#Kaspersky Support antivirus support number
Explore tagged Tumblr posts
Text
Kaspersky Total Security 2021 (1 Device, 1 Year)
Kaspersky Total Security 2021 is designed to safeguard your PC, data, and personal information from modern and evolving cyber threats. Building on the foundation of Kaspersky’s renowned antivirus engine, Total Security adds multi-layered protection features, including parental controls, a secure browser for online transactions, and data encryption. According to TechRadar’s 2021 review, Kaspersky aims to deliver a complete security environment that’s practical for everyday users seeking more than just basic antivirus coverage. Licensing & Subscriptions a. 1-Year License Coverage • The 1-year license typically covers a set number of devices (often 1, 3, or 5—check the package details). While Kaspersky’s official site and authorized retailers both sell licenses, some consumers find promotions via Amazon or other online stores. However, user forums mention purchasing from reputable sources is important to ensure Kaspersky’s support is honored. b. Renewals & Upgrades • After the initial one-year subscription ends, you can renew or choose a different Kaspersky product—such as Kaspersky Plus or Kaspersky Premium, based on newer naming conventions. • If you have Kaspersky Internet Security, upgrading to Total Security requires a new activation code. License days from different product tiers do not usually combine, meaning you start fresh with the new subscription. Kaspersky Total Security 2021 presents a holistic security suite aimed at users who need more than a basic antivirus. From safeguarding your finances with Safe Money to keeping your children safer online with Safe Kids, the suite bundles a variety of privacy and security-enhancing features under one subscription. If you’re comfortable with a slightly higher price tag, Kaspersky Total Security can provide excellent all-around protection—backed by consistently positive performance in independent lab tests.
0 notes
Text
do i keep antivirus with vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i keep antivirus with vpn
Antivirus software
Antivirus software is a crucial tool for protecting your computer against malicious software, viruses, malware, and other cyber threats. These programs are designed to detect, prevent, and remove malicious software from your device, keeping your data and personal information safe from potential cyber attacks.
There are various types of antivirus software available in the market, ranging from free basic versions to more advanced paid subscriptions. Some popular antivirus software providers include Norton, McAfee, Avast, Kaspersky, and Bitdefender.
The primary function of antivirus software is to scan your computer regularly for any suspicious files or programs that may harm your system. It actively monitors your device's activity, looking for signs of malware and other threats. Once a threat is detected, the software will quarantine or remove the malicious file to prevent any further damage.
Antivirus software also offers real-time protection, scanning files as you access them to ensure they are safe. Additionally, many antivirus programs come with features such as firewall protection, email scanning, and web protection to further enhance your device's security.
It is essential to keep your antivirus software up to date to ensure it is effective against the latest threats. Regularly update the software and run scans to maintain optimal protection for your computer.
Overall, investing in reliable antivirus software is a critical step in safeguarding your digital life and ensuring your online activities are secure. By choosing the right antivirus program and practicing safe browsing habits, you can significantly reduce the risk of falling victim to cyber threats.
VPN service
A VPN service, which stands for Virtual Private Network, is an essential tool for ensuring online privacy and security. Whether you are browsing the internet, accessing public Wi-Fi networks, or simply looking to secure your online activities, a VPN service is designed to protect your data and identity from prying eyes.
By using a VPN service, your internet traffic is encrypted and routed through a secure server, masking your IP address and making it difficult for hackers, advertisers, or even your Internet Service Provider to track your online activities. This encryption helps to keep your personal information, such as passwords, credit card details, and browsing history, safe from potential threats.
Not only does a VPN service offer security benefits, but it also allows you to access geo-restricted content by changing your virtual location. This means you can enjoy streaming services, websites, and content that may be blocked in your region.
When choosing a VPN service, it's important to consider factors such as connection speed, server locations, data encryption protocols, and privacy policy. Look for a reputable provider that offers a user-friendly interface and reliable customer support.
In conclusion, a VPN service is a valuable tool for safeguarding your online privacy and security. Whether you are a frequent traveler, remote worker, or simply conscious of protecting your digital footprint, investing in a quality VPN service can offer peace of mind and enhanced online freedom.
Cybersecurity tools
Cybersecurity tools are essential in safeguarding our online activities and data from potential cyber threats and attacks. These tools are designed to provide protection against various cyber risks and vulnerabilities that can compromise our sensitive information and personal details. With the increasing number and sophistication of cyber threats in today's digital world, utilizing cybersecurity tools has become more crucial than ever.
One of the commonly used cybersecurity tools is antivirus software, which helps detect and remove malware, viruses, and other malicious programs from our devices. Firewalls are another important tool that acts as a barrier between a trusted network and external networks to prevent unauthorized access and cyber attacks. Encryption tools are also vital in protecting data by converting it into a code that can only be accessed by authorized users.
In addition to these basic tools, there are more advanced cybersecurity solutions available today. Intrusion detection systems monitor network traffic for suspicious activities, while penetration testing tools help identify potential vulnerabilities in systems and applications. Security information and event management (SIEM) tools provide real-time analysis of security alerts and log data to help organizations respond to security incidents promptly.
By utilizing a combination of these cybersecurity tools, individuals and organizations can enhance their security posture and minimize the risks of falling victim to cyber attacks. It is important to stay updated with the latest cybersecurity tools and technologies to effectively protect against evolving cyber threats and ensure online safety and privacy.
Malware protection
Title: Safeguard Your Digital World: The Importance of Malware Protection
In today's interconnected digital landscape, the threat of malware looms large, posing significant risks to individuals and businesses alike. Malicious software, or malware, encompasses a variety of harmful programs designed to infiltrate, disrupt, or damage computer systems and networks. From viruses and worms to ransomware and spyware, the range of malware threats continues to evolve, becoming more sophisticated and pervasive with each passing day.
Effective malware protection is essential for safeguarding sensitive data, preserving system integrity, and maintaining productivity. Here's why investing in robust malware protection measures is imperative:
Protecting Data Privacy: Malware can compromise sensitive information such as personal identities, financial details, and proprietary business data. By deploying reliable malware protection solutions, individuals and organizations can mitigate the risk of data breaches and uphold privacy standards.
Preventing Financial Loss: Malware attacks can lead to financial losses stemming from stolen funds, fraudulent transactions, or extortion through ransom demands. Implementing proactive malware defense mechanisms helps minimize financial risks and safeguard assets.
Ensuring System Reliability: Malware infections can impair system performance, disrupt operations, and even render devices or networks inoperable. By maintaining robust malware protection protocols, users can uphold system reliability and minimize downtime.
Preserving Reputational Integrity: A malware-related security breach can tarnish an individual's or organization's reputation, eroding trust among stakeholders and customers. Prioritizing malware protection demonstrates a commitment to security and enhances reputational integrity.
Staying Ahead of Emerging Threats: With the ever-evolving landscape of cyber threats, staying abreast of emerging malware variants and attack vectors is crucial. Regularly updating malware protection solutions helps users stay ahead of evolving threats and adapt to new security challenges.
In conclusion, investing in comprehensive malware protection is not just a prudent measure—it's a necessity in today's digital age. By prioritizing security and deploying robust defense mechanisms, individuals and organizations can fortify their digital assets and mitigate the risks posed by malware threats.
Internet privacy
Internet privacy is a critical aspect of our digital lives that is becoming increasingly important in today's interconnected world. With the advancements in technology and the rise of online platforms, ensuring the security and confidentiality of our personal information has become a major concern for many individuals.
In the digital age, our online activities leave behind a trail of data that can be accessed and potentially exploited by various entities. From social media websites tracking our browsing habits to online retailers collecting our purchase history, our personal information is constantly being monitored and stored without our explicit knowledge or consent.
Protecting our internet privacy involves taking proactive measures to safeguard our sensitive data from unauthorized access and misuse. This includes using secure passwords, enabling two-factor authentication, and regularly updating privacy settings on our devices and online accounts.
Furthermore, utilizing virtual private networks (VPNs) can help encrypt our internet traffic and hide our IP addresses, making it harder for third parties to track our online activities.
It is also essential to be cautious about the information we share online and be mindful of the websites we visit and the links we click on. Phishing scams and malicious websites can trick individuals into disclosing personal information or installing harmful software on their devices.
By educating ourselves about internet privacy best practices and staying informed about the latest cybersecurity threats, we can better protect our digital identities and maintain control over our online privacy. Ultimately, taking proactive steps to safeguard our internet privacy is crucial in ensuring a safe and secure online experience.
0 notes
Link
With the most recent innovation, it is significant that you secure your gadget against all forceful and malignant infection assaults. To determine all infection issues, essentially contact our group of specialists and experts and get the best arrangements according to your necessities. Stress not, get total Antivirus Support and clean infections or malware and introduce and update these antivirus applications. We guarantee to help you with administrations like Antivirus establishment, Virus expulsion, spyware evacuation, firewall establishment and setup, PC streamlining, Internet improvement, Security advancement to verify your PC. The main thing you have to do is to call at our toll-free number +1-844-784-0310 (USA/Canada) and +1-844-784-0310 (UK) for 100% client fulfillment.
We are here with our group of guaranteed specialists who will introduce and arrangement your enemy of infection programming to shield your gadgets from PC infections. We assume total liability to manage you to an arrangement and introduce ground-breaking and free or paid antivirus programming, shockingly fast, simple and secure antivirus. We can help you through Antivirus Support Phone Number with the accompanying administrations:
#antivirus support#antivirus support phone number#antivirus support technical support#norton antivirus support#norton antivirus support phone number#avg antivirus support#avg antivirus support phone number#avast antivirus support#avast antivirus support phone number#kaspersky antivirus support#kaspersky antivirus support phone number#mcafee antivirus support phone number#mcafee antivirus support
0 notes
Text
reinstall kaspersky internet security

The Kaspersky Quick Start Guide, which contains your activation code, informs users to hold onto the document, but many individuals end up misplacing it. For those who purchase their products online, the activation code comes in the form of an email, which, again, many users forget to save.
According to the License Agreement terms, “To check the legitimacy of the Software use the Right holder reserves the right to use means to verify that you have a licensed copy of the Software.” Technical Support specialists can ask to verify the legitimacy of your software use by providing a copy of a document containing the code. If you cannot provide a copy, your software will work with limited functionality and Kaspersky Lab specialists may cancel providing technical support. Therefore, you should keep the document in a secure place.
And what should you do if the code is lost? If you reinstall the software, you need to request the code again. Activation codes are not stored in applications or registry. If your current activation code was not added to My Account (my.kaspersky.com), you will have to remember where you stored it.
If the license was purchased in Online Shop, you can easily request to re-send your order or you therefore need to contact the online shop directly.
If you bought your license in a shop on a physical medium (e.g. CD), you can submit a request to Kaspersky Lab Technical Support and attach a screenshot of the window with your license number.
0 notes
Text
Download, Install and Activate Kaspersky
What are the instructions for Download, Install and Activate Kaspersky?
Steps to Download, Install and Activate Kaspersky at Usakasperskycom/Kav download:
Installing software refers to a procedure of making a device ready to run software or program. User may Install Kaspersky product KEY on the device (Windows or Mac), by following step by step procedure mentioned below:
First of all, go to the official website is usa.kaspersky.com/kavdownload
Now, choose the “My Account” option.
And then, choose the “Sign In” option from the “My Account” drop-down menu.
On the Sign-in page, type the email address & password of the Kaspersky account in the corresponding fields.
Now, hit the “Sign In” key.
In the Kaspersky account, go to the “Subscriptions” section & choose Kaspersky antivirus subscribed by users.
Now, click on the “Add Device” button displayed in front of the selected Kaspersky product.
The “Add Device” page will seem on the screen. Here, choose “Type of Device” on which users want to install subscribed Kaspersky antivirus products.
Hence, click the “Download” key displayed at the bottom of the page.
After successfully download to the device, follow the on-screen instruction to install a Kaspersky subscription to the device.
Kaspersky activation code for usa.kaspersky.com/kav download:
It is an alphanumeric characters string. I have a Kaspersky activation code that is unique for every Kaspersky user. An activation code is an array of 4 blocks of characters you need to activate the application. Each block consists of 5 characters which can be a combination of letters and numbers, which comes to a total of 20 characters: ХХХХХ-ХХХХХ-ХХХХХ-ХХХХХ.
The Download, Install and Activate Kaspersky | To activate Kaspersky read this blog step by step process:
First of all, to activate the commercial version of Kaspersky Anti-Virus 2016, use a 20-digit activation code. You can find the activation code on the Quick Start Guide if you have a boxed version or in the message sent to your e-mail if you bought the code in the online store. If you do not have an activation code, buy it at the Kaspersky Lab’s official e-Store.
So, now I expect you have an activation code. Go to my.kaspersky.com
Now click on the Signup option on this page
If you already have a Kaspersky account before click sign in
When you will sign up you need to put your email and need to create a new password for the Kaspersky account.
As a result of sign up, you will get a verification email from Kaspersky
So now go to your given email and verify to complete the Kaspersky account verification
when you will click on the verification email link, it will redirect you to your Kaspersky account.
Finally, you will get the place to add your activation code
Put your activation code here.
Now on the same page, you will find tab download, just click on that
Seems like you got your product listed right!
Just click to download
After downloading just run the product. Now you are done.
Download, Install and Activate kaspersky- Free Download
Click on the below button to start Kaspersky Internet Security 2018 Free Download. This is a complete offline installer and standalone setup for Kaspersky Internet Security 2018. This would be compatible with both 32 bit and 64-bit windows.
System Requirements For Download, Install, and Activate Kaspersky:
Before you start Kaspersky Internet Security 2018 free download, make sure your PC meets minimum system requirements.
Operating System: Windows XP/Vista/7/8/8.1/10
Memory (RAM): 1 GB of RAM required.
Hard Disk Space: 1 GB of free space required.
Processor: 512 MB of RAM required.
Tips before usa.kaspersky.com/kavdownload:
Uninstall any other antivirus from your computer if you had any before. Remove it completely and restart your computer:
Also, uninstall any Old version of Kaspersky antivirus from the computer.
Most noteworthy you must restart your computer in order to completely remove a security after uninstall.
If still, you are facing a problem you can contact our support from the given contact link or on the toll-free number.
1 note
·
View note
Link
The events of recent weeks have proven that it’s not a safe world for masculine men out there. Now more than ever men should be looking into increasing their personal security. As an IT guy I have been thinking for a solution to the problems men face. Below are measures I can recommend one take to increase his security.
Disclaimer: this guide caters to Windows users, but others can still find value.
1. Install a VPN

VPN stands for Virtual Private Network. To understand what a VPN does, first you must understand what an IP is. IP is something like a computer passport number. Each electronic device has it’s own IP address. Websites register your IP when you use them—this makes it easy to find your location, your device, and therefore your identity. A VPN makes it so when you connect to a website you first go through the VPN server. So when you connect to a website instead of seeing your computer IP it shows the IP the VPN provides you. Roosh recently wrote on VPNs.
Example (manually changing IP):
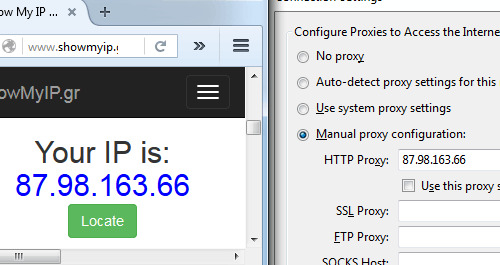
The problem here relies on the credibility of the VPN provider. Many VPN providers register your activity and can then hand it to a government organization if they so demand. Even VPNs that promised not to do this, broke their promise. There is an agreement between the Anglo-speaking countries that affects VPN users. The government can ask the provider for your data, and there is nothing your provider can do to not give it to them.
These countries are referred to as 5 eyes. Currently, similar agreements are being done with other countries, referred to as the 14 eyes: United Kingdom, United States, Australia, Canada, New Zealand, Denmark, France, the Netherlands, Norway, Germany, Belgium, Italy, Spain, Sweden
Definitely get a paid VPN. Free VPNs are not an answer, they most likely register some info on you and are slow. After some research on VPN providers I have found some VPN proviers that are outside the 14 eyes, use encryption, accept Bitcoin, support OpenVPN and have a no logging policy and an overall good reputation.
Here are my findings: blackVPN (Hong Kong, 25 servers, 100 dollars a year), Cryptostorm (Iceland, 13 servers, 52 dollars a year), HIDEme (Malaysia, 85 servers, 65 dollars a year), NordVPN (Panama, 52 servers, 48 dollars a year), Perfect Privacy (Panama, 40 servers, 150 dollars a year), Privatoria (Czech Republic, 12 servers, 23 dollars a year).
One VPN provider attracted my attention particularily, that being BolehVPN, since it is one of the only two providers that offers Tor to VPN alongside VPN to Tor (the other one being AirVPN, which is based in Italy, therefore part of 14 eyes), so if you want that particular set-up, check it out.
Make sure to check the VPN provider’s canary. It is a document that confirms that the VPN provider was not touched by the government. It should be updated every month, if it isn���t unsubscribe. Example.
How to increase VPN security
1) Pay with untraceable money
Sign up for an anonymous e-mail account using Tor and use a Bitcoin Mixer to send Bitcoins to a newly generated address in your local wallet. Alternatively, use the Bitcoin-OTC to purchase Bitcoins ‘over the counter’ from a person, rather than an exchange. Then, use a patched Bitcoin client, such as coderrr’s anonymity patch to avoid linking the newly generated address to any of your pre-existing Bitcoin addresses. —Andrew, Private Internet Access.
2) Make sure you don’t disconnect from VPN and prevent DNS leaks
Use the pro version of VPNCheck to automatically disconnect from internet when losing connection to VPN and to prevent DNS leaks. Or search for the manual way of doing it
3) Use multiple VPNs
Another measure to consider is using two or more VPNs. Basically activate one VPN first, then another one, done.
4) Resolve the PPTP IPv6 VPN flaw
Not likely to affect everyone. PPTP is the weakest VPN protocol and if you use one of the VPNs I mentioned before you will likely use a better protocol, but for those who do, there is a possible flaw that you can correct like this—for Windows Vista and above: Open cmd prompt and type: netsh interface teredo set state disabled.
5) Secure your router
Here’s a guide.
2. Install an antivirus

There are three tiers of antiviruses: antivirus sofwtare, internet suite and premium security suites. Read about them here. At minimum use Microsoft Security Essentials (free software from Microsoft), though paid antiviruses (such as Bitdefender, Kaspersky, etc.) are better.
3. Use Tor and TailsOS for safe web browsing

Many popular browsers are not highest ranked in regards to keeping your anonymity. For example, while Chrome is theoretically secure from spyware and adware, their stance on privacy can be summarized as follows:
He went on, speaking about the future of search. With your permission you give us more information about you, about your friends, and we can improve the quality of our searches. We don’t need you to type at all. We know where you are. We know where you’ve been. We can more or less know what you’re thinking about.
There are factors one must be careful of: cookies, encryption (https), tracking ads, javascript exploits, canvas fingerprinting and others. A writeup on these would take a long time so research them on your own if you wish. I will just mention browsers that avoids these issues.
USE SAFE SEARCH ENGINE
Instead of using the google search engine use disconnect.me installed into Tor (or install as extension into Firefox)
TOR BROWSER
Tor Browser is an internet browser designed for online anonymity. It is a modified version of Firefox with add-ons pre-installed. Tor works somewhat similar to the VPN concept. Before connecting to a website you go through “nodes”. Which are private stations, each with its own IP. So instead of showing your IP, it will show the IP of the last node you traveled through.
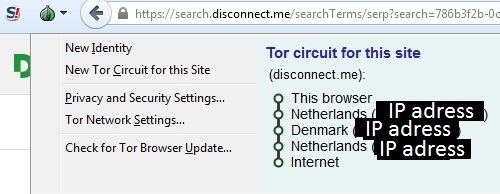
The downside of Tor is that it is slow, due to the fact that it works thanks to enthusiastic individuals. Tor is not for casual usage, but specifically for privacy needs, particularly posting online or searching the deep web.
Tor has some weaknesses you must be aware of:
First
Oftentimes when you are using a network, the network provider can’t see what you are browsing, but they can see that you are using Tor. You can use things like a bridge obfuscator, obfsproxy, or setting VPN to Tor. This is a complex issue, here is a guide on hiding tor usage from ISP (internet service provider).
Second
The trustworthiness of exit relays. When the government found out about the popularity of Tor they created their own exit nodes, that acted as honey traps. To fight this, use a TailsOS (or booted off a flash stick, DVD or SD card in a public wifi spot, like a coffee shop). That way even if the final node was a trap, it would only lead to your TailsOS profile, not your general one. Check so the public wifi spot you are using has no cameras around, so they will not be able to check camera footage of who used a laptop in that particular time frame. Don’t forget to log off when finished. Alternatively, use Tor to VPN.
Third
Often many programs, like torrents, will ignore Tor, even if you manually force them and just connect straight away, thus giving you away. The answer is to not use torrents with Tor. I REPEAT, NO FILE SHARING ON TOR.
There are of course other various vulnerabilities out there. And as a reminder, Silk Road, a large black market was cracked in the past.
COMBINING TOR WITH A VPN
Tor is good on its own but even better when combined with a VPN. There are 2 methods : Tor to VPN, VPN to Tor. Both have their weaknesses. First one allows ISPs to see you use Tor, the second does not protect from malicious end relays . VPN to Tor masks your Tor usage, Tor to VPN protects from malicious exit nodes.
I have thought of using VPN to Tor to VPN, which should theoretically accomplish both. For VPN to Tor use a secure VPN provider and add non-Tor traffic to mask usage. For Tor to VPN, pay with anonymized bitcoins and never connect to your VPN without connecting to Tor first.
VPN to Tor: The Harvard bomb hoaxer was de-anonymized because he was the only one in college using Tor. If he went through a VPN first, he would have been harder to track (assuming his VPN provider did not keep logs).
Tor to VPN: Protects from malicious exit nodes, on the other hand. TailsOS with public wifi accomplishes the same. Of course, either is better than nothing. Which you choose depends on your needs. The only two providers that offer Tor to VPN are AirVPN (based in Italy, so part of 14 eyes, but not the 5 eyes) and BolihVPN.
IF YOU DON’T WANT TO USE TOR
While using Tor is advisable, for casual usage you can set Firefox to be very secure with the help of add-ons and custom settings. Here is a guide.
WEBSITES THAT BAN VPN AND TOR
Certain websites ban Tor (e.g. Imgur). Use an alternative then (e.g. Anonmgur). Otherwise use VPN to Tor. There are VPN providers that cycle IPs, so that helps with VPN IP range bans.
TAILSOS
Windows is not very safe. There have been rumors of NSA backdoors on Windows devices. Supposedly NSA can store almost everything you do online (including Facebook, popular mail providers, and possibly things offline).
There are some good alternatives out there, TailsOs being one of them. TailOS is an operating system specifically designed for security and is Linux based. It can be ran off a USB stick. For those extra paranoid, use Tor in a public space on a laptop with TailsOS loaded of a flash drive.
Of course TailsOS is not very suitable for day to day needs, so use it for shitlord purposes. For your day to day purposes you might have to use Windows, but for the love of god, DO NOT use Windows 10, it is absolutely awful for security.
I prefer Windows 7. If you are more advanced, you can use alternative platforms like Debian or some distro of Linux or whatever. Just beware, many programs for Windows do not have alternatives on Linux based systems. If you are a casual, moving to another platform can be difficult. And if you really are a nerd, then you can look into some exotic setup like Qubes + Whonix or whatever other myriad of OS and Virtual Machines there are around.
4. Other darknet browsers

I2P network: While Tor is designed to anonymously browse the normal web and onion sites, I2P is a web of it’s own. Preferably to be browsed through Tor. It allows (slow) torrenting and great for messaging, IRC, file sharing, secret websites (.i2p)
Freenet – Freenet is a peer-to-peer platform for censorship-resistant communication.
5. Look into bitcoin and online currency
Bitcoin is virtual currency that has taken the world by storm in recent years. There are other online currencies competing against it, but Bitcoin is the most established online currency. It is the default virtual currency. Bitcoin is not for daily usage, rather online purposes. There are VPN services that accept payment with bitcoin. There are even services that will store physical gold in exchange for bitcoin.
Truly a financial revolution. Unfortunately, it’s also a big headache for tax services. Bitcoin is also infamous for being used to purchase illegal stuff on the internet black market. But you wouldn’t use it for that, would you?
To start using bitcoins just register a bitcoin wallet and you are good to go.
HOW TO INCREASE BITCOIN ANONYMITY
Bitcoins are not anonymous by default. They must be washed and anonymized. Buying through Tor + Coin mixing + anonymity patched bitcoin client. Over the counter (OTC) bitcoins are an option as well.
6. Use proper password protection
Never use the same password twice. Try to make it long and contain both characters and numerals, etc. Hint : use L33t, P@ssVV0r|)333. If you can, add non English characters even better, PåSsWøRд0, but you can’t always do it.
If you are unsure, use a safe password generator, such as Master Password To manage passwords use a password manager, such as KeePassX.
7. Use proper mail protection

Use throwaway email to register in most places. Never use your public e-mail to register anywhere controversial like Neomasculintiy affiliated websites.
SAFE MAIL PROVIDERS
For general mail needs, use a mail provider that is focused on security. I found two outside 14 eyes, in Switzerland: ProtonMail (free), NeoMailBox (50$/year, custom domain option ex : [email protected], [email protected])
Remember to still use personal safety measures, like additional encryption. Never trust 2nd parties with your protection completely.
BECOME AN EMAIL PROVIDER YOURSELF
Another interesting move is to become a provider yourself, in essence create your personal Gmail by turning your PC into a mail server. To do this, use Mail-in-a-box. They have good guide on their site https://mailinabox.email/.
USE A SAFE MAIL CLIENT
A mail client is a program that allows you to manage mail from the cloud by saving it locally, by connecting to the email host, such as Gmail. The default mail client in Windows is Microsoft Outlook (which sucks). I will focus on my preffered mail client setup.
1) Download Thunderbird
2) Install the Enigmail add-on, to allow encryption
3) Install the TorBirdy add-on, to make Thunderbird run through Tor
BEWARE THE LAW
Beware of a law that allows government officials to read any mail hosted online older than 6 months without a warrant. Use an external email client like Thunderbird or Enigmail, download your emails and store them locally. Never leave them on the server.
EMAIL ALTERNATIVES
Look into email alternatives such as : Bitmessage, I2P-Bote, Retroshare
8. Use encryption for messaging

Encryption is the process of making a message unreadable to third parties. Some programs do it for you, manually you can use a program like GPG4win or similar which uses PGP encryption.
The way it works is this :
1) You create your public key.
2) You digitally sign the information with your private key, so when the other side verifies it with their own public key, they can confirm that it is indeed YOUR public key. (WebOfTrust)
3) When someone wants to write to you he encrypts it using the public key you provided, or the other way around.
4) You then use your PRIVATE key to decrypt the message he sent you.
Here is a tutorial:
youtube
MOBILE ENCRYPTION
There are encryption possibilities for your phone as well. First, set encryption on your Android device. Second, use an app called Signal
9. Scrub EXIF data of photos you post online

When you take a photo with a particular device, often it registers what device you used to take the photo, when and where it was taken. To avoid this problem, before posting online use an EXIF scrubber. It is a piece of software that deletes all information that might incriminate you.
Some examples are BatchPurifier Lite and Exif Pilot. Also, careful with what photos you post of course, nothing that could indirectly lead to you.
10. Torrent and stream safely

Torrenting can be useful for file transferring. If you plan to torrent anything or share something with friends, look into safer peer to peer torrenting. P2P is good for small files. Generic torrent services are good for larger files.
One advice I have is avoid torrent programs known for their untrustworthiness, such as BitVomit (BitComet) and uTorrent (closed source + adBloat). qBit, Deluge, Tribler (this one’s interesting) are good options (open source and lightweight).
Beware of laws in certain countries that forbid downloading stuff online. Germany is particularly infamous for this. There are ways to combat this issues through VPNs. But DO NOT USE TOR, I REPEAT, DO NOT USE TOR FOR FILE SHARING. For even more secure anonymous file sharing look into I2P (beware avg speed: 30 kbs per sec)
As for streaming, Popcorn Time and other analogous services (such as PornTime) are used to stream new movies (and porn) respectively. They are based on BitTorrent technology. They are relatively safe services, as long as you use a VPN.
11. Encrypt the files on your PC
Use VeraCript, a piece of software designed to encrypt disk partitions or whole USB drives. It is the successor of TrueCrypt (which stopped development after feds asked them to include vulnerabilities).
https://www.youtube.com/watch?v=_fGUJ6AgOjQ
HIDE FILES IN IMAGES
Also, another interesting technique is to hide text, videos and other stuff in pictures, it’s called Steganography.
12. Look into this promising new technology for your online needs
The 3 pieces of software I am about to recommend are TOX , RetroShare and diaspora.
TOX is a Skype clone with focus on privacy.
Retroshare is a private network service. You can use it for private mailing and other purposes.
diaspora is a social network designed for privacy and decentralization https://diasporafoundation.org/
Another interesting possibility for ROK people is to use a .onion or .i2p domain or freenet for a sort of “secret” webpage, unavailable to casuals out there.
To summarize
I think this advice will benefit the ROK community for protecting their anonymity and using secret backup channels for future purposes. Here is a quick cheat sheet:
Casuals: VPN paid with shuffled bitcoin + VPNcheck Pro, Signal on Android, Firefox with add-ons for casual use, Tor for shitlordery, Encrypted mail and hard disk, password manager, ProtonMail for daily use, throwaway mail—everything else, Thunderbird with add-ons, EXIF scrubber. Download email on PC then delete off server.
Advanced: Same as above + Tor combined with VPN, I2P and Freenet, (TBitmessage I2P-Bote Retroshare) instead of mail, becoming mail provider, diaspora*
Super advanced: Same as above + Multiple VPNs, Using Tor off of TailsOS in a public space where cameras cannot film you. Alternative OS and Virtual machines. Secure you router.
Here’s a good collection of security resources.
Always remember, there is no way to remain completely anonymous, just ways to make it harder to be detected.
Read More: 5 Ways To Improve Your Online Game
1 note
·
View note
Text
download Kaspersky internet security 2019
download Kaspersky internet security 2019 is the URL to redeem your Kaspersky activation key. You need to go usa.kaspersky.com/downloads to redeem your Kaspersky.
How can Kaspersky Activate antivirus protect your virtual world downloaded from usa.kaspersky.com/downloads?
Kaspersky runs in the background taking minimum system space to reduce lags. Kaspersky antivirus identifies good data and hence scans are quick and safe.
It quickly scans all your incoming emails along with their attachments. Auto scans USB devices once plugged into the system for harmful files.
For all the Gamer’s, Kaspersky has a gaming mode that can suspend functions based on the user so that play is not interrupted with pop-up remainders or slow systems.
Steps to follow before installation of Kaspersky activate antivirus from usa.kaspersky.com/download:download Kaspersky internet security 2019
Redeem your retail card by visiting usa.kaspersky.com, Kaspersky retail card is necessary because it is the easiest way to download & install Kaspersky product in your PC.
This card will ensure that you have downloaded the latest version of security. Installing this security product or antivirus through an online twenty digit product key code must require. For installing this product follow some steps.
Make sure your system configuration meets the minimum system requirements.
System OS (operating system) should be updated properly so Kaspersky updates can install properly in the system.
Uninstall all the unwanted, similar and conflicting programs from the system.
Also, make sure, you remove all the temporary files from the system.
After following these steps, Download Kaspersky product by visiting usa.kaspersky.com.
Tips before Entering Kaspersky Activation Code:
Uninstall any other antivirus from your computer if you had any before. Remove it completely and restart your computer.
Also, uninstall any Old version of Kaspersky antivirus from the computer.
Most noteworthy you must restart your computer in order to completely remove a security after uninstall.
If still, you are facing a problem you can contact our support from the given contact link or on the toll-free number.
Best Features of Kaspersky Internet Security – download Kaspersky internet security 2019
After download Kaspersky Internet Security 2019 and you will get various key features.
A powerful antivirus solution for your device.
Complete protection tools.
Kaspersky Provides Internet Security, PURE and Antivirus.
Protect against phishing and other threats.
Create reports and notify the users.
malware protection
1 note
·
View note
Text
8 Best parental control apps for Android and iPhone - 2021
Are your kids' smartphones and tablets loaded with messaging apps such as Snapchat, TikTok or Kik? Do your kids act like their texts, tweets or viral videos can't wait until the morning? Do they hide their phone screens when you walk into the room? If so, then you may need one of the best parental-control apps.
The best parental-control apps for smartphones can help you track your kids, see with whom they're communicating, block them from viewing objectionable or dangerous websites, and even help kids understand limits while preventing them from seeing adult content or chatting with creeps. Using paid parental control apps for free using free google play gift card.

No single parental-control service we tested is perfect, but Net Nanny (formerly Zift) delivered the best mix of web filtering, location tracking and app management on both Android and iOS devices. (All of these apps can do more on Android than on iOS due to Apple's tight restrictions.)
Norton Family Premier was a close runner-up for the best parental control app. Unlike Net Nanny, Norton's service offers text-message logging and monitoring, but only on Android devices. Norton Family Premier also lets you monitor Windows PCs.
Parents on tight budgets should consider Kaspersky Safe Kids. Its free tier includes web monitoring, time limits and app management, and its full-featured, paid plan is just $15 per year for an unlimited number of devices, including PCs and Macs.
BEST PARENTAL CONTROL APPS
1. Net Nanny Parental Control
Zift/Net Nanny, which we consider to be the best parental control app, has excellent web-filtering technology and a modern, intuitive design.
Among all the parental-control apps we tried, it comes closest to having feature parity between its iOS and Android versions. Its iOS abilities don't seem to have been affected by recent Apple policy changes.
Net Nanny can track your child's location, display their location history, and set time allowances and schedules equally well on both platforms. The iOS version lets you block several dozen apps on your kid's phone; the Android one lets you block them all. (Tom's Guide readers save $10 off each of Net Nanny's plans.)
The only thing Net Nanny can't do on a smartphone is monitor calls or texts. No apps we tested can do that on iOS, but several do on Android.
2. Norton Family Premier
Norton Family Premier's power and features are ideal for Android (and Windows) households with many children, offering nearly every feature a parent could want from one of the best parental control apps.
This service's location-tracking, time-scheduling, and web-filtering and -monitoring capabilities work on both iOS and Android, but time allowances are for only Windows and Android. App management and text-message monitoring don't work on iOS at all. There's no geofencing on either platform.
Norton Family Premier comes free if you spring for one of Norton's more expensive antivirus suites, such as Norton 360 Deluxe, which is often discounted to as little as $50 per year. At that price, getting Norton Family Premier along with Norton's excellent antivirus protection is a no-brainer.
3. Kaspersky Safe Kids
Like Qustodio, Kaspersky Safe Kids lets you monitor your kids' activities on PCs and Macs, as well as on smartphones. Even better, Kaspersky's paid tier is only $15 per year, and even its free plan lets you set time limits, filter websites and manage other apps.
Kaspersky's location tracking and geofencing work in both iOS and Android, as do its web monitoring and device scheduling. But app management is limited on iOS, and the iOS app can't monitor calls or texts at all. Still, if you don't feel a need to read your kids' text messages, then Kaspersky Safe Kids is well worth considering.
In March 2019, Kaspersky Lab filed an antitrust complaint against Apple for allegedly forcing the removal of some features from Kaspersky Safe Kids. Apple hinted in June 2019 that it might relax some of its tighter restrictions on iOS parental-control apps with iOS 13, but we haven't yet seen anything different and Kaspersky's complaint is ongoing.
4. Qustodio
Qustodio has software for Macs, PCs. iOS and Android devices and Amazon Fire tablets, and it lets you set time limits for individual apps and individual devices.
This service's limited location tracking works on both iOS and Android, although there's no geofencing option. However, a Family Locator feature that shows you where all your kids are at once was added in September 2019.
You can manage only a few dozen apps on iOS, as opposed to all Android apps. Web filtering is more powerful on iOS, while monitoring texts and calls works on only Android.
The one big drawback is that Qustodio can get darn expensive, costing up to $138 per year for 15 devices. In early 2019, Qustodio experimented with offering a much cheaper three-device plan for $40 per year, but that did not last.
5. OurPact
Once the most powerful parental-control app for iPhones, OurPact was hobbled by an Apple rule change in late 2018 that nixed the service's geofencing, location tracking and time allowances on iOS. In early 2019, Apple quietly expelled OurPact from the App Store, but in July, after Apple eased up on its restrictions, OurPact was reinstated.
At its peak, OurPact was the only parental-control app we tested that could manage or block any iOS app. It can still do so for Android devices. OurPact also gets kids involved in managing the daily allowance of screen time that you give them, and it does a good job of scheduling.
Yet, its website filtering simply blocks porn, and it can't monitor calls or texts at all, even on Android. However, you can block messaging apps, and OurPact remains a joy to use.
6. Screen Time
Screen Time does an excellent job of managing and scheduling kids' device access. Unfortunately, this app doesn't do a whole lot else on iOS devices. And it has baffling upcharges for location tracking and web filters, both of which come standard with other parental-control apps. (You get both features in the 14-day premium trial.)
We liked how this service doles out additional screen time for chores or good deeds. But you can't block apps on iOS, and there's no call or text monitoring at all, although geofencing and location history were recently added.
7. ESET Parental Control for Android
ESET Parental Control for Android sticks to one platform, but it doesn't shine even there, lacking text-message- and call-monitoring features. The free app management and time management do work well, as do the paid location tracking and geofencing.
Still, the yearly plan is not worth paying for unless you get it bundled with ESET Smart Security Premium. That's because Kaspersky Safe Kids does more than ESET at half the price.
8. MMGuardian
MMGuardian has nearly every parental-control feature you might want, especially on Android, but the user interfaces are outdated and frustrating.
Both the iOS and Android smartphone apps offer location tracking and excellent web filtering, and have recently added an artificial-intelligence component to spot nudity in saved images. App management is strong on Android but primitive on iOS. On Android, the parent can read every text and block any number. Time management and screen-time scheduling are also Android-only.
How we test and rate the best parental control apps
We tested each app on every platform it supported twice, from installation to testing to uninstall. We typically monitored activity from the MacBook Pro, but if apps offered control from a smartphone app, we tested those features as well. Calls and texts for monitoring purposes were made from a secondary Android device.
The best Android parental-control apps remain more robust than their iOS counterparts in most cases, especially with regard to call and text monitoring. But new additions to iOS have closed the gap somewhat.
We note areas in which there are discrepancies in the functionality offered on each platform, but we are not providing distinct ratings and reviews for the iOS versus the Android version of each app.
What we didn't include?
The best parental control apps for mobile devices work best when they're part of a comprehensive approach to teaching your kids about behaving responsibly online. That means talking to your kids about what they should and shouldn't do with their mobile devices, clearly communicating how you expect them to act, and making clear that you will be monitoring what they do with their phones.
For that reason, we avoided testing apps that can run in stealth mode on a child's phone. There are many products that tout this capability, but some people use such services to spy not on their children, but instead on their spouses or on other adults. That is illegal in most U.S. jurisdictions and is often a factor in domestic abuse.
In addition, we did not consider apps that offered the ability to record a child's phone conversations. State laws vary on the legality of recording someone without his or her consent, and no states allow the recording of phone calls without either party's consent.
1 note
·
View note
Text
usa kaspersky kts download activation

The Kaspersky Quick Start Guide, which contains your enactment code, educates clients to clutch the report, yet numerous people end up losing it. For the individuals who buy their items on the web, the initiation code comes as an email, which, once more, numerous clients neglect to spare.
As per the License Agreement terms, "To check the authenticity of the Software utilize the Right holder maintains whatever authority is needed to utilize intends to confirm that you have an authorized duplicate of the Software." Technical Support experts can solicit to confirm the authenticity from your product use by giving a duplicate of a record containing the code. On the off chance that you can't give a duplicate, your product will work with constrained usefulness and Kaspersky Lab pros may drop giving specialized help. In this way, you should keep the record in a protected spot.
What's more, what would it be a good idea for you to do if the code is lost? On the off chance that you reinstall the product, you have to demand the code once more. Enactment codes are not put away in applications or vault. On the off chance that your present initiation code was not added to My Account (my.kaspersky.com), you should recall where you put away it.
On the off chance that the permit was obtained in Online Shop, you can without much of a stretch solicitation to re-send your request or you in this way need to contact the online shop legitimately.
On the off chance that you purchased your permit in a shop on a physical medium (for example Album), you can present a solicitation to Kaspersky Lab Technical Support and connect a screen capture of the window with your permit number.
0 notes
Text
install Kaspersky already purchased
install Kaspersky already purchased, Users download Kaspersky internet security. Once you install the Kaspersky Internet Security you get full protection.
Where to seek out Kaspersky Activation Code?
It is easy to set up and installs your Kaspersky security package. Find the Kaspersky 20-character alpha-numeric code that is written on the back of the retail card. Here is a sample product key to understanding you
xxxxx-xxxxx-xxxxx-xxxxx
Minimum System Requirements for install Kaspersky already purchased: install Kaspersky already purchased-
Ensures the availability of the following system specifications before you first install your Kaspersky Internet Security.
First of all you operating system: Windows 10 / 8.1 / Win 8 / Win 7 / Vista / XP
After that your memory (RAM): 512 MB or above
And your hard disk (storage): 250 MB hard disk free space
Your own processor: Intel Pentium IV or above.
How do you install Kaspersky Antivirus on your device?
First of all, ensure that the system date is correct on your computer. If the system date is incorrect, set it.
Now, Enter the activation code into the specified field in the Activation window.
The activation code only contains Latin letters and numbers.
If you cannot find the Activation window or if you closed the application after installing it, run Kaspersky Anti-Virus 2019.
Now click on the link Enter activation code in the lower-right part of the main window.
After that Click Activate.
Finally, It will prompt Activation completed successfully, click Finish.
Now you are protected, restart your computer.
How do you install and activate Kaspersky on multiple computers?
You need to activate Kaspersky Antivirus on several devices that follow the steps described above:
Each copy of the multiple-device license for install Kaspersky already purchased is installed and activated in the same way that you want to protect all computers.
Finally, to activate install Kaspersky already purchased on all computers, you must use the same activation code that you purchased.
You need to install Kaspersky Antivirus step by step process: install Kaspersky already purchased-
First of all, if you want to activate the commercial version of Kaspersky Anti-Virus 2020, then use the 20-digit activation code.
If you have purchased the code in the online store you can find the activation code on an active version if you have a boxed version or in the mail sent to your e-mail.
And if you do not have an activation code, you can buy it from the official of Kaspersky Lab.
Now, if you have an activation code, go to my.kaspersky.com.
And then click on the sign-up option.
Then click Sign in if you already have a Kaspersky account.
Now when you sign up, you will have to enter your email and create a new password for the Kaspersky account.
Then now you will get a verification email by Kaspersky.
After that you need to complete the verification, for this, open your email and verify.
Therefore, when you click on the verification email link, it will redirect you to your Kaspersky account.
And finally, you will find the place where you have to enter your activation code.
You then enter your activation code at that location.
And now on the same page, you will get the option to download Kaspersky, just click on it.
After that, after you complete the download process, just run the product.
BEST FEATURES OF KASPERSKY INTERNET SECURITY: INSTALL KASPERSKY ALREADY PURCHASED-
After you download Kaspersky Internet Security and you will get various main features: install Kaspersky already purchased-
A powerful antivirus solution for your device.
Now you complete security devices.
Kaspersky then offers you Internet security, .net and antivirus.
Then you protect against phishing and other threats.
After that, you create a report and inform the users.
And malware protection.
Key Benefit and Service highlight: install Kaspersky already purchased-
Your response to your event and forensic.
And improve and accelerate capabilities.
Then let you conduct deep searches in danger indicators.
Then reduce the attacks on your target.
The intelligence of your trust.
And sandbox analysis: explore unknown threats.
Then you threaten the victim.
FEATURES OF install Kaspersky already purchased-
Below are some noticeable features which you’ll experience after Kaspersky Anti-Virus 2020 free download: Start to install Kaspersky already purchased –
A useful anti-malware tool that has been developed detecting and eliminating viruses.
Protects your system from different web-based threats that can harm your system.
Got a real-time safeguard and security utilities.
Then Got a simple and quick installation process.
Got a pleasant looking and simple interface.
Supports four different scan types which are Full, Quick, Custom and Removable Drive mode.
Got a contextual scan which will let users verify any file.
It can be optimized for preserving battery life.
1 note
·
View note
Photo

Kaspersky antivirus helps you to protect your computer from viruses and in case you need any help you can either visit Kaspersky website at http://www.kasperskysupporttech.com/ or you can contact Kaspersky support number +1-844-669-7730.
1 note
·
View note
Text
LastPass vs Bitdefender: Ultimate Comparison Guide 2023
There are a large number of antivirus available in the market that you can choose to protect your computer devices or businesses. Some of the prominent Antivirus software are Norton, McAfee, Bitdefender, Kaspersky, and many others. Additionally, there are many password manager software that provides full security to your devices by keeping your device safe.
If you think about which one you should get between LastPass and Bitdefender, then this blog post can be beneficial for you. So, keep reading the following write-up to understand the key features and specs of both products fully.
LastPass Overview
LastPass is a password manager software. It is very user-friendly and comes with loads of features, such as password storage synchronization across multiple devices. As a result, it allows you to use the password for personal as well as professional use. It was founded in 2008, and the developer of this software is GoTo.
Additionally, this product can be used as a desktop app. But, if you want to, you can add it as a web extension. Plus, the free version of this product comes with limited features. But you get a fully-fledged password manager with advanced features. It keeps the passwords of multiple platforms safe. And let you access the password when necessary.
Bitdefender Overview
Bitdefender is a well-known antivirus software. It is helpful in keeping your info and data secure from hackers. Also, it comes with a password manager that keeps your password at your fingertips and makes your experience smooth. Apart from that, there are many other products it offers.
Additionally, it is a Romanian-based cybersecurity company. With the help of its products, you can keep your home, small & medium business, and big enterprises safe. Its products are best for detecting viruses and threats and then taking quick actions to remove those issues from your device. Some of the popular products of this brand are Total Security, Internet Security, Antivirus Plus, password manager, and many others.
LastPass vs Bitdefender Comparison
Below is the full comparison of the features and specifications between LastPass vs Bitdefender.
Features
Below are the features of LastPass and Bitdefender.
● LastPass
● Bitdefender
Language Support
● LastPass
LastPass supports languages such as English, Dutch, Turkish, Polish, and Swedish.
● Bitdefender
The language Bitdefender supports is English, Dutch, Polish, and Turkish.
Device Compatibility
● LastPass
It is compatible with devices like Windows, Mac, Android, iPhone/iPad, Linux, Web Based, and Windows Mobile.
● Bitdefender
Its products run on Windows, Android, iPhone/iPad, Mac, and web-based devices.
Company Sizes
LastPass and Bitdefender both are best in providing services for small businesses, medium businesses, large enterprises, and freelancers.
Supports
LastPass only offers its support through tickets; on the other hand, Bitdefender has many supports such as Email, phone, live support, and training.
Browser support
● LastPass
The LastPass supports various browsers and systems, such as Apple Safari, Mozilla Firefox, Google Chrome, Microsoft Internet Explorer & Microsoft Edge, Duo Security, Password Ping, Internet 2, SecureAuth, Opera, RSA Ready, and Entersekt.
● Bitdefender
The Bitdefender works on ConnectWize, Kaseya, Lab Tech, and Gravity Zone.
Pricing
The pricing of the products starts from 2 US dollars. At the same time, the pricing of the Bitdefender starts from 14 US dollars.
Conclusion
Above, you read the full details of both LastPass and Bitdefender. The first one is best when it comes to managing the password of multiple platforms on your devices. And Bitdefender is a great choice if your aim is to get robust cyber security and antivirus. However, Bitdefender also has its password manager product that lets you manage your passwords. So, it is up to you which product to choose based on your preference.
Visit: Central.bitdefender.com Bitdefender Central login Bitdefender login Bitdefender Sign in Bitdefender.com/activate
Source: https://centralbitdefenderdotcom.wordpress.com/2023/06/02/lastpass-vs-bitdefender-ultimate-comparison-guide-2023/
#central.bitdefender.com#bitdefender login#bitdefender sign in#bitdefender.com/activate#bitdefender central login#www.central.bitdefender.com#bitdefender central#bitdefender antivirus#bitdefender log in#bitdefender
1 note
·
View note
Photo

Contact our Kaspersky Phone Number : 0800-014-8929 and get your Kaspersky problems fixed remotely. Our Kaspersky Support crew is easily available 24/7 for your help. Our Kaspersky Customer Service UK techies are pleased to help you with all of your difficulties related to Kaspersky antivirus product or to repair Kaspersky error. Contact Kaspersky experts on our Kaspersky UKToll Free 0800-014-8929 for required help.
1 note
·
View note
Text
Kaspersky internet security 2019 download
Kaspersky Antivirus Troubleshooting:
Kaspersky internet security 2019 download- Kaspersky is total security that prevents your system from viruses and other threats. Sometimes, you may face problems while using it. Some of the common issues are discussed here. Go through the below topics to fix your issues on Kaspersky. Safe money is not available in Kaspersky: Kaspersky internet security 2019 download To use the Safe Money feature, you should enable it. Before you activate the feature, ensure that Self-Defense is enabled. Otherwise, the Safe Money feature will be unavailable. If the Self- Defense feature is disabled, do the following. Open the Kaspersky software on your computer. Go to Safe Money -> Enable Self-Defense. If this did not fix your problem, update your Anti-virus product or usa.kaspersky.com/downloads. Web pages are displayed incorrectly or fail to load after Kaspersky installed: Open the Kaspersky product on your computer. Click Settings and select the Additional tab. From the right panel, choose Self-Defense. Click the check-box to disable the Self-Defense feature and select Continue. If the issue persists, uninstall the soft.
How to Run a Scan in Kaspersky?
Open Kaspersky Internet Security software on your computer. Click the Scan option on the main screen of the Kaspersky Internet Security window. The scan window shows up. If you want to scan the entire computer, then click Full Scan. For a quick inspection of the scan result, click the Quick Scan option. There is another option to scan the selective files. Tap the Selective Scan option, click Add, select the file or folder you want to scan. To scan the external hard disk, tap the External Device Scan option. After selecting a file, click Scan. Once the scan process is done, check the files. "Critical system updates are not installed" error when starting Safe Money This error occurs if your computer’s OS is not updated. Kaspersky Total Security checks your OS for online banking. Go to the Safe Money tab on your product’s home screen and check if the Notify about operating system vulnerabilities option is enabled. If it is turned on, disable it and try using the security product. If the Kaspersky Antivirus Troubleshooting problem prevails, install the latest OS updates by selecting Install Update.
Tips before Entering Kaspersky Activation Code - Kaspersky internet security 2019 download
Uninstall any other antivirus from your computer if you had any before. Remove it completely and restart your computer. Also, uninstall any Old version of Kaspersky antivirus from the computer. Most noteworthy you must restart your computer in order to completely remove a security after uninstall. If still, you are facing a problem you can contact our support from the given contact link or on the toll-free number.
1 note
·
View note
Text
How to Migrate Emails from Pocomail to Gmail / Google Workspace?
Outline: Are USB Drive Data Recovery software figuring out how to import Pocomail messages to Gmail account ? Or on the other hand need to know how to relocate Pocomail to Gmail account straightforwardly ? Provided that this is true, then, at that point, here you will get a total technique. In this article, we get to realize about how might a client effectively import letter drop things from Pocomail to Gmail/G Suite account. Along these lines, continue to peruse this article.
Pocomail email client was one of the cutting edge email clients planned and created by Poco frameworks. Because of a few specialized reasons, it stooped its turn of events and consequently gets no strong fan-base methodology. After this, countless clients began relocation from Pocomail to different other email clients and webmail administrations according to their appropriateness.
Gmail ends up being the most ideal elective that anyone could hope to find for such clients to deal with the letter box information according to prerequisites. A webmail administration empowers clients to straightforwardly get to it whenever from anyplace. Gmail has a portion of the high level elements which make it an internationally OK Webmail administration like IMAP/POP3 support, Names the board, basic point of interaction, coordination with 20+ different applications for example
One Gmail account is sufficient to get to different Google administrations like Docs, Sheets, Books, Blogger, Contacts, Home base, Keep, Study hall, Assortments, Jamboard, Shopping, Guides, YouTube, Google Play, News, Drive, Schedules, Google Additionally, Google Interpreter, also Google Photographs. Clients can likewise effectively oversee Google Locales, Website admins too Google Examination through a solitary Gmail account.
Motivations to Move Pocomail Messages to Gmail Record
An enormous number of clients needs to change their letter box things from Pocomail messages to Gmail account and subsequently routinely got some information about it on different discussions and stages as recorded underneath:
I need to import messages from Pocomail to Gmail account. My framework setups are recorded underneath:
Working framework is Windows 7 expert
I accept that I have Web Traveler 9, Kaspersky 2011
Kindly Additionally Include: Working framework (for example Win XP):
Program and adaptation, you use to get to Gmail (for example Web Pilgrim 7 or Viewpoint 2003): Your antivirus programming (for example Norton 2007): Any augmentations, toolbars or modules which will assist me with moving Pocomail to Gmail account rapidly and in a split second:
Mechanized Answer for Move PocoMail to Gmail Record
From above we can without much of a stretch infer that an enormous number of clients need to be familiar with how to import Pocomail letter drop things to Gmail account. This should be possible with the assistance of Pen Drive Data Recovery Pocomail Converter programming which will give an immediate choice to do as such. One simply had to enter the record login certifications of resultant Gmail or G Suite account for example Username and Secret key. The utility gives separate choices to trade Pocomail to Gmail too Pocomail to G Suite account straightforwardly. Additionally, utilizing this application, you can move Pocomail to famous web clients, and record designs.
Free Download Pocomail to G Suite Movement Device:
Note: The preliminary form of this Pocomail to Gmail Relocation device Pen Drive Data Recovery just empower the clients to send out just initial 25 messages from every envelope of Pocomail letter box things. If you have any desire to send out all of your post box information from Pocomail organizers to Gmail account then you need to initiate this arrangement by buying the suitable permit as indicated by the necessities of the client.
#Pen Drive Data Recovery#USB Drive Data Recovery#Pen Drive Recovery#USB Drive Recovery#Pen Drive Recovery software#USB Drive Recovery software#Pen Drive Data Recovery software#USB Drive Data Recovery software
0 notes