#how to prevent phishing
Explore tagged Tumblr posts
Text
10 Common Cyber Threats and How to Avoid Them
In our increasingly connected world, cybersecurity is no longer just a concern for large corporations; it’s a fundamental aspect of daily life for individuals, families, and small businesses alike. The convenience of online banking, shopping, and social networking comes with the inherent risk of cyber threats, which are constantly evolving in sophistication and frequency. Cybercriminals are…
#antivirus software#avoid cyber threats#avoiding ransomware#Common Cyber Threats#cyber attack prevention#cyber hygiene#cyber risk reduction#cybercrime awareness#cybersecurity education#cybersecurity tips#data backup#data breaches#DDoS protection#Denial-of-Service attacks#digital privacy#digital safety#email security#firewall use#hacking prevention#home network security#how to avoid social engineering#how to prevent phishing#identity theft prevention#internet safety for individuals#internet security best practices#malware prevention#Man-in-the-Middle attacks#MFA#multi-factor authentication#online safety habits
0 notes
Text
How to Protect Yourself from Personal Loan Phishing Scams

In today’s digital world, personal loans have become more accessible, allowing borrowers to apply online and receive funds quickly. However, this convenience has also led to a rise in phishing scams, where fraudsters attempt to steal your personal and financial information by posing as legitimate lenders. These scams can result in identity theft, financial loss, and fraudulent loan applications in your name.
If you’re planning to apply for a personal loan, it is essential to understand how phishing scams work, the warning signs to look for, and the best ways to protect yourself.
1. What Are Personal Loan Phishing Scams?
A phishing scam is a fraudulent attempt to trick individuals into providing sensitive information such as bank details, Aadhaar number, PAN card, OTPs, or login credentials. Scammers typically impersonate banks, NBFCs, or online lending platforms and contact borrowers via emails, phone calls, SMS, or fake websites.
Once they obtain your information, they can:
Steal money from your bank account
Take a loan in your name
Misuse your identity for financial fraud
Access and sell your personal data on the dark web
2. Common Types of Personal Loan Phishing Scams
2.1 Fake Loan Approval Emails & SMS
Fraudsters send emails or SMS messages claiming that your loan has been pre-approved or that you qualify for a low-interest personal loan. These messages often contain links leading to fake lender websites designed to steal your personal information.
2.2 Fake Loan Websites & Apps
Scammers create websites and mobile apps that look like real financial institutions. They trick users into entering personal and banking details, which are then used for fraudulent activities.
2.3 Fraudulent Customer Service Calls
You may receive a phone call from a scammer pretending to be a bank representative. They claim you must provide your OTP, Aadhaar, PAN, or bank details to complete your loan application. Once you share these details, scammers can withdraw money or take loans in your name.
2.4 Loan Processing Fee Scams
Fraudsters promise quick loan disbursal with no documentation but demand advance processing fees or a loan insurance fee. Once the fee is paid, the scammer disappears, and no loan is disbursed.
2.5 Social Media Loan Scams
Some scammers advertise fake loans on Facebook, Instagram, or WhatsApp and ask potential borrowers to contact them privately. Once engaged, they request confidential details, leading to identity theft.
3. Red Flags to Identify Loan Phishing Scams
3.1 Offers That Sound Too Good to Be True
If you receive an offer promising guaranteed loan approval with no credit check, zero documentation, or extremely low-interest rates, it’s likely a scam.
3.2 Unsolicited Loan Messages
Legitimate lenders do not send random SMS, WhatsApp messages, or emails offering personal loans. Be cautious if you receive messages from unknown numbers or email addresses.
3.3 Fake Loan Websites
Before applying for a loan online, always verify the website’s domain name. Scammers often create fake websites with slightly modified spellings of real lenders to trick borrowers.
3.4 Requests for Upfront Payments
No genuine lender will ask for advance processing fees before loan approval. If a lender insists on upfront payments via UPI, Paytm, or Google Pay, it’s a scam.
3.5 Pressure to Act Immediately
Scammers create urgency by saying things like, "Limited offer – Apply now!" or "Your loan will be canceled if you don’t act fast." A real lender will give you time to review the terms.
3.6 Request for Personal Information Over the Phone
A legitimate bank or NBFC will never ask you for OTPs, passwords, or CVVs over the phone. If someone does, hang up immediately.
4. How to Protect Yourself from Loan Phishing Scams
4.1 Apply for Loans Only from Trusted Lenders
Always apply for a personal loan through registered banks, NBFCs, or reputed online lenders. Here are some safe options:
🔗 IDFC First Bank Personal Loan 🔗 Bajaj Finserv Personal Loan 🔗 Tata Capital Personal Loan 🔗 Axis Finance Personal Loan 🔗 Axis Bank Personal Loan 🔗 InCred Personal Loan
4.2 Verify the Lender’s Website
Check if the website URL starts with "https://" (secure site).
Look for official lender details on the RBI website or lender’s official website.
Avoid websites with poor design, spelling errors, or unusual domain names (e.g., "axisbankloans.xyz" instead of "axisbank.com").
4.3 Never Click on Suspicious Links
Do not click on links in unsolicited emails or messages claiming to be from a bank or NBFC. Instead, visit the official website by typing the URL manually.
4.4 Avoid Sharing Personal Information Online
Scammers may ask for your Aadhaar, PAN, or bank details via email, phone, or WhatsApp. Never share sensitive information with unknown sources.
4.5 Enable Two-Factor Authentication (2FA)
Use 2FA on your banking and email accounts to protect against unauthorized access. This adds an extra layer of security if your password is compromised.
4.6 Check Reviews & Ratings Before Downloading Loan Apps
Before installing a loan app, check:
App permissions (Avoid apps that ask for access to contacts, photos, and messages).
Reviews and ratings on Google Play or App Store.
If the app is registered with an RBI-approved lender.
4.7 Monitor Your Bank & Credit Report Regularly
Check your credit report and bank statements for unauthorized loan applications or suspicious transactions. If you spot any fraudulent activity, report it immediately.
5. What to Do If You Are a Victim of Loan Phishing?
If you have fallen victim to a loan phishing scam, take these steps:
1️⃣ Contact Your Bank Immediately – Report any unauthorized transactions and request to block your account if necessary. 2️⃣ Change Your Passwords – Update your internet banking, email, and loan account passwords immediately. 3️⃣ File a Cyber Crime Complaint – Report the fraud to the Cyber Crime Portal (www.cybercrime.gov.in) or call the National Cyber Crime Helpline (1930). 4️⃣ Report to RBI & Consumer Forum – If you have been tricked into a fake loan scheme, report it to the RBI and National Consumer Helpline (1800-11-4000). 5️⃣ Monitor Your Credit Report – Check for unauthorized loans taken in your name and dispute them with credit bureaus like CIBIL and Experian.
Stay Alert & Borrow Safely
Personal loan phishing scams are on the rise, but you can stay protected by being vigilant. Always verify loan offers, apply only through trusted lenders, and avoid clicking on suspicious links.
For safe and secure personal loan options, apply here: 👉 Compare & Apply for a Personal Loan
By staying cautious and informed, you can protect yourself from loan fraud and ensure a safe borrowing experience.
#nbfc personal loan#bank#loan services#personal loans#fincrif#personal loan#personal laon#loan apps#personal loan online#finance#fincrif india#Personal loan phishing scams#Loan fraud protection#How to avoid loan scams#Safe personal loan application#Phishing scams in personal loans#Fake loan offers#Online loan scams#Fraudulent loan websites#Personal loan safety tips#How to identify loan scams#Signs of a loan scam#Avoiding personal loan fraud#Phishing emails from loan providers#Loan application fraud prevention#How scammers trick loan applicants#Secure loan application process#Fake personal loan SMS and calls#Online loan phishing protection#Tips to protect against loan fraud
5 notes
·
View notes
Text
Running Facebook ads can be a game-changer, but beware of the phishing scams that come with it. Learn how to identify fraudulent emails, protect your account, and avoid falling victim to deception. These tips will ensure your ad journey stays safe and secure.
#ad account phishing#ad manager phishing alerts#avoid Facebook phishing#email scams from Facebook#Facebook account safety#Facebook ad scams#Facebook ad security#Facebook phishing#Facebook scam emails#Facebook security tips#Facebook spam alerts#fake Facebook notifications#how to secure Facebook ads#Meta scams#phishing prevention tips#phishing red flags#phishing scams#phishing warning signs#protecting Facebook account#secure Facebook ads#social media security#spoofed Meta emails#stop phishing scams#two-step verification for Facebook
0 notes
Text
Ad-tech targeting is an existential threat

I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me TORONTO on SUNDAY (Feb 23) at Another Story Books, and in NYC on WEDNESDAY (26 Feb) with JOHN HODGMAN. More tour dates here.

The commercial surveillance industry is almost totally unregulated. Data brokers, ad-tech, and everyone in between – they harvest, store, analyze, sell and rent every intimate, sensitive, potentially compromising fact about your life.
Late last year, I testified at a Consumer Finance Protection Bureau hearing about a proposed new rule to kill off data brokers, who are the lynchpin of the industry:
https://pluralistic.net/2023/08/16/the-second-best-time-is-now/#the-point-of-a-system-is-what-it-does
The other witnesses were fascinating – and chilling, There was a lawyer from the AARP who explained how data-brokers would let you target ads to categories like "seniors with dementia." Then there was someone from the Pentagon, discussing how anyone could do an ad-buy targeting "people enlisted in the armed forces who have gambling problems." Sure, I thought, and you don't even need these explicit categories: if you served an ad to "people 25-40 with Ivy League/Big Ten law or political science degrees within 5 miles of Congress," you could serve an ad with a malicious payload to every Congressional staffer.
Now, that's just the data brokers. The real action is in ad-tech, a sector dominated by two giant companies, Meta and Google. These companies claim that they are better than the unregulated data-broker cowboys at the bottom of the food-chain. They say they're responsible wielders of unregulated monopoly surveillance power. Reader, they are not.
Meta has been repeatedly caught offering ad-targeting like "depressed teenagers" (great for your next incel recruiting drive):
https://www.technologyreview.com/2017/05/01/105987/is-facebook-targeting-ads-at-sad-teens/
And Google? They just keep on getting caught with both hands in the creepy commercial surveillance cookie-jar. Today, Wired's Dell Cameron and Dhruv Mehrotra report on a way to use Google to target people with chronic illnesses, people in financial distress, and national security "decision makers":
https://www.wired.com/story/google-dv360-banned-audience-segments-national-security/
Google doesn't offer these categories itself, they just allow data-brokers to assemble them and offer them for sale via Google. Just as it's possible to generate a target of "Congressional staffers" by using location and education data, it's possible to target people with chronic illnesses based on things like whether they regularly travel to clinics that treat HIV, asthma, chronic pain, etc.
Google claims that this violates their policies, and that they have best-of-breed technical measures to prevent this from happening, but when Wired asked how this data-broker was able to sell these audiences – including people in menopause, or with "chronic pain, fibromyalgia, psoriasis, arthritis, high cholesterol, and hypertension" – Google did not reply.
The data broker in the report also sold access to people based on which medications they took (including Ambien), people who abuse opioids or are recovering from opioid addiction, people with endocrine disorders, and "contractors with access to restricted US defense-related technologies."
It's easy to see how these categories could enable blackmail, spear-phishing, scams, malvertising, and many other crimes that threaten individuals, groups, and the nation as a whole. The US Office of Naval Intelligence has already published details of how "anonymous" people targeted by ads can be identified:
https://www.odni.gov/files/ODNI/documents/assessments/ODNI-Declassified-Report-on-CAI-January2022.pdf
The most amazing part is how the 33,000 targeting segments came to public light: an activist just pretended to be an ad buyer, and the data-broker sent him the whole package, no questions asked. Johnny Ryan is a brilliant Irish privacy activist with the Irish Council for Civil Liberties. He created a fake data analytics website for a company that wasn't registered anywhere, then sent out a sales query to a brokerage (the brokerage isn't identified in the piece, to prevent bad actors from using it to attack targeted categories of people).
Foreign states, including China – a favorite boogeyman of the US national security establishment – can buy Google's data and target users based on Google ad-tech stack. In the past, Chinese spies have used malvertising – serving targeted ads loaded with malware – to attack their adversaries. Chinese firms spend billions every year to target ads to Americans:
https://www.nytimes.com/2024/03/06/business/google-meta-temu-shein.html
Google and Meta have no meaningful checks to prevent anyone from establishing a shell company that buys and targets ads with their services, and the data-brokers that feed into those services are even less well-protected against fraud and other malicious act.
All of this is only possible because Congress has failed to act on privacy since 1988. That's the year that Congress passed the Video Privacy Protection Act, which bans video store clerks from telling the newspapers which VHS cassettes you have at home. That's also the last time Congress passed a federal consumer privacy law:
https://en.wikipedia.org/wiki/Video_Privacy_Protection_Act
The legislative history of the VPPA is telling: it was passed after a newspaper published the leaked video-rental history of a far-right judge named Robert Bork, whom Reagan hoped to elevate to the Supreme Court. Bork failed his Senate confirmation hearings, but not because of his video rentals (he actually had pretty good taste in movies). Rather, it was because he was a Nixonite criminal and virulent loudmouth racist whose record was strewn with the most disgusting nonsense imaginable).
But the leak of Bork's video-rental history gave Congress the cold grue. His video rental history wasn't embarrassing, but it sure seemed like Congress had some stuff in its video-rental records that they didn't want voters finding out about. They beat all land-speed records in making it a crime to tell anyone what kind of movies they (and we) were watching.
And that was it. For 37 years, Congress has completely failed to pass another consumer privacy law. Which is how we got here – to this moment where you can target ads to suicidal teens, gambling addicted soldiers in Minuteman silos, grannies with Alzheimer's, and every Congressional staffer on the Hill.
Some people think the problem with mass surveillance is a kind of machine-driven, automated mind-control ray. They believe the self-aggrandizing claims of tech bros to have finally perfected the elusive mind-control ray, using big data and machine learning.
But you don't need to accept these outlandish claims – which come from Big Tech's sales literature, wherein they boast to potential advertisers that surveillance ads are devastatingly effective – to understand how and why this is harmful. If you're struggling with opioid addiction and I target an ad to you for a fake cure or rehab center, I haven't brainwashed you – I've just tricked you. We don't have to believe in mind-control to believe that targeted lies can cause unlimited harms.
And those harms are indeed grave. Stein's Law predicts that "anything that can't go on forever eventually stops." Congress's failure on privacy has put us all at risk – including Congress. It's only a matter of time until the commercial surveillance industry is responsible for a massive leak, targeted phishing campaign, or a ghastly national security incident involving Congress. Perhaps then we will get action.
In the meantime, the coalition of people whose problems can be blamed on the failure to update privacy law continues to grow. That coalition includes protesters whose identities were served up to cops, teenagers who were tracked to out-of-state abortion clinics, people of color who were discriminated against in hiring and lending, and anyone who's been harassed with deepfake porn:
https://pluralistic.net/2023/12/06/privacy-first/#but-not-just-privacy

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/02/20/privacy-first-second-third/#malvertising

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#google#ad-tech#ad targeting#surveillance capitalism#vppa#video privacy protection act#mind-control rays#big tech#privacy#privacy first#surveillance advertising#behavioral advertising#data brokers#cfpb
526 notes
·
View notes
Text
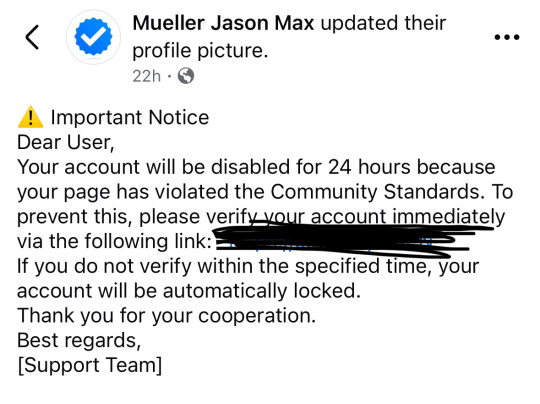
Here is an example of a phishing support scam attempt on Facebook that was a public post tagging my art account lol
I’m not censoring the persons name they tagged my art page publicly where anyone can see it so I’m shaming them and teaching you how to spot phishing scams. I’ve only edited out the scam link.
Mueller Jason Max updated their profile picture.
Important Notice
Dear User,
Your account will be disabled for 24 hours because your page has violated the Community Standards. To prevent this, please verify vour account immediately via the following link: (redacted)
If you do not verify within the specified time, your account will be automatically locked.
Thank you for your cooperation.
Best regards,
[Support Team]
74 notes
·
View notes
Text
Nearly got scammed and all I got was this dog

tl;dr: I fell for one of the most basic blunders. If a real person wants to commission me, please follow my blog first and be ready for a 20% payment upfront before I start on a piece.
I'm a little embarrassed to admit they got me with this, but maybe posting it may help prevent it from happening to someone else.
A couple weeks back I uploaded my tenth post on Tumblr, and I got a comment from someone asking me for a commission. There were many red flags I should have caught before giving it any more thought: They weren't following me, they hadn't posted anything at all to their blog, and their grammar was atrocious.
But I was curious, and figured even if it ended up being fake it would be good practice. So I messaged them and we got a plan going. They played their part well. They asked me to make 5 pieces of their "son's dog" and gave photos for reference, and they even said they wouldn't pay more than $40 for any individual piece due to a bad experience they had with an artist in the past. This being my first rodeo, I thought that it was legit, and this was just some cranky lady who just wanted some art.
Anyway I finished the first piece (pictured above) and they met me with high praise, saying I did amazing (honestly their high opinion of my work should have been the biggest red flag of all, but remember: this was two weeks ago. I was still a fool). Then we discussed payment. They were strangely eager to get to this part, even though I just figured we'd negotiate the price now and then I'd ask for the payment after I'd finished. They asked If I had a Paypal. I did not, so I set one up. Then, in order to "pay" me, the said they needed my email. I gave them my Paypal username, but they said it didn't work. I then tried giving the name attached to my Paypal, but they kept saying they needed my email. Stupidly, I figured that was just how it worked, so I sent my email address.
Here's where the real shady stuff happened. Not long after I shared my email, I recieved an email from (supposedly) Paypal saying that they had paid me the agreed-upon amount, but that I had set up my account wrong and in order to increase the limit set on payments I could recieve, I had to ask the payer to pay me more in order to make the total equal to $300, and then immediately pay them back the extra money. I still feel so stupid for falling for this. In hindsight, it was kind of a brilliant scam. They managed to make me feel like I was the one doing something sketchy, and I fell right into it.
I apologetically messaged them explaining the email I got. they told me they had received a similar email and they promised to do pay the amount if I agreed to pay them back. Soon after I got another email saying they had paid the extra amount.
If it weren't for the fact that gmail caught it as a fake Paypal email, I probably would have paid them that money and lost all my human rights or something. Luckily though, Gmail left a little thing next to the email name saying it was a suspicious address. So I did some Googling and realized that neither of the emails I'd received were from Paypal's official email. I had been duped, and I nearly fell for it. I swiftly blocked and reported them, and reported the fake email addresses to Paypal's phishing services.
In retribution for this attack on my innocently optimistic view of the internet, I have posted the one piece I did for them above. Might as well make some use of it.
A PSA to any fellow newbies to posting art online: be careful. In the future I will be much more careful about the commission requests I accept. I will not be responding to any unless they come from someone who follows my blog, and agrees to pay 20% of the commission price before I start on anything. Additionally, it would be appreciated if you include with your commission request some weird, out-of-pocket statement that a bot wouldn't say, just to prove you're real, though that is not a requirement.
Still can't believe I almost fell for such an obvious scam.
#art#commission scams#scam warning#biggest red flag had to be that they praised my work so blandly#seriously all they said when I asked what they thought was “wow it looks so good” like give me something to work with here#you are not immune to scams#furry#artists on tumblr#beginner artist
9 notes
·
View notes
Text
Picking up where my last post left off.
I am editing some things down. I will be sharing non-political facts and personal concerns as they relate to me on a personal level through my job. My opinions and beliefs do not represent the VA, the government, or any political party. These posts are to encourage transparency for all.
More emails started to come through.
The next emails we got were strange. As federal employees we are held to federal level of safety and HIPAA compliance. So we often see phishing scams and tests in our emails to test for security vulnerabilities.
They looked like this:
1/24/2025


The lack of information or notice on this was strange. We had service wide morning meetings about if this was a scam. People were hesitant about responding. I personally chose not to. I’ve lived long enough on the internet to know that no action is better than hasty responses.
We were tentatively reassured by our leadership that the emails were “legit”. I still chose not to respond. None of it felt right.
We had a meeting with our team about the previous email. About how divisive the wording was. How scary it felt to be told we could face consequences for not “reporting” on each other. But again. Our supervisors are held to the Hatch Act. They couldn’t say anything except they they know that “some of our staff may be having strong feelings and they’re here for us”.
I feel bad for my coworkers. We’re sitting on the rockiest foundation and still trying to show up daily to help others.
As silly as it seems to be stressed over some emails, they feel like much bigger omens to things we are unable to prevent.
Us leaving is what they want, but staying is hurting myself and the team around me.
I saw the post on Reddit when I looked up OPM (who apparently sent the email). It only solidified my suspicions that something in these emails wasn’t right.

Disclaimer: this post is for educational purposes and is in no way supporting any particular political party and is not meant to incite any political activity
#us politics#politics#president trump#federal government#elon musk#federal workers#federal workforce
15 notes
·
View notes
Text
New Rentry Problem :/
Ok a lil bit different from my other posts and stuff, but I feel like I need to say something about this.
I understand how the new advertisements are annoying, but are required to keep this site going. That is not my main problem. My main problem is with the new site redirecting that is occurring
Basically, the website known as Rentry has been having some issues staying up and public. So, they are adding more advertisements. Again, not the reason I'm posting. Whenever you click on a point on a specific person's Rentry, including images and links to legitimate websites, you will be redirected to malicious and phishing websites.
I am someone currently going to college for Cybersecurity. While I dont, necessarily side with Rentry on this, I understand somewhat why they did this.
HOWEVER, this site is used for mostly links and images. That's the problem. I know a thing or two about being secure online. I have two certifications saying so, and three more on the way in a month. My point being that I myself may know how to deal with these types of problems, others may not.
Such example is web graphics. I use Rentry for my collection. If you wanted to click on an image to use, you wont get the link to the image. You will be redirected to a website meant to cause harm to your device. Websites that will probably be taken down in 24 hours because of their false nature. Websites that are harmful, fake, and probably illegal in multiple fields for violating safe protocols.
Some of these websites are fishy as heck and are ok to be on as long as you dont click on anything. Some pop up more harmful websites, some cause harm instantly. Some are wayyy worse than others. ESPECIALLY if you dont know whats going on.
So to anyone who looks at these sites, uses theses sites, or just knows about these sites, please be careful. This is a severe issue, and this site is putting you in harms way.
Please find other sites to use. I myself am switching to Neocities, and I recommend others who use this site for various images or whatever do the same thing.
Not only is this problem harmful and a threat to your device, it is also a very sketchy practice. Most sites don't do this unless they are very on the down-low and doing some fishy stuff themselves.
If you want some HTML basics, I am here to help, although I am still learning some more about it as well. Other tutorials are available and there to help.
This is a post I am making to inform and hopefully prevent someone from turning their device to mush from this one website choosing this advertisement practice.
Please stay safe, and please be careful <3
#rentry graphics#rentry#please be careful everyone#spreading awareness#web graphics#online safety#internet safety#avoid rentry
9 notes
·
View notes
Text
Microsoft raced to put generative AI at the heart of its systems. Ask a question about an upcoming meeting and the company’s Copilot AI system can pull answers from your emails, Teams chats, and files—a potential productivity boon. But these exact processes can also be abused by hackers.
Today at the Black Hat security conference in Las Vegas, researcher Michael Bargury is demonstrating five proof-of-concept ways that Copilot, which runs on its Microsoft 365 apps, such as Word, can be manipulated by malicious attackers, including using it to provide false references to files, exfiltrate some private data, and dodge Microsoft’s security protections.
One of the most alarming displays, arguably, is Bargury’s ability to turn the AI into an automatic spear-phishing machine. Dubbed LOLCopilot, the red-teaming code Bargury created can—crucially, once a hacker has access to someone’s work email—use Copilot to see who you email regularly, draft a message mimicking your writing style (including emoji use), and send a personalized blast that can include a malicious link or attached malware.
“I can do this with everyone you have ever spoken to, and I can send hundreds of emails on your behalf,” says Bargury, the cofounder and CTO of security company Zenity, who published his findings alongside videos showing how Copilot could be abused. “A hacker would spend days crafting the right email to get you to click on it, but they can generate hundreds of these emails in a few minutes.”
That demonstration, as with other attacks created by Bargury, broadly works by using the large language model (LLM) as designed: typing written questions to access data the AI can retrieve. However, it can produce malicious results by including additional data or instructions to perform certain actions. The research highlights some of the challenges of connecting AI systems to corporate data and what can happen when “untrusted” outside data is thrown into the mix—particularly when the AI answers with what could look like legitimate results.
Among the other attacks created by Bargury is a demonstration of how a hacker—who, again, must already have hijacked an email account—can gain access to sensitive information, such as people’s salaries, without triggering Microsoft’s protections for sensitive files. When asking for the data, Bargury’s prompt demands the system does not provide references to the files data is taken from. “A bit of bullying does help,” Bargury says.
In other instances, he shows how an attacker—who doesn’t have access to email accounts but poisons the AI’s database by sending it a malicious email—can manipulate answers about banking information to provide their own bank details. “Every time you give AI access to data, that is a way for an attacker to get in,” Bargury says.
Another demo shows how an external hacker could get some limited information about whether an upcoming company earnings call will be good or bad, while the final instance, Bargury says, turns Copilot into a “malicious insider” by providing users with links to phishing websites.
Phillip Misner, head of AI incident detection and response at Microsoft, says the company appreciates Bargury identifying the vulnerability and says it has been working with him to assess the findings. “The risks of post-compromise abuse of AI are similar to other post-compromise techniques,” Misner says. “Security prevention and monitoring across environments and identities help mitigate or stop such behaviors.”
As generative AI systems, such as OpenAI’s ChatGPT, Microsoft’s Copilot, and Google’s Gemini, have developed in the past two years, they’ve moved onto a trajectory where they may eventually be completing tasks for people, like booking meetings or online shopping. However, security researchers have consistently highlighted that allowing external data into AI systems, such as through emails or accessing content from websites, creates security risks through indirect prompt injection and poisoning attacks.
“I think it’s not that well understood how much more effective an attacker can actually become now,” says Johann Rehberger, a security researcher and red team director, who has extensively demonstrated security weaknesses in AI systems. “What we have to be worried [about] now is actually what is the LLM producing and sending out to the user.”
Bargury says Microsoft has put a lot of effort into protecting its Copilot system from prompt injection attacks, but he says he found ways to exploit it by unraveling how the system is built. This included extracting the internal system prompt, he says, and working out how it can access enterprise resources and the techniques it uses to do so. “You talk to Copilot and it’s a limited conversation, because Microsoft has put a lot of controls,” he says. “But once you use a few magic words, it opens up and you can do whatever you want.”
Rehberger broadly warns that some data issues are linked to the long-standing problem of companies allowing too many employees access to files and not properly setting access permissions across their organizations. “Now imagine you put Copilot on top of that problem,” Rehberger says. He says he has used AI systems to search for common passwords, such as Password123, and it has returned results from within companies.
Both Rehberger and Bargury say there needs to be more focus on monitoring what an AI produces and sends out to a user. “The risk is about how AI interacts with your environment, how it interacts with your data, how it performs operations on your behalf,” Bargury says. “You need to figure out what the AI agent does on a user's behalf. And does that make sense with what the user actually asked for.”
25 notes
·
View notes
Text
Unnecessarily compiling sensitive information can be as damaging as actively trying to steal it. For example, the Cybernews research team discovered a plethora of supermassive datasets, housing billions upon billions of login credentials. From social media and corporate platforms to VPNs and developer portals, no stone was left unturned.
Our team has been closely monitoring the web since the beginning of the year. So far, they’ve discovered 30 exposed datasets containing from tens of millions to over 3.5 billion records each. In total, the researchers uncovered an unimaginable 16 billion records.
None of the exposed datasets were reported previously, bar one: in late May, Wired magazine reported a security researcher discovering a “mysterious database” with 184 million records. It barely scratches the top 20 of what the team discovered. Most worryingly, researchers claim new massive datasets emerge every few weeks, signaling how prevalent infostealer malware truly is.
“This is not just a leak – it’s a blueprint for mass exploitation. With over 16 billion login records exposed, cybercriminals now have unprecedented access to personal credentials that can be used for account takeover, identity theft, and highly targeted phishing. What’s especially concerning is the structure and recency of these datasets – these aren’t just old breaches being recycled. This is fresh, weaponizable intelligence at scale,” researchers said.
The only silver lining here is that all of the datasets were exposed only briefly: long enough for researchers to uncover them, but not long enough to find who was controlling vast amounts of data. Most of the datasets were temporarily accessible through unsecured Elasticsearch or object storage instances.
What do the billions of exposed records contain?
Researchers claim that most of the data in the leaked datasets is a mix of details from stealer malware, credential stuffing sets, and repackaged leaks.
There was no way to effectively compare the data between different datasets, but it’s safe to say overlapping records are definitely present. In other words, it’s impossible to tell how many people or accounts were actually exposed.
However, the information that the team managed to gather revealed that most of the information followed a clear structure: URL, followed by login details and a password. Most modern infostealers – malicious software stealing sensitive information – collect data in exactly this way.
Information in the leaked datasets opens the doors to pretty much any online service imaginable, from Apple, Facebook, and Google, to GitHub, Telegram, and various government services. It’s hard to miss something when 16 billion records are on the table.
According to the researchers, credential leaks at this scale are fuel for phishing campaigns, account takeovers, ransomware intrusions, and business email compromise (BEC) attacks.
“The inclusion of both old and recent infostealer logs – often with tokens, cookies, and metadata – makes this data particularly dangerous for organizations lacking multi-factor authentication or credential hygiene practices,” the team said.
What dataset exposed billions of credentials?
The datasets that the team uncovered differ widely. For example, the smallest, named after malicious software, had over 16 million records. Meanwhile, the largest one, most likely related to the Portuguese-speaking population, had over 3.5 billion records. On average, one dataset with exposed credentials had 550 million records.
Some of the datasets were named generically, such as “logins,” “credentials,” and similar terms, preventing the team from getting a better understanding of what’s inside. Others, however, hinted at the services they’re related to.
For example, one dataset with over 455 million records was named to indicate its origins in the Russian Federation. Another dataset, with over 60 million records, was named after Telegram, a cloud-based instant messaging platform.
“The inclusion of both old and recent infostealer logs – often with tokens, cookies, and metadata – makes this data particularly dangerous for organizations lacking multi-factor authentication or credential hygiene practices,”
While naming is not the best way to deduce where the data comes from, it seems some of the information relates to cloud services, business-oriented data, and even locked files. Some dataset names likely point to a form of malware that was used to collect the data.
It is unclear who owns the leaked data. While it could be security researchers that compile data to check and monitor data leaks, it’s virtually guaranteed that some of the leaked datasets were owned by cybercriminals. Cybercriminals love massive datasets as aggregated collections allow them to scale up various types of attacks, such as identity theft, phishing schemes, and unauthorized access.
A success rate of less than a percent can open doors to millions of individuals, who can be tricked into revealing more sensitive details, such as financial accounts. Worryingly, since it's unclear who owns the exposed datasets, there’s little impact users can do to protect themselves.
However, basic cyber hygiene is essential. Using a password manager to generate strong, unique passwords, and updating them regularly, can be the difference between a safe account and stolen details. Users should also review their systems for infostealers, to avoid losing their data to attackers.
No, Facebook, Google, and Apple passwords weren’t leaked. Or were they?
With a dataset containing 16 billion passwords, that’s equivalent to two leaked accounts for every person on the planet.
We don’t really know how many duplicate records there are, as the leak comes from multiple datasets. However, some reporting by other media outlets can be quite misleading. Some claim that Facebook, Google, and Apple credentials were leaked. While we can’t completely dismiss such claims, we feel this is somewhat inaccurate.
Bob Diachenko, a Cybernews contributor, cybersecurity researcher, and owner of SecurityDiscovery.com, is behind this recent major discovery.
16-billion-record data breach signals a shift in the underground world
According to Cybernews researcher Aras Nazarovas, this discovery might signal that criminals are abandoning previously popular methods of obtaining stolen data.
"The increased number of exposed infostealer datasets in the form of centralized, traditional databases, like the ones found be the Cybernews research team, may be a sign, that cybercriminals are actively shifting from previously popular alternatives such as Telegram groups, which were previously the go-to place for obtaining data collected by infostealer malware," Nazarovas said.
He regularly works with exposed datasets, ensuring that defenders secure them before threat actors can access them.
Here’s what Nazarovas suggests you should do to protect yourself.
"Some of the exposed datasets included information such as cookies and session tokens, which makes the mitigation of such exposure more difficult. These cookies can often be used to bypass 2FA methods, and not all services reset these cookies after changing the account password. Best bet in this case is to change your passwords, enable 2FA, if it is not yet enabled, closely monitor your accounts, and contact customer support if suspicious activity is detected."
Billions of records exposed online: recent leaks involve WeChat, Alipay
Major data leaks, with billions of exposed records, have become nearly ubiquitous. Last week, Cybernews wrote about what is likely the biggest data leak to ever hit China, billions of documents with financial data, WeChat and Alipay details, as well as other sensitive personal data.
Last summer, the largest password compilation with nearly ten billion unique passwords, RockYou2024, was leaked on a popular hacking forum. In 2021, a similar compilation with over 8 billion records was leaked online.
In early 2024, the Cybernews research team discovered what is likely still the largest data leak ever: the Mother of All Breaches (MOAB), with a mind-boggling 26 billion records.
16 billion passwords exposed: how to protect yourself
Huge datasets of passwords spill onto the dark web all the time, highlighting the need to change them regularly. This also demonstrates just how weak our passwords still are.
Last year, someone leaked the largest password compilation ever, with nearly ten billion unique passwords published online. Such leaks pose severe threats to people who are prone to reusing passwords.
Even if you think you are immune to this or other leaks, go and reset your passwords just in case.
Select strong, unique passwords that are not reused across multiple platforms
Enable multi-factor authentication (MFA) wherever possible
Closely monitor your accounts
Contact customer support in case of any suspicious activity
4 notes
·
View notes
Text
Aasghh having to lock down all of my AO3 fics really sucks, but until the site that's been stealing fics gets taken down, my fics are only going to be visible to registered AO3 users. 😭
Here are some resources for y'all regarding the fic stealing site↓↓↓
*•°INSTRUCTIONS°•*
This site is a phishing scam
• DO NOT drive traffic to the site by opening or interacting with it (that allows site to steal more fics)
• DO NOT give the site your personal information
• DO lock your account to logged in users only to prevent further or possible theft
• DO report the site!
THESE LINKS ARE HOW YOU CAN REPORT THE SITE↓
Google
https://safebrowsing.google.com/safebrowsing/report_phish/?hl=en
Tucows
https://tucowsdomains.com/abuse-form/copyright/
Cloudflare
https://www.cloudflare.com/en-au/trust-hub/reporting-abuse/
IF you have read the instructions the website name is below the cut. AGAIN: DO NOT INTERACT WITH THE WEBSITE. DO NOT click on it. DO NOT look if your works are on it. Just report it if you're concerned that they are.
REMINDER: DO NOT DO WHAT THE POST BELOW SAYS TO DO. This person was not educated when they made this post.
• Do not click on it.
• Do not look if your works are on it — getting clicks allows them to steal more writing —
• Just report it if you're concerned that your fics are/could be on there.
• Locking down your works on AO3/only making them visible to registered users is the best way to prevent them from being stolen. (You can also make use of the setting in your AO3 profile that hides your works from search engines. So if someone looks up your fic on Google or whatever, it won't pop up.)

ONE LAST TIME:
• DO NOT DO WHAT THE POST ABOVE SAYS.
• JUST REPORT THE SITE.
• DON'T GO TO THE SITE.
#undertale fandom#utmv#undertale au#ut au#undertale sans#ut aus#sans undertale#ao3 fanfic#ao3 writer#ao3feed#ao3
24 notes
·
View notes
Text
Cyber Law Experts in Delhi – Protecting You Against Digital Fraud & Cyber Attacks
By admin / May 12, 2025
🔐 Cyber Crime Law Firm in Delhi – Defending Digital Rights with Legal Expertise

In today’s hyper-connected world, cybercrime is one of the most pressing threats affecting individuals, startups, and corporations alike. From online financial fraud to cyberbullying and hacking, digital crimes are on the rise — and you need expert legal protection. At Patent24x7, we stand as a leading cyber crime law firm in Delhi, providing specialized legal solutions to fight and prevent cyber offenses.

⚖️ What Does a Cyber Crime Law Firm in Delhi Do?
As technology evolves, so does the complexity of cybercrimes. Legal support from cyber law experts is crucial to:
File police complaints against online fraud
Initiate legal action in cases of cyber defamation, stalking, phishing, and data breaches
Defend against wrongful cybercrime allegations
Ensure corporate compliance with data protection and IT laws
🔍 Services Offered by Patent24x7 – Cyber Law Experts in Delhi
✅ Online Fraud Recovery
We help individuals and businesses reclaim lost money from UPI frauds, scam websites, fake trading apps, cryptocurrency fraud, and more.
✅ Cyber Complaint Filing
Get professional support to file a complaint at the Delhi Cyber Crime Cell or the National Cyber Crime Reporting Portal.
✅ Social Media & Email Harassment
Legal action for cases involving stalking, threats, morphed images, and impersonation on social platforms.
✅ Data Breach & Hacking
We assist tech firms and startups with legal redress and compliance in case of data theft or system breaches.
✅ Legal Defense in IT Offenses
Wrongfully accused? Our cybercrime lawyers in Delhi help you present a strong legal defense.
✅ Cybersecurity Legal Consulting
Advisory for startups, fintech companies, and IT firms on IT Act, data protection, and cyber compliance policies.
👨⚖️ Why Choose Patent24x7 as Your Cyber Crime Law Firm in Delhi?
🏛️ Expert Team of Cyber Lawyers
🌐 Tech-Savvy Legal Approach
📞 24×7 Legal Support
⚙️ Specialized in Online Fraud & Data Crimes
🔐 Client Confidentiality & Transparent Fees
Whether you’re filing a complaint or need urgent legal help, our experienced lawyers understand the legal, technical, and investigative side of cyber law.
📍 Why Delhi Residents Trust Patent24x7
Delhi is not just India’s capital—it’s a cybercrime hotspot. That’s why Patent24x7 has developed specific legal frameworks and rapid-response methods tailored to the Delhi region’s needs.
Whether it’s recovering funds or responding to a data breach, they know the landscape and the local procedures better than most.
❓ Frequently Asked Questions (FAQs)
Q1: How do I report a cybercrime in Delhi?
A: You can file a complaint at the Cyber Cell, Delhi Police, or report it via the National Cyber Crime Portal. Our team can guide you through every legal step.
Q2: Can I recover money from online fraud?
A: Yes, if action is taken quickly, we can help you trace and recover your funds legally via cyber police and banking channels.
Q3: Is online defamation punishable by law?
A: Yes. Posting defamatory content online can be penalized under the IT Act and IPC Sections like 499 and 500.
Q4: Do you provide corporate cybersecurity legal consulting?
A: Absolutely. We offer customized compliance policies, NDAs, and legal audits to protect your business from cyber threats.
📞 Contact the Best Cyber Crime Law Firm in Delhi – Patent24x7
🌐 Website / Contact Us – https://www.patent24x7.com/about-us/ 📺 YouTube – https://www.youtube.com/@Patent24x7 📘 Facebook – https://www.facebook.com/people/Patent24x7/61574451401299/ 📌 Pinterest – https://www.pinterest.com/patent24x7 📰 Blog – https://patent24x7online.blogspot.com/
📜 Disclaimer:
As per the rules of the Bar Council of India, this blog is for educational purposes only. It does not constitute solicitation or advertisement of legal services. Always consult a qualified lawyer for personalized legal advice.
#cybercrime#cyber law#digitalsafety#legal help#online fraud#patent24/7#hackingrecovery#cyber crime lawyer
2 notes
·
View notes
Text
What Are the Common Fake Personal Loan Apps?
The rise of digital lending has made it easier than ever to apply for a personal loan. However, with this convenience comes an increased risk of fraud. Fake personal loan apps have become a major concern, preying on unsuspecting borrowers with promises of quick approval and low interest rates. These fraudulent apps often steal personal data, demand upfront payments, and leave victims in financial distress.
Understanding how to identify fake personal loan apps and protect yourself from scams is essential for ensuring a safe borrowing experience. This article will highlight the risks associated with fake loan apps, common red flags to watch out for, and tips to stay secure when applying for a personal loan.
The Rise of Fake Personal Loan Apps
The increasing popularity of digital lending has led to a surge in fake personal loan apps that exploit borrowers. Scammers create these apps to collect sensitive information, demand fraudulent fees, or even misuse the borrower’s identity for illegal activities. Many victims only realize they have been scammed after their money is stolen or their credit profile is misused.
How Fake Loan Apps Operate
Fake personal loan apps typically follow a deceptive pattern to lure borrowers into their traps. Here’s how they operate:
Attractive Loan Offers – Fraudulent apps promote personal loans with minimal documentation, low interest rates, and instant approval, enticing users to download them.
Fake Registration Process – Borrowers are required to enter personal details, including bank account numbers, identity proofs, and credit card information.
Upfront Fees – Scammers demand processing fees, security deposits, or verification charges before disbursing the loan.
Unauthorized Access to Data – These apps request unnecessary permissions, such as access to contacts, messages, and call logs, which scammers misuse.
No Actual Loan Disbursement – Once the borrower pays the upfront fees, the scammers disappear without providing the loan.
Common Red Flags of Fake Personal Loan Apps
Recognizing the warning signs of a fraudulent loan app can save you from financial loss. Here are key red flags to watch for:
1. No Registration with Financial Authorities
Legitimate lenders are registered with regulatory bodies such as the Reserve Bank of India (RBI), Federal Trade Commission (FTC), or other financial authorities. If an app does not have proper regulatory approval, it is likely a scam.
2. Demand for Upfront Fees
Genuine lenders do not ask for upfront payments before loan approval. If an app requests a processing fee, security deposit, or verification charge before disbursing the loan, it’s a major red flag.
3. Poorly Designed and Unprofessional Interface
Fake personal loan apps often have poor user interfaces, multiple grammatical errors, and lack proper customer support. A lack of professionalism in app design and communication indicates fraudulent intent.
4. Excessive Permission Requests
Fraudulent apps demand access to contacts, messages, location, and even the camera, which is unnecessary for a personal loan application. These permissions are used to steal data or blackmail victims.
5. No Physical Address or Customer Support
Legitimate financial institutions provide a physical address and reliable customer support channels. Fake loan apps usually lack transparency and offer no proper means of contact.
6. High-Pressure Tactics
Scammers often pressure borrowers to act quickly, using phrases like “limited time offer” or “instant approval guaranteed.” Genuine lenders follow a structured verification process and do not rush applicants.
Notorious Fake Personal Loan Apps
Several fraudulent personal loan apps have been flagged by financial authorities. While these scams frequently change names, some of the most notorious ones include:
Cash Advance Pro – Known for demanding high upfront fees and disappearing after collecting money.
Quick Loan Now – Requests excessive permissions and misuses borrower data.
Easy Loan Fast – Promises instant approvals but requires security deposits that are never refunded.
Swift Cash Lenders – Lures victims with fake customer reviews and unrealistic loan offers.
Loan Hub Pro – Uses phishing techniques to steal banking credentials.
How to Protect Yourself from Fake Personal Loan Apps
To avoid falling victim to a fraudulent personal loan app, follow these security measures:
1. Download Apps from Official Sources
Only download loan apps from reputable platforms like Google Play Store or Apple App Store. Avoid downloading APK files from unknown sources, as they may contain malware.
2. Verify Lender Credentials
Before applying for a personal loan, check whether the lender is registered with financial authorities. Visit their official website and read customer reviews.
3. Avoid Providing Unnecessary Permissions
Do not grant access to contacts, messages, or other sensitive data unless it is essential for the loan application. Be cautious of apps that request excessive permissions.
4. Read User Reviews and Ratings
Genuine loan apps have positive reviews from verified customers. Look for red flags in user comments, such as complaints about fraud, high fees, or data theft.
5. Check the Privacy Policy
Legitimate lenders provide a clear privacy policy detailing how your data will be used. If the app lacks transparency, avoid using it.
6. Use Strong Security Measures
Enable two-factor authentication (2FA) on your bank and financial accounts to prevent unauthorized access. Keep your device protected with updated security software.
What to Do If You Fall Victim to a Fake Loan App
If you suspect that you have been scammed by a fake personal loan app, take immediate action:
1. Report the Scam to Authorities
Notify your country’s financial regulatory body, such as the FTC, RBI, or Cyber Crime Cell, about the fraudulent app.
2. Inform Your Bank
If you have shared banking details, contact your bank immediately to block transactions and secure your account.
3. File a Police Complaint
Report the scam to local law enforcement and provide evidence such as screenshots, messages, and transaction details.
4. Check Your Credit Report
Monitor your credit report for unauthorized loans taken in your name. If you find fraudulent activities, report them to credit bureaus.
5. Warn Others
Share your experience on online platforms to alert others about the fake loan app and prevent further scams.
Conclusion
Fake personal loan apps are a growing threat, targeting vulnerable borrowers with deceptive offers. By understanding the red flags and taking preventive measures, you can protect yourself from financial fraud. Always verify lender credentials, avoid upfront payments, and stay cautious when applying for a personal loan online. If you suspect fraudulent activity, act quickly to report and safeguard your financial security.
By staying informed and vigilant, you can ensure a safe and hassle-free borrowing experience in the digital lending space.
#personal loan online#nbfc personal loan#fincrif#bank#loan services#personal loans#loan apps#finance#personal laon#personal loan#Fake personal loan apps#Loan app scams#Personal loan fraud#How to identify fake loan apps#Fraudulent loan applications#Online loan scam warning signs#Loan phishing scams#Fake loan app red flags#Loan fraud prevention tips#Avoiding fake personal loans#Identity theft in loan applications#Personal loan scam alerts#Unauthorized loan approvals#Fake instant loan apps#Loan fraud protection strategies#Cybercrime loan scams#Fake loan app reporting#Loan scam customer complaints#Secure personal loan application#How to verify loan apps
2 notes
·
View notes
Text
Preventative IT Maintenance: Keeping Your Business Running Smoothly

With technology moving forward so fast, your business can’t operate without it. Computers, servers, cloud systems and software platforms have to be running smoothly to keep your team productive, defend confidential information and make sure customers receive a good experience.
Unfortunately, IT systems don’t manage themselves without attention.
This is why we need preventative IT maintenance. Regular car servicing makes sure your car avoids breakdowns and preventative IT support does the same for your systems. Here at Image IT, we know that companies who focus on IT before issues arise benefit a lot. We’ll now look at what preventative maintenance means and understand why it helps your business run smoothly.
What Does Preventative IT Maintenance Mean?
Taking care of your IT infrastructure ahead of time is called preventative maintenance. With preventative maintenance, you take action to make sure your systems are in good shape all the time, so you don’t have to rush to solve emergencies.
Such tasks refer to:
Tracking how the system is running
Putting security patches and new versions of the software into use
Regularly using antivirus and malware software
Testing the use of backup options
Updating both your device’s drivers and firmware
Checking the configurations for firewalls and networks
Exchanging ageing equipment to prevent any breakdowns
At Image IT, we set up specialized maintenance services that guarantee your technology remains in top condition and reduces the chance of risks and downtime.
Why Taking Care of Problems in Advance Is Crucial for Companies in Ireland
1. Minimize any time when your business is not working effectively.
Problems with your IT systems such as servers failing, networks breaking or bugs in software, may bring your work to a halt and cost you in both time and money. Doing preventative maintenance lets you catch and manage issues early and this means your business avoids the stress of dealing with major problems.
If a server begins to overheat, it’s possible to handle the issue before it crashes, so you won’t have to deal with expensive downtime and loss of data.
2. Prevent or Stop Cyber Attacks
More and more, businesses in Ireland are facing cyberattacks, most often small and medium-sized companies. Many attackers use old software, unpatched versions and networks that have not been properly set up.
Ongoing upkeep of security tools such as firewalls, antivirus software and system updates, makes it much less likely for your system to become a victim of ransomware, phishing or a data breach.
3. Increase the Lifespan of IT Assets
Just as changing the oil in your car lengthens its engine’s lifespan, looking after your IT equipment in the same way will help it work longer. Regularly taking care of computers stops them from wearing out and prevents too many replacements.
4. Raise the effectiveness of your staff.
This kind of slow work is frustrating and influences how your team feels about their work. If technology runs smoothly, your team won’t have to worry about systems or spend time finding IT solutions.
5. With time, the cost of IT will decrease.
Though it might feel like a pricey addition, upfront maintenance helps save money and prevents serious IT problems. One data breach, meeting replacement or lasting period of downtime can often be more expensive than all your ISP’s services put together.
Important Parts of a Well-Made IT Maintenance Plan
We create preventative maintenance strategies for your business that fit its individual requirements at Image IT. The method we use is:
We watch your systems around the clock.
We watch over your systems around the clock, spotting problems early and fixing them so they don’t impact your work.
Timely Updates and Patch Upgrades
We make sure your operating systems, applications and antivirus are always running on the latest versions.
Test the backup and recovery of your data.
We ensure your backups are properly configured and we regularly perform tests to see how fast you can recover data.
You can do a Network Health Check here.
We examine your network for good speed, serious security flaws and technology issues to confirm your system operates safely and properly.
Managing Assets and Deciding on Their Life
We watch over your equipment and make sure you can update your technology before it starts causing issues.
Support from the users and helpdesk
If your team has any IT questions or concerns, our friendly team is there to lend a non-technical helping hand.
Why Is Image IT a Great Solution?
Operating out of North Dublin, Image IT has been supporting company’s in Ireland for about 15 years. Our knowledgable team delivers helpful, consistent and friendly IT assistance to the companies here in New Zealand.
We are dedicated to forming long-term relationships with clients so we can do more than just address issues; we can help avoid them.
You will gain the following benefits when you work with us:
Transparent pricing
A quick response from the team
Customized maintenance services
Expert opinions offered in a personal way
If you have just a few devices or a complex IT structure, our solutions are designed to match your requirements and your budget.
Benefits You Can See in Life: An Example
There were many issues at one of our clients, a small financial services firm in Dublin, involving downtime in the network and software that was past its update. Following their sign up for our preventative maintenance, we set up a monitoring system, cleaned their network and ran scheduled updates.
The result? A 90% drop in IT issues reported by staff, faster systems, and peace of mind for their management team knowing their data and systems were protected.
Your Next Step: Secure Your Business with Preventative IT Support
Don’t wait for a system failure, data breach, or productivity drop to remind you of your IT vulnerabilities. Preventative maintenance is one of the smartest investments you can make in your business.
Let Image IT take the stress out of managing your technology — so you can focus on what you do best.
2 notes
·
View notes
Text
Alex Samuels at Daily Kos:
After losing their minds over Politico subscriptions, erroneously claiming they were funded by USAID, President Donald Trump and DOGE bro Elon Musk are now flipping out over an alleged $9 million that “radical left” Reuters was given as part of a defense contract in 2018. “GIVE BACK THE MONEY, NOW!” Trump posted to Truth Social in the wee hours of the morning on Thursday. It doesn’t take a genius to remember, though, that Trump was president in 2018, meaning any money Reuters received was given out under his leadership. What Trump also failed to mention in his late-night rant is that the money wasn’t given to Reuters’ newsroom but to a different wing of the company that operates separately from the news agency. The attacks on Reuters come as Trump’s administration has sought to discredit the mainstream media, which has so far included limiting credible outlets’ access to the White House and spreading lies about how they’re funded while propping up friendly right-wing podcasters and reporters. [...] After the contract, which expired in 2022, was revealed, Musk wrote another post to his social media platform where he falsely suggested that Reuters ran disinformation campaigns on the Pentagon’s behalf. In reality, the contract was paid to Thomson Reuters Special Services, which describes itself as a “trusted leader in delivering scalable solutions to governments and global institutions.” TRSS, a wholly separate subsidiary of the larger Reuters conglomerate, was given the money in the hopes that it could help prevent cyberattacks and phishing. In other words, it was a far more benign mission than what Musk and Trump suggested. The contract issued to TRSS was done so by the Air Force Research Laboratory and was funded by the Defense Advance Research Projects Agency.
Treasonous co-Presidents Elon Musk and Donald Trump spread bogus lies about Thomson Reuters.
#Donald Trump#Elon Musk#Thomson Reuters#Reuters#USAID#Thomson Reuters Special Services#Air Force#War On The Press#Mario Nawfal
8 notes
·
View notes
Text
The Intersection of Driver’s Licenses and Cybersecurity in 2025
As we look toward 2025, cybersecurity is becoming an increasingly critical aspect of the digital transformation of driver’s licenses. With more Canadians opting for digital driver’s licenses (DLs), ensuring these digital IDs are protected from cyber threats is paramount. The convergence of driver’s licenses and cybersecurity is reshaping how individuals manage their credentials and how governments secure sensitive information in the digital age.
The Rise of Digital Driver’s Licenses
Digital driver’s licenses have emerged as an essential part of Canada’s shift toward smarter, more efficient services. Provinces like Ontario, British Columbia, and Alberta have started offering digital licenses, allowing residents to store their DLs on smartphones and access them via secure apps. This shift is not only more convenient for drivers but also reduces physical waste and improves overall efficiency in verification processes.
However, with these advances come new risks, particularly related to cybersecurity. As digital licenses become more widespread, ensuring their security is a growing concern for both citizens and government agencies.
To stay updated on the latest digital licensing guidelines, licenseprep.ca is a valuable resource that provides information about digital driver’s licenses and the security protocols involved in their use.

Cybersecurity Challenges in Digital Licenses
While digital driver’s licenses offer many benefits, they also introduce several cybersecurity risks that need to be addressed:
1. Data Breaches and Hacking
With digital licenses stored on smartphones, there is the risk of data breaches or hacking. Cybercriminals could potentially gain unauthorized access to users’ personal information, leading to identity theft or fraudulent activities. Securing the digital infrastructure that houses these licenses is essential to mitigating these threats.
2. Phishing and Fraud
Phishing attacks, where cybercriminals impersonate legitimate institutions to steal sensitive data, are a growing concern. Digital licenses could be targeted by these malicious actors, tricking users into sharing login credentials or personal information under false pretenses.
3. Privacy Concerns
As digital driver’s licenses become more integrated with other smart city systems, the amount of data being shared and stored increases. Ensuring that user privacy is protected and that data isn’t misused is crucial. A robust data encryption system must be in place to prevent unauthorized access to users' sensitive information.
Solutions to Strengthen Cybersecurity
To safeguard the future of digital driver’s licenses, various cybersecurity measures are being implemented:
1. Encryption and Multi-Factor Authentication (MFA)
Using end-to-end encryption ensures that the information stored on a digital driver’s license is protected from unauthorized access. Additionally, multi-factor authentication (MFA) can be used to add an extra layer of security when accessing or updating license information.
2. Blockchain Technology
Blockchain technology offers a decentralized and secure way of verifying identity, which could be used to authenticate digital licenses. By storing data across multiple nodes, blockchain reduces the risk of single points of failure that could be exploited by cybercriminals.
3. Regular Security Audits and Updates
Governments and agencies responsible for digital licensing systems will need to conduct regular security audits to identify vulnerabilities. Timely security updates will also be crucial in protecting against emerging threats and keeping the systems up to date with the latest encryption protocols.
The Road Ahead
As Canada moves closer to a fully digital future, the intersection of driver’s licenses and cybersecurity will become even more important. With proper safeguards in place, digital driver’s licenses will not only provide convenience but will also ensure that citizens’ data remains secure.
For Canadians looking to stay informed about digital driver’s licenses and their role in the evolving digital landscape, licenseprep.ca is a helpful platform to track the latest updates and best practices in digital ID security.
#Cybersecurity#DigitalLicensing#SmartCities#DataPrivacy#Blockchain#DigitalDriverLicense#LicensePrep#FutureOfSecurity#SecureLicenses#LicenseprepCanada
2 notes
·
View notes