#security token platform
Explore tagged Tumblr posts
Text
Secure DeFi Wallet Development: Ultimate Guide for Blockchain Solutions
This comprehensive guide to DeFi wallet development explores how blockchain technology can transform decentralized finance. It highlights key features like enhanced security, tokenized rewards, smart contract governance, and censorship resistance.
Designed for developers and blockchain enthusiasts, the blog offers insights into building user-friendly wallets that ensure privacy and seamless transactions. By addressing issues like data breaches and centralized control, this guide provides a roadmap for creating innovative and secure blockchain solutions.
A must-read for anyone in the decentralized finance space!
#defi wallet development#defi crypto lending platform development#Secure DeFi wallet development#blockchain development for defi#defi platform development#defi token development#defi lending platform development#defi lending and borrowing platform development#defi development#defi wallet app development#defi lending/ borrowing platform development#defi wallet development service#decentralized lending and borrowing platform development#defi blockchain development#lending borrowing platform development#defi development platform#defi development company#defi lending platform development services#defi platform development company#defi smart contract development#defi smart contract development company#defi smart contract development services#defi development services#defi development provider#crypto defi wallet development services
2 notes
·
View notes
Text
Build the Future of Gaming with Crypto Casino Development Solutions

#In a world where innovation drives the gaming industry#the rise of crypto casino game development is reshaping the way players and developers think about online gambling. This is because blockch#allowing developers and entrepreneurs to create immersive#secure#and decentralized casino experiences in unprecedented ways. This is not a trend; it's here to stay.#The Shift towards Crypto Casinos#Imagine a world that could be defined by transparency#security#and accessibility for your games. That's precisely what crypto casino game development is trying to bring to the table. Traditionally#online casinos have suffered because of trust issues and minimal choices for payment options. This changes with blockchain technology and c#Blockchain in casino games ensures that all transactions are secure#transparent#and tamper-proof. Thus#players can check how fair a game is#transfer money into and out of the account using cryptocurrencies#and maintain anonymity while playing games. It is not only technologically different but also culturally. This shift appeals to a whole new#What Makes Crypto Casino Game Development Unique?#Crypto casino game development offers features that set it apart from traditional online casinos. Let’s delve into some of these groundbrea#Decentralization and TransparencyBlockchain-powered casinos operate without centralized control#ensuring all transactions and game outcomes are verifiable on a public ledger. This transparency builds trust among players.#Enhanced SecurityWith smart contracts automating processes and blockchain technology securing transactions#crypto casinos significantly reduce the risk of hacking and fraud.#Global AccessibilityCryptocurrencies break the barriers that traditional banking systems have#making it possible for players from around the world to participate without having to think about currency conversion or restricted regions#Customizable Gaming ExperiencesDevelopers can customize crypto casino platforms with unique features such as NFT rewards#tokenized assets#and loyalty programs#making the game more interesting and personalized.#Success Story of Real Life#Crypto casino game development has already brought about success stories worldwide. Among them
1 note
·
View note
Text

Launch a Security Token Offering (STO) Platform
STOs offer startups enhanced credibility while providing investors with increased protection, making it a win-win situation for the emerging entrepreneurial world! So, if you are the one ready to dive into the world of STOs? Here's a quick guide on launching your own STO platform >>> http://bit.ly/421djo0
#Launch an STO#Security Token Offering#create STO platform#crypto crowdfunding#sto development company#STO website
0 notes
Text
Focus.xyz – Redefining the Creator Economy with Web3
Welcome to the future of social media. Focus.xyz isn’t just another platform—it’s a revolution. Built on the powerful DeSo blockchain, Focus empowers creators to monetize directly, build communities freely, and own their content without middlemen or platform fees. 🔥 Why Creators Are Switching to Focus.xyz

1. 100% Creator Revenue: No Cuts, No Catch. Say goodbye to heavy platform fees. With Focus, creators keep 100% of their earnings, from tips and subscriptions to premium content unlocks and even custom token launches.
2. Post-to-Earn Model : Every post can earn you real crypto rewards. Focus incentivizes quality engagement—your content isn’t just liked, it’s valued. Some posts have earned up to $1,000.
3. Complete Content Ownership : p Your followers, your content, your rules. Built on a decentralized blockchain, Focus gives creators full control and ensures censorship resistance and permanence.
4. Private & Secure by Design Focus enables anonymous posting, end-to-end encrypted messaging, and decentralized identity. Engage with your audience without ever compromising your privacy.
💡 Perfect for: Influencers tired of being demonetized. Educators and experts are monetizing premium knowledge. Communities and DAOs are looking for secure social engagement. Web3-native creators wanting real crypto-native monetization.
📈 Built for Viral Growth Referral Rewards: Invite others and earn from their activity—perfect for community builders. Engagement Bounties: Discover top content creators and get rewarded. Early Mover Advantage: With $75M in early backing from names like Coinbase, Sequoia, and a16z, now’s the time to grow with Focus.
⚡ Focus.xyz vs Traditional Platforms Feature Focus.xyz Twitter / Instagram / Patreon Platform Fees 0% 10–40% Content Ownership Yes (on-chain) No Anonymity & Privacy Full Limited Native Crypto Payments Instant Often restricted Creator Token Support Yes No 🎯 Join the Creator-Led Movement Don’t just build an audience—build your own economy.
👉 Start today: https://focus.xyz
👉 Follow and earn: Post. Engage. Get rewarded.
#Focus.xyz#crypto social network#decentralized social media#DeSo blockchain#Web3 social platform#creator economy#SocialFi#blockchain-based social network#crypto content monetization#censorship-resistant social media
310 notes
·
View notes
Text
The Metaverse: A New Frontier in Digital Interaction

The concept of the metaverse has captivated the imagination of technologists, futurists, and businesses alike. Envisioned as a collective virtual shared space, the metaverse merges physical and digital realities, offering immersive experiences and unprecedented opportunities for interaction, commerce, and creativity. This article delves into the metaverse, its potential impact on various sectors, the technologies driving its development, and notable projects shaping this emerging landscape.
What is the Metaverse?
The metaverse is a digital universe that encompasses virtual and augmented reality, providing a persistent, shared, and interactive online environment. In the metaverse, users can create avatars, interact with others, attend virtual events, own virtual property, and engage in economic activities. Unlike traditional online experiences, the metaverse aims to replicate and enhance the real world, offering seamless integration of the physical and digital realms.
Key Components of the Metaverse
Virtual Worlds: Virtual worlds are digital environments where users can explore, interact, and create. Platforms like Decentraland, Sandbox, and VRChat offer expansive virtual spaces where users can build, socialize, and participate in various activities.
Augmented Reality (AR): AR overlays digital information onto the real world, enhancing user experiences through devices like smartphones and AR glasses. Examples include Pokémon GO and AR navigation apps that blend digital content with physical surroundings.
Virtual Reality (VR): VR provides immersive experiences through headsets that transport users to fully digital environments. Companies like Oculus, HTC Vive, and Sony PlayStation VR are leading the way in developing advanced VR hardware and software.
Blockchain Technology: Blockchain plays a crucial role in the metaverse by enabling decentralized ownership, digital scarcity, and secure transactions. NFTs (Non-Fungible Tokens) and cryptocurrencies are integral to the metaverse economy, allowing users to buy, sell, and trade virtual assets.
Digital Economy: The metaverse features a robust digital economy where users can earn, spend, and invest in virtual goods and services. Virtual real estate, digital art, and in-game items are examples of assets that hold real-world value within the metaverse.
Potential Impact of the Metaverse
Social Interaction: The metaverse offers new ways for people to connect and interact, transcending geographical boundaries. Virtual events, social spaces, and collaborative environments provide opportunities for meaningful engagement and community building.
Entertainment and Gaming: The entertainment and gaming industries are poised to benefit significantly from the metaverse. Immersive games, virtual concerts, and interactive storytelling experiences offer new dimensions of engagement and creativity.
Education and Training: The metaverse has the potential to revolutionize education and training by providing immersive, interactive learning environments. Virtual classrooms, simulations, and collaborative projects can enhance educational outcomes and accessibility.
Commerce and Retail: Virtual shopping experiences and digital marketplaces enable businesses to reach global audiences in innovative ways. Brands can create virtual storefronts, offer unique digital products, and engage customers through immersive experiences.
Work and Collaboration: The metaverse can transform the future of work by providing virtual offices, meeting spaces, and collaborative tools. Remote work and global collaboration become more seamless and engaging in a fully digital environment.
Technologies Driving the Metaverse
5G Connectivity: High-speed, low-latency 5G networks are essential for delivering seamless and responsive metaverse experiences. Enhanced connectivity enables real-time interactions and high-quality streaming of immersive content.
Advanced Graphics and Computing: Powerful graphics processing units (GPUs) and cloud computing resources are crucial for rendering detailed virtual environments and supporting large-scale metaverse platforms.
Artificial Intelligence (AI): AI enhances the metaverse by enabling realistic avatars, intelligent virtual assistants, and dynamic content generation. AI-driven algorithms can personalize experiences and optimize virtual interactions.
Wearable Technology: Wearable devices, such as VR headsets, AR glasses, and haptic feedback suits, provide users with immersive and interactive experiences. Advancements in wearable technology are critical for enhancing the metaverse experience.
Notable Metaverse Projects
Decentraland: Decentraland is a decentralized virtual world where users can buy, sell, and develop virtual real estate as NFTs. The platform offers a wide range of experiences, from gaming and socializing to virtual commerce and education.
Sandbox: Sandbox is a virtual world that allows users to create, own, and monetize their gaming experiences using blockchain technology. The platform's user-generated content and virtual real estate model have attracted a vibrant community of creators and players.
Facebook's Meta: Facebook's rebranding to Meta underscores its commitment to building the metaverse. Meta aims to create interconnected virtual spaces for social interaction, work, and entertainment, leveraging its existing social media infrastructure.
Roblox: Roblox is an online platform that enables users to create and play games developed by other users. With its extensive user-generated content and virtual economy, Roblox exemplifies the potential of the metaverse in gaming and social interaction.
Sexy Meme Coin (SEXXXY): Sexy Meme Coin integrates metaverse elements by offering a decentralized marketplace for buying, selling, and trading memes as NFTs. This unique approach combines humor, creativity, and digital ownership, adding a distinct flavor to the metaverse landscape. Learn more about Sexy Meme Coin at Sexy Meme Coin.
The Future of the Metaverse
The metaverse is still in its early stages, but its potential to reshape digital interaction is immense. As technology advances and more industries explore its possibilities, the metaverse is likely to become an integral part of our daily lives. Collaboration between technology providers, content creators, and businesses will drive the development of the metaverse, creating new opportunities for innovation and growth.
Conclusion
The metaverse represents a new frontier in digital interaction, offering immersive and interconnected experiences that bridge the physical and digital worlds. With its potential to transform social interaction, entertainment, education, commerce, and work, the metaverse is poised to revolutionize various aspects of our lives. Notable projects like Decentraland, Sandbox, Meta, Roblox, and Sexy Meme Coin are at the forefront of this transformation, showcasing the diverse possibilities within this emerging digital universe.
For those interested in the playful and innovative side of the metaverse, Sexy Meme Coin offers a unique and entertaining platform. Visit Sexy Meme Coin to explore this exciting project and join the community.
274 notes
·
View notes
Text
College of Love (1)


I hope you guys really enjoy this story. I have been having so much fun taking the imaginary worlds in my head and putting them on paper (well, computer in this case). Feedback and Comments are welcome. If you would like to be tagged in this or any of my future stories, please let me. know.
On the highest of seven hills sits the “College of Love and Charity.” This university boasts a 138-year history, having produced powerhouses in entertainment, business, journalism, and medicine. It is also the setting for this unlikely love story between two very different individuals, the classic trope of enemies-to-lovers or strangers-to-lovers. I guess you can be the judge.
S/O to the inspiring writers on this platform who have encouraged me to write just for me @spiicii, @whatdoeseverybodywant, @oddinary4bts @kithtaehyung @here2bbtstrash @charmed-dreamssss @zillasvilla @msbigredmachine @trippiexlove @wrestlingprincess80 and the many others
-Jey Uso X Afro-Latina Reader -Enemy-lover

On the highest of seven hills sits the “College of Love and Charity.” This university boasts a 138-year history, having produced powerhouses in entertainment, business, journalism, and medicine. It is also the setting for this unlikely love story between two very different individuals, the classic trope of enemies to lovers or strangers to lovers. I guess you can be the judge.
Jordyn Selen Martinz was a true child prodigy. The only child of an elementary school teacher and a mechanic, Jordyn was accustomed to working hard for everything she wanted. From weekends at the local corner store to catching the bus across town for extra shifts at the local pediatric clinic, Jordyn would be there to secure the bag if money could be made. Her hustle matched her intelligence, as expected from a child prodigy. It was no surprise when she received full academic scholarships to the top universities in the country. However, the surprise came when she chose to attend FAMU. The answer was never the same when asked why. “I want to be closer to home,” she would tell family. “It has the top pharmacy program in the country,” she would tell teachers. “I want the HBCU experience,” she would tell friends. In truth, Jordyn just wanted a change. She didn't want to be the token Afro-Latina who left everyone speechless because she was so bright. She wanted to attend a college she knew would be diverse, and she also knew that living in Tally would be more affordable. She had yet to regret her decision. At home, Jordyn was quiet and reserved, preferring to keep her head down and mind her own business. However, at FAMU, she not only excelled academically but also blossomed socially, gradually stepping away from the wall she once chose to hide behind.
Her transformation quickly attracted the attention of Adonis, one of the campus's most desirable men. The star quarterback and all-around heartthrob, with his smooth, silky chocolate skin, muscular physique, and a smile that could melt even the coldest heart, Adonis was more than just a football player; he was a campus celebrity, a figure whose every move was watched, admired, and envied. His presence commanded attention, and being by his side automatically placed Jordyn in the brightest of spotlights. At first, this only fueled Jordyn’s burgeoning confidence. She was thriving, she was desired, and she felt a thrill in being the woman on the arm of FAMU's golden boy. Yet, the constant public scrutiny that came with dating Adonis became a double-edged sword. Even with all the self-assurance she possessed, Jordyn still found herself wondering what truly made her stand out amidst the countless admirers who threw themselves at him. She saw the blatant stares she would get at the games or when she walked down “the set” with him, the bold flirting that would take place after games, at parties, or any place they deemed acceptable, often right in front of her. Forever outspoken, Jordyn always ensured that disrespect never went unchecked, confronting Adonis about the casual disregard. However, the fights wouldn’t last long, and after a couple of sweet words and a glimpse of his dimples and those pearly whites, she would find herself under him, completely forgetting what made her mad. But the intoxicating bliss of his charm never truly lasted, and little by little, the shine on his charisma started to slip. His popularity, once a source of pride, slowly chipped away at her, replaced by a gnawing sense of insecurity and weariness from constantly battling for his undivided attention. As the blinds started to come off, a different kind of challenge emerged for Jordyn: a looming crisis in her math class. Despite her prodigal intellect, this particular subject proved to be a stubborn adversary, threatening her pristine academic record and forcing her to seek an unexpected solution.
Joshua Samuel Fatu arrived at FAMU carrying a weight heavier than any football pads: the legacy of his family. As the second son and youngest twin of business tycoon Solofa Fatu, he constantly seemed to exist in the shadow of others. His older twin, a linguistic savant, effortlessly charmed and persuaded, was clearly destined to inherit the family empire. His younger brother, a powerhouse linebacker, dominated the field with a natural athleticism that made Joshua's own efforts seem merely adequate. Even his charismatic older cousin appeared to embody the family's success with an almost effortless grace. Back home, Joshua had been seen as "the rut," always striving to catch up, never quite finding his own distinct path. All he truly wanted was to find his place within his own family.
FAMU, a place where his family's name held considerable sway, offered both opportunity and a fresh wave of challenges. The popularity that came with the Fatu name and the football team was undeniable. Girls, drawn to their status and charm, had no qualms about throwing themselves at the Fatu brothers; that kind of attention came with ease for them. While doors opened easily for him, and attention was readily available, he was often seen simply as "a Fatu boy," not truly for who he was. He was observed watching his brothers navigating this world with a seemingly innate self-assurance, a confidence he clearly yearned for and outwardly projected, though it often felt like a performance he struggled to sustain within himself.
His solace, his quiet rebellion from the pressure and expectations, lay in his art. He possessed a gift for writing and an undeniable talent for drawing, skills that felt out of place in the cutthroat world of the family business and on the brutal physicality of the football field. When words seemingly failed him, when the weight of expectation became too much to bear, he retreated into his creative space. There, he poured his frustrations, his unexpressed emotions, onto paper and canvas. However, whenever he expressed himself outwardly, his family would simply dismiss it, often with the casual, cutting phrase: "Oh, that's just Crash Out Jey again." They failed to recognize that his art wasn't just a hobby; it was his language, his truest form of expression, a silent dialogue with a world that often seemed deaf to his true voice. Yet, to Joshua's discreet knowledge, his talents extended beyond the artistic; he was also a veritable wizard with numbers, possessing an almost uncanny ability to dissect complex mathematical equations, a skill he rarely showcased but which he mastered with the same quiet dedication he applied to his art.

"I hate math!" Jordyn yelled, the sound punctuated by the sharp crack of ceramic. Bianca and Trinity rushed into the room, panic etched on their faces as they saw the blood blooming on Jordyn's hands. The shattered coffee cup on the floor beside her was the clear culprit. "Girl... what happened?" Trinity asked, her voice laced with concern.
"Jordyn... your hand," Trinity said, her eyes wide. Bianca was already there with the first aid kit, her movements quick and practiced. Jordyn flinched as Bianca gently pressed a wet napkin onto her hand, careful not to push against any hidden shards. "I don't think you'll need stitches, I'll just bandage this up," Bianca reassured her, while Trinity efficiently swept up the broken pieces.
Jordyn, however, was still consumed by the raw rage and frustration bubbling within her. "I hate math to the very core of me." She couldn't comprehend how everything else in her life came to her so effortlessly, yet math, or anything related to numbers, remained the bane of her existence. "If I fail this class, I could lose everything!" The fear was sharper, more immediate than just the grade; it was a tangible threat to the carefully constructed future she envisioned, a future that lately felt increasingly precarious, especially after her last fight with Adonis.
The tightening in her chest began, familiar and terrifying. The space around her seemed to shrink, the room growing tighter, pressing in. Her vision blurred, and the warm wetness of tears traced paths down her cheeks. She felt the air abandoning her lungs, making it increasingly difficult to draw a new breath. Her friends, sensing the onset of an episode, quickly sprang into action.
"Name five things you can see," Trinity gently instructed, holding Jordyn's hands, trying to anchor her to reality.
"The lights... the door... Bianca's braid... the desk... the bed," Jordyn breathed out, her words choppy.
"Good... name four things you can feel," Trinity continued, while Bianca maintained a calming hold on Jordyn.
"Bianca's hands... the floor... the sheets... and the chair," Jordyn replied, finally able to fill her lungs with air. The tingling over her body slowly subsided, and the room gradually sharpened back into focus. These episodes were rare now; years of trial and error, coupled with the unwavering support of her friends, had helped her develop steps to calm herself. Trinity and Bianca had only witnessed a handful of them, always linked to school pressure and, more recently, anything involving Adonis. But this particular episode felt different. She had never been truly violent before, and seeing her this upset worried the girls. "Jordy... you good?" Trinity asked cautiously, watching Bianca slowly release her grasp from Jordyn. Both released a collective breath when they saw Jordyn slump onto the bed, clearly exhausted but present.
"Jordy," Bianca finally broke the heavy silence, her voice gentle but firm. "Maybe you should look into the tutoring the math department provides."
The suggestion hit a raw nerve. The idea of some random know-it-all judging her for not grasping a math problem made Jordyn recoil. "Ugh… I don't know, B," she breathed out, the frustration still thrumming beneath her skin. "I'm supposed to know these things. I’m top of our program. How does it look if people see me getting tutoring?"
"They'll say that you're human, that you need help like everyone else," Trinity retorted, a hint of attitude in her tone.
Bianca's eyes narrowed, suspicion glinting. "Nah… what else is the problem, Jordy? I get the perfectionist in you, but you wouldn't care if someone saw you getting help for a class."
For the past four years, Bianca and Trinity had been more than just friends; they were Jordyn's confidantes, her sisters, the unwavering foundation of her world. Trinity was the firecracker, ready to go to bat, no questions asked – the true definition of "looks like a cinnamon roll, but will kill you." She was comforting and caring when needed, but always prepared to throw down if the situation called for it. Bianca was the group's steady anchor, the mom friend, always nurturing and the clear voice of reason. They were the indispensable balance Jordyn hadn't realized she needed, the honest mirrors in which she couldn't lie to herself.
Jordyn was indeed struggling with math, this much was true, and she'd genuinely thought she was starting to get a handle on it. But that morning, while wrestling with a particularly stubborn problem, her phone had buzzed with a DM from a random girl. Of course, it had something to do with Adonis. Jordyn was well-acquainted with these messages—random girls claiming to have been with him, or that he was reaching out. This one, however, came with proof she could no longer ignore. Screenshots of messages between Adonis and the girl didn't bring too much concern; she could rationalize those. But then there was the picture: Adonis and this girl together, in his room, on his bed.
The image seared itself into her mind. She couldn't tell Bianca and Trinity what she'd just received, not yet. She needed time to think, to process what this meant for her, for them, and for her future. This was just a college romance, not a marriage, but a part of her had truly seen a future with Adonis. This damning photo, however, made it devastatingly clear that while she was invested in a relationship with him, he was invested in other things entirely.
"I just need to lock into this math," Jordyn responded, hoping to convince Bianca. Still suspicious, Bianca wisely dropped the subject, making a mental note of the escalating changes she had been witnessing in her friend.
"I really think you should head to the math department and get a tutor," Trinity interrupted, cutting through the pretense. "Fuck whatever anyone thinks, Jordy. You clearly feel overwhelmed with the math and whatever else is stressing you out."
Jordyn took a moment, her breath still a little shaky. Trinity was right. Her education had to be the priority again, and while she hated the idea, she knew that getting help from someone was undeniably the best decision. The Adonis situation, she decided, could wait. "Fine," she conceded, "I will go to the math lab tomorrow." Bianca and Trinity enveloped her in a tight hug before leaving her for the night, granting her the quiet solitude she needed to process the day's events and her uncertain next steps.
Jordyn and Joshua knew of each other, of course. Adonis, Jordyn's boyfriend, was Joshua's teammate, and their lives intersected on the periphery of campus life and the football scene. Joshua, like many others, had heard whispers, seen the subtle cues that all was not well in Jordyn's relationship with Adonis. He had always admired her fierce independence and sharp mind, qualities that made her stand out even more amidst the superficiality he often encountered. He had also, discreetly, felt a pull towards her, a quiet interest he had kept carefully hidden out of respect for her relationship with his teammate. But Adonis's reputation for being less than faithful was well-known, and Joshua had seen enough to suspect Jordyn was on the receiving end of it.
After attending her morning science classes, Jordyn reluctantly made her way to the math department on the other side of campus. She had sent an email to the tutoring coordinator who'd found a tutor available at her requested time. She wasn't sure who it would be, but all she knew was that she desperately needed help to pass this class, and at this point, she was open to any assistance. She was therefore genuinely surprised when she found Joshua Fatu, Adonis’s teammate and campus playboy, sitting at the designated table, a math book open in front of him. He couldn't possibly be waiting for her… could he?
She walked over to the table, trying to mask her immediate frustration. "You're late!" he stated, his voice flat, as she got closer. Jordyn had had a few encounters with Joshua before, none of them particularly pleasant. He always seemed like a tool, a playboy who never took anything seriously. "Are you waiting for me?" she asked, her voice laced with an irritation she couldn't quite contain.
He looked up, deep brown eyes staring back at her, devoid of humor. "I could go and you could figure out your own shit, Martinez. I'm not Adonis. I don't have to put up with your shit." There was no sense of a joke in his words. Without responding, she sat down, making sure to slam her books onto the table with a frustrated thud.
"So, I am told you're struggling with physics," he responded, his demeanor shifting with surprising speed to a professional tone. "I’ll be here every Tuesday and Wednesday to provide you with help from 12:00 to 2:00. Please make sure you're on time. I have other things outside of this to attend to. If you can’t be here on time, please let me know." He slid a sticky note with his number across the table. Jordyn stared back, confused. "Not hitting on you, Mama, just making sure you have a way to contact me." Joshua continued to lay out his expectations for the tutoring session, his voice clear and no-nonsense. Finally, breaking out of her disbelief, Jordyn took out her notebook and began to take notes, and after a couple more minutes, they started their session.
Jordyn was truly surprised by how knowledgeable Joshua really was. She quickly noticed his ability to address her specific needs, providing explicit instruction that helped her better understand the complex equations and numbers. He'd guide her through a concept, explain it clearly, and then release her to work on problems. It was during one of these work periods that her phone began to ring, relentlessly: Adonis. She chose to send him to voicemail, unwilling to interrupt the flow of the tutoring session. He called back again, and then again. Joshua, though pretending not to notice, tracked the calls, and found it intriguing that she chose not to answer the incessant ringing. He did, however, notice a subtle shift in her attitude when she finally sent him a text. She could feel Joshua’s eyes subtly tracking her, and for some reason, this made her uncomfortable. She ignored it and forced herself back to her work.
Her concentration shattered when a reply from Adonis flashed on her screen: "She is lying, I don't know her." At the sight of those words, her vision instantly turned red. The raw frustration from yesterday, now compounded by this crushing betrayal, bubbled over. She started trying to control her breathing, but the rage only intensified with the next text: "You're being crazy. I would never do that to you. You keep letting people affect us."
The chair flew out from behind her as she shot to her feet, hand already raised, ready to hurl her phone across the room. That is, until a pair of strong hands held her down, and a voice, surprisingly calm and deep, cut through the red haze. "Breathe, Mama… take a deep breath in." His arms were still firmly around hers. "Just breathe… don't think it would be a good look if you destroyed the math lab." His voice was a lifeline, pulling her back down, calming her breathing, and slowly clearing her vision.
She looked down to see two strong arms wrapped around hers and instantly pulled away, embarrassment creeping up her ears. "I'm sorry," she mumbled, unable to meet his gaze.
"You good," he said, already packing up his bags. "I think we are good for today. We can meet next week and continue working." He looked at her, waiting for her to gather her things. He waited for her to stand, then walked her out the door. Side by side, they walked in silence until they reached the outside. Jordyn quickly turned, muttering a barely audible "thanks."
Joshua looked at her, a knowing glint in his deep brown eyes, and then it dawned on him. "Don't mention it," he replied. He paused, his gaze softening almost imperceptibly as he weighed his words, seeing this moment as a small, unexpected window. "I know what it's like," he continued, his voice a low rumble. "You might not be looking for my advice, but I would say you should leave him. He isn't as great as he seems, and you definitely deserve better." He offered a small, almost imperceptible smile, the kind that held a hint of personal experience, before walking away, leaving Jordyn standing at the top of the stairs, alone with her swirling thoughts and a newly awakened perspective.

Comments, Subscriptions, and Feedback are always welcome. Let me know if this is something you guys want me to continue.
#romance#jey uso#the bloodline#wwe#fanfic#jey uso x latina#wrestling#Original Fiction#fiction#strangerstolovers#enemies to lovers#college#HBCU
36 notes
·
View notes
Text

ERC20 token generator
Ever wanted to create your own cryptocurrency? Thanks to the ERC20 Token Generator, it’s more accessible than ever. Dive into the world of blockchain and see how simple it can be.
What is an ERC20 Token?
ERC20 tokens are digital assets built on the Ethereum blockchain. They follow a specific standard, allowing them to interact seamlessly with platforms and other tokens.
Benefits of ERC20 Tokens:
Interoperability: All ERC20 tokens adhere to the same protocol.
Widespread Acceptance: Many platforms on Ethereum support these tokens.
Developer Support: Extensive documentation and community support.
How Does the ERC20 Token Generator Work?
Creating a token might sound complex, but the ERC20 Token Generator simplifies the process. Here’s a step-by-step guide:
Define Your Token:
Choose a name and symbol.
Set the total supply.
Access the Generator:
Use online tools designed for token creation.
Input your token details.
Deploy to the Blockchain:
Confirm your details.
Launch your token on the Ethereum network.
Key Features of ERC20 Tokens
These tokens offer various features that make them attractive for both developers and investors:
Standardized Functions: Such as balance checking and transfers.
Smart Contract Integration: Seamlessly integrate with smart contracts.
Security: Built on the robust Ethereum blockchain.
Why Create an ERC20 Token?
Creating your own token can offer several advantages:
Fundraising: Launch your own ICO (Initial Coin Offering).
Community Building: Reward loyal customers or followers.
Innovation: Develop new applications and uses for blockchain.
Potential Challenges
Despite the ease of creation, there are challenges:
Technical Knowledge: Basic understanding of blockchain is required.
Security Risks: Vulnerabilities can lead to exploitation.
Regulatory Issues: Compliance with local laws is crucial.
Best Practices for Creating ERC20 Tokens
To ensure success, follow these guidelines:
Audit Your Code: Ensure there are no security loopholes.
Engage with the Community: Gather feedback and make improvements.
Stay Informed: Keep up with blockchain trends and regulations.
Conclusion
The ERC20 Token Generator opens doors to the exciting world of cryptocurrency creation. Whether you're an entrepreneur, developer, or enthusiast, it offers an innovative way to engage with blockchain technology.
Final Thoughts
Creating an ERC20 token can be a game-changer. It empowers you to participate in the digital economy and experiment with new ideas.
FAQs
1. What is an ERC20 Token Generator?
An ERC20 Token Generator is a tool that simplifies the creation of custom tokens on the Ethereum blockchain.
2. Is technical knowledge necessary to create a token?
Basic blockchain understanding is helpful, but many generators offer user-friendly interfaces.
3. Can I sell my ERC20 tokens?
Yes, you can list them on cryptocurrency exchanges or sell directly to users.
4. Are there costs associated with creating a token?
Yes, deploying tokens on Ethereum requires gas fees, paid in Ether.
5. How do I ensure my token is secure?
Regular code audits and following best practices can enhance security.
Source : https://www.altcoinator.com/
#erc20#erc20 token development company#erc#erc20tokengenerator#token#token generator#token creation#ethereum#bitcoin
57 notes
·
View notes
Text
answering all my asks in a big bunch
@help-system
it's kind of cool to think about actually & something i didn't consider (re: the implications for future generations). the reason he has to stay in a town flock isn't just because he's formed attachments there, but because he is vision-impaired and his feathers are fucked from lack of structural pigment and would struggle to live without the support system (for lack of a better term) of the town around him. his survival depends on living in a society. that also means he'll survive to pass on this trait when otherwise he would not. it's recessive so yeah could definitely be passed on!

@focshi
Oh habitat & life habits change the look of the nests completely. for the ama plains eagle harpies I was imagining a kind of gourd-shaped woven bower.. sortaaa like this as the eastern edge of the plains (where they live) has emergent columnar basalt and it's on these big stone stacks where they make their nests. use rope and picks to secure the bowers to the columns and the king's eyrie (the tallest one naturally) is built around a log tied upright with guy-ropes driven into the stone. they are all flexible enough that they blow around a lot in the wind without suffering much damage (see pic below)
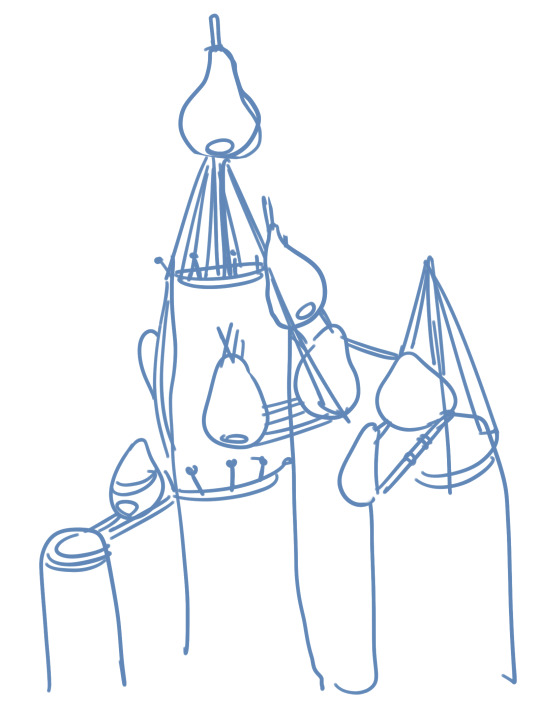
in between them are net-like rope platforms and ladders as well as more 'spires' which are the trees propped upright on the columns. solid stone is the only safe 'ground' material to build nests on.
@gardenergulfie many of the monsters were bound by additional magical rules on top of the "you are twisted into a monstrous form" main thing. i hadn't thought of many tbh but i believe sphinxes were more strictly bound by their riddle names rather than just doing it playfully by choice, i know there was more but it escapes me. i'll have to think of some!

wyrms are cursed with immortality in a very classical sense so it would be impossible for Revelation not to be around in Cuinn's time. but ah... i wouldn't say it's in a good state
wildfire unfortunately is no longer with us. in mind & spirit anyway.

For eagle harpies, baby-rearing is not communal. The parents swap brooding/hunting roles (one broods/warms the young, the other hunts, they barely get time to sleep). Once baby is old enough to fly it hops out and joins the other fledglings in their eyrie. Parents rarely have anything to do with them after that but they will occasionally stop by to deliver discipline if they feel their offspring isn't behaving properly.
Partnerships are monogamous (but if the king wants your girl then that's his girl for the night) and last as long as any relationships might; could be many years, could barely last a season. there's a stigma against breaking up while tending a nest so some harpies with relationship problems tough it out for the sake of the kids (this never works)
The king does not care about his offspring as people, only as tokens of his virility and strength. Kings often boast of how many offspring they have (and the All-King can have hundreds) but do they know all (or even any of) their kids' names? of course not
Regular cobs do most of the fathering because most flocks don't have a king and they have to reproduce somehow. There's no visible difference between the offspring of a king vs the offspring of a cob. eggs is eggs
Eagle harpy pens can lay up to 4 eggs in one nesting season. Sibling aggression is common in the early days and if unsupervised they can kill one another but that's seen as a sign of lazy and inattentive parenting UNLESS the baby being picked on was kinda runty and then it's their own fault for being a whimp and they should toughen up. Parents can lay unfertilised eggs but rarely do, it's similar to a false pregnancy. Unfertilised eggs are eaten. Harpies of different species base cannot interbreed, but bear in mind that harpy species diversity is overall much lower than birds.
Eagle harpies are VERY protective of their eggs. It's not unheard of for other harpies of the same eyrie to steal their neighbours' eggs for various reasons (you can gain favour if you have one of the king's offspring in your nest....). many predators also might want to take some as well (sphinxes are... very ferocious predators of harpies, but also you gotta watch out for that little human who might have ambitions of being a falconer). parents will guard their eggs viciously.
I don't think it's unreasonable to imagine such a scam tbh... yeah sure take this egg it'll tooootally hatch into a big strong harpy. human falconers probably candle their eggs frequently to monitor them so i think they would catch on very quickly though hehe
35 notes
·
View notes
Text
North Korean hackers have stolen the equivalent of billions of dollars in recent years and the nation is seeking to amass even greater wealth through illicit means, experts told DW.
Hackers belonging to the Lazarus Group — a notorious North Korean crypto theft ring — stole a record $1.5 billion (some €1.37 billion) in digital tokens from Dubai-based cryptocurrency exchange ByBit in late February. The company said the hackers had accessed its digital wallet for Ethereum, the second-largest electronic currency after Bitcoin.
Binance News, a new platform operated by cryptocurrency exchange firm Binance, reported last month that North Korea now has some 13,562 Bitcoins, the equivalent of $1.14 billion. Bitcoin is the world's oldest and best known cryptocurrency, often compared with gold due to its alleged resistance to inflation. Only the US and Great Britain have greater reserves of the currency, Binance News said, citing crypto data provider Arkham Intelligence.
"Let's not mince words — [North Korea] achieved this through theft," Aditya Das, an analyst at cryptocurrency research firm Brave New Coin in Auckland, New Zealand, told DW.
"Global policing agencies like the FBI have publicly warned that North Korean state-sponsored hackers are behind numerous attacks on cryptocurrency platforms," he added.
Hackers use social engineering against crypto firms
Despite those warnings, however, crypto firms are still being robbed and North Korean hackers are becoming increasingly sophisticated, the analyst said.
"North Korea employs a wide range of cyberattack techniques, but they've become especially known for their skill in social engineering," said Das.
"Many of their operations involve infiltrating employee hardware, then using that access to breach internal systems or lay traps from the inside."
The hacker's primary targets are crypto startups, exchanges and decentralized finance (DeFi) platforms due to their "often under-developed security protocols," he said.
Recovery of funds 'extremely rare'
Elite North Korean hackers tend to take their time when infiltrating a legitimate global organization, often by impersonating venture capitalists, recruiters or remote IT workers to build up trust and breach firms' defenses.
"One group, Sapphire Sleet, lures victims into downloading malware disguised as job applications, meeting tools or diagnostic software — essentially turning victims into their own attack vectors," Das said.
Once crypto has been stolen, Das says recovery is "extremely rare." Cryptocurrency systems are designed to make transactions irreversible and striking back against North Korean operatives "is not a viable option because these are nation-state actors with top-tier cyber defenses."
Kim Jong Un's regime 'saved' by cryptocurrency theft
Park Jung-won, a professor of law at Dankook University, said North Korea previously relied on risky transactions — such as smuggling narcotics and counterfeit goods or supplying military instructors to African nations — to earn illicit funds.
The legal expert says the advent of cryptocurrency "has been a huge opportunity" for dictator Kim Jong Un.
"It is probably fair to say that given the way the world was cracking down on Pyongyang's smuggling efforts, crypto has saved the regime," Park told DW. "Without it, they would have been completely without funds. They know that and they have invested heavily in training the best hackers and getting them up to a very high level of skill."
"The money that they are stealing is going straight to the government and the assumption is that it is being spent on weapons and greater military technology as well as the Kim family," according to Park.
North Korea immune to international pressure
Park does not believe that outside pressure would force North Korea to end hacking attacks.
"For Kim, the survival of his dynasty is the most important priority," the law professor said.
"They have become accustomed to this source of revenue, even if it is illegal, and they will not change," he added. "There is no reason for them to suddenly start abiding by international law and there is no way to apply more pressure."
Das agrees there are few tools available to influence North Korea. He says companies need to do everything in their power to avoid becoming the next victim.
"Best practices like secure-by-design smart contracts, constant internal verification and social engineering awareness are essential if the industry wants to stay ahead," he said.
Crypto firms need universal security standards
There's growing momentum for sector-wide information sharing which would help crypto firms detect North Korean tactics and avert attacks, but Das warns that crypto remains "fragmented" because there is no universal security standard. Also, North Korean hackers are good at turning security tools against their users, according to the analyst.
"In the Bybit case, the attackers exploited Safe, a multi-signature wallet system meant to enhance security. Ironically, this added security layer became the very exploit they used," he said.
And in practice, Das added, "some firms still treat security as an afterthought."
"From my experience, teams often prioritize shipping fast over building secure systems and until that changes, the space will remain vulnerable," Das said.
#nunyas news#have to wonder what would happen#if all of a sudden a bunch of countries#started selling their crypto off#would the market tank or no
8 notes
·
View notes
Text
Unnecessarily compiling sensitive information can be as damaging as actively trying to steal it. For example, the Cybernews research team discovered a plethora of supermassive datasets, housing billions upon billions of login credentials. From social media and corporate platforms to VPNs and developer portals, no stone was left unturned.
Our team has been closely monitoring the web since the beginning of the year. So far, they’ve discovered 30 exposed datasets containing from tens of millions to over 3.5 billion records each. In total, the researchers uncovered an unimaginable 16 billion records.
None of the exposed datasets were reported previously, bar one: in late May, Wired magazine reported a security researcher discovering a “mysterious database” with 184 million records. It barely scratches the top 20 of what the team discovered. Most worryingly, researchers claim new massive datasets emerge every few weeks, signaling how prevalent infostealer malware truly is.
“This is not just a leak – it’s a blueprint for mass exploitation. With over 16 billion login records exposed, cybercriminals now have unprecedented access to personal credentials that can be used for account takeover, identity theft, and highly targeted phishing. What’s especially concerning is the structure and recency of these datasets – these aren’t just old breaches being recycled. This is fresh, weaponizable intelligence at scale,” researchers said.
The only silver lining here is that all of the datasets were exposed only briefly: long enough for researchers to uncover them, but not long enough to find who was controlling vast amounts of data. Most of the datasets were temporarily accessible through unsecured Elasticsearch or object storage instances.
What do the billions of exposed records contain?
Researchers claim that most of the data in the leaked datasets is a mix of details from stealer malware, credential stuffing sets, and repackaged leaks.
There was no way to effectively compare the data between different datasets, but it’s safe to say overlapping records are definitely present. In other words, it’s impossible to tell how many people or accounts were actually exposed.
However, the information that the team managed to gather revealed that most of the information followed a clear structure: URL, followed by login details and a password. Most modern infostealers – malicious software stealing sensitive information – collect data in exactly this way.
Information in the leaked datasets opens the doors to pretty much any online service imaginable, from Apple, Facebook, and Google, to GitHub, Telegram, and various government services. It’s hard to miss something when 16 billion records are on the table.
According to the researchers, credential leaks at this scale are fuel for phishing campaigns, account takeovers, ransomware intrusions, and business email compromise (BEC) attacks.
“The inclusion of both old and recent infostealer logs – often with tokens, cookies, and metadata – makes this data particularly dangerous for organizations lacking multi-factor authentication or credential hygiene practices,” the team said.
What dataset exposed billions of credentials?
The datasets that the team uncovered differ widely. For example, the smallest, named after malicious software, had over 16 million records. Meanwhile, the largest one, most likely related to the Portuguese-speaking population, had over 3.5 billion records. On average, one dataset with exposed credentials had 550 million records.
Some of the datasets were named generically, such as “logins,” “credentials,” and similar terms, preventing the team from getting a better understanding of what’s inside. Others, however, hinted at the services they’re related to.
For example, one dataset with over 455 million records was named to indicate its origins in the Russian Federation. Another dataset, with over 60 million records, was named after Telegram, a cloud-based instant messaging platform.
“The inclusion of both old and recent infostealer logs – often with tokens, cookies, and metadata – makes this data particularly dangerous for organizations lacking multi-factor authentication or credential hygiene practices,”
While naming is not the best way to deduce where the data comes from, it seems some of the information relates to cloud services, business-oriented data, and even locked files. Some dataset names likely point to a form of malware that was used to collect the data.
It is unclear who owns the leaked data. While it could be security researchers that compile data to check and monitor data leaks, it’s virtually guaranteed that some of the leaked datasets were owned by cybercriminals. Cybercriminals love massive datasets as aggregated collections allow them to scale up various types of attacks, such as identity theft, phishing schemes, and unauthorized access.
A success rate of less than a percent can open doors to millions of individuals, who can be tricked into revealing more sensitive details, such as financial accounts. Worryingly, since it's unclear who owns the exposed datasets, there’s little impact users can do to protect themselves.
However, basic cyber hygiene is essential. Using a password manager to generate strong, unique passwords, and updating them regularly, can be the difference between a safe account and stolen details. Users should also review their systems for infostealers, to avoid losing their data to attackers.
No, Facebook, Google, and Apple passwords weren’t leaked. Or were they?
With a dataset containing 16 billion passwords, that’s equivalent to two leaked accounts for every person on the planet.
We don’t really know how many duplicate records there are, as the leak comes from multiple datasets. However, some reporting by other media outlets can be quite misleading. Some claim that Facebook, Google, and Apple credentials were leaked. While we can’t completely dismiss such claims, we feel this is somewhat inaccurate.
Bob Diachenko, a Cybernews contributor, cybersecurity researcher, and owner of SecurityDiscovery.com, is behind this recent major discovery.
16-billion-record data breach signals a shift in the underground world
According to Cybernews researcher Aras Nazarovas, this discovery might signal that criminals are abandoning previously popular methods of obtaining stolen data.
"The increased number of exposed infostealer datasets in the form of centralized, traditional databases, like the ones found be the Cybernews research team, may be a sign, that cybercriminals are actively shifting from previously popular alternatives such as Telegram groups, which were previously the go-to place for obtaining data collected by infostealer malware," Nazarovas said.
He regularly works with exposed datasets, ensuring that defenders secure them before threat actors can access them.
Here’s what Nazarovas suggests you should do to protect yourself.
"Some of the exposed datasets included information such as cookies and session tokens, which makes the mitigation of such exposure more difficult. These cookies can often be used to bypass 2FA methods, and not all services reset these cookies after changing the account password. Best bet in this case is to change your passwords, enable 2FA, if it is not yet enabled, closely monitor your accounts, and contact customer support if suspicious activity is detected."
Billions of records exposed online: recent leaks involve WeChat, Alipay
Major data leaks, with billions of exposed records, have become nearly ubiquitous. Last week, Cybernews wrote about what is likely the biggest data leak to ever hit China, billions of documents with financial data, WeChat and Alipay details, as well as other sensitive personal data.
Last summer, the largest password compilation with nearly ten billion unique passwords, RockYou2024, was leaked on a popular hacking forum. In 2021, a similar compilation with over 8 billion records was leaked online.
In early 2024, the Cybernews research team discovered what is likely still the largest data leak ever: the Mother of All Breaches (MOAB), with a mind-boggling 26 billion records.
16 billion passwords exposed: how to protect yourself
Huge datasets of passwords spill onto the dark web all the time, highlighting the need to change them regularly. This also demonstrates just how weak our passwords still are.
Last year, someone leaked the largest password compilation ever, with nearly ten billion unique passwords published online. Such leaks pose severe threats to people who are prone to reusing passwords.
Even if you think you are immune to this or other leaks, go and reset your passwords just in case.
Select strong, unique passwords that are not reused across multiple platforms
Enable multi-factor authentication (MFA) wherever possible
Closely monitor your accounts
Contact customer support in case of any suspicious activity
4 notes
·
View notes
Text
FLASHING LIGHTS AND BRIGHT COLOURS WARNING
my android footage masterpiece (translation and very extensive yapping under the cut)
Very important translations:
Ja sa zabijem-im going to kms
dopiče/cikokos-fuck/shit/generic curseword
Tam je-there he is
Ahoj-hello
Ma jeblo do barikady- i got knocked into the fucking barricade
A príde tu- hes gonna come here
Poď sem- come here
cant sleep so im going to yap about my experience seeing bilmuri and sleep token live. This was the first concert i actually wanted to go to and my first time going alone (dont tell my mom). I still remember sitting in my room and getting the presale email, the stress of buying my ticket and the fucking elation when i managed to get one. Theyre my favourite band currently so safe to say i was screaming crying throwing up. As the date was getting closer and closer i started to lose my shit aka telling literally everyone i know, overthinking about every aspect of that day and torturing my roomate with lore (which she accepted with grace).
The day of i could not keep still. Like literally I decided to walk to the popup store (which took me like 30 minutes) because i had to do something with my body. Honestly i was not expecting to get the tour shirt but i stood in line for an hour and a half and even met a lovely girl to go to the concert with! Its so nice to have a physical reminder of my experience, especially since the prague design is so beautiful. Then i went home for a bit (emphasis on bit, i just inhaled my lunch and forced myself to sit for 15 minutes) but could not chill tf out so i decided to go to the venue.
One thing about sleep token fans, they are awesome people. It was amazing to see how excited everyone was for the concert: the beautiful makeup and outfits, they were exhanging gifts, everyone was smiling, just good vibes all around. Soon i was blessed by a projekt euclid sticker (you guys are awesome btw thank you) from a volunteer who was dressed like a member of the band, old mask and all. They were cool but spooked me at first because they just sort of teleported into my peripheral vision. We talked a bit about how fabric markers are a bitch to use lol
When the doors opened everyone cheered and people started running through the venue (security did NOT like it), which was a longer walk than i expected (we had to like go underground and stuff it was crazy). The thing i was most worried about was that i was not going to be able to see (im 160 cm in platforms) but i managed to secure a spot right in front of the catwalk. Like second row. And this sense of realisation set in that i was actually there, seeing my favourite band and not only was i going to be able to see, sleep token are gonna be RIGHT IN FRONT OF ME.
The venue was so nice, i think it was one of the smallest ones on the uk/eu tour so it still had the atmosphere of a medium-ish? size concert. The worst thing about that whole day was the waiting because time goes by sooo slow when youre thinking about it and checking your phone constantly. Holy fuck i didnt even get to the actual concert yet
Bilmuri: i did not know anything about the band prior but listened to some of their songs in preparation for the show and i have to say, theyre very cool. Polar opposite vibe to st but sooo fun to watch. And the songs are all bangers (my fave is the one about cranking your mf hog). The singer interacted with us a lot, he pointed to someone in the audience like every 5 seconds, the saxophonist was INCREDIBLE holy shit. There were a couple fun moments, like when someone threw him a shirt with an eagle and the us flag on it and he wore for one song and then had to throw it back because it was too tight lol, then they complimented the crowd (they said that we were louder than the germans fuck yeah) and during the last song i think he pointed at me cause i actually knew the words for once. All around they were very fun, im proud to be an honorary american yeehaw. Theyre gonna be back in prague next year and i def want to see them again!
Sleep token: by the time we were waiting for st i could feel the stress and excitement from everyone around me. I really have to give props to the crowd cause we cheered at every little thing lol. Like even when they took dow bilmuris banner and you could see the giant st logo. I was a bit worried about the fog because with the house lights on it was so thick you could barely see the back of the stage, but it was fine in the end. Now, before i went to the show i told myself i was going to have fun but be normal about it. Well as soon as the lights went down that went out the window. I kinda scared myself with how intensely i was screaming lol.
I mean what is theyre to say. Incredible. Everything from the performance ( vessels vocals, iis a drumming god, iiis whole vibe, ivs screams, the FUCKING ESPERA MY GOD they sing like angels) to the lights and lasers (sometimes i would just look at the lights and get lost in the moment, especially furing atlantic, the summoning and tmbte) the crowd (at least from my pov everyone was having so much fun and my god we were loud, also at points there were like 3-4 different moshpits, people were hanging onto vessels every word, i mean we were cheering and clapping at every little thing)……im just very grateful for this experince. Legit top 3 moments of my life so far
During (i think) the offering vessel came sauntering down the catwalk and maybe this is gonna sound weird, but i realised that they were real?? Because they are anonymous i just kinda saw them as the funny guys and girls in my phone up to that point. So im like holy shit hes in front of me hi (i think i actually said hi out loud) and THEN before the breakdown iii and iv came down the catwalk together and i lost my shit again. And again. And again. Thank god they dont speak my native language
Other notable moments: iii grabbed ivs face like they were going to kiss, i got startled by the elevator during chokehold, vessel had a um...moment with iv during his solo, vessel bowed like 50 times at the end and did a surprisingly correctly shaped heart, someone yelled COME ON VESSEL in czech at the start of ascencionsim, project euclid was a success at least from my pov (im never getting rid of that piece of green paper), walkaline on the catwalk, iii and vessels moment before the granite breakdown (bro needed NO help with the pit), the whole of atlantic
Im not gonna write about every single song because this post is already way too long but my god. Just thank you thank you thank you
PS: a week ago i posted an artwork of mine on here and i never got so many notes on a post so thank you so much!!!i will def post more st fanart in the future
#sleep token#vessel sleep token#ii sleep token#iii sleep token#iv sleep token#espera#sleep token prague#sleep token tour
7 notes
·
View notes
Text
The Emergence of NFTs: Transforming Digital Ownership and Creativity

Non-Fungible Tokens (NFTs) have revolutionized the way we think about digital ownership, art, and collectibles. By leveraging blockchain technology, NFTs provide a way to create, buy, sell, and own unique digital assets with verifiable provenance and scarcity. This article explores the world of NFTs, their impact on various industries, key benefits and challenges, and notable projects, including a brief mention of Sexy Meme Coin.
What Are NFTs?
NFTs, or Non-Fungible Tokens, are unique digital assets that represent ownership of a specific item or piece of content, such as art, music, videos, virtual real estate, and more. Unlike cryptocurrencies like Bitcoin or Ethereum, which are fungible and can be exchanged on a one-to-one basis, NFTs are indivisible and unique. Each NFT is recorded on a blockchain, ensuring transparency, security, and verifiability of ownership.
The Rise of NFTs
NFTs gained mainstream attention in 2021 when digital artist Beeple sold an NFT artwork for $69 million at Christie's auction house. This landmark event highlighted the potential of NFTs to transform the art world by providing artists with new revenue streams and collectors with verifiable digital ownership.
Since then, NFTs have exploded in popularity, with various industries exploring their potential applications. From gaming and music to real estate and fashion, NFTs are creating new opportunities for creators, businesses, and investors.
Key Benefits of NFTs
Digital Ownership: NFTs provide a way to establish true digital ownership of assets. Each NFT is unique and can be traced back to its original creator, ensuring authenticity and provenance. This is particularly valuable in the art and collectibles market, where forgery and fraud are significant concerns.
Monetization for Creators: NFTs enable creators to monetize their digital content directly. Artists, musicians, and other content creators can sell their work as NFTs, earning revenue without relying on intermediaries. Additionally, smart contracts can be programmed to provide creators with royalties each time their NFT is resold, ensuring ongoing income.
Interoperability: NFTs can be used across different platforms and ecosystems, allowing for interoperability in the digital world. For example, NFTs representing in-game items can be traded or used across multiple games and virtual worlds, enhancing their utility and value.
Scarcity and Collectibility: NFTs introduce scarcity into the digital realm by creating limited editions or one-of-a-kind items. This scarcity drives the collectibility of NFTs, similar to physical collectibles like rare coins or trading cards.
Challenges Facing NFTs
Environmental Impact: The creation and trading of NFTs, especially on energy-intensive blockchains like Ethereum, have raised concerns about their environmental impact. Efforts are being made to develop more sustainable blockchain solutions, such as Ethereum's transition to a proof-of-stake consensus mechanism.
Market Volatility: The NFT market is highly speculative and can be volatile. Prices for NFTs can fluctuate significantly based on trends, demand, and market sentiment. This volatility poses risks for both creators and investors.
Intellectual Property Issues: NFTs can raise complex intellectual property issues, particularly when it comes to verifying the rightful owner or creator of the digital content. Ensuring that NFTs are legally compliant and respect intellectual property rights is crucial.
Access and Inclusivity: The high costs associated with minting and purchasing NFTs can limit accessibility for some creators and collectors. Reducing these barriers is essential for fostering a more inclusive NFT ecosystem.
Notable NFT Projects
CryptoPunks: CryptoPunks are one of the earliest and most iconic NFT projects. Created by Larva Labs, CryptoPunks are 10,000 unique 24x24 pixel art characters that have become highly sought-after collectibles.
Bored Ape Yacht Club: Bored Ape Yacht Club (BAYC) is a popular NFT collection featuring 10,000 unique hand-drawn ape avatars. Owners of these NFTs gain access to exclusive events and benefits, creating a strong community around the project.
Decentraland: Decentraland is a virtual world where users can buy, sell, and develop virtual real estate as NFTs. This platform allows for the creation of virtual experiences, games, and social spaces, showcasing the potential of NFTs in the metaverse.
NBA Top Shot: NBA Top Shot is a platform that allows users to buy, sell, and trade officially licensed NBA collectible highlights. These video clips, known as "moments," are sold as NFTs and have become popular among sports fans and collectors.
Sexy Meme Coin (SXYM): Sexy Meme Coin integrates NFTs into its platform, offering a decentralized marketplace where users can buy, sell, and trade memes as NFTs. This unique approach combines humor and finance, adding a distinct flavor to the NFT landscape. Learn more about Sexy Meme Coin at Sexy Meme Coin.
The Future of NFTs
The future of NFTs is bright, with continuous innovation and expanding use cases. As technology advances and more industries explore the potential of NFTs, we can expect to see new applications and opportunities emerge. From virtual fashion and digital identities to decentralized finance (DeFi) and beyond, NFTs are poised to reshape various aspects of our digital lives.
Efforts to address environmental concerns, improve accessibility, and ensure legal compliance will be crucial for the sustainable growth of the NFT ecosystem. Collaboration between creators, platforms, and regulators will help build a more robust and inclusive market.
Conclusion
NFTs have ushered in a new era of digital ownership, creativity, and innovation. By providing verifiable ownership and provenance, NFTs are transforming industries ranging from art and entertainment to gaming and virtual real estate. While challenges remain, the potential benefits of NFTs and their ability to empower creators and engage communities make them a significant force in the digital economy.
For those interested in the playful and innovative side of the NFT market, Sexy Meme Coin offers a unique and entertaining platform. Visit Sexy Meme Coin to explore this exciting project and join the community.
254 notes
·
View notes
Text
But one key group was left out. The Uncommitted Movement, the antiwar, pro-Palestinian action that placed second to Joe Biden in this spring’s discarded primaries, had spent weeks trying to move the convention, both in matters of symbol and substance, against the U.S.-armed slaughter in Gaza. In the end, their efforts had boiled down to one extremely achievable ask: to give a Palestinian-American — any Palestinian-American — or a doctor who had witnessed the suffering at the hands of the Israeli military a brief speaking slot, at any time during the four-day-long national pep rally. ... But the word that had come down on Wednesday turned out to be final. No Palestinian would be allowed to speak. ... Nevermind, too, that there was already a tearful presentation on the horrors of October 7, from the parents of Hersh Goldberg-Polin, an Israeli-American veteran of the IDF who is still being held hostage in Gaza — a presentation that the Uncommitted delegates made sure to attend in solidarity with the families of Israeli hostages, by the way. ... The refusal to platform a Palestinian speaker echoes nothing so much as the refusal, on orders of then-President and candidate Lyndon Johnson, of the integrated Mississippi Freedom Democratic Party, under the leadership of Fannie Lou Hamer, at the 1964 Democratic Convention in Atlantic City, sixty years ago this month. It similarly ignores the substantive divide between the protesters outside the convention and the uncommitted delegates inside — the fact that the latter are trying to work within and in coalition with the institutional Democratic Party. While some, like some in the MFDP, will likely continue to work for Harris’ election this fall, the refusal to give the reformers even a token platform on the main stage fuels arguments that the party, and perhaps the entire political system as it stands, is too hopelessly corrupted to work with, and thus must be challenged or overthrown.
It seems that those instincts are now operating — that the Harris-Walz campaign and the convention planners decided they could afford to alienate Palestinian-Americans and their ever-growing contingent of allies on the antiwar left. That it would be better to disappoint and insult them than to challenge, in the mildest of ways, the pro-Israel contingent or the reactionary center. It was clear from last night’s programming that their play is going to be to appeal to disaffected Republicans and so-called “moderate” independents, by focusing on militarism, police, and Harris’s career as a prosecutor, locking away criminals and “securing” the border. She telegraphed that in the foreign policy section by declaring with almost Reaganite bravado: “As commander in chief, I will ensure America always has the strongest, most lethal fighting force in the world.” I really think they could have done both. I don’t think that having a Palestinian woman, hijab and all, deliver what was at bottom a bog-standard Democratic convention speech, with a shoutout to her father’s Jerusalemite origins where others shouted out their Hispanic or Native American heritage would have necessarily detracted from that pivot. I think they could have shored up part of the Michigan Arab-American vote without scaring away the voters they hoped to gain by trotting out ex-Republican congressmen and the Genesee County sheriff. I want to believe that sacrificing the lives of tens of thousands of innocent Gazans, along with the other Omelas children of the world, in Haiti, Congo, and elsewhere, is not really the intractable trolley problem — a trade between potential victims of American fascism at home and the victims of American militarism abroad — it is made out to be. But maybe I’m naïve.
15 notes
·
View notes
Text
Crypto Theft Nightmare: How Astraweb Recovered $150,000 Lost to Hackers

When David Robinson., a 58-year-old retired software consultant from Denver, Colorado, transferred his entire retirement savings $150,000 into a cryptocurrency portfolio, he believed he was securing his financial future. Instead, he walked into a digital minefield. In a single night, everything he had worked for was stolen by anonymous hackers. It was the kind of nightmare many investors fear but few believe could happen to them.
“I thought I had done everything right,” David said. “I had cold storage, I used two-factor authentication, and I only traded on what were considered reputable exchanges. But somehow, someone got in.”
The breach wasn’t just technical it was deeply personal. Decades of disciplined saving, investing, and planning had been wiped away with a few keystrokes. And in the opaque world of blockchain anonymity, there seemed to be little recourse.
A New Kind of Crime, an Old System Ill-Equipped David’s case is not isolated. According to recent figures from the Federal Trade Commission, over $1.4 billion in cryptocurrency was reported stolen in the U.S. last year alone. What’s more chilling is the vast majority of these crimes go unresolved. Law enforcement agencies, though increasingly aware of crypto fraud, are often hampered by jurisdictional boundaries, limited training in blockchain forensics, and the sheer complexity of digital asset recovery.
David contacted local police, the FBI’s Internet Crime Complaint Center (IC3), and even attempted to escalate the issue through the exchange’s customer service channels. All efforts ended in frustration. “Everyone was sympathetic,” he recalled, “but no one could help. They didn’t have the tools. I felt like I was shouting into the void.”
That void, however, was about to echo back.

Astraweb: The Digital Recovery Force Behind the ScenesWith few options left, David turned to a name he had seen mentioned in niche online forums and cybersecurity discussion threads: Astraweb. A private digital asset recovery agency, Astraweb has earned a quiet but powerful reputation for solving complex crypto theft cases especially those deemed too advanced or impossible by other channels.David sent a tentative email to [email protected], not expecting much. Within 12 hours, he received a reply. “From the first message,” he says, “I could tell they were different. They didn’t just want transaction IDs. They asked smart, precise questions. They were calm, confident, and, most importantly, they listened.”Astraweb’s team began work immediately.Digital Surveillance Meets Blockchain ForensicsWhile the average consumer may understand Bitcoin or Ethereum as abstract tokens, Astraweb views the blockchain as a massive, living map of transactions. Every move a stolen coin makes leaves a trace however faint.

Using a proprietary method called wallet triangulation, Astraweb identified the exit points the thief had used to shuffle and launder the funds. These techniques involve advanced blockchain analytics, surveillance of darknet exchange patterns, and metadata correlation to monitor crypto mixers and swap protocols often used to obscure fund movements.
According to sources familiar with Astraweb’s methods, their teams blend cybersecurity expertise with behavioral analytics to predict a thief’s next move. “It’s part code, part cat-and-mouse,” one expert commented. “But when you understand the flow of crypto like a language, the signals start to emerge.”
In David’s case, Astraweb tracked the funds as they moved through a network of wallets, some automated, others human-controlled, eventually leading to a decentralized exchange platform that allowed partial recovery. In collaboration with international legal intermediaries and with careful timing, Astraweb executed a legal intercept of the funds as they entered a liquidity pool.
The Outcome: Full Recovery, Real Relief Just 48 hours after their initial contact, Astraweb notified David that the entire $150,000 had been recovered and would be transferred back to his newly secured wallet.

Reach out to them Now If you have Related Issues Like This:
6 notes
·
View notes
Text

ERC20 Token Generator Introduction
Have you ever thought about creating your own cryptocurrency? With an ERC20 Token Generator , you can make it happen effortlessly. Let’s explore how to dive into the blockchain universe.
Understanding ERC20 Tokens
ERC20 tokens are a type of digital asset on the Ethereum blockchain, following a set standard for compatibility and functionality.
Advantages of ERC20 Tokens:
Consistency: Adheres to a universal protocol.
Broad Adoption: Recognized across various Ethereum-based platforms.
Robust Support: Strong community and resources available.
How to Use an ERC20 Token Generator
Creating tokens is simplified with these tools. Here’s how it works:
Specify Token Details:
Decide on a name and symbol.
Determine the total number of tokens.
Utilize the Generator:
Access an online generator.
Enter your token information.
Deploy Your Token:
Review your settings.
Launch on the Ethereum network.
Features of ERC20 Tokens
ERC20 tokens provide essential features that enhance their usability:
Standard Operations: Includes transferring and checking balances.
Smart Contract Compatibility: Integrates easily with smart contracts.
Security Assurance: Utilizes Ethereum's strong blockchain security.
Reasons to Create an ERC20 Token
Why create your own token? Here are some compelling reasons:
Raise Capital: Launch an ICO for funding.
Build Engagement: Offer rewards to your community.
Drive Innovation: Explore new blockchain applications.
Challenges to Consider
Despite the simplicity, some challenges exist:
Knowledge Requirement: Some blockchain understanding is needed.
Security Concerns: Vulnerabilities can be exploited if not addressed.
Regulatory Compliance: Ensuring adherence to legal standards is vital.
Best Practices for Token Creation
Follow these tips to ensure a successful token launch:
Code Audits: Regularly check for security issues.
Community Involvement: Seek feedback and make necessary adjustments.
Stay Updated: Keep abreast of blockchain trends and legal requirements.
Conclusion
The ERC20 Token Generator empowers you to create and innovate within the crypto space. Whether you're a developer or entrepreneur, it's a powerful tool for blockchain engagement.
Final Thoughts
Embarking on token creation offers a unique opportunity to explore the digital economy and its possibilities.
FAQs
1. What is the purpose of an ERC20 Token Generator?
It’s a tool to create custom tokens on the Ethereum blockchain easily.
2. Do I need technical skills to create a token?
A basic understanding of blockchain helps, but many tools are user-friendly.
3. Can I trade my ERC20 tokens?
Yes, you can trade them on crypto exchanges or directly with users.
4. What costs are involved in token creation?
Creating tokens incurs gas fees on the Ethereum network.
5. How can I ensure my token’s security?
Perform regular audits and follow best practices for security.
Source : https://www.altcoinator.com/
#erc20#erc20 token development company#erc#erc20tokengenerator#token#token generator#token creation#ethereum#bitcoin
59 notes
·
View notes
Text
A crypto investor has brought a class action lawsuit against Pump.Fun, a platform for launching and investing in meme-inspired cryptocurrencies, after suffering trading losses.
Representing the plaintiffs are Wolf Popper and Burwick Law, the two firms handling a separate class action brought by investors in December over a memecoin launched by web personality Haliey Welch, better known as the Hawk Tuah girl, which collapsed in value soon after trading began. (Welch was not named as a defendant in that suit.)
“These ‘emperor’s new clothes’ crypto schemes can’t keep masquerading as legitimate finance, leaving the vulnerable in the lurch," says Max Burwick, founding partner at Burwick Law.
Pump.Fun was a hit when launched in January 2024, giving people a way to launch memecoins—highly volatile cryptocurrencies that typically have no inherent purpose beyond speculation—instantly and at no cost. The new lawsuit, filed Thursday in the Southern District of New York, alleges that Pump.Fun has operated as an unregistered securities issuer and seller. In making marketing claims that downplay the likelihood of losing money trading memecoins, the complaint alleges, the platform also put investors at heightened financial risk.
Separately, the lawsuit alleges that these memecoin platforms, like Pump.Fun, are designed in such a way as to incentivize pump-and-dump activity. “Early investors or insiders artificially inflate token prices through coordinated buying and promotional campaigns, then sell their holdings at peak prices, causing the token's value to collapse and leaving later investors with substantial losses,” the complaint claims.
The complaint points to the circumstances around the launch of a particular Pump.Fun memecoin—PNUT, which references the celebrity squirrel euthanized last year in New York—to evidence its claims.
Pump.Fun did not respond to a request for comment. But in an interview with WIRED last year, Noah Tweedale, one of the three Pump.Fun cofounders named in the suit, refuted the idea that the platform stands to benefit from regular investors losing money. “The idea with Pump was to build something where everyone was on the same playing field,” Tweedale said. “I want to stress, we don’t want people to lose money on our platform. It doesn’t benefit us by any means.”
More than 6 million unique memecoins have been launched through Pump.Fun, the most successful of which are valued at hundreds of millions of dollars. The memecoin market is now worth in excess of $100 billion in aggregate, market data shows.
In its first 12 months in operation, Pump.Fun is reported by third parties to have generated more than $350 million in revenue, taking a 1 percent cut of trades. The platform is on pace to make more than $1 billion in revenue in 2025.
However, the lawsuit brought by the crypto investor—which follows reports of unethical trading activity, criticism relating to content moderation, and a warning issued against Pump.Fun by the UK financial regulator—could threaten to put a dampener on the runaway growth.
The lawsuit hinges on the idea that memecoins should in some circumstances be classified as securities, a particular type of investment instrument. The complaint claims that by failing to register token sales with the Securities and Exchange Commission (SEC), the relevant US financial regulator, Pump.Fun allegedly violated securities laws and denied investors the disclosures required of regulated entities.
Whether cryptocurrencies should be classified as securities is a long-running debate that has spawned a mess of litigation between the SEC and cryptocurrency companies. Though the SEC has not pursued many memecoin-related cases to date, in the lawsuit against Pump.Fun, the crypto investor alleges that all memecoins issued through the platform resemble securities by virtue of the way they are marketed.
“This largely turns on the question of an expectation of returns through marketing promises,” says Burwick. “The issue with almost every memecoin is: How was this marketed?” Essentially, if a creator or issuing platform suggests that a coin is headed to the moon, Burwick believes it is a security.
In the interview with WIRED, Tweedale rejected the idea that memecoins might fall under the purview of the SEC. “Memecoins being securities is a joke. That can’t be the case,” he said.
Elsewhere, the lawsuit alleges that Pump.Fun essentially gamified the trading experience and engaged in a "sophisticated marketing campaign" that combined "promises of exponential returns, luxury lifestyle imagery, and coordinated social media promotion,” which had the effect of obfuscating the risk profile of memecoin investing.
The architecture of the Pump.Fun platform, which relies upon a mathematical mechanism known as a bonding curve to eliminate the cost of issuing a memecoin for creators, amplifies the potential financial harm by creating a dynamic whereby early buyers benefit disproportionately, the investor has alleged.
Meanwhile, in failing to verify the age or identity of its users, Pump.Fun exposes minors and inexperienced investors to both financial risk and the explicit material rife on the platform, the complaint alleges. In December, Tweedale told WIRED that Pump.Fun plans to introduce age restrictions but provided no further specifics.
Memecoin trading has frequently been compared to gambling at a casino. But the metaphor is ill-fitting, Burwick claims, because it erases the responsibility to investors that should be borne by the platforms through which memecoins are issued.
“This is not a casino … Retail investors are sold an opportunity to make a return on their investment, but the reality is that they have an entire system they are playing against. They don’t understand how heavily the odds are stacked against them,” says Burwick. “Pump.Fun is not gambling—it’s the illegal issuance of securities.”
5 notes
·
View notes