#isp radius solution
Explore tagged Tumblr posts
Text
ISP Cloud Billing Software: Features, Benefits & Best Tools

With internet usage becoming more prevalent, Internet Service Providers (ISPs) are finding the need to better manage customers, data usage, and payments. Most ISPs operate on very fluid business models which, unfortunately, traditional billing systems do not cater to. It is for that reason that many of the providers are turning to ISP cloud billing software, a turnaround solution that increases efficiency with automation, streamlining of workflows, and cushioning customer interactions.
What Is ISP Cloud Billing Software?
ISP cloud billing software is a solution to ISP’s billing problems as it automates and simplifies billing using a centralized platform available via the cloud. Unlike older billing system that depends on physical servers, cloud billing software is hosted online and can be accessed from anywhere, anytime. This permits ISPs to automate customer billing, data monitoring, subscription management and collection of payments electronically.
Key Features of ISP Cloud Billing Software
- Real-Time Usage Monitoring: Live tracking of bandwidth and data enables accurate billing and transparency for all users.
- Automated Invoicing & Payments: Recurring invoices as well as coupon-based payment automation can be seamlessly toggled through available gateways.
- Cloud-Based Dashboard: If gadgets have an internet connection, access to the entire billing system is guaranteed, done away is the time-consuming installation on premises.
- Customer Self-Service Portals: Users are granted permission to view their consumption, download invoices, make payments, and escalate support tickets.
- CRM Integration: Refresh customer databases to improve interactions and trim down communication, service adjustments, and user administration.
- Support API: Interact seamlessly with external tools and systems to create a tailored ISP ecosystem for management with Custom ISP Management Ecosystem.
Cloud Billing Benefits for ISPs
With ISP cloud billing software, companies gain the following benefits:
- Scalable: Scale up easily with hundreds or thousands of users without purchasing additional infrastructure.
- Automation: Spend less time on billing, usage alerts, payment reminders, etc., to automate tasks and reduce human error.
- Access from Anywhere: Interconnected systems allow you to manage your billing system from any location—perfect for multi-location or distributed ISPs.
- Security & Backup: Many cloud platforms encrypt data to store, backup regularly, and have automated recovery in case of data loss.
- Cost-Efficient: Pay only for what you use, without physical hardware spent, software upkeep, or servers requiring upgrades.
Top ISP Cloud Software Solutions
These are some of the most effective ISP Cloud billing software used globally:
- Splynx: Well-known amongst WISPs and fiber operators, Splynx provides all-in-one automation, CRM, and bandwidth control.
- Powercode: Provides an integration and customer portal as well as an easy to navigate user interface for small and medium-sized ISPs.
- NetElastic: Gained recognition for its automated billing system and its virtual broadband network gateway.
- ISPmate: A preferred option for ISPs in developing regions and is rapidly gaining popularity due to its region tailored compliance and customer behavior features.
ISPs should consider their size, budget, technical requirements, and the unique features and pricing options provided by each tool.
Final Thoughts
The operational model of ISPs is being changed by the adoption of cloud technology. With ISP cloud billing software, an ISP can automate intricate billing systems, boost customer happiness and enabling efficient scaling. A dependable billing solution places providers, whether they are startup WISPs or large-scale broadband providers, well positioned for future advancements.
#isp billing software in delhi#aaa solution for isp#best isp billing software#billing software for isp#isp billing software#isp billing solution#isp crm software#isp erp#isp management software#isp radius solution
0 notes
Text
6 Common Challenges in ISP Billing and Solutions
Effective billing systems form the backbone of any successful Internet Service Provider. More so, in the absence of a reliable and strong billing system, managing payments, customer accounts, and revenue tracking would be futile. Streamlined billing operations not only enhance the operational efficiency of ISPs, but also improve customer satisfaction.
ISPMate, a professional ISP Billing Solution Provider, is aware of these issues and offers innovative tools to help ISPs cope with them. Below are six common challenges that ISPs face in billing and how ISPMate provides an effective solution to address them.
Challenge 1: Managing Complex Pricing Structures
ISPs will experience a myriad of pricing models, tiered and promotional packages, and customized corporate packages. Managing these complexities manually or through old systems may lead to mistakes, dissatisfied customers, and revenue loss.
ISPMate's Solution:
ISPMate offers flexible configurations for billing, making it an easy system for ISPs to develop and manage custom plans. ISPMate provides the support of customizable price tiers with discounts and promotions, which can have all their billing done accurately and smoothly on every customer.
Challenge 2: Inefficient Payment Processing
Delayed and erroneous payments, payment workflows like manual invoice generation, and limited payment options cause frustration to the customers and unexplained cash flow to the ISPs.
Solution by ISPMate :
ISPMate streamlines payment processing through automated payment gateways, supports multiple currencies, and allows for recurring billing. Upon integration with popular payment platforms, ISPMate ensures hassle-free, secure, and uninterrupted transactions for both ISPs and their customers.
Challenge 3: Error-Prone Manual Processes
Manual interventions in billing processes lead to erroneous invoices, disputes, and wasted resources. These errors can ruin an ISP's reputation and lose customer trust over time.
ISPMate's Solution:
ISPMate No manual processing will be seen in the automation process. From generating the invoices to reconciling payments, everything is efficiently covered in the billings and reduces mistakes and saves time.
Challenge 4: Scale Back as Customer Base Expands
As ISPs expand their customer base, billing systems have to scale to accommodate higher demands. Legacy systems tend to struggle in trying to catch up, which causes delays and inefficiencies.
ISPMate offers cloud-based ISP Billing Solutions that are designed for scalability. Whether you’re serving a hundred customers or a hundred thousand, ISPMate’s platform ensures consistent performance and reliability as your business grows.
Challenge 5: Poor Integration with Other Systems
Billing operations are rarely standalone processes. Without integration with other systems like CRM, ticketing, and network monitoring tools, ISPs face data silos, operational inefficiencies, and a fragmented customer experience.
ISPMate’s Solution:
ISPMate's platform is fully integrable with various third-party systems, enabling seamless data flow and coordination. This unified approach helps enhance operational efficiency and provides an all-round view of customer interactions.
Challenge 6: Lack of Real-Time Reporting and Analytics
ISPs require access to real-time insights to track revenue, monitor customer trends, and make informed business decisions. Traditional billing systems often lack comprehensive reporting and analytics capabilities.
ISPMate Solution:
The ISPMate reports offer advanced reporting tools for ISPs. ISPs can look at real-time dashboards and customizable reports and track performance metrics and identify growth opportunities and optimize their operation.
Conclusion
Billings systems in an ISP dictate its success. The headache of complex pricing structures, inefficient payment processing, manual error, scalability, integration issues, and lack of analytics can thwart growth and customer satisfaction.
ISPMate comes back to these challenges and solutions with its own innovative ISP billing solutions so that ISPs can work smoothly and come ahead in competition.
Select ISPMate today for all-rounded billing service which empowers your ISP to thrive in a competitive market.
#isp crm software#Isp software for billing in Delhi#Isp billing software in delhi#best isp billing software#isp billing software in Delhi#isp management software#isp erp#isp billing software#ISP Billing Solution#billing software for isp#isp radius solution#AAA solution for isp#complaints management system
0 notes
Text
does a vpn protect from network admin wpa2 enterprise
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does a vpn protect from network admin wpa2 enterprise
VPN encryption
VPN encryption is a vital aspect of any Virtual Private Network (VPN) service that ensures the security and privacy of users' online activities. Encryption is the process of converting data into a code to prevent unauthorized access, and it plays a crucial role in safeguarding sensitive information transmitted over the internet.
When a user connects to a VPN server, their data is encrypted before being transmitted through a secure tunnel to the destination server. This encryption process involves scrambling the data using complex algorithms, making it virtually impossible for hackers, ISPs, or government agencies to intercept and decipher the information.
There are different levels of encryption used by VPN providers, with the most common being 128-bit and 256-bit AES encryption. The higher the number of bits, the more secure the encryption is, as it requires more computational power and time to crack the code.
By encrypting data, VPNs can protect users' privacy by hiding their online activities from prying eyes. This is particularly important when using public Wi-Fi networks, where cybercriminals often lurk to steal sensitive information like passwords, credit card details, and personal data.
In conclusion, VPN encryption is a crucial component of online security, providing users with peace of mind knowing that their internet traffic is protected from potential threats. It is essential to choose a reputable VPN provider that offers strong encryption to ensure the highest level of privacy and security online.
WPA2 Enterprise security
Title: Understanding the Robust Security of WPA2 Enterprise
In today's interconnected world, safeguarding sensitive data is paramount for businesses and organizations. One of the key components in achieving this is implementing robust security measures for wireless networks. WPA2 Enterprise stands out as a gold standard in wireless security protocols, offering a high level of protection against unauthorized access and data breaches.
Unlike its counterpart, WPA2 Personal, which is commonly used in home networks, WPA2 Enterprise is designed for larger-scale deployments in businesses, universities, and government institutions. It operates within a framework known as IEEE 802.1X, which provides authentication and authorization mechanisms for users and devices connecting to the network.
One of the primary features of WPA2 Enterprise is its use of Extensible Authentication Protocol (EAP), which enables a variety of authentication methods, including passwords, digital certificates, and smart cards. This multi-factor authentication adds an extra layer of security, making it significantly more challenging for attackers to compromise the network.
Furthermore, WPA2 Enterprise employs the use of a RADIUS (Remote Authentication Dial-In User Service) server, which centralizes authentication and access control. This allows administrators to manage user accounts, define access policies, and monitor network activity from a single point of control.
Moreover, WPA2 Enterprise supports dynamic encryption key generation, ensuring that each session between a client device and the network is encrypted with a unique key. This mitigates the risk of eavesdropping and replay attacks, enhancing the overall security posture of the network.
In conclusion, WPA2 Enterprise offers a robust and comprehensive security solution for organizations looking to protect their wireless networks and sensitive data. By implementing strong authentication mechanisms, centralized access control, and dynamic encryption, businesses can mitigate the risks posed by potential cyber threats and maintain the integrity of their network infrastructure.
Network administrator monitoring
Network administrator monitoring is a crucial aspect of ensuring the smooth operation and security of a company's network infrastructure. A network administrator is responsible for overseeing the management, maintenance, and optimization of a network to guarantee that it functions at its best capacity.
One of the primary tasks of a network administrator is to continuously monitor the network for any potential issues or anomalies. By utilizing monitoring tools and software, network administrators can keep track of network performance, traffic patterns, and security threats in real-time. Monitoring allows them to promptly identify and address any problems that may arise, preventing potential network downtime and data breaches.
Through monitoring, network administrators can also ensure that the network operates efficiently and effectively. They can analyze data traffic, identify areas of congestion or bottlenecks, and implement solutions to optimize network performance. Monitoring also enables network administrators to detect unauthorized access attempts or suspicious activities, helping to enhance network security and protect sensitive information.
Furthermore, network administrator monitoring plays a vital role in compliance with regulations and standards, as it helps in maintaining data integrity and privacy. By monitoring network activity, administrators can generate reports on network performance, security incidents, and compliance adherence, which are essential for audits and regulatory compliance.
In conclusion, network administrator monitoring is essential for maintaining a reliable and secure network environment. By actively monitoring network activity, administrators can ensure optimal performance, timely issue resolution, and adherence to compliance requirements, ultimately contributing to the overall success of an organization.
VPN tunneling
VPN tunneling is a crucial aspect of Virtual Private Networks (VPNs), playing a pivotal role in ensuring secure and private online communication. At its core, VPN tunneling involves the encapsulation of data within a secure "tunnel" as it travels between the user's device and the VPN server.
The process begins with the initiation of a VPN connection from the user's device to the VPN server. During this phase, encryption protocols such as IPSec (Internet Protocol Security) or OpenVPN are often employed to secure the data transmitted over the network. These protocols establish a secure channel, encrypting the data to prevent unauthorized access or interception by third parties.
Once the VPN connection is established, the data packets are encapsulated within a secure outer packet, effectively creating a "tunnel" through which the data can travel safely. This outer packet contains information necessary for routing the data to its destination, including the user's IP address and the VPN server's IP address.
As the encapsulated data traverses the internet, it remains protected from eavesdropping, surveillance, and other forms of cyber threats. This is especially crucial when accessing sensitive information or connecting to public Wi-Fi networks, where the risk of data interception is higher.
Moreover, VPN tunneling allows users to bypass geographical restrictions and censorship by masking their true IP address with that of the VPN server. This enables access to geo-blocked content and websites that may otherwise be inaccessible.
In conclusion, VPN tunneling is a fundamental mechanism that ensures the confidentiality, integrity, and security of data transmitted over the internet. By creating a secure "tunnel" between the user's device and the VPN server, VPN tunneling safeguards sensitive information and preserves online privacy in an increasingly interconnected world.
Data privacy and protection
Title: Safeguarding Your Digital Footprint: The Importance of Data Privacy and Protection
In today's digital age, where virtually every aspect of our lives is intertwined with technology, the importance of data privacy and protection cannot be overstated. From personal information stored on social media platforms to financial data used for online transactions, our digital footprint is vast and vulnerable. Therefore, understanding and implementing measures to safeguard this data is paramount.
Data privacy refers to the right of individuals to control how their personal information is collected, used, and shared. This includes everything from name and address to browsing history and preferences. Without adequate protection, this information can be exploited by malicious actors for various purposes, including identity theft, fraud, and targeted advertising.
To ensure data privacy, individuals must be vigilant about the platforms and services they use, opting for those with robust privacy policies and encryption measures. Additionally, regularly reviewing and updating privacy settings can help limit the amount of personal information that is accessible to third parties.
Data protection, on the other hand, involves safeguarding this information from unauthorized access, use, or disclosure. This requires employing security measures such as firewalls, encryption, and multi-factor authentication to prevent data breaches and cyber attacks.
Furthermore, businesses and organizations have a responsibility to prioritize data privacy and protection for their customers and clients. This includes implementing stringent security protocols, conducting regular audits, and providing clear and transparent privacy policies.
In conclusion, data privacy and protection are essential aspects of our digital lives. By taking proactive steps to safeguard our personal information and holding businesses accountable for their data practices, we can help create a safer and more secure online environment for everyone. Remember, your data is valuable – protect it accordingly.
0 notes
Text
0x0002#SA#Beating Mac Filter
Introduction
Mac address is a common concept for today's electronic device, every device has at least one mac address used for authentication and authorization when they connect to the network. A Mac address is 48-bits long, first 24-bits for factory identity, last 24-bits for user identity. In wireless world, almost every wifi-router can set Mac address filter to block illegal user access the network
The weakness of the protocol
If I didn't learn security, I would say Mac address is unique in the world. But the truth is, in the wireless world, mac address can be exploited bypassing the Mac filter in a wifi-router. There are many tools can be found on the internet to change our Mac address to another one. If we change our mac address to a legal user, then we can still access the internet.
Feasibility
This kind of attack is very common in the real world. Even most of the router using this method to cheap ISP connect multiple devices.
It can happen only a legal user is using the wireless network, then we can capture the mac address then make our mac as same as the legal user.
In the folwing steps, I will simulate the scenario of the attack in the real world
Steps:
Assume I am an attacker who is connecting a WIFI-router and surfing on the internet.
Then the router administrator find the attacker mac address to forbid attacker access the network

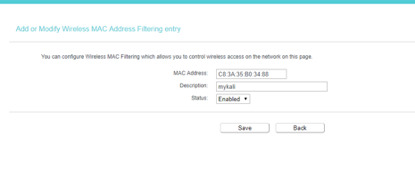
We can see that our system can not connect the wifi anymore
Then we init an attack to capture the mac address of a legal user
iwconfig #check our interface status airmon-ng check kill #close the conflict process airmon-ng start wlan0 #open our interface as monitor mode airodump-ng wlan0mon #start monitoring and find the target channel and bssid mac address
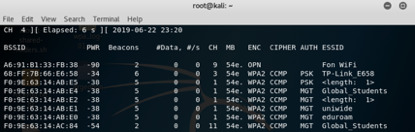
airodump- ng -c 11 -a --bssid <mac> wlan0mon #find the user mac address
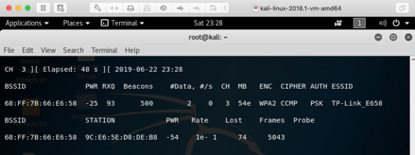
#we can see that there is one legal user is using this wifi-router and his mac address
let's close our monitor mode first airmon-ng stop wlan0mon
Because there is a confliction between network-manager and airmon-ng and we kill it before
then we can use our tool which is build-in kali Linux to change our mac address
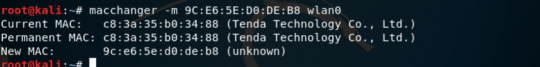
So we need to restart the service
run command: service network-manager start
then Try to connect the target network again
we can see that we connect the router successfully
How to prevent it?
Well, mac filter is a simple way to forbid the illegal user access the network The key thing is that you can not stop other people copy your mac address The possible solution may implement the wap-enterprise to let user input their auth code or do some RADIUS stuff
3 notes
·
View notes
Text
Stay Connected Anywhere with Wireless Solutions
In today present era, every day we as individuals has a lot of agenda that needs to be done through personal or just need to have some connectivity using our gadgets such as, smartphones, laptops, personal desktop, and tablets. Over the development of technology, were spontaneously move and done our accomplishments in anyplace. Communication with the internet has remained essential and gives a lot of influences to be more accommodating on work that we need to do. Since the traditional wired technology into wireless solutions, individuals and some businesses can get numerous benefits from this. It has an ability to have additional in the availability of more users to reduce all the traditional way (wired technology) that result delay and hassle for installation. Together with this, it can offer secure and developed bandwidth for better connectivity for your home or administrations.
Different kinds of Wireless
Wireless networks/ networks can be established using these altered technologies.
i. Bluetooth uses radio waves for exchanging data between close devices. ii. Cellular is the common that we frequently use as a global transceiver and transmit data. iii. RFID is transmitting the unique identification of signals. iv. Satellite are the devices that launched into space to relay signals on the earth stations. v. Wi-fi is helping to connect devices and transmit some data between one device to another.
Different types of wireless solutions
a. Point-to-point connectivity: is a connection between two sites that achieves high data transfer speeds. This is convenient as a mainstay link for detached radio access points through your primary internet source. These necessities to use 5 GHz and 2.4 GHz for wireless customers ‘kits.
b. Point to multipoint connectivity: This shows how the ISPs connect to the customers by putting access points with towers above their city or in any high building so that they extremity their clients’ projections to its access point.
c. Extreme/Nstreme2 Connectivity: It aims to achieve outstanding performance with long-range links with MikroTik proprietary wireless protocols. An unvarying wireless connection needs a substantial delay for data circulation over a long distance, but through the Nstreme, it’s not necessary to worry; it goes even further just by using two wireless cards at each end. One for the reception and transmission.
d. Base Station Setup: This is meant to be placed at 360 degrees radius for full coverage within up to 5 and 6 Kms. The capacity is always founded on position change upon the antenna gain and radio power. With this, it be able to competently manage and ease troubleshooting.
e. Wireless mesh setup: this is made up of radio nodes, and there are two communication pathways for each node. That one covers a single network in agreement, able to have a radio network. Web is reliable and gives idleness.
f. Infrastructure Monitoring: it has monitoring tools to ensure the maximum business continuity for our customers; it brings tools, protocols, and technologies to bear some of the IT Equipment.
g. Wi-Fi Hotspot with user manager: this offers Wi-Fi access to public locations.
h. WISP setup: the setup comprises all the services.
A lot of people are wanted an unended connectivity so there are some wireless solutions that being developed and introduced to us, to help and get some easy living every day. With these we can easily watch and communication just open our smartphones and other gadgets.
Want to know more about wireless? Visit our website at https://www.unlimitedwireless.net

0 notes
Text
Winbox for mac download

#Winbox for mac download for mac#
All Winbox interface functions are as close as possible mirroring the console functions, that is why there are no Winbox sections in the manual. Winbox versions 3.21 through the current (Updates in App) for macOS 64-bit Catalina and newer. You can also download MikroTik Winbox directly from. Downloads If you have an M1 MAC, I believe that the best option is to use crossover. MikroTik Winbox is the official app from MikroTik to configure MikroTik routers or RouterOS devices. It is a native Win32 binary, but can be run on Linux and MacOS (OSX) using Wine. Navigate to Contents/Resources/ from within the application Replace the winbo圆4.exe with one downloaded from MikroTik. ,ShadowrocketShadowsockswinbox winboxmy winboxmalaysia.
#Winbox for mac download for mac#
Username is 'demo' and there is no password. Download Shadowrocket iOS Download Shadowrocket freeload for Mac and. Connect via SSH or download our graphical application WinBox (latest version).When connecting in either way, use the address demo.mt.lv or demo2.mt.lv. Winbox is a small utility that allows administration of MikroTik RouterOS using a fast and simple GUI. Try RouterOS now by using our online demo routers.You can run the app from anywhere but I recommend moving it to your Applications folder. Download one of the versions below (I recommend the newest). I have complied “Winbox” by MikroTik with Wine in order to make it usable on Mac.Leading Internet providers that have hundreds or thousands of subscribers can easily integrate SPLYNX into their businesses to eliminate manual billing in the company, improve network management and radius server, make use of own CRM, Helpdesk, Scheduling and Inventory management modules. Having qualified as 100 adware and spiware free, older versions of Winbox for Mac are available for download from Softpedia. SPLYNX is a powerful all-in-one software solution tailormade for ISPs to handle billing, BSS & OSS.

1 note
·
View note
Text
TP-Link JetStream T2600G-28SQ 28-Port Gigabit SFP L2 Managed Switch

Vendor: TP-Link Type: Hubs and Switches Price: 714.02
TP-Link JetStream T2600G-28SQ Switch Review Highlights
Advanced QoS features
IGMP Snooping V1/V2/V3
Reliable, secure solution for enterprise, campus and ISP networks
TP-Link JetStream T2600G-28SQ Switch Features
24 X Gigabit SFP Slots
4 X Combo 10/100/1000 Mbps RJ45 Ports
4 X 10G SFP+ Slots
1 X RJ45 Console Port
1 X Micro-USB Console Port
L2+ feature - Static Routing, helps to route traffic between subnets without an extra router
IP-MAC-Port binding, ACL, Port Security, DoS Defend, Storm control, DHCP Snooping, 802.1X Authentication and Radius provide all the tools you need for robust security policies
IPv6 functions including dual IPv4/IPv6 stack, MLD snooping, IPv6 neighbor discovery
Web, CLI (Console Port, Telnet, SSH), SNMP, RMON and Dual Image for management and monitoring
2 X Fan
CE, FCC, RoHS certification
What Comes in the Box
1 X TP-Link JetStream T2600G-28SQ 28-Port Gigabit SFP L2 Managed Switch
1 X Singapore Power Adapter
Rackmount Kit
Rubber Feet
1 X Installation Guide
Warranty
Three-Year Carry-in Singapore Limited Hardware Warranty
Dimensions
Length 44.00 cm
Width 22.00 cm
Height 4.40 cm
Weight 910 gm
TP-Link JetStream T2600G-28SQ Switch Specifications
Standard Protocols:
IEEE 802.3i, IEEE 802.3u, IEEE 802.3ab, IEEE802.3z,
IEEE 802.3ad, IEEE 802.3x, IEEE 802.1d, IEEE 802.1s,
IEEE 802.1w, IEEE 802.1q, IEEE 802.1x, IEEE 802.1p
Network Media:
10BASE-T: UTP category 3, 4, 5 cable (maximum 100m)
100BASE-TX/1000Base-T: UTP category 5, 5e or above cable (maximum 100 m)
1000BASE-X: MMF, SMF
10GBASE-X:MMF, SMF
10GSFP+CU “SFP+ Direct Attach Cable” (TXC432-CU1M, TXC432-CU3M)
Power Supply: 100 ~ 240 VAC, 50/60 Hz
Power Consumption 29.7 W
Bandwidth/Backplane 128 Gbps
Packet Forwarding Rate 95.2 Mpps
MAC Address Table 16 k
Jumbo Frame 9216 Bytes
Physical security lock
Mounting 19 inch 1U rack mountable
Max Heat Dissipation 101.2 BTU/h
UPC Code
845973099954
from Tech2Cool https://ift.tt/38E9n2F
0 notes
Text
ISP Billing Software with Real-Time Usage & Automated Payments

In the rapidly growing internet service provider sector, the bottlenecks need to be dealt with quickly. ISPs must be capable of managing customer accounts with billing systems that are accurate and efficient. The problem comes when providers implement manual billing systems, as they always lead to accuracy issues. This is exactly why ISP billing software exist. Billing software lets ISPs automate themselves and take care of their customers by removing any tasks that occur repeatedly.
What Is ISP Billing Software?
ISP billing software is an all in one solution for internet service providers that lets them streamline and automate the billing process as well as track their customer’s bandwidth in real time and manage the service plans appropriately. It has support for functionalities like payment for services rendered, invoicing, bandwidth control, real time monitoring, alert messaging and much more. Whether you own a fiber network, a broadband service, or a Wireless ISP(WISP), having a smart billing system is pivotal for smooth growth of business operations.
Key Features of Modern ISP Billing Software
The ISP billing software solutions are designed after analyzing what ISPs need and thus come with some advanced features:
• Real-time monitoring of paid services: View the customer's data cap usage in real-time. This prevents clients from going over their limits, guarantees that they are billed fairly, and increases trust.
• Automated invoicing and billing: Issued and refunded invoices is processed automatically based on the customer's data usage, their plan, or preset time frames (monthly, prepaid, postpaid).
• Online Payment Gateway: Integration fetches advanced payment collection methods like UPI, Credit/Debit cards, Net banking, digital wallets.
• Portals of Self-Service Customer: provide a ticket raising interface along with payments and usage checking, taking the burden of calling support from the user.
• Custom Plans & Discounts: enables users to set, adjust, and automate limits of data, vouchers, and plans for users on demand.
• CRM & Ticketing: Integration permits users to track conversations with clients and their issues or requests for services through integrated support systems.
Advantages for ISPs
ISPs can actively manage and reduce the workload done manually through ISP billing software systems while improving accuracy along with the customer experience. Here are the primary benefits:
• Automation that Saves Time: Forgotten payments, manual, billing, and even tracking of usage ratio can be automated and run in the background with no external aid.
• Voiding Errors in Invoicing: Automation and use of algorithms to compute numbers cuts down chances of conflicts over bills making clients trust the service more.
• Customer Visibility: Alerts and reports give users real-time insights into usage metrics which improves billing transparency.
• Optimizing Revenue: Over looking unpaid invoices or incorrect usage tracking leads to revenue loss which optimizes revenue.
• Enhanced scalability: These billing systems that are based on the cloud can expand alongside your company, accommodating tens of thousands of users effortlessly.
Picking the Ideal ISP Billing Software
When choosing the right ISP billing software, keep these in mind:
• Installed locally vs Cloud-based: Accessibility from anywhere, higher uptime, and easier to modify updates makes cloud software a better choice at remote access.
• Scalability & Customization: Make sure the software can manage your growth and merge with your CRM, network tools, or other applications, and mitigate issues well within your reach.
• User Interface & Support: Having a streamlined dashboard improves ease of use, while attentive and responsive support enhances the experience.
• Compliance & Security: Make certain the platform adheres to best practices in security risk management.
Conclusion ISP billing software is essential for ISPs because it helps them stay competitive as well as operationally efficient. An advanced ISP billing system permits real-time usage tracking, automated billing issuance, a dynamic invoicing system with auto-schedulers, tiered service plan configurations, and seamless revenue growth, enabling ISPs to better service their customers. From my point of view, every ISP should be looking to invest in these systems.
#isp billing software in delhi#aaa solution for isp#best isp billing software#billing software for isp#isp billing software#isp billing solution#isp crm software#isp erp#isp management software#isp radius solution
0 notes
Text
How Complaints Management Systems Can Improve Customer Satisfaction for ISPs
Introduction:
Importance of Customer Satisfaction in ISP Industry
In the era of digitalism, the customer relies on the Internet Service Provider to deliver the smoothest internet experience possible. Customers demand an ISP with increasing speed and reliability as well as high availability and service continuity, therefore, satisfaction for these customers in this sector is crucial because a minor break or several hours of service interruption results in complaints that ultimately lead to frustration and eventually churn. Therefore, quality of service in terms of customer service is the biggest difference in such a highly competitive ISP arena.
Effective management of complaints is one of the most important tools for retaining customers, reducing churn, and enhancing brand loyalty in the case of ISPs. A strong complaints management system helps to resolve customer complaints efficiently, satisfies the customers, and provides a healthy relationship with the users.
Role of Complaints Management in Customer Satisfaction
Every service industry should surely see some complaints, and ISPs are no exception. But the way such complaints are handled is what makes all the difference. A complaint management system may indeed resolve complaints but also gives ISPs enough information on how to handle repetitive complaints and understand the requirements of customers. Here's how a well-managed complaint system can increase customer satisfaction:
Fast Trouble-Handling: Consumers always wish that problems can be tackled immediately. The complaints handling system of the ISPs properly classifies and prioritizes and resolves grievances speedily thus addressing customers at appropriate time.
Transparency and Communicate: In such system customer satisfaction becomes more authentic where status is given by resolving the complaints. Thus complaint management systems should enable a regular reporting status with the resolution process for improving transparence that the problems or issues are considered.
The service quality, thereby, is improved by the ISPs having a structured complaint processing. An organized approach to complaint processing reduces time-to-response, ensures higher accuracy, and reduces repeated interactions related to the same issues-improving the customer experience as well.
Data-Driven Improvements: A complaint management system that is efficient not only solves problems but also gathers data regarding the recurrences of the problems. ISPs can take informed decisions, taking preventive measures to prevent future occurrences, based on these insights.
Key Features for ISPs in a Complaints Management System
An ISP would need the most appropriate complaints management system. The system should have the following specific features that ISPs need:
Automated Ticketing System: It automatically logs complaints and assigns them to tickets for routing into the proper teams based on priority, kind of problem, or a customer's segment.
Multi-Channel Support: The company should have a way where customers can submit complaints on different channels, including social media, email, live chat, and even phones. ISPs should meet their customers at any point that favors them.
Real-Time Tracking and Notifications: This would enable real-time monitoring by the customer of complaint status. Automated notifications will keep them informed at each step, thereby leading to transparency, trust, and cooperation.
Root Cause Analysis and Reporting: Being able to take care of advanced analytics, such a system helps in finding out root causes of most common problems. In this way, ISPs become in a better position to address causes rather than symptoms alone.
The complaints management system will be integrated into the ISP's current ISP management software, reducing redundant data flow and thereby maximizing the efficiency of their general operations. The availability of customer data, network information, and service history in support agents' working consoles would therefore ensure that matters were sorted out as soon as possible.
customer feedback and survey tools: After the resolution of complaints, customer contact for feedback is an important activity for continuing to improve operations. Integrated survey tools provide very useful feedback on the satisfaction of customers with regard to the resolution process.
Integration of Complaint Management with ISP Management Software
To function at their best, an ISP should integrate its complaints management system with its existing ISP management software. Integration not only consolidates customer data but also provides a unified view of the customer journey. Here's how this synergy improves overall ISP performance:
Improved Data Accessibility: When customer and network data are unified, support agents can view relevant information immediately, allowing them to diagnose and resolve issues faster.
Improved Customer Insights: Through merging the complaint data with ISP management software, the ISP can identify trends across services. As a result, it can use that data towards making better and informed decisions and the prevention of such issues.
Streamlined Communication Across Teams: Integration of customer service, technical support, and network maintenance teams can help information flow easily. As a result, departments can work in coordination toward efficiently settling the complaints of customers.
Automation of Follow-Up Actions: The proper integrated system can mail follow-up actions to the customer even after resolution. Thus, there will be a positive feeling from the customer's side along with creating engagement.
Conclusion: Benefits and Next Steps
A dedicated complaints management system is a way in which ISPs can effectively address their customers' grievances, resulting in higher satisfaction levels and lower churn rates - a competitive advantage in the market. Integration of this with ISP management software enables ISPs to craft a seamless, data-driven approach that encourages continuous improvement, swift resolutions, and ultimately, happier customers.
An ISP seeking to adopt or upgrade its complaints management approach should look to invest in a system that integrates well with existing infrastructures. This enhances operational efficiency and strengthens relationships with customers, thereby providing a good foundation for long-term growth and success within an increasingly dynamic industry.
#complaints management system#AAA solution for isp#isp radius solution#billing software for isp#ISP Billing Solutionisp crm software#Isp software for billing in Delhi#Isp billing software in delhi#best isp billing software#isp billing software in Delhi#isp management software#isp erp#isp billing software
0 notes
Photo

New Post has been published on https://www.hackzhub.com/zooqle/
All You Need To Know About "Zooqle" - Torrent's Best Search Engine
Zooqle was founded in 2008 and was formerly known as Bitsnoop. It is a torrent indexing website which provides a database containing verified torrents for download. You can download movies, TV shows, games, PDFs, applications, software, anime, and audiobooks. There are some 36,000 films and more than 160,000 correspond to hundreds of television programs.
Everything on Zooqle is organized by categories and has a release calendar with the most recent series and movies. It takes advantage of TMDb to show information about the titles. You can register on the site to create subscriptions and add content to an RSS feed so you know when there are new torrents of things that interest you will appear.
.u85916a3b5b62adf8f563072c381e916d , .u85916a3b5b62adf8f563072c381e916d .postImageUrl , .u85916a3b5b62adf8f563072c381e916d .centered-text-area min-height: 80px; position: relative; .u85916a3b5b62adf8f563072c381e916d , .u85916a3b5b62adf8f563072c381e916d:hover , .u85916a3b5b62adf8f563072c381e916d:visited , .u85916a3b5b62adf8f563072c381e916d:active border:0!important; .u85916a3b5b62adf8f563072c381e916d .clearfix:after content: ""; display: table; clear: both; .u85916a3b5b62adf8f563072c381e916d display: block; transition: background-color 250ms; webkit-transition: background-color 250ms; width: 100%; opacity: 1; transition: opacity 250ms; webkit-transition: opacity 250ms; background-color: #3498DB; box-shadow: 0 1px 2px rgba(0, 0, 0, 0.17); -moz-box-shadow: 0 1px 2px rgba(0, 0, 0, 0.17); -o-box-shadow: 0 1px 2px rgba(0, 0, 0, 0.17); -webkit-box-shadow: 0 1px 2px rgba(0, 0, 0, 0.17); .u85916a3b5b62adf8f563072c381e916d:active , .u85916a3b5b62adf8f563072c381e916d:hover opacity: 1; transition: opacity 250ms; webkit-transition: opacity 250ms; background-color: #2ECC71; .u85916a3b5b62adf8f563072c381e916d .centered-text-area width: 100%; position: relative; .u85916a3b5b62adf8f563072c381e916d .ctaText border-bottom: 0 solid #fff; color: #FFFFFF; font-size: 16px; font-weight: bold; margin: 0; padding: 0; text-decoration: underline; .u85916a3b5b62adf8f563072c381e916d .postTitle color: #000000; font-size: 16px; font-weight: 600; margin: 0; padding: 0; width: 100%; .u85916a3b5b62adf8f563072c381e916d .ctaButton background-color: #2980B9!important; color: #FFFFFF; border: none; border-radius: 3px; box-shadow: none; font-size: 14px; font-weight: bold; line-height: 26px; moz-border-radius: 3px; text-align: center; text-decoration: none; text-shadow: none; width: 80px; min-height: 80px; background: url(https://www.hackzhub.com/wp-content/plugins/intelly-related-posts/assets/images/simple-arrow.png)no-repeat; position: absolute; right: 0; top: 0; .u85916a3b5b62adf8f563072c381e916d:hover .ctaButton background-color: #27AE60!important; .u85916a3b5b62adf8f563072c381e916d .centered-text display: table; height: 80px; padding-left: 18px; top: 0; .u85916a3b5b62adf8f563072c381e916d .u85916a3b5b62adf8f563072c381e916d-content display: table-cell; margin: 0; padding: 0; padding-right: 108px; position: relative; vertical-align: middle; width: 100%; .u85916a3b5b62adf8f563072c381e916d:after content: ""; display: block; clear: both;
READ ALSO: Top 5 Best Torrent Sites For Downloading 2017
Zooqle has been known as one of the biggest torrent sites with more than 3.5 Million verified torrents and thousands are added every day. More than 2,200 trackers are supporting it sharing more than 32 million parts. You just need to have a BitTorrent client like uTorrent in your PC and you can get almost anything you’re looking for from this site.
Zooqle does not show advertising banners everywhere. In fact, you’ll not get one on the home page also but every now and then it shows some pop-up window with offers, something which can be easily blocked with tools like uBlock Origin if you want.
When Zooqle is opened, it completely appears as a media streaming website. There is a search bar at the top-left corner and the rest of the screen real estate is reserved for images and artwork. Zooqle showcases the most popular categories on the front page, where popular movies, TV shows, music and alike can be seen. When you click on any of these images, it’ll show you a deep overview of the title. For example, if a TV show title is clicked, the seasons and episodes will appear. You just have to pick up your choice. This narrows down the search.
However, many ISPs have blocked access to Zooqle due to high internet piracy and copyright laws. This is the reason Zooqle is blocked to access many websites and doesn’t work for many users. But there are different ways to unblock Zooqle.
Zooqle Proxy & Mirror sites
Zooqle Proxy and Mirror sites are available in countries where Zooqle has not been blocked yet. Those who can’t access Zooqle directly can access it by means of using these proxies. The Proxy sites or Mirrors have the same data, torrent files, and community except for a name.
Zooqle Proxy/Mirror
URL
https://zooqle.unblocked.re/
https://zooqle.unblocked.re/
Zooqle proxy bunker
https://zooqle.proxybunker.co.uk/help/api.html
https://zooqle.immunicity.kim/
https://zooqle.immunicity.kim/
Zooqle proxy server
https://zooqle.torrent.cricket/
Zooqle proxy UK
https://zooqle.megafiletube.pw/
https://zooqle.bypassed.kim/
https://zooqle.bypassed.kim/
https://zooqle4-com.unblocked.lol/
https://zooqle4-com.unblocked.lol
https://zooqle.unblocked.kim/
https://zooqle.unblocked.kim/
https://zooqle.unblocked.tw/
https://zooqle.unblocked.tw/
Zooqle unblocked
https://zooqle.nocensor.cc/
Zooqle movies download
https://unblocked.tk/zooqle.php
What if the Proxy also doesn’t Work?
It may happen that the proxy site also doesn’t work. Proxy sites, as you all know, are usually not protected. They also have no privacy rules and are very easily detected by modern-day firewalls. Therefore, you need to have a permanent and powerful solution like VPN so that the proxy sites work effectively. A VPN (Virtual Private Network) encrypts data and guides you through a virtual IP address. This ensures protection from the government who cannot see what you are watching or doing.
Zooqle Alternatives Sites
These websites offer the same result and work which Zooqle offers.
The Pirate Bay
It offers millions of downloads and torrent links through which all kinds of movies, TV shows, games, software and many more can be accessed.
1337x
It offers plenty of downloads verified torrents for movies, music anime and a lot more.
Demonoid
This is not just a website offering downloads and surfing but serves as a torrent tracker. It has an amazing quality of speed and authenticity. It is considered as the best alternative for Zooqle.
Torlock
It has no fake file issue and also has a huge collection of movies, games, tv shows, and other e-stuff.
RARBG
The links provided by this site can be shared easily with your friends. Use BitTorrent protocol and enjoy movies, TV shows, software, and music, etc.
.uf16580cf00fa0c037cbb39d8719e23cd , .uf16580cf00fa0c037cbb39d8719e23cd .postImageUrl , .uf16580cf00fa0c037cbb39d8719e23cd .centered-text-area min-height: 80px; position: relative; .uf16580cf00fa0c037cbb39d8719e23cd , .uf16580cf00fa0c037cbb39d8719e23cd:hover , .uf16580cf00fa0c037cbb39d8719e23cd:visited , .uf16580cf00fa0c037cbb39d8719e23cd:active border:0!important; .uf16580cf00fa0c037cbb39d8719e23cd .clearfix:after content: ""; display: table; clear: both; .uf16580cf00fa0c037cbb39d8719e23cd display: block; transition: background-color 250ms; webkit-transition: background-color 250ms; width: 100%; opacity: 1; transition: opacity 250ms; webkit-transition: opacity 250ms; background-color: #3498DB; box-shadow: 0 1px 2px rgba(0, 0, 0, 0.17); -moz-box-shadow: 0 1px 2px rgba(0, 0, 0, 0.17); -o-box-shadow: 0 1px 2px rgba(0, 0, 0, 0.17); -webkit-box-shadow: 0 1px 2px rgba(0, 0, 0, 0.17); .uf16580cf00fa0c037cbb39d8719e23cd:active , .uf16580cf00fa0c037cbb39d8719e23cd:hover opacity: 1; transition: opacity 250ms; webkit-transition: opacity 250ms; background-color: #2ECC71; .uf16580cf00fa0c037cbb39d8719e23cd .centered-text-area width: 100%; position: relative; .uf16580cf00fa0c037cbb39d8719e23cd .ctaText border-bottom: 0 solid #fff; color: #FFFFFF; font-size: 16px; font-weight: bold; margin: 0; padding: 0; text-decoration: underline; .uf16580cf00fa0c037cbb39d8719e23cd .postTitle color: #000000; font-size: 16px; font-weight: 600; margin: 0; padding: 0; width: 100%; .uf16580cf00fa0c037cbb39d8719e23cd .ctaButton background-color: #2980B9!important; color: #FFFFFF; border: none; border-radius: 3px; box-shadow: none; font-size: 14px; font-weight: bold; line-height: 26px; moz-border-radius: 3px; text-align: center; text-decoration: none; text-shadow: none; width: 80px; min-height: 80px; background: url(https://www.hackzhub.com/wp-content/plugins/intelly-related-posts/assets/images/simple-arrow.png)no-repeat; position: absolute; right: 0; top: 0; .uf16580cf00fa0c037cbb39d8719e23cd:hover .ctaButton background-color: #27AE60!important; .uf16580cf00fa0c037cbb39d8719e23cd .centered-text display: table; height: 80px; padding-left: 18px; top: 0; .uf16580cf00fa0c037cbb39d8719e23cd .uf16580cf00fa0c037cbb39d8719e23cd-content display: table-cell; margin: 0; padding: 0; padding-right: 108px; position: relative; vertical-align: middle; width: 100%; .uf16580cf00fa0c037cbb39d8719e23cd:after content: ""; display: block; clear: both;
READ ALSO: 5 Reasons To Use Torrent Sites Despite Being Illegal
Conclusion
The world of torrent download sites has never been consistent. Some have completely disappeared as Kickass Torrents and ExtraTorrent while others are blocked in many countries as the case of The Pirate Bay. Zooqle which is relatively new in the torrent world has proved to be an excellent alternative to more popular trackers. Zooqle has impressed with its clean and user-friendly design and the search engine also gives suggestions when you start typing.
0 notes
Text
ISP Management Systems Market Size, Status and Forecast to 2027
An Internet service provider (ISP) is also known as an Internet access provider (IAP). ISP management systems enable Internet service providers (ISPs) to centrally and smoothly manage end-to-end processes or the process of their Internet business. ISP management systems provide complete authentication, authorization, and accounting (AAA) as well as operations and billing management modules including OSS and BSS. These systems support flexible deployment options such as on-premise deployment and cloud-hosting on a SaaS model deployment. ISP management systems are developed or designed for managing the web server, sites, and payments and services related to Internet.
ISP management systems are used for managing all Internet operations, which can occur during the lifecycle of an Internet business, such as radius – authentication, authorization, and accounting (AAA) management, plan management, subscriber management, billing management, partner management, and compliance management. ISP management systems also offer real-time status of data usage, renewal reminders, and network issue notifications to users.
To obtain all-inclusive information on forecast analysis of global market, request a PDF brochure here.
The global ISP management systems market is driven by rise in the demand for auto-generated invoices and bills by Internet service provider companies or organizations. Rise in the adoption of cloud/web-based technologies is another key factor propelling the global ISP management systems market. Easy access to online services for games, streaming high-definition videos, social networking sites, cameras, GPS receivers, and Wi-Fi with improved network connectivity is driving the ISP management systems market. Additionally, increasing use of Internet-based services led by availability of advanced LTE networks is anticipated to boost the demand for ISP management systems worldwide during the forecast period.
ISP management systems manage unlimited number of users in a dynamic network with the help of user migration facilities, user authentication processes, and user deletion/update/addition management functions. These systems enable service providers to easily manage issues such as revenue leakage, network congestion, and user monitoring. Thus, the increasing need to handle or monitor all of the subscriber data is also projected to fuel the demand for ISP management systems globally in the near future. However, lack of awareness about features of ISP management systems among organizations is hampering the demand for ISP management systems across the globe.
The global ISP management systems market can be segmented based on component, deployment, enterprise size, technology, and region. In terms of component, the ISP management systems market can be bifurcated into software and services. The services segment can be sub-divided into Internet access, Internet transit, domain name registration, web hosting, usenet service, and colocation. Based on deployment, the ISP management systems market can be segmented into on-premise and cloud-based. In terms of enterprise size, the global ISP management systems market can be categorized into small & medium enterprises and large enterprises. Based on technology, the ISP management systems market can be classified into dial-up, DSL, cable modem, and wireless or dedicated high-speed interconnects.
In terms of region, the global ISP management systems market can be segmented into Europe (EU), North America (NA), Middle East & Africa (MEA), South America (SA), and Asia Pacific (APAC). The ISP management systems market in North America is estimated to expand rapidly during the forecast period. High adoption of ISP management systems led by the presence of established vendors in the region is driving the ISP management systems market in North America. The ISP management systems market in Asia Pacific is anticipated to expand at a significant CAGR during the forecast period.
For more actionable insights into the competitive landscape of global market, get a customized report here.
Demand for ISP management systems is high in Asia Pacific. This is primarily due to increasing Internet penetration and smartphone usage in the region. Furthermore, rapid development and innovations in smart phones and growing awareness about ISP management systems among end-users are expected to create new opportunities for the ISP management systems market in Asia Pacific during the forecast period.
Major players operating in the global ISP management systems market are Splynx s.r.o., Xonware Technologies Pvt. Ltd., Huawei Technologies Co., Ltd., SoftifyBD, Inventum Technologies Private Limited, Netwall Expert, Hydra Billing Solutions LLC, and ICONWAVE TECHNOLOGIES PVT. LTD.
0 notes
Text
Better & Easier Connectivity with Wireless Solutions
Every day some individuals has a lot of agenda that needs to be done through personal or just need to have some connectivity using our gadgets such as, smartphones, laptops, personal desktop, and tablets. Through the advancement of technology, were freely move and done our activities anywhere. Interaction with the internet has been important and gives a lot of impacts to be more flexible on work that we need to do. From the traditional wired technology into wireless solutions, people and some businesses can get many benefits from this.
Wireless solutions have an ability to increase the availability of more users to lessen all the traditional way (wired technology) that result delay and hassle for installation. With this, it can provide secure and higher bandwidth for better connectivity for your home or organizations.
Kinds of Wireless technologies
Wireless networks/ connections can be established using these different technologies.
o Bluetooth uses radio waves for exchanging data between close devices. o Cellular is the common that we frequently use as a global transceiver and transmit data. o RFID is transmitting the unique identification of signals. o Satellite are the devices that launched into space to relay signals on the earth stations. o Wi-fi is helping to connect devices and transmit some data between one device to another.
Different types of wireless solutions
1. Point-to-point connectivity: is a connection between two sites that achieves high data transfer speeds. This is useful as a backbone link for distant radio access points through your primary internet source. This needs to use 5 GHz and 2.4 GHz for wireless clients' kits.
2. Point to multipoint connectivity: This shows how the ISPs connect to the customers by putting access points with towers above their city or in any high building so that they end their clients antennas to its access point.
3. Extreme/Nstreme2 Connectivity: It aims to achieve outstanding performance with long-range links with MikroTik proprietary wireless protocols. A regular wireless connection needs a considerable delay for data distribution over a long distance, but with the Nstreme, you don' t need to worry; it goes even further just by using two wireless cards at each end. One for the reception and transmission.
4. Base Station Setup: This is meant to be placed at 360 degrees radius for full coverage within up to 5 and 6 Kms. The range is always based on station change upon the antenna gain and radio power. With this, it can efficiently manage and ease troubleshooting.
5. Wireless mesh setup: this is made up of radio nodes, and there are two communication pathways for each node. It covers a single network in harmony, able to have a radio network. Mesh is reliable and gives redundancy.
6. Infrastructure Monitoring: it has monitoring tools to ensure the maximum business continuity for our customers; it brings tools, protocols, and technologies to bear some of the IT Equipment.
7. Wi-Fi Hotspot with user manager: this offers Wi-Fi access to public locations.
8. WISP setup: the setup comprises all the services.
There's a lot of use of wireless connection in our daily lives, whether it's good or bad. We just need to identify how we manage and know all the different types of ways by using a mobile phone. Without these, we can experience interruption in communication and other activities.
For more information about Wireless activity, just visit our website at https://www.unlimitedwirelessplans.net

0 notes
Text
ISP Billing Software | WISP Billing Bandwidth Management Software
ICONRADIUS provides advanced features which can integrate with multiple NAS like Cisco ASR 1000 and 9000 series, Juniper MX series, Huawei NetEngine and Mikrotik routers. Iconwave offers expert solutions for ISP's with advanced and sophisticated strategies for best results with an expert team more than 11 years of experience and master at networking management provides the best productivity results.
We have around 15,000,00 subscribers across india, South Africa, Bangladesh, Dubai, Singapore and also expanding its fraternity across the globe with a secured and safe connectivity
Key Features of Iconradius : Subscriber Management Contact and billing information of the customer, Managing customer services, Administration and history of issued invoices and payments, Messages and notes, Records and administration of contracts and testimonies, Send emails / Reminders for unpaid payments ,and Sent / Received SMS.
NETWORK MANAGEMENT ICONRADIUS supports the most comprehensive network management and operation devices MikroTik, Cisco and Ubiquiti.
Multiple payment gateway integration individual payment gateway integration for each franchise we also support hotspot, DHCP, and PPPOE, Authentication
NETWORK MONITORING To ensure real-time reliable server performance, Monitoring of individual devices on the network (routers, servers, UPS, etc.), Possibility to connect SMS gateway Report error statuses on the network Setting Notification Groups SMS, email, push and Dashboard notifications.
MOBILE APPLICATION View assigned tasks to employee Navigate to the client address Manage Task - Add a solution and close a task Show all (online/offline) network devices on the map, or their distance and direction,and Synchronize with your mobile device calendar.
Complete user information Renew user Change password Wallet history Renewal history Invoice Payments Renewal schedule Package history Complaints Traffic report Session history User MRTG Graph MAC Login Permanent disconnect Franchise management Franchise list, Add franchise, Deposit report, Payment reports, Revenue sharing report, SMS Deposits, and Franchise renewal report.
Customize settings and privileges Customizable settings and privileges as per the roles and responsibilities of the employee
Individual services and tariffs, System functionality, Client Portal, Routers, and Backup, Forms of contracts, emails and SMS, Employee Access Permissions, Alerts, SNMP Templates, and Nagios Notifications,and IP pools for both Radius and NAT. Track employee status Track employee status using the mobile application provided to the employee
Connectivity with the customer database - the ability to generate invoice the work done, including the material used, Adding new tasks to the particular technician, Overview scheduled work to technicians for the current week, Tracking the workload of technicians, Daily, weekly and monthly reports of scheduled tasks, Synchronize with Google Calendar, Reports and statistics of completed / uncompleted tasks, solution procedures,and Complete history of resolved and uncompleted tasks. Complaints Add Complaints My Complaints Open Complaints In process Resolved complaints Closed Complaints Complaints category Inventory management
Mass storage of material Survey of goods by season (purchase and sales prices) Assigning goods to technicians, clients and routers Loading goods into the system using a barcode reader,Record-keeping and administration of all goods Ability to assign goods to engineers, customers, routers, sites, etc.,and Complete history of the movement of goods.
Generate invoice Monthly, quarterly, semi-annual, yearly and multi-year billing, Feasibility to issue a separate invoice, Support billing groups - multiple businesses in a single system, Automatic payments with individual invoices / customers, Payments and statistics reports, Notification payment delays, Preconfiguration, Possibility to issue advance invoices, Repayment schedule,and tax records.
Multiple types of package Creations FUP(Fair usage policy) Unlimited, Double speed package, Day wise package.
Insights and Analytics Traffic and server usage information, such as running processes, memory usage, and CPU, preview clients (additions, transfers, total counts) according to the type of connection or tariff, Data collection from the system log of MikroTik routers,and Overview of events and changes in the database.
https://www.iconwavetech.com/isp-management-software MikroTik #casionetwork Juniper Networks Huawei Network
0 notes
Text
VPN Safe Protected Solutions Safety
VPN. A Electronic Individual System (VPN) integrates rural personnel, business practices, and business companions using the Internet and obtains protected tunnels between locations. An Access VPN is employed to get in touch distant users to the enterprise network. The distant workstation or laptop use an entry world such as for example Cable, DSL or Wireless for connecting to an area Internet Company Service (ISP). With a client-initiated design, pc software on the remote workstation builds an secured canal from the laptop to the ISP using IPSec, Layer 2 Tunneling Process (L2TP), or Indicate Level Tunneling Process (PPTP). The user should authenticate as a allowed VPN user with the ISP. After that's finished, the ISP builds an protected tunnel to the company VPN router or concentrator. TACACS, RADIUS or Windows servers may authenticate the remote person as an employee that is permitted access to the business network. With that finished, the remote person must then authenticate to the local Windows domain host, Unix server or Mainframe number based upon wherever there network account is located. The ISP caused product is less protected compared to the client-initiated design because the protected tunnel is built from the ISP to the organization VPN switch or VPN concentrator only. As properly the secure VPN tunnel is constructed with L2TP or gizlilikveguvenlik.com . IPSec operation may be worth noting since it this type of predominant security method applied nowadays with Virtual Private Networking. IPSec is given with RFC 2401 and developed being an open common for secure transportation of IP across the general public Internet. The box structure is comprised of an IP header/IPSec header/Encapsulating Safety Payload. IPSec offers security solutions with 3DES and verification with MD5. Additionally there is Net Critical Exchange (IKE) and ISAKMP, which automate the circulation of key tips between IPSec expert devices (concentrators and routers). These protocols are needed for settling one-way or two-way protection associations. IPSec security associations are made up of an encryption algorithm (3DES), hash algorithm (MD5) and an verification approach (MD5). Access VPN implementations employ 3 security associations (SA) per connection (transmit, get and IKE). An enterprise system with several IPSec fellow products can start using a Certificate Authority for scalability with the verification method as opposed to IKE/pre-shared keys. The Access VPN can control the accessibility and low priced Internet for connectivity to the business core company with WiFi, DSL and Cable access tracks from local Internet Support Providers. The key situation is that business data should be secured since it travels throughout the Internet from the telecommuter notebook to the business primary office. The client-initiated product will undoubtedly be used which builds an IPSec canal from each client laptop, which can be terminated at a VPN concentrator. Each laptop will soon be constructed with VPN client software, which will run with Windows. The telecommuter must first dial an area accessibility quantity and authenticate with the ISP. The RADIUS host can authenticate each switch connection as an approved telecommuter. After that is finished, the remote person will authenticate and authorize with Windows, Solaris or even a Mainframe host prior to starting any applications. You can find combined VPN concentrators that'll be configured for crash around with electronic redirecting redundancy method (VRRP) must one be unavailable. Each concentrator is connected involving the additional hub and the firewall. A brand new function with the VPN concentrators prevent rejection of support (DOS) attacks from outside hackers that can affect system availability. The firewalls are configured to enable resource and location IP addresses, which are given to each telecommuter from the pre-defined range. As properly, any program and process slots will undoubtedly be allowed through the firewall that is required. Extranet VPN Style The Extranet VPN is designed to allow secure connectivity from each organization spouse company to the business core office. Protection is the principal focus considering that the Net is going to be applied for transporting all information traffic from each company partner. There would have been a signal connection from each business partner which will cancel at a VPN router at the organization key office. Each business partner and its look VPN hub at the primary office can start using a router with a VPN module. That component offers IPSec and high-speed electronics encryption of packets before they are carried throughout the Internet. Expert VPN modems at the company core company are dual homed to various multilayer buttons for url diversity should one of many links be unavailable. It is essential that traffic from company spouse does not wind up at still another company spouse office. The turns are located between external and inner firewalls and applied for joining community machines and the outside DNS server. That isn't a protection situation because the outside firewall is selection public Web traffic. Furthermore filter can be executed at each network change as effectively to avoid channels from being advertised or vulnerabilities exploited from having company spouse connections at the company key office multilayer switches. Split VLAN's will be given at each system switch for each organization spouse to improve safety and segmenting of subnet traffic. The tier 2 additional firewall will study each packet and enable people that have company spouse source and location IP handle, application and project locations they require. Company partner periods will have to authenticate with a RADIUS server. Once that is finished, they will authenticate at Windows, Solaris or Mainframe hosts prior to starting any applications.
0 notes
Text
50% off #PHP for Beginners – $10
PHP for Beginners: Learn to Code in PHP Using Real World Examples! PHP for Beginners Course 2016
All Levels, – Video: 5 hours Other: 1 hour, 138 lectures
Average rating 4.0/5 (4.0)
Course requirements:
Have access to a computer with internet connection and browser Some HTML and CSS knowledge would be beneficial but the tutor will explain everything as he goes
Course description:
REGULARLY UPDATED PHP FOR BEGINNERS COURSE.
Students consistently say how much they LOVE this course due to its unique delivery method and challenges which enable you to use your new skills immediately.
This PHP for beginners course introduces you to PHP through carefully crafted examples and fully worked mini tasks. LEARNING by DOING is what this course is all about. You will experience real world examples of PHP code use.
Have you seen other courses that use complex terms or that jump steps and leave you thinking “why did that just happen��? You won’t find that with this carefully crafted course.
This course has been designed with the coding beginner in mind or those who may have picked up bad habits and wish to refresh their coding skills.
On hand to help and guide you is a renowned national award-winning teacher who has taught 1000s of students over a career of over 25 years.
Highlights of this course include:
Full code from every example and mini task shared with you online Carefully crafted challenges and full solutions with FULL explanations of every line Demonstration of a shared coding environment Dozens of real world examples with more added on a regular basis A tutor who cares about his students Regular updates and new challenges
If you want to learn PHP and take your first steps into the world of web development then this PHP for Beginners course is for you.
Every line of code is explained in full detail to ensure that you can progress from absolute beginner to competent coder in a few weeks.
Launch yourself onto a new career path by taking this course now.
MONEY BACK GUARANTEE
There is absolutely no risk with a full 30 day money-back guarantee.
Enrol now.
Full details a true PHP for Beginners course with step-by-step lessons learn how to code using PHP from a national award-winning teacher you will be taken from absolute PHP beginner to confident coder with every step clearly explained create dozens of useful PHP scripts create a Rock Paper Scissors game create a basic hit counter via sessions create a 2 player Tic Tac Toe game create a bad word filter create a ‘How many days until Christmas’ script create and use HTML forms and process the data using PHP create, read, update and delete sessions and cookies access to regularly updated content including lesson notes, downloadable code, HD quality video tutorials, and quizzes 25 PHP coding challenges (more added regularly) with full video solutions and downloadable PHP code access real world coding challenges and examples including full video solutions and downloadable code manipulate words and sentences (strings) using string functions use mathematical operators e.g. addition, subtraction, multiplication, division (and more) to solve practical problems e.g. calculate the area of a circle if the user inputs the radius or diameter use loops to simplify processes use conditional statements to test properties and action processes based on the result create and use simple arrays and solve problems involving array functions use associative arrays and manipulate them using array functions use PHP internal functions and create your own use the date() function to perform calculations based on date a tutor who responds quickly to questions and who regularly updates the course 30 day money back guarantee! …and much more!
Full details No PHP coding experience is required – this is a true PHP for Beginners course Complete beginners to PHP are welcome and encouraged to enrol Anyone interested in learning PHP at a basic to intermediate level If you are looking to learn complex Object Oriented Programming (OOP) then this course is not for you
Reviews:
“Easy to follow with great information.” (Student2)
“The pace feels right, lectures are clear, exercises are well structured, 5 stars.” (Sergiorola)
“Thank you for this easy to follow video on PHP development. The videos are short but content dense. I would definitely take the opportunity to take any classes you produce in the future.” (Nevin Herring)
About Instructor:
Patrick Morrow
Patrick is a very experienced teacher who is consistently recognised for helping students achieve their true potential. This quality has been recognised by the National Teaching Awards with Patrick awarded Outstanding Teacher of the Year. Other establishments including Her Majesty’s Inspectorate in the UK use his models as examples of best practice. Patrick is a Google Certified Educator and was invited by Apple to participate in the Apple Distinguished Leaders Program 2016. Patrick has been featured on television and in the Financial Times, ISP World, and Computer Weekly. He has taught students at all levels, has been guest speaker at multiple conferences and has been invited by a top university to ‘lecture anytime’. “Patrick is not only a quality teacher, he is a mover and motivator of minds.” “A genius of his profession.” “Of course this guy’s popular, he’s the definition of a perfect teacher in a myriad of so many imperfect ones.”
Instructor Other Courses:
…………………………………………………………… Patrick Morrow coupons Development course coupon Udemy Development course coupon Web Development course coupon Udemy Web Development course coupon PHP for Beginners PHP for Beginners course coupon PHP for Beginners coupon coupons
The post 50% off #PHP for Beginners – $10 appeared first on Udemy Cupón.
from http://www.xpresslearn.com/udemy/coupon/50-off-php-for-beginners-10/
0 notes
Text
What is the Best Cloud Management Platform?

The need to control businesses IT systems from the cloud has increased the use and demand for cloud-based solutions, particularly in the case of businesses that need to manage their IT infrastructure efficiently and cost-effectively. To address the needs of the businesses, advanced cloud management platforms have emerged, which optimize cloud operations. When it comes to cloud management, billing is one of the most crucial elements and this is where ISP cloud billing software is of critical importance. But what exactly makes a cloud management platform the best for your business needs? In this article, we’ll discuss the fundamental features of primary cloud management platforms while focusing on ISP cloud billing software and its impact on the overall cloud management.
What is a Cloud Management Platform?
As with any other system, cloud services as well as infrastructures used by enterprises require a proper set of tools to manage and administer them. Thus, A cloud management platform (CMP) Cloud helps businesses manage their cloud services as well as infrastructure. CMPs offer a centralized point of control and thus, visibility over cloud, resource optimization, and cost management. They assist in automating resource deployment, performance monitoring, and security compliance. More importantly, a CMP unifies multiple cloud services and resources ensuring scalable business operations in a flexible manner while safeguarding cloud environments.
Other offerings provide features like:
Resource Management - Making certain that cloud resources are provided and used efficiently.
Cost Management and Optimization - Monitoring the use of cloud and predicting expenditures, providing recommendations for reduction in waste.
Security and Compliance - Protecting cloud environments by assuring industry standards and compliance regulations.
Billing and Invoicing - Automating and managing payments serves critical businesses functions in the context of cloud service utilization.
Automation and Orchestration - Improving workflows and automating processes for efficiency gain.
Why is ISP Cloud Billing Software important for enterprises?
ISP cloud billing software is vital to any cloud management’s core functionality. It integrates seamlessly into the infrastructure of a business leveraging cloud services. The software provides a robust billing system that tackles complicated pricing structures, payment schedules, and invoicing cycles.
Key Attributes of ISP Cloud Billing Software:
Flexible Pricing Models - ISP cloud billing software supports several billing models priced on a per use basis, through subscriptions, or tiered pricing model. This flexibility is important for businesses selling cloud services to users with diverse billing preferences.
Real Time Billing: Businesses can monitor consumption of services and issue invoices immediately service consulting takes place. This feature helps enterprises avert billing discrepancies and enhances cash flow precision.
Automated Invoicing: Reduction in the administrative workload and lowering the chances of human error is achieved through automating invoicing, which aids businesses in producing timely and accurate invoices for customers.
Cost Allocation and Resource Tracking: ISP cloud billing software assists businesses in monitoring resource consumption at a departmental or client level, making accurate cost allocation and optimization of cloud resources possible.
Integration with Other Cloud Platforms: The leading providers of cloud services, such as AWS, Microsoft Azure, and Google Cloud, are integrated with ISP cloud billing software for effortless billing, which improves the management of cloud operations and streamlines centralized billing for more efficiency.
Scalable Solutions: ISP cloud billing software’s adaptability to growth in clients or services through enhanced functionality makes it possible for the software to scale with an organization’s expansion and increased reliance on cloud technology aids in the streamlining of billing operations.
Security and Compliance: Internet service provider (ISP) cloud billing software comes with billing data protection features such as encryption, authentication, and auditing which aids businesses in safeguarding confidential information, ensuring that data security and regulatory compliance are met.
Consider This – The Best Cloud Management Platforms Out There
When selecting a cloud management platform for your business, it is critical to look into several factors such as ease, integration with other services, billing functionalities, and more. Below are some of the best cloud management platforms that come with powerful ISP cloud billing software:
CloudBolt
CloudBolt is widely regarded for its hybrid cloud offerings and cost optimization capabilities. As one of the top cloud management platforms, it helps companies optimize and manage multi-cloud ecosystems. It also offers valuable insights into cloud resouces and spending.
Features:
Management of multi-cloud costs
Improvement of resources waste optimization
AWS, Azure, and Google Cloud integrations
Cloud billing and invoicing in real time
Customization of cost allocation
To help companies that have cloud finance management challenges, CloudBolt developed their billing software with reporting and invoicing features that are automated, requiring minimal interaction while providing accurate solutions in real time.
CloudHealth by VMware
This is another contender on the list of best cloud management platforms. It is widely recognized for its capability to manage and optimize cloud costs alongside resources and security. It also provides a powerful cloud billing tool suitable for enterprises that operate multiple heavily laden cloud environments.
Overview:
Managing and optimizing cloud expenditures.
Monitoring resources and alerting budget thresholds.
Invoicing and billing automatic systems.
Reporting analytics on finances.
Integration with AWS, Azure, and Google Cloud Services.
With ISP cloud billing software, CloudHealth provides advanced capabilities for forecasting costs, analyzing billing data, and creating custom reports, enabling companies to effectively monitor their cloud expenditures.
RightScale (Now Part Of Flexera)
Now part of Flexera, RightScale is a cloud management platform whose proprietary technology focuses on cost optimization, while providing businesses visibility to their cloud activities.
Key Features:
Cost and usage reporting.
Resource tagging and cost allocation.
Support for multiple clouds (AWS, Azure, Google Cloud, etc).
Real-time billing and invoicing.
Automation of cloud resource deployments.
RightScale helps businesses manage automated billing and provides detailed insights into the usage of cloud resources, enabling flexible pricing.
Microsoft Azure Cost Management and Billing
Azure customers can access the Azure Cost Management and Billing tool, which is an integral part of cloud management suite, providing a holistic view of cloud spend and usage along with billing functionalities.
Features:
Complete cost breakdown per resource, subscription, or department Managing alerts and budgets Automated invoicing and billing summaries Reporting automation Service integration within the Azure ecosystem For businesses in need of efficient billing and a fully integrated solution, especially those utilizing Azure environments. The focus is on providing robust options within the Azure ecosystem.
AWS CloudWatch & Cost Explorer
Amazon Web Services (AWS) users have the integrated option of cloud monitoring and cost management provided by the combination of AWS CloudWatch and Cost Explorer.
Features:
Real-time billing for utilized AWS services Cost anomaly detection and forecasting Advanced tracking for costs, resource utilization, and allocation Customizable reports for billing Companies whose primary cloud service provider is AWS will find AWS’s native billing software an exceptional option as it provides seamless access to billing information and consumption trends.
How ISP Cloud Billing Software Improves Overall Cloud Management
Utilizing ISP cloud billing software within your cloud management platform improves tracking, management, and optimization capabilities regarding cloud costs, enabling businesses to:
Enhance Cost Control: Monitor cloud consumption in real-time to eliminate billing inaccuracies and budget issues.
Enhance Financial Forecasting: Improved budget management and cost control through innovative billing software alternatives result in stronger budget planning. Avoid surprise expenses by effective framework optimization.
Simplifying Billing and Invoicing: Automated billing enhances efficiency by generating accurate invoices in real-time, reducing manual errors and improving operational workflows.
Brighter Business Strategies: Enhanced visibility of cloud expenses gives businesses greater understanding when it comes to resource allocation, usage optimization, and selection of pricing plans, providing more value for their dollar.
Summary
Your specific needs will dictate which cloud management platform is best for your business, but an impactful difference can be made by selecting one with robust ISP cloud billing software. Such software provides real-time billing, cost allocation, and comprehensive integration to the primary cloud services, assisting businesses in managing cloud spending, resource usage, and the financial outlook.
Startups and enterprises alike can streamline operations restructuring and maximize cloud investments by incorporating a sound cloud management platform that includes advanced resource billing.
#isp billing software in delhi#aaa solution for isp#best isp billing software#isp billing software#billing software for isp#isp billing solution#isp crm software#isp erp#isp radius solution#isp management software
0 notes