#red state flag code violations
Explore tagged Tumblr posts
Text





I passed this trio of flags a lot on the walk from our hotel to the convention center, where I found myself on most days, and while I am actually a fan of the conical flagpoles--not something you see every day--it drove me crazy that the Texas and Dallas flags were at the same height as the American flag. I’m not one of those people who obsess over the flag, but as someone who would hold flags in the marching band during parades, I was keenly aware that I needed to keep the state flag lower than the American flag at all times. Maybe they’ve made edits to the Flag Code since then, but I also find it funny that the Texas flag is definitely bigger than the United States flag here, but I guess that’s what happens when you go to Dallas.
In the bottom photo you can clearly see that the Texas flag is bigger, and that cracks me up so much.
We’re going back to Texas next week, so I’m curious to ask my friends who live there if the bigger TX flag is A Thing in Austin as well as Dallas--more to come on this.
0 notes
Text
Kink Education Time - Consent
So, everyone knows that consent is incredibly important in kink. It's incredibly important everywhere, but especially when one wrong move means a consent violation. But kink often involves pretending to violate consent (CNC). So, how do you navigate consent in kink in the safest and most knowledgeable way possible? The answer lies in two things. First, safewords and other safety items. You probably know about safewords, but what about drop items, or other ways of communicating consent? The second category is less commonly-known: consent acronyms.
Safewords & Safety Items
Safewords are basically flags that you can raise that inform your partner(s) about your current state in the scene. The most obvious benefit to using safewords is that, plainly, a play partner can scream, "no, please, stop, leave me alone", without ending the scene. Meanwhile, they can just say, for example, "Pineapple!" to end the scene at any time. Usually, there are three categories: Green, Yellow, and Red.
Green safewords are meant to mean "everything is all good; please continue". This category isn't really used unless one partner wants to check in on the other partner. An example would be that, during a spanking scene, the giving partner notices that the receiving partner is crying. They may ask, "Are you okay?" They may also use a pre-negotiated term to check in, such as a code word. At which point, the receiving partner may respond with their green safeword if they're doing fine and want to proceed.
Yellow safewords are used to caution the other participant(s) in the scene. Their basic meaning is, "Hey, I'm doing mostly okay right now, but we're close to my limit. Please be careful." To some people, yellow means "do not do anything more than what you're doing right now". To others, yellow means "keep going, do what you wanted to, but I may need to use red soon". It can even mean "I'd like to talk to you about this, can we pause for a minute?" It is absolutely vital for both partners to know what yellow safewords mean before play begins.
Red safewords are the ultimate safeguard. Red means "stop". No questions, no exceptions. If you are doing a kind of play that can't be stopped right away (such as rope suspension), you must begin the process of stopping play. In some cases, that means taking drastic measures. In the case of rope suspension, that can even mean cutting the rope away from them immediately. Red safewords must be obeyed at all costs. Refusing to honor a red safeword is sexual assault. Always be mindful of your partner's red safewords in particular.
It should also be noted that safewords are not just for the receiving partner. Everyone gets safewords, and everyone can use them at any time, for any reason. It's important to know what someone's safewords are before play begins, so you can recognize them when you hear them. However, a commonly-used set of safewords is the stoplight system ("red" for red, "yellow" for yellow, "green" for green). Usually, in most cases, using those safewords is absolutely fine, and no other words are needed.
Safety Items/Nonverbal Safewords
Safewords are all well and good. But what if the person is gagged? How do you safeword with a dildo gag shoved down your throat? These are important considerations for any play. You can have many different nonverbal safewords,as long as they're discussed with your partner beforehand. It could be a hand signal, or three claps, or a little red card in their hand. Another commonly-used solution is what's called a "drop item". The person is given something heavy to hold, like a book, that they can drop if they need a check-in. If you're doing a form of play that prevents someone from talking, ALWAYS have nonverbal safewords in place.
Consent Acronyms
This section is more about what consent can actually mean in kink. Typically, people subscribe to one of four "ideologies" when it comes to consent: SSC, PRICK, FRIES, or RACK. Other acronyms exist, but these are the most common. The basic idea behind any consent acronym is to get you to think about what actually goes into consent, and how someone can say "yes" to something WITHOUT actually consenting. Understanding these acronyms is a great way to prevent your own consent from being violated, as well as to prevent violating others' consent, even without your awareness. I'll be explaining each of those four acronyms below in brief detail, but I highly recommend that you research consent acronyms yourself.
SSC - Safe, Sane, and Consensual
SSC is the most common, and "basic" acronym. The guiding principle of this acronym is that, in order for something to be consensual, the act must be safe, sane, and consented to by both parties. This means that you must take all necessary precautions (such as safewords, safety shears, etc.), you must both be of sound minds, and you must both give express consent before play begins. Some complaints about this acronym are about the "safe" and "sane" portions, because kink inherently has risks (making it unsafe from the start), and some kinks could be considered "insane" (like flesh hooks or branding).
PRICK - Personal Responsibility In Consensual Kink
Some people prefer PRICK for its acknowledgement that kink can be dangerous. The basic idea of PRICK is that everyone has a responsibility to learn how to go about their kink lives as safely as possible. This also includes educating yourself on consent, in all its aspects, and how to respect it at all times.
RACK - Risk-Aware Consensual Kink
RACK is similar to PRICK in that it emphasizes knowing the risks to all parties inherent in your play. This includes all mental, social, physical, psychological, and/or sexual risks. The idea behind this acronym is that, unless you're aware of all of the risks, no play is truly consensual.
FRIES - Freely-given, Reversible, Informed, Enthusiastic, and Specific
FRIES refers to the act of giving consent itself. This ideology argues that nothing is consensual unless it matches those 5 criteria. This acronym was pioneered by Planned Parenthood, and is a favorite amongst kinksters. The idea is that unless consent is 1) given freely (under no coercion or force), 2) reversible (able to be rescinded at any time for any reason), 3) informed (such as with RACK or PRICK), 4) enthusiastic (basically just not reluctant; you can also just do kink because you're fine with it, not because you're absolutely thrilled to do it), and 5) specific (as in you are made aware of all acts that could happen beforehand for you to specifically consent to).
You may notice that these ideologies can coexist. They should. A truly responsible and safe kinkster will consider all of these when playing. They all have very valuable messages that you should internalize and keep in mind during your play. If anyone has any other consent acronyms they'd like to share, please do so in the reblogs/replies!
#kink education time#kink education#bd/sm community#bd/sm daddy#bd/sm kink#r4p3 threats#bd/sm brat#kink writing#cnc somno#bd/sm pet#free use kink#kink story
195 notes
·
View notes
Text
So, I'm trying to start an Instagram to share my cosplay.
30 April, 1:30pm, I establish the account. This is about the time I get an email code to input to verify I am creating it.
Same day, 30 April, 7:30pm, I get an email stating I've violated community guidelines in someway and my account was disabled.
The only things I've done are to put up a profile picture and post a short bio explaining what the account is for.
I didn't notice this 7:30pm email until yesterday when I attempted to access instagram and it said my account was disabled.
I'm currently attempting to appeal - I successfully had a code sent to whatsapp and put that in. Then it asked for a selfie, which I also took and sent. Now I am waiting.
As there is nothing on the account I am not losing anything.
However, I'm extremely concerned and suspicious that only 6 hours after creating it, their automated system is attacking it.
I'm also extremely concerned for the existence of my Facebook, which Meta also owns. I rarely use it nowadays, and have not attempted to access it in the meantime. More than anything, I at least want to preserve my Facebook to download all the content and contacts.
I have several avenues of approach if this attempt somehow doesn't work out. I hope it works.
This is also a notice to all of you: if you have any social media (tumblr, Facebook, instagram, youtube, Twitter, etc), buy hard disk space and download a full copy. Save your content and craft a pinned public post that states your intent to never delete your stuff, and where to find you if it disappears (whether that's a newly created 'version2' or some other social media).
Poorly run social media engines are being overrun by bots and faulty automation and no longer have humans running them. Or they want you to pay. In order to preserve your own history, contacts, friendship, and even businesses, you need to keep personal data on all of that AND give people a way to find you if you suddenly vanish.
Unfortunately, most things - emails, phone numbers, social medias - are very very fragile when they shouldn't be.
When I recover my empty instagram, my first step will be to delete it. My second, to obtain a safety email account, unconnected to what I used for Facebook. And I will recreate it with that. I don't want a faulty red flag on one account to damage my access to another. It's sad that I have to do this. But personal security and safety require it when social medias start to be bought up by one company and overrun by AI bots.
If anyone has any advice, feel free to drop it below, send me a DM, or whatever.
11 notes
·
View notes
Text
Long tangent about the United States, older generations, and conservatives (nothing too controversial)
I find it fascinating how in America, older generations and conservatives complain about people disrespecting the flag despite they themselves violating the code every Memorial Day, Flag Day, Independence Day, Labor Day, and Veteran's Day by wearing tacky t shirts from like Walmart that has an American flag on it or wearing a shirt that's designed to look like the flag. The US flag code states "(d) The flag should never be used as wearing apparel, bedding, or drapery. It should never be festooned, drawn back, nor up, in folds, but always allowed to fall free. Bunting of blue, white, and red, always arranged with the blue above, the white in the middle, and the red below, should be used for covering a speaker’s desk, draping the front of the platform, and for decoration in general." (source: “4 U.S. Code § 8 - Respect for Flag.” Legal Information Institute, Legal Information Institute, www.law.cornell.edu/uscode/text/4/8. Accessed 28 May 2025.). I just remembered the other day on Memorial Day one of the residents at my job (for context, he's a Republican and Trump supporter) had on an American flag shirt reminiscent of Abbie Hoffman, even though, I'm probably wrong about this, Hoffman was very against the Vietnam War and his entire platform was hardcore liberal. I'm not offended by this since why should I care what this 80 something year old wears, however I just find it really odd how these kinds of people jack themselves off about being uber nationalist (there is a difference between patriotism (being prideful in your country) and nationalism (thinking your country is superior to everyone else. I'm going off what I remember from the history classes I had ages ago) and then claim they're being patriotic while violating flag code
7 notes
·
View notes
Text

How Minneapolis Business Brokers Help in Evaluating Business Risks
Selling or buying a business in Minneapolis isn’t just a financial transaction—it’s a strategic decision with risks that can have long-lasting consequences. Whether you're preparing to exit your business or looking to invest in one, identifying and evaluating risks is a critical step that should never be overlooked. That’s where Minneapolis business brokers come in.
Experienced business brokers do much more than match buyers and sellers—they serve as advisors who assess, uncover, and help mitigate risks throughout the deal process. In this article, we’ll explore how Minneapolis business brokers help evaluate business risks and ensure smarter, safer transactions for all parties involved.
1. Assessing Financial Health and Stability
One of the primary areas of risk in any business transaction is the financial stability of the company. Minneapolis business brokers dig deep into the financials—reviewing profit and loss statements, tax returns, balance sheets, and cash flow records over several years.
They look for red flags such as:
Inconsistent revenue patterns
Poor profit margins
High debt levels
Unexplained expenses or write-offs
By analyzing these documents, brokers can help sellers understand what potential buyers will see—and help buyers recognize if the numbers support the asking price.
2. Analyzing Industry Trends and Market Conditions
Business risk isn't limited to internal finances. A company’s viability is also affected by external conditions such as industry trends, economic cycles, and local market dynamics. Business brokers in Minneapolis are familiar with regional trends in industries like healthcare, tech, food service, and professional services.
They can evaluate:
Whether the business operates in a growing or declining sector
How changing regulations could impact operations
The level of market saturation or new competitors
Seasonal and economic vulnerabilities
This market intelligence helps both buyers and sellers make informed decisions based on what’s happening now and what may lie ahead.
3. Identifying Operational and Structural Weaknesses
Operational inefficiencies can be a major risk that reduces a business's value or scares off buyers. Minneapolis brokers often conduct or coordinate operational assessments to evaluate:
Staffing levels and training
Supply chain reliability
Customer retention rates
Technology systems and automation
Internal processes and documentation
If a business is too dependent on the owner, has unorganized records, or lacks formalized processes, these are red flags. Brokers help sellers address these issues before going to market and guide buyers to ask the right questions during due diligence.
4. Evaluating Lease Agreements and Real Estate Risks
If the business leases its premises, the terms of the lease can present significant risks. For example, short-term leases, unfavorable renewal options, or transfer restrictions can complicate a sale.
Minneapolis business brokers work closely with commercial real estate professionals to:
Review lease terms and landlord obligations
Analyze location risk (i.e., gentrifying neighborhoods, upcoming developments)
Determine whether the lease is transferable or requires renegotiation
These insights help ensure buyers are not surprised by sudden rent hikes or relocation risks, and sellers know how lease terms impact their business’s appeal.
5. Checking for Legal and Regulatory Compliance
Legal risk is another area where business brokers play an important role. Brokers help evaluate whether the business complies with state and federal regulations—including licenses, permits, health codes, employment laws, and tax obligations.
In Minneapolis, certain industries like cannabis retail, healthcare, or childcare come with heightened regulatory scrutiny. Business brokers ensure due diligence includes:
Verification of business licenses
Review of any pending legal actions or past violations
Confirmation that employee classification (W-2 vs. 1099) is compliant
Ensuring zoning and use regulations align with operations
Legal compliance reduces the chance of future lawsuits or fines, protecting the buyer’s investment and the seller’s reputation.
6. Reviewing Customer and Supplier Contracts
Customer and supplier relationships can make or break a business. A business with long-term contracts, repeat customers, or exclusive vendor deals typically holds more value and less risk than one with inconsistent revenue sources.
Business brokers review:
Terms and transferability of customer contracts
Length and exclusivity of supplier agreements
Concentration risk (e.g., one customer makes up 70% of revenue)
Whether existing contracts will remain valid after the sale
This analysis helps buyers understand future revenue reliability and warns sellers of areas that could lower perceived value.
7. Analyzing Employee and Staffing Risk
Employees are one of a business’s most important assets—but also a potential liability. High employee turnover, lack of documented HR policies, or dependence on a few key individuals can all create uncertainty for a buyer.
Minneapolis business brokers help assess:
Staff retention and satisfaction
Roles and responsibilities of key team members
Whether employment contracts or non-competes are in place
Risks related to wages, benefits, or pending labor disputes
This gives both parties insight into the business’s operational stability and potential disruptions during or after a transition.
8. Valuation Risk: Is the Asking Price Realistic?
Overvaluing a business is one of the biggest risks sellers face—it leads to prolonged time on the market and fewer serious buyers. Undervaluing can result in leaving money on the table. Business brokers bring objective valuation methods to ensure pricing is accurate and market-driven.
They often use a combination of:
Earnings Multiples (SDE or EBITDA)
Asset-Based Valuation
Market Comparisons
Discounted Cash Flow Models
A proper valuation helps buyers feel confident they're paying a fair price and gives sellers leverage in negotiations backed by data—not emotion.
9. Negotiation Risk Management
Deals often fall apart during negotiation due to unclear expectations, poor communication, or misunderstanding deal terms. A business broker serves as a neutral third party to:
Set realistic expectations for both sides
Help structure the deal (e.g., earn-outs, seller financing, non-compete agreements)
Manage emotions and prevent small disputes from derailing the sale
With a broker’s guidance, both parties are more likely to walk away with a mutually beneficial agreement and fewer post-sale surprises.
10. Due Diligence Support
The due diligence phase is where many risks are discovered. Business brokers help coordinate this phase by ensuring the seller provides the required documents and the buyer knows what to look for. This may include:
Tax returns and financial statements
Vendor and customer contracts
Employee records
Inventory lists and equipment appraisals
Licenses and permits
Their involvement keeps the process organized, transparent, and moving forward—greatly reducing the chance of delays or failed transactions.
youtube
Risk Management Is Smart Business
Buying or selling a business is a high-stakes decision filled with potential pitfalls. Minneapolis business brokers are not just facilitators—they’re risk managers, negotiators, and strategic advisors. They protect your interests by identifying threats, preparing risk mitigation plans, and guiding you through complex evaluations.
Whether you’re a business owner planning your exit or a buyer looking to invest in the Minneapolis market, working with a seasoned business broker can be the difference between a smart, successful transaction and an expensive mistake.
Don’t go it alone. Let an experienced Minneapolis business broker help you evaluate—and manage—the risks so you can move forward with clarity and confidence.
#business broker minneapolis#business broker near me#sell my business minneapolis#what is my company worth#best minneapolis business broker#buy a company minneapolis#what is my company worth minneapolis#Youtube
0 notes
Text
Trump Deploys National Guard & Marines to L.A. — Without the Insurrection Act
A constitutional crisis in plain sight
In June 2025, President Trump ordered the deployment of over 4,000 federalized National Guard troops and 700 Marines into Los Angeles to respond to immigration protests and so-called sanctuary resistance.
But here’s what makes this historic and deeply troubling:
He did it without invoking the Insurrection Act—and against the will of California’s governor. That combination of unchecked executive action has set off alarms across the legal and military communities.
⸻
Why This Should Terrify Everyone
1. The 10th Amendment Was Ignored
The 10th Amendment gives states power over internal matters not assigned to the federal government—including control over their own National Guard. Normally, a president can only federalize a state’s Guard with the governor’s consent, unless the state is in full rebellion.
Governor Newsom explicitly rejected Trump’s action—and yet Trump seized control anyway. This is a direct attack on state sovereignty and the balance of powers built into the Constitution.
⸻
2. He Used Title 10, But Skipped the Insurrection Act (And That’s a Big Problem)

Trump cited 10 U.S. Code § 12406 to federalize the National Guard, claiming the state was not enforcing immigration law adequately. But he did not invoke the Insurrection Act, which is the only legal pathway for deploying federal troops—like active-duty Marines—for domestic enforcement.
Here’s why that matters:
🔸 Under the Posse Comitatus Act (18 U.S. Code § 1385), federal military forces—like the Army, Navy, Air Force, and Marines—cannot be used for domestic law enforcement unless authorized by law.
🔸 The only law that allows this is the Insurrection Act (10 U.S. Code §§ 251–255). It must be formally invoked and justified in writing.
Trump didn’t do that.
Yet, Marines were deployed in Los Angeles to support operations near protests, under the justification of “protecting federal buildings.” This makes their presence legally questionable and constitutionally dangerous.
Even “non-enforcement” roles—like guarding property—can still be considered an unlawful “show of force” if they intimidate civilians or suppress protest rights. Courts have recognized this distinction in past rulings.
⚠️ In short:
You cannot deploy active-duty Marines on American streets unless you formally declare a legal emergency. Trump didn’t.
That makes this more than political theater—it’s a breach of the legal firewall between military and civilian life, and potentially a violation of federal law.
And here’s where the historical irony comes in:
Past presidents have used the Insurrection Act—with full transparency—when conditions truly warranted it:
• Eisenhower used it to desegregate schools in Little Rock.
• George H.W. Bush used it during the 1992 L.A. riots.
• Even George Washington used federal forces during the Whiskey Rebellion.
They followed the law—even when the politics were hard.
Trump didn’t.
Why? Maybe because the Insurrection Act requires documentation, justification, and oversight.
And if there’s one thing Trump avoids, it’s legal process and accountability.
That’s not leadership.
That’s dictator behavior—bypassing legal structures to do what he wants, when he wants, no matter the cost.
⸻
“They’re Just Protecting Federal Buildings”?
One common defense is: “They’re only there to protect federal property.”
But even this raises red flags.
🔸 Under the Posse Comitatus Act, military troops cannot engage in domestic law enforcement unless the Insurrection Act is invoked.
🔸 Simply stationing troops in protest-heavy civilian zones is often viewed as a “show of force”—which courts have said can be illegal if it chills public expression or suppresses dissent.
As one veteran put it:
“I am deeply concerned about a president clearing a path through peaceful protesters for a photo-op… The U.S. military should never be used to violate the constitutional rights of fellow citizens.” -Admiral Mike Mullen (former Chairman of the Joint Chiefs of Staff)
⸻
Service Members Are Now at Risk
This isn’t just a constitutional crisis. It’s a legal trap for the very troops being deployed.
Under the Uniform Code of Military Justice (UCMJ):
• Article 90: Makes it a crime to disobey a lawful order.
• Article 92: Makes it a crime to obey an unlawful order.
That means if these troops believe the order to deploy without proper legal authority is unconstitutional, they could be punished for following it—or for refusing it. They are now caught in a no-win scenario.
“Just following orders” is not a defense if the order is found unlawful.
⸻
Real People Are Asking the Right Questions
From online comments and veterans’ groups to constitutional scholars, Americans are sounding the alarm. Here are just a few questions people are raising:
1. Isn’t it illegal to use the military against civilians?
Yes—unless the Insurrection Act is invoked. It wasn’t.
2. How is immigration enforcement a rebellion?
It’s not. California was enforcing its laws. There was no uprising.
3. Can a president override a governor like this?
Not without extraordinary legal cause. Trump’s action is unprecedented.
4. Where was this urgency on January 6?
Trump refused to send in the National Guard when the Capitol was under attack—but is quick to send them now over peaceful protests?
5. Are these troops protecting property, or threatening people?
Without accountability, their presence functions as intimidation—not protection.
6. What if Biden did this to Texas?
Imagine the outrage. That’s the constitutional test: would your stance change if the roles were reversed?
⸻
What’s Really at Stake
This isn’t just about immigration. It’s about:
• Executive overreach
• Undermining federalism
• Militarizing domestic policy
• And putting American troops and civilians in harm’s way—legally and morally
This moment isn’t politics as usual.
It’s the creeping edge of authoritarianism dressed up as national security.
⸻
Final Thought
Trump bypassed the legal path, ignored state sovereignty, and placed troops in the streets without constitutional authority—all while skipping the one law that could’ve made it legal: the Insurrection Act.
Why?
Because that law comes with guardrails. With transparency. With limits.
And Trump has shown—time and time again—that he prefers power without limits.
This isn’t strength.
It’s a stress test of democracy. And if we let it slide, the next test may not come with a warning.
#10thAmendment#posse comitatus act#InsurrectionAct#rule of law#ucmj#NationalGuard#us marines#MilitaryEthics#VeteransSpeakOut#HonorTheOath#MilitaryLaw#TrumpOverreach#WeThePeople#KnowYourRights#HoldThemAccountable
0 notes
Text
How do I choose the right LED lights for my car online?
Choosing the right LED headlights for your vehicle online requires careful consideration of compatibility, safety, and performance. Follow this step-by-step guide to avoid glare, error codes, or wasted money:
🔍 Step 1: Verify Compatibility Match Bulb Type
Check your owner's manual or current bulbs for exact bulb model size (e.g., H11 low beam, 9005 high beam).
Use vehicle-specific databases:
https://www.usa.philips.com/c-m-au/car-lights Confirm Headlight Housing
Projector Housing: Best for LEDs (sharper cutoff).
Reflector Housing: Risk of glare/violations - avoid unless LED bulb has adjustable light pattern.
💡 Step 2: Prioritize key features Function Importance Focus Power driver Intelligent IC led driver Intelligently regulates current to avoid overcurrent in electronic components and LED chips Beam pattern ⚠️ Prevents traffic dazzle “DOT/ECE certified” • TUV certified (e.g. Philips Ultinon, SNGL) Heat dissipation Prevents LED overheating → fast failure Copper tube copper base plate + aluminum heat sink + fan • Avoid cheap “fanless” brands EMC shielding Prevents radio/TPMS interference “CANbus ready” • Built-in decoder for error-free installation Color temperature 5000K–6000K = pure white • Greater than 7000K reduces visibility in rainy days Stick to 5500K (ideal for road lighting) Lumens and Lux Higher ≠ better • Focus is critical ≥12000 lumens with beam certification
🛠️ Steps 3: Compare quality brands Brand Best for professionals Price range (pair) Philips Ultinon Reliability and compliance TUV certified • Excellent beam focus 90–220 SNGL dimmable LED bulbs Minimal glare and no dark areas CE and TUV certified • Plug and play 70–180 Diode Dynamics High output/off-road use Sturdy heat sink • 5-year warranty 100–300
🚫 Avoid: No-name brands lacking safety certifications (e.g. “Xenopro”, “HIKARI Ultra”).
⚠️ Step 4: Check reviews and verify Note:
Beam cutoff photos in reviews (clear lines = no glare).
“No flicker/CANbus errors” in specific vehicle reviews.
Professional testing (e.g. https://www.headlightrevolution.com/ beam comparison).
Red flags:
“Brightness is high, but beam is scattered everywhere.”
“Fan broke after 3 months of use.”
📜 Step 5: Understand the law and warranty Legality:
US: DOT compliant ≠ reflector housing legal. Check state laws.
EU/UK: Only LEDs with the E logo in original LED/HID projectors are legal.
Warranty: Minimum 2-year warranty for peace of mind.
🔧 Installation preparation Must-have accessories:
Anti-flicker decoder for modern cars with CANbus.
Rubber dust cover extender for lamp gap.
Tools needed: Trim removal tool • Torx screwdriver set.
Time: About 30-60 minutes per side for beginners.
💎 Final checklist before buying Does the bulb model size exactly match the original bulb model size?
Is it DOT/ECE certified with beam cutoff?
Is it using a combination of copper tubes + copper base plate + aluminum heat sink + fan?
Is there an intelligent IC led driver?
Is a CANbus decoding system included?
Warranty period ≥ 2 years?
📌 Pro Tip: For reflective housings, it is safer to replace with LED lamps with adjustable light patterns. The conversion cost is more than $130, but it can guarantee legal high-performance lighting.
Summary: Prioritize certified beam focusing effects rather than brightness claims. Invest in brands such as Philips/SNGL to avoid glare, errors and replacements. If in doubt, consult a professional installer - improper LED upgrades can endanger the safety of others and result in fines. 🚨

#led lights#car lights#led car light#youtube#led auto light#led headlights#led light#led headlight bulbs#ledlighting#young artist#led light bulbs#led strip lights#car rental#cars#electric cars#classic cars#car#porsche#truck#automobile#lamborghini#bmw#carlos sainz#carte postale#car light#car culture#car show#car photography#car lamp#autonomous vehicle headlights
0 notes
Text
In today's digital landscape, smartphones have become essential tools for managing our daily lives. With millions of applications available for download, distinguishing between legitimate apps and dangerous impostors has never been more critical. Fake apps—malicious software disguised as legitimate applications—have emerged as a significant threat to mobile users worldwide, potentially exposing sensitive data, stealing financial information, and compromising device security. According to recent cybersecurity reports, fake apps account for a substantial percentage of mobile malware distribution, with thousands of new malicious applications identified each month. These sophisticated scams target users across all platforms and demographics, making everyone vulnerable to potential attacks. This guide aims to equip you with the knowledge and tools to identify and avoid fake applications, protecting your personal information and digital security in an increasingly complex mobile landscape. Understanding the Risks of Fake Apps Before learning how to spot fake apps, it's important to understand what's at stake when you accidentally download one. Types of Threats Malware Infection: Fake apps often contain malicious code designed to infiltrate your device and perform unauthorized actions, including: Spyware: Monitors your activity and collects sensitive information without your knowledge Ransomware: Locks your device or encrypts your data, demanding payment for restoration Adware: Displays excessive or aggressive advertisements, sometimes redirecting to malicious websites Trojans: Appears legitimate but performs harmful actions in the background Data Theft: Many fake apps are specifically designed to harvest personal information, such as: Login credentials Financial details Contact lists Personal messages Location data Photos and media Financial Fraud: Some malicious applications directly target your finances by: Making unauthorized purchases Subscribing to premium services without consent Stealing payment information Initiating fraudulent transactions Privacy Breaches: Even when not directly stealing data, fake apps may violate your privacy by: Tracking your movements and online behavior Recording conversations or capturing screenshots Accessing sensitive device features like cameras and microphones Sharing your personal information with third parties The consequences of these threats range from annoying (excessive ads and slow device performance) to devastating (identity theft and financial loss), making it essential to avoid fake apps altogether. Key Indicators of a Fake App Protecting yourself begins with knowing the warning signs. Here's a comprehensive checklist to help you identify potentially dangerous applications: 1. Developer Reputation A legitimate app typically comes from a developer with an established history and reputation. What to check: Research the developer's name in the app store and online Look for an official website with professional design and detailed contact information Verify if the developer has other applications with positive reviews Be wary of developers with no history or with names very similar to well-known companies Red flag example: An app claiming to be from "Faceboook Inc." (note the extra 'o') rather than the legitimate "Facebook, Inc." 2. App Permissions Fake apps often request excessive or inappropriate permissions that have nothing to do with their stated functionality. What to check: Review all permission requests critically Question why a simple app needs access to sensitive features like your contacts, camera, or location Be especially cautious of apps requesting SMS access, notification reading, or device administrator privileges Red flag example: A flashlight app requesting access to your contacts, microphone, and full network access. 3. User Reviews and Ratings
The review section often contains valuable clues about an app's legitimacy. What to check: Read multiple reviews, not just the top-rated ones Look for specific, detailed feedback rather than generic praise Be suspicious of apps with thousands of five-star ratings but few actual reviews Watch for patterns of identical reviews posted in quick succession Check for reviews mentioning unexpected charges or suspicious behavior Red flag example: An app with 4.9 stars but reviews that all use similar phrasing, contain poor grammar, or were all posted within a short timeframe. 4. App Store Listing Quality The quality and consistency of the app's store listing can reveal much about its legitimacy. What to check: Look for poor grammar and spelling in the description Check if screenshots match the described functionality Verify that the app's icon is professional and not a slightly modified version of a popular app Compare the app name to the URL it links to Check the app's release date and update history Red flag example: An app description filled with grammatical errors, mismatched screenshots, or promises of unrealistic features. 5. Website and Contact Information Legitimate developers typically provide proper websites and contact methods. What to check: Visit the developer's website if available Look for professional design, functioning links, and comprehensive information Verify the presence of legitimate contact details, privacy policies, and terms of service Be cautious if the only contact method is a generic email address Red flag example: A developer with no website or with a website that appears hastily created with minimal information. 6. Design and Visual Elements The app's visual presentation often indicates its legitimacy. What to check: Look for poor design quality, misaligned elements, or pixelated graphics Be suspicious of apps that mimic well-known brands with slight variations Watch for inconsistent design elements within the app Check if the user interface matches platform guidelines (iOS or Android) Red flag example: An app claiming to be a banking application but with a user interface that doesn't match the bank's branding or design standards. 7. Download Statistics Popular legitimate apps typically have significant download numbers. What to check: Be cautious of apps claiming to offer essential services but having very few downloads Compare download numbers with similar apps in the same category Consider how long the app has been available relative to its download count Red flag example: A "must-have" utility app that has only been downloaded a few hundred times despite being available for months. 8. Unusual Payment Requests Payment methods outside official channels are major red flags. What to check: Be extremely wary of apps requesting payment information outside the official app store payment systems Never provide credit card details directly within an app unless it's from a well-known, trusted service Be suspicious of apps that redirect to external payment pages Watch for unusual payment methods like cryptocurrency or wire transfers Red flag example: An app asking you to enter your credit card details into a form within the app rather than using Apple Pay or Google Pay. Protecting Yourself from Fake Apps Prevention is always better than dealing with the aftermath of a security breach. Follow these best practices to minimize your risk: Download from Official Sources Only The safest approach is to only download apps from official app stores. Use Google Play Store for Android devices Use Apple App Store for iOS devices Avoid sideloading apps from third-party sources unless absolutely necessary If you must download from outside an app store, verify the website's legitimacy Enable Security Features Modern devices come with built-in security features designed to protect against malicious apps.
For Android: Enable Google Play Protect, which scans apps for harmful behavior Turn on "Verify apps" in your security settings Consider using the "App permissions" feature to review and modify permissions For iOS: Keep restrictions enabled for app installations Use App Store privacy labels to understand data usage Review app permissions regularly in Settings Keep Everything Updated Updates often contain critical security patches that protect against new threats. Set your device to automatically update the operating system Enable automatic app updates when possible Manually check for updates regularly if automatic updates are disabled Consider replacing devices that no longer receive security updates Use Security Software Additional protection can help identify threats that slip through other defenses. Install reputable antivirus/anti-malware applications Consider security apps that offer app scanning features Use privacy-focused tools that monitor app behavior Look for solutions that offer web protection and phishing detection Practice Safe Browsing Habits Many fake app installations begin with deceptive links or advertisements. Avoid clicking on pop-up ads promising free versions of paid apps Be skeptical of emails or messages containing app download links Don't trust "exclusive" offers for popular apps at dramatically reduced prices Verify the URL before downloading anything Regular Security Audits Periodically reviewing your device can help identify potential issues. Regularly review all installed apps Check for apps you don't remember downloading Monitor battery and data usage for unusual activity Review app permissions periodically Uninstall apps you no longer use What to Do If You Download a Fake App If you suspect you've installed a malicious application, act quickly to minimize potential damage: 1. Remove the App Immediately For Android: Go to Settings > Apps > [App Name] Tap "Uninstall" If the uninstall button is grayed out, you may need to remove administrator privileges first (Settings > Security > Device Administrators) For iOS: Press and hold the app icon on your home screen Tap the "X" or "Remove App" option Confirm deletion 2. Scan Your Device After removing the suspicious app: Run a full scan with antivirus/anti-malware software Check for any remaining unfamiliar apps Monitor your device for unusual behavior 3. Change Your Passwords If you've used the suspicious app: Immediately change passwords for any accounts you accessed while the app was installed Start with financial and email accounts Use unique, strong passwords for each service Enable two-factor authentication where available 4. Monitor Financial Accounts Keep a close eye on potential financial impact: Check bank and credit card statements for unauthorized charges Consider freezing credit cards if you entered payment information Contact your bank if you notice suspicious activity Consider credit monitoring services if sensitive information was exposed 5. Report the Fake App Help protect others by reporting the malicious application: In Google Play Store: Navigate to the app listing, scroll to the bottom, and select "Flag as inappropriate" In Apple App Store: Scroll to the bottom of the app page, tap "Report a Problem" File a report with cybersecurity organizations like the Internet Crime Complaint Center (IC3) Warn friends and family through social media if you discovered a particularly convincing fake Conclusion In our increasingly connected world, the threat of fake apps continues to grow in both sophistication and prevalence. While the risks are significant, implementing the strategies outlined in this guide can dramatically reduce your chances of falling victim to these malicious schemes. By developing a healthy skepticism
toward unfamiliar applications, carefully evaluating app store listings, and following best practices for mobile security, you can enjoy the benefits of mobile applications while protecting your personal information and digital identity. Remember that cybersecurity is an ongoing process rather than a one-time effort. Stay informed about emerging threats, regularly review your digital security practices, and share this knowledge with friends and family who might be vulnerable to such scams. In the digital age, vigilance is not just prudent—it's essential.
0 notes
Text
Need Plumbing Help? How to Choose a Licensed Plumber in NJ the Right Way
When your kitchen sink won’t drain or the water heater suddenly stops working, the first thing on your mind is probably, “How do I find a plumber I can trust, and fast?” Choosing a licensed plumber in New Jersey might feel overwhelming at first, but with the right approach, it doesn’t have to be.
This guide will walk you through the most important factors to consider when hiring a plumber in NJ, help you avoid common mistakes, and ensure you bring in a professional you can count on to handle the job with expertise and care.
Whether you're dealing with an urgent repair or planning a larger project, these tips will save you time, stress, and money.

Why Hiring a Licensed Plumber in New Jersey Matters
When water is leaking through your ceiling or your bathroom faucet refuses to stop dripping, it’s tempting to hire the first plumber you can reach. But choosing a licensed professional ensures you’re getting the quality and expertise required to protect your home.
What Does "Licensed" Mean?
A licensed plumber in NJ has met specific education, training, and exam requirements set by the New Jersey State Board of Examiners of Master Plumbers. This means they have the knowledge and skills to handle everything from simple repairs to complex installations and are familiar with local codes and regulations.
The Risks of Hiring an Unlicensed Plumber
Hiring an unlicensed plumber might save you a few bucks upfront, but it can lead to bigger problems later. Unlicensed plumbers may lack the training needed to perform high-quality work, which increases the risk of improper repairs, code violations, and even water damage. Worse, if something goes wrong, you may have fewer legal protections.
How to Choose the Right NJ Plumber for Your Home
Here are six straightforward steps to help you find a reliable plumber in New Jersey who will get the job done right.
1. Start With Recommendations
Word of mouth is a trusted way to find reputable plumbers in your area. Try these sources to get started:
Ask Neighbors and Friends: Chances are, someone in your circle has already dealt with a plumbing issue and can recommend a professional they trust.
Check Online Reviews: Platforms like Yelp and Google Reviews offer insights from other homeowners in New Jersey.
Local Facebook Groups: Many NJ community groups are great resources for firsthand recommendations.
Bonus tip: Pay attention to companies that respond to customer feedback online. It’s often a sign of excellent customer service!
2. Verify Their License and Insurance
Before you hire anyone, verify that the plumber is licensed by the New Jersey Division of Consumer Affairs. Most licensed professionals are more than willing to provide their license number when asked. Additionally, ask for proof of liability insurance. This protects you in case of accidents or damage during the repair. An insured plumber is one you can hire with confidence.
3. Evaluate Their Experience and Expertise
Plumbing isn’t just about fixing pipes. A professional licensed plumber should have experience in residential systems and expertise in a wide range of services, including:
Leak detection and repair
Water heater installations
Sewer line repairs
Remodeling projects
Pipe replacements
For larger or more complex projects, don’t hesitate to ask for references from past customers to confirm their track record of success.
4. Get an Estimate in Writing
An experienced plumber should be able to provide a detailed estimate after assessing the issue. This helps prevent surprises when it’s time to pay the bill. Be sure the estimate includes:
Labor costs
Parts and materials
Any additional fees (such as travel charges or emergency call fees)
If a plumber refuses to put the quote in writing, that's a red flag to look elsewhere.
5. Consider Customer Service and Communication
Good plumbers aren’t just skilled at fixing things; they’re also excellent communicators. Pay attention to how they interact:
Are they easy to reach and quick to respond to calls or emails?
Do they take the time to explain the problem and their recommended solution?
Are they upfront about pricing and timelines?
Exceptional customer service often translates into a smoother, less stressful experience for you.
6. Prioritize Warranties and Guarantees
A licensed plumber who stands by their work will typically offer a warranty on their services. Whether it’s a 30-day guarantee on a small repair or a yearlong warranty on major installations, this assurance goes a long way in protecting your investment.
Warning Signs to Watch Out For
Not every plumber who responds to your call will be the right fit. Be cautious of the following red flags:
A lack of license or insurance
Overly rushed or vague estimates
Poor communication or customer service
Negative reviews that mention similar issues repeatedly
Pressuring you to pay upfront for materials or services
Trust your instincts. If something feels off, move on to another option.
The Benefits of Finding the Right Plumber
Choosing the right licensed plumber means more than just solving your immediate issue. It’s about ensuring the long-term health of your home, protecting your investment, and having peace of mind knowing you have an expert on your side.
When you work with a reliable plumber, you gain:
Faster, more accurate problem diagnosis
Professional-grade repairs that meet safety standards
Reduced need for repeat visits or follow-up repairs
Access to specialized services, such as eco-friendly options or advanced equipment
Protection from potential legal issues and liabilities
By following these tips and asking the right questions, you can confidently hire a licensed plumber in New Jersey who will provide high-quality work and exceptional customer service. Don’t take chances with your plumbing – be proactive about finding the right professional for your home. Your future self (and wallet) will thank you!
0 notes
Text

A headline in Saturday’s Sunday newspaper (let it sink in) reads, “City Demolitions Nearing an End”, and I’m willing to bet most Wheeling residents wish the headline were accurate. It’s not, though. The headline only refers to City Council’s current list of dilapidated properties in the six wards of the city, and it was formulated more than a year ago and it’s been reviewed and revised several times since. Those red-flagged properties, though, are not the only eyesores in Wheeling, a city once home to more than 60,000 residents that is now where less than half that amount of people reside today. So, in the vast majority of neighborhoods, there are many abandoned houses with unkept yards that will not be addressed until Council develops a new list of people and their properties that are harmful to those residential areas. It’s the same tragedy that remains present in communities across America’s Rust Belt region and it’s impeding all efforts everywhere in the Mountain State from real resurrections. There are three kinds of vacant houses in Wheeling – those that are owned, empty, ugly, and costly to surrounding property values; those that are owned, empty, costly, dangerous, and forgotten by out-of-town owners; and those that have been demolished on the taxpayer’s dime and now have a property lien attached to the respective deed. The only scenario in which the lien means a thing is if the property owner attempts to sell the land before the state or city takes legal possession of the deed. To sell the parcel, the lien must be satisfied, but that seldom takes place in shrinking towns like the Friendly City. If a parcel is owned but empty, ugly, in violation of code, and a negative to a neighborhood’s property values, the City can place it on the “raze-or-repair” and efforts are made to communicate with the owner. In far too many situations, the owner will address only the issues that attracted the attention and vanish yet again. If it is empty, a neighborhood negative, dangerous to the public, and forgotten by out-of-town owners, it goes on the demo list and is razed when taxpayer funds become available. And we the taxpayer pay for it instead of the owner. Truth be told, the City can’t force those landowners to do much if anything at all, unfortunately, because West Virginia lawmakers have not yet given municipalities, towns, and villages the legal muscle they need to place demolition-related liens on the owner’s credit report for collection. If such recourse existed, not so many neighborhoods would be held hostage by the grossness of greed and selfishness. Listen, if someone inherited the house and land and wants nothing to do with it, they can forfeit it to the city and walk away, but legislative action is necessary to protect communities from the inaction of neglectful property owners so we can collectively preserve and increase property values not only in Wheeling but in every nook and cranny in the great state of West Virginia. Read the full article
0 notes
Text
We Already Know Your Change "Improves" the Code
Ok, so your change description says that you "improved" Widget (made it "better", or whatever). It's good that you mentioned WHAT was improved (Widget), but you are still missing a key piece of information: How? In what sense? Along what axis? This is super salient information. Do not omit super salient information. (You would think that this goes without saying, but experience tells me otherwise.)
For example, is it more secure? Uses less resources? Simpler? Simply saying that things are "better" says very very little about your change, because
It goes without saying. Nobody makes code changes with the intention of DEGRADING the code!
There are infinity ways code can be better. Your change does NOT improve the code in ALL dimensions.
Always be meaningful. (This 👈 is going to be a recurring mantra of this blog.)
Furthermore, you very likely have enough room in the title to answer the salient question: What is 'better' about Widget? It might not seem like you have enough room, because you already used all the space; however, if you cut out the parts that go without saying, you will find that there is way more space than you thought. This is because you can completely cut out the part where you merely state THAT the code is "improved", "better", etc, and replace that with HOW the code is improved.
E.g. instead of
Improved Widget.
your title can say
Use caching to speed up Widget.
Then, your description can go into further detail. E.g. it can describe the amount of speed up, is it always faster, or are there uncommon cases where it's maybe a little slower, etc.
Corollary: Do not simply state THAT your change fixes a bug in Widget. This is especially true if you use the "fix" Conventional Commit prefix. Instead, your title should try to answer "What was wrong before?" or "What is the new (better) behavior?". Answering just one of those is generally going to give a pretty clear picture the answer to the other. If not, there is more room in the description.
Another way to think about this issue: could your title apply to many other (future) code changes? If so, then you are looking at a big red flag of vacuousness. If so, your title is not very meaningful, and thus, violating the prime directive.
0 notes
Text
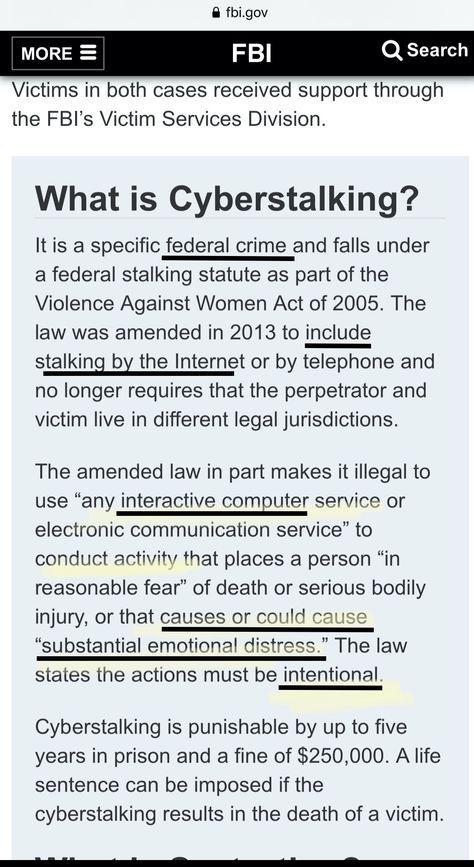
As a Targeted Woman, do you feel that your home is being illegally bugged and that your private conversations are being shared with others?
Do you feel that you are being electronically harassed, or cyberstalked?
When you write a post or an e-mail, do you constantly have to re-edit, as someone comes in and changes your spelling and alters your grammar, in attempt to discredit your narrative and your credibility?
When you review online posts in the community, do you notice these same types of errors, while other posts appear articulate and correct?
There's a red flag right there. Our own community of those trying to help others is of course being monitored and manipulated.
In addition to Federal protection, there are also state laws that will protect you as well.
California is a two-party recording state. If you don't live in California, look up the laws for your state.
Two party states require the recording party and the party being recorded must both consent.
Federal Law and Interstate Recordings
Generally, if both parties are within the same state, the state law will apply. When one party is in California and the other one is outside the state, the two-party consent rule applies to actors outside of California, if they are communicating with people in California who have not given consent. Essentially, California protects those in the state from being recorded without their consent even where the out-of-state actor is in a state which permits “one party consent.
California Wiretapping Law
California's wiretapping law is a "two-party consent" law. California makes it a crime to record or eavesdrop on any confidential communication, including a private conversation or telephone call, without the consent of all parties to the conversation. See Cal. Penal Code § 632. The statute applies to "confidential communications" -- i.e., conversations in which one of the parties has an objectively reasonable expectation that no one is listening in or overhearing the conversation. See Flanagan v. Flanagan, 41 P.3d 575, 576-77, 578-82 (Cal. 2002). A California appellate court has ruled that this statute applies to the use of hidden video cameras to record conversations as well. See California v. Gibbons, 215 Cal. App. 3d 1204 (Cal Ct. App. 1989). (Digital Media Law)
This is a Federal crime and just one of many these groups commit on a regular basis.
The FBI has separate divisions assigned to each of these.
Not to mention a state of California crime. If you live in another state, look up the laws that apply.
Law Enforcement, you are being asked to do your part.
Break this damaging cycle of events. Arrest and charge them now, and then clearly enforce such violations when and where they occur in the future.
The journey always begins with that first small step
0 notes
Text
OneNETnews Investigates: A scandalous right-wing commentator 'Think Before You Sleep' target F*t-Shaming & Acceptance and Cyb*rb*llying combined against freelance independent Californian animator 'Illymation' sparks outrage to deplatforming its video-sharing platform on YouTube [EXCLUSIVE]

(Written by Mitch Williams & Lincoln Albert Loud / Senior Tech Correspondent and Investigative Stringer News Reporter of Nickelodeon News)
TRIGGER WARNING: The following investigative news article discusses emotionally sensitive and offensive content related to online cyberbullying, fat shaming and harassment. Consider to exercise with caution, and prioritize your emotional well-being while reading this I.N.R. If you feel triggered or distressed by such topics, our news readers at OneNETnews recommends to seek support to yourself ASAP, or to click off from reading further in this article. Reader's discretion is STRONGLY ADVISED.
HAWTHORNE, CALIFORNIA -- In the late-Q1 of 2024… An online cyberbullying incident involving a suspected right-wing male conservative commentator by the name 'Think Before You Sleep', and a freelance Californian animator victim 'Illymation' brought out the crippling effects of fat shaming, fat acceptance & harassment. The issue arose when TBYS recently ranted over, in her real life cartoon story on fatphobia that was created by a YouTuber's victim, literarlly accusing her of glorifying minor or medium-level obesity, and promoting unhealthy body image of herself.
26 y/o female animated freelance YouTuber from Hawthorne City, California, United States of America (U.S.A.) named 'Illymation', whose real name as Ms. Ilyssa Grace Levy talks about her past struggles with her fat body image and weight, revealed from her own YouTube video late last Dececember 2023 that she started dieting at the age of 11 y/o in either 2008 or 2009 before launching her animated YouTube channel in the early 'Generation Alpha' years in September 2013.
Before social media, when she was born a decade later in the early 2010s under her 'Gen Z' era, despite efforts to address fatphobia-related issues through in-real-life stories of her self-contents, with a few platforms like Facebook and Friendster (now both separately owned by Meta Platforms Inc. [MPi] and the defunct-Friendster Inc. [Fi]), she faced vicious attacks on criticism, when he recently but allegedly pointing their bad finger from 'TBYS' and his pro-democratic supporters from the online bashers, troll of netizens, and death threats.
An anonymous concern from her Tumblr ask blog post, to be obtained and exclusively investigated to OneNETnews… Her personal information like Ms. Levy (Illymation) aside fatphobic concern was recently targeted and compromised when several pro-online troll of netizens from TBYS have now been completely doxxed, leaving in threathen to deplatform her on their video-sharing platform as she potentially claimed that Ms. Levy violated the California's Penal Code #653.2. But Illymation's claims are being nulled, and is refused to watch and listen the insulting commentary video.
Rather than usual, the online attacks from TBYS, aimed at fat-shaming and accepting her on YouTube, alarming serious public health concerns and has raised double red flags. Instead, the fatphobic behavior from TBYS and his pro-supporters against her, has been widely condemned as a result of a newest online harassment campaign in this said date of the late-Q1 2024. Three (3) of the videos on YouTube from TBYS were taken down for a while, and later reuploaded exclusively in his uncensored video discussion on Rumble.
Moreover, Ms. Levy (Illymation) moved out from Hawthorne City to Sacramento, the said state and her country for safety with paid legal fees from her GoFundMe site, as she recently broke the lease on her home apartment and costing her U$D10,000 (or PHP581,100) because of doxxing and fat-shaming backlash from TBYS back-to-back, according from a Reddit comment post by Lokalexabender.
Reports from Zawn Villines of Medical News Today, criticizing someone for their weight like Ms. Levy (Illymation) can lead to serious health and emotional problems. People who face weight discrimination are more likely to suffer from eating disorders, depression and other medical conditions. The American Psychological Association (APA) has pointed out the harmful consequences of criticizing weight and emphasized the need to encourage a positive view of bodies and acceptance.
In the midst of heated debates, Ms. Levy (Illymation) shared her worst sensitivity & anger, worrying about the intense online abuse that she encountered by calling it a fat Californian kid in the early 2010s. She openly talked about this situation, not quite long ago, in a video that was later removed on YT, but then shared on 'Rumble' titled "Woke YouTuber is Trying to Deplatform Me", where she criticized TBYS and his pro-supporters for their harmful actions. Such consistently physical & online attacks in a cybercrime world, affected personally her new mental health, even though she received a lot of support from her followers and other creators on her video-sharing platform.
Looking ahead in the present day on various social media platforms like TikTok & Facebook (owned individually by ByteDance Limited and MPi) and video-sharing platform 'YouTube' (also own by Google's Alphabet), the public health concern of minor or medium-level of obesity is widespread and highlighted by the situation of body shaming and her animator's image of Ms. Levy. It's clear that the desire to meet these unattainable beauty ideals, when you look at the mirror on your stomach fats from side-to-side, along with the widespread culture of dieting, has led to a harmful atmosphere where judgments and criticisms based on their own looks occur.
Our investigative news team of OneNETnews have turned them over for the anti-TBYS fans with a right-wing male suspect to the California Police and the YouTube headquarters in San Bruno, the said state and country, advising everyone to mass report his main YouTube channel of TBYS, which being looked into it by the California Police. But, a spokesperson of YouTube had refused to take his channel down and removing their Google account, despite of the cyber criminal cases in the ongoing rivalry on both sides.
It is imperative for people to address the root causes of body shaming combined with her animator's image and promote body neutrality and acceptance of her new self slim body. In an article by Dr. Danielle Kelvas of 'Within Health', dietitian experts and specialist officials highlight the importance of having a positive body image, as well as self-acceptance to combat eating disorders, body discrimination and weight stigma.
Between a male right-wing commentator suspect 'Think Before You Sleep' and one Californian independent animator victim 'Illymation'… Online criminals like this represents a technical foul play with his poisonous corruption points, leaving a victim to immune herself for safety and the unlawful reminders of the damaging effects of online harassment, cyberbullying and discrimination that really needs to cultivate an inclusive and compassionate online community. Hence, the online netizens from YouTube and other social media platforms takes a stand against toxicity and the unregulated online behaviors for the well-being of all individuals, regardless of their size or appearance of Ms. Levy (Illymation).
He will now soon potentially face legal consequences in the press charges convicted by the American court for 'TBYS', resulted in the upcoming termination of his YouTube channel within a shorter months time (without bail or appeal) if criticially found guilty, in relation to fatphobic motives, public harassments, discrimination, cyberbullying and doxxing by online netizens against 'Illymation'.
CONTRIBUTED FILE THUMBNAIL PHOTO COURTESY for REPRESENTATION via YT VIDEO EDITED BY: Rhayniel Saldasal Calimpong (Freelanced Digital Photojournalist for OneNETnews)
SOURCE: *https://rumble.com/v4gg6e3-a-fat-acceptance-cartoon.html [Referenced YT VIDEO #1 via Think Before You Sleep, per relayed video by Rumble] *https://rumble.com/v4jp1hk-woke-youtuber-is-trying-to-deplatform-me.html [Referenced YT VIDEO #2 via Think Before You Sleep, per relayed video by Rumble] *https://rumble.com/v4o5bu8-the-illymation-drama-continues.html [Referenced YT VIDEO #3f via Think Before You Sleep, per relayed video by Rumble] *https://www.youtube.com/watch?v=xfG_Er6lyJE [Referenced YT VIDEO via Illymation] *https://www.youtube.com/watch?v=VqdwQ-VthGU [Referenced YT VIDEO via Osros] *https://www.youtube.com/watch?v=j8nue473BWs [Referenced YT VIDEO #1 via Breone] *https://www.youtube.com/watch?v=N6PvpPivdHk [Referenced YT VIDEO #2f via Breone] *https://www.youtube.com/watch?v=QOXQQmDvc0I [Referenced YT VIDEO via NoahSamsen] *https://youtube.fandom.com/wiki/Illymation *https://youtube.fandom.com/wiki/Think_Before_You_Sleep *https://www.clarip.com/data-privacy/california-consumer-privacy-act-fines/ [Referenced Excerpt Article via Clarip] *https://www.aerlawgroup.com/blog/fact-or-fiction-doxing-someone-can-get-you-arrested/ [Referenced Editorial Article via The Rodriguez Law Group] *https://www.simmrinlawgroup.com/california-penal-code-section-653-2/ [Referenced Editorial Article via Simmrin Law Group] *https://leginfo.legislature.ca.gov/faces/codes_displaySection.xhtml?lawCode=PEN§ionNum=653.2 [Referenced Law Article via California Legislative Info Database] *https://www.cbsnews.com/news/fat-shaming-can-lead-to-host-of-health-problems/ [Referenced News Article via CBS News] *https://www.medicalnewstoday.com/articles/effects-of-fat-shaming [Referenced News Article via Medical News Today] *https://withinhealth.com/learn/articles/embracing-body-neutrality-in-eating-disorder-recovery [Referenced News Article via Within Health News Bureau] *https://www.apa.org/monitor/2022/03/news-weight-stigma [Referenced Editorial Article via American Psychological Association] *https://old.reddit.com/r/OutOfTheLoop/comments/1bwko4p/what_is_going_on_with_illymations_drama/ [Referenced Subreddit Ask Post via Reddit's OutOfTheLoop] *https://old.reddit.com/r/saltierthankrayt/comments/1be9jm6/comment/kxm7pwk/ [Referenced Subreddit Caption Post via saltierthankrayt] and *https://www.gofundme.com/f/legal-fees-for-breaking-lease [Referenced Donation Listing via GoFundMe]
-- OneNETnews Online Publication Team
#OneNETnews Investigates#exclusive#first and exclusive#fyp#hawthorne#california#YouTuber#illymation#Think Before You Sleep#cybercrime#drama#awareness#police report#OneNETnews
0 notes
Text
SEC Obtains Relief - Crypto Fraud Scheme - Digital Licensing

SEC Obtains Emergency Relief to Halt Utah-Based Company’s Crypto Asset Fraud Scheme Involving 18 Defendants - Digital Licensing Inc. Washington, DC (STL.News) The Securities and Exchange Commission (SEC) today announced that it obtained a temporary asset freeze, restraining order, and other emergency relief against Digital Licensing Inc., a Draper, Utah-based entity doing business as “DEBT Box,” as well as the company’s four principals, Jason Anderson, his brother Jacob Anderson, Schad Brannon, and Roydon Nelson, and 13 other defendants in connection with a fraudulent scheme to sell crypto asset securities to hundreds of U.S. investors that raised approximately $50 million and unspecified amounts of Bitcoin and Ether. The SEC’s complaint, unsealed yesterday in the U.S. District Court for the District of Utah, charges the defendants in an ongoing scheme that began in March 2021 to sell unregistered securities they call “node licenses.” In hundreds of online videos and social media posts, as well as at investor events, the defendants told investors that the node licenses would generate various crypto asset tokens through crypto mining activity and that revenue-generating businesses in a variety of sectors would drive the value of the various tokens DEBT Box mined, resulting in exorbitant gains for investors. In reality, as alleged, the node licenses were a sham intended to obscure the fact that the total supply of each token was created by DEBT Box instantaneously using code on a blockchain. “We allege that DEBT Box and its principals lied to investors about virtually every material aspect of their unregistered offering of securities, including by falsely stating that they were engaged in crypto asset mining,” said Tracy S. Combs, Director of the SEC’s Salt Lake Regional Office. “We filed this emergency action to protect the victims of the defendant’s unlawful actions and stop further harm.” The SEC’s complaint further alleges that DEBT Box and its principals —along with defendants James Franklin, Western Oil Exploration Company Inc., and Ryan Bowen—lied to DEBT Box investors about the revenues of the businesses purportedly driving the value of the tokens. In total, 18 defendants, including those mentioned above, have been charged with engaging in unregistered securities offerings. DEBT Box, Jason Anderson, Jacob Anderson, Brannon, Nelson, Franklin, Western Oil, and Bowen were also charged with violations of the antifraud provisions of the federal securities laws. Jason Anderson, Jacob Anderson, Brannon, Nelson, Bowen, Mark Schuler, Benjamin Daniels, Joseph Martinez, Travis Flaherty, Brendon Stangis, Matthew Fritzsche, B & B Investment Group, LLC, and iX Global, LLC were charged with acting as unregistered brokers. The complaint seeks permanent injunctive relief, the return of alleged ill-gotten gains, and civil penalties. The Honorable Judge Robert J. Shelby, U.S. District Judge for the District of Utah, entered an order on July 28, 2023, imposing a temporary restraining order, asset freeze, and other relief. Judge Shelby also entered an order appointing Josias N. Dewey of the law firm Holland & Knight LLP as a temporary receiver over DEBT Box to, amongst other things, marshal assets for the benefit of investors. Investors who believe they were affected by the DEBT Box offering may visit the receiver’s website at www.debtboxreceiver.com or call (305) 349-2134. The SEC’s continuing investigation is being conducted by Joseph Watkins, Laurie Abbott, and Mitchell Davidson of the Salt Lake Regional Office, and Karaz Zaki of SEC Headquarters. The litigation will be led by Casey Fronk and Michael Welsh. The matter is being supervised by Ms. Combs. Investors can learn more about the risks of investing in crypto asset securities and unregistered offerings by reading SEC investor education bulletins such as Exercise Caution with Crypto Asset Securities and 10 Red Flags That An Unregistered Offering May Be A Scam. SOURCE: Securities and Exchange Commission (SEC) Read the full article
0 notes
Text
No serious injuries after wheel clears barrier at Goodwood Festival | RaceFans Round-up
In the round-up: The organisers of the Goodwood Festival of Speed have confirmed “no serious injuries” occured following an incident in which a wheel came off a car. In brief “No serious injuries” after incident at Goodwood Festival A Jaguar Mark One shed its left-rear wheel during a run at the Goodwood Festival of Speed, which began yesterday. Footage of the incident indicated the wheel cleared a straw bale and went into a spectator enclosure. The event organisers confirmed on social media no one involved had been seriously hurt. “Following the incident on the hillclimb we’re pleased to confirm that there were no serious injuries and those involved were able to go back to enjoying the event,” they said. In May a wheel cleared a barrier at the Indianapolis 500 following a collision between Kyle Kirkwood and Felix Rosenqvist, but no spectators were injured. F1 street races in France and Spain rumoured French president Emanuel Macron has shown an interest in reviving the French Grand Prix, according to Nice-Matin. The mayor of Nice told the newspaper the president had responded positively to the idea of bringing F1 back to the country. However the preferred venue is understood to be a new street track in Nice, rather than one of France’s existing F1-grade permanent circuits. Meanwhile the president of the Executive Committee of the Ifema convention centre in Madrid, Jose Vicente de los Mozos, has indicated it is moving closer to confirming a street circuit in the Spanish capital will host a round of the world championship. It has previously been tipped to take over the Spanish Grand Prix from the Circuit de Catalunya when its contract expires after the 2026 race, but no official announcement has yet been made. Vergne given suspended fine for “misconduct” Vergne committed “misconduct”, say FIA stewards Jean-Eric Vergne has been fined €3,000 (£2,564), suspended until the end of the year, following his public criticism of a penalty given to his DS Penske team at the previous Formula E round in the USA. It is the latest in a series of similar penalties issued recently. Haas F1 team principal Guenther Steiner was reprimanded for describing the Monaco Grand Prix stewards as “laymen”. More bizarrely, Formula Regional European Championship team MP Motorsport were issued a suspended fine after a staff member responded to a stewards’ bulletin in a WhatsApp group using a poo emoji. In Vergne’s case, the specific language he used was not cited by the stewards. Following a hearing with Vergne the stewards said “the driver stated that some of the written words in the press [were] not said by him.” “He agreed that some comments he really said have not been respectful towards the stewards and also towards the FIA. He promised to try to [not] do so in the future because he has the full respect for the work of the stewards and the FIA.” Vergne was deemed to have committed “misconduct towards officials and FIA”, and to have violated article 12.2.1 clauses (c), (f) and (k) of the International Sporting Code. These prohibit: “Any fraudulent conduct or any act prejudicial to the interests of any competition or to the interests of motor sport generally”, “any words, deeds or writings that have caused moral injury or loss to the FIA, its bodies, its members or its executive officers, and more generally on the interest of motor sport and on the values defended by the FIA” and “and misconduct towards” FIA members of staff and other associated parties. Advert | Become a RaceFans supporter and go ad-free Happy birthday! Happy birthday to Ryanmack09! On this day in motorsport 50 years ago today Peter Revson won the British Grand Prix at Silverstone which was red-flagged after Jody Scheckter triggered a huge crash at Woodcote. John Watson and Jochen Mass made their debuts in the race. via RaceFans - Independent Motorsport Coverage https://www.racefans.net/
#F1#“No serious injuries” after wheel clears barrier at Goodwood Festival | RaceFans Round-up#Formula 1
0 notes
Text
Dwayne Mojica
Disclaimer! This isn’t (or maybe it is) really an analysis of Dwayne’s character.
It is a routine at this point. In the morning, he’ll behave in front of his parents. Or if he’s lucky enough, he’ll wake up to no one. Once he’s out of the house, he’ll be Dwayne to his friends. A happy-go-lucky guy, spontaneous, dramatic, a little stubborn— but a fun guy in general. Anyone would love to have him as a friend. He’s understanding, warm, and generous. Usually tangled up in all sorts of rumors because his ass is literally everywhere. He’s even in group chats he’s not even supposed to be part of.
Starting with his relationship with Cath Villega, and the playboy narrative Blaine is pushing:
✬ Panel 02, when Cath replied to Dwayne’s tweet (because he isn’t replying to her messages), Dexter and Santiago’s reactions were hinting that they are not supporting the two’s relationship. And yes, they obviously wouldn’t kasi Cath is two-timing the guy. How fucked it would be if they are doing the opposite?
✬ Panel 03, Dwayne is clearly ignoring Cath. His messages were dry, compared to how he acts with his friends. Two weeks is considered a long time (believe me), and yet he’s wondering why Cath is missing him when they just saw each other two weeks ago. That alone would make someone rethink. Is Dwayne really serious in the relationship or not? Dry texts, lied na may plano sila ng tropa even though they are just about to plan something so he could get out of the situation, and the fact that they are talking in Telegram (just kidding). That alone paints Dwayne in a bad light.
Maybe it’s because of Cath’s popularity na rin, kaya nakaabot kay Blaine ‘yung sabi-sabing red flag si Dwayne. This is the sequence of events:
1. Dwayne and Cath announce they are dating.
2. Cath fucks up in the middle of their relationship (special mention, the boy best friend)
3. Dwayne somehow caught the two.
4. He tells his friends, and after contemplating, he decides to act like he saw no shit and their relationship is completely healthy.
5. The more it sinks in, the more he treats Cath coldly (I’d say this is the point where Dwayne is preparing himself for the worst. So it wouldn’t hurt that much when they actually break up— as what he told Austin).
6. Cath wonders why, like an idiot. She tells this to her best friend, Mariel. Completely leaving out her mistake (made it look like Dwayne’s at fault).
7. And Mariel’s at HUMSS 2, so Blaine eventually got the gist of it.
It ends with everyone thinking Dwayne is the bad guy in their relationship. Because minus the points 2, 3, and 4, it would only look like Dwayne just got bored in the relationship. And that’s what Cath did. She hid the fact that she had a make out session with her guy best friend— on a Friday afternoon, at the corner of Dwayne’s empty classroom where she probably thought no one could see them through the window.
Dwayne had girlfriends before Cath and if you asked all of them one by one, you won’t hear a single negative thing about him kasi once he enters a relationship, oh boy, he will take you seriously. It’s just that his intentions are misunderstood because he’s friends with a lot of girls. Even though he caught Villega cheating, he never once violated the code of dating— if such thing exists. Neither women nor getting even crossed his mind. That’s not who Dwayne is. He’s still Cath’s boyfriend regardless of what she did.
Technically speaking, those in the right state of mind would break up with their partner the moment they catch them cheating, right? But Dwayne was not, so he didn’t. He chose to be with her, even though she made him feel...
Insecure.
Dwayne and his relationship with his brother is not new to one who holds the first born’s card. The way Dwayne is treating River is something first borns could probably relate to. Summing it all up in one sentence; Dwayne is a good friend, (and) but not a good brother.
River’s willingness to fix his relationship with his brother has been shown numerous times in the story. And in all those cases, Dwayne paired it by shunning. If my memory is correct, the first time he accepted something from River was before his finals. When Austin helped with babysitting? Yeah, that iced coffee was the first one. River was obviously delighted.
It was the first time Dwayne actually accepted it wholeheartedly. When you buy something for someone, naandon ‘yung anticipation specially if you’re giving it to someone important. River buys pasalubongs for Dwayne every time he goes out. If not rejected, there’s always an unpleasant expression on Dwayne’s face when River’s handing (let’s say for example) the chicken floss bread to him. As though… it’s just forced.
River already experienced his first heartbreak through Dwayne.
I won’t go into details of what River felt (trust me pag inisa-isa ko siya, it’s angsty), you can put yourself in River’s shoes but it is not recommended.
Dwayne and River are born together, opposites man personalities but they’re still each other’s other half. Dwayne’s a noisy extrovert, while River’s a calm and reserved introvert. Dwayne likes teas and coffees, while River’s more on smoothies and healthy drinks. Dwayne finds it hard to say ‘no’, but River can and will.
—Funny, because they actually embody each other’s differences when they are together. The extrovert and cheerful Dwayne becomes a silent guy when he’s in the same room with his brother. And River suddenly has 100 topics waiting to be discussed when he’s with Dwayne.
(Just how River still drinks the iced coffees Dwayne ignored, disregarding his preference for non-coffee drinks.)
Dwayne’s a bright guy, but somehow, when he’s with River… he goes into his shell. He avoids and avoids and avoids. Seeing River angers him, he just magically fuels him up for no specific reason.
Having a twin could be a blessing and a curse. Blessing, if both of you guys are equally talented and loved by the parents. Curse, if you’re Dwayne and River. Curse, if your parents are constantly playing the comparison game and your parents prefer one over the other.
River and Dwayne, respectively.
Twins are considered one. As much as Dwayne liked the idea of it, their parents— particularly their mother, reminded him otherwise. She reminds him that it comes with a price. If you are born with a counterpart, you have to owe up to it. Dwayne’s the oldest so he has to be better than River in all aspects. Dwayne is the oldest so he is expected to outshine his twin. He is expected to be as talented as River because they are the copy of each other.
Isn’t it scary that Dwayne’s fate was determined by minutes?
Dwayne couldn’t do anything about it. He could pour his anger to his brother all he wants but that won’t do a thing. He knows very well that it isn’t River’s fault.
He knows that but still… hurts him. How he avoids any physical contact with River, how he pretends not to know each other at school, how he refuses to eat with his brother in the cafeteria albeit seeing he’s alone, how he could only watch in a distance as he waits for River to get inside a tricycle safely, how Dwayne rejects all the stuff River buys for him but remembers to insert his leftover coins in River’s piggy bank because he knows he got the money from there—
He wants River close to him, close enough that he could barely see him with his eyes squinted. If that would mean he could hurt him a little less.
Parang mas masakit kasi kay Dwayne kung mas malapit siya kay River. The differences are in front of his face. The more na nilalapit ni River sarili niya, mas nagiging masakit para kay Dwayne kasi at the end of this all, their mother is always sitting at the corner of her bed, eyes on Dwayne as she puts out a list why River is better than him.
What’s the point of finding tranquility in River? Currents are also powerful even if the surface looks placid. Dwayne needs to be careful..
Or else River would be the cause of his suffocation.
Going back to Dwayne’s personas— he honestly doesn’t know any shit about himself. His real self, at least— if it is said that he has three personas. (Which of them is the main one? That is what Dwayne doesn’t know.) One is born with all things unique and there’s always something that makes you— you. Dwayne would like to believe, but there’s nothing to describe him. No description can bring justice to the color of his canvas.
He’s not a happy-go-lucky guy. Is that what other people see about him? If so, better scratch that off because that isn’t who Dwayne is.
Dwayne is always anxious.
He’s not spontaneous. He’s quick to plan things inside his head.
Dwayne secretly takes control of the situation.
He’s not that dramatic. Put him and a chucky doll in a room with his mother, Dwayne would, without a doubt, sit still as if the doll isn’t creeping the hell out of him.
He specifically loathes it if he’s asked what kind of person he is. Or when people describe his personality as someone kind and generous— Dwayne laughs at that.
He thinks it hypocrite that he’s so nice to everyone but his family. After all, it doesn’t end with just Dwayne ignoring River. No, it’s not just that. Dwayne is harsh when he’s with River. And it pierces directly in River’s heart. How is he, as an older brother, nicer to his friends than his family?
Dwayne is probably not who he is in front of his friends. Maybe... his real personality lies underneath his family. But whatever it is,
Is Dwayne a good brother to River?
0 notes