#how to enable sudo
Explore tagged Tumblr posts
Text
God I hate how normalized not being in control of your own devices has become. My phone updates in the middle of the night without asking me shit or getting my consent for anything and its like "Oh hi I'm your new AI, please enjoy this forced overlay that you can't exit out of until you go through my tutorial"
"Great fuck you, I would like to uninstall you" "Oh I'm sorry you can't uninstall me! I'm a core system application and if you uninstall me your phone won't function correctly despite the fact that I did not exist yesterday and your phone worked fine" "....." "You can disable parts of my functionality but I will always be here and I will pop up notifications asking you to re-enable me unless you figure out how to disable those too! Then I will still show up in a different color at the top of your settings application telling you that you need to 'fix" a 'problem' with your phone, that problem being that I am disabled. Does that help?"
Like, you know what I can do on my desktop? "sudo pacman -Rdd linux" , this will just fucking remove the entire linux kernel. Fundamentally breaking my computer until I boot up a live disk and chroot in and reinstall it or whatever, and the computer will go "Are you sure (y/n)" or whatever and i'm like "y" and it will just go "Ok you got it boss"
But its mine, I get to do what I want with it. I control the computer, the computer does not control me. I refuse to cede control to my phone or anything else. The thing is a lot of people will joke that like "Oh I love just letting the machine tell me what to do, I don't know what I'm doing, it knows best" or whatever but the thing you have to realize is that when you say that you are abstracting away that "the phone" or whatever is not some value neutral logic driven robot like from sci-fi, it is a collection of the the capitalistic and fascistic desires of the tech oligarch fuckwits that are burning the world to the ground right now. You aren't submitting to the phone, you are submitting to Musk, Bezos, Nadella, Pichai, Cook and all those other evil bastards.
Fuck them, fuck their little AI toys, and fuck this.
5K notes
·
View notes
Text
How to host local Club Penguin Private Server (CPPS) on Silicon Mac (M1/M2/M3) thru play.localserver & Solero's Wand install.
I spent so long looking for a solution to this that I want to contribute what worked for me. I got so frustrated looking for something that worked, and I hope this guide will help others avoid that frustration.
This is NOT a guide on hosting or serving a CPPS. This is a guide on making a CPPS playable by locally hosting your server on your Silicon M1/M2/M3 Macbook. This worked on my M3 Macbook, and, in my experience, it seems the newer the hardware/operating system gets, the harder it is accomplish this.
DISCLAIMER *I do not know very much about this topic. I can paste commands into terminal and execute them, I know how to install DMG files I downloaded from the internet (the bar is in hell, I am aware), and I know how to enter play.localhost to run this in a browser. I am no expert; this guide is for beginners like myself who want a CPPS. This is beginner-level stuff. If you want advice or need help hosting, refer to the Wand Github page, Solero's Dash (an actual web-hosting solution for Houdini/Wand), Solero's discord, or, when in doubt, Google it. (I recommend only asking for help in Solero's discord for help AFTER trying your best to search for a solution, and even after that, trying to search key terms in their chat logs. They often have to repeat the same advice over, and over, and over again.)*
TLDR; IDK shit about shit
USING WAND INSTALLER
wand description from github: Wand makes it easy to configure dash, houdini and a media server utilizing docker & docker-compose.
All the assets are located here.
Installation instructions from the above link:
Installation script 1. run the script: bash <(curl -s https://raw.githubusercontent.com/solero/wand/master/install.sh) 2. Answer Questions which are: Database password (Leave blank for random password) Hostname (example: clubpenguin.com) (Leave empty for localhost) External IP Address (Leave empty for localhost) 3. Run and enjoy. Run this command: $ cd wand && sudo docker-compose up
The steps I took:
1. Install Docker via Terminal & Homebrew.
Installing the Docker DMG file did not work properly when I tried. I realized later that Docker is seperate from Docker Desktop (the DMG file). I got Docker to work by using Terminal to install Homebrew, and then using Homebrew to install Docker.
Indented text = paste into Terminal.
Command to install Homebrew:
/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/HEAD/install.sh)"
Ensure Homebrew is installed:
brew --version
Install Docker:
brew install docker
Recommended: Install Docker Desktop (useful in determining if your server is running, stopped, or stuck in a restart loop).
brew install --cask docker
Run Docker Desktop:
open -a Docker
2. Run installation script:
bash <(curl -s https://raw.githubusercontent.com/solero/wand/master/install.sh)
From Github instructions:
Answer Questions which are:
Database password (Leave blank for random password)
Hostname (example: clubpenguin.com) (Leave empty for localhost)
External IP Address (Leave empty for localhost)
3. $ cd wand && sudo docker-compose up
This is what is provided in the Github. This command didn't work on Mac; I believe it's formatted for Linux OS. Here's how I broke it up and enabled it to run from Mac's Terminal.
Navigate to Wand directory:
cd wand
Double-check if you're in the right directory:
ls
Start Docker container:
docker-compose up
If the above doesn't work, try
docker compose up
or
brew install docker-compose
Takes a second...

Ensure Docker is running:
docker info
If it isn't, open the Docker Desktop application.
*After using compose up, this error may appear:*
WARN[0000] /Users/[user]/wand/docker-compose.yml: the attribute version is obsolete, it will be ignored, please remove it to avoid potential confusion
This is harmless. If you get annoyed by errors, this can be solved by:
nano docker-compose.yml

See Version 3.7 at the top? Delete that line.
Ctrl-X (NOT COMMAND-X) to exit, Y to save, Enter.
PLAY.LOCALHOST
Type http://PLAY.LOCALHOST into a browser.

Create a penguin.

Try logging in that penguin:

This step was agony. I'm not savvy with running obsolete or deprecated software, and, of course, Club Penguin (and Houdini/Wand's assest) uses Flash, which was discontinued, and timebombed by Adobe, in 2021.
I tried Ruffle. Club Penguin Journey uses Ruffle, so why can't I?
Running Ruffle in Firefox:


No luck.
In the Solero discord, they'll direct to this blog post:

This method does not work on Mac M1/M2/M3. The program is "out of date" and you cannot run it. It works on Macbook's running Sonoma and backward. I'm on an M3 running Sequoia.
they'll often post this video in the discord:

In theory, this method should work, and it does for many, but for whatever reason, not on my M3. I tried different versions of Ungoogled, I tried so many different patches of Pepperflash, and it never cooperated. I tried Pepperflash, I tried Fast Patch!, I tried dedicated Flash browsers, running Flash plugins for Pale Moon, Ungoogled, Waterfox, but I could never get past him.

Every time I see this stupid penguin's face I'm filled with rage. But I am going to save you that rage!!!
If you get this method to work, yay! I could not. Maybe I don't know enough about patching, maybe I'm a little tech stupid.
WHAT WORKED: Using a dedicated CPPS desktop application that allows you to plug in a URL.
I give you...

He is your solution, your answer to

I discovered this solution through Solero's Discord, when someone answered a question re: playing online.

Waddle Forever was not what I was looking forever, but I noticed in their credits:
The electron client is originally forked from the Club Penguin Avalanche client. The server is based in solero's works in reverse engineering the Club Penguin server (Houdini server emulator). The media server is also mostly from solero's media servers.
And that's how I found out the solution: Using CPA Client
Download the CPAvalanche Client
It runs Adode Flash x64. Easy peasy.
(the instructions are in Portuguese, but for English users:
Navigate to releases.

And download this one:

Once downloaded, open.

Drag into applications.
Run http://play.localhost through the client:
Open CPAvalanche Client. It will direct you to CPAvalance once loaded, but you're here because you want to play play.localhost.
Navigate to CPAvalanche Client next to your Apple. Click Mudar a URL do Club Penguin.

Press Sim.

URL: http://play.localhost
Ok.

Press Login once the page loads, and...

That's it! No more penguin! Have fun :)
CREDITS:
Solero Discord / Waddle Forever / Wand / CPA Client / Solero.Me
#solero/wand#wand#solero#cpps#club penguin private server#cpps localhost#club penguin#macbook#macbook silicon#mac m1#mac m2#mac m3#apple silicon
2 notes
·
View notes
Text
How to enable Hardware acceleration in Firefox ESR
For reference, my computer has intel integrated graphics, and my operating system is Debian 12 Bookworm with VA-API for graphics. While I had hardware video acceleration enabled for many application, I had to spend some time last year trying to figure out out how to enable it for Firefox. While I found this article and followed it, I couldn't figure out at first how to use the environment variable. So here's a guide now for anyone new to Linux!
First, determine whether you are using the Wayland or X11 protocol Windowing system if you haven't already. In a terminal, enter:
echo "$XDG_SESSION_TYPE"
This will tell you which Windowing system you are using. Once you've followed the instructions in the article linked, edit (as root or with root privileges) /usr/share/applications/firefox-esr.desktop with your favorite text-editing software. I like to use nano! So for example, you would enter in a terminal:
sudo nano /usr/share/applications/firefox-esr.desktop
Then, navigate to the line that says "Exec=...". Replace that line with the following line, depending on whether you use Wayland or X11. If you use Wayland:
Exec=env MOZ_ENABLE_WAYLAND=1 firefox
If you use X11:
Exec=env MOZ_X11_EGL=1 firefox
Then save the file! If you are using the nano editor, press Ctrl+x, then press Y and then press enter! Restart Firefox ESR if you were already on it, and it should now work! Enjoy!
#linux#debian#gnu/linux#hardware acceleration#transfemme#Honestly I might start doing more Linux tutorials!#Linux is fun!
6 notes
·
View notes
Text
Oh shit. Another curiouscat I had to move to tumblr because I broke character limit again.
So I am combining these two together in the same ask because, in truth, I don't think you can talk about Luca and Alva being mischaracterized separate from each other. So much of their mischaracterization comes from a respective opposing interpretation of the other character. I'm actually going to start with Luca, because I do think this is his story for better or for worse.
Guys. Luca is an adult.
More then that, Luca is an abuse victim and an adult runaway. Like that's not a headcanon, that's plain text canon. His dad neglected his family. He got a college application and rejected it within his deductions. 1900 wasn't so long ago that people were going to college at 16. By the time we meet him in the canon of the story, He's an abuse victim still dealing with that, a newly disabled former able bodied man, and coming out of Victorian prison.
A lot of people view Luca as being very childish for how he handled the fight with Alva. And to some degree it was, Luca doesn't seem like he has very good emotional regulation in the way a lot of young adults in that age range just generally are not. Even in the modern day, the amount of early 20 something's having breakdowns on their Twitter page about the injustices of the world is immeasurable.
But he wasn't /in the wrong/. From Luca's perspective, for all the information that he has. Alva Lorenz IS a thief. Not only is he a thief, but he's a thief in such a way that it, TO LUCA'S KNOWLEDGE, profited off his fathers work at the expense of his families well being. His mom died, man. And learning that Alva had those plans recontextualizes it to be just as much Alvas fault as it is his father's.
He has every right to feel betrayed! He has ever right to indignation! Alvas entire platform, to the information Luca has available to him, is based on plagiarization and theft of his families ideas. While there's shown to be a confrontation, we know this argument went on for a significant amount of time because Lucas deductions SHOW people talking about it. Luca accused him of being a thief before the confrontation that killed Alva and disabled Luca, and at any point inbetween that process Alva Lorenz could have sat him down and explained to him that he worked with his father, and that he had as much right to their ideas as his family.
But he didn't. Because Alva Lorenz is kind of a coward! He thought it would go away on its own!
This is where we get into the Alva Lorenz side of things.
Alva, from everything we have been given, is an incredibly immature man hiding that immaturity under the guise of stem professionalism, and then religious authority. With all of the above in mind, even if their relationship WAS strictly a platonic mentor-student relationship, let alone a sudo-familial one, it would not be a healthy one. Their relationship is not a healthy one.
They are both adults. Alva Lorenz is the adult with more life experience. He is the one that should have sat Luca down and explained himself. But he did not. Alva is not mature. He is not a good man. He would NOT be a good father figure. People, when they ship him with Herman, really try to make the fact they have wives work with lavender marriage. You are being too kind to his character. He would have cheated on his wife to be with Herman. And I understand wanting a more positive approach to these relationships, I understand not wanting the female characters to suffer. But that is not the canon we are presented. And we know this, because of how he treated Ann.
If he was a father figure, he would be willing to enable Herman's neglect. He was willing to enable the cat cults abuse of power to get what he needed, and he would be willing to enable Herman's neglect for that same reason. We don't know what he got from the cat cult yet, but we know he was willing to work with them. We know from Ann's perspective that he ruined her life. We know from Alvas perspective that he doesn't even think about the fact that he ruined her life, because she is NONEXISTENT in his narrative. It is ALL about Luca, and his relationship to the Balsa's.
And that's good writing. I know people are disappointed that she doesn't pop up more with him, but that tells you exactly the kind of authority figure he is. She was no one to him, and he treats her like she's no one.
The thing about Luca Balsa is that he loves passionately. Everything he does is from a place of sincere belief in the *rightness* of it. He feels as strongly as he does about perpetual motion because he believes it can help people, and if HE discovers it, HE is helping people. He sincerely does care about the people in his life, even if he is a moron about it. I think Alva Lorenz is a selfish man. I think he loved Herman, and Loves Luca, and because he cares about them that's what his focus is. He does not care that he hurt Ann through the cat cult. As far as we can tell, he does not care that Ann exists. Alva Lorenz exists in a perpetual state of "fuck you I got mine."
The most infuriating part about all of this is that Luca already has a surrogate father figure within The narrative of IDV. He HAS someone that does want to be a healthy mentor figure to him. It's BURKE. burke has been projecting onto him since we have gotten his second year letter. This relationship with Burke is literally what people who don't like Alvaluca characterize the Alva & Luca relationship to be. But at the end of the day, their goal isn't exploring a complications student-teacher relationship. It's engaging with a set of characters in a way they personally see as being morally correct.
And don't get me wrong. I do have a few issues with the Alvaluca community's interpretation of the two that I've never been quite quiet about, and that gets a lot of AlvaLuca people really defensive sometimes. The Alvaluca relationship IS an unhealthy one. You cannot get around that. No matter how much they love and care about eachother, they are so deeply and horribly bad for eachother. But that's the meat of it. They're soulmates in the worst possible way. Theyre always going to effect eachother, intrinsically and miserably.
Above all else, I want to explore Alvaluca as this really uncomfortable relationship. I want the eternity manor au to be brimming with melodrama over the Alvaluca relationship. I want Tracy to try and talk to him directly about her concern only for him to dismiss her. I want Naib to try and bring it up while they're smoking only for Luca to LIE HIS ASS OFF about not thinking anything is wrong with their dynamic. I want Edgar to hate Alvas guts because he's fucking Luca, because he sees the situation and he projects his situation with Sarai and sees red.
Because the unfortunate reality of being an adult that exists in the working world is that your friends will get into these deeply uncomfortable, deeply unhealthy relationships. There will probably be a time where someone you personally care about date someone two decades older than them. One of your college classmates will get caught hooking up with the professor. One of your retail coworkers will get caught fucking in the break room. Some of these relationships will crash and burn, some of them will move on to marriage despite the power imbalance. These are very real things that happen all the time and to say that we are forbidden from exploring that in Media is absolutely goddamn ridiculous.
#It's not to completely tangent#but this is what I mean when I say we don't actually have any toxic yuri in idv.#EmmaEmily is the closest thing we have to that#and people start getting squeamish when their relationship is still being portrayed as relatively positive and caring#just from a former power imbalance. That is aside from the point! Just something I wanted to bring up because you have me ranting and raving#we dont have any femslash pairings that have quite the same level of THIS complexity in its toxicity#unless 15 year olds are calling you out for shipping it its not a true toxic ship
19 notes
·
View notes
Text
Glitch.GUI Cross Platform Glitch Art Generator and Effects Processor
Linux

macOS

Windows
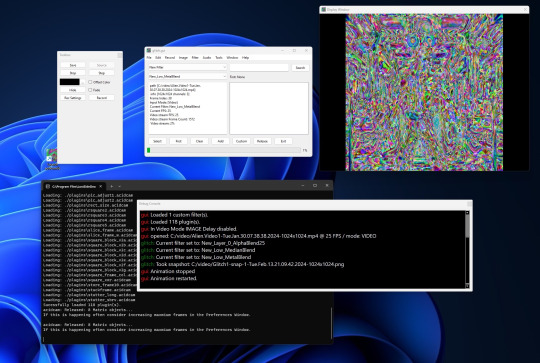
Glitch Art Generator and Effects Processor
This application enables users to generate captivating glitch art to use as base images for AI or apply various effects to any image or video, including those generated by AI. Users can chain effects together for both images and video files, and they have the ability to save custom filters created by mixing and matching different filters and plugins. Additionally, users can opt to incorporate sound from the original source video into their edited videos. The application also offers the functionality to rotate videos between portrait and landscape orientations.
How It Works
Input Files: Provide an example image or video file to begin the process.
Start Animation: Initiate the desired animation effect.
Save Output: Press the "Save" button or the shortcut key "s" to save a snapshot of the generated art.
Record Video: Optionally, record a video file by configuring the recording settings.
Navigation: Use the arrow keys to navigate through available distortion filters. Press "s" to save, "d" to start/stop recording, "e" to step through, or utilize the GUI buttons to perform the same operations.
Filter Application: Note that some filters may appear to have no effect on an image initially. In such cases, select a filter that induces visible changes, press the first button, and then choose the seemingly inactive filter. This is because certain filters require an animation to execute their intended action.
Required libraries: OpenCV 4, http://github.com/lostjared/libacidcam - libacidcam, Qt6, Qt6 Web Engine Widgets (on debian qt6-webengine-dev)
To compile for Linux download and install libacidcam
git clone https://github.com/lostjared/libacidcam.git
cd libacidcam
build cmake ../
make -j8 && sudo make install
enter directory of glitch.gui
qmake6
make -j8
./glitch.gui
Note: This program is pre-release so it may contain errors or bugs. We are working to make the program the best it can be.
Jared Bruni
2 notes
·
View notes
Text
How to fix Guilty Gear Strive can't connect to online on Linux
Most likely if you're unable to connect online, it's due to time sync issues. This an issue on Windows as well as Linux, and I've experienced this annoyance on both. To fix this, we need to sync our clock.
First, open a command prompt.
Type in "timedatectl"
Timedatectl will most likely show this:

In this case we need to enable ntp. To do this, simply type in "sudo timedatectl set-ntp true"
We also may need to install ntp if on arch, in which case type "pacman -S ntp"
And after restarting the game, it should connect just fine. I hope this helps!
Sources:
5 notes
·
View notes
Text
LMDE 6 Beta First impressions.
I've been trying out the Linux Mint Debian Edition 6 public beta for little over a day now, and I have no complaints or bugs so far. LMDE is the version of Linux Mint that is based directly on Debian rather than Ubuntu, unlike the mainline Mint distro. LMDE 6, "Faye", is based on Debian 12. The point is to become as similar in features as the regular Ubuntu version. And it exists as a Plan B in case Ubuntu disappears or becomes unuseable as a base for Mint.
And It's good that this safety plan exists, because Canonical and Ubuntu are not that reliable. The Mint devs has had to rebel against Canonical's decisions multiple times, creating work for them. The Mint documentation has an entire page criticizing Canonical's preferred package format, Snap and why it's not included by default in Mint. The version of Firefox included in Mint is packaged by the devs themselves, since the Ubuntu version of Firefox is a snap (and if you try to install it via Apt, it will install a snap package instead). And ubuntu is moving more and more towards snaps, including an immutable all-snap Ubuntu. If that becomes the default Ubuntu release, derivative distros that don't use snap are pretty much finished.
I started my Linux journey with Mint, but moved upstream to Debian for awhile precisely because I was not comfortable with my operating system standing on such unsure ground. And unlike most Ubuntu-based distros (of which there are many), it's smart of the Mint team to realize that and create LMDE as a plan B. And now I'm on LMDE, because well that moves my computer off Ubuntu, while also enabling me to support Mint, which remains such an important part of the LInux ecosystem for being so beginner-friendly.
So how it is as a distro? How does it compare to mainline Ubuntu? and what does it add to its Debian base?
LMDE uses Debian stable, and as such the packages are outdated, but it's rocksolid stable. I'm running the beta, and because it's debian-based, the majority of the packages were well-tested by the time Debian 12 was released. So I haven't found any bugs so far. And Mint includes flatpaks by default, so you can get newer software in sandboxed containers without sacrificing overall system stability.
Mint adds to the basic Debian experience in many ways, the main addition is the many GUI tools Mint has developed. The software manager handles both debs and flatpaks by default with a slick interface. And the update manager handles updates with friendly non-pushy notifications, I've sang its praises before. Mint also provides tools to manage your software sources (to switch to a local mirror for example) and to create a backup of your home folder.
These tools are what make Mint so famously easy to use, as I written about before. For most common use cases, you never need to see the command line. It's similar to what MX Linux adds to Debian, which I've written about here. I think Mint probably has better looking and more intuitive GUI design than the MX equivalents, although the MX tools have more features. They are both great.
KDE Plasma and Gnome desktops does add somewhat similar functionality to base Debian, but I have reasons not to use those DEs. Gnome lacks customizability and forces a particular workflow, while I found Plasma to be a complete crashfest.
I ended up using xfce, which best met my needs, it's lightweight, easy to use and stable. And I didn't want to pollute it by pulling in bits of other desktops with all its dependencies. It did however require me to use the command line for things like installing and updating flatpaks, and i found running "sudo apt update" and "sudo apt upgrade" easier than using synaptic. I had figured out the command line by that point, so I could make do without the functionality of Mint, but the Mint tools are great to have. Having update notifications is great for an absent-minded person like me.
And they are sometimes objectively better than their Debian equivalents. For example the software sources manager that is in the Debian repos has been broken for months with a bug that leaves your apt.sources.list in a broken state that cuts your OS off from security updates, something I discovered the hard way and I had to manually edit my sources.list to fix it. The Mint equivalent works perfectly fine.
There is a lot of polish for desktop users In LMDE compared to base debian. It does add a lot of value that way.
How is it compared to ubuntu-based Mint (LMUE) though? And as someone who used LMUE cinnamon for months, I have to say the majority of functionality is all there. My experience is basically the same.
The only thing missing I could find is the driver manager, which can be very useful as it detects missing hardware drivers and pulls them in from either online or the installation media. The driver manager is to my understanding tied into Ubuntu's repos for additional drivers. Ubuntu has some of the best hardware support in the LInux distro world. Debian however has compromised their commitment to free software in favor of practicality, and now includes non-free drivers with their installation media by default, so maybe that functionality is not that necessary anymore. I've had no problems with wi-fi and blu-ray drivers on this laptop I'm typing this on, even with base Debian.
Another thing missing in LMDE is a choice of desktop environments by default. You only get cinnamon, the flagship DE developed by the Mint devs primarily for MInt. LMUE also offers Mate and Xfce by default. This is because LMDE is a "Plan B", and supporting multiple DEs on a second base would mean a too heavy workload for the devs. The Debian repos does however have Mate and Xfce in its massive package selection, plus several more DEs, and you can install them manually If you want, and still use the MInt tools, I tried it with xfce myself.
As a derivate distro, LMDE does also drag behind Debian releases quite a bit, when a new Debian drops it takes awhile for Mint to develop an LMDE version based on it. LMDE 6 was a quick turnaround by LMDE standards and it still took like three months after Debian 12's release. LMUE's turnaround for Ubuntu LTS releases is far quicker, because it remains a relative priority for the devs.
Still LMDE 6 is here now, and it's a great distro. It proves that Linux Mint is not relaint on Ubuntu, and adds useful functionalities to its Debian base.
#my writings#linux mint#linux#debian#linux mint debian edition#lmde#welcome to another installment of ''lena rambles about linux''
3 notes
·
View notes
Text
Remote Access IoT Devices with SSH: A Secure Gateway to Smarter Control
In the age of smart homes, connected factories, and remote monitoring, the Internet of Things (IoT) has transformed how we interact with the world around us. Whether it's a Raspberry Pi running a weather station or a smart irrigation system in a remote location, the ability to control IoT devices from afar is essential. One of the most secure and flexible ways to achieve this is through SSH (Secure Shell

What is SSH?
SSH is a cryptographic network protocol that allows secure remote login from one computer to another. It encrypts the communication between devices, ensuring that data transferred over public or private networks remains confidential. For IoT, SSH is especially powerful—it allows administrators and developers to connect to remote devices, execute commands, transfer files, and perform maintenance securely.
Why Use SSH for Remote IoT Access?
Many IoT devices operate in remote or hard-to-reach environments. Physically accessing them for updates, monitoring, or troubleshooting can be costly and impractical. SSH provides the ability to:
Manage devices securely: Prevent unauthorized access through strong authentication and encrypted sessions.
Transfer files: Use tools like scp or rsync over SSH to move data, firmware, or logs between systems.
Monitor performance: Check system resources, running processes, and network status in real-time.
Perform maintenance: Restart services, update software, or even reboot the device remotely.
Setting Up SSH on IoT Devices
Most Linux-based IoT devices (like Raspberry Pi, BeagleBone, or ESP32 with Linux firmware) come with SSH support built-in. Here are the general steps to enable and use SSH:
Install OpenSSH Server: bashCopyEditsudo apt-get install openssh-server
Enable the SSH service: bashCopyEditsudo systemctl enable ssh sudo systemctl start ssh
Find the IP address of the IoT device: bashCopyEdithostname -I
Connect remotely from your local machine: bashCopyEditssh user@ip_address
Use SSH keys for passwordless and more secure access: bashCopyEditssh-keygen ssh-copy-id user@ip_address
Security Considerations
Remote access exposes your devices to remote access iot ssh the internet or wider network, so proper security practices are critical:
Use strong passwords or key-based authentication.
Change the default SSH port to reduce the risk of automated attacks.
Implement firewalls and allow SSH connections only from trusted IP addresses.
Keep firmware and SSH software up to date to patch known vulnerabilities.
Advanced Use Cases
Reverse SSH tunneling: Useful when the IoT device is behind a NAT or firewall and cannot be accessed directly.
VPN with SSH: Combine SSH with a VPN for even more secure connections.
Automation: Integrate SSH commands into scripts or IoT platforms to automate updates and data collection.
Conclusion
SSH offers a robust and secure method to manage IoT devices remotely. As the number of connected devices continues to grow, leveraging SSH for remote access ensures that you can maintain control, security, and efficiency across your IoT network. Whether you're a hobbyist tinkering with smart sensors or a business deploying thousands of IoT endpoints, SSH is a fundamental tool in your toolkit.
You said:
anuther creat
ChatGPT said:
Sure! Here's a new and unique 500-word blog post on "Remote Access IoT SSH" with a different angle and writing style:
Title: Unlocking IoT Potential: How SSH Enables Secure Remote Access
In today’s hyperconnected world, Internet of Things (IoT) devices are powering smart cities, homes, factories, and farms. But having smart devices is just the start—what truly unlocks their potential is the ability to remotely access and manage them. This is where SSH (Secure Shell) comes in as a critical technology for secure remote access.
What is SSH and Why Does It Matter?
SSH is a network protocol that allows you to remotely access a device over a secure, encrypted channel. Think of it as a digital key to your IoT devices. Unlike traditional access methods, SSH keeps your data protected even when sent over public networks.
For IoT devices deployed in remote or hard-to-reach locations—like a smart weather station in the mountains or a water sensor in an agricultural field—SSH enables developers and engineers to connect, troubleshoot, update, or reboot devices without physical contact.
Real-World Use Cases
Smart Agriculture: A farmer uses SSH to update irrigation sensor software remotely.
Industrial IoT: Engineers access factory sensors for real-time diagnostics.
Home Automation: Tech-savvy homeowners tweak Raspberry Pi-based smart devices using SSH.
With SSH, it’s no longer necessary to be on-site. All you need is the device’s IP address, credentials, and a network connection.
How to Enable SSH on an IoT Device
Most Linux-based IoT devices support SSH. Here’s a simplified setup guide:
Install the SSH server (if not already installed): bashCopyEditsudo apt install openssh-server
Enable and start the service: bashCopyEditsudo systemctl enable ssh sudo systemctl start ssh
Find your device’s IP address: bashCopyEditifconfig or hostname -I
From your PC, connect to the device: bashCopyEditssh [email protected]
To improve security and convenience, set up SSH key-based authentication and disable password login.
Keeping Remote Access Secure
Opening a device to remote access increases the attack surface. Here are essential tips to secure your IoT-SSH setup:
Use SSH keys instead of passwords: More secure and convenient.
Change the default SSH port: Avoid port 22 to reduce bot attacks.
Disable root login: Limit user privileges.
Use firewalls and IP whitelisting: Restrict who can connect.
Keep your device updated: Regularly apply security patches.
Advanced Remote Access Techniques
Reverse SSH Tunnels: Useful when the device is behind a NAT or firewall.
Dynamic DNS + Port Forwarding: Helps connect devices with changing IPs.
Bastion Hosts: Use a central secure server to connect to multiple devices.
Final Thoughts
Remote SSH access is more than just a convenience—it’s a necessity in the IoT world. It empowers developers, reduces downtime, and enhances control over smart systems. As IoT deployments scale globally, SSH remains a lightweight yet powerful way to ensure reliable, secure, and flexible device management.
Whether you’re managing five smart sensors or a thousand industrial nodes, SSH is the bridge that connects your command center to the edge—safely and efficiently.
0 notes
Text
Server Security: Analyze and Harden Your Defenses in today’s increasingly digital world, securing your server is paramount. Whether you’re a beginner in ethical hacking or a tech enthusiast eager to strengthen your skills, understanding how to analyze adn harden server security configurations is essential to protect your infrastructure from cyber threats. This comprehensive guide walks you through the key processes of evaluating your server’s setup and implementing measures that enhance it's resilience. Materials and Tools Needed Material/ToolDescriptionPurposeServer Access (SSH/Console)Secure shell or direct console access to the serverTo review configurations and apply changesSecurity Audit ToolsTools like Lynis, OpenVAS, or NessusTo scan and identify vulnerabilitiesConfiguration Management ToolsTools such as Ansible, Puppet, or ChefFor automating security hardening tasksFirewall Management InterfaceAccess to configure firewalls like iptables, ufw, or cloud firewallTo manage network-level security policiesLog Monitoring UtilitySoftware like Logwatch, Splunk, or GraylogTo track suspicious events and audit security Step-by-Step Guide to Analyzing and Hardening Server Security 1. Assess Current Server Security Posture Log in securely: Use SSH with key-based authentication or direct console access to avoid exposing passwords. Run a security audit tool: Use lynis or OpenVAS to scan your server for weaknesses in installed software, configurations, and open ports. Review system policies: Check password policies, user privileges, and group memberships to ensure they follow the principle of least privilege. Analyze running services: Identify and disable unnecessary services that increase the attack surface. 2. Harden Network Security Configure firewalls: Set up strict firewall rules using iptables, ufw, or your cloud provider’s firewall to restrict inbound and outbound traffic. Limit open ports: Only allow essential ports (e.g., 22 for SSH, 80/443 for web traffic). Implement VPN access: For critical server administration, enforce VPN tunnels to add an extra layer of security. 3. Secure Authentication Mechanisms Switch to key-based SSH authentication: Disable password login to prevent brute-force attacks. Enable multi-factor authentication (MFA): Wherever possible, introduce MFA for all administrative access. Use strong passwords and rotate them: If passwords must be used,enforce complexity and periodic changes. 4. Update and Patch Software Regularly Enable automatic updates: Configure your server to automatically receive security patches for the OS and installed applications. Verify patch status: Periodically check versions of critical software to ensure they are up to date. 5. Configure System Integrity and Logging Install intrusion detection systems (IDS): Use tools like Tripwire or AIDE to monitor changes in system files. Set up centralized logging and monitoring: Collect logs with tools like syslog, Graylog, or Splunk to detect anomalies quickly. Review logs regularly: Look for repeated login failures, unexpected system changes, or new user accounts. 6. Apply Security Best Practices Disable root login: prevent direct root access via SSH; rather,use sudo for privilege escalation. Restrict user commands: Limit shell access and commands using tools like sudoers or restricted shells. Encrypt sensitive data: Use encryption for data at rest (e.g., disk encryption) and in transit (e.g., TLS/SSL). Backup configurations and data: Maintain regular, secure backups to facilitate recovery from attacks or failures. Additional Tips and Warnings Tip: Test changes on a staging environment before applying them to production to avoid service disruptions. Warning: Avoid disabling security components unless you fully understand the consequences. Tip: Document all configuration changes and security policies for auditing and compliance purposes.
Warning: Never expose unnecessary services to the internet; always verify exposure with port scanning tools. Summary Table: Key Server Security Checks Security AspectCheck or ActionFrequencyNetwork PortsScan open ports and block unauthorized onesWeeklySoftware UpdatesApply patches and updatesDaily or WeeklyAuthenticationVerify SSH keys,passwords,MFAMonthlyLogsReview logs for suspicious activityDailyFirewall RulesAudit and update firewall configurationsMonthly By following this structured guide,you can confidently analyze and harden your server security configurations. Remember, security is a continuous process — regular audits, timely updates, and proactive monitoring will help safeguard your server against evolving threats. Ethical hacking principles emphasize protecting systems responsibly, and mastering server security is a crucial step in this journey.
0 notes
Text
How to shrink and create new partition on Windows Server
In this guide, you will learn how to shrink and create new partition on Windows Server. On Windows, you can decrease the space used by primary partitions and logical drives by shrinking them into adjacent, contiguous space on the same disk. Please, see how to Enable and use Sudo in Windows 11, how to Add Another Hard Drive to a Virtual Machine in HyperV, and how to Locate, Find and Grep: How to…
0 notes
Text
How to enable the root user in ubuntu
By default in the ubuntu installation root user is disabled. Fire the command from installed user which has super privilage or created while installing the ubuntu Enabling the root account sudo passwd Sudo will ask for your password then prompt for root password two times as : [sudo] password for username: (enter own password) Enter new UNIX password: (enter a new password for root…
0 notes
Text
This Week in Rust 598
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @thisweekinrust.bsky.social on Bluesky or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub and archives can be viewed at this-week-in-rust.org. If you find any errors in this week's issue, please submit a PR.
Want TWIR in your inbox? Subscribe here.
Updates from Rust Community
Official
Announcing rustup 1.28.2
Project/Tooling Updates
Announcing Malai - Share your dev server (and more) over P2P
Streaming data analytics, Fluvio 0.17.2 release
Leptos v0.8.0
This Month in Redox - April 2025
Observations/Thoughts
Automatic interleaving of high-level concurrent operations
Flattening Rust's Learning Curve
The Evolution of Rust
std::mem is... interesting
[audio] Svix with Tom Hacohen
Rust Walkthroughs
Authentication with Axum
Newtyped Indices are Proofs
What is my fuzzer doing?
A Rust API Inspired by Python, Powered by Serde
How to create small and secure Docker images for Rust (FROM scratch)
[video] Rust + SQLite: Complete Tutorial (Schema, CRUD, JSON & Async)
Research
An Interactive Debugger for Rust Trait Errors
RustAssistant: Using LLMs to Fix Compilation Errors in Rust Code
Miscellaneous
Memory-safe sudo to become the default in Ubuntu
How To Get A Rust Job Part I: Companies Already Using Rust
GOSIM Spotlight Finalists at RustWeek
Crate of the Week
This week's crate is structstruck, a proc-macro crate for enabling nested struct/enum definitions.
Thanks to Julius Michaelis for the self-suggestion!
Please submit your suggestions and votes for next week!
Calls for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization.
If you are a feature implementer and would like your RFC to appear in this list, add a call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
No calls for testing were issued this week by Rust, Rust language RFCs or Rustup.
Let us know if you would like your feature to be tracked as a part of this list.
RFCs
Rust
Rustup
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Call for Participation; projects and speakers
CFP - Projects
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
* Hyperswitch - Move connector-specific utility functions to respective connector modules * Hyperswitch - Refactor ACI connector to reuse utilities from utils.rs * Hyperswitch - Analyze and remove unused functions in connector/utils.rs * rama - add ffi/rama-rhai: support ability to use services and layers written in rhai * rama - support (TLS) peetprint in rama-net fingerprinting * rama - support akamai h2 passive fingerprint and expose in echo + fp services * rama - add into_stream to BodyExtractExt trait
If you are a Rust project owner and are looking for contributors, please submit tasks here or through a PR to TWiR or by reaching out on X (formerly Twitter) or Mastodon!
CFP - Events
Are you a new or experienced speaker looking for a place to share something cool? This section highlights events that are being planned and are accepting submissions to join their event as a speaker.
No Calls for papers or presentations were submitted this week.
If you are an event organizer hoping to expand the reach of your event, please submit a link to the website through a PR to TWiR or by reaching out on X (formerly Twitter) or Mastodon!
Updates from the Rust Project
447 pull requests were merged in the last week
Compiler
handle paren in macro expand for let-init-else expr
implement or-patterns for pattern types
initial support for dynamically linked crates
mir-opt: execute MatchBranchSimplification after GVN
refactor rustc_on_unimplemented's filter parser
perf: optimize the codegen for Span::from_expansion
perf: delay checking of #[rustc_no_implicit_autorefs] in autoref lint
perf: simplify LazyAttrTokenStream
perf: use a closure instead of three chained iterators
transmutability: merge contiguous runs with a common destination
transmutability: uninit transition matches unit byte only
Library
avoid redundant WTF-8 checks in PathBuf
delegate to inner vec::IntoIter from env::ArgsOs
implement Iterator::last for vec::IntoIter
stabilize ptr::swap_nonoverlapping in const
stabilize select_unpredictable
streamline the format macro
Cargo
cargo add: suggest similarly named features
in package-workspace, keep dev-dependencies if they have a version
Rustdoc
fix doctest heuristic for main fn wrapping
Rustfmt
also allow bool literals as first item of let chain
Clippy
don't warn about unloaded crates
fix collapsible_if false positive on block stmt before expr
fix manual_unwrap_or_default false positive on ref binding
fix: manual_slice_fill false positive on IndexMut overload
fix: unused_async false positive on default impl
gate collapsible_if let_chains lints on edition 2024 and MSRV
Rust-Analyzer
add PGO support to install
better handle parallelism in cache priming
disable fixpoint for variance computation temporarily
add an assist to unwrap a type with a generic arg
correct assoc ty bound var starting index
correct span info for mir::Operand
don't panic on some weird code
fix move_bounds assists not working for lifetimes
fix incorrect handling of unresolved non-module imports in name resolution
fix proc-macro API creating malformed negative literals
implement mut to const ptr cast for method resolution
improve parser recovery a bit
negative nums in concat! expansion
remove unnecessary token length check for macros in renaming
improve the let code snippet
render more lifetimes
support environment variable CARGO_MANIFEST_PATH
Rust Compiler Performance Triage
A relatively noisy week due to addition of new benchmarks as part of our 2025 benchmark update, and a number of large regressions in a rollup landing late in the week (and so not yet investigated).
Triage done by @simulacrum. Revision range: 25cdf1f6..62c5f58f
2 Regressions, 2 Improvements, 6 Mixed; 3 of them in rollups 31 artifact comparisons made in total
Full report here.
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
No RFCs were approved this week.
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
Tracking Issues & PRs
Rust
Temporary lifetime extension through tuple struct and tuple variant constructors
Stabilize the avx512 target features
Make missing_fragment_specifier an unconditional error
Error on recursive opaque ty in HIR typeck
Add std::io::Seek instance for std::io::Take
remove intrinsics::drop_in_place
Stabilize tcp_quickack
Change the desugaring of assert! for better error output
[Tracking Issue for non_null_from_ref](https://github.com/rust-lang/rust/issues/130823)
Make well-formedness predicates no longer coinductive
Fix parameter order for _by() variants of min / max/ minmax in std::cmp
Finalize repeat expr inference behaviour with inferred repeat counts
Implement (part of) ACP 429: add DerefMut to Lazy[Cell/Lock]
Other Areas
Cargo
Stabilize doctest-xcompile
Rust RFCs
RFC: map_or_default in Option and Result
No Items entered Final Comment Period this week for Language Reference, Language Team or Unsafe Code Guidelines.
Let us know if you would like your PRs, Tracking Issues or RFCs to be tracked as a part of this list.
New and Updated RFCs
RFC: enable derive(From) for single-field structs
#![register_{attribute,lint}_tool]
RFC: Add an attribute for raising the alignment of various items
Upcoming Events
Rusty Events between 2025-05-07 - 2025-06-04 🦀
Virtual
2025-05-07 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2025-05-07 | Virtual (Rotterdam, NL) | Bevy Game Development
Bevy Meetup #10
2025-05-08 | Virtual (Berlin, DE) | Rust Berlin
Rust Hack and Learn
2025-05-08 | Virtual (Girona, ES) | Rust Girona
Sessió setmanal de codificació / Weekly coding session
2025-05-08 | Virtual (Tel Aviv-Yafo, IL) | Rust 🦀 TLV
שיחה חופשית ווירטואלית על ראסט
2025-05-08 | Virtual (Zürich, CH) | Rust Zürisee
🦀 Celebrating 10 years of Rust 1.0 (co-event with berline.rs) 🦀
2025-05-10 | Virtual | Leptos Community
Leptos Meetup: 0.8 Release and Server Fn Websockets Demo
2025-05-11 | Virtual (Dallas, TX, US) | Dallas Rust User Meetup
Rust Readers Discord Discussion: Async Rust
2025-05-11 | Virtual (Dallas, TX, US) | Dallas Rust User Meetup
Rust Readers Discord Discussion: Async Rust
2025-05-13 | Virtual (Dallas, TX, US) | Dallas Rust User Meetup
Second Tuesday
2025-05-15 | Hybrid (Redmond, WA, US) | Seattle Rust User Group
May, 2025 SRUG (Seattle Rust User Group) Meetup
2025-05-15 | Virtual (Joint Meetup, Europe + Israel) | Rust Berlin, Rust Paris, London Rust Project Group, Rust Zürisee, Rust TLV, Rust Nürnberg, Rust Munich, Rust Aarhus, lunch.rs
🦀 Celebrating 10 years of Rust 1.0 🦀
2025-05-15 | Virtual (Girona, ES) | Rust Girona
Sessió setmanal de codificació / Weekly coding session
2025-05-18 | Virtual (Dallas, TX, US) | Dallas Rust User Meetup
Rust Readers Discord Discussion: Async Rust
2025-05-19 | Virtual (Tel Aviv-Yafo, IL) | Rust 🦀 TLV
Tauri: Cross-Platform desktop applications with Rust and web technologies
2025-05-20 | Virtual (London, UK) | Women in Rust
Threading through lifetimes of borrowing - the Rust way
2025-05-20 | Virtual (Tel Aviv, IL) | Code Mavens 🦀 - 🐍 - 🐪
Rust at Work a conversation with Ran Reichman Co-Founder & CEO of Flarion
2025-05-20 | Virtual (Washington, DC, US) | Rust DC
Mid-month Rustful
2025-05-21 | Hybrid (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out
2025-05-22 | Virtual (Berlin, DE) | Rust Berlin
Rust Hack and Learn
2025-05-22 | Virtual (Girona, ES) | Rust Girona
Sessió setmanal de codificació / Weekly coding session
2025-05-25 | Virtual (Dallas, TX, US) | Dallas Rust User Meetup
Rust Readers Discord Discussion: Async Rust
2025-05-25 | Virtual (Dallas, TX, US) | Dallas Rust User Meetup
Rust Readers Discord Discussion: Async Rust
2025-05-27 | Virtual (Dallas, TX, US) | Dallas Rust User Meetup
Fourth Tuesday
2025-05-27 | Virtual (Tel Aviv, IL) | Code Mavens 🦀 - 🐍 - 🐪
Rust at Work - conversation with Eli Shalom & Igal Tabachnik of Eureka Labs
2025-05-29 | Virtual (Nürnberg, DE) | Rust Nuremberg
Rust Nürnberg online
2025-06-01 | Virtual (Dallas, TX, US) | Dallas Rust User Meetup
Rust Readers Discord Discussion: Async Rust
2025-06-04 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
Asia
2025-05-17 | Delhi, IN | Rust Delhi
Rust Delhi Meetup #10
2025-05-24 | Bangalore/Bengaluru, IN | Rust Bangalore
May 2025 Rustacean meetup
Europe
2025-05-07 | Girona, ES | Rust Girona
Rust Girona Hack & Learn 05 2025
2025-05-07 | Köln, DE | Rust Cologne
Rust in May: FFI
2025-05-07 | Madrid, ES | MadRust
VII Lenguajes, VII Perspectivas, I Problema
2025-05-07 | Oxford, UK | Oxford Rust Meetup Group
Oxford Rust and C++ social
2025-05-08 | Gdansk, PL | Rust Gdansk
Rust Gdansk Meetup #8
2025-05-08 | London, UK | London Rust Project Group
Adopting Rust (Hosted by Lloyds bank)
2025-05-12 | Amsterdam, NL | RustNL
Bowling at Rust Week
2025-05-12 | Amsterdam, NL | RustNL
Create your rusty steel Rust logo!
2025-05-12 | Amsterdam, NL | RustNL
Walking Tour around Utrecht - Monday (afternoon)
2025-05-12 | Amsterdam, NL | RustNL
Walking Tour around Utrecht - Monday
2025-05-13 | Amsterdam, NL | RustNL
RustWeek 2025 announcement
2025-05-13 - 2025-05-17 | Utrecht, NL | Rust NL
RustWeek 2025
2025-05-14 | Reading, UK | Reading Rust Workshop
Reading Rust Meetup
2025-05-15 | Oslo, NO | Rust Oslo
Rust 10-year anniversary @ Appear
2025-05-16 | Amsterdam, NL | RustNL
Rust Week Hackathon
2025-05-16 | Utrecht, NL | Rust NL Meetup Group
RustWeek Hackathon
2025-05-17 | Amsterdam, NL | RustNL
Walking Tour around Utrecht - Saturday
2025-05-20 | Aarhus, DK | Rust Aarhus
Hack Night - Robot Edition
2025-05-20 | Leipzig, SN, DE | Rust - Modern Systems Programming in Leipzig
Topic TBD
2025-05-22 | Augsburg, DE | Rust Augsburg
Rust meetup #13
2025-05-22 | Bern, CH | Rust Bern
2025 Rust Talks Bern #3 @zentroom
2025-05-22 | Paris, FR | Rust Paris
Rust meetup #77
2025-05-22 | Stockholm, SE | Stockholm Rust
Rust Meetup @UXStream
2025-05-27 | Basel, CH | Rust Basel
Rust Meetup #11 @ Letsboot Basel
2025-05-29 | Oslo, NO | Rust Oslo
Rust Hack'n'Learn at Kampen Bistro
2025-06-04 | München, DE | Rust Munich
Rust Munich 2025 / 2 - Hacking Evening
2025-06-04 | Oxford, UK | Oxford Rust Meetup Group
Oxford Rust and C++ social
North America
2025-05-07 | Chicago, IL, US | Chicago Rust Meetup
Rust Happy Hour
2025-05-08 | México City, MX | Rust MX
Calculando con el compilador: Compiler time vs Run time. Introducción a uv
2025-05-08 | Portland, OR, US | PDXRust
Apache DataFusion: A Fast, Extensible, Modular Analytic Query Engine in Rust
2025-05-11 | Boston, MA, US | Boston Rust Meetup
Porter Square Rust Lunch, May 11
2025-05-13 | New York, NY, US | Rust NYC
Multi-Platform App in Rust @ Warp.dev && Verifying Rust's Stdlib @ CMU
2025-05-15 | Mountain View, CA, US | Hacker Dojo
RUST MEETUP at HACKER DOJO
2025-05-15 | Nashville, TN, US | Music City Rust Developers
Using Rust For Web Series 2 : Why you, Yes You. Should use Hyperscript!
2025-05-15 | Hybrid (Redmond, WA, US) | Seattle Rust User Group
May, 2025 SRUG (Seattle Rust User Group) Meetup
2025-05-20 | San Francisco, CA, US | San Francisco Rust Study Group
Rust Hacking in Person
2025-05-21 | Hybrid (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out
2025-05-28 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
2025-05-29 | Atlanta, GA, US | Rust Atlanta
Rust-Atl
South America
2025-05-28 | Montevideo, DE, UY | Rust Meetup Uruguay
Primera meetup de Rust de 2025!
2025-05-31 | São Paulo, BR | Rust São Paulo Meetup
Encontro do Rust-SP na WillBank
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
Well, the answer is basically yes. Our firmware is all Rust. Every component of our autonomy stack is Rust. Our app is 50% in Rust. And, our visualization tools are in Rust. Our production tools are in rust. The production QC software, which we ship to China, is in rust. Our internal websites are in rust. It's rust all over. We’ve drank the Rust Kool-Aid. In fact, there is no Python installed on the robots. This is not to dis Python at all, but it’s just simply not there.
We use Python for neural network training. But Python is boxed to that. Everything else is Rust. And, the advantage of using Rust exponentially builds up.
– Vivek Bagaria on filtra.io
Thanks to Brian Kung for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, U007D, joelmarcey, mariannegoldin, bennyvasquez, bdillo
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
1 note
·
View note
Text
Executing Ebpf In Github Actions

At Keploy, we wanted our tool to be part of the Github pipeline so that developers could be guaranteed that modifications made in pull requests could be safely merged and deployed. The only problem we had was ~ is it possible.
The reason for this question is because Keploy uses eBPF to track network calls, which requires sudo capabilities. So the question becomes, will GitHub grant users sudo rights for a program they construct and execute on their systems?
If you're interested in how eBPF can be used in other projects and environments like OpenWRT, check out our community post on Connecting a Hosted UI Website to an AWS EC2 Instance.
How does a regular merging cycle work?
A typical merge cycle is simple: you create a PR, certain workflows are run, and if passed, the reviewer merges.
How are the workflows run?
A workflow is a customizable automated process that does one or more jobs. Workflows are defined by a YAML file that is checked into your repository and will run when prompted by an event in your repository, manually, or on a set schedule.|.github |->workflows |-> go.yml #our sample workflow file
So, in a normal merging cycle, these runners are used to check that the test of tests pre-computed rules are followed and that the program acts as expected.
What is eBPF and why do we use it?
The extended Berkeley Packet Filter (eBPF) enables the programmable, safe, and efficient tracing and monitoring of kernel and user-space processes. So, by monitoring system calls, we'll be able to see incoming and outgoing calls to the program without having to interact with the application code.
Want to understand what information can eBPF tell us about an incoming packet? It includes metadata like packet size, destination IP, ports, and protocol type—perfect for tracing network activity without interfering with app logic.
We intend to run this process whenever a pull request is sent to the main branch.
Running eBPF in runner
A sample workflow to run Keploy in github action would look like something below.name: Golang On Linux on: [pull_request] jobs: golang_linux: runs-on: ubuntu-latest steps: - name: Checkout repository uses: actions/checkout@v2 - name: Build binary run: | go build -o keployv2 //Build the binary - name: Run samples-go application run: | cd samples-go/gin-mongo source ./../../.github/workflows/golang-linux.sh //the script
The script for the aforementioned runner might look something like this. In my example, I used the Keploy repository to run in "record" and "test" mode to track network calls.#!/bin/bash # Start mongo before starting binary. docker run --rm -d -p27017:27017 --name mongoDb mongo # Build the binary of the app to be traced with eBPF program. go build -o ginApp # Start the gin-mongo app in record mode and record testcases and mocks. sudo -E env PATH="$PATH" ./../../keployv2 record -c "./ginApp" --generateGithubActions=false & sleep 15 # Get the pid of the application. pid=$(pgrep keploy) curl -X GET http://localhost:8080/CJBKJd92 # Wait for 5 seconds for keploy to record the tcs and mocks. sleep 5 # Stop the gin-mongo app. sudo kill $pid # Wait for 5 seconds for keploy to stop. sleep 5 done # Start the gin-mongo app in test mode. sudo -E env PATH="$PATH" ./../../keployv2 test -c "./ginApp" --delay 7 --generateGithubActions=false
How can we gain the ability to read network calls?
Cgroups (control groups) are a Linux kernel feature that hierarchically organizes processes and distributes system resources in a controlled and flexible manner.
GitHub-hosted runners do not provide access to edit or configure cgroups due to their secure multi-tenant environment.
So how are we capturing network activity?
We use eBPF hooks (specifically kprobes) that don’t require cgroup manipulation. Our Keploy implementation can still observe system calls and packet information passively.
Want to go deeper into how this tech links with native code? Check out Java Native Interface on our blog.
Additionally, if you're deploying in OpenWRT environments, you might be curious how to enable eBPF in the kernel in OpenWRT. It typically involves enabling kernel config options like CONFIG_BPF and CONFIG_BPF_SYSCALL, then recompiling the firmware.
The results of running eBPF:
Github and Gitlab both give us sudo privileges for runners (letting us attach hooks on kprobes). Bitbucket, on the other hand, does not.
These configurations helped us learn we need custom runners for ARM64 architecture. Below is a snippet that demonstrates HTTP requests being captured multiple times by Keploy.
Conclusion
There are a few learnings from this venture:
GitHub runner does give us root-like privilege by allowing us to attach hooks to kprobes.
GitHub runners are 2-core, 7 GB RAM, 14 GB SSD disk space beasts, perfect for running eBPF-based tools.
GitHub integration is possible even with root-level operations like network monitoring using eBPF.
For more insights into developer tools, tech communities, and tips, check out 10 Developer Communities to Be a Part of in 2025 on our blog.
Explore more eBPF and integration use cases on www.keploy.io.
FAQ’S
1. Can eBPF run inside GitHub Actions without full root access? Yes, eBPF can run in GitHub Actions because it attaches to kernel hooks like kprobes. These hooks don’t require full root or cgroup configuration access. GitHub runners provide limited sudo privileges, which are enough for Keploy. This allows passive network tracing during pull requests safely.
2. What kind of data can eBPF extract from incoming packets? eBPF can capture metadata like source and destination IPs, ports, and protocols. It can also track packet sizes, timings, and system call context. This makes it useful for tracing and debugging network activity. All this happens without modifying the application code.
3. How do you enable eBPF in OpenWRT? To enable eBPF in OpenWRT, you need to recompile the kernel with BPF options. Enable flags like CONFIG_BPF and CONFIG_BPF_SYSCALL in kernel config. Also include bpftool and required headers for runtime utilities. Then flash the firmware and verify with bpftool commands.
4. Why does Keploy use eBPF in its GitHub workflow? Keploy uses eBPF to monitor network calls without touching the app code. This lets it auto-generate test cases and mocks by passively observing traffic. Running it in GitHub ensures every PR gets verified safely. It’s a powerful way to integrate deep network tracing into CI/CD.
5. How is GitHub integration handled for eBPF-based tools like Keploy? GitHub workflows use YAML files to define steps and runners. Keploy is built, run, and tested in these workflows using sudo where needed. The eBPF logic runs inside custom bash scripts that are triggered per PR. This seamless integration allows consistent testing across environments.
0 notes
Link
#accesspoint#cloud#configuration#Controller#firewall#Install#IT#Monitoring#networkmanagement#networking#Performance#Security#self-hosted#Server#systemadministration#Ubiquiti#Ubuntu22.04#Ubuntu24.04#UniFi#WiFi#Wireless
0 notes
Text
How to Set Up a Dedicated Server for Your Website?
Setting up a dedicated server for your website can greatly enhance performance, security, and reliability. Unlike shared hosting, where multiple users share the same resources, a dedicated server provides an exclusive environment tailored to your specific needs. This means faster load times, better uptime, and the ability to handle high traffic without disruptions. Additionally, dedicated servers offer improved security, reducing the risk of cyberattacks and data breaches, as you have complete control over security configurations, firewalls, and access permissions.

A dedicated server is particularly beneficial for business websites, e-commerce platforms, or high-traffic blogs that require high availability and customization. For businesses handling sensitive customer data or financial transactions, dedicated hosting ensures compliance with industry standards and regulations. Furthermore, dedicated servers allow for custom software installations, advanced caching techniques, and database optimizations that are not always possible with shared hosting or VPS solutions.
Although setting up a dedicated server requires technical expertise, the benefits far outweigh the challenges. From selecting the right hardware and software to configuring security and performance optimizations, this guide will walk you through the process step by step, ensuring that your website operates efficiently and securely in a dedicated hosting environment.
Step 1: Choose the Right Dedicated Server
Before you begin, it’s crucial to select a dedicated server that meets your requirements. Consider factors such as the processor (CPU), which should be powerful enough to handle your website's traffic and workload, with options like Intel Xeon or AMD EPYC. Memory (RAM) is another important consideration, as it determines how smoothly your website processes run. Storage should be chosen based on your needs—HDDs provide high capacity, while SSDs offer better speed and reliability. Bandwidth is also crucial, as higher traffic websites require more bandwidth to avoid slowdowns. Lastly, decide on an operating system, choosing between Linux (Ubuntu, CentOS, Debian) and Windows Server based on your software requirements. You can purchase a dedicated server from web hosting providers such as M2Host and WebHostingWorld, or set up your own physical server.
Step 2: Install and Configure the Operating System
Once you have your dedicated server, the next step is to install and configure the operating system. If you are using Linux, download the latest ISO file from the official website and use a bootable USB or remote management interface to install it. Follow the installation steps carefully, set up a root password, and create a new user with sudo privileges. After installation, update the system to ensure it runs smoothly. If you opt for Windows Server, download the Windows Server ISO and boot the server from the installation media. Follow the on-screen installation prompts, set up an administrator password, and update Windows to install necessary drivers.
Step 3: Secure Your Server
Security is a crucial aspect of managing a dedicated server. Begin by changing default SSH or RDP ports to reduce the risk of brute-force attacks. Set up a firewall using tools to restrict access. On Linux servers, disable root login by modifying the SSH configuration file and enforce the use of SSH keys instead of passwords. Enabling automatic updates ensures that security patches are applied regularly. Additionally, install security software such as Fail2Ban to monitor and prevent unauthorized access attempts.
Step 4: Install a Web Server
A web server is necessary to host your website files. The two most common options are Apache and Nginx. To install Apache on Linux, use the package manager to install it and enable it to start on boot. For Nginx, follow a similar installation process. If you are using Windows Server, install Internet Information Services (IIS) via the Server Manager by selecting “Add Roles and Features” and enabling the Web Server (IIS) option. Once installed, configure the web server settings as needed to optimize performance.
Step 5: Install and Configure a Database Server
Most websites require a database to store user data, content, and configurations. If you choose MySQL on Linux, install it using the package manager and secure it. PostgreSQL is another option that can be installed similarly. For Windows users, Microsoft SQL Server is a popular choice, which can be installed and managed through SQL Server Management Studio (SSMS). Ensure that your database server is configured for security and optimized for performance.
Step 6: Set Up a Domain Name and SSL Certificate
To make your website accessible via a domain name, purchase a domain from a registrar and configure the DNS settings to point to your server’s IP address. Securing your website with an SSL certificate is crucial for HTTPS encryption. If you are using Linux, install Let’s Encrypt SSL using Certbot. For Apache, run the Certbot command specific to Apache, and for Nginx, use the respective command. If using Windows, install SSL via the IIS Manager.
Step 7: Upload Your Website Files
Once your web server is set up, you need to upload your website files to the appropriate directory. File transfer tools like FTP (FileZilla) or SCP can be used to move files from your local machine to the server.
Step 8: Set Up Automatic Backups
Regular backups are crucial to prevent data loss in case of server failures or security breaches. On Linux, use tools to create scheduled backups of your website files and databases. For Windows, the built-in Windows Backup tool or third-party software like Veeam can be used. Additionally, you can store backups in cloud storage solutions like AWS S3 or Google Drive to ensure redundancy.
Step 9: Monitor and Optimize Performance
Monitoring your server’s performance is essential to ensure it operates efficiently. Linux users can utilize command-line tools, while Windows users can use Task Manager, Resource Monitor, or Performance Monitor. Installing dedicated monitoring tools like Netdata can provide real-time insights. Performance optimization techniques include enabling caching (using Redis or Memcached), integrating a Content Delivery Network (CDN) such as Cloudflare, and optimizing images and database queries to reduce load times.
Step 10: Keep Your Server Maintained
Maintaining your server is essential to ensure stability and security. Regularly updating the operating system and software prevents vulnerabilities. Checking for security patches and restarting services, when necessary, helps prevent memory leaks and downtime. Monitoring access logs can help identify unusual activity and mitigate potential threats. Routine maintenance ensures your dedicated server remains secure and performs optimally.
Benefits of a Dedicated Server for Your Website-
A dedicated server provides numerous advantages, making it an excellent choice for businesses, high-traffic websites, and applications that require enhanced security and performance. Some of the key benefits include:
Improved Performance and Speed – With dedicated resources, your website operates at optimal speed without being affected by other users. This ensures faster page load times and better overall performance, enhancing user experience and search engine rankings.
Enhanced Security – Dedicated servers provide a higher level of security since you are not sharing resources with other websites. You have full control over firewalls, security protocols, and monitoring tools, reducing the risk of cyber threats, data breaches, and malware attacks.
Better Reliability and Uptime – Since your server resources are not shared, your website experiences minimal downtime. Dedicated hosting ensures high availability, making it ideal for businesses that rely on continuous online presence.
Full Control and Customization – A dedicated server allows you to configure the operating system, software, and security settings to suit your specific needs. You can install custom applications, optimize performance settings, and adjust security measures according to your business requirements.
Scalability and Flexibility – As your website grows, a dedicated server provides the flexibility to upgrade hardware components such as RAM, CPU, and storage without affecting performance. This ensures your server can handle increased traffic and data loads efficiently.
Better Compliance and Data Privacy – Businesses handling sensitive information, such as financial institutions and healthcare organizations, benefit from dedicated servers due to enhanced compliance with data protection regulations. Since your data is not shared, it remains private and secure.
Dedicated IP Address – Unlike shared hosting, where multiple websites share a single IP address, a dedicated server provides a unique IP address, reducing the risk of being blacklisted and improving email deliverability.
Optimized Resource Utilization – With dedicated hosting, you avoid issues related to resource allocation, such as bandwidth throttling and CPU limitations that often occur in shared environments. This results in smoother operations and better website performance.
By leveraging the advantages of a dedicated server, businesses and website owners can ensure better performance, security, and reliability while maintaining full control over their hosting environment.
Conclusion-
Setting up a dedicated server for your website requires careful planning, but the rewards include better performance, security, and flexibility. By following this guide, you can establish a robust, secure, and optimized server that serves your website efficiently. Whether you choose Linux or Windows, a dedicated server gives you full control, making it the best option for high-traffic websites and businesses looking for reliability.

Ann Taylor
M2Host m2host.com We provide experienced web hosting services tailored to your unique needs. Facebook Twitter Instagram YouTube
#dedicated server#cheap dedicated server#dedicated hosting#webhostingprovider#best web hosting#m2host#webhostingservice#affordablehosting#cheap web hosting
0 notes