#systemfile
Explore tagged Tumblr posts
Text
What is OpenAL? OpenAL: Should I Remove It?

Have you ever looked at your installed software or system programs and noticed something called OpenAL? You might have been asking yourself, "What is OpenAL, and do I need it?" Here in this article, we will tell you all there is to know about OpenAL, its purpose on your computer, if it's safe, and if you can remove it.
What is OpenAL?
OpenAL is an abbreviation for Open Audio Library, a cross-platform audio API (Application Programming Interface) used for the rendering of multichannel three-dimensional positional audio. It was authored by Loki Software and then continued to be supported by Creative Labs, the same entity responsible for Sound Blaster sound cards.
The API has the same idea as OpenGL (Open Graphics Library), but for rendering graphics. Although OpenGL is concentrated on graphics, OpenAL is concentrated on 3D audio, particularly in 3D environments such as video games or simulations.
Simply put, OpenAL gives realistic sound experiences through emulating how a sound behaves in three-dimensional space. It enables programmers to define how sound propagates from various directions, how it reflects off surfaces, and how it varies based on listener movement, contributing to realism in a game or program.
Why Is OpenAL Installed on My Computer?
Now that we’ve answered "What is OpenAL?", the next logical question is, Why is it on my system?
You might not remember installing it yourself, and that’s perfectly normal. OpenAL typically gets installed automatically alongside certain games, multimedia applications, or drivers that use it for audio rendering.
Some common scenarios include:
PC Games: Titles that use 3D audio may bundle OpenAL with the game installer.
Sound Card Drivers: Especially those from Realtek or Creative Labs will include OpenAL as part of their driver package.
Software Suites: Certain multimedia editing software and simulation games have OpenAL available for their advanced sound playback.
Basically, if an application relies on OpenAL for sound capabilities, it will automatically install it, usually without prompting, since it's considered a runtime dependency.
Is OpenAL a Virus or Malware?
Not at all. OpenAL is not a virus, malware, or malicious software of any kind. It's an authentic audio API utilised by programmers to improve the audio performance and experience.
Since OpenAL tends to appear without user-initiated installation, some users may mistakenly think it's suspicious. But you don't have to worry—it's a safe and stable component created and supported by reputable companies.
If you're still in doubt, you can scan for security using your antivirus or anti-malware software, but OpenAL itself doesn't have any inherent danger.
What Does OpenAL Do?
Let's dive deeper into what it can do. OpenAL supports precise simulation of 3D audio, which makes it perfect for:
Video Games: Sound effects such as footsteps, shots, and ambient sounds can seem like they're coming from certain directions and distances.
Virtual Reality (VR): Precise audio positioning adds to the sense of immersion.
Simulations and Training Software: Realistic sound placement aids in the creation of realistic situations.
Multimedia Editing: In certain situations, editing tools might utilise OpenAL for 3D audio track rendering or previewing.
OpenAL uses a listener-source model. Think of the "listener" as your ears (the player), and "sources" as the various sounds in a game environment. OpenAL then calculates how those sounds should be heard based on position, movement, and acoustics.
OpenAL Versions and Compatibility
OpenAL is designed to be cross-platform, meaning it works on Windows, macOS, and Linux systems. There are different versions and implementations, including:
OpenAL Soft: A widely used open-source version of OpenAL, frequently employed as a drop-in replacement for the original.
Creative Lab's OpenAL: The closed-source edition is occasionally included with sound cards.
Most current systems or games utilise OpenAL Soft nowadays because of its continuing development and support for new systems.
OpenAL and Gaming: Does It Enhance Performance?
In games, OpenAL doesn't accelerate system performance itself, but plays its role in sound quality and immersion. You may not get additional FPS (frames per second), but:
Sound will be more natural-sounding and responsive.
Directional audio cues will be more precise, particularly in 3D environments or first-person shooters.
Hardware acceleration (in certain sound cards) can transfer audio processing from the CPU.
So while OpenAL isn't a performance enhancer in the classical sense, it is a boost to your audio experience, and that can be a vital part of gameplay.
Should I Remove OpenAL?
This is one of the most popular questions you will get after finding OpenAL installed on your machines. The short response? In most instances, no, you don't need to remove it.
If you're gaming in 3D, playing virtual reality software, or launching any program that provides surround sound, OpenAL is probably necessary to make those applications function properly. Even if you don't know whether a program employs it, uninstalling OpenAL may cause problems with sound to behave unexpectedly or for applications to crash when you play games or multimedia software.
Alternatively, if you've completely removed old games or software from your system and you're certain that nothing you're using relies upon it, you can remove OpenAL. To be honest, though, the software is small—usually under 10 MB—and won't affect system performance or storage in any significant way. So, unless you're purposefully seeking to clear space of unwanted software, there's no advantage in getting rid of it.
In summary, if you haven't had any issues, it's best to leave OpenAL alone. It's harmless, lightweight, and can still be needed by some programs that you utilise today, or perhaps use in the future.
Can I Reinstall OpenAL?
Yes! If you uninstall OpenAL and subsequently discover that a program or game requires it, you can simply reinstall it.
Here's how:
Have the game or app reinstall itself—most will ask or do so quietly at launch.
Manually download it from reputable sources such as the OpenAL website or through Steam/driver packages.
OpenAL alternatives
While OpenAL is prevalent, there are other audio APIs:
FMOD – Used frequently in indie and AAA titles for more complex audio.
Wwise – A professional, highly customizable audio engine.
DirectSound / XAudio2 – Microsoft's closed-source audio libraries.
These alternatives can be employed at the whim of the developer, but a lot of older and even some modern games still make use of OpenAL for certain audio functionality.
Conclusion: Is OpenAL Worth Keeping?
Let's summarise:
What is OpenAL? It's an API for cross-platform delivery of 3D audio in games and software.
Why is it on your system? Installed with games or drivers that need it.
Is it safe? Yes, 100%.
Does it do any good? For supported games and applications, yes—it enhances audio immersion.
Should you uninstall it? Only if you are certain you don't need it, and you're trying to eliminate unnecessary programs. Even then, its effect is minimal.
In the majority of instances, it's better to leave OpenAL installed. It will not do any harm to your system, does not occupy much space, and may be essential to your gaming or multimedia experience. If unsure, leave it be, particularly if you play 3D games or have VR software.
#OpenAL#WhatIsOpenAL#AudioAPI#3DSound#PCGamingTips#TechExplained#GameAudio#SystemFiles#ShouldIRemoveIt#TechSupport#WindowsHelp#GamingAudio#PCOptimization
0 notes
Text
Get Started Here
The SFC (System File Checker) command is a great one to use if your Windows PC is giving you problems. SFC can tell you a lot about the root cause of problems, including Blue Screen of Death (BSOD) and system faults, and it will immediately solve them.
System File Checker (SFC) - sfc/scannow
An administrator has the ability to check the versions of all protected files using System File Checker. When System File Checker notices that a protected file has been rewritten, it searches the cache folder or the source files of the Windows installation for the right version of the file and replaces the corrupted one. The cache folder is examined and updated by System File Checker. To use System File Checker, you must be logged on as an administrator or a member of the Administrators group. The sfc /scannow, sfc /scannce, or sfc /scanboot commands can be used to restore the contents of the Caches folder if it becomes corrupted or useless.
How to Fix Windows 7 System Files with the SFC Utility?
To fix Windows 7 system files using the SFC (System File Checker) utility, you can follow these steps:
Open Command Prompt as an administrator. You can do this by typing "cmd" in the search bar, right-clicking on "Command Prompt," and selecting "Run as administrator".
In the Command Prompt window, type the following command and press Enter: sfc /scannow. This command will scan all protected system files and replace any corrupted files with a cached copy located in a compressed folder at %WinDir%\System32\dllcache.
Wait for the scanning process to complete. This may take some time, so be patient.
Once the scanning is finished, you will see the scan results. If the SFC utility finds any corrupted files and repairs them successfully, you'll see a message stating "Windows Resource Protection found corrupt files and successfully repaired them."
If the SFC utility is unable to repair all the corrupted files, you can try using the DISM (Deployment Image Servicing and Management) tool to fix any remaining issues. In the same Command Prompt window, type the following command and press Enter: DISM /Online /Cleanup-Image /RestoreHealth. Wait for the process to complete.
After the DISM tool finishes its task, restart your computer.
Related:-
System File Checker
1 note
·
View note
Photo

Dnes další klient do ročného mentoringu🙏 Milujem ľudí ktorí naozaj chcú svoj biznis posunúť online na vyšší level. Ak zápasis s online biznisom alebo chceš začať tak neváhaj a kontaktuj má a dohodni si 15 min hovor Zadarmo a prejdeme spolu ako na to a nájdeme spoločne to najlepšie riešenie pre teba. Stačí napísať správu alebo kliknúť na link v bio a vybrať si termín ktorý tebe vyhovuje. #onlinementoring #menorirng #koucing #onlinebiznis #onlinebizsecret #milanvaskoofficial #poddotoho #konzultaciazadarmo #ozvisa #investicedosebe #investiciadoseba #vzdelavanie #vzdelávanie #systemfile #akonainstagram #socialnediamarketing (at Island of Gods - Bali) https://www.instagram.com/p/Cow6HxJSEFX/?igshid=NGJjMDIxMWI=
#onlinementoring#menorirng#koucing#onlinebiznis#onlinebizsecret#milanvaskoofficial#poddotoho#konzultaciazadarmo#ozvisa#investicedosebe#investiciadoseba#vzdelavanie#vzdelávanie#systemfile#akonainstagram#socialnediamarketing
0 notes
Text

Is your computer running slow and out of space? It's time to try Cleanmgr - the built-in utility in Windows that can help you free up disk space and optimize your PC's performance! In this step-by-step guide, we'll show you how to use Cleanmgr to delete unnecessary files and improve your computer's speed and efficiency. From temporary files to system files, we'll cover all the types of files you can safely delete with Cleanmgr. Say goodbye to clutter and hello to a faster, more streamlined computer experience! https://youtube.com/shorts/bg34YTIFYfY?feature=share #cleanmgr #diskcleanup #windowsutility #PCperformance #computeroptimization #freeupdiskspace #temporaryfiles #systemfiles #fasterboottimes #smootherperformance #stepbystepguide #algorithminc #microsoft #thealgorithm #thealgorithminc #tutorial #windows #algorithm #troubleshooting
0 notes
Text
#kudos #but #wtf #appalledPokemon @microsoft .@microsoft @windows .@windows @windowsdev @windowsdocs .@windowsdev .@windowsdocs #phew #microsoft #icac ls seen as obsoleteby intels?can lock over ************* users rights i ntegritylevel ownership a n d ? over container affiliation and if oneof these icacls tweaks fail even takeown flows around these but without takeown first icacls cant set ************** wow. thats the right stuff to do but t hereis no good visual documentation thatshows icacls can reassign inherit labe ls too and integritylevels too and notjust users and each has these implications a n d to it all a hidden superadministrator elevated admin beats trus ted installers priority but otherwise allplay three layers in low integrity la yers around allofthat? and then someone plugs in a phone and readsout allda ta arbitrarily or a shitty app makes holes inthe firewall asifitsnothing wha ... //// wait..icacls canassign container labels too? *medival_vegg i_storm for not knowing* @microsoft .@microsoft @windows .@windows @windowsde v @windowsdoc hmmmm elevated hidden administrator above trustedinstaller abovesystem hmmm ///// Trustedinstaller runs highestpriority, abovesystem ,a dmin high integrity. Hmm what can deny takeown.exe in highpriority admin, access: (!!)/setowner "trusted installer" then / inheritance:r +chkdsk /f /sdc leanup /// theonly option ithink is.... takeown and icacls is NOT HIGH i ntegrity. yes? theonlyrationalthing totry /// terrorlooping: icacls removes inheritance, chkdsk sdcleanup reruns icacls cant access systemfiles takeown, icacls denied access lost acls@microsoft #howto #create #a #blackhole #in #w indows reboot error correction commandprompt cmd as admin ******* runas /user: trustedinstaller cmd.exe ******* im stuckin a terror loop to takeown .exe that cmd can write icacls.exe traits atall took alotof google tofigur eout itneeds ntauthority/system (full) and nt service/trustedinstaller(ful l) soisuspect it c a n t harm a dministrators (full) a f t e r takeown works atall first else foreverloop 100kfiles accessdenied but 33k fil es eeeeeheeveryone fullaccess and besides all integritylevel high? I am Christian KISS BabyAWACS – Raw Independent Sophistication #THINKTANK + #IN TEL #HELLHOLE #BLOG https://www.BabyAWACS.com/ [email protected] PHONE / FAX +493212 611 34 64 Helpful? Pay. Support. Donnate. paypal.me/ChristianKiss
#kudos #but #wtf #appalledPokemon @microsoft .@microsoft @windows .@windows @windowsdev @windowsdocs .@windowsdev .@windowsdocs #phew #microsoft #icac ls seen as obsoleteby intels?can lock over ************* users rights i ntegritylevel ownership a n d ? over container affiliation and if oneof these icacls tweaks fail even takeown flows around these but without takeown first icacls cant set ************** wow. thats the right stuff to do but t hereis no good visual documentation thatshows icacls can reassign inherit labe ls too and integritylevels too and notjust users and each has these implications a n d to it all a hidden superadministrator elevated admin beats trus ted installers priority but otherwise allplay three layers in low integrity la yers around allofthat? and then someone plugs in a phone and readsout allda ta arbitrarily or a shitty app makes holes inthe firewall asifitsnothing wha … //// wait..icacls canassign container labels too? *medival_vegg i_storm for not knowing* @microsoft .@microsoft @windows .@windows @windowsde v @windowsdoc hmmmm elevated hidden administrator above trustedinstaller abovesystem hmmm ///// Trustedinstaller runs highestpriority, abovesystem ,a dmin high integrity. Hmm what can deny takeown.exe in highpriority admin, access: (!!)/setowner “trusted installer” then / inheritance:r +chkdsk /f /sdc leanup /// theonly option ithink is…. takeown and icacls is NOT HIGH i ntegrity. yes? theonlyrationalthing totry /// terrorlooping: icacls removes inheritance, chkdsk sdcleanup reruns icacls cant access systemfiles takeown, icacls denied access lost acls@microsoft #howto #create #a #blackhole #in #w indows reboot error correction commandprompt cmd as admin ******* runas /user: trustedinstaller cmd.exe ******* im stuckin a terror loop to takeown .exe that cmd can write icacls.exe traits atall took alotof google tofigur eout itneeds ntauthority/system (full) and nt service/trustedinstaller(ful l) soisuspect it c a n t harm a dministrators (full) a f t e r takeown works atall first else foreverloop 100kfiles accessdenied but 33k fil es eeeeeheeveryone fullaccess and besides all integritylevel high? I am Christian KISS BabyAWACS – Raw Independent Sophistication #THINKTANK + #IN TEL #HELLHOLE #BLOG https://www.BabyAWACS.com/ [email protected] PHONE / FAX +493212 611 34 64 Helpful? Pay. Support. Donnate. paypal.me/ChristianKiss
#kudos #but #wtf #appalledPokemon @microsoft .@microsoft @windows .@windows @windowsdev @windowsdocs .@windowsdev .@windowsdocs #phew #microsoft #icacls seen as obsoleteby intels?can lock over ************* users rights integritylevel ownership a n d ? over container affiliation and if oneofthese icacls tweaks fail even takeown flows around these but without takeown first icacls cant…
View On WordPress
0 notes
Photo

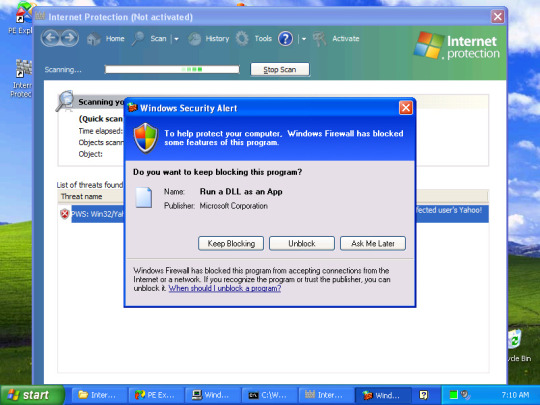
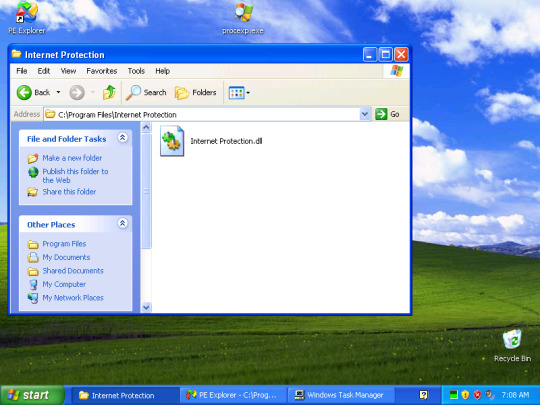

Internet Protection is an worst scareware is an dll with three random commands
and it imitate to impression Windows Defender.When loaded it install itself in Internet Explorer disable Security Center Real and various of payloads
His threats scanned are a fake so none of them are real it imitate the virus name detected by Microsoft .
This type of virus is using Rundll32 a systemfile to make itself work with an command
0 notes
Text
Snabbare dator 2 - Ta bort funktioner och städa hårddisken

1 - Windows installeras med många funktioner som ingen använder. Du kan rensa bort sådant som du inte behöver för att frigöra lite resurser till annan användning. Öppna Program i Kontrollpanelen och klicka på Aktivera eller inaktivera Windows-funktioner i vänstra panelen (under Program och funktioner).
Listan du får upp visar vad som är aktiverat. Bestäm själv vad du inte behöver, eller prova och se vad effekten blir av en avstängning. Det är bara att ta bort bockarna och klicka på OK.
När du ändå är i Program och funktioner, passa också på att avinstallera onödiga program. Det finns säkert sådant som du inte använder längre, plus en massa så kallad bloatware, alltså program som var installerade när datorn köptes och inte behövs till någonting.

2 - I Windows 10 kan du om du vill i stället göra detta genom att gå till Inställningar, välja Appar, och sedan Appar och funktioner. Klicka på önskat program eller app och välj Avinstallera.
Och då är vi inne på hårddisken. Med en ren hårddisk får du mer utrymme och Windows får mer plats att arbeta. Det senare är extra viktigt om det inte är en hederlig snurrdisk, utan en ssd. På en sådan måste alltid minst 25 procent av utrymmet vara ledigt för att de automatiska optimeringsfunktionerna ska fungera som de ska.

3 - Använd programmet Diskrensning med jämna mellanrum för att ta bort allt onödigt och alla tillfälliga filer. Bocka för allt du vill bli av med och använd gärna också knappen Rensa systemfiler för att få ännu fler val. Använd också Utforskaren för att tömma mappen C:\Windows\Temp med regelbundna mellanrum.
Om ditt Windows är en uppgradering från en tidigare version finns kanske också en gigantisk mapp som heter C:\Windows.old. Den kan du också ta bort under Rensa systemfiler.
Vill du ha ännu effektivare rensning och också få möjlighet att städa i systemregistret kan du i stället använda det förträffliga programmet CCleaner som du laddar hem gratis på www.piriform.com.

4 - En städad hårddisk behöver säkert defragmenteras eller, som Microsoft kallar det numera, optimeras. Det är egentligen ingenting du behöver tänka på, eftersom det sköter sig helt automatiskt. En snurrdisk defragmenteras och en ssd trimmas och Windows sköter om alltihop.
Om du ändå vill starta en manuell optimering eller ändra inställningarna för hur ofta optimeringen ska göras, klicka på startknappen och skriv opti. Starta Defragmentera och optimera enheter.

0 notes
Text
Best Mean Stack Development Training in Mohali | Chandigarh
The MEAN stack is a list of JavaScript open-source software. MEAN is an abbreviation used for JavaScript-based technologies in the MEAN stack construct. M's MongoDB, E's Express JS, A's Angular JS, and N's Node.js. Four such powerhouse technologies combine to create a FullStack JavaScript architecture used to build web applications quickly and easily.
MongoDB
MongoDB This is a cross-platform database that uses a document-oriented data model in MEAN stack creation and is one of several database styles. For relational databases, MongoDB is based on the architecture of documents as well as collections, rather than implementing rows and columns.
Express JS
This platform is a lightweight and minimal code Node.js that provides robust functionality for your web and mobile applications. Express.js and Node.js allow JavaScript on the back-end with innovative features. This allows developers to build JavaScript applications on the server-side. This is the common application system of Node.js.
Angular JS
Using the MEAN stack development services, a modular framework called AngularJS can be used to create dynamic web apps. It provides you with HTML as the base language and allows you to briefly expand the syntax of HTML to describe the components of your application.
Node.JS
Node.js is a cross-platform runtime environment that runs on the server-side with JavaScript code. While JavaScript is used for client-side scripting; Node.js also allows programmers to use JavaScript for server-side scripting. Before a web page is sent to a user's browser, it results in building dynamic web applications.
Where you can start your career as a MEAN Stack Developer?
Erginous designed MEAN stack development course to grow your skills as a full stack developer. At Erginous Technologies you work on a real-world exercise that helps you enhance your development techniques in your workflow. Moreover, with Erginous you will get a chance to work on live projects with an experienced team of developers.
Course highlights
Node Projects
The Node Package Manager
Creating a project
The package.json configuration file
Global vs. local package installation
Automating tasks with Grunt.
HTTP
The HTTP protocol
Building an HTTP server
Rendering a response
Processing query strings
Using Representational State Transfer
Configuring TLS
Introduction to AngularJS
What does AngularJS do for me?
Who controls AngularJS?
How can I get AngularJS?
Who Should Join
What does AngularJS do for me?
Who controls AngularJS?
How can I get AngularJS?
Our First AngularJS Application
A basic application
Using angular-seed
The pieces of the puzzle
How it fits together
Model, View, Controller from the AngularJS Perspective
Single Page Applications (SPA)
A basic application
Using angular-seed
The pieces of the puzzle
How it fits together
Model, View, Controller from the AngularJS Perspective
Controllers
Where Controllers fit in, and what they do, from Angular’s perspective
Managing Scope
Setting up Behavior
Building a basic controller
A more advanced controller
Models
How to create a model
Explicit models
Implicit models
Expressions
Expressions are lightweight code snippets
Expression capabilities
Limitations
The border between expressions and $eval
Filters
Standard filters
Writing your own filter
Tying filters together
Scopes
What are scopes?
What do scopes provide?
Scope lifecycle
Scopes as glue between controller and view
Scope hierarchies
Scope and events
Angular Forms
Angular forms vs HTML forms
Angular form controls
Form events
The form controller
Form validation
Ajax, Data, and Angular
Directives
Testing in Angul
File System
File SystemFile SystemFile System
Path and directory operations
F_dirname and __filename
The asynchronous file reads and write
Buffers, Streams, and Events
Using buffers for binary data
Flowing vs. non-flowing streams
Streaming I/O from files and other sources
Processing streams asynchronously
Configuring event handlers
Modules and Unit Testing
Modularization
The CommonJS and RequireJS specifications
Defining modules with exports
Modules are singletons
Creating a package
Module scope and construction
Unit testing frameworks
What to test and how to test it
Building unit tests with Jasmine
For more visit here:- http://erginous.co.in/mean-stack-training-mohali-chandigarh.html
#mean stack#mean stack development#mean stack development training#full-stack#full-stack development#industrial training#6 Months Industrial Training in Chandigarh
0 notes
Text
Entvölkerung - Das System ist gegen Dich
Entvölkerung – Das System ist gegen Dich
SYSTEMFILES (PDF SAMMLUNG) -https://www.dropbox.com/sh/0xmep77xb5…
Informier dich selbst! http://www.strahlung-gratis.de/ http://www.mobilfunkstudien.org/ http://www.buergerwelle.de/de/ http://www.elektrosmognews.de/ http://www.antariksha.de/ http://www.stoppt-tetrafunk.de/ http://www.der-mast-muss-weg.de/ http://www.elektrosmog.com/ http://www.emf-portal.de/ https://www.diagnose-funk.org/ http://strahlento…
View On WordPress
0 notes
Text
Entvölkerung - Das System ist gegen Dich
Entvölkerung – Das System ist gegen Dich
SYSTEMFILES (PDF SAMMLUNG) -https://ift.tt/2la6Wz9
Informier dich selbst! https://ift.tt/2DZOQr4 https://ift.tt/1TcmudT https://ift.tt/2DZadcd https://ift.tt/VKqRm3 https://ift.tt/2DZOTDg https://ift.tt/2b0hkP7 https://ift.tt/2bjOiNI https://ift.tt/2FwHjxh https://ift.tt/1s10R63 https://ift.tt/29Rul0I https://ift.tt/2BIPRCh
TETRA Der Trower…
View On WordPress
0 notes
Text
McRip SystemFiles 2.0.2014.03.26
McRip SystemFiles - A practical software installer that provides you with updated redistributable packages for Flash, Java, DirectX, Shockwave, Silverlight and other runtimes source https://www.softlookup.com/display.asp?id=272097
0 notes
Text
theonly option ithink is.... takeown and icacls is NOT HIGH integrity. yes? th eonlyrationalthing totry @microsoft .@microsoft @windows .@windows @windowsdev @w indowsdoc terrorlooping: icacls removes inheritance, chkdsk sdcleanup reruns icacls cant access systemfiles takeown,icacls denied access lost acls@microsoft
theonly option ithink is…. takeown and icacls is NOT HIGH integrity. yes? th eonlyrationalthing totry @microsoft .@microsoft @windows .@windows @windowsdev @w indowsdoc terrorlooping: icacls removes inheritance, chkdsk sdcleanup reruns icacls cant access systemfiles takeown,icacls denied access lost acls@microsoft
theonly option ithink is…. takeown and icacls is NOT HIGH integrity. yes? theonlyrationalthing totry @microsoft .@microsoft @windows .@windows @windowsdev @windowsdoc terrorlooping: icacls removes inheritance, chkdsk sdcleanup reruns icacls cant access systemfiles takeown,icacls denied access lost acls@microsoft #howto #create #a #blackhole #in #windows reboot error correction commandprompt cmd…
View On WordPress
0 notes
Text
Virus: Så og nu
I øjeblikket ved vi, at vira er bare skadelige stykker af ondsindet kode, der er lavet til rod i vores computers system. Men kun få mennesker ved, hvad slags sjov de bragte til programmører i de seneste år. Lad os se på vira fra et andet perspektiv ved at se tilbage til fortiden. Virus, som ordet antyder, er en skadelig slags software, der er analog med den biologiske virus, som vi ved. Den spredes i computeren via inficeret hardware eller hjemmeside og replikerer sig selv, når den injiceres til en vært, ligesom en virkelig virus opfører sig. Selvom denne definition lyder skadelig, finder programmører af 70’erne, at de er sjove at lege med. Det var i 1970, at den første virus blev oprettet med ingen hensigt at ødelægge et helt system. Det er kun lavet til sjov af programmørerne fra Bell Laboratories. Spillet blev kaldt Core War. Dette spil kører inden for firmanetværket, og målet med spillet er at fuldstændig ødelægge programmerne på en anden computer, samtidig med at det sikres, at det spredes i miljøet. Udviklerne ville kode software, der kunne replikere, reparere sig selv og flytte i forskellige dele af hukommelsen og angribe software ved at skrive en tilfældig modstander i modstanderens computerhukommelse. Spillet slutter efter en bestemt tid, eller når modstanderens programmer er helt inaktive eller ødelagt. Selv om dette lød en skræmmende, var det sikkert på det tidspunkt, fordi udviklerne vidste, hvor de ville lede deres software, og det er alt indeholdt i et kontrolleret miljø. I 1984 blev der lavet et spil, der havde den samme hensigt som den ovenfor nævnte. Dette spil blev scenen for fremtidige vira. ARPANET blev også inficeret af software kaldet hjerne (som var en virus), der omdøber alle disk boot-systemer til (C) Brain. Denne software gav også navn, telefonnummer og adresse til den inficerede computer, fordi dette blev lavet til reklameformål. I dag behandles vira forskelligt fra hvordan det var dengang. Virusser har i dag en eneste hensigt at rive med en computers systemfiler og ødelægge det hele. Virus er nu sneakier og mere skadelige end dem, der tidligere blev udviklet, fordi de ikke udelukkende har til hensigt at bryde systemet, men de bryder også gennem ens privatliv ved at indsamle oplysninger fra offeret. De kan nu passe i almindelige programmer og angribe den uønskede bruger. Internettet, der er en af de mest tilgængelige informationskilder, er også blevet en stor arena for virusserne og udviklerne, der har skabt dem. Det var igennem det, at den udbredte af latente vira er blevet hurtigt lavet. Nu hvor teknologien går hurtigt, bliver forbindelser stærkere, hvilket giver mulighed for lettere spredning af vira. Kendskab til virusets nuværende intentioner, bør vi være ekstra forsigtige, når du installerer en software eller surfer på en side. Dens intentioner er stadig sjovt, selvom de nu er lavet med ondsindet hensigt til udviklerens fordel.
from WordPress http://bit.ly/2WUpQLk via IFTTT
0 notes
Text
Hurtig omdirigering af virusfjernelse kan hjælpe med at holde din identitet sikker, mens du er online
Der er flere måder at få din identitet stjålet i disse dage. Disse tyve gør alt fra at tage mail, manipulere visitkort og udtrække kreditkortoplysninger gennem din lomme eller pengepung. Men den mest omfattende hub til personlige oplysninger er din computer. Din computer tilbyder en buffet med oplysninger, der kan bruges til at gøre alt fra at begå forbrydelser til at købe huse. Omdirigere Virusfrustration En af de mest fremtrædende trusler mod computeren i sen tid er Search Redirect Virus. Denne virus indleder i grunden omdirigeringsoplysninger i dine systemfiler for at sende alle dine søgeresultater, hvor det vil du skal hen. Så som du forsøger at finde de oplysninger, du oprindeligt søgte efter, omdirigeres du til flere ikke-relaterede websteder. Det er yderst irriterende og frustrerende. Dette er det mest oplagte tegn på, at du måske har denne virus. Andre tegn kan indeholde begrænset hukommelse, lav hastighed og lang opstartstid. Disse indikerer, at det er tid til fjernelse af omdirigering af virus. Identitetstrussel Denne virus er en stor trussel mod din identitet på grund af dets oprindelse og funktion. Oprindelsen er en rootkit, som er designet til at opbygge en gateway for ondsindet software og filer for at infiltrere dit system. Funktionen af denne virus er at tage kontrol over din computer. Derfor er du med glæde af, hvad malware beslutter sig for at besøge din computer og bruge den kontrol, der tages af omdirigeringsviruset, til at udtrække enhver information, den er designet til at få. Det er her en identitetstyv vil gå på arbejde med dig. Nu har han / hun ikke kun adgang til alle dine gemte filer, men har også adgang til alle brugernavne og adgangskoder, du giver i løbet af den tid, omdirigeringsvirus er aktiv. Tyveri tidsramme Den tid du har før dette bliver et stort problem for din identitet varierer. Alt dette afhænger af, hvad rootkit bag omdirigeringsvirussen var designet til at gøre. I nogle tilfælde har du imidlertid længe det kræver en malware, der er bygget til at stjæle en identitet flyder ind i dit system. I andre er du et offer inden for den første time, din computer er inficeret. Vær opmærksom på, at jo længere det tager dig at identificere infektionen og få den fjernet, desto mere sandsynligt er du at blive offer. Vent ikke. Hvis du føler, at du måske har en rootkit af enhver art, skal du sørge for det med det samme. Hold din identitet sikker fra disse typer trusler ved at opdage, fjerne og beskytte mod fremtidige rootkits på din computer. Sørg for at holde et anti-malware-program, en solid anti-virus software og rootkit detektion / fjernelse program. Eller har sagen til stede af en professionel.
from WordPress http://bit.ly/2wvO9Ai via IFTTT
0 notes
Text
terrorlooping: icacls removes inheritance, chkdsk sdcleanup reruns icacls cant access systemfiles takeown,icacls denied acc ess lost acls@microsoft .@microsoft @windows .@windows @window sdev @windowsdoc #howto #create #a #blackhole #in #windows
terrorlooping: icacls removes inheritance, chkdsk sdcleanup reruns icacls cant access systemfiles takeown,icacls denied acc ess lost acls@microsoft .@microsoft @windows .@windows @window sdev @windowsdoc #howto #create #a #blackhole #in #windows
terrorlooping: icacls removes inheritance, chkdsk sdcleanup reruns icacls cant access systemfiles takeown,icacls denied access lost acls@microsoft .@microsoft @windows .@windows @windowsdev @windowsdoc #howto #create #a #blackhole #in #windows reboot error correction commandprompt cmd as admin ******* runas /user: trustedinstaller cmd.exe ******* im stuckin a terror loop to takeown.exe that cmd…
View On WordPress
0 notes