#Always On SQL Server
Explore tagged Tumblr posts
Text
Build a Robust Data Infrastructure with SQL Server 2016 Standard
Empowering Your Business with a Reliable Data Backbone
In today's fast-paced digital landscape, having a dependable and efficient data platform is essential for success. SQL Server 2016 Standard continues to stand out as a premier choice for organizations seeking a powerful, secure, and cost-effective database solution. Its blend of advanced features and reliability makes it an ideal foundation for diverse business needs.
One of the most compelling reasons to choose SQL Server 2016 Standard is its robust security capabilities, notably the Always Encrypted feature. This technology ensures sensitive data remains encrypted both at rest and in transit, providing peace of mind against cyber threats. By safeguarding your data, SQL Server 2016 helps build trust with clients and partners, reinforcing your company's reputation.
Performance is another critical aspect where SQL Server 2016 excels. The introduction of In-Memory OLTP dramatically enhances transaction processing speeds. This means faster query responses and improved overall system efficiency, which is vital for mission-critical applications. Whether you're managing large-scale transactional data or real-time analytics, SQL Server 2016's in-memory capabilities ensure your operations run smoothly.
Cost-effectiveness is often a decisive factor for businesses of all sizes. SQL Server 2016 Standard offers an affordable yet comprehensive solution that doesn't compromise on features. It enables organizations to implement advanced business intelligence tools, such as integrated reporting and data visualization, facilitating better decision-making without overspending. For companies looking to maximize their IT budget, SQL Server 2016 provides excellent value.
Furthermore, the platform is designed for flexibility and scalability. As your business grows, SQL Server 2016 Standard can adapt to increasing data volumes and user demands. Its support for large databases and high availability options ensures minimal downtime and continuous access to critical information.
Implementing a resilient data platform isn't just about technology—it's about empowering teams to innovate and excel. SQL Server 2016's comprehensive suite of features simplifies database management, enhances security, and boosts performance. This combination makes it a trusted choice for organizations aiming to strengthen their data infrastructure.
Ready to upgrade or establish your data foundation? You can buy sql server 2016 standard key today and unlock the full potential of your data environment. Embrace a solution that is proven, scalable, and designed to support your business goals for years to come.
#cheap sql server 2016 license#always encrypted security feature#in-memory OLTP performance#cost-effective business intelligence#robust database for critical applications
0 notes
Text
Always On VPN and SQL Target Principal Name Incorrect
Microsoft Always On VPN provides seamless and transparent remote access to corporate applications and data. In most cases, accessing resources over the VPN works the same as on-premises. However, a few folks have asked recently about an issue they found when using the SQL Server Management Studio (SMSS) to connect to a remote SQL server over Always On VPN. Principal Name…

View On WordPress
#administration#Always On VPN#AOVPN#authentication#error#kerberos#Microsoft#Mobility#remote administration#security#SMSS#SQL#SQL server#SQL Server Management Studio#VPN#warning#Windows
0 notes
Text
Ok I've had a very random train of thoughts and now wanna compile it into post.
Some MM characters computer-related (???) headcanons lol
Riley:
Has above average knowledge of Excel/Google sheets due to studying finance, but after four years with no practise forgot most of it.
The "Sooon, I have a problem" person in their family. Actually, surprisingly good and patient at explaining computer stuff to older people.
Has a higher responsibility of doing taxes (finance, after all). Even he never fails to do them right, Ed always double checks. Sometimes they get into argument, where inevitably Riley proves he is right but his father would never admit it.
Warren, Leeza, Ooker and other teens:
Also nothing outstanding in terms of skills, except few of them have interest in IT.
They have bunch of small local Discord servers and one big main server with some very stupid name.
Few times Bev tried to bring up importance of parental control over this "new and rapidly growing young community", but thanks God no one took her concerns seriously
Leeza moderates it and her moder role called "Mayor-mini". Like father like daughter.
All teens local jokes and memes were bourn/spread though that server.
Bev:
Rumors says she sacrificed her humanity to obtain such powers with Microsoft software package.
Can build up Access database from scratch, using basic SQL commands, assemble primitive, but surprisingly sufficient interface to it and synchronize it with Excel in span of one day or less.
In her laptop there're every pupil's personal file, countless Excel tables, several automatised document accounts, Google calendar with precisely planned schedule for next several months (for school, church, island and personal matters) and probably Pentagon files.
Probably can find all Pi numbers with Excel formulas.
Never lets anyone to her laptop.
Spends her free time at different forums, mostly gardening-related.
Wade:
Made a very fucking poor decision to let Bev do all the legwork with digital document accounting.
Now has no idea how some of things even work, so just goes with a flow and does what Bev tells.
No wander she got away with embezzlement.
Knows about kid's server. Very proud of Leeza for managing it :)
Because of that, he knows one or two memes from there, but keeps them in secret.
Has hobby of fixing office equipment. Does it with Sturge in spare time due to Dupuytren's contracture not letting him operate his hand fully.
Sarah:
There's no good medical technicians on island, so when something goes wrong with equipment electronics - tries to fix it herself to best of her ability.
Always monitors electronic e-shops for spare details or equipment. Grows more and more addicted to it.
Frequently updates her selection of sites with useful medical information, because Erin asked her for help guiding teens though puberty. For that receives glances from Bev, but doesn't give a shit.
Has reputation of cool aunt among kids, so she was one and only adult invited to main Discord server. Didn't accept it (doesn't even have Discord acc), but still grateful for trust.
Plays solitaire a lot.
John:
Back when he was playing Paul, Bev asked him to do something with Excel. In conclusion, poor bastard had to learn basic computer skills and Excel in span of several days. Now he is traumatized for rest of his life.
Will do all the work manually just to not touch laptop again.
Upsets very easly when does something wrong.
Doesn't own laptop. Don't give that man laptop, he will cry.
By his own will uses it only to watch baseball. Always asks someone to help with that.
#midnight mass#midnight mass headcanons#beverly keane#idk I just felt silly and wanted to write it down#riley flynn#warren flynn#leeza scarborough#wade scarborough#sarah gunning#john pruitt#monsignor pruitt#father paul hill
25 notes
·
View notes
Note
how does the element stuff work in you system? Feel free to answer privately or not answer at all!
Thought I'd done a post on this already, I'll assume I didn't because I'm always looking for a way to talk about this xD
An Introduction To EleWe »
EleWe is our elements and weapons system, it runs off ten elements and ten weapons - so it has a hundred possible entries - and because only one member per entry, it also runs off Phases.
Phases are a group of a hundred members, a Phase has to be completely filled before a new one opens. Phase III is actually just about to open, and we pray this does not break our database, which was only designed for the first two Phases, because we didn't think we'd exceed two hundred members. (It shouldn't, right? O-o) (I'm not bad at coding, I'm sure it won't-)
The Database »
Just a small section on the database. Our database runs by having all possible combinations as an entry, and having columns for each Phase. When searching the database, we look for things like "element in (x)" and "phase x is empty" (that's in English, I'm not going to write SQL here lmao)
Elements »
Okay so, elements. As I said, there's ten total elements, these are:
Cosmica | Dark
Sonia | Sound
Hydria | Water
Glaciera | Ice
Flora | Plants
Aria | Air
Lumina | Light
Terra (prev Eartha) | Earth
Inferna | Fire
Electria | Electricity
Each one has reactions to other elements. I used to have a list, no clue where it went (probably died when my pc corrupted), so I'll do this from memory (o-o;)
Cosmica + Lumina = Detonate
Sonia + Aria = Diffuse
Sonia + Electria = Boost
Hydria + Glaciera = Freeze
Hydria + Aria = Storm
Hydria + Flora = Grow
Hydria + Inferna = Vaporise
Hydria + Electria = Conduct
Glaciera + Aria = Blizzard
Glaciera + Inferna = Melt
Glaciera + Electria = Conduct
Flora + Terra = Sprout
Flora + Inferna = Burn
Flora + Electria = Burgeon
Aria + Inferna = Stoke
This was originally designed with The Kansukki Project in mind.
This list (with the reaction names) was only ever used in The Kansukki Project, whereas The Kīara'h Project just uses the reactions (have some random trivia)
Weapons »
As also said in the intro, there are ten weapons! These are: (listed with general classification and explanation if needed)
Axe [Short Range]
Bow [Long Range]
Crossbow [Mid Range]
Combat [Short Range] | Hand to hand combat
Gem [Mid Range] | Magic
Knife [Short Range - Long Range] | Depending on if you can throw / previously throwing knives
Polearm [Mid Range] | Death stick :)
Scythe [Mid Range]
Staff [Long Range] | Long ranged gem
Sword [Mid Range]
There were originally eight weapons but apparently we got OCDed ¯\_(ツ)_/¯ (more trivia)
So.. How Does It Work? (And Why?) »
Each member is assigned one element and weapon combination, usually this is based on their past. Each member can only specialise in that element.
(except if they have a copycat ability, such as Amethyst who studied more than one element and use their Sonia to mimic other's elements)
For weapons, it's a little different. Most members only have one, and although some members may know other weapons, they only specialise in one.
Mostly, these will be used within stories and headspace, however some members may be able to wield their weapons in the outside world.
Energy »
Another part of EleWe is elemental energy, it lowers by using abilities/powers and when lowering, can cause members to not be able to cast spells, or even, if it gets extremely low, can impact their body and physical/mental energy and can't recover on its own.
(I won't touch on this too much because it's more or less its own thing.)
Technical Notes »
Element reaction names source: an old post we made on The Kansukki Project's server.
If I remember correctly, this is EleWe v6, (technically v5, but I'm calling it v6, because it will be soon with Phase III)
Most of this was originally done for The Kansukki Project, not The Kīara'h Project, but it has since been adapted.
Kuro from MeD wrote this post (and is very unqualified to write this post)
Hope this answers your ask? Lol
#Kīara'h Asks#Kīara'h Asks : drowntowns#The Kīara'h Organisation#Kīara'h [MeD] Kuro posts#endo safe#pro endo#endo friendly#please send asks#i need more things to do lol
11 notes
·
View notes
Text
How to test app for the SQL injection

During code review
Check for any queries to the database are not done via prepared statements.
If dynamic statements are being made please check if the data is sanitized before used as part of the statement.
Auditors should always look for uses of sp_execute, execute or exec within SQL Server stored procedures. Similar audit guidelines are necessary for similar functions for other vendors.
Automated Exploitation
Most of the situation and techniques on testing an app for SQLi can be performed in a automated way using some tools (e.g. perform an automated auditing using SQLMap)
Equally Static Code Analysis Data flow rules can detect of unsanitised user controlled input can change the SQL query.
Stored Procedure Injection
When using dynamic SQL within a stored procedure, the application must properly sanitise the user input to eliminate the risk of code injection. If not sanitised, the user could enter malicious SQL that will be executed within the stored procedure.
Time delay Exploitation technique
The time delay exploitation technique is very useful when the tester find a Blind SQL Injection situation, in which nothing is known on the outcome of an operation. This technique consists in sending an injected query and in case the conditional is true, the tester can monitor the time taken to for the server to respond. If there is a delay, the tester can assume the result of the conditional query is true. This exploitation technique can be different from DBMS to DBMS.
http://www.example.com/product.php?id=10 AND IF(version() like '5%', sleep(10), 'false'))--
In this example the tester is checking whether the MySql version is 5.x or not, making the server delay the answer by 10 seconds. The tester can increase the delay time and monitor the responses. The tester also doesn't need to wait for the response. Sometimes they can set a very high value (e.g. 100) and cancel the request after some seconds.
Out-of-band Exploitation technique
This technique is very useful when the tester find a Blind SQL Injection situation, in which nothing is known on the outcome of an operation. The technique consists of the use of DBMS functions to perform an out of band connection and deliver the results of the injected query as part of the request to the tester's server. Like the error based techniques, each DBMS has its own functions. Check for specific DBMS section.
4 notes
·
View notes
Text
Power of Data Visualization: A Deep Dive into Microsoft Power BI Services
In today’s data-driven world, the ability to transform raw data into actionable insights is a crucial asset for businesses. As organizations accumulate vast amounts of data from various sources, the challenge lies not just in storing and managing this data but in making sense of it. This is where Microsoft Power BI Services comes into play—a powerful tool designed to bring data to life through intuitive and dynamic visualizations.
What is Microsoft Power BI?
Microsoft Power BI is a suite of business analytics tools that enables organizations to analyze data and share insights. It provides interactive visualizations and business intelligence capabilities with a simple interface, making it accessible to both technical and non-technical users. Whether you are analyzing sales performance, tracking customer behavior, or monitoring operational efficiency, Power BI empowers you to create dashboards and reports that highlight the key metrics driving your business.
Key Features of Microsoft Power BI Services
User-Friendly Interface: One of the standout features of Power BI is its user-friendly interface. Even those with minimal technical expertise can quickly learn to create reports and dashboards. The drag-and-drop functionality allows users to effortlessly build visualizations, while pre-built templates and AI-powered insights help accelerate the decision-making process.
Data Connectivity: Power BI supports a wide range of data sources, including Excel, SQL Server, cloud-based data warehouses, and even social media platforms. This extensive connectivity ensures that users can pull in data from various systems and consolidate it into a single, coherent view. The ability to connect to both on-premises and cloud-based data sources provides flexibility and scalability as your data needs evolve.
Real-Time Analytics: In today’s fast-paced business environment, real-time data is critical. Power BI’s real-time analytics capabilities allow users to monitor data as it’s collected, providing up-to-the-minute insights. Whether tracking website traffic, monitoring social media engagement, or analyzing sales figures, Power BI ensures that you are always equipped with the latest information.
Custom Visualizations: While Power BI comes with a robust library of standard visualizations, it also supports custom visuals. Organizations can create unique visualizations that cater to specific business needs, ensuring that the data is presented in the most effective way possible. These custom visuals can be developed in-house or sourced from the Power BI community, offering endless possibilities for data representation.
Collaboration and Sharing: Collaboration is key to making data-driven decisions. Power BI makes it easy to share insights with colleagues, whether through interactive reports or shared dashboards. Reports can be published to the Power BI service, embedded in websites, or shared via email, ensuring that stakeholders have access to the information they need, when they need it.
Integration with Microsoft Ecosystem: As part of the Microsoft ecosystem, Power BI seamlessly integrates with other Microsoft products like Excel, Azure, and SharePoint. This integration enhances productivity by allowing users to leverage familiar tools and workflows. For example, users can import Excel data directly into Power BI, or embed Power BI reports in SharePoint for easy access.
The Benefits of Microsoft Power BI Services for Businesses
The adoption of Microsoft Power BI Services offers numerous benefits for businesses looking to harness the power of their data:
Enhanced Decision-Making: By providing real-time, data-driven insights, Power BI enables businesses to make informed decisions faster. The ability to visualize data through dashboards and reports ensures that critical information is easily accessible, allowing decision-makers to respond to trends and challenges with agility.
Cost-Effective Solution: Power BI offers a cost-effective solution for businesses of all sizes. With a range of pricing options, including a free version, Power BI is accessible to small businesses and large enterprises alike. The cloud-based service model also reduces the need for expensive hardware and IT infrastructure, making it a scalable option as your business grows.
Improved Data Governance: Data governance is a growing concern for many organizations. Power BI helps address this by providing centralized control over data access and usage. Administrators can set permissions and define data access policies, ensuring that sensitive information is protected and that users only have access to the data they need.
Scalability and Flexibility: As businesses grow and their data needs evolve, Power BI scales effortlessly to accommodate new data sources, users, and reporting requirements. Whether expanding to new markets, launching new products, or adapting to regulatory changes, Power BI provides the flexibility to adapt and thrive in a dynamic business environment.
Streamlined Reporting: Traditional reporting processes can be time-consuming and prone to errors. Power BI automates many of these processes, reducing the time spent on report creation and ensuring accuracy. With Power BI, reports are not only generated faster but are also more insightful, helping businesses to stay ahead of the competition.
Empowering Non-Technical Users: One of Power BI’s greatest strengths is its accessibility. Non-technical users can easily create and share reports without relying on IT departments. This democratization of data empowers teams across the organization to take ownership of their data and contribute to data-driven decision-making.
Use Cases of Microsoft Power BI Services
Power BI’s versatility makes it suitable for a wide range of industries and use cases:
Retail: Retailers use Power BI to analyze sales data, track inventory levels, and understand customer behavior. Real-time dashboards help retail managers make quick decisions on pricing, promotions, and stock replenishment.
Finance: Financial institutions rely on Power BI to monitor key performance indicators (KPIs), analyze risk, and ensure compliance with regulatory requirements. Power BI’s robust data security features make it an ideal choice for handling sensitive financial data.
Healthcare: In healthcare, Power BI is used to track patient outcomes, monitor resource utilization, and analyze population health trends. The ability to visualize complex data sets helps healthcare providers deliver better care and improve operational efficiency.
Manufacturing: Manufacturers leverage Power BI to monitor production processes, optimize supply chains, and manage quality control. Real-time analytics enable manufacturers to identify bottlenecks and make data-driven adjustments on the fly.
Conclusion
In an era where data is a key driver of business success, Microsoft Power BI Services offers a powerful, flexible, and cost-effective solution for transforming raw data into actionable insights. Its user-friendly interface, extensive data connectivity, and real-time analytics capabilities make it an invaluable tool for organizations across industries. By adopting Power BI, businesses can unlock the full potential of their data, making informed decisions that drive growth, efficiency, and innovation.
5 notes
·
View notes
Text
Backend update
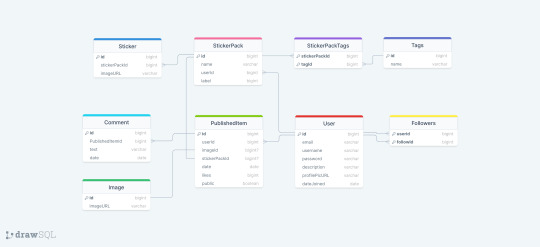
Had the most horrible time working with Sequelize today! As I usually do whenever I work with Sequelize! Sequelize is an SQL ORM - instead of writing raw SQL, ORM gives you an option to code it in a way that looks much more like an OOP, which is arguably simpler if you are used to programming that way. So to explain my project a little bit, it's a full stack web app - an online photo editor for dragging and dropping stickers onto canvas/picture. Here is the diagram.
I'm doing it with Next which I've never used before, I only did vanilla js, React and a lil bit of Angular before. The architecture of a next project immediately messed me up so much, it's way different from the ones I've used before and I often got lost in the folders and where to put stuff properly (this is a huge thing to me because I always want it to be organized by the industry standard and I had no reference Next projects from any previous jobs/college so it got really overwhelming really soon :/) . The next problem was setting up my MySQL database with Sequelize because I know from my past experience that Sequelize is very sensitive to where you position certain files/functions and in which order are they. I made all the models (Sequelize equivalent of tables) and when it was time to sync, it would sync only two models out of nine. I figured it was because the other ones weren't called anywhere. Btw a fun fact

So I imported them to my index.js file I made in my database folder. It was reporting an db.define() is not a function error now. That was weird because it didn't report that for the first two tables that went through. To make a really long story short - because I was used to an server/client architecture, I didn't properly run the index.js file, but just did an "npm run dev" and was counting on all of the files to run in an order I am used to, that was not the case tho. After about an hour, I figured I just needed to run index.js solo first. The only reasons those first two tables went through in the beginning is because of the test api calls I made to them in a separate file :I I cannot wait to finish this project, it is for my bachelors thesis or whatever it's called...wish me luck to finish this by 1.9. XD
Also if you have any questions about any of the technologies I used here, feel free to message me c: <3 Bye!
#codeblr#code#programming#webdevelopment#mysql#nextjs#sequelize#full stack web development#fullstackdeveloper#student#computer science#women in stem#backend#studyblr
15 notes
·
View notes
Text
10 security tips for MVC applications in 2023

Model-view-controller or MVC is an architecture for web app development. As one of the most popular architectures of app development frameworks, it ensures multiple advantages to the developers. If you are planning to create an MVC-based web app solution for your business, you must have known about the security features of this architecture from your web development agency. Yes, MVC architecture not only ensures the scalability of applications but also a high level of security. And that’s the reason so many web apps are being developed with this architecture. But, if you are looking for ways to strengthen the security features of your MVC app further, you need to know some useful tips.
To help you in this task, we are sharing our 10 security tips for MVC applications in 2023! Read on till the end and apply these tips easily to ensure high-security measures in your app.
1. SQL Injection: Every business has some confidential data in their app, which needs optimum security measures. SQL Injection is a great threat to security measures as it can steal confidential data through SQL codes. You need to focus on the prevention of SQL injection with parameterized queries, storing encrypted data, inputs validation etc.
2. Version Discloser: Version information can also be dangerous for your business data as it provides hackers with your specific version information. Accordingly, they can attempt to attack your app development version and become successful. Hence, you need to hide the information such as the server, x-powered-by, x-sourcefiles and others.
3. Updated Software: Old, un-updated software can be the reason for a cyber attack. The MVC platforms out there comprise security features that keep on updating. If you also update your MVC platform from time to time, the chances of a cyber attack will be minimized. You can search for the latest security updates at the official sites.
4. Cross-Site Scripting: The authentication information and login credentials of applications are always vulnerable elements that should be protected. Cross-Site Scripting is one of the most dangerous attempts to steal this information. Hence, you need to focus on Cross-Site Scripting prevention through URL encoding, HTML encoding, etc.
5. Strong Authentication: Besides protecting your authentication information, it’s also crucial to ensure a very strong authentication that’s difficult to hack. You need to have a strong password and multi-factor authentication to prevent unauthorized access to your app. You can also plan to hire security expert to ensure strong authentication of your app.
6. Session Management: Another vital security tip for MVA applications is session management. That’s because session-related vulnerabilities are also quite challenging. There are many session management strategies and techniques that you can consider such as secure cookie flags, session expiration, session regeneration etc. to protect access.
7. Cross-Site Request Forgery: It is one of the most common cyber attacks MVC apps are facing these days. When stires process forged data from an untrusted source, it’s known as Cross-Site Request Forgery. Anti-forgery tokens can be really helpful in protecting CSRP and saving your site from the potential danger of data leakage and forgery.
8. XXE (XML External Entity) Attack: XXE attacks are done through malicious XML codes, which can be prevented with the help of DtdProcessing. All you need to do is enable Ignore and Prohibit options in the DtdProcessing property. You can take the help of your web development company to accomplish these tasks as they are the best at it.
9. Role-Based Access Control: Every business has certain roles performed by different professionals, be it in any industry. So, when it comes to giving access to your MVC application, you can provide role-based access. This way, professionals will get relevant information only and all the confidential information will be protected from unauthorized access.
10. Security Testing: Finally, it’s really important to conduct security testing on a regular basis to protect business data on the app from vulnerability. Some techniques like vulnerability scanning and penetration testing can be implied to ensure regular security assessments. It’s crucial to take prompt actions to prevent data leakage and forgery as well.
Since maintaining security should be an ongoing process rather than a one-time action, you need to be really proactive with the above 10 tips. Also, choose a reliable web development consulting agency for a security check of your website or web application. A security expert can implement the best tech stack for better security and high performance on any website or application.
#web development agency#web development consulting#hire security expert#hire web developer#hire web designer#website design company#website development company in usa
2 notes
·
View notes
Text
Hi there! This is a sideblog to help gauge interest and facilitate discussion about a potential upcoming Pokémon-themed clicker game.
I am the mod of this blog and have experience with software engineering, so I will be working on development. I have lots of ideas for unique features that I would love feedback on! I’m more of a developer than an ideas person, and I believe collaboration will make a better game!
For anyone interested in collaborating, I am looking for the following (crossed out text means we’ve found someone/people to fill that role!):
Kind, friendly, and social people with experience in communicating professionally with others.
Pixelart artists experienced with Pokémon pixelart and background art.
Creative, highly organized problem-solvers interested in turning user feedback and ideas into outlines for features and requirements. Professional writing ability is a must!
Anyone who doesn’t mind tedious data entry and can work through such work efficiently enough to provide a workable amount of data for me to test different areas with!
People experienced with software and web development. You must have experience with the following languages: HTML, CSS, JavaScript/TypeScript, SQL, and C# (or something similar). These are the languages I plan to use. I would also prefer anyone familiar with the Angular framework!
I am interested in these kinds of people to become staff or helpers for this site! Before messaging me and letting me know you’re interested, please be aware of the following requirements for staff members:
You must be at least 21 years old. Age is not always an indication of maturity, but I think it can help eliminate some of those issues early on, and I’d like to have a team of people who are all approximately adults.
You must be kind, accepting, and open-minded. This site will not tolerate hate speech, bullying, and any behavior deemed predatory. Similarly, I will not tolerate any of this behavior from staff.
Excellent communication skills are important! You at least must be able to communicate your availability and ability to do something—I want to build a team that’s comfortable with each other, but also professional enough with each other, to let others know when they can’t do something, need help, or will be unavailable.
You must be trustworthy and responsible!
Finally (and this is a tall order, I know), if you are willing to volunteer your time and talent for free in the beginning to get us started, that would be very much appreciated! I would like for us to eventually be in a place where the time that developers and artists put in is compensated monetarily, but at this time I cannot say how soon that will happen—it all depends on how this all kicks off and the amount of interest we get from the community.
For anyone concerned about the potential of pay-to-play being a thing in this site: Don’t worry! It is a primary concern of mine to keep this site as free-to-play as possible! However, costs like servers exist, so some arrangement will have to be made. I don’t really believe in subscription models, so I hope to build a generous community that are interested in donating even just a little to help fund release cycles that would include new Pokémon and site features. Smaller features and bugfixes would always occur regularly regardless of the status of any funding goals.
3 notes
·
View notes
Text
Web Development in 2025: The Rise of AI-Driven Innovation
web development is undergoing an earthquake change by advanced in Artificial Intelligence. From automated code generation to individual user experiences, AI is no longer a future concept - it is an essential toolkit for modern developers and businesses seeking competitive benefits. This article explains how AI-powered innovation web development is re-shaping every stage of the life cycle, which brings profit, and the teams of challenges have to navigate to exploit their full potential.

1. AI-August Design & Prototyping
Intelligent wireframing: AI -run equipment can now explain the brief of the natural language to generate wireframe within minutes. Instead of sketching the layout by hand, the designers describe their vision, and produce a clickable prototype designed for the AI review.
Automatic Style Guide: Machine Learning algorithms analyze existing brand assets- logos, color straps, typography- and automatically construct constant styling guides. This design cuts from phase to days and aligns each page with corporate identity.
Predictive UX Test: AI-operated analytics platforms follow user interactions to identify possible purposeful issues before the development begins. By predicting pain points, teams can continuously adapt to navigation flow and page layout.
2. Code generation and optimization
Natural Language Coding: In 2025, developers regularly use AI assistants to translate plain-English signals into the production-cod snipet. Whether a custom form verification or a complex animation sequence is formed, AI speeds up to 50%coding.
Performance tuning: Machine learning models monitor the performance of the real-world site and recommend adaptation-like image compression levels, cashing strategies, and lazy olds loading thresholds to ensure the page load in less than two seconds.
3. Individual user experience
Dynamic Content Generation: AI algorithms analyze user's behavior, preferences and demographics, which are to generate personal headlines, product recommendations and even the entire page layout on the fly. This level of adaptation greatly increases engagement and conversion rates.
Chatbots and Virtual Assistant: Interactive AI directly handles the constrich customer questions in websites 24/7, handles books appointments, and collects feedback. With emotion analysis, these bots customize tone and language to match each visitor, causing a human experience on a scale.
Adaptive interface: using real-time data, AI UI can adjust the components-such as button size, contrast ratio and content conforming with density-individual requirements, including access requirements. This ensures inclusion without separate growth track.
4. Uninterrupted integration and deployment
Devops automation: AI-powered pipeline orchestrate tests, security scans and deployment in many environment. Continuous integration triggers reduce discrepancies, downtime and manual intervention found during automatic rollbacks or therapeutic scripts.
API Orchitation: As microsarvis architecture, AI platforms manage dependence graphs, automatically update the service closing points and monitor health check -ups. This ensures that the front-end application always optimal back. End connect with resources.
Cloud Resource Adaptation: Machine learning models predict traffic spikes and provisions server -free functions or container institutes. This reduces the cost just the time by maintaining extreme performance in the scalability.
5. Safety and compliance
Intelligent Threat Detection: AI systems analyze millions of logs per second to identify unusual patterns - such as DDOS attacks or credentials stuffing - often prevent violations before impressing users.
Automatic Code Auditing: Safety-focused AI tools scan new committees for weaknesses such as SQL injection or cross-site scripting (XSS). They destroy issues in bridge requests and even suggest remade codes, which spend time security teams on manual reviews.
Regulatory Compliance Monitoring: For industries under GDPR, HIPAA, or other rules, AI monitors data flow and configuration, automatically generates audit reports and alerts teams to non -use changes.
6. Challenges and ideas
While AI provides transformational benefits, it requires careful planning to adopt it effectively:
Data privacy: comprehensive user data collection fuel privatization engine. Organizations should apply strict data governance policies, anonymity protocols and clear opts in mechanisms.
Prejudice mitigation: Trained AI model materials on diagonally dataset can eliminate bias in recommendations or code tips. Regular bias audit and diverse training data are essential safety measures.
Skill Development: Teams must be excusable to work with AI tools - how to validate early engineering, model boundaries, and AI output.
Ethical Uses: Transparent AI use produces the user trust. Websites should disclose AI - Povered features (eg, chatbots, personalization) and provide an option of human fall.
7. Looking forward
As we move towards the end of 2025, AI's role in web development will only increase. Future innovations can be involved:
Generative 3D web experience: Beyond the flat page, AI can automate the creation of an immersive 3D interface that immediately load in browsers.
Emotion Inters Conscious Interface: Detection of real Ootion through webcam can cause material tone and visual to fit the user's mood.
Self -Heling website: Advanced AI agents can autonomally break up link, patch safety holes, and update the leveled libraries without human intervention.
conclusion
AI-run innovation is redefining web development in 2025. From automatic to automatic tasks to craft the hyper onsoursalized user trips, the artificial intelligence empowers the teams to rapidly, intelligent, intelligent and distribute more secure websites. By embracing AI responsibly - promoting privacy, morality and continuous learning - the development team can unlock new levels of creativity and efficiency, puts their businesses at the forefront of digital frontier.
0 notes
Text
How the Best Website Development Company in Ahmedabad Ensures Security in Every Build
In today's highly connected world, keeping your website secure isn't optional, it's essential. As online threats become more advanced every day, businesses can't afford to ignore security or leave it until the end. That’s why choosing the best website development company in Ahmedabad matters more than ever in 2025.
Ahmedabad has emerged as a hub of digital innovation and reliable development services. Among the many web service providers in India, companies in this city stand out for their ability to blend technology, creativity, and most importantly robust security protocols into every project.
In this article, we’ll explore how top-tier developers in Ahmedabad are integrating end-to-end security at every stage of a web project and what makes them the ideal choice for your business website.
Why Website Security Is Non-Negotiable in 2025
Website breaches are no longer rare occurrences. According to recent reports, small and medium-sized businesses are among the top targets for cybercriminals. From data breaches to ransomware attacks, even a small vulnerability in your website can result in significant reputational and financial loss.
That’s why the best website development company in Ahmedabad follows strict security guidelines from planning and coding to hosting and maintenance. These companies do not just create visually appealing and responsive websites; they also build digital fortresses to protect user data and business operations.
Let's take a look at security methods these reliable agencies use in 2025.
1. Security-First Architecture and Planning
Every secure website begins with thoughtful planning. The best development agencies in Ahmedabad follow a security-first mindset, incorporating safeguards into the core architecture.
Key Practices:
Threat Modeling During Planning: Before writing a single line of code, the team maps potential vulnerabilities through threat modeling. This helps them preemptively secure data entry points, admin panels, and integrations.
Use of Secure Frameworks: Instead of building from scratch or using outdated platforms, developers choose modern frameworks with built-in security features.
Compliance-Driven Development: Whether it’s GDPR, HIPAA, or PCI-DSS, leading developers ensure that the site complies with international data protection standards right from the start.
By focusing on structure, the best agencies ensure your website has a solid, secure foundation that is harder for hackers to exploit.
2. Secure Coding Standards and Best Practices
The most sophisticated websites are only as safe as their code. Vulnerabilities often originate from careless coding, third-party scripts, or outdated plugins.
How Ahmedabad’s Top Developers Handle It:
OWASP Guidelines: Development teams stick to the OWASP Top 10, a well known global list of major security threats in web applications.These threats include SQL injection, cross site scripting, and unsafe data handling.
Code Review & Pair Programming: Many leading firms adopt peer reviews and pair programming sessions to double-check every code snippet for flaws.
Sanitization & Validation: User input is always validated on both the client and server sides to prevent injection attacks.
Secure coding isn’t just about writing clean code, it's about anticipating potential misuse and sealing off loopholes from day one.
3. HTTPS, SSL, and Data Encryption
Transmitting sensitive data without encryption is a major red flag. The best website development companies in Ahmedabad implement end-to-end encryption by default.
How It’s Done:
HTTPS by Default: SSL certificates are installed at the beginning of the deployment process, ensuring all communications between the user and the server are encrypted.
TLS 1.3 Protocol: Businesses now use TLS 1.3 because it's quicker and safer than older versions.
Encrypted Databases: Sensitive user data such as passwords, payment information, and personal identification details are stored in hashed and salted formats using secure algorithms like bcrypt or SHA-256.
By encrypting both data at rest and data in transit, agencies reduce the likelihood of data theft even in the case of server breaches.
4. Role-Based Access Control and Admin Security
Managing who can access what on a website is one of the most ignored parts of web security. Developers in Ahmedabad now incorporate Role-Based Access Control (RBAC) to ensure that users only access what they are authorized to.

Best Practices in Use:
Multi - Factor Authentication: Admin panels and CMS dashboards are secured with two step or multi-step verification methods.
Audit Trails & Logs: Every admin action is logged, making it easier to identify malicious activities.
Limited Access Permissions: Access to sensitive functions is strictly restricted to verified roles, reducing the attack surface area.
These practices prevent internal threats and unauthorized access, especially on content-heavy or eCommerce sites.
5. Automated Vulnerability Scanning & Regular Penetration Testing
Creating a secure website isn't something you do just once, it's a continuous effort. The best website development companies in Ahmedabad offer ongoing security audits as part of their post-launch services.
Tools and Techniques:
SAST & DAST Tools: Static and dynamic analysis tools (like SonarQube or Burp Suite) are used to continuously scan for vulnerabilities.
Penetration Testing: Ethical hackers are employed to simulate real-world attacks, uncovering any weaknesses.
Regular Updates: CMS systems, plugins, themes, and libraries are frequently updated to fix newly found security issues.
These post-deployment measures ensure that your site stays protected even as cyber threats evolve.
6. Secure Hosting and Cloud Infrastructure
Even a secure website can be compromised by poor hosting choices. Recognizing this, the best agencies in Ahmedabad recommend or provide secure cloud hosting environments.
Hosting Security Measures Include:
Firewalls and WAFs
Auto-scaling & DDoS Mitigation
Secure Shell (SSH) Access Only
Automated Backups with Ransomware Protection
Cloud providers like AWS, Google Cloud, and Azure are often the go-to platforms for these agencies, and they leverage features like IAM and network isolation to protect client data.
7. User Education & Secure UX
Security also depends on the end-user. A secure site can still be compromised if users fall for phishing attacks or use weak passwords. The best web development firms in Ahmedabad offer secure UX features and user education.
Some Features Include:
Password Strength Meters
CAPTCHAs & Bot Protection
Real-time Alerts for Suspicious Login Attempts
Security-focused Onboarding for Admins
Security isn’t just backend-focused anymore it extends to the frontend design, ensuring that users are actively involved in maintaining site integrity.
Conclusion
With the growing reliance on digital channels, your website must be more than just functional and attractive; it needs to be secure at its core. The best website development company in Ahmedabad understands this responsibility. From architecture to hosting, from code to customer education, every part of the build is designed with security-first principles.
In 2025, web security is not optional. It’s the backbone of your digital credibility and customer trust. Partnering with a web development company that values and implements comprehensive security measures is the smartest investment a business can make today.
Whether you're launching an eCommerce site, a corporate portal, or a SaaS platform, don't settle for anything less than excellence. Choose a company that prioritizes security in every pixel, every process, and every piece of code.
0 notes
Text
C# connections to PostgreSQL in Docker - The Easy way
PostgreSQL is free to use and can be an alternative to SQL Server. I’ve always been a huge fan of SQL Server, but sometimes clients insist on PostgreSQL. So in this article, I’ll go over how to spin up an instance of PostgreSQL in Docker, maintain the data outside of docker and then connect to it with a very simple Entity Framework connection. Step 1: Setup Docker I assume you have Docker…

View On WordPress
0 notes
Text
Microsoft License: Revolutionizing Access to Genuine Microsoft Software for Global Businesses

Barcelona, April 22, 2025 — In an era where digital transformation is no longer optional but essential, the integrity and reliability of software solutions have never been more critical. Microsoft License, a trusted subsidiary of Talee Limited and an official Microsoft Partner, has emerged as a leading provider of 100% genuine Microsoft software licenses, serving businesses, institutions, and IT professionals around the globe.
Founded on the principles of transparency, authenticity, and customer empowerment, Microsoft License provides direct access to the full suite of Microsoft products — including Windows operating systems, Microsoft Office, Windows Server, SQL Server, and Microsoft Azure. Each product sold through https://microsoftlicense.com is backed by verifiable license keys and lifetime support, ensuring complete compliance and peace of mind for clients.
“With over 12 years in the industry, our goal has always been to simplify software procurement while maintaining the highest standards of legitimacy,” said a Microsoft License spokesperson. “We want to ensure that businesses, regardless of their size or location, can operate with the tools they need — legally, securely, and efficiently.”
Unmatched Value and Immediate Delivery
Unlike traditional resellers, Microsoft License distinguishes itself by offering instant digital delivery of license keys upon purchase. This allows clients to start using their software within minutes of ordering, eliminating unnecessary delays and ensuring productivity is never compromised.
Moreover, the company’s unique pricing model enables clients to save up to 70% compared to retail pricing without sacrificing authenticity or quality. Their portfolio caters to individual users, small businesses, educational institutions, and large enterprises alike — all of whom benefit from Microsoft License’s strong vendor relationships and bulk purchasing power.
Lifetime Support and Customer-Centric Approach
What truly sets Microsoft License apart is its commitment to post-purchase service. Customers receive lifetime technical support from a dedicated team of certified professionals, available to assist with installation, activation, and ongoing maintenance.
This white-glove support has earned Microsoft License a loyal customer base and exceptional trust scores across international review platforms. With thousands of satisfied clients across Europe, North America, Asia, and the Middle East, the company has positioned itself as a beacon of excellence in the software licensing industry.
A Global Vision for a Secure Digital Future
As part of its long-term vision, Microsoft License continues to invest in cybersecurity education, compliance training, and digital access programs aimed at bridging the digital divide in underserved regions. These initiatives reflect the company's belief in technology as a force for global empowerment.
“We see ourselves not just as a reseller but as a partner in our clients' digital journeys,” the spokesperson added. “Whether you're building an enterprise IT infrastructure or simply upgrading your home PC, Microsoft License is here to provide the tools and confidence to move forward.”
Visit and Explore
To learn more about the full range of products and services offered, or to purchase genuine Microsoft software licenses with instant delivery, visit: https://microsoftlicense.com/
Stay connected and follow the latest updates via our website: https://microsoftlicense.com/
About Microsoft License:
Microsoft License is an authorized Microsoft Partner and subsidiary of Talee Limited, registered in the United Kingdom. The company specializes in the distribution of authentic Microsoft software licenses with a strong focus on customer service, compliance, and value delivery.
0 notes
Text
Magento 2 Security Extension — Protect Your Store from the Inside Out
Running an eCommerce business on Magento 2 gives you power, flexibility, and performance. But with great power comes great responsibility—especially when it comes to security. Magento is a widely used platform, making it a common target for cyber threats, data breaches, and fraud. That’s why installing a Magento 2 Security Extension is one of the smartest decisions any store owner can make.
This article explores how security extensions safeguard your Magento 2 store, how address validation plays a key role in fraud prevention, and which features you should prioritize when choosing the right security solution.
Why Magento 2 Needs Security Enhancements
Magento 2 offers solid built-in security features, including two-factor authentication (2FA), file system permissions, and CAPTCHA. However, these tools aren’t always enough. Most store owners still face threats like:
Fake user registrations
Fraudulent orders
Bot attacks
SQL injections
Data tampering
Checkout manipulation
Because Magento 2 is open-source and highly customizable, vulnerabilities can emerge through third-party modules, outdated plugins, or improper server configurations. A dedicated security extension provides an extra layer of defense against such risks.
The Hidden Threat: Invalid or Fake Addresses
One of the most overlooked security gaps in Magento 2 stores is invalid or fake address entries during checkout. Cybercriminals and bots often use fake addresses to:
Test stolen credit cards
Place high-risk or fraudulent orders
Flood your system with fake data
Manipulate shipping or billing info to trigger chargebacks
This is where address validation steps in—not just as a logistics tool, but as a powerful security filter.
How Address Validation Boosts Magento 2 Security
An address validation extension like the one offered by EcomPlugins doesn't just help verify locations for delivery—it helps verify the user’s intent and legitimacy.
Here’s how it strengthens your store’s security:
1. Detects Suspicious Address Patterns
Invalid zip codes, incomplete fields, or mismatched city-state combinations are red flags. Automatically detecting these issues helps you block risky transactions before they occur.
2. Reduces Chargebacks and Payment Disputes
A significant number of fraudulent orders use fake billing addresses. Real-time validation ensures that billing information aligns with what payment gateways expect, reducing the risk of false disputes.
3. Prevents Fake User Registrations
If your extension validates addresses at registration (or checkout), it becomes harder for bots or scammers to create dummy accounts with fake data.
4. Enhances Data Integrity
Address validation ensures that your CRM, analytics tools, and marketing automations only work with clean, verified data—essential for both security and performance.
Features to Look for in a Magento 2 Security Extension
While address validation is a great start, here are additional features to look for in a well-rounded Magento 2 security extension:
1. Two-Factor Authentication (2FA)
Adds an extra layer of login protection by requiring a secondary code, usually sent to a device.
2. IP Whitelisting and Blacklisting
Control which IPs can access your admin panel and block suspicious or high-risk addresses.
3. Login Attempt Limits
Prevent brute-force attacks by locking users out after a certain number of failed login attempts.
4. Admin URL Customization
Change your default admin URL so that bots and hackers can't easily guess where to target attacks.
5. Firewall Rules
Use application-level firewalls to filter traffic, restrict bots, and block known attackers.
6. Activity Logs and Alerts
Monitor admin and customer activity in real-time. Automated alerts notify you of suspicious behavior like multiple failed logins or bulk data exports.
EcomPlugins: Secure Checkout with Built-in Address Validation
If you're looking for a lightweight yet powerful solution to improve your Magento 2 store’s security, EcomPlugins’ Magento 2 Address Validation extension is a great place to start.
Here’s what sets it apart:
USPS-based real-time address verification
Validation for both billing and shipping addresses
Auto-suggestions for correcting typos and missing details
Support for U.S. merchants and USPS standards
Quick installation and Magento 2 compatibility
Although primarily focused on logistics, this extension acts as a security filter by preventing invalid or malicious addresses from slipping through your checkout.
Why Security = Trust = Higher Conversions
Security isn’t just about protecting your site—it’s about protecting your customers. Shoppers are becoming more cautious about who they buy from. Even a small sign of weakness, like a failed order or shipping error, can reduce trust and hurt conversion rates.
By using a security-enhancing tool like an address validation extension, you demonstrate professionalism, protect customer data, and improve fulfillment accuracy—all of which build long-term trust.
Final Thoughts
Magento 2 is a powerful eCommerce platform, but it’s not invulnerable. Cyber threats are evolving every day, and relying solely on default security settings is risky. A Magento 2 Security Extension—especially one with built-in address validation—can be your first line of defense against fraudulent behavior, shipping errors, and data integrity issues.
For store owners who want to secure their operations and deliver a flawless checkout experience, EcomPlugins’ Magento 2 Checkout Address Validation extension offers the perfect blend of security, usability, and logistics support.
Protect your store from the inside out—start with smarter address validation today.
0 notes
Text
A Rock-Solid Data Platform: Why SQL Server 2016 Standard Remains a Top Choice
Unleashing the Power of SQL Server 2016: A Reliable Foundation for Modern Data Needs
In today’s rapidly evolving digital landscape, organizations require a robust and reliable data platform to support their critical operations and strategic initiatives. SQL Server 2016 Standard stands out as a versatile, powerful choice that continues to deliver exceptional performance, security, and flexibility. Its comprehensive features make it an ideal solution for businesses seeking stability and scalability in their data management infrastructure.
One of the key strengths of SQL Server 2016 Standard is its enhanced security capabilities. With features like Always Encrypted, it ensures sensitive data remains protected, even in the event of a breach. This encryption technology allows data to be encrypted at rest and in transit, providing peace of mind for organizations handling confidential information. Furthermore, dynamic data masking helps prevent unauthorized access by hiding sensitive data from users who do not need to see it, fostering a secure environment for data handling.
Beyond security, SQL Server 2016 excels in supporting business intelligence (BI) initiatives. Its integrated analytics tools enable companies to analyze vast amounts of data efficiently, transforming raw data into actionable insights. Power BI integration facilitates interactive visualizations, empowering decision-makers with real-time data dashboards. This seamless BI capability ensures organizations can stay ahead of market trends and respond swiftly to changing business conditions.
Performance enhancements in SQL Server 2016, such as in-memory OLTP and operational analytics, significantly boost transaction processing speeds and reduce latency. These features are particularly beneficial for applications requiring high throughput and low latency, such as financial systems or e-commerce platforms. The in-memory technology allows for real-time data processing, which is crucial for competitive advantage in today's fast-paced environment.
Scalability is another cornerstone of SQL Server 2016 Standard. Its ability to handle large volumes of data and concurrent users makes it suitable for organizations of all sizes. Whether managing small departmental databases or enterprise-wide data warehouses, SQL Server 2016 adapts to your needs, ensuring reliable performance without compromising security or functionality.
Moreover, SQL Server 2016 offers comprehensive tools for data management and automation. Its robust backup and recovery options, coupled with advanced monitoring features, enable administrators to maintain high availability and system integrity. These tools simplify database administration, reduce downtime, and enhance overall operational efficiency.
Choosing a database platform is a strategic decision that impacts every aspect of an organization. SQL Server 2016 Standard continues to be a top choice because it combines tried-and-true stability with innovative features that meet modern data demands. Its cost-effectiveness, combined with enterprise-grade capabilities, makes it an attractive solution for businesses aiming for growth and resilience.
In conclusion, SQL Server 2016 Standard offers a comprehensive, secure, and high-performing data platform that supports a wide range of business needs. Its combination of security features, BI integration, performance enhancements, and scalability makes it a reliable foundation for any organization’s data strategy. To learn more about how this platform can elevate your data management, visit A Rock-Solid Data Platform: Why SQL Server 2016 Standard Remains a Top Choice.
#SQL Server 2016#Data Platform#Database Security#Business Intelligence#Data Management#In-Memory OLTP#Enterprise Data Solutions
0 notes
Text
SSRS in Action: Visualizing Big Data for Decision Making
In today's data-driven world, effective reporting is crucial for informed decision-making. SQL Server Reporting Services (SSRS) provides a powerful platform for creating, deploying, and managing reports for organizations of all sizes. In this blog, we will explore how SSRS can transform raw data into insightful visualizations, aiding businesses in making strategic decisions.
Introduction to SQL Server Reporting Services (SSRS)
SQL Server Reporting Services (SSRS) is a server-based reporting platform that enables the creation of interactive, tabular, graphical, or free-form reports from relational, multidimensional, or XML-based data sources. Whether you are a business analyst, data engineer, or decision-maker, SSRS offers tools to design, publish, and manage reports that can be delivered over the web or via email.
One of SSRS's key strengths is its integration with Microsoft SQL Server, which allows for seamless data retrieval and manipulation. The platform provides a range of tools that cater to varying levels of expertise, from simple report builders to advanced design tools for complex reporting needs.

SSRS
Creating Parameterized Reports
Parameterized reports in SSRS allow users to input specific criteria, providing flexibility and control over the data that is displayed. This feature is particularly useful for generating reports that need to adapt to different user requirements or scenarios.
For instance, a sales report might include parameters for date range, region, or product category. By inputting these parameters, users can generate targeted reports that hone in on the specific data they need, rather than sifting through irrelevant information. This not only saves time but also enhances the precision of the data analysis.
Designing Dashboards and Charts
Data visualization is a critical aspect of effective reporting. SSRS offers a variety of tools to design dashboards and charts that provide a clear and concise presentation of data trends and patterns. With SSRS, users can create custom dashboards that combine several reports into a single, cohesive view, making it easier to monitor key performance indicators (KPIs) and business metrics.
Charts in SSRS can range from simple bar graphs and pie charts to more complex data visualizations like heat maps or scatter plots. The ability to customize these visualizations allows for a tailored presentation that aligns with the specific needs of the organization.

SSRS Dashboard
Publishing Reports for End-Users
Once reports are created and tested, SSRS makes it easy to publish them for end-user access. Reports can be deployed to a report server, where they can be managed, secured, and shared with users across the organization. SSRS supports a variety of formats for report delivery, including HTML, PDF, Excel, and Word, ensuring compatibility with different user preferences and technical requirements.
The platform also supports scheduled report delivery, allowing users to receive updated reports automatically via email or save them to a shared location. This automation reduces manual effort and ensures that stakeholders always have access to the most recent data.
Embedding SSRS in Web Portals
SSRS can be embedded in web portals, providing seamless integration with existing web applications. This feature enhances the user experience by allowing users to access reports within familiar environments, without the need to switch between different applications.
SSRS Web Portal
By embedding SSRS reports into web portals, organizations can provide a unified interface for data access and analysis. This integration can be achieved through the use of the SSRS REST API, which enables developers to customize report embedding to meet specific business needs.
FAQ
1. What are the system requirements for SSRS? SSRS requires a compatible version of Microsoft SQL Server, Windows Server, and .NET Framework. It's advisable to check the official documentation for specific version compatibility.
2. Can SSRS handle real-time data reporting? While SSRS is designed for scheduled reporting, it can be configured to display near-real-time data by frequently updating the data source and refreshing the reports.
3. Is it possible to customize the look and feel of SSRS reports? Yes, SSRS offers a range of design tools that allow for customization of report layouts, styles, and themes to align with corporate branding and design preferences.
4. How does SSRS ensure data security? SSRS provides role-based security features, allowing administrators to control access to reports and data sources based on user roles and permissions.
5. Can SSRS be integrated with other Microsoft tools? Yes, SSRS integrates seamlessly with other Microsoft tools such as Power BI, SharePoint, and Excel, enhancing its functionality and versatility in business environments.
In conclusion, SQL Server Reporting Services is a robust tool for transforming data into actionable insights. Its comprehensive features for report creation, customization, and deployment make it an essential component for any organization looking to leverage big data for strategic decision-making.
Home
instagram
youtube
#SSRS#DataReporting#SQLReports#BusinessIntelligence#ReportAutomation#DataVisualization#SQLServer#SunshineDigitalServices#TechReporting#BIInsights#Instagram#Youtube
0 notes