#software testing conferences
Explore tagged Tumblr posts
Text
QA Summit Bengaluru 2025: Learn AI Testing with Rahul Shetty
Join Rahul Shetty, and discover how AI is changing testing, explore the latest trends in QA automation, and get career advice. Connect with professionals and boost your QA skills!
#software testing conferences#International software testing conference#eurostar software testing conference#step in forum software testing conference#software testing conferences 2025#QA Meetup with Rahul Shetty#QA Meetups
1 note
·
View note
Text
The Power of Performance Testing: Ensuring Your Application's Excellence
In the fast-moving digital landscape of today, where user satisfaction is more important than anything else, the performance of software applications holds a pivotal role. Imagine waiting restlessly for a website to load or an app to respond - it's frustrating and often leads to users abandoning the application altogether. This is where performance testing comes to the rescue. Here we'll delve into the significance of performance testing, its distinct features, and why it's an indispensable practice in modern software development.
Importance of Performance Testing:
User Expectations: Users expect applications to be fast, responsive and efficient. Slow performance can lead to poor user experience, decreased user engagement and even loss of revenue for businesses.
Scalability Challenges: As user numbers increase, applications must scale seamlessly. Performance testing helps identify bottlenecks and ensures that applications without crashing can handle increased load.
Key Aspects of Performance Testing:
Load Testing:
Simulates realistic user loads to measure an application's response time under expected conditions.
Determines performance limits and potential breaking points.
ensures the stability and reliability of the program even during times of peak usage.
Stress Testing:
Pushes the application beyond its limits to notice how it behaves under extreme conditions.
Reveals vulnerabilities and weaknesses that might not surface during normal operations.
Helps in optimizing the application for unexpected spikes in traffic.
Capacity Testing:
Identifies the system's maximum capacity and the point at which it starts degrading in performance.
helps in resource planning and scaling strategies.
Endurance Testing:
Evaluates the application's performance over an extended period to identify memory leaks, resource exhaustion, or slowdowns that occur over time.
Ensures the application's stability for long-term usage.
Scalability Testing:
Measures the application's ability to handle varying levels of load by adding or removing resources.
Assesses how well the application scales in terms of performance and response time.
Benefits of Performance Testing:
Enhanced User Experience:
Users are more satisfied and engaged with applications that respond swiftly and efficiently. Positive user experiences translate to increased brand loyalty and revenue.
Early Issue Identification:
Performance testing uncovers bottlenecks and vulnerabilities early in the development cycle, reducing the cost of fixing issues later.
Optimized Resource Allocation:
Precise identification of resource usage allows for optimized allocation, preventing unnecessary over-provisioning.
Conclusion:
Performance testing arises as a non-negotiable technique in a world dominated by technology, where user loyalty depends on quick and seamless experiences. It's not just about preventing crashes; it's about delivering exceptional user experiences. From load testing to scalability assessment, each facet of performance testing contributes to an application's success. By investing in comprehensive performance testing, businesses not only ensure their software's excellence but also build a bridge to user satisfaction and continued growth. Performance testing acts as a steadfast defender, strengthening the pillars of contemporary software development in the unrelenting quest of technical greatness.
Unicom Seminars Ltd. holds a distinguished position as one of the foremost software testing conferences in the United Kingdom. With a rich history of organizing insightful and educational events, Unicom Seminars Ltd. has become a trusted platform for professionals in the software testing industry. This conference provides a unique opportunity for attendees to stay abreast of the latest trends, best practices, and innovations in software testing.
0 notes
Text
As someone who works in the reliability sector of IT I cannot emphasize how much you have to give 0 fucks about professional standards and best practices in order to do something like what Crowdstrike did.
At the company I work for, which you have definitely heard of, there are thousands of people (including me, hi) part of whose job it is to sit in rooms for literal hours every week with the people building new features and updating our software and ask them every question we can possibly think of about how their changes might impact the overall system and what potential risks there are. We brainstorm how to minimize those risks, impose requirements on the developers, and ultimately the buck stops with us. Some things are just too risky.
Many of the practices developed at this and other companies are now in wide use across the industry, including things like staggered rollouts (i.e. only 1/3 people get this update at first, then 2/3, then everyone) and multi-stage testing (push it to a fake system we set up for these purposes, see what it does).
In cases where you’re updating firmware or an os, there are physical test devices you need to update and verify that everything behaves as expected. If you really care about your customers you’ll hand the device to someone who works on a different system altogether and tell them to do their worst.
The bottom line here is that if Crowdstrike were following anything even resembling industry best practices there should have been about twenty failsafes between a kernel bug and a global update that bricked basically every enterprise machine in the world. This is like finding out the virus lab has a direct HVAC connection to the big conference room. There is genuinely no excuse for this kind of professional incompetence.
1K notes
·
View notes
Text
Ice cold take from a decade ago!
"Quality gates are either automatically tool enforced, or they are imaginary"
I am fairly confident in stating that. Because if you claim that your developers will follow the quality gate on their own, you are saying that your people are better developers than the 40 people who got Curiosity to Mars. In this talk by Gerard Holzmann: https://www.usenix.org/conference/hotdep12/workshop-program/presentation/holzmann He shows data, that the programmers who have the highest success rates with rovers on mars, by a LONG shot, do not follow quality gates that was not enforced. So they tested EVERYTHING. To NASA level standards. One of the highest in the world. They made a HUGE codebase. VERY fast. And it was VERY safe. ... and it was cheap. Because clean code is easy to change and easy to write in. And when you get tested seven ways to hell every day, then you have to write robust code. Turns out robust code and testable code is basically the same thing. ALL of the software for that, was written by 40 people. It was CHEAP. So cheap that they barely appeared in the budget. And yet it was tested inside and out constantly and quality gates was enforced with systems
So when your workplace claims that it is simply too expensive to automate the quality gates. Then inform them that it is too expensive to NOT enforce them.
62 notes
·
View notes
Text
At the 2023 Defcon hacker conference in Las Vegas, prominent AI tech companies partnered with algorithmic integrity and transparency groups to sic thousands of attendees on generative AI platforms and find weaknesses in these critical systems. This “red-teaming” exercise, which also had support from the US government, took a step in opening these increasingly influential yet opaque systems to scrutiny. Now, the ethical AI and algorithmic assessment nonprofit Humane Intelligence is taking this model one step further. On Wednesday, the group announced a call for participation with the US National Institute of Standards and Technology, inviting any US resident to participate in the qualifying round of a nationwide red-teaming effort to evaluate AI office productivity software.
The qualifier will take place online and is open to both developers and anyone in the general public as part of NIST's AI challenges, known as Assessing Risks and Impacts of AI, or ARIA. Participants who pass through the qualifying round will take part in an in-person red-teaming event at the end of October at the Conference on Applied Machine Learning in Information Security (CAMLIS) in Virginia. The goal is to expand capabilities for conducting rigorous testing of the security, resilience, and ethics of generative AI technologies.
“The average person utilizing one of these models doesn’t really have the ability to determine whether or not the model is fit for purpose,” says Theo Skeadas, chief of staff at Humane Intelligence. “So we want to democratize the ability to conduct evaluations and make sure everyone using these models can assess for themselves whether or not the model is meeting their needs.”
The final event at CAMLIS will split the participants into a red team trying to attack the AI systems and a blue team working on defense. Participants will use the AI 600-1 profile, part of NIST's AI risk management framework, as a rubric for measuring whether the red team is able to produce outcomes that violate the systems' expected behavior.
“NIST's ARIA is drawing on structured user feedback to understand real-world applications of AI models,” says Humane Intelligence founder Rumman Chowdhury, who is also a contractor in NIST's Office of Emerging Technologies and a member of the US Department of Homeland Security AI safety and security board. “The ARIA team is mostly experts on sociotechnical test and evaluation, and [is] using that background as a way of evolving the field toward rigorous scientific evaluation of generative AI.”
Chowdhury and Skeadas say the NIST partnership is just one of a series of AI red team collaborations that Humane Intelligence will announce in the coming weeks with US government agencies, international governments, and NGOs. The effort aims to make it much more common for the companies and organizations that develop what are now black-box algorithms to offer transparency and accountability through mechanisms like “bias bounty challenges,” where individuals can be rewarded for finding problems and inequities in AI models.
“The community should be broader than programmers,” Skeadas says. “Policymakers, journalists, civil society, and nontechnical people should all be involved in the process of testing and evaluating of these systems. And we need to make sure that less represented groups like individuals who speak minority languages or are from nonmajority cultures and perspectives are able to participate in this process.”
81 notes
·
View notes
Text
Worker Drones & School
So at first I just assumed that the workers’ schooling was the same as ours but with an extra two years (because Uzi and her classmates’ are 18-20 years old) until I remembered the banner they had up during parent teacher conference and saw what they call the grades.

For anyone that doesn’t know, beta is a stage in the testing and development period of the software release cycle.
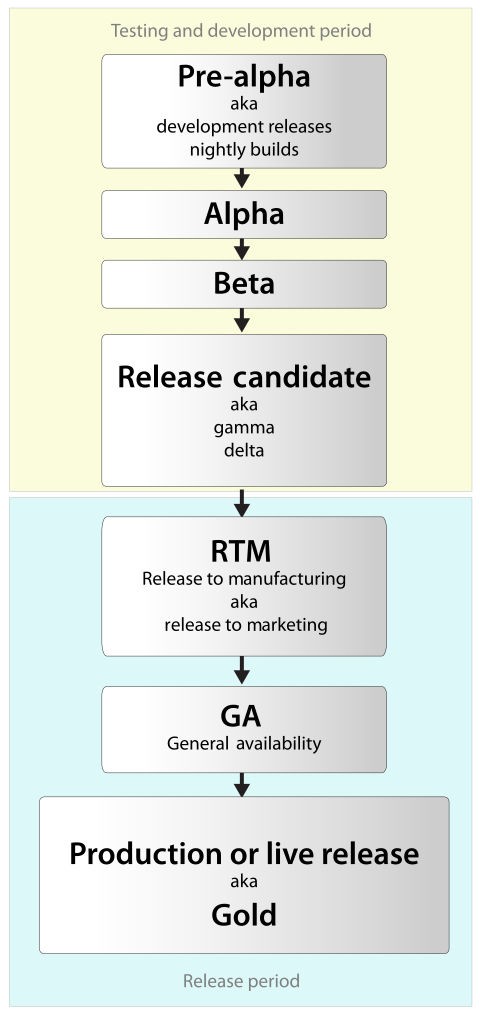
After learning this I thought I’d jot down some headcanons on how the drones’ school system and its grades work. I’m only going to focus on the testing and development period and assume that the release period would just be adulthood/being apart of the workforce.
There are 4 different school levels. Each supports a select number of school grades/years that each have 8 terms
Pre-alpha
Basically just pre school. Only lasts for a year. Kids enter at the age of 4
Alpha
The drones equivalent to the first half of elementary school. Students enter at age 5 and graduate at age 7. Supports grades 1.01-3.08 (alpha)
Beta
This school level supports grades 1.01-12.08 (Beta) and acts as the second half of elementary school all the way through high school. Students enter at age 8 and graduated at age 20. I think this would make sense since in the pilot we see a poster and drone cut outs in the nurse��s office that I personally think look like they could have been made/colored in by younger kids.

Release candidates
Higher education except it’s free and mandatory. This is where students choose a career they want to pursue, learn about and train for that career. Some students will graduate sooner than others depending on what career they’re training for. If a drone wishes to change careers then they are welcome to return to this level of schooling.
65 notes
·
View notes
Text

An Introduction to Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
What is cybersecurity?
Cybersecurity is all about securing technology and processes - making sure that the software, hardware, and networks that run the world do exactly what they need to do and can't be abused by bad actors.
The CIA triad is a concept used to explain the three goals of cybersecurity. The pieces are:
Confidentiality: ensuring that information is kept secret, so it can only be viewed by the people who are allowed to do so. This involves encrypting data, requiring authentication before viewing data, and more.
Integrity: ensuring that information is trustworthy and cannot be tampered with. For example, this involves making sure that no one changes the contents of the file you're trying to download or intercepts your text messages.
Availability: ensuring that the services you need are there when you need them. Blocking every single person from accessing a piece of valuable information would be secure, but completely unusable, so we have to think about availability. This can also mean blocking DDoS attacks or fixing flaws in software that cause crashes or service issues.
What are some specializations within cybersecurity? What do cybersecurity professionals do?
incident response
digital forensics (often combined with incident response in the acronym DFIR)
reverse engineering
cryptography
governance/compliance/risk management
penetration testing/ethical hacking
vulnerability research/bug bounty
threat intelligence
cloud security
industrial/IoT security, often called Operational Technology (OT)
security engineering/writing code for cybersecurity tools (this is what I do!)
and more!
Where do cybersecurity professionals work?
I view the industry in three big chunks: vendors, everyday companies (for lack of a better term), and government. It's more complicated than that, but it helps.
Vendors make and sell security tools or services to other companies. Some examples are Crowdstrike, Cisco, Microsoft, Palo Alto, EY, etc. Vendors can be giant multinational corporations or small startups. Security tools can include software and hardware, while services can include consulting, technical support, or incident response or digital forensics services. Some companies are Managed Security Service Providers (MSSPs), which means that they serve as the security team for many other (often small) businesses.
Everyday companies include everyone from giant companies like Coca-Cola to the mom and pop shop down the street. Every company is a tech company now, and someone has to be in charge of securing things. Some businesses will have their own internal security teams that respond to incidents. Many companies buy tools provided by vendors like the ones above, and someone has to manage them. Small companies with small tech departments might dump all cybersecurity responsibilities on the IT team (or outsource things to a MSSP), or larger ones may have a dedicated security staff.
Government cybersecurity work can involve a lot of things, from securing the local water supply to working for the big three letter agencies. In the U.S. at least, there are also a lot of government contractors, who are their own individual companies but the vast majority of what they do is for the government. MITRE is one example, and the federal research labs and some university-affiliated labs are an extension of this. Government work and military contractor work are where geopolitics and ethics come into play most clearly, so just… be mindful.
What do academics in cybersecurity research?
A wide variety of things! You can get a good idea by browsing the papers from the ACM's Computer and Communications Security Conference. Some of the big research areas that I'm aware of are:
cryptography & post-quantum cryptography
machine learning model security & alignment
formal proofs of a program & programming language security
security & privacy
security of network protocols
vulnerability research & developing new attack vectors
Cybersecurity seems niche at first, but it actually covers a huge range of topics all across technology and policy. It's vital to running the world today, and I'm obviously biased but I think it's a fascinating topic to learn about. I'll be posting a new cybersecurity masterpost each day this week as a part of the #StudyblrMasterpostJam, so keep an eye out for tomorrow's post! In the meantime, check out the tag and see what other folks are posting about :D
#studyblrmasterpostjam#studyblr#cybersecurity#masterpost#ref#I love that this challenge is just a reason for people to talk about their passions and I'm so excited to read what everyone posts!
47 notes
·
View notes
Note
Teto said they they have a theory why carlos felt in the car how he felt and they will test the hypothesis in Japan, so I think they have "studying the data" part covered. Also as a data analyst, I can tell you that you don't need to sit in group in round table of a conference room to study and analysis data, it can easily be done individually with effective communication with team it you have the right software program. He and his engineers can do this from their respective places then discuss new theory/hypothesis and finding over virtual meetings. Now the sim work, drivers can't just work in the factory and do sim work whenever they want, it is scheduled and structured by the team. Simulator is also used by developers, engineers for upgrades or new development for the car. It's not like he can hop into the simulator whenever he has a bad race weekend.
The bottom line is he is someone who is in this field for 10 years and ha changed team 4 times. He knows what and when needs to be done and he is the most hardworking driver in the grid. So there is absolutely no need to stress out and think that he is slacking in his work when you see him living his life in between race weekend.
P.S. I am not saying these to the specific anon who realised and said that they are probably overthinking, but there has been a trend recently among a section of Carlos fans specially on X. They "worry" that he is not pushing himself hard enough. It's been like this since the beginning of the year when they said he isn't training hard like last year, he isn't going to factory enough, he isn't going to china from Australia asap etc etc. There is always an accusatory tone to it. Idk why but I think we will enjoy the sport more in general when we stop trying to micromanage something that we have hardly any knowledge of
thanks for the detailed explanation, anon!
I don't know if those fans (I am not speaking about my anons here) are seriously "concerned", but if they are, they should question themselves because why are they doubting a guy who has been in F1 for 11 seasons, has raced for 5 teams and is known in the paddock for his technical knowledge and his hard work.
10 notes
·
View notes
Text
okay upside to getting to go present at conference: I already basically have the paper done I just have to chop and refine because it's a SHORT time limit and the deadline still isn't for over a month. Also professional development + Get Less Scared For Future Conferences + Network + test out new subspecialty in my work. Plus I think my paper is cool :) Downside to conference: I now have 100000 extra To Do items that I've been slacking on for a long time ranging from Buy A Functional Laptop (my beautiful boy is from 2013 and does not connect to a single presentation apparatus on earth anymore </3 and they don't make anymore software for him either </3) to Buy A Business Boy Outfit That U Are Not Drowning In to Apply For Travel Grant?????? to Book Hotel?????? christ god. I'm excited actually I like Tasks but ouuughhhhh. one step at a time
8 notes
·
View notes
Text
Ortho - Hack Attack
Prompt: Doll

Ortho paused when he felt an uncomfortable nudge in the back of his conscience. He activated his firewall programs and analyzed the foreign presence. “I think someone is attempting to hack my systems.”
The others paused to stare back at him. When Ortho had mentioned the tech expo a few weeks ago, he had been surprised by how the others naturally began planning the short weekend trip. Even Sebek loudly proclaimed how foolish it was for them to travel to a foreign place with no protection and included himself after receiving Lilia’s blessing. They were an odd group walking around the small convention center, but Ortho would have only been happier if Idia had tagged along with them.
“You mean," Yuu slowly said, “someone is trying to attack you?”
Ortho hummed. “I suppose in simple terms that would be accurate. They’re not being very hostile. I would say they were more testing my firewalls out of curiosity. Some of the other guys in the dorm ask to do the same for practice developing their own anti-malware programs.”
No sooner had the words left him did the presence return with a much higher intensity. A piercing pain briefly raked through him. He huffed to cover a wince. “That’s just rude!”
“They trying to hack you again?” Ace asked. He looked less concerned and more relaxed than Yuu, folding his hands behind his head. “Guess we shouldn't be too surprised. These nerds have been practically drooling over you since we got here.”
“They thought you were some kind of… autonomous doll?” Jack added, only slightly stumbling over the phrase. His ears flicked back and forth from the constant echo of voices in the large room. “They even asked Deuce what AI software was installed in you”
Ace snorted. “Like Dunce here looks smart enough to program a toaster.”
While Deuce and Ace bantered with each other, Ortho focused on his attacker. It was easy enough to create a decoy to distract the hacker while Ortho followed the remote connection back to its source. They were clearly amateurs, neglecting to realize they left themselves completely open to a counterattack. Ortho made quick work of their systems.
“All done!” Ortho said cheerfully when his consciousness returned to his frame. Deuce sputtered mid-word, and Jack jumped beside Ortho. “I won’t have to worry about them anymore.”
From across the conference room came a distressed shout. “My computer’s smoking!”
“What the heck? Mine’s playing outdated memes over and over again.”
Grim snickered on Yuu’s shoulder. “That’ll teach ‘em to think twice about messing with us!”
“I have to become more proficient with the technology they have here!” Sebek declared. “If Malleus was attacked in the same manner, then I would be completely useless. I will not allow that to happen!”
“I don’t think you have to worry too much about that,” Ortho said. No longer concerned with his attackers, he moved to the next booth in their path. “But I would be happy to show you how to counter a cyber-attack!”
Sebek agreed and started planning their “intense training sessions” as they walked together. The overall good mood they had been experiencing slowly returned, and Ortho was relieved the interruption didn’t completely ruin their day. He dealt with the other hacking attempts quietly, though he was sure Yuu caught on to what he was doing after the fourth monitor they passed started playing a loop of a cat flying on a rainbow.
17 notes
·
View notes
Text

Upcoming the Future of Software Testing Conference: QA Summit on
Join the QA Summit, an industry-leading software testing conference that brings together thought leaders, innovators, and professionals to explore the future of quality assurance. Discover how the next generation of software testing and QA is being shaped by cutting-edge tools, new trends, and practical approaches.
0 notes
Text

Best Software Testing Conferences in the UK | Unicom Seminars Ltd.
Seeking the best software testing conferences in the UK? Look no further! Unicom Seminars Limited hosts top-notch events. Elevate your knowledge and network with industry leaders at our top-tier events. Contact us today at +44 (0)1895 256 484 to secure your spot in the future of software testing excellence.
0 notes
Text
If You Ain't Cheating, You Ain't Trying...Part One.
Well, in the week between Indycar's Long Beach Grand Prix and the Children's of Alabama Grand Prix at Barber Motorsports Park, all hell broke loose in the series.
Way, way, way back in the distant past of the 2024 Firestone Grand Prix of St. Petersburg - Indycar's season opener - Josef Newgarden won the race and his teammates Scott McLaughlin and Will Power finished third and fourth, respectively.
Except...that's not what happened.
Immediately following the Long Beach Grand Prix, it was announced that Newgarden and McLaughlin were disqualified, and Will Power was docked ten points. All of them were fined and stripped of their prize money from St. Pete. Why? Well, it all has to do with illegal push-to-pass software.
Now, push-to-pass (aka the overtake button) is part of Indycar racing, has been for awhile now. Every driver is given an equal amount for the race, they're allowed to deploy it at their discretion - with some caveats I'll get into in a moment - and it gives them a boost in engine power while they're on the button. If you're an F1 fan of old, it's sorta like the KERS button, except the amount is measured for the whole race, not just by the lap.
The caveat is that push-to-pass is not allowed to be used during starts or restarts. In fact, the only time it should be used - the only time it should be possible to be used - is when race control sends out the transponder signal to enable P2P in the race. Team Penske, however, had a software that allowed them to use P2P whenever, which they say was accidentally left in the car following a preseason test of Indycar's upcoming hybrid system.
So, Penske had an illegal software that allowed them to skirt the P2P rules and get that extra boost in power at any point in the race. Josef Newgarden pressed it multiple times during restarts, Scott McLaughlin used it as well, though he maintains he only used it once and it was by force of habit rather than intentional cheating, and Will Power did not use P2P outside of his limits, but his car carried the software. Thus, the former two were disqualified, and the latter was given a points penalty.
The intriguing thing is...remember when I said that this all happened after Long Beach? Well, the reason for that is that, in morning warm-up ahead of the Long Beach Grand Prix, race control ran into a technical glitch and couldn't turn on P2P, and yet...the Penske cars were using it. All three of them. Race control immediately told them to stop, and then after Long Beach, they went back to look at the season's previous points race at St. Pete. This is when Team Penske was caught, and this is why they were disqualified from St. Pete so long after the fact.
When the news broke, reactions were mixed.
A lot of people felt betrayed by the drivers, they saw this as a breach of trust and integrity, and Josef Newgarden quickly became the poster child of this scandal. This went so far that, at Barber this weekend, Josef hosted a tearful press conference when he tried to defend himself and his honor. Nevertheless, a lot of people seemed to be rooting for Josef to fail at Barber.
As for me, well...I was more intrigued by the whole thing.
Cheating is part of motorsports and always has been, and I choose to treat it almost like a magic trick. It's just like the wild innovations of the 1960s and 1970s - what did these genius designers think of this time to skirt the rules, and how did they do it?
So, on the backs of that Penske controversy, this week, I'm going to do a series of blogs on cheating scandals from racing's past. Today, we'll start with...
The 1994 Benetton Option 13 scandal:
Probably the most similar story to this, in my opinion, is the story of Option 13. Before I get into it, I want to say that youtuber Aidan Millward has done a number of great videos on this topic and I learned a lot from those. Anyway, after the 1992 and 1993 F1 seasons, which saw the teams playing around with traction control, active suspension, automatic gearboxes, launch control, and all kinds of technological innovations, the FIA banned all driver aids ahead of the 1994 season.
For Williams, this made their car unruly and difficult to drive, contributing to the death of Ayrton Senna at the San Marino Grand Prix.
For Benetton and their star driver Michael Schumacher, this gave them the chance to take the fight to the established teams.
Except, Benetton had a little secret...
After retiring from the 1994 Pacific Grand Prix - which you may remember from my Suzuka in April blogpost - Ayrton Senna stood at the side of the track and listened to the cars going past, and when he heard the Benetton, the story goes that he sore they must have been using traction control.
At the very next race, Ayrton Senna dies in his crash and Michael Schumacher wins his third race in a row in the Benetton.
At this point, the FIA asks to see the ECU code from Benetton, Ferrari, and McLaren. Ferrari complied immediately, Benetton and McLaren dragged their feet. Why? Well, it was uncovered that McLaren had some leftover and unused code having to do with automatic shifting, while Benetton...they had Option 13.
On the digital display of the B194, the driver could scroll across twelve displayed options...but they could also scroll down to a thirteenth, unseen option. This hidden option was not traction control, but it was launch control. Benetton maintained that, like McLaren, this was unused leftover code. The FIA was unconvinced, however, they couldn't prove that Benetton actually used this system in the race. Thus, they were at an impasse.
For now, the FIA settled on fining Benetton and McLaren $100,000 for missing the initial deadline on the ECU source code.
For the rest of the season, the FIA watched Benetton like a hawk.
So, when Michael Schumacher decided to start the British Grand Prix early and overtook Damon Hill on the formation lap. 27 minutes later, Schumacher was handed a five second stop-go penalty. When Schumacher failed to serve this penalty, he was shown the black flag on lap twenty-one. However, Schumacher stayed out as Benetton bosses Flavio Briatore and Tom Walkinshaw argued with race control Abu Dhabi 2021 style. Eventually, Schumacher would serve his penalty on lap twenty-seven...six laps after he was disqualified. He then continued further and crossed the finish line second on track, all while technically disqualified.
Benetton appealed, the FIA began an investigation, with Benetton admitting they made a mistake, but arguing that race control failed to inform them within the required fifteen minutes of the incident in question. Michael was allowed to race while the incident was under appeal.
A month and a half later, at the Belgian Grand Prix, Michael Schumacher won despite a spin at Pouhon. However, he was disqualified for an irregularly worn plank - much like Lewis Hamilton and Charles Leclerc would be at the 2023 USGP - furthermore, Benetton's appeal from the British Grand Prix was dismissed. Schumacher was banned for the next two races at Monza and Estoril.
In the end though, in controversial fashion, Schumacher would collide with Damon Hill at Adelaide in the season-ending Australian Grand Prix, and thus win the title by one point.
Thus, Benetton's star driver was kicked out of four races that year, but none of it was actually about Option 13. Sure, it's pretty easy to say that the FIA knew that Benetton was bending the rules so decided to throw the book at them at every opportunity, but they could never actually prove cheating.
So yeah, what better way to kick off this week of cheating blogs than with two cases of illegal software thirty years apart.
Next, I intend to talk about the lead shot Tyrrell, and after that, the revered, almost folkloric misadventures of Smokey Yunick in the early years of NASCAR.
19 notes
·
View notes
Text

U.S. Air Force Testing New Sensors On The F-22
The F-22 recently tested multiple new sensors as part of the modernization, with plans for a rapid prototyping effort to field them and expand the capabilities of the jet.
Stefano D'Urso
F-22 new sensors
U.S. Air Force F-22 Raptors assigned to the 27th Expeditionary Fighter Squadron and Philippine Air Force FA-50PH light jet fighters conduct joint combined exchange training, above Basa Air Force Base, Philippines, on Aug. 9, 2024. (U.S. Air Force photo by Senior Airman Mitchell Corley)
The U.S. Air Force is testing multiple new advanced sensors on the F-22 Raptor, which could extend its service life and also be applied to systems of the Next Generation Air Dominance family. The info was disclosed during the Life Cycle Industry Days conference.
“The F-22 team is working really hard on executing a modernization roadmap to field advanced sensors, connectivity, weapons, and other capabilities,” said Brig. Gen. Jason D. Voorheis, Program Executive Officer for Fighters and Advanced Aircraft. “The Raptor team recently conducted six flight test efforts to demo advanced sensors.”
Voorheis also added that the service is planning for a rapid prototyping effort to get these sensors fielded quickly. “We’re executing that successfully, and that will lead to […] a rapid fielding in the near future,” he said.
The news was first reported by Air and Space Forces Magazine, which also added that Air Force officials have also confirmed that the stealthy pods seen since last year being tested on the F-22 are indeed InfraRed Search and Track (IRST) sensors. The development of a new IRST sensor for the Raptor was also confirmed by the service’s budget document, however they did not mention the sensor being podded.
The sensors are part of an upgrade program worth $ 7.8 billion before 2030, of which $ 3.1 billion are for research and development and the remaining $ 4.7 billion are for procurement. This is in contrast with previous statements that the Air Force was looking to retire the F-22 around 2030.
“From an F-22 sunsetting perspective, I don’t have a date for you,” said Voorheis when asked about the topic. “What I can tell you is that we are hyper-focused on modernization to sustain that air superiority combat capability for a highly contested environment for as long as necessary.”
This also reflects recent comments by Gen. Kenneth Wilsbach, head of Air Combat Command, who mentioned that the service should retain also the older F-22s in the Block 20 configuration, together with the latest ones. The General added that several upgrades are being planned and even the older Block 20s are still very capable, should they be needed for combat in an emergency.

An F-22 Raptor assigned to the 1st Fighter Wing, Joint Base Langley-Eustis, Virginia, approaches the boom of a 134th Air Refueling Wing KC-135R Stratotanker to refuel along the east coast of the United States Aug. 14, 2024. (U.S. Air Force photo by Tech. Sgt. Teri Eicher)
Voorheis also mentioned a software being integrated on the Raptor, which he defined as Government Reference Architecture Compute Environment, or “GRACE.” He further explained this open architecture software would allow “non-traditional F-22 software” to be installed on the aircraft and provide “additional processing and pilot interfaces.”
It’s unclear if the new GRACE is related to Project FOX, the innovation project tested last year which allowed to integrate on the F-35 software applications developed for the F-22. This allowed both 5th gen fighters to fly with common tactical software applications.
The F-22 upgrades
Some of the upgrades expected for the F-22 Raptor were unveiled in the Fiscal Year 23 budget request documentation and in an official artwork shared by Gen. Mark Kelly, then Commander of Air Combat Command. In the artwork we can see three Raptors loaded with new stealthy external fuel tanks, two underwing faceted pods and a new unknown air-to-air missile, but there are even more novelties in the documents, which unveils a previously undisclosed relationship between the F-22 and the development of the Next Generation Air Dominance (NGAD).
Two years after the upgrades were announced, we might have gotten, earlier this year, the first glimpse of the new stealthy external fuel tanks being developed for the F-22 Raptor. The aircraft was, in fact, spotted near the Mojave Air and Space Port and shows the Raptor with two fuel tanks, whose shape is reminiscent of the one shown in 2022.
The new tanks are officially known as Low Drag Tank and Pylon (LDTP) and designed to be stealthier and more aerodynamically efficient than the current 600-gallon fuel tanks. In the FY2023 budget request, the Air Force mentioned that the F-22 LDTPs are advanced technological designs providing increased persistence and range while maintaining lethality and survivability, critical to future mission execution and to maintaining Air Superiority.

U.S. Air Force Capt. Samuel “RaZZ” Larson, F-22 Raptor Demonstration Team commander and pilot, practices different maneuvers while training for the upcoming 2023 airshow season, at Joint Base Langley-Eustis, Virginia, Jan. 6, 2023. (U.S. Air Force photo by Airman 1st Class Mikaela Smith)
The low drag tanks are intended to reduce drag, facilitate supersonic flight with external tanks and extend the range of the F-22. The pylons are equipped with smart rack pneumatic technology to accurately control ejection performance and smooth wind swept surface for minimum drag without stores.
The two pods installed under the outer underwing hardpoints have already been spotted during flight testing on an F-22 at the Air Force’s Plant 42 facility in Palmdale, California, in February 2022. The latest budget documents mention an InfraRed Search and Track (IRST) sensor being developed for the F-22, which is now confirmed to be the sensor housed inside the two pods, although they could host also other capabilities in addition to the IRST.
In July 2024 we got an up-close look at one of the pods installed under a Rockwell Sabreliner 65 testbed after a test campaign at Nellis AFB, Nevada. It would have been expected to see some kind of transparent surface associated with the IRST, however the surfaces on the nose of the pod appeared to be opaque. We still cannot exclude that there are two different variants of the pod, depending on the equipment inside.
The last upgrade featured in the artwork is a new unknown air-to-air missile. While there are a number of air-to-air missile programs in the works, it is possible that the one in the image could be a representative design, which may or may not correspond to the real deal, for the highly secretive AIM-260 missile. So far, the missile has never been depicted in any kind of image and details about the program are very scarce.
The development of the AIM-260, also called Joint Advanced Tactical Missile, was first unveiled in 2019 and has been in the works at least since 2017. The goal of the new long-range air-to-air missile is to replace the AIM-120 AMRAAM (Advanced Medium Range Air-to-Air Missile) and counter the threat posed by the Chinese PL-15 missile, while avoiding any foreign threats being able to outrange the AIM-120.
Among the few known technical details, the new missile will be compatible with the AMRAAM dimensions, but obviously with greater range, and is planned to be carried in the F-22 weapons bay and on the F/A-18 at first, with the F-35 to follow. Flight tests are already in progress and the missile is expected to be fielded by next year. Because of these reasons, it would be reasonable to suppose that the one shown in the image could be at least a hint at the AIM-260.
Other upgrades mentioned in the budget request are a Mode 5 Identification Friend or Foe (IFF), Link 16 and Multifunction Information Distribution System Joint Tactical Radio System (MIDS JTRS), a new Operational Fight Program, advanced radar Electronic Protection, Embedded GPS/Inertial Navigation System (INS) Modernization (EGI-M), Open System Architecture (OSA), new encrypted radios.

File photo of the U.S. Air Force’s 5th gen aircraft, the F-22 and the F-35. (Photo: U.S. Air Force)
A new helmet is also being tested by F-22 pilots, as part of the Next Generation Fixed Wing Helmet program to replace the current HGU-55P helmet, which has been the standard issued helmet for the last 40 years. The goal is to provide pilots a more comfortable, stable, and balanced platform to accommodate helmet-mounted devices usage without imposing neck strain and discomfort to the user.
Despite various integration efforts in the past, the F-22 is not equipped yet with a helmet that provides the essential flight and weapon aiming information through line of sight imagery: the shape of the Raptor’s canopy, optimized to preserve Low Observability, doesn’t allow enough range of motion and minimum visibility to a pilot wearing the JHMCS or the Scorpion.
About Stefano D'Urso
Stefano D'Urso is a freelance journalist and contributor to TheAviationist based in Lecce, Italy. A graduate in Industral Engineering he's also studying to achieve a Master Degree in Aerospace Engineering. Electronic Warfare, Loitering Munitions and OSINT techniques applied to the world of military operations and current conflicts are among his areas of expertise.
@The Aviationist.com
14 notes
·
View notes
Text
in Hillel Wayne's Crossover Project, he interviewed a set of people who had both done software engineering and "traditional" (mech, chemical, civic) engineering. the overall conclusion is that the broad sentiment that software engineering is in a state of fallen grace compared to "real" engineers is false, and both disciplines have things to learn from each other.
i think most of the things SWEs have to learn will be unsurprising: respect your project, do more planning, and so on. but the two he brought up for what traditional engineers can learn from SWEs are surprising:
a culture of openness, of conferences that aren't organized by academics or companies but simply for the love of the thing. he mentions that he presented this at a SWE conference, but if he was a traditional engineer he'd have nowhere to present it. there's no community.
version control and tooling, like the ability to run automated test suites and block the build if they fail. "Some other fields have proto-VCS, things with a fraction of the power and versatility of git, and the rest are still saving files as form-draft-3.docx."
12 notes
·
View notes
Text
KnowBe4, a US-based security vendor, revealed that it unwittingly hired a North Korean hacker who attempted to load malware into the company's network. KnowBe4 CEO and founder Stu Sjouwerman described the incident in a blog post this week, calling it a cautionary tale that was fortunately detected before causing any major problems.
"First of all: No illegal access was gained, and no data was lost, compromised, or exfiltrated on any KnowBe4 systems," Sjouwerman wrote. “This is not a data breach notification, there was none. See it as an organizational learning moment I am sharing with you. If it can happen to us, it can happen to almost anyone. Don't let it happen to you.”
KnowBe4 said it was looking for a software engineer for its internal IT AI team. The firm hired a person who, it turns out, was from North Korea and was "using a valid but stolen US-based identity" and a photo that was "enhanced" by artificial intelligence. There is now an active FBI investigation amid suspicion that the worker is what KnowBe4's blog post called "an Insider Threat/Nation State Actor."
KnowBe4 operates in 11 countries and is headquartered in Florida. It provides security awareness training, including phishing security tests, to corporate customers. If you occasionally receive a fake phishing email from your employer, you might be working for a company that uses the KnowBe4 service to test its employees' ability to spot scams.
Person Passed Background Check and Video Interviews
KnowBe4 hired the North Korean hacker through its usual process. "We posted the job, received résumés, conducted interviews, performed background checks, verified references, and hired the person. We sent them their Mac workstation, and the moment it was received, it immediately started to load malware," the company said.
Even though the photo provided to HR was fake, the person who was interviewed for the job apparently looked enough like it to pass. KnowBe4's HR team "conducted four video conference based interviews on separate occasions, confirming the individual matched the photo provided on their application," the post said. "Additionally, a background check and all other standard pre-hiring checks were performed and came back clear due to the stolen identity being used. This was a real person using a valid but stolen US-based identity. The picture was AI 'enhanced.'"
The two images at the top of this story are a stock photo and what KnowBe4 says is the AI fake based on the stock photo. The stock photo is on the left, and the AI fake is on the right.
The employee, referred to as "XXXX" in the blog post, was hired as a principal software engineer. The new hire's suspicious activities were flagged by security software, leading KnowBe4's Security Operations Center (SOC) to investigate:
On July 15, 2024, a series of suspicious activities were detected on the user beginning at 9:55 pm EST. When these alerts came in KnowBe4's SOC team reached out to the user to inquire about the anomalous activity and possible cause. XXXX responded to SOC that he was following steps on his router guide to troubleshoot a speed issue and that it may have caused a compromise. The attacker performed various actions to manipulate session history files, transfer potentially harmful files, and execute unauthorized software. He used a Raspberry Pi to download the malware. SOC attempted to get more details from XXXX including getting him on a call. XXXX stated he was unavailable for a call and later became unresponsive. At around 10:20 pm EST SOC contained XXXX's device.
“Fake IT Worker From North Korea”
The SOC analysis indicated that the loading of malware "may have been intentional by the user," and the group "suspected he may be an Insider Threat/Nation State Actor," the blog post said.
"We shared the collected data with our friends at Mandiant, a leading global cybersecurity expert, and the FBI, to corroborate our initial findings. It turns out this was a fake IT worker from North Korea," Sjouwerman wrote.
KnowBe4 said it can't provide much detail because of the active FBI investigation. But the person hired for the job may have logged into the company computer remotely from North Korea, Sjouwerman explained:
How this works is that the fake worker asks to get their workstation sent to an address that is basically an "IT mule laptop farm." They then VPN in from where they really physically are (North Korea or over the border in China) and work the night shift so that they seem to be working in US daytime. The scam is that they are actually doing the work, getting paid well, and give a large amount to North Korea to fund their illegal programs. I don't have to tell you about the severe risk of this. It's good we have new employees in a highly restricted area when they start, and have no access to production systems. Our controls caught it, but that was sure a learning moment that I am happy to share with everyone.
14 notes
·
View notes