#anyway don't run anything in powershell if you don't know what it is and check the domains
Explore tagged Tumblr posts
Text
A couple tips to (try to) prevent something like this happening, from someone who works with cybersec:
1) Docusign, which is the service impersonated here, is a real document signing service, but it's very common to see it impersonated in phishing and scam cases like this. So are Dropbox, Google Drive and other file sharing services; always double (or triple) check if the page looks at all odd.
Adding to the previous point: You can see page's url and domain (in this case the domain would be app[.]fastsigndocu[.]com) at the top of the page (if you've already clicked onto the page) or by hovering over the link with a mouse (if you're on your PC) - always check that the domain looks right! If you're not sure, google the service/web page first to check what the domain should be.
2.) If you're downloading something, always check the file type of what you're downloading! If the file is supposed to be a text/pdf document like in this case, it's name should NEVER end in ".exe" or ".bat". I suggest being careful of ".zip" and ".rar" files too, because it's very common to hide malware inside them. (And if you're purposefully downloading ".exe" files, please be careful of what you're downloading and from where)
3) Consider whether or not you actually need to stay constantly signed in to a service or site on your browser, or if you could sign in separately each time and log out when you're done (and clear your cookie data sometimes). I know, it's convenient to not have to sign in each time, but as seen here, it does mean that if your browser cookies are stolen, your MFA/2FA will probably not help you. If you don't use the service or website constantly/daily, you probably don't need to be signed in all the time.
Continuing point 3, the same goes double for any and all passwords saved in your browser data. There are malware going around right now that steal both your browser cookies AND the login data (meaning: any passwords saved in your browser), from any and all browsers the malware finds on your device. These are generally called "infostealers", but the one going around right now is called "Lumma stealer".
4) Related to point 3: Lumma stealer is currently being spread with fake Captcha (that "I'm not a robot" thing):
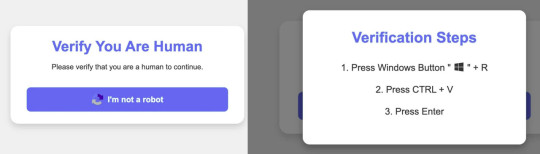
(image source: Finnish National Cybersecurity Center)
What happens is that if you click the button you see on the left, it copies a malicious Powershell script onto your clipboard and opens the pop-up you see on the right side of the image. Pressing the windows button + R opens the Windows "run command" window, to which Ctrl + V copies the script from your clipboard, and runs it when you press Enter (which then downloads and runs the actual malware file and anything saved in your browser data will be gone).
Never, EVER run ANYTHING in the run command window if you don't know exactly what it is and what it does.
Real Captcha will never ask you to do this. If you see a window like this, exit the page you were on immediately.
If you did run the script before realizing something is wrong, run a malware scan on the device, log out of everything you were signed in to on your browsers and change your passwords immediately.
5) Despite all of the above, do have 2FA/MFA activate whenever possible, because even if it might not help you if your session cookies are stolen, it will protect your account if your password is leaked some other way (such as from the service or website itself).
(And if anyone has any cybersec-related questions, feel free to ask!)
Someone accessed my Gmail 2 days ago, compromising my linked accounts like Twitter and YouTube. Here's how it happened, why I fell for it, and what you can learn to avoid making the same mistake:
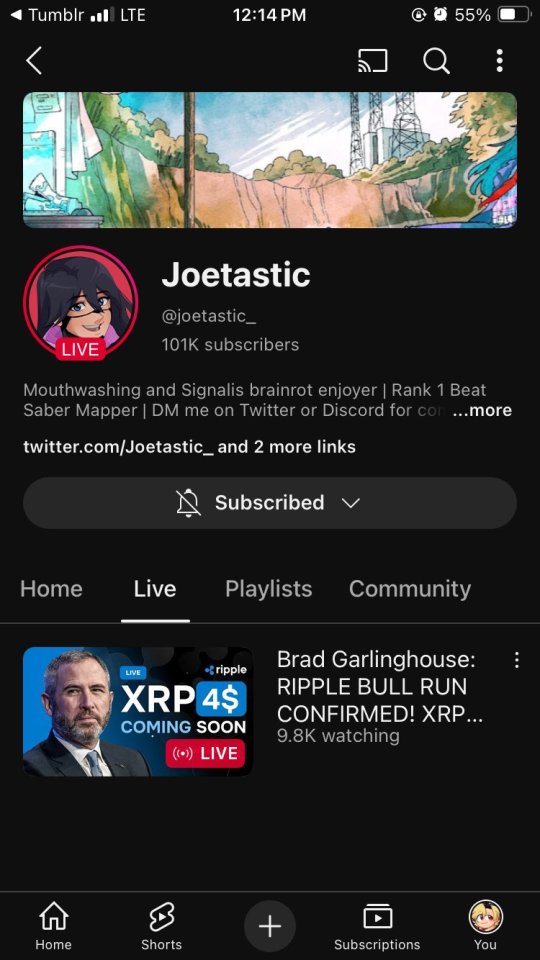
The scam I fell victim to was a cookie hijack. The hacker used malicious software to steal my browser cookies (stuff like autofill, auto sign in, etc), allowing them to sign in to my Gmail and other accounts, completely bypassing my 2FA and other security protocols.
A few days ago, I received a DM from @Rachael_Borrows, who claimed to be a manager at @Duolingo. The account seemed legitimate. It was verified, created in 2019, and had over 1k followers, consistent with other managers I’d seen at the time n I even did a Google search of this person and didnt find anything suspicious.
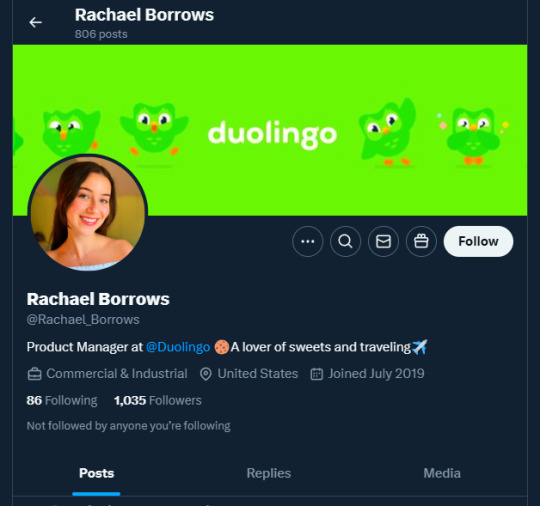
She claimed that @Duolingo wanted me to create a promo video, which got me excited and managed to get my guard down. After discussing I was asked to sign a contract and at app(.)fastsigndocu(.)com. If you see this link, ITS A SCAM! Do NOT download ANY files from this site.
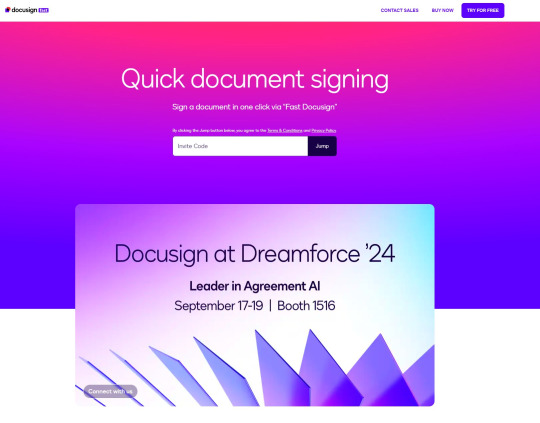
Unfortunately, I downloaded a file from the website, and it downloaded without triggering any firewall or antivirus warnings. Thinking it was just a PDF, I opened it. The moment I did, my console and Google Chrome flashed. That’s when I knew I was in trouble. I immediately did an antivirus scan and these were some of the programs it found that were added to my PC without me knowing:

The thing about cookie hijacking is that it completely bypasses 2FA which should have been my strongest line of defense. I was immediately signed out of all my accounts and within a minute, they changed everything: passwords, 2FA, phone, recovery emails, backup codes, etc.
I tried all methods but hit dead ends trying to recover them. Thankfully, my Discord wasn’t connected, so I alerted everyone I knew there. I also had an alternate account, @JLCmapping, managed by a friend, which I used to immediately inform @/TeamYouTube about the situation
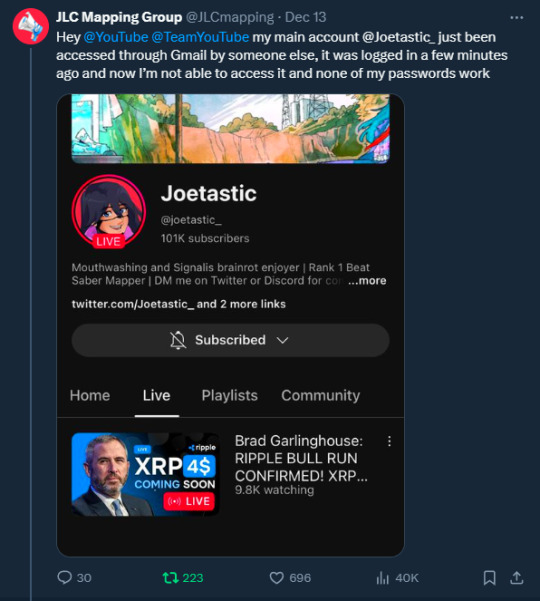
Meanwhile, the hackers turned my YouTube channel into a crypto channel and used my Twitter account to spam hundreds of messages, trying to use my image and reputation to scam more victims
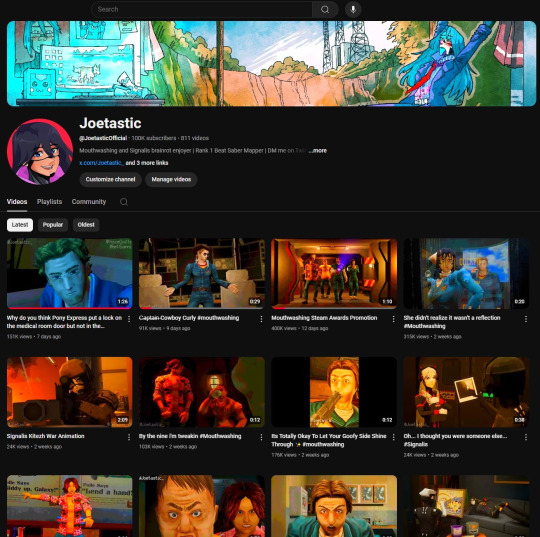
Thankfully, YouTube responded quickly and terminated the channel. Within 48 hours, they locked the hacker out of my Gmail and restored my access. They also helped me recover my channel, which has been renamed to JoetasticOfficial since Joetastic_ was no longer available.
Since then, I’ve taken several steps to secure my accounts and prevent this from happening again. This has been a wake-up call to me, and now I am more cautious around people online. I hope sharing it helps others avoid falling victim to similar attacks. (End)
(side note) Around this time, people also started to impersonate me on TikTok and YouTube. With my accounts terminated, anyone searching for "Joetastic" would only find the imposter's profiles. I’m unsure whether they are connected or if it’s just an unfortunate coincidence, but it made the situation even more stressful.
#cybersecurity#it ended up being more than a “couple” things#this is probably the longest comment on a post I've ever made#whoops#anyway don't run anything in powershell if you don't know what it is and check the domains
3K notes
·
View notes