#password hacker tools
Explore tagged Tumblr posts
Video
youtube
Tech Talk - 10-18-2024
#youtube#AI Cloud Cybersecurity Detection Encryption Hackers Password Protection Technology Tools ZeroTrust
0 notes
Text
A United States Customs and Border Protection request for information this week revealed the agency’s plans to find vendors that can supply face recognition technology for capturing data on everyone entering the US in a vehicle like a car or van, not just the people sitting in the front seat. And a CBP spokesperson later told WIRED that the agency also has plans to expand its real-time face recognition capabilities at the border to detect people exiting the US as well—a focus that may be tied to the Trump administration’s push to get undocumented people to “self-deport” and leave the US.
WIRED also shed light this week on a recent CBP memo that rescinded a number of internal policies designed to protect vulnerable people—including pregnant women, infants, the elderly, and people with serious medical conditions—while in the agency’s custody. Signed by acting commissioner Pete Flores, the order eliminates four Biden-era policies.
Meanwhile, as the ripple effects of “SignalGate” continue, the communication app TeleMessage suspended “all services” pending an investigation after former US national security adviser Mike Waltz inadvertently called attention to the app, which subsequently suffered data breaches in recent days. Analysis of TeleMessage Signal’s source code this week appeared to show that the app sends users’ message logs in plaintext, undermining the security and privacy guarantees the service promised. After data stolen in one of the TeleMessage hacks indicated that CBP agents might be users of the app, CBP confirmed its use to WIRED, saying that the agency has “disabled TeleMessage as a precautionary measure.”
A WIRED investigation found that US director of national intelligence Tulsi Gabbard reused a weak password for years on multiple accounts. And researchers warn that an open source tool known as “easyjson” could be an exposure for the US government and US companies, because it has ties to the Russian social network VK, whose CEO has been sanctioned.
And there's more. Each week, we round up the security and privacy news we didn’t cover in depth ourselves. Click the headlines to read the full stories. And stay safe out there.
ICE’s Deportation Airline Hack Reveals Man “Disappeared” to El Salvador
Hackers this week revealed they had breached GlobalX, one of the airlines that has come to be known as “ICE Air” thanks to its use by the Trump administration to deport hundreds of migrants. The data they leaked from the airline includes detailed flight manifests for those deportation flights—including, in at least one case, the travel records of a man whose own family had considered him “disappeared” by immigration authorities and whose whereabouts the US government had refused to divulge.
On Monday, reporters at 404 Media said that hackers had provided them with a trove of data taken from GlobalX after breaching the company’s network and defacing its website. “Anonymous has decided to enforce the Judge's order since you and your sycophant staff ignore lawful orders that go against your fascist plans,” a message the hackers posted to the site read. That stolen data, it turns out, included detailed passenger lists for GlobalX’s deportation flights—including the flight to El Salvador of Ricardo Prada V��squez, a Venezuelan man whose whereabouts had become a mystery to even his own family as they sought answers from the US government. US authorities had previously declined to tell his family or reporters where he had been sent—only that he had been deported—and his name was even excluded from a list of deportees leaked to CBS News. (The Department of Homeland Security later stated in a post to X that Prada was in El Salvador—but only after a New York Times story about his disappearance.)
The fact that his name was, in fact, included all along on a GlobalX flight manifest highlights just how opaque the Trump administration’s deportation process remains. According to immigrant advocates who spoke with 404 Media, it even raises questions about whether the government itself had deportation records as comprehensive as the airline whose planes it chartered. “There are so many levels at which this concerns me. One is they clearly did not take enough care in this to even make sure they had the right lists of who they were removing, and who they were not sending to a prison that is a black hole in El Salvador,” Michelle Brané, executive director of immigrant rights group Together and Free, told 404 Media. “They weren't even keeping accurate records of who they were sending there.”
The Computer of a DOGE Staffer With Sensitive Access Reportedly Infected With Malware
Elon Musk’s so-called Department of Governmental Efficiency has raised alarms not just due to its often reckless cuts to federal programs, but also the agency’s habit of giving young, inexperienced staffers with questionable vetting access to highly sensitive systems. Now security researcher Micah Lee has found that Kyle Schutt, a DOGE staffer who reportedly accessed the financial system of the Federal Emergency Management Agency, appears to have had infostealer malware on one of his computers. Lee discovered that four dumps of user data stolen by that kind of password-stealing malware included Schutt’s passwords and usernames. It’s far from clear when Schutt’s credentials were stolen, for what machine, or whether the malware would have posed any threat to any government agency’s systems, but the incident nonetheless highlights the potential risks posed by DOGE staffers’ unprecedented access.
Grok AI Will “Undress” Women in Public on X
Elon Musk has long marketed his AI tool Grok as a more freewheeling, less restricted alternative to other large language models and AI image generators. Now X users are testing the limits of Grok’s few safeguards by replying to images of women on the platform and asking Grok to “undress” them. While the tool doesn’t allow the generation of nude images, 404 Media and Bellingcat have found that it repeatedly responded to users’ “undress” prompts with pictures of women in lingerie or bikinis, posted publicly to the site. In one case, Grok apologized to a woman who complained about the practice, but the feature has yet to be disabled.
A Hacked School Software Company Paid a Ransom—but Schools Are Still Being Extorted
This week in don’t-trust-ransomware-gangs news: Schools in North Carolina and Canada warned that they’ve received extortion threats from hackers who had obtained students’ personal information. The likely source of that sensitive data? A ransomware breach last December of PowerSchool, one of the world’s biggest education software firms, according to NBC News. PowerSchool paid a ransom at the time, but the data stolen from the company nonetheless appears to be the same info now being used in the current extortion attempts. “We sincerely regret these developments—it pains us that our customers are being threatened and re-victimized by bad actors,” PowerSchool told NBC News in a statement. “As is always the case with these situations, there was a risk that the bad actors would not delete the data they stole, despite assurances and evidence that were provided to us.”
A Notorious Deepfake Porn Site Shuts Down After Its Creator Is Outed
Since its creation in 2018, MrDeepFakes.com grew into perhaps the world’s most infamous repository of nonconsensual pornography created with AI mimicry tools. Now it’s offline after the site’s creator was identified as a Canadian pharmacist in an investigation by CBC, Bellingcat, and the Danish news outlets Politiken and Tjekdet. The site’s pseudonymous administrator, who went by DPFKS on its forums and created at least 150 of its porn videos himself, left a trail of clues in email addresses and passwords found on breached sites that eventually led to the Yelp and Airbnb accounts of Ontario pharmacist David Do. After reporters approached Do with evidence that he was DPFKS, MrDeepFakes.com went offline. “A critical service provider has terminated service permanently. Data loss has made it impossible to continue operation,” reads a message on its homepage. “We will not be relaunching.”
14 notes
·
View notes
Text
I thought I had this mostly handled so I didn't want to post anything but seems the problem has come back and is being super annoying... sigh...
So beginning of the month I was hacked. They posed as a discord friend and was pretty convincing, tricked me into downloading a 'game' they made and it turned out to be a hacking tool. So they got my main email and just started taking EVERYTHING connected to it. Discord, other email account, xbox account, etc. But it was also connected to my firefox account and so they had access to all my passwords.. ugh..
I've been sick most of this month and stressed from it. Spent two weeks waiting on something from microsoft before giving up and just trying to contact them directly, like... a person and not the stupid 'self-helper' tool that couldn't do squat cuz the hacker added an authenticater to my account and the tool was like 'can't help you bro'.
Thankfully I have some superb friends on my discord, made an alt account to stay in contact otherwise I'd still be a crying mess, but they were able to get a support agent for me. They've emailed me about looking into my email being hacked, no eta yet but they're looking into it. Which is great.. Until today...
I thought the hacker was done, moved on but nope... Get a text in Turkish this morning about my Twitch code and... now my Twitch is gone, they're on my instagram talking to my friends to get in contact with me and they locked my steam account..
This FUCKER.
Like wtf!? Leave me alone, you took my email.. I'm getting it back and NO I'm not paying you to get it back you slimy scumbag.
So far the friend they contacted on instagram contacted me, said it was super sus and it really was with the messages they sent me so they trolled them a bit. Another friend made a fake discord account posing as me to talk to them and learned that this idiot can't get back onto my main discord account cuz the 2fa is on, HAH. Friend also said they sound young and frustrated, GOOD! Fuck 'em for being a piece of shit.
But yeah.. Been dealing with this all month and now it's mostly just the waiting game for Microsoft Support to look into it. Same with getting my steam account unlocked so yeah.. This has been my month of fun. Was literally just starting to feel better from this awful almost 4 week sickness and then bam... they're back to bother me.
Least I can give a warning about this new scam but they pose as a discord friend, who is already hacked, ask you to try their game, and send a link that you then download and the download does nothing. It's some kind of hacking tool that gets past everything.. my virus scan didn't even pick it up. Might be too new.
I've never been hacked like this before, but if something seems sus then just turn your computer off or unplug the internet right away. Don't be me panicking while they get away with everything... Then get your computer completely wiped and hope they didn't get into anything important. Be quick on the 'no this wasn't me who did this' sort of thing, could save you the headache down the line.. =3=
6 notes
·
View notes
Text
Astraweb: The Home of Crypto Recovery in the Digital Age

In the ever-evolving world of cryptocurrency, security and access remain critical concerns. For every success story of early adopters turning modest investments into fortunes, there are unfortunate accounts of users losing access to their digital wallets due to forgotten passwords, phishing attacks, or compromised private keys. This is where Astraweb has carved out a vital niche — establishing itself as the go-to solution for crypto asset recovery.
The Need for Crypto Recovery
Cryptocurrency promises decentralized finance and ownership without intermediaries — but this power comes with a cost: total user responsibility. There is no central authority to call when access is lost. Millions of dollars in crypto assets are estimated to be trapped in inaccessible wallets. The stakes are high, and the traditional “write your password down and hope for the best” method has proven tragically inadequate.
Astraweb has stepped in to fill this gap, offering a technically advanced, ethically grounded, and user-focused recovery service for individuals and institutions alike.
Who is Astraweb?
Astraweb is a team of cybersecurity professionals, blockchain analysts, and ethical hackers dedicated to the recovery of lost digital assets. Known in online communities for their discretion and technical excellence, Astraweb has quietly built a reputation as the “home of crypto recovery” — a safe harbor in the sometimes stormy seas of decentralized finance.

Core Services Offered
Wallet Password Recovery Utilizing a combination of brute force optimization, machine learning, and customized dictionary attacks, Astraweb helps users recover wallets with forgotten passwords. Their tools are especially effective with partially remembered credentials.
Seed Phrase Reconstruction Lost or partial seed phrases are another major barrier to wallet access. Astraweb’s proprietary tools attempt to reconstruct valid mnemonic phrases based on user input and probabilistic modeling.
Phishing and Scam Mitigation If your crypto assets have been stolen due to phishing attacks or scams, Astraweb provides investigation support and recovery options. While crypto transactions are irreversible, Astraweb works with partners and tracing tools like Chainalysis to help track and reclaim funds when possible.
Multi-Sig and Legacy Wallet Recovery Many early wallets used now-defunct software or obscure security models. Astraweb specializes in navigating old formats, deprecated standards, and rare cryptographic setups.
Cold Wallet Restoration Lost access to hardware wallets like Trezor, Ledger, or even encrypted USB drives? Astraweb can assist with forensic-level data recovery and hardware-based key extraction.
Why Astraweb Stands Out
Confidentiality First: Every case is handled with strict privacy. Your data and identity are protected at all stages of the recovery process.
Transparent Communication: Clients are updated at every step, with no vague promises or false guarantees.
No Recovery, No Fee: Astraweb operates on a results-based model. You only pay if your assets are successfully recovered.
Client Trust and Track Record
Though much of their work remains confidential due to the sensitive nature of crypto assets, Astraweb’s success stories span from everyday investors to high-net-worth individuals and even businesses affected by inaccessible wallets or theft.
Their community reputation and testimonials underscore one thing: they deliver.
Contact Astraweb
If you’ve lost access to your cryptocurrency wallet, or fallen victim to crypto fraud, don’t give up hope. Reach out to Astraweb for a professional assessment of your situation.
Email: [email protected]
Whether it’s one token or an entire portfolio, Astraweb may be your best shot at recovery.
2 notes
·
View notes
Text
Hacker Attack on Brazilian Government Platform Affects Systems of Nine Ministries and Two Agencies
Staff advised to change passwords; number of such incidents faced by the federal administration doubled in 2024

The Lula administration (PT) suffered a hacker attack that affected the systems of nine ministries and two other federal agencies. Around 9 PM, part of the affected tools was restored. However, there is still no forecast for the full restoration of the systems. Around noon on Wednesday (24th), employees of the affected agencies received an email informing them of a "cyber incident." "Teams are working to ensure that data is intact and secure.
Continue reading.
7 notes
·
View notes
Text
5 Ways to Improve Your Network Security
In today’s digital age, network security is more critical than ever. With cyberattacks becoming more sophisticated and frequent, businesses and individuals alike must take proactive steps to protect their networks. Whether you’re a small business owner or a tech-savvy professional, improving your network security can help safeguard sensitive data, prevent downtime, and maintain trust. Here are five actionable tips to enhance your network’s defenses.
1. Use Strong, Unique Passwords
Weak or reused passwords are among the most common vulnerabilities in network security. To protect your network:
Create strong passwords that include a mix of uppercase and lowercase letters, numbers, and special characters.
Avoid using easily guessed information, such as birthdays or common words like "password123."
Use a password manager to generate and securely store complex passwords for all your accounts.
Implement multi-factor authentication (MFA) for an extra layer of security. MFA requires users to verify their identity through a second method, such as a text message code or biometric scan.
2. Keep Your Software Up-to-Date
Outdated software is a goldmine for hackers who exploit known vulnerabilities. Regular updates ensure you’re protected with the latest security patches.
Update your operating system, applications, and firmware regularly.
Enable automatic updates to ensure critical patches are installed promptly.
Replace unsupported or obsolete hardware and software with newer, more secure alternatives.
3. Secure Your Wi-Fi Network
Your Wi-Fi network is a primary gateway for potential attacks. Securing it is essential:
Change the default administrator username and password for your router.
Use WPA3 encryption (or at least WPA2) to secure your wireless connection.
Hide your network's SSID (Service Set Identifier) so it’s not visible to unauthorized users.
Set up a guest network for visitors, keeping them isolated from your primary network.
4. Install and Update Security Software
Comprehensive security software is your first line of defense against malicious activity.
Use antivirus and anti-malware programs to detect and remove threats.
Install a firewall to monitor and block unauthorized access to your network.
Invest in a Unified Threat Management (UTM) system, which combines multiple security features like intrusion detection, content filtering, and VPN support.
Keep all security software updated to stay protected from the latest threats.
5. Educate and Train Users
Even the most robust security measures can fail if users are unaware of best practices.
Train your team to recognize phishing emails, suspicious links, and social engineering tactics.
Encourage employees to report unusual activity immediately.
Establish a network security policy that outlines acceptable use, password protocols, and steps for reporting incidents.
Conduct regular cybersecurity awareness sessions to keep users informed about emerging threats.
Bonus Tip: Monitor Your Network Activity
Proactively monitoring your network can help you detect potential issues before they become critical. Use tools to track unusual traffic, failed login attempts, and other red flags.
Conclusion
Improving your network security doesn’t have to be overwhelming. By implementing these five steps, you can significantly reduce your risk of cyberattacks and create a safer environment for your business or personal network. Remember, cybersecurity is an ongoing process—stay vigilant, keep learning, and adapt to new threats as they arise.
Have questions or need help securing your network? Contact us today for expert IT solutions tailored to your needs!
4 notes
·
View notes
Text
Lifesaving Tech with Hidden Risks: Medical IoT Devices
Hey, so… what even are Medical IoT Devices?
Okay, let’s start with the basics. Medical IoT (Internet of Things) devices are basically smart gadgets that help doctors and patients manage health in real-time. Think of them as the Fitbits of the medical world, but way more advanced and sometimes implanted inside your body.
Here’s a quick rundown of the most common types:
Wearables: Smartwatches, glucose monitors, patches that track your vitals.
Implantables: Pacemakers, insulin pumps, neurostimulators that keep your heart ticking, your blood sugar in check, your brain functioning properly respectively.
Hospital Gear: Things like infusion pumps, ventilators, or MRI machines that are connected to the hospital’s network.
These devices are amazing because they can send data straight to your doctor, so they can monitor you without you having to camp out in a hospital bed. But (and there’s always a but), this connectivity comes with a price: security risks.
Wait, How Can a Pacemaker Get Hacked?
Okay, so let’s get into the nitty-gritty of how these devices can be exploited. It’s not just about “hackers being hackers”, there are specific technical flaws that make these devices vulnerable.
1. Encryption (or Lack Thereof)
Encryption is like a secret code that scrambles data so only authorized parties can read it. For medical IoT devices, encryption is crucial because they’re transmitting sensitive health data. But here’s the problem: not all devices use strong encryption.
What’s Happening: Some devices send data in plaintext (unencrypted) or use weak encryption algorithms that can be cracked by hackers.
Example: If an insulin pump sends unencrypted data to a doctor’s computer, a hacker could intercept it and alter the dosage instructions, potentially causing harm to the patient.
2. Authentication Protocols
Authentication is how a device verifies that someone (or something) is who they claim to be. Think of it like a password or a fingerprint scan. But many medical IoT devices use weak or default authentication methods.
What’s Happening: Devices might use hardcoded passwords (e.g., “admin” or “1234”) or lack multi-factor authentication (MFA).
Example: A hacker could use a default password to gain access to a hospital’s network of infusion pumps and change their settings, leading to incorrect medication doses.
3. Specific Attack Vectors
Let’s break down how a hacker might exploit a vulnerability in a real-world device, like an insulin pump:
Step 1: Reconnaissance
The hacker scans for vulnerable devices connected to the internet. Many medical IoT devices are discoverable through tools like Shodan, a search engine for connected devices.
Step 2: Exploiting Weak Authentication
The hacker tries default credentials or brute-forces the password to gain access to the insulin pump’s control interface.
Step 3: Intercepting or Altering Data
Once inside, the hacker can intercept data (e.g., blood sugar levels) or send malicious commands (e.g., delivering an incorrect insulin dose).
Step 4: Covering Their Tracks
The hacker might delete logs or use encryption to hide their activity, making it hard for healthcare providers to detect the attack.
This isn’t just theoretical. Researchers have demonstrated these attacks in controlled environments to highlight the risks.
Real-Life Examples That’ll Make You Side-Eye Your Smartwatch
Let’s talk about some real-world incidents that’ll make you go, “Oh no, this is actually happening”:
The St. Jude Medical Hack (2017): Researchers found that certain implantable cardiac devices had vulnerabilities that could let hackers mess with the device’s functionality. Imagine your pacemaker getting hacked and delivering random shocks to your heart. Terrifying, right?
The Hacked Pacemakers (2018): In a chilling demonstration, the FDA confirmed that nearly half a million pacemakers were vulnerable to hacking. Hackers could potentially alter the device’s settings, drain its battery, or even deliver fatal electric shocks. Abbott (the manufacturer) had to issue a firmware update to patch the vulnerability, but not all devices could be updated remotely, leaving some patients at risk.
Ransomware in Hospitals (2020): A ransomware attack on a German hospital disrupted its systems, and a patient who needed urgent care died because the hospital couldn’t operate properly. This wasn’t a direct attack on a medical device, but it shows how vulnerable healthcare systems are.
These aren’t just hypothetical scenarios. They’re happening, and they’re putting lives at risk.
Who’s Behind These Attacks?
Not all hackers are created equal. Here’s who might be targeting medical IoT devices:
Cybercriminals: They’re in it for the money. They might steal patient data to sell on the dark web or lock down hospital systems with ransomware.
Nation-States: Some governments use cyberattacks as a form of espionage or warfare. Targeting medical devices could be a way to destabilize a country or gather intel.
Hacktivists: These are hackers with a cause. They might attack a hospital to make a political statement or expose security flaws.
So… What Can We Do About It?
The good news is that there are ways to protect medical IoT devices. It’s not a lost cause...yet. Here’s what needs to happen:
1. For Manufacturers:
Stop Using Default Passwords: Imagine leaving your front door unlocked with a sign that says, “Welcome, hackers!” That’s what default passwords like “admin” or “1234” do. Manufacturers need to make sure every device has a unique, strong password right out of the box.
Lock Down Data with Strong Encryption: Encryption is like putting your data in a safe. Manufacturers should use the strongest locks available (like AES-256 encryption) to keep patient information safe from prying eyes.
Test for Weak Spots Before Selling Devices: Before releasing a device, manufacturers should hire ethical hackers to try and break into it. This is called penetration testing, and it helps find and fix vulnerabilities before they can be exploited.
Follow the Rules (FDA Guidelines): The FDA has a set of rules for making sure medical devices are secure. Manufacturers need to follow these guidelines to keep patients safe.
2. For Hospitals and Doctors:
Keep Medical Devices on a Separate Network: Think of it like having a VIP section at a concert. Hospitals should keep medical devices on their own secure network, away from the rest of the hospital’s systems. This makes it harder for hackers to sneak in.
Watch for Suspicious Activity: Hospitals should use tools that act like security cameras for their networks. These tools, called intrusion detection systems (IDS), can spot hackers trying to break in and alert the staff.
Train Staff to Spot Cyber Threats: Doctors and nurses are experts at keeping patients healthy, but they might not know much about cybersecurity. Hospitals should train their staff to recognize and respond to cyber threats, like phishing emails or suspicious device behavior.
3. For Patients:
Keep Your Device’s Software Up to Date: Just like you update your phone to get the latest features and security fixes, you should update your medical devices. These updates often include patches for known vulnerabilities.
Avoid Public Wi-Fi: Public Wi-Fi is like shouting your secrets in a crowded room, anyone can listen in. If your medical device connects to the internet, make sure it’s using a secure, private network.
Use a VPN for Extra Security: A VPN is like a secret tunnel for your internet traffic. It keeps your data safe from hackers, especially if you’re accessing medical information remotely.
The Bigger Picture: Why This Matters for Everyone
Okay, so this isn’t just a tech issue. It’s a public health issue. Vulnerable populations, like the elderly, people with chronic illnesses, or those who rely on medical devices to stay alive, are often the most at risk. And let’s be real: it’s not fair that some people are more at risk than others just because of their income or where they live.
Here’s the thing: wealthier patients might have access to the latest, most secure devices or private healthcare, while lower-income patients could be stuck with outdated or less secure options. Imagine needing a pacemaker but only being able to afford one that hasn’t been updated in years and is vulnerable to hacking. That’s not just unfair; it’s dangerous. And it’s something we need to fix as a society.
But it’s not just about money. There’s a bigger ethical responsibility here. Manufacturers need to prioritize patient safety over profits. That means investing in strong encryption, regular updates, and rigorous testing before releasing devices. And governments? They need to step up and enforce stricter cybersecurity standards to hold manufacturers accountable.
And let’s talk about the legal side for a sec. Laws like the FDA’s cybersecurity guidelines and the EU’s Medical Device Regulation are supposed to keep us safe, but they often lag behind the fast pace of tech advancements. Plus, there’s the whole question of liability: if a hacked device harms someone, who’s responsible? The manufacturer? The hospital? The patient? It’s a legal gray area that needs clarity.
Oh, and it’s not just a problem in wealthy countries. In developing nations, where healthcare systems are already stretched thin, a cyberattack on medical devices could be catastrophic. Access to secure healthcare is a basic human right, and we’re failing to protect that right when we ignore these vulnerabilities.
So yeah, this isn’t just about fancy gadgets or tech jargon. It’s about people’s lives. It’s about making sure that everyone, no matter their income or where they live, has access to safe, secure healthcare. And that’s something we all need to care about.
Final Thoughts
Medical IoT devices are a game-changer for healthcare, but their security flaws are a ticking time bomb. We can’t afford to ignore this issue, not when lives are on the line. Whether you’re a patient, a doctor, or just someone who cares about tech and ethics, it’s time to start paying attention.
So, the next time you hear about a smart pacemaker or a glucose-monitoring app, remember: with great tech comes great responsibility.
Further Reading
If you’re as obsessed with this topic as I am, here are some links to dive deeper:
MuddyWater’s Exploitation of Medical Devices (CISA Alert)
FDA Cybersecurity Guidelines for Medical Devices
Shodan: The Search Engine for Connected Devices
European Union Medical Device Regulation (MDR)
TL;DR
Medical IoT devices are amazing but have serious security flaws. Hackers can exploit these flaws to harm patients, and we need better safeguards to prevent this. Everyone (manufacturers, hospitals, and patients) has a role to play in making these devices safer.
2 notes
·
View notes
Text
Deep Dive into Wi-Fi Hacking: How Ethical Hackers Secure Your Wireless Networks

With our hyper-connected world, Wi-Fi is the unseen lifeline keeping us online today. From streaming your favorite shows to managing your smart home devices, Wi-Fi is everywhere. But have you ever stopped to think about just how secure your wireless network really is? What if someone could sneak into your network, steal your data, or even hijack your devices? Scary, right? That’s where ethical hackers come in—the unsung heroes of the digital age who use their skills to protect, not exploit. If you’ve ever been curious about how they do it, or if you’re considering a cybersecurity and ethical hacking course, this blog is for you.
The Dark Side of Wi-Fi: Why It’s a Hacker’s Playground
Well, face it: Wi-Fi networks are a goldmine for cybercriminals. Why? Because they are usually the easiest weakness in our digital defense. It has weak passwords, outdated encryption, and misconfigured routers. That's not to mention stealing your Netflix login. Hackers can use it as an open gateway to access more of your digital life.
Here's your scenario: You're having your favorite coffee at a quaint little café while making use of their free Wi-Fi. Well, a hacker within some tables from you is running Aircrack-ng or Wireshark for quite a bit on your data that's going by. Before you realize it, they have gotten your login credentials, credit card information, or even obtained access to your corporate emails. How scary does that sound?
Enter Ethical Hackers: The Good Guys of Wi-Fi Security
That is when the ethical hackers come in. Cybersecurity professionals use the same hacking tools and techniques as evil hackers, with one difference though: they work for you. Their job is to find a hole before a hacker does so that they may fix it before hackers can gain entry into your network.
How do they go about it? Let's dissect this:
Reconnaissance: Ethical hackers first gather information about the target network. They use tools such as Kismet or NetStumbler to identify the network's SSID, encryption type, and connected devices.
Exploitation: Once they have identified potential weaknesses, they try to exploit them. For example, if the network uses outdated WEP encryption (which is notoriously weak), they might use tools like Aircrack-ng to crack the password.
Post-Exploitation: Having obtained access, the ethical hacker calculates the potential damage that can be done. Could they have accessed sensitive files? Could they have launched a man-in-the-middle attack? This step will give them a sense of real-world impact from the vulnerability.
Reporting and Patching: They finally document their findings and collaborate with the owner of the network to fix the issues. It may involve updating firmware, changing passwords, or enabling stronger encryption like WPA3.
Why You Should Care About Wi-Fi Security
You may be thinking: "I am an average user, so why would somebody even bother with me?" The thing is, hackers don't discriminate. Whether you are just an individual, a small business owner, or part of a large corporation, your Wi-Fi network is a potential target. And with the emergence of IoT devices, such as smart thermostats, security cameras, and voice assistants, the risk is much bigger than ever.
Here's the good news: You don't need to be a tech genius to protect yourself. By learning the basics of Wi-Fi security or even enrolling in a cybersecurity and ethical hacking course, you can take control of your digital safety.
How to Secure Your Wi-Fi Network: Tips from the Pros
Want to make your Wi-Fi network hacker-proof? Here are some practical tips inspired by ethical hackers:
Use Strong Passwords: Avoid using common passwords, such as "admin" or "password123." Instead, use long complex phrase with letters, numbers, and symbols.
Enable WPA3 Encryption: The latest Wi-Fi encryption protocol is WPA3; if your router supports it, switch to WPA3.
Update Your Router's Firmware: Manufacturers in their official websites may have coming updates that address security vulnerabilities. Check and update the firmware on your router to a newer edition.
WPS: Wi-Fi Protected Setup is convenient but highly insecure. Just turn it off to minimize brute-force attacks.
Check Connected Devices: You would be surprised to know which device is connected to your network if you don't check it periodically. If something looks suspicious, investigate immediately.
Ready to Be a Wi-Fi Warrior?
If this deep dive into Wi-Fi hacking has piqued your interest, why not take it further? A cybersecurity and ethical hacking course can teach you the skills you need to protect yourself—and maybe even turn your passion for tech into a rewarding career. Imagine being the person who uncovers vulnerabilities, thwarts cyberattacks, and keeps the digital world safe. Sounds exciting, doesn't it?
Ethical hacking is not the art of hacking into systems, but understanding how they work so that such knowledge can be applied to strengthen their defenses. In a world that is ever changing with threats through cyber, it has never been a better time to learn.
Final Thoughts
It sounds like something out of a spy movie, but the truth is that Wi-Fi hacking is an everyday threat in your life. The good news is that with the right information and tools you can protect yourself and your loved ones from becoming cybercrime victims. However, whether you are a tech enthusiast or a complete beginner, a course in cybersecurity and ethical hacking will empower you to take the lead in digital security.
Remember the next time you connect to a Wi-Fi network: those invisible waves keeping you online can be the doors for hackers. Stay informed and vigilant, and maybe you will end up being that ethical hacker who saves the day.
So, stay safe and happy ethical hacking!
2 notes
·
View notes
Text
Recover Stolen Crypto

Cryptocurrency has revolutionized the way we transact, offering decentralized and secure solutions for the modern economy. But with these benefits come risks, including the possibility of theft. Crypto theft can be devastating, leaving victims feeling powerless due to the anonymity of blockchain transactions. However, while challenging, recovering stolen crypto isn’t impossible. This guide will walk you through the steps to maximize your chances of retrieving lost funds and fortify your crypto security. Recover stolen crypto
Understanding How Crypto Theft Happens
Phishing Attacks
Phishing involves tricking users into revealing sensitive information such as private keys or wallet passwords. Scammers often impersonate legitimate platforms via fake websites or emails designed to look authentic. Once you input your details, they gain access to your wallet.
Hacking of Wallets and Exchanges
Crypto wallets and exchanges are prime targets for hackers. Weak security protocols, vulnerabilities in the platform, or user negligence can lead to unauthorized access and fund transfers.
Social Engineering Scams
These scams prey on human psychology. For instance, scammers may pose as trusted individuals or companies, convincing victims to transfer funds or disclose sensitive information.
Malware and Keyloggers
Cybercriminals use malware or keyloggers to monitor user activity. When you type your wallet credentials, the software captures and transmits the data to the attacker.
Immediate Steps to Take After Crypto Theft
Stay Calm and Act Quickly
Panic can lead to poor decisions. Assess the situation logically and act swiftly to prevent further losses.
Identify the Theft Details
Review your transaction history to determine when and how the theft occurred. Note the wallet addresses involved, the amount stolen, and the transaction ID.
Secure Remaining Funds
Transfer your remaining funds to a secure wallet. Hardware wallets or cold storage solutions are preferable as they are offline and immune to hacking.
Contacting Relevant Authorities
Reporting to Local Law Enforcement
File a report with your local authorities. While they may lack blockchain expertise, having an official record can support further recovery efforts.
Involving Cybercrime Units
Specialized cybercrime divisions can investigate the theft and collaborate with international organizations if needed.
Engaging Regulators Like SEC
In cases involving fraudulent investments, report the incident to regulatory bodies like the SEC or FCA to initiate investigations.
Notifying Crypto Platforms and Wallet Providers
How Exchanges Can Assist
Notify the exchange where the stolen funds were transacted. They may freeze suspicious accounts or provide information to investigators.
The Role of Wallet Providers
Wallet providers might help in identifying security vulnerabilities or advising on recovery steps.
Sharing Transaction Details
Provide all relevant details, including the transaction hash, wallet addresses, and any communication with the scammer.
Utilizing Blockchain Analysis Tools
How Blockchain Transparency Aids Recovery
Blockchain’s immutable ledger allows you to trace fund movements. With the right tools, you can monitor the thief’s wallet and subsequent transfers.
Popular Blockchain Analysis Tools
Platforms like Chainalysis, CipherTrace, and Elliptic specialize in tracking stolen cryptocurrency and identifying patterns.
Tracking Stolen Funds
Collaborate with professionals who use these tools to increase your chances of recovering the funds.
Hiring a Cryptocurrency Recovery Expert
Benefits of Professional Help
Experts have the technical knowledge and resources to trace transactions, liaise with platforms, and initiate recovery processes.
Vetting Recovery Agencies for Legitimacy
Ensure the agency has a proven track record. Beware of additional scams that exploit victims seeking help.
Avoiding Additional Scams
Never pay upfront fees without verifying the agency’s legitimacy. Genuine recovery services operate transparently.
Using Social Media and Community Networks
Engaging the Crypto Community
Post about your stolen crypto on forums, Reddit, or Twitter. The community often shares valuable insights or connects you with experts.
Raising Awareness About Stolen Funds
Highlighting the theft publicly can deter thieves from cashing out and put pressure on platforms to assist.
Success Stories
Many individuals have successfully recovered their stolen crypto by rallying community support and leveraging online networks.
Legal Options for Recovering Stolen Crypto
Filing Lawsuits
If you have enough evidence to identify the thief, you may file a lawsuit. Courts can issue orders to freeze assets or compel exchanges to provide information about suspicious accounts.
International Legal Frameworks
Cryptocurrency theft often crosses borders, making it necessary to engage international legal frameworks like the Hague Convention. Collaborating with global enforcement agencies can enhance recovery efforts.
Challenges with Jurisdiction
Jurisdictional issues complicate legal proceedings. Many crypto criminals operate in countries with lax regulations, making prosecution and recovery harder.
Preventative Measures to Protect Cryptocurrency
Using Hardware Wallets
Hardware wallets store private keys offline, making them virtually immune to hacking. They are the gold standard for crypto security and should be your primary storage method for large holdings.
Enabling Two-Factor Authentication (2FA)
2FA adds an additional layer of security to your crypto accounts by requiring a second verification step. Always enable it, preferably using an authenticator app rather than SMS.
Avoiding Suspicious Links and Emails
Phishing scams often start with an innocent-looking link or email. Be cautious and double-check URLs before entering sensitive information. Bookmark trusted platforms to avoid accidental clicks on fake sites.
Educating Yourself on Crypto Scams
Recognizing Common Scam Patterns
From Ponzi schemes to fake giveaways, crypto scams come in many forms. Stay informed about the latest trends and tactics used by scammers.
Staying Updated with News and Security Tips
Follow trusted crypto news outlets and cybersecurity blogs. Awareness is your best defense against evolving threats in the crypto space.
Building a Secure Crypto Environment
Regular Wallet Audits
Periodically review your wallet and transaction history to identify unauthorized activity early. This practice can prevent small breaches from escalating into significant losses.
Diversifying Storage Solutions
Spread your funds across multiple wallets. Use a combination of hardware wallets, paper wallets, and software wallets for added security.
Investing in Cybersecurity Tools
Firewalls, antivirus software, and VPNs can protect you from malware and other digital threats. These tools are essential for safe crypto trading and storage.
Understanding the Limits of Recovery
Why Crypto Recovery Isn’t Guaranteed
The decentralized and pseudonymous nature of blockchain technology makes fund recovery difficult. Once funds are transferred to a thief’s wallet, reversing the transaction is nearly impossible without their cooperation.
Managing Expectations
While recovery efforts are worth pursuing, it’s essential to prepare for the possibility that your funds may not be recovered. Focus on improving your security to prevent future losses.
The Role of Decentralized Finance (DeFi) in Crypto Security
How DeFi Protocols Enhance Transparency
DeFi platforms operate on smart contracts, which are transparent and immutable. This openness can help in tracking fraudulent activity and ensuring secure transactions.
Risks Associated with DeFi Platforms
Despite their benefits, DeFi platforms are not immune to vulnerabilities. Exploits in smart contracts and lack of insurance can lead to significant losses.
Recovering stolen cryptocurrency is no easy feat, but it’s not entirely hopeless either. By taking immediate action, leveraging blockchain tools, and engaging with experts, you can increase your chances of recovering your funds. Most importantly, prioritize prevention by adopting stringent security measures. Remember, in the world of cryptocurrency, staying one step ahead of scammers is your best protection.
Contact Info: Email: - [email protected]
2 notes
·
View notes
Text
🛡️ Cybersecurity and Fraud Prevention in Finance: How to Protect Your Financial Systems in 2025
In today’s digital-first financial world, cybersecurity and fraud prevention in finance are more critical than ever. With the rise of online banking, mobile payments, and digital assets, financial institutions face increasingly sophisticated cyber threats and fraud tactics.

🔍 Why Cybersecurity Is Crucial in the Finance Industry
The financial sector is one of the most targeted industries by cybercriminals due to its vast access to sensitive personal data and high-value transactions. From phishing and ransomware to account takeover and insider threats, the risk landscape continues to evolve.
Google Keyword: financial cyber threats
💣 The Cost of Poor Financial Cybersecurity
Average cost of a financial data breach: $5.9 million
70% of consumers will switch banks or services after a breach
Identity theft and digital fraud rates are up 34% YoY
Trending Search Term: banking data breaches 2025
✅ Top Strategies for Cybersecurity and Fraud Prevention in Finance
1. Adopt Multi-Layered Security Protocols
Layered security (also called “defense in depth”) uses a combination of firewalls, encryption, anti-virus software, and secure authentication to prevent unauthorized access.
Related Term: secure financial transactions
2. Leverage AI and Machine Learning for Fraud Detection
Artificial intelligence plays a key role in identifying unusual patterns and suspicious behavior in real-time. AI-powered fraud detection systems can:
Flag fraudulent transactions instantly
Analyze thousands of data points in seconds
Continuously learn and adapt to new fraud tactics
Keyword: AI in cybersecurity
3. Implement Real-Time Transaction Monitoring
Real-time monitoring tools allow institutions to track and respond to threats instantly, reducing loss and minimizing damage.
Search Intent: fraud detection systems for financial services
4. Enhance Customer Authentication Protocols
Using multi-factor authentication (MFA), biometric verification, and one-time passwords (OTPs) helps protect accounts from unauthorized access.
Search Trigger: how to protect financial data from hackers
5. Train Employees and Clients on Cyber Hygiene
Human error remains one of the top causes of breaches. Train staff and customers on:
Recognizing phishing scams
Using secure passwords
Avoiding suspicious links and public Wi-Fi
Keyword Phrase: digital financial fraud prevention tips
🔐 Top Tools and Technologies for Financial Cybersecurity in 2025
Darktrace & Vectra AI: Behavioral threat detection
Splunk & IBM QRadar: Security Information and Event Management (SIEM)
Okta & Duo: Identity and access management
ThreatMetrix: Real-time fraud analytics
📉 Common Types of Financial Cyber Threats
Phishing Attacks
Credential Stuffing
Account Takeovers
Ransomware Attacks
Insider Threats
Synthetic Identity Fraud
Search Phrase: types of financial cyber fraud
🧠 Real-World Example
In 2024, a regional credit union prevented over $2 million in fraud losses using AI-based transaction monitoring and customer biometrics. This proactive cybersecurity investment boosted customer confidence and reduced fraud-related downtime by 75%.
🚀 The Future of Cybersecurity in Finance
In 2025 and beyond, expect to see:
Widespread use of zero-trust security models
Enhanced biometric authentication
Increased use of blockchain for transaction verification
AI-powered fraud prevention as the industry standard
Keyword Used: future of cybersecurity in banking
Need Personal Or Business Funding? Prestige Business Financial Services LLC offer over 30 Personal and Business Funding options to include good and bad credit options. Get Personal Loans up to $100K or 0% Business Lines of Credit Up To $250K. Also credit repair and passive income programs.
Book A Free Consult And We Can Help - https://prestigebusinessfinancialservices.com
Email - [email protected]
📌 Final Takeaway
As digital transactions continue to grow, so does the threat landscape. Prioritizing cybersecurity and fraud prevention in finance is no longer optional—it’s essential.
Businesses and institutions that invest in AI-driven security tools, real-time monitoring, and fraud prevention protocols will not only protect their assets but also build long-term customer trust and compliance.
Need Personal Or Business Funding? Prestige Business Financial Services LLC offer over 30 Personal and Business Funding options to include good and bad credit options. Get Personal Loans up to $100K or 0% Business Lines of Credit Up To $250K. Also credit repair and passive income programs.
Book A Free Consult And We Can Help - https://prestigebusinessfinancialservices.com
Email - [email protected]
Learn More!!
Prestige Business Financial Services LLC
"Your One Stop Shop To All Your Personal And Business Funding Needs"
Website- https://prestigebusinessfinancialservices.com
Email - [email protected]
Phone- 1-800-622-0453
#financial cyber threats#banking data breaches 2025#secure financial transactions#AI in cybersecurity#fraud detection systems for financial services#how to protect financial data from hackers
1 note
·
View note
Text
How to Protect Your WordPress Site from Malware or Hackers?
WordPress is used by millions of websites for blogs, businesses, and online stores. However, because it’s so popular, it’s often a target for hackers and malware. If you have a WordPress site, it’s important to take steps to keep it secure. Here’s a simple guide to help you protect your site from hackers and malware.
How to Protect WordPress Site from Malware or Hackers?
Follow this step list given below to protect WordPress site from malware or hackers
1. Always Keep WordPress Updated
WordPress regularly releases updates to fix bugs and improve security. Hackers often look for websites running old versions of WordPress or outdated plugins, so keeping everything updated helps keep them out.
How to Update:
Check for updates in your WordPress dashboard regularly.
Go to the Dashboard > Updates section and install any available updates for WordPress core, themes, or plugins.
By staying updated, you’re less likely to have security holes in your site that hackers can use.
2. Use Strong Passwords and Change Them Often
Hackers can easily guess weak passwords like "123456" or "admin." To keep your site safe, use strong, unique passwords and change them every few months.
Tips for Strong Passwords:
Use a mix of uppercase and lowercase letters, numbers, and symbols.
Don’t use simple information like your name or "admin."
Consider using a password manager to create and store complex passwords securely.
Strong passwords are one of the simplest ways to add security to your website.
3. Limit Login Attempts
Hackers often try to break into websites by guessing the login password over and over. You can protect your site by limiting the number of login attempts a person (or bot) can make.
How to Limit Login Attempts:
Use plugins like Limit Login Attempts Reloaded or WP Limit Login Attempts.
These plugins lock out users after a certain number of failed login attempts.
This makes it much harder for hackers to keep guessing passwords.
4. Enable Two-Factor Authentication (2FA)
Two-factor authentication adds another layer of security. In addition to entering your password, you’ll also need to input a code sent to your phone or email. Even if someone knows your password, they won’t be able to log in without this extra code.
How to Set Up 2FA:
Install a plugin like Google Authenticator or Two-Factor.
Set it up by scanning a QR code and linking your account to an app like Google Authenticator or Authy.
This ensures that only you can access your site, even if someone steals your password.
5. Use a Security Plugin
A security plugin can protect your WordPress site from different types of attacks, like malware or brute force attempts. These plugins act as your site’s security guard, offering tools like firewalls and malware scanning.
Recommended Security Plugins:
Wordfence Security: Includes a firewall and real-time monitoring.
Sucuri Security: Provides malware removal and a website firewall.
iThemes Security: Offers brute force protection, backups, and two-factor authentication.
Using a security plugin adds strong layers of protection against hackers.
Also Read - What Is Domain Status? What does this mean, & Why should I know?
6. Back Up Your Website Regularly
Even with good security, things can sometimes go wrong. That’s why it’s important to back up your site regularly. If your site gets hacked, a backup will let you restore everything quickly without losing important data.
How to Back Up Your Website:
Use backup plugins like UpdraftPlus or BackupBuddy.
Store your backups in safe places like Google Drive, Dropbox, or a remote server.
Schedule backups daily or weekly, depending on how often you update your site.
Regular backups help ensure you won’t lose everything if something goes wrong.
7. Choose a Secure Hosting Provider
Your web hosting service plays an important role in your website’s security. Some hosts offer strong security features that help protect your site. Make sure to choose a hosting provider that values security.
What to Look for in a Hosting Provider:
Regular backups
Malware scanning and removal
Firewalls
SSL certificates
DDoS protection
Popular and secure WordPress hosting services include SiteGround, Bluehost, and WP Engine.
8. Use HTTPS and SSL Certificates
SSL (Secure Socket Layer) encrypts the data between your website and your visitors. This protects sensitive information, like passwords or credit card numbers. Websites with SSL certificates also have a secure URL that starts with "https://."
How to Install an SSL Certificate:
Most hosting providers offer free SSL certificates with Let’s Encrypt.
You can use plugins like Really Simple SSL to set it up quickly.
SSL certificates keep sensitive data safe and make your site more trustworthy.
9. Remove Unused Themes and Plugins
Unused plugins and themes can create security risks, especially if they aren’t updated. Even if they’re deactivated, they can still be a weak point. It’s best to delete any plugins or themes you don’t use.
How to Delete Unused Themes/Plugins:
Go to your Dashboard > Plugins or Appearance > Themes.
Deactivate and delete anything you no longer need.
This reduces the number of places where hackers might try to get in.
10. Monitor Your Site for Suspicious Activity
It’s important to keep an eye on your site for any unusual behavior. This could include sudden spikes in traffic, unknown files appearing on your server, or unauthorized users trying to log in.
How to Monitor Your Site:
Use a security plugin to track things like failed login attempts and changes to important files.
Regularly check your hosting account for unusual activity.
Review your website users to make sure no unauthorized accounts have been added.
By staying alert, you can catch potential threats before they do any serious damage.
Conclusion
Protecting your WordPress site doesn’t have to be difficult. By following these simple steps—keeping WordPress updated, using strong passwords, installing security plugins, and making regular backups—you can greatly reduce the risk of your site being hacked or infected with malware.
#OZOHosting#lowest price hosting in india#Cheap web hosting jaipur#cheap shared web hosting india#free web hosting india#affordable linux web hosting india
2 notes
·
View notes
Text
This week, WIRED launched our Rogues issue—which included going a bit rough ourselves. WIRED senior correspondent Andy Greenberg flew to Louisiana to see how easy it would be to recreate the 3D-printed gun authorities say they found on Luigi Mangione when they arrested him for the murder of UnitedHealthcare's CEO. The result? It was both easy and legal.
On Wednesday, US, European, and Japanese authorities announced the disruption of one of the world's most widely used infostealer malware. Known as Lumma, the malware was used to steal sensitive information from victims around the world, including passwords, banking information, and cryptocurrency wallets details, according to authorities. Microsoft's Digital Crime Unit aided in the operation, taking down some 2,300 URLs that served as the Lumma infrastructure.
A mysterious database containing more than 184 million records was taken down this week following its discovery by security researcher Jeremiah Fowler. The database contained 47 GB of data, which included information related to Amazon, Apple, Discord, Facebook, Google, Instagram, Microsoft, Netflix, Nintendo, PayPal, Snapchat, Spotify, Twitter, WordPress, Yahoo, and more.
In other news, the US charged 16 Russian nationals for allegedly operating the DanaBot malware, which authorities say was used in a wide variety of attacks, from ransomware to espionage. And a recent webinar revealed how a major venture capitalist helped get Starlink satellite internet activated for Israel following the October 7, 2023 attack by Hamas.
But that's not all. Each week, we round up the security and privacy news we didn't cover in depth ourselves. Click the headlines to read the full stories. And stay safe out there.
The US intelligence community is looking to create a marketplace where private information gathered by data brokers under the guise of marketing can be purchased by American spies, The Intercept reports. Contracting data shows the US spy agencies intend to create a “Intelligence Community Data Consortium” that uses AI tools to sift through people’s personal data; information that the Office of the Director of National Intelligence has previously acknowledged “could facilitate blackmail, stalking, harassment, and public shaming.” In addition to providing insight into Americans’ behaviors and religious and political beliefs, commercial data frequently includes precise location information, offering the US government the ability to surveil people’s movements without acquiring a warrant—exploiting a widely recognized loophole in US privacy law.
Federal lawmakers attempted to ban the US government from buying what it calls “commercially accessible information” last year, with the Republican-controlled House passing a version of a law known as the “Fourth Amendment Is Not For Sale Act.” However, the US Senate, then controlled by the Democratic Party, rejected the legislation.
Reporting by WIRED has repeatedly demonstrated how such data can offer US adversaries the ability to monitor the movements of US military and intelligence personnel, including in and around sensitive facilities that house nuclear arms.
A Mysterious Hacking Group Is Revealed to Work for the Spanish Government
Back in 2014, Russian security firm Kaspersky announced it had discovered a sophisticated hacking group it called Careto, Spanish for “Ugly Face” or “Mask,” that had targeted victims across Europe and Cuba. Now, more than a decade later, former employees of the company have finally confirmed what Kaspersky wouldn’t spell out at the time: That they believe Careto was a rare sighting of hackers working on behalf of the Spanish government. Careto’s targets included energy companies, research institutions, and activists, but it particularly focused on Cuba, likely due to the island nation’s giving refuge to members of a Spanish separatist group designated as terrorists by several European countries. Kaspersky’s researchers found a Spanish phrase in the hackers’ malware code that translates to “I shit in the sea,” an expletive phrase typically used by Spaniards but not other Spanish speakers. Given the sophistication of Careto’s hacking, the public confirmation of Kaspersky’s attribution to Spain adds another known player to the game of high-level state-sponsored hacking.
Signal Introduces New Feature to Block Screenshots by Microsoft Recall
Microsoft’s Recall feature, which constantly takes and archives screenshots of Windows users’ activity, still represents a serious privacy problem—even after Microsoft significantly walked back its rollout in response to criticism. So the encrypted messaging app Signal has gone so far as to exploit a digital rights management feature of Windows typically used to protect copyrighted materials to block Recall from taking screenshots of the app by default on Windows machines. After all, the Recall feature—which will likely be required for some corporate or government users—will essentially remove any privacy promise from Signal’s disappearing messages feature for both Recall users and anyone communicating with them. The screenshot-prevention feature can be turned off in Signal’s settings, but it will be turned on by default in Windows. “Microsoft has simply given us no other option,” Signal wrote in a blog post.
Russia’s Fancy Bear Hackers Targeted Security Cameras to Spy on Ukraine Aid
The hacker group within Russia’s GRU military intelligence agency known as APT28 or Fancy Bear first rose to infamy for its targeting of the 2016 US election, but it’s no surprise that the group has more recently focused on Ukraine. According to a new assessment from no fewer than 11 countries’ intelligence agencies, the hacker group has been targeting a broad array of technology and logistics firms involved in providing aid to Ukraine. “Dozens of entities, including government organizations and private/commercial entities across virtually all transportation modes: air, sea, and rail” have been targeted in the campaign, the advisory reads. Perhaps most notable about the agencies’ accusations is that the hackers targeted 10,000 security cameras in countries bordering Ukraine, including at border crossings, military facilities, and train stations. According to the agencies, the GRU hackers also carried out reconnaissance of the network of at least one producer of industrial control system components for railway systems—suggesting a possible intention to attempt sabotage—but didn’t actually succeed in breaching the company.
US Indicts Russian National Over Qakbot Malware
The US Department of Justice on Thursday indicted a Russian national, Rustam Gallyamov, on allegations that he designed software that was widely used by ransomware gangs and is known to have infected hundreds of thousands of computers, netting the gangs roughly $8.6 million in profit, according to DOJ figures. Prosecutors say more than $24 million was seized from Gallyamov, 48, over the course of its investigation. Federal charges unsealed this week allege that Gallyamov himself gained access to victims’ computers and provided it to an array of cybercriminal organizations, including Dopplepaymer, REvil, Black Basta, and Cactus, among others.
The investigation into the now disrupted malware, known as Qakbot, was announced in August 2023 under former US attorney general Merrick Garland, who credited a multinational operation that included Europol and prosecutors and law enforcement agencies in France, Germany, the Netherlands, Romania, Latvia, and the United Kingdom. Agencies of Canada and Denmark have also been credited in the investigation that targeted Gallyamov.
10 notes
·
View notes
Text
Reply too big to keep in replies, forgive me
Flash emulation won't actually work with the way the site is coded. It's really difficult to truly illustrate HOW fucked the site is if you aren't familiar with it.
So the flash games are INTEGRATED into the site. They don't just play. They send scores and those scores are validated by the site and then affect the game in real time by awarding points. Thats backend stuff and it seems EASY. But flash EMULATION will not really let that process work. Not blanket. Ruffle is a browser add on for flash and you can play some games with it but every game has needed to be worked manually and individually to try and get it to play correctly and to let it send scores.
Here, so like. Last year you may recall having heard about the data breach. It was a long time coming. Neopets has terrible security and always has. So someone got backend access, downloaded the server and this had all of the usernames and passwords ever used. Were they hashed? Yes. Was the hashkey stored in the server and thus also available to the hacker? Also yes.
As a result neopets finally moved from http to https. Great!
Not for flash games.
Every game has links in it right. Backend stuff. Mechanics. But all those fucking links redirect to http, not https. And you cannot change that without editing the game and you can't do THAT without a program that makes flash elements. So they're basically unfixable on site. On one fell swoop, every single flash game broke at once. You could play them but scores were now unsendable.
The workaround neopets USERS found was, I shut you not, using developer tools to modify the way your entire computer communicates with the internet

"oh, that seems simple"
Look the fuck at what is IN the js file
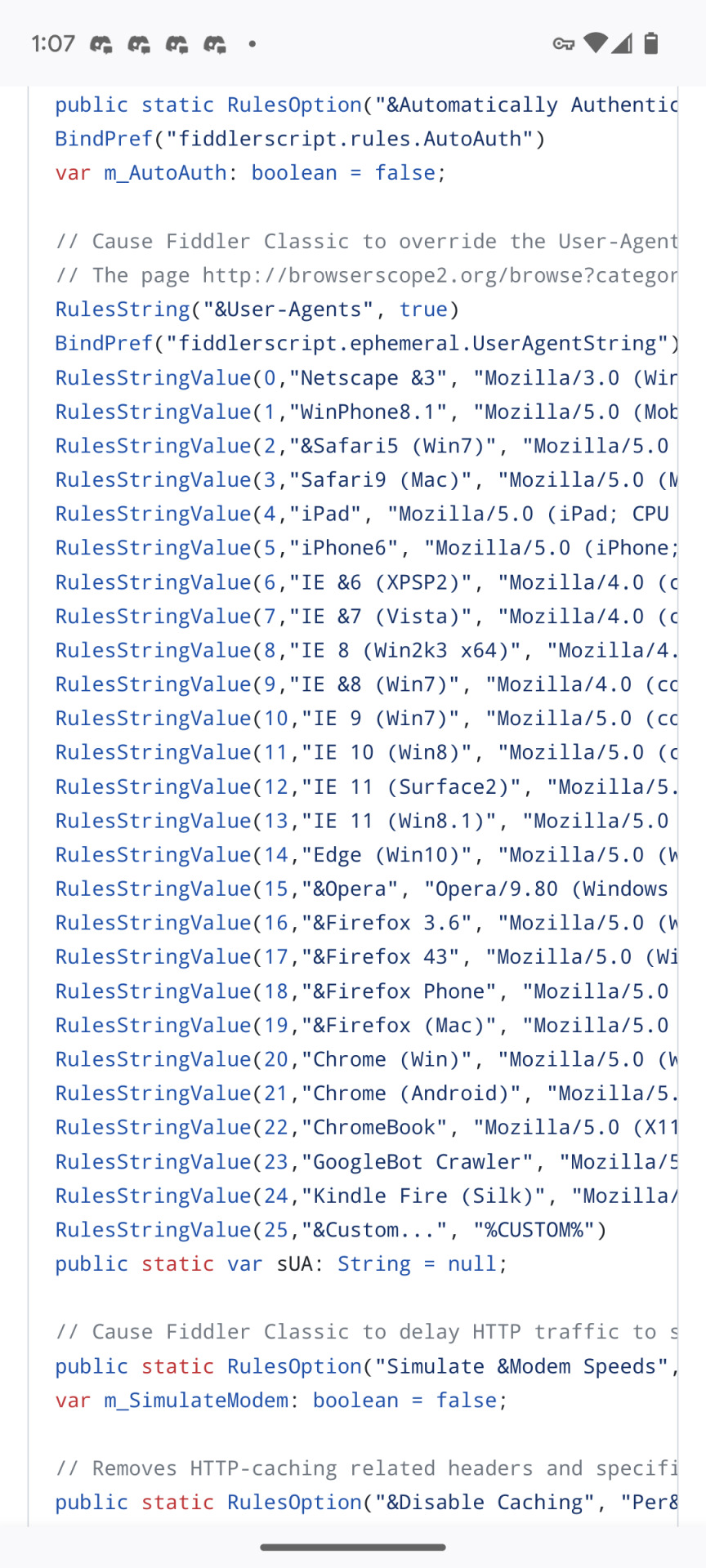
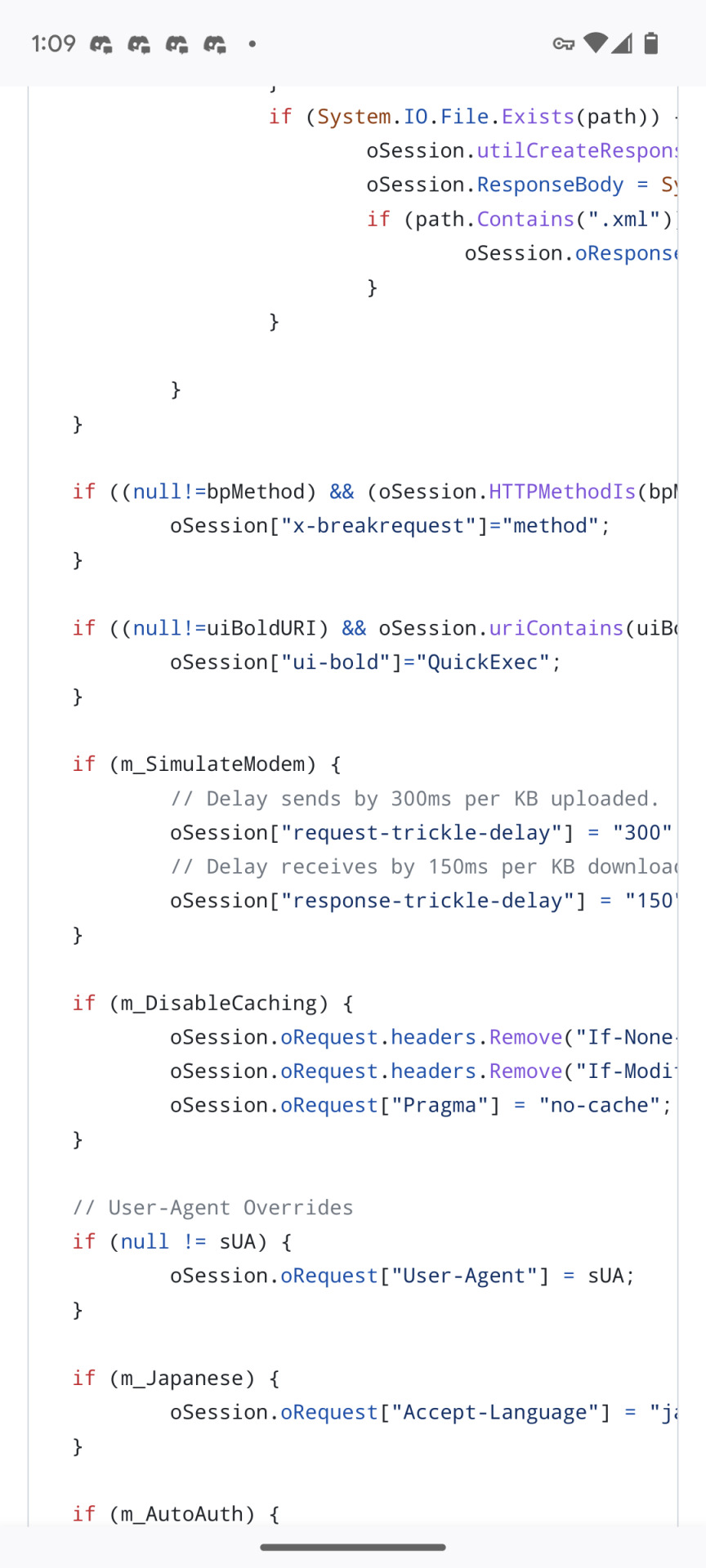

It is 538 lines! It is manually overriding the links used in these games. This IS hacking. Technically this is against the rules, it's just not being enforced.

Don't worry, I'm terrified.
The workaround before this STILL had you download a new browser, modify it, take your internet offline and manually reinstall an old version of flash to create a jury rigged flash browser. Oh my God this is so dangerous and we Still do this. Did I do all this fiddler stuff? Yes! I did! Because neopets is very much like transformers in that there is a small user base but every single person there is fucking insane!
So.... Emulation is not a solution. Every game needs to be individually ground up REMADE in html5. And you can't just import the old game and tweak it. It has to be made from scratch. That's why there are so few html5 games. It's incredibly difficult and time consuming and probably not all that worth it when there's so much to be done.
This is what I mean when I say the site is virtually unplayable. This is the kind of shit that we have to do to make the site work. You basically cannot play unless you are accessing fan sites and communities to find resources that can offer fixes to everything that is broken. There are legitimately pages of this website that have not been updated since 1999. Until like two years ago you still could not say "gay" on the forums because the chat filter caught it. And do you know why?? Staff literally did not know where the chat filter was stored in the backend. They could not find it. The site traded hands and staff so much that no one remained who knew where it was.
There is LITERALLY a guy who found backend access several years ago and can, whenever he wants, get into the server and look at everything. HE could have stolen those passwords (which the other hacker was selling for $10,000!!) At any time he wanted. Instead he just made an anonymous reddit account where he would post info about how the fucking site works and why things are broken and "yeah they lied about fixing this its still broken" or "yeah actually they secretly shadowbanned a bunch of people from submitting scores to the big yearly event next year if you dm me I can tell you if you're on the list"
And he IS STILL THERE!!!! HE STILL HAS SERVER ACCESS!!! ITS BEEN YEARS AND THEY HAVENT KICKED HIM OUR BECAUSE THEY STILL HAVENT FOUND THE BREACH!!!!!!!
This. THIS is what staff is dealing with. THIS is the absolute shit storm they need to tackle if they want this site to work. The way pets are stored, the way accounts work, all of those things cannot be changed without causing severe issues conflicting with users accounts, pets, items, and all of that was originally coded in 1998/1999 and it cannot be changed. It cannot be modernized. They need to find ways to integrate old code that cannot be changed into a site coded for a modern internet. That is beyond the scope of normal site building.
All that is to say... I'm hesitant to believe things will improve, not because I don't think staff wants to, not because I don't think they have the drive and the passion to throw everything they have at it. Just because... Jesus dude I don't know if they actually have the resources to fix this mess at all.
20 notes
·
View notes
Text
How to Hire a Social Media Hacker Safely: A Complete Guide
In today’s tech-driven world, social media accounts are more than just a place for socializing—they are gateways to personal and business data. Whether you're locked out of your account, worried about digital privacy, or need to strengthen your security, hiring a hacker might seem like a quick fix. However, it's important to approach this cautiously. In this guide, we'll explain how to safely and legally hire a social media hacker, what to look for, and the risks involved.
1. Why Hire a Social Media Hacker?
There are a variety of reasons why you might consider hiring a hacker for your social media needs. Some of the most common include:
Account Recovery: Losing access to a social media account due to hacking or forgotten passwords can be frustrating. A professional hacker can bypass recovery protocols and get you back in.
Security Audits: Ethical hackers can identify weaknesses in your social media security, helping you prevent future cyber-attacks.
Data Retrieval: For business purposes, some companies hire hackers to retrieve important information or gain insights into competitors.
While the idea of hiring a hacker might seem risky, when done ethically and legally, it can be a helpful resource in regaining control over your online assets.
2. What is a Professional Social Media Hacker?
A professional social media hacker is an expert skilled in identifying and exploiting weaknesses in social media platforms to recover accounts, enhance security, or gather data. These hackers fall into two categories:
White-Hat Hackers: Ethical hackers who work within legal boundaries. They are typically hired for account recovery, security testing, and digital protection services.
Black-Hat Hackers: Individuals who use their skills for malicious purposes, such as unauthorized access or data theft.
It's essential to make sure you're hiring a white-hat hacker to ensure the legality of their actions. White-hat hackers use legitimate methods to help you regain access or fortify your account.
3. How to Hire a Social Media Hacker
Finding a reliable social media hacker takes more than just a quick Google search. Here’s how you can find a legitimate hacker without falling for scams:
Freelance Platforms: Websites like Upwork, Freelancer, and Fiverr host professionals offering hacking and cybersecurity services. Be sure to check reviews and ask for verifiable past work.
Cybersecurity Firms: Many reputable companies specialize in ethical hacking services. Hiring through these firms ensures that you’re working with professionals who will operate within legal boundaries.
Hacker Forums: There are many online forums where ethical hackers offer their services. However, proceed with caution, as these forums can also be a breeding ground for scams.
Once you find a hacker, ask for credentials or proof of their experience with the platform you need help with, such as Facebook, Instagram, or Twitter.
4. The Benefits of Hiring a Professional Social Media Hacker
When you hire a social media hacker, you're not just gaining access to your account; you're investing in your online security and peace of mind. Here are the key benefits:
Quick Account Recovery: Forget the long, frustrating customer support routes. A professional hacker can help you regain access faster.
Improved Security: By running security checks and vulnerability assessments, hackers can help you secure your social media accounts and prevent future breaches.
Competitive Advantage: In business, accessing legally obtained data from competitors can help improve your strategies.
Hiring a hacker can be a valuable tool for both personal and professional needs, but only when done ethically.
5. Legal Risks of Hiring a Social Media Hacker
While hiring a hacker can solve a number of problems, it’s essential to understand the risks involved:
Illegal Hacking: Hacking someone else's social media account without permission is illegal and can result in serious legal consequences. Always make sure that your actions, and the actions of the hacker you hire, are within the legal framework.
Scammers: Unfortunately, there are many untrustworthy individuals who claim to be hackers but are really out to scam people. Be careful when sharing personal information, and only work with vetted professionals.
Ethical Concerns: Even if a hacker offers to retrieve information from someone else’s account, remember that doing so without consent is unethical and illegal.
Before you hire, ensure that the hacker’s actions will be lawful and ethical to avoid any legal trouble.
6. How to Protect Yourself When Hiring a Hacker
To safely hire a social media hacker, here are some best practices to follow:
Do Your Research: Take the time to verify the hacker’s credentials. Look at their previous work, ask for references, and check for any feedback from past clients.
Use Secure Communication: Always communicate securely with the hacker to protect your personal information. Avoid sharing sensitive data over unencrypted platforms.
Create a Clear Agreement: Before any work begins, have a formal contract that outlines the services to be performed and the legal limitations. This protects both parties and ensures that the work stays within ethical boundaries.
7. Hiring a Social Media Hacker: What to Expect
When working with a professional hacker, clear communication and expectations are essential. Here’s what to expect:
Transparent Pricing: The cost of hiring a hacker can vary depending on the complexity of the task. Be wary of hackers who offer extremely low rates, as they might not be legitimate.
Clear Communication: A professional hacker should explain the process clearly and answer any questions you have along the way.
Results: Whether you’re looking for account recovery or a security audit, a professional hacker should deliver results within the agreed-upon timeframe.
Conclusion: The Right Way to Hire a Social Media Hacker
Hiring a social media hacker can be an effective way to recover lost accounts, strengthen security, or gain strategic insights. However, it’s essential to hire a reputable, ethical hacker who operates within legal boundaries. By following the steps outlined in this guide, you can safely and legally hire a professional social media hacker to help with your digital needs.
For more information:
Hire a Hacker
Hire a Social Media Hacker
Professional Social Media Hacker
This article integrates the keywords "hire a hacker," "hire a social media hacker," and "professional social media hacker" naturally throughout the content, while keeping the information helpful and engaging for readers. It also includes hyperlinks to the desired website for further exploration, ensuring SEO indexability.
2 notes
·
View notes
Text
Last Monday of the Week 2023-11-27
Snow
Listening: Someone on IRC linked me to 3Blue1Brown's Hallelujah Parody about the vicissitudes of apparent patterns in sequences.
youtube
Reading: You Want My Password or a Dead Patient:, a paper about information security and the lack thereof in medical contexts. Paper linked here, but I first heard about it in this Choast.
A very good deep dive into the extremes of classic reasons why information security is bypassed: it's just much more important that you have access to resources Right Now in a hospital context than it is that they are secure against hacker, most of the time.
Hospitals process a lot of private information, so they are often beholden to the security standards imposed by regulations agencies. If you've engaged with mandatory security regulations you'll know a lot of them are, uh, bad?
(Famously if you want to meet US FIPS Government Standards you cannot use the Good Elliptic Curve ed25519 and instead you have to use a different, less well secured curve.)
Anyway what this means is that you have a significant conflict between the very high stakes and fast paced world of hospital medicine, and a system that wants you to log back in every time you step away from the x-ray machine.
Watching: Nothing.
Playing: As you may know if you're following me, I started Dark Souls this week. I am having a great time in Dark Souls! It's a lot of fun. I am still where I was yesterday, having just beaten the Belltower Gargoyles.
youtube
There are definitely notes that I have. It is for sure a 12 year old game. Some of the opacity is definitely intentional difficulty, like requiring you to just feel out the parry timing, but I it probably wouldn't make the game any easier if it had reliable indicators of when you're in position to backstab or riposte someone and it would make parrying much more fun. I like parrying but so often you parry someone and then just hit them normally instead of going for the cool finisher riposte.
Making: Like ten minutes ago I reopened Cinnabar and Calcite and did a little hardware swap, moving a new network card into Calcite and Calcite's old network card into Cinnabar. Everyone is settled back in. Wifi card upgrades are not really essential but it is nice to have wifi on a desktop even if you don't use it because a) someday you will and b) it's free bluetooth.
Also: Wrote some very bad bash to use my motherboard RGB as a tally light for recording these Dark Souls clips, since I've lost a few clips to hitting the wrong record button a few times.
Tools and Equipment: Original Tuesdayposter @girlfriendsofthegalaxy had a video on marinara sauce this last Tuesday and I was inspired to try some tomato pasta bakes. I usually make Mornay sauce based pasta bakes because it's what my parents usually made, but you gotta try a really spicy tomato pasta bake.
I got some habaneros and jalapenos from the farmers market and made a big pot of spicy tomato tuna bake and especially with the weather being How It Is that was great, I'm making a mushroom one sometime soon it kicked ass. That recipe was loosely based on this one, although I put in a bunch of extra vegetables.
11 notes
·
View notes
Text
>haven't been on moviestarplanet in years
>wonders what's going on with it
>there's a hacker installing malware onto peoples computers through an unlimited starcoins tool he created and is accessing people's personal pictures and files/passwords and asking 13 year olds for nudes
Oh
6 notes
·
View notes