#ramsomware attack
Explore tagged Tumblr posts
Text
Has your heart ever skipped a beat reading a headline about a ransomware attack? Have you ever wondered if your precious photos, crucial work documents, or even your entire system could be held hostage by malicious software? You're not alone. Ransomware attacks are a growing threat, targeting individuals and organizations alike, and the consequences can be devastating. But here's the good news: preventing ransomware attacks is largely within your control.
In this blog post, we’re going to dive deep into practical, actionable strategies that will help you secure your computer from ransomware, safeguarding your digital life. Get ready to empower yourself with knowledge and build a robust defense!
0 notes
Photo

Are you looking for a solution to protect your data and devices from malicious software? We have the best solution for you. Click here to know more about the product and get it today to prevent the entry of ransomware.visit us :http://bit.ly/2pTdJup
0 notes
Text
NO CONFIDENCE in DC:
The same Admin, deep state and Pentagon that just lost a 20 yr war to goat herders are directing our responses in Ukraine....that's serious cause for concern.By imposing a no-fly zone, supplying weapons and intel to Ukraine, conducting a propaganda war to isolate Russia and crippling the their economy with sanctions we have effectively declared war on Russia or at least that's how Russian will interpret it....so you can bet Russia is weighing up a retaliation. They can't sanction us but they could seize US corporate assets in Russia, they could shut off energy to Europe, they could go scorched earth in Ukraine.....an even more extreme though unlikely option would be to take out an American city, gambling that O'Biden doesn't have the backbone to excalate into a full blown world nuclear war...SO remember that ramsomware attack that happened on the East Coast 6 mths ago that our deep state blamed on Russia? if true that would suggest that they have the capability to hit us with a CYBER ATTACK on any number of things, banking, power grid etc....do you see how the grandstanding fools in DC are playing with fire by backing Putin into a corner ?
0 notes
Text
Ransomware Threat Response Services – Cybersecop

Cybercriminals have turned to ransomware as the latest go-to tool for attacking and extorting businesses using a wide range of variants such as Dharma, Wallet, WannaCry, Cryptowall, Samas, Locky, and TeslaCrypt. The outbreak of WannaCry was one of the largest and worst ransomware campaigns ever. Traditional signature-based antivirus and threat detection methods have proven to be woefully ineffective against such attacks.
Multiple ransomware strain are currently in the wild, we respond to at least 4 to 5 cases a week in ransomware related incidents. We help with settlement and 100% of the time get the ransom reduced. Attacker could cripple your business, not having the right team to help you remediate the ransomware and communicate with the attacker to get your data decrypted can lead to permanent data loss.
RANSOMWARE REMEDIATION, RANSOMWARE PREVENTION
We’ll diagnose and remediate the Ransomware Incident within a few hours, in most cases. We understand how important this is to your business.
Our cyber experts are brilliant at restoring your files, dealing with it yourself may can cause you to lose your files permanently.
Pay the Ransom - Paying criminals, a ransom doesn’t guarantee you’ll get your data back. If for some reason we can't recover you data, and has to pay the ransom, we will negotiate with the hacker to reduce ransom.
Ransomware Incident Digital Forensics - No matter what kind of data you need to work with, the experts at CyberSecOp Data Forensics will help you recover, reconstruct, and review the data. When you need data examined by court-tested forensic experts, you need CyberSecOP Forensics.
Ransomware Incident E-Discovery - We bridge the communication gap between the IT department and attorneys, pre-, during and post-trial, with your goals as our driving force. If you have a matter that requires technical expertise with a get-it-done attitude, call us right now.
Cybersecurity - Whether hackers have just broken into your network, or you've just discovered that a trusted employee has been stealing company data, the firm you decide on to remediate the situation is critical.
Expert Testimony - We have testified as computer forensics experts in Federal, State, and County Courts. Our work and reporting have been upheld by the courts as admissible and valid. If your case sees its day in court, our computer forensic findings are ready to stand up to intense technical scrutiny and the most grueling cross-examinations.
RANSOMWARE VIRUS REMOVAL, AND THREAT RESPONSE SERVICES
CyberSecOP Ransomware Endpoint protection that goes far beyond malware to effectively combat today’s threats. CyberSecOP Ramsomware Flash Detect antivirus brings machine learning and behavioral analytics to your endpoint protection. Protect against malware, ransomware, file-less attacks, and fill the gaps left by legacy antivirus solutions.
CyberSecOP Ransomware protection starts blocking at the attack’s initial entrance vector (e.g. phishing) and keeps blocking across the entire attack lifecycle including exploit installation/execution and the command and control phase.
Security teams today are overwhelmed with alerts from ineffective products that lack any context or prioritization of attacks; so they end up missing the real threats targeting their data. Our Analytics and Reporting Cloud quickly filter through potential anomalies and only triggers alarms for the high fidelity events that warrant additional investigation.
Source: https://cybersecop.com/ransomware-threat-response
#Cyber Security Consultant#cybersecurtiy consulting#it security services#Ransomware Services#cybersecurity services#cyber security consulting#managed security services#Managed Detection and Response#security assessment services
0 notes
Text
Ransomware Threat Response Services – Cybersecop

Cybercriminals have turned to ransomware as the latest go-to tool for attacking and extorting businesses using a wide range of variants such as Dharma, Wallet, WannaCry, Cryptowall, Samas, Locky, and TeslaCrypt. The outbreak of WannaCry was one of the largest and worst ransomware campaigns ever. Traditional signature-based antivirus and threat detection methods have proven to be woefully ineffective against such attacks.
Multiple ransomware strain are currently in the wild, we respond to at least 4 to 5 cases a week in ransomware related incidents. We help with settlement and 100% of the time get the ransom reduced. Attacker could cripple your business, not having the right team to help you remediate the ransomware and communicate with the attacker to get your data decrypted can lead to permanent data loss.
RANSOMWARE REMEDIATION, RANSOMWARE PREVENTION
We’ll diagnose and remediate the Ransomware Incident within a few hours, in most cases. We understand how important this is to your business.
Our cyber experts are brilliant at restoring your files, dealing with it yourself may can cause you to lose your files permanently.
Pay the Ransom - Paying criminals, a ransom doesn’t guarantee you’ll get your data back. If for some reason we can't recover you data, and has to pay the ransom, we will negotiate with the hacker to reduce ransom.
Ransomware Incident Digital Forensics - No matter what kind of data you need to work with, the experts at CyberSecOp Data Forensics will help you recover, reconstruct, and review the data. When you need data examined by court-tested forensic experts, you need CyberSecOP Forensics.
Ransomware Incident E-Discovery - We bridge the communication gap between the IT department and attorneys, pre-, during and post-trial, with your goals as our driving force. If you have a matter that requires technical expertise with a get-it-done attitude, call us right now.
Cybersecurity - Whether hackers have just broken into your network, or you've just discovered that a trusted employee has been stealing company data, the firm you decide on to remediate the situation is critical.
Expert Testimony - We have testified as computer forensics experts in Federal, State, and County Courts. Our work and reporting have been upheld by the courts as admissible and valid. If your case sees its day in court, our computer forensic findings are ready to stand up to intense technical scrutiny and the most grueling cross-examinations.
RANSOMWARE VIRUS REMOVAL, AND THREAT RESPONSE SERVICES
CyberSecOP Ransomware Endpoint protection that goes far beyond malware to effectively combat today’s threats. CyberSecOP Ramsomware Flash Detect antivirus brings machine learning and behavioral analytics to your endpoint protection. Protect against malware, ransomware, file-less attacks, and fill the gaps left by legacy antivirus solutions.
CyberSecOP Ransomware protection starts blocking at the attack’s initial entrance vector (e.g. phishing) and keeps blocking across the entire attack lifecycle including exploit installation/execution and the command and control phase.
Security teams today are overwhelmed with alerts from ineffective products that lack any context or prioritization of attacks; so they end up missing the real threats targeting their data. Our Analytics and Reporting Cloud quickly filter through potential anomalies and only triggers alarms for the high fidelity events that warrant additional investigation.
Source: https://cybersecop.com/ransomware-threat-response
#Cyber Security Services#cybersecurity consulting#it security services#managed security services#Managed Detection and Response#cybersecurity consultant#Ransomware Services#security assessment services
0 notes
Text
Ransomware Threat Response Services – Cybersecop

Cybercriminals have turned to ransomware as the latest go-to tool for attacking and extorting businesses using a wide range of variants such as Dharma, Wallet, WannaCry, Cryptowall, Samas, Locky, and TeslaCrypt. The outbreak of WannaCry was one of the largest and worst ransomware campaigns ever. Traditional signature-based antivirus and threat detection methods have proven to be woefully ineffective against such attacks.
Multiple ransomware strain are currently in the wild, we respond to at least 4 to 5 cases a week in ransomware related incidents. We help with settlement and 100% of the time get the ransom reduced. Attacker could cripple your business, not having the right team to help you remediate the ransomware and communicate with the attacker to get your data decrypted can lead to permanent data loss.
RANSOMWARE REMEDIATION, RANSOMWARE PREVENTION
We’ll diagnose and remediate the Ransomware Incident within a few hours, in most cases. We understand how important this is to your business.
Our cyber experts are brilliant at restoring your files, dealing with it yourself may can cause you to lose your files permanently.
Pay the Ransom - Paying criminals, a ransom doesn’t guarantee you’ll get your data back. If for some reason we can't recover you data, and has to pay the ransom, we will negotiate with the hacker to reduce ransom.
Ransomware Incident Digital Forensics - No matter what kind of data you need to work with, the experts at CyberSecOp Data Forensics will help you recover, reconstruct, and review the data. When you need data examined by court-tested forensic experts, you need CyberSecOP Forensics.
Ransomware Incident E-Discovery - We bridge the communication gap between the IT department and attorneys, pre-, during and post-trial, with your goals as our driving force. If you have a matter that requires technical expertise with a get-it-done attitude, call us right now.
Cybersecurity - Whether hackers have just broken into your network, or you've just discovered that a trusted employee has been stealing company data, the firm you decide on to remediate the situation is critical.
Expert Testimony - We have testified as computer forensics experts in Federal, State, and County Courts. Our work and reporting have been upheld by the courts as admissible and valid. If your case sees its day in court, our computer forensic findings are ready to stand up to intense technical scrutiny and the most grueling cross-examinations.
RANSOMWARE VIRUS REMOVAL, AND THREAT RESPONSE SERVICES
CyberSecOP Ransomware Endpoint protection that goes far beyond malware to effectively combat today’s threats. CyberSecOP Ramsomware Flash Detect antivirus brings machine learning and behavioral analytics to your endpoint protection. Protect against malware, ransomware, file-less attacks, and fill the gaps left by legacy antivirus solutions.
CyberSecOP Ransomware protection starts blocking at the attack’s initial entrance vector (e.g. phishing) and keeps blocking across the entire attack lifecycle including exploit installation/execution and the command and control phase.
Security teams today are overwhelmed with alerts from ineffective products that lack any context or prioritization of attacks; so they end up missing the real threats targeting their data. Our Analytics and Reporting Cloud quickly filter through potential anomalies and only triggers alarms for the high fidelity events that warrant additional investigation.
Source: https://cybersecop.com/ransomware-threat-response
#Cyber Security Services#Cyber Security Consultant#it security services#Managed Detection and Response#managed security services#Ransomware Services
0 notes
Text
15 Tips To Keep Your System Safe From Cyber Attacks

A month ago, i.e May of 2017 will be recalled always in history of digital security. A ransomware named 'WannaCry' surprised the world, Europe being the focal point of this greatest digital assault ever. WannaCry planned to assault frameworks through a helplessness in Windows OS. It was first found by NSA and later was uncovered by Shadow Brokers. In not many introductory hours, 200,000 frameworks were influenced, including those of associations like Renault and NHS.
What is a Ransomware?
Ransomware is a development sort of malware which obstructs the casualty from getting to his/her own framework. It's commonly a bit of code which comes as a connection in email in mask. When you click, it gets introduced in your framework and lock your entrance to it. To get back your entrance, you have to pay payment to the programmer who has focused on your framework.
The ransomware comes in 2 structures:
Encryptors: This sort of ramsomware joins a propelled sort of algorithmic key to your framework documents. To recover your entrance you need an unscrambling key which will unblock the substance of your framework. Storage spaces: Lockers lock down the working arrangement of the casualty's framework. It implies that you can't boot your framework once programmer has assaulted your framework with 'storage'. Here Digital Marketing Companies in Phoenix and there the storage is executed at MBR (Master Boot Record). The programmer requests recover sum to open the framework.
So how might you protect your framework from ransomware assaults?
Here a portion of the tips you ought to follow to protect your framework:
For neighborhood PC
Try not to store significant information just in My Documents and My PC Keep 2 reinforcements of information, in an outer drive and in cloud Open Goole Drive/Dropbox/One Drive and so forth. Just once per day to transfer and synchronize information and close them once done. Update your OS and different applications consistently alongside security patches For every day use, use 'client' account with constrained benefit rather than overseer account.
Read Also:- MOZCON: The best conference for SEO to attend in July 2020
Mood killer macros in MS Office suite and program
Expel modules like Adobe Flash, Adobe Reader, Java and silverlight when you needn't bother with them Alter your program's security and private settings for most extreme insurance Evacuate obsolete modules which are not being used any longer Use Digital Marketing Companies in Nashville promotion blocker to oppose pernicious advertisements
Online Behavior
Never open sends from obscure sources. Imprint them as spam
Never download connections from suspicious sends
Never click interfaces in suspicious sends
Security Tools
Utilize dependable and marked enemy of infection item which routinely gets refreshed consequently Utilize a decent traffic separating answer for master dynamic assurance against ransomware Anticipation is superior to fix. Follow the above tips, and surf online securely.
0 notes
Text
Android ransomware variant hoodwinks AV software by waiting 4 hours before striking
Android ransomware variant hoodwinks AV software by waiting 4 hours before striking
Publicado por SC Magazine
A newly discovered variant of the Android ransomware PornDroid eludes all antivirus programs by waiting four hours before executing its malicious activity as well as by employing heavy amounts of obfuscation
Despite these clever innovations, PornDroid lacks one core piece of functionality – it does not actually unlock victims’ screen after they pay up, according to Zscal…
View On WordPress
0 notes
Text
[Wk3] Hwk from Lecture
Prediction of a Data Breach between now and the end of the course
With the increasing prevalance of telehealth services I predict there will be a breach that will reveal people’s medical records or private health data. E.g. Government, Apple/Samsung Health platforms, Garmin, Strava etc
Prediction of something that seems bold, crazy but plausible
I predict that over the next, say, 2 years there will be another ramsomware attack, more serious than the previous ones. Along with revealing data and allowing attackers to gain control, it attracts attention and gets people scared. Technically speaking, it can be seen as an example of terrrorism perhaps?
Look into separation of powers
A: Look for examples of governments trying to undo separation of power
Aust encryption laws: government <->police/intelligence
Many countries that persecute whistle blowers: government ↔︎ media
Religions freedom debate: church ↔︎ state
B: Non-govt examples
Perhaps larger companies building an increasingly larger ecosystem of products - e.g. Google, Facebook, Amazon. Perhaps it’ll give them greater leverage over time.
C: How did Romans and Greeks do separation of powers?
Ancient political theorists recognised the effect of human nature on politics. People united due to weakness and fear. The strongest rose to the top.
Except from the article I read: As long as fear exists, people will cooperate and sympathize with one another, producing a stable society. Problems arise when members of a society lack the imaginative capacity to put themselves in the place of others. This results in the unsympathetic person practicing little, if any restraint and benefiting themselves at the expense of others.
Cycles of government - It is natural to begin pure and become corrupt
The 2nd generation often is a decline from the first: Monarchy → Tyranny, Aristocracy → Oligarchy, Democracy → Mob rule
Solution
The Romans had three parts of government - the Consuls, the Senate, and the Popular Assemblies
Checks and balances - each part had its own power, and would fear the other parts encroaching on that power → Stability
Fix outdated table
Intelligence agency
1024bit is susceptible to cracking, according to US Govt. documentation: https://arstechnica.com/information-technology/2013/09/of-course-nsa-can-crack-crypto-anyone-can-the-question-is-how-much/
2012 - Stricture Consulting Group - 25 GPU cluster
285bit password cracked by equivalent of small organisation
Using Amazon HPC p3.16xlarge:
$24.48 per hour for 8x Tesla V100 GPUs
0 notes
Link
What is Rabbit Ransomware? How to remove Rabbit Ransomware virus? Download free Ransomware removal tool to clean Bad Rabbit Ransomware Easily from your computer
0 notes
Photo
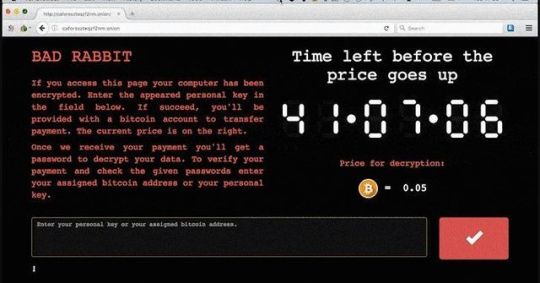
Beware! Bad Rabbit: New Ransomware Attack Rapidly Spreading Across Europe A new widespread ransomware attack is spreading like wildfire around Europe and has already affected over 200 major organisations, primarily in Russia, Ukraine, Turkey and Germany, in the past few hours. Dubbed "Bad Rabbit," is reportedly a new Petya-like targeted ransomware attack against corporate networks, demanding 0.05 bitcoin (~ $285) as ransom from victims to unlock their systems. http://thehackernews.com/2017/10/bad-rabbit-ransomware-attack.html #ramsomware #cybersecurity #badrabbit #ITSecurity #Security #hacker #hacked #hack #petya #adobe #FlashPlayer
0 notes
Text
Ramsomware Attacks: How To Protect Your Business
Ramsomware Attacks: How To Protect Your Business
Two weeks ago over 100 countries and thousands of computers were victimized by WannaCry, an aptly named ransomware, and a cruel reminder how important it is to protect computers, file servers, and other technology equipment.
Ransomware is a malicious software that first appeared around 2005, threatening to destroy people’s data if a ransom is not paid. It is just one type of “malware” (malicious…
View On WordPress
0 notes
Text
RANSOMWARE THREAT RESPONSE WITH CYBERSECOP
· Ongoing scanning services – a component of a vulnerability assessment program, you can be notified when a scan comes across out-of-date or unpatched software on your system.
· Network architecture review – a cyber engineering service that can evaluate and optimize or redesign and build your network to be more resilient to ransomware attacks.
· Paying the ransom – if you’re compromised, do you know how to obtain Bitcoin, setup a paying server on the dark web? If your risk management process points to paying a ransom, we can assist in this effort.
· Root cause analysis – digital forensics services can evaluate your environment to identify how your organization was compromised and provide remediation guidance or services to remove the identified vulnerability or vulnerabilities.
· Threat hunt operations – we can evaluate your network for hidden threats – ransomware that hasn’t executed, yet – or other indicators of compromise and presence of another malware.
· Training and awareness programs – training your staff to recognize social engineering / phishing attacks.

RANSOMWARE REMEDIATION, RANSOMWARE PREVENTION
· We’ll diagnose and remediate the Ransomware Incident within a few hours, in most cases. We understand how important this is to your business.
· Our cyber experts are brilliant at restoring your files, dealing with it yourself may can cause you to lose your files permanently.
· Pay the Ransom - Paying criminals, a ransom doesn’t guarantee you’ll get your data back. If for some reason we can't recover you data, and has to pay the ransom, we will negotiate with the hacker to reduce ransom.
· Ransomware Incident Digital Forensics - No matter what kind of data you need to work with, the experts at CyberSecOp Data Forensics will help you recover, reconstruct, and review the data. When you need data examined by court-tested forensic experts, you need CyberSecOP Forensics.
· Ransomware Incident E-Discovery - We bridge the communication gap between the IT department and attorneys, pre-, during and post-trial, with your goals as our driving force. If you have a matter that requires technical expertise with a get-it-done attitude, call us right now.
· Cybersecurity - Whether hackers have just broken into your network, or you've just discovered that a trusted employee has been stealing company data, the firm you decide on to remediate the situation is critical.
· Expert Testimony - We have testified as computer forensics experts in Federal, State, and County Courts. Our work and reporting have been upheld by the courts as admissible and valid. If your case sees its day in court, our computer forensic findings are ready to stand up to intense technical scrutiny and the most grueling cross-examinations.
RANSOMWARE VIRUS REMOVAL, AND THREAT RESPONSE SERVICES
· CyberSecOP Ransomware Endpoint protection that goes far beyond malware to effectively combat today’s threats. CyberSecOP Ramsomware Flash Detect antivirus brings machine learning and behavioral analytics to your endpoint protection. Protect against malware, ransomware, file-less attacks, and fill the gaps left by legacy antivirus solutions.
· CyberSecOP Ransomware protection starts blocking at the attack’s initial entrance vector (e.g. phishing) and keeps blocking across the entire attack lifecycle including exploit installation/execution and the command and control phase.
· Security teams today are overwhelmed with alerts from ineffective products that lack any context or prioritization of attacks; so they end up missing the real threats targeting their data. Our Analytics and Reporting Cloud quickly filter through potential anomalies and only triggers alarms for the high fidelity events that warrant additional investigation.
Source: https://cybersecop.com/ransomware-threat-response
0 notes
Text
RANSOMWARE THREAT RESPONSE WITH CYBERSECOP
Cybercriminals have turned to ransomware as the latest go-to tool for attacking and extorting businesses using a wide range of variants such as Dharma, Wallet, WannaCry, Cryptowall, Samas, Locky, and TeslaCrypt. The outbreak of WannaCry was one of the largest and worst ransomware campaigns ever. Traditional signature-based antivirus and threat detection methods have proven to be woefully ineffective against such attacks.

Ongoing scanning services – a component of a vulnerability assessment program, you can be notified when a scan comes across out-of-date or unpatched software on your system.
Network architecture review – a cyber engineering service that can evaluate and optimize or redesign and build your network to be more resilient to ransomware attacks.
Paying the ransom – if you’re compromised, do you know how to obtain Bitcoin, setup a paying server on the dark web? If your risk management process points to paying a ransom, we can assist in this effort.
Root cause analysis – digital forensics services can evaluate your environment to identify how your organization was compromised and provide remediation guidance or services to remove the identified vulnerability or vulnerabilities.
Threat hunt operations – we can evaluate your network for hidden threats – ransomware that hasn’t executed, yet – or other indicators of compromise and presence of another malware.
Training and awareness programs – training your staff to recognize social engineering / phishing attacks.
RANSOMWARE REMEDIATION, RANSOMWARE PREVENTION
We’ll diagnose and remediate the Ransomware Incident within a few hours, in most cases. We understand how important this is to your business.
Our cyber experts are brilliant at restoring your files, dealing with it yourself may can cause you to lose your files permanently.
Pay the Ransom - Paying criminals, a ransom doesn’t guarantee you’ll get your data back. If for some reason we can't recover you data, and has to pay the ransom, we will negotiate with the hacker to reduce ransom.
Ransomware Incident Digital Forensics - No matter what kind of data you need to work with, the experts at CyberSecOp Data Forensics will help you recover, reconstruct, and review the data. When you need data examined by court-tested forensic experts, you need CyberSecOP Forensics.
Ransomware Incident E-Discovery - We bridge the communication gap between the IT department and attorneys, pre-, during and post-trial, with your goals as our driving force. If you have a matter that requires technical expertise with a get-it-done attitude, call us right now.
Cybersecurity - Whether hackers have just broken into your network, or you've just discovered that a trusted employee has been stealing company data, the firm you decide on to remediate the situation is critical.
Expert Testimony - We have testified as computer forensics experts in Federal, State, and County Courts. Our work and reporting have been upheld by the courts as admissible and valid. If your case sees its day in court, our computer forensic findings are ready to stand up to intense technical scrutiny and the most grueling cross-examinations.
RANSOMWARE VIRUS REMOVAL, AND THREAT RESPONSE SERVICES
CyberSecOP Ransomware Endpoint protection that goes far beyond malware to effectively combat today’s threats. CyberSecOP Ramsomware Flash Detect antivirus brings machine learning and behavioral analytics to your endpoint protection. Protect against malware, ransomware, file-less attacks, and fill the gaps left by legacy antivirus solutions.
CyberSecOP Ransomware protection starts blocking at the attack’s initial entrance vector (e.g. phishing) and keeps blocking across the entire attack lifecycle including exploit installation/execution and the command and control phase.
Security teams today are overwhelmed with alerts from ineffective products that lack any context or prioritization of attacks; so they end up missing the real threats targeting their data. Our Analytics and Reporting Cloud quickly filter through potential anomalies and only triggers alarms for the high fidelity events that warrant additional investigation.
Source:
https://cybersecop.com/ransomware-threat-response
0 notes
Text
RANSOMWARE THREAT RESPONSE WITH CYBERSECOP

· Ongoing scanning services – a component of a vulnerability assessment program, you can be notified when a scan comes across out-of-date or unpatched software on your system.
· Network architecture review – a cyber engineering service that can evaluate and optimize or redesign and build your network to be more resilient to ransomware attacks.
· Paying the ransom – if you’re compromised, do you know how to obtain Bitcoin, setup a paying server on the dark web? If your risk management process points to paying a ransom, we can assist in this effort.
· Root cause analysis – digital forensics services can evaluate your environment to identify how your organization was compromised and provide remediation guidance or services to remove the identified vulnerability or vulnerabilities.
· Threat hunt operations – we can evaluate your network for hidden threats – ransomware that hasn’t executed, yet – or other indicators of compromise and presence of another malware.
· Training and awareness programs – training your staff to recognize social engineering / phishing attacks.
RANSOMWARE REMEDIATION, RANSOMWARE PREVENTION
· We’ll diagnose and remediate the Ransomware Incident within a few hours, in most cases. We understand how important this is to your business.
· Our cyber experts are brilliant at restoring your files, dealing with it yourself may can cause you to lose your files permanently.
· Pay the Ransom - Paying criminals, a ransom doesn’t guarantee you’ll get your data back. If for some reason we can't recover you data, and has to pay the ransom, we will negotiate with the hacker to reduce ransom.
· Ransomware Incident Digital Forensics - No matter what kind of data you need to work with, the experts at CyberSecOp Data Forensics will help you recover, reconstruct, and review the data. When you need data examined by court-tested forensic experts, you need CyberSecOP Forensics.
· Ransomware Incident E-Discovery - We bridge the communication gap between the IT department and attorneys, pre-, during and post-trial, with your goals as our driving force. If you have a matter that requires technical expertise with a get-it-done attitude, call us right now.
· Cybersecurity - Whether hackers have just broken into your network, or you've just discovered that a trusted employee has been stealing company data, the firm you decide on to remediate the situation is critical.
· Expert Testimony - We have testified as computer forensics experts in Federal, State, and County Courts. Our work and reporting have been upheld by the courts as admissible and valid. If your case sees its day in court, our computer forensic findings are ready to stand up to intense technical scrutiny and the most grueling cross-examinations.
RANSOMWARE VIRUS REMOVAL, AND THREAT RESPONSE SERVICES
· CyberSecOP Ransomware Endpoint protection that goes far beyond malware to effectively combat today’s threats. CyberSecOP Ramsomware Flash Detect antivirus brings machine learning and behavioral analytics to your endpoint protection. Protect against malware, ransomware, file-less attacks, and fill the gaps left by legacy antivirus solutions.
· CyberSecOP Ransomware protection starts blocking at the attack’s initial entrance vector (e.g. phishing) and keeps blocking across the entire attack lifecycle including exploit installation/execution and the command and control phase.
· Security teams today are overwhelmed with alerts from ineffective products that lack any context or prioritization of attacks; so they end up missing the real threats targeting their data. Our Analytics and Reporting Cloud quickly filter through potential anomalies and only triggers alarms for the high fidelity events that warrant additional investigation.
Source: https://cybersecop.com/ransomware-threat-response
0 notes
Text
WannaCry ramsomware is appearing in obscure places after global cyber attack | WannaCry
As security researchers investigate last Friday's massive attack from the WannaCry ransomware, they've noticed clues that may link it with a North Korean hacking group that has been blamed for attacking banks across the world. A massive cyberattack hit the world on Friday, May 12, United States time, affecting 200,000 computers in 150 countries - and counting. Security researchers have found digital clues in the malware used in last weekend's global ransomware attack that might indicate North Korea is involved, although they caution the evidence is not conclusive. As governments around the world grapple with the fallout from the appositely named malware WannaCry, insurers will be weeping with joy.
Washington: Cyber security researchers have found technical clues they said could link North Korea with the global WannaCry ransomware cyber attack that has infected more than 300,000 machines in 150 countries since Friday. The impact of the attack, using a virus known as 'WannaCry', appears limited in the United States so far, although security analysts fear that could change in the coming days. But Scott Vernick, a data security lawyer at Fox Rothschild that represents companies, said he was skeptical that WannaCry would produce a flood of consumer lawsuits.
0 notes