#Ethical hacking Training
Explore tagged Tumblr posts
Text

Six months of ethical hacking training in the areas of cybersecurity basics, vulnerabilities of network and systems, wireless and web security, and preparation for CEH exams using lab sessions and actual techniques.
#Ethical Hacking#Ethical Hacking Course#Learn Ethical Hacking#Ethical Hacking Training#Ethical Hacking Certification
1 note
·
View note
Text
Top 5 Skills to Promote Your Career in IT
Asquare Technologies is emphasizing some cutting-edge skills for career changers in 2024. Here’s a breakdown of each skill and why it’s important:
1.Analytics: This skill involves gathering, interpreting, and presenting data to make informed business decisions. In today’s data-driven world, companies rely heavily on analytics to understand customer behavior, optimize operations, and drive growth.

Top Job Roles
Data Analyst
Business Analyst
Tableau Developer
PowerBI Developer
Business Intelligence Developer
2. Data Science: Data science goes beyond basic analytics, utilizing advanced algorithms and machine learning techniques to extract insights and predictions from large datasets. With the exponential growth of data, data scientists are in high demand across industries.

Top Job Roles
Machine Learning Engineer
Data Engineer
Database Administrator
Data Analyst
Data Scientist
3. Cloud Computing: Cloud computing has revolutionized the way businesses operate by providing scalable and flexible infrastructure and services. Proficiency in cloud computing platforms like AWS, Azure, or Google Cloud is essential for modern IT professionals.

Top Job Roles
Cloud Engineer
Cloud Administrator
Cloud Developer
DevOps Engineer
Cloud Support Engineer
4. Blockchain: Blockchain technology, known for its security and transparency, is disrupting various sectors, including finance, supply chain, and healthcare. Understanding blockchain principles and their applications can open up new career opportunities in emerging industries.

Top Job Roles
Blockchain Developer
Blockchain Engineer
Blockchain Analyst
Blockchain Project Manager
Law
5. UX Design: User Experience (UX) design focuses on creating intuitive and engaging digital experiences for users. As more businesses shift online and prioritize customer satisfaction, UX designers play a crucial role in product development and innovation.

Top Job Roles
UX Designer
UX Engineer
Software Testing
UX Writer
Interaction design
Information Architecture
By mastering these skills, you’ll be well-equipped to navigate the rapidly evolving job market and pursue exciting career opportunities in technology and beyond.
#business analytics#cybersecurity#business analytics course in kochi#data analytics#data science#data analytics training#data science course#data analytics course#data analytics course in kochi#business analytics course#ethical hacking training
0 notes
Text
Cybersecurity Education: Your Path to Becoming a Digital Guardian in an Ever-Changing Landscape
In an era dominated by digital technologies, the importance of cybersecurity has never been greater. As cyber dangers and attacks proliferate, the requirement for qualified professionals capable of protecting against them grows. In this article, we look at how cybersecurity education can help individuals become digital guardians in an ever-changing landscape of cyber threats.
The Growing Importance of Cybersecurity:
With the fast proliferation of digital infrastructure and the increasing interconnection of systems, potential vulnerabilities and dangers have grown dramatically. Organizations in all industries confront ongoing risks to their digital assets, ranging from large-scale data breaches to sophisticated ransomware assaults. As a result, there is an urgent demand for skilled cybersecurity specialists who can predict, detect, and successfully neutralize these risks.
Cybersecurity Education: Laying the Groundwork:
Cybersecurity education sets the framework for individuals to obtain the skills and knowledge required to address the wide range of difficulties provided by cyber attacks. Students learn about basic concepts like network security, cryptography, threat analysis, and incident response through comprehensive training programmes. Furthermore, they learn about emerging technologies and dynamic attack vectors, which prepares them to respond to changing threat landscapes.
Practical Experience and Hands-on Learning:
One of the distinguishing features of cybersecurity education is the emphasis on practical experience and hands-on learning. Students can use their theoretical understanding in real-world circumstances by modeling cyber attacks and defense techniques in controlled conditions. By participating in practical exercises including penetration testing, vulnerability assessments, and forensic analysis, students gain vital skills that may be applied directly to industry.
Specialization and certification:
Cybersecurity education provides a wide number of specialization options, allowing students to personalize their learning experience to their specific interests and professional aspirations. Whether they specialize in network security, cloud security, ethical hacking, or digital forensics, students can pursue certificates and qualifications that confirm their cybersecurity skills. These qualifications not only boost credibility, but they also strengthen employment prospects in a competitive labor environment.
Addressing the skill gap:
Despite the increasing demand for cybersecurity workers, there is a major skills gap in the business. Individuals who invest in cybersecurity education not only position themselves for profitable career prospects, but they also help to close the essential skills gap. Cybersecurity experts play an important role in boosting organizations' overall security posture and protecting digital assets from changing threats by engaging in continuous learning and professional development.
Conclusion:
In conclusion, cybersecurity education is the foundation for those seeking to become digital guardians in an ever-changing landscape of cyber threats. Students who get the necessary information, skills, and certifications can pursue rewarding jobs in cybersecurity, where they play an important role in defending against malicious actors and protecting the integrity of digital systems. As technology advances, the demand for qualified cybersecurity experts will grow, making cybersecurity education more important than ever.
Join the CACMS Institute for comprehensive cybersecurity education today. Receive hands-on practical instruction and guidance from our seasoned experts. Take the first step towards becoming a digital guardian in the ever-changing world of cyber threats.
For further information and to enroll, please call +91 8288040281 or visit CACMS!
Secure your future in cybersecurity with CACMS Institute.
#cacms institute#cacms#techeducation#techskills#digital landscape#ethical hacking course#ethical hacking training#ethical hacking course in Amritsar#ethical hacking certification#Cybersecurity education#cybersecurity course in amritsar
0 notes
Text
Certification Exam Center | PMP CISA CISM Oracle CCNA AWS GCP Azure ITIL Salesforce Institute in Pune

The Certification Exam Center in Pune offers a range of certification exams for professionals in the IT industry. These certifications are highly valued and recognized worldwide, and passing them can significantly enhance one's career prospects. The center offers exams for a variety of certifications, including PMP, CISA, CISM, Oracle, CCNA, AWS, GCP, Azure, ITIL, and Salesforce Institute. The center provides a convenient and comfortable environment for taking the exams. It has state-of-the-art facilities and equipment to ensure that candidates have a smooth and hassle-free experience during the exam. The exam rooms are spacious and well-lit, with comfortable seating arrangements and noise-cancelling headphones to help candidates.
Visit: https://www.certificationscenter.com/top-certifications
Address: SR N 48, OFFICE NUMBER 009 1ST FLOOR, EXAM CENTER, CERTIFICATION, Lane No. 4, Sai Nagari, Mathura Nagar, Wadgaon Sheri, Pune, Maharashtra 411014
Business Phone: 91020 02147
Business Category: Software Training Institute
Business Hours: 8am-8pm Monday to Sunday
Business Email: [email protected]
Payment Method: Paypal, Local Bank Wire Transfer
Social links:
https://www.facebook.com/certificationscenter
https://twitter.com/cert_center
https://www.youtube.com/@certificationcenter
https://www.linkedin.com/company/it-certification-exam-and-preparation-center
#Linux Training#Aws Training#Cyber security Training#Ethical Hacking Training#RHLS Cost#DevOps Training#Azure Training#RHCSA Training#OpenShift Training#Networking Training#CCNA Training#CEH Training#GCP Training#Cloud Security Training#OSCP Training
1 note
·
View note
Text

#eduvatech#online study#online cyber security in noida#cybersecurity#ethicalhacking#ethical hacking training
0 notes
Text
Enumeration in Ethical Hacking: Unveiling Vulnerabilities Through Systematic Exploration
In the realm of ethical hacking, enumeration plays a crucial role as a systematic process of gathering information about a target system. This phase involves actively probing and analyzing various resources to identify vulnerabilities, potential entry points, and gain an overall understanding of the system architecture.

Let’s explore the way for a successful path in hacking. So, buckle up and get ready for an adventure into the world of ethical hacking from the Best ethical hacking Training Institute in Bangalore
Understanding Enumeration in Ethical Hacking: Enumeration is a pivotal phase in the information gathering stage of an ethical hacking engagement. It entails actively collecting data about a target system, including IP addresses, network services, user accounts, shared resources, and system configurations.
By conducting enumeration, ethical hackers aim to gain a comprehensive understanding of the target environment, which assists in identifying potential weaknesses and formulating an effective penetration testing strategy.
The Importance of Enumeration:
Vulnerability Identification: Enumeration aids in identifying potential vulnerabilities within a system or network. By gathering information about running services, open ports, and user accounts, ethical hackers can pinpoint weak points that can be exploited during subsequent stages of an engagement.
Attack Surface Analysis: Enumeration helps security professionals map out the attack surface of a target system. This knowledge assists in understanding the system’s structure, identifying potential entry points, and determining how an attacker may navigate through the network.
Privilege Escalation: Enumeration techniques can expose privileged user accounts, misconfigured access controls, and weak passwords. This information allows ethical hackers to exploit these weaknesses and escalate their privileges within the system, simulating real-world threat scenarios.

Port Scanning: Port scanning involves sending network packets to target systems to identify open ports and services. Tools like Nmap and Masscan are commonly used to perform port scanning and provide information about running services, version numbers, and potential vulnerabilities associated with specific services.
Service Identification: Once open ports are discovered, ethical hackers employ techniques to identify the services running on those ports. They analyze service banners, perform service fingerprinting, and use tools like Banner Grabbing to gather information about the services and their versions.
User Enumeration: User enumeration involves identifying valid user accounts or system usernames. Techniques like brute-forcing, querying system directories, or using specialized tools like enum4linux for Windows systems can aid in user enumeration.
Network Mapping and Discovery: Ethical hackers use tools like Nmap and automated network mapping techniques to discover network topology, identify connected devices, and gather information about routers, firewalls, and other network infrastructure components.
Web Application Enumeration: For web applications, enumeration techniques involve identifying directories, files, and server configurations that may reveal valuable information. Tools like DirBuster, Nikto, and Burp Suite can be used to perform web application enumeration.
Enumeration serves as a critical phase in ethical hacking, enabling security professionals to gather valuable information about a target system or network. By systematically exploring services, open ports, user accounts, and system configurations, ethical hackers can identify vulnerabilities, potential entry points, and weaknesses to be addressed during penetration testing.
Enumeration plays a pivotal role in the identification and mitigation of security risks, reinforcing the overall resilience of systems and networks in the face of potential threats.
If you’re keen on ethical hacking, consider enrolling in an Ethical Hacking course in Bangalore. They often provide certifications, mentorship, and job placement opportunities to support your learning journey.
0 notes
Text

#ethical hacking course#ethical hacking courses#ethical hacking institute#ethical hacking online institute#ethical hacking training#best ethical hacking#ethical hacking job#ethical hacking services#ethical hacking course in delhi#ethical hacking courses in delhi#best ethical hacking institute in delhi#ethical hacking institute in delhi#job based ethical hacking training in delhi#ethical hacking course in rohini
0 notes
Text
Guide to a Successful Career Path in Cyber Security
In our hyper-connected digital world, the demand for skilled cyber security professionals is higher than ever. As technology continues to advance, so do the threats to our digital infrastructure. If you’re considering a career in cyber security or are already on this exciting journey, this guide will help you navigate the complex landscape and carve out a successful career path in Cybersecurity and Ethical Hacking.
Your journey into the world of ethical hacking starts with a blend of education, skills, and a passion for ethical cybersecurity. This guide, tailored for admission into ethical hacking, will help you unlock the potential for an exciting and impactful career. Embrace curiosity, stay committed to learning, and embark on a journey to secure the digital world ethically.
India faces a growing threat from cyber attacks, with a rise in incidents targeting key sectors like finance, healthcare, and government institutions. The nation’s increasing digital reliance and a surge in internet users make it an attractive target for various cyber threats, including ransomware and phishing scams. To counter these challenges, the Indian government is working on enhancing its cybersecurity measures through initiatives such as the National Cyber Security Policy, emphasizing the need for awareness, collaboration, and technological investments.
Recent Cyber-attack in India
BSNL DATA BREACH:
State-owned telecom operator Bharat Sanchar Nigam Ltd (BSNL) has allegedly suffered a data breach including sensitive details of fiber and landline users of BSNL. The compromised data include email addresses, billing details, contact numbers. The breach, involving sensitive information not only compromises the privacy of the users but also places them at risk of identity theft, financial fraud, and targeted phishing attacks.
The hacker claims that the number of rows of data to be around 2.9 million, which indicates a high probability that it is a single website that may have been breached. The sample data structure available on the dark web points to possible exploitation of a SQL (Structured Query Language) Injection vulnerability.
SQL injection, also known as SQLI, is a common attack vector that uses malicious SQL code for backend database manipulation to access information that was not intended to be displayed. This information may include any number of items, including sensitive company data, user lists, and private customer details.
To secure ourselves and our nation from these kinds of cyber attacks, learn cybersecurity and become a hero.
What is Cyber security and Ethical Hacking?
Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. These cyberattacks are usually aimed at accessing, changing, or destroying sensitive information; extorting money from users via ransomware; or interrupting normal business processes.
Key components of cybersecurity include:
Network Security: Protecting computer networks from unauthorized access and cyber-attacks through the implementation of firewalls, intrusion detection systems, and other security measures.
Information Security: Safeguarding sensitive information and data to prevent unauthorized access, disclosure, alteration, or destruction.
Endpoint Security: Securing individual devices such as computers, laptops, and mobile devices from malware, ransomware, and other threats.
Cloud Security: Ensuring the security of data and applications stored in cloud environments, including data encryption, access controls, and secure configurations.
Incident Response: Developing and implementing plans to respond effectively to cybersecurity incidents, minimizing the impact and facilitating recovery.
Security Awareness Training: Educating users and employees about cybersecurity best practices to reduce the risk of human-related vulnerabilities, such as social engineering attacks.
Ethical hacking involves an authorized attempt to gain unauthorized access to a computer system, application, or data. Carrying out an ethical hack involves duplicating strategies and actions of malicious attackers.
Key aspects of ethical hacking include:
Penetration Testing: Conducting controlled simulated cyber attacks to assess the security of systems, identify vulnerabilities, and provide recommendations for improvement.
Vulnerability Assessment: Evaluating systems for weaknesses, misconfigurations, or other security issues that could be exploited by malicious actors.
Security Auditing: Examining the security controls, policies, and procedures of an organization to ensure they align with best practices and compliance standards.
Red Team vs. Blue Team Exercises: Red teaming involves simulating a real-world attack to test the organization’s defenses, while blue teaming involves defending against simulated attacks and improving security measures.
Reporting and Recommendations: Ethical hackers provide detailed reports of vulnerabilities and weaknesses, along with recommendations for mitigating risks and enhancing overall cybersecurity posture.
Different Types of Cyber Attacks
Malware:
Description: Malicious software designed to disrupt, damage, or gain unauthorized access to computer systems. Examples: Viruses, worms, trojans, ransomware, spyware.
Phishing:
Description: Deceptive attempts to trick individuals into revealing sensitive information, often through fake emails or websites. Examples: Email phishing, spear phishing, vishing (voice phishing), smishing (SMS phishing).
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS):
Description: Overloading a system, network, or service to make it unavailable to users. Examples: Flooding a website with traffic, using botnets to amplify the attack.
Man-in-the-Middle (MitM):
Description: Intercepting and potentially altering communication between two parties without their knowledge. Examples: Eavesdropping on Wi-Fi communications, session hijacking, DNS spoofing.
SQL Injection:
Description: Exploiting vulnerabilities in web applications by injecting malicious SQL code, often to gain unauthorized access to a database. Example: Modifying SQL queries in input fields to manipulate database responses.
Cross-Site Scripting (XSS):
Description: Injecting malicious scripts into websites, which are then executed by users’ browsers. Example: Embedding scripts in input fields that are executed when other users view the affected web page.
Cross-Site Request Forgery (CSRF):
Description: Forcing users to perform unintended actions on a web application in which they are authenticated. Example: Tricking a user into clicking a link that performs an action (e.g., changing their password) without their consent.
Zero-Day Exploits:
Description: Targeting vulnerabilities in software or hardware that are not yet known to the vendor or have no available patches. Example: Exploiting a recently discovered flaw before a fix is developed.
Ransomware:
Description: Encrypting files or systems and demanding payment (usually in cryptocurrency) for their release. Example: WannaCry, NotPetya, CryptoLocker.
Social Engineering:
Description: Manipulating individuals into divulging confidential information or performing actions that may compromise security. Examples: Impersonation, pretexting, baiting, quid pro quo.
IoT-Based Attacks:
Description: Exploiting vulnerabilities in Internet of Things (IoT) devices to gain unauthorized access or launch attacks. Example: Taking control of smart home devices, using IoT devices for DDoS attacks.
Password Attacks:
Description: Attempts to obtain passwords through various methods, such as brute force attacks, credential stuffing, or password spraying. Examples: Dictionary attacks, rainbow table attacks, credential stuffing.
These are just a few examples of the many cyber threats and attack vectors that individuals and organizations face.
Importance of Cyber Security
Cybersecurity is crucial in safeguarding individuals, organizations, and nations against a myriad of digital threats. It plays a pivotal role in protecting sensitive data, financial assets, and critical infrastructure from unauthorized access, data breaches, and cyber attacks. As our dependence on digital technologies continues to grow, the importance of cybersecurity becomes paramount in ensuring the integrity, confidentiality, and availability of information, ultimately preserving trust in online systems and fostering a secure digital environment.
Why Choose Cybersecurity as a Career?
High Demand for Experts: The demand for cybersecurity professionals is soaring globally. Organizations across industries are actively seeking individuals with the skills to safeguard their digital assets from cyber threats.
Diverse Career Opportunities: Cybersecurity is not a one-size-fits-all field. With specializations ranging from ethical hacking and penetration testing to incident response and security analysis, there’s a niche for every interest.
Impactful Work: As a cybersecurity professional, you play a crucial role in securing sensitive information, ensuring data integrity, and safeguarding individuals and organizations from the devastating consequences of cyber attacks.
Jobs for Ethical hacker and Cyber Security Professionals
Information Security Analyst:
Responsibilities: Monitor an organization’s networks for security breaches, analyze security measures, and implement solutions to protect sensitive information.
Skills: Network security, vulnerability assessment, incident response.
Penetration Tester (Ethical Hacker):
Responsibilities: Conduct controlled cyber attacks to identify vulnerabilities in systems, networks, or applications, and provide recommendations to strengthen security.
Skills: Penetration testing, vulnerability assessment, ethical hacking.
Security Consultant:
Responsibilities: Advise organizations on their overall security posture, conduct risk assessments, and recommend strategies to improve security.
Skills: Security consulting, risk management, policy development.
Security Engineer:
Responsibilities: Design and implement security solutions, configure firewalls, and monitor for security threats.
Skills: Network security, security architecture, firewall management.
Incident Responder:
Responsibilities: Investigate and respond to security incidents, analyze breaches, and implement measures to prevent future incidents.
Skills: Incident response, forensics, threat intelligence.
Security Analyst (SOC Analyst):
Responsibilities: Work in a Security Operations Center (SOC) to monitor security alerts, analyze data, and respond to potential security incidents.
Skills: Security monitoring, log analysis, threat detection.
Security Administrator:
Responsibilities: Manage and configure security tools, enforce security policies, and ensure the integrity of IT systems.
Skills: Security administration, access control, identity management.
Cybersecurity Manager/Director:
Responsibilities: Oversee an organization’s overall cybersecurity strategy, manage security teams, and ensure compliance with industry regulations.
Skills: Leadership, strategic planning, risk management.
Cryptographer:
Responsibilities: Develop and implement cryptographic solutions to secure data and communications.
Skills: Cryptography, encryption algorithms, key management.
Security Software Developer:
Responsibilities: Develop secure software applications, identify and fix vulnerabilities in code, and contribute to the creation of secure software products.
Skills: Secure coding practices, software development, code analysis.
Threat Intelligence Analyst:
Responsibilities: Collect and analyze threat intelligence data to identify potential cyber threats, assess risks, and provide proactive measures.
Skills: Threat intelligence, analysis, risk assessment.
Security Trainer/Educator:
Responsibilities: Educate individuals or organizations on cybersecurity best practices, conduct training sessions, and develop educational materials.
Skills: Training, communication, cybersecurity knowledge.
Why Choose Our Institution?
Cutting-Edge Curriculum: Our cybersecurity program is designed to provide a comprehensive understanding of the latest threats and defenses. The curriculum is regularly updated to align with industry standards.
Hands-On Training: Gain practical experience through hands-on training, simulations, and access to state-of-the-art cybersecurity labs. We believe in equipping our students with the skills needed to tackle real-world scenarios.
Industry Connections: Our institution maintains strong ties with industry leaders, offering students opportunities for internships, networking, and exposure to the latest trends in cybersecurity.
Admissions Open – Secure Your Future !
Now is the time to take a step towards a dynamic and rewarding career in cybersecurity. With the digital landscape constantly evolving, the need for skilled professionals is greater than ever. Don’t miss the chance to join our institution and become a guardian of the digital realm.
OUR COURSE DETAILS
DURATION 5 MONTHS (4 Months Training +1 Month Internship)
Contents:
Introduction to Cyber Security
IT System Infrastructure
Linux
Network Security
Offensive Security
EC-COUNCIL V12 Modules.
Internship in VAPT (Vulnerability assessment and Penetration testing)
0 notes
Text
Cybersecurity: The Key to Protecting Your Digital Identity and Privacy
In an era where our lives are increasingly connected with the digital sphere, protecting our digital identity and privacy has become critical. With the exponential growth of online activities, from social media interactions to financial transactions, the risks of cyber attacks are greater than ever before. In this digital age, cybersecurity has emerged as the primary shield protecting our digital life.
Understanding The Threat Landscape
Cyber risks take many forms, including data breaches, identity theft, malware, and phishing attempts. These dangers jeopardize sensitive personal information while also undermining trust in online systems and services. As technology advances, so do fraudsters' strategies, making it critical for individuals to be cautious and knowledgeable about cybersecurity best practices.
Significance of Digital Identity Protection
Our digital identities contain a variety of data, including personal information, financial records, and online behaviors. Securing this information is critical not only to prevent identity theft, but also to maintain our reputation and reliability in the digital sphere. A compromise of our digital identity can have serious ramifications for our financial stability, professional chances, and even our personal relationships.
Preserving Privacy in the Digital Age
Privacy is the foundation of individual freedom and liberty. However, in today's hyper-connected society, keeping privacy has grown more difficult. From surveillance technologies to data mining tactics, our online activities leave digital trails that dangerous actors can exploit. Cybersecurity measures are critical in protecting our privacy rights by ensuring that our personal information stays safe and protected from unauthorized access.
Empowering Individuals with Cybersecurity Education
While cybersecurity dangers may appear frightening, individuals may empower themselves by learning and developing cybersecurity skills. Education is an excellent technique for combating cyber threats because it teaches people how to detect possible risks, minimize vulnerabilities, and respond effectively to security crises. Individuals who invest in cybersecurity education improve not only their own digital safety but also the broader resilience of cyberspace.
Conclusion
In an increasingly linked world, cybersecurity is the foundation of our digital security and privacy. Individuals who recognise the importance of preserving their digital identity and privacy can take proactive efforts to reduce cyber risks and protect themselves from online dangers. We can create a safer and more secure digital future for ourselves and future generations by promoting cybersecurity education, awareness, and adherence to best practices.
Remember that in the digital world, cybersecurity is no longer an option—it is a requirement. Let's work together to protect our digital identities and privacy rights in an ever-changing online world.
Ready to take charge of your digital security? Join CACMS Institute today for comprehensive cybersecurity training that will provide you with hands-on practical skills and professional assistance.
Enroll in our Cyber Security Course in Amritsar and obtain the knowledge and competence required to properly protect your digital identity and privacy. Our professional teaching staff ensures that you receive a high-quality education and personalized attention throughout your learning journey.
Protect yourself online before it's too late. Contact us at +91 8288040281 or visit cacms.in to learn more about our Cyber Security Course in Amritsar and begin your path to a secure digital future now.
#cacms institute#cacms#techskills#techeducation#cyber security course in amritsar#cyber security#data privacy#digital identity#protecting digital Identity#ethical hacking course#ethical hacking training#ethical hacking certification#best computer institute in amritsar
0 notes
Text
The Role of Ethical Hacking in Preventing Cyberattacks
As cyberthreats change, ethical hacking has become essential to thorough security measures in many businesses. Through bug bounty programs, companies such as Google and Facebook aggressively use ethical hackers to find vulnerabilities in their systems. The proactive approach of ethical hacking promotes a security-conscious culture within businesses and helps avoid expensive data breaches. To safeguard sensitive data, ethical hackers continuously evaluate and enhance security protocols in our Ethical Hacking Course in Bangalore.

What Ethical Hacking Means
"Ethical hacking" refers to techniques that are permissible for identifying vulnerabilities in systems, networks, and applications. In the late 1990s, this discipline began to gain traction as companies realized they needed to implement proactive security measures. By employing the same methods as authorized hostile hackers, ethical hackers also referred to as "white-hat" hackers improve security.
Ethical hacking has a promising future. Ethical hackers will use increasingly sophisticated techniques to identify vulnerabilities as AI and machine learning proliferate. As cyberthreats continue to rise, it will become increasingly important for businesses to hire ethical hackers who can stop these attacks.
The benefits of ethical hacking in cybersecurity
1. Evaluating the Present Dangers
System vulnerabilities are found via ethical hacking before malevolent hackers may take use of them. The likelihood of expensive data breaches is greatly decreased by this proactive strategy. By fixing vulnerabilities with penetration testing tools like Metasploit or Burp Suite, businesses can save a significant amount of money.
2. Better Security Posture
Regular ethical hacking assessments strengthen a company's overall security posture. With the assistance of knowledgeable ethical hackers, organizations can conduct red team exercises that mimic real attacks. Organizations can increase their resistance to changing cyberthreats by routinely testing and fortifying security measures. Effective protections against such threats are maintained by this ongoing upgrade.
3. Respect for the law
Businesses can utilize ethical hacking to comply with regulations like GDPR and HIPAA. Businesses may stay out of trouble and safeguard their reputation by adhering to these rules. Compliance demonstrates a commitment to protecting confidential data and maintaining customer trust. Our Software Training Institute needs ethical hacking testing on a regular basis to find security vulnerabilities and guarantee compliance.
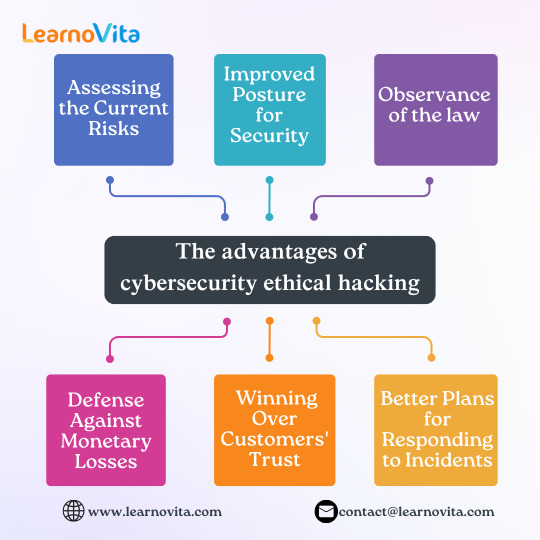
4. Protection Against Financial Losses
Data breaches can cost organizations millions of dollars in lost revenue and recovery expenses. Ethical hacking raises awareness of vulnerabilities by identifying and fixing them before attackers may exploit them. This preventive measure ultimately protects the organization's financial stability.
5. Gaining the Trust of Customers
Customer loyalty and trust are increased when ethical hacking is used to demonstrate a commitment to cybersecurity. Customers are more likely to engage with businesses who secure their data proactively. Regular security audits must be encouraged in order to reassure clients that their data is safe. Building a reputation for reliability and accountability also includes managing sensitive data.
6. Improved Incident Response Plans
Ethical hacking allows companies to assess their incident response plans by mimicking real attacks. This practice helps identify weaknesses in reaction strategy. It also assists businesses in strengthening their processes to make them more resilient to threats.
Conclusion
The role that ethical hackers play in protecting digital assets cannot be overstated. The cyber security network that strengthens an organization's cyber security policies and creates new ways to improve them depends on them. If you want to be sure that you will have a lot of possibilities after you graduate, you must earn this degree from an accredited university. There are currently several different cyber security certification programs available. However, nothing compares to a degree program for expanding your knowledge and skill set. Do the necessary research and pick a school that can provide you with thorough cyber security training. The future is bright for professionals who possess the necessary education and experience in this field.
1 note
·
View note
Text

“To beat a hacker, think like one” Ethical hacker Not leaves behind any evidence that they were there. Ethical hackers earn ₹3,18,370 and above per month. We prepare for (CEH), (OSCP), (and CPT) Certification for newbies to professionals. Get hold of us today.
Contact us: +91 9315519124 / +91 8287266809 Email: [email protected] Website: https://www.eduvatech.com/
#learningopportunity#studynoida#learning #learningindias
#online cyber security in noida#online ethical hacker training#eduvatech#ethicalhacking#online courses#online training#ethical hacking certification#ethical hacking course#ethical hacking training#online study adcademy#online study
0 notes
Text
#ethical hacking course in delhi#ethical hacking courses in delhi#best ethical hacking institute in delhi#ethical hacking institute in delhi#job based ethical hacking training in delhi#ethical hacking course in rohini#ethical hacking course#ethical hacking courses#ethical hacking institute#ethical hacking online institute#ethical hacking training#best ethical hacking#ethical hacking job#ethical hacking services#SoundCloud
1 note
·
View note
Text
Cyber Security Course in Jaipur

Join the top-rated Cyber Security Course in Jaipur at Cyber Crime Awareness Society. Learn from certified experts and gain hands-on experience in network security, ethical hacking, and cybercrime prevention. Ideal for students and professionals aiming to build a secure tech career. Enroll now! Call +91 97842 68547 to start your cybersecurity training today.
0 notes
Text
The Contribution of Ethical Hackers to Cybersecurity
The Role of Ethical Hackers in Cybersecurity
In today’s digital age, cybersecurity has become a critical concern for organizations worldwide. With increasing threats and sophisticated cyber-attacks, the need for skilled professionals to safeguard information systems has never been greater. Ethical hackers, also known as penetration testers or white-hat hackers, play a crucial role in this domain. This blog explores the role of ethical hackers in cybersecurity, outlining their responsibilities, the skills required, and how they can be prepared through appropriate training and certification.
Understanding the Role of Ethical Hackers
Ethical hackers are cybersecurity experts who simulate attacks on systems to identify vulnerabilities and weaknesses before malicious hackers can exploit them. They are employed by organizations to conduct comprehensive security assessments, ensuring that their IT infrastructure is robust and secure. By uncovering potential threats and recommending improvements, ethical hackers help in fortifying defenses against cyber-attacks.
Their role involves not only identifying security flaws but also understanding how these flaws can be exploited. This requires a deep knowledge of various attack vectors, cybersecurity tools, and best practices. Ethical hackers use their skills to test and verify the effectiveness of an organization’s security measures.
The Path to Becoming an Ethical Hacker
To embark on a career in ethical hacking, it is essential to receive proper training and certification. Many professionals start by enrolling in an ethical hacking course with job assistance. These courses provide foundational knowledge and practical skills needed to excel in the field. Opting for training from a top ethical hacking institute ensures that you receive high-quality education from experienced instructors.
Training programs often include hands-on labs and real-world scenarios that help build practical skills. Such experiences are invaluable for understanding the intricacies of ethical hacking and preparing for real-life challenges. Furthermore, enrolling in an ethical hacking training institute with a strong reputation can provide better networking opportunities and career support.
The Importance of Certification
Certification is a critical step in establishing credibility and demonstrating expertise in ethical hacking. Obtaining an ethical hacking certification validates your skills and knowledge, making you more competitive in the job market. Certifications such as the Certified Ethical Hacker (CEH) and Offensive Security Certified Professional (OSCP) are widely recognized and respected in the industry.
Many candidates prepare for certification exams through courses offered by top ethical hacking institutes. These courses are designed to cover the material required for certification and often include practice exams to help gauge readiness. While the ethical hacking fee for these programs can vary, investing in a reputable certification is worth the cost for the potential career benefits it brings.
Biggest Cyber Attacks in the World
youtube
The Skills and Tools of Ethical Hackers
Ethical hackers need a diverse set of skills and tools to perform their job effectively. Key skills include knowledge of network protocols, operating systems, and programming languages. They must be adept at using various cybersecurity tools and techniques to conduct penetration testing and vulnerability assessments.
Practical experience gained from ethical hacking training institutes and real-world projects is crucial. Ethical hackers often use tools like Nmap, Metasploit, and Burp Suite to identify and exploit vulnerabilities. Understanding how to use these tools effectively is essential for conducting thorough security assessments.
The Impact of Ethical Hacking on Organizations
Organizations benefit significantly from the expertise of ethical hackers. By identifying and addressing security weaknesses, they can prevent data breaches and cyber-attacks that could otherwise result in substantial financial and reputational damage. Ethical hackers help organizations to comply with regulatory requirements and industry standards, ensuring that their security practices are up-to-date and effective.
Moreover, ethical hacking contributes to the overall improvement of cybersecurity practices. By simulating attacks and providing actionable recommendations, ethical hackers help organizations to strengthen their defenses and enhance their security posture.
Career Prospects and Opportunities
The demand for ethical hackers is on the rise, and career opportunities in this field are diverse. Ethical hackers can work in various sectors, including finance, healthcare, government, and technology. Many organizations seek to employ ethical hackers full-time or contract them for specific projects.
Career advancement in ethical hacking often involves gaining additional certifications and specialized knowledge. Continuing education through ethical hacking training institutes and staying updated with the latest cybersecurity trends and techniques can help professionals advance their careers. Networking with industry peers and participating in cybersecurity conferences can also open doors to new opportunities.
Ethical hackers play a vital role in safeguarding digital assets and enhancing cybersecurity. By identifying vulnerabilities and providing actionable insights, they help organizations protect themselves from cyber threats. Pursuing education and certification through reputable ethical hacking institutes can provide the necessary skills and credentials to succeed in this field. Despite the ethical hacking fee associated with training and certification, the investment is worthwhile for the career benefits and opportunities it offers.
As the digital landscape continues to evolve, the role of ethical hackers will remain critical in defending against emerging threats. For those interested in a career in cybersecurity, ethical hacking offers a rewarding and impactful profession with numerous opportunities for growth and advancement.
0 notes
Text

Join Kochi’s trusted institute for a certified cybersecurity course. Learn from pros and get industry-ready.
1 note
·
View note
Text

CEH v13: Outsmart Hackers by Securing the Human Layer
Some of the most dangerous cyberattacks start with people, not code. CEH v13 exposes social engineering tactics and psychological tricks used by attackers—because cybersecurity means defending minds as well as machines.
Visit: https://www.eccouncil.org/
0 notes