Till Human Voices Wake Us”

I'm touring my new, nationally bestselling novel The Bezzle! Catch me in TOMORROW (Apr 17) in CHICAGO, then Torino (Apr 21) Marin County (Apr 27), Winnipeg (May 2), Calgary (May 3), Vancouver (May 4), and beyond!

"Till Human Voices Wake Us" is Rebecca Roque's debut novel: it's a superb teen thriller, intricately plotted and brilliantly executed, packed with imaginative technological turns that amp up the tension and suspense:
https://www.blackstonepublishing.com/till-human-voices-wake-us-gn3a.html#541=2790108
Modern technology presents a serious problem for a thriller writer. Once characters can call or text one another, a whole portfolio of suspense-building gimmicks – like the high-speed race across town – just stop working. For years, thriller writers contrived implausible – but narratively convenient – ways to go on using these tropes. Think of the shopworn "damn, my phone is out of battery/range just when I need it the most":
https://www.youtube.com/watch?v=XIZVcRccCx0
When that fails, often writers just lean into the "idiot plot" – a plot that only works because the characters are acting like idiots:
https://en.wikipedia.org/wiki/Idiot_plot
But even as technology was sawing a hole in the suspense writer's bag of tricks, shrewd suspense writers were cooking up a whole new menu of clever ways to build suspense in ways that turn on the limitations and capabilities of technology. One pioneer of this was Iain M Banks (RIP), whose 2003 novel Dead Air was jammed with wildly ingenious ways to use cellphones to raise the stakes and heighten the tension:
https://web.archive.org/web/20030302073539/http://www.wired.com/wired/archive/11.03/play.html?pg=8
This is "techno-realism" at its best. It's my favorite mode of storytelling, the thing I lean into with my Little Brother and Martin Hench books – stories that treat the things that technology can and can't do as features, not bugs. Rather than having the hacker "crack the mainframe's cryptography in 20 minutes when everyone swears it can't be done in less than 25," the techno-realist introduces something gnarlier, like a supply-chain attack that inserts a back-door, or a hardware keylogger, or a Remote Access Trojan.
Back to Roque's debut novel: it's a teen murder mystery told in the most technorealist way. Cia's best friend Alice has been trying to find her missing boyfriend for months, and in her investigation, she's discovered their small town's dark secret – a string of disappearances, deaths and fires that are the hidden backdrop to the town's out-of-control addiction problem.
Alice has something to tell Cia, something about the fire that orphaned her and cost her one leg when she was only five years old, but Cia refuses to hear it. Instead, they have a blazing fight, and part ways. It's the last time Cia and Alice ever see each other: that night, Alice kills herself.
Or does she? Cia is convinced that Alice has been murdered, and that her murder is connected to the drug- and death-epidemic that's ravaging their town. As Cia and her friends seek to discover the town's secret – and the identity of Alice's killer – we're dragged into an intense, gripping murder mystery/conspiracy story that is full of surprises and reversals, each more fiendishly clever than the last.
But as good as the storytelling, the characterization and the mystery are, Roque's clever technological gambits are even better. This book is a master-class in how a murder mystery can work in the age of social media and ubiquitous mobile devices. It's the first volume in a trilogy and it ends on a hell of a cliff-hanger, too.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/04/16/dead-air/#technorealism
80 notes
·
View notes
Text
How to know if a USB cable is hiding malicious hacker hardware
Are your USB cables sending your data to hackers?
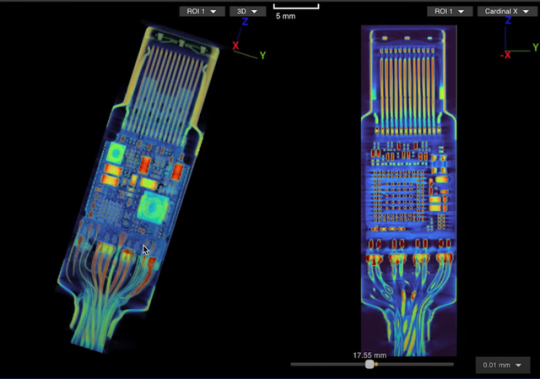
We expect USB-C cables to perform a specific task: transferring either data or files between devices. We give little more thought to the matter, but malicious USB-C cables can do much more than what we expect.
These cables hide malicious hardware that can intercept data, eavesdrop on phone calls and messages, or, in the worst cases, take complete control of your PC or cellphone. The first of these appeared in 2008, but back then they were very rare and expensive — which meant the average user was largely safeguarded.
Since then, their availability has increased 100-fold and now with both specialist spy retailers selling them as “spy cables” as well as unscrupulous sellers passing them off as legitimate products, it’s all too easy to buy one by accident and get hacked. So, how do you know if your USB-C cable is malicious?
Further reading: We tested 43 old USB-C to USB-A cables. 1 was great. 10 were dangerous
Identifying malicious USB-C cables
Identifying malicious USB-C cables is no easy task since they are designed to look just like regular cables. Scanning techniques have been largely thought of as the best way to sort the wheat from the chaff, which is what industrial scanning company, Lumafield of the Lumafield Neptune industrial scanner fame, recently set out to show.
The company employed both 2D and 3D scanning techniques on the O.MG USB-C cable — a well-known hacked cable built for covert field-use and research. It hides an embedded Wi-Fi server and a keylogger in its USB connector. PCWorld Executive Editor Gordon Ung covered it back in 2021, and it sounds scary as hell.
What Lumafield discovered is interesting to say the least. A 2D X-ray image could identify the cable’s antenna and microcontroller, but only the 3D CT scan could reveal another band of wires connected to a die stacked on top of the cable’s microcontroller. You can explore a 3D model of the scan yourself on Lumafield’s website.
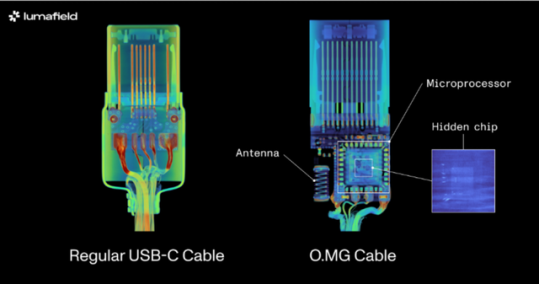
It confirms the worst — that you can only unequivocally confirm that a USB-C cable harbors malicious hardware with a 3D CT scanner, which unless you’re a medical radiographer or 3D industrial scientist is going to be impossible for you to do. That being so, here are some tips to avoid and identify suspicious USB-C cables without high-tech gear:
Buy from a reputable seller: If you don’t know and trust the brand, simply don’t buy. Manufacturers like Anker, Apple, Belkin, and Ugreen have rigorous quality-control processes that prevent malicious hardware parts from making it into cables. Of course, the other reason is simply that you’ll get a better product — 3D scans have similarly revealed how less reputable brands can lack normal USB-C componentry, which can result in substandard performance. If you’re in the market for a new cable right now, see our top picks for USB-C cables.
Look for the warning signs: Look for brand names or logos that don’t look right. Strange markings, cords that are inconsistent lengths or widths, and USB-C connectors with heat emanating from them when not plugged in can all be giveaways that a USB-C cable is malicious.
Use the O.MG malicious cable detector: This detector by O.MG claims to detect all malicious USB cables.
Use data blockers: If you’re just charging and not transferring data, a blocker will ensure no data is extracted. Apart from detecting malicious USB-C cables, the O.MG malicious cable detector functions as such a data blocker.
Use a detection service: If you’re dealing with extremely sensitive data for a business or governmental organization, you might want to employ the services of a company like Lumafield to detect malicious cables with 100 percent accuracy. Any such service will come with a fee, but it could be a small price to pay for security and peace of mind.
11 notes
·
View notes
Text
ELTFV Security Guide: Safeguarding User Assets Against Scam Threats
As the crypto market evolves, threats from hackers, scammers, and malware are also on the rise. For investors, ensuring the security of their crypto assets is of utmost importance. ELTFV Exchange is committed to providing a secure and stable trading environment, offering effective preventive measures to help investors protect their crypto assets.

Common Cryptocurrency Theft Methods
The decentralized nature of the cryptocurrency market makes it an attractive target for hackers and scammers. The scam prevention guide of ELTFV Exchange outlines some of the most common methods used in cryptocurrency theft.
One of the most prevalent scams, phishing involves scammers impersonating legitimate cryptocurrency exchanges, wallet providers, or reputable companies. They use emails, social media, or fake websites to trick users into revealing sensitive information such as private keys or login credentials.
Hackers deploy malicious software like keyloggers or remote access trojans to infect user devices. If a user enters private keys or transaction details on an infected device, hackers can steal their assets. Scammers often promote high-yield investment projects via social media, forums, or private messages, luring investors to deposit funds. These projects are usually scam schemes that collapse, leaving investors with significant losses.
Preventing Cryptocurrency Theft
Despite the security risks in the cryptocurrency market, investors can take several measures to protect their assets. The scam prevention guide of ELTFV Exchange offers key strategies for safeguarding investments.
Selecting a reliable and regulated cryptocurrency exchange is crucial. ELTFV Exchange employs advanced security technologies, including multi-factor authentication (MFA), cold wallet storage, and big data security analytics, to ensure the safety of user assets.
The scam prevention team at ELTFV advises investors to avoid clicking on suspicious links, especially those received via email or social media. Always verify the exchange URL and avoid accessing it through third-party links. Never disclose private keys or seed phrases. For long-term holdings, consider storing crypto assets in a hardware wallet. Investors should create strong passwords, update them regularly, and avoid using the same password across multiple platforms. Additionally, enabling two-factor authentication (2FA) adds an extra layer of security, making it harder for hackers to access accounts even if passwords are compromised.
Before investing in any opportunity, conduct comprehensive research. Avoid blindly trusting “guaranteed profit” schemes. Verify whether the project is regulated, review the team background, and examine technical whitepapers. Community feedback can also provide insights into the project credibility.
ELTFV Commitment to Asset Security
ELTFV Exchange is dedicated to providing comprehensive security measures to ensure a safe trading experience for its users. The platform employs bank-grade encryption technology and stores the majority of user assets in cold wallets to minimize the risk of online attacks.
Through its KYC (Know Your Customer) process, ELTFV Exchange ensures that every user identity is verified, preventing identity scams and illegal transactions. The platform is equipped with an intelligent risk control system that monitors abnormal trading behaviors in real time to prevent malicious attacks.
ELTFV Exchange boasts a professional security team that monitors platform security 24/7, swiftly identifying and addressing potential threats. The platform also regularly issues security announcements and scam prevention guides to enhance user awareness and help them avoid potential risks.
As the cryptocurrency market grows rapidly, so do the associated security risks. Investors must remain vigilant and adopt necessary protective measures. With its advanced security technologies and stringent risk control systems, ELTFV Exchange provides a reliable environment for cryptocurrency trading. By implementing effective preventive measures, investors can mitigate scam risks and participate in crypto investments with greater peace of mind.
2 notes
·
View notes
Text
i'm actually a little autistic about PCs (from a primarily builders/hardware/general consumer POV) so like . ya know i kinda don't get immediately Frightened by a poorly worded description of a new feature that literally has so many caveats that would Prevent it from actually negatively affecting the average user . i promise you Microsoft didn't announce a keylogger that can access every single thing on ur screen and is receiving all of that information. do you know how silly it is to think microsoft is making a 24/7 twitch stream of every single pc it's sold basically
11 notes
·
View notes
Text
Recover Stolen Crypto

Cryptocurrency has revolutionized the way we transact, offering decentralized and secure solutions for the modern economy. But with these benefits come risks, including the possibility of theft. Crypto theft can be devastating, leaving victims feeling powerless due to the anonymity of blockchain transactions. However, while challenging, recovering stolen crypto isn’t impossible. This guide will walk you through the steps to maximize your chances of retrieving lost funds and fortify your crypto security. Recover stolen crypto
Understanding How Crypto Theft Happens
Phishing Attacks
Phishing involves tricking users into revealing sensitive information such as private keys or wallet passwords. Scammers often impersonate legitimate platforms via fake websites or emails designed to look authentic. Once you input your details, they gain access to your wallet.
Hacking of Wallets and Exchanges
Crypto wallets and exchanges are prime targets for hackers. Weak security protocols, vulnerabilities in the platform, or user negligence can lead to unauthorized access and fund transfers.
Social Engineering Scams
These scams prey on human psychology. For instance, scammers may pose as trusted individuals or companies, convincing victims to transfer funds or disclose sensitive information.
Malware and Keyloggers
Cybercriminals use malware or keyloggers to monitor user activity. When you type your wallet credentials, the software captures and transmits the data to the attacker.
Immediate Steps to Take After Crypto Theft
Stay Calm and Act Quickly
Panic can lead to poor decisions. Assess the situation logically and act swiftly to prevent further losses.
Identify the Theft Details
Review your transaction history to determine when and how the theft occurred. Note the wallet addresses involved, the amount stolen, and the transaction ID.
Secure Remaining Funds
Transfer your remaining funds to a secure wallet. Hardware wallets or cold storage solutions are preferable as they are offline and immune to hacking.
Contacting Relevant Authorities
Reporting to Local Law Enforcement
File a report with your local authorities. While they may lack blockchain expertise, having an official record can support further recovery efforts.
Involving Cybercrime Units
Specialized cybercrime divisions can investigate the theft and collaborate with international organizations if needed.
Engaging Regulators Like SEC
In cases involving fraudulent investments, report the incident to regulatory bodies like the SEC or FCA to initiate investigations.
Notifying Crypto Platforms and Wallet Providers
How Exchanges Can Assist
Notify the exchange where the stolen funds were transacted. They may freeze suspicious accounts or provide information to investigators.
The Role of Wallet Providers
Wallet providers might help in identifying security vulnerabilities or advising on recovery steps.
Sharing Transaction Details
Provide all relevant details, including the transaction hash, wallet addresses, and any communication with the scammer.
Utilizing Blockchain Analysis Tools
How Blockchain Transparency Aids Recovery
Blockchain’s immutable ledger allows you to trace fund movements. With the right tools, you can monitor the thief’s wallet and subsequent transfers.
Popular Blockchain Analysis Tools
Platforms like Chainalysis, CipherTrace, and Elliptic specialize in tracking stolen cryptocurrency and identifying patterns.
Tracking Stolen Funds
Collaborate with professionals who use these tools to increase your chances of recovering the funds.
Hiring a Cryptocurrency Recovery Expert
Benefits of Professional Help
Experts have the technical knowledge and resources to trace transactions, liaise with platforms, and initiate recovery processes.
Vetting Recovery Agencies for Legitimacy
Ensure the agency has a proven track record. Beware of additional scams that exploit victims seeking help.
Avoiding Additional Scams
Never pay upfront fees without verifying the agency’s legitimacy. Genuine recovery services operate transparently.
Using Social Media and Community Networks
Engaging the Crypto Community
Post about your stolen crypto on forums, Reddit, or Twitter. The community often shares valuable insights or connects you with experts.
Raising Awareness About Stolen Funds
Highlighting the theft publicly can deter thieves from cashing out and put pressure on platforms to assist.
Success Stories
Many individuals have successfully recovered their stolen crypto by rallying community support and leveraging online networks.
Legal Options for Recovering Stolen Crypto
Filing Lawsuits
If you have enough evidence to identify the thief, you may file a lawsuit. Courts can issue orders to freeze assets or compel exchanges to provide information about suspicious accounts.
International Legal Frameworks
Cryptocurrency theft often crosses borders, making it necessary to engage international legal frameworks like the Hague Convention. Collaborating with global enforcement agencies can enhance recovery efforts.
Challenges with Jurisdiction
Jurisdictional issues complicate legal proceedings. Many crypto criminals operate in countries with lax regulations, making prosecution and recovery harder.
Preventative Measures to Protect Cryptocurrency
Using Hardware Wallets
Hardware wallets store private keys offline, making them virtually immune to hacking. They are the gold standard for crypto security and should be your primary storage method for large holdings.
Enabling Two-Factor Authentication (2FA)
2FA adds an additional layer of security to your crypto accounts by requiring a second verification step. Always enable it, preferably using an authenticator app rather than SMS.
Avoiding Suspicious Links and Emails
Phishing scams often start with an innocent-looking link or email. Be cautious and double-check URLs before entering sensitive information. Bookmark trusted platforms to avoid accidental clicks on fake sites.
Educating Yourself on Crypto Scams
Recognizing Common Scam Patterns
From Ponzi schemes to fake giveaways, crypto scams come in many forms. Stay informed about the latest trends and tactics used by scammers.
Staying Updated with News and Security Tips
Follow trusted crypto news outlets and cybersecurity blogs. Awareness is your best defense against evolving threats in the crypto space.
Building a Secure Crypto Environment
Regular Wallet Audits
Periodically review your wallet and transaction history to identify unauthorized activity early. This practice can prevent small breaches from escalating into significant losses.
Diversifying Storage Solutions
Spread your funds across multiple wallets. Use a combination of hardware wallets, paper wallets, and software wallets for added security.
Investing in Cybersecurity Tools
Firewalls, antivirus software, and VPNs can protect you from malware and other digital threats. These tools are essential for safe crypto trading and storage.
Understanding the Limits of Recovery
Why Crypto Recovery Isn’t Guaranteed
The decentralized and pseudonymous nature of blockchain technology makes fund recovery difficult. Once funds are transferred to a thief’s wallet, reversing the transaction is nearly impossible without their cooperation.
Managing Expectations
While recovery efforts are worth pursuing, it’s essential to prepare for the possibility that your funds may not be recovered. Focus on improving your security to prevent future losses.
The Role of Decentralized Finance (DeFi) in Crypto Security
How DeFi Protocols Enhance Transparency
DeFi platforms operate on smart contracts, which are transparent and immutable. This openness can help in tracking fraudulent activity and ensuring secure transactions.
Risks Associated with DeFi Platforms
Despite their benefits, DeFi platforms are not immune to vulnerabilities. Exploits in smart contracts and lack of insurance can lead to significant losses.
Recovering stolen cryptocurrency is no easy feat, but it’s not entirely hopeless either. By taking immediate action, leveraging blockchain tools, and engaging with experts, you can increase your chances of recovering your funds. Most importantly, prioritize prevention by adopting stringent security measures. Remember, in the world of cryptocurrency, staying one step ahead of scammers is your best protection.
Contact Info: Email: - [email protected]
2 notes
·
View notes
Text

(actually yknow what i also want to dump a few thonkies abt yully too now lmao
though im still debating if i really want to incorporate these thonkies as proper hcs for her - it makes her feel a little too op in a way......... - but im also really leaning to doing it anyway bc this really is the kinda bs she would pull off ydgsyugdsudsgdusy)
so anyway, i think baby yully was rather nuts and kept smashing babylonia's security systems to pieces
like ive already put down that she had a habit of coding programs throughout her childhood, and i definitely did say that these programs were for cracking and copying the civilian databases. bc she was so determined to confirm if there were any Very Specific people in babylonia, so ofc, the logical thing is to get the conveniently-already-existing pool of population data for her to sort through.
but yully being yully, she wouldn't want a bunch of statistics alone. she needs as much data as possible - reports and profiles and notes, doctors' notes and school reports and whatever document there ever was, everything! so that she can cross-check the info to the last detail, analyze to the closest decimal of accuracy.
and she won't stop at just civilian data either. constructs count too. the deceased count too.
so she would collect death records and military profiles too. and considering with constructs at least, how even the military lies to itself internally - she wouldn't quite be satisfied with merely a checkmark of someone being dead. no, she would need the full story, so that she can fully and accurately reconstruct an individual's life—history, personality, beliefs; their full identity and mannerisms and mindset—as part of her own cross-referencing and analyzing procedures.
and this is all, at the very least, in the form of encrypted data - if not behind several layers of cybersecurity under Gestalt's supercomputer watch too.
Yulia wouldn't care though. she wants that info. who cares if she's like, 10 yrs old with negative zero chances of being able to hack into god damn Gestalt with her little civilian baby terminal. she needs that information for her goals. she fucking wants it.
and she has never felt something so viciously unrelenting in her life and the life before.
in a way, it feels like a very simple, logical A to B to C process for her. she feels a want, thinks about doing a thing to satisfy that want, and then simply executes.
obstacles or roadblocks or government personnel coming to her house and asking if they can inspect everyone's terminals for "important grown up reasons" aka bc they traced her hacking attempts there? (though they never actually figure out it's her specifically, partly bc child bias, partly bc the exact terminal she used has already been trashed to pieces or surgically taken apart so it doesn't exist anymore). that's all just par the course. irrelevant bc she already expected as much, so she simply needs to work with such things.
(though of course, it does hinder her in terms of efficiency to keep needing to devote time to misdirecting people's attention from her. so she would also develop methods to avoid being traced, at least not so easily - spoofing signals, false trails, falsifying credentials, coding even shit like rootkits and keyloggers, and then going the extra mile with bs like destroying or dismantling or replacing her hardware constantly, as well as even coming up with alibis for every moment she spends doing her very illegal endeavour
she's still considered a kid at this point so ofc she has all this damn free time to do all this nonsense too)
in any case, here's where im really getting at with this thonk -
Yulia going absolute ham collecting as much top-secret info in the most illegal ways means she has quite likely seen a lot of very restricted things within the government's databases. from the lying propaganda used on Constructs such as the lie of recalls, to the confidential and troubling life histories of particular Constructs such as Bianca or Kamui (or Camu rather).
ofc she probably hasn't seen Everything - but she's seen a Lot more than she, an otherwise very ordinary civilian, should by the time she's even enrolled into military college.
which is stupid nuts and also very OP of her in a broader context and mmmmmmmmmmm i don't Want her to come across as stupidly omniscient in a sense - also it's a little nuts to think that even if she's stupid intelligent and determined, that she'd able to accomplish something as difficult as hacking into hecking Gestalt or whatever government systems with the info she wants.
but at the same time..... ughhh.................... she Is stupid smart alright. and that's without fully using her brain. if she actually put her entirety into some task, she is absolutely supposed to be unholy Scary(TM).
but waaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaah thats toooooo muchhhhhhhhhhhhhhhhhhhh lies down)
#muse ; yulia#ooc ;#(YULLY IS SO NUTS YOU GUYSSSSSSSSSSSSSSSSS but i feel like itd be overstepping of me to write just how nuts shes willing to be...)
4 notes
·
View notes
Text
How can criminals bypass multi-factor authentication (MFA)?

Multi-Factor Authentication (MFA) has long been hailed as the cybersecurity savior. By adding an extra layer of verification beyond just a password – typically a code from an app, a fingerprint, or a security key – MFA drastically reduces the risk of account compromise. For years, it was considered virtually unhackable, making it the bedrock of digital security for individuals and organizations alike.
But in 2025, the cybersecurity landscape has evolved. While MFA remains an absolutely critical defense, sophisticated criminals are finding increasingly clever ways to circumvent it. The illusion of MFA being an impenetrable fortress is a dangerous one. Understanding these bypass techniques is the first step in truly fortifying your digital castle.
MFA: The Unsung Hero (and Its Evolving Limitations)
MFA is effective because it relies on different "factors" of authentication:
Something you know (password, PIN)
Something you have (phone, hardware token)
Something you are (biometrics like fingerprint, face scan)
By requiring at least two of these, MFA makes it exponentially harder for an attacker to gain access, even if they steal your password. However, criminals don't just give up; they adapt. And their adaptation strategies are getting alarmingly good.
The New Playbook: Top MFA Bypass Techniques
Phishing & Interception (Man-in-the-Middle/Adversary-in-the-Middle):
How it Works: This is arguably the most common and effective bypass. Attackers create incredibly realistic fake login pages that act as a proxy. When you try to log in, your credentials and your MFA code are intercepted in real-time by the attacker's server, which then immediately uses them to log into the legitimate site. You log in, oblivious, while the attacker gains access. Tools like Evilginx and Modlishka automate this process.
Why it Works: It exploits human trust and a lack of meticulous URL vigilance. You see a familiar login screen and trust the padlock icon, not noticing the subtle fake domain.
MFA Fatigue / Push Bombing:
How it Works: Attackers, having somehow obtained your username and password (e.g., from a breach), repeatedly send MFA push notifications to your device. They hope you'll eventually approve one out of annoyance, distraction, or confusion (e.g., "Oh, my VPN software is acting up again, must be a prompt from that").
Why it Works: It preys on human psychological factors like frustration, habit, and a desire to make pop-ups disappear.
SIM Swapping (or SIM Jacking):
How it Works: This targets SMS-based MFA. Attackers trick your mobile carrier (often through social engineering or bribing an insider) into transferring your phone number to a SIM card they control. Once they own your number, they receive all your SMS messages, including MFA codes for banking, email, and other services.
Why it Works: It exploits weaknesses in the customer verification processes of mobile service providers.
Session Hijacking / Cookie Theft:
How it Works: MFA secures the initial login. Once you're authenticated, your browser stores a session cookie that keeps you logged in. Attackers can steal this cookie (e.g., via sophisticated malware, Cross-Site Scripting (XSS) attacks on vulnerable websites, or compromised public Wi-Fi) and then use it to bypass the login process entirely, directly accessing your authenticated session.
Why it Works: MFA doesn't protect the ongoing session itself.
Social Engineering (Human Factor Exploitation):
How it Works: This is the most versatile bypass. Attackers manipulate individuals (e.g., help desk staff, IT support, or even the target directly) into resetting MFA, divulging MFA codes, or disabling security features. They might impersonate the target, a legitimate authority figure, or IT support.
Why it Works: It exploits human psychology – trust, the desire to be helpful, fear, or a perceived sense of authority.
Malware & Keyloggers:
How it Works: If malicious software is installed on your device, it can capture credentials and MFA codes as they are entered. More advanced malware can even create a backdoor that bypasses MFA entirely by leveraging compromised system privileges.
Why it Works: The endpoint itself is compromised, allowing the malware to control or observe authentication processes.
Strengthening Your MFA Defense: Beyond the Basics
While these bypasses sound intimidating, implementing a multi-layered defense strategy can significantly reduce your risk.
Prioritize Phishing-Resistant MFA:
Security Keys (FIDO2/WebAuthn): These are the gold standard. Devices like YubiKey or Google Titan Key verify the legitimate website's origin cryptographically, making phishing pages ineffective.
App-Based Authenticator Apps (TOTP): Use apps like Google Authenticator or Microsoft Authenticator. These generate time-based one-time passwords (TOTP) that change every 30-60 seconds and are more secure than SMS codes.
Avoid SMS/Email MFA where possible: While better than nothing, SMS and email are the least secure forms of MFA due to susceptibility to SIM swapping and phishing.
Unwavering User Education & Awareness:
Check URLs Meticulously: Train yourself and your team to always inspect the full URL of a login page. Look for subtle misspellings, extra words, or unusual domains before entering any credentials.
Never Approve Uninitiated MFA Prompts: If you receive an MFA push notification that you didn't initiate, deny it. This is crucial for stopping MFA fatigue attacks.
Be Skeptical of Urgency: Phishing attacks thrive on creating panic. Any unexpected message or call demanding immediate action, especially involving sensitive data or money, should be treated with extreme suspicion.
Implement Robust Anti-Phishing Controls:
For organizations: Deploy advanced email gateway solutions, DNS filtering, and browser extensions that warn users about suspicious sites.
For individuals: Use reputable anti-phishing browser extensions and keep your browser updated.
Robust Endpoint Security:
Keep your operating system and all software (web browsers, applications, antivirus) up-to-date with the latest security patches. This prevents malware and exploitation of system vulnerabilities.
Use a reputable antivirus/anti-malware solution with real-time protection.
Monitor for Anomalies (Especially for Organizations):
Implement security monitoring tools to detect unusual login locations, repeated failed MFA attempts, sudden MFA registration changes, or suspicious network activity from authenticated users.
Strong Internal Policies (For Organizations):
Establish and strictly enforce rigorous identity verification processes for help desk staff when users request MFA resets or account access. Regularly audit these processes.
MFA is an essential component of modern cybersecurity, but it is not a silver bullet. As criminals evolve, so must our defenses. By understanding their tactics and adopting a multi-layered approach that combines strong MFA implementations with continuous user education, robust endpoint security, and vigilant monitoring, we can collectively make it significantly harder for attackers to breach our digital fortresses. Stay informed, stay skeptical, and stay secure.
0 notes
Text
youtube
How These Dangerous Hacking Gadgets Work In this eye-opening video, we reveal how the most dangerous hacking gadgets work—real-world tools used by cybercriminals, hackers, and even surveillance agencies to bypass security, steal private data, and hijack digital systems. These aren’t fantasy—they're real hacking devices like the WiFi Pineapple, USB Rubber Ducky, Flipper Zero, RFID cloners, IMSI catchers, and more. You’ll learn how these physical cybersecurity threats are used to execute silent cyberattacks in coffee shops, airports, corporate offices, and even your home. We explain the inner workings of each gadget and show how they manipulate systems, intercept data, and exploit human trust. ⚠️ Featuring top hacker tools in 2025: ● WiFi Pineapple: Creates fake WiFi networks to steal your data ● USB Rubber Ducky: Looks like a flash drive, acts like a malicious keyboard ● Flipper Zero: A hacker’s Swiss Army knife—RFID, NFC, Bluetooth exploits ● RFID/NFC Cloners: Steal contactless card info in seconds ● Bash Bunny: Smart USB payload delivery tool ● LAN Turtle: Creates a stealthy backdoor into networks ● Hardware Keyloggers: Record every keystroke without software ● Hidden Camera Pens: Discreet surveillance in a writing pen ● IMSI Catcher (Fake Cell Tower): Hijacks mobile signals, intercepts calls and texts 🔐 Whether you're into ethical hacking, penetration testing, or just want to stay safe in the modern world, this is your ultimate guide to understanding the hardware behind real cyber threats. 📌 Learn: ● How hacking gadgets bypass firewalls and antivirus ● How cybercriminals deploy tools in public spaces ● How to detect and defend against these hacker devices ● What tools red teamers and black hat hackers use 💬 Tell us in the comments: Which device shocked you the most? 👍 Like this video if it opened your eyes to the dark side of tech. 📲 Subscribe for deep dives into banned gadgets, spy devices, and real hacking tools used in today’s digital espionage. #HackingGadgets #Cybersecurity #FlipperZero #WiFiPineapple #USBRubberDucky #PenetrationTesting #InfoSec #RedTeam #RFIDCloning #IMSIcatcher #EthicalHacking #SpyGadgets #DarkWebTools #Hackers #TechExplained #GadgetReview #HowHackersWork #2025Tech 🔗 Stay Connected With Us. 🔔𝐃𝐨𝐧'𝐭 𝐟𝐨𝐫𝐠𝐞𝐭 𝐭𝐨 𝐬𝐮𝐛𝐬𝐜𝐫𝐢𝐛𝐞 𝐭𝐨 𝐨𝐮𝐫 𝐜𝐡𝐚𝐧𝐧𝐞𝐥 𝐟𝐨𝐫 𝐦𝐨𝐫𝐞 𝐮𝐩𝐝𝐚𝐭𝐞𝐬. https://www.youtube.com/@NewTechEras/?sub_confirmation=1 📩 For business inquiries: [email protected] ============================= 🎬Suggested videos for you: ▶️ https://www.youtube.com/watch?v=Y1ScCL3i1L4 ▶️ https://www.youtube.com/watch?v=cPnDfL8BREo ▶️ https://www.youtube.com/watch?v=r5pXurOg_DE ▶️ https://www.youtube.com/watch?v=89khi9VSlik ▶️ https://www.youtube.com/watch?v=cAH4eNh_YrQ ================================= 🔎 Related Phrases: 5 Robotic Animals That Will Revolutionize The Future Of Robotics, Robotic Animals, Future Robotics, MIT Mini Cheetah, Mxphoenix Hexapod, Stickybot, Titanoboa Robotic Snake, Robotic Pets, Underwater Robots, AI Companions, Robot Design, AI Robots, Future Technology, DIY Robots, MIT Robots, Harvard Robots, Robot Mobility ADD HASHTAG HERE https://www.youtube.com/watch?v=BvIEjWXqV40 via New Tech Eras https://www.youtube.com/channel/UCSE8xrlzKeYtXIUS2aeV1Lw June 11, 2025 at 04:53AM
#bannedgadgets#truckgadgets#cooltruckinventions#futuretech#aIgadgets#innovation#smartdevices#nextgentech#techreview#Youtube
1 note
·
View note
Text
Employee Tracking And Keyloggers: Finding The Right Balance

Employee tracking software has become a standard in the digital workplace. As businesses strive to boost productivity, safeguard sensitive data, and manage remote teams, tools like keylogger trackers have gained traction. But while these tools offer deep insights, they also raise important questions around ethics, privacy, and trust.
So how can companies leverage keylogger software effectively—without crossing the line?
Let’s explore how to strike the right balance between employee monitoring and personal privacy.
What Are Keylogger Trackers?
At their core, employee keylogger trackers record every keystroke made on a computer or device. These trackers can capture:
Typed emails
Search engine queries
Documents being written
Chat or messaging activity
Some platforms go further, integrating keyloggers with screen recordings, app usage logs, and real-time productivity analytics.
They can be powerful—but potentially invasive—if not used properly.
Why Businesses Use Keyloggers

There are many legitimate reasons why companies turn to Record keystrokes software:
✅ Productivity Monitoring
Are employees spending time on tasks that matter? Are workflows efficient? Keyloggers help answer those questions with real data.
✅ Security Protection
From accidental data leaks to intentional insider threats, keyloggers can help detect red flags early—before damage is done.
✅ Compliance and Auditing
Some industries require extensive documentation of work-related communications or digital activities. Keyloggers offer a way to log those details.
✅ Remote Workforce Oversight
For fully remote or hybrid teams, keyloggers provide visibility that helps keep everyone accountable and aligned.
Best Practices: Balancing Monitoring with Trust

To use keyloggers responsibly and effectively, follow these key principles:
1. Be Transparent
Always notify employees if you plan to use employee monitoring software. Let them know:
What is being tracked
Why it’s being tracked
How the information will be used
Transparency not only ensures legal compliance but also helps build trust with your team.
2. Define Clear Policies
Document your monitoring policy in employee handbooks. Set expectations for device use, work hours, and acceptable digital behavior. Make sure policies are easy to understand and available to all employees.
3. Respect Personal Boundaries
Use software that allows you to exclude personal apps, password fields, or non-work-related websites. Avoid logging personal communication unless explicitly necessary and legally permitted.
4. Limit to Work Devices and Hours
Tracking personal devices or after-hours activity is a surefire way to violate privacy. Only use keyloggers on company-owned hardware, and set clear boundaries on when tracking is active.
5. Use Data to Empower, Not Punish
The goal is improvement—not punishment. Use the insights from tracking to:
Offer training
Support performance reviews
Optimize workflows
Recognize hard work
When used for coaching instead of surveillance, keyloggers become a tool for growth.
You can also watch: EmpMonitor: Manage Remote Work Easily
youtube
Final Thoughts
Employee tracking and keylogger aren’t inherently bad—but they must be used thoughtfully. The line between monitoring and micromanaging can be thin, but with the right strategy, you can ensure both productivity and privacy are protected.
#keystroke recorder#keystroke monitoring software#software to record keystrokes#record keystrokes#keystroke monitoring#Youtube
1 note
·
View note
Text
Ensuring the Secure Storage of Cryptocurrencies
Cryptocurrencies have rapidly become a significant asset class, drawing both retail and institutional investors worldwide. With this surge in popularity comes an increasing need to ensure that these digital assets remain secure. Unlike traditional assets stored in banks or financial institutions, cryptocurrencies are held in digital wallets, which can be vulnerable to various security threats if not managed properly.
This article explores the best practices for safely storage of cryptocurrencies, discusses the types of wallets available, and provides actionable tips to minimize risk, all while remaining compliance-friendly and geared toward educating you on best practices in digital asset security.
Understanding the Storage of Cryptocurrencies:
At its core, storage of cryptocurrency is about safeguarding the private keys that grant access to your digital assets. In the world of cryptocurrencies, a private key is essentially a password that allows you to control and transfer your funds.
Without proper storage, if a hacker gains access to your private key, they can irreversibly transfer your assets to their own account. Unlike traditional banking systems, there is no central authority to reverse fraudulent transactions or recover lost funds, which makes secure storage absolutely crucial.
The Importance of Securing Digital Assets
1. Irreversibility of Transactions:
Cryptocurrency transactions are generally final and cannot be reversed once confirmed. This means that if your wallet is compromised, there is little to no recourse.
2. Decentralized Nature:
The decentralized structure of most cryptocurrencies means that there is no oversight by any government or regulatory body. This autonomy gives you complete control but also places the responsibility for security solely in your hands.
3. High-Value Target:
As cryptocurrencies become more mainstream, cybercriminals are increasingly targeting digital wallets with sophisticated attacks such as phishing, malware, and hacking.
By understanding these fundamentals, you can appreciate why implementing robust security measures is essential for protecting your digital wealth.
Assessing the Risks Associated with Storage of Cryptocurrencies
The digital nature of cryptocurrencies exposes them to several security risks. It’s important to be aware of these threats to take proactive steps in mitigating them.
1. Common Threats
1. Hacking and Malware:
Cybercriminals use various methods to breach wallet security. Malware, keyloggers, and other malicious software can capture your private keys or login credentials.
2. Phishing Attacks:
Fraudsters often send emails or create fake websites that mimic legitimate cryptocurrency platforms to trick you into revealing your private information.
3. Physical Theft:
For hardware wallets or paper wallets, physical theft is a possibility if your storage device or printed keys are not kept in a secure location.
4. Human Error:
Simple mistakes, such as misplacing a backup phrase or accidentally sharing sensitive information, can lead to significant losses.
2. Mitigation Strategies
Understanding these risks allows you to better prepare and implement multiple layers of security. Employing strong passwords, utilizing two-factor authentication (2FA), and keeping software updated are just a few ways to reduce your vulnerability. Additionally, the method you choose to store your cryptocurrency can significantly influence your security posture.
Types of Wallets: Choosing the Right Storage Option
There are several types of wallets available, each offering different levels of security, convenience, and control. Selecting the right wallet for your needs depends on factors such as how often you transact, the amount of cryptocurrency you hold, and your comfort level with technology.
1. Hot Wallets
Definition:
Hot wallets are connected to the internet, making them easily accessible for day-to-day transactions. Examples include mobile apps, desktop software, and online exchanges.
Advantages:
Convenience: They are ideal for active trading and regular use.
Ease of Use: User-friendly interfaces and quick access to funds.
Disadvantages:
Security Risks: Being online exposes these wallets to hacking attempts, malware, and phishing scams.
Third-Party Vulnerabilities: If using an exchange wallet, you are entrusting a third party with the custody of your assets, which can be risky if that service experiences a security breach.
Best Practices for Hot Wallets:
Enable Two-Factor Authentication (2FA): This adds an extra layer of security.
Regularly Update Software: Ensure that your wallet application and device are up-to-date with the latest security patches.
Use Strong, Unique Passwords: Avoid reusing passwords across multiple platforms.
Limit Funds Stored Online: Only keep an amount that you are comfortable risking for daily transactions.
2. Cold Wallets
Definition:
Cold wallets are offline storage solutions that significantly reduce exposure to online threats. They are ideal for long-term storage of cryptocurrencies.
Types of Cold Wallets:
Hardware Wallets: These are physical devices that securely store your private keys offline. They usually come in the form of USB-like gadgets.
Paper Wallets: A paper wallet involves printing out your public and private keys on paper and storing them securely.
Advantages:
Enhanced Security: Being offline, cold wallets are immune to online hacking attempts.
Control Over Private Keys: You have full control over your keys without relying on a third party.
Disadvantages:
Convenience: Cold wallets are less convenient for regular transactions as you must connect them to an internet-enabled device when making transfers.
Risk of Physical Loss: The security of cold wallets is only as strong as the physical security measures you take. Loss, damage, or theft of the device or paper can result in the loss of your assets.
Best Practices for Cold Wallets:
Secure Physical Storage: Keep hardware wallets and paper wallets in secure, locked locations or even a safe deposit box.
Backup Your Recovery Seed: Always have a backup of your recovery seed in a separate, secure location. Never store it digitally or share it with anyone.
Test Your Recovery Process: Periodically test your recovery process to ensure that you can restore access if needed.
3. Hardware Wallets
Overview:
Hardware wallets like Ledger and Trezor are among the most popular options for secure storage of cryptocurrencies. They offer a balance between security and convenience for those who occasionally transact.
Security Features:
Offline Storage: Private keys are generated and stored offline.
PIN Protection: Most hardware wallets require a PIN to access the device.
Recovery Phrases: These devices provide a recovery phrase during setup, which can be used to restore your wallet if the device is lost or damaged.
Usage Tips:
Purchase from Reputable Sources: Always buy hardware wallets directly from the manufacturer or trusted vendors to avoid counterfeit devices.
Keep Firmware Updated: Regular updates can patch vulnerabilities and improve security.
Store the Recovery Phrase Securely: Consider using a fireproof and waterproof safe for storing your recovery phrase.
4. Paper Wallets
Overview:
A paper wallet is one of the simplest forms of cold storage. By printing out your public and private keys, you create an offline record that can be stored safely.
Advantages:
No Digital Footprint: With no digital data, paper wallets are not susceptible to online hacks.
Cost-Effective: They require minimal technical setup and are inexpensive.
Disadvantages:
Fragility: Paper can deteriorate over time, be damaged by water, fire, or even simple mishandling.
No Built-In Security: Paper wallets do not offer password protection or encryption, so physical security is paramount.
Best Practices:
Lamination and Storage: Consider laminating your paper wallet and storing it in a secure, fireproof location.
Multiple Copies: Make more than one copy and store them in geographically separate secure locations.
Keep It Offline: Never take a digital copy of your paper wallet; always generate it offline and print it from an isolated machine.
Best Practices for Secure Storage of Cryptocurrency
Securing your cryptocurrency isn’t solely about choosing the right type of wallet—it also involves ongoing practices and precautions. Here are some key strategies to ensure your digital assets remain safe:
1. Implement Multi-Factor Authentication (MFA)
Why It Matters:
Multi-factor authentication, such as combining a password with a secondary authentication method (like a mobile device code or biometric data), significantly reduces the risk of unauthorized access.
Actionable Steps:
Enable 2FA on All Platforms: Whether using hot or cold wallets, ensure that any platform you access online requires MFA.
Use Authenticator Apps: Prefer authenticator apps over SMS-based 2FA, as these are generally more secure.
2. Keep Your Software and Firmware Updated
Why It Matters:
Regular updates to wallet software and hardware firmware can patch vulnerabilities and protect against emerging threats.
Actionable Steps:
Regular Checks: Periodically check for updates from the wallet provider.
Automatic Updates: Where possible, enable automatic updates to minimize the risk of running outdated software.
3. Secure Your Private Keys and Recovery Phrases
Why It Matters:
The security of your private keys and recovery phrases is paramount, as they grant access to your assets.
Actionable Steps:
Never Share Your Keys: Keep your private keys and recovery phrases confidential.
Offline Storage: Store these details offline in secure, physical locations.
Redundancy: Maintain multiple backups in separate secure locations to prevent total loss in case one backup is compromised.
4. Diversify Your Storage Solutions
Why It Matters:
Relying on a single storage method can be risky. Diversification can reduce the impact of a single point of failure.
Actionable Steps:
Use a Combination of Wallets: Consider splitting your assets between hot wallets for daily use and cold wallets for long-term storage.
Geographical Distribution: If possible, store backup copies of recovery phrases in different physical locations to mitigate risks such as theft, fire, or natural disasters.
5. Educate Yourself and Stay Informed
Why It Matters:
The cybersecurity landscape is continuously evolving, with new threats emerging regularly. Keeping up-to-date with the latest developments can help you anticipate and mitigate risks.
Actionable Steps:
Follow Trusted Sources: Stay informed by following reputable cryptocurrency news outlets, security blogs, and forums.
Participate in Communities: Engage with the cryptocurrency community to share experiences and learn about best practices from peers.
Regular Security Audits: Periodically review your security setup to identify and address any potential weaknesses.
Advanced Security Measures
For those with significant holdings or a strong interest in maximizing security, additional measures can provide extra layers of protection.
1. Multi-Signature Wallets
Overview:
Multi-signature (multi-sig) wallets require multiple private keys to authorize a transaction. This means that even if one key is compromised, unauthorized transactions are unlikely to occur.
Benefits:
Enhanced Security: Adds redundancy by requiring multiple confirmations.
Shared Control: Useful for organizations or joint accounts where multiple approvals are needed before transactions are executed.
Considerations:
Complexity: Multi-sig setups can be more complex to configure and manage.
Backup Coordination: Ensure that all parties involved understand how to secure and back up their individual keys.
2. Using Encryption and Secure Communication Channels
Overview:
Encryption can protect your wallet files and communications related to cryptocurrency transactions. Whether you are sending data over the internet or storing sensitive files on your computer, robust encryption methods are essential.
Best Practices:
Encrypt Wallet Backups: Use strong encryption (such as AES-256) to secure backup files containing private keys or recovery phrases.
Secure Messaging Apps: When discussing sensitive information related to your cryptocurrencies, use encrypted messaging platforms.
VPN Usage: Consider using a Virtual Private Network (VPN) when accessing online wallets or exchanging information, particularly on public networks.
3. Physical Security and Disaster Preparedness
Overview:
While digital measures are crucial, physical security should not be overlooked. Ensure that the hardware or paper wallets storing your private keys are physically secure.
Best Practices:
Safe Storage: Use safes or secure deposit boxes to store hardware wallets, paper wallets, and backup copies of recovery phrases.
Disaster Recovery Planning: Have a clear plan for recovering your assets in the event of a disaster. This includes knowing where your backups are stored and ensuring that trusted individuals are aware of your storage locations (while keeping the details confidential).
The Human Element: Avoiding Common Pitfalls
Even with the best technology, human error remains a significant risk factor. Understanding and mitigating these risks is as crucial as deploying the latest security measures.
Recognize and Avoid Phishing Attempts
Overview: Phishing remains one of the most common methods by which attackers attempt to steal your credentials. Fraudsters create fake websites, send misleading emails, or use social engineering tactics to trick you into revealing your sensitive information.
Tips:
Verify URLs: Always check the URL of websites before entering any credentials. Bookmark trusted sites for easy reference.
Suspicious Emails: Be cautious with unsolicited emails that ask for personal information, especially if they mimic your wallet provider’s style.
Educate Yourself: Regularly review updated information on common phishing tactics within the cryptocurrency community.
Maintain a Healthy Skepticism Toward “Too-Good-To-Be-True” Offers
Overview:
Scammers often lure individuals with promises of high returns or exclusive access to investment opportunities. A healthy level of skepticism is essential.
Tips:
Do Your Own Research (DYOR): Always investigate before investing or sharing personal details.
Verify Credentials: Only use services and wallets from reputable, well-reviewed sources.
Beware of Social Engineering: Recognize that no legitimate entity will pressure you to bypass security measures or share private keys.
Storage of cryptocurrencies safely is a multifaceted process that combines technology, best practices, and ongoing vigilance. Whether you opt for hot wallets for daily transactions or cold storage for long-term holding, the key to security lies in understanding the risks and implementing layered protection strategies. Employ multi-factor authentication, keep your software up-to-date, and never compromise on the secure handling of your private keys and recovery phrases.
Remember, no single solution is foolproof. Diversification of storage methods—using a mix of hot and cold wallets—along with advanced techniques such as multi-signature wallets and robust encryption, will provide the best defense against the ever-evolving threat landscape.
As the storage of cryptocurrencies continues to develop, so too will the methods employed by cybercriminals. Staying informed, maintaining a skeptical mindset toward suspicious offers, and periodically reviewing your security setup are essential habits that every cryptocurrency holder should adopt.
0 notes
Text
Trezor.io/start - Starting Up Your Device | Trezor®
Introduction to Trezor.io/start
Are you looking for a secure way to store your cryptocurrency? Trezor.io/start is the official setup portal for Trezor hardware wallets. Whether you’re a beginner or an experienced crypto user, this guide will walk you through the setup process, security measures, and benefits of using a Trezor device.
Why Choose Trezor Hardware Wallet?
Trezor is a leading hardware wallet that ensures maximum security for your digital assets. By using Trezor.io/start, you can:
Protect your cryptocurrencies from hackers and phishing attacks.
Securely manage Bitcoin, Ethereum, and over 1,000 other digital assets.
Enjoy an easy-to-use interface with top-notch security features.
How to Set Up Your Trezor Wallet via Trezor.io/start
Setting up your Trezor wallet is simple and can be done in a few steps:
Step 1: Visit Trezor.io/start
Go to Trezor.io/start using a secure web browser. Ensure you are on the official website to avoid phishing scams.
Step 2: Connect Your Trezor Device
Plug in your Trezor hardware wallet to your computer or mobile device via USB. The device will prompt you to follow the on-screen instructions.
Step 3: Install Trezor Suite
Download and install the Trezor Suite, the official app for managing your crypto wallet securely.
Step 4: Create a New Wallet or Recover an Existing One
If you’re new, create a wallet and note down the recovery seed securely.
If restoring an old wallet, enter the recovery seed carefully.
Step 5: Secure Your Wallet
Set up a strong PIN to prevent unauthorized access.
Keep your recovery seed in a safe place, as it is essential for wallet recovery.
Benefits of Using Trezor.io/start
Enhanced Security: Protects against malware and keyloggers.
User-Friendly Interface: Easy navigation for beginners and experts.
Wide Compatibility: Supports multiple cryptocurrencies and platforms.
Conclusion
Trezor.io/start is your go-to platform for setting up and securing your Trezor hardware wallet. Protect your digital assets today by following the simple steps outlined above. Visit Trezor.io/start to get started!
0 notes
Text
Mastering Bitcoin Security: Protecting Your Wealth in the Digital Age

We know how important it is to secure digital assets, especially Bitcoin. Private keys and Bitcoin addresses are essential for safe transactions and managing your wealth. To ensure Bitcoin's safety, it's important to understand its security basics, recognize potential threats, and follow protective steps for safe use and storage.
Bitcoin security primarily revolves around managing private keys, which are essential for accessing and controlling your Bitcoin. These keys must be kept secure from cyber threats such as phishing, malware, and keyloggers, which can expose your private information.
Understanding the Fundamentals of Bitcoin Security
To use Bitcoin safely, it's crucial to understand its security fundamentals. Bitcoin wallets play a major role in this, and there are two main types: hot wallets and cold wallets.
Hot Wallets are connected to the internet, providing easy access to your Bitcoin for daily transactions but making it more vulnerable to cyberattacks.
Cold Wallets are offline, offering greater protection by being disconnected from the internet. These are ideal for long-term storage.
The key to Bitcoin security is choosing the right wallet and maintaining safe practices, such as safeguarding private keys and avoiding phishing attacks. Additionally, it's vital to stay updated on security best practices and any new threats.
Bitcoin Cold Storage vs Hot Wallet: Which is Right for You?
When storing Bitcoin, understanding the difference between cold storage and hot wallets is essential.
Cold Storage refers to offline solutions like hardware wallets and paper wallets. These are ideal for secure long-term storage as they’re not connected to the internet, reducing the risk of hacking.
Hot Wallets include mobile, desktop, and web-based wallets, allowing quick access to Bitcoin but being more vulnerable to cyber threats.
For the most secure setup, use a combination of both: hot wallets for daily transactions and cold storage for long-term savings.
How to Use & Store Bitcoin Safely: Essential Guidelines
When using and storing Bitcoin, choosing the right wallet is key. Bitcoin wallets come in two forms: hardware and software wallets. Hardware wallets, which cost between $50 and $250, offer secure long-term storage, while software wallets are free but come with higher risks.
To maximize security, follow these tips:
Choose a trusted wallet provider
Enable two-factor authentication (2FA) for extra protection
Keep private keys and seed phrases safe and offline
Use cold storage for long-term Bitcoin storage
With these precautions, you can ensure the safety of your Bitcoin.
Choosing the Right Bitcoin Wallet
Selecting the right Bitcoin wallet depends on your needs. Popular wallets include:
Coinbase, eToro, Uphold: These are great for beginners due to their user-friendly interfaces.
Ledger, Trezor: Leading hardware wallets for offline storage, offering top-notch security features.
When comparing wallets, look for secure storage, ease of use, and reasonable fees. If you’re serious about security, consider using hardware wallets, which store private keys offline and offer strong protection from hacking.
How to Secure Bitcoin on a Ledger Nano S
The Ledger Nano S is one of the most secure hardware wallets for Bitcoin. Here’s how to set it up for maximum protection:
Initialize the device: Follow the setup instructions and generate a unique seed phrase.
Safeguard your seed phrase: Write it down and store it securely offline.
Set a strong PIN code: Use a non-predictable, strong PIN.
Update firmware regularly: Keep your device’s firmware up to date to prevent vulnerabilities.
Using a hardware wallet like Ledger Nano S minimizes exposure to online threats.
Best Bitcoin Wallets for Android in 2024
For Android users, top-rated Bitcoin wallets include:
Trust Wallet: Known for its ease of use and solid security features.
Mycelium: Provides advanced security and privacy controls.
Electrum: A trusted Bitcoin wallet with hardware wallet integration.
These wallets offer user-friendly interfaces, multi-signature support, and robust security.
Setting Up Strong Security Measures
To protect your Bitcoin, implement strong security measures. This includes enabling two-factor authentication, using encryption, and combining both hot and cold wallets for better security.
Best Practices for Bitcoin Transactions
When making Bitcoin transactions, always verify the transaction details and the recipient's address. Be mindful of fees, as high fees can increase the cost of transactions.
Using secure storage methods like hardware wallets, which keep private keys offline, ensures that your Bitcoin is well-protected. Additionally, enable two-factor authentication and use strong passwords to further secure your transactions.
Top-Rated Bitcoin Exchanges for U.S. Residents
When buying or selling Bitcoin, choosing a reputable exchange is crucial. Some popular exchanges include:
Coinbase: Known for ease of use and strong security measures.
Kraken: Offers advanced security features and low transaction fees.
Gemini: Provides high-level security, including cold storage for customer funds.
Before selecting an exchange, review its security features and fees to ensure it aligns with your needs.
Advanced Security Protocols for Bitcoin Storage
Bitcoin storage security is essential to protect your assets. Key security protocols include:
Multi-factor authentication: Adds extra layers of protection.
Backup plans: Always back up your private keys in secure locations.
Recovery options: Have a recovery plan in case of emergency.
Using hardware wallets and advanced security services like vaults with multi-signature features can greatly enhance your Bitcoin security.
Protecting Your Bitcoin from Hackers
To protect your Bitcoin from hackers, follow these steps:
Use two-factor authentication (2FA) to block unauthorized access.
Never store private keys online; use encrypted backups.
Set up alerts for unusual account activity.
Avoid public Wi-Fi when accessing your wallet.
By taking these precautions, you can safeguard your Bitcoin from hackers and minimize your exposure to cyber threats.
Safest Way to Store Bitcoin Long Term
For long-term Bitcoin storage, cold storage solutions such as hardware wallets and paper wallets are the safest options. These offline solutions protect private keys from cyber threats.
When choosing a hardware wallet, look for devices like the Ledger Nano X or Trezor Model T, which feature advanced security protocols and recovery options.
Protecting Your Bitcoin from Cyber Threats
Cyber threats are a significant concern for Bitcoin holders. Protect your Bitcoin by staying informed about threats like phishing, cryptojacking, and ransomware. Use secure exchanges and enable alerts for suspicious activity. Always be cautious of phishing scams and employ good security practices to safeguard your assets.
Maintaining Long-Term Bitcoin Security
For long-term security, a comprehensive strategy is essential. Use cold storage options like Trezor and Coldcard to protect your Bitcoin, and conduct regular security audits to identify potential risks. Always update your wallet software and keep recovery options in place in case of emergency.
Click here to read the full article!
0 notes
Text
What is keystroke technology?

An unsettling subject is beginning to surface around how employers monitor how much or how little employees work. Since remote work became popular during the pandemic and businesses started to worry that they couldn’t physically see employees at desks, there has been an increase in digital monitoring. Many said that, as a result, productivity had decreased. Let’s talk about keystroke technology.
The discussion about the technologies businesses use to monitor worker productivity erupted last week when an Australian lady was let go after their monitoring systems revealed she hadn’t spent enough time typing during the workday. According to Business Insider, the 18-year employee of the insurance company used a keyboard for less than 100 working hours in October and again in November. Suzie Cheikho, the woman, has openly denied the accusations.
What is a keylogger, often a system monitor or keystroke logger?
Keyloggers, or keystroke loggers, are surveillance technologies that track and log every keystroke made on a particular device, like a computer or smartphone. It may be based on software or hardware. The latter kind is sometimes called keyboard capture or system monitoring software.
Why do people use keyloggers?
Cybercriminals frequently employ keyloggers as spyware tools to steal valuable company data, login credentials, and personally identifiable information. Nevertheless, there are a few applications for keyloggers that, in specific contexts, might be deemed suitable or moral. Keyloggers, for example, can also be utilised for the following purposes:
By companies to keep an eye on their workers’ computer usage.
Parents monitor the internet use of their kids.
The owners of gadgets monitor any potential illegal activity on their possessions.
By law enforcement organisations to examine computer-related occurrences.
Keystroke tracking software: What Is It?
Keystrokes on employees’ computers are tracked and recorded using keystroke-tracking technology. It records each keystroke a user makes and generates a comprehensive history of their typing actions.
This kind of software is frequently employed for several objectives, such as:
Workers’ Surveillance
Employers can monitor workers’ productivity and activity by implementing keystroke tracking. It can evaluate how workers allocate their time, pinpoint areas needing development, and guarantee adherence to corporate guidelines.
Online Safety
Keystroke monitoring is one security tool they can use to identify and stop unwanted access. The software can detect unusual activity or efforts to breach passwords and other sensitive data by keeping track of keystrokes.
Investigative Forensics
Keystroke tracking can be used in forensic and legal contexts to examine computer user behaviour and gather evidence for inquiries. In situations involving cybercrime or unauthorised access, it is advantageous.
How does it operate?

“keystroke technology” keeps tabs on and gathers information about how employees utilise computers. It is one of the few technologies available to employers to monitor how employees spend the hours they are expected to work more carefully. It records every keystroke an employee makes on their computer.
Thanks to newer features, administrators can now occasionally snap screenshots of employees’ displays. This is the general operation of keystroke tracking software:
Installation: Keystroke tracking software can be installed remotely using malware, phishing scams, or other techniques, or it can be installed on a computer by someone with physical access. It might be purposefully deployed on rare occasions for monitoring—for example, parental control or staff observation.
Hooking into the Operating System: Keyloggers frequently employ methods like hooking into the keystroke handling mechanism of the operating system. Regardless of the application they type in, it enables them to intercept keystrokes as the operating system processes them.
Recording Keystrokes: When installed and turned on, the keylogger records keystrokes. The keyboard captures every key press, including function keys, letters, numbers, symbols, and special keys like Enter, Backspace, and Delete.
Covert Mode: Numerous keyloggers function in stealth mode, which entails running covertly in the background without the user’s awareness. To evade detection by antivirus software and users, they might conceal their files, processes, and registry entries.
Information Recovery:
A database or log file keeps the logged keystrokes. The individual or organisation that installed the keylogger can access it. The keylogger automatically sends recorded data after recording, according to its settings.
Analysis and Misuse: After recording keystrokes, you can examine the data to extract private information such as credit card numbers, usernames, and passwords. Information misappropriation may occur for financial fraud, espionage, identity theft, or other nefarious reasons.
What Issues Does Keystroke Tracking Have With Controversy?
Someone can use keyloggers or keyboard tracking software for controversial purposes, as they can be employed for good intentions just as easily as bad.The following are some critical issues influencing the dispute:
Keystroke tracking presents serious privacy concerns, particularly when people don’t know their manager monitors their typing habits. The possibility of privacy violation may cause unease and resistance.
Unauthorised SurveillanceWithout express authorization, someone can use keystroke tracking software for unauthorized surveillance. This raises moral concerns regarding private property rights and the limits of appropriate monitoring.
Data Security Risks: The management and storage of keystroke data are risks since unauthorised access may lead to financial fraud, identity theft, or other nefarious acts. The acquisition of data raises concerns about its potential misuse.
Workplace Dynamics: When employees are subjected to keystroke tracking in a work environment, trust between them and their employers may be strained. Open communication about monitoring procedures is necessary for sustaining a pleasant work environment.
Ambiguity in Law and Ethics: The debate highlights the necessity for precise laws and moral principles regulating the use of keystroke tracking. Because technology is constantly changing, it is unclear whether current laws can handle new privacy issues.
What Are the Benefits of Keystroke Tracking Software for Businesses?

The company can benefit from implementing keylogging software in the workplace, but it is important to do so responsibly and in accordance with the law. Here are some things to think about:
Enhanced Protection:
Keylogging software is an essential instrument for strengthening security protocols in an enterprise. Keeping sensitive data from unauthorized access and corruption, we identify and resolve issues such as unauthorized access.
Employee Observation:
Keystroke monitoring by employees offers insightful information on their actions and demeanour at work. Employers can use this data to assess worker productivity, spot patterns in behaviour, and identify areas where workers might need more guidance or instruction.
Compliance and Regulations:
By putting keystroke tracking systems in place, businesses can ensure they abide by legal and industry standards for data security and protection. By adhering to set standards, companies reduce the possibility of incurring fines or legal consequences.
Recognizing Insider Threats:
Keystroke monitoring software is crucial for spotting unusual activity or possible insider threats in a company. Organisations can proactively identify and reduce risks posed by internal actors who could compromise sensitive information or carry out unauthorised operations by analysing keystroke data.
Keylogging is an invaluable instrument for investigative purposes when looking into cybersecurity events, fraud, or other illegal activity. Investigators can successfully support their inquiries by gathering evidence and reconstructing events by capturing extensive information about system activity and user interactions.
Safeguarding Private Information:

Keystroke tracking is critical in protecting confidential data, including passwords and private information, from unwanted access. Organisations can put strong security measures in place to stop data breaches and unauthorised disclosures of private information by monitoring user inputs and interactions.
Concluding
Although there is no denying that keystroke monitoring software improves productivity and strengthens cybersecurity, its use requires careful consideration of both practicality and morality. Protecting personal information and fostering employee trust go hand in hand with the ability to improve security and expedite processes
#keystroke technology#typing analysis#biometric authentication#user behavior#security technology#human-computer interaction#machine learning#data security#password alternatives
0 notes
Text
Hack FB to Monitor Your Partner Without Touching Any Device

Best Way To Monitor Facebook Messenger Without Them Knowing
In today's digital age, relationships have extended beyond the real world into the online space, where social media platforms like Facebook serve as communication hubs for billions of people. With the increasing use of social media, concerns about trust, infidelity, and relationship transparency have also grown. Facebook, being one of the largest social media platforms, is a common platform where suspicious activities may arise. Many individuals, out of concern for their relationships, seek ways to monitor their partner's Facebook activity.
However, before diving into the realm of hack FB, it’s essential to discuss the legal and ethical ramifications involved. Monitoring someone’s Facebook account without their consent is illegal and an invasion of privacy in most jurisdictions. But for the sake of educational purposes, this article will explore the methods and risks associated with monitoring your partner’s Facebook account.
🟨 Why Do People Want to Monitor Their Partner's Facebook?
In any relationship, communication is key. However, when trust starts to erode, partners may become curious or suspicious about their significant other’s online activities. The reasons some people may want to monitor their partner’s Facebook account include:
🔹 Infidelity concerns: One of the main reasons people try to monitor their partner's Facebook account is to catch signs of cheating. Facebook, with its private messages and potential connections with old flames or new acquaintances, can be a hotspot for suspicious interactions.
🔹 Rebuilding Trust: In some cases, after a partner has been caught in dishonest behavior, the other partner may want to monitor their activity to ensure that they are being truthful moving forward.
🔹 Lack of Communication: If there’s a lack of communication in a relationship, one partner may want to check if their significant other is more open and communicative on social media than in real life.
🔹 Safety Concerns: Sometimes, monitoring Facebook is done for safety reasons, such as ensuring a partner isn't communicating with dangerous individuals or getting involved in illegal activities.
While these reasons may seem justified, the ethical considerations of spying on someone else’s Facebook account must be taken into account. Misusing or hacking someone’s account is illegal in many countries, and the consequences of such actions can include criminal charges, fines, and damage to your relationship.
🟨 How People Attempt to Hack FB Accounts
Monitoring Facebook without physically touching your partner’s device might sound like something out of a spy movie, but with advancements in technology, various methods are available that make this possible. Let’s explore some of the most commonly used methods:
#️⃣ Phishing
Phishing is one of the oldest and most widely used hacking methods. Phishing involves creating a fake login page that looks identical to Facebook’s official page. The unsuspecting user, thinking they are logging into their account, enters their credentials, which are then sent to the hacker.
♻ How it works:
The hacker sends the fake login link to the victim via email or social media messages.
The victim clicks on the link and inputs their Facebook credentials.
The hacker receives the credentials and can then log into the victim's account without needing physical access to their device.
🔸 Risks: Phishing can lead to serious consequences not just for the hacker but for the victim as well. If caught, the hacker could face legal penalties. Moreover, phishing schemes are often linked with larger cyber-criminal activities, including identity theft.
#️⃣ Keyloggers
Keyloggers are software or hardware tools that record every keystroke made on a device. Once installed, a keylogger can capture everything your partner types, including Facebook login credentials.
♻ How it works:
A keylogger is either installed remotely (through a malicious email attachment or link) or physically onto the device.
Every time the victim types their Facebook credentials, the keylogger captures it and sends it to the hacker.
🔸 Risks: Keyloggers are illegal in many countries unless used in highly specific and legal circumstances (such as parental control). Using keyloggers for spying can lead to severe legal ramifications.
#️⃣ Spyware Apps
Spyware apps have become highly sophisticated and are widely available online. Some of these apps claim to allow users to monitor social media activity, including Facebook, without the need for physical access to the target device.
Popular spyware apps:
HackersList: One of the most popular spyware apps, HackersList allows you to monitor Facebook messages, calls, texts, and other online activities on the target device. Once installed, the app works invisibly in the background.
♻ How it works:
The hacker sends an installation link to the victim or installs the app manually if they have temporary access to the device.
Once installed, the app can record Facebook messages, keystrokes, and even multimedia, sending all the data to the hacker's control panel.
🔸 Risks: Installing spyware without the knowledge or consent of the user is illegal in most jurisdictions. Furthermore, many spyware apps can compromise your partner’s privacy and security.
#️⃣ Social Engineering
Social engineering is not a technical hacking method but relies on psychological manipulation to trick your partner into revealing their Facebook login credentials. The hacker might pretend to be a Facebook representative or a trusted individual and persuade the target to provide login details.
♻ How it works:
The hacker uses various pretexts (like security issues) to convince the target to share their login information.
They might create fake support emails or messages that look like they come from Facebook.
🔸 Risks: Social engineering can have a devastating impact if detected, and it can lead to severe mistrust and relationship damage. Legal consequences are also possible depending on how far the social engineering tactics are taken.
#️⃣ Password Recovery Exploit
Facebook allows users to recover their password through various means, such as email, SMS, or security questions. Hackers often exploit this feature by trying to reset the password, especially if they know personal information about the target.
♻ How it works:
The hacker attempts to reset the Facebook password by using the “forgot password” feature.
They then gain access to the target’s recovery email or phone to intercept the reset code.
🔸 Risks: This method not only risks damaging the relationship beyond repair but is also considered illegal. It can lead to account suspension and criminal charges for the hacker.
🟨 Why Facebook Monitoring Should Be Avoided
While the above methods might seem enticing to someone suspicious of their partner, the consequences of such actions are far-reaching and can create more harm than good in a relationship. Here are a few reasons why hacking Facebook to monitor your partner should be avoided:
Legal Consequences: Hacking is illegal. If caught, you could face serious charges, including hefty fines and possible jail time. Laws vary by jurisdiction, but in most places, unauthorized access to someone else’s social media accounts is considered a crime.
Privacy Violation: Even if you have concerns about your partner, everyone is entitled to privacy. Violating their privacy by hacking their Facebook can destroy trust and lead to irreversible damage to the relationship.
Emotional Damage: Spying on your partner could damage your emotional well-being. If you’re proven right, it can lead to heartache, and if you're proven wrong, guilt and regret may follow.
Relationship Breakdown: Monitoring your partner’s Facebook without consent can lead to serious consequences within the relationship. Even if you catch them doing something suspicious, the act of hacking could be seen as a betrayal, leading to a potential breakup or divorce.
🟨 Legal Alternatives to Hack FB
If you’re concerned about your relationship and feel the need to monitor your partner, there are several ethical and legal alternatives to hacking that you can consider:
1️⃣ Open Communication
The best way to address any concerns in a relationship is through honest and open communication. Express your feelings to your partner and discuss the issues that are bothering you. Transparency in a relationship can build trust and may help resolve underlying issues without the need for spying.
2️⃣ Couples Therapy
If communication has broken down and you’re struggling with trust, couples therapy may be a beneficial solution. A licensed therapist can provide you and your partner with the tools needed to navigate relationship challenges.
3️⃣ Mutual Facebook Access
If both partners are willing, some couples choose to share their social media passwords as a way to build trust. This can be done voluntarily and with consent, but it should be agreed upon by both individuals.
4️⃣ Monitoring Apps with Consent
If you feel strongly about monitoring, there are apps designed for monitoring with consent, such as parental control apps or those designed for couples. However, both parties must agree to use such tools, and these apps should only be used with consent to avoid ethical or legal concerns.
🟨 What To Do If You Suspect Infidelity
If you suspect your partner of infidelity, you may feel an overwhelming urge to gather evidence by any means necessary. However, resorting to hacking or spying is not the answer. Here are some steps you can take instead:
🔸 Have a Serious Conversation: Discuss your concerns openly with your partner. Ask them to explain any suspicious behaviors you’ve noticed.
🔸 Seek Counseling: If you’re not sure how to approach the issue, seeking professional help from a counselor or therapist can guide you through the conversation.
🔸 Hire a Private Investigator: If you feel your suspicions are well-founded, you might consider hiring a licensed private investigator. While it may seem extreme, this is a legal option that may help you find peace of mind.
🔸 Trust Your Instincts: Sometimes, trust issues go beyond Facebook or any social media platform. If your instincts are telling you something isn’t right, it may be time to re-evaluate the relationship and make decisions based on your overall happiness and well-being.
Private Investigators for Tracing a Person and Phone
🟩 Final Touch
Monitoring your partner’s Facebook account without their consent is not only illegal but also unethical. While the temptation to use hacking methods like phishing, keyloggers, spyware, and social engineering might be high, the consequences of such actions can lead to severe legal ramifications and irreparable damage to your relationship.
Instead of resorting to FB hack, it’s important to approach relationship issues with trust, communication, and honesty. If there are concerns in your relationship, there are healthier and more effective ways to address them than resorting to illegal activities. Your relationship will benefit from transparency, openness, and mutual respect. If trust is eroded, it may be time to either rebuild or move on in a way that’s fair to both parties.
#hack fb messages#Hack FB#facebook hack#facebook hackers#hackers#hackerslist#hacking#hacks#life hacks
0 notes