#usb disk security
Explore tagged Tumblr posts
Text
Deny execute access: Restrict Access to USB Drives on Windows
In this article, we shall discuss “Deny execute access: Restrict Access to USB Drives on Windows”. A USB flash drive is a data storage device that includes flash memory with an integrated USB interface. I will be performing this demonstration using the Local Group Policy. In subsequent tutorials, I will cover the implementation using the Group Policy Management Console which can affect numerous…
#Block USB drives#Deny execute access#Device Installation Restriction#Disable USB ports#disk#Group Policy USB restriction#Microsoft Windows#Prevent USB access#Removable Disks#Restrict Access to USB Drives#Restrict removable storage#USB#USB device restriction#USB drive lockdown#USB port disable policy#USB security settings#Windows#Windows 10#Windows 11#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2019#Windows Server 2022#Windows USB control
0 notes
Text
AAA games? Pfft. Indie games? Double pfft.
I only play games from the alternate history where Hillary Clinton was elected in 2008 and banned all video games. You can only imagine how weird their underground gaming scene is. People like to call unlicensed games "bootlegs" but they've got actual bootlegged games! I've played games about helping your grandmother in hospice care realize she's a lesbian by reading Sappho to her, at 2am in a speakeasy in Baltimore. The cops raided it the next night, hundreds of Gamers were arrested. They posted pictures all over Friendster of the Baltimore PD destroying the arcades with axes.
I nearly got busted once because I was imaging old disks from a 386 and someone tipped off the gaming cops that there was a copy of Commander Keen in there. I had to prove that I didn't know it, I was imaging the disks blind and then indexing them later, and I would of course turn over any contraband to the proper authorities.
I was already on a watch list because I'd been known to have some gamedev-related activities pre-ban. They can't arrest me for making games back in 2007 when it was still legal, but they do want to keep an eye on me since I have the skills to break the law.
Anyway that universe's bootlegs are mainly PC games. Can't really have console games if there hasn't been a console release since the Wii/PS3/360 era. At one point Nintendo threatened to release the Wii SDK so game devs in the US could make unlicensed games, but that didn't happen as there were quickly no functional Wiis left in the US, except for very rare holdouts that never move. PC games are easy to distribute samizdat and hide on a USB stick or CD-R labeled "nickelback".
Japan's games industry is still going, so the later Nintendo and Sony consoles still exist, but Microsoft got out of the business of course. They sold the franchise to Sega who were hoping to release the 360 successor (the Xbox One in our universe) as the Sega Phoenix but it never materialized, either through their own financial incompetence or because of pressure from the US. There's a lot of international treaties that the US has pushed "and this aid only goes through if you ban games" clauses into. That would have been an official UN resolution if the USSR hadn't vetoed it. For once, thank God for the security council, eh?
I mainly get my gaming news through Japanese gaming sites (through a set of VPNs, since they're blocked at the border firewall), and some tor onion site run by a weird guy in Minnesota who is obsessed with documenting all the underground US games.
There's a lot being worked on, but it's always a tricky trade off. Too much attention and the police might be able to track down the creators, and it's basically impossible to fund underground games, as the VISA/PayPal etc funds get seized immediately. There's a whole task force for that.
Anyway one of the weirdest differences between our two time lines is that they've gone back and edited out gaming from a bunch of movies. Those that they can, of course. War games was just banned because they couldn't remove the tic tac toe ending. The Net just removed the scene at the beginning where she's playing Wolfenstein 3D, by recording some new screen footage and a new voice over. She's fixing a spreadsheet in the new edition.
(Yes, I've seen The Net from this alternate timeline. On Laserdisc, of course. I'm just that kind of person!)
They even edited Star Wars. You know that scene where R2-D2 is playing holochess with Chewie? They edited it to be a board game instead of holograms, because that made it too "video gamey".
Technically it's not illegal to show gaming in a movie, but it needs to be an 18+ film and you have to show the deleterious effects of gaming and/or the gamesters coming to a bad end.
This has affected films less than you'd think, to be honest. They were never great about showing video games even before they banned them.
Anyway, go have fun playing your AAA games with hundred-million-dollar budgets. I only play indie games made by people under a constant threat of arrest for their art.
2K notes
·
View notes
Text
Leveragetober23 Day 5: birthday
It was his birthday. Ugh.
Yet another humdrum day of feigned well wishes from silly little sycophants that just want to be as high up as him, hoping to step on him on their own way up. (He knows he's better than all of them, but do they really need to remind him every time they open their mouths and let drivel pour out? NO. But they do it anyway. *Sigh*) Yet another backpack from the higher ups as a show of "appreciation" for his dedication to the organization all these years. Yet another pointed text from his ex-wife reveling in his advanced age -- congratulations waylaid and thrown over a cliff long before she ever got to the "happy" part of happy birthday.
The only joy this day brings him is the wonderful dinner his daughter treats him to every year. Since she was 7 she decided it was her job to get her dad to show one real smile (not solely aimed at her) at least one day a year, so she always sends him some sort of surprise gift when he leasts expects it. Ironically, he has therefore come to completely expect it, but she still manages to surprises him every year (though it really shouldn't given the type of woman she has become) with caring and thoughtful gifts that mean the world to him. She may never understand how much, but she is the reason for his joy, and if she wants him to be happy, then he will, simply for her.
Therefore, he was excited (deep, deep down in his gut, probably somewhere behind his left kidney), and not all that suspicious, when he came back from yet another meeting on this damnable day to find the CD port of his computer popped open, with a disk lying in the slot, topped with a large pink bow. On the CD, someone had written "SURPRISE!" and beneath it, "Happy Birthday!"
Feeling a small bounce of excitement within him (that he will forever deny on pain of death or sodium pentathol), and wondering what his daughter had gotten him this year, he moved the bow aside and pushed in the disk.
BOOOOOOM
Confetti explodes from tubes hidden throughout his office! His plants somehow start singing happy birthday songs, each in a different language! His blinds act on their own accord, closing to reveal another birthday message across the shutters! A party hat descends from a pulley machine lowering down from the ceiling tiles, to hang jauntily off the side of his head! His drawers pop open to reveal a cake that looks like it was baked, iced, and decorated in his desk! And his computer! Oh his computer…
His screen has been taken over by a repeating video of Eliot Spencer, Alec Hardison, and Parker, all in party hats, blowing kazoos with shrieking noises emanating from his speakers, and hoisting red solo cups and cupcakes at him mockingly from under a banner declaring "Happy Birthday!" in joyful, bright font. At the bottom of the screen, once the video had replayed enough times and he could hear again after the confetti pipe bombs stopped exploding in his face, a small message appeared at the bottom of the screen.
"Check the confetti." He scowled. He checked the confetti.
"Your birthday present is in your couch." He scowled. He checked his couch.
A close examination revealed the cushions were not at the exact angle he always left them in (to allow any interlopers who dared one, enter his office or two, sit on his furniture, to immediately slouch and slide forward in an unbecoming manner). Pulling away the cushions revealed a large streamer acting as a pull tab to open the base of his couch, and when he pulled it (cringing inside at the thought of any more…surprises) it revealed…A man. A man, wrapped in wrapping paper and ribbon (is that duct tape?), in a surprisingly secure manner to keep him from escaping. A man with a bow on his head and a USB taped to his forehead, along with a note. A note that read, "This is Colin Mason (also know to very few people as "Chaos," and to many more as "that asshole"). Please feel free to detain him at your leisure, you will find proof of many of his more embarrassingly simply hacking crimes on the USB (see: forehead)."
Suddenly, there was a knock on the door, and a young blonde woman hesitantly stepped inside while the rest of the floor looked in behind her, attempting to see what had transpired in his office in the past two minutes. Looking around curiously, having missed the start of the party, she finished her look-about to give him a small smile and said, "Heyyy, Dad, what's going on in here? And…nice…hat?"
He growled.
It is Jim Sterling's 53rd birthday. Ugh.
#leveragetober23#leveragetober#ao3#alec hardison#eliot spencer#parker#leverage#jim sterling#surprise#birthday surprise
65 notes
·
View notes
Text
Leading Hard Drive Destruction And Shredding Services In London UK
Secure and Certified Hard Drive Destruction with Total Shred
In today’s digital world, simply deleting files from a hard drive is not enough to protect sensitive information. Data can still be recovered using advanced techniques, putting businesses and individuals at risk of data breaches, identity theft, and cybercrime. At Total Shred, we provide leading hard drive destruction and shredding services in London, UK, ensuring that your digital data is permanently destroyed and 100% unrecoverable.

Why Choose Hard Drive Destruction Services?
Businesses and individuals store vast amounts of sensitive information on hard drives, including financial records, personal data, legal documents, and confidential business files. Improper disposal of these devices can lead to serious security threats. Total Shred offers a secure and certified solution, eliminating all risks associated with data leaks by completely destroying your hard drives and other storage devices.
Our hard drive destruction services comply with GDPR, UK data protection laws, and industry standards, ensuring full regulatory compliance for businesses handling personal or client data. Every destroyed hard drive comes with a Certificate of Destruction, providing verifiable proof that your data has been permanently erased in a legally compliant manner.
Our Hard Drive Destruction Process
At Total Shred, we use a specialized shredding process to guarantee the complete destruction of digital data. Our process includes:
Secure Collection: We collect your hard drives from your location using secure transportation methods or provide locked bins for safe storage until destruction.
On-Site or Off-Site Shredding: Choose between on-site shredding, where we destroy the drives at your premises, or off-site shredding, where they are transported to our high-security shredding facility for destruction.
Physical Destruction: We use industrial-grade shredders to break hard drives into tiny, irreparable fragments, rendering all data completely inaccessible.
Certificate of Destruction: Upon completion, we issue a Certificate of Destruction, ensuring full compliance with data protection laws and proving that your data has been permanently erased.
Eco-Friendly Disposal: We prioritize sustainability by recycling shredded materials whenever possible, reducing environmental impact.
Devices We Destroy
Our hard drive destruction services cover a wide range of storage devices, including:
Traditional Hard Disk Drives (HDDs)
Solid State Drives (SSDs)
USB Flash Drives and Memory Sticks
External Hard Drives
CDs, DVDs, and Blu-ray Discs
Backup Tapes and Magnetic Storage Devices
Laptops and Computers (with drive destruction)
Who Needs Hard Drive Destruction Services?
Our services cater to businesses, government agencies, healthcare organizations, financial institutions, and individuals looking for secure and compliant disposal of digital storage devices. Whether you are an IT manager decommissioning outdated equipment, a business owner upgrading technology, or an individual safeguarding personal data, Total Shred provides tailored solutions to meet your needs.
Benefits of Our Hard Drive Destruction Services
100% Data Security – Our advanced shredding techniques ensure that all data is permanently destroyed and cannot be recovered.
GDPR & UK Compliance – We help businesses meet legal requirements for data disposal, avoiding penalties and security risks.
On-Site & Off-Site Shredding Options – Choose the level of convenience and security that suits your needs.
Certificate of Destruction – Get proof of proper disposal for auditing and compliance purposes.
Eco-Friendly Recycling – We responsibly recycle shredded materials to minimize environmental impact.
Convenient Scheduling – We offer one-time destruction services and regular scheduled shredding for businesses handling high volumes of digital data.
The Risks of Improper Hard Drive Disposal
Failing to properly destroy hard drives can lead to serious security breaches. Cybercriminals can recover deleted files, accessing sensitive information such as financial records, passwords, and customer data. Data breaches can result in severe consequences, including legal fines, reputational damage, and financial loss. By using Total Shred’s professional hard drive destruction services, you eliminate these risks and protect your business, clients, and personal data.
Why Trust Total Shred?
With years of experience in secure document and media destruction, Total Shred is the trusted choice for businesses and individuals seeking reliable, compliant, and cost-effective shredding solutions. Our state-of-the-art shredding technology ensures complete destruction of hard drives, storage devices, and digital media, safeguarding your information from unauthorized access.
We take security seriously, implementing strict chain-of-custody procedures from collection to final destruction. Our trained professionals handle your devices with care, confidentiality, and professionalism, ensuring that your data is protected at every stage.
We also offer Residential Shredding Services in the UK, ensuring homeowners can securely dispose of personal data stored on hard drives, documents, or other digital media.
Whether you need secure disposal for home or business, we provide a Professional Shredding Service in the UK tailored to your needs.
Schedule Your Hard Drive Destruction Today
Don’t take chances with your sensitive digital data. Total Shred’s hard drive destruction and shredding services in London, UK provide the highest level of security and compliance for your data disposal needs. Whether you need a single hard drive destroyed or have bulk devices requiring disposal, we offer customized shredding solutions to ensure your data is permanently erased.
Contact Total Shred today to schedule your secure hard drive destruction and protect your business, clients, and personal data from security risks.
#Hard Drive Destruction in UK#Shredding Services In London#Drive Destruction service in UK#Drive Destruction
2 notes
·
View notes
Text
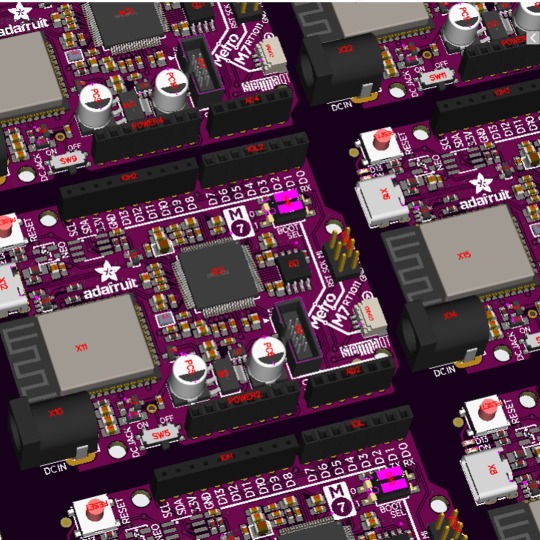
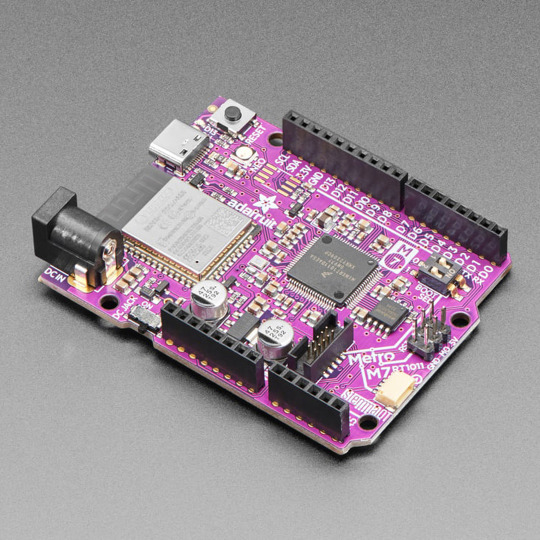

PCB of the day! Adafruit Metro M7 with AirLift - Featuring NXP iMX RT1011 🚀💾🌐
Speedy NXP iMX RT1011 microcontroller with a 500 MHz ARM Cortex M7 processor. 8 MB of QSPI for firmware and disk storage, and 128KB of in-chip SRAM - includes an AirLift WiFi Co-processor for secure, fast wireless integration via CircuitPython library support, and high speed USB.
Leggings and t-shirt of the PCB pattern for fun :)
27 notes
·
View notes
Text
Tails OS
Have you ever traveled and succumbed to using a public computer that could be compromised and could potentially steal your data? Or even want to increase your privacy and anonymity against surveillance? The Tails operating system covers this. After doing some Tor browser surfing, I recently discovered Tails and decided to dig deeper into it and play around with it as I am always looking for new tools and protection measures, I can learn and use. Tails, or “The Amnesic Incognito Live System", is a security-focused Debian-based Linux distribution that connects to the internet only through the Tor network. works by routing internet traffic through a series of volunteer-operated servers called nodes or relays. Each user's data is encrypted multiple times and then sent through a randomly selected path of these nodes before reaching its final destination. At each node, one layer of encryption is removed, revealing only the next node in the path, like peeling layers of an onion, hence its logo and nickname.
Tail's most notable feature is its ability to boot from a USB or CD to turn any computer into a temporary” secure” machine by creating an almost ghost-like presence on the machine. When using Tails nothing is written to the hard disk and only runs from the memory on the computer. On top of this, Tails will actually overwrite the memory when exiting to prevent any cold boot attacks. Meaning, that once you shut down the OS all of your actions and information will be erased from memory. This is much more secure than just using incognito mode in your browser because that information could still be retrieved using computer forensics measures. Despite all this, Tails is not a hundred percent secure. There is still room for vulnerabilities like everything in the cyber realm and you do have the ability to sore data on the portable device to transfer between sessions and it is automatically encrypted, but this can be another vulnerability.
Fun fact: Tails it was used by Edward Snowden the ex-N NSA employee who leaked government secrets.
Sources:
youtube
2 notes
·
View notes
Text
Idk how to explain this without being long-winded, but it’s my blog so whatever.
Basically, I have a 2011 MacBook Pro 15”. I’ve replaced the battery and upgraded the RAM and replaced the 500GB HDD with a 500GB SSD. It’s great! The machine is truly the fastest mobile computer I have.
The 2011 MBP was let go from software updates a while ago, meaning, natively, macOS High Sierra is as high as I can get the thing.
Luckily, this computer is from an era when Apple actually made computers and not eWaste, so I just erased macOS off of it and flashed Zorin OS (an Ubuntu-based Linux distro) onto it. The computer is now even better! It’s my primary productivity machine. The display, speakers, battery life, and thermals are all pretty bad, but it’s just so snappy and problem free I can’t help it.
Now, when I set up Zorin OS I used LVM Encryption to encrypt the entire disk. Basically, upon booting, before anything happens, I’m prompted with a password box. Once I put in the encryption key, the computer would continue booting and bring me to my usual login screen. Great! Easy peasy, extra secur-sy. Well. That was the case.
Somehow, in my efforts to find a way to stop Linux from using my MBP’s Discrete GPU in favor of its Integrated (more efficient, less power hungry) one, I broke something in the EFI or SMC idk. Reinstalling didn’t help. MacOS Recovery mode didn’t help. The only way I fixed it was by wiping the device, running the installer USB, downloading the script I used to fuck it up, and then running it to undo what I previous had it do. This worked. Luckily, I was keeping the machine backed up with Timeshift. So, I wiped the computer again and installed Zorin OS, fresh, reinstalled Timeshift, and restored from backup. The only problem?
When I reinstalled Zorin, I didn’t use LVM Encryption because I was tired of having to manually type in that 25 randomized character password I chose. As a result, now every time I boot the computer, I’m prompted with a “Waiting for encrypted device, (name).” That prevents the machine from booting for about 5 minutes until it just randomly decides “ope, never mind” and finally takes me to my login screen. It does nothing in prohibiting me from using the computer expect prolong it. It’s just annoying and weird as hell, and I have no idea how to get rid of it.
Clearly, the way Timeshift resorted the device has it thinking it’s still an encrypted volume, and I have no idea how to tell it that it is not.
But anyway, it just aggravates me, and I needed to ramble and vent about it. Carry on.
#rambles#computer#computer operating system#os#software#linux#zorin#zorinos#zorin os#annoying#annoyance#apple#fuck apple#macbook#macbook pro
11 notes
·
View notes
Note
orochimaru stood in the corner. darkness covering him. he was busy the past week. not much contact with kabuto other than telling him where to go and what to do next. but while studying new lab results he had a hunch that he had missed something. orochimaru wasn't one to celebrate things like birthdays (or other things). but he wasn't a fool either. keeping a group's morale up by shifting focu onto someone else but himself did result in stronger loyalty coming from his minions.
"kabuto..." he purred, "come here. i have something for you."
@vilesn4ke

"In a moment Lord Orochimaru, I need to save all of this data first." Kabuto replied as the clicking and tapping of the keyboard fills the silence as he is putting away all of the filed data into their folders and saving them in the disks and USBs where he'll keep them in a secure place.

He finally turns off the bright screen and he rubs his eyes to soothe the aching from the bright screen. His eyes try to adjust to the darkness of the room behind him though Orochimaru's beige shirt could be seen in the darkness. If only a little.
"What is it, Lord Orochimaru? Is there something you need from me?" He asks as he approaches them and stops just three feet from them to give them some space.
5 notes
·
View notes
Text
What Things Should Never Be Kept In A Home Safe?
We often find that the issues that people stay in a good would be the similar stuff that mustn't be there. This can include documents which might be rarely if needed together with large sums of cash. Somethings should be kept in a safe whilst others should be store either in a bank or a safety deposit box. Firstly, this is a brief listing of things that you must retain in a home safe: Passports Insurance Policies Power of Attorneys Last Will and Testament It is considered that the best rule to follow along with is to keep anything that is of worth to YOU however, not a thief ought to be trapped in your house safe whilst anything irreplaceable needs to be held in a bank. A home safe is how a thief will expect you to keep valuables and could easily force you to definitely open it if there were to be a break in. A home safe should always be securely anchored on the floor and personal documents should be saved in it. If you can't bolt it down, it is advisable to keep important documents in the bank although generally it's possible to bolt them down. Anything that is very important must be helped by care this also is again a significant consideration with regards to deciding what you're gonna stay in your safe. What to keep in the bank/safety deposit box Valuables for example heirlooms, precious metals and any situation that is not replaced should invariably be saved in the lending company until someone is ready to use it. There is also little time keeping large sums of income for any time period in a good. One reason is that it can get stolen but these guys that's may be earning going back in a very checking account or in another investment. Also, many insurance coverage won't cover a large amount of income in the event of the break in any way so anything stolen wouldn't be recoverable. There are a couple of documents that you will never need outside of regular banking hours like birth certificates and papers for your car. This must be kept securely on your bottom line and will also also save cluttering up your safe. If you have taken any photos or videos of your home possessions for insurance purposes, these again ought to be held in the lending company as storing them in a secure the place where a thief might have to go could lead to these details being stolen too. It has become increasingly common for people to store sensitive data on computer media items for example hard-drives, USBs and CDs. There are several reasons behind this with the most obvious being that they are harder to steal. In Gun Safes , the lender's vault will not vunerable to extreme temperatures or magnetic interference that could erase data. Physical media would typically be a backup for critical data with a computer or tablet, or home-cloud storage systems (these are essentially just an external hard disk drive with Wi-Fi capability), which might be destroyed in the fire
1 note
·
View note
Text
Imagine a butch who dates robotgirls and she's got the belt and carabiner "ready for business" look down, but all the stuff hanging from it is reverse-engineering tools.
A full set of screwdriver bits (including security torx and those weird tri-wing Nintendo ones), assorted spuders, those little rubber suction-cups you use to remove LCDs, a line flashlight, macro lenses, IPA wipes, chip pullers, portable hot air rework gun and a pinecil soldering iron, desoldering braid, a wide variety of ESD-safe tweezers, and one of those anti-stack wristbands but on a retractable lead like it's for walking a dog.
She left her backpack at home but it's got a stereo inspection station, a full set of lockpicks (including those tubular lock impresioning ones), and an aging ThinkPad with a bunch of USB adapters: every memory card format you can imagine, all the major hard drive interfaces, and even 3.5"/5.25" floppy disks thanks to a 3D printed enclosure with a greaseweazle flux imager (the Applesauce stays at home connected to her Mac Mini). A USB optical drive that can read and burn all the cd formats, and a as small plastic case of some blank CD-Rs, DVD-Rs, and Blu-rays. A bunch of USB flash drives, some blank, some preflashed with assorted tools and marked with little keychain labels: some linuxes, a warezed all-in-one windows installer, live distros for tails and kali and partionmagic and DBAN.
She's ready for anything.
#Robot girls#Robotgirls#Thee Silver Mt Zion Memorial Orchestra has an album called This Is Our Punk Rock#And this?#This Is My Pornography
1K notes
·
View notes
Text

I can't find the exact one but one of my favorite childhood CD holders looked something like the above. It was a plastic transparent-but-not-see-through drawer that you opened by pushing into the front to pop it open, and then the front part would pop forwards a little to make it easier to access.
The inside was a bunch of soft sleeves attached to the drawer that you could sort your CDs into. I remember not having very much room and pushing CDs together and very carefully sliding them in to avoid scratching them because I was a child and couldn't just go out and buy new CD holders.
That, combined with spindles like this:

And books like in the original post were everywhere in my home.
And let me tell you: I preferred the floppy disks so much. I had a bunch of 3½" floppy disks (the kind where they're hard plastic and only the internal diskette is still floppy, vs the older kinds where the whole thing was floppy) and they were so nice because they were much easier to store safely, could be rewritten multiple times, and just felt really great to use (the ker-klunk when sliding them in, the ker-pop when ejecting them).

Not nearly as much storage space but files were so small back then. CDs were more for storing larger archival data (backups) and software (installers, games), and floppies were how I moved files around between computers. How I shared them.
I never used zip drives or any of that family. I didn't need that much storage space.

But man I really would love to go to an era where the evolution of the ZIP drive, the Clik drive, was the norm.

Mainly for aesthetic reasons. I think USB drives are fine, but they don't have the satisfying clicks and ejects.
More than anything, though, I wish that people still relied on physical media the way they used to. Now everything's being sent around in cloud storage servers, and backed up to cloud storage servers, and lost in cloud storage server sync failures...
Physical media was so much more under your own control. You didn't have to worry about people tracking what you were doing (even if you think you're not breaking any laws, trust me when I say you'll end up with a record if anybody truly audited your life against the books; so many things that seem intuitively fine are either breach of contract from an EULA you didn't read well enough or surprisingly criminal). You didn't have to worry about the cloud service going offline. Or losing internet.
Electricity was out? As long as you had a generator, those files were still accessible. (I didn't have a generator... couldn't install one in the condos I grew up in, which sucked considering the amount of power outages.)
Internet is so much less reliable by comparison. Cloud providers even less so.
Sure, you had to keep your physical media in the right conditions. The right temperature, humidity, etc. But in my opinion, that's much easier than making sure that your account is secure at all times.
IDK. This sort of thing is why I'm a big fan of Cassette Futurism era of Cyberpunk. The modern Internet-focused Cyberpunk narratives are great for writing dystopian fiction, but the old "haha I stored your soul on a mini CD" era has so much aesthetic appeal and comfort to me.

#compact disk#data storage#floppy disk#zip drive#clik drive#Wishing for certain aspects of a bygone era but not other aspects of it because honestly I think life is better now it's just there are#certain things I would've liked to develop in a different direction
38K notes
·
View notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] From the manufacturer Canvio Ready - Ready To Store. Simple To Use. Toshiba’s Canvio Ready external hard drive uses USB 3.2 Gen 1 technology for transfer speeds of up to 5 Gbit/s – and with plug-and-play technology you’re able to quickly save and secure up to 4 TB of media to a compact, portable device. The Canvio Ready includes ramp load design that prevents damage to the disk while mobile, and a shock sensor that will cut the power to protect data in the event of physical stress – so you can rest assured that your files are safe. 2.5” External Hard Drive | Two-Tone Matte and Gloss Finish | SuperSpeed USB 3.2 Gen 1 | USB-Powered | Drag-and-Drop UseCapacities: 1TB | 2TB | 4TB Key Features High Transfer Speeds The Canvio Ready’s incredibly fast and backward compatible USB 3.2 Gen 1 technology means that you’re able to save and secure documents, photos, movies, and more at speeds of up to 5 Gbit/s. Ready To Plug And Play There’s no setup or waiting with the Canvio Ready – just plug the device in to quickly access and organise your files, before unplugging and going mobile. The Canvio Ready is the ideal companion for busy users who need quick and easy storage. Go In Style Since your Canvio Ready will accompany you on the road, looks are important. That’s why we have given it a distinctive two-tone matte and gloss black finish that’s both stylish and easy to carry. Box Content • Canvio Ready Portable External Hard Drive • USB 3.2 Gen 1 Cable (Type-A to Micro-B) • Quick Start Guide • User’s Manual (Pre-Installed on the Hard Drive) Fast transfer rates up to 5.0 Gb/s Plug-and-play operation no software installation required. USB 3.2 Gen1 backwards compatible (USB 3.0 / 2.0) Reformatting may be required for use with Mac. 3 years Limited Warranty [ad_2]
0 notes
Text
Overcoming Common PC Performance Challenges
Navigating PC Access Issues
In today’s digital age, where personal computers are central to work, gaming, and communication, losing access due to a forgotten password can be a frustrating roadblock. The issue of How To Fix Forgot Windows Password & Can't Sign In is a common challenge for users across the globe. This problem often arises when a user forgets their login credentials or inherits a device with an unknown password. Fortunately, several methods can restore access without compromising data. One effective approach involves using a password reset disk, created prior to the issue, which allows users to reset their credentials via the login screen’s recovery option.
Alternatively, booting into Safe Mode with Command Prompt can enable users to reset the password by accessing the administrator account and entering commands like “net user [username] [newpassword].” For those without recovery tools, creating a bootable USB with a third-party utility can bypass the login, though caution is needed to avoid data loss or security risks. These solutions empower users to regain control, ensuring their PC remains a reliable tool for daily tasks.
Maintaining Optimal PC Performance
Beyond access issues, maintaining a PC’s performance is critical to its longevity and efficiency. The challenge of Check for Overheating & Improve Cooling in PC is vital, as excessive heat can throttle performance, cause crashes, or damage components like the CPU or GPU. Overheating often stems from dust buildup, inadequate airflow, or outdated cooling systems. Users can start by monitoring temperatures using software that tracks CPU and GPU heat levels, with safe thresholds typically below 85°C under load. If temperatures exceed this, physical
inspection is necessary. Opening the PC case to clean dust from fans and heat sinks with compressed air can significantly improve airflow. Ensuring proper fan placement—intake fans at the front and exhaust fans at the rear—creates a balanced cooling system. Upgrading to high-performance case fans or liquid cooling solutions can further reduce temperatures, especially for gaming rigs or workstations running intensive tasks. These steps prevent thermal throttling, maintaining smooth operation and extending hardware life.
Diagnosing and Resolving Access Problems
When addressing How To Fix Forgot Windows Password & Can't Sign In, preparation and caution are key. For users with a Microsoft account, resetting the password online via another device is straightforward, requiring only an email or phone verification. Local accounts, however, demand more technical steps, such as accessing the Recovery Environment by restarting the PC and pressing F11 or Shift+F8 during boot. From there, users can navigate to advanced options to reset credentials or restore the system to a previous point. If these methods fail, reinstalling the operating system is a last resort, though it risks data loss unless files are backed up. Consulting online forums or professional technicians can provide additional guidance, especially for complex setups involving encrypted drives. These approaches ensure users regain access without compromising security, keeping their digital lives on track.
Enhancing Cooling for Long-Term Reliability
To effectively Check for Overheating & Improve Cooling in PC, proactive maintenance is essential. Dust accumulation, a common culprit, can be mitigated by cleaning the PC every three to six months, focusing on areas like the power supply and GPU fans. Reapplying thermal paste on the CPU every two years, costing around $10, improves heat transfer to the heat sink. For users in warmer climates or with high-performance systems, investing in aftermarket coolers, priced between $50 and $150, can lower temperatures by 10-20°C. Ensuring proper case ventilation, with at least two intake and one exhaust fan, maintains consistent airflow. Monitoring software can also alert users to spikes in temperature, allowing timely intervention. These measures protect components, preventing costly repairs and ensuring PCs handle demanding tasks like video editing or gaming without lag.
The Impact on User Experience
Addressing these PC challenges transforms user experience, fostering confidence and productivity. A user who resolved a forgotten password issue shared how regaining access to their work files prevented a missed deadline, highlighting the relief of quick solutions. Similarly, a gamer noted that improving cooling eliminated stuttering during intense sessions, enhancing enjoyment. By tackling How To Fix Forgot Windows Password & Can't Sign In and Check for Overheating & Improve Cooling in PC, users avoid frustration and maintain reliable systems. These fixes empower individuals, from students to professionals, to rely on their PCs for critical tasks, reinforcing the importance of proactive maintenance.
Practical Steps for Implementation
For password issues, users should prepare recovery options in advance, such as setting up security questions or linking a Microsoft account. When addressing How To Fix Forgot Windows Password & Can't Sign In, backing up data before attempting resets is crucial, using external drives or cloud storage. For cooling, regular checks using free monitoring tools can catch issues early. Cleaning requires minimal tools—compressed air cans cost $5-$10—and takes under an hour. For Check for Overheating & Improve Cooling in PC, investing in a cooling pad for laptops, priced at $20-$40, is a simple upgrade.
0 notes
Text
The Illusion of Safety: Why Antivirus Alone Won't Keep Your Information Safe in 2025

For decades, antivirus software was the undisputed champion of digital defense. It sat vigilantly on our computers, scanning files, blocking known viruses, and providing a reassuring sense of security. "I have antivirus, so I'm safe," was a common refrain.
In 2025, that statement is a dangerous illusion. While antivirus remains a fundamental layer of cybersecurity, relying solely on it to protect your valuable information is like fortifying your front door while leaving all your windows and back doors wide open. The cyber threat landscape has evolved dramatically, leaving traditional antivirus solutions struggling to keep up.
Here's why your trusty antivirus, by itself, is no longer enough:
1. The Rise of Zero-Day Attacks
Traditional antivirus software primarily relies on signature-based detection. This means it identifies malware by matching its unique digital "fingerprint" (signature) against a database of known threats. The problem? Zero-day attacks exploit vulnerabilities that are unknown to software vendors and security companies.
Why AV Fails: Since there's no known signature for a zero-day exploit, traditional antivirus simply doesn't recognize it as malicious, allowing it to bypass detection and execute its payload unhindered.
2. The Stealth of Fileless Malware
Modern attackers are masters of evasion. Instead of dropping detectable executable files onto your disk, they increasingly "live off the land" by leveraging legitimate tools already present on your system (like PowerShell, WMI, or scripting engines).
Why AV Fails: Fileless malware operates primarily in memory, performing malicious actions without leaving a discernible file footprint for signature-based scanners to find. Antivirus, designed to scan files, often misses these in-memory threats.
3. The Power of Social Engineering & Phishing
The weakest link in any security chain is often the human one. No amount of antivirus software can stop a well-crafted phishing email or a convincing social engineering scam that tricks an employee into revealing credentials or clicking a malicious link.
Why AV Fails: Antivirus works at the machine level, not the human decision-making level. It can't prevent you from being manipulated into granting access or installing seemingly legitimate software that's actually malicious.
4. Ransomware's Evolving Evasion Tactics
Ransomware has become a sophisticated, adaptive beast. Modern variants use polymorphic code (changing their signature with each iteration), leverage fileless techniques, and are often "human-operated," mimicking legitimate administrative activities to avoid automated detection.
Why AV Fails: The rapid mutation of ransomware makes signature-based detection less effective. Human-operated ransomware often uses legitimate tools and moves slowly, blending into normal network traffic, making it hard for basic antivirus to differentiate malicious intent.
5. Cloud & SaaS Vulnerabilities
Our digital lives increasingly reside in the cloud, utilizing Software-as-a-Service (SaaS) applications and cloud infrastructure (IaaS, PaaS). Traditional antivirus primarily focuses on endpoints (your computer, server).
Why AV Fails: Antivirus doesn't provide visibility or protection for misconfigured cloud storage buckets, exposed APIs in SaaS applications, or insecure configurations in your cloud infrastructure that can lead to massive data leaks. These vulnerabilities are outside its scope.
6. Insider Threats (Malicious & Negligent)
Whether it's a disgruntled employee intentionally stealing data or a careless employee accidentally exposing sensitive information, insider threats bypass perimeter defenses that antivirus sits behind.
Why AV Fails: Antivirus isn't designed to monitor user intent or legitimate actions that become illegitimate (e.g., an employee copying a confidential database to a personal USB drive). It focuses on malware, not misuse of authorized access.
What's Needed Beyond Antivirus: The Modern Defense Strategy
In 2025, securing your information requires a layered, integrated, and adaptive approach. Think of it like building a secure fortress with multiple defenses, not just a locked door.
Endpoint Detection and Response (EDR) / Extended Detection and Response (XDR): These go beyond antivirus by continuously monitoring endpoint activity, analyzing behavior, and providing context for suspicious events, enabling rapid detection and response to advanced threats.
Zero Trust Architecture (ZTA): Assume no trust, even for internal users. Verify every user, device, and application attempting to access resources, regardless of their location.
Robust Security Awareness Training: Empower your "human firewall" with continuous education, realistic simulations, and a culture that prioritizes security.
Data Loss Prevention (DLP): Tools designed specifically to monitor, detect, and block unauthorized movement or exposure of sensitive data, whether accidental or malicious.
Cloud Security Posture Management (CSPM): Continuously monitors your cloud environments for misconfigurations and compliance violations that could lead to data leaks or breaches.
Identity and Access Management (IAM) & Multi-Factor Authentication (MFA): Strong controls over who can access what, reinforced by multiple authentication factors.
Network Detection and Response (NDR): Monitor network traffic for anomalies that might indicate ransomware spread, data exfiltration, or command-and-control communication.
Proactive Vulnerability Management & Patching: Regularly identify and fix software flaws before attackers can exploit them.
Incident Response Planning: Have a clear, rehearsed plan for what to do when (not if) a breach or attack occurs, to minimize damage and ensure rapid recovery.
Antivirus is still a foundational component of a good cybersecurity strategy, acting as your first line of defense against known threats. However, it's just one piece of a much larger, more complex puzzle. To truly keep your information safe in 2025, you need to move beyond a false sense of security and embrace a comprehensive, multi-layered approach that adapts as quickly as the threats themselves.
0 notes
Text
I would recommend Signal, Element (Matrix) and SimpleX for this.
Briar, Session, and Threema are also great, but have one or two issues which may be, well, issues.
Larger platforms, such as Discord, WhatsApp, FB Messenger, Snapchat, and WeChat, should be considered to be backdoored. SMS and RCS are out of the question entirely. I do not know how secure iMessage is.
Also, use a secure and trustworthy VPN. My recommendations are Mullvad, Proton, Riseup, Windscribe, and IVPN.
Tor is also a good option, though many websites' DDoS protection will block you if you use this.
I would not recommend more popular VPNs, such as Nord, Surfshark, and that weird offbrand one you probably have somewhere. They are proprietary, and almost always log your activity.
The VPN should be coupled with a trustworthy browser, such as Firefox, Librewolf, Tor Browser, Mullvad Browser, Brave, or some other open-source browser (like Konqueror or Epiphany or whatever).
Do not use Chrome, Opera, Yandex, or Maxthon, as they log your activity.
Likewise, do not use Google, Bing, or Yahoo!. Brave Search, DuckDuckGo, Startpage, Whoogle, and SearXNG are infinitely more private, and tend to give better results anyway.
Finally, I would recommend not using Windows or Chrome OS, as the former often contains backdoors and both of them (you guessed it) log your activity. I would personally recommend using a Linux distribution (such as Linux Mint) and enabling disk encryption during installation. This one's a little more advanced, though.
Alternatively, create a Tails USB and use that for your secret activity.
Finally, I'd recommend checking out Techlore and Privacy Guides for further advice.
Hope you find this helpful!
Please reblog for visibility.
Anyway American trans friends, now's the time to put "be gay do crime" into practice and the first step is to get onto secure communication channels so you're not discussing details of what you're doing and how on the public internet.
15K notes
·
View notes
Text
Ensure Data Integrity with Regular Disk Health Tests – ULink’s Smart Approach to Drive Health
In today’s digital-first world, data is everything. Whether you’re an individual professional or a business enterprise, the health of your storage drive plays a vital role in performance, security, and long-term reliability. That’s where a disk health test becomes essential. At ULink, we empower users with smart tools and advanced analytics to ensure their hard drives and SSDs stay healthy and failure-free.
What Is a Disk Health Test?
A disk health test is a diagnostic process that checks the physical and operational status of your hard drive or solid-state drive (SSD). It includes analyzing SMART (Self-Monitoring, Analysis, and Reporting Technology) data, checking read/write errors, bad sectors, temperature variations, and overall performance metrics.
ULink’s intelligent testing tools offer a fast, user-friendly, and precise disc health check that identifies potential problems before they result in data loss.
Why Is Disc Health Check Important?
Just like you go for regular health check-ups, your storage devices also need periodic inspections. Here’s why:
Early Detection of Failures: Prevent catastrophic data loss by identifying early signs of hardware failure.
Performance Optimization: Detect slowdowns caused by bad sectors or overheating.
Data Security: Keep your data safe by ensuring your disk is operating optimally.
Extended Drive Life: Regular checks help you adopt preventive measures and avoid abrupt failures.
ULink’s disc health check tools are designed to scan deeply while keeping it simple for both IT professionals and everyday users.
How ULink Helps You Monitor Disk Health
ULink offers industry-leading diagnostic solutions tailored for OEMs, system integrators, and IT service providers. Our advanced tools support:
Comprehensive SMART Analysis
Drive Usage and Temperature Monitoring
Bad Sector Detection
Predictive Failure Alerts
Detailed Health Reports
Whether it’s an internal HDD, external USB drive, or high-performance SSD, our disk health test systems are compatible with a wide range of devices.
When Should You Run a Disk Health Test?
ULink recommends running a disk health test:
Every 3-6 months for regular users
Monthly for professionals and IT admins
Immediately when you notice symptoms like slow boot, frequent crashes, or unusual noises
With ULink, scheduling automated scans and receiving real-time alerts makes drive maintenance hassle-free.
Conclusion
Don’t wait for a crash to remind you of your drive’s health. Regular disc health checks with ULink’s cutting-edge tools ensure your storage devices run smoothly and your data stays protected. Stay one step ahead of disk failures—because prevention is always better than recovery.
Visit us https://ulink-da.com/
0 notes