Don't wanna be here? Send us removal request.
Text
IT Security
Cyber attacks are a reality that never stops. The complexity and growth of the corporate assets of infrastructures, applications, clouds and IoT leads to the exponential growth of the attack surface. Effective IT Security requires visibility of all devices and all infrastructure in real-time but combined with a context: which devices represent a threat and what their capacity.
0 notes
Photo
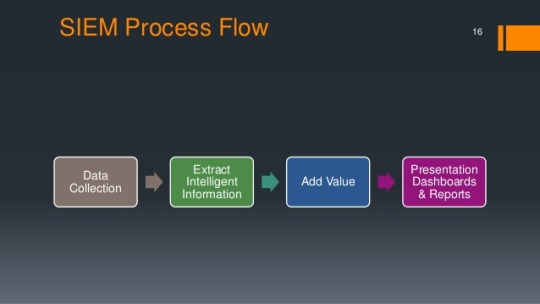
SIEM (Security Information and Event Management) SIEM software becomes a very important tool for IT infrastructure administrators, an indispensable component to dominate existing vulnerabilities in the system, to control the exposed surface.
#Automation#Continuous Integration#Data Protection#Datenschutz#Getting things done#IT Security#Log Management#SIEM (Security Information and Event Management)
0 notes
Text
Log Management
We use management tools to calculate and assign these time scales, as well as to use alerts and escalations to facilitate the response/resolution of incidents within the Log Management time. If you want to know what is happening on your network to get information about possible threats and stop them before they become an attack, then you should examine your records.
0 notes
Text
IT Security
We specialize in IT Security products and services, able to guarantee a high level of protection for the business network and individuals against, viruses, database encryption, and other cyber threats. Our technicians will establish a diagnosis of the vulnerability of their equipment or network infrastructure to prepare it to suit your needs and provide you with the peace of mind that your business needs.
0 notes
Text
SIEM (Security Information and Event Management)

Gronau IT Cloud Computing aims to help its customers protect their critical digital assets through a specialized portfolio of professional services. Our SIEM (Security Information and Event Management) solutions cover all stages of the service implementation, from the creation and management of security events and correlation rules to the filtering of security incidents 24/7. In particular, the solutions include the following services:
Identification of Information Systems that are considered critical for the business.
Analysis of the functional and security requirements of critical Information Systems.
Collection and analysis of the logos of critical Information Systems.
Send the flow design of these activity logs.
SIEM configuration in SaaS mode.
Integration of the Logos of the Information Systems considered in the SIEM.
SIEM service as a Service and support 24/7.
#SIEM (Security Information and Event Management)#microservices#It Security#seal kit#DevSecOps microservices
0 notes
Text
Continuous Delivery
Gronau IT Cloud Computing is a German company providing services in the following areas: IT infrastructure management; System Integration; Information Security - information security expert as a service; DevOps and IT Audit. We are able to Continuous Delivery the right level of service quality by applying best practices for maintaining the IT infrastructure with its relevant benefits: cost-effectiveness and guaranteed quality of service.
0 notes
Text
Log Management
Cloud computing is the most looked for after service known in the technology showcase; the explanation being that this service offers numerous benefits to the clients. The clients can practically get to it from anyplace and keep up Log Management reports or data online. For owners the advantage is that of decreasing the costing expended in recreating programming, presently renting the server space is progressively helpful and financially savvy.
0 notes
Text
Take Advantage of Cloud Computing With Experts of Leading Company
Cloud benefits additionally offers adaptability and Log Management to the clients in computing by setting aside time and cash for the supplier too for the client. The client won't need to sit around idly in designing data storage and data related different exercises that incorporate reinforcement. All these are dealt with by the service suppliers.

Storage Capacity-Storing and keeping up archives is basic for a client. The space gave is boundless cloud computing when contrasted with a PC. Furthermore this implies the client doesn't have to perform any framework up-degree also. The service suppliers don't require contracting labor to refresh servers, the client then again need not download refreshes for programming. These capacities are done on the server consequently.
Another preferred position that cloud offers the client is the component of portability and Continuous Integration which empowers in associating the client paying little mind to owning a framework. The client can associate from any framework planted anyplace given the state of internet availability. Presently, regardless of where you will be you will have the option to get to your data from any machine situated at any land area.
A key segment of cloud computing is the capacity to give sharing of assets. The assets accessible can be gotten to by anybody for all intents and purposes. This can likewise incorporate specified clients and gatherings or organizations offering archives to clients characterized through cloud computing. Chipping away at same report with different clients is simple particularly when more than one individual is included on an equivalent undertaking. Furthermore, you can contact the professionals of leading company to take advantage of cloud computing and Getting things done as well as other services for your organization.
#Log Management#cloud computing#continuous integration#continuous delivery#Cloud Computing in Berlin#getting things done
0 notes
Text
Take Advantage of Cloud Computing With Experts of Leading Company
Take Advantage of Cloud Computing With Experts of Leading Company
Cloud benefits additionally offers adaptability and Log Management to the clients in computing by setting aside time and cash for the supplier too for the client. The client won’t need to sit around idly in designing data storage and data related different exercises that incorporate reinforcement. All these are dealt with by the service suppliers.

Storage Capacity-Storing and keeping up archives…
View On WordPress
#Automation#Cloud Computing#Continuous Integration#Data Protection#Datenschutz#Development#Getting things done#IT Security#IT Sicherheit#Log Management#Microservices
0 notes
Text
Continuous Delivery
Business organizations additionally comprehend the significance of safeguarding the earth and this is the motivation behind why businesses have gone online and started to Continuous Delivery. These days, an ever increasing number of businesses are moving towards sparing vitality and this thusly causes them to spare our regular habitat. Much different nations on the planet lay accentuation on advancing condition neighborly items and services.
0 notes
Text
Continuous Integration

The organizational culture is based on the characteristics of the people and the way in which they communicate and relate to each other. Continuous Integration is a software development technique that allows changes to the code and is transferred to an environment where functional tests are performed and automated.
0 notes
Photo

Continuous Delivery The integration continues is a technique of software development is to combine changes periodically code in a central repository, building code and testing it frequently using static tests.
#Automation#Continuous Delivery#Continuous Integration#Data Protection#Datenschutz#Development#Getting things done#IT Security#Log Management
0 notes
Text
IT Sicherheit
Neue digitale Landschaften, der Umzug in die Cloud, die Ausweitung vernetzter Objekte, die Ankunft des Quantencomputers und die allgemeine Geschwindigkeit der digitalen Transformation verändern die Art und Weise, wie wir Geschäfte tätigen. Infolgedessen nimmt der Oberflächenangriff zu und die Bedrohungslandschaft entwickelt sich mit dem Eintreffen neuer und ausgefeilterer Angriffe rasant weiter. Erfahren Sie, wie die Hardware- und Softwarelösungen von Gronau IT Cloud Computing für IT Sicherheit die ultimative Sicherheit für Ihre wichtigsten Daten gewährleisten.
0 notes
Text
SIEM (Security Information and Event Management)
As a rule, IT infrastructure devices keep records of incoming requests as well as responses to them. We simply call them logos. SIEM (Security Information and Event Management) is an integrated suite of products for collecting, managing and intelligently interpreting events in the IT infrastructure. It helps in detecting incidents that may jeopardize the business of organizations.
0 notes
Text
IT Sicherheit
Wir sind heute als einer der führenden IT-fähigen Dienstleister bekannt und können auf eine bemerkenswerte Erfolgsbilanz bei der Bereitstellung funktionsfähiger und robuster Lösungen zurückblicken. Dies wird möglich, wenn wir uns fortwährend der Innovation und der Qualität verschreiben, Prozesse implementieren und verfeinern und technologische Kompetenz nutzen. Beauftragen Sie uns mit…
View On WordPress
#Automation#Cloud Computing#Continuous Integration#Data Protection#Datenschutz#Development#Getting things done#IT Security#IT Sicherheit#Log Management#Microservices#SEAL Kit
0 notes
Text
Continuous Integration
Every time a developer checks changes, a tool all sources, collects everything, runs all unit tests and immediately reports on the results. This cycle has come to be known as Continuous Integration. Their use of the word “integration” meant the unification of all pieces of software, when various programmers of the team, working traditionally, that is, in isolation from each other, get together and spend days or weeks together to make everything work. Practices like pair programming and automated builds have everything but the integration hell. If you can test this integration at the very beginning of the project, and iteratively develop this testing as your requirements and the system evolve, over time you will find yourself in a much better position.
0 notes
Text
IT Security

The mission of Gronau IT Cloud Computing is to create competitive advantages for customers through the use of the latest information technologies and their effective use. Our strength lies in the progressiveness and functionality of the solutions used, which is the key to the success of the company. Thanks to the expert team of IT Security specialists, the use of new, demanded technologies and their competent application in practice to create solutions that have no analogs on the market.
#IT Security#microservices#seal kit#DevSecOps microservices#SIEM (Security Information and Event Management)
0 notes