#spyware terminator
Explore tagged Tumblr posts
Text
microsoft recall is an optional feature btw, you need to turn it on for it to even do anything on your computer and you can uninstall it via a terminal just as u can uninstall things on linux via a terminal
#and for the record i'm very much team linux over windows#but every time windows releases a new feature you have people fearmongering over it and it's...#getting a little stale tbh#like yes you can't just easily uninstall it in two clicks but to uninstall it you're just doing what you do in linux#pull it up in the terminal#it's bloatware yes but i wouldn't call it spyware out of the box
3 notes
·
View notes
Text
i missed out on the decades of hype and sci-fi thirsting over One Device to Rule Them All but grew up during the transition from Wow ! Gadgets ! to turbomaxxing smartphones. the phone/ipod/internet communications device congealment. bought into it.
who remembers igoogle ? wave ? there's an app for that ? early attempts at "os in a browser", thin client replacements ? docs before it became drive ? text to tweet ? cloud. integrations. smartphone. integrations. integrated integrations.
the ultimate Gadget and it's in your pocket, and on the cloud. you are the cloud. your whole life the cloud.
and we got it, complete with malware. spyware. ads. ads for spyware. spyware for ads tracking. locked in. not like that ! walled gardens, monopolies, too big to fail !!
baby synthia, kid synthia, teen synthia, even young adult synthia, all got hyped got hyper over it. not the spyware. i grew up using linux in the fuckign 00s did schoolwork on it. but like. bluetooth peripherals, wow !! 2.4ghz wireless peripherals, wow !!! webmail webapps cloud storage i had blogger/blogspot on my first smartphone i was amazed at sync via google account i dreamed of smarthomes and alexas. like a fool.
but, doing that shit early ? i got out early too. too many wires are a pain and there are cases for wireless things (K400 plus controlling jellyfin/plex), but wires are reliable. dependable. don't need batteries. i want Gadgets and Gizmos. sometimes this trades convenience for reliability, but well-designed gadgets are only inconvenient for task-switching. and maybe that friction would stop us being so chronically online.
this lacks the funny interaction or initial oneliner into reblog chain to gain any traction but idc. read a classic blog post once in a while.
gadgets, much like the part where i live mostly in the terminal, represent bringing whimsy back into tech my relationship with it. but they also represent an attempt to balance things and enforce a boundary with myself. i spend a lot of time on my desktop and i miss spending time sat in other places, or outside for fun, or tinkering with projects, a million other things. reading an ebook on the sofa, laying in bed with just an mp3 player, treating internet use on my thinkpad as transactional from time to time, that's an attempt to find balancce. that's renegotiating things. and telling corporate tech to fuck off especially.
54 notes
·
View notes
Text
android: "this 2 mb update may take a while" *25 minutes go by while you can't use the device and it ends by restarting*
windows: "kill yourself. i'm updating whether you want me to or not. oh is little piss baby in the middle of something? grow up. you're getting more spyware." *25 minutes go by while you can't use the device and it restarts 3 times*
linux: "hey bud there're some packages that need updating, whenever you feel like it. no big hurry." *you open the terminal and input the command and before you can even get back to what you were doing the update is done*
36 notes
·
View notes
Text
This month, Andrew Bernier, a US Army Corps of Engineers researcher and a union leader, says that he has received a barrage of menacing messages from the same anonymous email account. Unfolding like short chapters in a dystopian novel, they have spoken of the genius of Elon Musk, referenced the power of the billionaire’s so-called Department of Government Efficiency (DOGE), and foretold the downfall of “corrupt” union bosses.
But the most eerie thing about the emails, which Bernier says began arriving after he filed an official charge accusing the Trump administration of violating his union’s collective bargaining agreement, is that they included personal details about his life—some of which he believes might have come from surveillance of his work laptop. The author referenced Bernier’s union activities, nickname, job, travel details, and even the green notebook he regularly uses. The most recent email implied that his computer was loaded with spyware. “Andy's crusade, like so many before it, had been doomed from the start,” one email stated. “The real tragedy wasn't his failure—it was his belief that the fight had ever been real.”
The unsettling messages, which were reviewed by WIRED, are an extreme example of the kinds of encounters that workers across the US government say they have had with technology since President Donald Trump took office. WIRED spoke to current employees at 13 federal agencies for this story who expressed fears about potentially being monitored by software programs, some of which they described as unfamiliar. Others said that routine software updates and notifications, perhaps once readily glossed over, have taken on ominous new meanings. Several reported feeling anxious and hyperaware of the devices and technology around them.
At the General Services Administration (GSA), one worker cited a Chrome browser extension called Dynatrace, an existing program for monitoring app performance. Inside the Social Security Administration (SSA), another employee pointed to Splunk, a longstanding tool that’s used to alert IT staff to security anomalies like when an unauthorized USB drive is plugged into a laptop. At the US Agency for International Development (USAID), one worker was caught off guard by Google’s Gemini AI chatbot, installations of which kicked off days before Trump took office.
“Everyone has been talking about whether our laptops are now able to listen to our conversations and track what we do,” says a current GSA employee, who like other workers in this story, was granted anonymity because they didn’t have authorization to speak and feared retaliation.
Dynatrace and Splunk did not respond to requests for comment from WIRED.
The workers’ accounts come as Musk’s DOGE organization is rapidly burrowing into various government agencies and departments, often gaining access to personnel records, logs of financial transactions, and other sensitive information in the process. The efforts are part of the Trump administration’s broader plan to terminate thousands of government employees and remake the face of federal agencies.
Like many private companies, US federal agencies disclose to staff that they have tools to monitor what workers do on their computers and networks. The US government’s capabilities in this area have also expanded over the past decade.
It couldn’t be learned whether the Trump administration has begun using existing tools to monitor employees in new ways; multiple agencies, including the Social Security Administration and the General Services Administration, denied that they have. The White House did not respond to requests for comment. Public evidence has not emerged of new government purchases of user-monitoring software, which is generally needed for detailed surveillance such as tracking which files a worker has copied onto a thumb drive. Some of the updates and changes that have been noticed by federal workers date back to software purchases and plans enacted long before Trump was in power, WIRED reporting shows.
“I will say my concerns are primarily based in general fear as opposed to specific knowledge,” says a worker at the Department of Homeland Security, who adds: “I’d love to be told I’m wrong.”
But activity that some workers perceive as signs of increased surveillance has prompted them to take precautions. Bernier, who works as a civil engineer for the Army Corps based in Hanover, New Hampshire, says the messages he received spooked him enough that he asked local police to keep an eye on his home, removed the battery from his work-issued laptop, and kept his work phone on airplane mode while traveling to a non-work conference last week. “There are things I don’t control but actions I can take to protect myself and my family,” he says.
Bernier’s anonymous emailer and the Army Corps did not respond to requests for comment.
A person inside the Environmental Protection Agency told WIRED last week that they’ve witnessed coworkers back out of Microsoft Teams meetings, which can be easily recorded and automatically transcribed, when they are related to topics they believe could get them fired. “Definite chilling effect,” the person says. The EPA did not respond to a request for comment.
An employee at the National Oceanic and Atmospheric Administration (NOAA), whose work with international partners is being audited by DOGE operatives, says they and their colleagues began avoiding messaging one another and have “really cut down on putting things in writing” in recent weeks. They report that correspondence from their supervisors has also significantly dropped off. NOAA declined to comment.
At the Federal Bureau of Investigation, anxiety around officials possibly targeting officers and activities perceived as being disloyal to the president has cratered morale, a federal law enforcement source with knowledge of the agents' concerns tells WIRED. The FBI declined to comment.
Aryani Ong, a civil rights activist and cofounder of Asian American Federal Employees for Nondiscrimination, a group that advocates for government workers, says those she’s been in contact with are in a heightened state of alert. In response, some federal employees have turned to encrypted communications apps to connect with colleagues and taken steps to anonymize their social media accounts, Ong says. (Federal workers are granted an allowance to use non-official communication tools only “in exceptional circumstances.”)
Insider Threat
Long before Trump’s inauguration, user activity monitoring was already mandated for federal agencies and networks that handle classified information—the result of an executive order signed by then-president Barack Obama in the wake of a massive breach of classified diplomatic cables and information about the wars in Iraq and Afghanistan in 2010. The capability is part of government-wide insider threat (InTh) programs that greatly expanded after Edward Snowden’s leak of classified surveillance documents in 2013, and again after an Army specialist murdered four colleagues and injured 16 others at Fort Hood in 2014.
The US government’s current approach to digitally monitoring federal workers has largely been guided by a directive issued by the Committee on National Security Systems in 2014, which orders relevant agencies to tie user activity to “specific users.” The public portions of the document call for “every executive branch department and agency” handling classified information to have capabilities to take screenshots, capture keystrokes, and intercept chats and email on employee devices. They are also instructed to deploy “file shadowing,” meaning secretly producing facsimiles of every file a user edits or opens.
The insider threat programs at departments such as Health and Human Services, Transportation, and Veterans Affairs, also have policies that protect unclassified government information, which enable them to monitor employees’ clicks and communications, according to notices in the Federal Register, an official source of rulemaking documents. Policies for the Department of the Interior, the Internal Revenue Service, and the Federal Deposit Insurance Corporate (FDIC), also allow collecting and assessing employees’ social media content.
These internal agency programs, overseen by a national task force led by the attorney general and director of national intelligence, aim to identify behaviors that may indicate the heightened risk of not only leaks and workplace violence, but also the “loss” or "degradation" of a federal agency’s “resources or capabilities.” Over 60 percent of insider threat incidents in the federal sector involve fraud, such as stealing money or taking someone's personal information, and are non-espionage related, according to analysis by Carnegie Mellon researchers.
“Fraud,” “disgruntlement,” “ideological challenges,” “moral outrage,” or discussion of moral concerns deemed “unrelated to work duties” are some of the possible signs that a worker poses a threat, according to US government training literature.
Of the 15 Cabinet-level departments such as energy, labor, and veterans affairs, at least nine had contracts as of late last year with suppliers such as Everfox and Dtex Systems that allowed for digitally monitoring of a portion of employees, according to public spending data. Everfox declined to comment.
Dtex’s Intercept software, which is used by multiple federal agencies, is one example of a newer class of programs that generate individual risk scores by analyzing anonymized metadata, such as which URLs workers are visiting and which files they’re opening and printing out on their work devices, according to the company. When an agency wants to identify and further investigate someone with a high score, two people have to sign off in some versions of its tool, according to the company. Dtex’s software doesn’t have to log keystrokes or scan the content of emails, calls, chats, or social media posts.
But that isn't how things work broadly across the government, where employees are warned explicitly in a recurring message when they boot up their devices that they have "no reasonable expectation of privacy" in their communications or in any data stored or transmitted through government networks. The question remains if and to what extent DOGE’s operatives are relying on existing monitoring programs to carry out Trump’s mission to rapidly eliminate federal workers that his administration views as unaligned with the president’s agenda or disloyal.
Rajan Koo, the chief technology officer of Dtex tells WIRED that he hopes the Trump administration will adjust the government’s approach to monitoring. Events such as widespread layoffs coupled with a reliance on what Koo described as intrusive surveillance tools can stir up an environment in which workers feel disgruntled, he says. “You can create a culture of reciprocal loyalty,” says Koo, or “the perfect breeding ground for insider threats.”
Already Overwhelmed
Sources with knowledge of the US government’s insider threat programs describe them as largely inefficient and labor intensive, requiring overstretched teams of analysts to manually pore through daily barrages of alerts that include many false positives. Multiple sources said that the systems are currently “overwhelmed.” Any effort by the Trump administration to extend the reach of such tools or widen their parameters—to more closely surveil for perceived signs of insubordination or disloyalty to partisan fealties, for instance—likely would result in a significant spike in false positives that would take considerable time to comb through, according to the people familiar with the work.
In an email last month seeking federal employees’ voluntary resignations, the Trump administration wrote that it wanted a “reliable, loyal, trustworthy” workforce. Attempts to use insider threat programs to enforce that vision could be met by a number of legal challenges.
US intelligence community analysts are required by law and directive to provide unbiased and objective work. That means avoiding cherry-picking information to deliberately alter judgements or falling prey to outside pressure, including from personal or political biases. These standards, even when not officially codified, are core to the professional ethics of any intelligence practitioner or law enforcement analyst conducting assessments of insider threats.
A 2018 national insider threat task force framework notes that federal programs should comply with “all applicable legal, privacy and civil liberties rights, and whistleblower protections.” Bradley Moss, an attorney representing US intelligence and law enforcement personnel, says that "disloyalty" to the Trump administration is “too vague” an excuse to terminate employees with civil service protections, adding that if "they're going to go through the statutory process, they need to demonstrate actual cause for termination."
A federal law enforcement source warns that monitoring could theoretically be used to gather political intelligence on federal employees, while the administration looks for more palatable reasons to terminate them later; similar to how law enforcement may obtain evidence that's inadmissible in the course of a criminal investigation, but then search for another evidentiary basis to file charges.
Joe Spielberger, senior legal counsel at the Project On Government Oversight, a nonpartisan group fighting alleged corruption, says that if Musk were serious about cutting government waste, he would be strengthening protections for people who report corruption and mismanagement. Any warrantless or mass surveillance of federal workers without transparent guidelines, he says, would represent a major concern.
“When you create this culture of fear and intimidation and have that chilling effect of making people even more fearful about calling out wrongdoing, it ensures that corruption goes unnoticed and unaddressed,” Spielberger says.
24 notes
·
View notes
Text
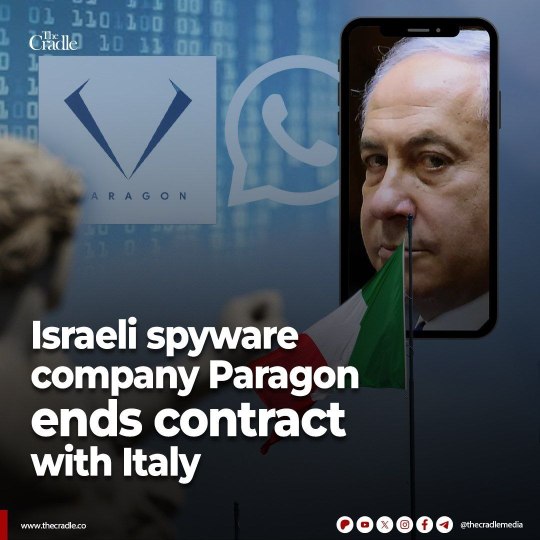
(The Cradle) Israeli spyware company Paragon Solutions has ended its client relationship with Italy, according The Guardian.
This decision comes less than a week after WhatsApp disclosed that Paragon’s spyware had been used to target dozens (https://t.me/thecradlemedia/29277) of individuals.
The termination of the Italy contract followed investigations that an Italian investigative journalist and two activists critical of Italy’s dealings with Libya were among those targeted by the spyware. All three individuals have been outspoken critics of Italian Prime Minister Giorgia Meloni’s government.
A source, speaking to The Guardian on condition of anonymity, said that Paragon had initially “out of an abundance of caution” suspended the Italy contract last Friday, following the first allegation of potential spyware abuse. The full termination of the contract, the source stated, was decided on Wednesday after Paragon determined that Italy had violated the terms of service and ethical guidelines outlined in the agreement.
When The Guardian asked for comment, a Paragon representative neither confirmed nor denied the development, stating that the company does not discuss potential client matters.
#free gaza#free palestine#gaza#jerusalem#yemen#israel#current events#tel aviv#palestine#palestine news
16 notes
·
View notes
Text
It really is spectacular how much you don't realize a situation was bad until you leave it. I'm about 13 months removed from my old job now, and it came up in conversation with one of my direct reports. She commented jokingly about the security cameras we have, and I explained to her how my old company had forced software onto everyone's computers that they insisted was only a "tool" to help identify "processes that could benefit from efficiencies" but was, unsurprisingly, essentially spyware that they used to harass and terminate people for not spending every waking second of the day working. It was some AI-assisted nightmare that would begin recording if you hadn't clicked your mouse between screens or typed in 120 seconds. It logged everything you typed, whether you sent/posted it or not. It had a set "idea" of tasks it deemed value add or unproductive. It did not account for meetings or phone calls, it did not account for certain external and internal sites that were 100% job related. If you did not score a 97% average "productivity up" time at the end of the week, you were admonished. Yes, you should always assume your employer is "watching" but I cannot describe to you what it feels like to not only know that but to have that data rubbed in your face and to be made to feel like human dirt because you were sick or had a bad day or simply had a bunch of tasks that the system wasn't smart enough to deem productive. The irony of them telling me that I should utilize the company therapist/take a walk/stretch to cure the crippling depression I was experiencing at that job when their own software would punish me for not spending that time working. I know this kind of thing isn't unheard of with remote jobs, and obviously if someone is playing WoW all day every day instead of working then it's a problem. But most places you would hope would only look into that data if someone was really falling apart or you suspected like, illicit behavior. Instead they micromanaged everyone to death, uplifted the bootlickers and encouraged a culture of surveillance. I made a joke about how I still sometimes find myself frantically clicking around on my system at work as a reflex, and she was like "....dude, that's literally inhumane and I think you might be mildly traumatized." And you know what? She's probably not wrong! I remember always feeling crazy talking to friends in other jobs who were just like "yeah as long as you do your job description and aren't downloading porn to the work laptop no one really cares what you're doing." But I stayed because of my warped sense of self worth being tied to my salary and look what it got me. Yes, yes, it lead me to what is now a very good place but I also feel like... sometimes you do not need to be thankful for suffering. Sometimes it was just Bad.
#maybe one day i'll feel up to telling the full story about how i quit in spectacular fashion#because it was in fact related to this particular productivity program lol
21 notes
·
View notes
Note
I've been having a series of weird dreams where I'm Saruhiko. Today was no different. In my dream, Saruhiko was computer pet, you know, those that are supposed to help you with computer tasks and that are also Spywares? Yeah, and the one owning the computer was Yata.
Imagine like future AU where there are like all these virtual ‘assistants’ that you can purchase to help you with various tasks, kinda like in Chobits. Yata isn’t very good at computers but he needs one for his part time job so he decides to get an assistant that specializes in computer tasks, since you can just plug the terminal into the computer and you’ll have your own little virtual pet right on your desktop who can do things for you. Most assistants are really expensive though so Yata ends up at this like kinda shady place that was suggested to him by one of his friends, Kusanagi, who runs a bar near Yata’s place and lets Yata do odd jobs for him. Yata gets a little confused by the instructions since he accidentally spilled soda on them though but he thinks he must be in the right place, he did end up at a junk shop after all. The only guy in the shop at the counter isn’t paying attention at all and Yata ends up picking up this little robot penguin. The shop guy doesn’t remember where that one came from but yeah it’s probably good with computers, just give me whatever you think it’s worth.
So Yata takes home his little penguin robot, he thinks it’s actually kinda cute in a weird way with its nerdy blocky glasses. It came with a cord to charge and another one to connect it to the computer so that’s what Yata does, the penguin opens its eyes and a little virtual person with glasses that match the penguin’s appears on his screen. Yata’s proud that he got it to work and to his surprise the virtual assistant makes a small sound like ‘tch’ and says it wasn’t hard, you just had to plug in a cord. Yata can’t believe his own virtual assistant is talking back to him. When he clicks on the screen a little box saying ‘Fushim1’ opens above the character’s head so Yata figures that must be his name, and he tells Fushimi to help him first with cleaning out this old PC Yata got secondhand. Fushimi makes the ‘tch’ noise again and says Yata must be really useless at computers, if he bought one as bad as this. Fushimi can tell that the whole thing is virus ridden and what kind of idiot buys a computer without checking for malware first. Yata’s all well that’s what I bought you for and Fushimi rolls his eyes as a little broom pops into his hand and he says Yata’s lucky Fushimi finds the code of the virus just interesting enough to play with.
Fushimi fixes up the computer and Yata’s all impressed, so he did get the coolest virtual assistant after all. Fushimi actually looks almost happy about that, or at least Yata thinks, but it’s hard to tell and anyway were these virtual assistants even supposed to have expressions. Yata assumes this must just be how they are and doesn’t think about it until his friend Kamamoto stops by and hears Yata arguing with his computer, Yata’s like yeah my virtual assistant is kinda hard to deal with. Kamamoto looks confused and says the virtual assistants are supposed to do whatever you ask without question and he’s never heard of one being difficult (or gloomy, or ‘an annoying bastard in glasses,’ as Yata keeps complaining). Yata’s like huh mine isn’t like that at all, he tries asking Fushimi about it but when he does Fushimi’s face suddenly goes blank and he says ‘classified’ in this unnaturally flat voice. Yata wonders if he could go back to the shop and ask but remembers the guy there didn’t recognize the penguin either, he decides to look at the penguin terminal but all he finds is a barcode with ‘Saruhiko’ above it. Maybe after this Fushimi starts glitching a little and Yata’s suddenly worried about losing him, even knowing that this should just be a virtual pet and nothing more, and he decides he needs to find out the truth behind Fushimi’s origin.
#sarumi#Talking K#Fushimi could be an experimental human-like AI created by Niki#or maybe Fushimi himself created the penguin and it's not an assistant it's a terminal#he's controlling the virtual Fushimi himself from where Niki has locked him in his room#it's like Rapunzel but he's using computers and a robot penguin to find his prince
8 notes
·
View notes
Text
IT’S DOMINIONWEEK!! This is my entry for the first prompt Paranoia.
•••
Lizaan scowled at the four little purple berries he’d found hidden in his sleeping area. This was the fifth time in as many days that he’d found rippleberries planted in his bunk.
When Lizaan’s cohort had been brought to Kurill Prime for the first time for a short outing as a reward for their hard work so far, they’d been expressly forbidden from taking anything home with them. Being found with such contraband was punishable with termination.
Someone had it out for him. Lizaan just knew it. But Lizaan was not going to die today. Especially not for something he hadn’t even done.
Today had been cutting it close, too. If he’d been just an hour later, the rippleberries surely would have been found when the instructor conducted the room searches that were scheduled for tonight. Not that Lizaan knew anything about the instructor’s schedule, because Lizaan would never have dared to sneak a glance at the instructor’s desk the last time he was in his office. Definitely not.
He scooped the rippleberries up and slipped them into his pocket. He needed to find somewhere he could safely dispose of them. He couldn’t risk just putting them in the trash, because he was fairly certain that the Aspirants’ garbage was “randomly” searched, too. But he also couldn’t just eat them, because that was against the rules. Someone was already trying to make him look guilty by planting the stolen rippleberries in his bunk. Lizaan wasn’t about to help them by incriminating himself. He considered reporting this to the instructor, but he figured this was probably something he had to take care of on his own. While he couldn’t risk incriminating himself, he also couldn’t afford to make himself look weak and incompetent.
He slipped through the corridors on quiet feet, heading in the direction of the Science Wing. Attendant Aspirants technically weren’t allowed there, but the instructor didn’t seem to care too much as long as it wasn’t a regular habit and they didn’t get caught without a good excuse.
Making sure he was securely in one of the few camera blind spots in the corridor, he took off his right boot and removed the sole. He took out the “borrowed” key card that he hid under there, put his shoe back on, and walked the rest of the way to the locked Science Wing door. He swiped the card along the locking mechanism, and the doors opened with a soft whoosh. The key card had been given to him by Marza, one of the Science Aspirants, and he’d given her a key card to the Attendant Aspirant Wing. Not that Marza had much use for it, not like Lizaan needed the Science Wing card. It was simply a nice thing to have, just in case.
The two had formed a sort of alliance. Marza was brilliant and Lizaan was quite competent and rather clever in his own right. They each figured that they both had a decent shot at reaching maturity, so forging an alliance early would likely be mutually beneficial in the future.
It also helped that Marza wasn’t competition. Lizaan had avoided making alliances with the others in his cohort. This left him somewhat vulnerable, but that was better than the alternative. Lizaan was a quick learner, and one of the first lessons he’d learned in his Aspirant training was that having an attachment to the others in his cohort was not a good idea. So Lizaan had gotten used to being the easy target with no one to back him up but himself, and he adapted. But that didn’t make it any less tiresome. So knowing that Marza had his back and he had hers without the looming knowledge that they’d have to kill each other one day was… quite nice.
Lizaan made his way to one of the laboratories, listening for the sounds of footsteps or doors opening as he went. Once there, he made his way to one of the lab stations. They each had an incinerator attached to clean up any messes. He picked one that he knew didn’t have any sort of hidden spyware and also didn’t belong to Marza, just to be safe, before taking the offending rippleberries and dropping them in unceremoniously. He tapped the button to turn the incinerator on for a few seconds, then pressed it again to shut it off. He leaned over a bit to inspect the ashes, and, once satisfied, pressed another button that emptied the ashes into an unseen garbage receptacle. He used the screen attached to the station to wipe the record of his unauthorized use of the incinerator. He probably didn’t do as good a job as a Science Aspirant might have, but it should hold up. Then, he turned on his heel and left the Science Wing as quickly as he could without looking suspicious.
He hurried back to his dormitory. He wanted to get there before the instructor had a chance to go through it, and if his estimation was right, he only had a few minutes. He picked up the pace to a brisk walk and only slowed a bit when he was close. Once he was back in his dormitory, he dug through his belongings again to make sure no one had planted anything again while he was gone. When he was sure there was nothing, he put everything back where it was supposed to be. The room was empty, the other Aspirants all making use of their preciously limited free time by studying in the classroom or, more likely, sneaking around and engaging in activities similar to his own. Yet, he still felt as though he was being watched. These days, there was always a tingling sensation on the back of his neck. He always felt eyes on him, whether they belonged to his rivals, his instructor, the surveillance system, or just nothing at all. Wherever he went in the cloning facility that seemed to shrink in on him each day, he never felt truly alone. In an attempt to escape the feeling of being watched in an empty room, as well as to not look suspicious, or at least no more suspicious than usual, he grabbed his pad from the drawer under his bunk and headed to the classroom to “study” as well.
He sat down at one of the desks a reasonable distance away from the other Aspirants who all had their heads down and their noses in a pad. The room was silent except for him moving around. No one even looked up at him, yet the feeling of eyes remained. He felt uneasy disrupting the silence. Once he sat down and settled in, the quiet was restored, and he breathed an inaudible little sigh of relief. He selected a history reading on his pad. Privately, he considered the sacred history texts to be his favorites, and he certainly didn’t need to brush up on them at the moment. However, he wasn’t actually there to study.
His gaze rested on the words on his pad without registering what they said as he ran through the mental list he’d been compiling of possible suspects. The most likely culprit was Torin. She was sly and ruthless and certainly had no love for Lizaan. Kazo was also a suspect. He had always been perfectly amicable towards Lizaan for no apparent reason. Lizaan didn’t know how it was in other cohorts, but the Aspirants of Lizaan’s cohort were frostily neutral towards each other at best and downright hostile at worst. Kazo’s civility was anomalous and highly suspect. Then again, no one in Lizaan’s cohort was exactly trustworthy. It could’ve been any one of them.
Lizaan glanced around the room without moving his head, watching the others. He’d have to do more reconnaissance. Maybe he could trade something with Marza for a few small cameras so he could catch his enemy in the act. Afterwards, he’d figure out how to strike back. This enemy wanted to take him out with underhanded sabotage. Well, two could play at that game. Lizaan returned his gaze to his pad, but his mind remained elsewhere as he began to scheme. It wasn’t revenge he was after. Not exactly. He just knew he had to get rid of his enemy before they succeeded in getting rid of him.
7 notes
·
View notes
Text
0 notes
Text
The Secrets to Radiant Beauty Confidence and Care Tips for Every Girl
Getting beautiful girls in today's digital environment has become simple and practical. Under a wide range of accessible information, many people still find porn content very appealing. Consuming such material is personal, but digital security must first be your priority. Adult use of the Internet leads people through risks such as injuries to beautiful girls, identity theft, malware, fraud, etc. Understanding the need for security and implementing defensive measures will help people ensure a safe and private online environment.
Securing your beautiful girl
Personal, beautiful girl privacy must be your priority when processing adult content. Many porn websites require consumers to register an account or provide payment details for premium materials. Disclosing personal information such as credit card numbers, email addresses, or names on unsecured websites consists of beautiful girls and the risk of fraud. Using a secure website with a lovely girl with encryption is essential. Therefore, we need to avoid the discovery of meaningless personal information.
Coinciding Beautiful Girls and Malware
Typically, websites aimed at the spread of viruses and malware will click on suspicious links and ads and then click on the device, causing the loss of girls and illegal access to private, beautiful girls. Leave it protected using a trusted antivirus program and an blocker. These technologies can stop unnecessary downloads and reduce the chances of walking through dangerous material while surfing porn content.
Shafting Theft and fraud
Scammers often use consumer curiosity about The Best Sexy call girl agencies and independent nude blogs content to get money and sensitive information. Typical fraud cases are phishing emails, incorrect payment gateways, and incorrect subscription companies. Visit a trusted website and reject offers that seem too good to prevent you from becoming a victim. Also, use security options to protect your financial information via virtual credit cards.
Preserving Anonymity and Privacy
People who interact with sexual content have big data protection issues. Many people can keep their browser behavior secret for personal or social reasons. Support anonymous storage by hiding IP addresses and devouring online activity. Another beautiful privacy option for girls is deleting cookies and wiping off browser history.
Notes from download
The beautiful girls’ content of from unreliable sources is a serious security risk. The file can contain spyware or hidden viruses that affect the safety of your device. Direct streaming of material from trusted websites is preferred over downloading files. If you download it, open the file using antivirus software.
Termination’s minors
Digital security also includes protecting young people exposed to unintended beautiful girls. Parents and legal guardians must use parental controls and content filters to block inappropriate content on real estate devices. It is also about teaching safe internet behavior, just as important as ensuring that children understand the limitations of online surfing.

0 notes
Text
I feel like the hugest idiot~~
I feel like the stupidest person alive simply cause I can't make up my mind on things...
and somehow in my toying around with my computer, my main hard drive that I have the OS installed on, and my data drive somehow switched ??
the OS hard drive was dev/sda1 and the data drive was dev/sdb1... but in my current fore of "lets install windows again to play games, then immediately the next day say screw it and go back to linux" they swapped places somehow??
now I have the OS on dev/sdb1 and boot to it from there.... so what happened? I don't touch the other drive at all when I'm wiping and messing with stuff so my data is intact.... so ??? how???
also for some reason linux mint debian edition 6 doesn't boot or install with secure boot on. not at all..... why? idk.....
yet straight up debian (tho I'm using debian 12 now instead of 11 and idk if that would have anything to do with LMDE but idk which version of debian it was based on....) cause i forgot if debian 11 also had that problem or not....
and don't want to poke around anymore and find out....
stuck in a cycle of "I want to game so reinstall windows and all games I have, then immediately get bored and reinstall linux again after a day. cause that was literally this time. so I think I should just stay with linux and accept that I'm not ever going to play any of my steam games.
but ye why did my hard drives swap on me? why does debian 12 install perfectly fine with secure boot enabled? cause I didn't change anything in the BIOS and still had fast boot and secure boot turned on....
I always also just default to xfce and idk why.... i tried messing around with KDE and don't like it. cinnamon was nice but boring, hadn't tried GNOME yet again after a decade, lxqt idk if I like or not. it would save ram and space tho but again I'm on a gaming pc so that's not a problem....
and once again my function keys sort of don't work under windows but DO under linux~~~~ and as always idk why.....
WE BACK TO LINUX BABY~~~~~~ AND I HOPE I'M SMART ENOUGH TO STAY HERE~~~~~
also for some reason everything in my data hard drive has a little lock next to it but you have to input a password to even access it so maybe it's that?
I FEEL LIKE I'M RUNNING AROUND IN CIRCLES LIKE AN IDIOT~~~
STAY WITH LINUX YOU FOOL~~~~~
but ye long story short saw a game about digging a hole and bought it, tried it for like a minute, it wanted to do something w windows that I didn't trust so I uninstalled it, and got a refund cause "it doesn't work on my pc" and then tonight just nuked windows after just nuking linux just to play a game about digging a hole......
lol
but ye to make the questions easier to find;
why did my hard drives switch like that? tho nothing broke and everything still works so that's good.
which desktop environment is better? course that's probably subjective and I gravitate towards xfce
the running around in circles is me not being able to make up my mind about stuff but I should just stick w linux cause windows 10 is reaching end of life and windows 11 is spyware..... imo anyway...
one more question that hopefully I can figure out~~~ how do I install updates on Debian? linux mint has an update installer... or maybe that's a cinnamon desktop environment thing? is it "apt-get update"
right now I know next to nothing about the terminal aside from ls which lists which directory you're in.... and "whoami" which tells you whos logged in.....
got a feeling I'll get "read the manual" tho... hopefully people aren't that hostile and mean......
all of this for wanting to play the silly hole game and then not playing the silly hole game.....
T_T;;;
#personal#thoughts#thinking#i think too much#all of this just to play a game#and then end up not playing the game and getting a refund#like#i reinstall windows after nuking my linux install#then immediately after nuke windows to install linux again#learned some stuff tho#but what happened to my hard drives?#whyd they swap like that?#works fine tho#OS#operating system#operating systems#windows#linux#windows 10#debian 12#xfce#to be more specific#question#questions#terminal#terminal help#and now I feel stupid#stick with linux you idiot
0 notes
Text
(obligatory not a lawyer and not legal advice disclaimer)
as funny as this post is (and it is) it is not inherently illegal to download youtube videos, or extract the mp3 file from a youtube video. downloading a video could only count as illegal if you're distributing it (i believe)
it is, however, against youtube's terms of service. see Your Use of the Service, Section 4 "Permissions and Restrictions", point 1:
"The following restrictions apply to your use of the Service. You are not allowed to [...] access, reproduce, download, distribute, transmit, broadcast, display, sell, license, alter, modify or otherwise use any part of the Service or any Content except: (a) as expressly authorized by the Service; or (b) with prior written permission from YouTube and, if applicable, the respective rights holders".
in practice, though, i can almost guarantee nobody is going to be terminated from the platform because they downloaded a few videos onto their computer lol. hell, i myself own an mp3 player with HUNDREDS of downloaded songs straight from youtube. it's honestly a much better way to listen to music plus i can support the artists i want to support directly rather than going through youtube's shitty ad program :P
if you're looking for a good site to download from that doesn't look like it's about to give you a ten billion spyware attack, cobalt is ad-free, open source, and supports crediting creators and fair use. i've had zero issues with it thus far
(sidenote: i've also heard the argument that "downloading can't be illegal/against TOS because your computer needs to download videos to even be able to stream them!" and this is. just. not the case. the transfer of packets is far different from downloading a physical, accessible file to your computer. although technically true, it's essentially like saying "murder can't be illegal because technically even vegans kill plants every day to eat them!!!". it's just a blatant misinterpretation of what "downloading" means in this context, and while technically correct, ONLY on a technicality.)
have fun on the seven seas mateys
108K notes
·
View notes
Text
Muss zum Zahnarzt habe noch nicht einmal einen Termin ausgemacht.
0 notes
Text
can you pirate vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can you pirate vpn
Risks of using pirated VPN
Using a pirated Virtual Private Network (VPN) may seem like a convenient and cost-effective solution for accessing restricted content or maintaining online privacy. However, there are significant risks associated with using pirated VPN services that can have serious consequences for users.
One of the primary risks of using pirated VPNs is compromised security. Legitimate VPN services invest in robust encryption protocols to protect user data and online activities. In contrast, pirated VPNs often lack essential security features, leaving users vulnerable to data breaches, information leaks, and hacking attacks. This can result in sensitive personal information being exposed to nefarious third parties, putting users at risk of identity theft and financial fraud.
Furthermore, pirated VPNs are notorious for injecting malware and spyware into users' devices. These malicious programs can monitor online activities, steal login credentials, and compromise the overall security of the device. Users of pirated VPNs may unknowingly expose themselves to a range of cybersecurity threats by installing compromised software on their devices.
In addition to security concerns, using a pirated VPN can also violate copyright laws and intellectual property rights. By accessing geo-restricted content through an unauthorized VPN service, users may be engaging in illegal activities that could lead to legal repercussions and penalties.
In conclusion, while the temptation to use a pirated VPN may be strong, the risks far outweigh any perceived benefits. To ensure online security and compliance with the law, it is essential to invest in a reputable and legitimate VPN service. By prioritizing security and authenticity, users can protect themselves from the dangers associated with pirated VPNs and enjoy a safe and secure online experience.
Legal implications of pirating VPN
Pirating a VPN, which involves the illegal copying, distribution, and use of virtual private network (VPN) services, can have severe legal implications. VPNs are commonly used to protect online privacy, bypass geo-restrictions, and ensure secure connections. However, utilizing pirated VPN services is considered a violation of intellectual property rights and can result in significant legal consequences.
One of the primary legal implications of pirating a VPN is copyright infringement. Most VPN services are protected by copyright law, and unauthorized distribution or use of these services without proper licensing is a violation of copyright laws. Those found guilty of engaging in illegal VPN piracy may be subject to civil lawsuits, hefty fines, and even criminal prosecution.
Moreover, pirating a VPN can also lead to breaches of terms of service agreements. VPN providers typically have strict terms of use in place that prohibit illegal activities such as copyright infringement or unlawful access to restricted content. Violating these terms can result in the termination of service, loss of subscription fees, and possible legal action by the VPN provider.
Additionally, using pirated VPN services can expose individuals to cyber threats and security risks. Pirated VPNs may contain malware, spyware, or other malicious software that can compromise users' privacy and data security. By pirating a VPN, users not only put themselves at legal risk but also jeopardize their online safety.
In conclusion, pirating a VPN is a serious offense with various legal implications, including copyright infringement, breach of terms of service, and cybersecurity risks. It is crucial for individuals to use legitimate VPN services and comply with all relevant laws and regulations to avoid legal troubles and safeguard their online security and privacy.
Impact on online privacy from pirated VPN
The Impact of Pirated VPNs on Online Privacy
In recent years, the use of Virtual Private Networks (VPNs) has surged as individuals seek to protect their online privacy and bypass geo-restrictions. However, the proliferation of pirated VPN services presents a significant threat to online privacy. Pirated VPNs, also known as cracked or unauthorized VPNs, are often marketed as free alternatives to legitimate VPN services. While they may seem appealing due to their cost-free nature, their usage can have severe consequences for users' privacy and security.
One of the most concerning aspects of pirated VPNs is their lack of encryption and security features. Legitimate VPN providers invest heavily in robust encryption protocols to safeguard users' data from interception by third parties. In contrast, pirated VPNs frequently lack such measures, leaving users vulnerable to hacking, surveillance, and data breaches. Without proper encryption, sensitive information such as passwords, financial details, and browsing history becomes susceptible to exploitation by malicious actors.
Furthermore, pirated VPNs often come bundled with malware and adware, further compromising users' privacy and security. These malicious elements can monitor users' online activities, harvest personal information, and inject unwanted advertisements into web browsers. As a result, individuals who unwittingly download and use pirated VPNs expose themselves to a myriad of privacy risks, including identity theft, phishing attacks, and financial fraud.
Moreover, the use of pirated VPNs undermines the integrity of the VPN industry as a whole. Legitimate VPN providers adhere to strict privacy policies and legal regulations to ensure the confidentiality and anonymity of their users. By supporting pirated VPNs, individuals not only put their own privacy at risk but also contribute to the proliferation of illicit online activities.
In conclusion, while the allure of free VPN services may be tempting, the use of pirated VPNs poses significant threats to online privacy. To safeguard their personal information and maintain anonymity online, individuals should opt for reputable VPN providers that prioritize security and privacy. Ultimately, investing in a legitimate VPN service is a small price to pay for the invaluable protection it provides in an increasingly digital world.
Secure alternatives to pirated VPN
In the digital age, the use of Virtual Private Networks (VPNs) has become increasingly common, offering users a secure way to browse the internet and protect their privacy. However, the temptation to resort to pirated VPN services can be alluring for some individuals seeking to save money. While pirated VPNs may seem like a cost-effective solution, they come with significant risks and drawbacks, including compromised security and legal repercussions.
Fortunately, there are numerous secure alternatives to pirated VPN services that offer reliable protection without breaking the law or putting users at risk. One such alternative is subscribing to reputable VPN providers that offer affordable plans with robust security features.
Leading VPN services such as ExpressVPN, NordVPN, and Surfshark prioritize user privacy and security, offering encryption protocols to safeguard data transmission and strict no-logs policies to ensure user anonymity. Additionally, these legitimate VPN providers offer a vast network of servers worldwide, allowing users to access geo-restricted content and enjoy fast, uninterrupted internet speeds.
For those concerned about the cost of subscription-based VPN services, there are also free options available from reputable providers. While free VPNs may have limitations such as data caps or slower speeds, they still offer a safer alternative to pirated services.
Furthermore, some internet browsers offer built-in VPN features, providing an added layer of protection without the need for additional software installation. Examples include Opera Browser's integrated VPN and the VPN functionality in the Tor Browser.
In conclusion, while pirated VPN services may seem appealing due to their cost-saving nature, the risks they pose far outweigh any perceived benefits. By opting for legitimate VPN alternatives, users can ensure their online security and privacy while staying on the right side of the law.
Ethical considerations when using VPN
Ethical Considerations When Using VPN
Virtual Private Networks (VPNs) have become increasingly popular for individuals and businesses alike, offering enhanced online security, privacy, and access to region-restricted content. However, while VPNs provide numerous benefits, it's essential to consider the ethical implications associated with their use.
Respecting Terms of Service: When using a VPN, it's crucial to adhere to the terms of service of the services and platforms you access. Some websites and online services explicitly prohibit the use of VPNs, and bypassing these restrictions may violate their terms of use.
Illegal Activities: While VPNs can protect your online activities from prying eyes, they can also be used for illegal purposes such as hacking, piracy, or accessing illicit content. Engaging in such activities not only violates ethical standards but may also lead to legal consequences.
Privacy and Data Protection: VPN providers promise enhanced privacy by encrypting your internet traffic. However, it's essential to choose a reputable VPN service that prioritizes user privacy and does not log your online activities. Using VPNs to invade others' privacy or engage in unethical data collection practices is unacceptable.
Circumventing Restrictions: VPNs are often used to bypass geo-blocks and access region-restricted content. While this can be convenient, it's important to respect copyright laws and licensing agreements. Accessing content that is not legally available in your region may harm content creators and undermine the principles of fair use.
Impact on Network Performance: In some cases, VPN usage can impact network performance, especially during peak hours or when connecting to servers located far away. Excessive bandwidth consumption or overloading VPN servers can disrupt service for other users, which is ethically questionable.
In conclusion, while VPNs offer valuable benefits in terms of online security and privacy, users must be mindful of the ethical considerations involved. By respecting terms of service, avoiding illegal activities, prioritizing privacy, adhering to copyright laws, and considering the impact on network performance, individuals can use VPNs responsibly and ethically.
0 notes
Text
The year is 2077. Over the years, ease of use in the average user computer market has gone up that most people have forgotten there is someone that operates the machine. It's worse than "what you see is what you get": "What you see is all there is." The average person can no longer manually turn on a computer, for that is done automatically. They can no longer move files, for all file that has to be moved is done so automatically. They no longer click icons on a desktop for all apps are launched at the computer's guess: all they do is tell, in plain English, what they want, and the machine will find a way to provide them. They no longer know what is hardware, they would never be able to repair a machine, even if the solution is as simple as plugging it in. They no longer understand what and why is a keyboard. They no longer understand, nor do they suspect.
For every hundred thousand, a thousand knows what an operating system is, 500 of which knows its possible to change it, but only 100 have done so. Communities that once would fill entire hotels with nerds and the curious uninformed alike now have been reduced to local metups where people exchange files of dubious legality, play, and develop further their little community. What unites them is the curse of knowledge. They know that if they went to the same thrift store as everyone and bought the same computer as everyone, they would be forced to use outdated, exploitable spyware, and pay completely incoherent fees for basic abilities.
The average user would think that it is like that, and you either pay or don't have it. But this group gets that these functionalities are basic things they could make themselves in minutes, and they have. Using layouts from expired patents, reversed-enginereed outdated machinery, and scrap parts, they are able to produce computer hardware that are free of any limitations and compatible with software of the old age, from which they have developed fully functioning operating systems with all capabilities you would expect in a modern day computer, which they distribute for the price of the thumb drive they come in. Most content they consume is pirated, as almost all content there is paid, but have extremely outdated piracy measures; the average user won't even think of the possibility of getting anything on the computer without paying.
The uninformed would never doubt the machine or its requests and, as a result, tracking is at its worst. Telemetry is feared. Machines smarter than the human made to hipnotise entire nations are out there, and all you can do is hide. No webcams, no names, no aliases, no trace-backable traits, not when using the computer. They keep it down and use cryptography on all their activity. They have no accounts in online services, they use spoofs to make it seem like they do. They only update with physical medias of their software, which they check first. Privacy now requires advanced understanding of computer science, to know your computer like it's your child.
The impact of those who fail their measures is psychological torture by a society: the machine will pressure whole cities to force a user to give up their basic rights. To try to ignore all they have learned, all those tales of freedom, all those warnings of dystopia, or live in a world that will be always playing the dice so that they are always in the worst. For they know, that no convenience is truly for free, that thank yous will never satisfy a machine of money making.
The steel can make your life the easiest. It only wants one thing.
You.
So learn the linux terminal or fucking else.
Telling young zoomers to "just switch to linux" is nuts some of these ipad kids have never even heard of a cmd.exe or BIOS you're throwing them to the wolves
61K notes
·
View notes
Link
0 notes