#legacy evaluation models
Explore tagged Tumblr posts
Text
Jason Todd that’s so used to feeling second best that he can’t quite believe it when someone chooses him. Sheila never wanted him, gave him up the first chance she got. Catherine never managed to pick him over the drugs (and he knows now that that’s not how addiction works but he was a child watching the only person who loved him love what was killing her more). Bruce picked him up as an afterthought, another poor little orphan boy to always fail at filling the shoes of the first. He’s barely cold in his grave when there’s another, better version already standing next Bruce. The Titans couldn’t see past the legacy Dick left behind, constantly compared Jason to him as the less adequate model; barely sufficient, much less welcomed. Jason wants so badly to be chosen first but time and experience has only ever taught him otherwise.
Jason falls in love with you, but he can never fully believe that the love is returned fully. He’s so eager to be your only choice that he’s terrified of when you’ll eventually pick someone else over him. He wants to be greedy, drink up the experience and novelty until he’s sick on it, but he can’t. Can’t help that creeping sense that your love and attention is in finite supply, unseen deadline looming closer. He’s always got one foot out the door, unable to fully commit to a relationship when he’s bracing for the blow of you leaving. Sure that one day you’ll finally see all the flaws that make him not enough, the flaws that everyone else in his life have already discovered. Convinces himself that there’s a middle ground, one where he gets to love you but at a distance that means the leaving won’t hurt so much. But that means always holding the two of you on edge, the pressure and expectation of your choice lingering and twisting until the two of you are no longer what you were in the beginning. To know when he gets too close, he has to constantly be re-evaluating your relationship. Every moment spent together waiting for you to flinch, to waver in your commitment to him, and ready to act when he sees it. Believes that if he’s the one holding the knife, it won’t cut as deep.
He can’t see that everyday you wake up and choose him, that your love has always been a choice you are willing to make for him. Everyday you have to bear the weight of his scrutiny and it is exhausting. You know he’ll never fully trust you because he can’t believe you won’t leave first. That he’ll never fully open up to you, because he doesn’t want to hand you weapons to hurt him with, to make you reconsider choosing him. You know that if you push him on this, he’ll only interpret it as the first stages of you leaving. You’d thought that with time and proof he’d start to believe. To choose you and your love as much as you’ve chosen him.
Now, now you are trapped in a cage of your own collaborative making. If you leave now, you’ll only have proven his greatest insecurity all along. If you stay, this love will continue to fester like a wound. There is no outcome where you both come out unscathed.
#the jason todd thesis for ydcmb (uibyt)#this is a man in desperate need of therapy#jason todd x reader#jason todd x you#jason todd headcanon#jason todd imagine#jason todd x y/n#jason todd x gender neutral reader#jason todd x fem!reader#jason todd x male reader#red hood x reader#red hood x you#jason todd fanfiction#jason todd fic#sunnie writes 🌻#snack fic
847 notes
·
View notes
Text
Look, Tyra Banks is problematic and has been rightfully criticized for the many, many problematic statements she had made on ANTM. But, there's something so hypocritical and rage-inducing about seeing White women viciously commenting on Tyra Banks' physique and appearance at the Victoria Secret Fashion Show, saying that she deserved it for making women feel bad on ANTM.
There are a couple things that I think need to be addressed which is:
1. Using fatphobic statements and bodyshaming Tyra Banks and thinking that it's justified becos she had made fatphobic and bodyshaming statements before, does not make you any better than she was. You are still bodyshaming. Also seeing White women thinking they are justified in shaming a Black woman's body? No, fucking no.
2. The individualizing of systemic problems to Tyra Banks. Banks is literally not the only person on ANTM who bodyshamed the contestants on the show. The other judges had participated in it as well, and it tells you a lot about the modelling industry in general. Banks has also been criticized and denied jobs in the past for not meeting beauty standards as a curvy Black woman. Is it too far of a stretch to consider that in order for her, a curvy Black woman, to succeed in the modelling industry, she'd internalized a bunch of toxic beauty standards?
All this to say, I think it's possible to re-evaluate Tyra Banks' legacy and hold her accountable for what she has said and the harm she's complicit in upholding, while also making space to be compassionate and nuanced about her. I mean, if (mostly White) women can see Ballerina Farm as a victim while she's been profitting off promoting white supremacist, cisheteronormative patriarchal values in a pretty soft-lit package to young impressionable pple, I think we can do the same for Tyra Banks?
Anyways, please read this:
#tyra banks#america's next top model#misogynoir#fatphobia#bodyshaming#white feminism#double standards
182 notes
·
View notes
Text

Celebrating 60 Years of the XB-70 Valkyrie Mach 3 Super Bomber
September 16, 2024 Military Aviation
XB-70 60th anniversary
The lone XB-70 Valkyrie is photographed as it is moved to a new building at the Museum of the United States Air Force located at Wright-Patterson Air Force Base, Ohio, on Oct. 27, 2015. Beginning in the late 1950s and continuing through the mid-1960s, tests were conducted at Arnold Air Force Base, Tenn., headquarters of Arnold Engineering Development Complex, in support of the XB-70 program. The now-retired aircraft made its first flight on Sept. 21, 1964. (U.S. Air Force photo by Will Haas)
The experimental legacy of the iconic XB-70 Valkyrie, which made its first flight on Sept. 21, 1964.
An article published on the U.S. Air Force website commemorates the 60th anniversary of the first flight of the legendary XB-70 Valkyrie, a supersonic bomber that captured the imagination of aviation enthusiasts and engineers alike. Known for its sleek and futuristic design, the XB-70 remains a symbol of the experimental and ambitious spirit of Cold War-era aircraft development. Despite only two prototypes ever being built, the aircraft has left an indelible mark on military aviation history.
The XB-70 Valkyrie was originally conceived in the 1950s as a high-speed, high-altitude bomber for the U.S. Air Force Strategic Air Command. At a time when technological advancements were rapidly accelerating, the U.S. Air Force sought a bomber capable of flying faster and higher than the B-52 Stratofortress, its workhorse of the era (as well as the backbone of the strategic bomber fleet today and for some more decades in the future…).
With a planned cruise speed of Mach 3 and an operating altitude of 70,000 feet, the XB-70 promised to outpace and outmaneuver Soviet defenses, which were a growing concern during the Cold War.
One of the most remarkable features of the XB-70 was its ability to “ride” its own shockwave, a design innovation that allowed it to maintain stability and performance at supersonic speeds. The Valkyrie’s iconic delta wing, combined with six powerful jet engines, gave it an exotic and striking appearance, making it one of the most visually distinctive aircraft ever built. Its outer wing panels were hinged, allowing them to be lowered during flight to optimize the aerodynamic performance at high speeds.

The XB-70 looks like an alien spacecraft from this angle. (Image credit: USAF)
The article highlights the crucial role played by Arnold Engineering Development Complex (AEDC) in the development of the XB-70.
The testing of the Valkyrie’s engines, aerodynamics, and other key components began at Arnold Air Force Base in the late 1950s, well before the first prototype took shape. The AEDC’s facilities were instrumental in pushing the boundaries of what was possible in aviation at the time. One of the earliest tests involved the air-breathing engine nozzles proposed for the XB-70 in March 1958. This was followed by extensive wind tunnel testing of scale models of the Valkyrie, where the aerodynamic characteristics of bombs dropped from the aircraft were also studied.
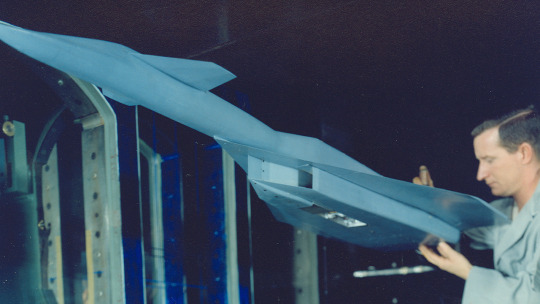
A technician makes adjustments to a scale model of the XB-70 Valkyrie before aerodynamic characteristics related to the aircraft are evaluated in Tunnel A of the von Kármán Gas Dynamics Facility at Arnold Air Force Base, Tenn., headquarters of Arnold Engineering Development Complex, in 1959. Beginning in the late 1950s and continuing through the mid-1960s, tests were conducted at Arnold Air Force Base, Tenn., headquarters of Arnold Engineering Development Complex, in support of the XB-70 program. Only two Valkyries were built, with only one of the pair remaining. The now-retired aircraft made its first flight on Sept. 21, 1964. (U.S. Air Force photo)
Development continued into the early 1960s, with the YJ93 turbojet engines, designed specifically for the XB-70, undergoing rigorous testing at AEDC. These engines were critical to the Valkyrie’s ability to reach and maintain supersonic speeds. However, in 1961, before the first prototype was even completed, the bomber program was canceled due to budget constraints and concerns over the bomber’s vulnerability to Soviet surface-to-air missiles, which had rapidly advanced in capability.
Although the XB-70 bomber program was terminated, the Valkyrie found new life as a research aircraft.

Three drag chutes were needed to slow down the landing roll of the XB-70. (Image credit: Reddit edit The Aviationist)
The U.S. Air Force recognized the potential of the aircraft to serve in aerodynamics and propulsion research, particularly in the study of large supersonic aircraft. Consequently, two XB-70 prototypes were completed, and testing continued, including at AEDC, where a scale version of the XB-70 inlet, paired with a full-scale YJ93 engine, was tested in August 1962.
XB-70A number 1 (62-001) made its first flight from Palmdale to Edwards Air Force Base, CA, on Sept. 21, 1964. The second XB-70A (62-207) made its first flight on Jul. 17, 1965. The latter differed from the first prototype for being built with an added 5 degrees of dihedral on the wings as suggested by the NASA Ames Research Center, Moffett Field, CA, wind-tunnel studies.

North American XB-70A Valkyrie on the taxiway with a cherry picker. Photo taken Sept. 21, 1964, the day of the first flight. Note: the left main landing gear brakes locked during the landing causing two tires to blow. (U.S. Air Force photo)
While the 62-001 made only one flight above Mach 3, because of poor directional stability experienced past Mach 2.5, the second XB-70, achieved Mach 3 for the first time on Jan. 3, 1966 and successfully completed a total of nine Mach 3 flights by June on the same year.
However, the Valkyrie program suffered a devastating setback in June 1966 when the second prototype was destroyed in a midair collision with an F-104N Starfighter during a photoshoot. This tragic accident resulted in the loss of key personnel and diminished the future prospects of the Valkyrie.

North American XB-70A Valkyrie just after collision. Note the F-104 is at the forward edge of the fireball and most of both XB-70A vertical stabilizers are gone. (U.S. Air Force photo)
Despite this setback, the remaining XB-70 continued to serve as a valuable research platform. In 1967, the U.S. Air Force transferred the aircraft to NASA, where it was used in support of the National Supersonic Transport (SST) program. NASA employed the XB-70 to investigate supersonic flight operations, but the SST program was eventually canceled in 1971, marking the end of America’s efforts to develop a commercial supersonic airliner.
The XB-70 Valkyrie’s final flight took place on Feb. 4, 1969, when it was flown to Wright-Patterson Air Force Base in Ohio. There, the aircraft was placed on display at what is now the National Museum of the United States Air Force, where it remains a testament to the audacious engineering and design of its era.

A view of the six massive afterburners on the XB-70 Valkyrie as the aircraft is towed out of its display hangar temporarily for museum maintenance. (Photo: National Museum of the U.S. Air Force via YouTube)
Though only two XB-70s were ever built, their legacy endures: the aircraft’s pioneering advancements in aerodynamics, engine performance, and high-speed flight helped shape the future of supersonic aviation.

Pilots who were to perform the first test flights for the XB-70 Valkyrie operate the YJ93 engine, the powerplant of the XB-70, while the engine is tested under simulated flight conditions in May 1964 in the Rocket Test Facility at Arnold Air Force Base, Tenn., headquarters of Arnold Engineering Development Complex. This was done to help the pilots familiarize themselves with the performance characteristics of the engine prior to the first XB-70 flight, which occurred on Sept. 21, 1964. Beginning in the late 1950s and continuing through the mid-1960s, tests were conducted at Arnold AFB in support of the XB-70 program. Only two Valkyries were built, with only one of the pair remaining. (U.S. Air Force photo)
The first prototype made a total of 83 flights, amassing 160 hours and 16 minutes of flight time, while the second prototype completed 46 flights, totaling 92 hours and 22 minutes.
The XB-70 Valkyrie, with its daring design and groundbreaking capabilities, continues to captivate aviation enthusiasts and engineers. Its story, though short-lived in terms of operational use, highlights the relentless pursuit of innovation that defines the U.S. Air Force and its engineering partners. Sixty years after its first flight, the Valkyrie remains an iconic symbol of the bold ambitions of Cold War-era aviation.

XB-70 Night Take-off. (Photo via Air Force Materiel Command History Office)
About David Cenciotti
David Cenciotti is a journalist based in Rome, Italy. He is the Founder and Editor of “The Aviationist”, one of the world’s most famous and read military aviation blogs. Since 1996, he has written for major worldwide magazines, including Air Forces Monthly, Combat Aircraft, and many others, covering aviation, defense, war, industry, intelligence, crime and cyberwar. He has reported from the U.S., Europe, Australia and Syria, and flown several combat planes with different air forces. He is a former 2nd Lt. of the Italian Air Force, a private pilot and a graduate in Computer Engineering. He has written five books and contributed to many more ones.
@TheAviationist.com
118 notes
·
View notes
Text

Part 5: The Potential for All For One Copycats and Miscellaneous Impacts in Post-Manga My Hero Academia
This analysis explores the likelihood of copycat villains emerging in the wake of All For One’s (AFO) defeat in My Hero Academia, considering his immense power and influence, and the societal conditions that persist post-manga. It evaluates the factors that could inspire or enable copycats, the mechanisms through which they might emulate AFO, and the broader implications for the world. Additionally, it addresses miscellaneous impacts of AFO’s legacy, including societal, cultural, and systemic effects not covered in prior analyses. This examination remains thorough, grounded in the series’ narrative, and accounts for the persistent societal flaws highlighted in the manga’s epilogue.
Context: AFO’s Legacy and Post-Manga World
AFO’s Defeat and Influence
All For One, the “Symbol of Evil,” was a towering figure whose Quirk-stealing ability, manipulative genius, and century-long influence shaped My Hero Academia’s world. His defeat in the Final War Arc—via physical erasure by Eri’s Rewind Quirk, vestige destruction by Izuku Midoriya, and the disintegration of Tomura Shigaraki’s body—marks a significant victory for hero society. However, the epilogue reveals that many societal issues persist:
Corrupt Institutions: The Hero Public Safety Commission (HPSC) undergoes reform attempts (e.g., Hawks’ efforts), but its history of corruption (e.g., Lady Nagant’s assassinations, Hawks’ training) suggests lingering vulnerabilities.
Quirk Singularity Theory: Dr. Kyudai Garaki’s theory, predicting Quirks growing increasingly powerful and unstable, is confirmed, raising the risk of god-like abilities emerging.
Villain Ideologies: Groups like the Meta Liberation Army (MLA) and figures inspired by Stain’s philosophy continue to influence villains, as seen with Spinner’s book documenting the League of Villains’ actions.
Societal Discontent: Despite hero reforms, Quirk-based discrimination and neglect of vulnerable individuals (e.g., Tenko Shimura’s backstory) persist, creating fertile ground for villainy.
AFO’s influence, through his actions (e.g., Villain Factory, Nomu) and ideology of power over morality, leaves a lasting imprint, making copycats not only possible but likely.
Post-Manga Setting
The epilogue, set eight years after the Final War Arc, depicts a world recovering but still flawed:
Hero Society: Heroes like Izuku (now Quirkless, teaching at U.A.), Bakugo, and Todoroki lead a new generation, but the hero system is strained by societal changes and Quirk evolution.
Villain Activity: While major threats like the League of Villains are dismantled, smaller villain groups and lone actors persist, inspired by AFO’s legacy or Spinner’s writings.
Global Context: International hero cooperation increases, but AFO’s global network (e.g., delaying foreign heroes) suggests residual influence abroad.
This setting provides the backdrop for assessing the potential for AFO copycats and miscellaneous impacts of his legacy.
Could There Be Many Copycats?
Factors Enabling Copycats
Several factors in the post-manga world make the emergence of AFO-inspired copycats highly plausible:
1. AFO’s Mythic Status
Symbol of Evil: AFO’s reputation as the ultimate villain, akin to a comic book Demon Lord, inspires awe and fear. His defeat, while a heroic triumph, elevates him to a legendary figure, much like Stain’s arrest video inspired villains like Spinner and Toga.
Spinner’s Book: The epilogue notes that Spinner, a former League member, publishes a book detailing the League’s actions and AFO’s influence. This text could serve as a manifesto, inspiring disaffected individuals to emulate AFO’s power-grabbing tactics or ideology.
Cultural Impact: AFO’s philosophy of might over right resonates with those marginalized by hero society, particularly in a world where Quirk discrimination persists. His charisma and success make him a model for aspiring villains.
2. Quirk Singularity Theory
Evolving Quirks: The Quirk Singularity Theory predicts that Quirks will become increasingly powerful, potentially producing abilities rivaling AFO’s All For One. A copycat could develop a Quirk-stealing or power-accumulating ability, mirroring AFO’s capabilities.
Precedent for Similar Quirks: The manga shows Quirks with parallel mechanics, such as Overhaul’s ability to manipulate matter or New Order’s reality-altering power. A naturally occurring Quirk-stealing ability is plausible, especially as Quirks grow more complex.
Technological Amplification: AFO’s Villain Factory and Dr. Garaki’s experiments (e.g., Trigger, Nomu) provide a blueprint for artificially creating or enhancing Quirks, potentially allowing a copycat to replicate AFO’s powers through science.
3. Persistent Societal Flaws
HPSC Corruption: Despite reforms, the HPSC’s history of unethical practices (e.g., grooming Hawks, commissioning assassinations) suggests that corrupt elements could persist, providing resources or cover for a copycat. A rogue HPSC official could access Quirk registries or experimental tech to emulate AFO.
Social Discontent: The neglect of individuals like Tenko Shimura, combined with ongoing Quirk discrimination, creates a pool of disenfranchised people susceptible to AFO’s ideology. A charismatic copycat could rally them, as AFO did with his followers.
Villain Networks: AFO’s global connections and surviving allies (e.g., Jailbreakers from Tartarus, remnants of the Villain Factory) could support a copycat, providing resources, knowledge, or manpower.
4. Precedents for Emulation
Stain’s Legacy: Stain’s ideology inspired a wave of villains (e.g., Spinner, Toga, Dabi), showing how a single figure’s philosophy can spark copycats. AFO’s broader influence and tangible power make him an even more compelling model.
Meta Liberation Army: The MLA’s persistence, even after Re-Destro’s defeat, demonstrates that villain ideologies endure. A copycat could revive or adapt AFO’s vision, blending it with MLA principles of Quirk liberation.
Villain Factory: AFO’s experiments with Number 6 and Trigger show that his methods are replicable. A scientist or villain with access to similar resources could create a new AFO-like figure.
Mechanisms for Copycat Emergence
Copycats could emulate AFO through various means, each grounded in the series’ mechanics:
1. Natural Quirk Development
Spontaneous Quirk: The Quirk Singularity Theory suggests a new villain could naturally develop a Quirk-stealing or power-accumulating ability. For example, a Quirk that absorbs or mimics others’ abilities could emerge, akin to Vermillion’s Power Copying Semblance from prior discussions.
Examples: A Quirk like Nine’s ability to wield multiple Quirks or Monoma’s Copy could evolve into a more permanent, AFO-like power. The manga’s emphasis on Quirk evolution supports this possibility.
2. Scientific Replication
Dr. Garaki’s Legacy: Garaki’s work on Nomu, Trigger, and Quirk duplication could be continued by a rogue scientist (e.g., a surviving Villain Factory member or HPSC affiliate). The Jaku General Hospital lab, though destroyed, sets a precedent for such experiments.
Quirk-Destroying Drug: AFO’s reverse-engineering of Overhaul’s Quirk-erasing drug shows that Quirks can be manipulated artificially. A copycat could develop a Quirk-stealing serum or device, using HPSC or black-market resources.
Nomu Technology: Creating a Nomu with AFO’s Quirk or consciousness, as speculated in Part 2, could produce a copycat entity, especially if Garaki’s notes or facilities survive.
3. Ideological Successors
Charismatic Leaders: A villain inspired by AFO’s philosophy could adopt his manipulative tactics without his Quirk. For example, a figure like Re-Destro, with MLA resources, could emulate AFO’s shadow rule, using charisma and strategy to amass power.
Spinner’s Influence: Spinner’s book could inspire a new generation of villains to mimic AFO’s methods, such as building networks or exploiting societal flaws. A charismatic copycat could rally these followers, as AFO did with the League.
4. HPSC or Criminal Networks
Rogue HPSC Operative: A corrupt HPSC member with access to Quirk registries or experimental tech could emulate AFO, stealing or enhancing Quirks to build power. The HPSC’s history of secrecy makes this plausible.
Jailbreakers and Allies: Surviving Jailbreakers (e.g., Lady Nagant, before her redemption) or AFO’s global contacts could support a copycat, providing resources or loyalty. The Tartarus breakout shows AFO’s ability to mobilize powerful allies.
Potential Copycat Profiles
Mad Scientist: A Garaki-like figure, using Villain Factory remnants or HPSC labs, creates a Quirk-stealing device or bio-engineered villain, mirroring AFO’s Nomu experiments.
Charismatic Ideologue: A villain inspired by Spinner’s book or AFO’s legend adopts his philosophy, building a new League-like group to challenge hero society.
Quirk Prodigy: A young villain with a naturally evolved Quirk-stealing ability emerges, driven by AFO’s mythos to surpass him.
HPSC Traitor: A high-ranking HPSC official, disillusioned like Lady Nagant, uses their authority to replicate AFO’s tactics, accessing Quirks or resources covertly.
International Warlord: A foreign villain, part of AFO’s global network, adopts his methods, using advanced Quirks to dominate their region and challenge Japan’s heroes.
Likelihood of Many Copycats
High Potential: The combination of AFO’s mythic status, the Quirk Singularity Theory, persistent societal flaws, and existing villain networks makes multiple copycats likely. The manga’s epilogue suggests that villainy persists, with Spinner’s book amplifying AFO’s influence.
Scale and Impact: While one or two copycats might achieve significant power (e.g., a Quirk-stealing prodigy), many would likely be lesser imitators, adopting AFO’s ideology or tactics without his full capabilities. The MLA’s widespread membership and Stain’s broad influence suggest a wave of smaller-scale copycats is plausible.
Counterforces: Heroes like Izuku, Bakugo, and Todoroki, along with global cooperation, would work to suppress copycats. However, the HPSC’s vulnerabilities and Quirk evolution could delay or complicate these efforts.
Miscellaneous Impacts of AFO’s Legacy
Societal Impacts
Quirk Regulation Challenges: The Quirk Singularity Theory’s confirmation forces hero society to implement stricter Quirk regulations, potentially alienating citizens and fueling copycat ideologies. AFO’s experiments (e.g., Trigger) set a precedent for unregulated Quirk enhancement, inspiring rogue scientists or villains.
Persistent Fear: AFO’s reign as the Symbol of Evil leaves a cultural scar, with the public fearing another AFO-like figure. This fear could undermine trust in heroes, as seen during the Paranormal Liberation War Arc.
Disenfranchised Youth: AFO’s manipulation of figures like Tenko Shimura highlights society’s failure to support vulnerable individuals. Post-manga, this issue persists, providing copycats with a pool of recruits, as seen with the K3 Gang’s initial villain worship in prior discussions.
Cultural Impacts
Villain Mythology: AFO’s Demon Lord persona, inspired by Captain Hero comics, becomes a cultural archetype, romanticized by some as a symbol of rebellion against hero society. Spinner’s book amplifies this, potentially inspiring fanatical copycats.
Heroic Backlash: The rise of copycats strengthens the resolve of heroes like Izuku, who teach the next generation to counter AFO’s ideology. This creates a cultural tug-of-war between heroic altruism and villainous power, echoing AFO’s conflict with Yoichi.
Media Influence: The media, which once glorified All Might, might sensationalize AFO’s legacy, inadvertently inspiring copycats. This mirrors how Stain’s arrest video fueled villainy, as discussed previously.
Systemic Impacts
HPSC Reforms: Hawks’ attempts to reform the HPSC face resistance from entrenched corruption, as noted in prior conversations. AFO’s influence over corrupt officials (e.g., pre-reform HPSC) suggests that copycats could exploit similar vulnerabilities, accessing resources or intelligence.
Villain Networks: Remnants of AFO’s network (e.g., Villain Factory, Jailbreakers) persist, providing infrastructure for copycats. The destruction of Jaku General Hospital and Gunga Mountain Villa does not eliminate all of AFO’s safe houses or allies, as speculated in Part 2.
Global Ramifications: AFO’s international connections, used to delay foreign heroes, could support copycats abroad. A foreign villain emulating AFO might destabilize regions with weaker hero systems, challenging global stability.
Economic Impacts
Black Market Growth: AFO’s Quirk trafficking and Trigger experiments created a black market for abilities, which likely persists post-manga. Copycats could exploit this market, trading stolen Quirks or enhancing their own, as seen with Onomura Pharma Corp.’s role in prior discussions.
Economic Strain: The cost of rebuilding after the Final War Arc strains hero society’s resources, potentially limiting responses to copycats. AFO’s fronts like Koga Constructions set a precedent for villains using legitimate businesses to fund operations.
Miscellaneous Threats
Humarise and MLA 2.0: As mentioned in prior conversations, groups like Humarise (anti-Quirk extremists) and the MLA could resurge, inspired by AFO’s legacy or Spinner’s book. A copycat might align with these groups, blending AFO’s Quirk-stealing tactics with their ideologies.
CRC Reemergence: The Creature Rejection Clan (CRC), driven by anti-heteromorph sentiment, could exploit post-war chaos to return, potentially aligning with a copycat who uses AFO’s philosophy to rally marginalized groups.
Eldritch Quirks: The Quirk Singularity Theory’s implication of “god-like” or “eldritch” Quirks, as noted previously, could produce copycats with powers rivaling AFO’s, posing existential threats to hero society.
Challenges to Copycats
Heroic Response: Heroes like Izuku, now a teacher, and Class 1-A graduates (e.g., Bakugo, Todoroki) are vigilant, trained to counter AFO-like threats. Global hero cooperation, strengthened post-war, could suppress copycats early.
Resource Scarcity: While AFO had access to vast resources, copycats may lack his infrastructure, limiting their scale. The destruction of key facilities (e.g., Jaku Hospital, Gunga Villa) hinders replication of his methods.
Ideological Resistance: AFO’s defeat reinforces heroic ideals, inspiring a generation to reject his philosophy. Copycats would face cultural pushback from a society valuing All Might’s legacy.
Quirk Instability: The Quirk Singularity Theory suggests that powerful Quirks could destabilize their users, potentially causing copycats to self-destruct, as seen with AFO’s Rewind overuse.
Conclusion
The post-manga world of My Hero Academia is ripe for All For One copycats due to his mythic status, the Quirk Singularity Theory, persistent societal flaws, and surviving villain networks. Copycats could emerge through natural Quirk development, scientific replication, ideological succession, or exploitation of corrupt systems like the HPSC. They might range from powerful Quirk-stealing prodigies to lesser imitators inspired by Spinner’s book. AFO’s legacy also manifests in miscellaneous impacts: societal fear, cultural villain worship, systemic vulnerabilities, and economic strain. While heroes and reforms counter these threats, the potential for Humarise, MLA, or CRC resurgence, combined with increasingly powerful Quirks, ensures that AFO’s influence lingers, challenging hero society’s stability and setting the stage for new conflicts.
#mha#mha villain#mha fandom#mha meta#mhanalysis#my hero academia fandom#bhna#bhna villains#bhna fandom#anaylsis mha#villain mha#mha shitpost#my hero academia shitpost#all for one#afo#all for one mha#zen shigaraki#mha zen shigaraki#mha all for one#all for one zen#my hero academy#my hero academy fandom#AllForOne#MyHeroAcademia#SymbolOfEvil#QuirkDoomsday#WorldDomination#VillainAnalysis#OneForAll#ZenShigaraki
21 notes
·
View notes
Text
New Sideproject - "What If" aircraft liveries
Got bored.
Downloaded AC7 aircraft models and retexture templates.
Made a thing.
Figured I'd share.

"F/A-23 Redback", of 75SQN, Royal Australian Air Force
[Lore/Story behind the aircraft below the cut]
When Lockheed Martin won the Advanced Tactical Fighter (ATF) program with their YF-22 Raptor demonstrator, Northrop & McDonnell Douglas placed their contender, the YF-23 Black Widow II's, into storage pending dismantling for static display.
However, fortune would come calling from an unsuspecting source: Australia. The Royal Australian Air Force had recently completed delivery of 75 brand new F/A-18A/B Hornets to replace their aging fleet of Mirage III's. However, planners within the Department of Defence and Australian Defence Force recognised the shifting landscape of aerial warfare, and payed close attention to the US's ATF program.
Initially, the RAAF wanted to purchase the F-22 after it won the program in 1991 and had expressed tentative interest, though didn't commit due to the high initial operating costs at the time and recent budgetary issues the ADF faced due to other concurrent modernization programs taking place. By the time the RAAF were ready to order the aircraft, the US had marked the aircraft as unavailable for export sales.
Lockheed Martin did offer the RAAF the opportunity to buy into the Joint Strike Fighter program, which would be the precursor program that resulted in the development of the F-35 Lighting II series of aircraft, however RAAF leadership turned to McDonnell Douglas and Northrop, recalling how well their YF-23 performed in the program demonstrations.
The two testbed aircraft, Spider and Grey Ghost, were shipped to Australian on loan for use by the RAAF's Aircraft Research & Development Unit (ARDU) for evaluations in the mid 1990's, as the operating environment in Australia was different to that of the United States. While the aircraft performed well, some modifications were suggested including the use of more fuel efficient engines, an adjusted cockpit panel layout, and provisions to mount external stores much like the F-22 had (primarily for long-distance ferry flights across Australia, but also for use in low-threat or permissive environments where stealth is not a concern).
Northrop & McDonnell Douglas accommodated the upgrades, and in 1999, an initial purchase of 24 F/A-23A stealth fighters was made to equip two squadrons with the modified design. The airframe was given the designator of Redback in reference to the small but dangerous spider that called the continent home, whilst also showing homage to the original name of Black Widow II.
No 75 SQN and No 77 SQNs were the first recipients of the new F/A-23As, operating as composite squadrons comprised of both the new Redback and the older F/A-18A+ Hornets. As the Hornets aged, they were transferred to No. 2 Operational Conversion Unit for training and adversarial use.
There was talk of purchasing more Redbacks to augment a strike gap left behind pending the retirement of the venerable F-111C Aardvarks, however the decision was made to purchase Boeing's F/A-18F Super Hornets (with Boeing having bought and merged with McDonnell Douglas).
F/A-23A Redback was the initial version developed in the late 1990s and early 2000's, with upgrades and enhancements introduced over time to incorporate newer technologies and extend the life of these aircraft. Upgraded aircraft were unofficially referred to as -23A+s, similar to how F/A-18As that were upgraded to match the capability of the newer F/A-18C/Ds were referred to as A/B+
In the late 2000's, the RAAF (under license from Northrop/Boeing) introduced a variant featuring new engines, a new radar and updated avionics to incorporate newly released weapons systems, designated F/A-23B.
With the F-35 coming into service with the US and other JSF partner nations, and the older legacy Hornets retired out of service, the RAAF were looking into how to compliment their fleet of Redbacks. The F/A-18F Super Hornets operated by No. 1 and No. 6 Squadron were due for upgrade, and Boeing proposed the "Advanced Super Hornet" as a upgrade package.
To sweeten the deal, components from ASH were splintered off for use to update the fleet of F/A-23Bs, now used by all three former Hornet squadrons (3, 75, & 77) as well as 2OCU and the ARDU. Forming the B+ 'Mid Life Update', components borrowed from the ASH included it's new IRST and AESA radar package, compatibility with the Enclosed Weapons Pod, and a fully glass cockpit display.
By 2020, both the Redback and Rhino finished their upgrades, and formed the backbone of Australia's air warfare component, with No.'s 3, 75, and 77 operating F/A-23B+ Redbacks, No. 1 operating the F/A-18F+ (informal designation for the Advanced Super Hornet) and No. 6 operating as a composite of F/A-18F+ and EA-18G+ (EA-18G Growlers given the Advanced Super Hornet upgrade package).
Australia remains the only operator of the YF-23 platform, though not for a lack of trying on the part of Northrop & McDonnell Douglas (later Boeing).
---
If you made it this far, good on 'ya.
This YF-23 "What If" concept livery is dedicated to my friend @kaitaiga, who I know is fucking obsessed with the YF-23 Black Widow II. The livery came first, and then of course my 'writer' brain had to think up a background as to how the RAAF got their hands on an F-22 equivalent aircraft and maintained its service instead of buying into the F-35 program.
I have nothing against F-35 (anymore) though I am still salty that we haven't gone full-send into the Advanced Super Hornet. The CFTs along the spine just look sleek as fuck.
Thank you for reading!
13 notes
·
View notes
Text
510 spoilers
i have so many thougths about 510 it's isane, i left a long ass comment on tvtime and i still can't stop thinking about what could happen in the rest of the season... IT'S INSANE.
my thought is, john changed his will more after 508 than what i thought which was s2/4.. like it was talked about between John and Beth at the end of that ep about hit and hiring professional and i'm sure John thought about the implication about it all (i don't remember if this was shown or not) and changed his will between 508 & 509..
NOW with the beginning of 510 we know Beth is cooking something, with early s5 we know it's something to do with bringing heavy ass revenue to the ranch... SO THOUGHTS ARE: what if we're still getting flashback from the period between 508 and 509 because we're gonna be shown that something.
We know she is taking the Texas ranch as a model of what she want to achieve for the Dutton ranch, i obviously don't think she could achieve that in 6 weeks.. but knowing her like we do, we know she did something and was successful at it.. which how Jamie said Beth is very resourceful sooo in 6 weeks girlie probably achieve a lot. Because she is like a bull when she has something in her line of sight.. oh she is unstopable. i'm so very curious as to what she has plan..
I also think that John will, will actually fuck over Jamie in some regards, maybe in a way to make him rethink his position in terms of the ranch and random big company putting an airport on it or in terms to re evaluate his position in the Dutton family, we know Jamie just want approval and love from his family... I don't want a redemption arc for him but we likely might get it.. what if John just took him off the will and put Rip in it instead of him? That'd be fun
I really do think Rip is somehow in that will, in what capacity idk, what he gain from it idk, but hopefully in a way that blocks Kayce from abandonning the ranch. because his conversation with Tate make it very obvious that he doesn't want to run the ranch if Tate doesn't want to have it? John knew that, heavily, maybe in a way to protect his legacy he put Rip in charge of the ranch? Because he knows that Rip would never willingly abandon the ranch... or he put Beth in charge.. but i think Kayce isn't mainly the only one (if at all) that inherit the right to be in charge of the ranch.
anyways so many thoughts, it's getting soooooo good, i'm loving this part of the season?
#yellowstone#510 spoilers#beth dutton#rip wheeler#kayce dutton#john dutton#jamie dutton#dutton ranch
7 notes
·
View notes
Text
I have so many thoughts about Octavian. so many. here are some of them.
!!!SPOILERS FOR HoO!!!
i feel so bad for Octavian. was he a good person? no! do I think he deserved to die from being thrown through the sky on a cannonball? also, no!!
I think about him a lot, especially as someone who looks into the antagonistic characters in the pjo universe (keep in mind, I dont think they've done no wrong, but I do like to evaluate characters a lot)
the issue with him was his fatal flaw being hubris, which is very common amongst PJO characters. the issue is that we actually see his fatal flaw being harmful, instead of Annabeths seething. he's acting out and causing harm, acting on a flaw quite literally designed to kill him. ontop of that, much like Luke, he's hearing voices promising that it can fix everything. he wants to "save Rome" because he has been taught that Rome is perfect and that it is everything. it isn't, but Octavian doesn't know that.
Octavian is a legacy. He's not a demigod. he has likely never left New Rome. he can not fathom that there are lives and people outside of rome -- including those with different viewpoints and ideas. He has spent his entire life fixated on Rome, specifically Ancient Rome, as it is what it is modeled after.
there is something so compelling about a character that has been led wrong. a character that has grown up with the idea that the society around him is perfect, fighting against change because "why would Rome need to change? it's already perfect". a characters fatal flaw quite literally tearing him apart at the seams. a character who can't learn. a character fueled to do more wrong, truly believing that he is aiding his people.
Octavian doesn't get a redemption arc. he doesn't end the war like Luke, but in my eyes, that just makes his character a lot more tragic. he doesn't get a happy ending. there is no debate over whether or not Octavian is a good person.
#AND HE WAS EIGHTEEN#A CHILD#A LITERAL CHILD#i have so many thoughts#please let this reach the right audience#hoo#octavian#new rome#pjo hoo toa
12 notes
·
View notes
Text

TRAINEE MISSION 020 ( PART 2 / MALE TRAINEES )
SCHEDULE TYPE: TRIMESTER ( PART 1 OUT OF 1 ) SCHEDULE RESTRICTIONS: Cannot be paired with another trimester schedule, unless stated otherwise. for reference as to whether your muse is eligible for this event, please click over HERE.
all of the MALE trainees were gathered in the auditorium later on in the day as they waited for news on what would happen in the next few months. once INSUNG appeared on stage, he began the meeting by talking about what they would be working on. “i’ve been informed that the boys will be having a trainee showcase tour in the upcoming months, so to prepare for that they’ve modified your schedules a bit to include more workshops in certain areas that all of you would need to work on.”
LANGUAGE WORKSHOPS
during JANUARY-FEBRUARY, all of the trainees will be attending language workshops. if any trainee muse does NOT have 100 KOREAN at the time of this post, they will be attending KOREAN workshops along with JAPANESE, ENGLISH, and MANDARIN. if the muse has 100 points in JAPANESE, ENGLISH and/or MANDARIN, that will be replaced with KOREAN ( if they don’t have 100 points ) OR more of a performance based workshop.
by the first week of MARCH, each trainee will be doing their evaluation in front of three coaches — JANG INSUNG, KWON SOYI, and SEO YOUNGJAE. for the evaluation, they will be asked to perform a song in a different language ( preferably whichever language they’re the least fluent at among the ones mentioned ). at the end of it, the coaches will give them feedback on what they will need to improve on for the next quarter.
PERFORMANCE BASED WORKSHOPS
in addition to the language workshops, the trainees will be doing more performance related workshops to prepare for the trainee showcase that they will be having in the next term.
here is a brief outline of what will be focused during each month:
JANUARY: singing OR rapping ( trainees may suggest which one they prefer to work on )
FEBRUARY: dancing
MARCH: performance AND acting
then by the end of MARCH, the trainees will be teaming up with 2-3 people for their performances ( must be the same gender ) where they will be asked to perform one of their lgc senior artist’s songs.
TRAINEE SHOWCASE – SPECIAL STAGE
all of the male trainee muses who participate in the WRITING CHALLENGE ( see info below ) AND fill out the form below will be a part of a special stage in the trainee showcase. ic wise, legacy will be having a casting call where any muses who are interested will be asked to audition. during the audition, they will be given a lyric sheet and sing to an original and untitled song ( ooc wise, it will be ‘UMM GREAT’ ). the coaches will not give them feedback during the audition, but a week after the auditions are done they will reveal who will be chosen for the song.
to make things easier for everyone, ooc the results as to who will be a part of this special stage will not be revealed until next term ( but ic, they would have known it sometime around middle of MARCH ). as a heads up, if you are planning on transferring your muse to the modeling OR acting path in the next term/Q2, it’s advised to not participate in this part of the event because they will not be able to do it in Q2.
please fill out the form below and send it to the lgcmanger blog before MARCH 22, 2025 11:59PM EDT if you are interested:
MUSE NAME · TRAINEE SHOWCASE (SPECIAL STAGE) - HARU SONG: ( which of the following HARU songs would your muse be interested in performing: nillili mambo [ originally by block b ], overcome [ originally by nu’est ], OR shangri-la [ originally by vixx ]. you can only pick one song! )
WRITING CHALLENGE
since all of the trainees will be spending more time on workshops during these few months, that means that the writing challenge will be happening instead to encourage character development and continue any past threads you may have! unlike the previous iterations of the writing challenge, there are some slight modifications with this one. here’s a reminder of the basic rules: any thread replies ( with a minimum of 8 lines ) written between TODAY until MARCH 22, 2025 11:59PM EDT will be counted. text threads will not count for this challenge unless the post includes a paragraph of at least 8 lines. as for starters, you can only write a maximum of TWO for this to count.
for this time around, the scores will determine how many points you will be getting for THREE skills that are decided by the admins ( in this case, it will be LANGUAGE and PERFORMANCE [singing/dancing/rapping/performance] SKILLS ). in addition to that, EVERY TWO posts are only counted in the scores. this means that if you so happen to have an odd number of posts ( say 31 ), it will be rounded down to an even number ( in this example, 30 ) of posts total.
if you are interested in doing this, please tag all of the posts as lgc:wc005 and you have until MARCH 22, 2025 11:59PM EDT to participate and submit your posts for this event. when you’re done, please submit the form below to the lgcpoints blog:
MUSE NAME ∙ WRITING CHALLENGE 005 - POSTS COMPLETED: [ # of posts; do include how many starters were written in case you wrote one ] - POSTS: [ link all of the posts ]
2 notes
·
View notes
Text
The Ultimate Guide to Classic Land Rover Defenders for Sale: What to Look For
If you're a fan of rugged, off-road vehicles, the classic Land Rover Defender is likely at the top of your list. Renowned for its durability and iconic design, the Defender has captured the hearts of enthusiasts worldwide. Whether you're in the market for a classic Land Rover Defender as a collector's item or an off-road adventure vehicle, this guide will help you navigate the process of buying one. Here’s what you need to know to ensure you find the best classic Defender for sale.

Understanding the Classic Land Rover Defender
Before diving into the specifics of what to look for, it’s essential to understand the classic Land Rover Defender’s legacy. Produced between 1983 and 2016, the Defender is celebrated for its robust construction and versatility. The classic models, especially those from the 1980s and 1990s, are highly sought after due to their vintage charm and less complex technology compared to modern vehicles.
1. Check the Vehicle’s History
One of the first things to do when considering a classic Land Rover Defender is to check its history. Request a comprehensive service history report to ensure the vehicle has been well-maintained. Look for any records of significant repairs or restorations, as these can impact the vehicle's value and reliability. If possible, obtain a Carfax or similar report to verify mileage and ownership history.
2. Inspect the Bodywork and Chassis
The Defender’s body and chassis are critical to its durability and performance. Classic Land Rover Defenders are prone to rust, especially in areas like the bulkhead, chassis rails, and wheel arches. Examine the vehicle thoroughly for any signs of corrosion or repair. Pay close attention to the condition of the frame; a rusted or damaged chassis can be expensive to repair and affect the vehicle’s overall safety.
3. Evaluate the Engine and Transmission
The engine is the heart of any vehicle, and classic Land Rover Defenders are no exception. Most classic models come with a 2.5-liter diesel engine, though variations exist. Start by assessing the engine’s performance—listen for unusual noises and check for leaks or smoke. Ensure the engine runs smoothly and responds well to acceleration.
The transmission should also be in good working condition. Test the gear changes to ensure they are smooth and free from grinding. Manual transmissions are standard in classic Defenders, so make sure the clutch operates correctly and the gearbox is responsive.
4. Examine the Interior Condition
The interior of a classic Land Rover Defender should reflect its overall care. Inspect the seats, dashboard, and controls for signs of wear and tear. Look for any modifications or aftermarket parts that may affect the vehicle’s originality and value. A well-preserved interior not only enhances comfort but also maintains the vehicle’s classic appeal.
5. Check for Authenticity and Modifications
Authenticity is crucial for classic Land Rover Defenders. Ensure that the vehicle retains its original parts and configurations, as significant modifications can impact its value. While some modifications, such as upgraded suspension or modern electronics, can enhance performance, they should be documented and preferably reversible. If the Defender has been extensively modified, ensure these changes align with your needs and preferences.
6. Review the Vehicle’s Documentation
Documentation is key when buying classic Land Rover Defenders for sale. Verify that the vehicle has a clean title and that all paperwork is in order. This includes registration, insurance, and any historical documentation of past ownership or significant work done. A well-documented vehicle provides peace of mind and facilitates a smoother transaction.
7. Assess the Price and Market Trends
Pricing for classic Land Rover Defenders can vary widely based on factors such as model year, condition, and rarity. Research current market trends to ensure you are paying a fair price. Compare prices of similar models and consider factors like mileage, condition, and originality. Keep in mind that while some Defenders may come with a premium price tag, their value often appreciates over time.
8. Consider a Professional Inspection
Given the complexity and potential hidden issues with classic vehicles, it’s wise to invest in a professional inspection. A qualified mechanic or classic car specialist can provide a detailed assessment of the Defender’s condition, identifying any issues that may not be immediately visible. This step can save you from costly repairs and provide additional negotiation leverage.
9. Test Drive the Vehicle
A test drive is essential to understanding how a classic Land Rover Defender performs on the road. Pay attention to the vehicle’s handling, braking, and overall driving experience. Test it under various conditions to gauge its reliability and ensure it meets your expectations. A well-performing Defender should offer a smooth and responsive drive.
10. Join Land Rover Enthusiast Communities
Connecting with Land Rover enthusiast communities can provide valuable insights and recommendations. Online forums, social media groups, and local clubs can offer advice on reputable sellers and help you find well-maintained classic Defenders. Engaging with fellow enthusiasts can also offer support and enhance your buying experience.
Conclusion: Buying classic Land Rover Defenders for sale is an exciting journey that requires careful consideration and due diligence. By following these guidelines, you can ensure you find a well-maintained, authentic, and reliable Defender that suits your needs. Whether you’re drawn to its rugged charm or its off-road capabilities, a classic Land Rover Defender is a timeless investment that can provide years of driving pleasure. Happy hunting!
Also Read = Top 10 Custom Land Rover Defender Modifications: Enhancing Your Off-Road Experience
2 notes
·
View notes
Text
Overcoming Challenges in Data Integration: Insights from Consulting Experts
Data integration for enterprises can take longer due to technological, financial, and time constraints. As a result, modifying data strategies to mitigate risks like incompatibility between many tools or budget overruns is crucial. Companies must also prepare for new compliance requirements to ensure ethical data operations. This post will explore such challenges in data integration while listing valuable insights from consulting experts in this domain.
What is Data Integration?
Data integration merges data from disparate origins and presents it to maximize comprehension, consolidation, and summarization effectiveness. Integrated data views rely on data ingestion, preparation, and advanced insight extraction. It also streamlines the data operations services across regulatory report creation, helpdesks, and 360-degree client life cycle management.
All data integration strategies involve the extract, transform, and load (ETL) pipelines regardless of business units or target industries. At the same time, the scope of planning and quality assurance in each process varies due to domain-specific data classification factors.
For instance, the accounting departments must handle extensive numerical data while interpreting legal and organizational requirements for transparency. On the other hand, production engineering and design professionals will use visualizations to improve goods or service packages. Accordingly, accountants will use unique tools distinct from engineers’ software.
Later, the leaders might want a comprehensive overview of the synergy between these departments. Therefore, they must determine efficient data integration strategies. The data will move between several programs, carrying forward many updates throughout a project’s progression based on those roadmaps.
Overcoming the Challenges in Data Integration Using Insights from Consulting Experts
1| Data Quality Hurdles
Linking, consolidating, and updating data from several sources will exponentially increase the quality-related threats. For instance, consider multimedia assets from social networks or unreliable news outlets. They can help your secondary market research and social listening initiatives. However, you want to verify the authenticity of gathered intelligence to avoid inaccurate data ingestion.
Evaluating relevance, freshness, and consistency is essential to data quality assurance from creation to archival. So, corporations have started leveraging data lifecycle management to boost dataset integrity, helping make integration less of a hassle.
Insights:
Most consulting experts suggest developing ecosystems that check and recheck quality metrics at each stage of a data integration lifecycle. Moreover, they recommend maintaining periodic data backups with robust version control mechanisms. Doing so will help quality preservation efforts if errors arise after a feature update or a malicious third party is likely to break the system using malware.
2| Networking and Computing Infrastructure Problems
Legacy hardware and software often introduce bottlenecks, hurting data integration’s efficiency. Modern integration strategies demand more capable IT infrastructure due to the breakthroughs like the internet of things (IoT), 5G networks, big data, and large language models. If a company fails to procure the necessary resources, it must postpone data integration.
Technologies integral to capturing, storing, checking, sorting, transferring, and encrypting data imply significant electricity consumption. Besides, a stable networking environment with adequate governance implementations enables secure data transactions. The underlying computing infrastructure is not immune to physical damage or downtime risks due to maintenance mishaps.
What Consulting Experts Say:
Enterprises must invest in reliable, scalable, and efficient hardware-software infrastructure. This will benefit them by providing a stable working environment and allowing employees to witness productivity improvements. Upgrading IT systems will also enhance cybersecurity, lowering the risk of zero-day vulnerabilities.
3| Data Availability Delays
Governments, global firms, educational institutions, hospitals, and import-export organizations have a vast network of regional offices. These offices must also interact with suppliers, contractors, and customers. Due to the scale of stakeholder engagement, reports concerning office-level performance and inventory might arrive late.
Underproductive employees, tech troubleshooting, slow internet connectivity, and a poor data compression ratio will make data sourcing, updating, and analyzing inefficient. As a result, a data integration officer must address time-consuming activities through strategic resource allocation. If left unaddressed, delays in data delivery will adversely affect conflict resolution and customer service.
Expert Insights:
Train your employees to maximize their potential and reduce data acquisition, categorization, and transformation delays. Additionally, you will want to embrace automation through artificial intelligence (AI) applications. Find methods to increase the data compression ratio and accelerate encryption-decryption processing cycles. These measures will help accomplish near-real-time data integration objectives.
4| Vendor Lock-ins
A vendor lock-in results from inconvenience and restrictions when a client wants to switch to another service provider or toolkit. Although data integration platforms claim they celebrate the ease of migrating databases with competitors, they might covertly create vendor lock-ins.
For instance, some data sourcing and sorting ecosystems might limit the supported formats for bulk export commands. Others will use misleading methods to design the graphical user interface (GUI) of account deletion and data export features. They involve too many alerts or generate corrupt export files.
Practical Insights:
Combining multiple proprietary and open-source software tools offers the best cost optimization opportunities. When you select a data vendor, audit the tools the willing data integration providers use to deliver their assistance. Do they use a completely proprietary system based on an unknown file format unsupported by other platforms?
Finally, you must check all the data import, export, and bulk transfer options in vendors’ documentation. After you check a data firm’s current client base, track its online ratings and scan for red flags indicating potential vendor lock-ins.
5| Data-Related Ethical and Legal Liabilities
Confidentiality of investor communication and stakeholders’ privacy rights are two components of legal risk exposure due to enterprise data integration. Additionally, brands must interpret industry guidelines and regional directives for regulatory disclosures.
They must comply with laws concerning personally identifiable information (PII) about employees and customers. Otherwise, they will attract policymakers’ ire, and customers will lose faith in brands that do not comply with the laws of their countries.
Insights:
Consulting experts recommend collaborating with regional legal teams and global governance compliance specialists. After all, mitigating legal risks can help increase business resilience.
Improved compliance ratings have also benefited several brands wanting to be attractive to impact investors. Meanwhile, customers demanding ethical data operations at business establishments love supporting brands with an exceptional governance culture.
Conclusion
Most brands need specialists' help to develop consolidated data views during reporting because they have flawed data integration strategies. So, they require trustworthy insights from reputed consulting experts with a proven track record of overcoming challenges in data integration. The selected data partners must excel at ETL implementation, governance compliance, and data quality management (DQM).
The corporate world champions data-centric business development. Understandably, the need for scalable data integration reflects the increased stakeholder awareness regarding the importance of connecting disparate data sources. With transparent, fast, and accurate data, organizations will enhance their competitive edge amid this intense digital transformation race.
3 notes
·
View notes
Text
sap migration
Overview of SAP migration and its importance
SAP migration is the process of moving all or part of a company's SAP system from one environment to another. This can involve transferring data, applications, and configurations to a new hardware infrastructure or transitioning the system from an on-premises installation to the cloud. The importance of SAP migration cannot be overstated, as it enables organizations to take advantage of new technologies, improve efficiency, and reduce costs.
One key benefit of SAP migration is the ability to leverage updated features and functionalities offered by newer versions of SAP software. As technology advances at a rapid pace, it is crucial for businesses to stay current in order to remain competitive. By migrating their SAP systems, companies can adopt new modules and tools that empower them with improved analytics capabilities, mobile functionality, and integration with other business applications.
Another significant advantage of SAP migration lies in its potential cost savings. Legacy systems require ongoing maintenance and support which incur high expenses over time. Migrating these systems onto modern platforms allows businesses to streamline processes and optimize resource utilization. Moreover, cloud-based migrations provide opportunities for pay-as-you-go models that eliminate upfront capital investments.
What is SAP migration?
SAP migration refers to the process of moving or transitioning data, applications, and other resources from one SAP system to another. As businesses grow and evolve, they may need to upgrade their existing SAP systems to newer versions or migrate their on-premise SAP solutions to cloud-based platforms. The goal of SAP migration is to ensure a seamless transfer of data and functionalities while minimizing disruption to business operations.

One key aspect of SAP migration is the careful planning and preparation required before the actual transition takes place. This includes assessing the existing infrastructure, identifying dependencies, and designing a roadmap for the migration process. It is crucial for businesses to understand that successful SAP migration goes beyond simply transferring data; it involves optimizing processes, mitigating risks, and ensuring compatibility with other systems within the organization.
Another factor worth considering in SAP migration is choosing the right approach. There are various methodologies like greenfield, brownfield, or selective data transition that can be employed based on specific business requirements. Each approach offers unique benefits and challenges that should be evaluated beforehand. Ultimately, embracing modern technologies through effective SAP migration enables organizations to streamline their operations, improve efficiency, increase scalability, and gain a competitive edge in today's fast-paced business landscape
Reasons for SAP migration
Reasons for SAP migration are diverse and varied, but they all share a common goal: to enhance business efficiency and competitiveness. One major driver is the need for modernization. Many organizations still run on outdated legacy systems that struggle to keep up with the pace of technological advances. By migrating to SAP, businesses gain access to state-of-the-art software and tools that can streamline processes, automate tasks, and improve overall productivity.
Another compelling reason for SAP migration is the desire for integration. In today's interconnected world, siloed systems are simply not sufficient to meet the demands of complex business operations. SAP offers a comprehensive suite of applications that seamlessly integrate with each other as well as with third-party systems. This enables companies to consolidate their IT landscape, eliminate data inconsistencies, and enable real-time visibility into key business metrics across departments.
Additionally, cost savings play a significant role in driving organizations towards SAP migration. As businesses grow and scale, so do their IT needs. Maintaining multiple custom-built systems or disparate software solutions can be an expensive endeavor with high maintenance costs and licensing fees. By consolidating everything under one SAP umbrella, companies can achieve economies of scale while benefiting from regular updates and support from a single vendor.
Steps involved in SAP migration process
The process of SAP migration is a complex and critical task that requires careful planning and execution. The first step in this process is to conduct a thorough assessment of the existing system, including hardware, software, and data. This will help identify any gaps or issues that need to be addressed during the migration.
Once the assessment is complete, the next step involves creating a detailed migration plan. This plan should outline the sequence of tasks, resources required, and estimated timelines for each stage of the migration. It is important to involve key stakeholders from various departments to ensure smooth coordination and communication throughout the process.

After finalizing the plan, it's time to prepare the new environment for SAP migration. This includes setting up hardware infrastructure, installing necessary software components, and configuring network connections. Data cleansing and transformation are also essential steps at this stage to ensure that only relevant data is migrated to avoid cluttering or overburdening the new system.
Best practices for successful SAP migration
1. Understanding the Complexity: One of the key best practices for a successful SAP migration is to thoroughly understand the complexity of the task at hand. Migrating an entire system can be a daunting process, and it's important to approach it with a clear plan and realistic expectations. This includes conducting a thorough audit of your current system, understanding its strengths and limitations, and identifying any potential challenges that may arise during migration.
2. Building a Comprehensive Timeline: Another crucial aspect of successful SAP migration is creating a comprehensive timeline that outlines all necessary tasks and milestones. This ensures that everyone involved in the process has a clear understanding of their responsibilities and deadlines. It's important to factor in ample time for testing, troubleshooting, and training to minimize disruptions once the migration is complete.
3. Prioritizing Data Security: Data security should always be top priority when migrating an SAP system. Implementing stringent security measures throughout the entire migration process is vital to ensure that sensitive data remains confidential and protected from external threats. Additionally, having backup systems in place can help mitigate any potential loss or damage during the transition period.
By following these best practices, organizations can maximize their chances of executing a successful SAP migration while minimizing risks associated with data loss, downtime, or other unforeseen issues. With careful planning, adequate resources, and strong collaboration between all stakeholders involved, businesses can seamlessly transition to their new SAP environment without significant disruptions to daily operations.
Conclusion: Importance of proper planning and execution
Proper planning and execution are crucial elements for success in any endeavor. Whether you are running a business or embarking on a personal project, having a well-thought-out plan and executing it efficiently can make all the difference. SKYPER BUSINESS SOLution recognizes the significance of these two aspects and offers comprehensive tools to streamline your planning and execution processes.

One of the key reasons why proper planning is important is that it allows you to set clear goals and objectives. When you have a concrete plan in place, you can prioritize tasks, allocate resources effectively, and stay focused on what needs to be achieved. SKYPER BUSSINESS SOLution provides innovative features that enable users to create detailed action plans with specific milestones and deadlines, ensuring accountability throughout the process.
Furthermore, effective execution is equally essential for turning your plans into reality. Without efficient implementation, even the most well-crafted plan can fall flat. With SKYPER BUSSINESS SOLutions user-friendly interface and advanced tracking capabilities, you can monitor progress in real-time, identify potential bottlenecks early on, and make necessary adjustments swiftly. This level of visibility not only enhances productivity but also helps maintain motivation among team members by showcasing their accomplishments along the way.
2 notes
·
View notes
Text
Haldiram Franchise: A Tasty Venture into the Food Industry
Are you a food enthusiast with dreams of owning a business that brings joy through delectable treats? Your dream can come true with the Haldiram franchise! Immerse yourself in a world of mouthwatering Indian snacks and sweets, and embark on a delicious venture that promises both satisfaction and success.

Why Choose the Haldiram Franchise?
Indulge in the legacy of Haldiram, renowned for its mouthwatering delicacies loved by all. Embark on your culinary venture with confidence:
Strong Brand Identity: Haldiram's reputation for scrumptious delights is a solid foundation for your franchise journey, making it easier to establish and operate.
Varied Product Range: From traditional Indian sweets to contemporary snacks, Haldiram offers a diverse menu that appeals to a wide audience, ensuring a steady flow of customers.
Proven Success: Benefit from a well-established business model that has flourished over time, reducing the risks associated with starting from scratch.
Effective Marketing: Leverage the power of national and regional marketing campaigns, enhancing brand visibility and attracting patrons to your franchise.
Comprehensive Support: Equip yourself with the essential skills and knowledge through comprehensive training and continuous support from Haldiram.
Steps to Join the Haldiram Family
Initial Exploration: Delve into Haldiram's brand, history, and franchise offerings through their website or direct communication.
Get in Touch: Reach out to Haldiram's franchise department, expressing your interest and seeking detailed insights.
Submit Application: Complete the franchise application form meticulously and submit it for assessment.
Evaluation and Interaction: Haldiram's experts will review your application, considering your alignment with their brand and your experience.
Agreement Stage: Engage in thorough discussions about terms, costs, and commitments, ensuring mutual understanding and satisfaction.
Comprehensive Training: Dive into an immersive training program covering various aspects of operating a successful Haldiram franchise.
Grand Opening: With preparation and training behind you, celebrate a successful grand opening with guidance and assistance from the Haldiram team.
Conclusion
The Haldiram franchise isn't just a business venture; it's an opportunity to be part of a flavorful legacy. With a reputable brand identity, a diverse range of offerings, and unwavering support, your journey in the culinary world is poised for triumph. Embrace the outlined steps as your roadmap to a fulfilling and exciting chapter as a Haldiram franchisee. Embark on this delectable adventure, and let the aroma of culinary success blend seamlessly with your journey!
3 notes
·
View notes
Text
How Generative AI Voice Bot Technology Is Replacing Traditional Call Centers with Instant, Scalable Automation
Call centers have long been the backbone of customer service operations. Whether resolving billing issues, answering product queries, or providing technical support, they’ve enabled businesses to maintain vital connections with their customers. However, this model is increasingly being challenged by the rise of Generative AI Voice Bot technology—a revolution that’s not just tweaking how support is delivered, but replacing the traditional call center altogether.
With natural-sounding speech, real-time reasoning, multilingual capabilities, and round-the-clock availability, Generative AI voice bots are becoming the new front line of communication. They offer instant, scalable, and cost-efficient automation, reshaping customer interactions while reducing operational friction.
This blog dives deep into how this shift is happening, the key drivers behind it, and what it means for the future of customer support.

The Pain Points of Traditional Call Centers
Before understanding the replacement, it’s essential to evaluate why the traditional model is failing in today’s fast-paced digital environment.
High Operational Costs: Maintaining physical infrastructure, hiring and training agents, and managing human resource turnover make call centers expensive.
Limited Scalability: Adding capacity often requires more hiring, equipment, and resources, making it hard to scale during seasonal peaks or emergencies.
Inconsistent Quality: Human agents vary in knowledge, tone, and efficiency, leading to uneven customer experiences.
Long Wait Times: Customers frequently endure long queues, leading to frustration and decreased satisfaction.
Time-Zone and Language Barriers: Global operations require agents in multiple geographies, which increases complexity and costs.
These limitations have created the perfect storm for a digital disruption—and Generative AI Voice Bot technology is leading the charge.
What Is Generative AI Voice Bot Technology?
Generative AI Voice Bots go beyond rule-based voice assistants. Powered by large language models (LLMs) and natural language processing (NLP), these bots can:
Understand customer intent in real time
Respond with human-like fluency
Handle complex, multi-turn conversations
Learn and adapt from previous interactions
Integrate with backend systems for dynamic query resolution
Unlike traditional IVR (Interactive Voice Response) systems, which rely on rigid menu trees and keyword triggers, Generative AI bots create natural, unscripted dialogues, much like a human would.
Key Features Powering the Shift
1. Instant Availability
AI voice bots operate 24/7, delivering immediate responses without wait times. This always-on capability is a game-changer, especially for global brands catering to customers across different time zones.
2. Cost Reduction at Scale
By automating a significant portion of calls—often up to 70-80%—companies can drastically cut labor, training, and infrastructure costs. For high-volume call centers, this can result in millions in annual savings.
3. Human-like Conversations
Thanks to LLMs like GPT, Claude, or Gemini, these bots can process nuances, detect emotions, and reply with empathy. Customers often can’t tell they’re speaking to a bot.
4. Multilingual Support
With built-in translation and multilingual training, AI voice bots can serve a global audience without hiring native speakers for every market.
5. Rapid Deployment and Updates
Unlike legacy systems that require extensive reprogramming, Generative AI bots can be updated almost instantly. This makes it easier to launch new features or respond to changing customer needs.
Industries Already Making the Shift
Several sectors have already begun replacing their call center operations with generative voice bots:
1. Telecommunications
Companies like Vodafone and Verizon use AI voice bots to handle billing queries, SIM activation, and basic troubleshooting, freeing up agents for high-level issues.
2. Banking and Financial Services
Banks like HSBC and Capital One use voice AI to authenticate users, provide balance information, and help with fraud detection.
3. Retail and E-commerce
Retailers automate order tracking, returns, and product recommendations with voice bots, enhancing the customer experience and cutting down on human-agent dependency.
4. Healthcare
Hospitals and clinics use AI voice assistants for appointment booking, prescription reminders, and patient follow-ups, ensuring patient engagement without human intervention.
Case Study: The Impact in Numbers
Company: A global consumer electronics brand Challenge: 15 million support calls annually, with high wait times and support costs Solution: Deployed a Generative AI Voice Bot across English and Spanish markets Results:
80% of tier-1 support calls resolved without human agent
40% reduction in overall call center cost
30-second average reduction in call handling time
25% improvement in CSAT (Customer Satisfaction Score)
This level of ROI is not rare. Most organizations that implement AI voice bots correctly report measurable improvements within the first quarter.
Reimagining the Customer Experience
The true power of Generative AI isn’t just cost savings—it’s experience transformation. Customers are no longer frustrated by robotic menus or long queues. They get quick, intelligent answers, personalized recommendations, and empathetic interactions.
Here’s what the modern AI-powered customer journey looks like:
Step 1: Customer calls support line.
Step 2: Voice bot greets with a warm, natural tone.
Step 3: Bot identifies intent (“I want to cancel my subscription”) and confirms.
Step 4: Bot accesses backend CRM, processes request, and offers retention incentives.
Step 5: Bot confirms cancellation and sends a follow-up SMS with details.
All this—without a human ever getting involved.
Addressing the Challenges
While the advantages are clear, adoption comes with hurdles:
1. Data Privacy & Compliance
AI voice systems must adhere to regulations like GDPR, HIPAA, and PCI-DSS. Vendors must ensure secure data storage, encryption, and consent-based interactions.
2. Accent & Dialect Recognition
Training models for diverse accents is crucial. Modern voice bots are getting better at this with continuous learning and regional voice data integration.
3. Customer Trust
Some customers still prefer human interaction. Hybrid models—where AI bots handle the bulk and escalate complex issues—are a popular transition strategy.
4. Integration with Legacy Systems
Many businesses still use outdated CRM or ERP systems. Bridging this gap with middleware and APIs is often necessary.
The Future of Customer Support Is AI-Driven
The writing is on the wall. Traditional call centers, once the cornerstone of enterprise support, are gradually being phased out in favor of AI-powered voice automation. With Generative AI Voice Bots, companies not only automate at scale but also deliver smarter, faster, and more human-like support.
In the next 3–5 years, we’ll likely see:
90%+ of first-contact support handled by AI voice bots
Full integration with predictive analytics to anticipate customer issues before they arise
Sentiment-driven conversation routing (e.g., escalating angry customers directly to a supervisor)
Voice bots embedded into wearables and smart home devices, expanding the customer touchpoints beyond phones
Conclusion: A Generative AI Voice Bot Future
As customer expectations evolve, brands can no longer afford outdated support systems. Traditional call centers, constrained by labor costs, slow response times, and operational complexity, are being replaced by AI-driven alternatives that are instant, scalable, and intelligent.
By embracing Generative AI Voice Bot technology, companies unlock unprecedented potential—not only in cost savings but also in delivering exceptional customer experiences that build trust, loyalty, and long-term brand value.
Now is the time for enterprises to act. The future of customer engagement isn’t waiting on hold—it’s already talking to an AI voice bot that’s always available, always learning, and always improving.
0 notes
Text
Cybersecurity Consultant Tips Every Business Owner Should Implement Today
In today’s fast-evolving digital landscape, cybersecurity is not just an IT concern—it’s a business survival strategy. Whether you're a startup, an e-commerce platform, or a service-based company, securing your digital assets is non-negotiable. A cybersecurity consultant plays a vital role in identifying vulnerabilities, developing defense strategies, and training teams to prevent security breaches.
Conduct a Comprehensive Risk Assessment
One of the first and most crucial tips any cybersecurity consultant will offer is to begin with a thorough risk assessment. This process identifies your company's most vulnerable areas—whether it’s outdated software, weak passwords, or unsecured cloud storage.
A cybersecurity consultant will typically evaluate:
Internal and external network vulnerabilities
Access controls and user privilege management
Data encryption practices
Backup and recovery strategies
Implement a Zero-Trust Security Model
Traditional perimeter-based security models are no longer enough. A cybersecurity consultant will likely recommend a Zero Trust Model, where no one—inside or outside the network—is automatically trusted.
This means:
Multi-factor authentication (MFA) for all users
Strict access control policies
Continuous verification and monitoring
Least-privilege access enforcement
Train Employees on Cyber Hygiene Practices
Human error is one of the biggest causes of data breaches. That’s why cybersecurity consultants emphasize employee training as a core security measure. Even the most advanced firewall won’t help if a staff member clicks on a phishing link.
Cybersecurity training should include:
Recognizing phishing attempts
Safe password creation and management
Secure file sharing practices
Reporting suspicious activity promptly
Monitor Systems Continuously and Set Alerts
A cybersecurity consultant understands that real-time monitoring is essential to detect and respond to suspicious activity before it escalates. This includes:
Network traffic analysis
Endpoint monitoring
Unauthorized access alerts
Suspicious login location detection
Backup Your Data with a Secure Disaster Recovery Plan
Cyberattacks like ransomware are increasingly common, and without backups, your business could face devastating losses. A cybersecurity consultant will ensure that you not only back up your data but also test your disaster recovery plan regularly.
Key backup practices include:
Automating regular backups
Storing backups in a secure, offsite or cloud-based location
Encrypting backup files
Testing recovery procedures to ensure quick restoration
Keep Software and Systems Regularly Updated
Outdated software and operating systems are open invitations for cybercriminals. A trusted cybersecurity consultant will urge businesses to maintain a strict update and patching schedule for all devices, servers, and applications.
Recommendations include:
Enabling automatic updates wherever possible
Replacing unsupported or legacy systems
Applying patches to plugins, web applications, and CMS platforms
Monitoring vendor notifications for urgent security updates
Use Encryption and Secure Communication Channels
Whether it’s internal communication or customer data transmission, encryption adds a strong layer of protection. A cybersecurity consultant advises encrypting:
Email content and attachments
Customer data in transit and at rest
Internal file transfers and document sharing
Wi-Fi networks and VPN traffic
Conclusion
Cybersecurity is not a one-time fix—it’s an ongoing commitment. The guidance of a cybersecurity consultant enables business owners to take a proactive approach rather than waiting for a cyberattack to happen. From building strong digital defenses and training staff to deploying real-time monitoring and having recovery plans, every tip discussed here can protect your business’s future. With threats evolving daily, investing in professional cybersecurity consulting can save you from financial loss, reputational damage, and legal liabilities. If you're ready to strengthen your cyber defense strategy, connect with a trusted cybersecurity consultant and start implementing these tips today.
0 notes
Text
Sam Altman Warns of AI Voice Fraud Crisis in Banking

OpenAI CEO Sam Altman has issued a stark warning to the global financial sector, calling out the growing threat of AI-powered voice fraud that can bypass traditional security systems. Speaking at a Federal Reserve conference in Washington, Altman described the current reliance on voiceprint authentication as “crazy” in today’s AI landscape.
“AI has fully defeated that,” Altman said, referring to voice-based verification systems still used by some banks to authenticate users.
Originally introduced over a decade ago, voiceprint technology became popular among banks, especially for high-net-worth clients. Customers would recite a specific phrase to gain access to their accounts. But with the advancement of AI voice cloning, these systems are now highly vulnerable.
Altman warned that AI tools can now mimic voices—and soon, even video personas—with near-perfect accuracy, making fraud "indistinguishable from reality." The implications for identity theft and financial crime are serious, and Altman urged institutions to rethink verification methods urgently.
Michelle Bowman, Vice Chair for Supervision at the Fed and host of the session, responded positively, saying the issue could be an area for collaborative policy efforts.
Altman’s comments come amid a growing chorus of tech and financial leaders urging updated regulation and multi-factor identity protections in response to generative AI's rapid evolution.
Altman’s remarks have resonated deeply across the banking and cybersecurity communities, as AI-generated voice clones are now capable of replicating subtle human traits—tone, rhythm, and accent—well enough to fool both humans and automated systems.
He emphasized that fraud prevention models must now evolve, warning that “we’re entering a phase where traditional biometrics like voice or even video can no longer be trusted as sole identifiers.” Altman urged the industry to invest in multi-factor authentication and AI-resistant verification systems, such as cryptographic keys, behavioral biometrics, and secure tokens.
Bowman, responding to the concerns, added:
“Financial institutions can no longer afford to depend on legacy identity tools. We’re open to public-private partnerships to ensure robust protection against next-gen fraud.”
Rising Incidents Globally: Recent cases have already proven Altman’s warning to be more than theoretical. In several countries, AI-cloned voices have been used to trick customer service agents into granting account access or authorizing transactions, leading to millions in fraud losses.
What Comes Next?
Banks are re-evaluating authentication practices amid pressure from regulators and security experts.
Consumer awareness campaigns are being planned to educate the public about social engineering and AI scams.
The Federal Reserve is expected to draft new guidance on voice biometrics in collaboration with AI experts and cybersecurity firms.
Altman concluded his address with a strong message:
“The tools we build are incredibly powerful. But without safeguards, they can be misused. It’s on all of us—builders, regulators, and institutions—to act now.”
The financial world is now on high alert, with many institutions moving quickly to phase out outdated voiceprint authentication and replace it with AI-resilient security infrastructure.
1 note
·
View note
Text
Digital Maturity Acceleration Plan: Step-by-Step for 2025
In 2025, organizations are under intense pressure to evolve digitally. The speed at which businesses must adapt to technology is no longer gradual it’s exponential. Companies must now evaluate and improve their digital maturity to stay competitive in the global marketplace. But what exactly does it mean to be digitally mature? And how can a business systematically reach that level?
This step-by-step guide offers a strategic approach for any organization ready to enhance its digital capabilities and scale transformation effectively in 2025.

Understanding Digital Maturity in 2025
Digital maturity refers to how well an organization uses digital technologies to improve performance. It’s not just about adopting tools like AI or cloud computing; it’s about integrating them into workflows, culture, leadership, and customer experiences.
In 2025, digital maturity has evolved beyond basic IT transformation. It includes:
Predictive analytics integration
AI-driven decision-making
Cross-platform digital operations
Real-time data collaboration
Agile organizational structure
Step 1: Assess Your Current Digital Maturity
The first step is to measure where your organization stands today. Conduct an internal digital audit across departments, systems, and strategies. Evaluate your strengths and gaps in areas like:
Digital tools and automation
Employee digital skills
IT infrastructure scalability
Cybersecurity framework
Data intelligence and customer engagement
Tools like digital maturity models and benchmarks can help you understand your current stage and what’s needed to progress.
Step 2: Define a Clear Digital Vision
Without a unified vision, digital initiatives often fail. Define what digital maturity looks like for your organization. Is it faster service delivery? A data-driven culture? Enhanced customer personalization?
Involve cross-functional leadership to build this vision and set measurable goals aligned with business outcomes. A mature digital enterprise must prioritize continuous innovation, not just digitization.
Step 3: Build a Roadmap for Transformation
Once your vision is clear, create a step-by-step roadmap to reach it. This roadmap should outline short-term wins and long-term transformations. Typical phases include:
Legacy system modernization
Cloud adoption
Employee reskilling
AI and machine learning implementation
CX and UX upgrades
Ensure that each initiative supports progress toward digital maturity and allows agility for real-time course correction.
Step 4: Upgrade Your Tech Stack Strategically
Throwing money at new tools doesn’t guarantee results. Technology investments must align with your roadmap and vision. Prioritize solutions that scale with you and integrate easily across departments.
In 2025, top tools that enhance digital maturity include:
Enterprise AI platforms
Predictive CRM solutions
Automation and RPA software
Data lakes and advanced analytics
Collaboration and remote work tools
Every tech decision should support your digital foundation while preparing for future disruptions.
Step 5: Foster a Digital-First Culture
Technology is only one part of the puzzle. Culture transformation is often the hardest but most vital aspect of digital maturity. Encourage employees at all levels to embrace innovation, experimentation, and ongoing learning.
Some effective culture-building strategies include:
Internal digital champions
Gamified upskilling programs
Open communication around digital goals
Recognizing innovation from all teams
Employees empowered with digital literacy are more likely to adopt new tools and approaches without resistance.
Step 6: Secure Your Digital Ecosystem
Cybersecurity is non-negotiable in 2025. With increased digitization comes greater vulnerability. Part of your digital maturity roadmap must include securing data, systems, and user access.
This includes:
Implementing zero-trust frameworks
Real-time threat detection tools
Regular risk assessments
Cybersecurity awareness training
A digitally mature organization anticipates and neutralizes cyber threats rather than reacting to them.
Step 7: Measure, Optimize, Repeat
Digital transformation is never really "finished." Businesses must regularly measure key performance indicators (KPIs) related to their digital goals. These could include:
Operational efficiency improvements
Employee adoption rates
Customer satisfaction metrics
Revenue from digital channels
Use data insights to optimize processes, re-align strategies, and improve your organization’s Digital Maturity continuously.
Read Full Article: https://businessinfopro.com/enhancing-digital-maturity-with-a-step-by-step-guide-in-2025/
About Us:
BusinessInfoPro is a dynamic B2B insights hub offering timely, expert‑driven content tailored for professionals in finance, HR, IT, marketing, sales and more. Through in‑depth articles, whitepapers and downloadable guides, we illuminate critical industry trends like AI’s economic impact, data‑driven decision‑making and strategic marketing in uncertain economies. Our resources empower leaders to optimize efficiency, strengthen customer engagement and embrace sustainable innovation. With fresh publications covering cutting‑edge topics sustainability, workforce transformation, real‑time architecture and practical tools from top platforms and thought‑leaders, Business Info Pro equips businesses to adapt, compete and thrive in a fast‑changing global landscape.
0 notes