Don't wanna be here? Send us removal request.
Text
How Blockchain Technology is Revolutionizing Cybersecurity
When I began my journey as a solution architect, I knew that the foundation of my expertise needed to be solid. One of the key milestones in shaping my career was enrolling in a cybersecurity training online program. The comprehensive curriculum and hands-on approach provided by the ACTE Institute opened new doors for me and gave me the confidence to tackle complex challenges in the tech space. This training not only equipped me with the necessary skills but also sparked my interest in how emerging technologies like blockchain could redefine cybersecurity.
Blockchain technology has become one of the most transformative innovations of the 21st century, fundamentally changing the way industries operate—and cybersecurity is no exception. As organizations face increasing threats from sophisticated cyberattacks, blockchain offers unique advantages that traditional systems often lack. Here's how blockchain is revolutionizing cybersecurity:

The Rise of Blockchain in Cybersecurity
Cybersecurity has always been about safeguarding data, networks, and systems from unauthorized access or attacks. However, with the exponential increase in the volume of data and the growing complexity of cyber threats, traditional solutions often fall short. Blockchain’s decentralized and tamper-proof architecture is becoming a game-changer in this context.
Unlike centralized systems, where a single point of failure can compromise the entire infrastructure, blockchain distributes data across a network of nodes. This decentralized approach ensures that even if one node is compromised, the integrity of the data remains intact. For cybersecurity professionals, this means creating systems that are inherently more secure and resilient to attacks.
Key Applications of Blockchain in Cybersecurity
1. Data Integrity and Protection
One of blockchain’s most significant contributions to cybersecurity is its ability to guarantee data integrity. By using cryptographic hashes, blockchain ensures that once data is written to the ledger, it cannot be altered without detection. This makes it nearly impossible for hackers to tamper with sensitive information, whether it's financial records, personal data, or intellectual property.
For example, in supply chain management, blockchain can track the provenance of goods and ensure that the data remains unaltered throughout its journey. Similarly, in healthcare, patient records can be securely stored and accessed only by authorized personnel, reducing the risk of breaches.
2. Securing Internet of Things (IoT) Devices
The rapid adoption of IoT devices has introduced a new frontier of cybersecurity challenges. These devices often have limited security protocols, making them prime targets for cyberattacks. Blockchain technology can address this issue by enabling secure and decentralized communication between devices.
Through blockchain, IoT devices can authenticate each other and establish secure communication channels without relying on a central authority. This reduces the likelihood of Distributed Denial-of-Service (DDoS) attacks and other vulnerabilities associated with IoT networks.
3. Identity Management
Traditional identity management systems often rely on centralized databases, which are attractive targets for hackers. Blockchain introduces a decentralized model for identity verification, where users have control over their data. This concept, known as Self-Sovereign Identity (SSI), allows individuals to store their credentials on a blockchain and share them securely with third parties when required.
By leveraging blockchain, organizations can reduce the risk of identity theft and fraud while enhancing user privacy. This is particularly relevant for industries like finance, healthcare, and e-commerce, where identity verification is critical.
4. Preventing DDoS Attacks
Distributed Denial-of-Service (DDoS) attacks are a significant threat to businesses, causing downtime and financial losses. Blockchain can mitigate this risk by decentralizing Domain Name System (DNS) infrastructure. Traditional DNS systems are centralized, making them vulnerable to attacks. By using blockchain, DNS records are distributed across a network, making it nearly impossible for attackers to target a single point of failure.
Blockchain Challenges in Cybersecurity
While blockchain holds immense potential for enhancing cybersecurity, it’s not without its challenges. Some of the key hurdles include:
Scalability: Blockchain networks often struggle to handle large volumes of transactions quickly, which can be a bottleneck for certain applications.
Energy Consumption: The consensus mechanisms used in blockchain, such as Proof of Work (PoW), are energy-intensive and may not be sustainable for all use cases.
Regulatory Compliance: Blockchain’s decentralized nature poses challenges for regulatory compliance, especially in industries with strict data protection laws.
Overcoming these challenges requires continued innovation and collaboration between blockchain developers and cybersecurity professionals.

Real-World Use Cases of Blockchain in Cybersecurity
Several organizations and industries are already leveraging blockchain to enhance their cybersecurity measures. Here are a few examples:
Financial Services: Blockchain-based solutions are being used to secure financial transactions, prevent fraud, and streamline Know Your Customer (KYC) processes.
Healthcare: Blockchain ensures the secure storage and sharing of electronic health records, reducing the risk of breaches and unauthorized access.
Supply Chain: Companies are adopting blockchain to verify the authenticity of products and prevent counterfeit goods from entering the market.
Government: Blockchain is being used to secure voting systems, ensuring transparency and reducing the risk of election fraud.
The Role of Cybersecurity Training in Embracing Blockchain
As a solution architect, my journey into the world of blockchain and cybersecurity would not have been possible without the foundational knowledge I gained from my training at the ACTE Institute. Their cybersecurity training in chennai equipped me with the practical skills and theoretical understanding necessary to navigate this complex field.
The training covered essential topics like cryptography, network security, and risk management, which laid the groundwork for understanding how blockchain technology could be applied to cybersecurity. The hands-on projects and real-world case studies provided me with the confidence to implement blockchain-based solutions in my current role.
The Future of Blockchain in Cybersecurity
The integration of blockchain technology into cybersecurity is still in its early stages, but the potential is undeniable. As organizations continue to adopt digital transformation initiatives, the demand for secure, scalable, and efficient solutions will only grow. Blockchain’s unique attributes position it as a critical tool in the fight against cyber threats.
However, realizing its full potential requires a collaborative effort between technology providers, cybersecurity experts, and regulatory bodies. By addressing the challenges and investing in education and training, we can unlock new possibilities and create a safer digital world.
Conclusion
Blockchain technology is revolutionizing the field of cybersecurity by addressing some of its most pressing challenges. From ensuring data integrity to securing IoT devices and preventing DDoS attacks, the applications of blockchain are vast and varied. For professionals looking to make an impact in this space, investing in comprehensive training programs like those offered by the ACTE Institute can be a game-changer.
Reflecting on my journey, I can confidently say that my cybersecurity training was instrumental in helping me land my current role and understand the transformative power of blockchain. With the right skills and knowledge, anyone can be a part of this exciting revolution
#ai#artificialintelligence#digitalmarketing#marketingstrategy#database#adtech#machinelearning#cybersecurity
0 notes
Text
Cloud-Native Security: Transforming Cyber Defense in a Multi-Cloud World
Cloud-Native Security: Transforming Cyber Defense in a Multi-Cloud World
As a solution architect, my work often involves designing and implementing robust systems in increasingly complex cloud environments. Recently, as I enhanced my expertise through cloud computing training online, I encountered the critical importance of cloud-native security in safeguarding multi-cloud ecosystems. The growing reliance on multi-cloud infrastructures demands a fundamental transformation in how we approach cyber defense.

What is Cloud-Native Security?
Cloud-native security refers to a framework tailored for cloud environments, where applications and services are designed, built, and deployed in the cloud. Unlike traditional security models, which focus on perimeter defenses, cloud-native security emphasizes integrating protection into every layer of the cloud infrastructure. Key principles include:
1. Microservices Security: Protecting each service within a distributed architecture.
2. Zero Trust: Assuming no inherent trust within the network, requiring strict verification.
3. Automation and Scalability: Leveraging automated tools to address dynamic cloud environments.
4. Integration Across CI/CD Pipelines: Embedding security into development workflows.
Why Multi-Cloud Adoption is Changing the Game
Organizations increasingly adopt multi-cloud strategies, leveraging the strengths of various providers like AWS, Azure, and Google Cloud. This approach offers flexibility and redundancy but introduces unique challenges:
● Complexity: Managing security policies across multiple platforms can be overwhelming.
● Inconsistency: Different providers have distinct tools and security configurations.
● Increased Attack Surface: More platforms mean more entry points for attackers.
Key Challenges in Cloud-Native Security
1. Visibility: Monitoring and managing assets spread across multiple clouds.
2. Compliance: Ensuring adherence to diverse regulatory requirements across regions.
3. Data Security: Protecting sensitive information during transfer, storage, and processing.
4. Misconfigurations: A common cause of breaches due to human error or lack of expertise.
Strategies for Cloud-Native Security
To address these challenges, organizations must adopt proactive and innovative strategies:
1. Unified Security Posture: Deploy centralized security tools to monitor and manage multi-cloud environments effectively.
2. Automation and AI: Utilize AI-driven solutions to detect anomalies, automate threat responses, and reduce manual workloads.
3. Identity and Access Management (IAM): Enforce least-privilege access across users, applications, and systems.
4. Shift-Left Security: Integrate security measures early in the development lifecycle.
5. Continuous Monitoring: Employ real-time monitoring tools to identify and address vulnerabilities swiftly.
The Role of Training and ExpertiseWorking with multi-cloud infrastructures demands continuous learning and adaptation.

Training programs, such as cloud computing training in Bangalore, equip professionals with the knowledge and skills to navigate complex cloud ecosystems. These program emphasize hands-on experience with the latest tools and frameworks, empowering architects and engineers to build secure systems tailored to their organization's needs.
Real-World Implications
Organizations that prioritize cloud-native security are better positioned to:
● Mitigate Breaches: Prevent unauthorized access and data leaks.
● Ensure Business Continuity: Minimize downtime caused by attacks.
● Achieve Compliance: Meet regulatory standards across industries and regions.
● Drive Innovation: Focus on growth without being hindered by security concerns.
Conclusion
Cloud-native security is no longer optional; it is essential in today’s multi-cloud world. As I’ve learned through my professional experiences and training, the journey toward robust cloud security involves both strategic planning and technical expertise. By leveraging resources like cloud computing training in Bangalore, professionals can stay ahead of evolving threats and contribute to creating resilient, secure infrastructures. The future of cybersecurity lies in our ability to adapt and innovate, ensuring a safer digital ecosystem for all.
0 notes
Text
Common Myths About Data Analytics and the Truth Behind Them
As a solution architect, my journey has been deeply intertwined with the evolving landscape of data analytics. Throughout this journey, I've encountered numerous misconceptions that often deter organizations from fully leveraging the power of data. Enrolling in data analytics training online at ACTE Institute was a pivotal decision that equipped me with the knowledge to debunk these myths and harness data analytics effectively.
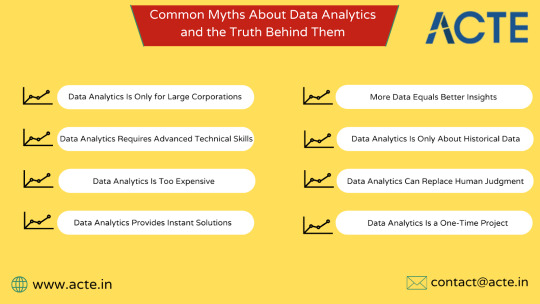
Myth 1: Data Analytics Is Only for Large Corporations
A prevalent belief is that data analytics is a domain exclusive to large enterprises with substantial resources. This misconception leads smaller businesses to shy away from adopting data-driven strategies.
Truth: Data analytics is scalable and accessible to businesses of all sizes. With the advent of user-friendly tools and cloud-based solutions, even small and medium-sized enterprises can implement data analytics to gain valuable insights. ACTE's training emphasized practical approaches, demonstrating that with the right tools and strategies, any organization can benefit from data analytics.
Myth 2: Data Analytics Requires Advanced Technical Skills
Many assume that a deep technical background is a prerequisite for engaging in data analytics, which can be intimidating for professionals from non-technical fields.
Truth: Modern data analytics tools are designed to be intuitive and user-friendly, lowering the barrier to entry. During my training at ACTE, I learned that with proper guidance and practice, individuals from diverse professional backgrounds can acquire the necessary skills to perform effective data analysis.
Myth 3: Data Analytics Is Too Expensive
The perceived high cost of data analytics solutions often discourages organizations from investing in them.
Truth: There are numerous cost-effective and even free data analytics tools available today. Open-source platforms like R and Python, along with affordable software solutions, make data analytics financially accessible. ACTE's curriculum included training on these tools, highlighting how organizations can implement data analytics without significant financial burdens.
Myth 4: Data Analytics Provides Instant Solutions
Some believe that data analytics offers immediate answers to complex business questions.
Truth: Data analytics is a process that involves data collection, cleaning, analysis, and interpretation. It requires time and iterative refinement to yield meaningful insights. ACTE's training instilled in me the importance of patience and diligence in the analytical process, ensuring that conclusions are well-founded and actionable.
Myth 5: More Data Equals Better Insights
There's a common assumption that accumulating vast amounts of data will automatically lead to better insights.
Truth: The quality of data is far more critical than quantity. Focusing on relevant and accurate data is essential for meaningful analysis. ACTE emphasized the importance of data governance and the need to prioritize data quality to derive valuable insights.
Myth 6: Data Analytics Is Only About Historical Data
Many view data analytics as a tool solely for examining past performance.
Truth: While historical data analysis is fundamental, data analytics also encompasses predictive and prescriptive analytics, which forecast future trends and recommend actions. ACTE's comprehensive training covered these advanced aspects, enabling me to apply analytics proactively rather than reactively.
Myth 7: Data Analytics Can Replace Human Judgment
There's a fear that data analytics might supplant human decision-making.
Truth: Data analytics is a tool that supports and enhances human judgment but does not replace it. The insights derived from data require contextual understanding and domain expertise to be effectively applied. ACTE highlighted the symbiotic relationship between data-driven insights and human intuition in decision-making processes.
Myth 8: Data Analytics Is a One-Time Project
Some organizations treat data analytics as a one-off initiative rather than an ongoing process.
Truth: Data analytics should be an integral part of an organization's continuous improvement strategy. Regular analysis allows businesses to stay agile and responsive to changing dynamics. ACTE's training reinforced the importance of embedding data analytics into the organizational culture for sustained success.
The Transformative Role of ACTE Institute
Myth-busting and skill acquisition in data analytics were significantly enhanced by the training I received at ACTE Institute. Their structured and practical approach demystified complex concepts and provided hands-on experience with industry-relevant tools. This training was instrumental in advancing my career and effectiveness as a solution architect.
Real-World Applications of Data Analytics
Implementing data analytics has led to tangible benefits in various projects:
Enhanced Operational Efficiency: By analyzing workflow data, we identified bottlenecks and streamlined processes, leading to increased productivity.
Improved Customer Insights: Data analytics enabled a deeper understanding of customer preferences, allowing for personalized marketing strategies that boosted engagement.
Risk Management: Predictive analytics facilitated the identification of potential risks, enabling proactive mitigation strategies.
Conclusion
Dispelling these common myths is crucial for organizations aiming to leverage data analytics effectively. The comprehensive training provided by ACTE Institute was pivotal in enhancing my understanding and application of data analytics. For professionals seeking to deepen their expertise, programs like data analytics training in Hyderabad offer valuable opportunities to develop practical skills and knowledge.
Embracing the realities of data analytics empowers organizations to make informed decisions, drive innovation, and maintain a competitive edge in today's data-driven world.
#adtech#artificialintelligence#digitalmarketing#database#ai#marketingstrategy#machinelearning#cybersecurity
0 notes
Text
The Impact of 5G on Network Security: What You Need to Know
Embarking on my journey as a solution architect, I quickly realized the growing significance of staying ahead in the realm of cybersecurity. To fortify my knowledge, I enrolled in a cybersecurity training online program at ACTE Institute. This decision proved to be the cornerstone of my professional growth, equipping me with the expertise necessary to tackle challenges in advanced technologies like 5G.
The rollout of 5G networks represents a monumental leap in connectivity, offering unparalleled speed, low latency, and the capacity to connect millions of devices simultaneously. However, with these advancements come profound security challenges that must be addressed to fully harness the potential of 5G.

What Makes 5G Unique?
Unlike its predecessors, 5G is not merely an upgrade in speed; it’s a transformative technology designed to support diverse applications, such as:
IoT Ecosystems: Connecting billions of devices, from smart appliances to industrial equipment.
Enhanced Mobile Broadband: Delivering ultra-fast internet for seamless streaming and communication.
Critical Communications: Enabling real-time responses for applications like autonomous vehicles and remote surgeries.
While these innovations are groundbreaking, they introduce complex vulnerabilities that expand the attack surface for potential cyber threats.
Key Security Challenges in 5G
1. Broader Attack Surface
With the integration of IoT and edge computing, 5G networks host a multitude of endpoints, each presenting a potential entry point for malicious actors. Securing this vast and distributed architecture is a significant challenge.
2. Network Slicing Vulnerabilities
5G allows for network slicing, where virtual networks operate independently on shared infrastructure. While this enhances flexibility, it also raises concerns about isolation breaches and unauthorized access between slices.
3. Supply Chain Risks
The global supply chain for 5G infrastructure components increases the risk of tampering and compromise during manufacturing or deployment.
4. Increased Dependency on Software
The software-driven nature of 5G networks introduces risks related to bugs, misconfigurations, and vulnerabilities that can be exploited by attackers.
How to Address 5G Security Challenges
1. Adopt Zero Trust Principles
Zero trust architectures ensure that every device and user is verified before gaining access to the network. Continuous monitoring and strict authentication protocols are essential to mitigate risks.
2. Secure IoT Devices
Manufacturers must prioritize security in IoT devices by implementing strong encryption, regular updates, and robust authentication mechanisms.
3. Enhance Collaboration
Governments, industry leaders, and technology providers must work together to establish unified security standards and share threat intelligence to counteract emerging risks.
4. Utilize Artificial Intelligence (AI) and Machine Learning (ML)
AI and ML can help detect anomalies, predict potential threats, and automate responses, thereby enhancing the overall security posture of 5G networks.
Real-World Applications of 5G and Their Security Implications
1. Smart Cities
5G enables smart city initiatives, such as intelligent traffic systems and connected infrastructure. However, breaches in these systems could disrupt critical services and endanger public safety.
2. Healthcare
Remote surgeries, telemedicine, and real-time health monitoring are revolutionized by 5G. Protecting patient data and ensuring the integrity of these systems are vital to maintaining trust and safety.
3. Autonomous Vehicles
The real-time communication capabilities of 5G are critical for self-driving cars. Securing these communication channels is essential to prevent accidents and malicious interference.
4. Industrial Automation
5G facilitates advanced automation in industries. Cybersecurity measures are required to safeguard intellectual property and prevent disruptions in production.

Reflecting on My Training and Experience
When I look back at my professional journey, the cybersecurity training I received at ACTE Institute in Bangalore stands out as a defining moment. This training not only deepened my understanding of network security but also provided hands-on experience in addressing real-world scenarios. From exploring advanced encryption techniques to implementing zero trust frameworks, the program laid the groundwork for my success as a solution architect.
Without this training, navigating the complexities of technologies like 5G would have been an uphill battle. It reinforced my ability to design robust security solutions, making me an indispensable asset to my organization.
Conclusion
The introduction of 5G networks signifies a new era of connectivity and innovation. While the technology offers transformative benefits, it also demands a proactive approach to security. By addressing its unique vulnerabilities and fostering collaboration among stakeholders, we can ensure a secure and resilient future.
For professionals aiming to excel in this dynamic field, investing in comprehensive training programs is imperative. My experience with ACTE’s cybersecurity training in Bangalore has been a game-changer, enabling me to embrace challenges and contribute meaningfully to the evolving landscape of network security. The knowledge and skills I gained continue to shape my career, proving that the right training can unlock endless opportunities.
#adtech#digitalmarketing#marketingstrategy#artificialintelligence#ai#machinelearning#cybersecurity#database
0 notes
Text
Data Warehousing vs. Data Lakes: Choosing the Right Approach for Your Organization
As a solution architect, my journey into data management has been shaped by years of experience and focused learning. My turning point was the data analytics training online, I completed at ACTE Institute. This program gave me the clarity and practical knowledge I needed to navigate modern data architectures, particularly in understanding the key differences between data warehousing and data lakes.
Both data warehousing and data lakes have become critical components of the data strategies for many organizations. However, choosing between them—or determining how to integrate both—can significantly impact how an organization manages and utilizes its data.
What is a Data Warehouse?
Data warehouses are specialized systems designed to store structured data. They act as centralized repositories where data from multiple sources is aggregated, cleaned, and stored in a consistent format. Businesses rely on data warehouses for generating reports, conducting historical analysis, and supporting decision-making processes.
Data warehouses are highly optimized for running complex queries and generating insights. This makes them a perfect fit for scenarios where the primary focus is on business intelligence (BI) and operational reporting.
Features of Data Warehouses:
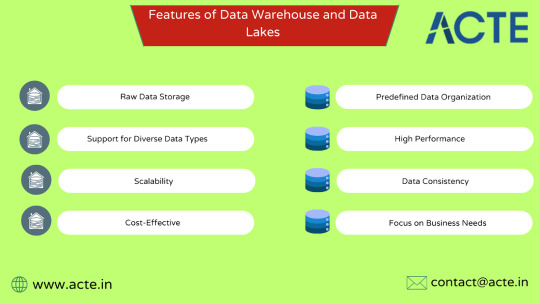
Predefined Data Organization: Data warehouses rely on schemas that structure the data before it is stored, making it easier to analyze later.
High Performance: Optimized for query processing, they deliver quick results for detailed analysis.
Data Consistency: By cleansing and standardizing data from multiple sources, warehouses ensure consistent and reliable insights.
Focus on Business Needs: These systems are designed to support the analytics required for day-to-day business decisions.
What is a Data Lake?
Data lakes, on the other hand, are designed for flexibility and scalability. They store vast amounts of raw data in its native format, whether structured, semi-structured, or unstructured. This approach is particularly valuable for organizations dealing with large-scale analytics, machine learning, and real-time data processing.
Unlike data warehouses, data lakes don’t require data to be structured before storage. Instead, they use a schema-on-read model, where the data is organized only when it’s accessed for analysis.
Features of Data Lakes:
Raw Data Storage: Data lakes retain data in its original form, providing flexibility for future analysis.
Support for Diverse Data Types: They can store everything from structured database records to unstructured video files or social media content.
Scalability: Built to handle massive amounts of data, data lakes are ideal for organizations with dynamic data needs.
Cost-Effective: Data lakes use low-cost storage options, making them an economical solution for large datasets.
Understanding the Differences
To decide which approach works best for your organization, it’s essential to understand the key differences between data warehouses and data lakes:
Data Structure: Data warehouses store data in a structured format, whereas data lakes support structured, semi-structured, and unstructured data.
Processing Methodology: Warehouses follow a schema-on-write model, while lakes use a schema-on-read approach, offering greater flexibility.
Purpose: Data warehouses are designed for business intelligence and operational reporting, while data lakes excel at advanced analytics and big data processing.
Cost and Scalability: Data lakes tend to be more cost-effective, especially when dealing with large, diverse datasets.
How to Choose the Right Approach
Choosing between a data warehouse and a data lake depends on your organization's goals, data strategy, and the type of insights you need.
When to Choose a Data Warehouse:
Your organization primarily deals with structured data that supports reporting and operational analysis.
Business intelligence is at the core of your decision-making process.
You need high-performance systems to run complex queries efficiently.
Data quality, consistency, and governance are critical to your operations.
When to Choose a Data Lake:
You work with diverse data types, including unstructured and semi-structured data.
Advanced analytics, machine learning, or big data solutions are part of your strategy.
Scalability and cost-efficiency are essential for managing large datasets.
You need a flexible solution that can adapt to emerging data use cases.
Combining Data Warehouses and Data Lakes
In many cases, organizations find value in adopting a hybrid approach that combines the strengths of data warehouses and data lakes. For example, raw data can be ingested into a data lake, where it’s stored until it’s needed for specific analytical use cases. The processed and structured data can then be moved to a data warehouse for BI and reporting purposes.
This integrated strategy allows organizations to benefit from the scalability of data lakes while retaining the performance and reliability of data warehouses.
My Learning Journey with ACTE Institute
During my career, I realized the importance of mastering these technologies to design efficient data architectures. The data analytics training in Hyderabad program at ACTE Institute provided me with a hands-on understanding of both data lakes and data warehouses. Their comprehensive curriculum, coupled with practical exercises, helped me bridge the gap between theoretical knowledge and real-world applications.
The instructors at ACTE emphasized industry best practices and use cases, enabling me to apply these concepts effectively in my projects. From understanding how to design scalable data lakes to optimizing data warehouses for performance, every concept I learned has played a vital role in my professional growth.
Final Thoughts
Data lakes and data warehouses each have unique strengths, and the choice between them depends on your organization's specific needs. With proper planning and strategy, it’s possible to harness the potential of both systems to create a robust and efficient data ecosystem.
My journey in mastering these technologies, thanks to the guidance of ACTE Institute, has not only elevated my career but also given me the tools to help organizations make informed decisions in their data strategies. Whether you're working with structured datasets or diving into advanced analytics, understanding these architectures is crucial for success in today’s data-driven world.
#machinelearning#artificialintelligence#digitalmarketing#marketingstrategy#adtech#database#cybersecurity#ai
0 notes
Text
Vendor Lock-in or Vendor Partnership: Navigating the New Cloud Ecosystem
As a solution architect, my journey through the evolving landscape of cloud computing has been both challenging and rewarding. The comprehensive cloud computing training online provided by ACTE Institute played a pivotal role in shaping my understanding and expertise in this domain. This training equipped me with the knowledge to navigate complex cloud ecosystems and make informed decisions that align with organizational goals.
In today's digital era, cloud computing has become the backbone of modern enterprises, offering scalability, flexibility, and cost-efficiency. However, with these advantages comes the critical consideration of how organizations engage with their cloud service providers. The debate between vendor lock-in and vendor partnership is central to this discussion, as it influences an organization's agility, innovation potential, and long-term success.

Understanding Vendor Lock-in
Vendor lock-in refers to a situation where a customer becomes dependent on a single cloud provider's products and services, making it challenging to switch to another provider without incurring substantial costs or facing technical difficulties. This dependency can arise from the use of proprietary technologies, unique service offerings, or data formats that are not easily transferable.
The implications of vendor lock-in are significant. Organizations may find themselves constrained by the limitations of their chosen provider, unable to leverage innovative solutions from other vendors. Additionally, they may face escalating costs, as the lack of competition can lead to unfavorable pricing models. The risk of service disruptions also looms large, as any issues with the provider can directly impact the organization's operations.
Embracing Vendor Partnership
On the other hand, viewing the relationship with cloud providers as a partnership can yield numerous benefits. A vendor partnership is characterized by collaboration, mutual trust, and shared objectives. In such a relationship, the provider becomes more than just a service supplier; they become a strategic ally invested in the organization's success.
This partnership approach fosters innovation, as both parties work together to develop customized solutions that drive business growth. It also enhances flexibility, allowing organizations to adapt to changing market dynamics swiftly. Moreover, a strong partnership can lead to better support and service quality, as the provider is more attuned to the organization's specific needs and challenges.
Strategies to Mitigate Vendor Lock-in
While the benefits of vendor partnerships are clear, it's essential to implement strategies that mitigate the risks associated with vendor lock-in. Here are some approaches that have proven effective in my experience:
Adopt Open Standards and Interoperability: Utilizing open-source technologies and adhering to industry standards can reduce dependency on a single provider. This approach ensures that applications and data are compatible across different platforms, facilitating easier migration if needed. citeturn0search0
Implement a Multi-Cloud Strategy: Distributing workloads across multiple cloud providers can prevent over-reliance on one vendor. This strategy not only mitigates the risk of lock-in but also allows organizations to leverage the unique strengths of different providers.
Regularly Review Contracts and SLAs: It's crucial to negotiate terms that provide flexibility and protect the organization's interests. Regular reviews ensure that the services align with evolving business needs and market conditions.
Invest in Staff Training and Development: Equipping the team with diverse cloud skills reduces reliance on vendor-specific solutions. Training programs, such as those offered by ACTE Institute, can broaden the team's expertise and enhance their ability to manage multi-cloud environments effectively.

The Role of ACTE Institute in My Professional Journey
Reflecting on my career, the cloud computing training in Bangalore provided by ACTE Institute stands out as a cornerstone of my professional development. The curriculum was meticulously designed to cover both foundational concepts and advanced topics, ensuring a holistic understanding of cloud ecosystems.
The instructors, with their extensive industry experience, provided practical insights that bridged the gap between theory and real-world application. The hands-on projects and case studies enabled me to apply the learned concepts, fostering a deeper comprehension and honing my problem-solving skills.
Moreover, the emphasis on emerging trends and best practices prepared me to navigate the complexities of vendor relationships effectively. The knowledge gained empowered me to establish strategic partnerships with cloud providers, leveraging their capabilities while safeguarding my organization's autonomy.
Conclusion
Navigating the new cloud ecosystem requires a delicate balance between leveraging vendor capabilities and maintaining organizational independence. By understanding the dynamics of vendor lock-in and embracing strategic partnerships, organizations can harness the full potential of cloud computing.
My journey, enriched by the training at ACTE Institute, has equipped me with the skills and insights to make informed decisions in this realm. As cloud technologies continue to evolve, staying abreast of best practices and fostering collaborative vendor relationships will be pivotal in driving sustained success.
#adtech#digitalmarketing#artificialintelligence#marketingstrategy#ai#machinelearning#database#cybersecurity
0 notes
Text
The Future of Multi-Cloud Architectures: Benefits and Challenges
When I started my journey as a solution architect, one of the most transformative decisions I made was enrolling in a cloud computing training online program at ACTE Institute. This training laid the foundation for my understanding of multi-cloud architectures and their increasing relevance in today’s dynamic IT landscape. Without this specialized training, stepping into my current role would have been incredibly challenging, if not impossible.
The rapid adoption of cloud computing has transformed how organizations operate, enabling scalability, flexibility, and cost-efficiency. As businesses grow, the need to diversify and adopt multi-cloud strategies has become paramount. Multi-cloud architectures allow organizations to leverage the strengths of multiple cloud providers, reducing dependency on a single vendor and ensuring greater resilience. However, these architectures come with their own set of challenges, which must be carefully navigated to maximize their potential.

What is a Multi-Cloud Architecture?
Multi-cloud refers to the use of multiple cloud computing services from different providers within a single heterogeneous architecture. Unlike hybrid cloud—which combines private and public clouds—multi-cloud involves leveraging multiple public cloud services to distribute workloads, optimize costs, and ensure redundancy.
Key characteristics of multi-cloud architectures include:
Flexibility: Organizations can select the best cloud services for specific workloads.
Redundancy: Ensures high availability and disaster recovery by distributing data across multiple providers.
Cost Optimization: Enables businesses to negotiate better pricing and avoid vendor lock-in.
Benefits of Multi-Cloud Architectures
1. Avoiding Vendor Lock-In
Relying on a single cloud provider can lead to dependency, limiting an organization’s flexibility and negotiating power. Multi-cloud strategies mitigate this risk by diversifying resources across providers.
2. Enhanced Resilience and Redundancy
By leveraging multiple cloud providers, organizations can ensure continuous service availability. In the event of a failure with one provider, workloads can seamlessly shift to another, minimizing downtime.
3. Optimized Performance
Different cloud providers excel in specific areas. A multi-cloud strategy allows organizations to choose the best-in-class services for their unique requirements, ensuring optimal performance.
4. Regulatory Compliance
Operating in multiple regions often involves adhering to varying regulatory requirements. Multi-cloud architectures enable businesses to use providers that meet specific regional compliance standards.
5. Cost Efficiency
Multi-cloud strategies allow businesses to optimize costs by choosing the most cost-effective solutions for specific workloads and taking advantage of pricing competition among providers.
Challenges of Multi-Cloud Architectures
1. Increased Complexity
Managing multiple cloud environments requires robust orchestration and monitoring tools. The complexity of maintaining consistent performance, security, and compliance across providers can be overwhelming.
2. Data Security and Compliance
Storing and processing data across multiple platforms increases the risk of breaches and compliance violations. Ensuring data protection and adhering to regulatory requirements necessitates a comprehensive security strategy.
3. Interoperability Issues
Different cloud providers often use proprietary technologies, making it challenging to ensure seamless interoperability between platforms.
4. Skill Requirements
Adopting a multi-cloud strategy demands expertise in various cloud platforms. Organizations must invest in upskilling their teams or hiring specialists to manage these environments effectively.
5. Cost Management
While multi-cloud can optimize costs, the lack of centralized cost monitoring tools can lead to inefficiencies. Organizations need to implement robust cost management practices to avoid overspending.
Key Strategies for Implementing Multi-Cloud Architectures
1. Define Clear Objectives
Before adopting a multi-cloud strategy, organizations should identify their goals, whether it’s cost optimization, improved performance, or enhanced resilience.
2. Invest in Training and Upskilling
Training programs, such as the one I completed at ACTE Institute, are crucial for equipping professionals with the knowledge and skills needed to manage multi-cloud environments effectively.
3. Leverage Cloud Management Tools
Cloud management platforms enable organizations to monitor and orchestrate resources across multiple providers, ensuring consistency and efficiency.
4. Focus on Security
Implementing a zero-trust architecture, encrypting data, and conducting regular security audits are essential for maintaining data integrity and compliance.
5. Plan for Interoperability
Organizations should prioritize using open standards and APIs to facilitate seamless integration and interoperability between different cloud platforms.

Real-World Use Cases of Multi-Cloud Architectures
1. Disaster Recovery and Business Continuity
Organizations can ensure uninterrupted service delivery by distributing workloads across multiple cloud providers. In the event of a failure, critical systems can quickly shift to a secondary provider.
2. Global Reach and Regional Compliance
Multi-cloud architectures allow businesses to operate in multiple regions while adhering to local regulatory requirements. For instance, data can be stored in compliance with GDPR in Europe and HIPAA in the United States.
3. Optimized Application Performance
By leveraging the strengths of different providers, businesses can optimize performance for specific applications. For example, a latency-sensitive application might run on a provider known for low-latency services, while data storage might be handled by a cost-efficient provider.
4. E-commerce Platforms
E-commerce companies often use multi-cloud strategies to handle traffic spikes during sales events. This ensures scalability and reliability, even during peak demand periods.
My Journey and the Role of Training
Reflecting on my career, the cloud computing training I received at ACTE Institute in Bangalore was instrumental in shaping my understanding of multi-cloud architectures. The course provided hands-on experience with leading cloud platforms, teaching me how to design, implement, and manage complex multi-cloud environments.
The training also emphasized practical applications, such as configuring disaster recovery solutions and optimizing workloads across providers. This knowledge has been invaluable in my role, enabling me to deliver innovative solutions that drive business success.
Conclusion
The future of multi-cloud architectures is undeniably promising. As organizations continue to embrace digital transformation, the flexibility, resilience, and performance benefits of multi-cloud strategies will play a critical role in shaping the IT landscape. However, navigating the challenges requires a proactive approach, robust tools, and skilled professionals.
For anyone aspiring to excel in this field, investing in comprehensive training is essential. My experience with ACTE’s cloud computing training in Bangalore was a game-changer, equipping me with the skills and confidence to thrive in this dynamic industry. With the right knowledge and tools, the possibilities in the world of multi-cloud architectures are truly limitless.
#machinelearning#artificialintelligence#digitalmarketing#adtech#marketingstrategy#cybersecurity#ai#database
0 notes
Text
The Impact of 5G on Network Security: What You Need to Know
Embarking on my journey as a solution architect, I quickly realized the growing significance of staying ahead in the realm of cybersecurity. To fortify my knowledge, I enrolled in a cybersecurity training online program at ACTE Institute. This decision proved to be the cornerstone of my professional growth, equipping me with the expertise necessary to tackle challenges in advanced technologies like 5G.
The rollout of 5G networks represents a monumental leap in connectivity, offering unparalleled speed, low latency, and the capacity to connect millions of devices simultaneously. However, with these advancements come profound security challenges that must be addressed to fully harness the potential of 5G.

What Makes 5G Unique?
Unlike its predecessors, 5G is not merely an upgrade in speed; it’s a transformative technology designed to support diverse applications, such as:
IoT Ecosystems: Connecting billions of devices, from smart appliances to industrial equipment.
Enhanced Mobile Broadband: Delivering ultra-fast internet for seamless streaming and communication.
Critical Communications: Enabling real-time responses for applications like autonomous vehicles and remote surgeries.
While these innovations are groundbreaking, they introduce complex vulnerabilities that expand the attack surface for potential cyber threats.
Key Security Challenges in 5G
1. Broader Attack Surface
With the integration of IoT and edge computing, 5G networks host a multitude of endpoints, each presenting a potential entry point for malicious actors. Securing this vast and distributed architecture is a significant challenge.
2. Network Slicing Vulnerabilities
5G allows for network slicing, where virtual networks operate independently on shared infrastructure. While this enhances flexibility, it also raises concerns about isolation breaches and unauthorized access between slices.
3. Supply Chain Risks
The global supply chain for 5G infrastructure components increases the risk of tampering and compromise during manufacturing or deployment.
4. Increased Dependency on Software
The software-driven nature of 5G networks introduces risks related to bugs, misconfigurations, and vulnerabilities that can be exploited by attackers.
How to Address 5G Security Challenges
1. Adopt Zero Trust Principles
Zero trust architectures ensure that every device and user is verified before gaining access to the network. Continuous monitoring and strict authentication protocols are essential to mitigate risks.
2. Secure IoT Devices
Manufacturers must prioritize security in IoT devices by implementing strong encryption, regular updates, and robust authentication mechanisms.
3. Enhance Collaboration
Governments, industry leaders, and technology providers must work together to establish unified security standards and share threat intelligence to counteract emerging risks.
4. Utilize Artificial Intelligence (AI) and Machine Learning (ML)
AI and ML can help detect anomalies, predict potential threats, and automate responses, thereby enhancing the overall security posture of 5G networks.
Real-World Applications of 5G and Their Security Implications
1. Smart Cities
5G enables smart city initiatives, such as intelligent traffic systems and connected infrastructure. However, breaches in these systems could disrupt critical services and endanger public safety.
2. Healthcare
Remote surgeries, telemedicine, and real-time health monitoring are revolutionized by 5G. Protecting patient data and ensuring the integrity of these systems are vital to maintaining trust and safety.
3. Autonomous Vehicles
The real-time communication capabilities of 5G are critical for self-driving cars. Securing these communication channels is essential to prevent accidents and malicious interference.
4. Industrial Automation
5G facilitates advanced automation in industries. Cybersecurity measures are required to safeguard intellectual property and prevent disruptions in production.

Reflecting on My Training and Experience
When I look back at my professional journey, the cybersecurity training I received at ACTE Institute in Bangalore stands out as a defining moment. This training not only deepened my understanding of network security but also provided hands-on experience in addressing real-world scenarios. From exploring advanced encryption techniques to implementing zero trust frameworks, the program laid the groundwork for my success as a solution architect.
Without this training, navigating the complexities of technologies like 5G would have been an uphill battle. It reinforced my ability to design robust security solutions, making me an indispensable asset to my organization.
Conclusion
The introduction of 5G networks signifies a new era of connectivity and innovation. While the technology offers transformative benefits, it also demands a proactive approach to security. By addressing its unique vulnerabilities and fostering collaboration among stakeholders, we can ensure a secure and resilient future.
For professionals aiming to excel in this dynamic field, investing in comprehensive training programs is imperative. My experience with ACTE’s cybersecurity training in Bangalore has been a game-changer, enabling me to embrace challenges and contribute meaningfully to the evolving landscape of network security. The knowledge and skills I gained continue to shape my career, proving that the right training can unlock endless opportunities.
#adtech#artificialintelligence#digitalmarketing#marketingstrategy#ai#machinelearning#database#cybersecurity
0 notes
Text
Python for Data Analytics: A Solution Architect’s Perspective
As a solution architect, my career has been centered on designing robust, scalable systems tailored to meet diverse business needs. Over the years, I’ve worked on projects spanning various domains—cloud computing, infrastructure optimization, and application development. However, the growing emphasis on data-driven decision-making reshaped my perspective. Organizations now rely heavily on extracting actionable insights from their data, which made me realize that understanding and leveraging data analytics is no longer optional.
This journey into the world of data analytics began with an enriching data analytics training online program. This training not only introduced me to foundational concepts but also provided a structured pathway to mastering Python for data analytics—a skill I now consider indispensable for any tech professional.
Why Python for Data Analytics?
Python has emerged as a game-changer in the data analytics space, and for good reasons:
Simplicity and Versatility: Python’s straightforward syntax makes it accessible for beginners, while its versatility allows professionals to handle complex tasks seamlessly.
Extensive Libraries: Libraries like Pandas, NumPy, Matplotlib, and Seaborn enable efficient data manipulation, visualization, and analysis. For advanced analytics, Scikit-learn and TensorFlow are the go-to tools for machine learning and predictive modeling.
Integration Capabilities: Python integrates effortlessly with other technologies and platforms, making it a preferred choice for end-to-end data solutions.
Community Support: With its vast global community, Python ensures you’ll always find support, tutorials, and updates to keep pace with the ever-evolving analytics landscape.
My First Steps with Python for Data Analytics
My initial foray into Python for data analytics was both exciting and challenging. While I was familiar with programming concepts, understanding the nuances of data manipulation required a shift in mindset. The training program I enrolled in emphasized hands-on projects, which was instrumental in solidifying my understanding.
One of my first projects involved analyzing system performance metrics. Using Python, I could process large datasets to identify patterns and anomalies in server utilization. Here’s what made Python stand out:
Data Manipulation with Pandas: I used Pandas to clean and restructure the data. Its DataFrame object made it easy to filter, sort, and aggregate information.
Visualization with Matplotlib and Seaborn: These libraries allowed me to create interactive and visually appealing graphs to present my findings to stakeholders.
Automation: By writing reusable scripts, I automated the process of monitoring and reporting, saving significant time and effort.
Diving Deeper: Advanced Applications of Python
As I delved deeper, I realized Python’s potential extended beyond basic analysis. It became a tool for solving complex business problems, such as:
Predictive Analytics: Using Scikit-learn, I developed models to forecast system downtimes based on historical data. This proactive approach helped in optimizing resources and minimizing disruptions.
Data Pipeline Development: Python’s integration capabilities allowed me to build ETL (Extract, Transform, Load) pipelines, ensuring seamless data flow between systems.
Real-Time Dashboards: By combining Flask (a lightweight web framework) with Python’s visualization libraries, I created dashboards that displayed real-time analytics, empowering teams to make informed decisions instantly.
The Role of Structured Training
While self-learning has its merits, structured training programs offer a unique edge, especially for professionals with limited time to explore on their own. My decision to undergo data analytics training in Hyderabad through ACTE Institute proved transformative.
Here’s what made this experience invaluable:
Expert Guidance: Industry professionals led the sessions, sharing insights that went beyond textbook knowledge.
Collaborative Environment: Engaging with peers from diverse backgrounds helped me understand different perspectives and approaches to problem-solving.
Hands-On Projects: Real-world scenarios provided a platform to apply theoretical concepts, bridging the gap between learning and implementation.
Feedback and Mentorship: Regular feedback from trainers ensured I stayed on track, while mentorship sessions helped me align my learning with career goals.
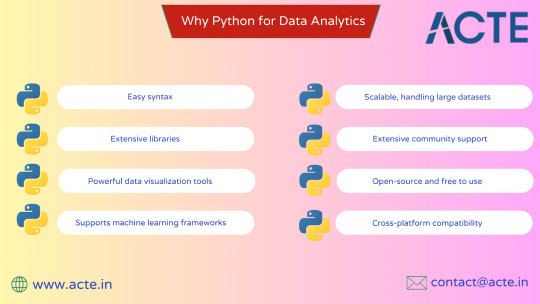
Key Learnings and Insights
The transition from a solution architect to a professional proficient in data analytics wasn’t without its challenges. However, every hurdle taught me something valuable:
Start Small, Think Big: It’s tempting to dive into complex machine learning models immediately. However, mastering the basics—data cleaning, exploration, and visualization—lays a strong foundation for advanced techniques.
Iterate and Experiment: Data analytics is an iterative process. The more you experiment, the better you understand the data and the tools you’re using.
Stay Curious: The field of data analytics is dynamic. Keeping up with the latest tools, techniques, and best practices ensures you remain relevant and effective.
Collaborate: Engaging with a community—be it through forums, training sessions, or professional networks—accelerates learning and opens doors to new opportunities.
Real-World Impact of Python for Data Analytics
Equipping myself with Python for data analytics has had a tangible impact on my work:
Enhanced Problem-Solving: Data-driven insights have enabled me to identify bottlenecks, predict outcomes, and design more effective solutions.
Improved Communication: Visualizations and dashboards created using Python help convey complex information in a clear and impactful way.
Career Growth: The ability to bridge technical expertise with analytical skills has positioned me as a more versatile and valuable professional.
Future Trends in Data Analytics
As I continue to explore Python for data analytics, I’m excited about the possibilities it holds for the future. Emerging trends like AI-driven analytics, natural language processing, and edge analytics are set to redefine how we interact with data. Python’s adaptability ensures it will remain a cornerstone of these advancements.
Final Thoughts
My journey into the world of data analytics has been transformative, both personally and professionally. From starting with a simple data analytics training online program to applying Python to solve complex business problems, the experience has been nothing short of rewarding.
If there’s one piece of advice I would offer to anyone contemplating this path, it’s this: invest in learning, embrace challenges, and don’t hesitate to experiment. Whether you’re an aspiring data analyst, a seasoned IT professional, or someone intrigued by the power of data, Python for data analytics is a skill worth mastering.
The training I received in data analytics training in Hyderabad served as a turning point, equipping me with the knowledge and confidence to navigate this exciting field. As organizations continue to prioritize data-driven strategies, the demand for professionals proficient in data analytics will only grow.
So, take that first step. Enroll in a training program, start exploring Python, and discover the endless possibilities that data analytics offers. Who knows? It might just redefine your career, as it did mine.
#ai#artificialintelligence#digitalmarketing#marketingstrategy#database#machinelearning#adtech#cybersecurity
0 notes
Text
Exploring the Azure Technology Stack: A Solution Architect’s Journey
Kavin
As a solution architect, my career revolves around solving complex problems and designing systems that are scalable, secure, and efficient. The rise of cloud computing has transformed the way we think about technology, and Microsoft Azure has been at the forefront of this evolution. With its diverse and powerful technology stack, Azure offers endless possibilities for businesses and developers alike. My journey with Azure began with Microsoft Azure training online, which not only deepened my understanding of cloud concepts but also helped me unlock the potential of Azure’s ecosystem.
In this blog, I will share my experience working with a specific Azure technology stack that has proven to be transformative in various projects. This stack primarily focuses on serverless computing, container orchestration, DevOps integration, and globally distributed data management. Let’s dive into how these components come together to create robust solutions for modern business challenges.

Understanding the Azure Ecosystem
Azure’s ecosystem is vast, encompassing services that cater to infrastructure, application development, analytics, machine learning, and more. For this blog, I will focus on a specific stack that includes:
Azure Functions for serverless computing.
Azure Kubernetes Service (AKS) for container orchestration.
Azure DevOps for streamlined development and deployment.
Azure Cosmos DB for globally distributed, scalable data storage.
Each of these services has unique strengths, and when used together, they form a powerful foundation for building modern, cloud-native applications.
1. Azure Functions: Embracing Serverless Architecture
Serverless computing has redefined how we build and deploy applications. With Azure Functions, developers can focus on writing code without worrying about managing infrastructure. Azure Functions supports multiple programming languages and offers seamless integration with other Azure services.
Real-World Application
In one of my projects, we needed to process real-time data from IoT devices deployed across multiple locations. Azure Functions was the perfect choice for this task. By integrating Azure Functions with Azure Event Hubs, we were able to create an event-driven architecture that processed millions of events daily. The serverless nature of Azure Functions allowed us to scale dynamically based on workload, ensuring cost-efficiency and high performance.
Key Benefits:
Auto-scaling: Automatically adjusts to handle workload variations.
Cost-effective: Pay only for the resources consumed during function execution.
Integration-ready: Easily connects with services like Logic Apps, Event Grid, and API Management.
2. Azure Kubernetes Service (AKS): The Power of Containers
Containers have become the backbone of modern application development, and Azure Kubernetes Service (AKS) simplifies container orchestration. AKS provides a managed Kubernetes environment, making it easier to deploy, manage, and scale containerized applications.
Real-World Application
In a project for a healthcare client, we built a microservices architecture using AKS. Each service—such as patient records, appointment scheduling, and billing—was containerized and deployed on AKS. This approach provided several advantages:
Isolation: Each service operated independently, improving fault tolerance.
Scalability: AKS scaled specific services based on demand, optimizing resource usage.
Observability: Using Azure Monitor, we gained deep insights into application performance and quickly resolved issues.
The integration of AKS with Azure DevOps further streamlined our CI/CD pipelines, enabling rapid deployment and updates without downtime.
Key Benefits:
Managed Kubernetes: Reduces operational overhead with automated updates and patching.
Multi-region support: Enables global application deployments.
Built-in security: Integrates with Azure Active Directory and offers role-based access control (RBAC).
3. Azure DevOps: Streamlining Development Workflows
Azure DevOps is an all-in-one platform for managing development workflows, from planning to deployment. It includes tools like Azure Repos, Azure Pipelines, and Azure Artifacts, which support collaboration and automation.
Real-World Application
For an e-commerce client, we used Azure DevOps to establish an efficient CI/CD pipeline. The project involved multiple teams working on front-end, back-end, and database components. Azure DevOps provided:
Version control: Using Azure Repos for centralized code management.
Automated pipelines: Azure Pipelines for building, testing, and deploying code.
Artifact management: Storing dependencies in Azure Artifacts for seamless integration.
The result? Deployment cycles that previously took weeks were reduced to just a few hours, enabling faster time-to-market and improved customer satisfaction.
Key Benefits:
End-to-end integration: Unifies tools for seamless development and deployment.
Scalability: Supports projects of all sizes, from startups to enterprises.
Collaboration: Facilitates team communication with built-in dashboards and tracking.

4. Azure Cosmos DB: Global Data at Scale
Azure Cosmos DB is a globally distributed, multi-model database service designed for mission-critical applications. It guarantees low latency, high availability, and scalability, making it ideal for applications requiring real-time data access across multiple regions.
Real-World Application
In a project for a financial services company, we used Azure Cosmos DB to manage transaction data across multiple continents. The database’s multi-region replication ensure data consistency and availability, even during regional outages. Additionally, Cosmos DB’s support for multiple APIs (SQL, MongoDB, Cassandra, etc.) allowed us to integrate seamlessly with existing systems.
Key Benefits:
Global distribution: Data is replicated across regions with minimal latency.
Flexibility: Supports various data models, including key-value, document, and graph.
SLAs: Offers industry-leading SLAs for availability, throughput, and latency.
Building a Cohesive Solution
Combining these Azure services creates a technology stack that is flexible, scalable, and efficient. Here’s how they work together in a hypothetical solution:
Data Ingestion: IoT devices send data to Azure Event Hubs.
Processing: Azure Functions processes the data in real-time.
Storage: Processed data is stored in Azure Cosmos DB for global access.
Application Logic: Containerized microservices run on AKS, providing APIs for accessing and manipulating data.
Deployment: Azure DevOps manages the CI/CD pipeline, ensuring seamless updates to the application.
This architecture demonstrates how Azure’s technology stack can address modern business challenges while maintaining high performance and reliability.
Final Thoughts
My journey with Azure has been both rewarding and transformative. The training I received at ACTE Institute provided me with a strong foundation to explore Azure’s capabilities and apply them effectively in real-world scenarios. For those new to cloud computing, I recommend starting with a solid training program that offers hands-on experience and practical insights.
As the demand for cloud professionals continues to grow, specializing in Azure’s technology stack can open doors to exciting opportunities. If you’re based in Hyderabad or prefer online learning, consider enrolling in Microsoft Azure training in Hyderabad to kickstart your journey.
Azure’s ecosystem is continuously evolving, offering new tools and features to address emerging challenges. By staying committed to learning and experimenting, we can harness the full potential of this powerful platform and drive innovation in every project we undertake.
#cybersecurity#database#marketingstrategy#digitalmarketing#adtech#artificialintelligence#machinelearning#ai
2 notes
·
View notes
Text
Python for Data Analytics: A Solution Architect’s Perspective
As a solution architect, my career has been centered on designing robust, scalable systems tailored to meet diverse business needs. Over the years, I’ve worked on projects spanning various domains—cloud computing, infrastructure optimization, and application development. However, the growing emphasis on data-driven decision-making reshaped my perspective. Organizations now rely heavily on extracting actionable insights from their data, which made me realize that understanding and leveraging data analytics is no longer optional.
This journey into the world of data analytics began with an enriching data analytics training online program. This training not only introduced me to foundational concepts but also provided a structured pathway to mastering Python for data analytics—a skill I now consider indispensable for any tech professional.

Why Python for Data Analytics?
Python has emerged as a game-changer in the data analytics space, and for good reasons:
Simplicity and Versatility: Python’s straightforward syntax makes it accessible for beginners, while its versatility allows professionals to handle complex tasks seamlessly.
Extensive Libraries: Libraries like Pandas, NumPy, Matplotlib, and Seaborn enable efficient data manipulation, visualization, and analysis. For advanced analytics, Scikit-learn and TensorFlow are the go-to tools for machine learning and predictive modeling.
Integration Capabilities: Python integrates effortlessly with other technologies and platforms, making it a preferred choice for end-to-end data solutions.
Community Support: With its vast global community, Python ensures you’ll always find support, tutorials, and updates to keep pace with the ever-evolving analytics landscape.
My First Steps with Python for Data Analytics
My initial foray into Python for data analytics was both exciting and challenging. While I was familiar with programming concepts, understanding the nuances of data manipulation required a shift in mindset. The training program I enrolled in emphasized hands-on projects, which was instrumental in solidifying my understanding.
One of my first projects involved analyzing system performance metrics. Using Python, I could process large datasets to identify patterns and anomalies in server utilization. Here’s what made Python stand out:
Data Manipulation with Pandas: I used Pandas to clean and restructure the data. Its DataFrame object made it easy to filter, sort, and aggregate information.
Visualization with Matplotlib and Seaborn: These libraries allowed me to create interactive and visually appealing graphs to present my findings to stakeholders.
Automation: By writing reusable scripts, I automated the process of monitoring and reporting, saving significant time and effort.
Diving Deeper: Advanced Applications of Python
As I delved deeper, I realized Python’s potential extended beyond basic analysis. It became a tool for solving complex business problems, such as:
Predictive Analytics: Using Scikit-learn, I developed models to forecast system downtimes based on historical data. This proactive approach helped in optimizing resources and minimizing disruptions.
Data Pipeline Development: Python’s integration capabilities allowed me to build ETL (Extract, Transform, Load) pipelines, ensuring seamless data flow between systems.
Real-Time Dashboards: By combining Flask (a lightweight web framework) with Python’s visualization libraries, I created dashboards that displayed real-time analytics, empowering teams to make informed decisions instantly.
The Role of Structured Training
While self-learning has its merits, structured training programs offer a unique edge, especially for professionals with limited time to explore on their own. My decision to undergo data analytics training in Hyderabad through ACTE Institute proved transformative.
Here’s what made this experience invaluable:
Expert Guidance: Industry professionals led the sessions, sharing insights that went beyond textbook knowledge.
Collaborative Environment: Engaging with peers from diverse backgrounds helped me understand different perspectives and approaches to problem-solving.
Hands-On Projects: Real-world scenarios provided a platform to apply theoretical concepts, bridging the gap between learning and implementation.
Feedback and Mentorship: Regular feedback from trainers ensured I stayed on track, while mentorship sessions helped me align my learning with career goals.

Key Learnings and Insights
The transition from a solution architect to a professional proficient in data analytics wasn’t without its challenges. However, every hurdle taught me something valuable:
Start Small, Think Big: It’s tempting to dive into complex machine learning models immediately. However, mastering the basics—data cleaning, exploration, and visualization—lays a strong foundation for advanced techniques.
Iterate and Experiment: Data analytics is an iterative process. The more you experiment, the better you understand the data and the tools you’re using.
Stay Curious: The field of data analytics is dynamic. Keeping up with the latest tools, techniques, and best practices ensures you remain relevant and effective.
Collaborate: Engaging with a community—be it through forums, training sessions, or professional networks—accelerates learning and opens doors to new opportunities.
Real-World Impact of Python for Data Analytics
Equipping myself with Python for data analytics has had a tangible impact on my work:
Enhanced Problem-Solving: Data-driven insights have enabled me to identify bottlenecks, predict outcomes, and design more effective solutions.
Improved Communication: Visualizations and dashboards created using Python help convey complex information in a clear and impactful way.
Career Growth: The ability to bridge technical expertise with analytical skills has positioned me as a more versatile and valuable professional.
Future Trends in Data Analytics
As I continue to explore Python for data analytics, I’m excited about the possibilities it holds for the future. Emerging trends like AI-driven analytics, natural language processing, and edge analytics are set to redefine how we interact with data. Python’s adaptability ensures it will remain a cornerstone of these advancements.
Final Thoughts
My journey into the world of data analytics has been transformative, both personally and professionally. From starting with a simple data analytics training online program to applying Python to solve complex business problems, the experience has been nothing short of rewarding.
If there’s one piece of advice I would offer to anyone contemplating this path, it’s this: invest in learning, embrace challenges, and don’t hesitate to experiment. Whether you’re an aspiring data analyst, a seasoned IT professional, or someone intrigued by the power of data, Python for data analytics is a skill worth mastering.
The training I received in data analytics training in Hyderabad served as a turning point, equipping me with the knowledge and confidence to navigate this exciting field. As organizations continue to prioritize data-driven strategies, the demand for professionals proficient in data analytics will only grow.
So, take that first step. Enroll in a training program, start exploring Python, and discover the endless possibilities that data analytics offers. Who knows? It might just redefine your career, as it did mine.
0 notes
Text
When I began my journey as a solution architect, I knew that the foundation of my expertise needed to be solid. One of the key milestones in shaping my career was enrolling in a cybersecurity training online program. The comprehensive curriculum and hands-on approach provided by the ACTE Institute opened new doors for me and gave me the confidence to tackle complex challenges in the tech space. This training not only equipped me with the necessary skills but also sparked my interest in how emerging technologies like blockchain could redefine cybersecurity.
Blockchain technology has become one of the most transformative innovations of the 21st century, fundamentally changing the way industries operate—and cybersecurity is no exception. As organizations face increasing threats from sophisticated cyberattacks, blockchain offers unique advantages that traditional systems often lack. Here's how blockchain is revolutionizing cybersecurity:

The Rise of Blockchain in Cybersecurity
Cybersecurity has always been about safeguarding data, networks, and systems from unauthorized access or attacks. However, with the exponential increase in the volume of data and the growing complexity of cyber threats, traditional solutions often fall short. Blockchain’s decentralized and tamper-proof architecture is becoming a game-changer in this context.
Unlike centralized systems, where a single point of failure can compromise the entire infrastructure, blockchain distributes data across a network of nodes. This decentralized approach ensures that even if one node is compromised, the integrity of the data remains intact. For cybersecurity professionals, this means creating systems that are inherently more secure and resilient to attacks.
Key Applications of Blockchain in Cybersecurity
1. Data Integrity and Protection
One of blockchain’s most significant contributions to cybersecurity is its ability to guarantee data integrity. By using cryptographic hashes, blockchain ensures that once data is written to the ledger, it cannot be altered without detection. This makes it nearly impossible for hackers to tamper with sensitive information, whether it's financial records, personal data, or intellectual property.
For example, in supply chain management, blockchain can track the provenance of goods and ensure that the data remains unaltered throughout its journey. Similarly, in healthcare, patient records can be securely stored and accessed only by authorized personnel, reducing the risk of breaches.
2. Securing Internet of Things (IoT) Devices
The rapid adoption of IoT devices has introduced a new frontier of cybersecurity challenges. These devices often have limited security protocols, making them prime targets for cyberattacks. Blockchain technology can address this issue by enabling secure and decentralized communication between devices.
Through blockchain, IoT devices can authenticate each other and establish secure communication channels without relying on a central authority. This reduces the likelihood of Distributed Denial-of-Service (DDoS) attacks and other vulnerabilities associated with IoT networks.
3. Identity Management
Traditional identity management systems often rely on centralized databases, which are attractive targets for hackers. Blockchain introduces a decentralized model for identity verification, where users have control over their data. This concept, known as Self-Sovereign Identity (SSI), allows individuals to store their credentials on a blockchain and share them securely with third parties when required.
By leveraging blockchain, organizations can reduce the risk of identity theft and fraud while enhancing user privacy. This is particularly relevant for industries like finance, healthcare, and e-commerce, where identity verification is critical.
4. Preventing DDoS Attacks
Distributed Denial-of-Service (DDoS) attacks are a significant threat to businesses, causing downtime and financial losses. Blockchain can mitigate this risk by decentralizing Domain Name System (DNS) infrastructure. Traditional DNS systems are centralized, making them vulnerable to attacks. By using blockchain, DNS records are distributed across a network, making it nearly impossible for attackers to target a single point of failure.
Blockchain Challenges in Cybersecurity
While blockchain holds immense potential for enhancing cybersecurity, it’s not without its challenges. Some of the key hurdles include:
Scalability: Blockchain networks often struggle to handle large volumes of transactions quickly, which can be a bottleneck for certain applications.
Energy Consumption: The consensus mechanisms used in blockchain, such as Proof of Work (PoW), are energy-intensive and may not be sustainable for all use cases.
Regulatory Compliance: Blockchain’s decentralized nature poses challenges for regulatory compliance, especially in industries with strict data protection laws.
Overcoming these challenges requires continued innovation and collaboration between blockchain developers and cybersecurity professionals.

Real-World Use Cases of Blockchain in Cybersecurity
Several organizations and industries are already leveraging blockchain to enhance their cybersecurity measures. Here are a few examples:
Financial Services: Blockchain-based solutions are being used to secure financial transactions, prevent fraud, and streamline Know Your Customer (KYC) processes.
Healthcare: Blockchain ensures the secure storage and sharing of electronic health records, reducing the risk of breaches and unauthorized access.
Supply Chain: Companies are adopting blockchain to verify the authenticity of products and prevent counterfeit goods from entering the market.
Government: Blockchain is being used to secure voting systems, ensuring transparency and reducing the risk of election fraud.
The Role of Cybersecurity Training in Embracing Blockchain
As a solution architect, my journey into the world of blockchain and cybersecurity would not have been possible without the foundational knowledge I gained from my training at the ACTE Institute. Their cybersecurity training in chennai equipped me with the practical skills and theoretical understanding necessary to navigate this complex field.
The training covered essential topics like cryptography, network security, and risk management, which laid the groundwork for understanding how blockchain technology could be applied to cybersecurity. The hands-on projects and real-world case studies provided me with the confidence to implement blockchain-based solutions in my current role.
The Future of Blockchain in Cybersecurity
The integration of blockchain technology into cybersecurity is still in its early stages, but the potential is undeniable. As organizations continue to adopt digital transformation initiatives, the demand for secure, scalable, and efficient solutions will only grow. Blockchain’s unique attributes position it as a critical tool in the fight against cyber threats.
However, realizing its full potential requires a collaborative effort between technology providers, cybersecurity experts, and regulatory bodies. By addressing the challenges and investing in education and training, we can unlock new possibilities and create a safer digital world.
Conclusion
Blockchain technology is revolutionizing the field of cybersecurity by addressing some of its most pressing challenges. From ensuring data integrity to securing IoT devices and preventing DDoS attacks, the applications of blockchain are vast and varied. For professionals looking to make an impact in this space, investing in comprehensive training programs like those offered by the ACTE Institute can be a game-changer.
Reflecting on my journey, I can confidently say that my cybersecurity training was instrumental in helping me land my current role and understand the transformative power of blockchain. With the right skills and knowledge, anyone can be a part of this exciting revolution
0 notes
Text
Edge Computing: Extending the Power of the Cloud
When I embarked on my journey into the world of cloud technologies, I had little idea how transformative it would be. The sheer breadth of cloud concepts and services initially overwhelmed me. I found it challenging to connect theoretical knowledge with practical applications, often feeling lost amidst the jargon and complexities. However, these problems transformed into learning and understanding by following a well-defined course and experimenting with projects gradually. My foundational knowledge came from an in-depth cloud computing online course with the ACTE Institute. This established a comprehensive view of the foundational aspects of clouds, which, later in life, served as the backbone for my profession as a solution architect. Initially, it was difficult to comprehend the scope of services and technologies, but structured learning with practical examples bridged the gap.
What is Edge Computing?
Edge computing is a technology paradigm that brings computation and data storage closer to the sources of data, such as IoT edge devices, to reduce latency and improve processing efficiency. This shift also has an impact on industries, such as reducing energy consumption and operational costs. An edge device consumes bandwidth by processing information locally, not requiring constant energy to transmit the data to a centralized server. With the reduction in reliance on cloud infrastructure, such big clouds, cost-cutting happens on data transfer as well as storing in a central location, so edge computing comes out as both cost-effective and eco-friendly. This reduces reliance on centralized cloud servers, allowing the edge servers and networks to process critical tasks on-site. Edge computing has significantly improved responses, which makes this shift vital for applications such as real-time processing in autonomous vehicles, healthcare monitoring, and industrial automation.
Edge computing also cuts down bandwidth utilization and operational cost. For example, rather than sending terabytes of raw data to the cloud for processing, edge devices filter and process the data locally, transmitting only what is relevant. This improves efficiency and enhances privacy by keeping sensitive data closer to its source.
Role of Edge Servers and Edge Networks
One of the projects that we implemented recently involved using edge servers for real-time analytics for a smart city initiative. We processed IoT data from sensors in place and saved huge amounts of time on decision-making, as was demonstrated in an example involving the analysis of traffic sensor data for congestion level updates. This improved the efficiency of traffic management systems, reduced fuel consumption from idling vehicles, and enhanced overall urban mobility. Localizing data processing further also helped reduce dependency on central cloud infrastructure for computation by saving cost and improving reliability in case of network disruptions. These scattered servers acted as intermediaries between IoT devices and the central cloud, exposed to strategic locations with the required physical infrastructure for networking. Edge networks further ensured seamless communication, thus reducing latency issues that would have otherwise hampered critical operations, such as traffic management and emergency responses.
One striking example was using edge servers for monitoring traffic congestion. By analyzing data from IoT sensors on the roads, the system provided instant updates and recommendations to drivers. This reduced delays and enhanced overall traffic flow.
Multi-Access and Mobile Edge Computing
I have also looked at multi-access edge computing and mobile edge computing as part of my work. MEC is an extension of cloud capabilities to the edge of the network, presenting the solutions required for low latency in applications such as autonomous vehicles or AR/VR experiences. For example, real-time map rendering can be available for the navigation of autonomous cars in high-traffic areas.
Similarly, mobile edge computing enables mobile devices to process data locally, which can be used for smoother gaming, video streaming, and IoT applications. A recent use case I worked on was leveraging MEC for a sports analytics platform. The platform delivered instant replays and analytics to fans in real time by processing video feeds from stadium cameras locally, creating an engaging experience.
Examples of Edge Computing in Action
During my stay at ACTE, I learned the basics that later helped me design practical edge computing examples in industries like healthcare, retail, and manufacturing. For example:
Healthcare: IoT edge devices monitor patients in real-time, providing critical data to edge servers for immediate analysis. In one hospital project, we used edge technology to track vital signs and alert medical staff during emergencies, significantly improving response times.
Retail: Edge computing technology powers personalized shopping experiences by analyzing customer behavior directly at the store. For example, an edge-based recommendation system suggested products to customers based on in-store browsing patterns, boosting sales.
Manufacturing: Edge computing devices streamline production lines by analyzing machine data on-site, predicting maintenance needs, and reducing downtime. In one factory, deploying edge servers helped identify equipment malfunctions before they escalated, saving significant costs.
Edge Cloud Computing and Platforms
Cloud providers have incorporated edge computing into their services, which gives rise to edge cloud computing. In contrast to the traditional model of cloud, which relies on centralized data centers for processing and storing data, edge cloud computing disperses such capabilities closer to the sources of data. For instance, while a legacy cloud model is likely to have latency issues with the distance between users and servers, edge cloud computing is much faster in responding because data processing is done locally. In addition, edge cloud computing reduces the amount of constant data transfer to a central server, thus cutting bandwidth costs and increasing system reliability in areas where the network is unreliable. Providers like AWS Edge Computing and Akamai Edge Compute offer robust platforms that bridge cloud and edge capabilities. AWS’s services like Greengrass enable developers to run applications locally on IoT devices, allowing for offline functionality and real-time decision-making. Similarly, Akamai’s platform accelerates content delivery and application performance, making it invaluable for industries like e-commerce and media.
During a project with a media streaming company, we used Akamai Edge Compute to optimize video delivery. This means that content will be cached nearer to users in order to lower buffering times and increase viewer satisfaction. In fact, it will show how the edge cloud is enhancing customer experience in every area.
Challenges and Future Trends
Even though edge computing has great potential, it isn't without challenges. In my projects, one challenge always kept on surfacing: making sure that distributed edge locations maintained data security. Each edge server and device offered a potential weakness, necessitating sophisticated encryption and real-time monitoring solutions. A second challenge was the high deployment and maintenance costs of edge infrastructure, which meant careful budgeting and optimization strategies. For instance, in a smart city project, we addressed the above challenges by implementing a mix of lightweight security protocols and periodic audits that balanced performance with cost-effectiveness. These experiences taught me that overcoming edge computing challenges often requires a tailored approach, aligning technology with specific project needs. Security concerns, infrastructure costs, and the complexity of managing distributed networks are significant hurdles. For example, securing data across multiple edge locations requires advanced encryption and monitoring solutions, which can be resource-intensive.
However, progress in edge computing technology is tackling the above-mentioned issues one after another. Trends include introducing AI at the edge, thus making devices capable of learning in real time and adaptation. Besides this, there will be improvement in 5G networks which is expected to strengthen edge computing as well through providing fast, stable connectivity of devices and applications.
Why Edge Computing Matters
In retrospect, I think it is unbelievable how edge computing devices and technologies have changed the way we look at data processing. They extended the power of the cloud to the very edge, which makes it possible for innovative solutions in various sectors, from better health outcomes to transforming retail experiences, and many others.
So if you are also interested in taking up a career in this rapidly changing field, I would say that professional learning is the first step. This is because such a specialized course in cloud computing course in Bangalore from ACTE Institute helped me shape my career into a solution architect. The on-the-job learning and industry insight I received continue to drive me forward in both passion and results.
#techinnovation#artificialintelligence#innovation#hybridminds#martech#digitalmarketing#adtech#digitaladvertising#marketingstrategy#ConquestAdvertising#DigitalMarketing#AdTech#MarketingStrategy#ArtificialIntelligence#MachineLearning#PredictiveAnalytics#ARVR#MetaverseMarketing#GenerativeAI#ProgrammaticAdvertising#CompetitiveStrategy#CustomerAcquisition#MarketingTrends#AdTechInsights#MarketingProfessionals#technology
0 notes
Text
The Role of AI in Transforming Data Analytics
As a solution architect, I have spent years dealing with some of the most complex challenges in data analytics. Throughout my professional journey, I realized the growing importance of artificial intelligence (AI) in this domain. I did a data analytics course online through ACTE Institute, and that was my foundation knowledge regarding the vast possibilities of AI with data analytics technology. I want to expand upon how AI has changed the data analytics paradigm, the advantages that it gives, and how business can take meaning from this in this blog.

From Traditional Analytics to AI-based Approaches
Traditionally, data analytics relied heavily on statistical methods and manual processing. Analysts would often spend days or weeks crunching numbers, cleaning data, and interpreting results. While this approach served its purpose, it had significant limitations in terms of scalability and speed. With the advent of AI, we’ve moved beyond traditional methods to intelligent, automated, and predictive analytics. AI algorithms can process large data sets in real-time, identify patterns, and predict with minimal human interference. It has not only accelerated data analytics but also made it more accurate and informative.
Applications of AI in Data Analytics
AI has impacted virtually every sphere of data analytics and transformed how organizations process and analyze data. Some critical applications are discussed below:
Data Cleaning and Preparation: Before analysis, data must be cleaned to remove inconsistencies, errors, and duplicates. AI tools can automate this process, saving time and minimizing the chances of human errors.
Predictive Analytics: AI excels in predictive modeling, allowing businesses to predict trends and outcomes. For example, e-commerce companies use AI to predict customer behavior and provide personalized recommendations.
Real-Time Analytics: In finance and healthcare, real-time data analysis is the need of the hour. AI algorithms can process incoming streams of data in real time. This enables the organization to make the right decisions in time.
Natural Language Processing: AI-driven NLP enables systems to analyze unstructured data, such as customer reviews, social media posts, or emails. This helps companies gauge customer sentiment and refine their strategies.
Anomaly Detection: AI can also be used to recognize anomalies in very important data which are vital for fraud detection, quality control, and cybersecurity.
Visual Data Representation:
AI is making the presentation of data much more dynamic and interactive and, therefore, easy for all concerned parties to understand complicated data sets.
Advantages of AI in Data Analytics
Adopting AI in data analytics will come with a wide range of advantages. Some of them are:
Increased Efficiency: Automation of operations, such as cleaning and data aggregation, accelerates the process of analytics. The analysts can then focus on thoughtful strategies.
Greater Accuracy: The result derived from AI algorithms is error-free, as human intervention is minimized. Therefore, integrity of information is maintained.
Scalability: AI systems can process vast databases, and hence they can be used in big data businesses.
Cost Effectiveness: AI reduces the overall cost of analytics by making operations more streamlined and minimizing manual effort.
Personalization: AI allows for hyper-personalization in marketing and customer engagement through the analysis of individual preferences and behaviors.
Data-Driven Decision-Making: AI enables organizations to make decisions based on the accuracy and timeliness of data rather than intuition.
How AI Empowers Various Industries
AI-based data analytics is transforming numerous industries:
Healthcare: AI scans patient information to enhance the precision of diagnosis, personalize the treatment plan, and predict the onset of disease.
Finance: From fraud detection to risk analysis, AI elevates the stakes in financial decision-making and operation efficiency.
Retail: AI lets retailers optimize stock, predict demand, and tailor shopping experiences.
Manufacturing: Predictive maintenance with AI cuts down on downtime and increases productivity.
Energy: AI optimizes energy consumption and predicts equipment failures in utilities and renewable energy sectors.

Challenges of the Implementation of AI in Data Analytics
Benefits of AI notwithstanding, its implementation in data analytics poses a set of challenges to its users.
Data Quality: Poor data can lead to flawed conclusions. It hence calls for well-established data governance frameworks.
Skill Gap: Most firms are unable to obtain experts having the skills with expertise in AI and data analytics.
Ethical Issues: AI raises several ethical issues such as data privacy and bias, hence there is a need for ethics and transparency in algorithms.
Integration Issues: Integrating AI tools to existing systems will be a pretty complex and resource-intensive process.
Role of Data Analytics Professionals in the AI Environment
Data analytics professionals have to adapt to this AI-driven landscape, acquiring the needed skills and knowledge. Here's how they could contribute:
Understand AI Algorithms: Professionals should know how an AI algorithm works in order to effectively understand and use results.
Ethical AI Practices: Ethical practices in the application of AI are crucial because it would only serve to gain trust and to comply with the regulations.
Continued Learning: Keeping up-to-date with the state of the latest developments in AI is vital to remain relevant in this field.
Personal Experience: I took a course on data analytics at ACTE Institute in Hyderabad, where I was given a solid foundation about analytical tools, statistical methods, and the role of AI in that field. I learned to apply AI-driven analytics in practical scenarios with hands-on projects and case studies. All of this knowledge has been critically important for me to be a solution architect, having the capability to design and deliver AI-powered solutions to clients involved in different sectors.
Conclusion
The world of data analytics has been revolutionized because of AI with much speed and accuracy in delivering actionable insights. From predictive modeling to anomaly detection, AI opens new avenues to help businesses utilize their data more effectively. I have seen, during my career as a solution architect, how analytics processes can get transformed by artificial intelligence to enhance business success. Proper training in the right toolset would also be possible and would help the professionals take maximum advantage of this data-driven age.
0 notes
Text
Ransomware: The most dangerous attack in cybersecurity and the business impact it carries.
As a solution architect with a keen focus on cybersecurity, I’ve often seen firsthand how malicious cyberattacks can disrupt businesses. One such attack that stands out for its sheer destructiveness and complexity is ransomware. My understanding of ransomware attacks deepened after completing a cybersecurity course online from ACTE Institute, which provided me with the skills to identify vulnerabilities and implement robust defense mechanisms.
In this blog, I’ll delve into ransomware attacks, their devastating effects on businesses, and how cybersecurity experts can proactively prevent them.

Understanding Ransomware
Ransomware is a type of malicious software that encrypts a victim’s data, rendering it inaccessible. The attackers then demand a ransom in exchange for the decryption key. These attacks target individuals, organizations, and even critical infrastructure, often leading to significant financial and reputational damage.
The evolution of ransomware was from simple, basic encryption malware to highly advanced multi-layered attack with double extortion, where hackers threaten to expose the exfiltrated data. The most renowned ransomware attacks that have caused extreme damage on an extensive scale have been WannaCry, Petya, and Ryuk.
Business Effect of Ransomware
Here is how an attack by a ransomware could affect a business:
Financial Losses: Companies incur direct costs in the form of ransom payments and indirect costs of downtime, data recovery, and lost productivity. In the case of the Colonial Pipeline attack in 2021, a $4.4 million ransom payment was made, besides millions more in operational losses.
Operational Disruption: Normally, ransomware totally disrupts business operations, whereby it can stop a production line or services or customer transaction. In 2017, the WannaCry attack paralysed the health care system around the world where patients were treated without a medical report.
Data breaches: The new double-extortion strategy has a double-edged sword; besides freezing the data, they steal some sensitive data. This hurts the company much in the areas of regulatory fines and customer's loss of confidence if the stolen data is subsequently leaked.
Loss of Reputation: A ransomware attack impacts one's reputation with the organization. Customers and associates may view it as unreliable and insecure and go elsewhere to enjoy business.
How Cyber Experts Can Assist One in Dodging Ransomware Attacks
As a cyber expert, here are the actions you can perform to safeguard an organization from ransomware attacks:
Awareness Training to Employees: Most ransomware attacks start as phishing emails. Awareness training needs to keep an eye for being careful in clicking links or emails, and an organization needs to organize awareness campaigns at regular intervals, along with simulations for phishing.
Data Backup and Recovery Plan: Periodic backup of vital data and exercising the recovery plan helps recover minimum losses when attacked. Besides, these copies should be kept off the premises or in well-guarded clouds.
Endpoint Protection and Monitoring: Advanced endpoint protection tools will be able to detect and block malicious activity. Continuous monitoring of unusual behavior ensures early detection of potential threats.
Patch Management : Update the systems and software. Most ransomware attacks rely on known vulnerabilities of outdated systems. For instance, the EternalBlue exploit in the WannaCry attack is based on that.
Zero Trust Architecture: The Zero Trust model checks identity stringently and provides access according to the identity. It thereby slows down the lateral movement of ransomware within a network.
Multi-Factor Authentication (MFA): MFA creates an extra level of security with the help of which even though credentials have been stolen, unauthorized access still will not occur.
Incident Response Planning: A good written incident response planning will make the organization ready before the attack occurred, thus cutting down time wastage and resulting in lesser losses before reacting faster.

Threat Intelligence: Utilizing tool-based threat intelligence, organizations benefit from new emerging ransomware patterns and vulnerabilities are made available
Reminds me of Colonial Pipeline ransomware attack how crucial it has become to our world of integration and proves, through attacks like this one, that investment in some more robust security practices as well as highly skilled professionals are indeed called for.
It has shaped up my solution architecture journey, learning from the Cloud computing course in Bangalore ACTE Institute. It gives me a fair amount of practice training with actual case studies about designing systems so that no future threats may pop up unexpectedly.
Conclusion
Ransomware attacks are one of the most dangerous threats to businesses today. Though their impact is destructive, there are proactive measures and skilled cybersecurity experts that can mitigate the risks. Businesses will be able to protect themselves from these evolving threats by keeping themselves informed, implementing best practices, and investing in ongoing education. In any case, mastering this field of cybersecurity requires training professionals in-depth. Such courses can help the professionals equip themselves with the needed skills to protect organizations from ransomware and other cyber threats.
0 notes
Text
How Kubernetes Facilitates the Orchestration of Containers in AWS
Containerization has transformed the design, deployment, and scaling of cloud applications. With k8s (Kubernetes), it is possible to be efficient when dealing with thousands of containers at scale. In AWS, Kubernetes proves crucial in providing benefits such as scalability, streamlined operations, and simplification of maintenance for organizations. In this blog, I’ll share insights on how Kubernetes aids container orchestration in AWS, its benefits, and ways to leverage it for building robust applications—a journey inspired by my foundational learning from the cloud computing course online at ACTE Institute.

Understanding Container Orchestration
Before getting into Kubernetes, it is important to understand container orchestration. It is the process of managing multiple containers for applications in distributed environments, automating tasks such as deployment, scaling, load balancing, and networking. Managing numerous containers in cloud environments like AWS is challenging, especially at scale, and that's where Kubernetes excels. Kubernetes, also known as K8s, is an open-source system designed to automate the deployment, scaling, and management of containerized applications. Initially developed by Google, Kubernetes has become the industry standard for container orchestration. Its ability to abstract complex tasks makes it an indispensable tool for developers and organizations.
Features of Kubernetes
Kubernetes offers numerous features, including:
Automated Scheduling: Efficiently assigns containers to nodes based on resource availability.
Self-Healing Mechanisms: Automatically restarts or replaces failed containers.
Load Balancing: Distributes traffic to ensure optimal performance.
Service Discovery: It enables seamless communication between microservices.
Horizontal Scaling: Dynamically adjusts container instances to match demand.
Rolling Updates and Rollbacks: Supports smooth application updates without downtime.
All this makes Kubernetes an ideal choice for managing containerized applications in dynamic and scalable environments like AWS.
Kubernetes on AWS: How It Works
There are two primary ways of running Kubernetes on AWS:
Amazon EKS (Elastic Kubernetes Service):
Amazon EKS is a managed service, which makes running Kubernetes clusters on AWS easier. Here's why it's in demand:
Managed Control Plane: AWS operates the Kubernetes control plane, taking away operational burdens.
Integration: Works natively with services like EC2, S3, IAM, and CloudWatch, making deployment and management easy and efficient.
Self-managed Kubernetes on EC2:
Organizations can set up Kubernetes manually on EC2 instances for better control. This is suitable for those who require a custom configuration but will incur more maintenance responsibility.
Advantages of Using Kubernetes in AWS
Scalability and Flexibility: Kubernetes supports horizontal scaling, meaning that container instances can be easily scaled up or down according to demand. AWS Auto Scaling helps to complement this by dynamically managing the resources in EC2.
For instance, on Black Friday, a retail application running on Kubernetes in AWS scaled up automatically to match the surge in traffic and continued serving the users uninterrupted.
High Availability and Fault Tolerance: Kubernetes makes sure that the applications stay available through its self-recovery capability. Through the deployment of clusters across several AWS Availability Zones, the applications stay resilient even while infrastructure fails.
Automated Deployment and Management: Kubernetes is highly compatible with CI/CD pipelines, which automate the deployment of applications. Rolling updates and rollbacks ensure smooth upgrades without downtime.
Cost Optimization: Kubernetes's integration with AWS Fargate allows for serverless compute, reducing the cost of infrastructure management. Using AWS spot instances also reduces EC2 costs by a significant amount.
Improved Security: The security features of Kubernetes combined with AWS tools ensure robust protection for containerized applications.

Integrating Kubernetes with AWS Services
AWS services enhance Kubernetes’s capabilities. Here are notable integrations:
Amazon RDS: Provides managed relational databases for Kubernetes applications.
Amazon S3: Offers scalable storage, accessible via Kubernetes with Elastic File System
(EFS) or Elastic Block Store (EBS).
AWS CloudWatch: Monitors Kubernetes clusters and applications, providing actionable insights.
AWS Load Balancer: Handles traffic distribution for Kubernetes applications automatically.
Kubernetes Across Other Cloud Platforms
Kubernetes isn’t exclusive to AWS. It’s widely used in:
Google Cloud Kubernetes (GKE): Provides a deep integration with Google's cloud ecosystem.
Azure Kubernetes Service (AKS): Makes it easier to deploy Kubernetes on Microsoft Azure.
Openshift Kubernetes: Merges Kubernetes with more enterprise features.
Monitoring Kubernetes with Prometheus : Prometheus is a powerful monitoring tool for Kubernetes clusters. The Kube Prometheus Stack provides dashboards and alerts, which enables proactive issue resolution. Combining Prometheus with AWS CloudWatch offers comprehensive visibility into system performance.
Conclusion
Learning Kubernetes transformed my career as a solution architect. From scalable application deployment to cost optimization, Kubernetes has become the bedrock of modern cloud computing. It all started from the cloud computing course in Bangalore at ACTE Institute, building a solid foundation in cloud technologies. Today, using Kubernetes on AWS, I help organizations design resilient and efficient systems-a testament to the power of continuous learning and innovation.
0 notes
Text
Cybersecurity Practices to Adopt in 2025

The Digital Age has still been a potential catch for cybercriminals with advancing technology. Every year marks emerging threats as the attackers are evolving and inventing newer technologies to penetrate into systems. The importance of cybersecurity in 2025 cannot be overemphasized, as it is a critical and complex challenge that people dealing with sensitive data, as well as businesses, face today. This article will outline the cybersecurity practices that organizations and individuals must adhere to in 2025 to protect their digital assets and ensure that their networks remain secure.
Introduction to the 2025 Cybersecurity Landscape:
One of the biggest concerns in the eyes of people and companies alike will be cybersecurity when the world enters 2025. This would be because the pace at which the digital landscape has been changing seems to have accelerated almost to rocket speed, mainly because of the growing trend of adopting cloud technologies and the soaring efforts of people working remotely, all besides gaining more popularity of artificial intelligence and machine learning. The latter two will bring enormous benefits but will also increase risk factor. For instance, the more a company relies on cloud services, the easier it is for it to suffer from data breaches. Such services remain open windows for cybercrime if their access control is misused. The new post-pandemic world of working remotely implies larger numbers of employees accessing company networks from different locations across the country and further around the globe, making an even wider attack surface for cybercriminals. All this
calls for stronger and more proactive cybersecurity measures. With all these threats hovering over them, businesses and individuals have to come up with a solid cybersecurity measures to float above the fray. In this book, we will delve into the best cybersecurity practices that you need to embrace in 2025 and how you can start putting them in place.
Top Cybersecurity Practices for 2025

Zero Trust Architecture: The New Standard for Network Security:
Zero Trust Architecture is where cybersecurity is going for 2025. It literally states, by name alone, that it never automatically trusts any user or device because whether it's coming from inside the company network or outside it doesn't matter, as long as users and devices pass proper verification before access is allowed to resources.
Why Zero Trust?
Trusting the users and internal devices and relying solely on an ever-changing world of changing threats makes a perimeter-based security model far too naïve. In 2025, companies going all remote work and entirely relying on the cloud services to run will become almost impossible to define periphery clearly. Lesser risks of unwanted access only arise in Zero Trust where verified continuous access monitoring of such systems takes place.
Any business that uses Zero Trust right will:
Sensitively identify the data: Clearly mention what the sensitive data is and to whom it should be accessed.
Reinforce identity and access management tools to authenticate users using multi-factor authentication. Provide them with the least privileges needed.
Continuously monitor the accesses: Continuously monitors the network activity for any suspicious activity and stops lateral movement by attackers.
Segment networks: Distinguish different segments of the network such that only selected parts of the network are accessed by sensitive systems.
Through Zero Trust, organizations can be sure that their networks are safe even when users and devices are spread out in different locations.
Multi-Factor Authentication (MFA): The Essential Layer of Security
MFA is one of those cybersecurity features that have been needed for the past years, and it becomes even more critical in 2025. MFA is a process when at least two or more types of verification are used to unlock systems, thereby including a user's password, one-time passcode transmitted through the client's phone or other biometric data.
youtube
Why MFA?
Since password-related breaches remain the biggest category of attack vectors, MFA comes with another layer of defense. In fact, where a hacker could access the information through password use, that second factor-wisely perhaps it is using one's smartphone or their biometric information to unlock their information-collaterally blocks the attacks at that point in any case makes attackers' work much tougher in succeeding.
Implement MFA for all accounts: Every email account has MFA in place, along with cloud services, VPN, and any kind of system that holds sensitive information in it.
Implement biometric authentication: Utilize fingerprints, facial recognition, voice recognition as extra factor.
Educate the employees: Employees must be informed as to why MFA is so necessary and the fact that employees never bypassed MFA even for the reason of convenience.
One of the best methods to ensure that your accounts and systems are safe in 2025, due to increasing attacks on login credentials, is through MFA.
End-to-End Encryption: Securing Data against Interception
End-to-end encryption, in simple words, is the security feature where data is encrypted from the point of leaving the sender's side to when it is decrypted at the recipient's end. It is a must-have for sensitive communications, like financial transactions or private emails.
Why E2EE?
The most sophisticated hackers do not care for such traditional approaches of safeguarding their information or messages, that is, security via firewalls and encryption in which the information remains static. Any data can't be captured and decoded except for the authorized user in case of interception at the time of sending. It would be quite essential in the commercial organizations which handle sensitive clients' information and proprietary information.
Applying E2EE will:
Email, instant messages, and files should be encrypted before they leave the network.
Use secure messaging apps like Signal or WhatsApp. These have in-built end-to-end encryption.
Cloud data should be encrypted in transit and at rest.
As most attackers are targeting data while in transit, E2EE gives 2025 the much-needed cyber security practice.
AI and ML Cybersecurity: Protect before the attack:
AI and ML are revolutionary technologies that change the face of cybersecurity. Using AI-driven tools for anomaly detection, these technologies help businesses identify potential threats before the damage is done in real terms.
Why AI and ML?
Today, cyber threats have become highly sophisticated, and the volume of data that an organization needs to process in real-time has exponentially been increased. AI and ML can filter out huge volumes of data to recognize odd patterns and identify security risks. It typically happens much faster than traditional methods to let organizations respond to these risks appropriately before a breach happens.
Implementation of AI and ML:
AI-based threat detection solutions: Invest in the solutions that use AI to sense anomalies and inform the security team about breaches.
Automation of Response: Use machine learning capabilities to automatically counter various types of threats by blocking certain malicious IP addresses or isolating an infected system.
Monitor Behavior: It can monitor user behavior over the network using AI and detects anomalous behavior pointing to a breach.
Regular Security Audits: Periodic Cybersecurity Health Check
Right maintenance and system checks will always be in line, no matter how perfect the cybersecurity could be. Security audits make sure that businesses learn about their vulnerabilities and gaps in infrastructure before hackers take an opportunity to exploit such gaps.
Why security audits?
Threats are constantly evolving, and every day, new vulnerabilities are discovered. Security audits on a daily basis ensure that your cybersecurity is updated and capable of protecting the organization from any recent threats. Audits also ensure compliance with relevant data protection regulations within your organization.
How to Carry Out Security Audits
Scans on the systems to look for weaknesses and patch up the ones found.
Simulated cyberattacks to test one's defenses on vulnerabilities in a security strategy
Access controls should be audited; only those people with sensitive information and systems should have access.
Always, security audits should become the process of maintaining the posture of cybersecurity
Security Training and Awareness: Resilience Building at the Human Edge
Although technology represents the core of cybersecurity, humans just so happen to be some of the weakest links. Cybercriminals expose employees to phishing attacks and social engineering techniques. Therefore, some form of security training and awareness is necessary to effectively minimize risk.
Why Training?
An informed workforce is a shield against cyber attacks. Educate your employees on how to recognize phishing, proper password handling, and more best practices concerning cybersecurity. They can easily defeat an attack on this account alone.
How to Implement Security Training
Cybersecurity training: Train your workers on how to handle phishing attempts and data sensitivity in relation to a company's security policy.
Simulated attacks: Simulate phishing campaigns that will guide your employees in spotting malicious e-mails and other forms of social engineering attempts.
Culture of security: Establish a culture where information security is paramount, and your employees do not fear or think it's inappropriate to report unusual activities.
Well-trained workforce-the best defense against cyber threats by 2025 .
Cybersecurity for Remote Work Protecting the Distributed Workforce
Perhaps one of the biggest changes in the workplace in recent years is a switch to working from home or even in hybrid workplaces. This change brings about an equally pressing need for greater security protecting these remote workers.
Why Remote Work Security?
The larger numbers of work-from-home or remote locations provide access to company networks and data with different devices that increase vulnerabilities. Cybercriminals also use the remote workers as a route to the corporate network.
Conclusion: Secure your future in 2025
In conclusion, staying ahead of cybersecurity challenges in 2025 requires a combination of proactive measures, cutting-edge technologies, and a strong security culture. Implementing practices like Zero Trust Architecture, Multi-Factor Authentication (MFA), end-to-end encryption, AI and ML-based threat detection, regular security audits, and ongoing security training are essential for businesses and individuals alike. As we continue to embrace remote work and cloud technologies, ensuring robust cybersecurity practices will safeguard sensitive data and reduce the risk of cyber threats.
If you’re looking to gain in-depth knowledge and expertise to face these challenges head-on, I recommend exploring ACTE’s Cyber Security Training in Chennai and Cyber Security Online Training. These comprehensive courses helped me build a strong foundation in cybersecurity and prepared me for the ever-evolving landscape of digital threats.
1 note
·
View note