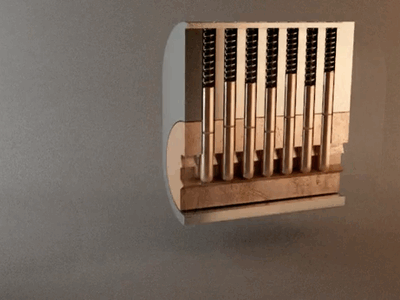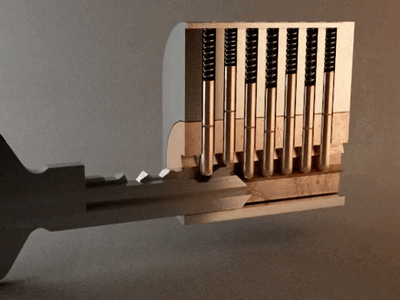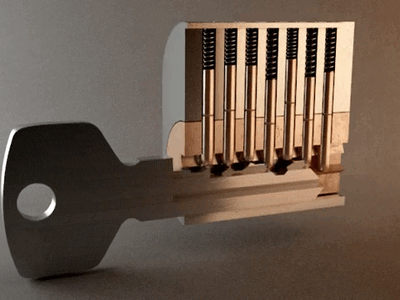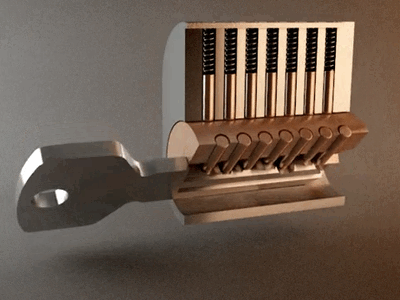
This is a page full of experiments and fun things I can do to break stuff. All actions are done on my own machines, my own network, and own property. I am not responsible for what people do with this information, don't break the law! Go to my twitter for security related things and stupid memes.
Don't wanna be here? Send us removal request.
Text
SQL Injection & The Dangers
SQL injection is super easy, and if you have a web app this can mean anyone with notepad and the ability to connect to the internet can run this attack. You will never know they got into your back end database. Let alone dumped all your usernames and passwords. The attack is simple, the mechanics behind it are complex because SQL databases are such a pain to deal with.

So here we have a basic database to look at movies and their information. Most people would look at this and just type their movie in and move on. However we will be a not so nice guy visiting this site. The site title gives me an indication that this page points to a data base so now I will test the application to see if it lets me inject special characters.

Typing “1′ “ in the search box gives me an error, telling me the DB admin has not used input validation on special characters. Let’s get some logins.

If you look at the URL box you will see I just typed some strings into the box. Anything after localhost/bWAPP/sqli_i.php?title= and &action=search is where I will be using SQL queries. In between those spots are the danger zone. So I input +order+by+150 and that tries to guess the maximum table length. The error tells me the table isn't that long. So I drop the number.

No movies were found! So that seems to be the end of the table after trying a little higher (8) and lower (6) 8 gave me an error, 6 gave me the same result so I know 7 is the end.

Notice in the URL I injected a new query. +union+select+1,2... is querying the DB and basically asking where are these tables located? The database gives me the result.

next, I inject user() into a table value. each one is different but for saving space I omitted my tries on other tables. So table 3 has a root login.... Interesting.

Replacing user() with database() tells the backend database to tell me the name of the database. This would mean table 3 is able to connect to the entire database library.

so now I query the DB to drop the column name, the layout and the table name. Look at the URL box to see the string. So the nice database gave me the main set and now I can go on from here, and dump information from wherever I want.

Want every single login on the database? What about every password? Just dump it, and there you go, basically root access to customer logins, login with top level people in the organization and then you have time to pivot and make a new attack or sell the information to people who would like to access some sensitive company information. So how do you stop people from looking at every user account in your database? Add input validation. Stop special characters from being entered.
0 notes
Text
bWAPP fun
I just started messing with the bWAPP virtual box and got root in a couple places.

Firing up my go to all in one scanner, SPARTA. Scanning the other hosts and am patting myself on the back for locking down all my hosts (even some that I personally could not configure) .24 has to be the BeeBox... look at all those services! Lets try looking at SSH.

So I ran sparta and came up with one login, root-blank. On trying to login on that port it, those credentials are blocked. Lets enumerate our users with SMTP VRFY

Ah yes, a nice list to load into hydra and start brute forcing.
Using a preloaded password list I get to cracking. Got the creds, got to root.

same with SQL

:)
0 notes
Photo

Made a gantt chart of my security + Cert path to practice some project management skills. Why? Because it is midnight and I can’t stop.
0 notes
Link
a Simple tool and not very special but this tool fast and easy create backdoor office exploitation using module metasploit packet. Like Microsoft Office in windows or mac , Open Office in linux , Macro attack , Buffer Overflow in word . Work in kali rolling , Parrot , Backbox .


43 notes
·
View notes
Text
Lmao. Logins should be unique. Security fail!

64 notes
·
View notes
Conversation
Sorry password must contain a special character
System: Enter password:
Me: ScoobyDoo
System: sorry password must contain a special character
Me: ScoobydooFeaturingBatman
421 notes
·
View notes
Text
Scan the network, find the target
Disclaimer: These actions are on my own network using my own virtual machines, this is for educational purposes only.
First off lets see what we are starting with, Kali VS a new install of windows 7 professional, no added AV or firewall rules just a basic, starting machine. Lets get the IP of my kali machine, being on the same logical network I can assume the target is on the same subnet.

(ignore the blocked out IP addresses the screen capture kinda messed up here)
Time to start finding my targets IP! Fire up Metasploit and run nmap

So ignoring the first 2 IP addresses I have 3 hosts up. .254 is useless so my only IP is highlighted. Looks like the target IP and MAC, maybe we can get some foot printing on the OS.... Wait a second... If I did an Nmap straight from MSF my IP would be shown, looking at a wireshark capture on my windows machine, My cover would have been blown.

Time to run my traffic trough a proxy chain, used some random proxies strung together and each test yielded TCP connections from China and Afghanistan so I am good! One issue, all ports are filtered. Running a SPARTA scan gave me an open port on Netbios but I want more options. Time to fire up Nessus.

After about 4 hours of loading Nessus was ready to run and decided to scan the entire subnet out of curiosity. Nessus turned up no vulnerabilities on my real target or my kali machine. In the next section I will just ignore breaking into the machine trough the network and send over a friendly, happy trojan horse over with some social engineering vectors.
0 notes