#Botnets
Explore tagged Tumblr posts
Text
WATCH FOR FROZEN BOTNETS, THAT NO MATTER HOW OLD OR NEW ARE ALL CONSISTENTLY CONSISTENT WITH THE OTHER VERSIONS OF THEMSELVES, NO MATTER THEIR AGES. ESSENTIALLY SET IN VARIOUS WAYS TO NEVER EVOLVE OR CHANGE, THOSE TYPES OF BOTNETS ARE ESSENTIALLY ALWAYS JUDGED AS RETARDED IN TERMS OF CRIMINAL SOPHISTICATION BY TIME TRAVELING CRIMINALS OR TIME TRAVELING MILITARIES OR TIME TRAVELING RESOURCE PIRATES FROM OUTSIDE THIS CLUSTER OF GALAXIES, AND DUE TO THOSE JUDGEMENTS, CONSISTENTLY ATTRACT CRIMINALS FROM OUTSIDE THIS AREA TO DIRECT THEIR ATTENTIONS THIS DIRECTION, HOPING FOR EASY SCORES
#frozen botnets#botnet#botnets#taylor swift#be on the lookout for botnets#original timeline#pi day#martin luther king jr#fashoing#melanie martinez#michelle obama#caprica#alice#tim kaine#o'#o'really#automatic#automated#parts#padraig
88 notes
·
View notes
Text
Botnets Just Launched the Largest DDoS Attack Eve
Cloudflare blocked a record-breaking DDoS attack peaking at 7.3 Tbps, part of over 6,500 hyper-volumetric strikes in Q2 2025. Most were powered by VM-based botnets targeting critical infrastructure and online platforms.
Source: Cloudflare
Read more: CyberSecBrief
3 notes
·
View notes
Text
The same problems continue no matter the platform.
Is it a fresh start for you and me, or for engagement clout chasing influencers making money off our attention?
Big time influencers and famous people who know how to build up a following, are now using tried and true things like engagement farming questions. Examples are asking the audience to recommend their favourite recipe or a good movie to watch on streaming, or a book to read. It’s funny to see long-time twitter hotshots reverting to these tricks starting out on bluesky.
I’m seeing a lot more people starting to point out, like I did last month, that the block lists circulating for Bluesky are questionable. If Bluesky is a decent platform that’s being managed well, you shouldn’t need to pre-block anyone like you did on Twitter to avoid being bombarded by it. All you should need to do is not follow, and unfollow anyone who’s reposting garbage stuff. And save the block button for nuisances who are deliberately trolling.
The other day something disappointing happened on Bluesky and I haven’t even been using it that much, though I’ve had the account for almost a year maybe. I was following someone on social media for years who posted a lot of nature content. And when they moved to Bluesky, then I followed them on Bluesky only to find the other day they were reposting “clever” posts by the author hotshot guy who a few years ago sent his alt-right fans after me. This famous guy posted a screenshot of some post of mine and held me up as an example of A Bad Person Online for criticizing a big shot famous person with a big following and hobnobbing with all the fancy people. I criticized a comment he made for its seemingly thoughtless disregard for disabled and high risk people. It’s apparently worse to criticize someone than for someone to be thoughtlessly cruel. So this guy’s alt-right type followers were for weeks telling me to commit suicide, saying gross things to me in DMs, and even harassing unwitting followers of mine, and I didn’t even know why at first, someone had to inform me of what had happened and why I was suddenly getting the mass trolling. This fancy author also accused me of “silencing” this bigshot scientist off of twitter, despite his huge platform, by merely voicing my concerns, as someone with no such platform. At least one woman with a huge platform backed him up too, even though she surely knew about the sexist harassment I was enduring because of all this. It was very disappointing. The thing is, this guy on bluesky who I was probably retweeting back on twitter, was probably also retweeting that horrid person who did that to me all the while, and I just didn’t know all that time because I had that author guy blocked. So here I was reposting content from someone who was boosting this gross guy, a published author with a huge following, who’d sent his legions of fans, mostly alt-right new atheist covid contrarian types, to come after me.
My point is that all the influencers, as well as the toxic people on twitter are moving over to bluesky because that’s where their targets are after all. They have other places where they congregate for their cozy community, and it’s not the open social media. Community activism doesn’t happen on the open unmoderated or lightly moderated anonymous social media with people prioritizing likes and subscribes and followers and attention farming. And posting online is not activism. Don’t rely on parasocial relationships with big shots. And it’s true that smaller groups in more moderated spaces are going to be more conducive to making friends – or plans. There’s a reason people form and like small chat groups. And also a reason why larger groups and forums need to have enforced rules.
Maybe over the past couple years if you’ve been on bluesky, it seemed like a more closed system. And nice in comparison to twitter because twitter is a total shitshow and everyone was boiled slowly like the apocryphal frog in the pot, so many people still don’t realize how bad it’s gotten. And bluesky at least has some moderation - and more importantly up until recently it was inhabited by primarily early adopters for a period of time, which creates a certain self selection of people. But it’s not going to be better just because. All the problems are migrating there, and the bots and sock puppets and troll farms will soon be in full operation there as well. The only benefit is that hopefully they won’t close down access to the data so that infosec researchers have access to it to analyse it and people who are interested will be able to find out.
There is no safe open social media platform, and arguably nothing that’s truly safe online. People follow "popular" gross violent people all the damn time - many times because they have no idea about many of the bad things because the app only shows people what they want to see and avoids showing people stuff that would make them disengage and close out.
All these platforms are all manipulated, internally and externally in some way. And they all seem to tend to be a diversion from better things because a large inherent priority is keeping people on the platform.
I realize people use them as a way to connect and advertise, and that makes sense, my point isn’t that everyone should just give up on social media and that everyone needs to go back to privately hosted blogs or bare bones email lists and RSS readers. The point is to know how these platforms go wrong, and avoid the pitfalls, and avoid letting any app become a pointless time sink. Though I do know people with full lives who’ve never had any accounts on any social media, so that is an option for many. Also, why not start a newsletter or blog of your own if you might have something important or interesting to communicate? You might be surprised that there are people interested.
I receive some interesting email replies and comments to my substack post emails. And at least when I see these emails in my inbox, I know it’s likely not just gonna be about sick burns for an audience, because it’s an email to me — so it’s typically someone genuinely interested in telling me about something, or asking about something, or at least just sounding off.
There’s going to be a lot to sound off about when even more of the information landscape is taken over by scammy crypto stuff and AI generated garbage.
I suggest writing to elected reps to complain about it first, before posting to social media. But maybe we’ll still see you on the next geocities.
(crossposted from my substack)
#geocities#twitter#social media#bluesky#elon musk#crypto scams#AI slop#the internet of fakes#scams#online marketing#target marketing#data collection#attention economy#online trolls#paid trolls#botnets#social media manipulation#weaponisation of everything#letters to reps#substack#platforms#RSS#blogging
1 note
·
View note
Text
Effective Strategies for Handling Malware
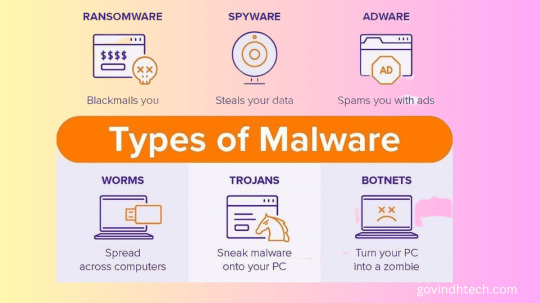
Malware history is long due to its volume and variety. Instead, here are some notorious malware moments.
1966: Malware theory
Mathematician and Manhattan Project contributor John von Neumann developed the idea of a program that could replicate and propagate throughout a system when the first modern computers were produced. Posthumously published in 1966, Theory of Self-Reproducing Automata is the theoretical foundation for computer viruses.
1971: Crawler
Within five years of John von Neumann’s theoretical work, Bob Thomas produced Creeper, an experimental software that moved between ARPANET computers, a predecessor to the Internet. His colleague Ray Tomlinson, the email inventor, adapted the Creeper program to copy itself between computers. Thus began the first computer worm.
Although Creeper is the first known worm, it is not malware. As a proof of concept, Creeper only displayed the whimsical message: “I’M THE CREEPER : CATCH ME IF YOU CAN.” The following year, Tomlinson created Reaper, the first antivirus software designed to delete Creeper by moving across the ARPANET.
Elk Cloner virus, 1982
Rich Skrenta created the Elk Cloner program at 15 as a prank. Skranta was known to change games and other software shared in his high school’s computer club, so many members refused to take disks from the prankster.
Skranta created the first Apple computer virus to change disk software he couldn’t access. Elk Cloner, a boot sector virus, infected Apple DOS 3.3 and copied itself to the computer’s memory from an infected floppy drive. Elk Cloner would transfer itself to an uninfected disk used later in the machine and spread to majority of Skranta’s friends. Elk Cloner could accidentally erase floppy disks while malignant. The beautiful message read:
ELK CLONER:
THE PROGRAM WITH A PERSONALITY
IT WILL GET ON ALL YOUR DISKS
IT WILL INFILTRATE YOUR CHIPS
YES IT’S CLONER!
IT WILL STICK TO YOU LIKE GLUE
IT WILL MODIFY RAM TOO
SEND IN THE CLONER!
1986 Brain virus
On the ARPANET, the Creeper worm could propagate across computers, although most malware was spread via floppy disks like Elk Cloner before the Internet. Elk Cloner affected one little computer club, but the Brain infection spread globally.
Brain, the first IBM Personal Computer virus, was created by Pakistani medical software distributors and brothers Amjad and Basit Farooq Alvi to prevent copyright theft. To prevent software copying, the virus was designed. Brain would tell pirates to phone the brothers for the vaccination when installed. Underestimating how extensive their piracy problem was, the Alvis received their first call from the US and many more from throughout the world.
1988: Morris Worm
Another malware forerunner, the Morris worm, was constructed as a proof-of-concept. The worm was more effective than MIT student Robert Morris expected, unfortunately. Internet access was limited to 60,000 machines, largely in colleges and the military. The worm, designed to exploit a Unix backdoor and stay secret, quickly copied itself and infected 10% of networked machines.
Because the worm transferred itself to other computers and frequently on infected machines, it unwittingly ate up RAM and froze many PCs. Some estimates put the damages in the millions as the first widespread internet strike. Robert Morris was the first US cybercriminal convicted of cyber fraud.
1999: Melissa worm
Melissa proved how rapidly malware can spread via email a decade later, infecting an estimated one million email accounts and at least 100,000 office machines. The fastest-spreading worm of its time, it overloaded Microsoft Outlook and Exchange email servers, slowing more than 300 corporations and government agencies, including Microsoft, the Pentagon’s Computer Emergency Response Team, and 250 others.
2000: ILOVEYOU virus
When 24-year-old Philippines resident Onel de Guzman couldn’t afford dialup internet, he created ILOVEYOU, the first significant piece of malware, to collect passwords. The attack is early social engineering and phishing. De Guzman exploited psychology to exploit curiosity and trick individuals into downloading love letter-like email attachments. De Guzman remarked, “I figured out that many people want a boyfriend, they want each other, they want love.
Aside from stealing passwords, the worm erased information, cost millions in damages, and briefly shut down the UK Parliament’s computer system. De Guzman was detained but acquitted since he had not breached any local laws.
2004: Mydoomworm
Email helped the Mydoom malware self-replicate and infect computers worldwide, like ILOVEYOU. Upon infection, Mydoom would commandeer a victim’s machine to send new copies. Mydoom spam once made up 25% of all emails sent worldwide, a record that’s never been broken, and caused $35 billion in losses. It remains the most financially devastating malware, adjusted for inflation.
Mydoom uses compromised machines to establish a botnet and launch DDoS assaults in addition to hijacking email programs to infect as many systems as possible. The cybercriminals behind Mydoom have never been captured or identified, despite its impact.
2007, Zeus virus
In 2007, Zeus attacked home computers via phishing and drive-by-downloads, demonstrating the dangers of a trojan-style malware that can unleash multiple unwanted programs. In 2011, its source code and instruction manual leaked, benefiting cybersecurity experts and hackers.
2013, CryptoLocker ransomware
CryptoLocker, one of the earliest ransomware attacks, spread quickly and used sophisticated asymmetric encryption. CryptoLocker from Zeus-infected botnets systematically encrypts PC data. If the infected PC is a library or office client, shared resources are targeted first.
The authors of CryptoLocker demanded two bitcoins, worth $715 USD, to decrypt these materials. Fortunately, in 2014, the Department of Justice and international agencies took control of the botnet and decrypted hostage data for free. Unfortunately, basic phishing tactics spread CyrptoLocker, a persistent danger.
Emotet trojan 2014
The Emotet trojan, termed the “king of malware” by Arne Schoenbohm, head of the German Office for Information Security, is a polymorphic spyware that is difficult to eradicate. Polymorphic malware creates a harmful variation by subtly modifying its code each time it reproduces. Polymorphic trojans are harder to detect and block, making them more harmful.
The Zeus trojan and Emotet are modular programs that spread additional malware through phishing campaigns.
Mirai botnet (2016)
Malware evolves with computers, from desktops to laptops, mobile devices, and networked devices. Smart IoT gadgets introduce new vulnerabilities. College student Paras Jha created the Mirai botnet, which infected many IoT-enabled CCTV cameras with inadequate protection.
The Mirai botnet, meant to assault gaming servers for DoS attacks, proved more powerful than Jha expected. It targeted a major DNS provider and shut out large parts of the eastern US from the internet for nearly a day.
2017: Cyberspionage
Malware had been used in cyber warfare for years, but 2017 was a banner year for state-sponsored assaults and virtual espionage, starting with Petya. Phishing disseminated Petya ransomware, which was deadly but not infectious until it was transformed into the NotPetya wiper worm, which destroyed user data even if ransom was paid. The WannaCry ransomware infection hit several high-profile European targets that year, including Britain’s National Health Service.
NotPetya may have been modified by Russian intelligence to strike Ukraine, and WannaCry may be linked to North Korean adversaries. What links these malware attacks? The National Security Agency discovered Eternalblue, a Microsoft Windows exploit, which enabled both. Microsoft found and fixed the weakness, but they chastised the NSA for not reporting it before hackers exploited it.
Ransomware-as-a-Service 2019
Ransomware malware has grown and declined in recent years. Though ransomware attacks are declining, hackers are targeting more high-profile targets and wreaking more harm. Recently, Ransomware-as-a-Service has become a worrying trend. RaaS may be purchased on dark web marketplaces and allows skilled hackers to launch ransomware attacks for a price. Previous virus attacks needed extensive technical skill, but RaaS mercenary groups empower anyone with evil will and money.
Emergency in 2021
In 2019, hackers broke into security staffing agency Allied Universal and threatened to leak their data online in the first high-profile double-extortion ransomware attack. Due to this extra layer, Allied Universal would still suffer a data breach even if they could decode their information. This incident was notable, but the 2021 Colonial Pipeline attack was more severe. The Colonial Pipeline supplied 45% of eastern US gasoline and jet fuel. The multi-day attack affected the east coast’s public and private sectors and caused President Biden to proclaim a state of emergency.
National emergency, 2022
Though ransomware attacks may be reducing, highly targeted and efficient operations remain a scary menace. Ransomware attacks in 2022 crippled the ministry of finance and civilian import/export firms in Costa Rica. Following an attack, the healthcare system went offline, affecting potentially every citizen. Costa Rica declared the first national state of emergency after a cyberattack.
Read more on Govindhtech.com
3 notes
·
View notes
Text
youtube
#NationSquid#video essay#spam#webcore#old web#Internet#ARPANET#Gary Thuerk#Monty Python's Flying Circus#meme#e-marketing#python#social engineering#malware#keylogger#Youtube#botnet#botnets
1 note
·
View note
Text
Politie haalt honderden servers offline
Bij nog zo’n grote internationale actie, Operation Endgame, zijn wereldwijd meer dan driehonderd servers offline gehaald. Zestig daarvan stonden in datacentra in Nederland. Met het oprollen van de servers werden meerdere botnets neergehaald. Behalve de servers is voor 3,5 miljoen euro aan cryptovaluta in beslag genomen. Twintig verdachte cybercriminelen uit Rusland zijn op de Europese…
0 notes
Text
Routeur D-Link attention aux botnets Ficora et Capsaicin, ça peut faire mal !
Depuis plusieurs mois, des experts en cybersécurité ont observé une augmentation inquiétante des attaques ciblant certains modèles de routeurs D-Link. Deux botnets, nommés Ficora et Capsaicin, exploitent des failles de sécurité pour transformer ces routeurs en outils d'attaques DDoS. Bien que ces vulnérabilités soient connues depuis plusieurs années, elles continuent d’être exploitées, mettant en lumière l'importance des mises à jour et des bonnes pratiques en matière de sécurité.

Routeur D-Link attention aux botnets Ficora et Capsaicin, ça peut faire mal ! - LaRevueGeek.com
#botnets#routeurs D-Link#attaques ciblées#vulnérabilités de sécurité#DDoS#mise à jour sécurité#cybersécurité#failles de sécurité#attaques réseau
0 notes
Text
BE ON THE LOOKOUT FOR BOTNETS USA
#botnet#botnet botnetting itself#botnet botnetting botnets like it#be on the lookout for botnets#be#on#the#lookout#for#botnets#cybersecurity#llama facebook meta#wikipedia#google gemini#microsoft bing copilot#baidu#yandex#dogpile.com#metacrawler#yahoo.com#taylor swift#original timeline#pi day#martin luther king jr#fashoing#melanie martinez#michelle obama#caprica#alice
18 notes
·
View notes
Text
Researchers Shut Down Cryptomining Botnets by Exploiting Pool Protocols

Cybersecurity experts developed two clever methods that cripple cryptomining botnets by submitting invalid shares or flooding attacker wallets, forcing mining pools to ban critical components and halt operations.
Researchers from Akamai discovered that exploiting weaknesses in the Stratum mining protocol allows defenders to ban mining proxies or attacker wallets. One technique, called “bad shares”, submits invalid mining results via the proxy to get it banned, dropping victim CPU usage from 100% to zero. The other floods attacker wallets with logins to trigger temporary bans, disrupting mining campaigns and forcing attackers to overhaul or abandon their setups. These methods effectively cut the profits of cryptominer botnets, mainly targeting Monero but extendable to other coins.
Sources: The Hacker News | Akamai
4 notes
·
View notes
Text
You missed it! Threat Actors simple paths into your network.
On December 3rd, 2024, six cybersecurity organizations published Enhanced Visibility and Hardening Guidance for Communications Infrastructure, detailing simple paths threat actors use to penetrate networks. Most people I talk to say, “This is nothing new.” “We’ve heard it all before.” “These are all Best Common Practices (BCPs); everyone should have deployed them already!” Do not ignore these…

View On WordPress
#Advanced Persistent Threat#APT#BCPs#BOTNETs#FTP#iACL#Infrast#Infrastructure ACLs#Living off the Land#malware#Salt Typhoon#Shadowserver Foundation#SNMP#Telnet#TFTP#Typhoon
0 notes
Text
lots of stuff is fake on the internet, no joke, but it is a joke
#pr#advertising#troll farms#sock puppets#chaos agents#agent provocateur#paid trolls#on the internet#influencers#influence#operatives#botnets#bots#fakes#the internet of fakes
1 note
·
View note
Text
Maybe a new anti-union bot came online with imprecise programming.
The internet of fakes.
There will probably be an uptick in anti-union ops online because of the dockworkers strike.
Every now and again, someone with very different priorities and cognition to me will discover a years-old Twitter thread of mine and go through it and reply to every post telling me how great their favorite rapacious multinational corporation is. It's hard to tell whether they're having an episode, or on someone's payroll, or what, but wow, is this ever weird-ass behavior.

Anyway, enjoy this essay from April 2023!
#the internet of fakes#botnets#troll farms#dockworkers#union#anti-union#labor#union busting#psyops#ops
136 notes
·
View notes
Text


Thanks again for stopping by! Be sure to be on the look out for these three on Art Fight! I'll be ready!
23 notes
·
View notes
Text
IOTA BETA MU TERRAN BOTNET CRIMES
CRIMINAL CONTROLLED BOTNET OPERATING USING IBM OR INTERNATIONAL BUSINESS MACHINES OR IOTA BETA MU COMPUTERS OPERATING FROM THE PLANET TERRA
#IOTA BETA MU TERRAN BOTNET CRIMES#CRIMINAL CONTROLLED BOTNET OPERATING USING IBM OR INTERNATIONAL BUSINESS MACHINES OR IOTA BETA MU COMPUTERS OPERATING FROM THE PLANET TERRA#INTERNATIONAL BUSINESS MACHINES#botnet#security advisory#tape based computers replaced more advanced systems to impersonate better computers#crime#criminal#cybersecurity#taylor swift#pi day#martin luther king jr#melanie martinez#michelle obama#caprica#tim kaine
61 notes
·
View notes
Text
"According to a recent report published by the Aargauer Zeitung (h/t Golem.de), around three million smart toothbrushes have been infected by hackers and enslaved into botnets. The source report says this sizable army of connected dental cleansing tools was used in a DDoS attack on a Swiss company’s website. The firm’s site collapsed under the strain of the attack, reportedly resulting in the loss of millions of Euros of business."
108 notes
·
View notes
