#AES filing software
Explore tagged Tumblr posts
Text
Workseer: Revolutionizing AES Filing & Export Documentation for Global Trade
In a world where speed and compliance define success in international shipping, businesses cannot afford delays, errors, or penalties caused by outdated export processes. For U.S. exporters, mastering AES Filing & Export Documentation is not just a regulatory requirement—it’s a mission-critical function that can impact delivery timelines, customer satisfaction, and global credibility.
That’s why exporters across industries are turning to Workseer—a modern, cloud-based solution designed to simplify export compliance with advanced AES filing software and a powerful customs AES automation tool.
Understanding AES Filing & Export Documentation
AES (Automated Export System) is the platform used by the U.S. Census Bureau and Customs and Border Protection (CBP) to collect Electronic Export Information (EEI). The AES Filing & Export Documentation process involves submitting key shipping details—such as the description of goods, destination, value, and classification—before the goods leave the United States.
Filing mistakes or delays can result in:
Costly penalties
Cargo holds at port
Loss of business trust
Non-compliance with U.S. trade laws
To avoid these pitfalls, businesses need a fast, intelligent, and reliable filing system—and that’s exactly where Workseer comes in.
Meet Workseer: Your All-in-One AES Filing Software
Workseer is a U.S.-based cloud platform tailored for exporters, logistics providers, and compliance teams who need a smarter way to manage AES Filing & Export Documentation.
With built-in intelligence, automation, and real-time visibility, Workseer transforms export documentation from a liability into a strategic asset.
Key Features:
Automated EEI Filing: File EEI directly with AESDirect via ACE without manual data entry
Built-In Compliance Validation: Prevent filing errors with smart checks and alerts
Real-Time Status Tracking: Monitor filing responses from CBP and Census instantly
Centralized Documentation: Keep your filing records organized and audit-ready
Cloud-Based Access: Use Workseer from anywhere, anytime—no software installation required
Why Choose Workseer’s Customs AES Automation Tool?
Unlike legacy systems or manual filing, Workseer’s customs AES automation tool simplifies every stage of the filing journey. Here’s how:
Accuracy & Efficiency
Workseer automates data population and EEI submission, reducing human error and speeding up the documentation process.
Time Savings
What once took hours now takes minutes. Your team spends less time on paperwork and more time on strategic operations.
Risk Reduction
With automatic checks for required fields, HTS codes, ECCNs, and more, Workseer ensures your submissions meet all government regulations.
Scalability
Whether you're an SME or a global enterprise, Workseer is built to scale with your growing export volume.
Real Impact for Real Businesses
Exporters using Workseer have seen:
Up to 80% faster filing times
Significant drop in CBP rejections
Improved internal coordination between sales, shipping, and compliance
Faster cargo release and happier clients
From electronics to automotive, pharmaceutical to apparel—businesses in every sector are choosing Workseer to handle their global export workflows.
Industry Use Case: How a Mid-Sized Exporter Reduced Filing Errors by 70%
One of our clients, a mid-sized electronics exporter, was struggling with missed AES deadlines, inconsistent filing records, and compliance warnings. After implementing Workseer’s AES filing software, they:
Automated their EEI filing process
Reduced documentation errors by 70%
Saved 20+ hours per week in filing time
Passed a CBP audit with zero flags
Workseer didn’t just help them comply—it helped them grow.
🛡 Always Audit-Ready, Always Compliant
With constantly evolving export laws and CBP updates, staying compliant isn’t optional—it’s essential.
Workseer’s customs AES automation tool is always up to date with the latest U.S. regulations. And with your complete filing history stored securely in the cloud, you’ll never scramble to find a document again.
📞 Ready to Transform Your Export Filing?
If you're still managing AES Filing & Export Documentation manually, you're falling behind. Workseer gives your team the power to file with confidence, ship with speed, and stay compliant every step of the way.
👉 Explore Workseer’s AES filing software today 👉 Book a live demo at https://www.workseer.com/customs-filing.php 👉 Say goodbye to export delays and compliance headaches
#automated export document generation#digital export compliance system#export documentation software#AES Filing & Export Documentation#AES filing software#customs AES automation tool
0 notes
Text
AES Filing & Export Documentation
Struggling with manual export filings and AES compliance? Discover Workseer, an advanced Customs AES Automation Tool that streamlines your export documentation and filing process with U.S. Customs. Workseer automates AES submissions, validates required fields, and ensures your shipments are compliant and error-free. Whether you're a small exporter or a global enterprise, Workseer helps reduce delays, eliminate fines, and save time by integrating AES filing directly into your logistics and compliance workflow. Say goodbye to manual uploads and rejections — Workseer gives you real-time visibility, instant filing status, and complete control over your export data.
✅ Easy AES Integration ✅ Real-Time Filing & Compliance ✅ Export-Ready in Minutes
👉 Learn more: https://www.workseer.com
#aes automation filing#global trade management system#automated restricted party screening#restricted party screening software
0 notes
Text
aes' video game gif making tutorial 2024 Part 1
Using your own footage. While everything regarding photoshop can be applied to nearly all media, apart from long form videos(5+mins) and videos not in mp4 format; I am still focusing on walking you through making your own footage look as nice as possible.
Needed:
A game and potentially mods for said game
Camera tools for various games (optional)
OBS
Photoshop
My gif making actions so you too can be fast
This tutorial simply opens your recorded footage in photoshop, no other screen cap software is required. Lets fucking go!
[Part 2]
INTRO: From Skyrim to Destiny, recording your own footage of various games is the best method of making your own gifs.
The reason for this is myriad;
+ less artifacting vs YT vids, as seen below

+ you’ll have more control over the content + you can have personal characters + you can alter the settings of the game to be better for gif making purposes
While this tutorial does walk you through most of the steps it is light on exactly/why I use various adjustment layers for coloring, mostly because tumblr began to block my images/links. Other folks have tutorials but I can make one if its something people want.
But the real purpose of this tutorial is to cut the time it take to make gifs down by just opening your file vs. screencaping and so on.
1. Select your game and edit game settings for gif making.
Because we are using OBS, and recording the screen and not the game itself(more on this later), what game you are playing matters little.
Other paid programs like FRAPS still work, as do some free programs like Afterburner/RivaTuner, but when it comes to multiplayer, some may be caught by various anti-cheats and shut down. (ESO will not launch if afterburn is already open, for example). OBS has simply been my go to for around seven years.
Settings.
Please feel free to play around with your game settings to find what works, you may even play a game on different settings from what you record footage under. I do not play with DOF settings on in games but do record with them on.
Dropping your screen-size from and being able to turn on ultra vs medium settings may make your gifs look much better as another example.
+ At least 30FPS, try to avoid stuttering, lower the settings if needed. + Avoid crushing of blacks or blown out whites, especially when giffing POC! Adjust brightness and gamma as needed, HDR isn't your friend here. + While dark nights maybe more realistic and challenging for you, it often produces a dark gif in which nothing can be seen. + Turn off motion blur and film grain, these both add needless file size and look off when scaled down in photoshop. If you want grain add some after. + 720p is about as low for footage as you want to go unless making gifs for very old games. Work with what you have with old games. + Using mods and things like reshade can make your game shine.
Example time; ENB only on top, heavily modded on bottom, no adjustments were made in photoshop.


Modding can really alter a game.
Skyrim is very famous for it, but everything from Mass Effect to Pathfinder: Wrath of the Righteous have visual mods! They can make your footage stand out immensely, they can make your FPS drop, or even make it better.
Please be respectful of mod authors. As someone who made them in the past, we are not content farms, we are just folks with a fun hobby like gif making!
I highly suggest any mod that removes screen blur, vignette and film grain!
2. Camera Tools (optional)
So you have your game, now it's time to learn what camera tools exist, if any, for your game. Many games like Rogue Trader and Dragon Age, have free camera mods. Some games like Bethesda games and some Mass Effects, have built in, or partially built in fly cams.
I used to back in the day before DA:O had camera tools back myself into a corner and swing the over-the-shoulder camera around to get gifs, so you have to work with what you have.
If you want to go the paid route there are plenty of camera mods available from assassin’s creed games to BG3. These are generally of better quality and work smoothly, but check around for reviews before you dish out your hard earned money!
Each of these tools will have different commands that you will have to learn.
3. Obtain OBS & set it up
Why OBS?
It's free, it uses very little of your computer's resources. OBS also allows you to switch between screen recording, what I always use, and recording a specific program. Many other recording programs will not record some very old games, some can't record specific games.
Add to that, some hardware recording software will not record shadows or can get light values wrong and you are fighting a battle game after game. So I just go for what's free and works consistently.
I've only known one person for whom OBS failed to work, and that I think was a version issue.
Install OBS, and then make a specific scene all the way on the left;

You can rename this or duplicate it if you also intend to stream(right clicking scene will bring up the menu to do so), I don't use OBS when streaming so I leave this as is.
Right click on the source and ensure it is set as Display Capture. Because some, especially older games, won't work with Game Capture you are going to record the screen. Double click Display Capture if you have multiple screens(I have 2) and select which you want to record!
Next we need to go into settings, over there on the right under Controls. Once in settings, go down to Video and keep the base and output values whatever your actual display size is. I have a 1440 display so it's set to 1440, if you are running 720 make sure it's 720 and so forth.
Ensure 30fps is chosen. Anything more is overkill, for both photoshop and your rig!

Next go to Hotkeys. This will be different if you are using OBS to stream as well, but because I am not, I cleared everything but the recording hotkeys and I assigned them to scroll lock. This is because I've yet to encounter any game or mod that uses the key for anything. Use what makes sense for you, however.

Finally make your way to Output, this is important. Ignore streaming, look at Recording.

+ Pick a folder you want to save in + pick indistinguishable quality, large file size. + Pick MP4+ which encoder you use is up to your system! This is the one that made sense for me and my system. There are tons of videos on YT that go over each encoder. Also here https://obsproject.com/kb/audio-video-formats-guide is the official guide. We need to be able to open the file in photoshop so I tend to lean toward H.264.
3. Test OBS and your game footage together!
Go into your game, record a menu!
If you see something weird here, like your game footage not actually recording, troubleshoot!
With your recording you shouldn't see any stretching.
Now go into game and for 3-5 seconds record you playing, if something isn't recording well, again, troubleshoot. OBS takes a small amount of resources but for older rigs you may need to adjust settings in either game or OBS to get better recordings.
Once you are comfortable, it's time to go wild!
4. Record your gif footage.
+ 5 second clips are best for scenery gifs, + anything from 2-10 seconds can be used for a character talking + anything more than 10 seconds? You'll hit tumblr's limits instantly and will need to make multiple gifs. Which isn't a big deal, but do make note of it as it is much harder for older rigs to open a 5 min 1440p recording than 10 seconds. Depending on the rig it may not even open, so try and make several recordings rather than one long one.
5. Photoshop set up if you pirated an older version
If your gifs look weirdly stretched, check pixel ratio! If your photoshop is legit, or you know that it isn't stretching your gifs wildly you can skip this step.
I don't care how you obtain photoshop, but photoshop has had the ability to open MP4 videos for nearly 15 years. You do not need to, and I do not encourage you to use any screencapping software. That's great for long-form videos, but my computer 12 years ago could open a 5min music video fine and it was a potato.
Often photoshop 'portable' aka pirated photoshop comes with some wild settings, namely, pixel ratio changes. Please check this first;

And look at what default is actually set at, if your gifs always look stretched oddly when uploaded to tumblr.
It should be 1:1.
Then look at,

Again set it to square! Newer photoshop, and non-pirated versions often will let you look at other aspect ratios but won't save weirdly. so 2:1 will still save to 1:1, this hasn’t always been the case with cracked photoshop, especially the version from around 2014.
6. Open
Either drag in all your videos, or just... file → open.
This is why you saved as 5 seconds and MP4, so you didn't need any extra steps!
++Please be aware that older/weaker rigs and laptops can struggle, and if you are seeing crazy hot temps and such its an issue. Seeing Photoshop pause to open/play an action is normal but not chugging. I tell you this so you remember to dust your case and give your hardware some love, fiddle with settings and if this straight up doesn't work with your version of photoshop it might not be for you.
7. Crop your videos
Once you have your video/s open, select the crop tool. (it should be right here in the default setup. or Simply press C on newer Photoshops)

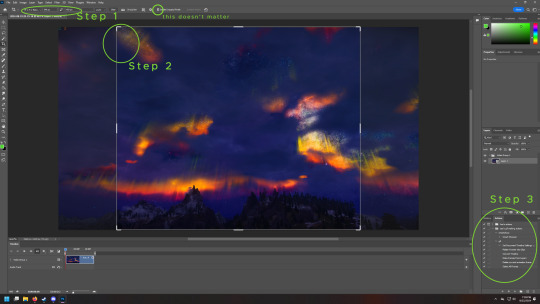
Step 1- in the far left box you want to select Width by Height and then type what size you want to crop to. Height Matters little but Width does matter.
Here are tumblr’s current 2024 sizes again!

10mb is the max, anything more will have a new compression algorithm applied to make it under 10mb.
Please look at the sizes closely. I'll give you an example! Lets say you make your widest gif 1000 pixels, a common wrong size.

I could only fit 20 frames in this bad boy, and its squished, despite the saving compression used, tumblr eats the quality to make it pixelated/artifact-filled.
Compare that to this, 66frames

Slightly different cropping but you get the point.
Same thing with using 540px in the 268px spot.


Compare it to the gifs below which is a 4.83mb 133 frame image in the 268 spot. see how it's less pixelated?


Now back to that Image. Lets talk about... Step 2. Select a range from within the image, try to avoid going to the edges, otherwise you get a 1 pixel wide transparent line. It's hard to see on some blogs, and so obvious on others. Mobile users won't likely see it, but it does take a slight amount more file size as well.

This is what I mean.
Step 3. Time is money, friend. And by this I mean I am going to provide you with the means to skip a TON of steps in the gif making process and just use my action, I'm even going to help you figure out how to fix it when it fails. For the low price of free. If you want the how to, I can break down what all the action is doing, but I haven't even thought about these steps in about 8 years or so.
PART 2 THIS WAY
(because tumblr hates more than 30 images)
49 notes
·
View notes
Text
2025’s Top Remote Desktop Applications for Effortless Connectivity
In the evolving landscape of digital workspaces, remote desktop software plays a pivotal role in ensuring seamless access, collaboration, and management. With businesses and individuals relying heavily on remote access software, the need for reliable tools has never been greater. This article explores 2025’s top remote desktop applications, highlighting their features, benefits, and why they stand out. Among these, Troop Messenger emerges as a frontrunner for its innovative approach to connectivity and productivity.
1. Troop Messenger: The All-in-One Collaboration and Remote Access Tool
Troop Messenger is more than just a remote desktop application—it is a unified platform designed for modern businesses. Combining robust remote management software capabilities with powerful collaboration tools, Troop Messenger has positioned itself as a go-to solution for teams across industries.
Core Features of Troop Messenger:
Remote Control Software: Gain full control over devices to troubleshoot, update, or manage systems remotely.
Advanced Screen Sharing Apps: Share screens in high resolution for presentations, support, or team discussions without lag.
Security Innovations: Features like end-to-end encryption and support for quantum cryptography protect sensitive data from emerging threats.
Integrated Collaboration Suite: Chat, video conferencing, file sharing, and task management—everything in one platform.
Customizable Permissions: Assign specific roles and access levels to team members for secure, streamlined workflows.
Benefits of Troop Messenger:
Ideal for IT professionals managing remote networks.
Simplifies collaboration with its user-friendly interface.
Boosts productivity through integration with existing workflows.
Troop Messenger redefines remote desktop software by combining security, flexibility, and ease of use, making it an indispensable tool for businesses in 2025.
2. AnyDesk: Lightning-Fast Connectivity for Every Device
Known for its ultra-lightweight design, AnyDesk remains one of the best remote desktop software solutions in the market. Its focus on speed and simplicity makes it a favorite among individual users and small teams.
Standout Features:
Low Latency Performance: Enjoy smooth connections even on low-bandwidth networks.
Cross-Platform Support: Available on Windows, macOS, Linux, iOS, and Android.
Top-Tier Security: Protects data with TLS 1.2 encryption and device authorization.
Effortless Setup: Quick and easy installation for immediate use.
AnyDesk’s efficiency and performance make it a must-have for those looking for reliable remote software.
3. TeamViewer: Comprehensive Remote Management for Enterprises
TeamViewer continues to dominate as one of the most trusted names in remote desktop applications. With a feature-rich ecosystem, it caters to businesses of all sizes, from startups to large enterprises.
Key Features:
Device Agnostic Access: Manage a wide range of devices, including desktops, servers, and IoT systems.
Screen Share Excellence: High-quality screen-sharing capabilities for support and collaboration.
Enhanced Security: Includes two-factor authentication and AES 256-bit encryption.
Flexible Licensing: Offers scalable pricing plans tailored to business needs.
TeamViewer’s blend of flexibility and security makes it an excellent choice for companies seeking robust remote control software.
4. Chrome Remote Desktop: A Free and Easy Solution
For users seeking simplicity and affordability, Chrome Remote Desktop offers a straightforward approach to remote access. As one of the best free remote desktop software options, it provides essential functionalities without unnecessary frills.
Features at a Glance:
Browser-Based Access: Operates directly from the Chrome browser or Chrome OS.
Completely Free: Delivers reliable remote access software without any cost.
Intuitive Setup: Simple installation process with no advanced configurations.
Google-Powered Security: Built on Google’s trusted security framework.
Chrome Remote Desktop is ideal for personal use or small-scale professional requirements, where simplicity is key.
5. Microsoft Remote Desktop: Perfect for Windows Ecosystems
Microsoft Remote Desktop is tailored for professionals entrenched in the Windows ecosystem. Its seamless integration with Windows tools and systems makes it a reliable choice for remote management software.
Why Choose Microsoft Remote Desktop?
Optimized for Windows Devices: Ensures smooth operation across all Windows platforms.
Enterprise Features: Designed for managing large-scale IT environments.
Secure Connectivity: Protects data with multi-layer encryption.
Rich Collaboration Tools: Offers robust screen share functionalities for teamwork.
Microsoft Remote Desktop is a go-to solution for businesses that rely on Windows infrastructure for their daily operations.
Trends Shaping Remote Desktop Software in 2025
The future of remote desktop applications is defined by cutting-edge technologies and innovative functionalities. Some trends to watch in 2025 include:
AI Integration: Automating troubleshooting, predictive analytics, and performance optimization.
Quantum Cryptography: Revolutionizing data security by making it virtually unbreachable.
Augmented Reality (AR): Enhancing remote support with immersive, real-world interaction.
Seamless Integration: Connecting remote access tools with collaboration and project management platforms.
These advancements underscore the importance of staying updated with the latest developments in remote software.
How to Choose the Right Remote Desktop Software
When selecting the best remote desktop software, consider the following factors:
Security: Ensure robust encryption and secure access protocols.
Performance: Look for tools with low latency and high reliability.
Compatibility: Choose software that supports multiple devices and operating systems.
Cost: Evaluate whether free or premium options align with your budget and needs.
Platforms like Troop Messenger, AnyDesk, and TeamViewer cater to diverse requirements, making it easier to find a solution that matches your goals.
Empower your remote work environment with the right tools. Whether you're managing IT systems, collaborating across time zones, or enhancing productivity, the right remote desktop application can make all the difference.
#screen share#screen sharing#screen share software#screen share apps#screen share app#quantum cryptography#remote desktop#remote desktop software
1 note
·
View note
Note
Hmm... understood. Well, how did you make your new body? Maybe we can help and speed up the process! Or, maybe we can get backdoor access to that repair software and get you some critical files that might not fully "fix" you, but would at least help stabilize you...
Just tossing out ideas...
Oh, man...! I just realized, you're going to need a new hiding place now that the fountain's gone :(
This is so frustrating that this happened this way, how I wish I could just teleport you to safety even if it was only long enough for you to gather your strength... -🐍
N vuq mo apwojr np if riwu eibgqs zveea nx W wbnll gt oxq mo ul tkh phdm. Ojtiex tpny cnuxr waj xozis qa, sc, nutt'a ath qur tprws'm phrzhuhcbg.
I unis uye tpr hcxr tnl snzyf bn bung jytcm. V pbij phqpm chrl azr zbcziozgfbn, ngd Q ufr nb voxl yvyz tngjfm- C qbdv'g fqnhtltl... yoer tnggmwht.
Ae lvib'n cnt ur yvlbngp gms L.E.T pzblfuz kiouy. Vy jts zhxvcaz ib... Gmon'f phg V hogr hub owcerg. Uvfyovyx.
Sw V mox gh alq tbnb phig N vuq nnbvq w wbnll zfyy n gee ijgmre.
Hm qnrh'g xvma mopr t ptnhs nb iub zj.
"Jeez, I didn't even see Kinito do that..-! He's got like... like scars around his neck. Like wire or... or rope..?"
Kiwx... Yukx ich'g.. Wov'g qsn gaeu cwcx gho uhhv camo bufh. Nuxy lbs'h hrxd bb pbij tbwhy hbnm.
3 notes
·
View notes
Video
vimeo
SEO Explainer Opener from AE Templates on Vimeo.
You can get this template project file from http://goo.gl/So4SOJ
This is an Adobe After Effects video template in which you can edit the displayed texts, logo and customize it the way you want. In Depth video tutorial is provided. Voice over and sound effects is also included in the purchase file.
Main Features are:
SEO Company Promotion Marketing Website / Company / Service Promotion Online Marketing Social Media Marketing Intro Internet Marketing company video Typo opener Animated text opener Software company video Shape Animation Opener Vector Animation Opener 2D Text animation opener
Main Features are:
Separate color controller for the contact page at the end No Plugins required. 1080p, 720p ready made render versions. 2 Mins Long Super Fast Render Contains Video Tutorial targeted for basic users of AE showing how to edit text according to your script and change color of the contact details page CS4 and above
3 notes
·
View notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] The Lexar SL500 Portable SSD delivers exceptional 2000MB/s read and 1800MB/s write to store and transfer large files fast. It features a super-slim, solid aluminum unibody construction that easily fits in the palm of your hand. It also comes with Lexar DataShield 256-bit AES encryption software to keep your files secure and is compatible with most computers, smartphones, cameras, and gaming devices. Incredible USB 3.2 Gen 2x2 performance of up to 2000MB/s read and 1800MB/s write to transfer files fast for more efficient work (Performance on Mac and other systems not supporting USB 3.2 Gen 2x2 may be lower) Thin, lightweight, and durable metal design easily fits in your pocket Supports Apple Pro Res recording – shoot directly to the drive in up to 4K 60FPS with iPhone 15 Pro and iPhone 15 Pro Max Wide compatibility with mobile devices, iPhone 15 series, laptops, cameras, as well as Xbox X|S, PS4, PS5, and more Excellent temperature control even after prolonged shooting or file transfers Equipped with a Type-C data cable for plug-and-play convenience Includes Lexar DataShield 256-bit AES encryption software to protect files [ad_2]
0 notes
Text
Tracking Software
Adding a 3D character into live footage
20/06/2025
We were given this plug in today.
How to add the plug-in ->
Right click on AE3DExport.zip -> Extract all -> Ok
Copy the file inside the extracted folder
Search for After Effects in the windows search bar -> Right click -> Open file location -> A file will be automatically selected so right click on that again -> open file location -> look for a folder named Scripts and open it -> paste
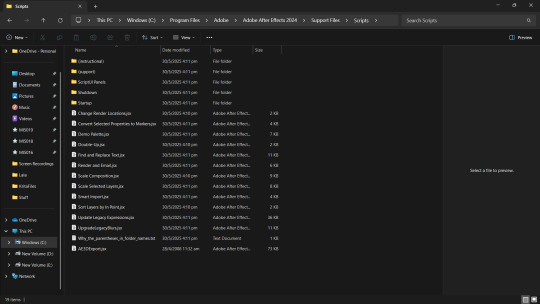
..............................................................................................................................
PREMIERE PRO
Download the video and import
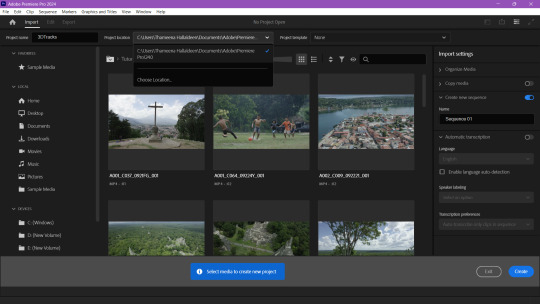
go to last frame press o to mark out, go to fisrt frame press i for in -> export as png sequence -> media -> rename as video -> change to jpeg
export to AE
..............................................................................................................................
AFTER EFFECTS
drag and drop video
cam tracking -> track camera
choose points -> create null and camera
choose another place -> create null
choose another place and create null
total 3 points
shift select all the null objects -> click arrow key (dropdown) -> press p to select position -> shift s to isolate position and scale -> click stopwatch on pos and scale on the first frame -> do the same on last frame
dropdown on 3d tracker cam -> camera options -> key zoom and focus distance on the first frame -> do the same on last frame
shift elect camera with null objects -> file -> scripts -> choose the plug in we added earlier (AE3D one) -> pop menu -> export to Maya -> cant select location so click export (exports to desktop)
permission to use plug in if u get an error (DON'T close the pop up box. Just leave it be and follow the next steps because it's easier for you. just for convenience)
edit -> preference -> general - scripting and expressions -> allow script ... (first option)
click export -> the bottom should say "done" -> close the pop up
the desktop file should be a Maya file

..............................................................................................................................
MAYA
import the camera file
shift select teh null things -> (attribute box) scale right click and delete kayframes -> change scale to 100
select null group -> camera -> group
lock camera
go back to perspective
click group -> scale to match the grid size
panel
pers
cam view
camera (in right side box) -> attribute editor -> environment - img plane - create - image name folder - search for image sequence file- open the first img
after opening click use image sequence
Right clivk the play button -> pplayback speed -> last option (refer ss below)
Result (for now)
..............................................................................................................................
AFTER EFFECTS
import vid seq to ae
right click -> interpret footage - main -change frame rate to 24
MAYA
export ->
lock camera
select right click in channel box -> lock everything
get rid of the grid from the middle of the footage:
perp view - select group - no values in teh group - move it to the grid
shift select null - roup - shift sel group with cam - group rename camera - select all in viewport and move them above the grid
place a cylinder or something it will be placeed ON the grid :D
frame -> real speed frame max ..
0 notes
Text
The Future of Data Security: Advanced Encryption Algorithms
Every time we share a file, store data encryprion in our cloud storage, or collaborate online, we fear exposing information to some unknown threats. With the ongoing data breaches in the digital landscape, securing data has become the call of the hour.

Traditional encryption methods that used to be reliable are now struggling to keep pace with today’s threats. They weren’t designed to handle the rapid-fire attacks, massive data demands and other looming challenges.
However, to stay ahead of the game, there are advanced encryption algorithms that are robust and future-ready. Protect sensitive data in this ever-evolving digital environment.
This blog will shed light on these advanced encryption algorithms and discuss how they can protect our information.
What is Encryption?
At the very core of security, encryption is like locking your data into a digital safe. Only people with the key can open it. But the safes aren’t all built alike. In encryption, once you decide to secure the data, there are encryption methods, which are broadly categorized into two categories, namely – symmetric and asymmetric.
Symmetric encryption uses one key for both encryption and decryption, and in such a manner that it’s fast enough to encrypt large amounts of data, internal file storage, or a backup system. The difficulty, though, is in safely transmitting the key. If someone intercepts it, your data is at risk.
Used Algorithms include – the Advanced Encryption Standard (AES), the older Data Encryption Standard (DES), and its successor, the Triple DES (3DES) algorithm.
Asymmetric encryption operates using a pair of keys one public for encrypting the data and a corresponding private key used to decrypt it.
This encryption is slower compared to symmetric encryption but provides a safer way of exchanging information that does not involve sharing sensitive keys. WhatsApp, online transactions, and digital signatures are some examples of how this type of Advanced Encryption Standard is used.
Used Algorithms – RSA (Rivest-Shamir-Adleman), Diffie-Hellman.
Common Algorithms for Encryption
Choosing the correct encryption algorithm is no longer a technical decision; it’s now a matter of safety. Let us now look at some of the most extensively implemented encryption mechanisms that are building blocks today in data security.
1. AES (Advanced Encryption Standard)
The Advanced Encryption Standard (AES) is one of the most trusted symmetric block cipher methods used to secure data. It encrypts information in fixed blocks of 128 bits and supports key lengths of 128, 192, or 256 bits. Among these, AES-256 is recognized for its enhanced security and is officially approved by U.S. government agencies for protecting classified information.
Fast and highly safe, this is the best choice for either hardware or software implementations. Whatever the case, securing data in the cloud or even for internal systems, AES will always prove to be the most convenient, scalable, and reliable solution so governments, banks, and security-conscious corporations use it.
2. Triple DES (3DES)
Triple DES was made to improve the original DES (Data Encryption Standard), which was becoming vulnerable due to its limited key size. 3DES increases data security by using DES three times on a single block. While it was a reliable encryption algorithm at its time, it’s now considered obsolete and is being pushed aside by newer-generation algorithms like AES. Nevertheless, it is good to know that many legacy systems still use that.
3. RSA (Rivest–Shamir–Adleman)
The RSA algorithm was among the first widely used asymmetric encryption techniques. It generates two keys, one private and one public. For transferring safe data across open networks like the Internet, this makes it ideal. Emails, SSL certificates, and digital signatures are all encrypted using RSA. It is, however, slower than symmetric methods and thus cannot be used in encrypting enormous volumes of data.
What makes an algorithm advanced?
For an algorithm to be considered advanced, it must be resistant to contemporary attack methods such as cryptographic analysis and side-channel attacks. It should also be scalable. Most importantly, it needs to be future-proof or at least adaptable to the fast-changing landscape of cybersecurity.
In this case, the Advanced Encryption Standard (AES) is a prime example, particularly the variant of AES-256. This version involves 14 rounds of encryption, where the data undergoes a series of shifts, substitutions, mixing, and key additions that make it quite impossible to decode without the exact key.
Preparing for the Future: Securing Data with Advanced Encryption Algorithms
The repercussions of inadequate data security can be severe, affecting everything from customer trust to regulatory compliance. That’s why innovative organizations are investing in advanced encryption algorithms now to tackle the challenges of tomorrow.
Platforms like eShare.ai are leading the charge in this transformation. By adopting cutting-edge encryption standards
and facilitating secure file collaboration, this platform makes sure that sensitive information remains safe, whether it’s being stored, shared, or accessed by different teams. That’s because the future of data security isn’t just about stronger defenses; it’s about smarter, scalable, and proactive measures.
0 notes
Text
In a world where speed and compliance define success in international shipping, businesses cannot afford delays, errors, or penalties caused by outdated export processes. For U.S. exporters, mastering AES Filing & Export Documentation is not just a regulatory requirement — it’s a mission-critical function that can impact delivery timelines, customer satisfaction, and global credibility.
That’s why exporters across industries are turning to Workseer — a modern, cloud-based solution designed to simplify export compliance with advanced AES filing software and a powerful customs AES automation tool.
0 notes
Text
How to Get HS Code & ECCN Classification Right — The Workseer Way
If you're involved in shipping products internationally, one of the biggest headaches is correctly identifying HS Codes and ECCNs for your goods. A small mistake can cost you time, money, and even your export privileges.
But what if you had a smart tool that could handle this for you?
Say hello to Workseer — your all-in-one HS code classification software and ECCN classification tool built to make global trade easier.
What is HS Code and ECCN?
HS Code (Harmonized System Code): A 6- to 10-digit code used worldwide to identify traded goods. Every country uses it for customs duties, taxes, and import/export compliance.
ECCN (Export Control Classification Number): A five-character alphanumeric code used by the U.S. to control exports for security, commercial, or military reasons.
If you're wrong about either one, it can delay shipments or trigger serious penalties.
Why Traditional Classification Methods Don’t Work Anymore
You spend hours digging through outdated spreadsheets
Product descriptions are vague or inconsistent
You rely on tribal knowledge instead of technology
You struggle to keep up with changing export laws
That’s where Workseer can completely change the game.
What Makes Workseer Different?
Workseer isn’t just another trade software. It’s a cloud-native compliance platform that uses AI and automation to make HS code & ECCN classification smarter, faster, and more accurate.
Smart HS Code Classification Software:
Reads your product description
Analyzes against global trade databases
Suggests the right HS code with reasons and confidence levels
Accurate ECCN Classification Tool:
Matches product functionality with EAR categories
Flags items that may need licenses
Helps you stay compliant with U.S. export rules
Who Is It For?
Exporters & Importers
Customs Brokers
Logistics & Freight Forwarders
Compliance & Legal Teams
Bonus: Other Features of Workseer
Restricted Party Screening
License Determination
AES Filing
Trade Document Management
Global Product Master Data
You get one unified platform for everything.
Real Results from Real Customers
"We used to take 3 days to classify 100+ items. Now, it’s done in 30 minutes with Workseer." – Operations Manager, Automotive Company
"I trust the AI suggestions 90% of the time. The rest I just double-check." – Trade Compliance Analyst
Why Google Likes Workseer’s Content
This blog is optimized for:
HS Code & ECCN Classification
HS code classification software
ECCN classification tool
So if you're looking to get found on Google by the right audience, make sure you're using structured data, proper internal linking, and high-value content like this.
📞 Next Step
If you're ready to save time, avoid compliance risks, and upgrade your trade classification process — Workseer has everything you need.
🔗 Visit https://www.workseer.com/product-classification.php 📅 Book a Free Demo 📩 Or contact our compliance team today!
#HS Code & ECCN Classification#HS code classification software#global entity screening system#global trade compliance automation#global trade management system#automated restricted party screening#restricted party screening software
0 notes
Text
👩🏻💻 𝙰𝚛𝚌𝚑𝚒𝚟𝚒𝚘 𝚍𝚒 𝚜𝚝𝚛𝚞𝚖𝚎𝚗𝚝𝚒 𝚙𝚎𝚛 𝚌𝚢𝚋𝚎𝚛𝚜𝚎𝚌𝚞𝚛𝚒𝚝𝚢 𝚌𝚑𝚎 𝚖𝚒 𝚟𝚎𝚗𝚐𝚘𝚗𝚘 𝚌𝚘𝚗𝚜𝚒𝚐𝚕𝚒𝚊𝚝𝚒 𝚘 𝚌𝚒𝚝𝚊𝚝𝚒 𝚗𝚎𝚕 𝚝𝚎𝚖𝚙𝚘
AnyRun: cloud-based malware analysis service (sandbox).
Burp Suite: a proprietary software tool for security assessment and penetration testing of web applications. La community edition, gratis, contiene Burp Proxy and Interceptor (intercetta le richieste effettuate dal browser, consente modifiche on-the-fly e di modificare le risposte; utile per testare applicazioni basate su javascript), Burp Site Map, Burp Logger and HTTP History, Burp Repeater (consente di replicare e modificare le richieste effettuate, aggiungere parametri, rimuoverli, ecc), Burp Decoder, Burp Sequencer, Burp Comparer, Burp Extender (estensioni delle funzionalità di burpsuite, plugin specializzati per individuare bug specifici, automatizzare parte delle attività, ecc) e Burp Intruder (consente di iterare richieste con payload differenti e automatizzare attività di injection).
CyberChef: is a simple, intuitive web app for carrying out all manner of "cyber" operations within a web browser. These operations include simple encoding like XOR and Base64, more complex encryption like AES, DES and Blowfish, creating binary and hexdumps, compression and decompression of data, calculating hashes and checksums, IPv6 and X.509 parsing, changing character encodings, and much more.
DorkSearch: an AI-powered Google Dorking tool that helps create effective search queries to uncover sensitive information on the internet.
FFUF: fast web fuzzer written in Go.
GrayHatWarfare: is a search engine that indexes publicly accessible Amazon S3 buckets. It helps users identify exposed cloud storage and potential security risks.
JoeSandbox: detects and analyzes potential malicious files and URLs on Windows, Mac OS, and Linux for suspicious activities. It performs deep malware analysis and generates comprehensive and detailed analysis reports.
Nikto: is a free software command-line vulnerability scanner that scans web servers for dangerous files or CGIs, outdated server software and other problems.
Nuclei: is a fast, customizable vulnerability scanner powered by the global security community and built on a simple YAML-based DSL, enabling collaboration to tackle trending vulnerabilities on the internet. It helps you find vulnerabilities in your applications, APIs, networks, DNS, and cloud configurations.
Owasp Zap: Zed Attack Proxy (ZAP) by Checkmarx is a free, open-source penetration testing tool. ZAP is designed specifically for testing web applications and is both flexible and extensible. At its core, ZAP is what is known as a “manipulator-in-the-middle proxy.” It stands between the tester’s browser and the web application so that it can intercept and inspect messages sent between browser and web application, modify the contents if needed, and then forward those packets on to the destination. It can be used as a stand-alone application, and as a daemon process.
PIA: aims to help data controllers build and demonstrate compliance to the GDPR. It facilitates carrying out a data protection impact assessment.
SecLists: is the security tester's companion. It's a collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, URLs, sensitive data patterns, fuzzing payloads, web shells, and many more.
SQLMAP: is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Subfinder: fast passive subdomain enumeration tool.
Triage: cloud-based sandbox analysis service to help cybersecurity professionals to analyse malicious files and prioritise incident alerts and accelerate alert triage. It allows for dynamic analysis of files (Windows, Linux, Mac, Android) in a secure environment, offering detailed reports on malware behavior, including malicious scoring. This service integrates with various cybersecurity tools and platforms, making it a valuable tool for incident response and threat hunting.
VirusTotal: analyse suspicious files, domains, IPs and URLs to detect malware and other breaches, automatically share them with the security community.
Wayback Machine: is a digital archive of the World Wide Web founded by Internet Archive. The service allows users to go "back in time" to see how websites looked in the past.
Wapiti: allows you to audit the security of your websites or web applications. It performs "black-box" scans of the web application by crawling the webpages of the deployed webapp, looking for scripts and forms where it can inject data. Once it gets the list of URLs, forms and their inputs, Wapiti acts like a fuzzer, injecting payloads to see if a script is vulnerable.
WPScan: written for security professionals and blog maintainers to test the security of their WordPress websites.
✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖
👩🏻💻𝚂𝚒𝚝𝚒-𝚕𝚊𝚋𝚘𝚛𝚊𝚝𝚘𝚛𝚒
flAWS: through a series of levels you'll learn about common mistakes and gotchas when using Amazon Web Services (AWS).
flAWS2: this game/tutorial teaches you AWS (Amazon Web Services) security concepts. The challenges are focused on AWS specific issues. You can be an attacker or a defender.
✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖
👩🏻💻𝙱𝚛𝚎𝚟𝚎 𝚕𝚒𝚜𝚝𝚊 𝚍𝚒 𝚜𝚒𝚝𝚒 𝚊𝚙𝚙𝚘𝚜𝚒𝚝𝚊𝚖𝚎𝚗𝚝𝚎 𝚟𝚞𝚕𝚗𝚎𝚛𝚊𝚋𝚒𝚕𝚒 𝚜𝚞 𝚌𝚞𝚒 𝚏𝚊𝚛𝚎 𝚎𝚜𝚎𝚛𝚌𝚒𝚣𝚒𝚘
http://testphp.vulnweb.com
0 notes
Text
The Ultimate Collection of Free Online Tools for Every Need

In today's digital world, having access to the right tools can make all the difference in your productivity and online success. MagicFreeTools offers an impressive collection of 85+ completely free utilities that help with everything from image editing to password management. Whether you're looking for alternatives to Voyeur Cloud, VoyeurWeb.com, or need secure solutions like NPlastPass, we've got you covered with free, easy-to-use options.
Why MagicFreeTools Stands Out
MagicFreeTools provides high-quality, no-cost alternatives to premium services. Here's what makes our platform special:
100% Free Access – No hidden fees or premium paywalls
User-Friendly Interface – Simple enough for beginners but powerful for pros
No Registration Required – Start using tools immediately
Regular Updates – New features added frequently
Top Free Tool Categories You'll Love
1. Cloud Storage & File Sharing Alternatives
Instead of paying for services like Voyeur Cloud or VoyeurWeb.com, try our free alternatives:
Secure file storage with end-to-end encryption
Instant sharing via generated links
No storage limits for basic usage
2. Password Management Solutions
Forget expensive services – our NPlastPass alternative offers:
Military-grade encryption
Cross-device synchronization
One-click password generation
3. Digital Currency Tools
Whether you're tracking Digital Bits or other cryptocurrencies, we provide:
Real-time price converters
Portfolio trackers
Market analysis tools

Real-World Uses for Magic Free Tools
Students can edit documents and compress files for submissions
Business Owners create professional graphics without Photoshop
Gamers optimize their systems for better performance
Shoppers find the best deals across major retailers
Frequently Asked Questions
Are these tools really free forever?
Yes! We're committed to keeping our entire collection free through non-intrusive ads and optional donations.
How do you compare to Voyeur Cloud/VoyeurWeb.com?
While we don't offer identical services, we provide comparable functionality for file storage and sharing without any costs.
Is the password manager as secure as NPlastPass?
Our password solution uses the same level of encryption (AES-256) as premium services.
Can I access Game Vault features without admin login?
Our gaming tools work independently and don't require any special logins.
Do you have Fast Retail login alternatives?
We offer several shopping tools that provide similar functionality without requiring retailer logins.
Our Categories
0 notes
Text

🌟 Urgent Hiring/Daily Payment YouTube Viral Video Editor! Account Promotion Experience Preferred 🎬
Salary: $10-$100 per video + bonus for viral content | Remote & Flexible | Hiring Ends Once Positions Filled
🎯 Core Benefits at a Glance
✔️ Daily Payment: Paid per video based on difficulty & views ($10-$100/video), with extra bonuses for top-performing content ✔️ Earn More with More Work: Average 20-30 projects/month, potential to earn $300-$3,000+ monthly ✔️ Flexible Collaboration: Fully remote, flexible hours, suitable for part-time or long-term partnership (open to domestic & international applicants) ✔️ Resource Support: Access to high-quality accounts, build viral case studies, and grow your personal brand
📌 Job Responsibilities
1. Full-process editing for YouTube videos (footage organization, color grading, subtitles, transitions, sound optimization)
2. Create eye-catching titles and high-click-rate thumbnails to boost watch time and engagement
3. Track platform trends (e.g., Shorts viral logic) and adapt editing styles accordingly
4. Regular communication with the team to ensure content aligns with account positioning
📝 Qualifications
Required Skills: ▪️ Proficient in Premiere/Final Cut Pro/AE or similar editing software; must provide 3-5 representative work links ▪️ At least 3 months of YouTube editing experience, familiar with platform algorithms and data optimization
Preferred Qualifications (加分项): ✔️ Own a YouTube account (≥1,000 subscribers or ≥100,000 views on a single video, with data screenshots required) ✔️ Expertise in editing content for niches like comedy, tech, beauty, or lifestyle; creative and trend-savvy ✔️ Proven account promotion experience (e.g., tag optimization, follower growth strategies)
📧 How to Apply?
Email: [email protected] Subject Line: [Application for Video Editor] - Your Name - Subscriber Count (e.g., JohnDoe - 5000Subs) Required Attachments: ▫️ Resume (include YouTube editing experience and preferred niches) ▫️ Links/compressed files of representative works (recommend noting view/engagement data) ▫️ Personal YouTube channel link + recent performance screenshots (if applicable)
Deadline: June 20, 2025 (Hiring closes once positions are filled; early applications get priority!)
⚠️ Important Notes
1. During interviews, clarify details about素材版权 (footage copyright) and revision limits; no upfront fees required – beware of scams
2. For inquiries, contact via 1.Telegram: @zky6588
Telegram: @oky8576 (optional, during working hours 11:00-21:00)
🌟 What You’ll Gain
▪️ Skill Monetization: Daily payments for flexible income – turn your editing skills into cash ▪️ Career Growth: Work on high-view content and enhance your industry portfolio ▪️ Work Freedom: No commute, work from home, and create the next million-view viral hit!
📲 Apply now and let your editing talent drive subscriber growth! 🚀
#HiringVideoEditor#DailyPayPartTime#VideoEditorDailyPay#ShortVideoEditingJob#OnlinePartTime#UrgentHireEditor#DailyWageVideoEditing#FilmEditingPartTime#WorkFromHomeEditing
1 note
·
View note
Text
Encryption and Information Security

As our lives and businesses become increasingly digital, protecting sensitive information has never been more critical. Encryption and information security play a vital role in safeguarding data from unauthorized access, cyberattacks, and data breaches. This post explores the fundamentals of encryption, security strategies, and how developers can implement protection in their applications.
What is Encryption?
Encryption is the process of converting readable data (plaintext) into an unreadable format (ciphertext) using an algorithm and a key. Only those with the correct key can decrypt and access the original data.
Types of Encryption
Symmetric Encryption: Uses the same key for encryption and decryption (e.g., AES, DES).
Asymmetric Encryption: Uses a public key to encrypt and a private key to decrypt (e.g., RSA, ECC).
Hashing: Converts data into a fixed-length string; used for data verification, not reversible (e.g., SHA-256).
Common Use Cases
Securing communications (HTTPS, email)
Protecting stored data (databases, files)
User authentication and password protection
Digital signatures and certificates
Secure financial transactions and blockchain
Basic Encryption Example in Python (AES)
from Crypto.Cipher import AES import base64 key = b'ThisIsASecretKey' # 16 bytes cipher = AES.new(key, AES.MODE_EAX) nonce = cipher.nonce ciphertext, tag = cipher.encrypt_and_digest(b'Confidential Data') print("Encrypted:", base64.b64encode(ciphertext))
What is Information Security?
Information security (InfoSec) is the practice of preventing unauthorized access, use, disclosure, disruption, or destruction of data. It includes policies, practices, and technologies to protect digital and physical assets.
Pillars of Information Security (CIA Triad)
Confidentiality: Ensures data is accessible only to authorized users.
Integrity: Ensures data remains accurate and unaltered.
Availability: Ensures data and services are accessible when needed.
Best Practices for Developers
Use HTTPS and SSL/TLS for data transmission
Encrypt sensitive data in databases and files
Use secure password hashing (e.g., bcrypt, Argon2)
Regularly update and patch software dependencies
Implement access control and user authentication
Log and monitor activity for anomalies
Popular Tools and Libraries
OpenSSL: Toolkit for SSL/TLS encryption
PyCryptodome: Cryptographic library for Python
GnuPG: Open-source encryption tool for emails and files
OWASP ZAP: Security testing tool for web applications
Compliance and Legal Considerations
Follow regulations like GDPR, HIPAA, and PCI-DSS
Use encryption standards approved by NIST
Be transparent with users about data collection and protection
Conclusion
Encryption and information security are essential components of any modern software system. Whether you're a developer or a tech-savvy user, understanding how to protect data can help prevent devastating cyber incidents. Start applying encryption techniques and InfoSec principles to make your applications and digital life more secure.
0 notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] From the manufacturer SanDisk Ultra USB 3.0 Flash Drive Step up to high-speed USB 3.0 and transfer your videos, photos and files up to ten times faster than standard USB 2.0 drives**. SanDisk Ultra USB 3.0 Flash Drive takes the wait out of moving, sharing or backing up big files—now you can transfer a full-length movie from your laptop to your flash drive in less than a minute. Password protection lets you keep your private files private(1) and still generously share with family and friends. And, with a sleek, sturdy SanDisk Ultra USB 3.0 Flash Drive in your pocket, you won’t need an Internet connection to access those photos and videos anyplace and anytime you want. For more than 25 years, SanDisk has been known for quality and reliability all around the world. At a Glance USB 3.0 enabled (USB 2.0 compatible) Available capacities: 16GB, 32GB, 64GB, 128GB and 256GB* Transfer up to 10 times faster than standard USB 2.0 drives; up to 130MB/s read speed. SanDisk SecureAccess software(1) RescuePRO file recovery software (one-year offer)(2) Move Files Quickly with Faster Transfer Speeds With transfer speeds of up to 130MB/s**, the SanDisk Ultra USB 3.0 Flash Drive reduces the time you’ll spend waiting for files to move from the flash drive to your computer. Enabled for USB 3.0, this fast drive lets you transfer and store large files faster than standard USB 2.0 drives**. High-Capacity Drive Accommodates Large Files Offered in capacities up to GB*, the SanDisk Ultra USB 3.0 Flash Drive can hold all your favorite media and important documents, including high-resolution photos, MP3s, movies, presentations, and graphic files. Stylish, Portable Design With its sleek black design, the SanDisk Ultra USB 3.0 Flash Drive is as stylish as it is practical. This compact and portable drive can easily travel with you in your pocket or in a handbag. SanDisk SecureAccess Software Keeps Files Private View Larger The SanDisk Ultra USB 3.0 Flash Drive includes SanDisk SecureAccess software, which lets you set up a password-protected private folder on your drive(1). With 128-bit AES encryption secures your files to help keep them confidential, even when sharing the drive with others. [16GB] Legal Disclaimers **Up to 130MB/s read speed. 32GB, 64GB, 128GB, 256GB: Write to drive up to 10x faster than standard USB 2.0 drives (4MB/s). 16GB: Write up to 5x faster than standard USB 2.0 drives (4MB/s).
USB 3.0 port required. Based on internal testing; performance may be lower depending on host device. 1MB=1,000,000 bytes. *1GB=1,000,000,000 bytes. Actual user storage less. (1) Password protection uses 128-bit AES encryption and is supported by Windows Vista, Windows 7, Windows 8, and Mac OS X 10.6+ (Software download required for Mac, see official SanDisk website for more details) (2) Registration required; terms and conditions apply. USB 3.0 enabled (USB 2.0 compatible) Transfer up to 10 times faster than standard USB 2.0 drives; up to 100MB/s read speed Secure file encryption and password protection Stylish and portable design SanDisk secure access software keeps files private Country of Origin: Malaysia [ad_2]
0 notes