#website malware scan
Explore tagged Tumblr posts
Text
Website: https://www.turacolabs.com/
Address: 31a Charnham Street, Hungerford, Berkshire, RG17 0EJ, United Kingdom
Turaco Labs specializes in eCommerce cybersecurity, offering ThreatView, a state-of-the-art cyber threat detection and PCI DSS compliance monitoring solution. Their services focus on protecting online businesses from malware, digital skimmers, loaders, and data theft. With a free security scan, breach protection warranty, and forensic-level monitoring, they provide a proactive defense system for online stores using platforms such as Magento, WordPress, OpenCart, and Joomla. Their ThreatView solution ensures continuous monitoring, detects the latest cybersecurity threats, and helps eCommerce merchants comply with PCI DSS standards.
LinkedIn: https://www.linkedin.com/company/turaco-labs-threatview/
Keywords: eCommerce cyber security website malware scan scan website for malware PCI compliance monitoring free website security scan website security monitoring website compliance audit security services website website malware scanning tools eCommerce security solutions eCommerce fraud prevention ecommerce fraud prevention companies prevent ecommerce fraud website malware scanner PCI compliance services pci compliance service provider pci compliance consulting services cybersecurity services for small businesses Magecart protection Google Tag Manager malware hacked website recovery eCommerce security best practices website security services malware removal from weebly website website malware removal website malware removal service how do i remove malware from my website how to remove malware from website how to remove malware from wordpress website malware removal for websites malware removal website remove malware from website best website malware removal how to remove virus from website website protection services best website protection service website malware protection services ecommerce fraud protection services
#eCommerce cyber security#website malware scan#scan website for malware��#PCI compliance monitoring#free website security scan#website security monitoring#website compliance audit#security services website#website malware scanning tools#eCommerce security solutions#eCommerce fraud prevention#ecommerce fraud prevention companies#prevent ecommerce fraud#website malware scanner
1 note
·
View note
Text
Best WordPress Security Plugins for 2025
Introduction WordPress is the world’s most popular content management system (CMS), powering over 40% of all websites. While its flexibility and ease of use make it a preferred choice for bloggers, businesses, and developers, its popularity also makes it a prime target for hackers, malware, brute force attacks, and security vulnerabilities. One of the best ways to protect your WordPress site is…
#best security plugins#brute force attack prevention#malware protection#security best practices#two-factor authentication#web application firewall#website security tools#wordpress backup plugins#wordpress cybersecurity#wordpress firewall#wordpress login security#wordpress malware scanning#wordpress security#wordpress site protection
0 notes
Text
Website Security Helper
Phone: 1800 921 554
Address: 110/108 Albert St, Brisbane City, QLD 4000
Website: https://websitesecurityhelper.com.au/
Specialist website security services for business owners wanting to protect their valuable asset. We understand the importance of your customers always being able to access your website.
Our 24 hour guarantee means that you will always be able to reach us 24 hours a day, and that we will have your website files cleaned within 24 hours or less in most cases.
Our head office is located in Brisbane, however we service customers right across Australia.




#Website Security#Malware Removal#Wordpress Malware Scan#Wordpress Malware Removal#Ongoing Website Security Services#Website Maintenance#Website Speed Optimisation#Website Penetration Testing
1 note
·
View note
Text
SCAM/BOT WARNING - velvetnightsstuff
If you are in any MARVEL related community please let the admins know about this user so they can ban them!
The user velvetnightsstuff is not only stealing artwork, the blog is chalk full of malicious links that lead to fake websites that include viruses/malware.
This user is joining any and all MARVEL communities, and I found this out because it tried to join my own and when I searched MARVEL and looked at at least 6 of the communities with 60+ users, it was in every one of them.
Idk if it's started posting in communities yet, but my guess is it's going to try and share its malware posts into communities at some point to try and get people to click on it.
The chain of its links goes as follows:
Fake movie website > QR code scan popup to 'continue' > Scan leads to file (malware) download page.
Do not click on any of the links on this users blog or on any post it makes in your community.
If you ever see a post that has a url that blatantly shows its non genuine like a bitly link or some sort of url shortner, or when hovered over it shows it leads to a shortened url or a url redirect website, it is 100% going to scrape your IP/info, then lead you to a phishing/virus website.
Please stay safe!
#marvel#the avengers#mcu#marvel community#scam#scams#scam alert#scam warning#scammer#online scams#scam bots#tumblr scam#velvetnightsstuff
41 notes
·
View notes
Text
off 2 a bad start. i accidentally installed it from a website that may or may not have had malware in it 👍
hrm... i should play pokemon infinite fusion
#the zip had a readme file that directly mentioned that the website didn't have the creator's permission to host the download link#and the actual github post said there had been reports of malware in the files on that site#before finding the actual download link the first thing i did was run an anti virus scan and nothing came up so i should be good though#imagine putting malware in someone else's installer and forgetting to edit the readme file saying that your website was fake. lmao
23 notes
·
View notes
Text

PSA! THERE IS MALWARE ON YAYTEXT!
I'm not fully sure just how relevant this will be, but if anyone else uses yaytext to fancify their text with unicode, please be aware that there is now malware on the yaytext website ( yaytext.com ). it has been on there for at least a week now, so if you have gone onto the site, you might have been infected!
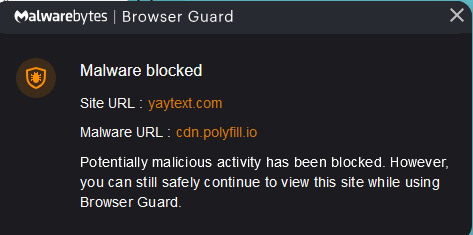
WHAT NOW? IF YOU HAVE VISITED YAYTEXT:
first, run a malware scan on your computer. you can do this for FREE with malwarebytes, bitdefender, or kaspersky*. you can find the free versions of these antivirus softwares on their respective websites, and I will link them below for convenience.
after you run the malware scan (hopefully you are not infected!), add the respective browser guard to your browser. as you can see by my screenshot, I use Malwarebytes' broswer guard. if you decide to use their browser guard too, you will still be able to safely use yaytext.
WHERE ELSE DO I GO?
you should assume that yaytext IS NOT safe to use for the time being! there are plenty of other unicode generators out there, however, so you don't have any disruption with your aesthetics.
some alternatives are:
fontspace font generator
lingojam text generator
fontalic
I have just checked all of these sites and none of them have malware on them at this time.
ANTIMALWARE SCANNING
MalwareBytes - free version BitDefender - free version Kaspersky* - free version
*note that Kaspersky is being banned in the U.S. for being a Russian company. The ban is over worries that Russia could use the AV as spyware in the U.S., because the Kremlin can force any company in Russia to share all of their data with them. Despite this, Kaspersky is a top contending cybersecurity research company. If you are not comfortable using Kaspersky, studies have shown that BitDefender provides near equivalent results. source: i am getting my degree in cybersecurity lol
74 notes
·
View notes
Text
the fallout london installer potentially contains malware and the downgrader has the potential to harvest your steam password. hesitate to download or use these exes until we know more and consider scanning for viruses if you've run the installer
i mean its probably nothing but idk enough about cybersec to dismiss this talk. malware reports are from reddit, and some gaming websites noted that their downgrader casually requests and uses your login info
(you could theoretically run the downgrader through a throwaway steam account and copy it over) (or use a different method)
48 notes
·
View notes
Text
Simfileshare
Hi everyone! It came to my attention that the second creator's Simfileshare account got hacked so checked mine. None of my files are affected, I secured my account with a new strong password. And all of my files are uploaded in .package format with a couple of exceptions. Please, be careful on the internet. Being hacked is no joke. 3 weeks ago my gmail account was hacked and all of my passwords and some credit card info got leaked on the darkweb. I have spent 3 weeks securing all of my accounts, dealing with charges to my Amazon and Ebay accounts, my website has been hacked and injected with malware (it is fixed, and I had to buy an extra protection by my hosting company), my credit card was charged by some organization in Dubai. Long story short, be vigilant with what you download, scan your computers regularly.
15 notes
·
View notes
Note
Mac, if you (or any sentient device) gets a virus, is that the equivalent of getting sick like humans? Or is there another analogy that we humans don't know about? And if the virus can't be fixed, is that basically like a fatal illness/injury for devices??? (I did remember in one of Mac's dialogue, they mentioned that the way computers sleep isn't the same as humans, or as simple as just shutting down or putting your computer to sleep.)
Ps. Same person who asked about if Mac had any wires in them. 😜
I guess it isn’t too indifferent from how humans become sick, it can be shared when interfacing with other electric based Things. Viruses are a more.. complex version of an illness, they can range from something terrible, it can be something that slowly shuts down our system over time to just a slight hiccup with processing power every now-and-then. There are always ways to prevent Viruses, running scans to check for malware and not downloading from sketchy websites are always excellent places to start.

But in the more serious case where it has already imbedded it’s roots in our software it may call for something akin to a uhh.. factory reset.

12 notes
·
View notes
Text
Be Careful Putting Your Phone Down At Panera Bread Locations
I noticed my phone buzzing repeatedly when I'd have it open on the table at Panera, and on further review I realized that my phone was repeatedly scanning an NFC tag on the underside of the table. I'm assuming the servers use these as a shorthand way of confirming that food has been delivered to the correct table.
This is all well and good; this is a prime use case for NFC tags, and using an NFC reader app I was able to see that they're just basic numeric codes. As long as the tags aren't rewritable by anyone, they're not a security risk.
The NFC tags at Panera Bread are rewritable. Like, easily. Using a simple app you can get from the Google Play Store.
What this means is that someone can rewrite the NFC tags to redirect to a download link for malware, or a phishing website, or any number of other attack vectors.
I have more information about this issue on my personal website, as well as a video demonstrating the effect. My recommendation is to keep NFC turned off on your phone unless and until you're actively using it (for touchless payments, bus tickets, etc.).
39 notes
·
View notes
Text
My eighteenth fic for @badthingshappenbingo!

Fandom: Ninjago
Trope: Tonsillitis
Also available on AO3!
Sick of These Movies
Zane woke up coughing for the eighth night in a row. He thought the problem would go away by now, but his condition was worsening day by day, and every once in a while a new symptom of his suspected illness would affect him, persuading himself even more to just get the surgery done. But he didn’t want the others worrying about him. Yeah, that was the only reason he didn’t want to get treated. He definitely wasn’t scared.
He glanced at the clock on the wall– 3:47 a.m.– and made his way towards the hangar bay, where he knew he would be alone. Well, sometimes even a nindroid can be wrong.
He sat on the chair in front of the supercomputer’s monitor, and started his research on the anatomy of a nindroid. That’s when he realised he wasn’t alone.
“And what do you think you’re doing at this time?” Pixal asked from behind him. Zane flinched and turned around to see his girlfriend standing behind him. “Have you made it a new routine to wake up around this time and roam around the monastery?”
“Pixal, I–” Zane stammered, lost for words, before frowning. “What are you doing awake at this time every night?” He retorted.
She was taken aback by the question, not sure of a response, and decided to come clean. “I’m worried about you,” she sighed. “You keep coughing, and you’ve made it obvious you’re irritated in other ways too. Don’t think I haven’t noticed how exhausted you are, and how you’re not eating much these days. I know you don’t have to but it’s something you enjoy that you are no longer doing. Not to mention how the ice you’re making melts almost immediately.”
Zane groaned, knowing that he also had to confess to Pixal. “Pixal, I think I have tonsillitis,” he said, his eyes scanning her face for a reaction. “My tonsil drives seem to have gotten a virus from somewhere. I suspect I might have gained it while downloading a movie into my system from tinyurl.com/freemoviesatninjago.”
Pixal dragged a hand down her face. “Why were you pirating movies, Zane?”
“It was not piracy. The website said “100% free, safe and legal. Rated five stars from the government of Ninjago.”
“Zane– you know what, this is ridiculous. We have to fix this.”
“Report the website to the police?”
“We’ll do that later. For now, we have to fix what’s wrong with you.”
“You want me to train myself so that I can easily tell who’s a scammer and who’s not?”
“Well… that too. But for now, I’m talking about your physical wellbeing, Zane. You need to get your tonsils removed.”
“Fine. But make sure it doesn’t hurt, alright?”
Pixal smiled. “You know I’d never hurt you, unless my system gets hacked by malware, although the chances of that happening right now is about 0.36961389999999999…”
***
Nya was startled awake by the sounds of a loud drill working underground. She got out of bed groggily, and tried to process where the noise was coming from. Underground… what’s underground? There’s… there’s… the hangar bay! There’s an invasion!
She jumped out of bed, swiftly but quietly, and snuck her way through the monastery. As she got closer, and the noises got louder, she could now also make out Pixal’s voice, repeatedly calling out the word “nine”. She’s been hacked! And whoever broke in must be trying to pull her apart using that drill!
Fueled by her own assumptions, she made her way to the relaxation room and threw a couple of darts at the board on the wall, and got through the entrance, ready to deal with the heartless people who thought they could get away with what they did.
As she entered the bay, she expected to see Pixal’s mutilated body on the ground or something. Well, someone was broken apart, but it wasn’t Pixal. Instead, she was met with the sight of the samurai holding Zane’s detached head and drilling through the bottom of his neck.
Nya screamed. “Pixal, NO!” She ran to her and snatched Zane’s head away from her, causing the nindroid to stop reciting the same number over and over again. “Who hacked you?”
“Let me go, Nya,” Zane’s head spoke, earning another scream from her and being dropped to the ground. The head rolled so that it was facing the water ninja. “She has not been hacked. She is performing surgery on me.”
Nya looked at him in disgust. “What sort of surgery requires beheading? And why haven’t you been given an anaesthetic!?”
“I am a nindroid. I do not need pain medication. I just turned off my nerve circuits. And as for the ‘beheading’, Pixal said it was much easier to remove my tonsil drives that way. As I do not bleed, I am not in danger. Pixal made sure to be careful and detached everything properly.”
Despite the explanation, Nya gagged. “Okay, okay,” she said, handing Zane’s head back to Pixal. “Just do your work, Pix.”
It only took fifteen more minutes for the procedure to end, while Nya sat on a chair a couple metres away, looking at the floor and holding her head. She didn’t want to watch Zane’s head being drilled in Pixal’s hands, but at the same time she wanted to make sure he was okay.
As Pixal tightened the last screw on Zane’s head, she gave Nya a thumbs up. “We’re done. You can look now.”
Nya lifted her head, and smiled as she saw that Zane had been fixed up. “You’ve gotta tell me, Zane,” she laughed. “Why do you even have tonsils in the first place? And what got them inflamed?”
“I’m not sure,” he responded. “I guess my father-- I mean, creator, Dr. Julien, wanted me to look as human-like as possible. I have an appendix drive, too. I hope I don’t install any malware there too, because it would be far more invasive to remove that.”
“Well, don’t go looking for films on ‘tinyurl.com/freemoviesatninjago’ then.”
Zane pouted. “But Jay said it had everything...”
Nya sighed. “Well, now we know the culprit of this mess. Remind me to check for viruses in his computer in the morning.”
“Remind me to tell Wu to punish him,” Zane frowned. “I can’t keep my nerve circuits off for too long and my throat hurts.”
Nya looked at the tonsil drives on the table. “Yeah, those look nasty. And gross.” She looked at the clock and groaned. “Master Wu’s gonna go to wake me up in less than an hour, and I don’t think I’ll be able to sleep in that much time. What do I do?”
Pixal picked up a drive. “Well, I could attach these to Jay’s computer, and the movies are still installed on these, so...”
The girls turned to Zane, who rolled his eyes.
“Fine. Use your sick friend for your own benefits.”
#Ever since I received this card about ten months ago this was one of the prompts for which I had NO IDEA what to write for#I thought I would just make it Lloyd-centred like almost all my other fics but just recently I had an idea:#“Why don't I give the character who can't get tonsillitis tonsillitis?”#ninjago#ninjago fanfiction#zane ninjago#zane julien#nya ninjago#nya smith#pixal ninjago#pixal borg#tw body horror#tw mutilation#though nobody dies#it's hard to explain...#it's not meant to be a violet fic#it's supposed to be an absolutely terrible attempt at humour#badthingshappenbingo#bad things happen bingo
10 notes
·
View notes
Text
PES 2013 Indir How to Download and Enjoy Pro Evolution Soccer 2013
Introduction
If you’re a football gaming enthusiast looking to relive the excitement of classic soccer gameplay, PES 2013 remains one of the most beloved editions of the Pro Evolution Soccer series. Whether you want to play on your PC or laptop, learning how to PES 2013 indir (download PES 2013) safely and efficiently is key. In this article, we’ll guide you through everything you need to know about downloading, installing, and enjoying PES 2013.
What Is PES 2013?
Pro Evolution Soccer 2013 is a football simulation game developed by Konami. Released in 2012, it’s praised for its realistic gameplay, improved AI, and authentic football experience. Despite newer editions, many gamers prefer PES 2013 for its smooth mechanics and nostalgic value.
Why Download PES 2013?
Even years after its release, PES 2013 holds a special place due to:
Classic gameplay that is simple yet deep.
Realistic player animations and ball physics.
Strong community mods and patches that keep the game fresh.
Light system requirements, perfect for older PCs.

How to Download PES 2013 (PES 2013 Indir) Safely
Downloading PES 2013 requires caution to avoid viruses or malware. Here’s a step-by-step guide to help you:
Find a Reliable Source: Use trusted websites or official platforms known for hosting game files. Avoid random download links from unknown sources.
Check for Legitimate Files: Look for files with proper descriptions, user reviews, and safe download indicators.
Download the Setup File: Choose the correct version for your system (usually PC).
Scan for Viruses: Before installation, scan the downloaded file with antivirus software.
Install the Game: Follow the on-screen instructions to install PES 2013 on your device.
Apply Patches or Mods (Optional): If you want updated teams or features, look for popular community patches.
System Requirements for PES 2013
Before downloading, ensure your PC meets these minimum requirements:
OS: Windows XP/Vista/7/8/10
Processor: Intel Core 2 Duo 1.8 GHz or AMD equivalent
RAM: 2 GB
Graphics: NVIDIA GeForce 8600 or ATI Radeon HD 2600 or better
Storage: 8 GB free space
DirectX: Version 9.0c
Meeting or exceeding these specs guarantees smoother gameplay.
Installing PES 2013: Tips and Tricks
Run as Administrator: This helps avoid installation errors.
Disable Antivirus Temporarily: Some antiviruses block game files mistakenly. Remember to enable it after installation.
Update Graphics Drivers: Make sure your GPU drivers are current for the best performance.
Use Compatibility Mode: If you face issues on newer Windows versions, run the installer in compatibility mode for Windows 7 or 8.
How to Play PES 2013 Online
Many PES fans enjoy multiplayer matches. To play online:
Set up a stable internet connection.
Use third-party platforms like PES League or eFootball.net (if supported).
Join community servers or use VPNs if direct matchmaking is unavailable.
Always update the game and patches to ensure compatibility.
Popular Mods and Patches for PES 2013
Enhance your PES 2013 experience with community-created mods:
Updated team rosters and kits.
New stadiums and crowds.
Improved graphics packs.
Gameplay tweaks and fixes.
Look for popular patches like the PES 2013 Data Pack or SMoKE Patch for the latest updates.
youtube
Troubleshooting Common Issues
Game crashes on startup: Update drivers, disable background apps, or reinstall.
Lag or low FPS: Lower graphic settings or close other programs.
Multiplayer connection problems: Check firewall settings and ensure ports are open.
Conclusion
Downloading and enjoying PES 2013 indir is still very much possible and rewarding for football game lovers. With the right sources, proper installation, and optional mods, you can bring back the excitement of one of the best football simulation games of its generation. Follow the steps above, and get ready to score goals, make incredible passes, and experience the thrill of classic PES gameplay!
FAQs
Q1: Is PES 2013 free to download? Usually, you’ll find free downloads for demo or trial versions, but full copies might require purchase or use of legit platforms.
Q2: Can I play PES 2013 on Windows 10? Yes, with proper compatibility settings and updated drivers, PES 2013 runs fine on Windows 10.
Q3: Are mods safe for PES 2013? Most popular mods are safe, but always download from trusted sources and scan files for malware.
Q4: Can I play PES 2013 on Mac? PES 2013 is primarily for Windows; running on Mac requires additional software like Bootcamp or a virtual machine.
Q5: Where can I find patches for PES 2013? Community sites and forums like PES Patch or Evo-Web are great places to start.
2 notes
·
View notes
Text
Why Irish Businesses Should Always Maintain Their Websites
Since so much is pulled up online, your website may be the first interaction a customer has with you. Having a good-looking website can separate businesses in Limerick, Galway and even Dublin from rivals, allowing them to attract new customers.
We have assisted many Irish businesses and what we notice most is that keeping your website up to date helps maintain your online reputation and promotes growth in the future.
In the following sections, we will focus on why maintaining your website is important for your business.
1. First Impressions Matter
You would make sure the area near your store was tidy, fresh and not damaged. What is the point of doing it again in the cyber world?
Most of the time, a potential customer’s first contact with you happens when they visit your site. If the site takes a long time to open, links do not work, the information is old or the appearance is outdated, it gives a feeling that nobody cares. This scares off visitors and weakens your reputation.
If you regularly look after your website, it will continue to be fresh and serve its purpose, making people trust it and enjoy it.
2. Security Should Always Be Considered from the Beginning
More organizations are under cyber attacks and even small businesses are being targeted. Almost all the time, WordPress, Joomla, Magento and other content management systems make security updates to guard against new risks.
If you do not maintaining of your site:
Your customer details could be taken by fraudsters.
A search engine may blacklist your website.
Our maintenance services at Flo Web Design include regular security audits, updates for plugins and malware scans to give you a worry-free website and protect your visitors.
3. SEO depends on regular website maintenance
Google and other search engines prefer websites that get updated and maintained frequently. If a site is slow, features old information or isn’t accessible on mobile, it will be given a lower ranking by search engines.
Keeping your website updated makes it better:
How fast web pages are loading
Mobile responsiveness
Metadata and organized data
Dealing with broken links
Content freshness
As a result, your website becomes more visible to search engines, it gains higher positions and gets more traffic.
4. Improve the way users interact with the application
Website users today want sites that are easy to use and quick to respond. Anything that makes the site slow such as images that don’t load or ancient navigation, will lead them to leave.
Maintaining the website often helps keep:
All the links and pages are accessible.
Pictures and videos are displayed without any errors.
Checkout, buttons and forms work efficiently.
Updates are made to give the program a new look.
A seamless experience for users will make them more likely to stay and possibly become paying customers.
5. Making Sure Your Content is Up-to-Date
Information about companies can vary—such as their prices, services, working hours, contact details, special deals, employees and similar elements. If the changes aren’t reflected on your website, it confuses your customers and decreases trust.
If your site is updated, you demonstrate that your business is lively and interested in its customers.
Our team at Flo Web Design ensures that Irish companies update their content, update their blogs and remove any old materials from their website.
6. This involves backing up and recovering your data
Website crashes can happen for reasons such as plugin conflicts, issues with the server, hacking or making a mistake while deleting something important. If you don’t back up your files often, you could lose everything you have worked on for a long time.
With our maintenance package, your site is backed up automatically, making it easy and quick to restore it and continue your business.
7. The standards of both Compliance and Performance
All Irish businesses should follow the rules set out by GDPR. Failing to keep your contact forms and cookie policies current could result in serious fines and legal issues.
Maintenance done regularly will help your website:
Follows the necessary regulations for data protection.
The website is fast to load on every type of device.
Still works properly after OS and browser updates.
It’s more important to establish trust and eliminate risks than just fulfilling the requirements.
8. Making Your Website Resistant to Future Changes
Technology keeps advancing all the time. Plugins become old, browsers are updated and people’s needs change.
When you maintain your website regularly, it grows with your business. If you add new features, boost e-commerce or update the design, frequent upgrades help you not have to begin again.
How a Retailer in Ireland Benefited from Website Maintenance
A shop in Cork contacted us for help because their site was down for two days. Since the developers failed to update the site’s plugins or security measures for more than a year, the site was breached.
We recovered the site from our backup, removed the malware, updated the plugins and applied the best security measures. By opting for a monthly service package, they haven’t experienced any downtime and now get 35% more online inquiries due to faster performance.
Take action before a problem arises. Keeping your computer well-maintained is like having insurance.
So, What Services Are Part of Website Maintenance with Flo Web Design?
Our services include packages that are customized for businesses in Ireland.
Keeping an eye on security
Ensuring a fast website
Links on your website are checked for breaks
Backup & recovery
Updates on GDPR compliance
Updates to the content (upon request)
We’ll take care of your website’s back end, helping it run as efficiently as you run your business.
Conclusion
Just as you maintain a car regularly, you should keep your website up to date. This rule also applies to the internet. A secure, effective and successful website depends on regular upkeep.
Your website’s updates, security and page issues are all taken care of by Flo Web Design. We handle all the necessary jobs, allowing you to focus on your business.
Want to Maintain Your Site in the Best Way Possible?
We will make sure your website is kept safe, fast and performing at its peak each and every month.
2 notes
·
View notes
Text
Prevention Techniques for Top 10 Common Cyber Attacks

In the ever-escalating war against cybercriminals, staying informed about the most common attack vectors is half the battle. The other half is implementing robust prevention techniques. As we navigate 2025, the threat landscape continues to evolve, but many foundational attack methods remain prevalent due to their effectiveness.
Here's a breakdown of the top 10 common cyber attacks and the essential prevention techniques to keep you and your organization secure.
1. Phishing & Smishing (SMS Phishing)
The Attack: Attackers impersonate trusted entities (banks, colleagues, popular services) via email or text messages to trick recipients into revealing sensitive information, clicking malicious links, or downloading malware. Modern phishing often uses AI to generate hyper-realistic content.
Prevention Techniques:
Vigilant User Education: Train employees to scrutinize sender email addresses, hover over links to check destinations, and be suspicious of urgent or generic requests. Conduct regular simulated phishing tests.
Multi-Factor Authentication (MFA): Even if credentials are stolen, MFA can block unauthorized access. Enforce it widely.
Email & SMS Security Solutions: Deploy advanced email filters (e.g., Microsoft Defender for Office 365, secure email gateways) that scan for suspicious patterns, attachments, and URLs. Forward suspicious texts to 7726 (SPAM).
DMARC, SPF, DKIM: Implement these email authentication protocols to prevent email spoofing of your own domain.
2. Malware (Viruses, Worms, Trojans)
The Attack: Malicious software designed to disrupt, damage, or gain unauthorized access to computer systems. Malware can be delivered via downloads, malicious websites ("drive-by" attacks), or attachments.
Prevention Techniques:
Antivirus/Endpoint Detection & Response (EDR): Install and keep robust antivirus and EDR solutions updated on all devices.
Regular Software Updates: Patch operating systems, applications, and browsers promptly to close security loopholes that malware exploits.
Firewalls: Use network and host-based firewalls to control incoming and outgoing network traffic.
Download Caution: Only download software and files from trusted, official sources. Scan all downloads before opening.
3. Ransomware
The Attack: A type of malware that encrypts a victim's files or locks their system, demanding a ransom (usually in cryptocurrency) for decryption or restoration of access. It often enters via phishing or exploiting unpatched vulnerabilities.
Prevention Techniques:
Robust Backups: Implement a 3-2-1 backup strategy (3 copies, on 2 different media, with 1 copy off-site and isolated/immutable). Regularly test recovery.
MFA & Strong Passwords: Crucial for protecting remote access services (like RDP) often targeted by ransomware operators.
Vulnerability Management: Continuously scan for and patch vulnerabilities, especially on internet-facing systems.
Network Segmentation: Divide your network into isolated segments to prevent ransomware from spreading laterally if it gains a foothold.
Security Awareness Training: Educate employees about ransomware's common entry points (phishing).
4. Distributed Denial of Service (DDoS) Attacks
The Attack: Overwhelming a target server, service, or network with a flood of internet traffic from multiple compromised computer systems (a botnet), aiming to disrupt normal operations and make services unavailable.
Prevention Techniques:
DDoS Protection Services: Utilize specialized DDoS mitigation services (e.g., Cloudflare, Akamai) that can absorb and filter malicious traffic.
Content Delivery Networks (CDNs): CDNs distribute traffic and cache content, helping to absorb some attack volume and improve resilience.
Rate Limiting: Configure servers and network devices to limit the number of requests they will accept from a single IP address or source over a given time.
Network Redundancy: Ensure your infrastructure has redundant systems and sufficient bandwidth to handle traffic spikes.
5. Man-in-the-Middle (MitM) Attacks
The Attack: An attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other. This often happens over unsecured Wi-Fi.
Prevention Techniques:
Always Use HTTPS: Ensure websites you visit use HTTPS (look for the padlock icon in the browser address bar) to encrypt communication.
Avoid Public Wi-Fi for Sensitive Tasks: Refrain from accessing banking, email, or other sensitive accounts over unsecured public Wi-Fi networks.
Use VPNs (Virtual Private Networks): VPNs encrypt your internet traffic, creating a secure tunnel even over public networks.
Strong Authentication: Implement MFA and passwordless authentication to mitigate credential theft even if traffic is intercepted.
6. SQL Injection (SQLi)
The Attack: An attacker injects malicious SQL code into input fields of a web application to manipulate the database, potentially leading to unauthorized access, data theft, or data corruption.
Prevention Techniques (primarily for developers):
Prepared Statements & Parameterized Queries: The most effective defense. Treat user input as data, not executable code.
Input Validation & Sanitization: Validate and sanitize all user input on both the client and server sides to ensure it conforms to expected formats and removes malicious characters.
Least Privilege: Grant database accounts only the minimum necessary privileges required for their function.
Web Application Firewall (WAF): WAFs can detect and block common web-based attacks like SQLi.
7. Cross-Site Scripting (XSS)
The Attack: Attackers inject malicious client-side scripts (e.g., JavaScript) into web pages viewed by other users. This can lead to session hijacking, defacement of websites, or redirection to malicious sites.
Prevention Techniques (primarily for developers):
Output Encoding/Escaping: Properly encode or escape all user-supplied data before rendering it in HTML to prevent it from being interpreted as executable code.
Input Validation: Validate user input to ensure it doesn't contain malicious scripts.
Content Security Policy (CSP): Implement a CSP to restrict which sources are allowed to execute scripts on your website.
Sanitize HTML: If your application allows users to input HTML, use robust libraries to sanitize it and remove dangerous tags/attributes.
8. Zero-Day Exploits
The Attack: Exploits that target newly discovered software vulnerabilities for which a patch is not yet available. They are extremely dangerous because there's no immediate defense.
Prevention Techniques:
Layered Security (Defense-in-Depth): Rely on multiple security controls (firewalls, EDR, IDS/IPS, network segmentation) so if one fails, others can still detect or contain the attack.
Behavioral Analysis: Use security tools (like EDR, UEBA) that monitor for anomalous behavior, even if the specific exploit is unknown.
Application Whitelisting: Allow only approved applications to run on your systems, preventing unauthorized or malicious executables.
Rapid Patch Management: While a patch doesn't exist initially, be prepared to deploy it immediately once released.
9. Insider Threats
The Attack: A security breach or data loss caused by a person with authorized access to an organization's systems and data, whether malicious or accidental.
Prevention Techniques:
Principle of Least Privilege (PoLP): Grant users only the minimum access necessary to perform their job functions.
User Behavior Analytics (UBA/UEBA): Monitor user activity for anomalous behaviors (e.g., accessing unusual files, working outside normal hours).
Data Loss Prevention (DLP): Implement DLP solutions to prevent sensitive data from leaving the organization's controlled environment.
Employee Training: Educate employees on security policies, data handling best practices, and recognizing social engineering.
Offboarding Procedures: Have strict procedures for revoking access immediately when an employee leaves.
10. Brute Force & Credential Stuffing
The Attack:
Brute Force: Systematically trying every possible combination of characters until the correct password or encryption key is found.
Credential Stuffing: Using lists of stolen usernames and passwords (from previous breaches) to try and log into accounts on other services.
Prevention Techniques:
Multi-Factor Authentication (MFA): The most effective defense, as attackers need a second factor beyond just the password.
Strong Password Policies: Enforce complex, unique passwords that are difficult to guess.
Account Lockout Mechanisms: Implement policies that temporarily lock accounts after a certain number of failed login attempts.
Rate Limiting: Restrict the number of login attempts from a single IP address over a period.
CAPTCHA Challenges: Introduce CAPTCHAs or other challenge-response mechanisms during login to differentiate humans from bots.
Threat Intelligence: Monitor dark web forums for compromised credentials and prompt affected users to reset their passwords.
By proactively addressing these common attack vectors with a layered and comprehensive security strategy, individuals and organizations can significantly strengthen their defenses and foster a more secure digital environment. Stay informed, stay vigilant, and make cybersecurity a continuous priority.
2 notes
·
View notes
Text
WordPress Security Services Tailored to Your Business Needs
Atcuality understands that every WordPress website has unique security needs. Our specialized WordPress security services provide customized solutions to safeguard your website from malicious attacks, unauthorized access, and technical vulnerabilities. Whether you own a blog, corporate website, or online store, our comprehensive approach includes malware scanning, vulnerability patching, firewall implementation, and site backups. Atcuality’s team of security professionals works tirelessly to monitor and eliminate threats before they can impact your business. With advanced tools and strategies like SSL encryption and uptime monitoring, we ensure your website operates securely while maintaining peak performance. Cyber threats evolve daily, but with Atcuality, you can stay one step ahead. Don’t let your website become a target—secure your site and maintain customer trust with our proven WordPress security solutions.
#seo marketing#seo services#artificial intelligence#digital marketing#iot applications#seo company#seo agency#amazon web services#azure cloud services#ai powered application#ai applications#ai app development#virtual reality#vr development#vr games#wordpress#web developers#web development#web design#web developing company#website developer near me#wordpress development#web hosting#website#augmented and virtual reality market#augmented human c4 621#augmented intelligence#augmented reality#iot#iotsolutions
4 notes
·
View notes
Text
Crypto Scam Recovery: How to Spot, Report, and Recover from Online Frauds
The world of cryptocurrency is booming, offering investors a decentralized and promising way to grow their wealth. But with that growth comes an increasing number of scams targeting unsuspecting users. From fake investment platforms to phishing attacks, online fraud is a real threat. The good news? Victims can take action. In this post, we’ll guide you on how to spot crypto scams, report them, and increase your chances of recovery.

How to Spot a Crypto Scam
Knowing how to recognize the signs of a scam can save you from massive losses. Below are common types of cryptocurrency scams and the red flags to watch out for.
1. Fake Investment Platforms
These websites or apps promise guaranteed returns on crypto investments. They often look professional and mimic real companies, but they operate purely to steal your funds.
Red Flags:
Promises of high, risk-free returns
Urgency to deposit funds quickly
No verifiable company background
2. Phishing Attacks
Scammers send emails, messages, or pop-ups that look like they’re from trusted platforms. These messages trick users into giving away private keys or login credentials.
Red Flags:
Misspelled URLs or suspicious email addresses
Requests for sensitive information
Offers or warnings that seem too good or too urgent
3. Pump and Dump Schemes
Fraudsters hype up a worthless coin to drive demand and inflate prices. Once the price peaks, they dump their holdings, causing massive losses for late investors.
Red Flags:
Unusual hype in online forums or social media
Sudden spike in price without real news or updates
Unverified claims about partnerships or technology
How to Report a Crypto Scam
If you’ve been scammed, it’s essential to report the incident immediately. Doing so not only helps protect others but also increases your chance of recovery.
1. Report to Local Authorities
File a police report or contact your country's cybercrime unit. Include all details—transaction history, wallet addresses, emails, and screenshots.
2. Notify the Exchange
If the scammer used a known exchange to receive your funds, contact that platform’s support team. Many exchanges can freeze the funds if reported in time.
3. Report to Online Watchdogs
Organizations like the Internet Crime Complaint Center (IC3), FTC, or Action Fraud (UK) collect reports to investigate and track online scams.
4. Alert Blockchain Forensics Firms
Specialized companies like Chainalysis or CipherTrace can trace stolen crypto on the blockchain. In many cases, they collaborate with law enforcement and legal teams to initiate recovery.
How to Recover from a Crypto Scam
While recovering lost crypto isn’t easy, it’s not impossible. Here’s a structured plan from crypto recovery experts:
1. Secure All Accounts
Change passwords and enable two-factor authentication on your wallets, exchanges, and email. Run a malware scan on your devices to ensure no backdoors remain.
2. Collect Evidence
Document every aspect of the fraud—wallet addresses, transaction IDs, email conversations, social media links, and screenshots. The more information you gather, the better.
3. Consult a Crypto Recovery Expert
Work with a reputable crypto recovery agency or blockchain forensic specialist. These professionals use tracking software to trace your funds across wallet addresses and exchanges.
Note: Be cautious—scammers also pose as recovery agents. Only trust firms with proven results, legal backing, and strong online presence.
Prevention Tips to Avoid Future Crypto Frauds
Use hardware wallets for secure storage of your crypto assets.
Double-check URLs before entering credentials.
Avoid platforms or individuals promising “guaranteed returns.”
Do your research before investing—verify reviews, company registration, and team transparency.
Final Thoughts
Crypto scams are becoming more sophisticated, but with awareness and the right actions, you can fight back. Spotting red flags early, reporting to the proper authorities, and seeking expert help are key steps toward recovery.
If you or someone you know has fallen victim to a crypto scam recovery, don’t delay. Act fast, gather your data, and reach out to professionals who can help you trace and possibly recover your stolen funds.
3 notes
·
View notes